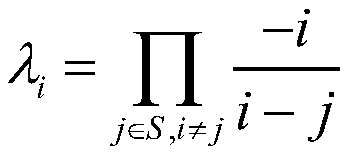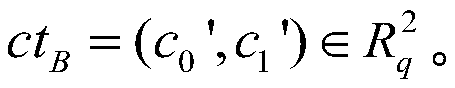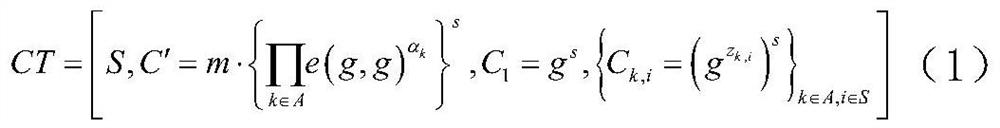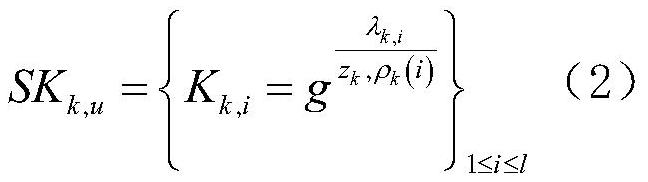Patents
Literature
62results about How to "Achieving verifiability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
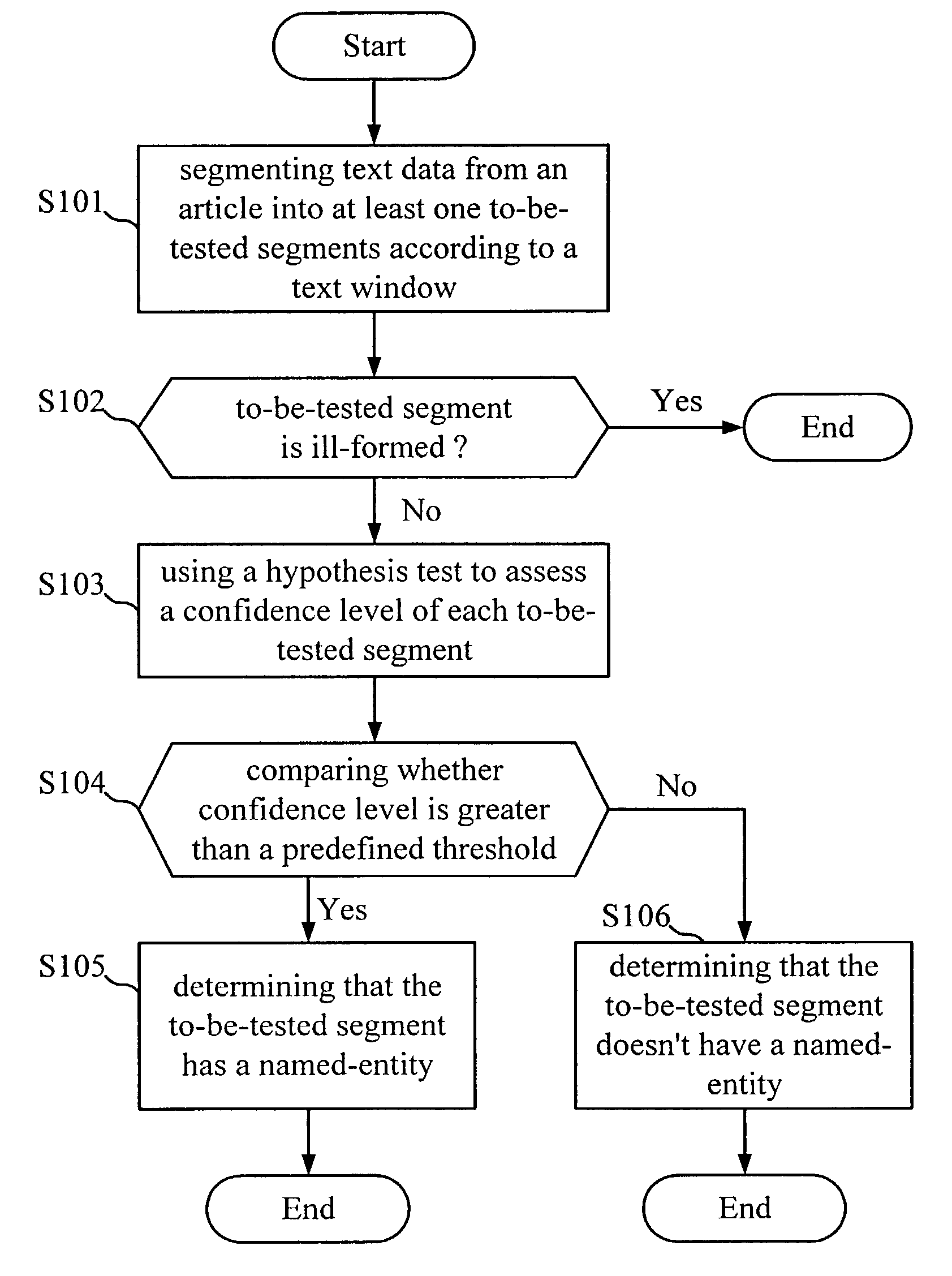
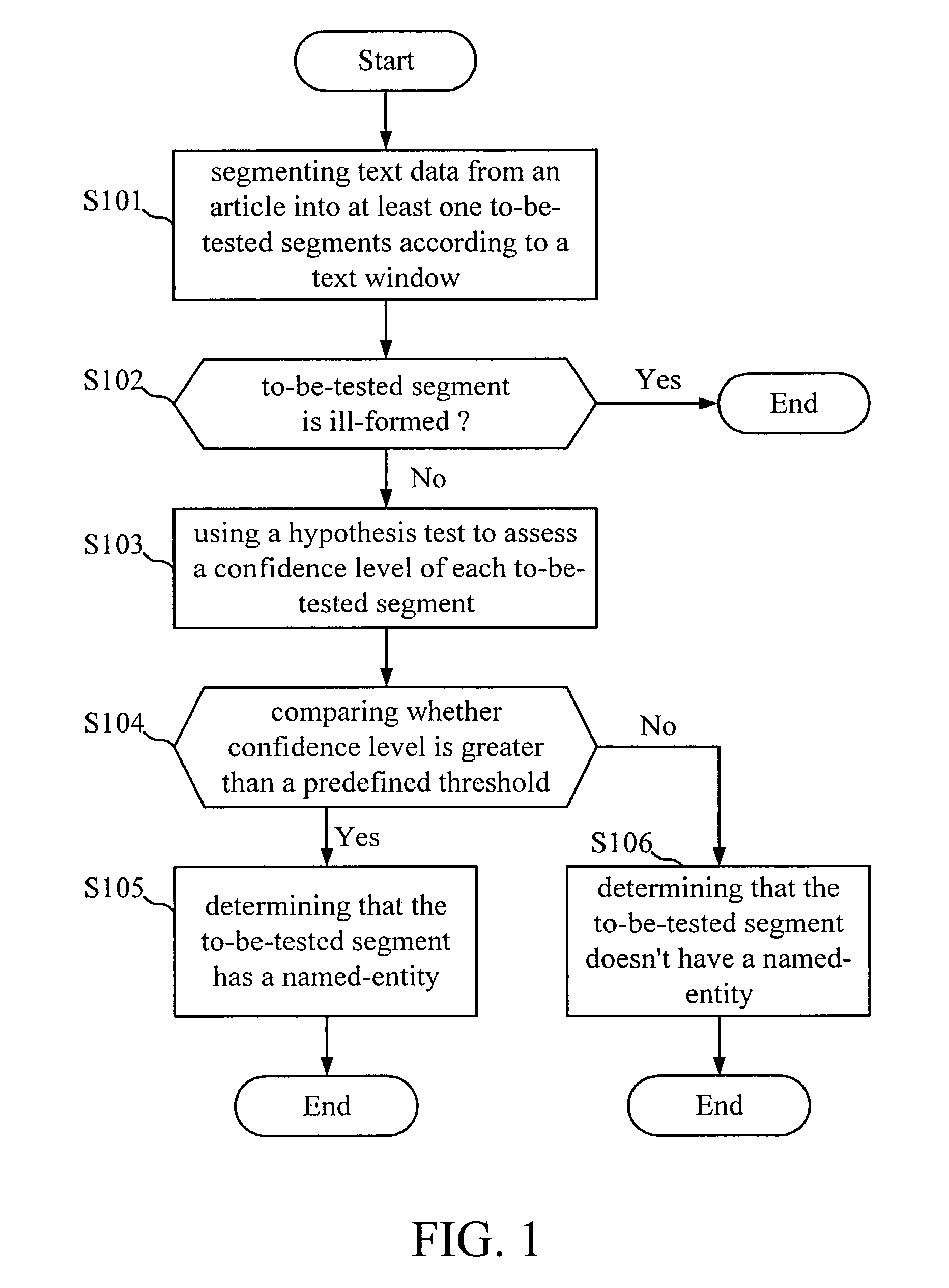
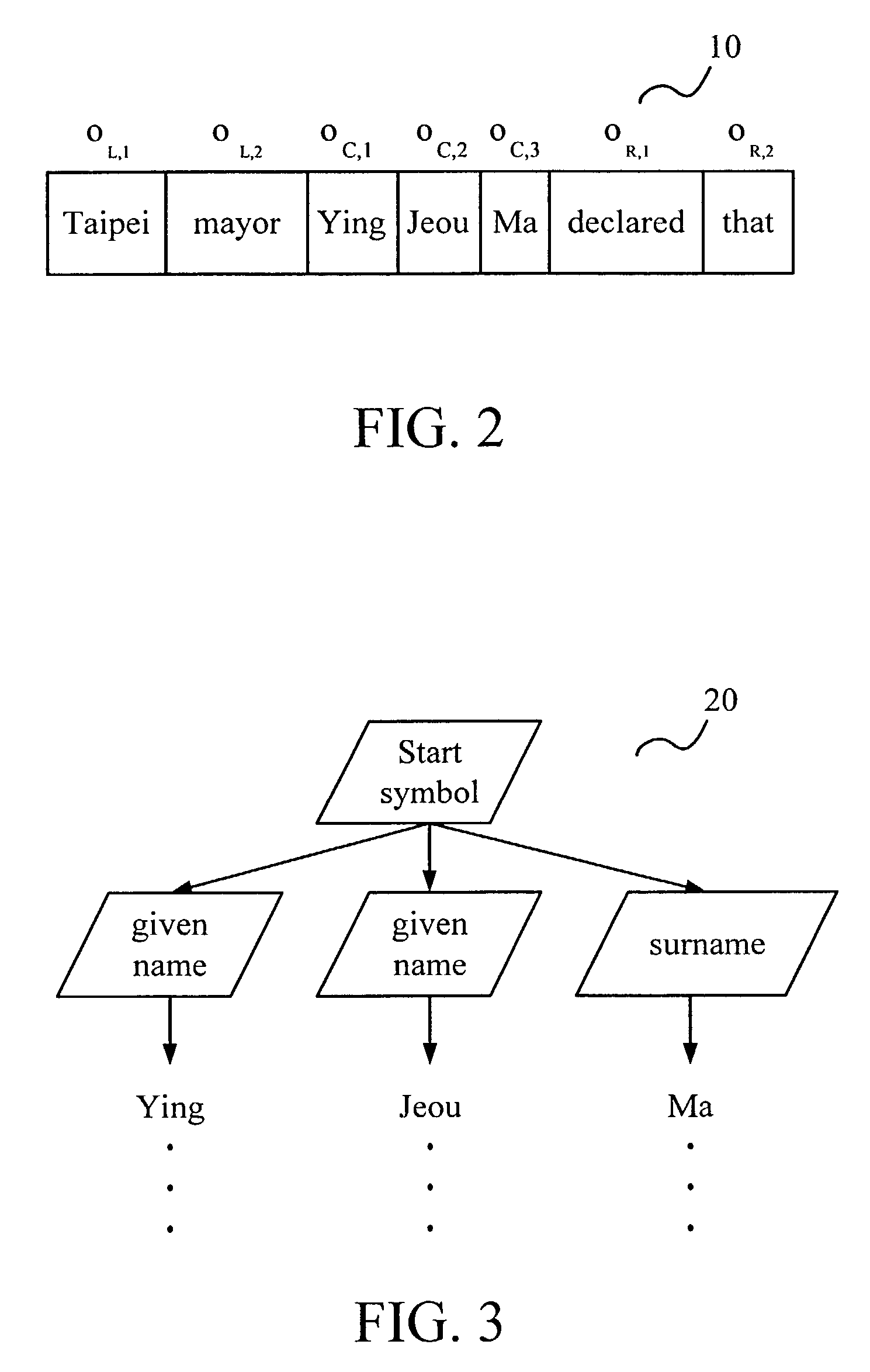
Method for named-entity recognition and verification
InactiveUS7171350B2Easy programmingImprove portabilityNatural language data processingSpecial data processing applicationsPattern recognitionNamed-entity recognition
A method for named-entity (NE) recognition and verification is provided. The method can extract at least one to-be-tested segments from an article according to a text window, and use a predefined grammar to parse the at least one to-be-tested segments to remove ill-formed ones. Then, a statistical verification model is used to calculate the confidence measurement of each to-be-tested segment to determine where the to-be-tested segment has a named-entity or not. If the confidence measurement is less than a predefined threshold, the to-be-tested segment will be rejected. Otherwise, it will be accepted.
Owner:IND TECH RES INST
Intelligent medical service method based on undistinguishable confusion
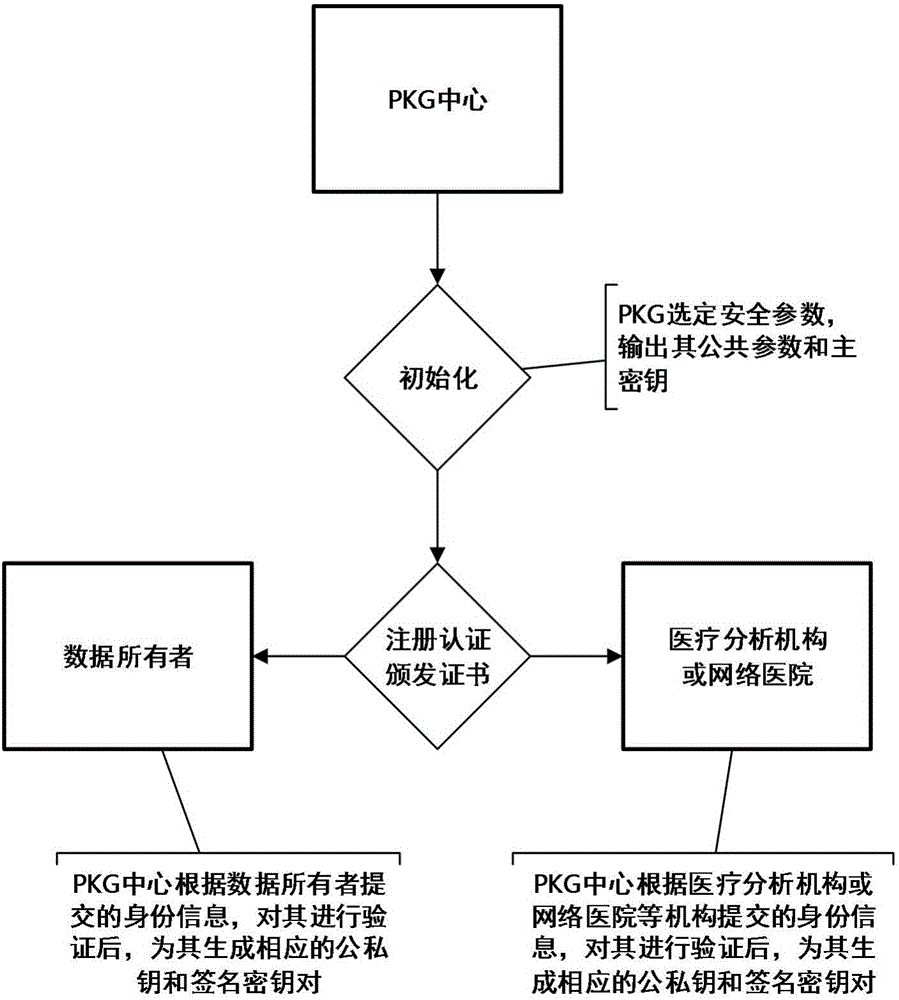
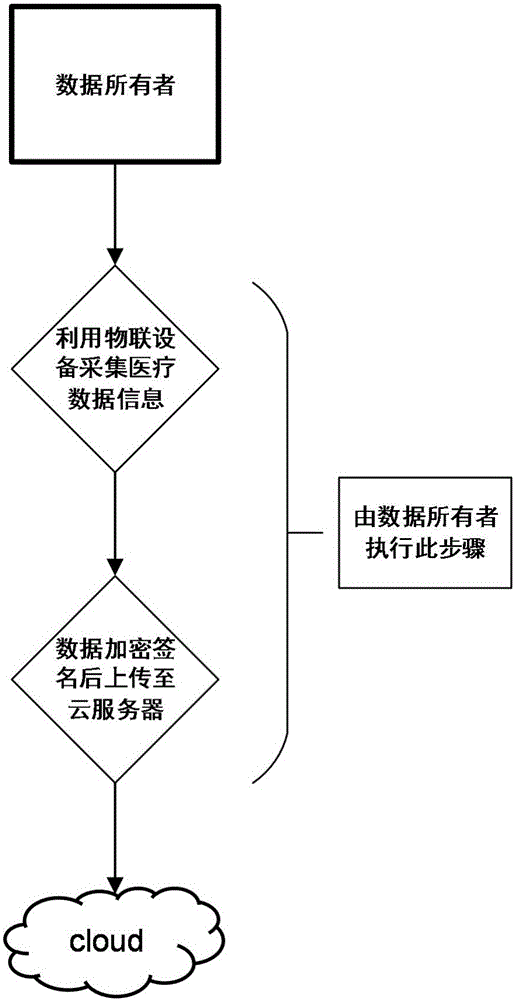
ActiveCN105978854AFlexible Control AllocationAssignment Convenience ControlKey distribution for secure communicationData processing applicationsCiphertextData access
The invention discloses an intelligent medical service method based on undistinguishable confusion, which is characterized in that a data owner independently decides allocation for the medical data access authority through carrying out security symmetric encryption on medical information uploaded to a cloud server; a medical data analysis mechanism carries out confusion on a medical data analysis program by using an undistinguishable confusion technology, the confused program is deployed to the cloud server, and security analysis is carried out on the medical data by using a confusion program so as to acquire a correct medical analysis result; and the access authority of other related mechanisms for a ciphertext can be controlled conveniently without changing the ciphertext structure by using a key sharing scheme. According to the invention, the privacy of data is realized, interaction of keys is reduced, and storage and management of a great number of keys are avoided; the integrity and the effectiveness of data can be verified; and the access type of medical data is decided by the user, the overall structure of an algorithm is not change at the same time, and the expansibility of the scheme is enhanced.
Owner:XIDIAN UNIV
Physical memory isolation method based on RISC-V instruction architecture
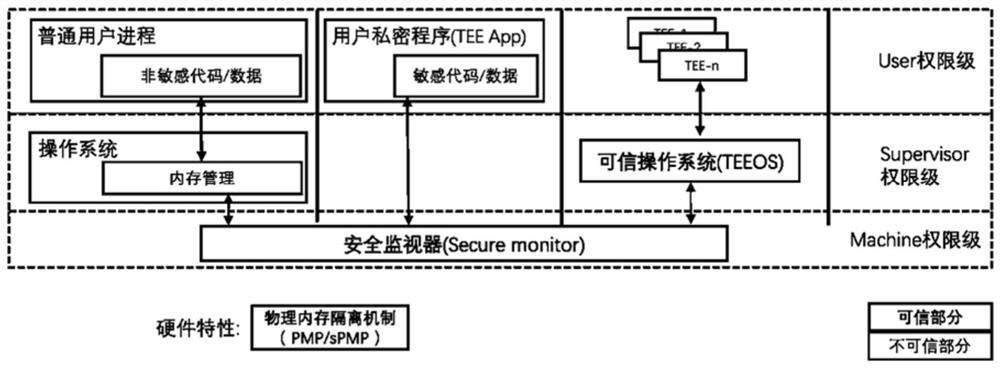
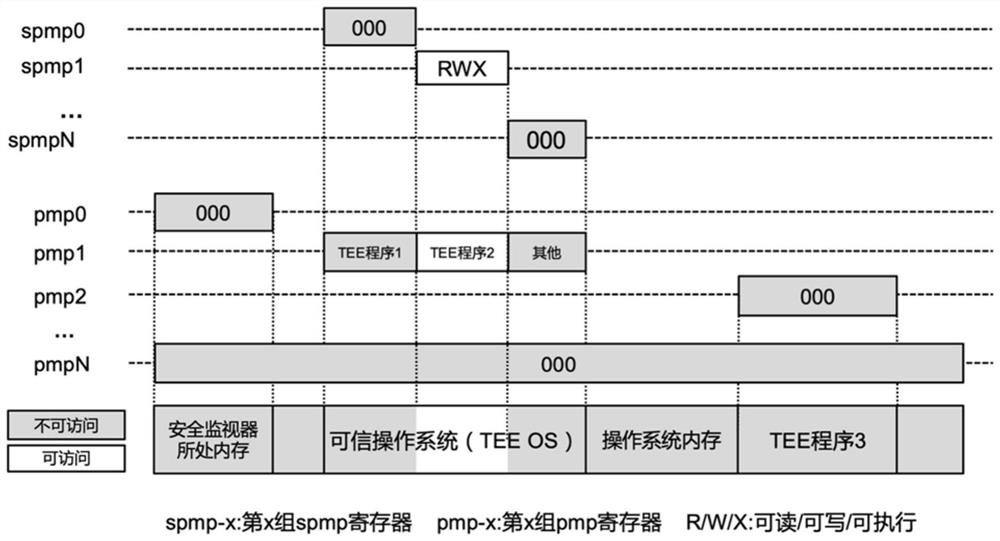
ActiveCN111651778AImprove securityAchieving verifiabilityDigital data protectionInternal/peripheral component protectionComputer architectureEngineering
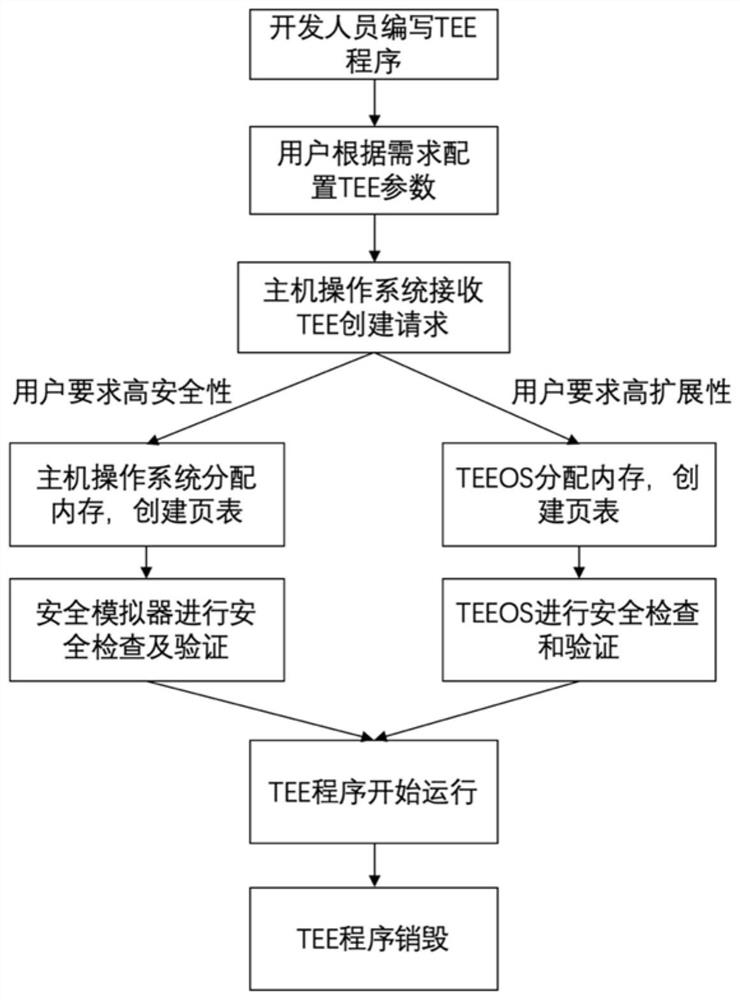
The invention provides a physical memory isolation method based on an RISC-V instruction architecture. According to the method, on the basis of an existing PMP (physical memory isolation) technology capable of being configured by a Machine mode of an RISC-V instruction architecture, an sPMP (physical memory isolation) technology capable of being configured by a Supervisor mode is added; the physical memory isolation technology sPMP depends on a plurality of groups of sPMP registers which can only be read and written by a Machine mode program and a Supervisor mode program. According to the invention, the limitation of the number of security applications of the existing TEE system based on the PMP register set is broken through, and the characteristics of efficient security application starting, efficient security application communication, fine-grained security application memory resource allocation and the like can be provided. Compared with the existing TEE design, the safety and theexpandability of the system are greatly improved.
Owner:SHANGHAI JIAO TONG UNIV
Block chain data processing method, apparatus and device, and storage medium
ActiveCN108804706AAchieving verifiabilityStrengthen the non-tampering featureSpecial data processing applicationsComputer hardwareChain network
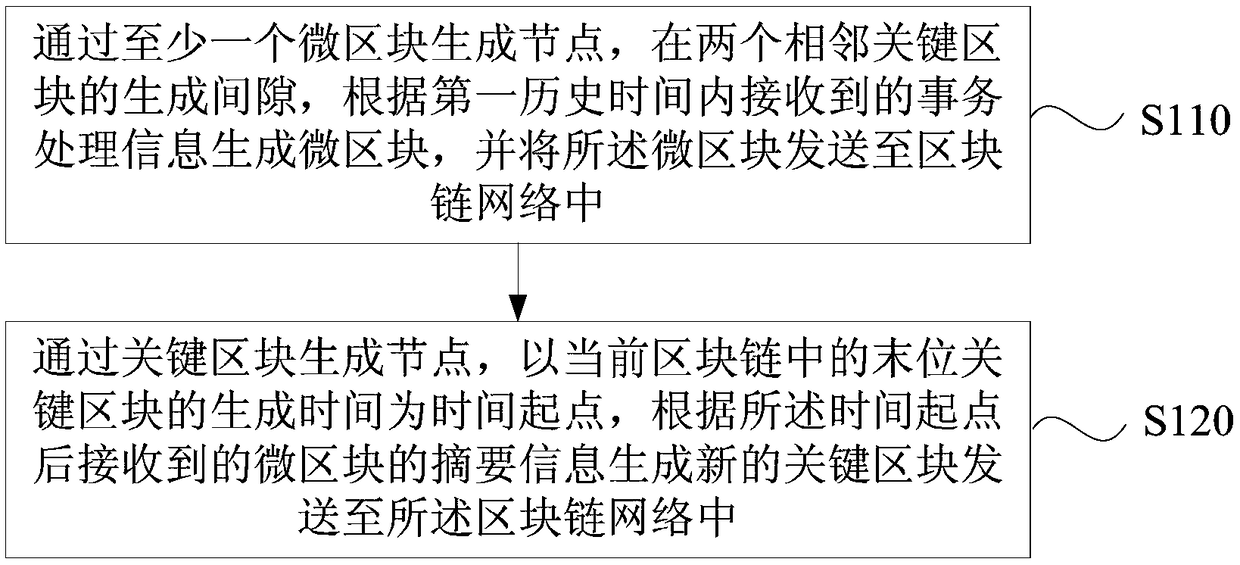
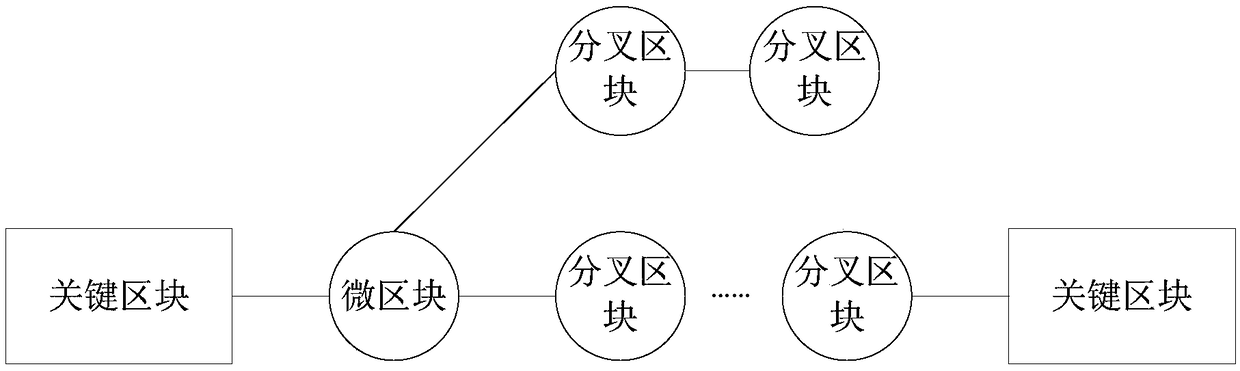
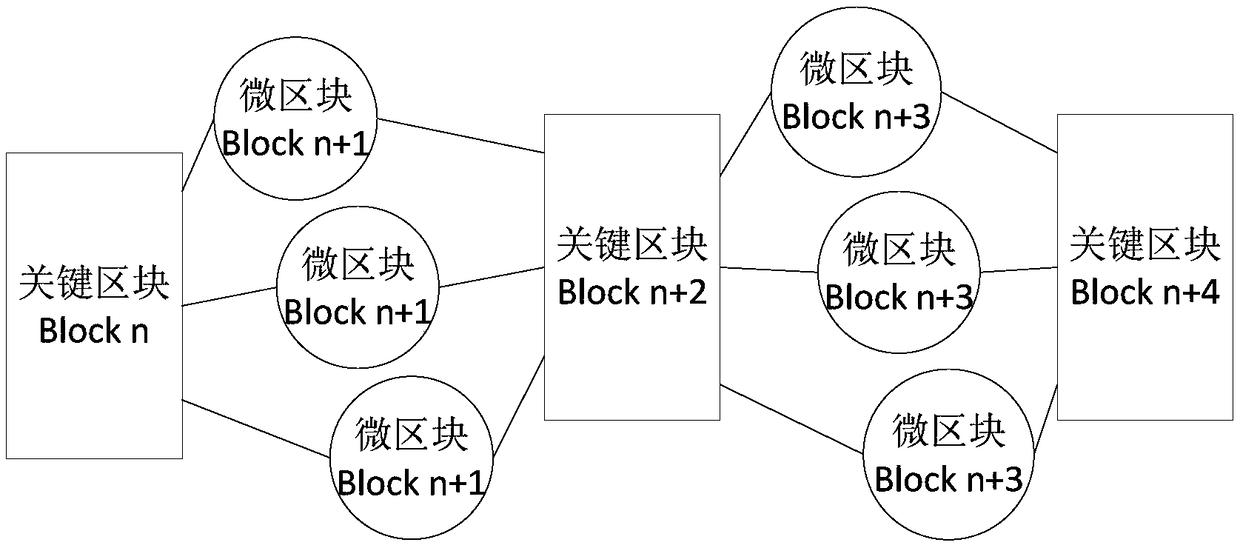
Embodiments of the invention disclose a block chain data processing method, apparatus and device, and a storage medium. The method comprises the steps of generating nodes through at least one micro-block, generating a gap between two adjacent key blocks, generating the micro-blocks according to transaction processing information received within first historical time, and sending the micro-blocks to a block chain network; and generating the nodes through the key blocks, taking generation time of the last key block in a current block chain as a time starting point, generating new key blocks according to abstract information of the micro-blocks received after the time starting point, and sending the new key blocks to the block chain network. According to the technical scheme, the block capacity can be effectively expanded, so that the throughput of the blocks can be increased; the verifiability of the transaction processing information is improved, so that the non-tampering characteristicof the block chain is enhanced; meanwhile, the overall difficulty and the attack difficulty of the block chain are improved, and the probability of system bifurcation is reduced, so that the securityand effectiveness of data in the block chain are ensured.
Owner:SOUTH UNIVERSITY OF SCIENCE AND TECHNOLOGY OF CHINA
Secure Network Extension Device and Method
ActiveUS20120030459A1Improve securityEnhance remote verifiabilityDigital data processing detailsMultiple digital computer combinationsTraffic capacityComputer module
A network extension device comprising a CPU, memory, protected I / O connectable to local controls and peripherals, external communications port, a trusted device connected to the CPU such that it can provide attestation of the network extension device's trusted operation to a connected known external network, and a protected interface connected to at least one network extension module that includes a local network communications port. Optionally, a traffic encryption module may be provided, and the trusted device's attestation may include a check of its operation. Also, a method comprising connecting the network extension device to an external network, performing an operating mode check, causing the network extension device to operate in a mode and perform a security check that correspond to the result, causing the trusted device to attest trusted operation to the external network and thereafter causing the CPU to function fully and permitting access to the external network.
Owner:ANALOG DEVICES INC
Verifiable ideal on-grid threshold proxy re-encryption method and verifiable ideal on-grid threshold proxy re-encryption system
ActiveCN111342976ADetect dishonesty in timeTimely detection of malicious conversion behaviorKey distribution for secure communicationUser identity/authority verificationHomomorphic signatureAlgorithm
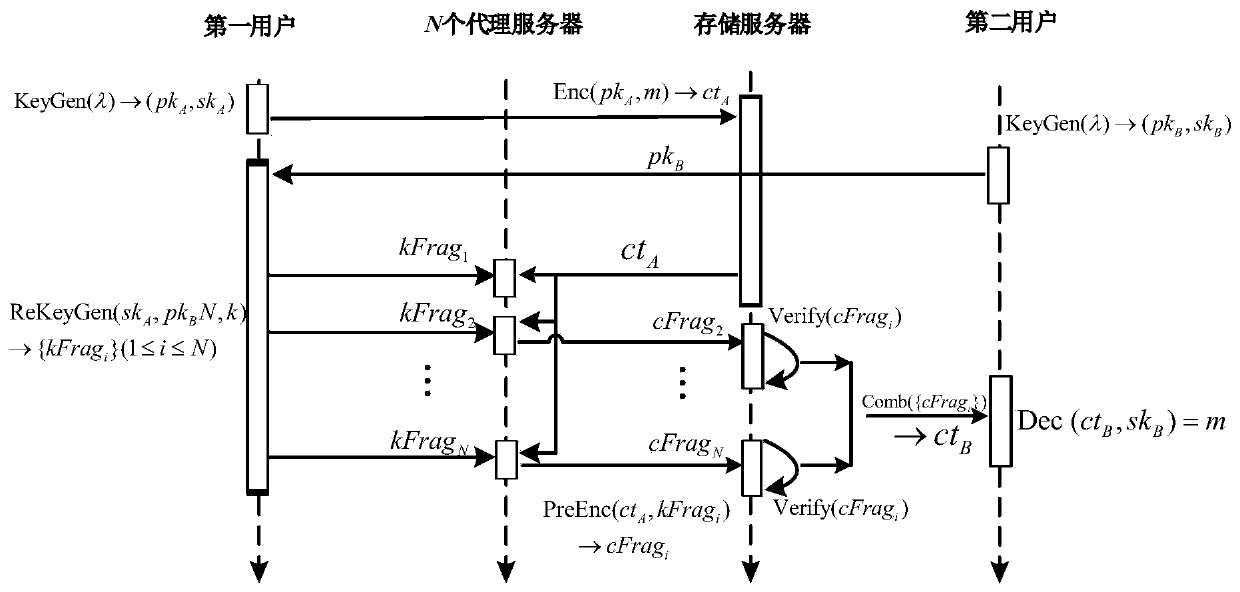
The invention belongs to the technical field of data encryption and privacy protection, and discloses a verifiable ideal on-grid threshold proxy re-encryption method and system, and the method comprises the following steps: generating a first public and private key and a second public and private key through a KeyGen algorithm; encrypting the original message according to the first public key to generate a ciphertext; generating an agent key through a ReKeyGen algorithm according to the first private key and the second public key, dividing the agent key into a plurality of key shares, and signing each key share through a homomorphic signature technology to obtain a plurality of key share signatures; converting the ciphertext into a plurality of ciphertext shares according to the pluralityof key shares, and converting the plurality of key share signatures into a plurality of ciphertext share signatures; verifying the legality of the corresponding ciphertext share according to each ciphertext share signature; combining the legal ciphertext shares into a re-encrypted ciphertext; decrypting the re-encrypted ciphertext according to the second private key to get the original message. According to the invention, the method and system have the advantages of high availability, low trust and strong security, can effectively resist quantum attacks, and is high in encryption efficiency.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Transcoding in data communications
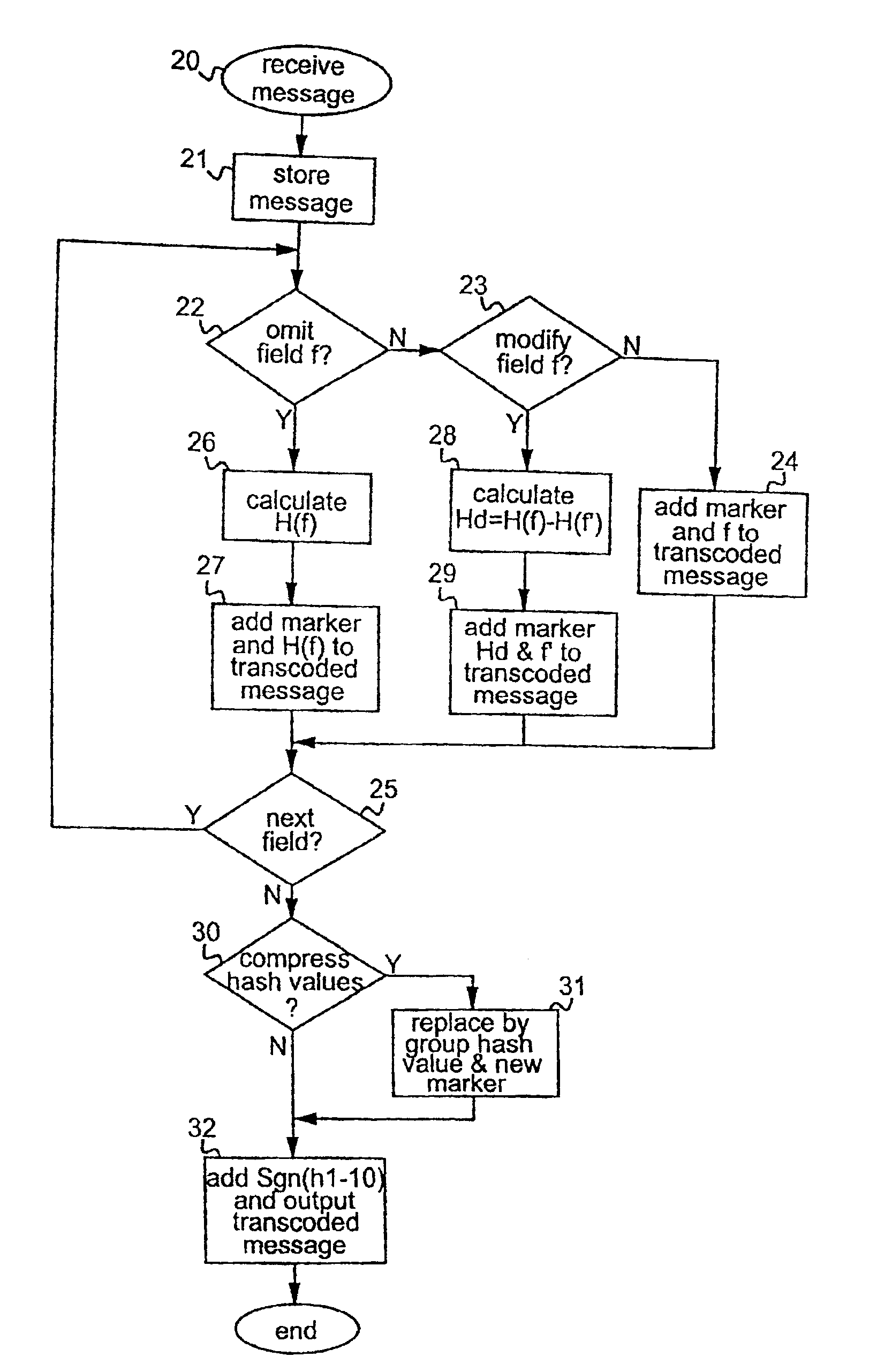
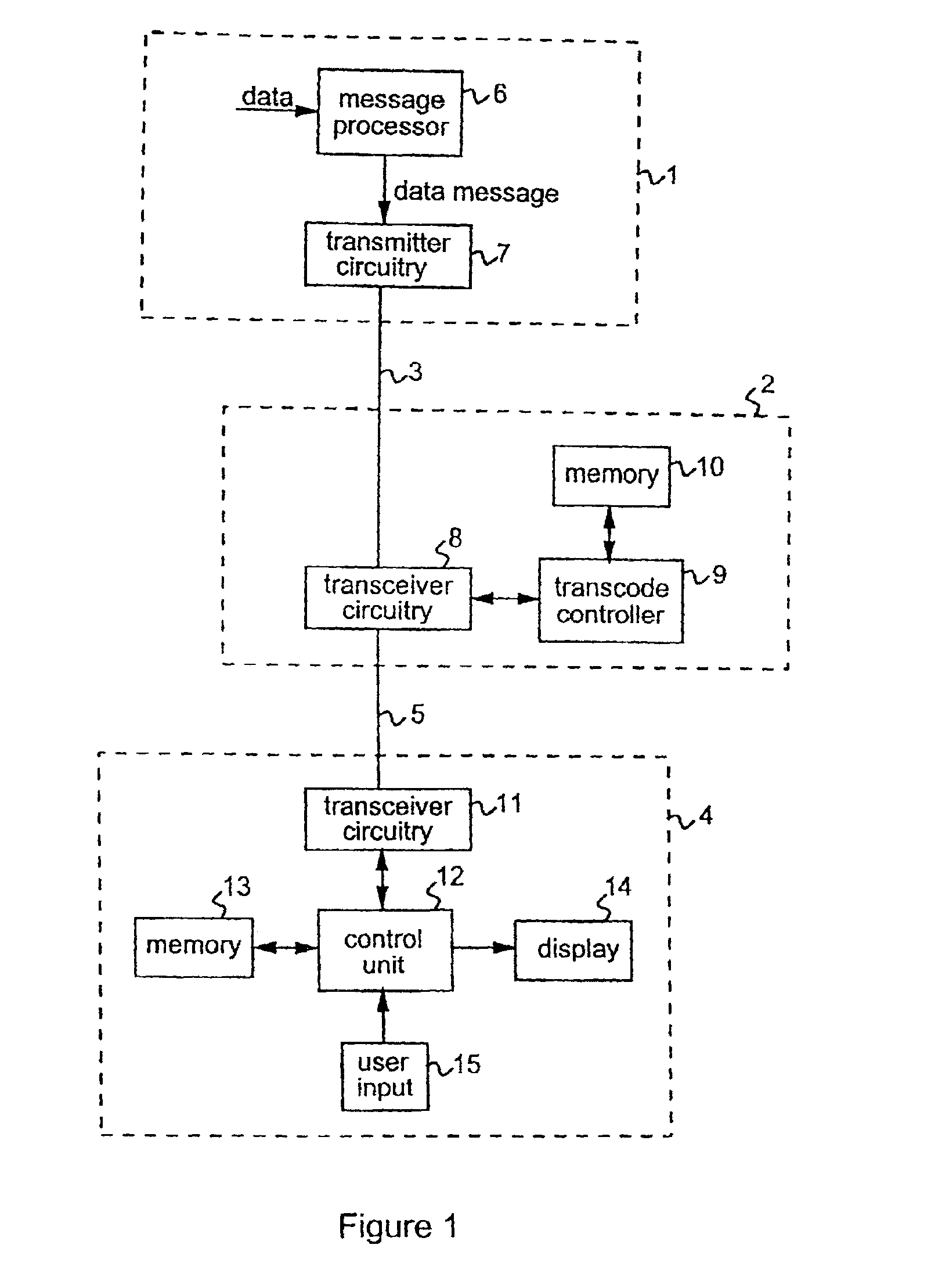
InactiveUS6922778B2Achieving verifiabilityEffective and practicalUser identity/authority verificationCode conversionProgramming languageTranscoding
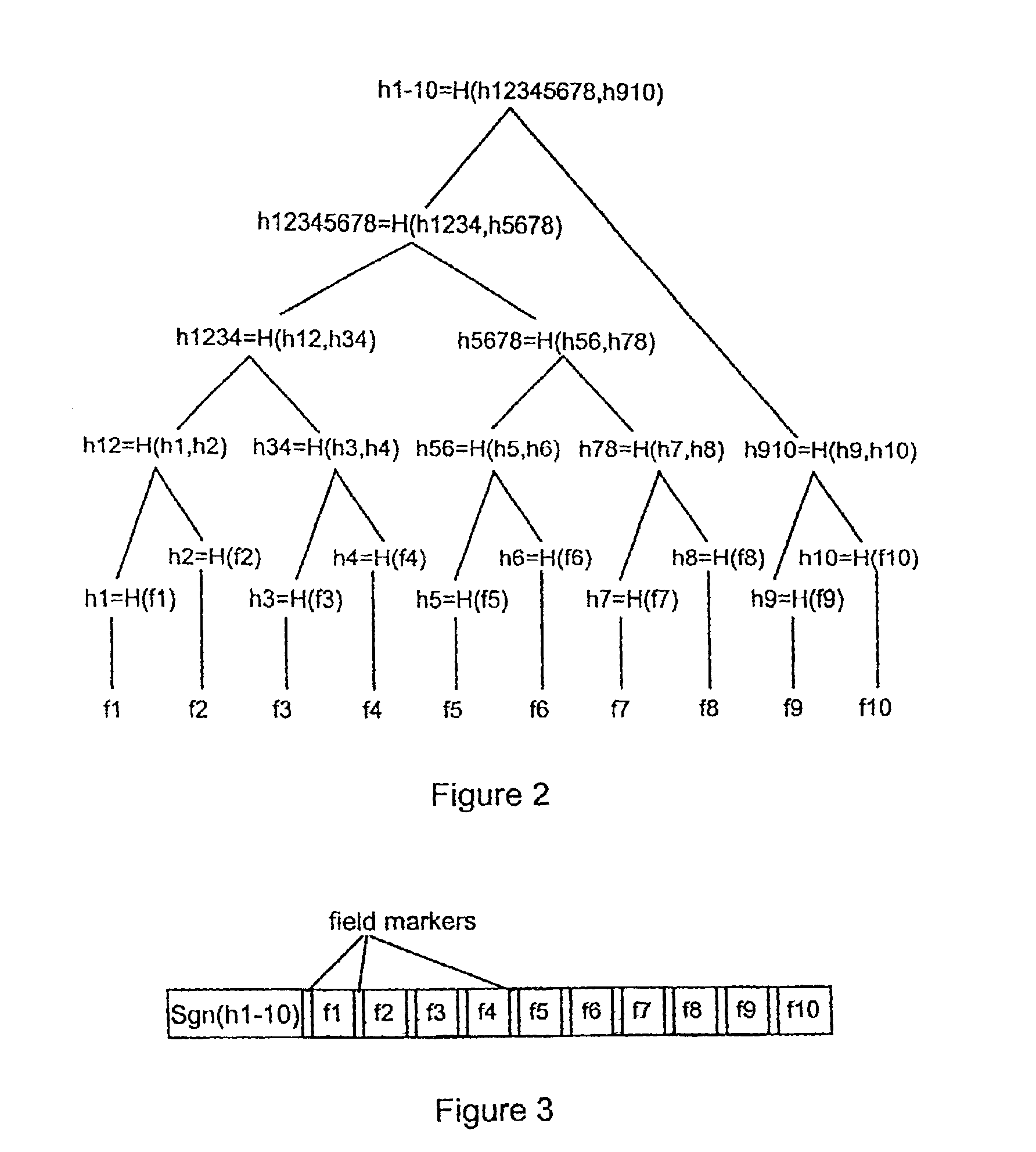
Methods and apparatus are provided for transcoding a data message, comprising a plurality of data fields (f1-f10) and an authentication code (Sgn(h1-10)), to produce a transcoded message for transmission to a destination device (4). The transcoding methods can be applied to such a data message which is received from a source device (1) wherein said data fields (f1-f10) have been coded in accordance with a first coding system, whereby respective data field codes (h1-h10) are generated for said data fields (f1-f10) and a message code (h1-10) is derived from said data field codes (h1-h10), and wherein said message code (h1-10) has been coded in accordance with a second coding system to generate said authentication code (Sgn(h1-10)). For each data field (f1-f10) of the received data message it is decided whether to maintain, modify or omit that field. For a field to be maintained, that field is maintained in the transcoded message. For a field to be omitted, that field is coded in accordance with said first coding system to generate an omitted field code dependent upon the data field code (h) for that field, and that field is replaced by said omitted field code in the transcoded message. For a field to be modified, that field is coded in accordance with said first coding system to generate a modified field code dependent upon the data field code (h) for that field, and that field is replaced by a modified field, comprising modified data (f′) and said modified field code, in the transcoded message. The received authentication code (Sgn(h1-10)) is also included in the transcoded message. Sufficient information is thereby included in the transcoded message to enable the destination device to verify the transcoding operation.
Owner:INT BUSINESS MASCH CORP
Secure outsourcing algorithm for large-scale matrix operation
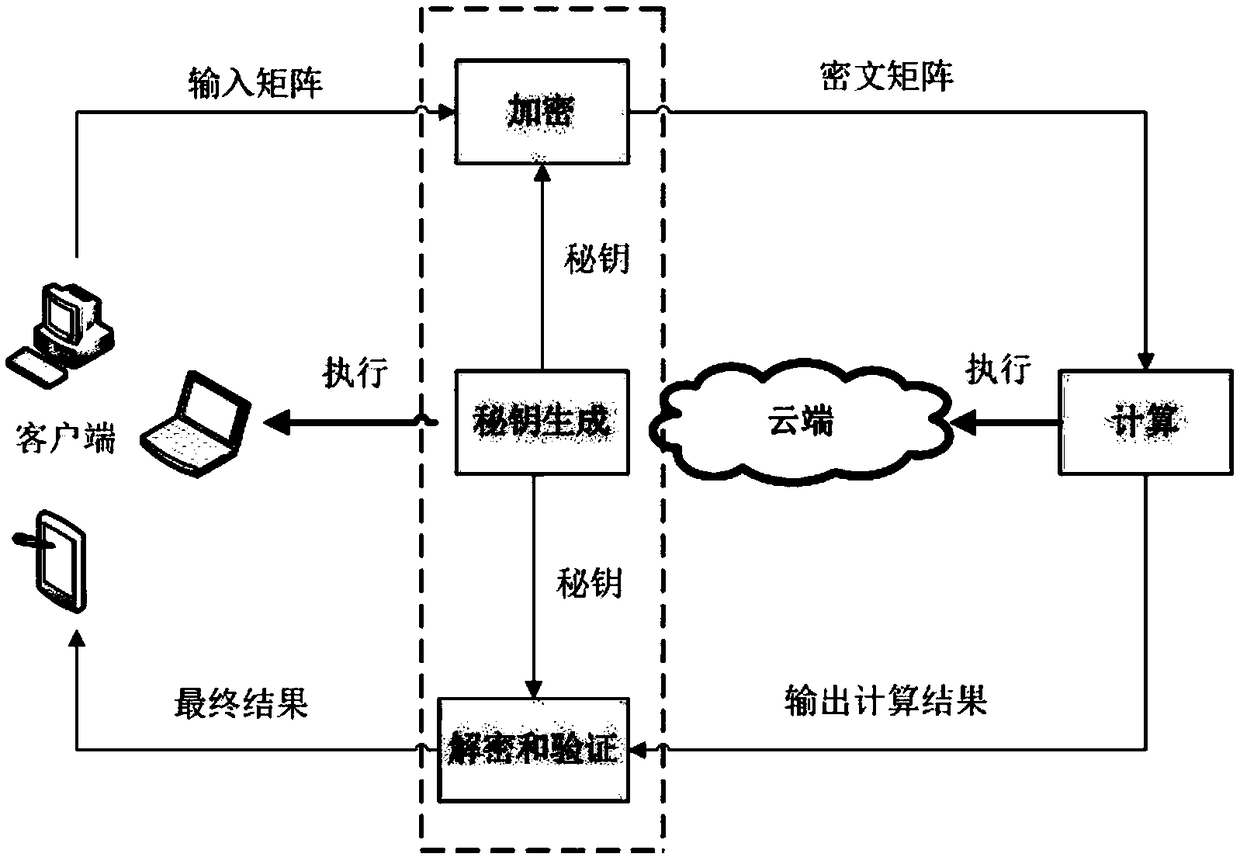
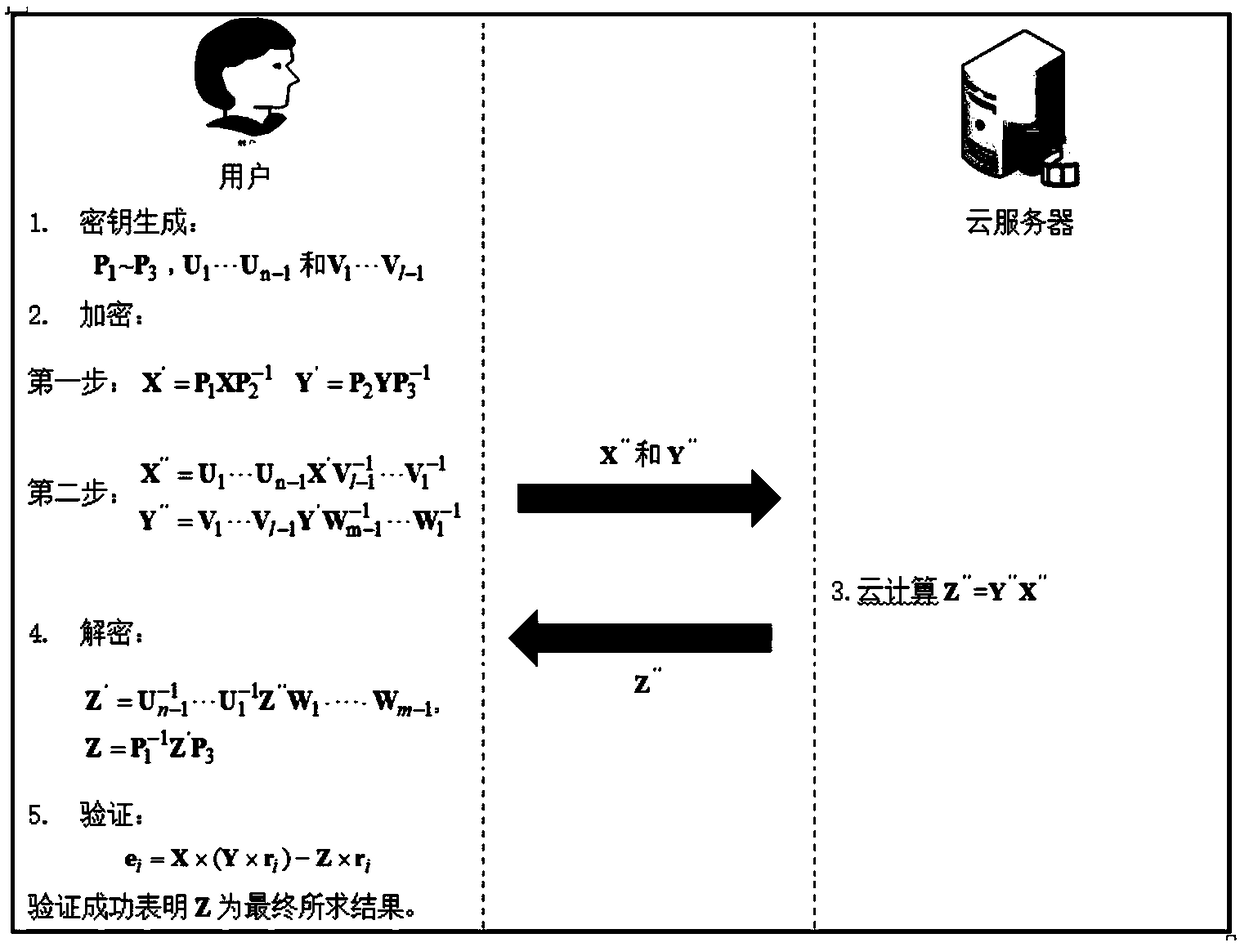
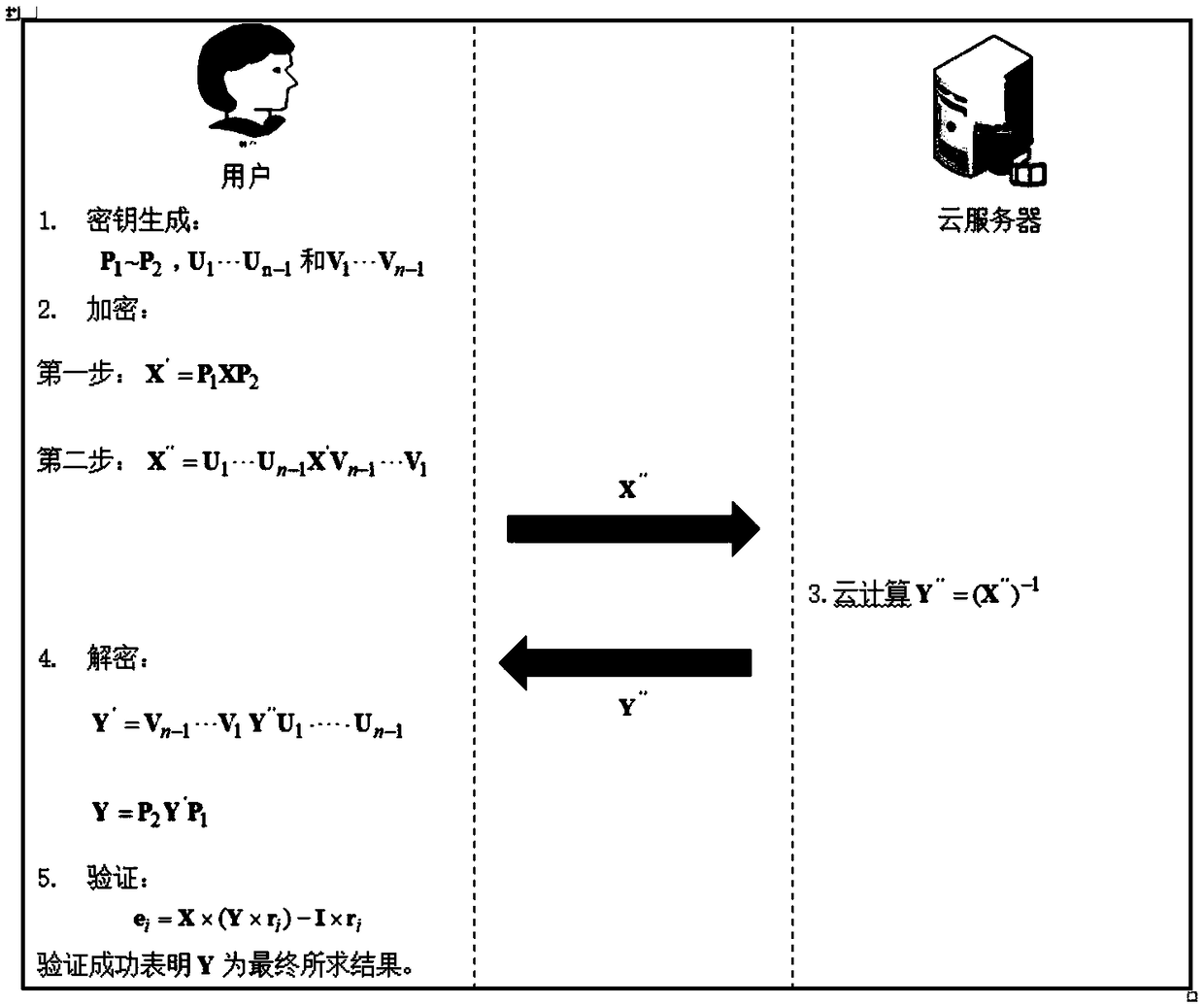
ActiveCN109460536AAchieve privacyAchieving verifiabilityTransmissionManufacturing computing systemsMatrix multiplicationComputer science
The invention provides a secure outsourcing algorithm for large-scale matrix operation, which adopts a continuous sparse 11-module matrix transformation encryption technology with a simple structure.On the one hand, multiple sparse transformations can encrypt dense matrices continuously, thus protecting the statistical information of specific elements of the original matrices; On the other hand,the combinability of matrix multiplication and the simplicity of sparse matrix structure ensure the high efficiency of matrix encryption and decryption. In addition, the technology has good universality, suitable for outsourcing MM, MIC, MDC and other matrix operations, giving good consideration to the privacy of input and output, high efficiency verifiability and efficiency.
Owner:QINGDAO UNIV
Mobile terminal E-voting method based on facial feature recognition and system thereof
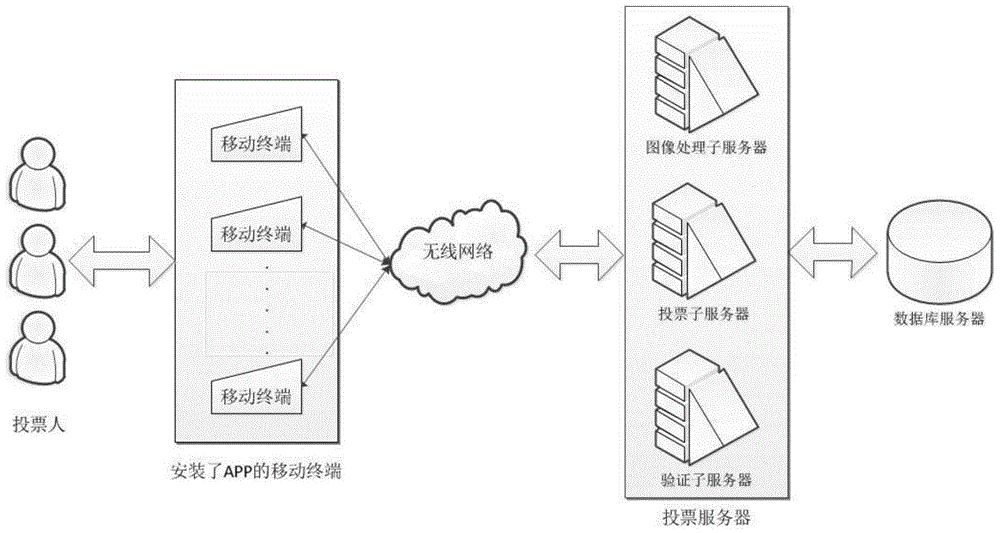
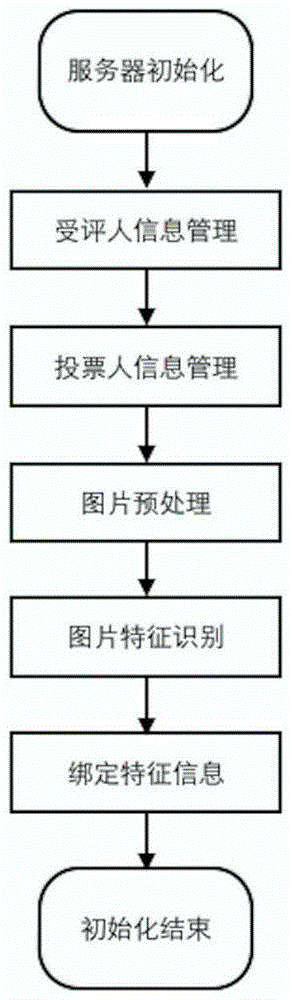
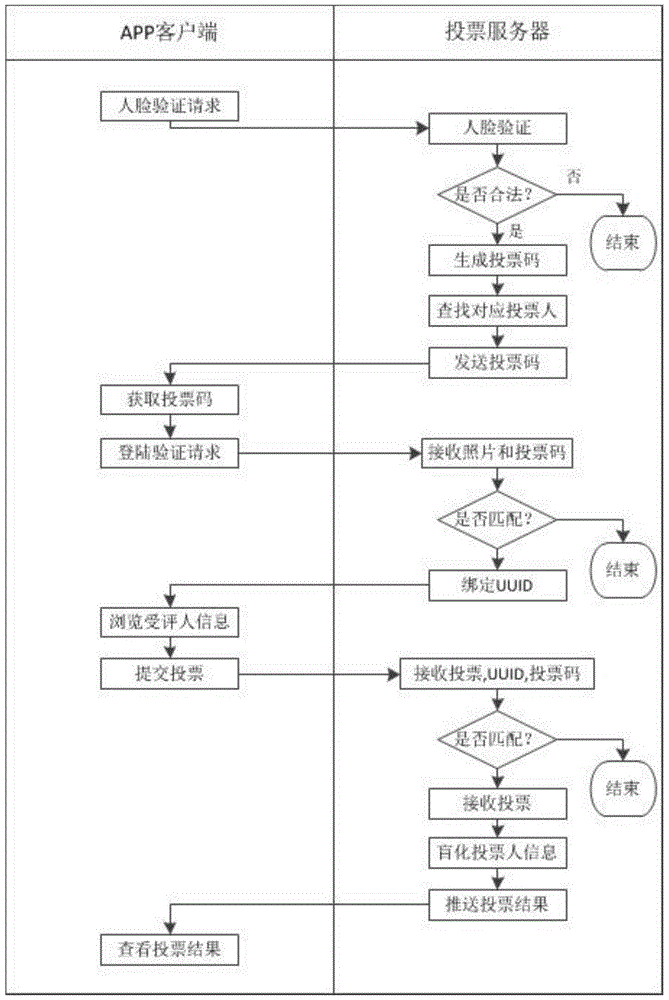
ActiveCN105225328AOvercome deficienciesImprove securityVoting apparatusUser identity/authority verificationConfidentialityComputer terminal
A mobile terminal E-voting method based on facial feature recognition comprises the following steps: (1) data of a voting server SS is initialized; and (2) a mobile terminal starts to vote. A voter needs to pass cross validation of a system during the voting process, and the process is as follows: (2.1) first validation: after first validation, jumping to a login interface and starting login certification which needs a voting code T_codei, equipment T_UUIDi and a face photo T_pici, wherein the voting code T_codei is obtained by a user from a mail-box T_maili and obtaining a voting code from the mail-box is second validation; and the equipment T_UUIDi is automatically obtained by an APP from equipment and the face photo T_pici is shot by an APP camera; (2.2) second validation: entering the voting code T_codei obtained from the mail-box T_maili; (2.3) third validation; and (2.4) voting. The invention also provides a mobile terminal E-voting system based on facial feature recognition. The method and the system consider both high security and high confidentiality and are convenient to use.
Owner:ZHEJIANG UNIV OF TECH
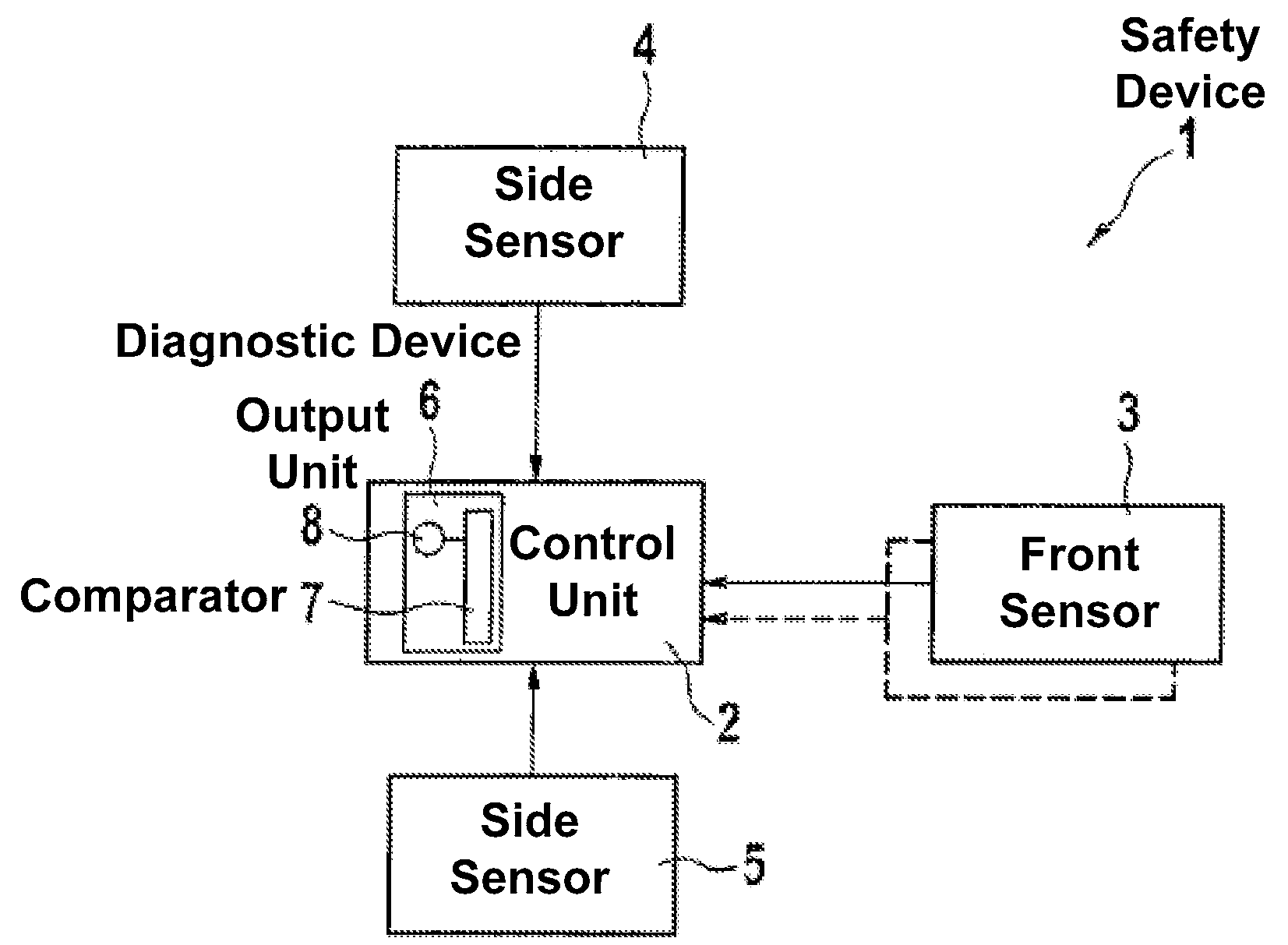
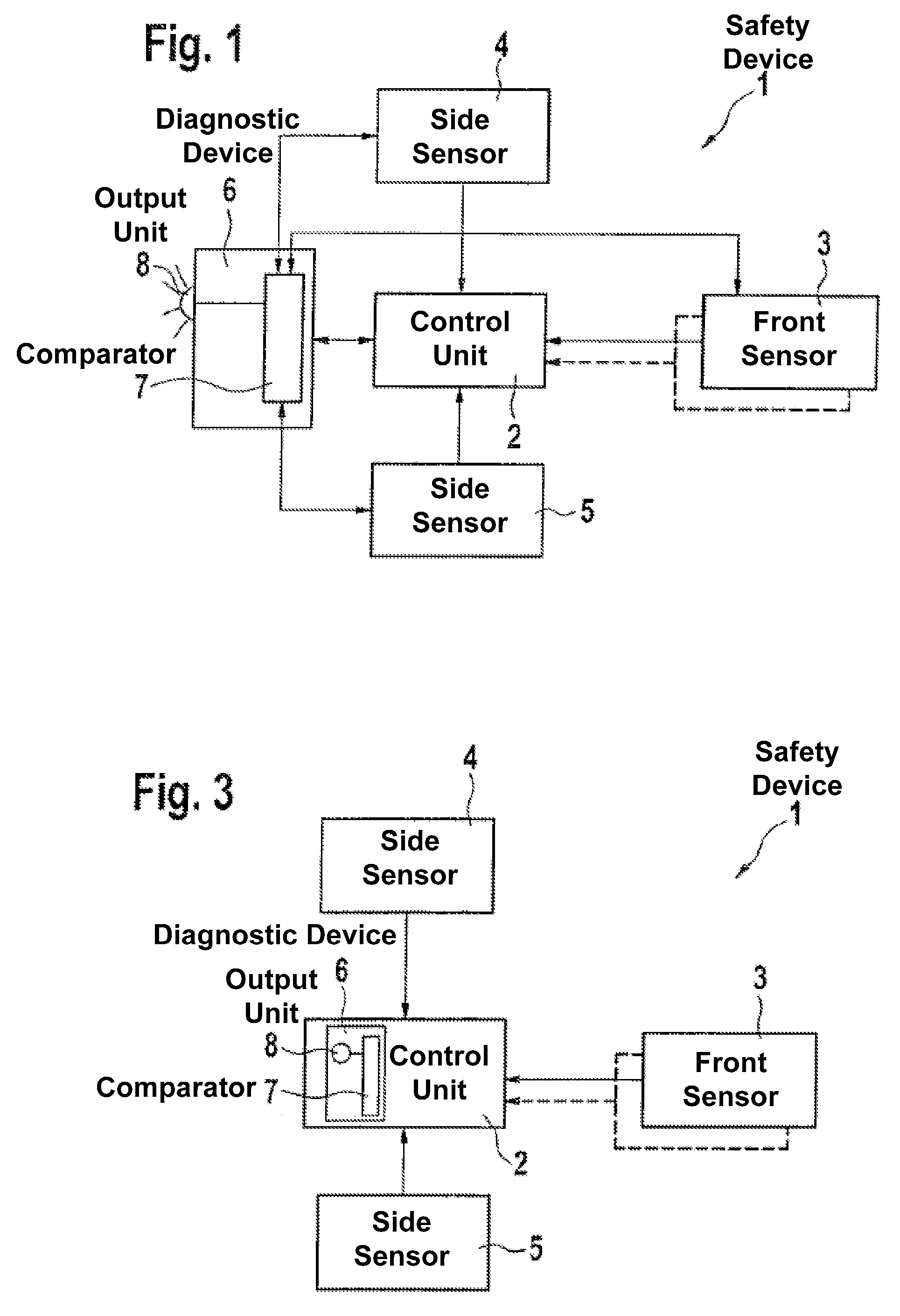
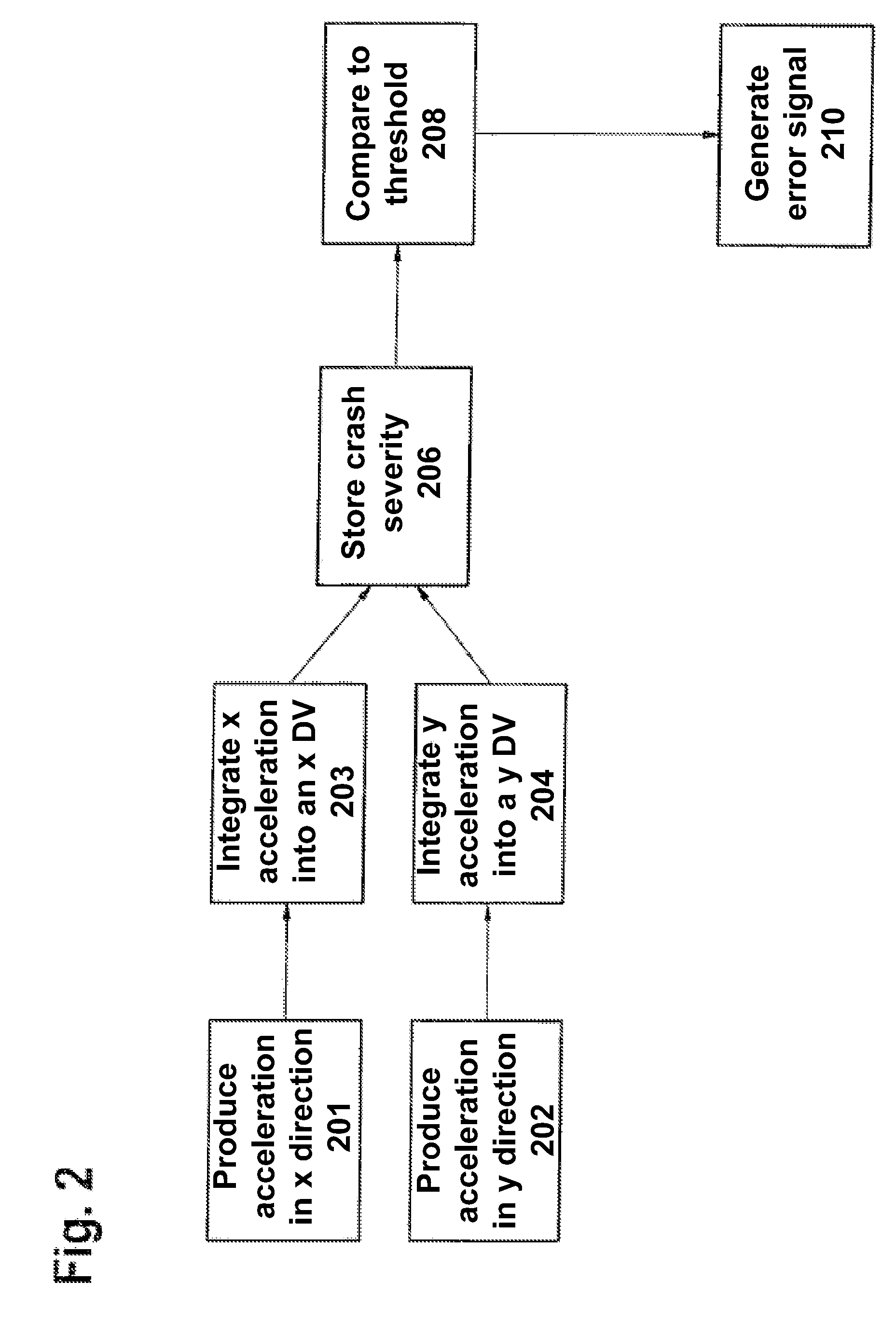
Method for monitoring the performance reliability of a control unit and diagnostic device
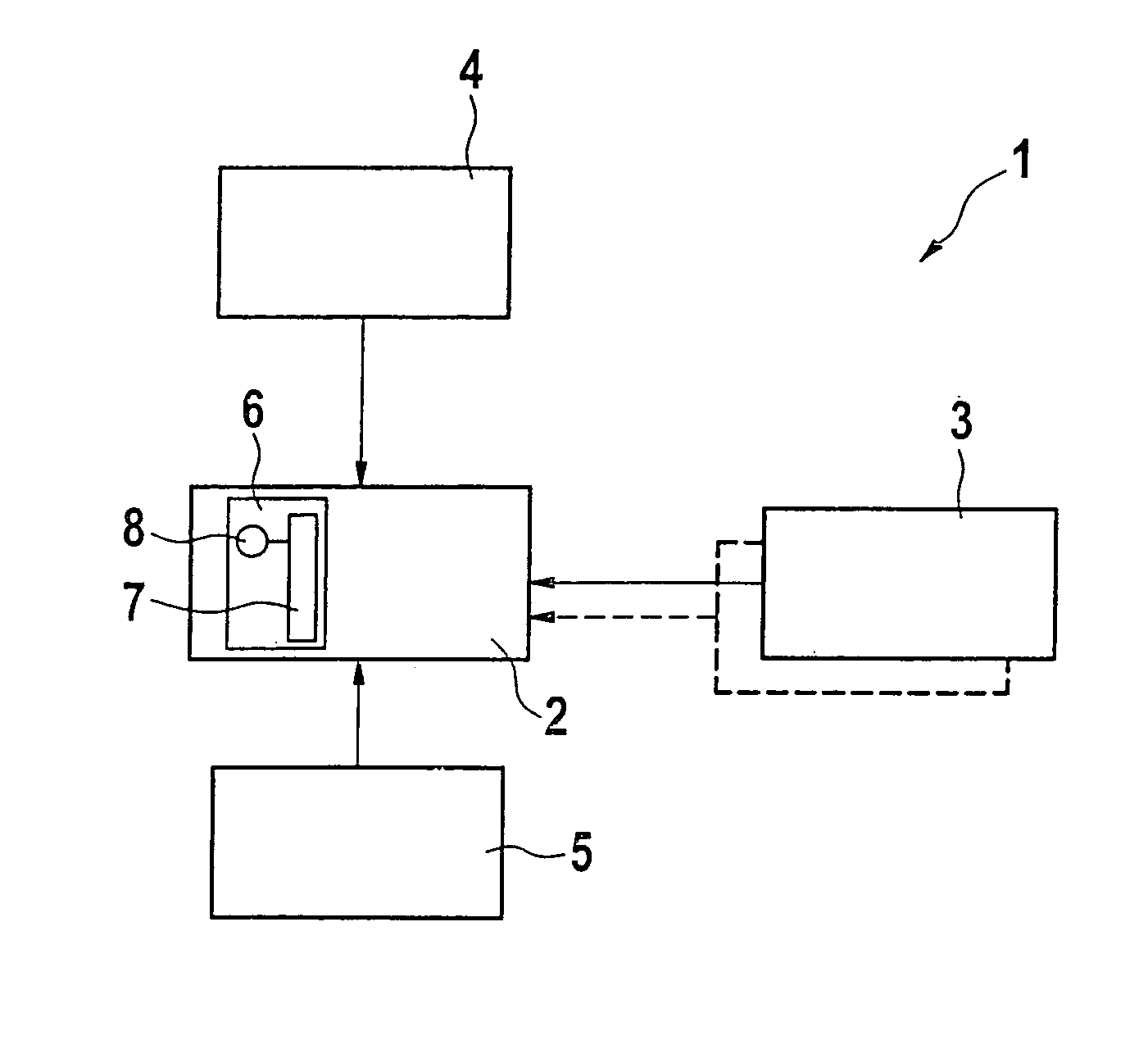
InactiveUS20070043485A1Reduce repair costsControlling the riskVehicle testingSafety arrangmentsEngineeringError function
The present arrangement provides a method for monitoring the performance reliability of a control unit and / or at least one sensor of a safety device for the protection of vehicle occupants, comprising the steps that a negative acceleration or velocity caused by an impact, in particular, be recorded; a value for the impact severity be derived from the recorded acceleration or velocity; and the value for the impact severity be compared to a predefined threshold value. If the value for the impact severity exceeds the predefined threshold value, an error-function signal will be output, which indicates that the proper functioning can no longer be ensured for the control unit and / or for at least one sensor. The present arrangement also relates to a diagnostic device for such a method.
Owner:ROBERT BOSCH GMBH
Symmetric searchable encryption method, device, equipment and medium
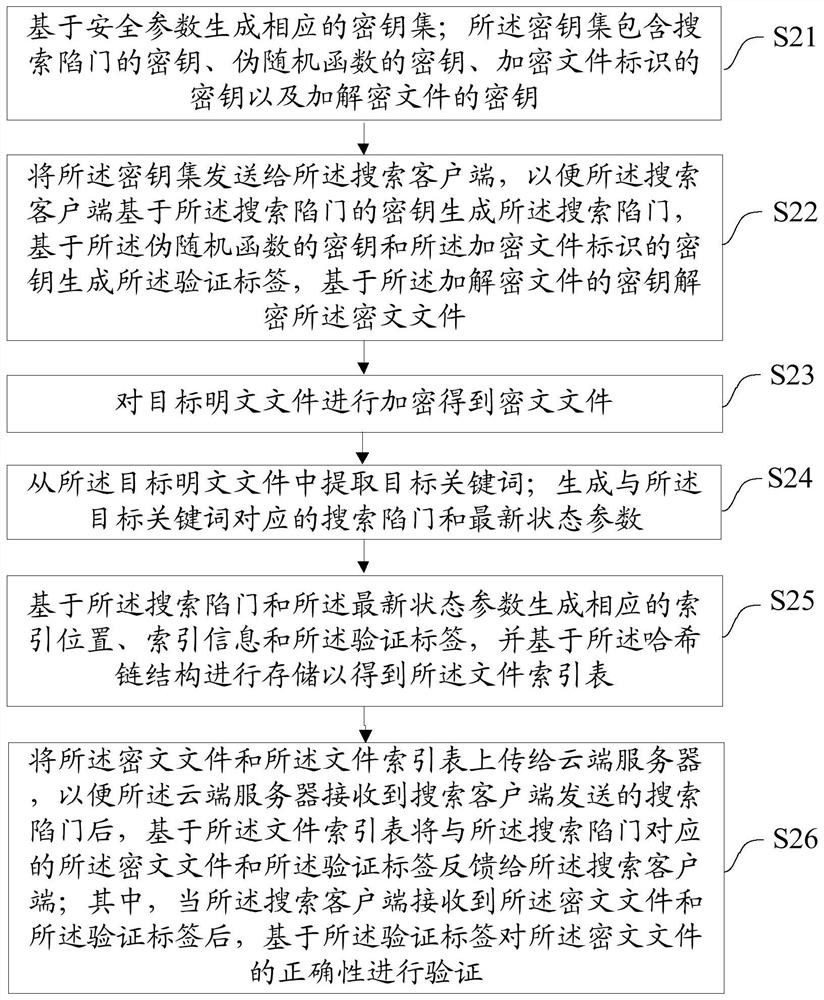
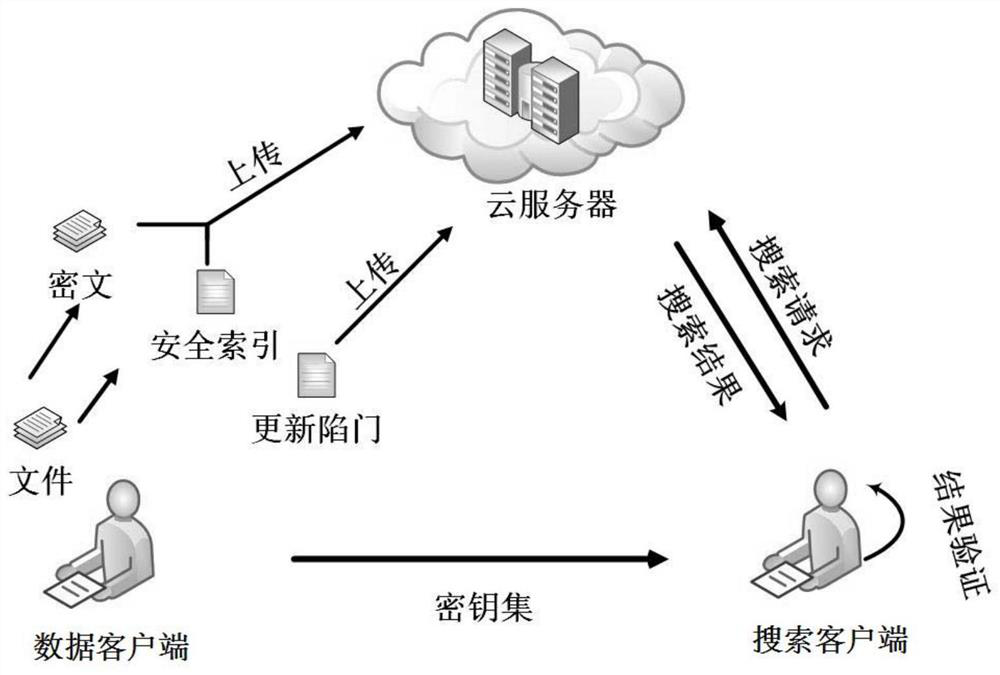
ActiveCN112182630AGuaranteed forward securityAchieving verifiabilityDigital data protectionFile access structuresPlaintextCiphertext
The invention discloses a symmetric searchable encryption method and device, equipment and a medium. The method comprises the following steps: encrypting a target plaintext file to obtain a ciphertextfile; creating a file index table based on the target plaintext file and a hash chain structure, wherein the file index table comprises an accumulative verification label and a continuously updated search trap door; and uploading the ciphertext file and the file index table to a cloud server, so that the cloud server feeds back the ciphertext file and the verification label corresponding to the search trap door to the search client based on the file index table after receiving the search trap door sent by the search client, wherein after the search client receives the ciphertext file and theverification label, the correctness of the ciphertext file is verified based on the verification label. According to the invention, the forward security and the complete verifiability of data search can be realized at the same time by creating the obtained file index table containing the accumulative verification label and the search trap door which is continuously updated.
Owner:QINGDAO UNIV
Network system safety protection method and device and related equipment thereof
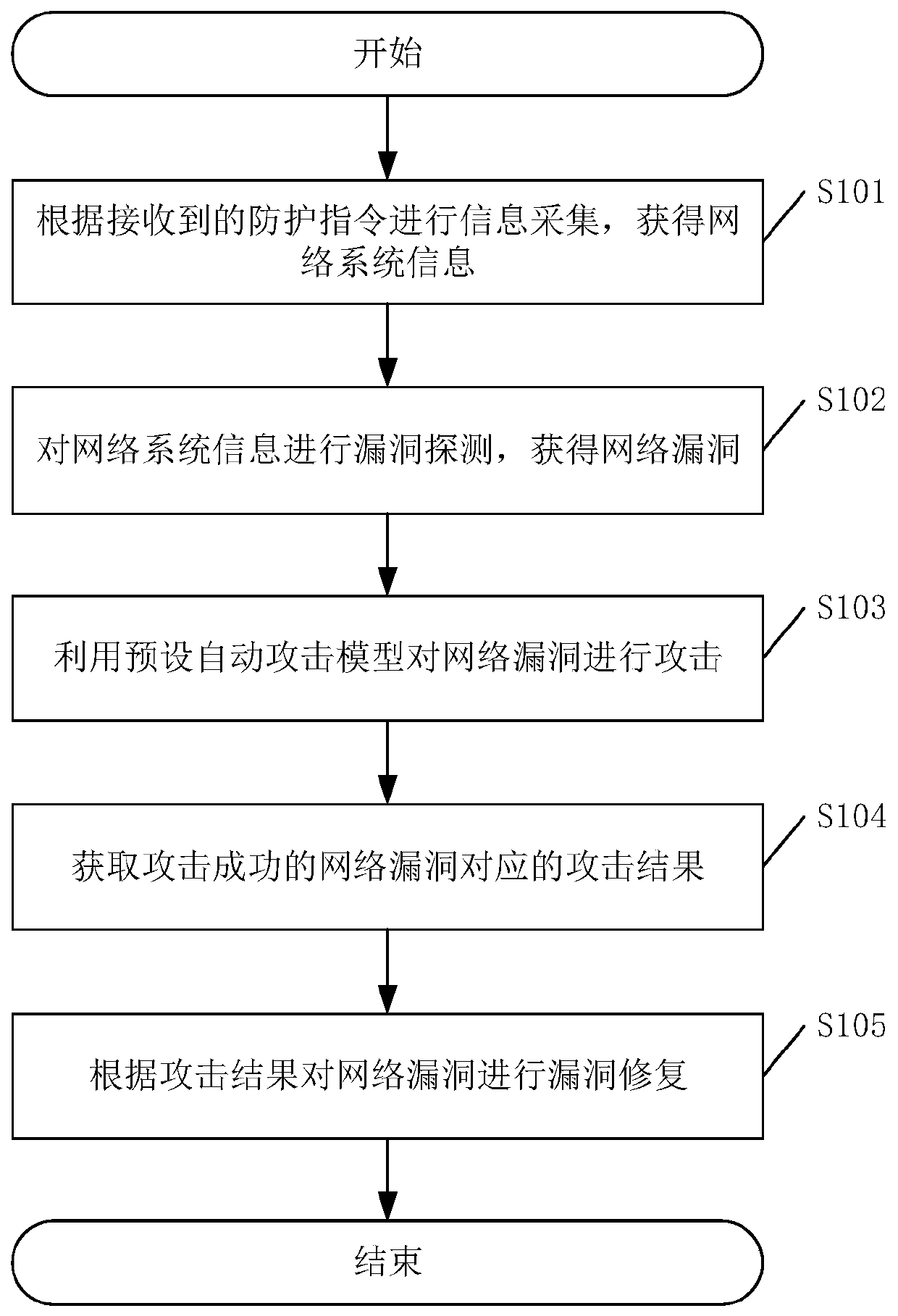
InactiveCN111049827AImprove accuracyRealize automatic offensive and defensive drillsTransmissionVulnerability detectionSystem information
The invention discloses a network system safety protection method, which comprises the steps of performing information collection according to a received protection instruction to obtain network system information; vulnerability detection is carried out on the network system information to obtain network vulnerabilities; attacking the network vulnerability by using a preset automatic attack model;obtaining an attack result corresponding to the successfully attacked network vulnerability; performing vulnerability repair on the network vulnerability according to the attack result; the network system safety protection method can effectively realize automatic, verifiable, high-efficiency and high-precision penetration test and real-time system defense. The invention also discloses a network system safety protection device and system, and a computer readable storage medium, which all have the above beneficial effects.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
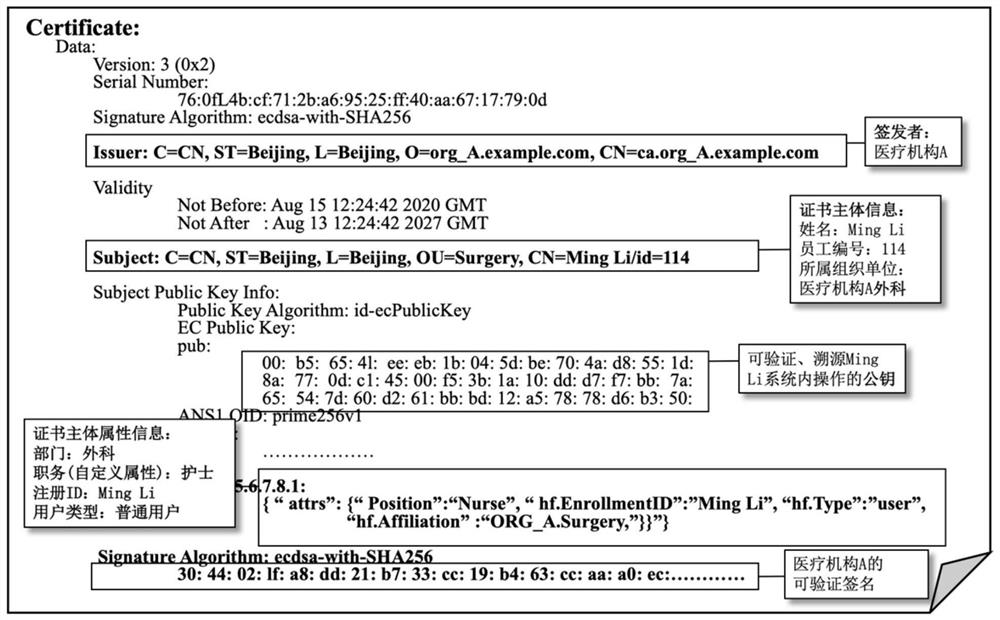
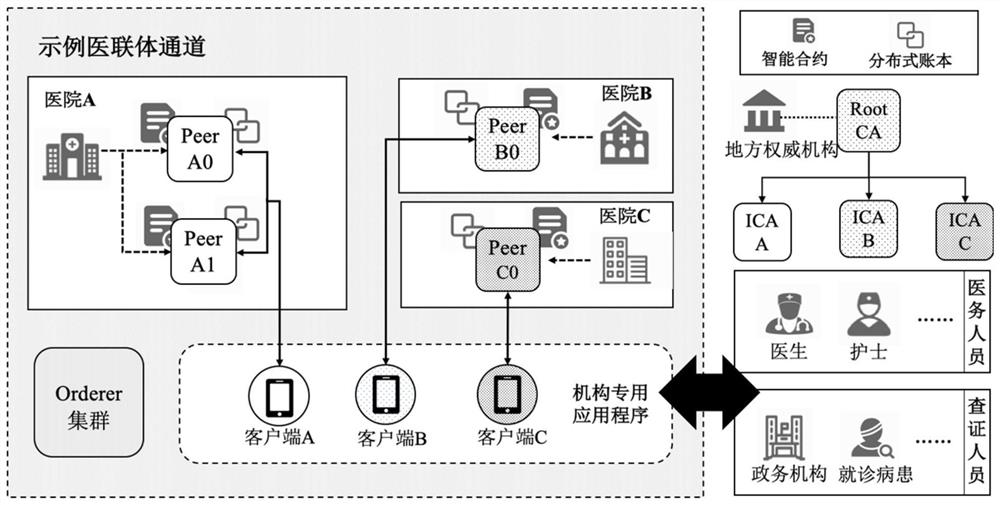
Medical certificate credible issuing and verifying system and method based on blockchain
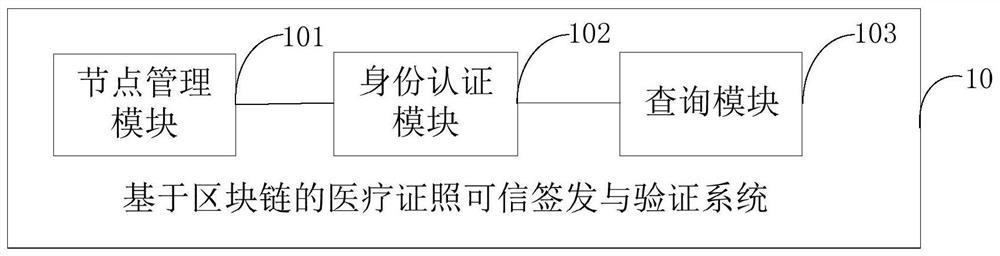
ActiveCN112565289AAchieving VerifiabilityTo achieve storage can not be tampered withData processing applicationsTransmissionTissue architectureNetwork architecture
The invention discloses a medical certificate credible issuing and verification system and method based on a blockchain, and the system comprises a node management module which is used for the building and maintenance of a medical conjoined blockchain network architecture, including the initialization and dynamic supervision of a member organization structure in a network, registration of medicalcertificate issuing institution nodes, creation of member services, and deployment of network function components according to function requirements; an identity authentication module which is used for issuing medical certificates of medical staff and auditing and filing identities of certificate inspectors; and a query module which is used for carrying out authorization examination on the certificate query application of the examiner and providing a certificate examination service of an application access control mechanism at the same time. According to the system, firstly, credibility of themedical certificate content and the issuing process thereof is realized; secondly, bidirectional verification and authorized access in the certificate checking process are realized, and the privacy security of system participation users is guaranteed; and finally, realizing a support framework for transaction processing right control between internal entities of the medical alliance and member institutions of the medical alliance.
Owner:BEIHANG UNIV
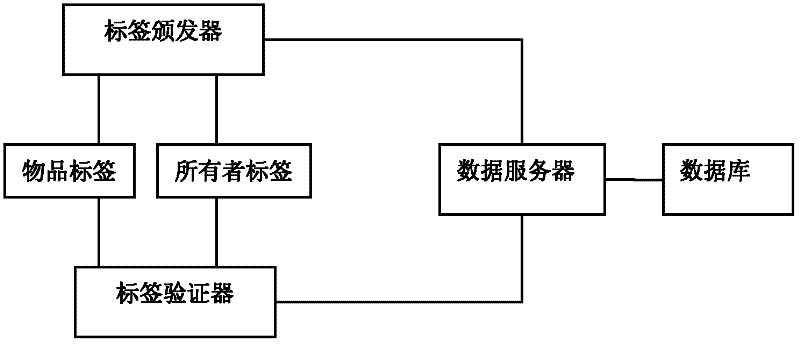
Safety anti-counterfeiting system and method based on two wireless radio frequency tags
InactiveCN102411748AGreat application valueEnsure safetySensing record carriersCommerceRadio frequencyEngineering
The invention discloses a safety anti-counterfeiting system and method based on two wireless radio frequency tags. The system comprises a tag issuing device, an object tag, an owner tag, a tag validator, a data server and a database, wherein both the object tag and the owner tag are issued by the tag issuing device and authenticated by the tag validator; data in the tag issuing device and the tagvalidator are synchronized through the data server; the data server is connected with the tag issuing device, the tag validator and the database; and the owner tag and the object tag are issued in pair so as to form a tag pair.
Owner:SOUTH CHINA NORMAL UNIVERSITY
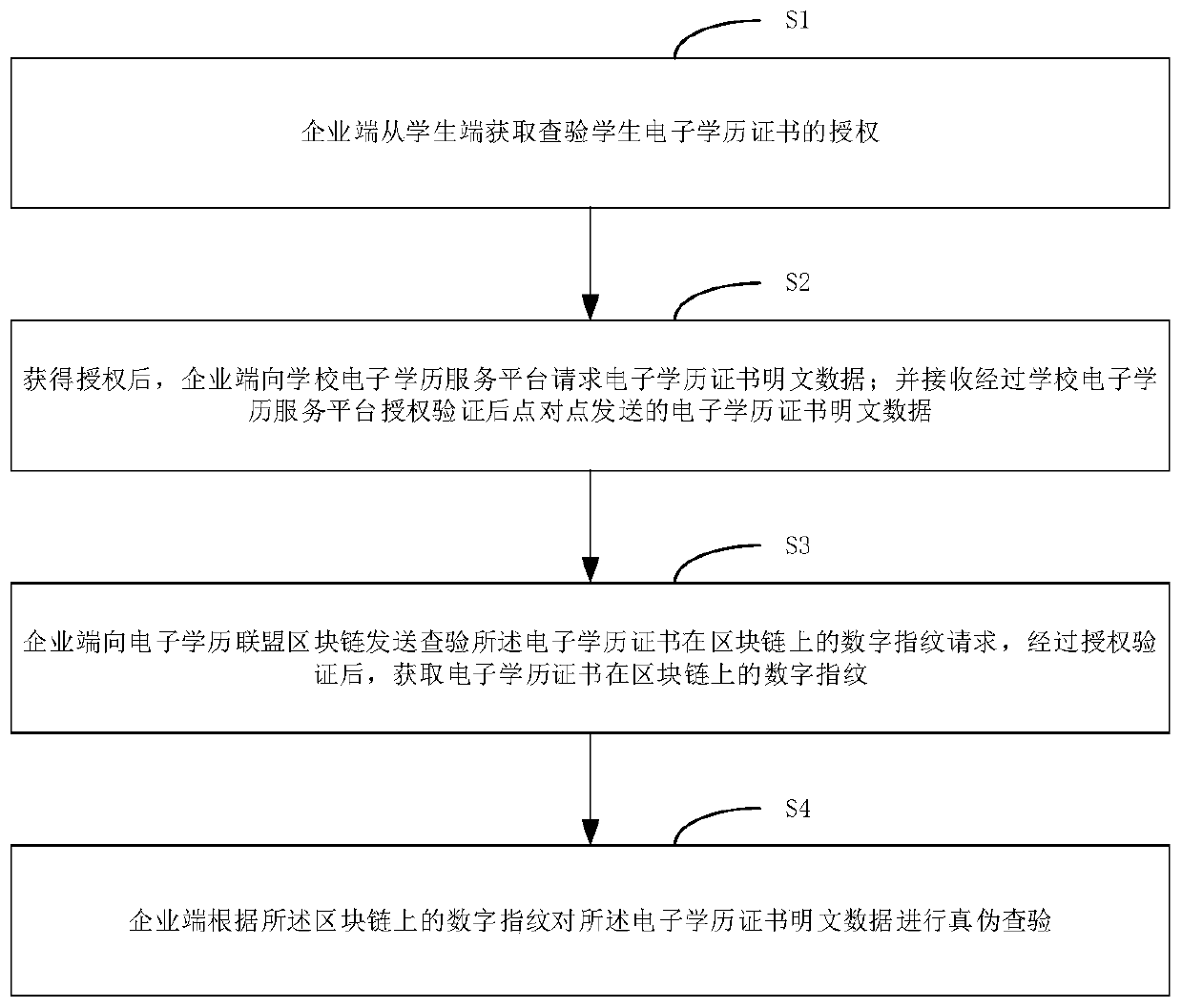
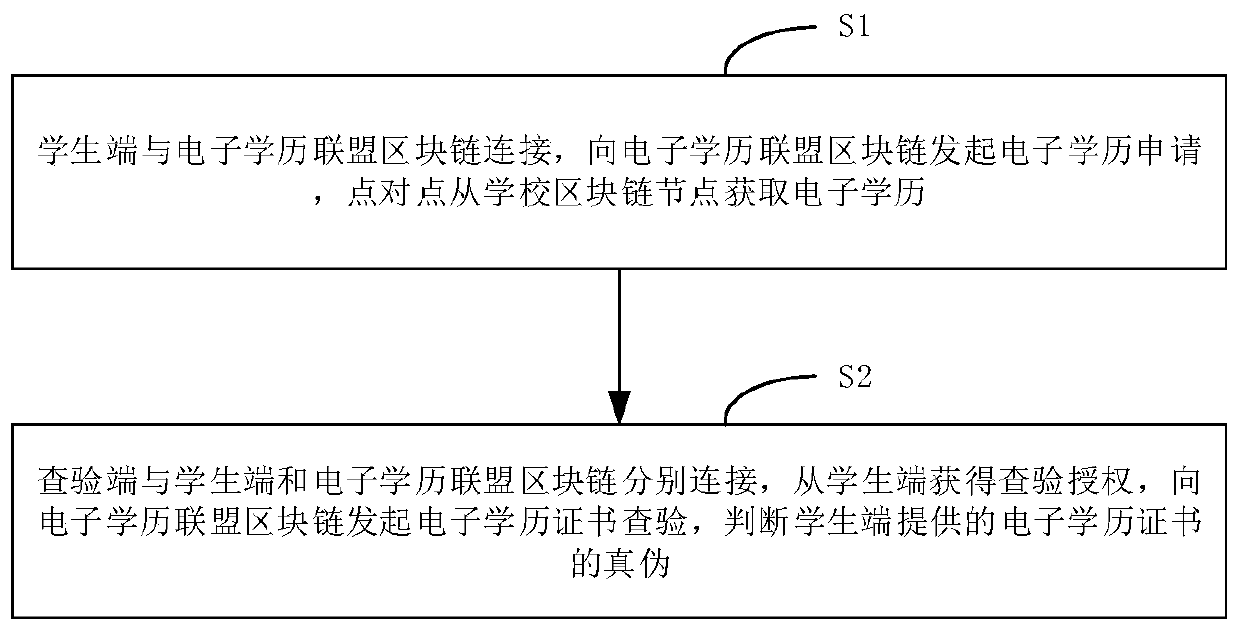
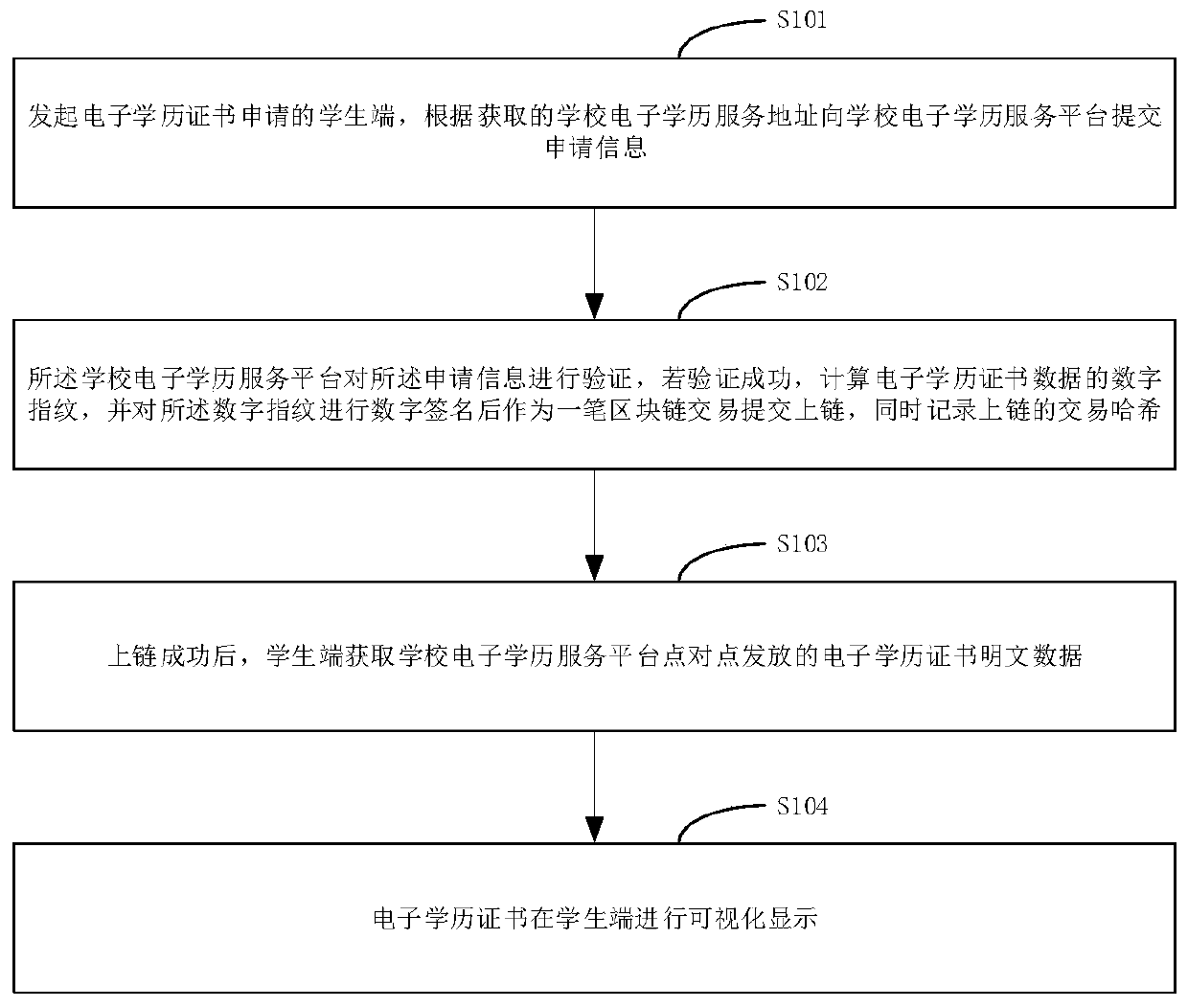
Decentralized electronic academic certificate checking method and system
ActiveCN110955699AAddressing the risks of centralizationImprove securityDatabase distribution/replicationCommercePlaintextInternet privacy
The invention relates to a decentralized electronic academic certificate checking method and system, belongs to the technical field of electronic academic certificate acquisition, and solves the problem of electronic academic certificate checking. The method comprises the following steps: acquiring authorization for checking an electronic academic certificate of a student from a student terminal;requesting electronic academic certificate plaintext data from a school electronic academic certificate service platform; receiving electronic academic certificate plaintext data sent in a point-to-point manner after being authorized and verified by the school electronic academic certificate service platform; sending a request for checking the digital fingerprint of the electronic academic certificate on the block chain to an electronic academic certificate alliance block chain, and obtaining the digital fingerprint of the electronic academic certificate on the block chain after authorizationverification; and checking the authenticity of the plaintext data of the electronic academic certificate according to the digital fingerprint on the blockchain. According to the invention, decentralization is realized, an application mode of a traditional centralized educational background authentication platform based on data collection is changed, the risk of electronic academic certificate plaintext data uploading is solved, and the security is improved.
Owner:YGSOFT INC
Electronic contract generation method and device, computer equipment and storage medium
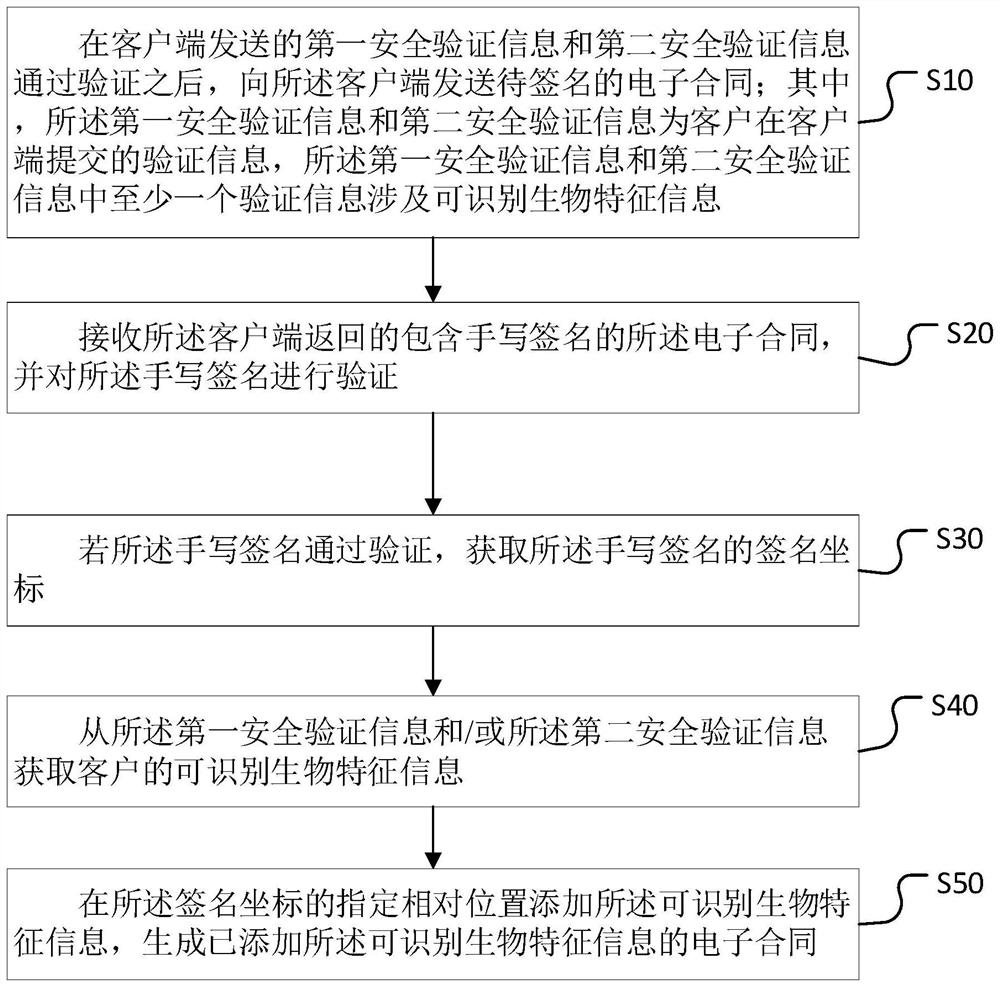
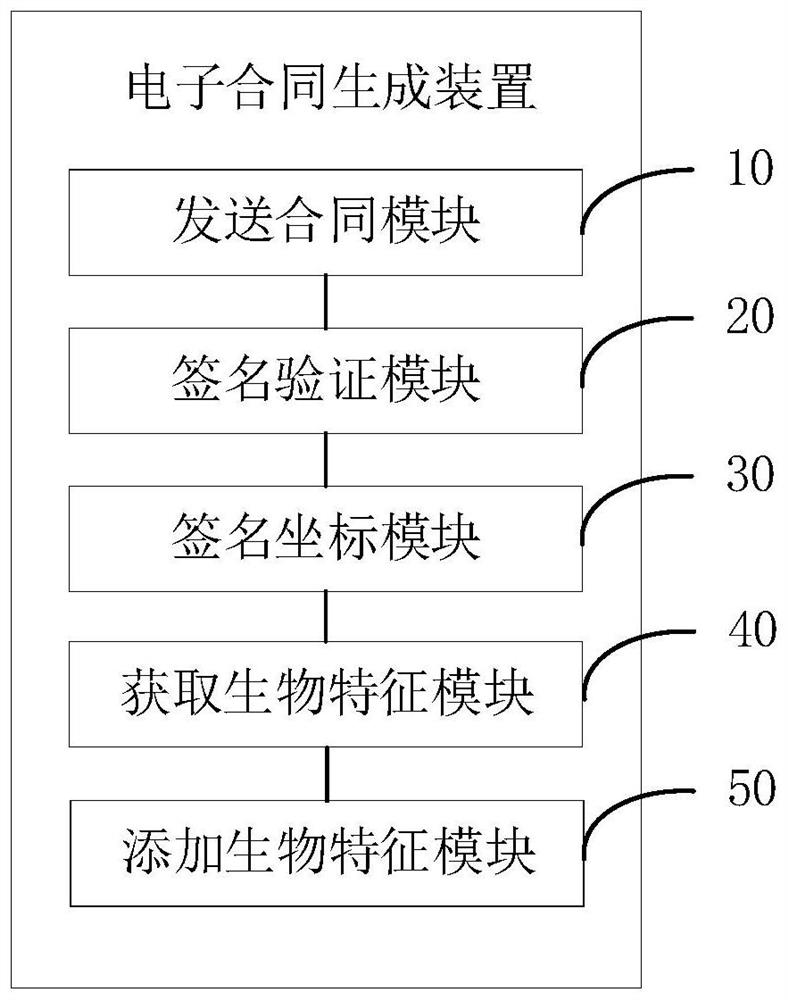
PendingCN112818300AAchieving verifiabilityImprove securityDigital data protectionDigital data authenticationComputer equipmentEngineering
The invention relates to the field of identity authentication, and discloses an electronic contract generation method and device, computer equipment and a storage medium, and the method comprises the steps: sending a to-be-signed electronic contract to a client after first safety verification information and second safety verification information sent by the client pass verification; receiving an electronic contract containing a handwritten signature returned by the client, and verifying the handwritten signature; if the handwritten signature passes verification, obtaining signature coordinates of the handwritten signature; obtaining recognizable biological characteristic information of the customer from the first security verification information and / or the second security verification information; and adding recognizable biological characteristic information at a specified relative position of the signature coordinate, and generating an electronic contract added with the recognizable biological characteristic information. According to the invention, the effectiveness of the electronic contract can be ensured, the operation cost of a client is reduced, and the signing efficiency of the electronic contract is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Method and device for dynamically updating sugarcane planting information
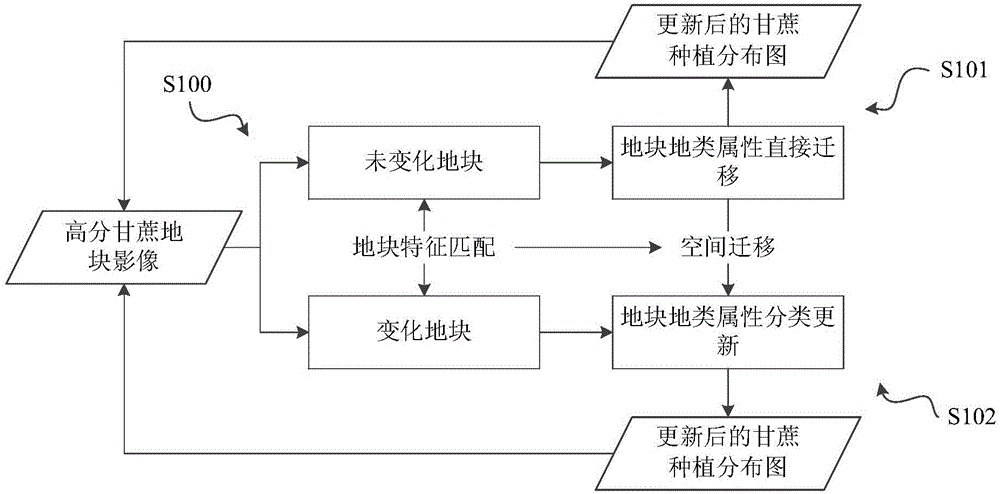
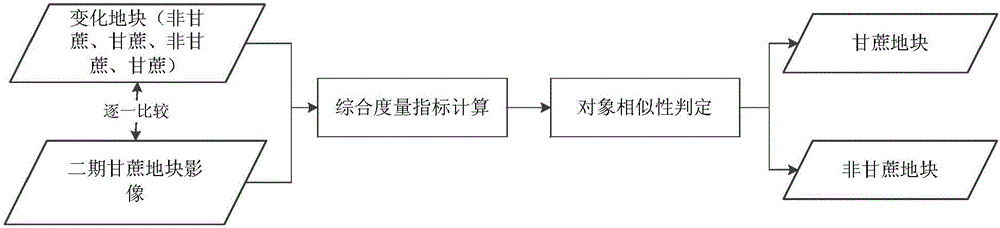
InactiveCN106339423AAchieving verifiabilityFast updateCharacter and pattern recognitionGeographical information databasesComputer scienceArea measurement
The invention discloses a method and a device for dynamically updating sugarcane planting information. The method comprises the following specific steps: acquiring high-resolution remote sensing images of sugarcane plots in the same region at different time phases, and identifying unchangeable plots and changeable plots; performing time dimension migration on the unchangeable plots by utilizing historical land properties; timely performing characteristic matching on the changeable plots and the unchangeable plots, and identifying sugarcane plots and non-sugarcane plots in the changeable plots. By the method, high-resolution data are used as a basis for identifying and classifying the plots, so that a phenomenon of 'salt and pepper' in pixel-class classification is avoided, and the classification accuracy, the area measurement accuracy and the result verifiability are improved; the conventional object-oriented irregular mode spots without natural and social attribute significances are replaced by a precise plot boundary; the updating rate and the updating frequency of the sugarcane planting information are improved, and the dependency on the data amount in the updating process is reduced.
Owner:李宇翔 +1
Quantum secret voting method based on single particle
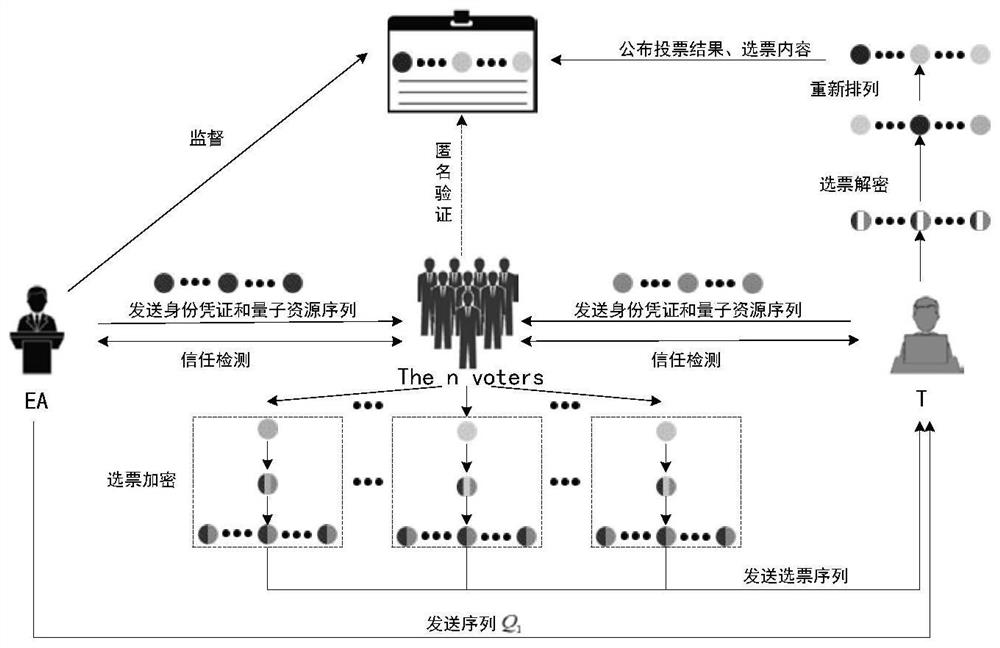
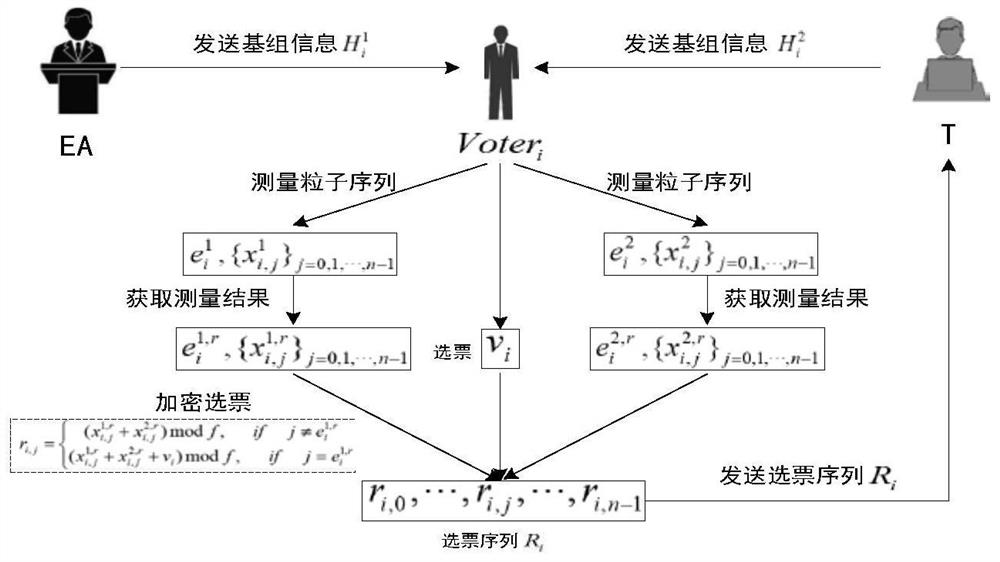
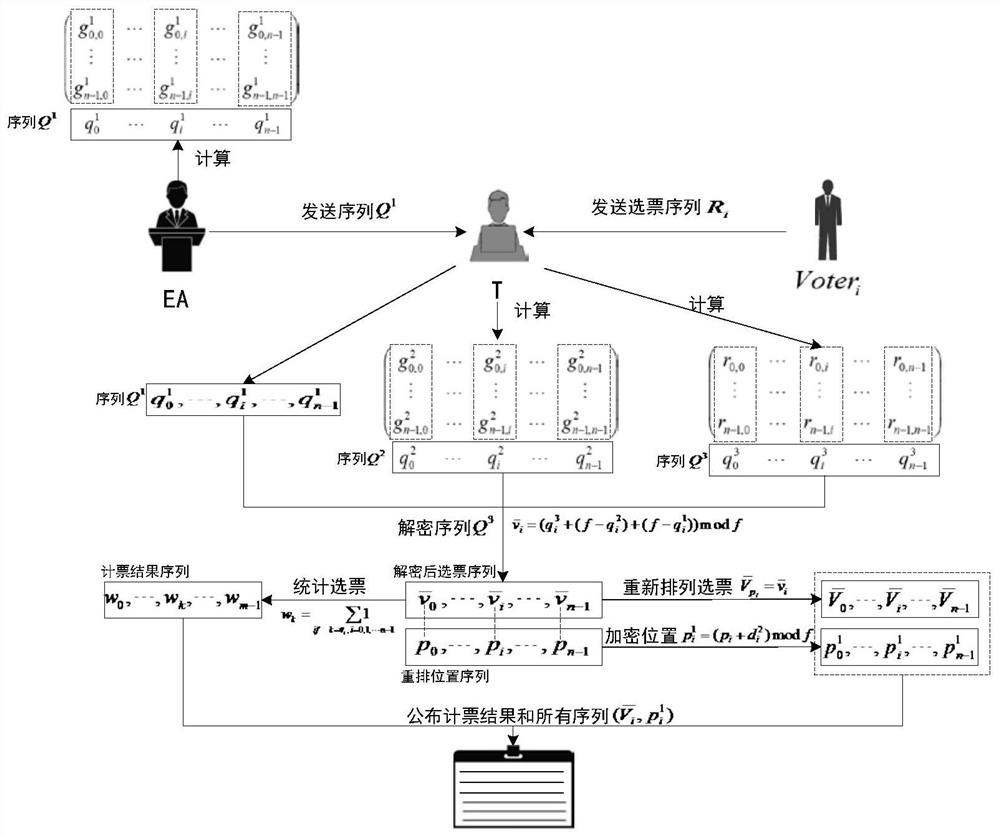
ActiveCN112511307ABreach of confidentialityAchieve fairnessVoting apparatusKey distribution for secure communicationQuantum informationInformation transmission
The invention relates to a quantum secret voting method based on a single particle. The quantum secret voting method is applied to a voting environment composed of a voting mechanism, a voter, a voterand an OADM. The OADMs are connected through optical fibers to form an annular classical quantum information fusion channel; wherein the voting mechanism, the voter and the voter are connected with an OADM and are connected to a classic quantum information fusion channel through the OADM to form a node so as to carry out information transmission between any nodes; the voting mechanism and the voter are assumed to be semi-honest, the voter is not limited to be semi-honest, in the voting process, the voting mechanism and the voter can check the identity of the voter, and identity certificates and quantum resources are distributed to the qualified voter; the voting institution and the voter respectively carry out trust detection with the voter, and the voter and the voter verify the identities of each other; the voter votes and sends the vote sequence to the vote counter; and after the voter completes voting, the voter counts votes and publishes a voting result.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
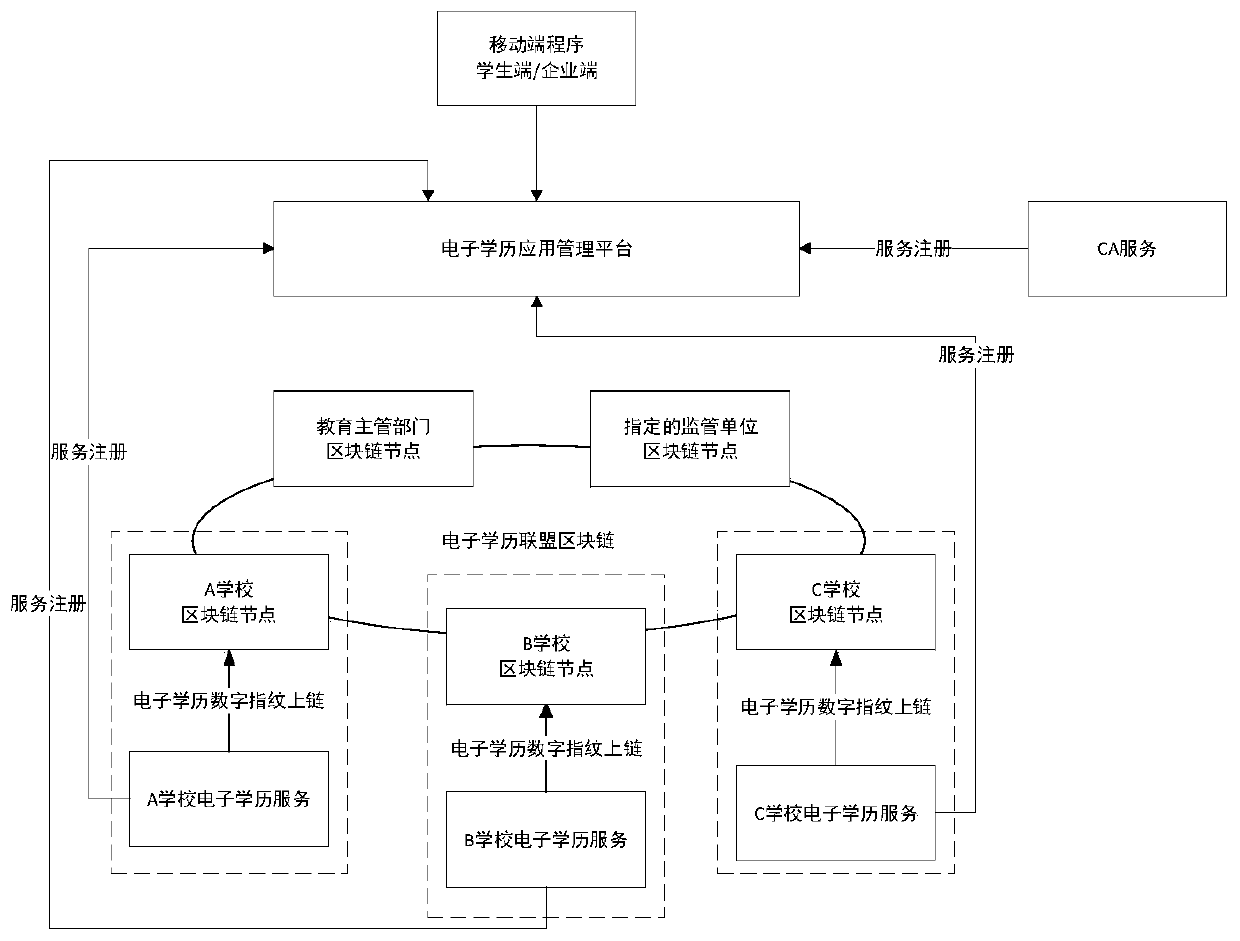
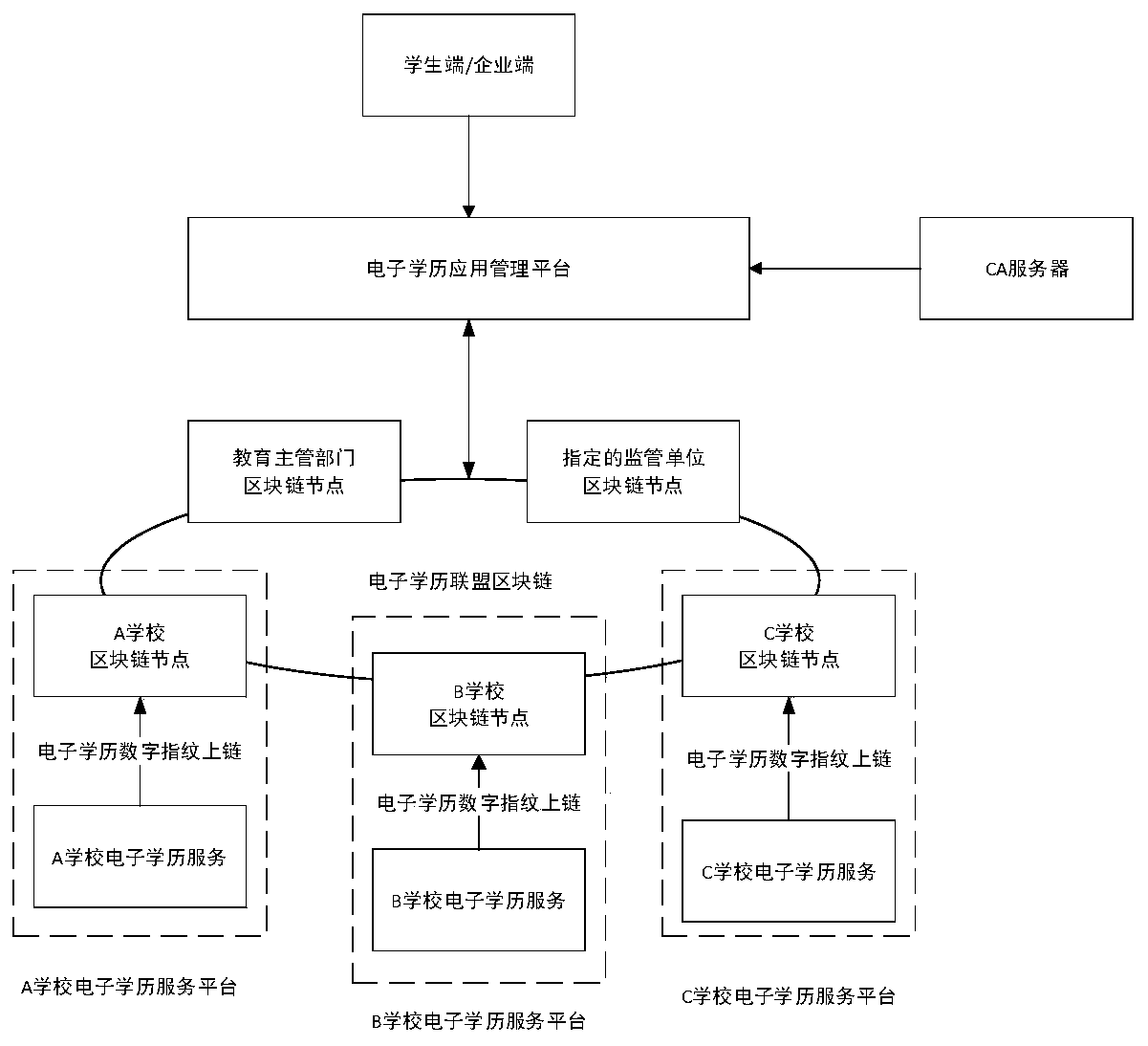
Decentralized electronic education background management system and method
ActiveCN110909388AAchieve decentralizationAddressing the risks of centralizationData processing applicationsDigital data protectionData setKnowledge management
The invention relates to a decentralized electronic education background management system and method, and belongs to the technical field of electronic education background certificate acquisition, solving the problems of electronic education background certificate application and inspection. The decentralized electronic education background management system comprises an electronic education background alliance block chain and a client, wherein the electronic education background alliance block chain processes the electronic education background certificate application and check request and performs uplink storage on the electronic education background application data; and the client establishes connection with the electronic education background alliance block chain, initiates an electronic educational background application request to the electronic educational background alliance block chain, and acquires electronic educational background plaintext data from school block chain nodes in the electronic education background alliance block chain in a point-to-point manner, or initiates an electronic education background check request to the electronic education background allianceblock chain, and judges the authenticity of the electronic education background. According to the decentralized electronic education background management system, decentralization is realized, and anapplication mode of a traditional centralized education background authentication platform based on data collection is changed, so that the risk of data centralization is solved, and the security isimproved.
Owner:YGSOFT INC
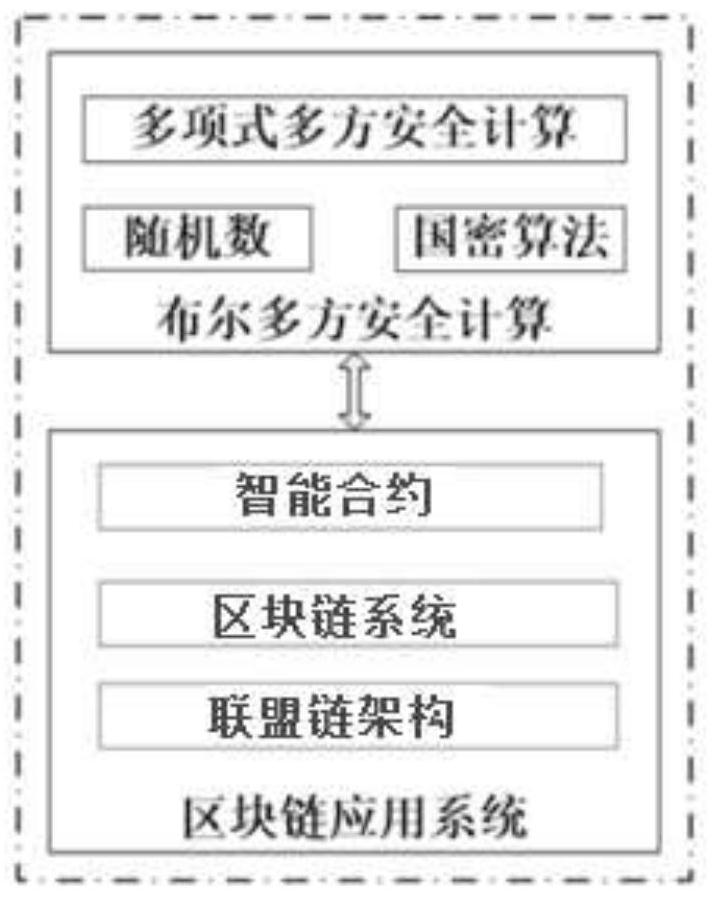
Multi-party security computing method and device based on block chain platform, and electronic equipment
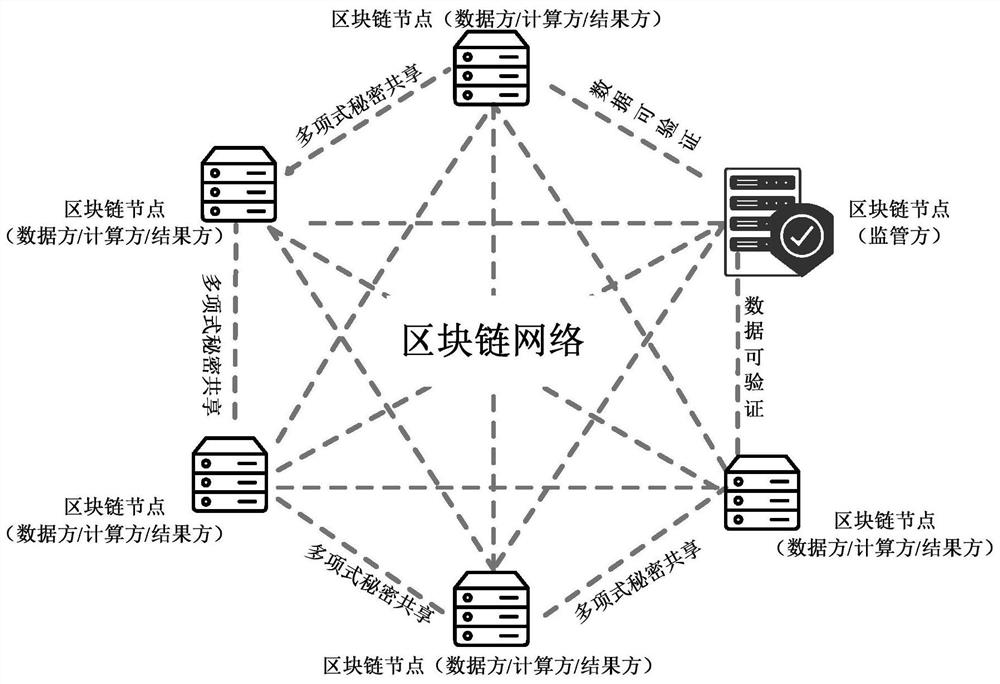
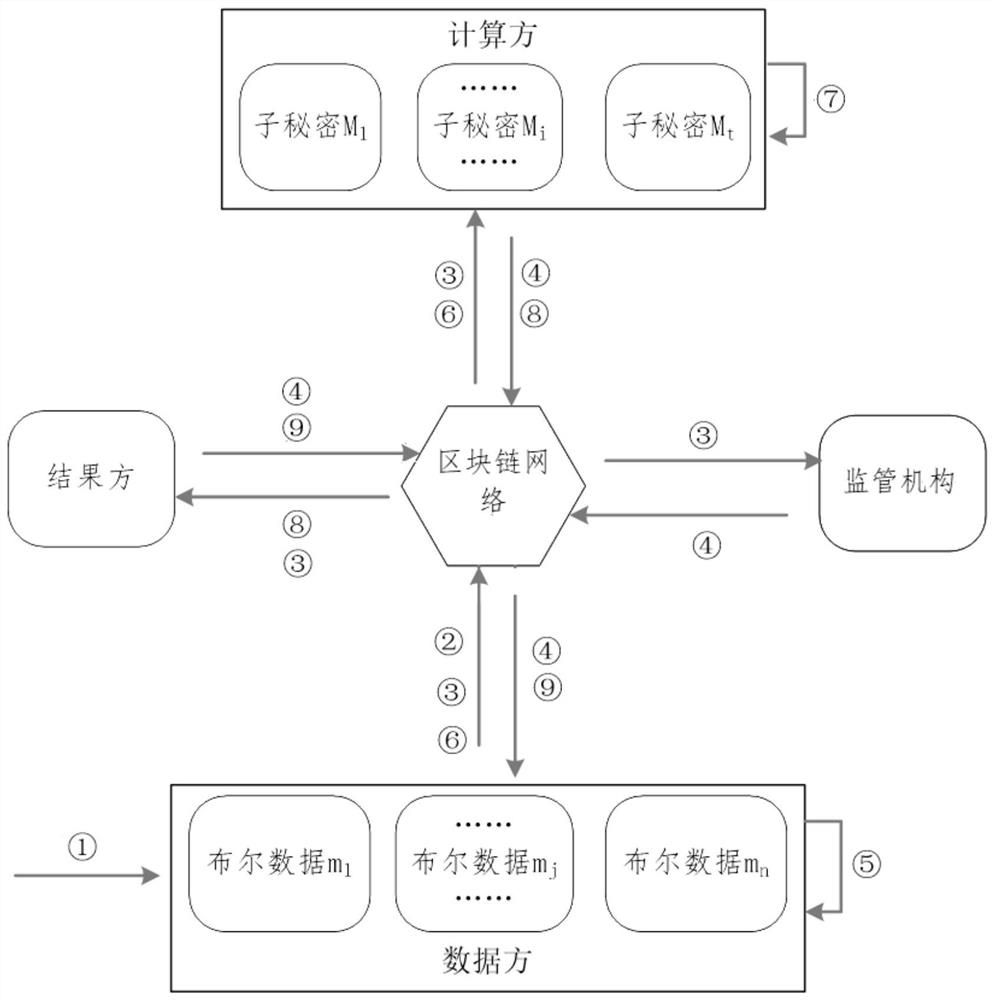
ActiveCN113098682AIncrease credibilityAchieving verifiabilityKey distribution for secure communicationUser identity/authority verificationSecure multi-party computationCalculation methods
The invention provides a multi-party security computing method and device based on a block chain platform and electronic equipment, and the method comprises the steps: taking an alliance chain as a block chain bottom layer support architecture, locally completing Boolean multi-party security computing, and uploading data and result information; nodes on the chain serving as participants and having roles of Boolean data multi-party security calculation including any one, two or all of a data party, a calculation party and a result party at the same time, and AND, NOT and XOR calculation of Boolean data security multi-party is achieved through security multi-party calculation of polynomial secret sharing on the basis of an underlying cryptographic algorithm. Under the mechanism of the alliance chain block chain, Boolean multi-party security calculation is combined with the block chain technology, polynomial Boolean multi-party security calculation based on the semi-honesty model is achieved, the credibility, verifiability and traceability of calculation are improved, and verifiability of multi-party security calculation is achieved.
Owner:HEBEI AISINO TECH CO LTD
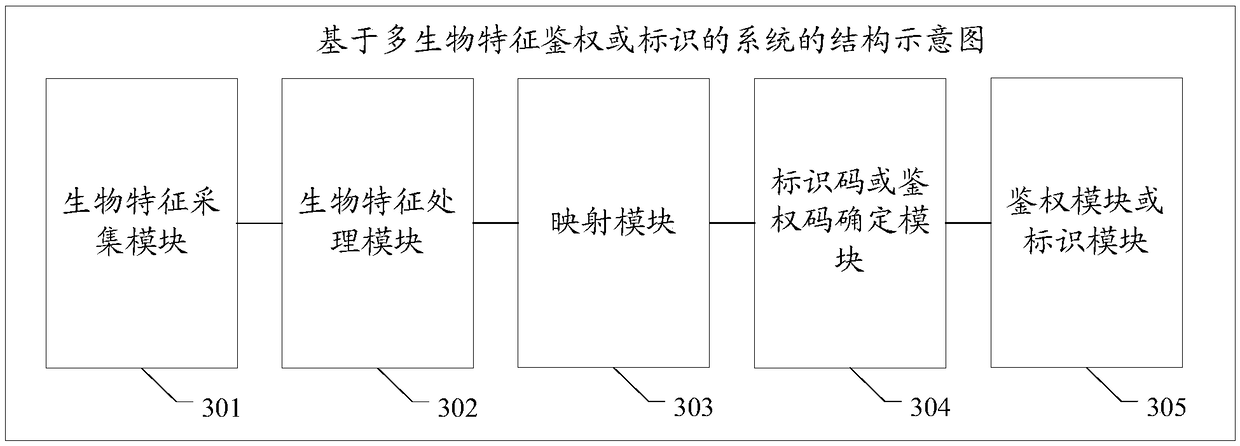
Multi-biological feature authentication or identification-based method and system
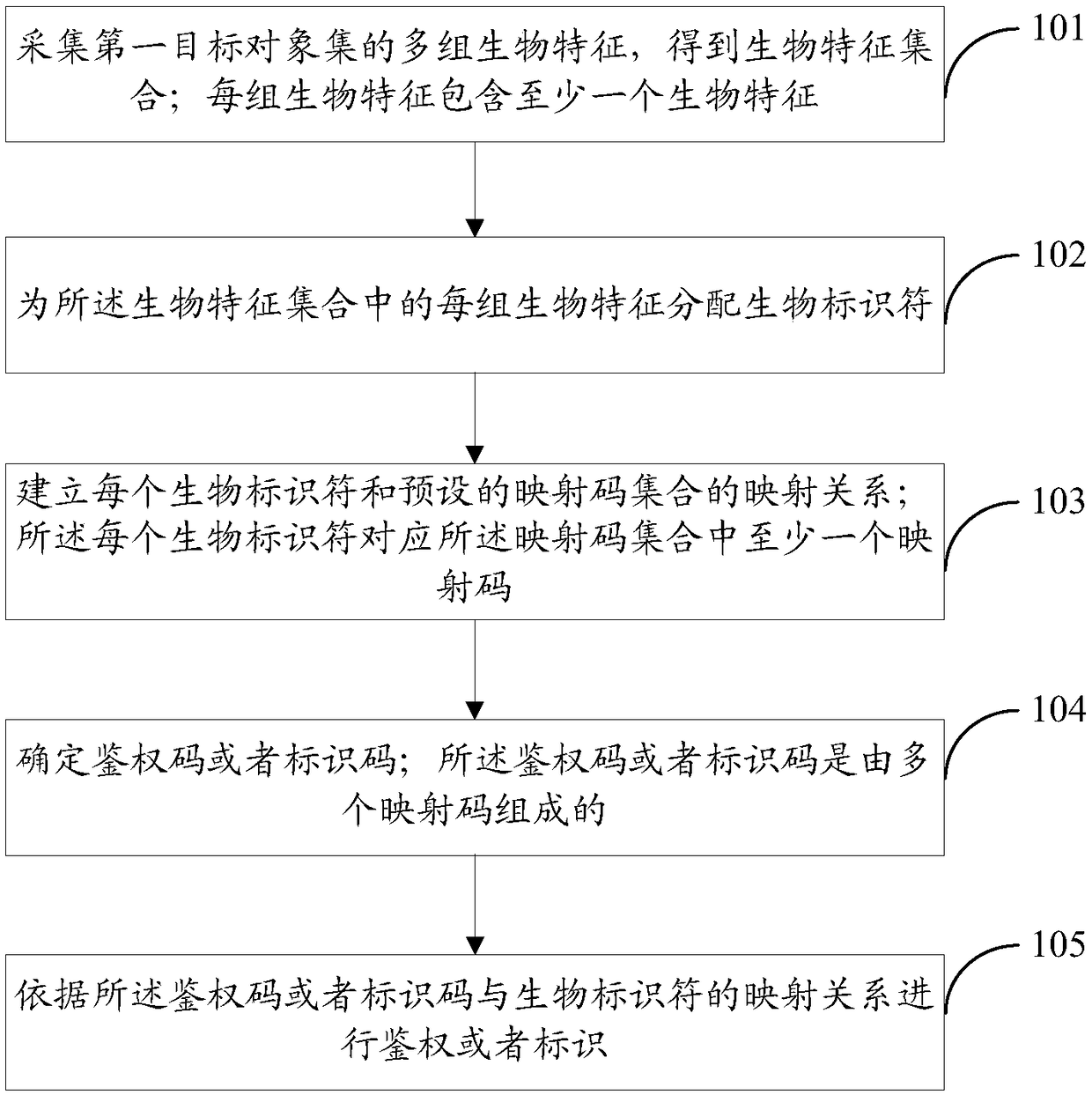
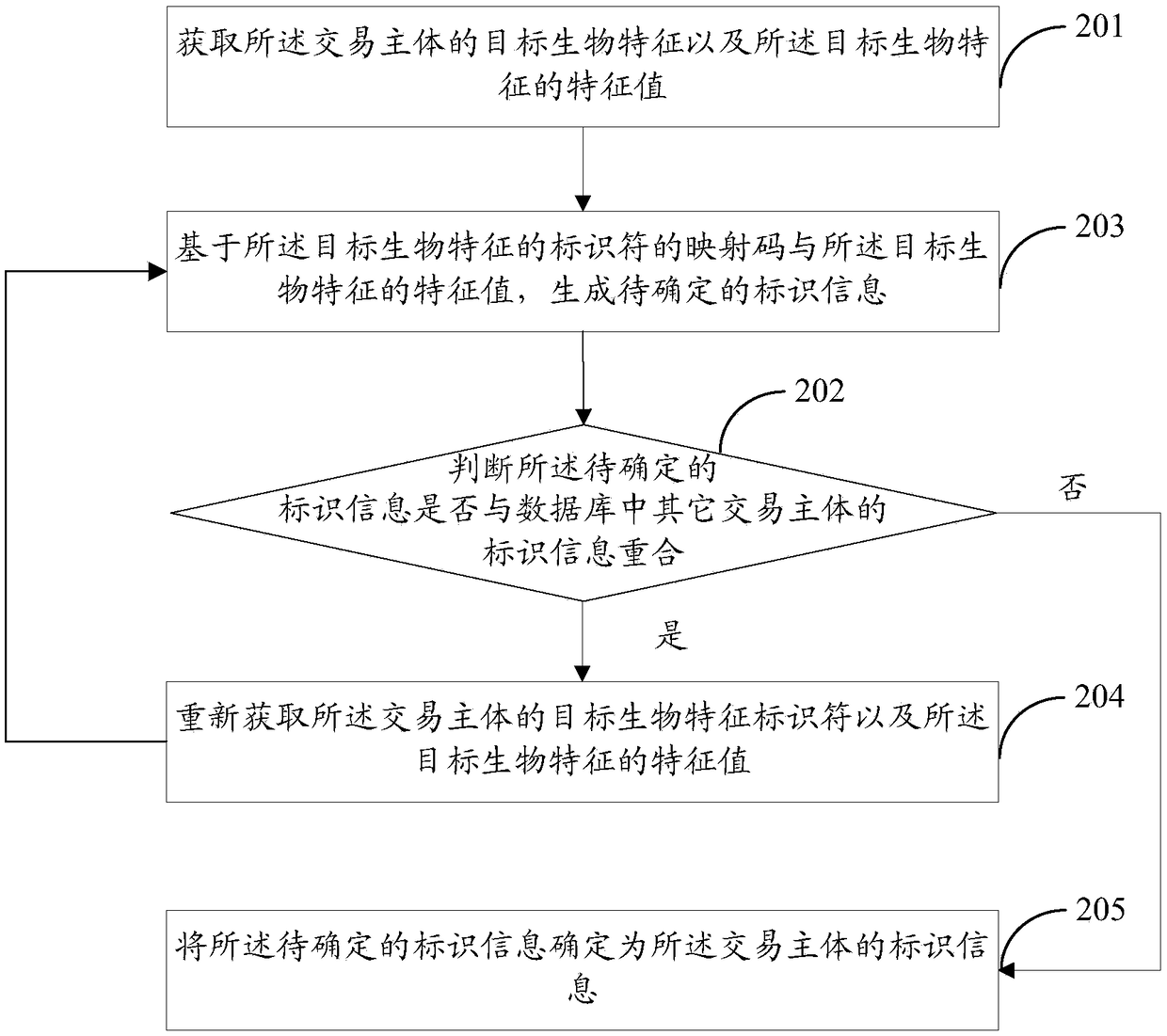
ActiveCN108717635AAvoid abuseImprove confidentialityProtocol authorisationPattern recognitionConfidentiality
The invention discloses a multi-biological feature authentication or identification-based method and system. The method comprises the following steps of: acquiring a plurality of groups of biologicalfeatures of a first target object set and obtaining biological feature values; in order to recognize each biological feature, distributing a biological feature identifier for each biological feature;establishing a mapping relationship between each biological feature identifier and a preset mapping code set; and after an authentication code or an identification code formed by mapping codes corresponding to a part or all of the biological feature identifiers is determined, carrying out authentication or identification according to the authentication code or the identification code. According tothe system and method, the problem that biological features of natural persons are abused as the biological features of the natural persons are leaked or the using of the biological features of the natural persons is not controlled by the natural persons is avoided, the confidentiality and verifiability of safety information are improved, and the non-repudiation is improved at the same time.
Owner:AGRICULTURAL BANK OF CHINA
Method for monitoring the performance reliability of a control unit and diagnostic device
InactiveUS7584035B2Controlling the riskLow costVehicle testingSafety arrangmentsEngineeringError function
The present arrangement provides a method for monitoring the performance reliability of a control unit and / or at least one sensor of a safety device for the protection of vehicle occupants, comprising the steps that a negative acceleration or velocity caused by an impact, in particular, be recorded; a value for the impact severity be derived from the recorded acceleration or velocity; and the value for the impact severity be compared to a predefined threshold value. If the value for the impact severity exceeds the predefined threshold value, an error-function signal will be output, which indicates that the proper functioning can no longer be ensured for the control unit and / or for at least one sensor. The present arrangement also relates to a diagnostic device for such a method.
Owner:ROBERT BOSCH GMBH
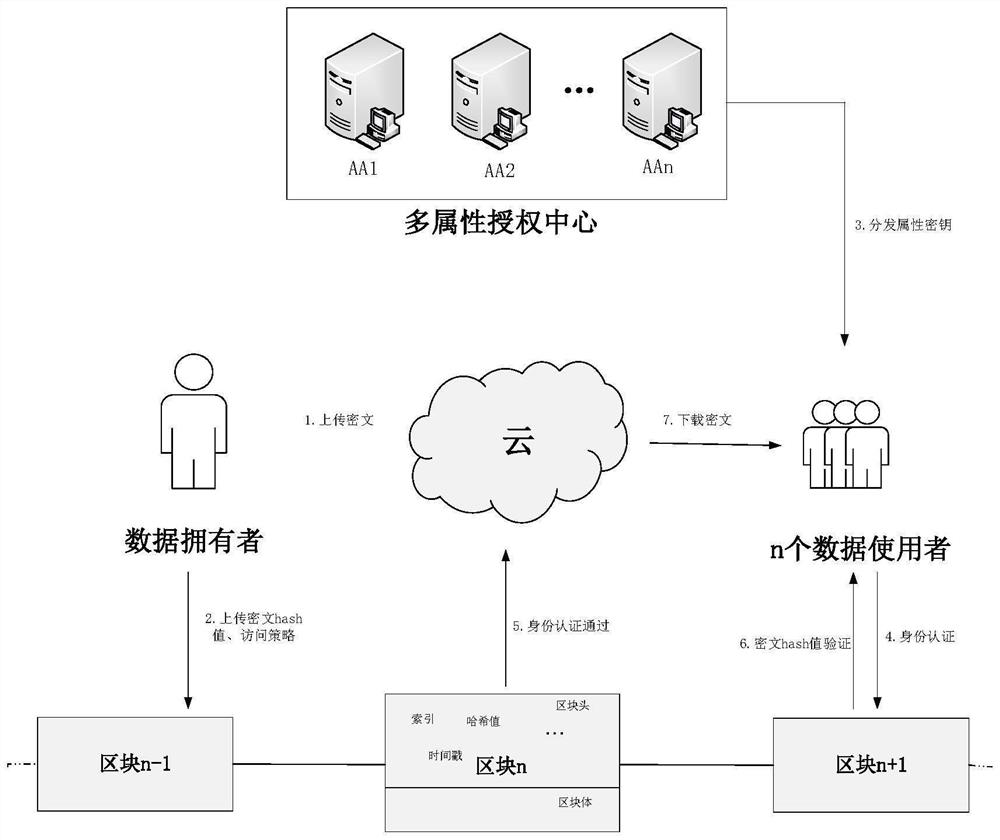
Multi-authorization attribute-based verifiable encryption method based on block chain
InactiveCN114143094AIncrease the difficultyIncrease costSecuring communicationData privacy protectionEngineering
The invention discloses a multi-authorization attribute-based verifiable encryption method based on a block chain, belongs to the technical field of block chain data privacy protection security, and is suitable for one-to-many data sharing and fine-grained access control. The method comprises the following steps: firstly, a data owner uploads encrypted data to a cloud end by using a system public key, and uploads a data ciphertext hash value and an access strategy to a block chain; and the cloud storage server is responsible for receiving and storing the ciphertext. Secondly, the data user receives the attribute key distributed by the multi-attribute authorization center and can verify the correctness of the key; and the block chain performs identity authentication on the data user, and returns an authentication result to the cloud server. And finally, only the legal user whose attribute private key accords with the access strategy can download the data from the cloud and verify whether the data is tampered or not.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
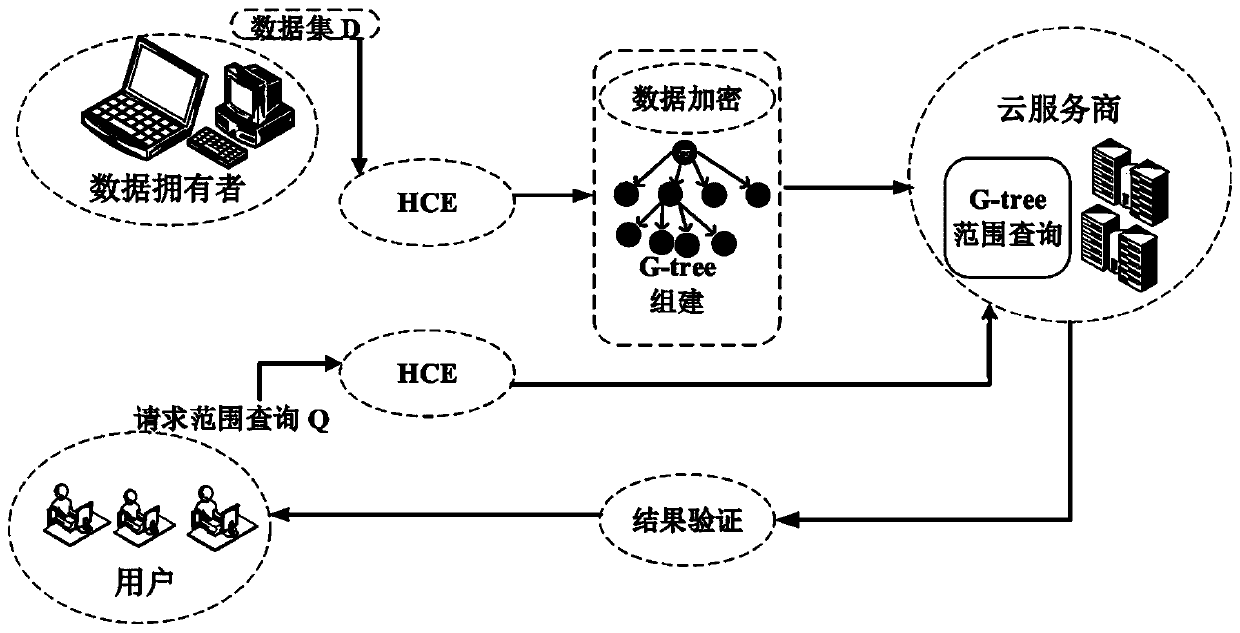
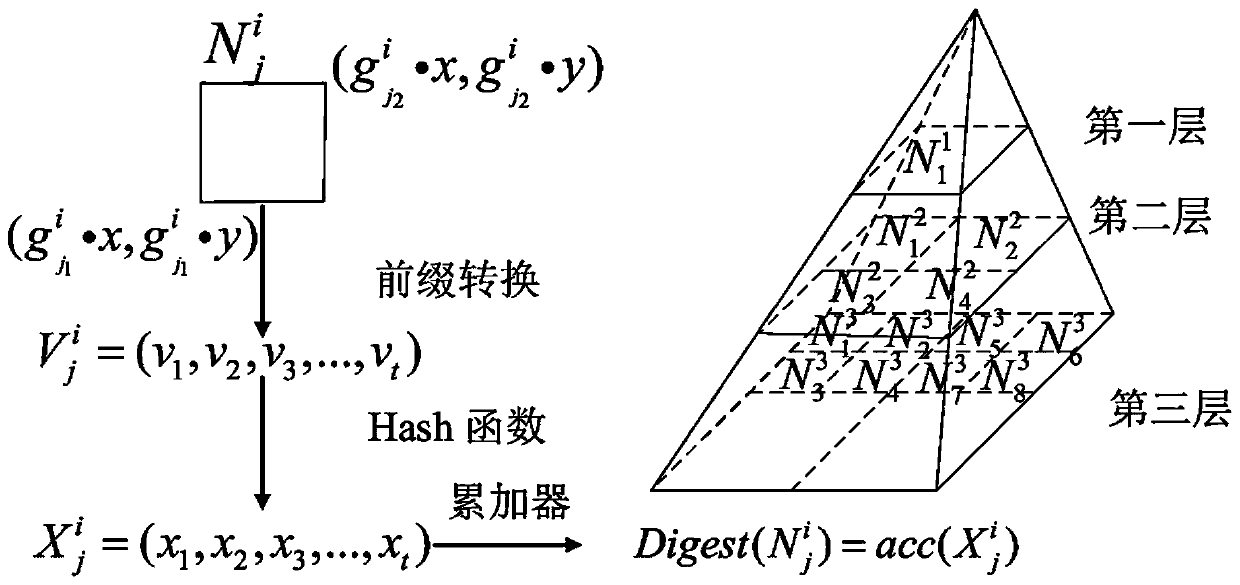
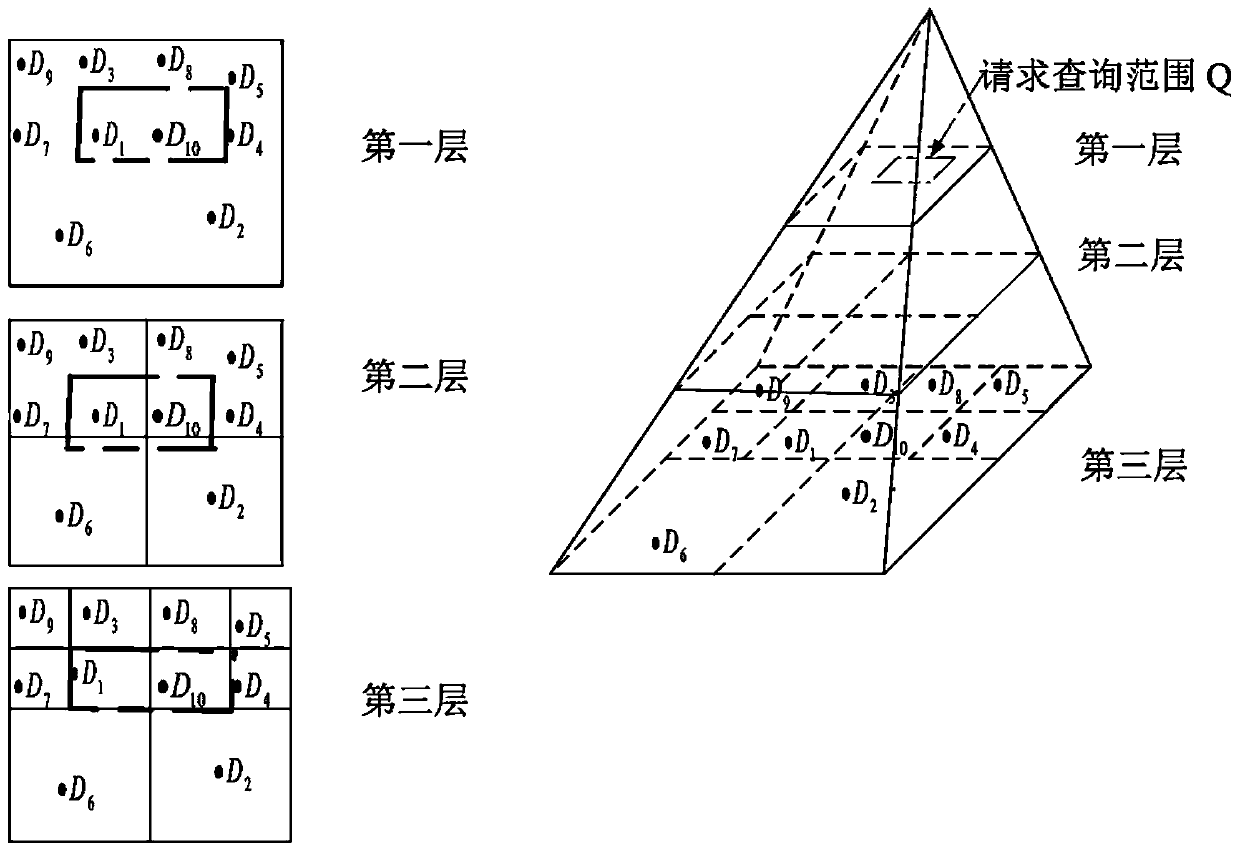
Verifiable range query method based on ciphertext spatio-temporal data
ActiveCN111274247AAchieving VerifiabilityRealization scopeDigital data protectionEnergy efficient computingAlgorithmCiphertext
The invention discloses a verifiable range query method based on ciphertext spatio-temporal data. The method comprises the following steps: step 1, a data owner generates different keys required in the whole verifiable range query process; step 2, a G-tree index structure is constructed by using a Hierachic cell based encoding algorithm, and the G-tree index structure is used for representing a G-tree index; 3, converting a query range request corresponding to spatio-temporal data sent by a query user into a prefix set in the G-tree index structure, and storing the prefix set into an accumulator to obtain a trap door of the range query request corresponding to the spatio-temporal data; and step 4, the cloud server searches the G-tree index structure according to a range query trap door corresponding to the spatio-temporal data to obtain a search result and verification information, and a query user verifies the search result to obtain the integrity of the search result. According to the method, the range query and verification of the ciphertext spatio-temporal data can be realized at the same time, the calculation overhead is reduced, and the query and verification efficiency is relatively high.
Owner:XIDIAN UNIV
Electronic ticket service system and realizing method thereof
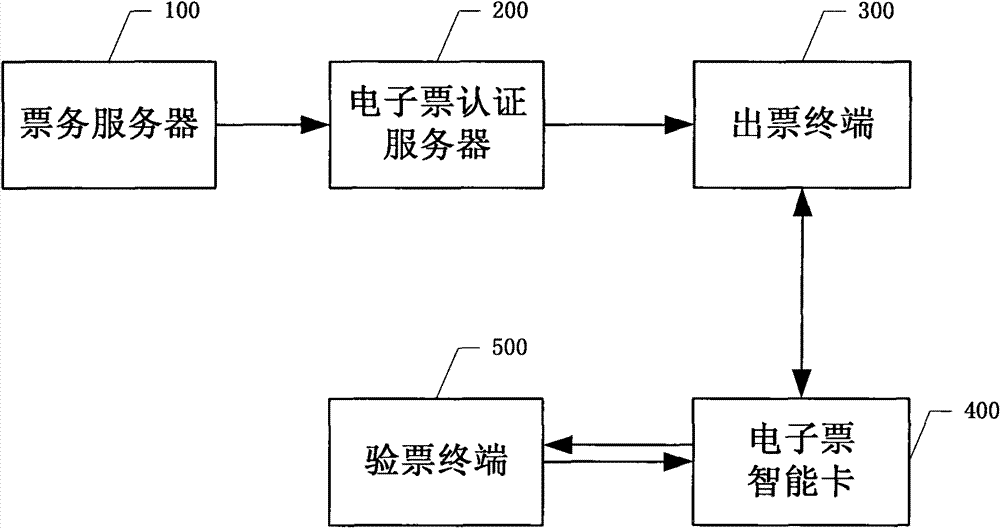
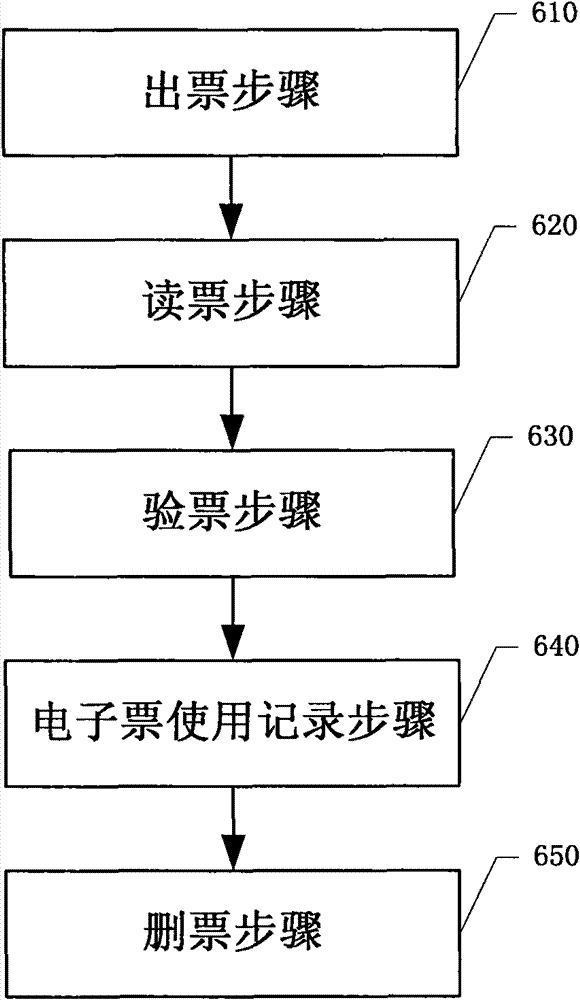
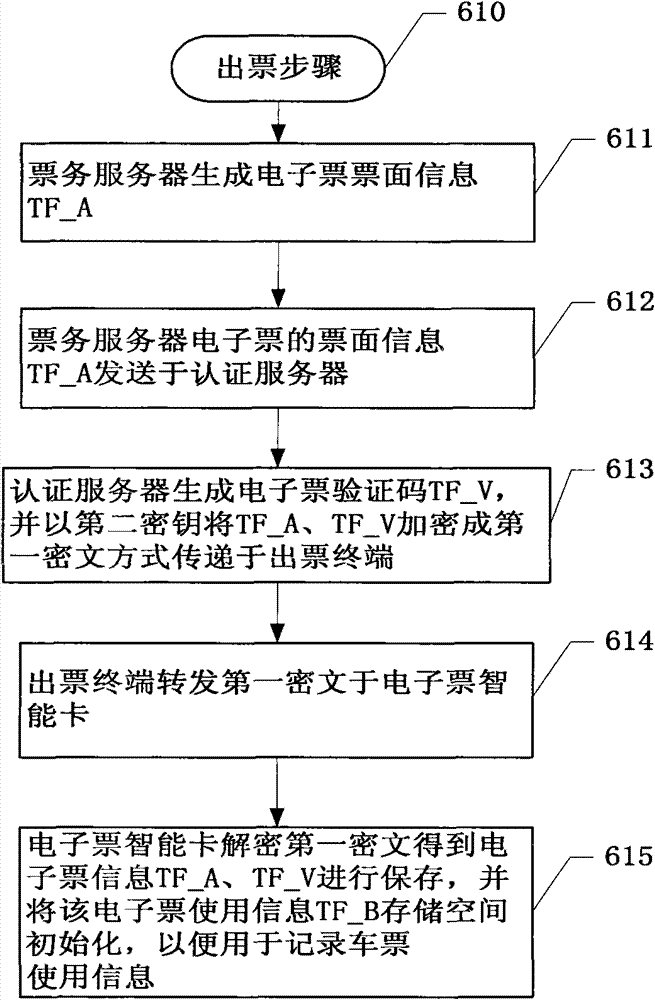
ActiveCN101859426BRealize electronicAchieving verifiabilityCommerceSpecial data processing applicationsCiphertextSmart card
The invention discloses an electronic ticket service system and a realizing method thereof. The method comprises the following steps of: generating electronic ticket surface information by a ticket service server; generating electronic ticket verification codes, encrypting the electronic ticket surface information and the electronic ticket verification codes into first ciphertext and transmittingto a ticket-drawing terminal in a safe mode by an electronic ticket authentification server; transferring the first ciphertext to an electronic ticket smart card by the ticket-drawing terminal; and receiving and decrypting the first ciphertext to acquire and store the electronic ticket surface information and the verification code by the electronic ticket smart card. The system and the method adopt a mode that the electronic ticket surface information which is generated by the ticket service server and the verification codes which is generated by the electronic ticket authentification server are safely transmitted to the ticket-drawing terminal, transferred in a ciphertext mode to the electronic ticket smart card and stored in the electronic ticket smart card, and the electronization, theverifiability, the accurate transmission, the safe storage and the copy protection of tickets and the record electronization of ticket use information are realized.
Owner:SHENZHEN NATIONZ ELECTRONIC COMMERCE CO LTD
Message source verification method, device and system and message sending method and device
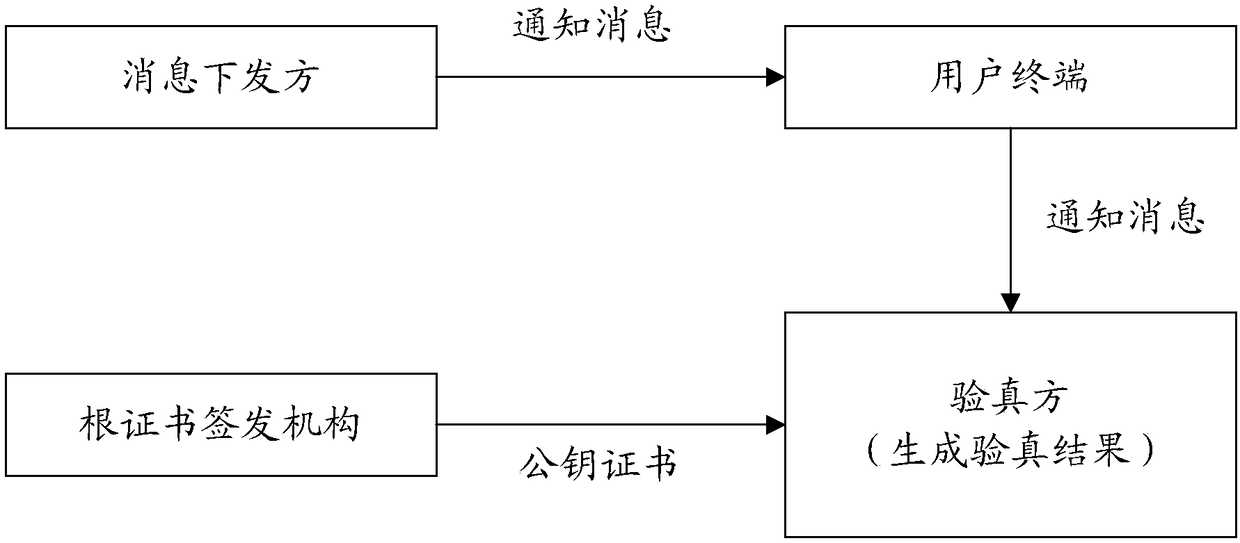
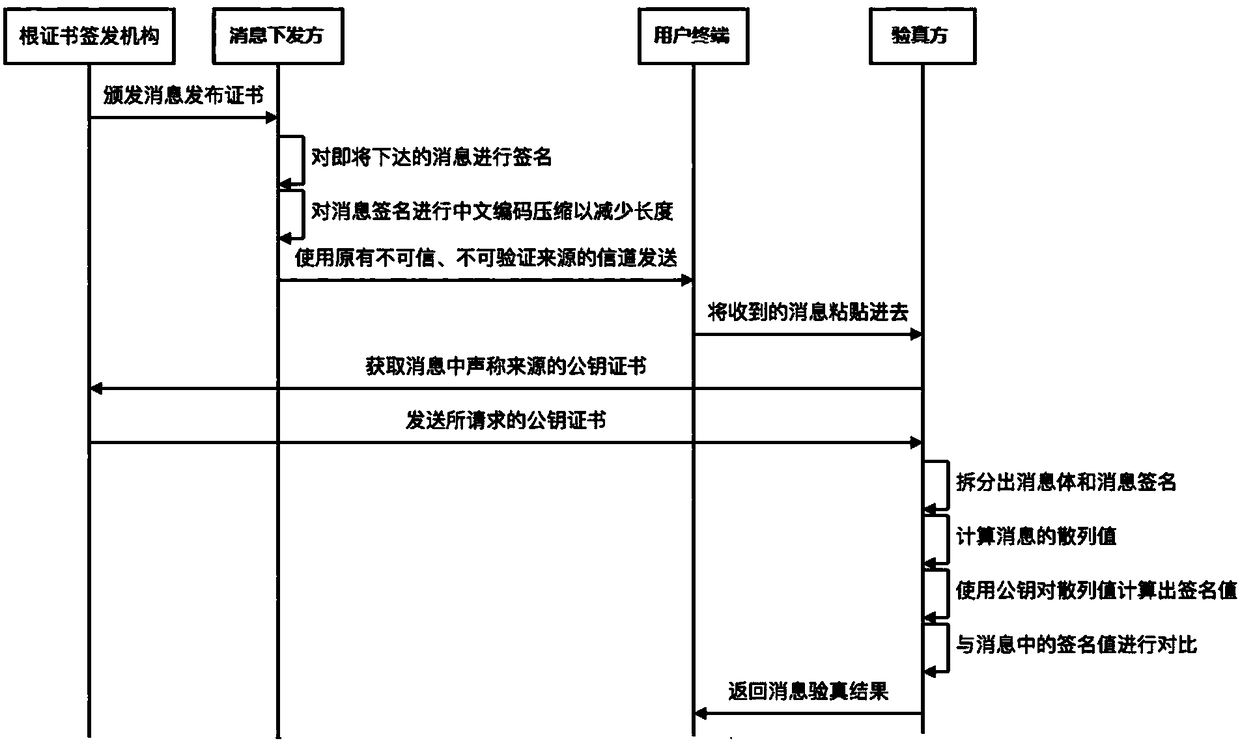
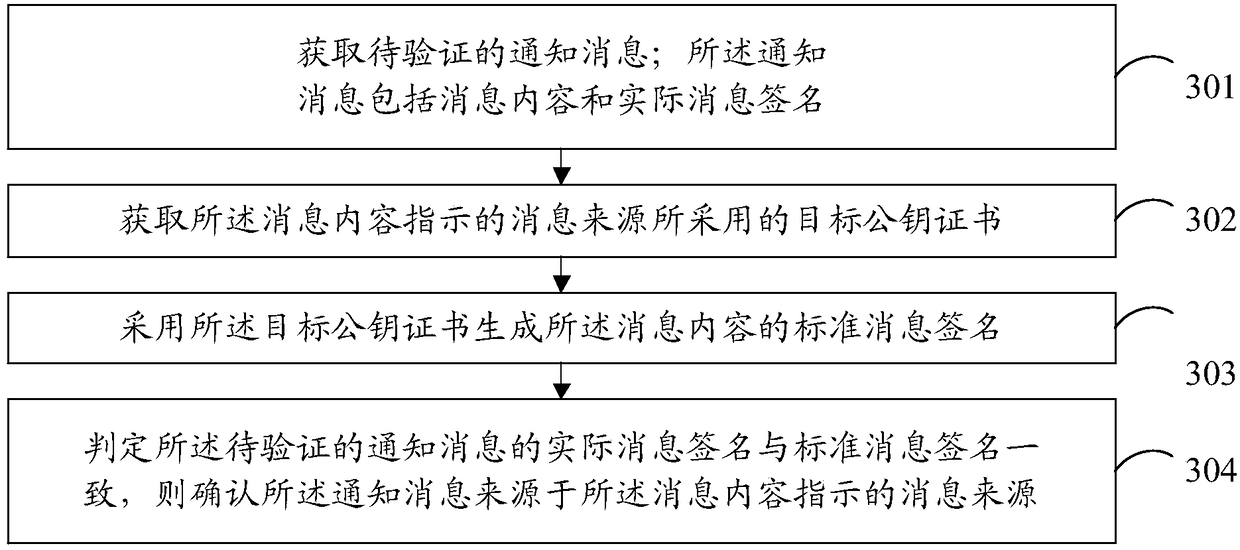
ActiveCN108270567AReduce risk of property damageImplement offline verificationUser identity/authority verificationComputer hardwarePublic key certificate
The embodiment of the invention provides a message source verification method and device. The method comprises the steps that a notification message to be verified is acquired, wherein the notification message includes the message content and the actual message signature; the target public key certificate acquired by the message source indicated by the message content is acquired; the standard message signature of the message content is generated by using the target public key certificate; and the actual message signature of the notification message to be verified is judged to be consistent with the standard message signature so that the notification message is ensured to be from the message source indicated by the message content. The reliability of the message source of the notificationmessage can be identified so that the risk of property loss caused by the fact that the forged and fake message source is difficult to be identified by the user can be reduced.
Owner:ALIBABA GRP HLDG LTD
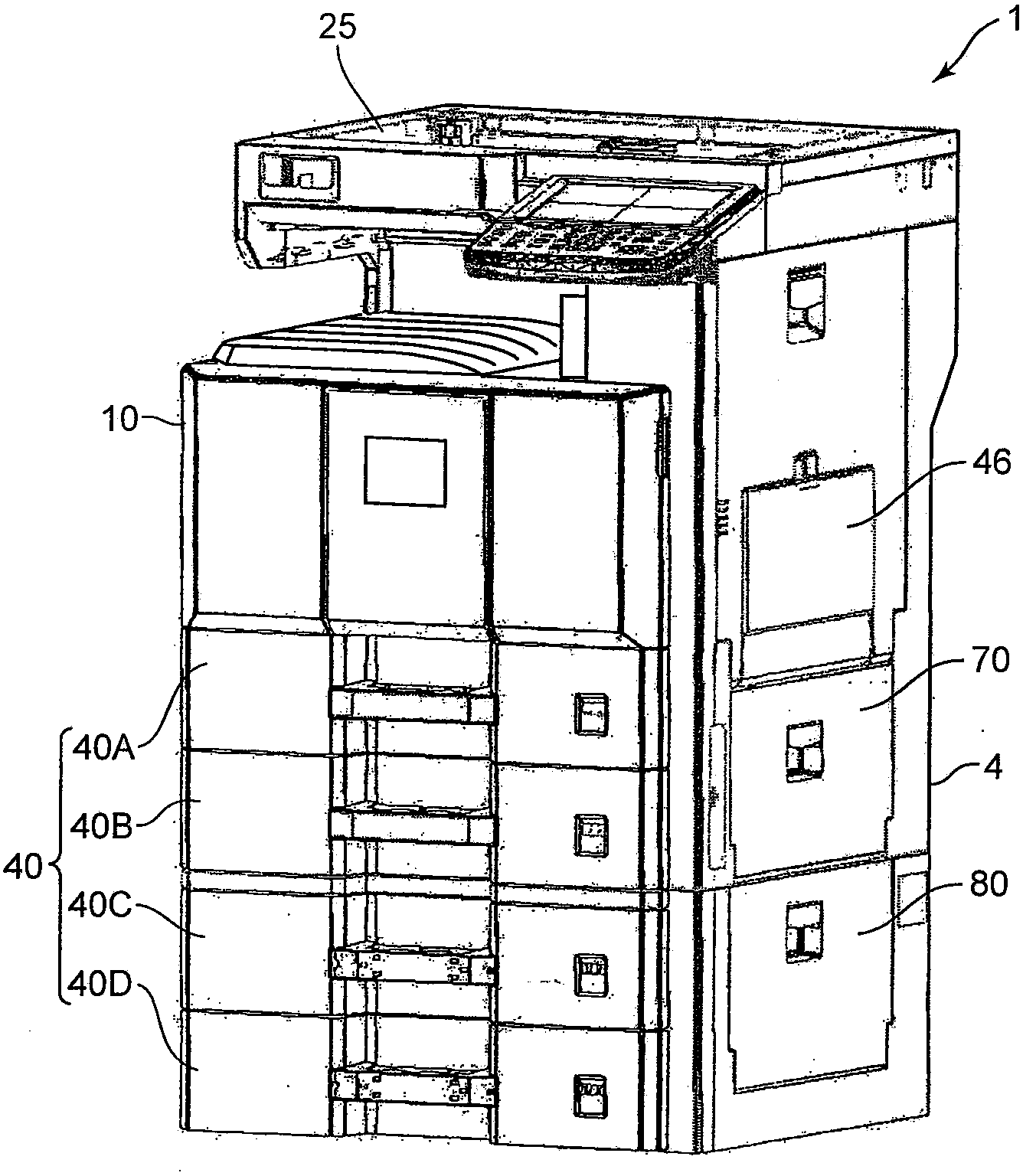
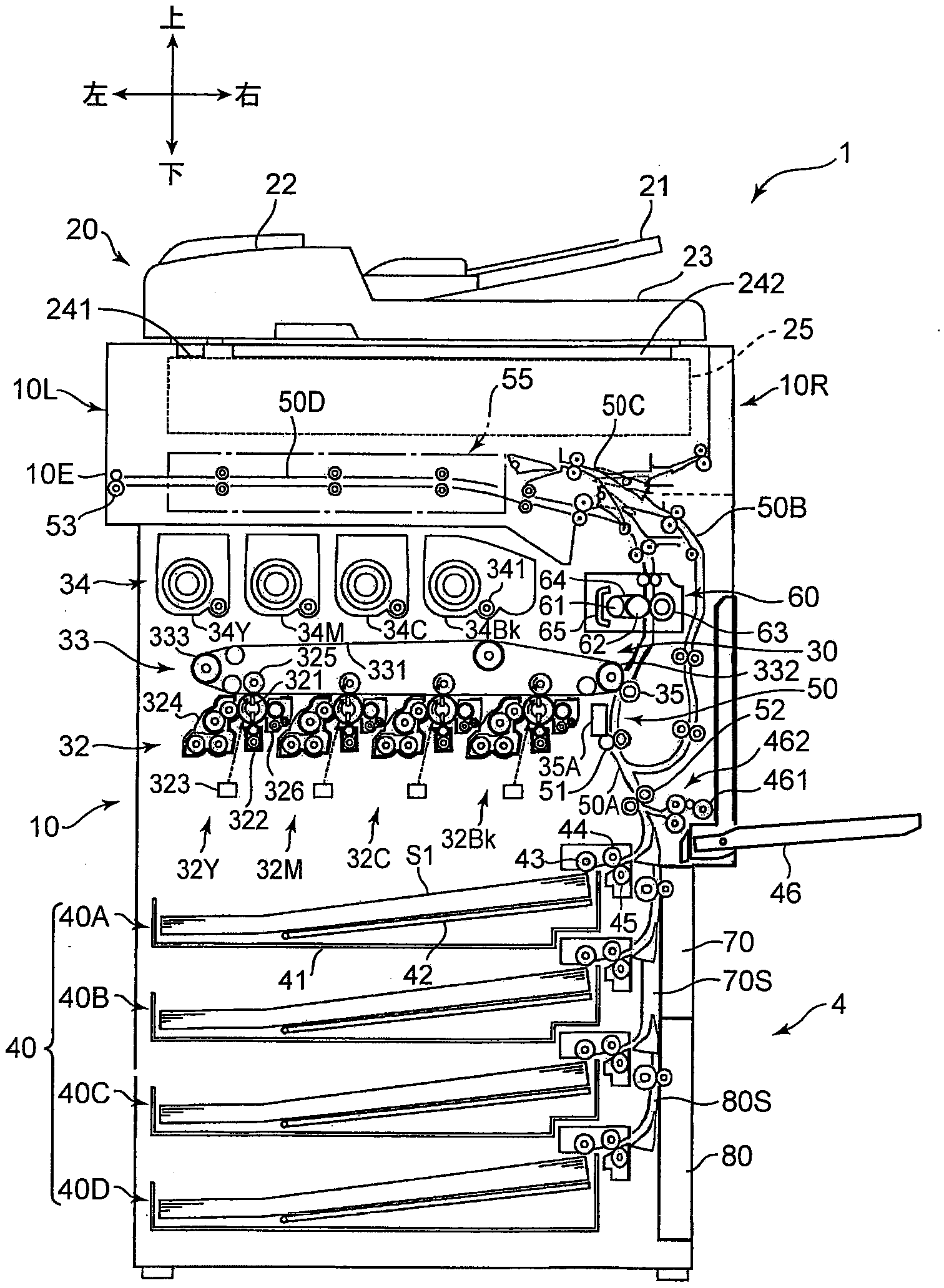
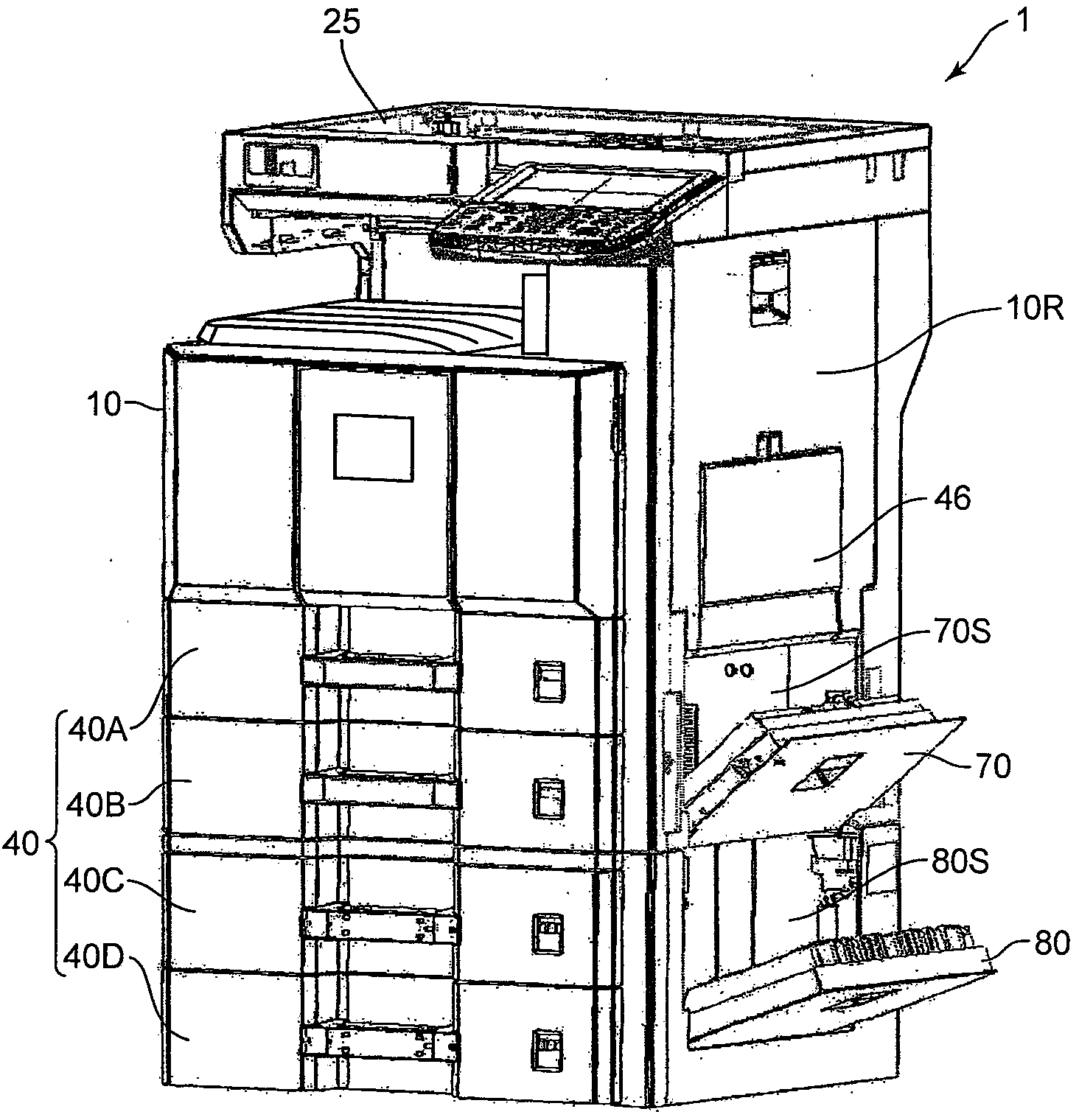
Sheet feeding device, and image forming apparatus provided with same
Owner:KYOCERA DOCUMENT SOLUTIONS INC
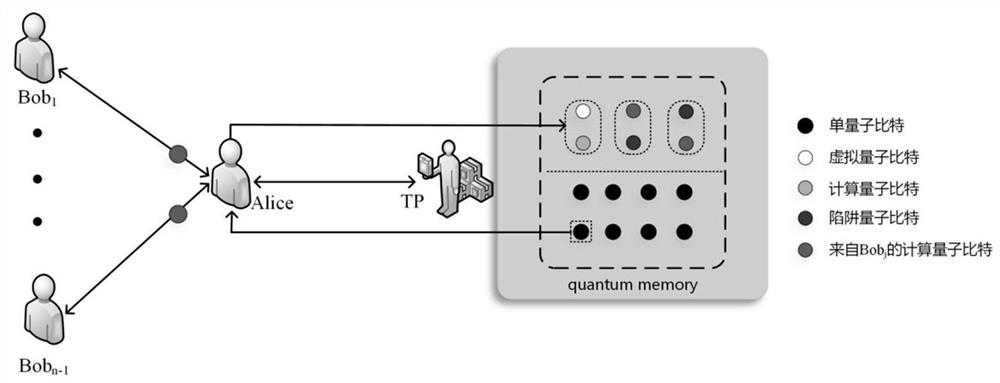
Secure multi-party computing method based on verifiable blind quantum computing
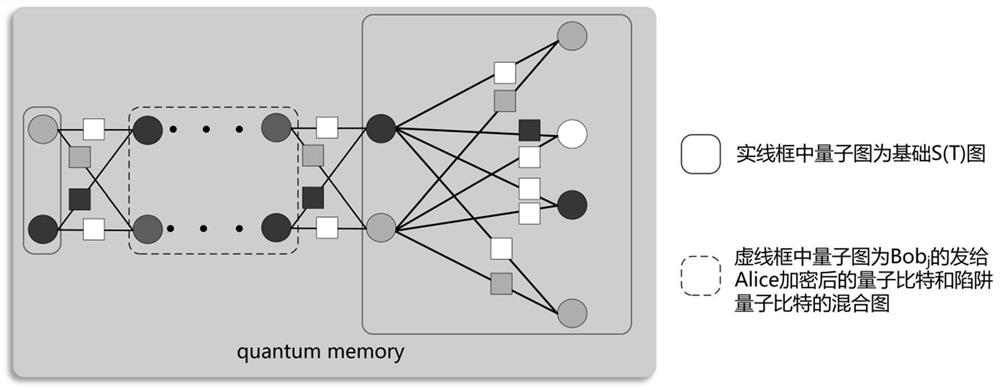
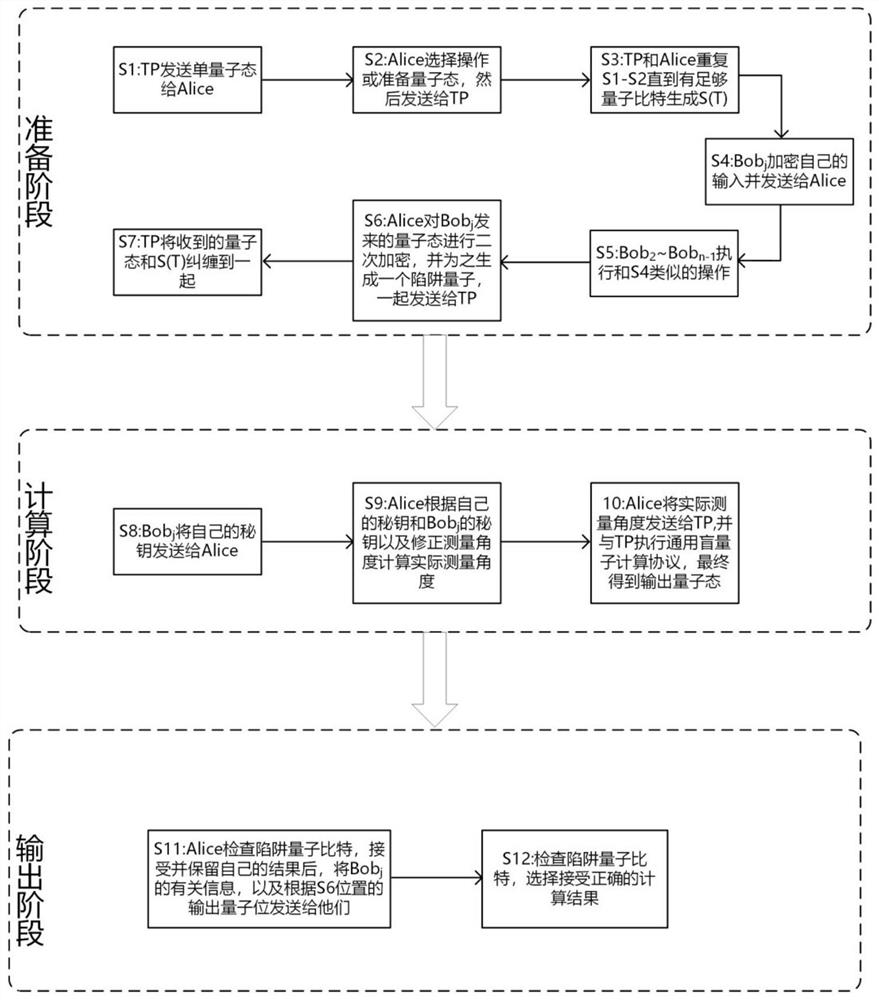
PendingCN113708926AReduce consumptionImprove practicalityQuantum computersKey distribution for secure communicationAlgorithmTheoretical computer science
The invention belongs to the field of quantum cryptography, and particularly relates to a secure multi-party computing method based on verifiable blind quantum computation. The secure multi-party computing method comprises the three stages that the first stage is a preparation stage, and in the preparation stage, an S (T) graph is systematically generated and generated quantum bits are subjected to data encryption processing; the second stage is a calculation stage, and the final output quantum state is calculated according to the actually measured angle by calculating the actually measured angle; and the third stage is an output stage, in the output stage, trap quantum bits are checked through Alice to determine a correct calculation result, and the result is output. According to the method, the number of participated clients is expanded from two clients to multiple clients, the requirement of multi-party calculation can be met, and the method has higher expansibility and practicability.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
System for storing, processing, and accessing medical data
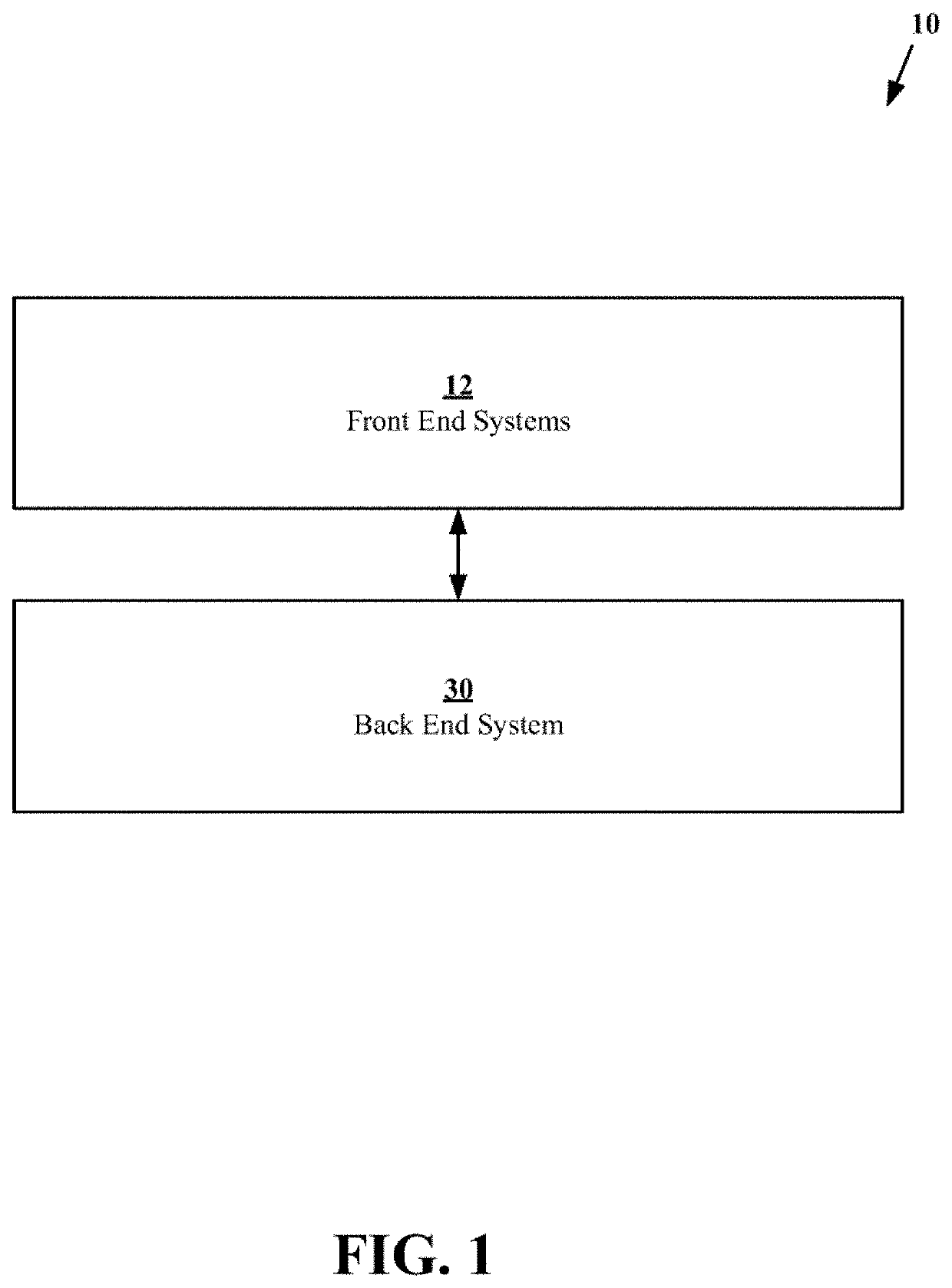
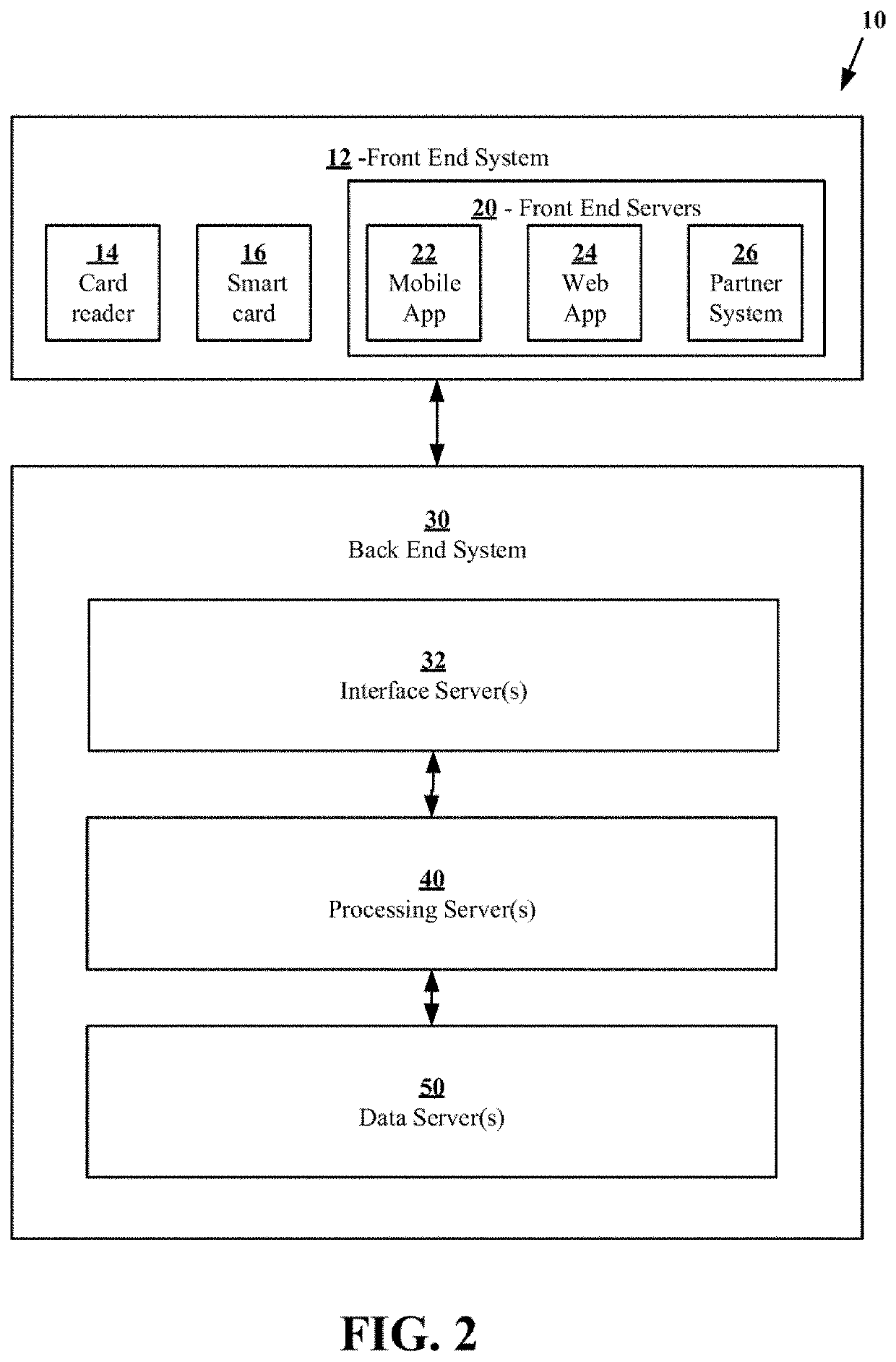
ActiveUS20210037117A1Facilitates transparencyImprove securityEncryption apparatus with shift registers/memoriesDrug and medicationsEnd systemEngineering
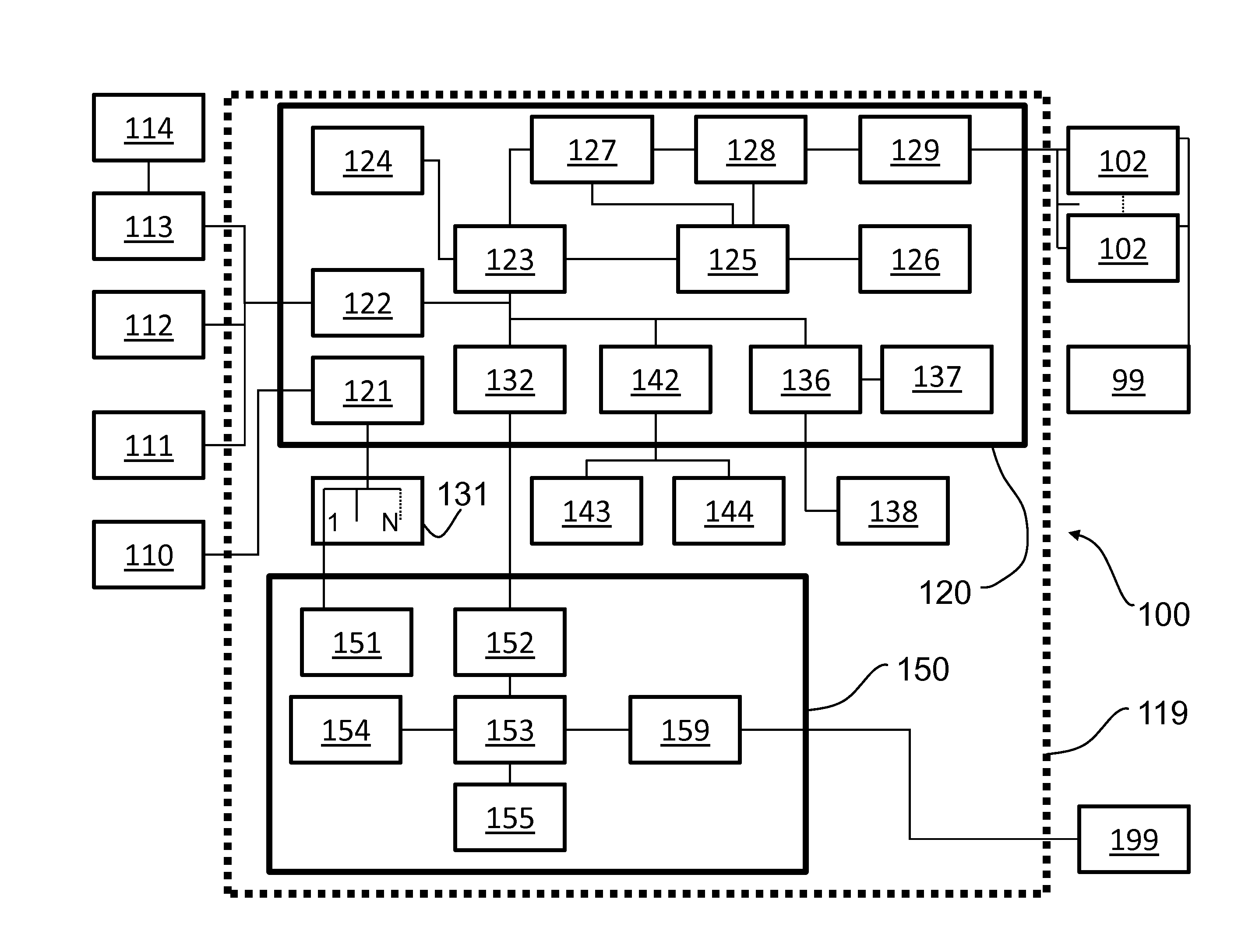
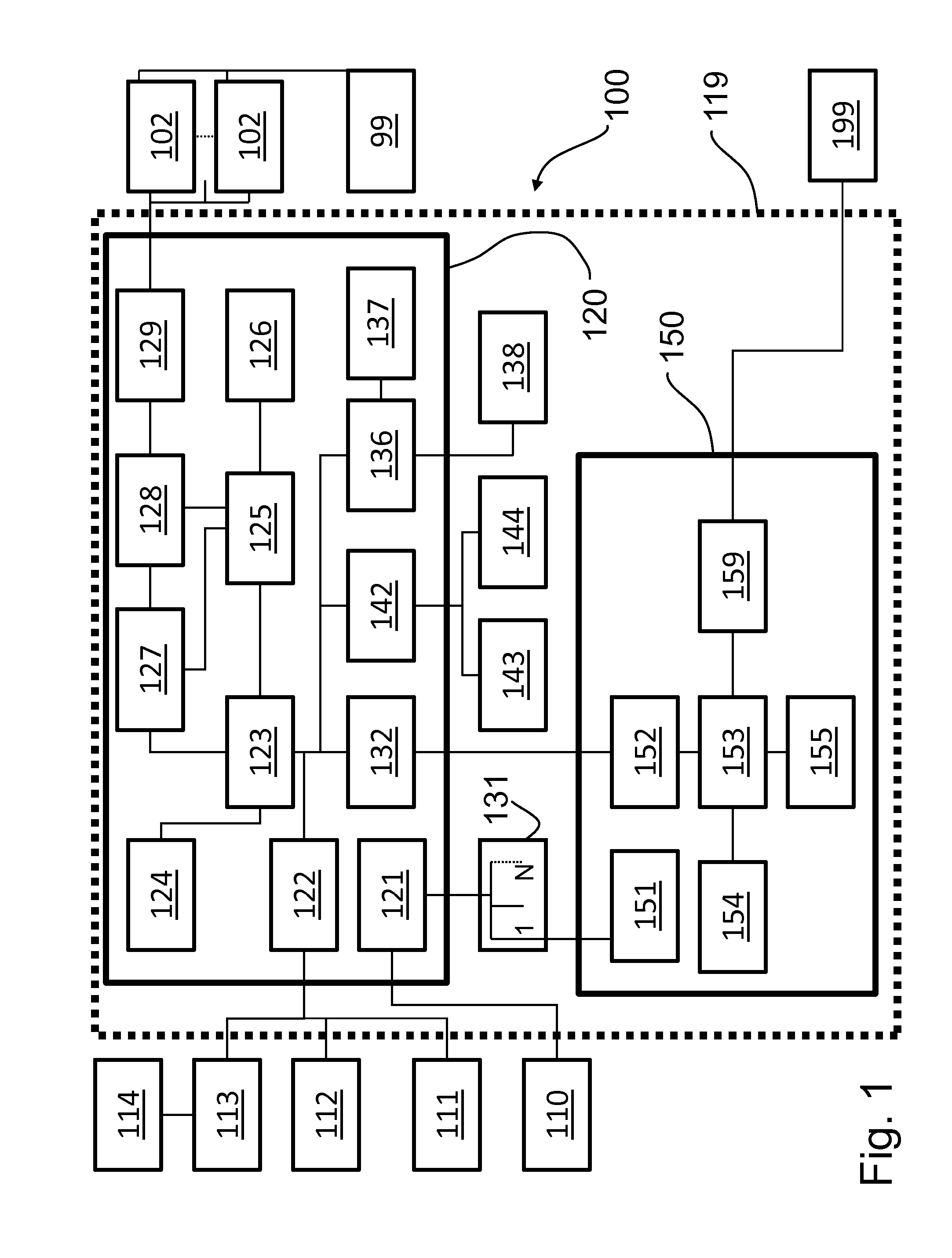
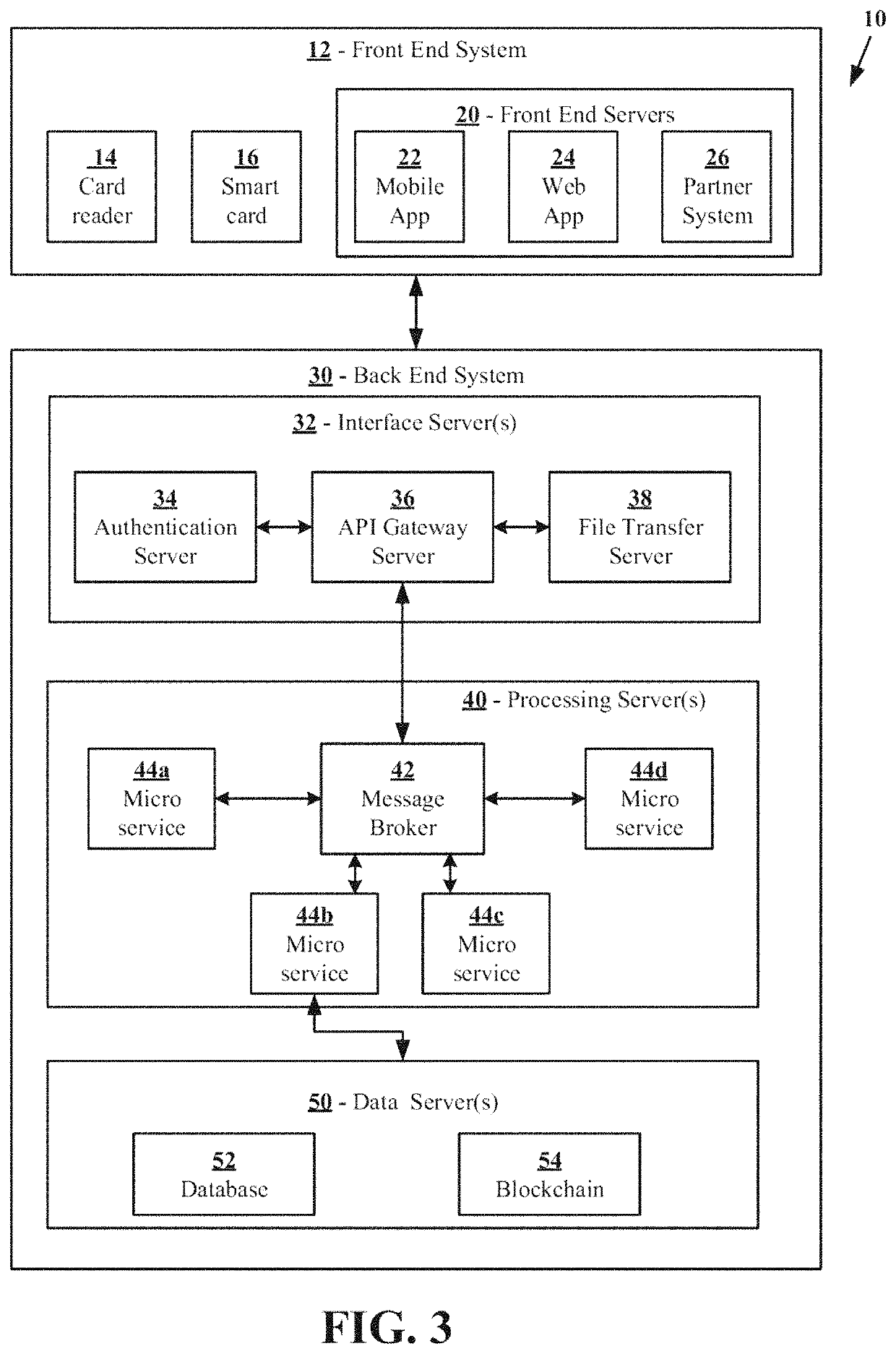
A system is disclosed for storage, processing, and accessing of data. The system includes a front end system and a back end system communicatively connected to the front end system. A front end system is configured to provide one or more user interfaces configured to store, process, and access data in a first data server, in response to user input, by sending messages to the back end system. The back end system includes the first data server and one or more processing servers. The one or more processing servers are configured to process messages received from the front end system by accessing in the first data server to perform one or more operations specified by the messages. The back end system also includes a blockchain server configured to maintain a record of changes made to data in the first data server by the one or more processing servers.
Owner:JOHNSON TIM DONALD
System for storing, processing, and accessing medical data
ActiveUS11277497B2Facilitates transparencyImprove securityEncryption apparatus with shift registers/memoriesDrug and medicationsEnd systemEngineering
A system is disclosed for storage, processing, and accessing of data. The system includes a front end system and a back end system communicatively connected to the front end system. A front end system is configured to provide one or more user interfaces configured to store, process, and access data in a first data server, in response to user input, by sending messages to the back end system. The back end system includes the first data server and one or more processing servers. The one or more processing servers are configured to process messages received from the front end system by accessing in the first data server to perform one or more operations specified by the messages. The back end system also includes a blockchain server configured to maintain a record of changes made to data in the first data server by the one or more processing servers.
Owner:JOHNSON TIM DONALD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com