Patents
Literature
47results about How to "Enhanced non-repudiation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Authentication system based on biological characteristics and identification authentication method thereof
InactiveCN101330386AAttack is notAttacks are not directlyUser identity/authority verificationCharacter and pattern recognitionInternet privacyComputer terminal
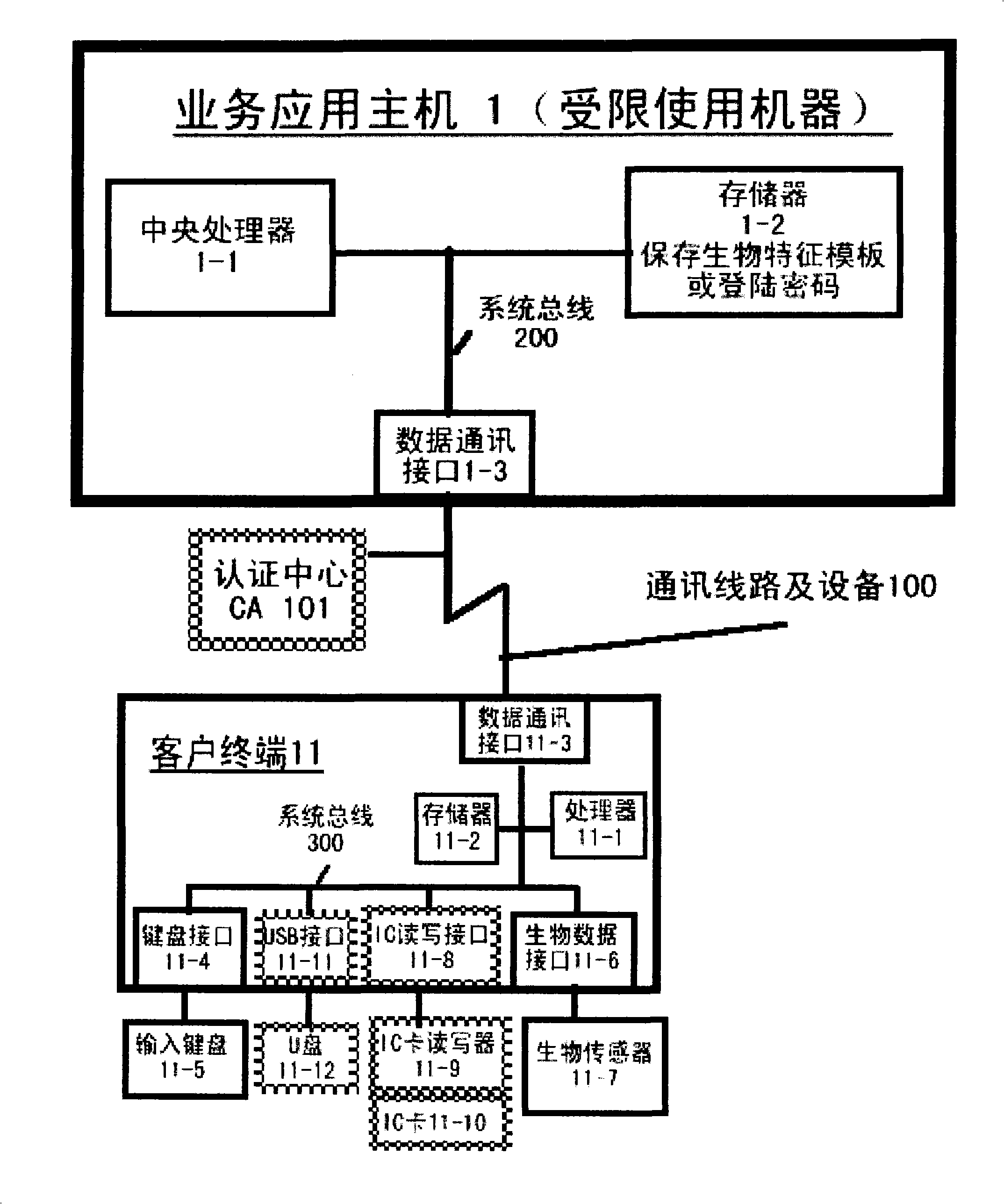
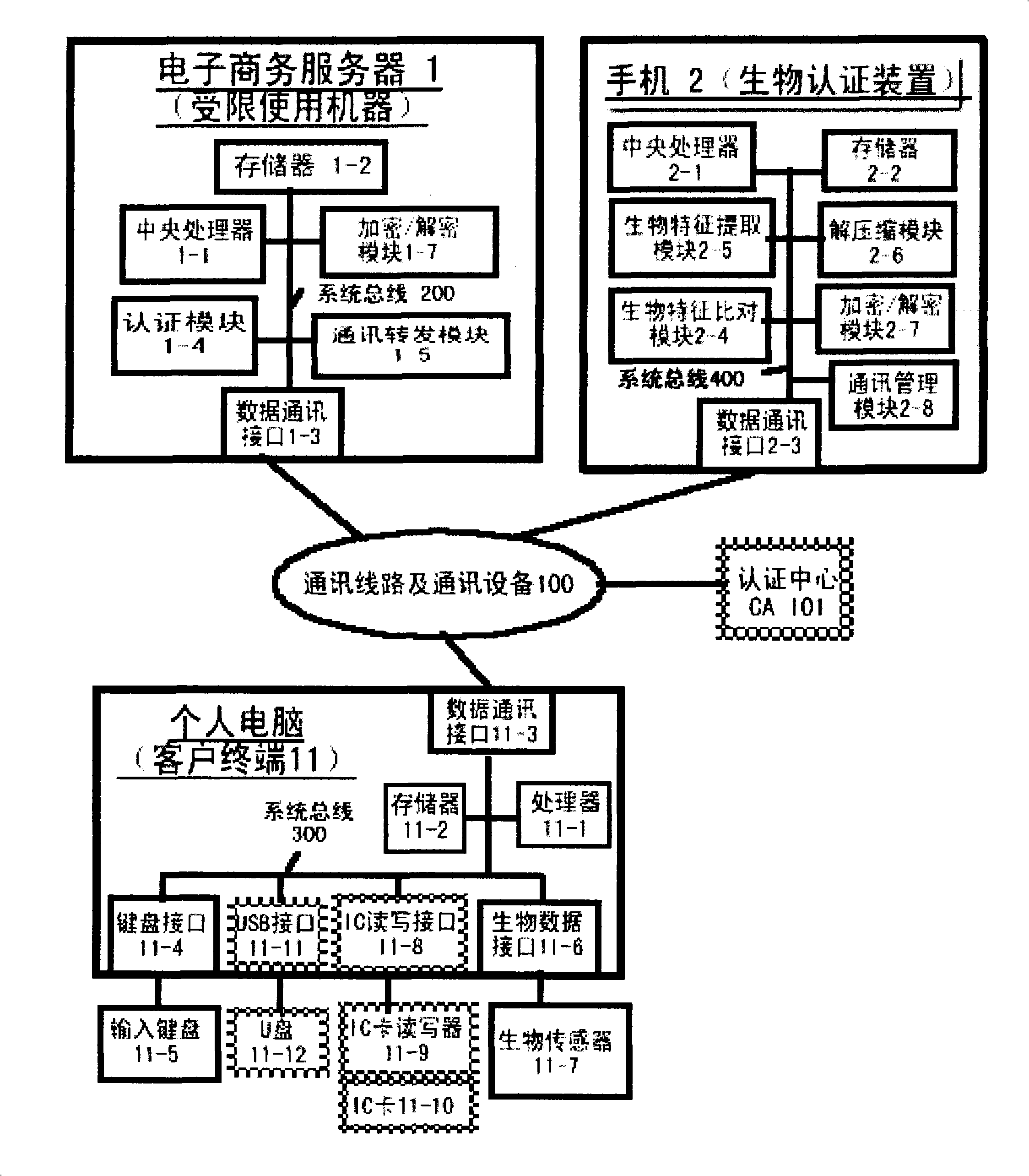
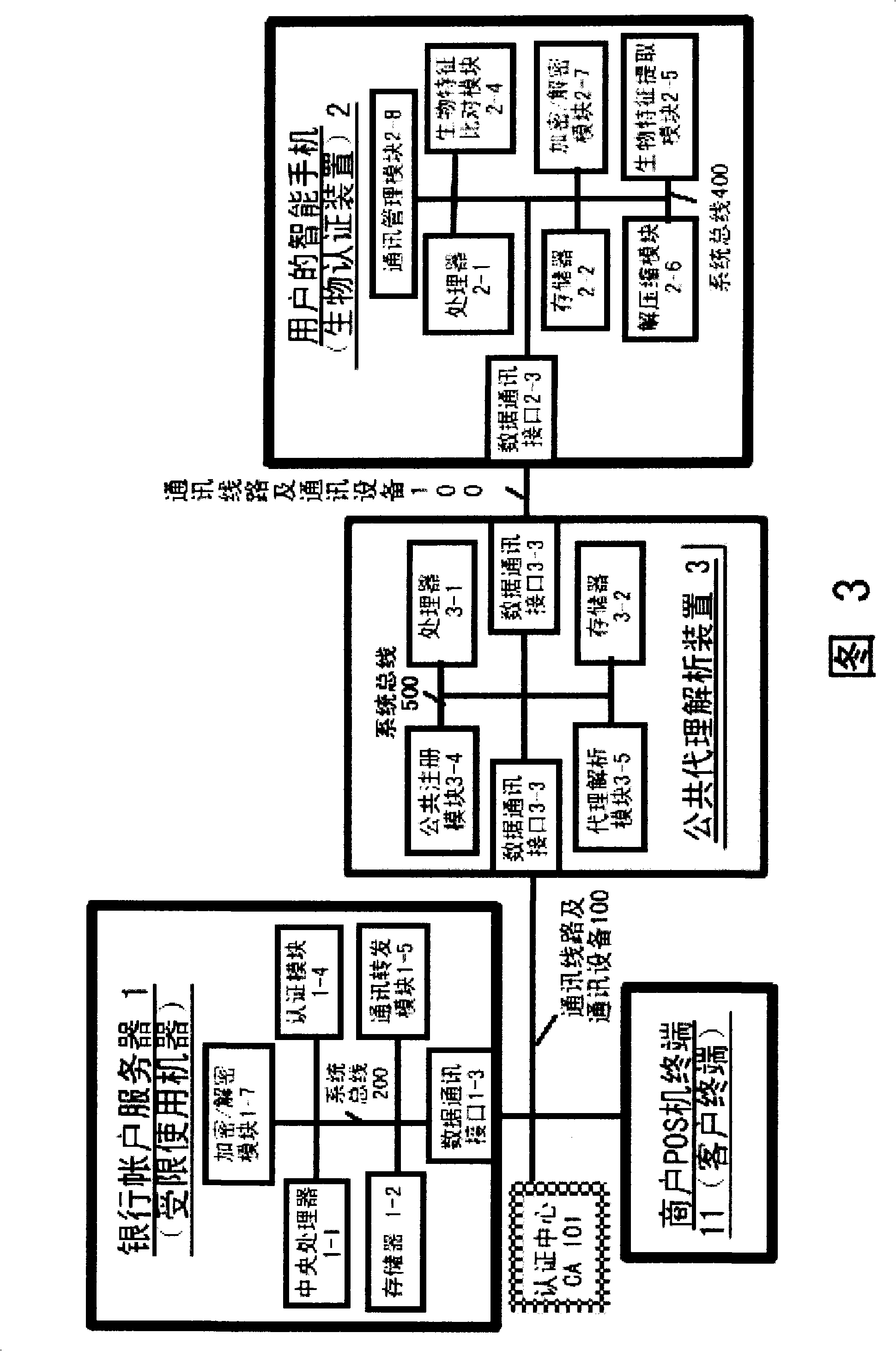
The invention relates to an authentication system and an authentication method based on biological features. The method comprises the steps of conducting centralized storage and biological feature comparison operation for a large quantity of user biological feature templates according to user ID identifiers stored on a memory on a limited use machine and corresponding biding ID identifiers thereof on a biological authentication device of a digital processing terminal; separating the biological feature templates from the authentication function of the limited use machine; allocating to digital processing terminals (including PCs, notebooks or mobile phones, PDAs of users)of users as biological authentication device-storing the biological feature templates with decentralization and operating and processing biological features to be authenticated with decentralization so as to conduct comparison with the biological feature templates pre-stored on the respective digital processing terminals; feeding back comparison and verification results to the limited use machines; authorizing to conduct equal authentication of the biological authentication device ID identifier on the digital processing terminal for the corresponding binding user ID identifiers by the centralized authentication of the limited use machine according to the comparison verification result data.
Owner:刘洪利
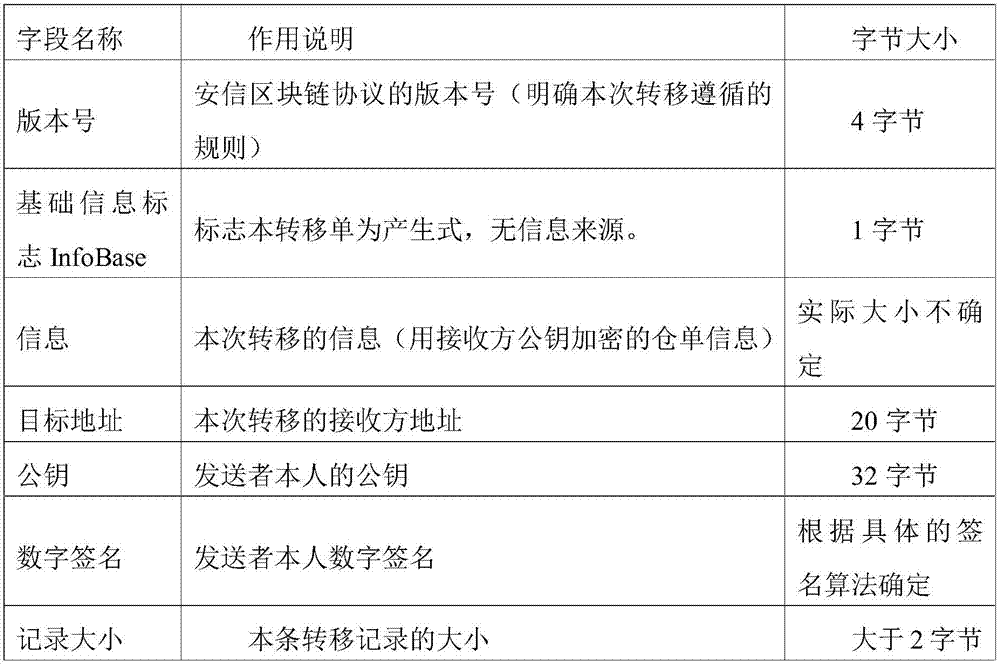
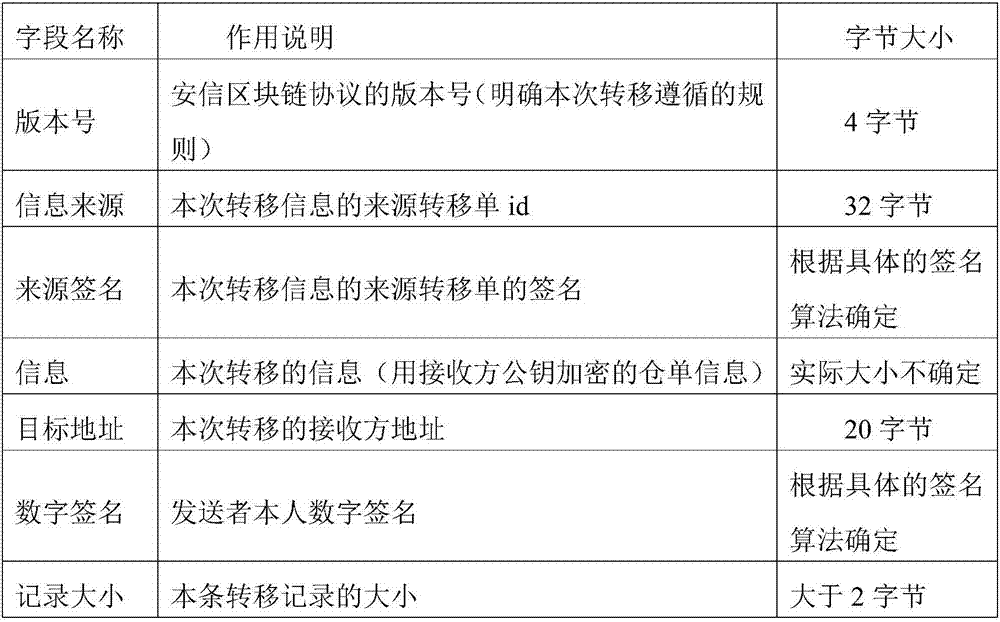
Warehouse receipt transaction security enhancing method in warehouse receipt system based on blockchain
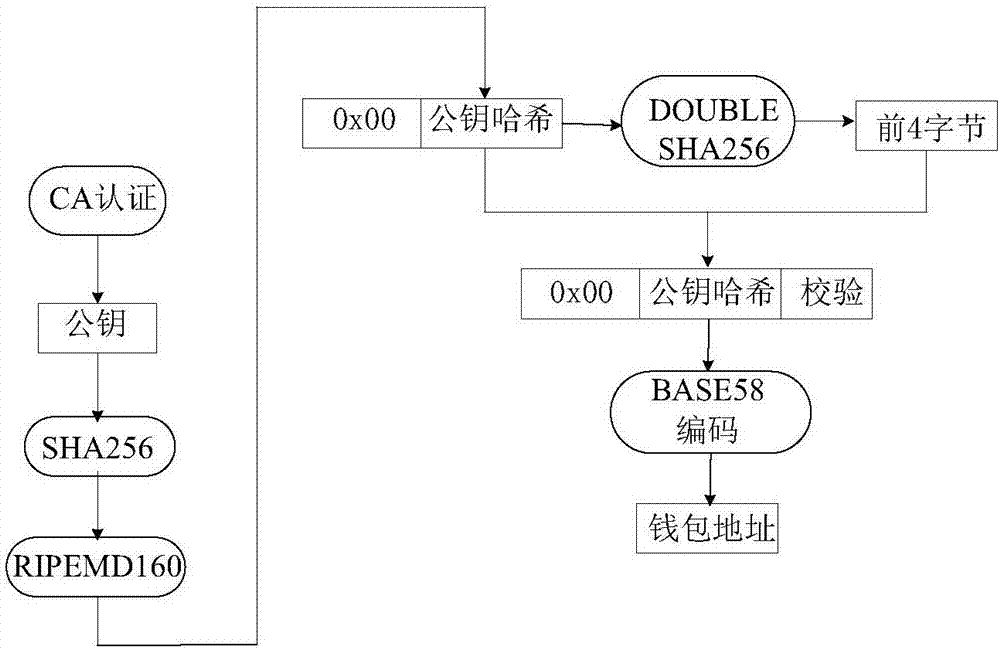
The present invention discloses a warehouse receipt transaction security enhancing method in a warehouse receipt system based on the blockchain. The method comprises that: public keys and private keys capable of verifying the identity of each node are generated by using a CA certification mechanism, wherein the warehouse receipt issuance node of the warehouse receipt system is taken as the node of a sender, a warehouse receipt is generated after the completion of warehousing, and warehouse information is encrypted by using the public key of the receiver to form a ciphertext; the ciphertext is signed by using the private key of the receiver, and a transfer order is made to be sent to the node of the receiver in the form of the broadcasting; and in each process of warehouse receipt transaction, the intermediate node and the node of the receiver use the public key of the sender to verify and sign the transfer order, and if the receiver needs to use the warehouse receipt, the private key of the receiver must be used to decrypt the warehouse receipt information on the transfer order. According to the warehouse receipt transaction security enhancing method in the warehouse receipt system based on the blockchain provided by the present invention, through the double verification mechanism of CA certification, and encryption and signature, the security of the warehouse receipt transaction and the privacy of the warehouse receipt system are improved.
Owner:深圳市华深安信科技有限公司
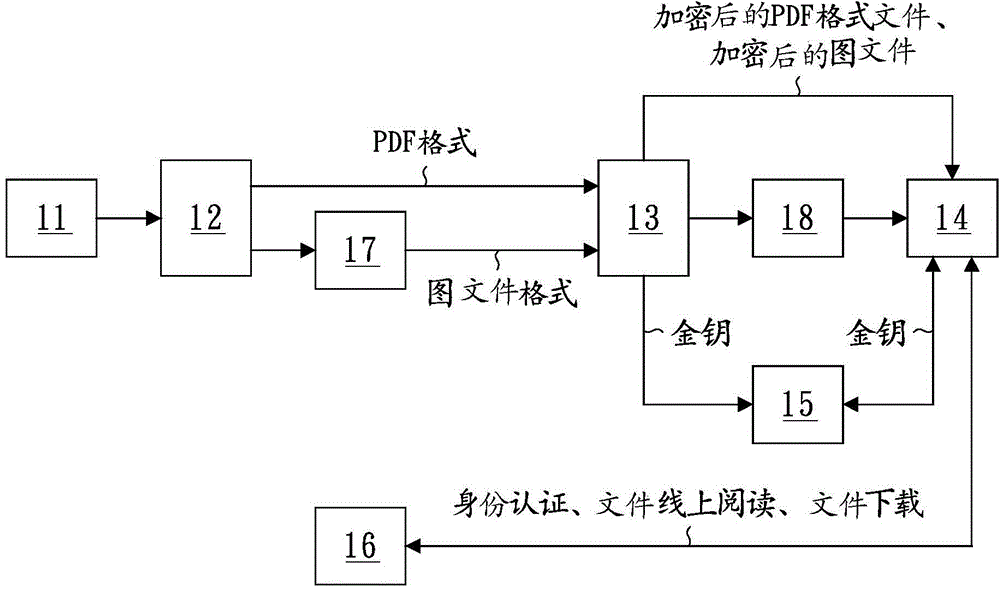
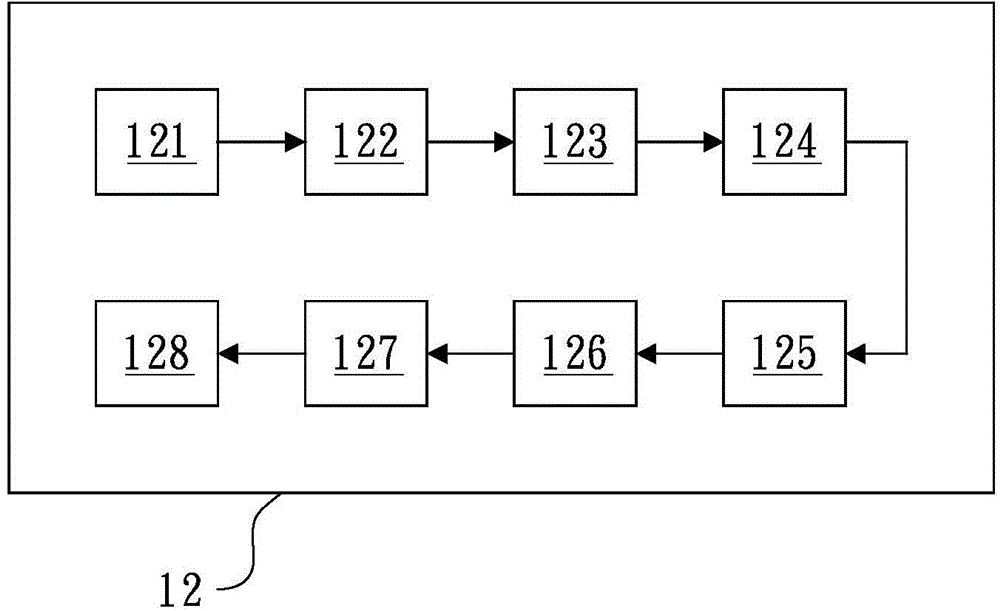
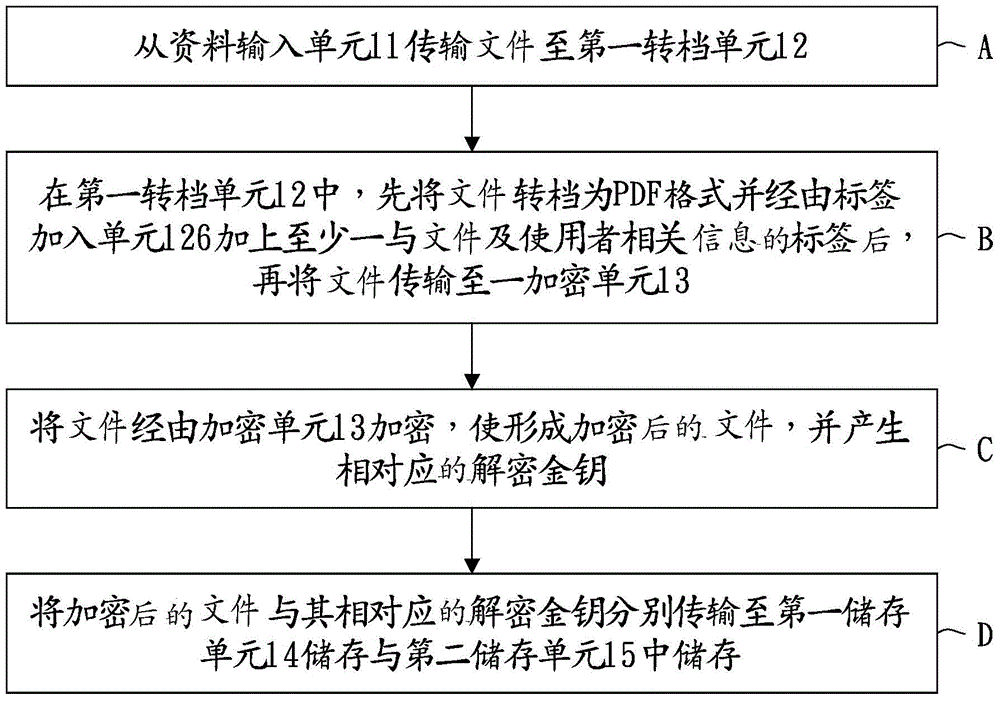
System and method for on-line adding of instant file dynamic label and on-line encryption
InactiveCN105323064AImprove securityImprove reliabilityKey distribution for secure communicationUser identity/authority verificationEncryptionDisk encryption
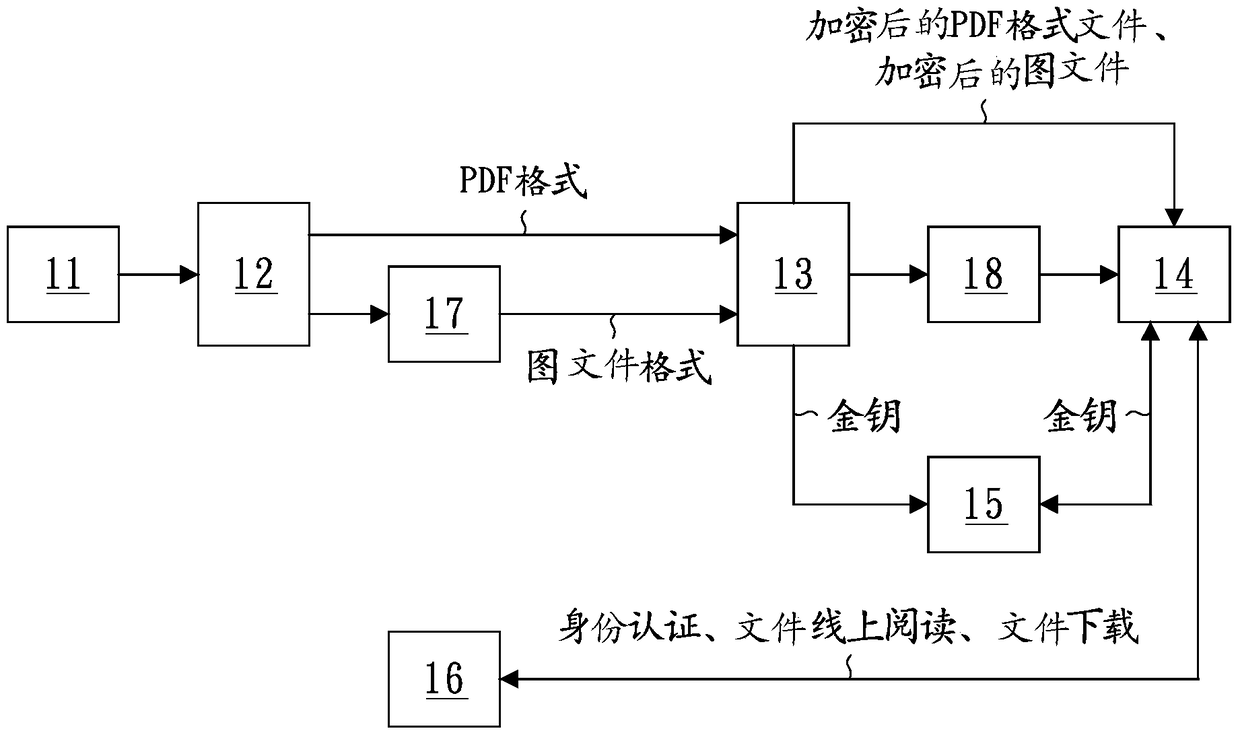
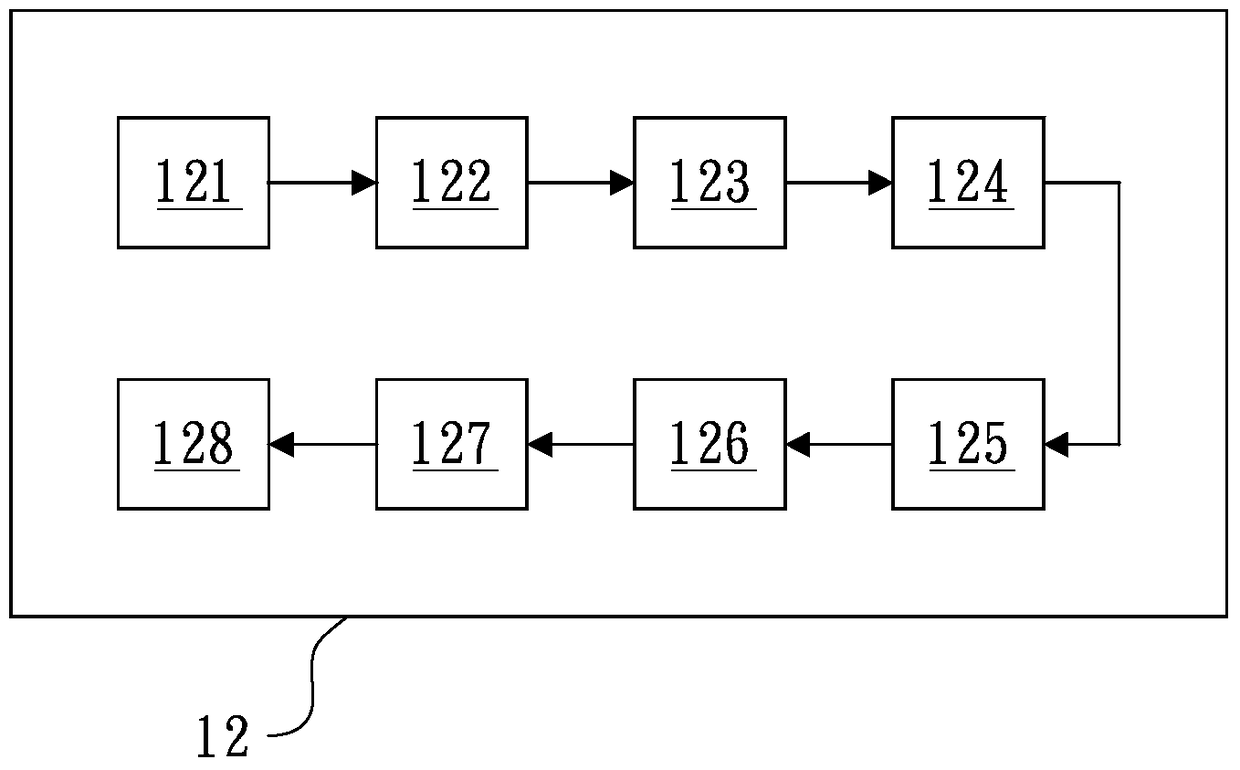
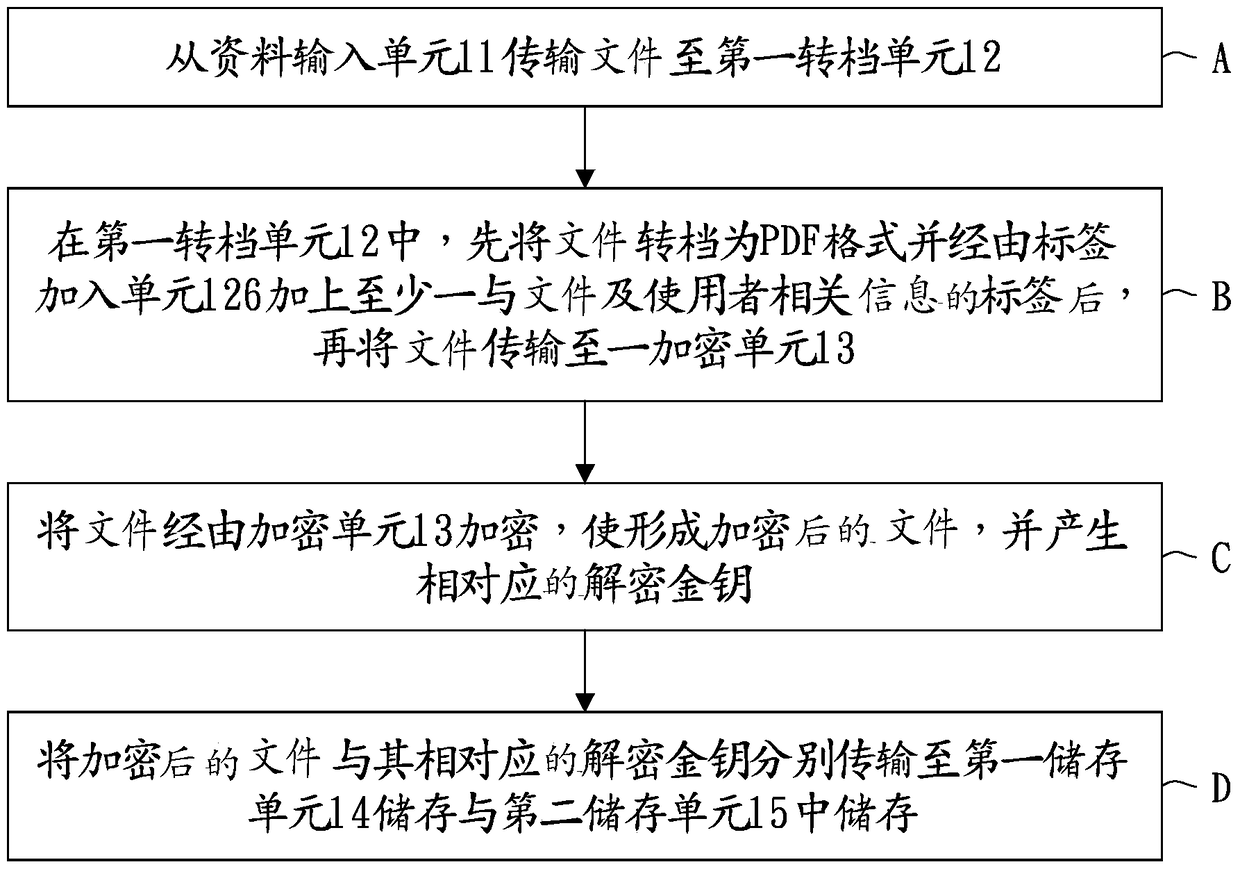
The invention discloses a system and method for the on-line adding of an instant file dynamic label and on-line encryption, and the system and method are used for converting each file, and adding at least one label which has the information related with the file and a user. According to the demands of the user, the system and method carry out encryption of the file, so that the user decrypts and watches the file. The method comprises the steps: firstly transmitting at least one file through a data input unit; secondly converting the file from the data input unit into a file at a format of PDF through a first conversion unit, and adding the label, which has the information related with the file and the user, through a label adding unit; thirdly carrying out the encryption of the file from the first conversion unit through an encryption unit, forming an encrypted file, and generating a corresponding decryption key; and finally enabling the encrypted file and the corresponding decryption key to be respectively transmitted to a first storage unit and a second storage unit for storage.
Owner:柯呈翰
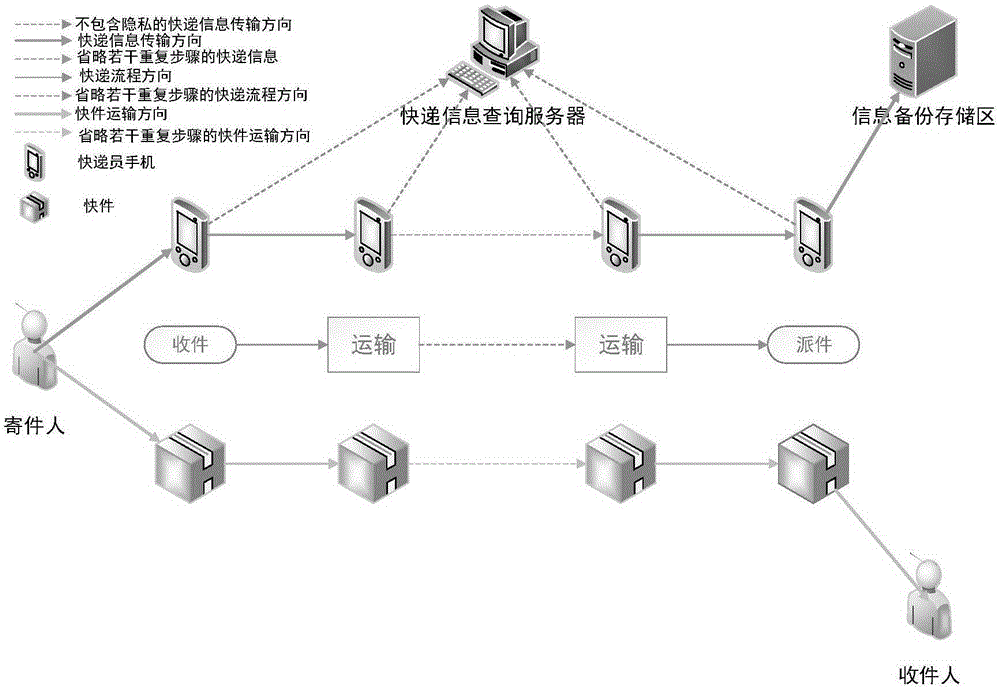
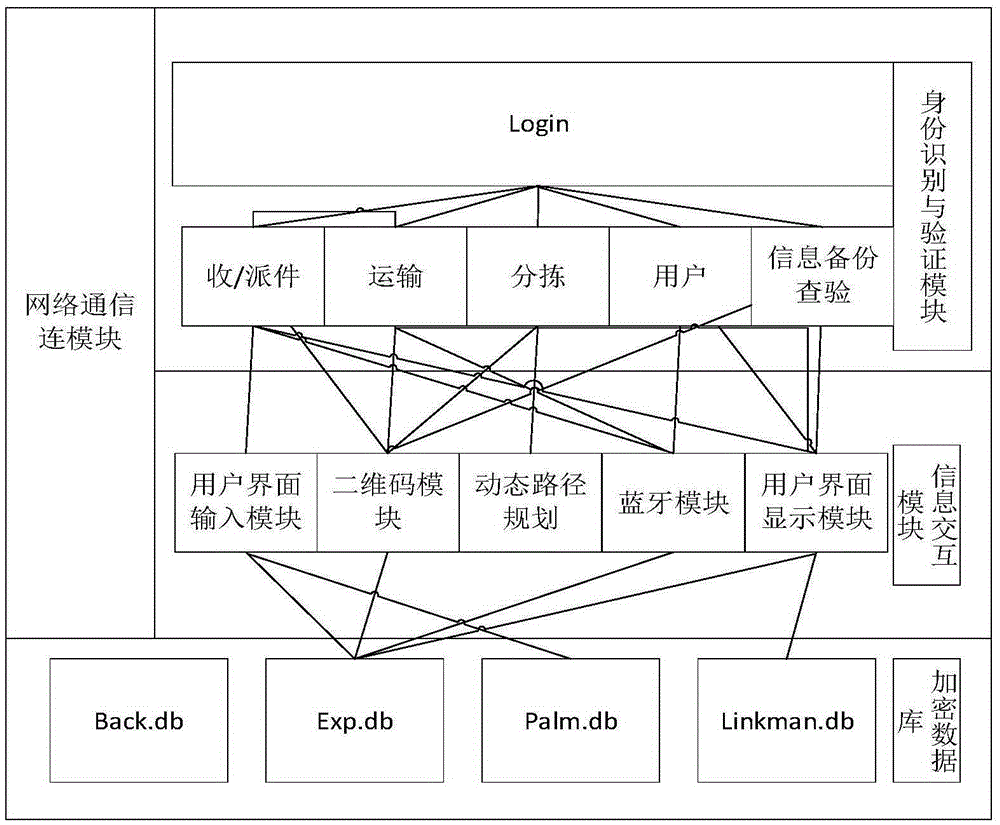
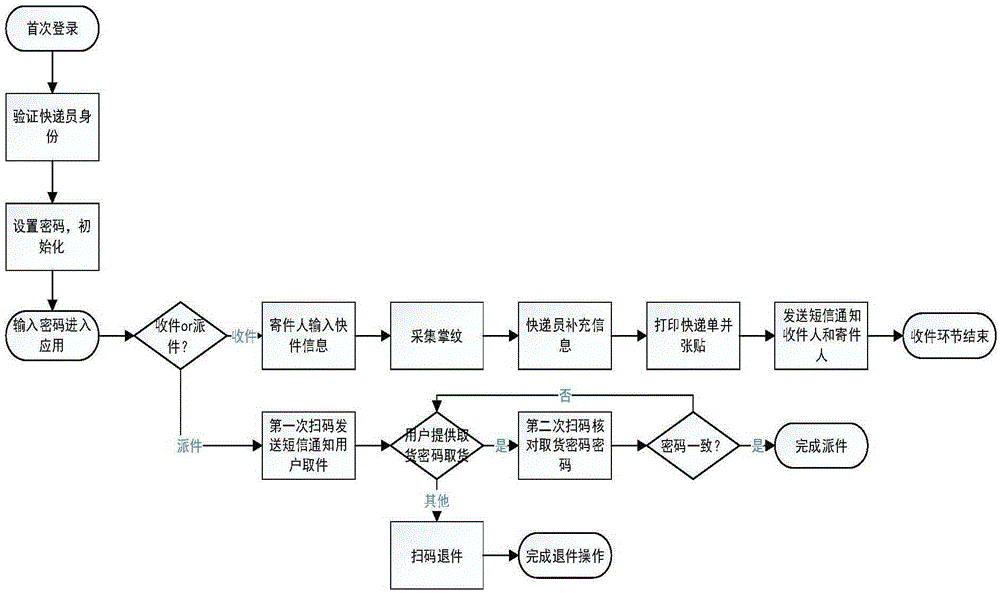
Double-line architecture express delivery information protection method based on mobile terminal
The invention provides a double-line architecture express delivery information protection method based on a mobile terminal for research on informatization management correlation technologies in the express delivery industry. According to the invention, when a dispatcher collects an express, privacy information of a user is input in a client-side local database of the dispatcher, palm print authentication is used for replacing traditional sign authentication, and an only two-dimension code generated according to express information is attached to the express; then the express information is blocked by improving a SQLCipher encryption database, and the safety of the express information is ensured; and during express delivery, the privacy information of the user is transmitted between dispatchers in a Bluetooth manner by means of the two-dimension code, the privacy information of the user is isolated from the dispatchers, express companies and the like, and the express is transported through a traditional logistics network. In order to improve the efficiency of express delivery business, an oriented push-out sorting model based on a net structure is provided, a path optimization scheme based on a Floyd algorithm is designed, and the sorting model and the path optimization scheme are enabled to cooperate with and compensate each other.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
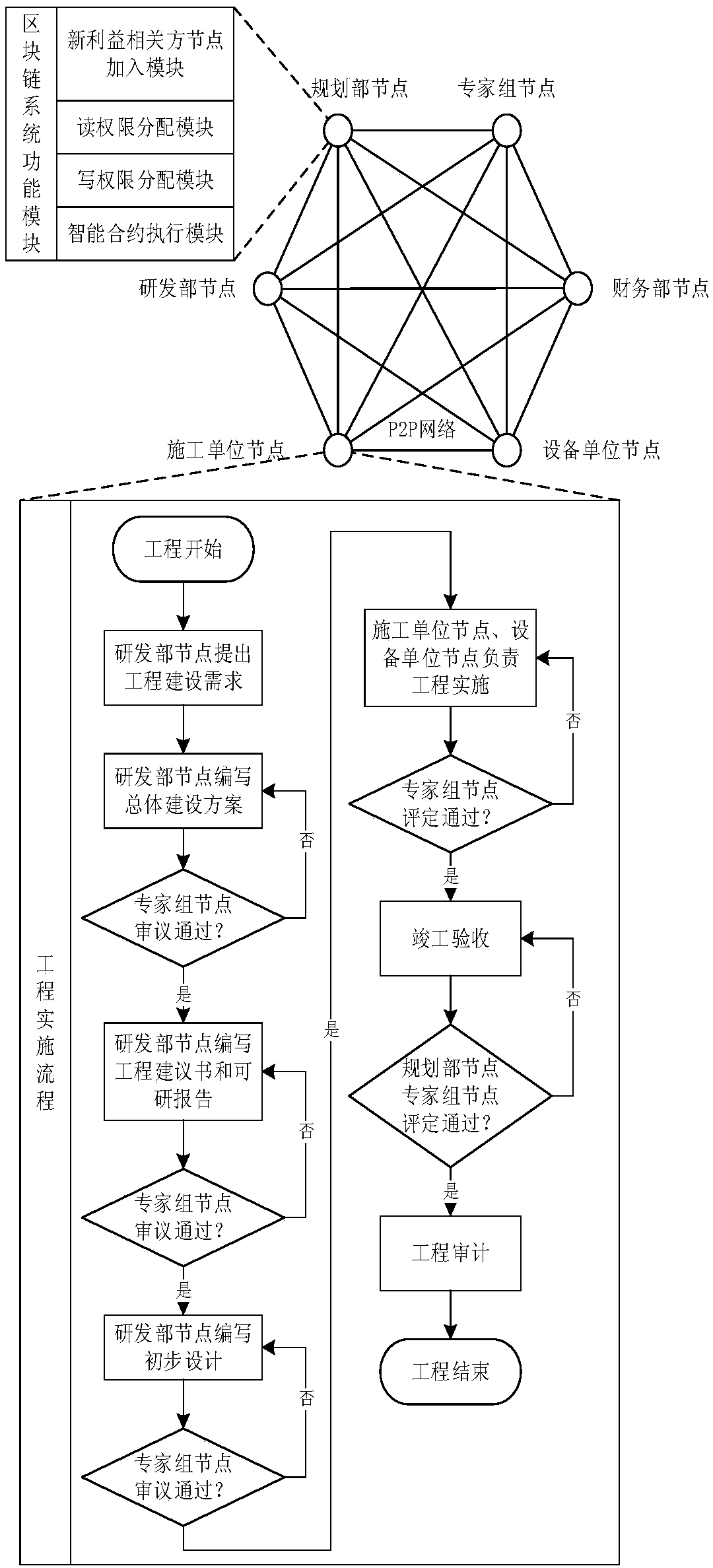
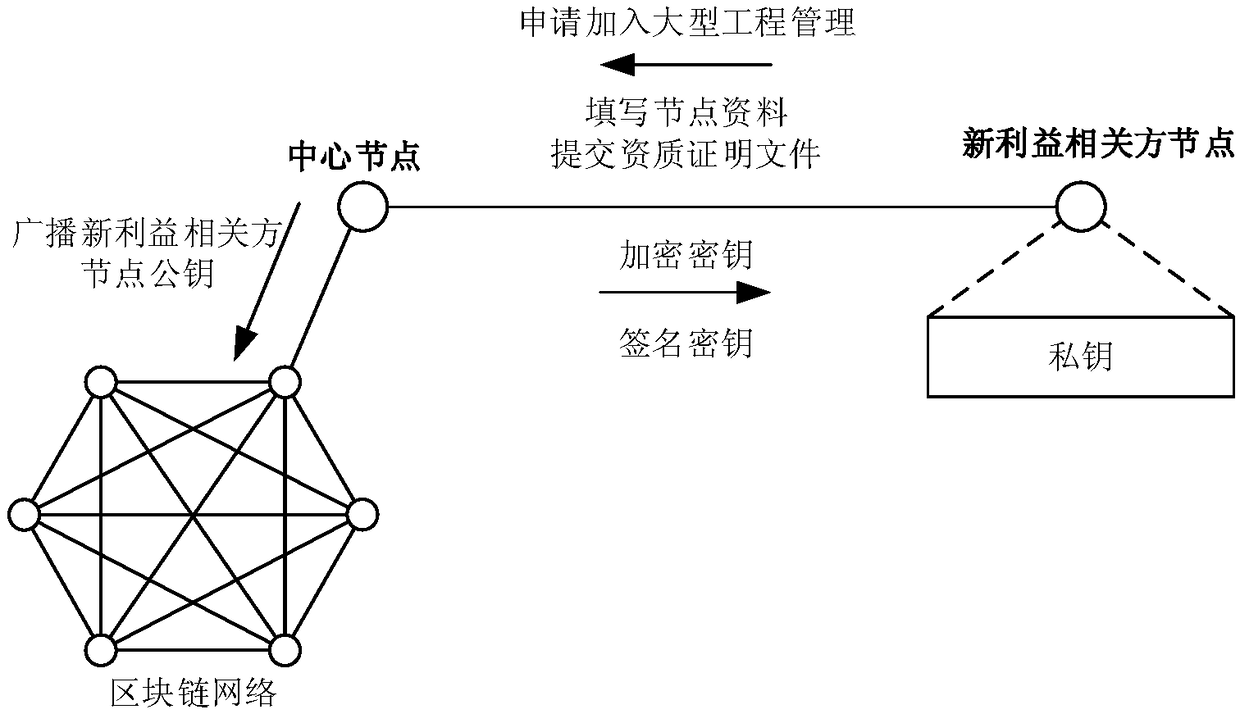
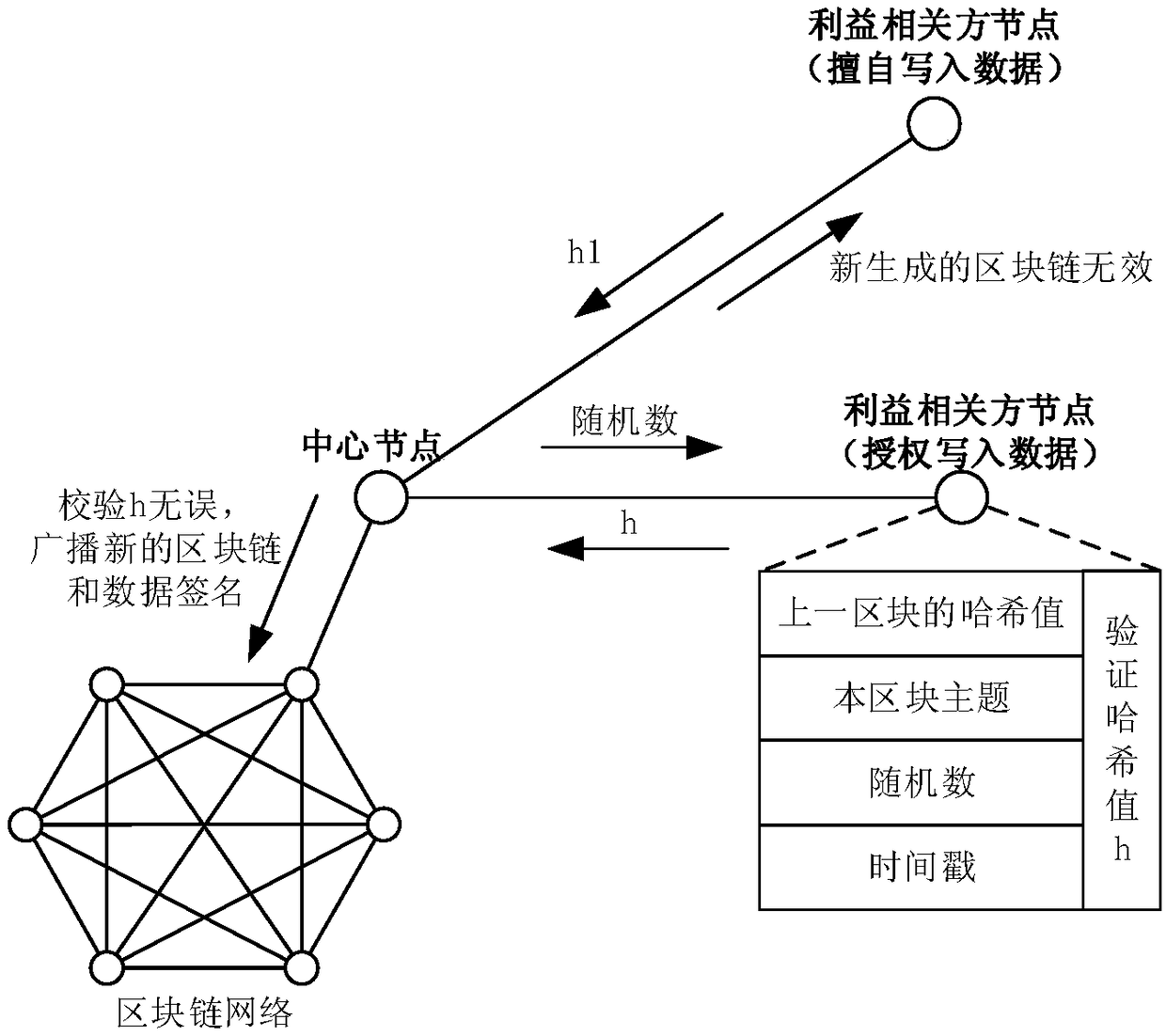
Large-scale project management system and method based on blockchain technology
InactiveCN108629564AEffective participationImprove usabilityUser identity/authority verificationOffice automationBlock structureData availability
The invention discloses a large-scale project management system based on the blockchain technology. A central node, stakeholder nodes, a key module, an information retrieval module and a block structure module form an integrated body; the central node is a planning department node, the stakeholder nodes are a R&D department node, an expert group node, a finance department node, a construction unitnode and a device unit node; the central node and the stakeholder nodes are connected through the P2P network. The system is advantaged in that the stakeholder nodes of the enterprise large-scale project and the project implementation flow are interconnected through the blockchain technology, and stakeholders are made to participate effectively in large-scale project management; data generated during project implementation are stored in the multiple nodes, and data availability is improved; blockchain reading and writing permissions are effectively allocated, and data security and non-repudiation are improved; the contract dispute risk and transaction cost are reduced, and transaction automation is promoted.
Owner:NO 719 RES INST CHINA SHIPBUILDING IND
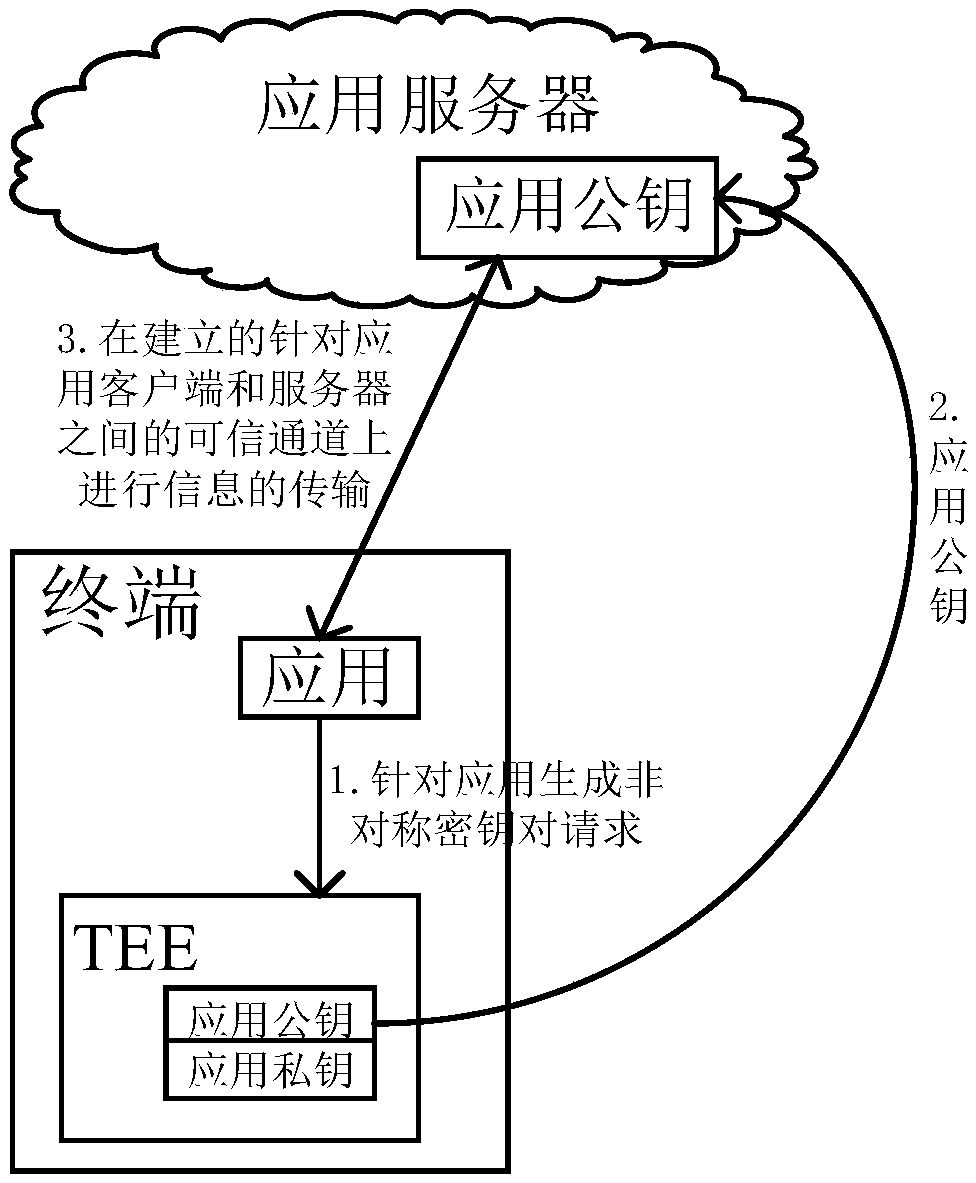
Methods of data sending and equipment
ActiveCN109639427AImprove reliabilityEnhanced non-repudiationUser identity/authority verificationApplication serverData transmission
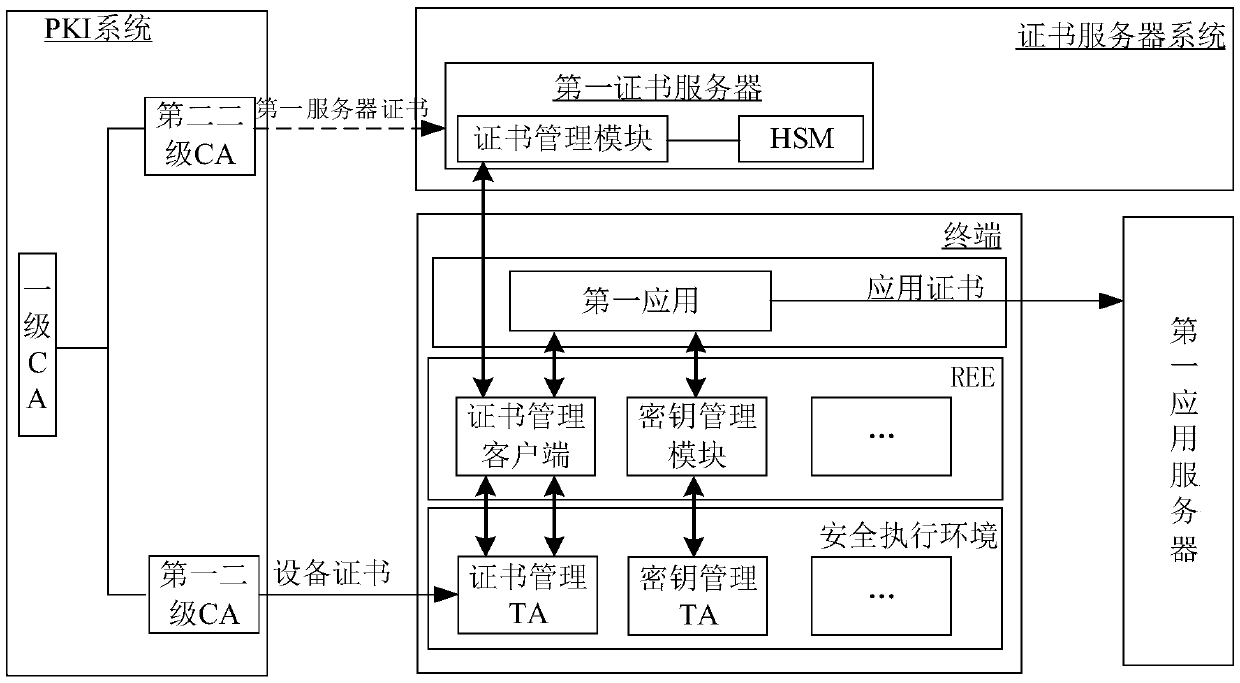
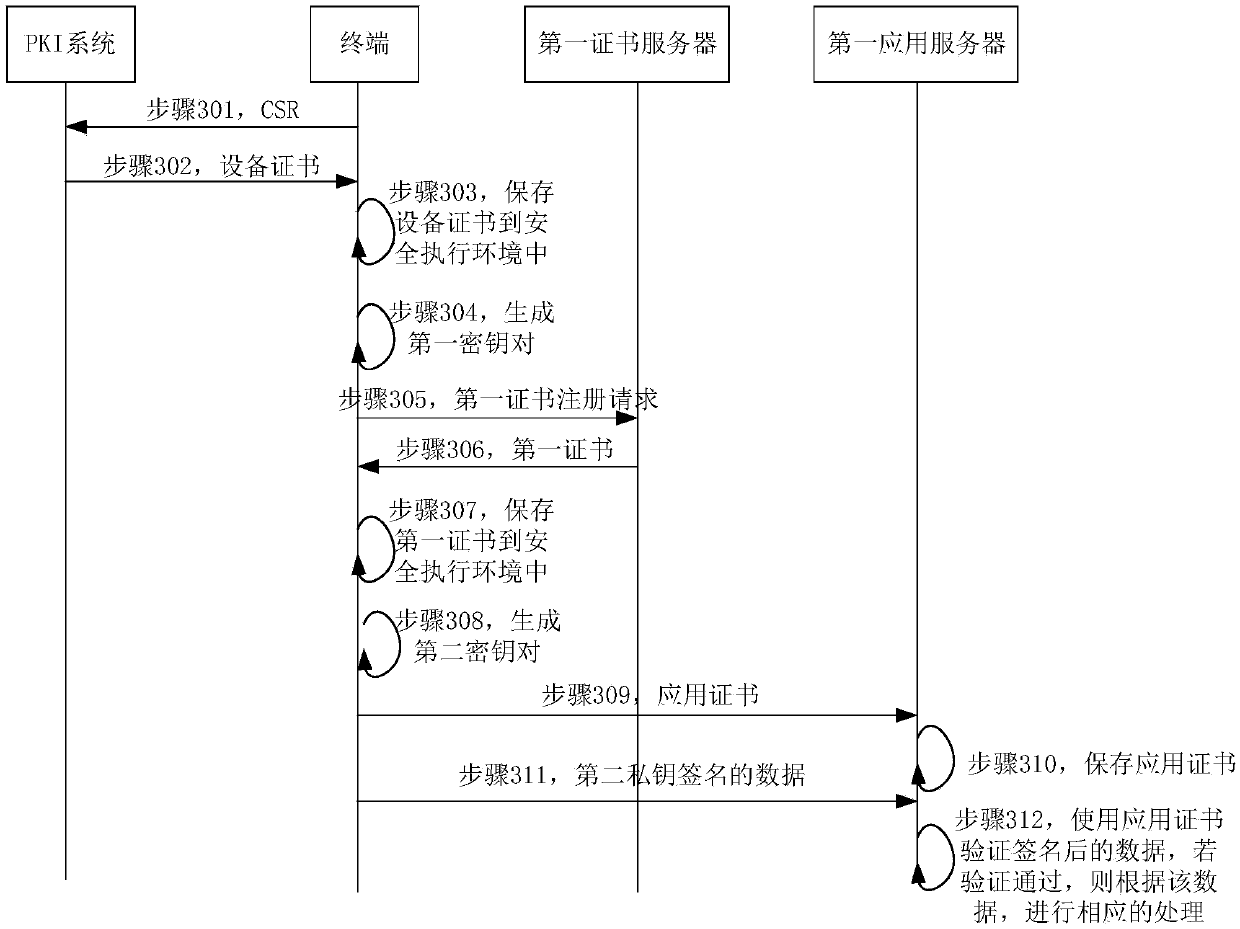
The invention discloses methods of data sending and equipment, and relates to the technical field of terminals. The method includes: receiving, by the terminal, an equipment certificate signed and issued by CA, generating a first key pair, sending a first certificate registration request to a first certificate server, and then receiving a first certificate sent by the first certificate server, wherein the first certificate is different from the device certificate; generating a second key pair by the terminal for a first application; using a first private key by the terminal to sign and issue an application certificate for the first application, and sending the application certificate to a first application server corresponding to the first application; and using a second private key by theterminal to sign data to be sent to the first application server, and sending the signed data to the first application server. The technical solution facilitates an effect of improving reliability, non-repudiation and security of data transmission, and facilitates, at the same time, an effect of avoiding leakage of sensitive information of manufacturing cycles, productivity and the like of terminal products of equipment merchants to application providers.
Owner:HUAWEI TECH CO LTD
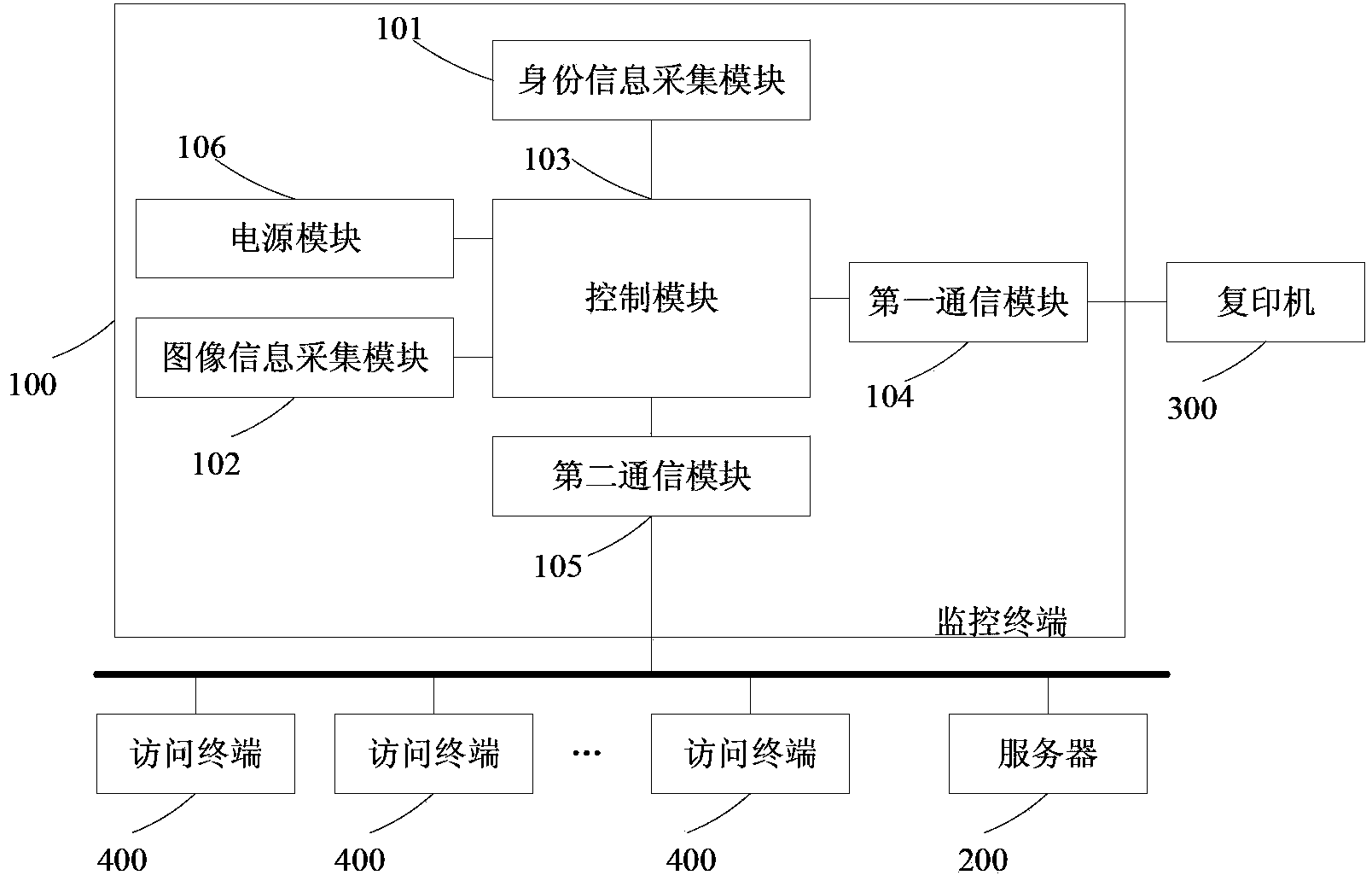
Duplicating monitoring system
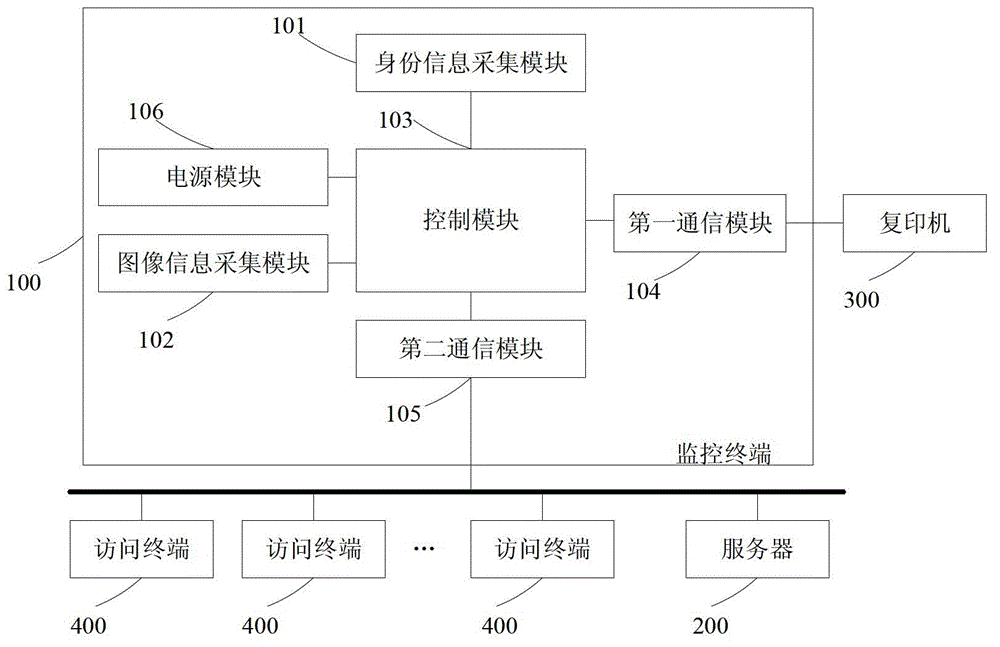
ActiveCN102749874AControl copy permissionsPrevent illegal useProgramme controlComputer controlDuplicate contentMonitoring system
The invention discloses a duplicating monitoring system and relates to the technical field of computer technology and information safety. The system comprises a monitoring terminal and a server, wherein the monitoring terminal is used for locking and unlocking a duplicator to obtain identity information and image information of a duplicator user and duplicating logs and duplicating contents of a legal user, and the identity information, the image information and the duplicating logs and the duplicating contents of the legal user can be uploaded to the server by the monitoring terminal in real time, and the server is used for checking legality of the user, receiving the user's identity information, image information, duplicating logs and duplicating contents sent by the monitoring terminal, generating an audit report which includes the identity information and the image information of the legal user and the corresponding duplicating logs and contents of the legal user, and supplying inquiry of the audit report. The system has the advantages that the duplicator is controlled to be merely used by authorized users, the duplicating logs can be comprehensively, accurately and automatically recorded, simultaneously the audit report of the duplicating logs is supplied, and the system is convenient for administrative stuffs to inquire and audit the duplicating operation.
Owner:BEIJING LANXUM COMP TECH
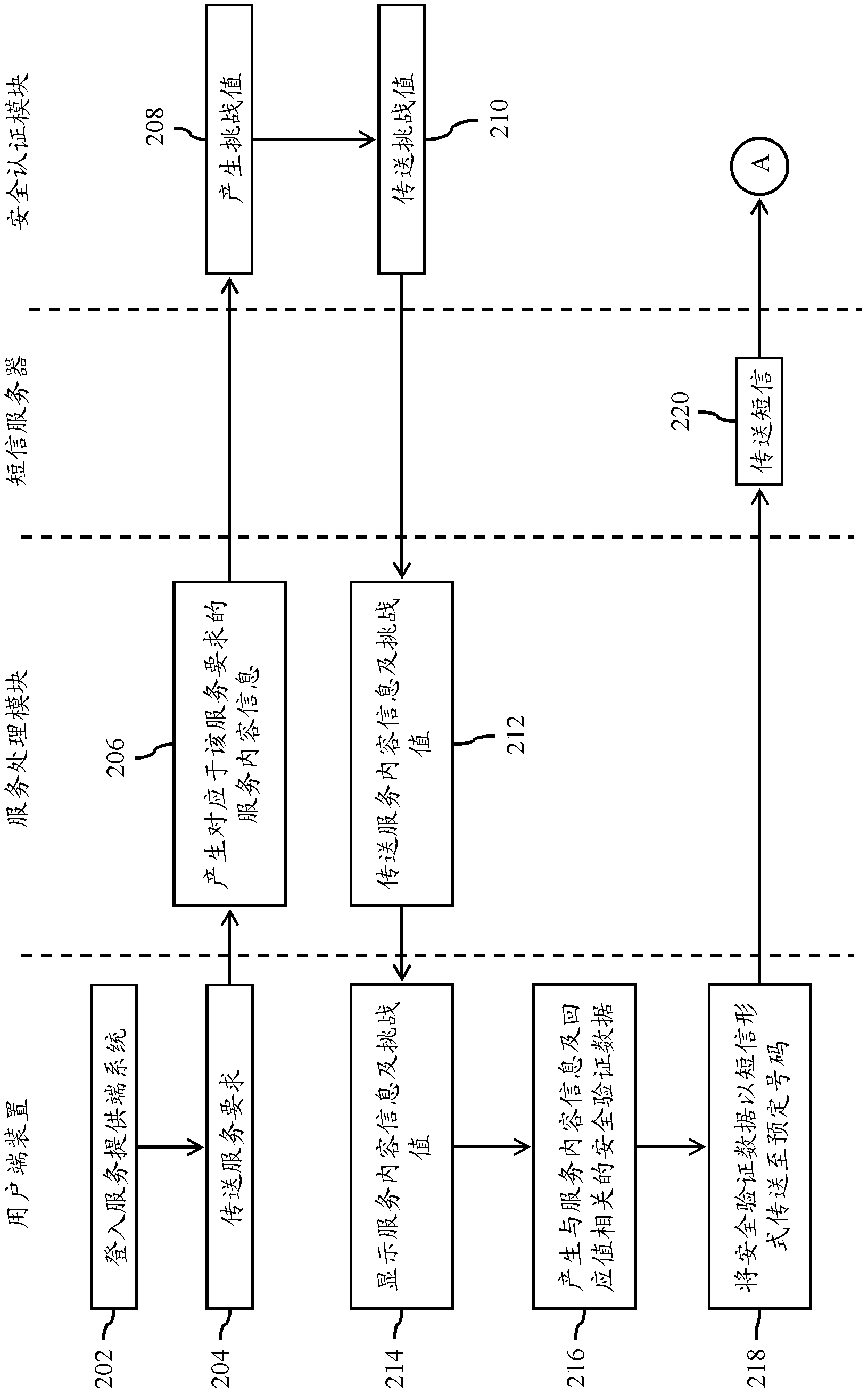
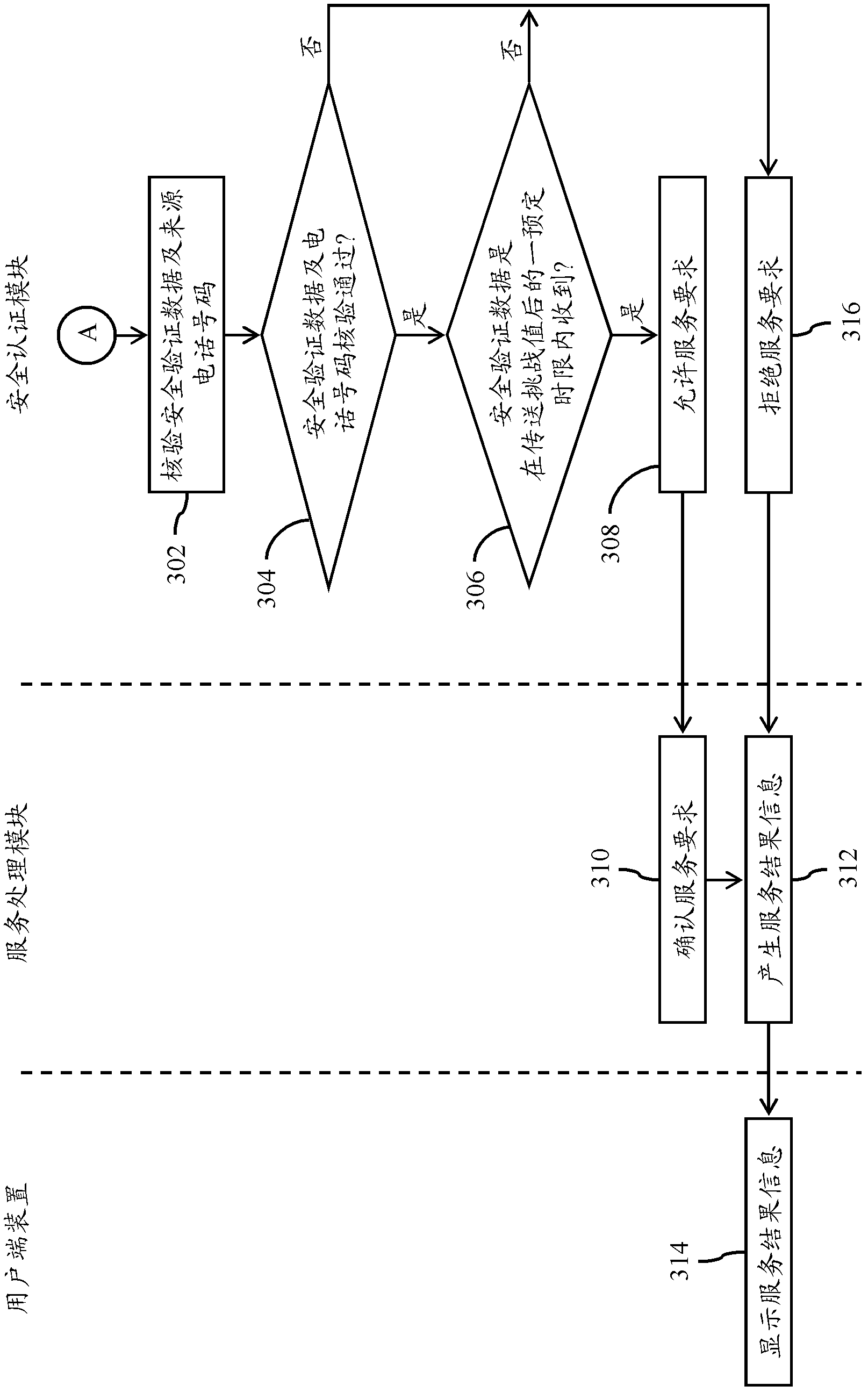
Multi-channel active type network identity verification system and network identity verification device
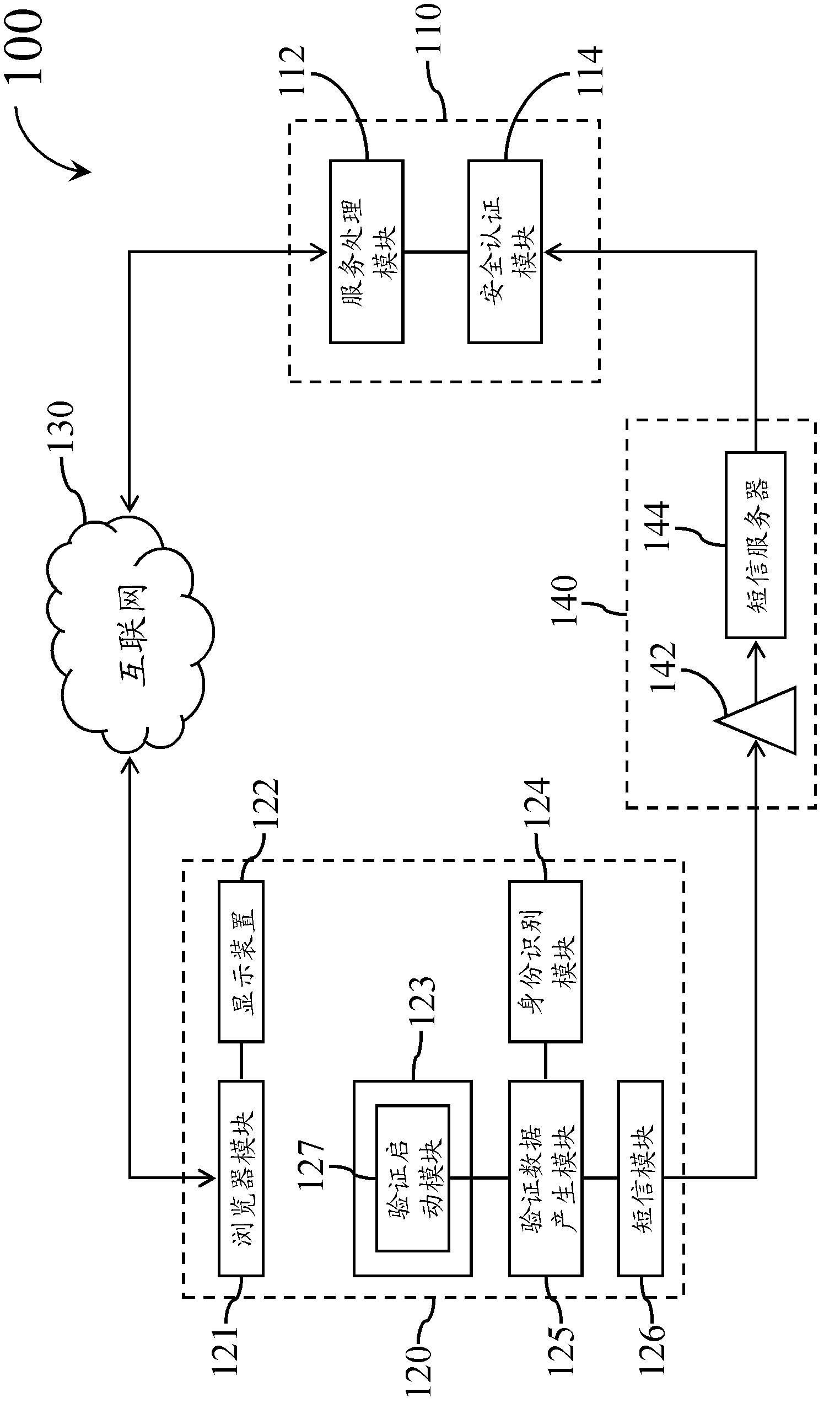
InactiveCN103139179AImprove accuracyImprove reliabilityTransmissionSecurity arrangementEnd systemTransmission channel
The invention provides one of multi-channel active type network identity verification systems. The multi-channel active type network identity verification system comprises a user end device and a service providing end system. The service providing end system comprises a service processing module and a safety certificating module. When the service processing module receives a service request sent from the user end device through a first transmission channel, the safety certificating module can generate a challenge value through a challenge response algorithm, and the service processing module is used for transmitting the challenge value to the user end device. The user end device generates a response value corresponding to the challenge value through a verification data generating module, the response value is encrypted to generate safety verification data, then the safety verification data is sent back to the safety verification module in a short message mode through a second transmission channel, and a network identity verification program can be completed. According to the system, non-repudiation and safety of the safety verification data sent by the user end device can be improved, and accuracy and reliability of network identity verification can be effectively strengthened.
Owner:JRSYS INT
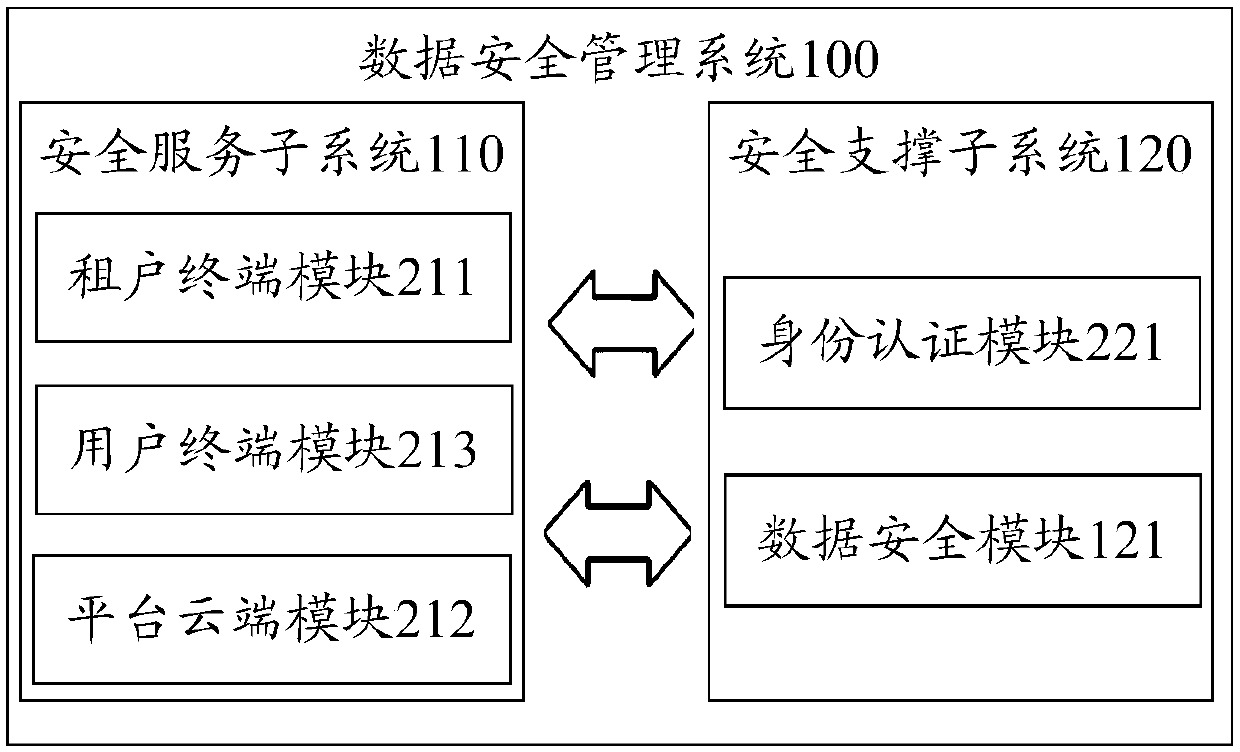
Data security management system and method
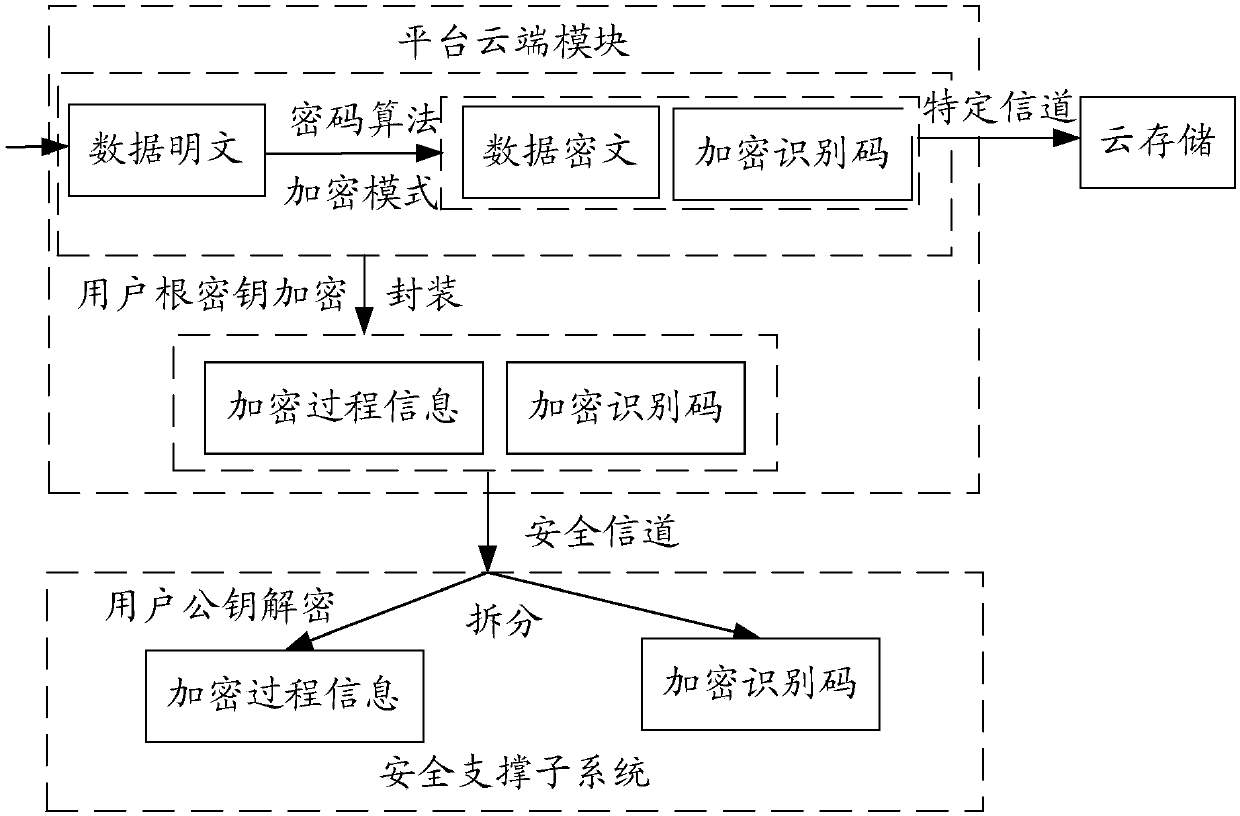
ActiveCN107911393AEnhance non-repudiationGuaranteed confidentialityTransmissionData securityCommon key
The invention provides a data security management system and method. The system comprises a security service subsystem and a security support subsystem, wherein the security service subsystem is usedfor encrypting a to-be-stored data plaintext according to encryption configuration information so as to obtain a data ciphertext and an encryption identification code, and sending the data ciphertextand the encryption identification code to a storage pool for associated storage; and encrypting encryption process information by using a pre-configured user root key, and submitting the encrypted encryption process information and the encryption identification code to the security support subsystem; and the security support subsystem is used for decrypting the encrypted encryption process information by using a user public key; and mapping the decrypted encryption process information according to the encryption identification code carried in a decryption request, processing the encryption process information, generating decryption configuration information and feeding back the decryption configuration information to the security service subsystem, so as to enable the security service subsystem to generate the data plaintext corresponding to the data ciphertext according to the decryption configuration information to deliver the data plaintext to a target application to meet service demands.
Owner:北京明朝万达科技股份有限公司
File usage authority defining system and method
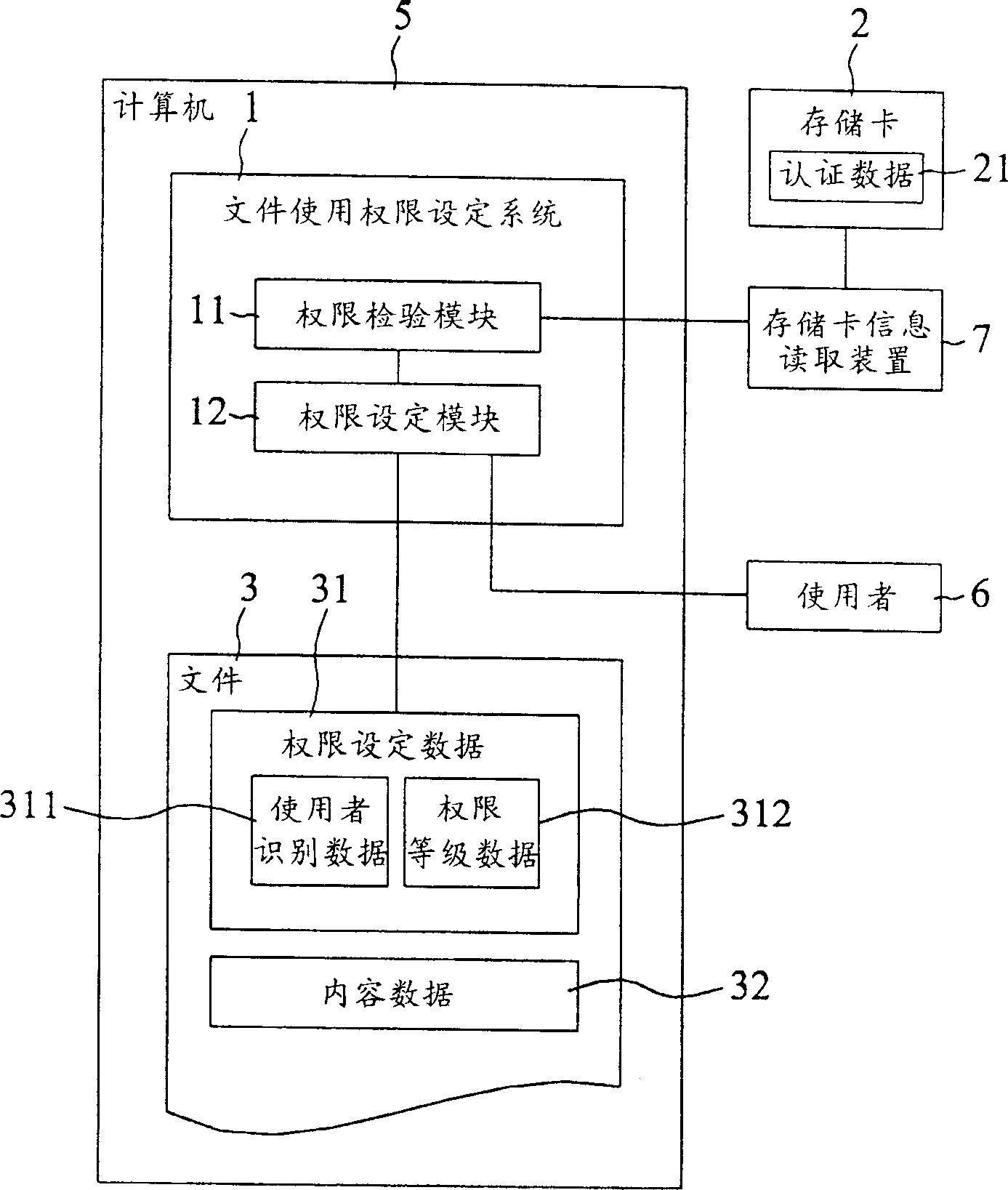
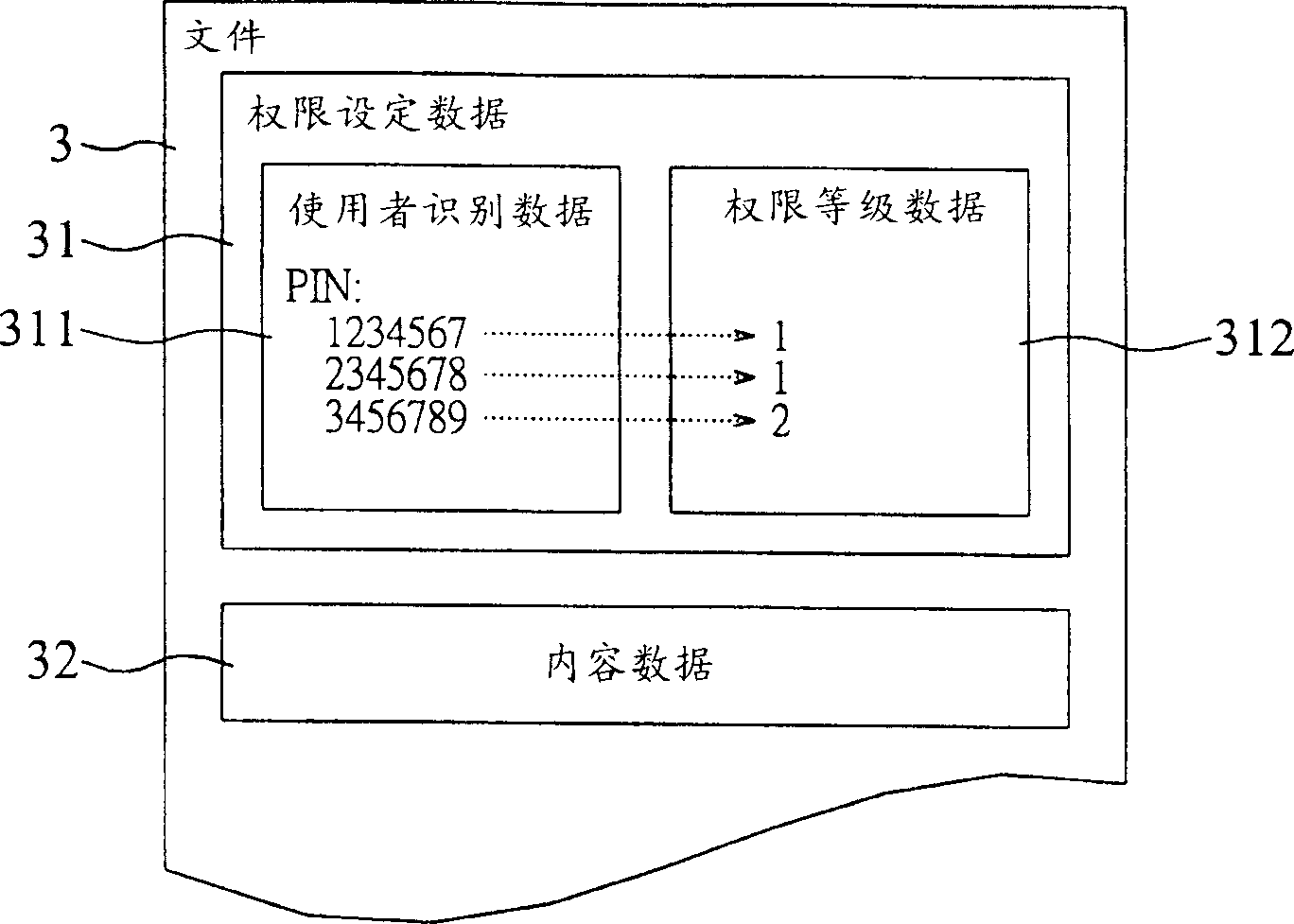
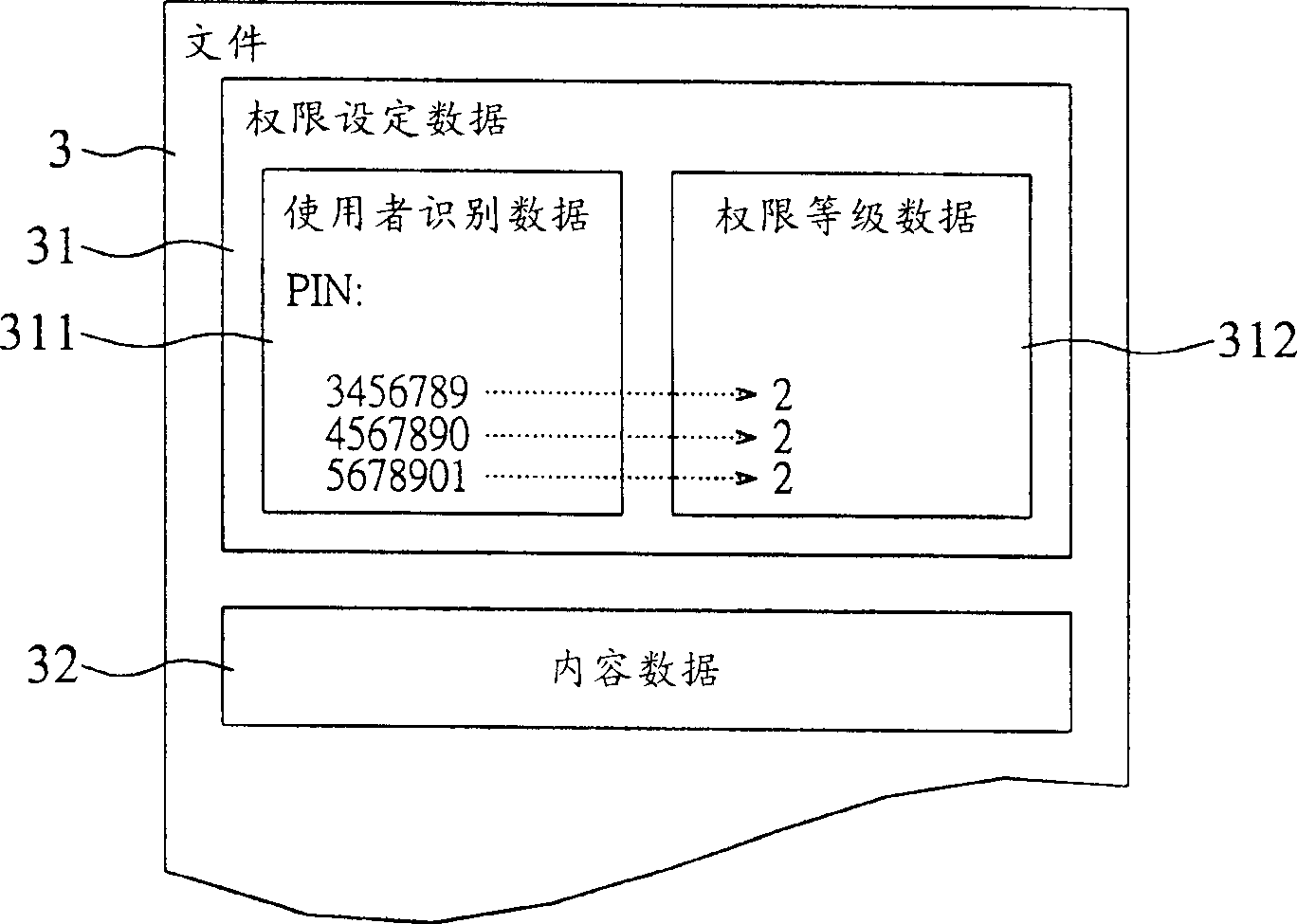
InactiveCN1395178AImprove efficiencyImprove securityMemory loss protectionUnauthorized memory use protectionData setDatabase
The system for setting the use authority of the file is utilzied for the data setting of at least part of authorities in the files. The data setting of the authorities incldues the user's id data and the hierarchy data of the user's authority. The ivnented system incldues the authority vertification module and the authority setting module. Based on the authority setting data, the authority vertification module verifies whether the use possesses the part of the authority to use the file or not. If the user possesses the part of the authority to use the file, base on the indication of the user, the authority setting module deletes the user's id data from the authority setting data. The invention also discloses the method for setting the use authority used by the system.
Owner:大买家科技股份有限公司
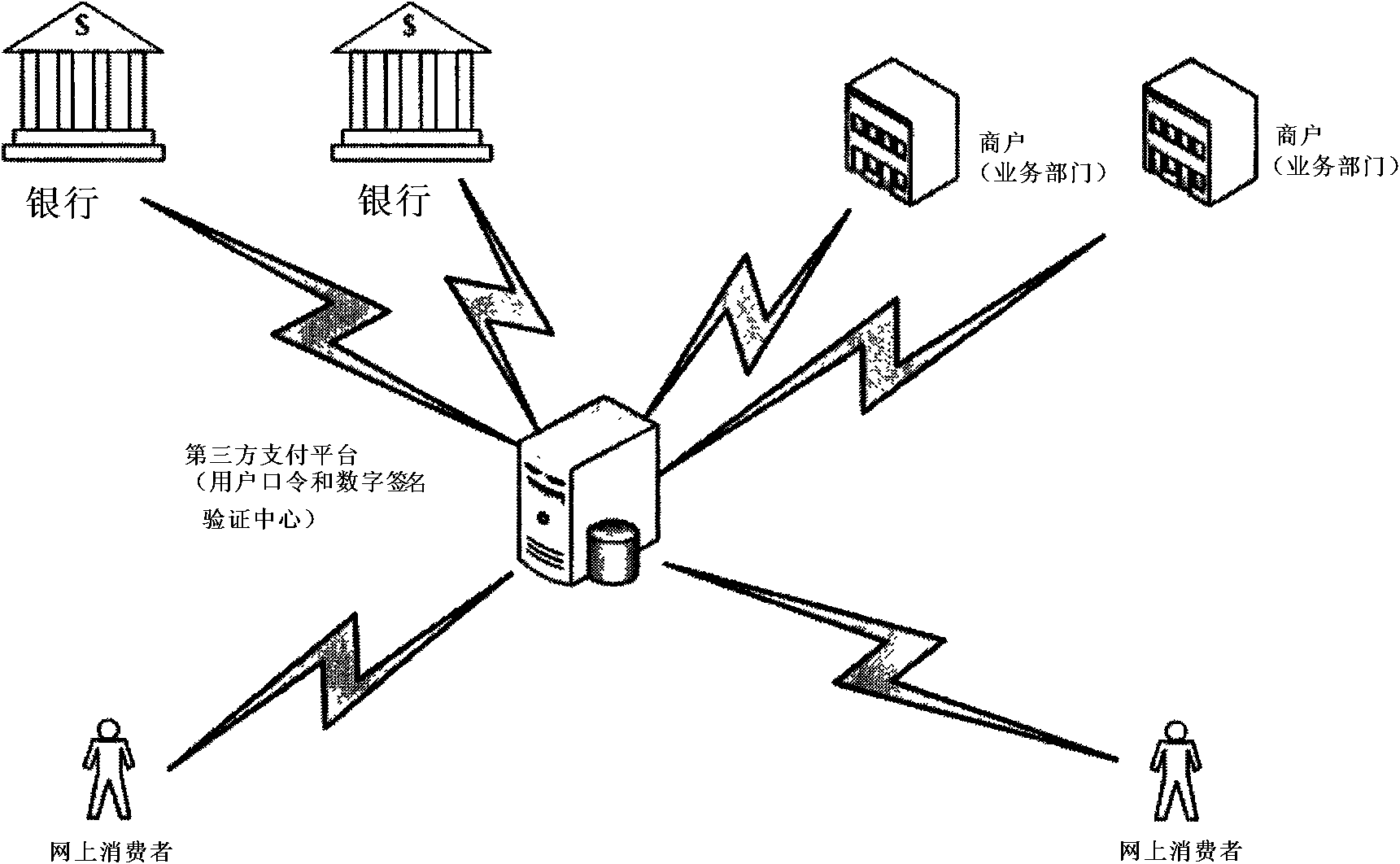
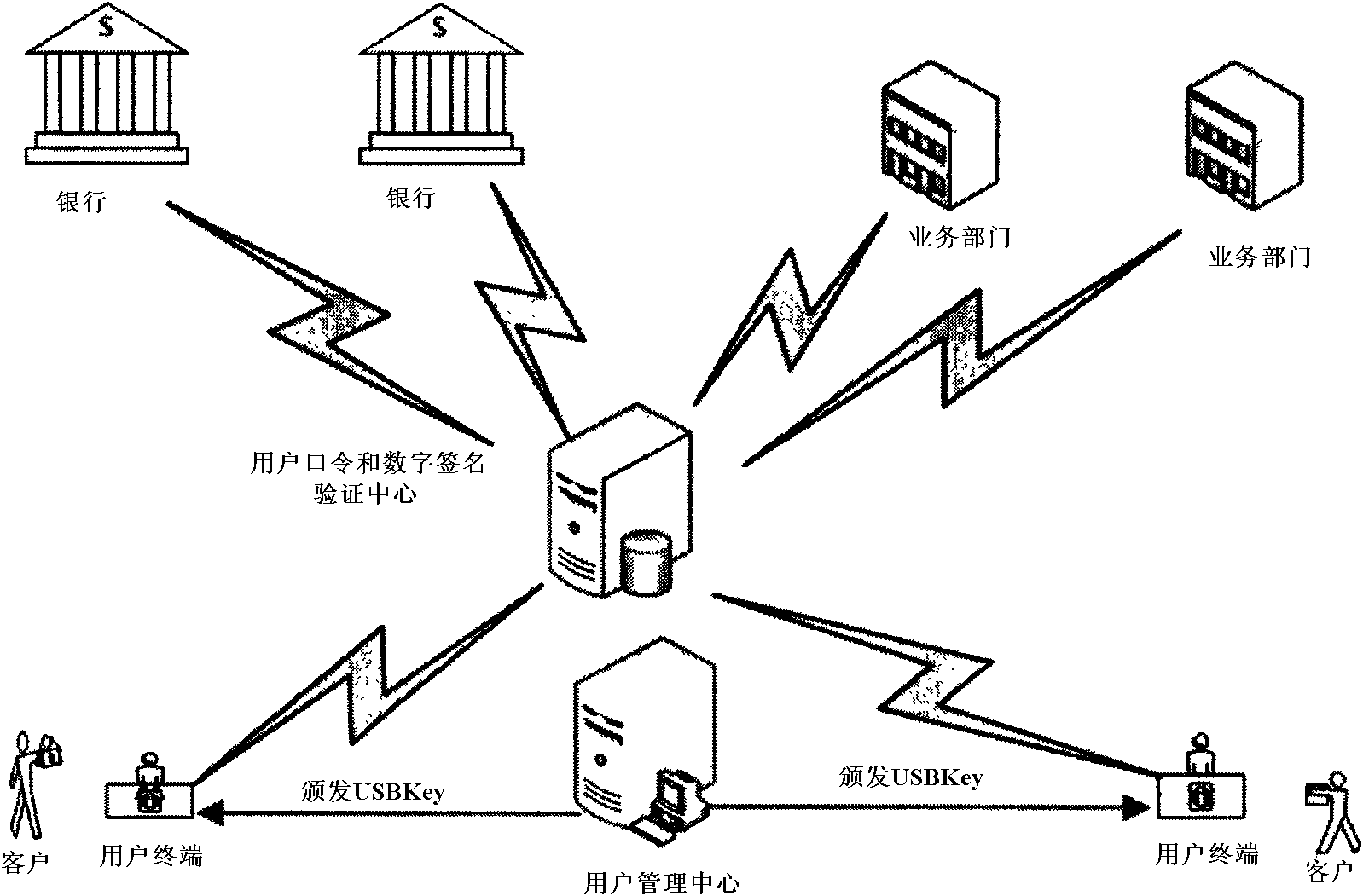
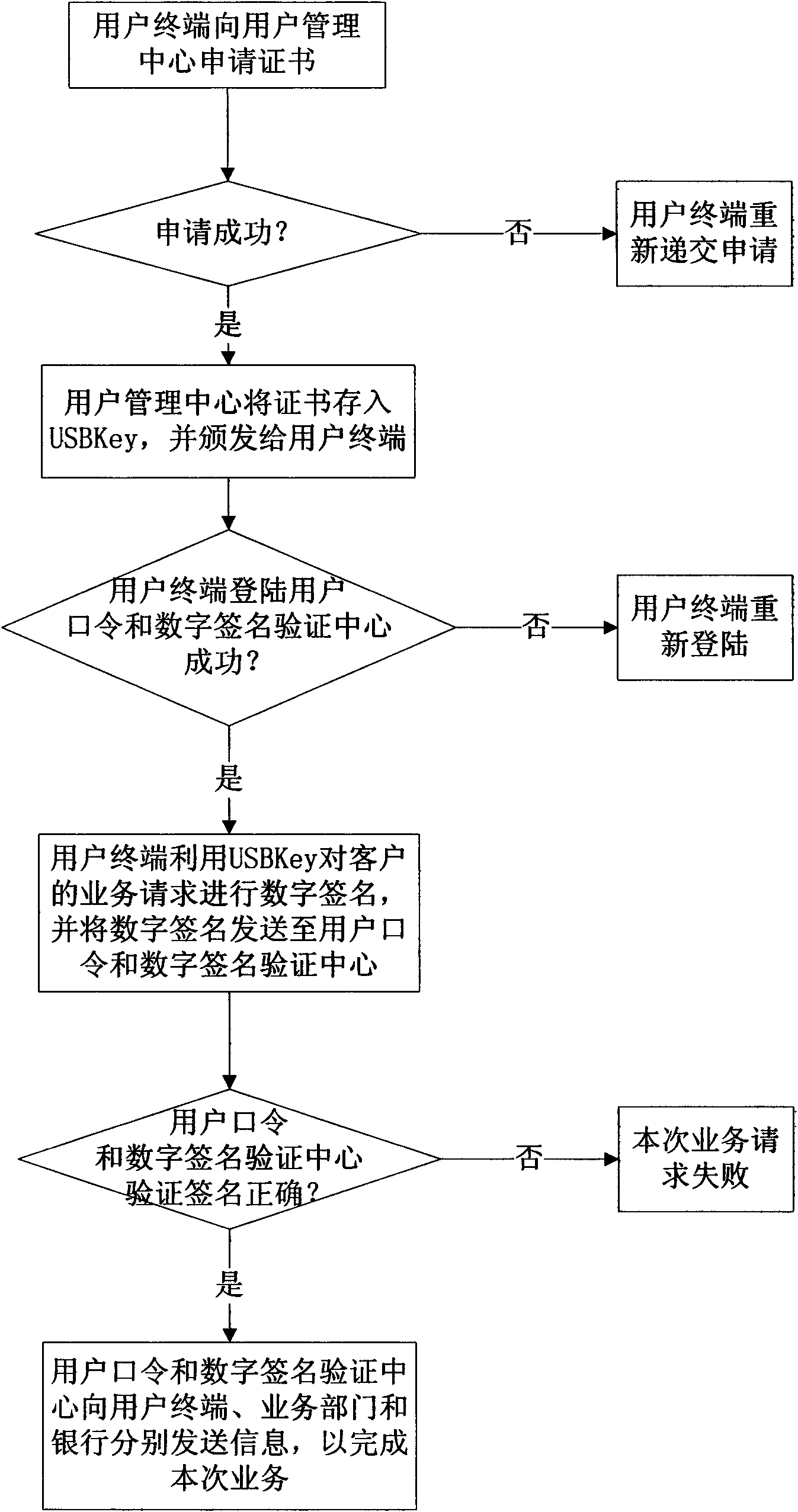
Digital signature authentication system based on third party and authentication method
InactiveCN101616146AEnhanced non-repudiationImprove securityUser identity/authority verificationService departmentAuthentication system
Owner:XIDIAN UNIV
Mobile payment assembly and system and method adopting same
InactiveCN103971234AAdd identity authenticationImprove recognitionProtocol authorisationFinancial transactionMobile payment
The invention discloses a mobile payment assembly and a system and method adopting the same. The mobile payment assembly comprises a mobile payment electronic device, a first key unit arranged in the mobile payment electronic device and an external payment device. The external payment device comprises a chip module and is connected to the mobile payment electronic device through signals. After a second key unit of the chip module and the first key unit of the mobile payment electronic device are confirmed, the external payment device is capable of executing a financial transaction action.
Owner:徐嘉宏
Data processing method and device
ActiveCN111953479AReduce the risk of single point of failureImprove securityKey distribution for secure communicationKey generationSecret share
The invention provides a data processing method and device. The data processing method comprises the steps that an ith secret key generation center obtains a first parameter xi and a first secret sharing share, the ith secret key generation center is any one of m preset secret key generation centers, the first parameter xi is a random positive integer, and m is an integer larger than 1; the ith key generation center generates a second secret sharing share according to the first parameter xi and the first secret sharing share; and the ith key generation center sends the first parameter xi and the second secret sharing share to the user. According to the technical scheme provided by the invention, the plurality of key generation centers participate in the generation process of an identification private key, so that security and non-repudiation of the identification private key are improved, and the load of a single key generation center and the cost of single-point failure are reduced.
Owner:HUAWEI TECH CO LTD
Quantum secret communication system based on secret sharing and communication method thereof
ActiveCN111416706AImprove securityImprove the ability of key serviceKey distribution for secure communicationUser identity/authority verificationCommunications systemStation
The invention discloses a quantum secret communication system based on secret sharing and a communication method thereof. The system comprises a plurality of user sides and a quantum communication service station, wherein the service station serves as an issuing service station or an access service station of the user side, the service station private key and the public keys of all service stations are stored in the service station secret key card, the user side private key and the issuing service station public key are stored in the user side secret key card, the ID of the user side carries the information of the issuing service station, the user side sends a login application to the issuing service station, and a dialogue secret key is generated in the login application process. According to the method provided by the invention, the user side is set to access the plurality of access service stations, the problem that identity authentication cannot be carried out due to limited maximum connection number is prevented, and the capability of providing key service of the network is improved; identity authentication is carried out by adopting encryption modes such as random numbers, offset and the like; the effectiveness and the non-repudiation of identity authentication are high.
Owner:南京如般量子科技有限公司 +1
Electronic signature generation and verification method with digital watermark and electronic device
ActiveCN110474773AEnhanced non-repudiationStrengthen the unique binding relationshipKey distribution for secure communicationUser identity/authority verificationValidation methodsDigital watermarking
The invention discloses a method for generating an electronic seal with a digital watermark. Performing by an electronic device, the invention relates to a method for generating a video. Obtaining a signature message abstract according to the file data related to the file and the mathematical function; for each image received by the video after the signature message abstract is obtained, the signature message abstract is extracted; generating signature trajectory data according to all the received trajectory information related to the signature trajectory of the signer before receiving the receiving time of the image; and the electronic device receives the signature track data and adds the signature track data into the image, and when the signature message abstract is obtained, the electronic device adds a digital watermark comprising the signature message abstract into the video so as to generate an electronic signature comprising the video. In addition, the invention further providesan electronic signature verification method and an electronic device.
Owner:THINKCLOUD DIGITAL TECH
Double medium and double authentication fast off-line payment method under public key system
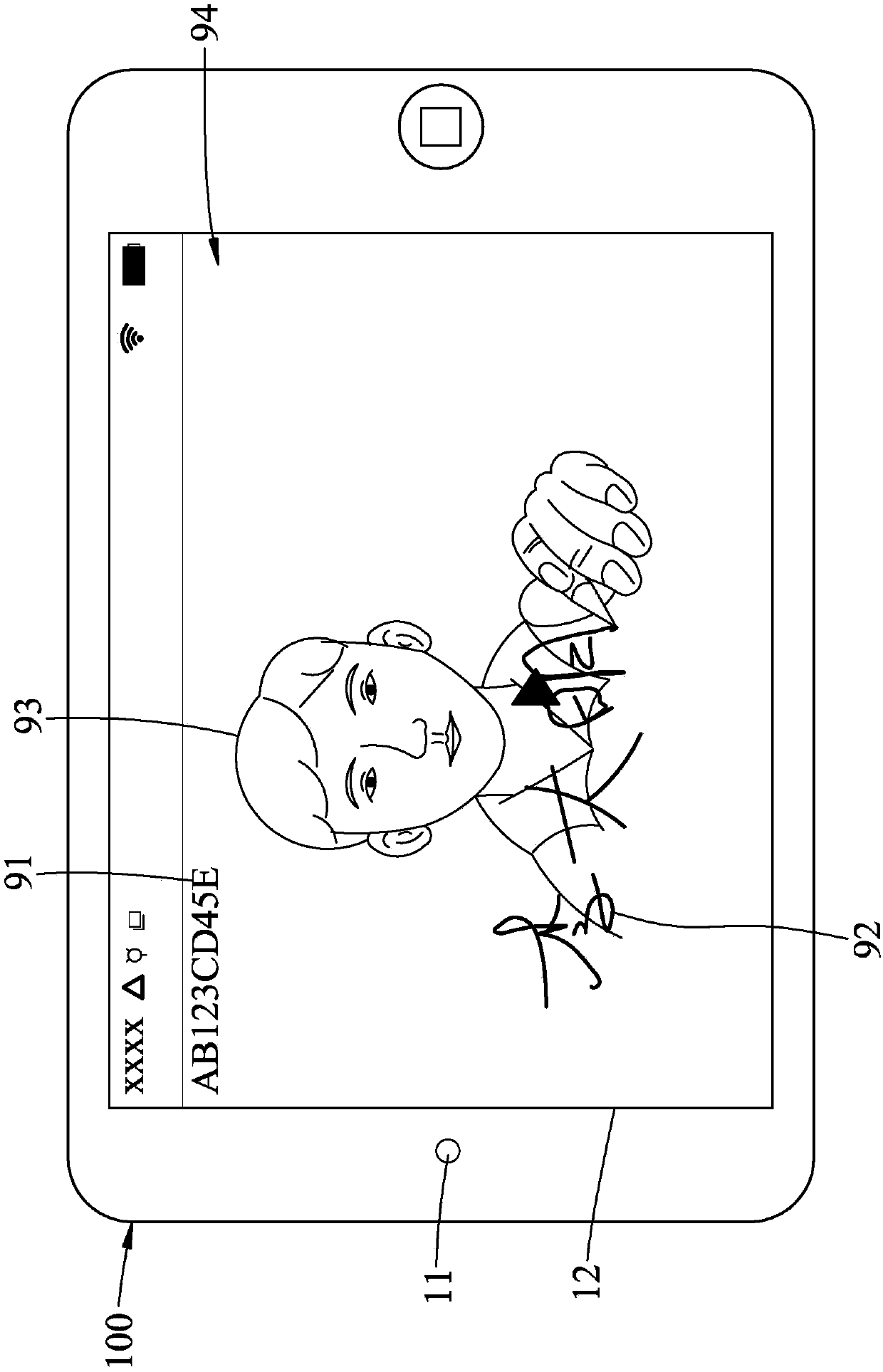
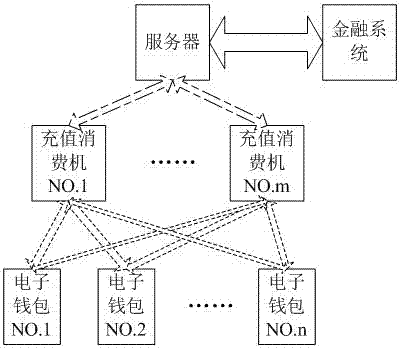
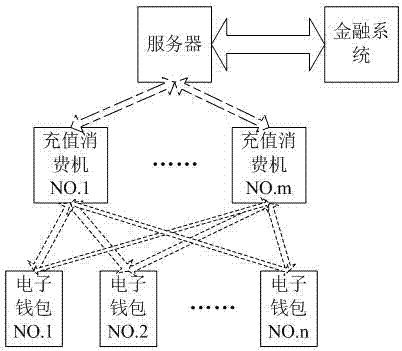
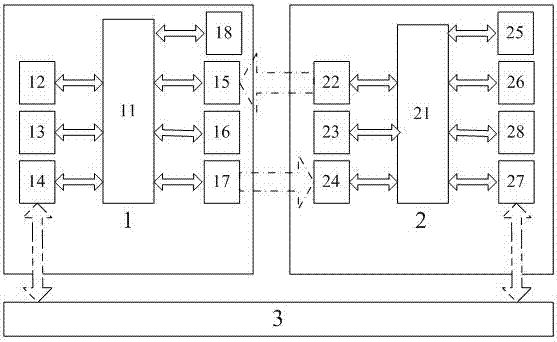
ActiveCN106920096AImprove securityEnhanced non-repudiationPublic key for secure communicationClose-range type systemsTransaction dataBarcode
The invention discloses a double medium and double authentication fast off-line payment method under a public key system, which comprises the steps that a double medium off-line payment device under a VLC (Visible Light Communication) and Barcode public key system is built, wherein the double medium off-line payment device comprises an electronic wallet, a consumption machine and a server; implementation of the payment method is accomplished by the consumption machine and the electronic wallet; the electronic wallet sends visible light signals in the payment process and scans a barcode displayed by the consumption machine; and the consumption machine receives the visible light signals and generates a display barcode provided for the electronic wallet to scan. Mutual verification is performed on the identity and transaction information of the consumption machine and the electronic wallet by adopting the public key system, and the security of the off-line payment method and the non-repudiation of the two transaction parties are effectively improved.
Owner:GUILIN UNIVERSITY OF TECHNOLOGY
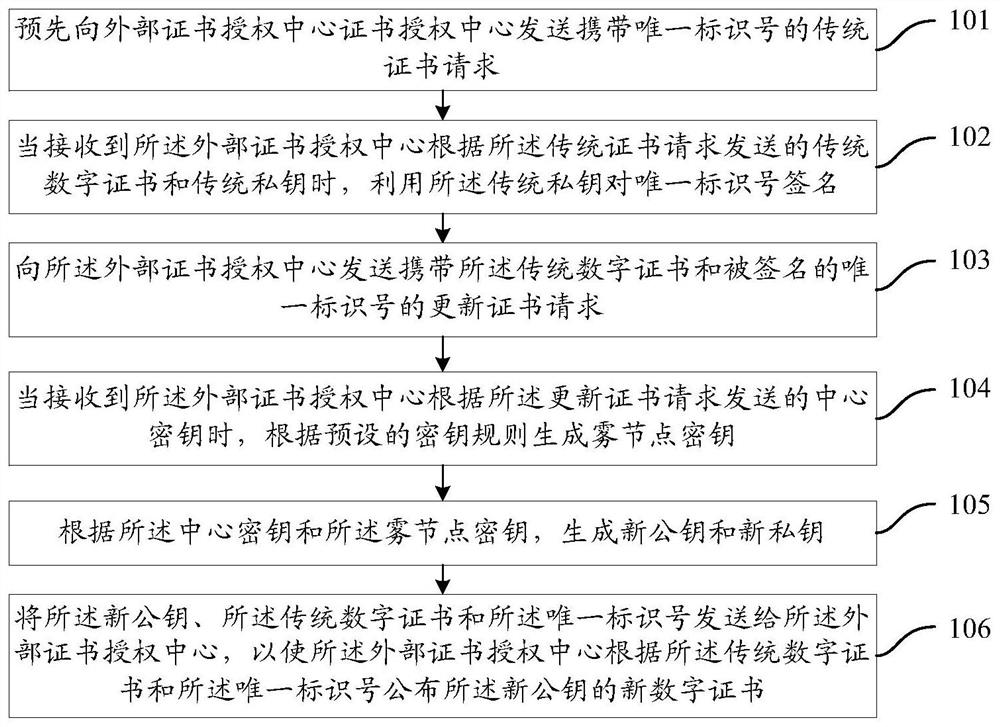
Digital certificate application method and system, fog node and certificate authority center
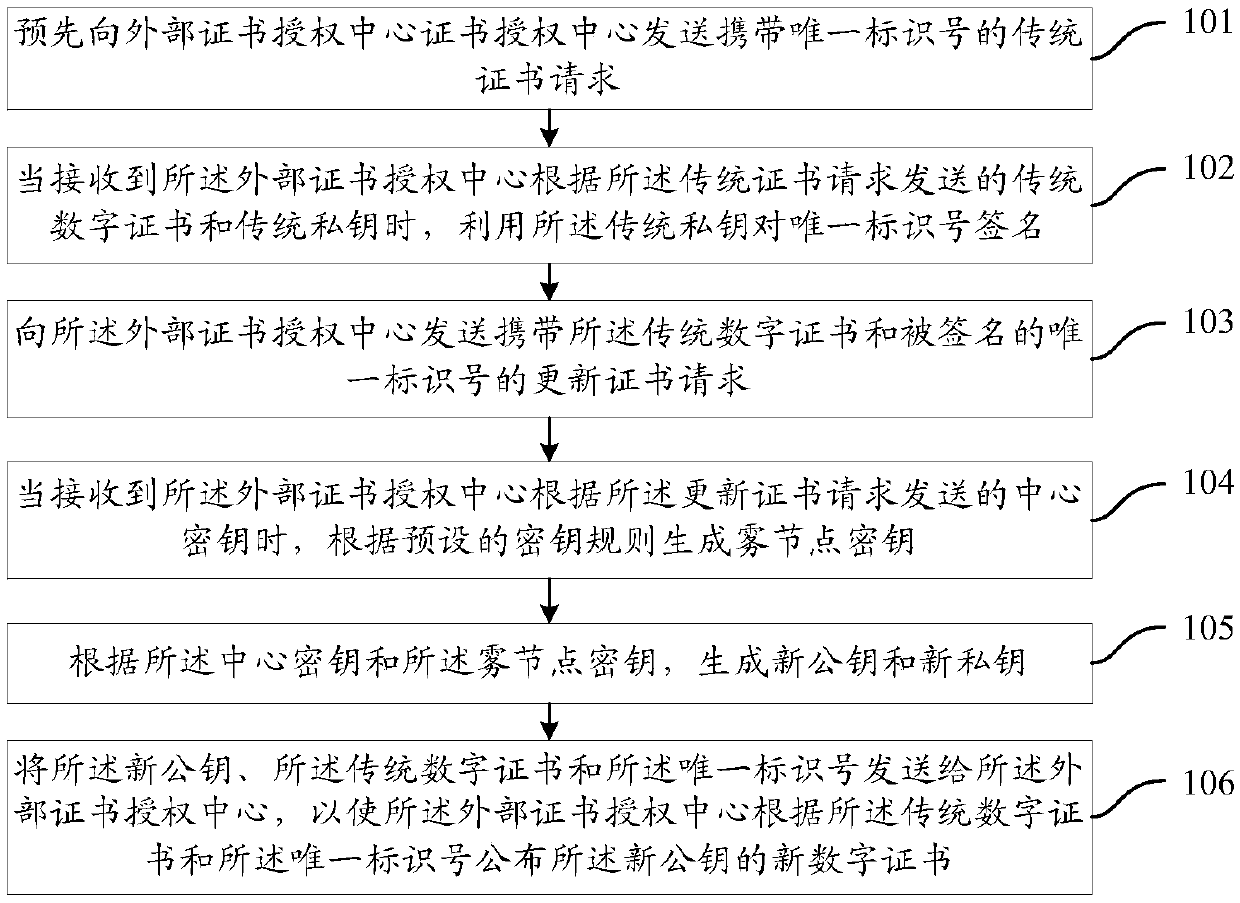
ActiveCN108683506AEnhanced non-repudiationImprove securityKey distribution for secure communicationUser identity/authority verificationComputer networkInternet privacy
The present invention provides a digital certificate application method and system, a fog node and a certificate authority center. The method for applying to the fog node includes: sending a traditional certificate request to an external certificate authority center; using a traditional private key to sign a unique identification number when a traditional digital certificate and the traditional private key sent by the external certificate authority center according to the traditional certificate request is received; sending an update certificate request carrying the traditional digital certificate and the signed unique identification number to the external certificate authority center; generating a fog node secret key according to a preset secret key generation rule while a central secretkey sent by the external certificate authority center is received; generating a new public key and a new private key according to the central secret key and the fog node key; sending the new public key, the traditional digital certificate, and the unique identification number to the external certificate authority center so that the external certificate authority center to publish a new digital certificate for the new public key according to the traditional digital certificate and the unique identification number. The scheme can improve the security of fog node communication.
Owner:INSPUR GROUP CO LTD
Cloud terminal identity authentication method based on blockchain encryption and biological information identification
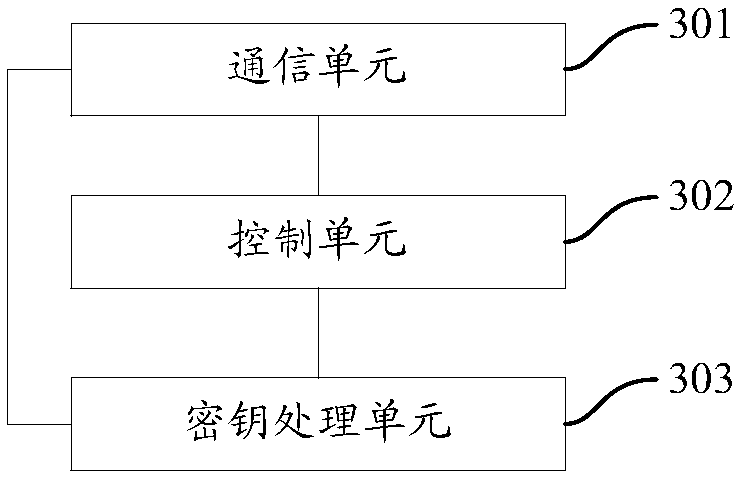
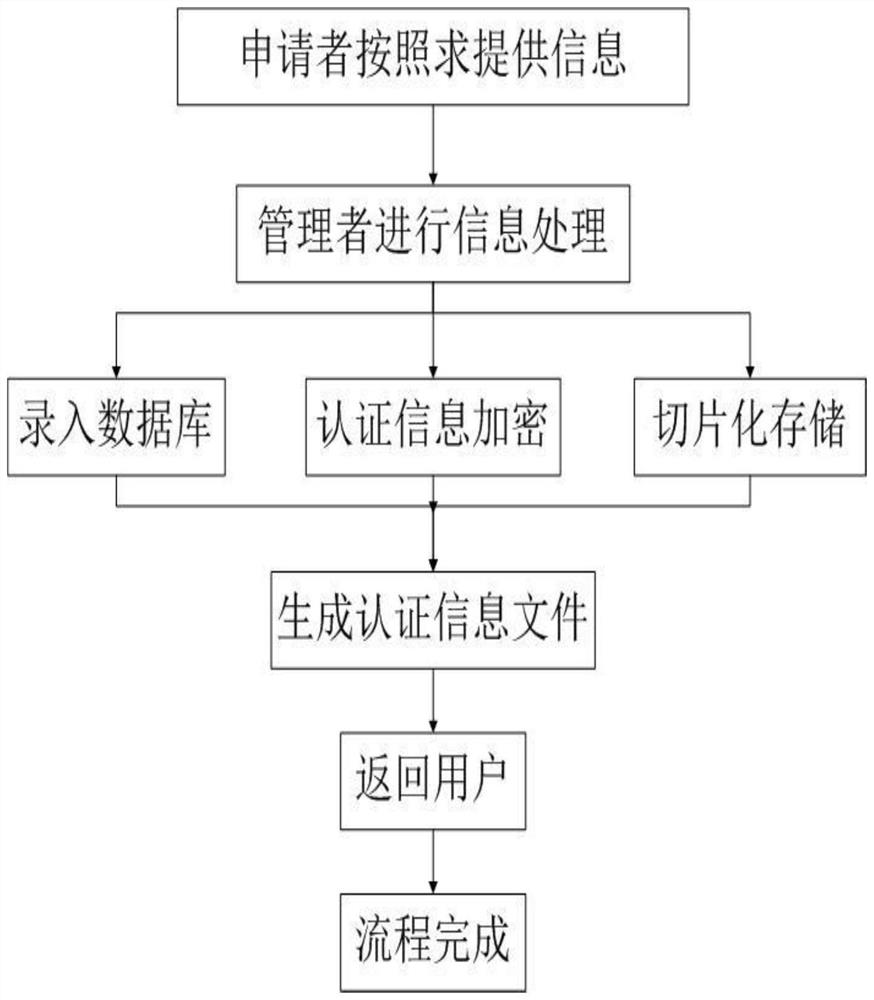
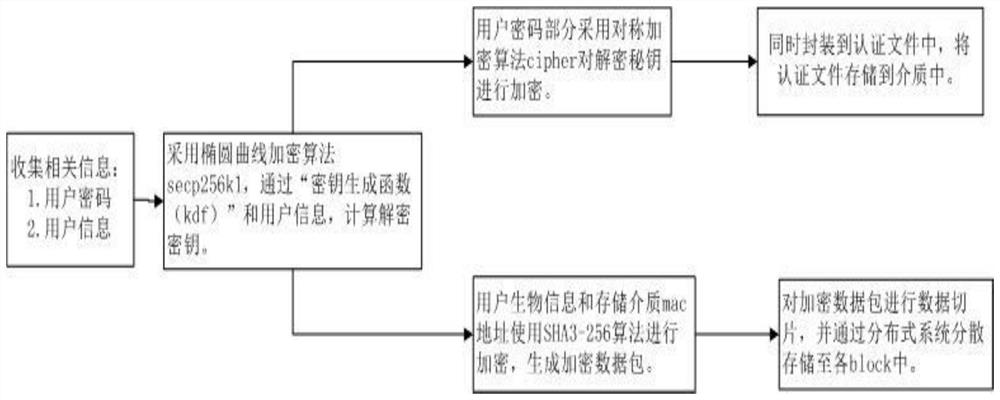
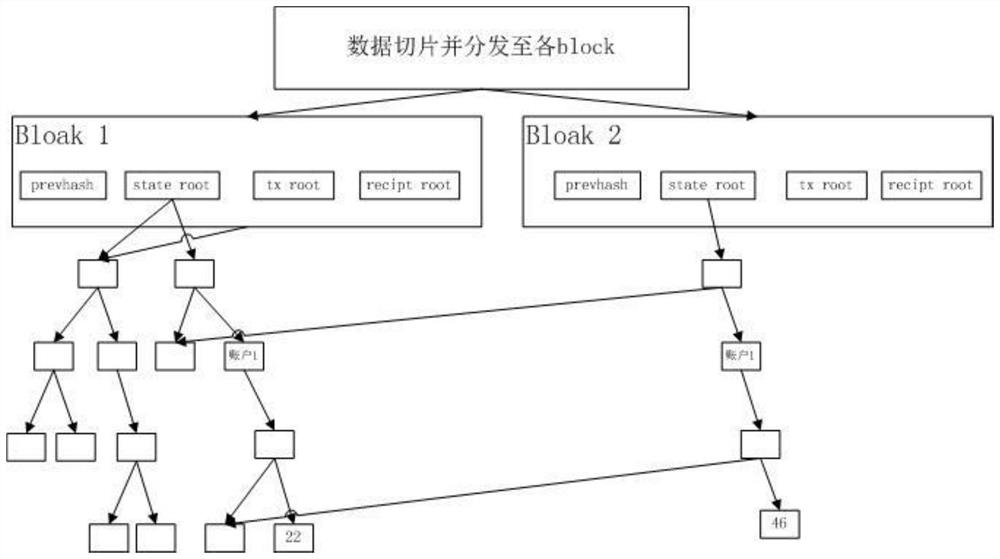
PendingCN112182533ARealize all-round protectionImprove securityDigital data authenticationInternet privacyServer-side
The invention relates to a cloud terminal identity authentication method based on blockchain encryption and biological information identification. The method comprises the steps of identity information authentication file issuing and identity information authentication login; identity information authentication file issuing comprises the steps of acquiring related information of an identity authentication applicant; encrypting the related information based on a blockchain elliptical encryption algorithm to generate an identity information authentication file, storing the identity information authentication file in a distributed storage system in a slicing manner, and storing the identity information authentication file in an identity authentication information storage medium at the same time; and issuing the identity information authentication file to an identity authentication applicant; the identity information authentication login comprises the following steps of enabling a cloud server to determine a user identity according to an identity information authentication file in an identity authentication information storage medium; and recording identity information authentication login operation and updating the identity information authentication file through the distributed storage system. According to the invention, all-round protection of user data security can be realized,and the possibility of cracking is greatly reduced.
Owner:中国大唐集团科学技术研究总院有限公司
LoRa encryption authentication communication method, storage medium and electronic terminal
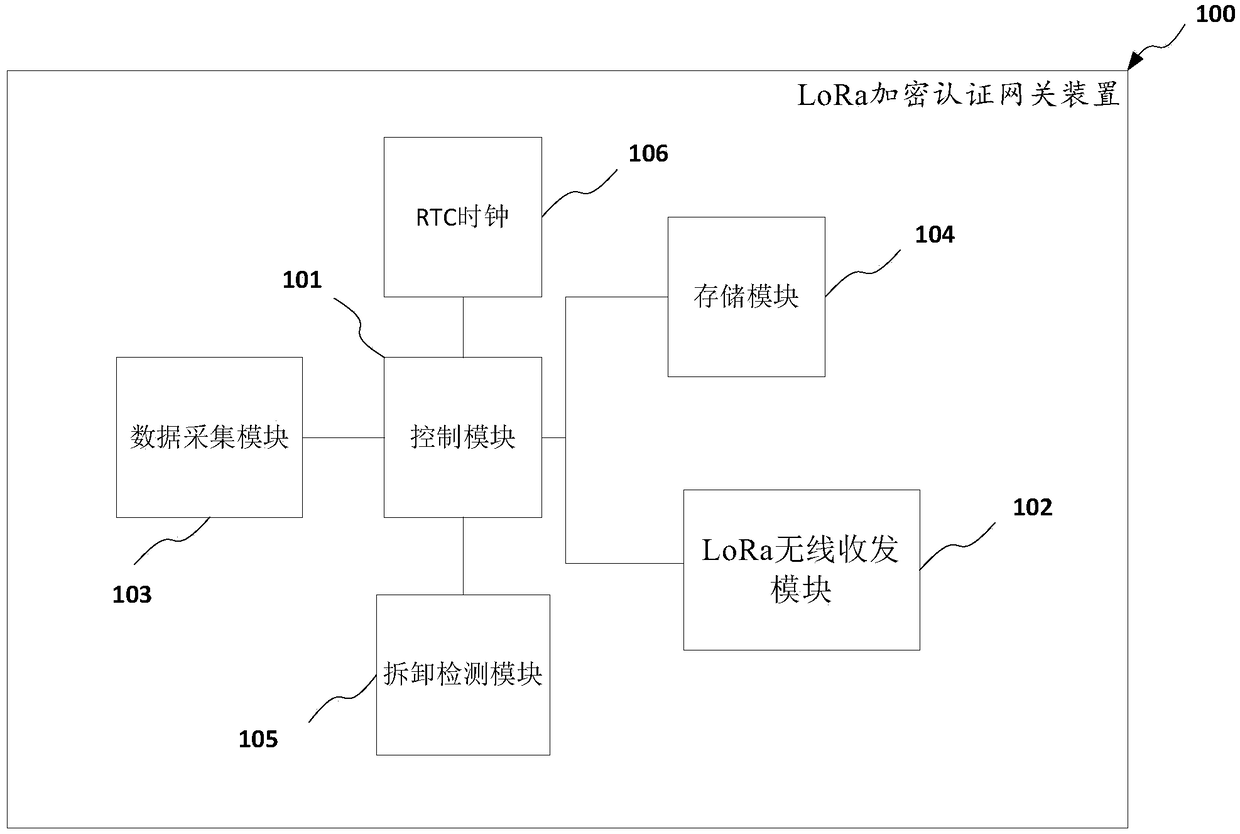
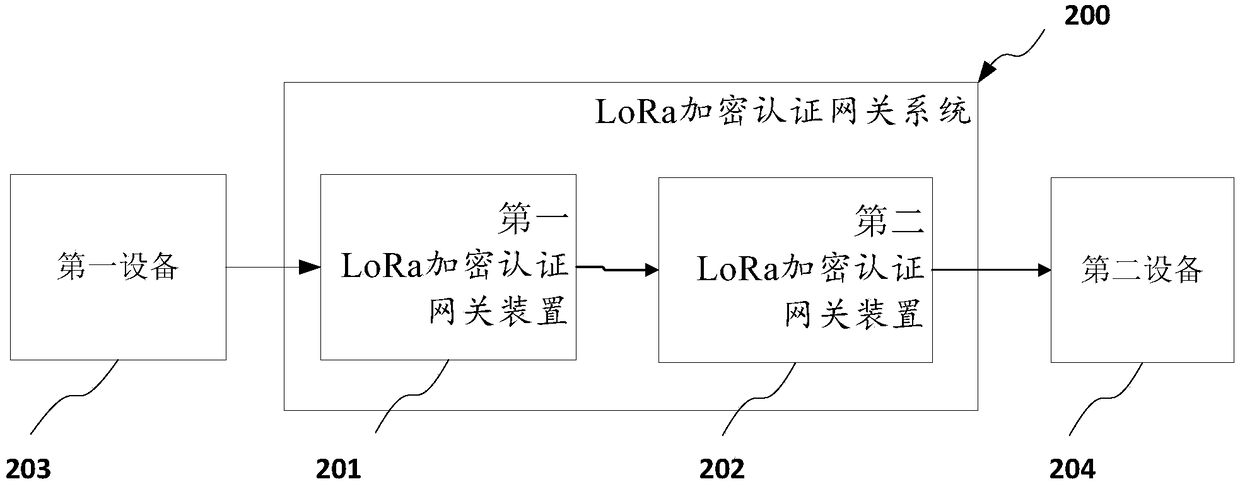
The invention discloses a LoRa encryption authentication communication method, a storage medium and an electronic terminal. The method comprises the following steps of making a control module of a LoRa encryption authentication gateway device generate a pair of public and private key pairs and carry out identity authentication to generate a session key; acquiring a plaintext message of a first device; encrypting the plaintext message to generate a corresponding ciphertext message; sending the ciphertext message to a remote LoRa encryption authentication gateway device; receiving the ciphertextmessage and verifying the ciphertext message; decrypting the ciphertext message into the plaintext message; and making the LoRa encryption authentication gateway device send the decrypted plaintext message to a second device through a serial interface. Through the adoption of the technical scheme, a LoRa encryption communication function can be realized, identity authentication and key managementfunctions are provided, and the non-repudiation and the key safety of the communication are improved.
Owner:广州邦讯信息系统有限公司 +1
Off-line payment method for bidirectional public key system authenticating of visible light and bar code
ActiveCN106910059AImprove securityEnhanced non-repudiationKey distribution for secure communicationProtocol authorisationPasswordData information
The invention discloses an off-line payment method for bidirectional public key system authenticating of visible light and a bar code. An off-line consumption apparatus with bidirectional authenticating of visible light and a bar code is established and consists of an electronic wallet, a consumption machine and a server. The payment method is implemented by the consumption machine and the electronic wallet. The electronic wallet sends a visible light signal and scans a bar code displayed by the consumption machine during the payment process; the consumption machine receives the visible light signal and generates a display bar code that can be scanned by the electronic wallet. Verification is carried out by using identity information of the consumption machine with a public key password system and the electronic wallet as well as transaction data information of the two sides, so that security of the off-line payment method can be improved and the non-repudiation property of the two sides in transaction can be guaranteed.
Owner:GUILIN UNIVERSITY OF TECHNOLOGY
Multi-biological feature authentication or identification-based method and system
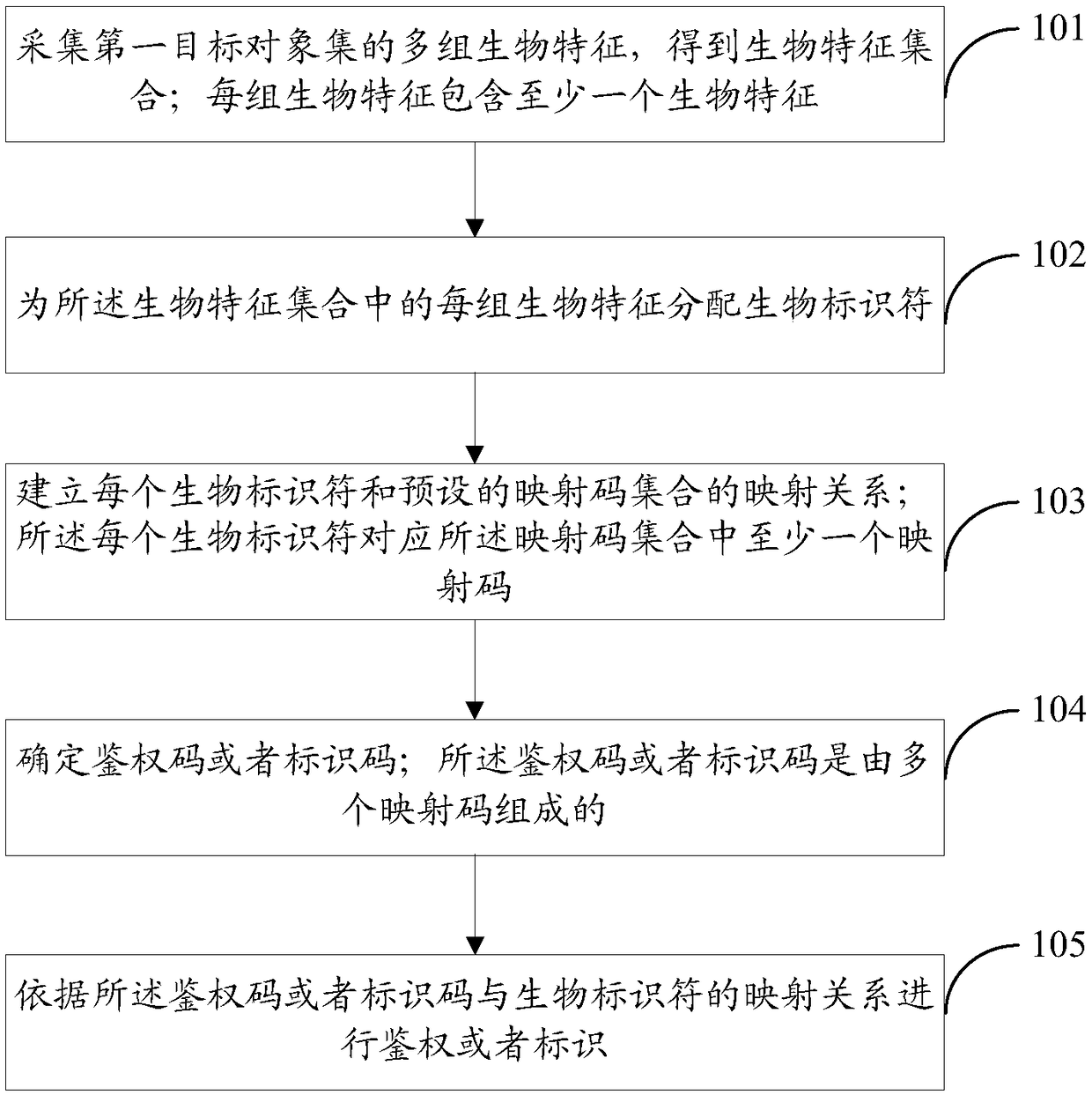
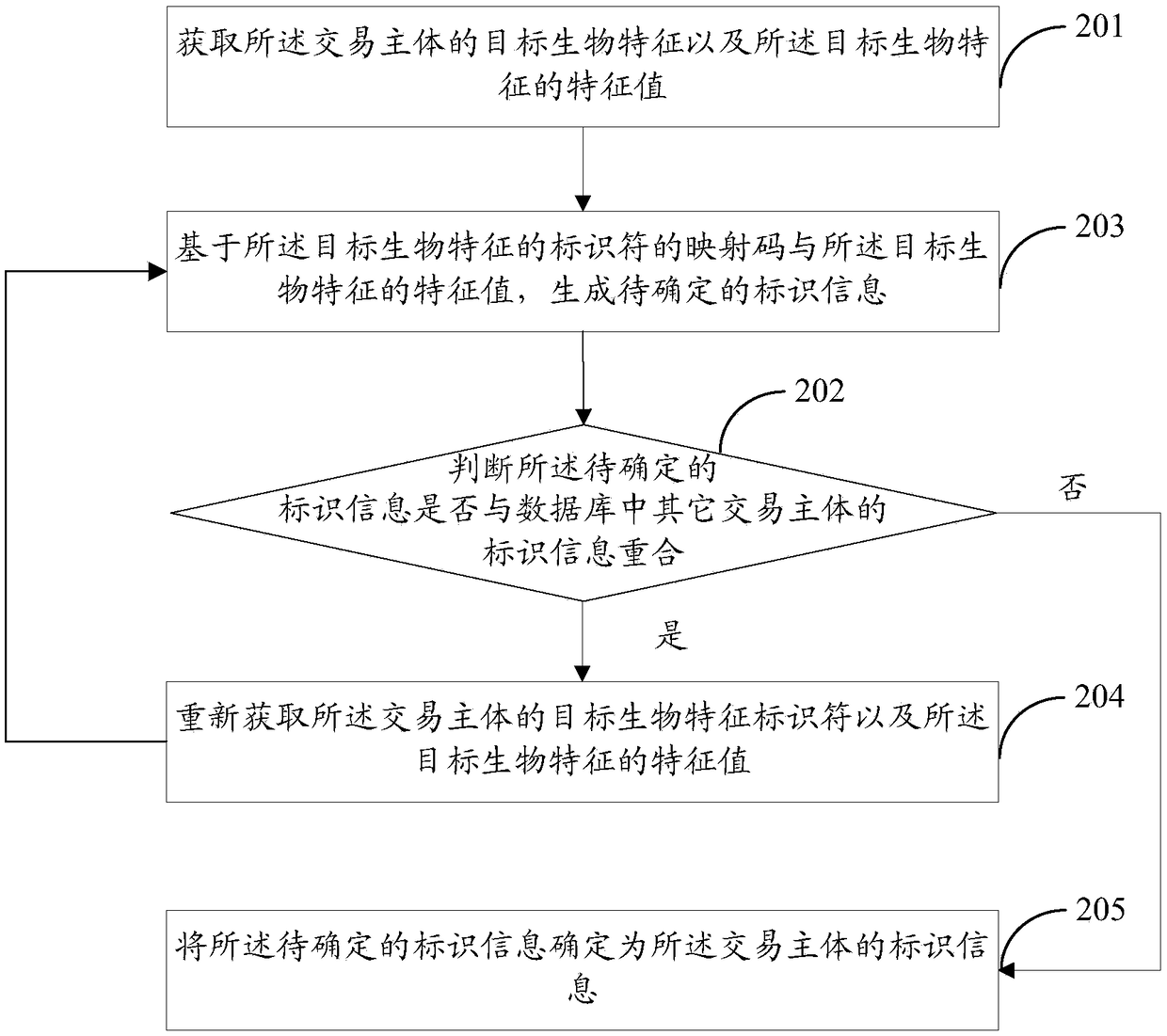
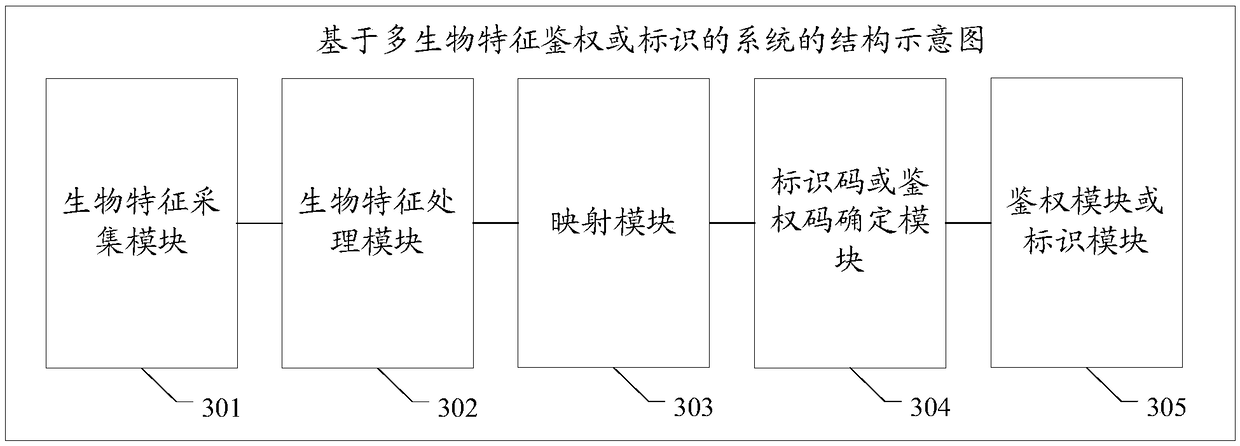
ActiveCN108717635AAvoid abuseImprove confidentialityProtocol authorisationPattern recognitionConfidentiality
The invention discloses a multi-biological feature authentication or identification-based method and system. The method comprises the following steps of: acquiring a plurality of groups of biologicalfeatures of a first target object set and obtaining biological feature values; in order to recognize each biological feature, distributing a biological feature identifier for each biological feature;establishing a mapping relationship between each biological feature identifier and a preset mapping code set; and after an authentication code or an identification code formed by mapping codes corresponding to a part or all of the biological feature identifiers is determined, carrying out authentication or identification according to the authentication code or the identification code. According tothe system and method, the problem that biological features of natural persons are abused as the biological features of the natural persons are leaked or the using of the biological features of the natural persons is not controlled by the natural persons is avoided, the confidentiality and verifiability of safety information are improved, and the non-repudiation is improved at the same time.
Owner:AGRICULTURAL BANK OF CHINA
Large agricultural product traceability management system based on block chain technology
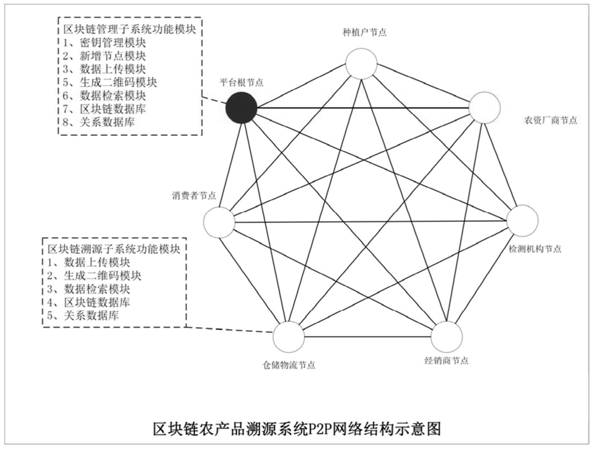
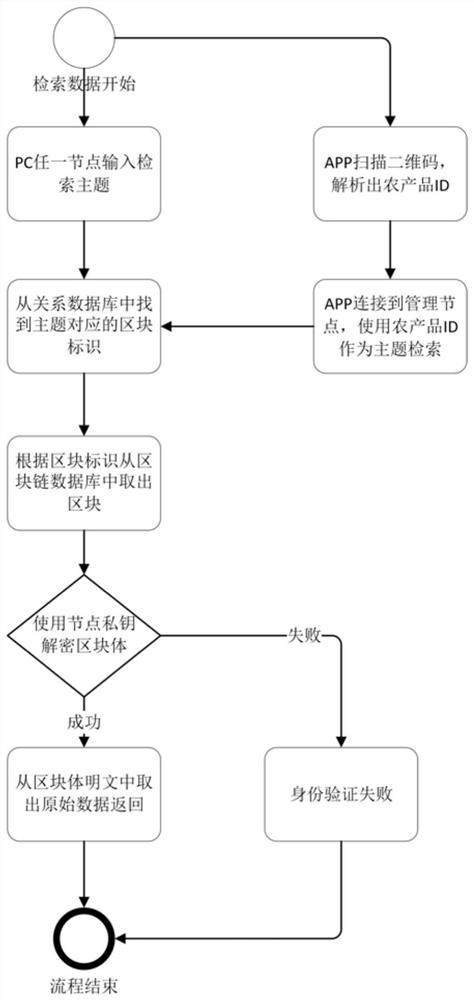
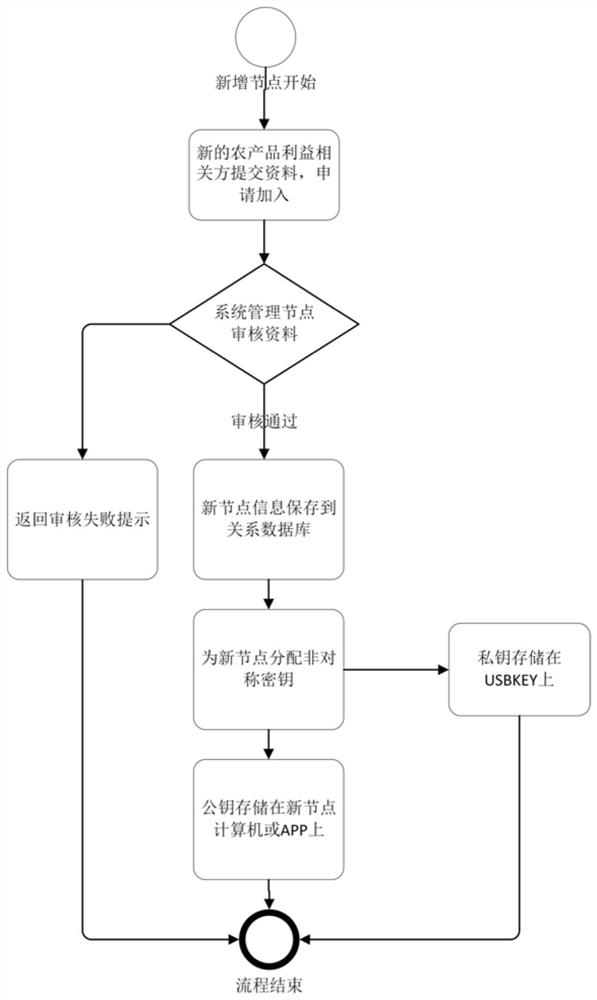
PendingCN112464253AStrong scalabilityImprove usabilityDatabase distribution/replicationRelational databasesBlockchainSource data
The invention discloses an agricultural product traceability management system based on a block chain technology. The agricultural product traceability management system comprises a management node, an agricultural product benefit related party node and a block chain management and block chain traceability subsystem. The management node is a platform root node, and the agricultural product benefitrelated party node is a collaborator and is responsible for uploading related process tracing data; the management node is in point-to-point connection with each agricultural product benefit relatedparty node through a P2P network. The block chain management subsystem is deployed on a management node server and is used for key management, node addition, data uploading and data retrieval; the block chain traceability subsystem is used for uploading data, generating a two-dimensional code and retrieving the data; the secret key management adopts an asymmetric secret key management system and is used for generating a pair of secret key public key and private key for the newly added node, and the public key is used for encrypting data and verifying signatures; and the private key is used fordecrypting the data and the personal signature. According to the agricultural product traceability management system, data cannot be tampered, the system is complete and real, and the trust problem of agricultural product traceability can be solved.
Owner:云南天质弘耕科技有限公司
Electricity stealing evidence data processing method and system based on space-time body measurement four-dimensional data
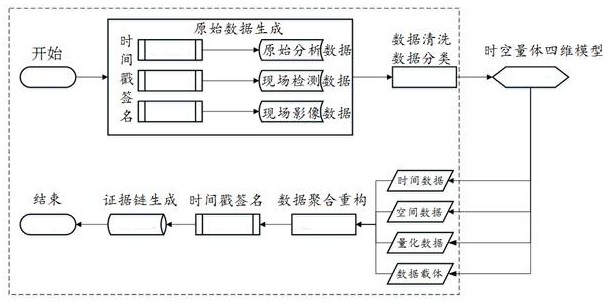
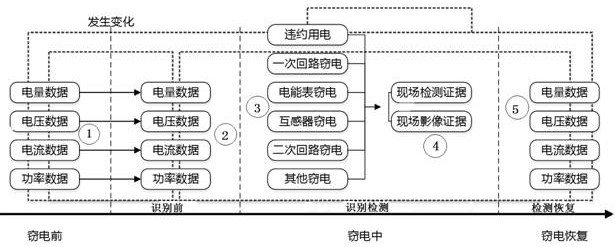
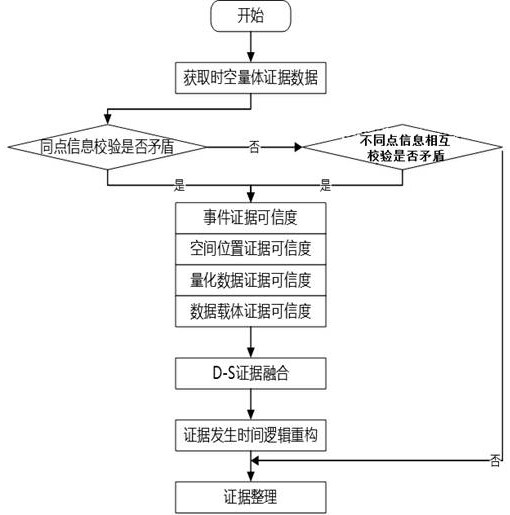
ActiveCN114416753AImprove relevanceIncrease authenticityDatabase updatingData processing applicationsTimestampOriginal data
The invention provides an electricity stealing evidence data processing method and system based on space-time body measurement four-dimensional data, and belongs to the technical field of data processing. Data to be processed is decomposed into time data, space position data, quantitative data and a data carrier by using a preset four-dimensional data model; according to the first dynamic event window, the second dynamic event window, the fourth dynamic event window and the fifth dynamic event window, the time data, the spatial position data, the quantitative data and the data carrier are reconstructed based on the D-S evidence theory; a credible timestamp signature is added to the reconstructed data to obtain final electricity stealing evidence key data; according to the method, a space-time body measurement four-dimensional evidence chain processing mechanism is established, original data, field detection evidence and field image evidence are refined into four dimensions of time, position space, quantitative data and data carriers, and relevance (obtained by time, places and the same equipment) among the evidences is enhanced; and the authenticity, integrity and effectiveness of the evidence data are improved.
Owner:国网山东省电力公司营销服务中心(计量中心) +1
Method for protecting digital certificate by iris recognition technology
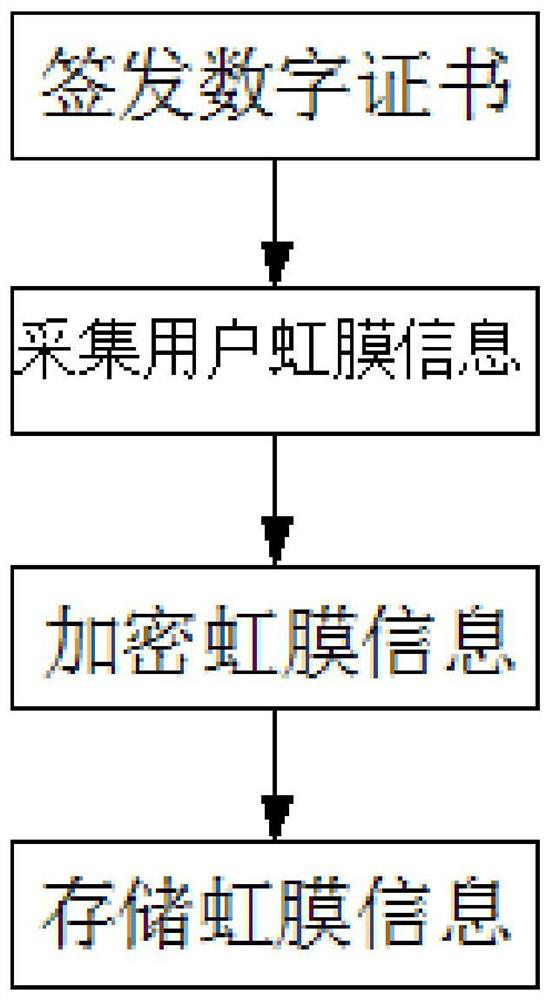
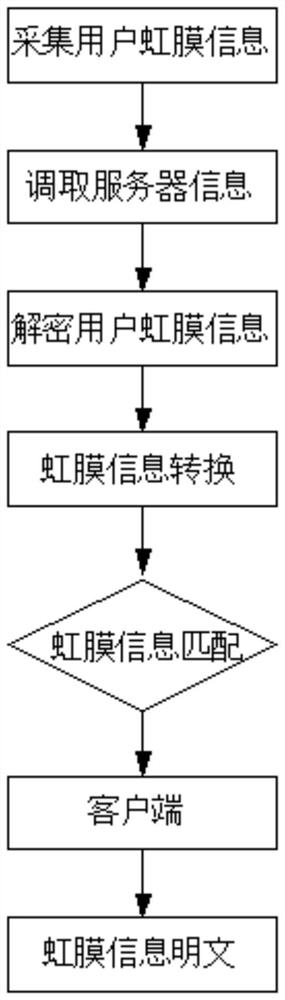
PendingCN111831993AImprove securityImprove convenienceCharacter and pattern recognitionDigital data authenticationPattern recognitionCiphertext
The invention relates to a method for protecting a digital certificate by an iris recognition technology. The method for protecting the digital certificate through the iris recognition technology comprises an iris acquisition instrument, a server, a client side and an iris recognition terminal, and comprises the following steps that a certificate issuing mechanism issues the digital certificate toa user, and iris image information is converted into binary iris information P1 through the iris acquisition instrument according to the iris image information of the user; binary exclusive-OR operation is carried out on the iris template P1 and certificate private key data to generate a ciphertext K1, and the ciphertext K1 is stored; the iris template data of the user is encrypted into a ciphertext P2 by using algorithms such as AES / SM2 and the like, and the ciphertext P2 is stored; a user uses the iris acquisition instrument to adopt the iris image information P1, the iris information is sent to a server, and the server converts the received user iris image information into binary iris information P2; and the server decrypts the locally stored user iris data to obtain an iris template P3, and the P2 is compared with the P3.
Owner:吉林无罔生物识别科技有限公司
System and method for adding real-time file dynamic tags and encryption online
InactiveCN105323064BImprove securityImprove reliabilityKey distribution for secure communicationUser identity/authority verificationEncryptionData input
Owner:柯呈翰
An identity authentication device combining digital signature, handwriting and fingerprint
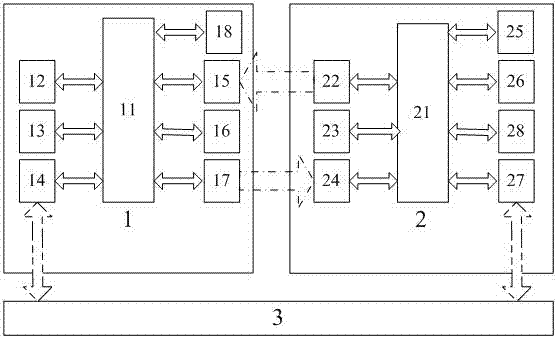
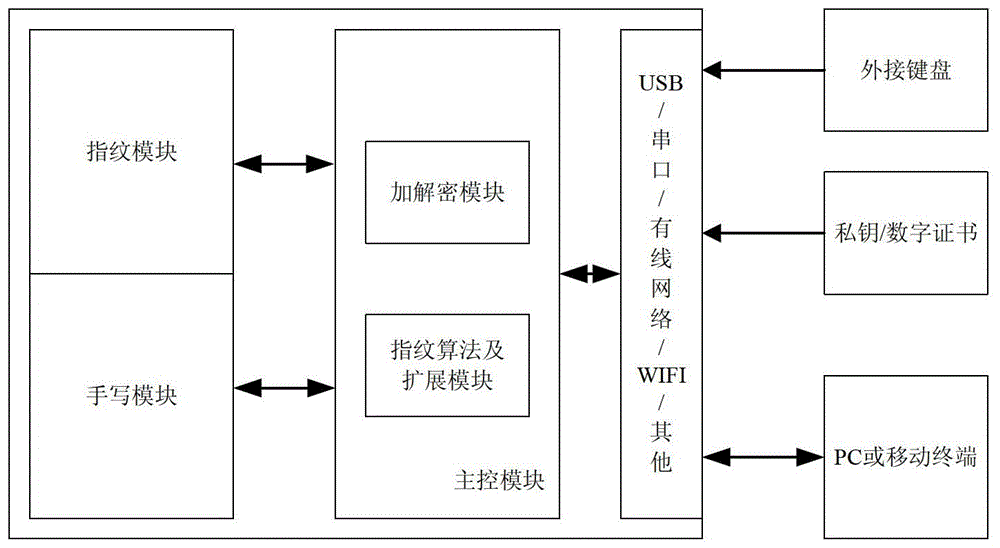
ActiveCN103259659BAchieve traceabilityEasy to integrateUser identity/authority verificationHandwritingUSB
The invention relates to an identity authentication device and method with a digital signature, handwriting and a fingerprint combined. The identity authentication device with the digital signature, the handwriting and the fingerprint combined comprises a main control module, a fingerprint module and a handwriting module, wherein the main control module is connected with a PC, or an external connecting disk, or a mobile terminal via a USB / a serial port / a wired network / a WIFI external data interface, the handwriting module is used for adding a handwriting signature to a relevant position of an electronic document under the condition that a user needs to carry out a traditional signature on the electronic document, the fingerprint module is used for obtaining a fingerprint image and delivering the fingerprint image to the main control module, the main control module will carry out identity authentication based on the fingerprint image and add the fingerprint to a relevant position of the document, and the main control module is used for providing an encryption and decryption algorithm and a fingerprint algorithm, main logical processing, external control and communication data processing. The identity authentication device with the digital signature, the handwriting and the fingerprint combined has the advantages that a traditional signature mode can be achieved in the paperless office environment, usage habits of a user are changed as few as possible, the application reliability is higher than that achieved by only usage of a PKI system, and the problems that the traditional paper signature is prone to damage, difficult to inquire, and high in saving cost are solved.
Owner:HANGZHOU SYNOCHIP DATA SECURITY TECH CO LTD
A digital certificate application method, system, fog node and certificate authority center
ActiveCN108683506BEnhanced non-repudiationImprove securityKey distribution for secure communicationUser identity/authority verificationComputer networkInternet privacy
Owner:INSPUR GROUP CO LTD
Electronic signature generation and verification method and electronic device with digital watermark
ActiveCN110474773BEnhanced non-repudiationStrengthen the unique binding relationshipKey distribution for secure communicationUser identity/authority verificationComputer hardwareEngineering
A method for generating an electronic signature with a digital watermark, executed by an electronic device, during a shooting period for generating a video, obtaining a summary of the signature message according to file data and mathematical functions related to the file, and obtaining a summary of the signature message for the video For each image received after the summary of the signature message, signature track data is generated according to all track messages related to the signer's signature track received before the reception time of the image, and the signature track data is converted into the signature track data. added to the image, and upon obtaining the signature message digest, the electronic device adds a digital watermark comprising the signature message digest to the video to generate an electronic signature comprising the video. In addition, the present invention also provides an electronic signature verification method and an electronic device.
Owner:THINKCLOUD DIGITAL TECH
Double-medium double-authentication fast offline payment method under the public key system
ActiveCN106920096BImprove securityEnhanced non-repudiationPublic key for secure communicationClose-range type systemsBarcodeEngineering
The invention discloses a double medium and double authentication fast off-line payment method under a public key system, which comprises the steps that a double medium off-line payment device under a VLC (Visible Light Communication) and Barcode public key system is built, wherein the double medium off-line payment device comprises an electronic wallet, a consumption machine and a server; implementation of the payment method is accomplished by the consumption machine and the electronic wallet; the electronic wallet sends visible light signals in the payment process and scans a barcode displayed by the consumption machine; and the consumption machine receives the visible light signals and generates a display barcode provided for the electronic wallet to scan. Mutual verification is performed on the identity and transaction information of the consumption machine and the electronic wallet by adopting the public key system, and the security of the off-line payment method and the non-repudiation of the two transaction parties are effectively improved.
Owner:GUILIN UNIVERSITY OF TECHNOLOGY
Duplicating monitoring system
ActiveCN102749874BControl copy permissionsPrevent illegal useProgramme controlComputer controlDuplicate contentMonitoring system
The invention discloses a duplicating monitoring system and relates to the technical field of computer technology and information safety. The system comprises a monitoring terminal and a server, wherein the monitoring terminal is used for locking and unlocking a duplicator to obtain identity information and image information of a duplicator user and duplicating logs and duplicating contents of a legal user, and the identity information, the image information and the duplicating logs and the duplicating contents of the legal user can be uploaded to the server by the monitoring terminal in real time, and the server is used for checking legality of the user, receiving the user's identity information, image information, duplicating logs and duplicating contents sent by the monitoring terminal, generating an audit report which includes the identity information and the image information of the legal user and the corresponding duplicating logs and contents of the legal user, and supplying inquiry of the audit report. The system has the advantages that the duplicator is controlled to be merely used by authorized users, the duplicating logs can be comprehensively, accurately and automatically recorded, simultaneously the audit report of the duplicating logs is supplied, and the system is convenient for administrative stuffs to inquire and audit the duplicating operation.
Owner:BEIJING LANXUM COMP TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com