Multi-biological feature authentication or identification-based method and system
A biometric and authentication technology, applied in the field of information security, can solve problems such as tampering with identification or authentication, information security cannot be guaranteed, and operators lose consciousness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
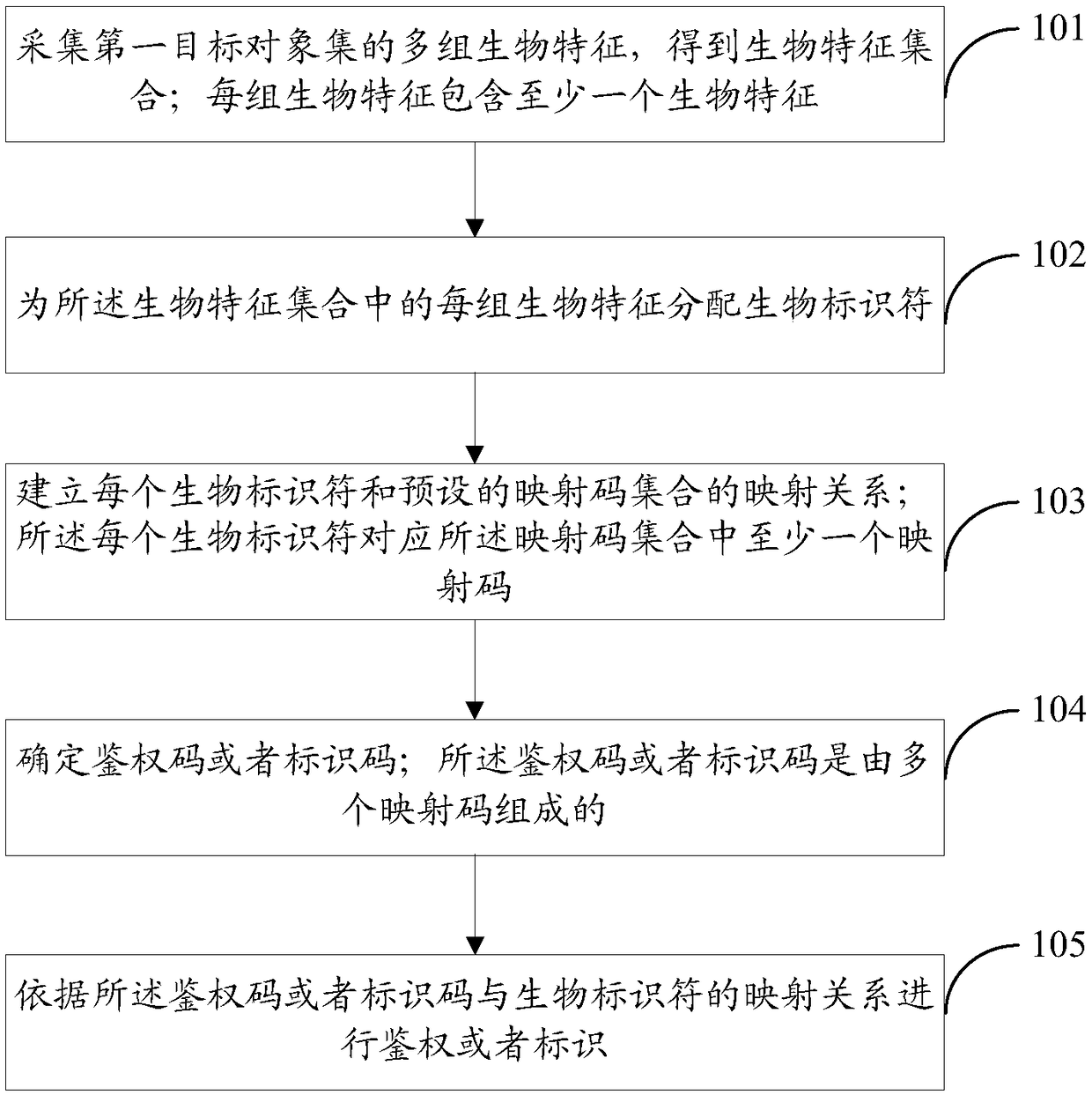
[0151] Embodiment 1: Call the pre-set authentication code or identification code from the database;
[0152] It can be seen that before executing S104, the authentication code or identification code has been set in advance, and the operation of this embodiment is to establish the mapping relationship between the original authentication code or identification code and the biometric feature, so that the biometric feature can be used for authentication. rights or identification.
Embodiment approach 2
[0153] Embodiment 2: Edit and / or combine multiple mapping codes to generate an authentication code or an identification code.
[0154] It can be seen that Embodiment 2 is generated after re-editing and / or combining the mapping code, and is generated after editing and / or combining the mapping code corresponding to the identification code of the biometric feature set. Among them, editing and / or combining the mapping codes may include multiple implementations, which are not limited in this embodiment. In order to facilitate the understanding of this part, this embodiment provides several optional implementations:
[0155] Method 1: Combine part or all of the mapping codes in an orderly manner to obtain the authentication code or identification code;
[0156] In this embodiment, it can be understood that the obtained authentication code or identification code is an ordered mapping code.
[0157] For example: Assume that the biometric feature set includes: fingerprint, iris, dynam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com