Patents
Literature
39results about How to "Improve data confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
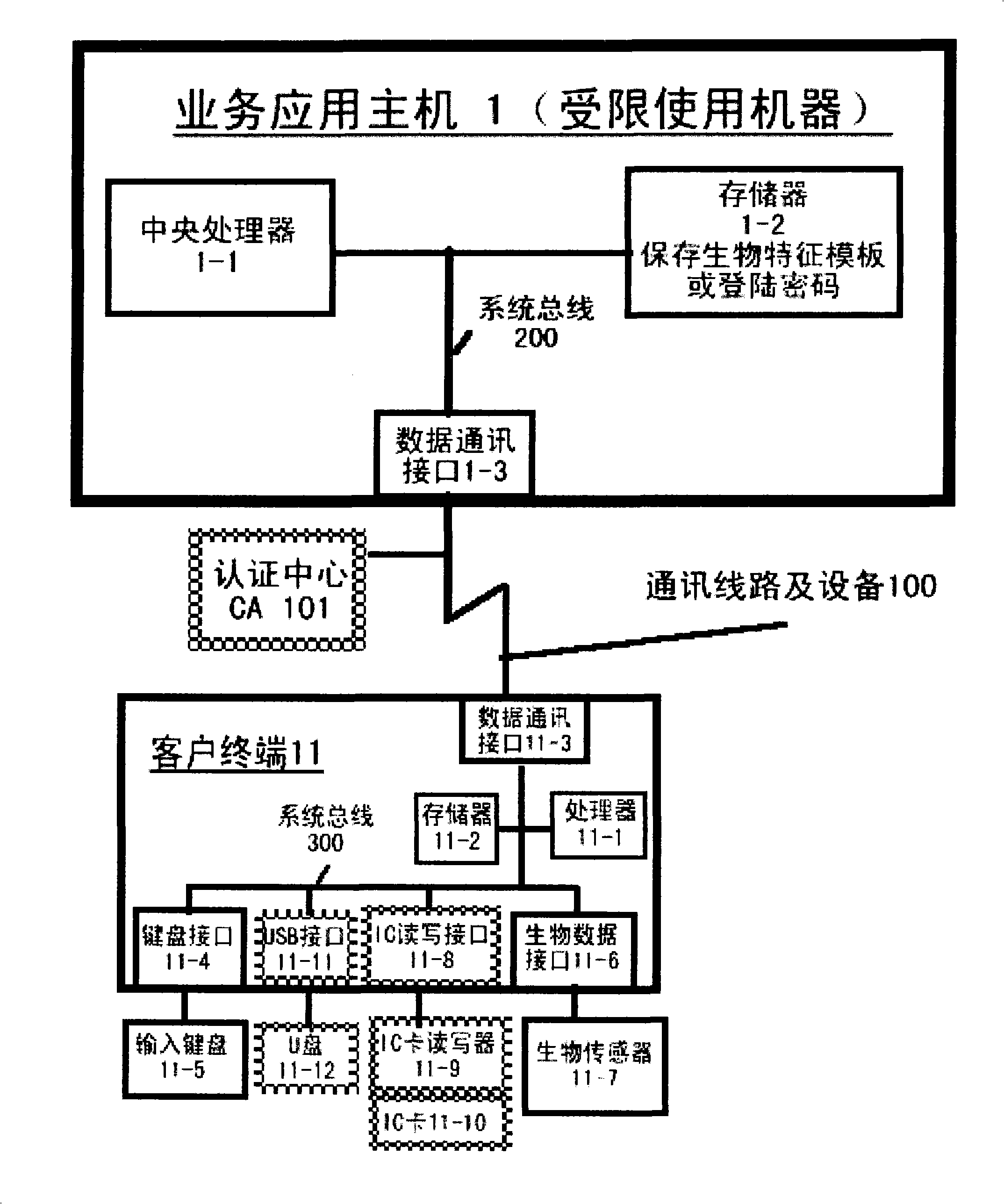
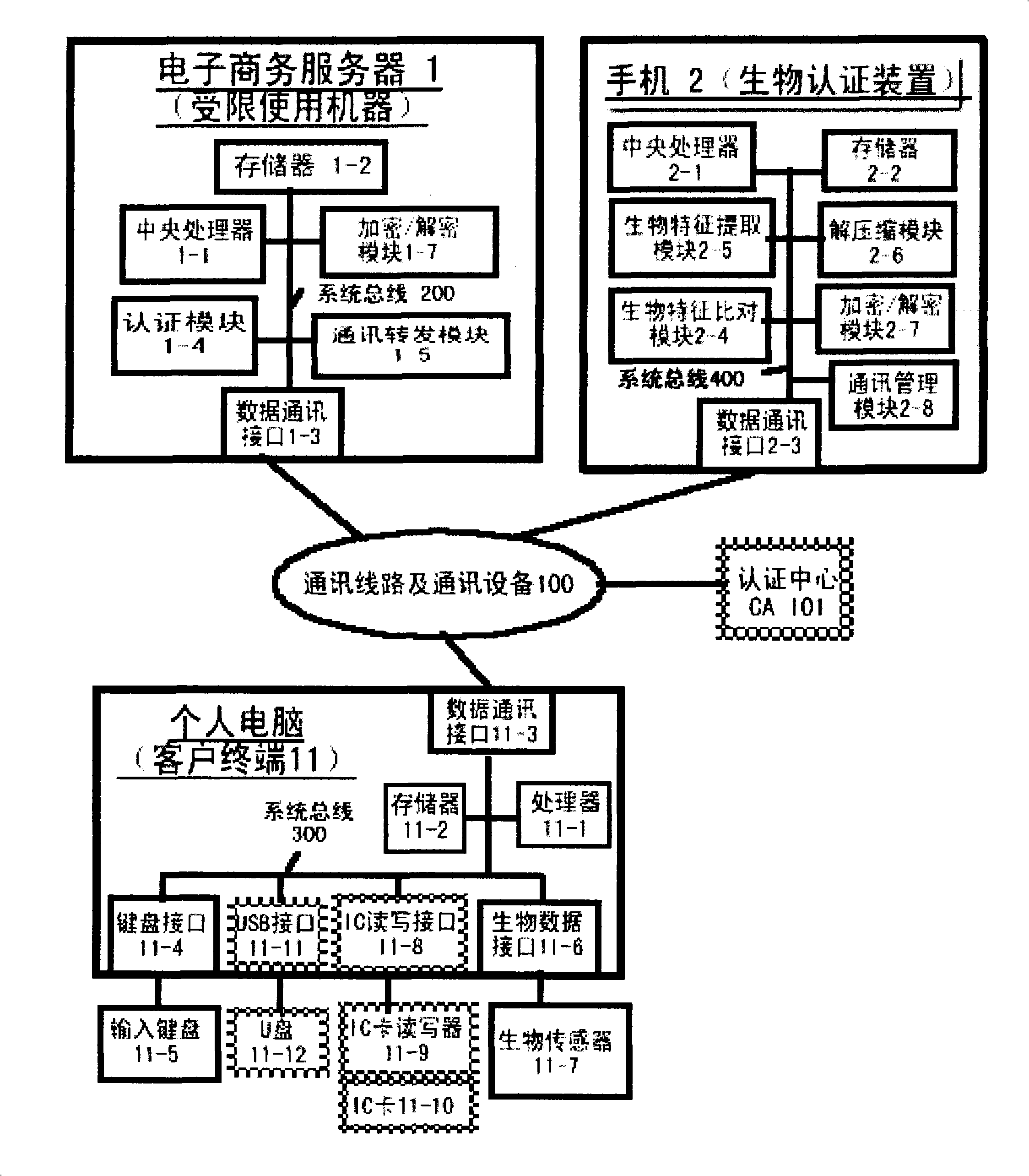
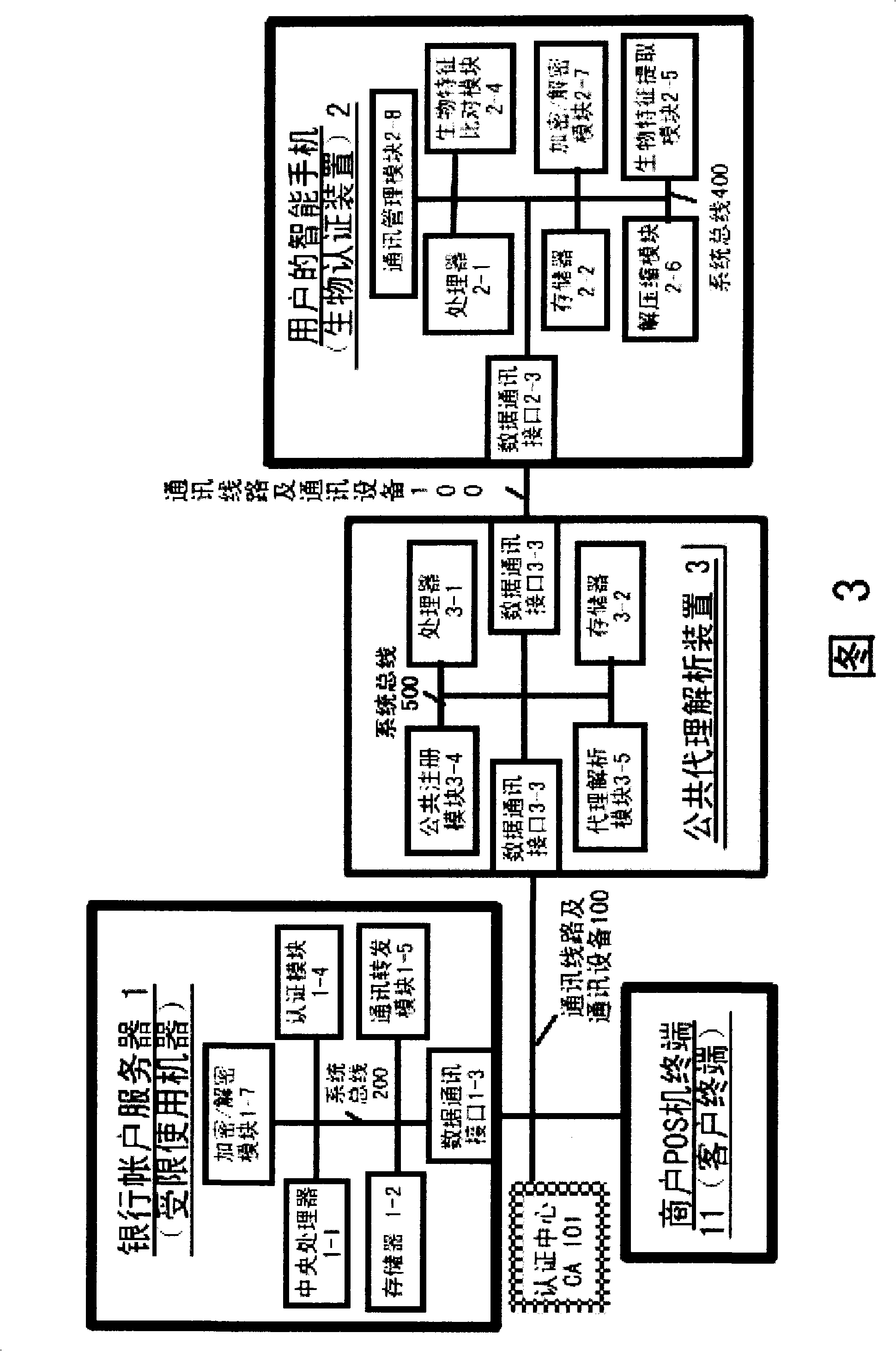
Authentication system based on biological characteristics and identification authentication method thereof
InactiveCN101330386AAttack is notAttacks are not directlyUser identity/authority verificationCharacter and pattern recognitionInternet privacyComputer terminal
The invention relates to an authentication system and an authentication method based on biological features. The method comprises the steps of conducting centralized storage and biological feature comparison operation for a large quantity of user biological feature templates according to user ID identifiers stored on a memory on a limited use machine and corresponding biding ID identifiers thereof on a biological authentication device of a digital processing terminal; separating the biological feature templates from the authentication function of the limited use machine; allocating to digital processing terminals (including PCs, notebooks or mobile phones, PDAs of users)of users as biological authentication device-storing the biological feature templates with decentralization and operating and processing biological features to be authenticated with decentralization so as to conduct comparison with the biological feature templates pre-stored on the respective digital processing terminals; feeding back comparison and verification results to the limited use machines; authorizing to conduct equal authentication of the biological authentication device ID identifier on the digital processing terminal for the corresponding binding user ID identifiers by the centralized authentication of the limited use machine according to the comparison verification result data.
Owner:刘洪利
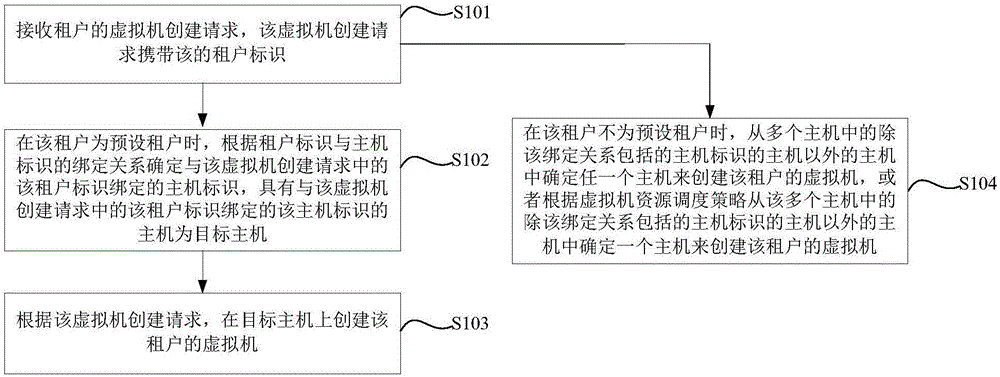
Virtual machine creating method and system and host
PendingCN106354544AAchieve physical isolationImprove data confidentialitySoftware simulation/interpretation/emulationData securityVirtual machine
The embodiment of the invention provides a virtual machine creating method and system and a host. Each host identity in a binding relationship between tenant identities and host identities only corresponds to one tenant identity; for any one tenant having a physical isolation requirement on the host, the virtual machine creating system can only create a virtual machine of the tenant in the host having the host identity corresponding to the tenant identity of the tenant but cannot create the virtual machine of the tenant in the hosts having the host identities corresponding to the tenant identities of other tenants, that is to say, the host having the host identity corresponding to the tenant identity of the tenant can only contain the virtual machine of the tenant but cannot contain the virtual machines of the other tenants; therefore, physical isolation among the virtual machines of different tenants is achieved, and then the data security among the virtual machines of different tenants is improved.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
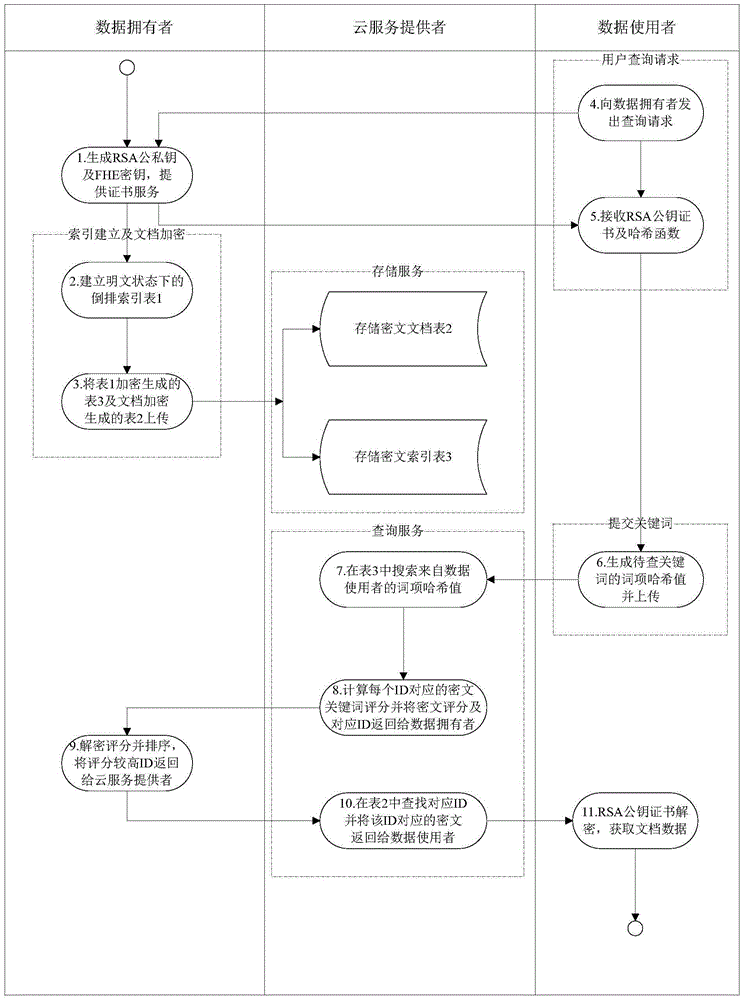
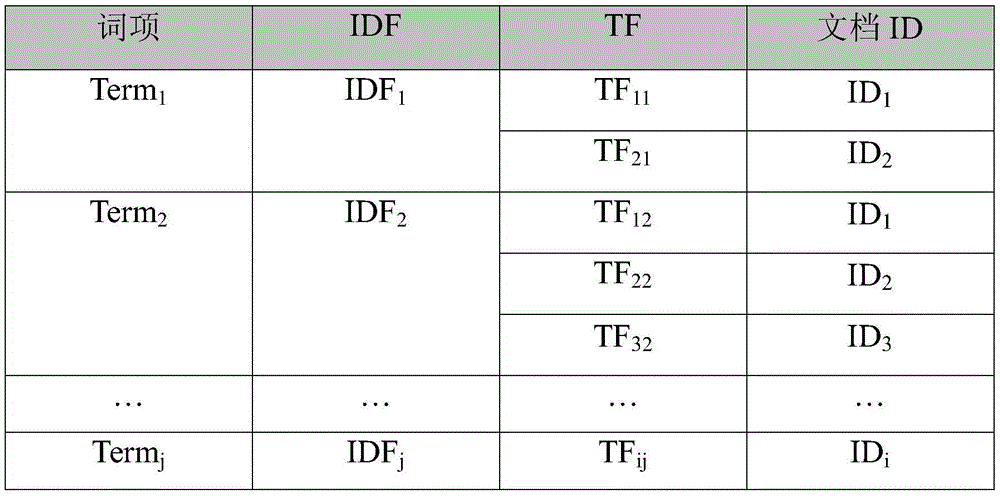
Cloud storage oriented ciphertext full-text search method and system based on full homomorphic ciphers
ActiveCN105610910ARealize privacy protectionImprove data confidentialityDigital data protectionTransmissionFull text searchCiphertext
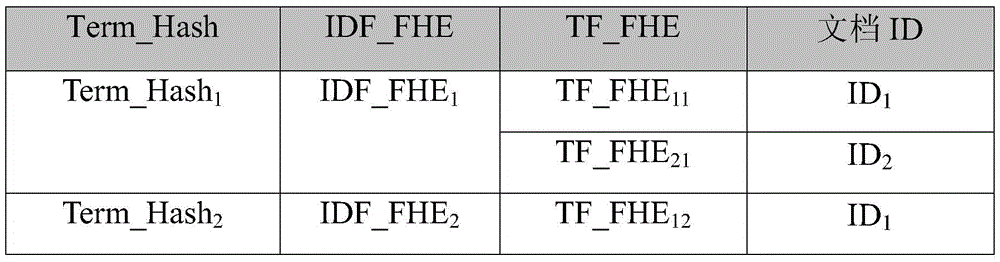
The invention discloses a cloud storage oriented ciphertext full-text search method and system based on full homomorphic ciphers. The method comprises that a data owner uploads document IDs, encrypted document ciphertexts and an encrypted document inverse index table to a cloud server; hash operation is carried out to the document terms on the inverse index table; TF (Term frequency) and IDF (Inverse document frequency) values are encrypted by a full homomorphic technique on integers; a public key certificate is issued to a data user; the data user carries out hash operation to to-be queried keywords and uploads to a cloud service provider; the cloud service provider compares and searches the hash operation values of the to-be queried keywords and the hash operation values of the document terms on the inverse index table; and the cloud service provider carries out full homomorphic multiplication and add operations. According to the method and the system of the invention, the calculation is carried out in a ciphertext state; in the calculation process, any information related to the documents will not be leaked to the cloud service provider and other attackers; the data privacy of the data owner and the query data privacy of the data user are protected; and moreover, the controllability of the data right of use is realized.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
Storage medium and method and apparatus for separately protecting data in different areas of the storage medium
InactiveUS20050251866A1Difficult to analyzeImprove data confidentialityInput/output to record carriersDigital data processing detailsCiphertextPassword
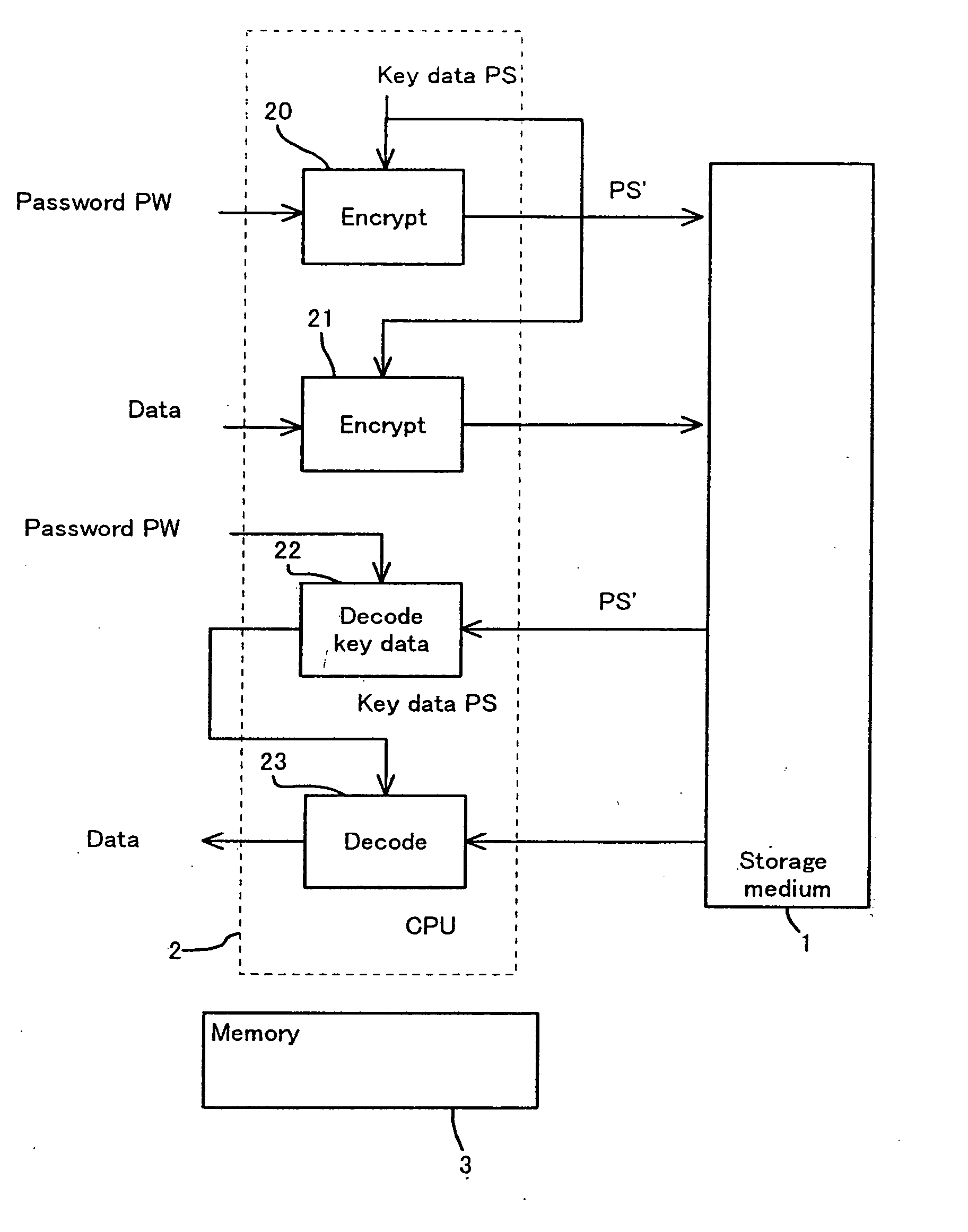
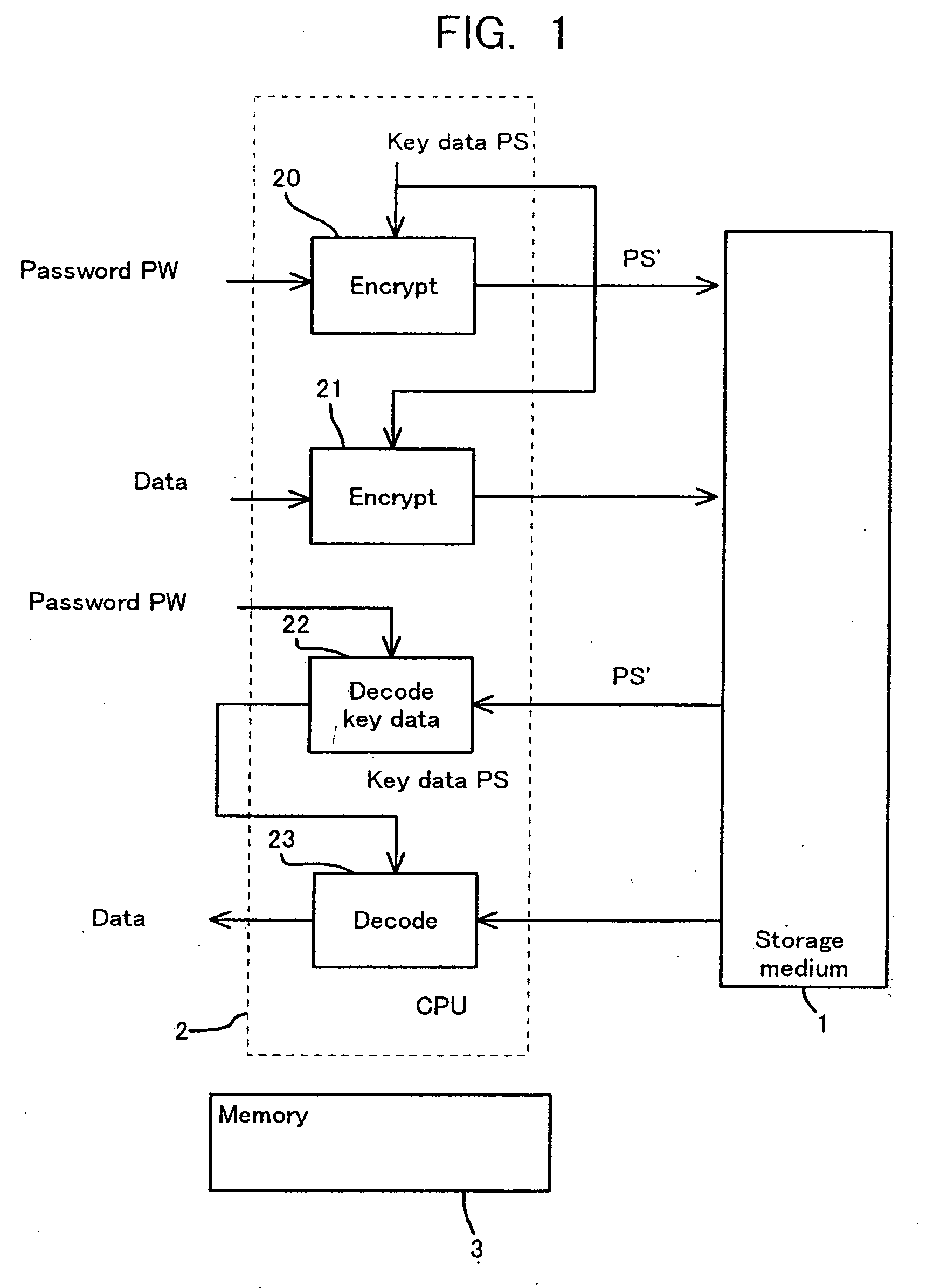
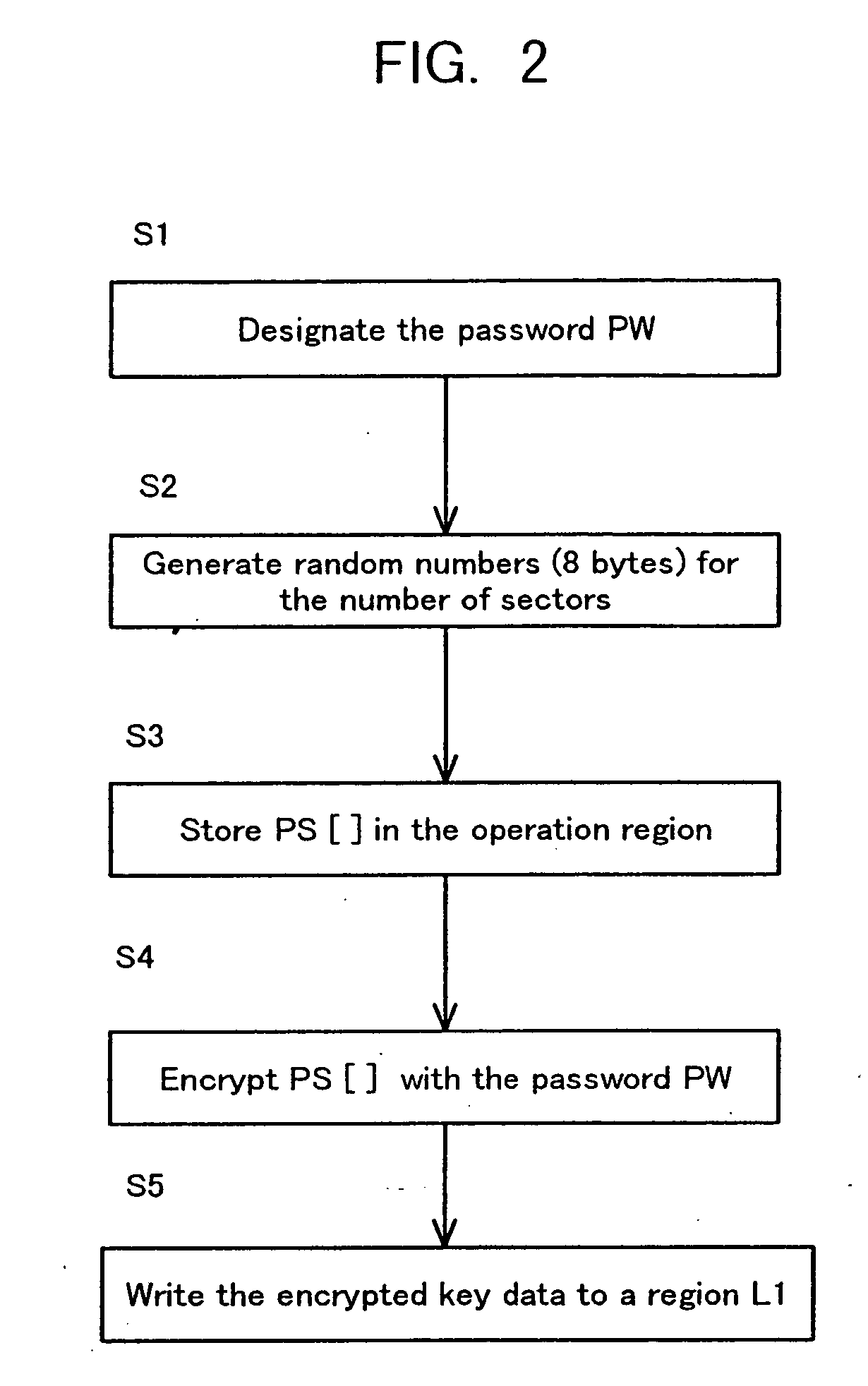
Disclosed are a method and an apparatus for protecting data on a storage medium by encrypting the data to be recorded on the storage medium with a password. This method comprises a step of, generating, for changing key data on each memory unit by one password, the key data, thereafter encrypting the key data with the password and writing the encrypted data to the storage medium, and a step of encrypting the data with the key data and encrypted data to the storage medium. The method further comprises a step of reading the encrypted key data from the storage medium, a step of decoding the encrypted key data with the password, and a step of decoding the data on the storage medium with the decoded key data. The encryption is done by using the key data generated separately from the password, and it is therefore feasible to prevent the password from being analyzed by decoding a cipher text.
Owner:FUJITSU LTD
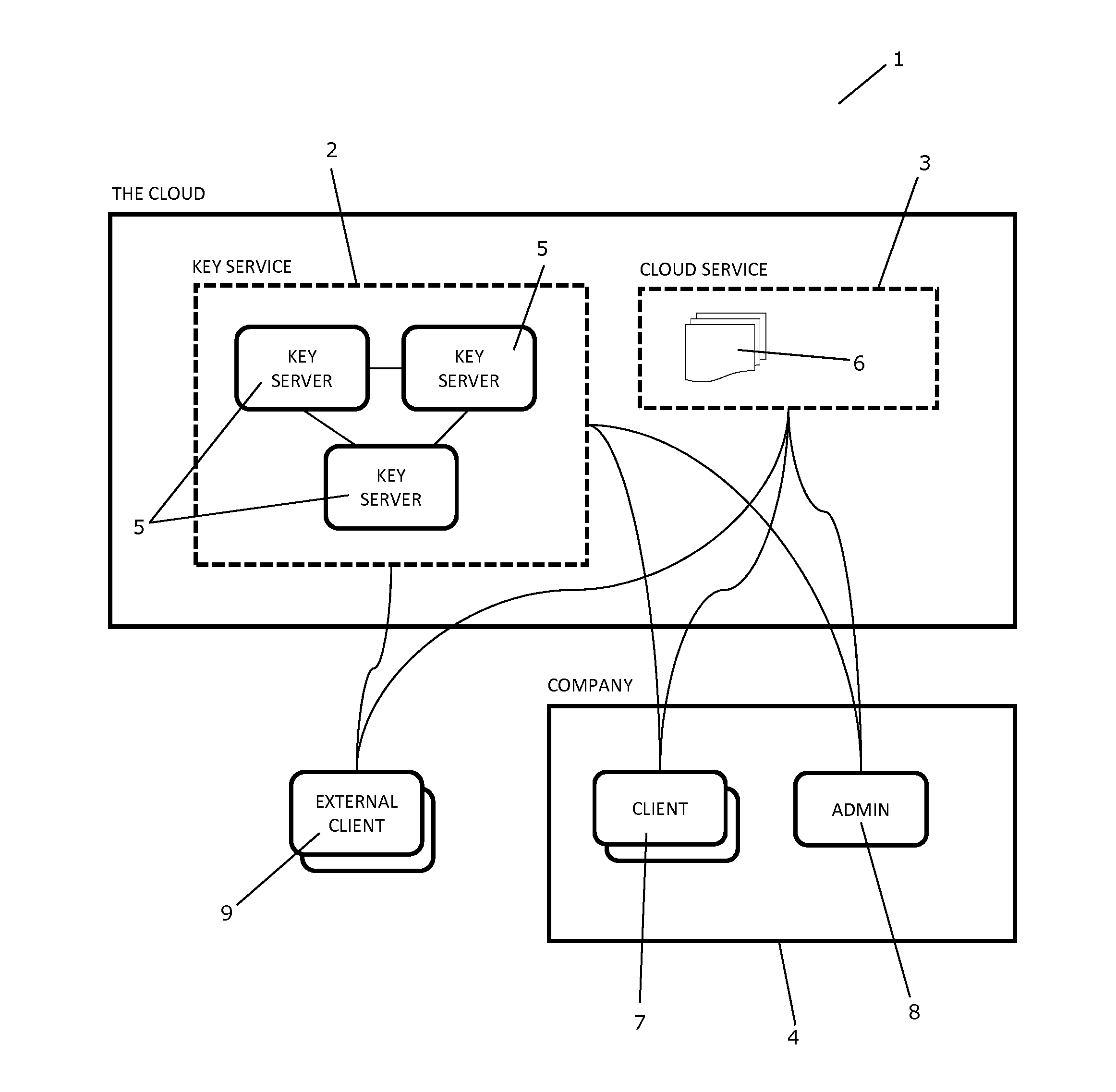
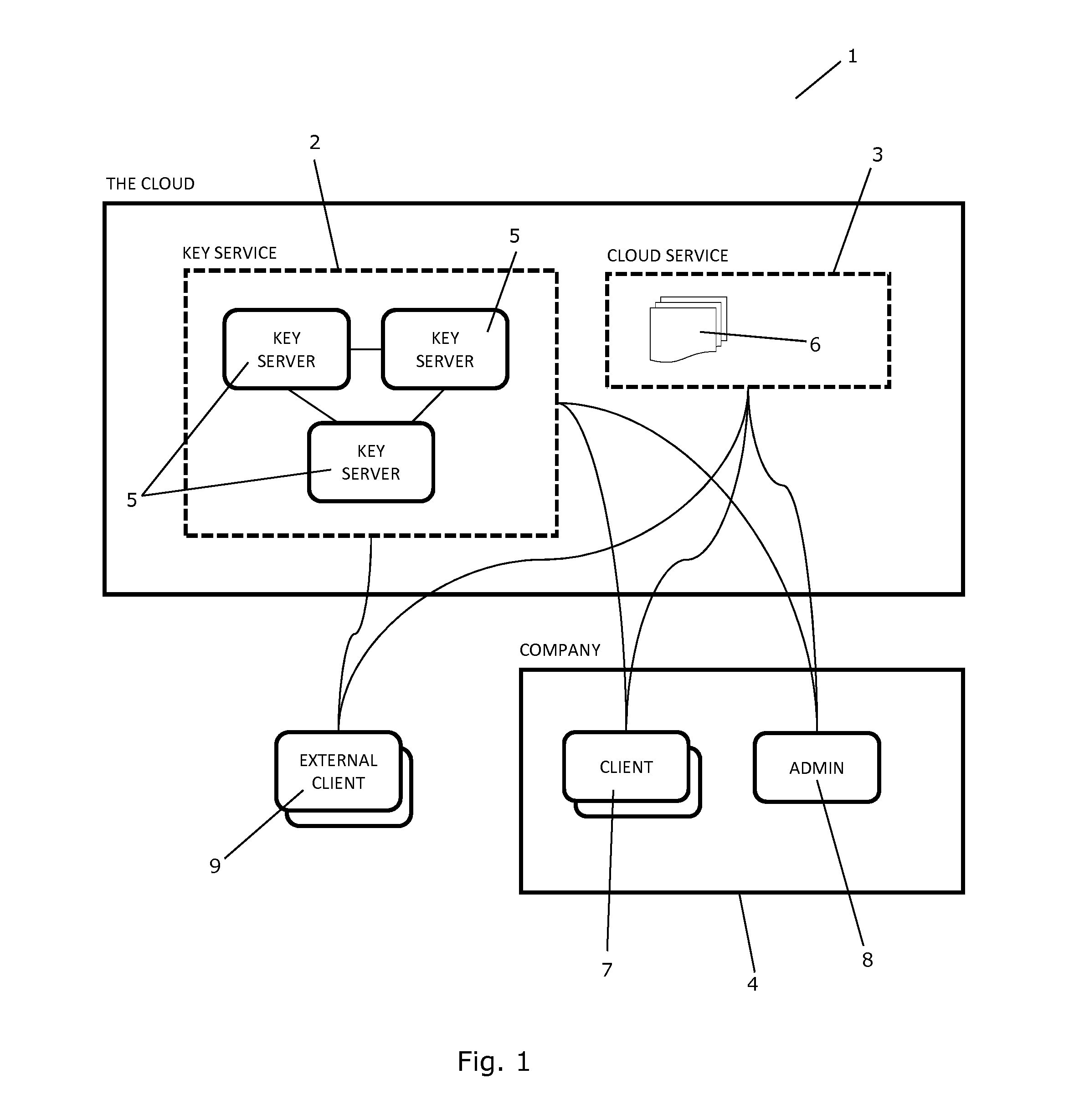
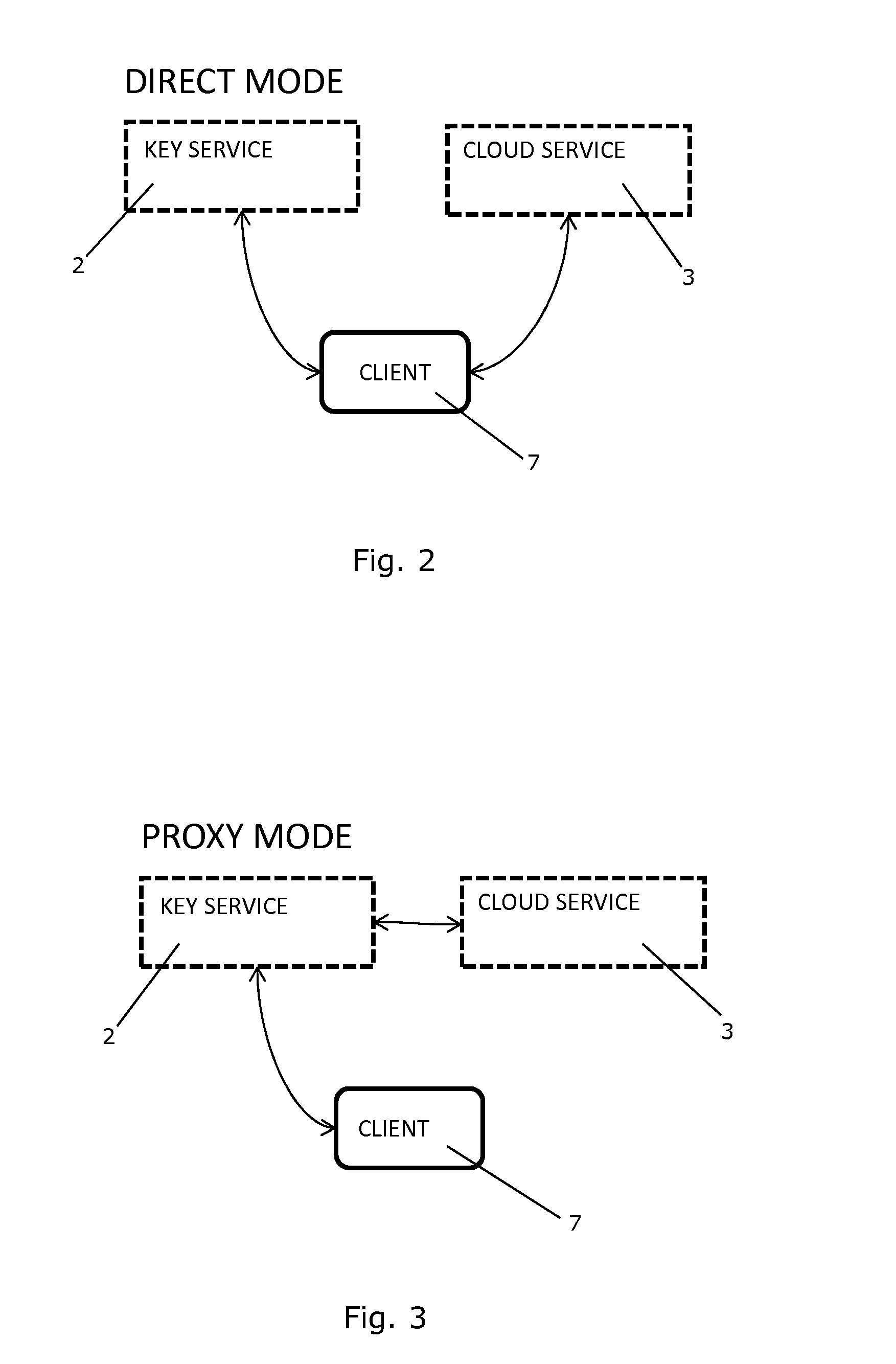
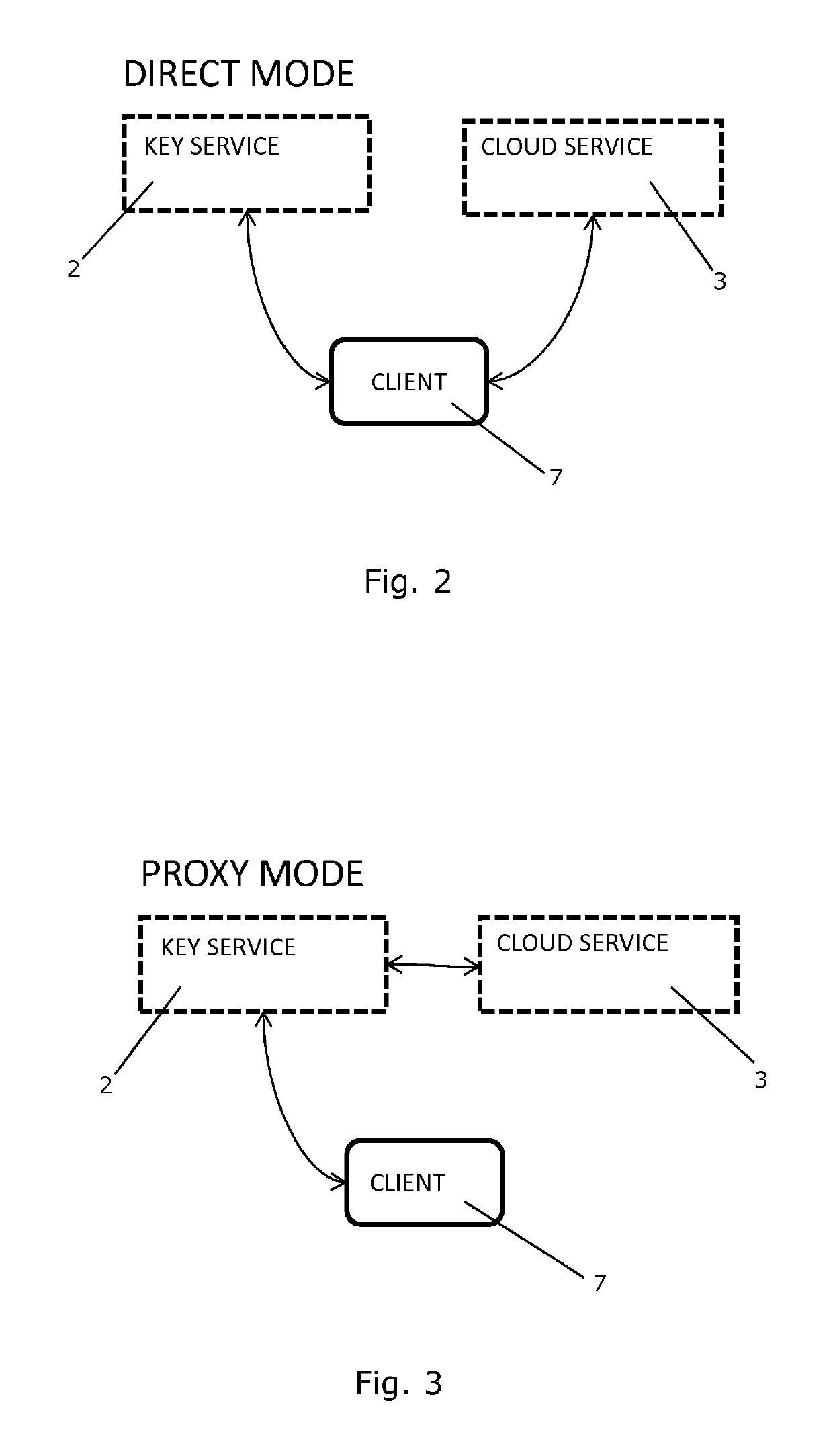
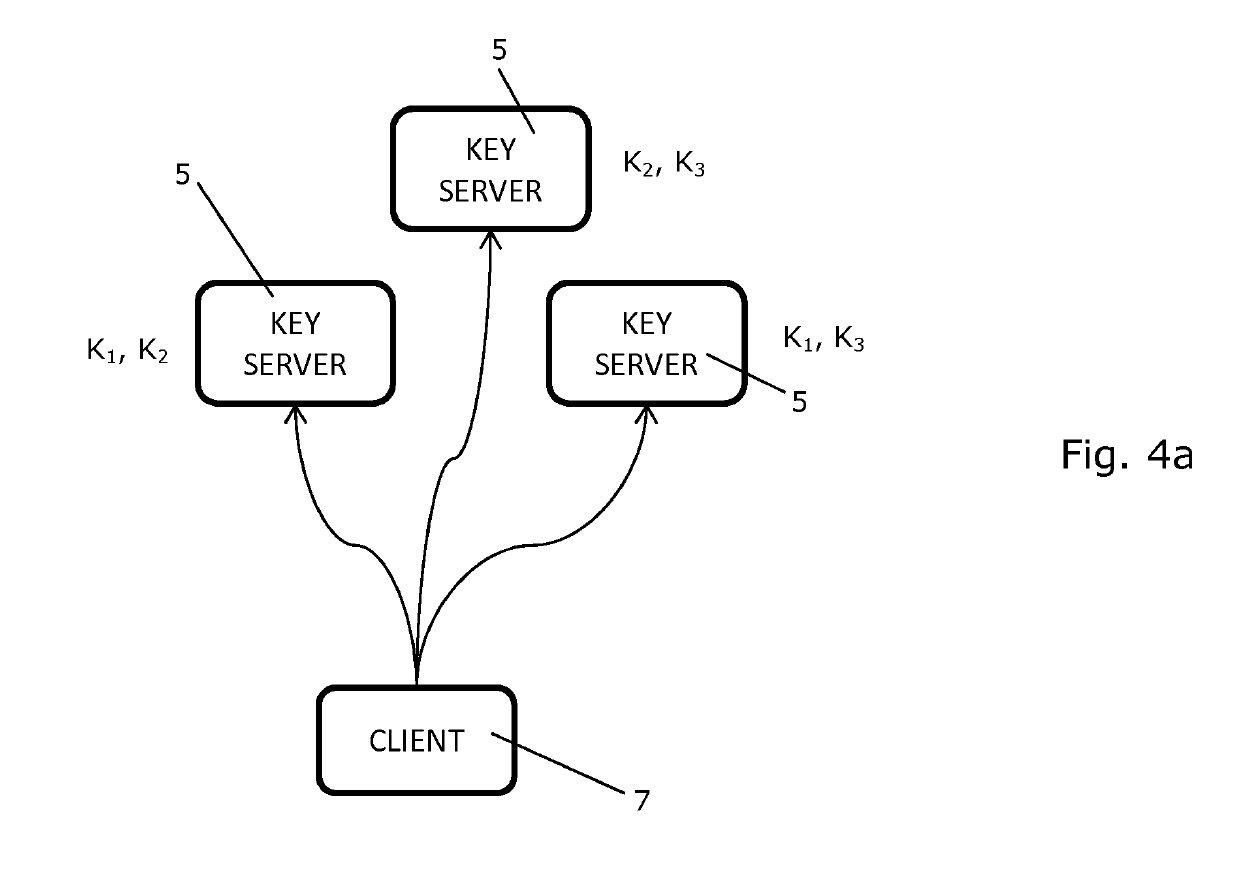
A System and a Method for Management of Confidential Data
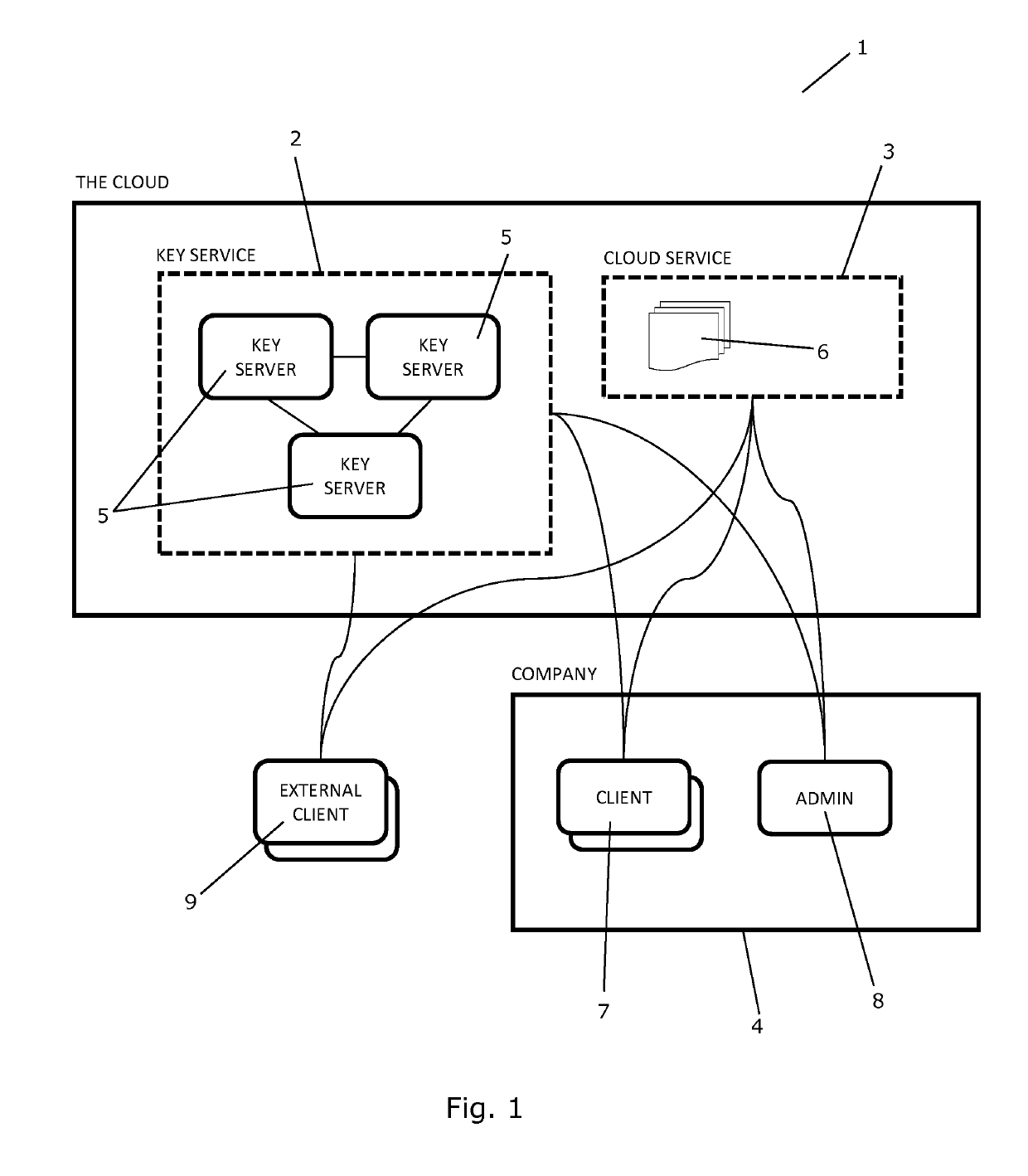
ActiveUS20160253515A1Improve data confidentialityImprove confidentialityKey distribution for secure communicationDigital data protectionEncryptionSingle point
A system and a method for managing confidential data in a cloud service is provided. The system comprises a cryptographic key service comprising two or more cryptographic key servers, Si, each being arranged to compute file encryption keys, kj, on the basis of information regarding data and using one or more cryptographic keys, Kj. The cryptographic keys, Kj, are secretly shared among the cryptographic key servers, Si, and none of the cryptographic key servers, Si, possesses knowledge of all of the cryptographic keys, Kj. A single point of trust at the cryptographic key service is avoided.
Owner:KMAAS APS
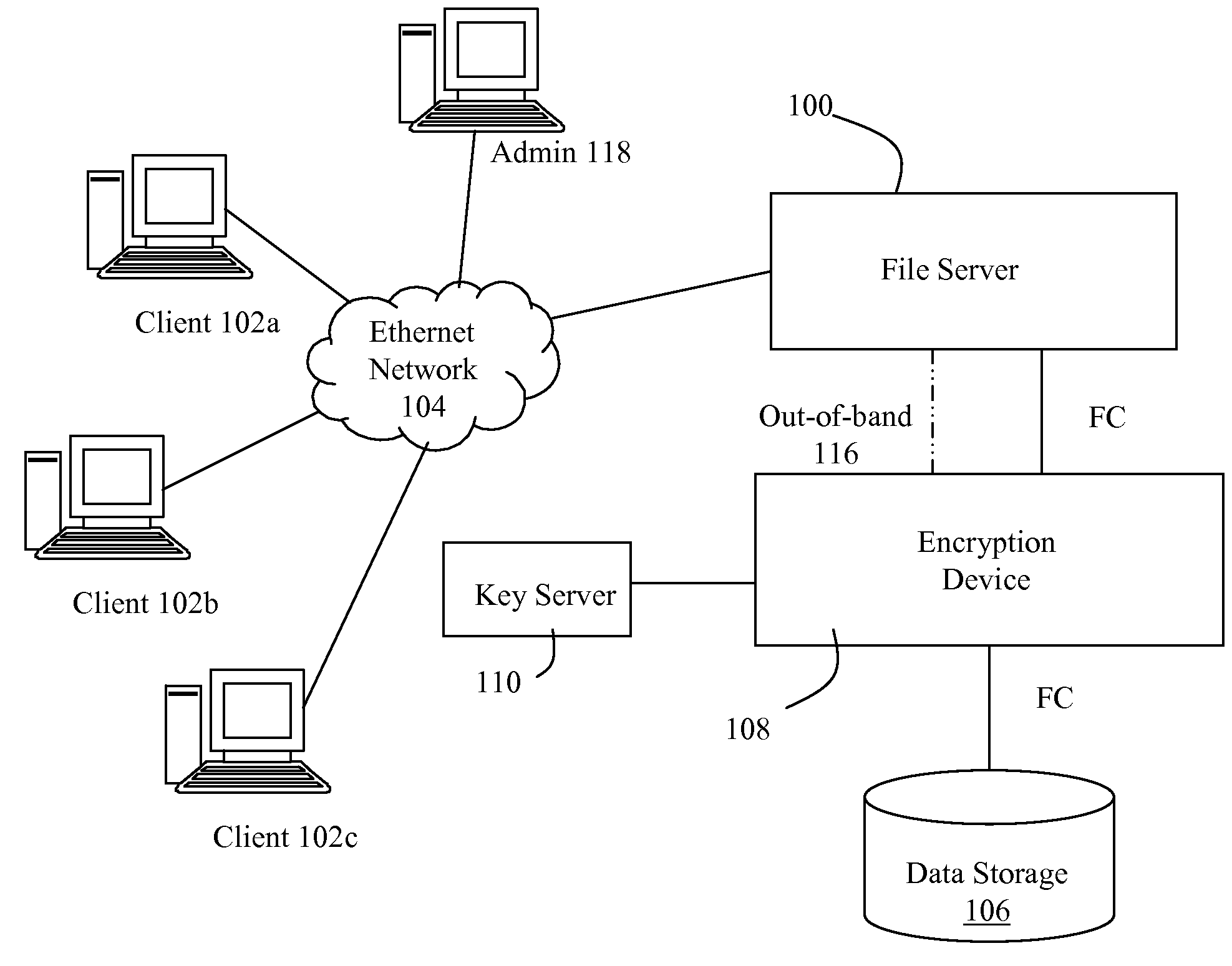
Identifying and enforcing strict file confidentiality in the presence of system and storage administrators in a nas system
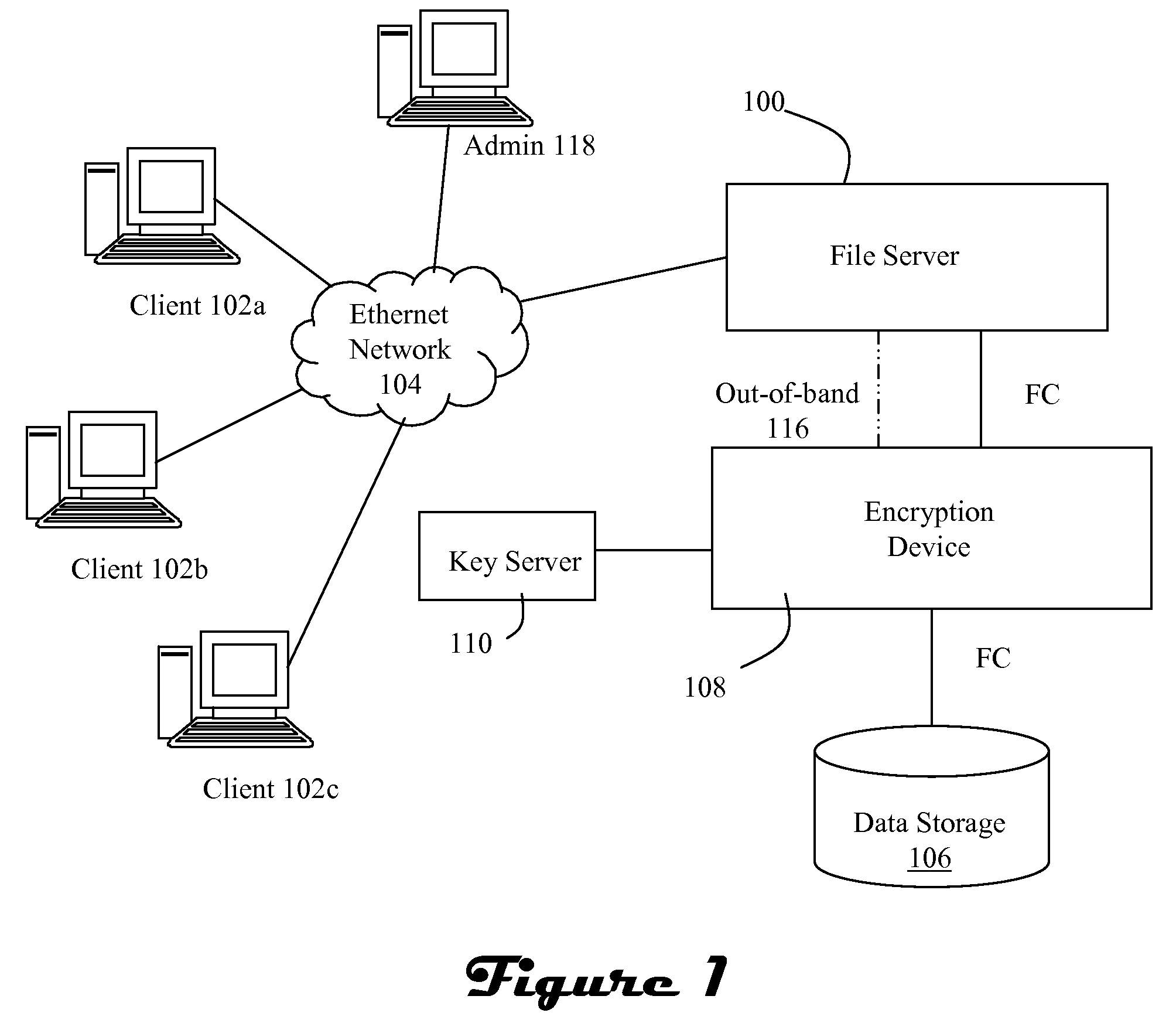
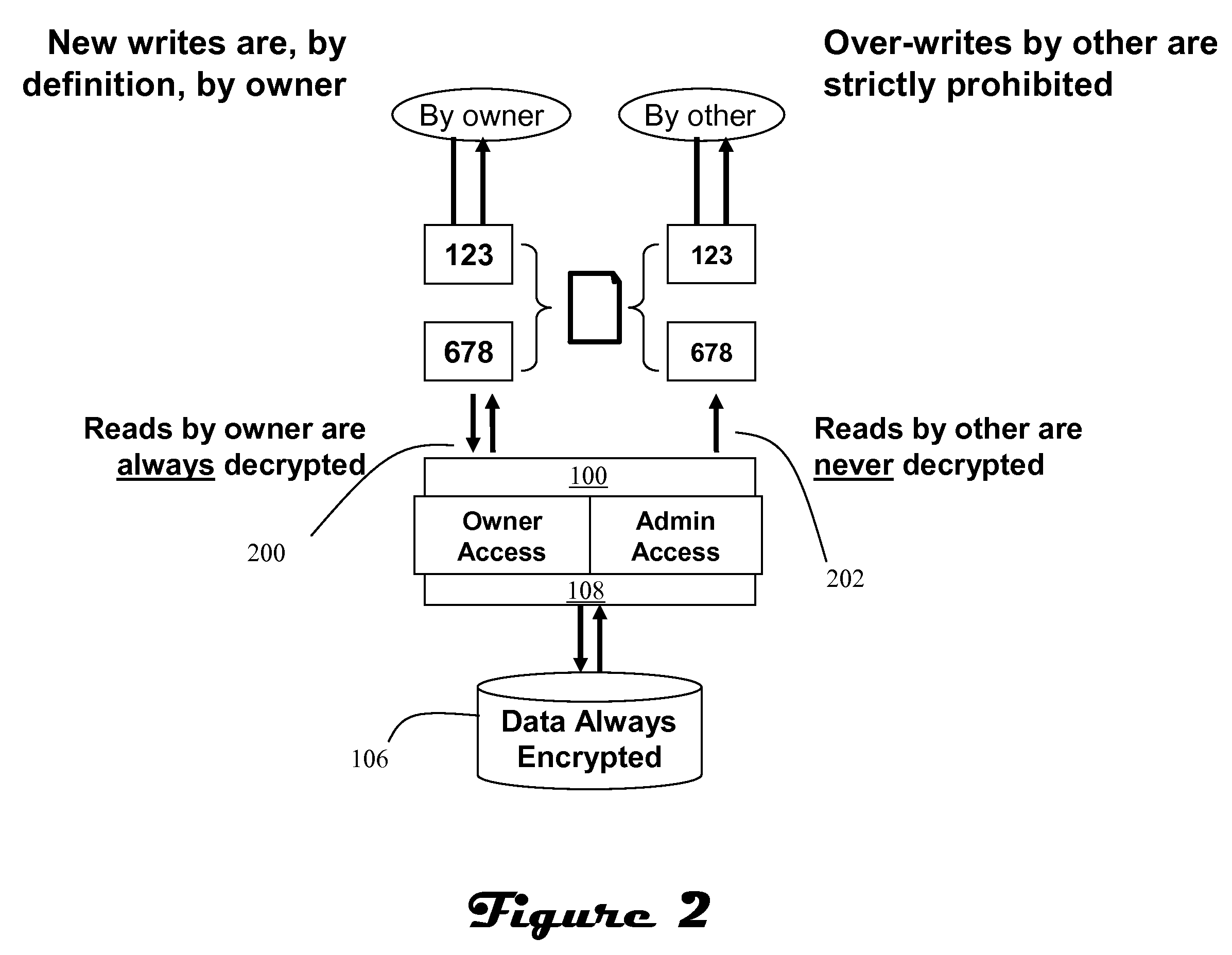
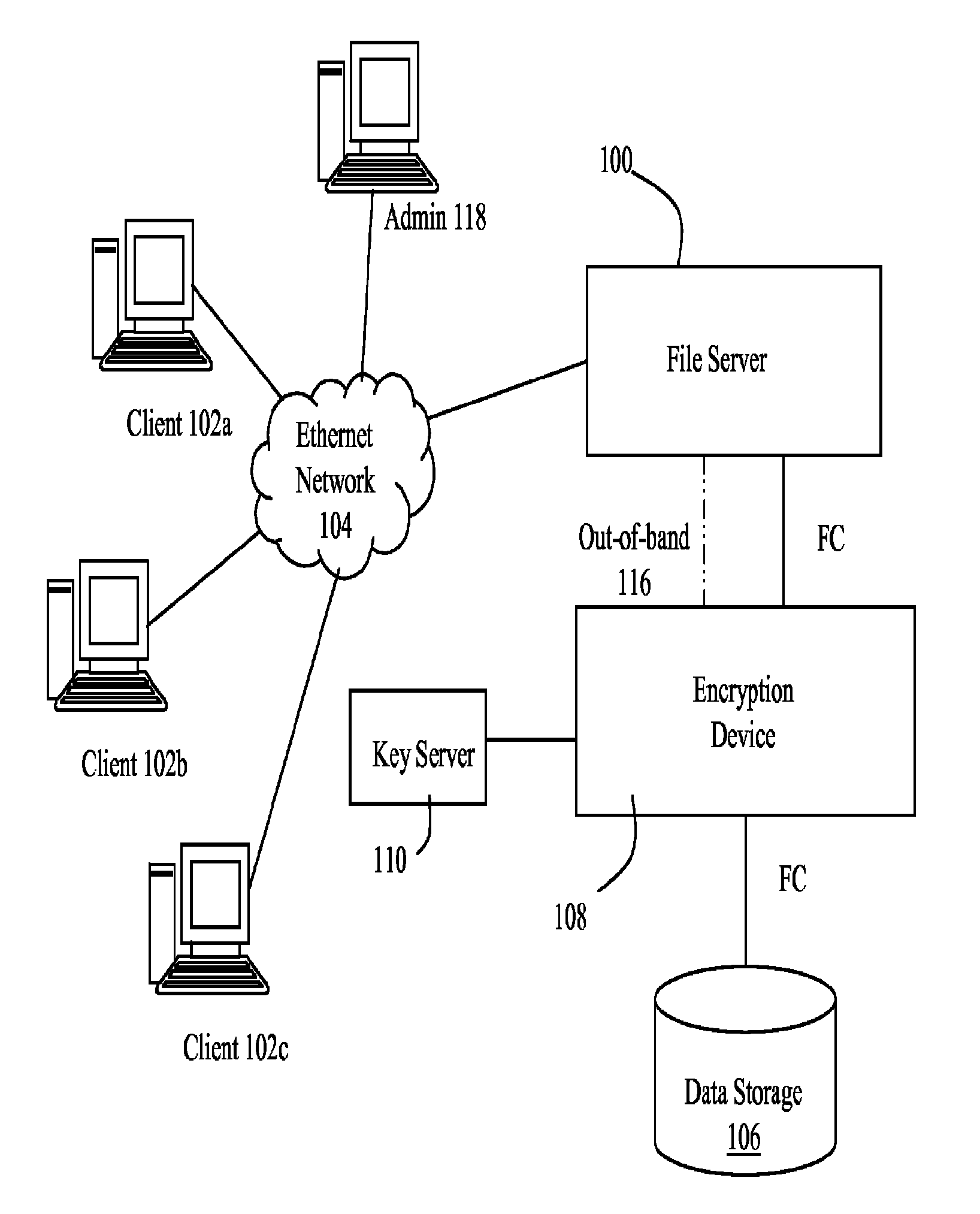
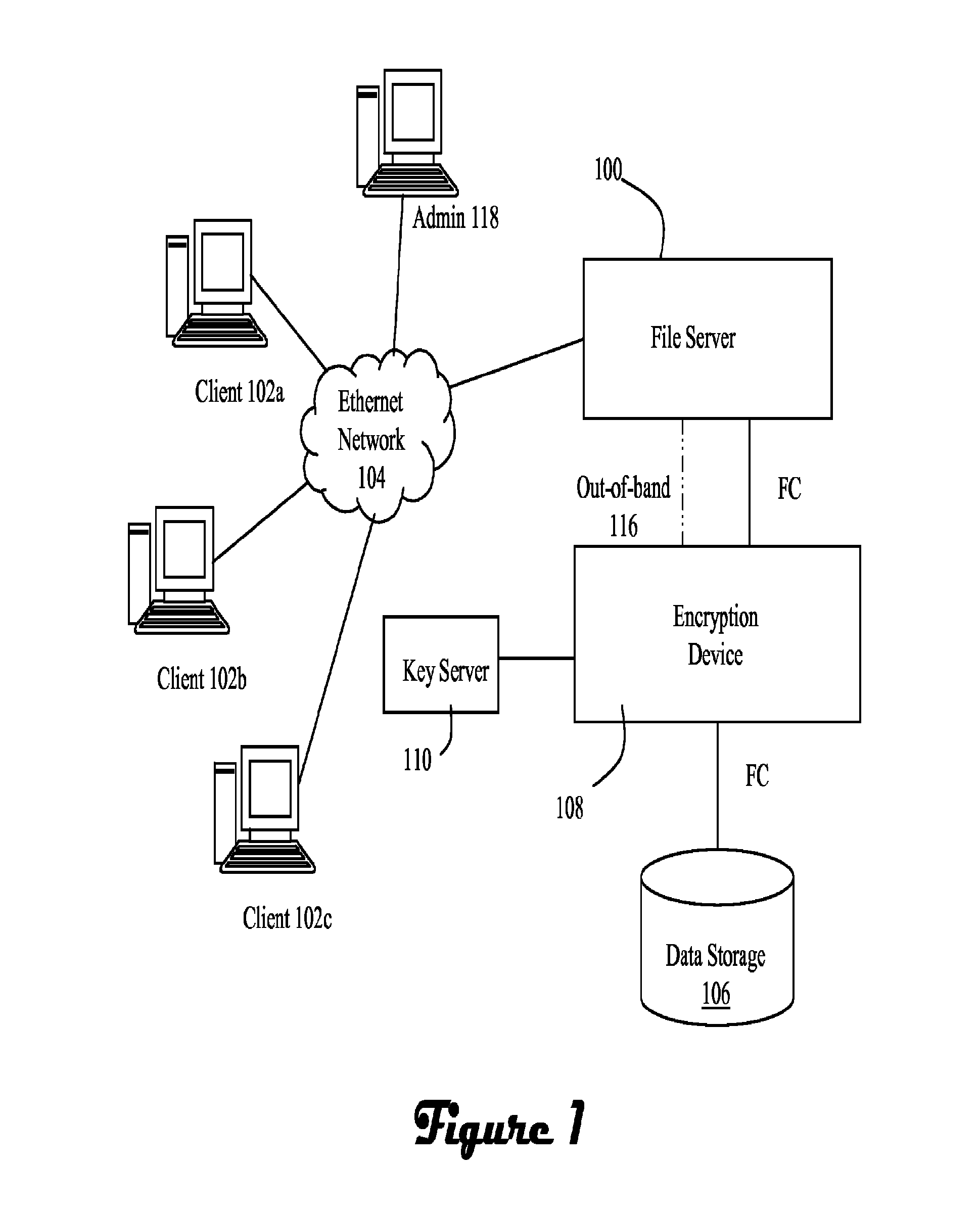
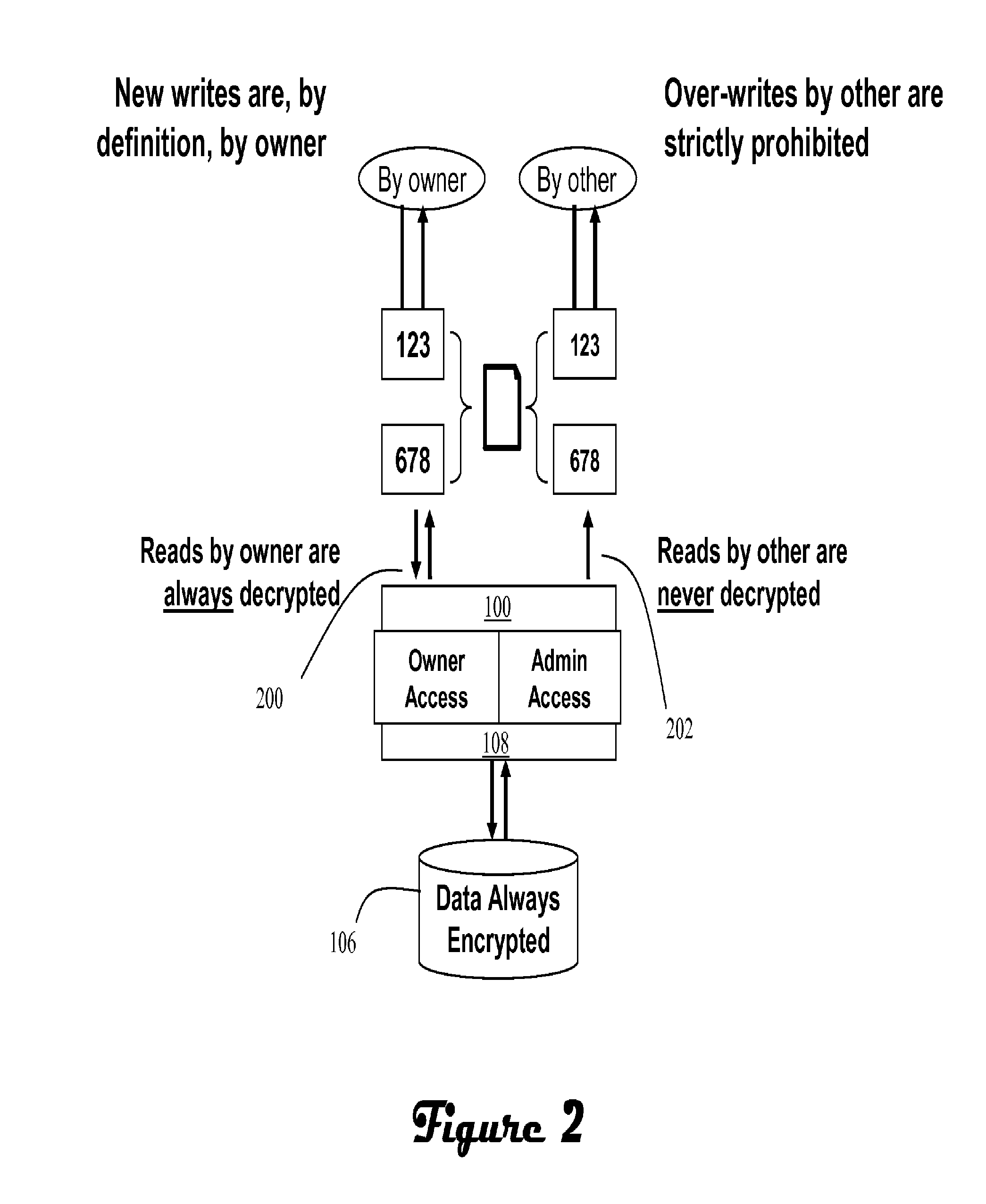
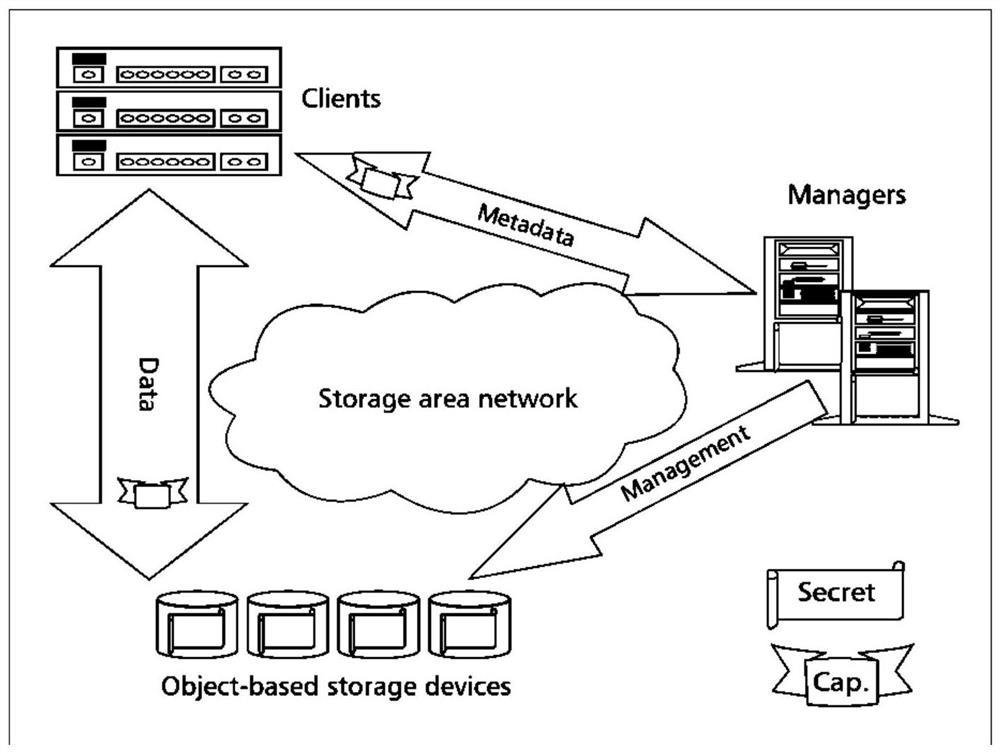
ActiveUS20070300062A1Improve data confidentialityDigital data processing detailsUser identity/authority verificationComputer hardwareConfidentiality
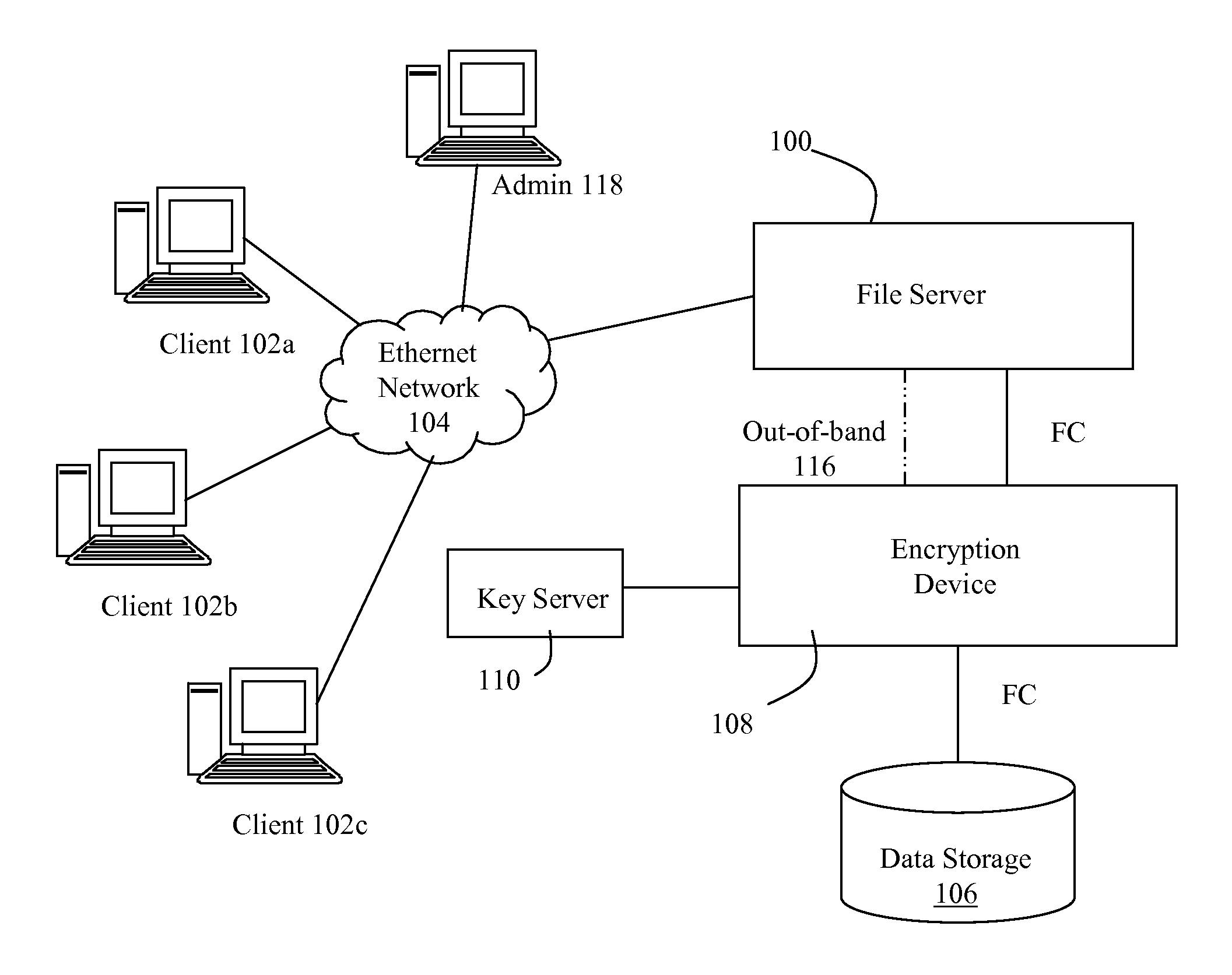
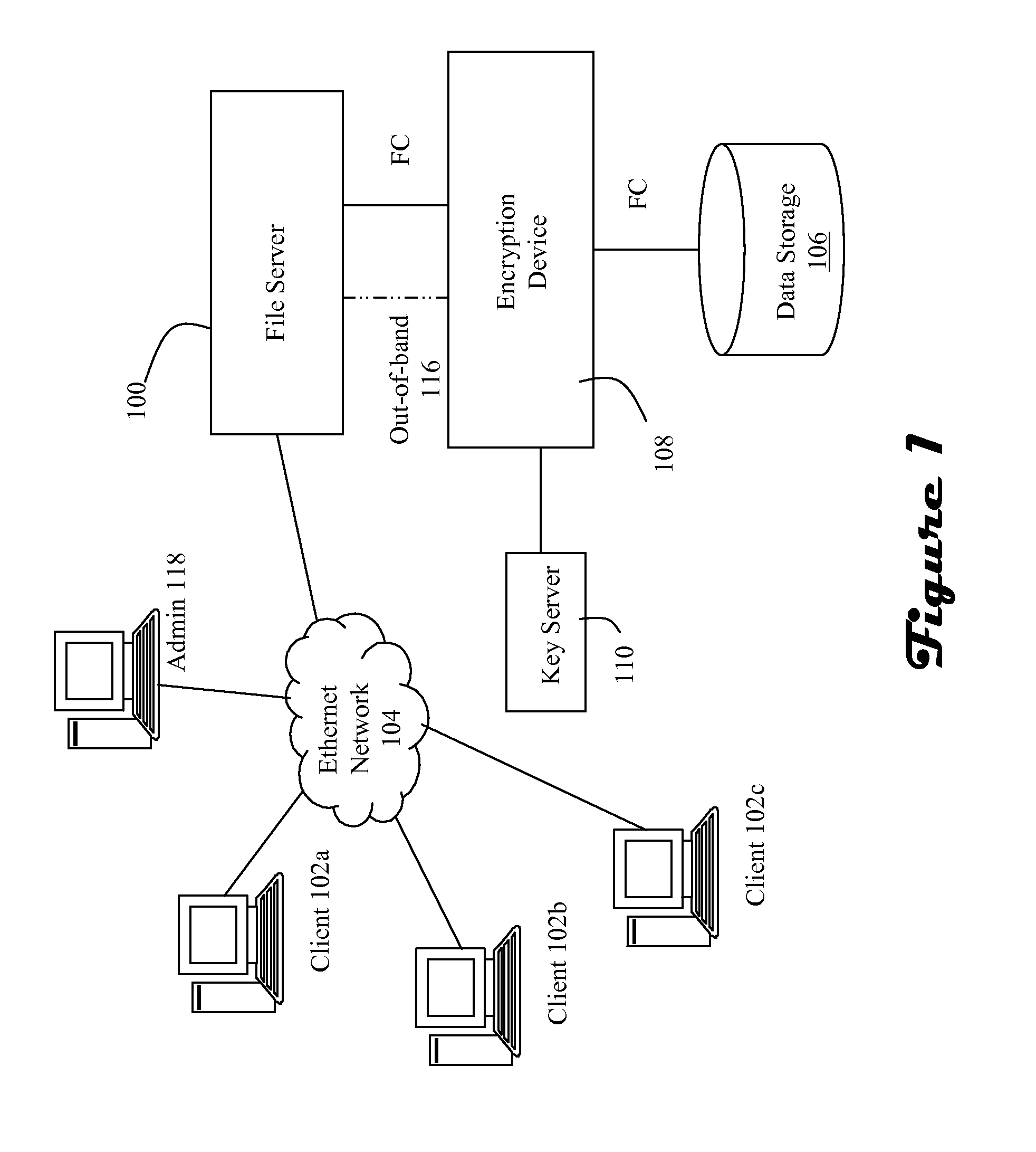
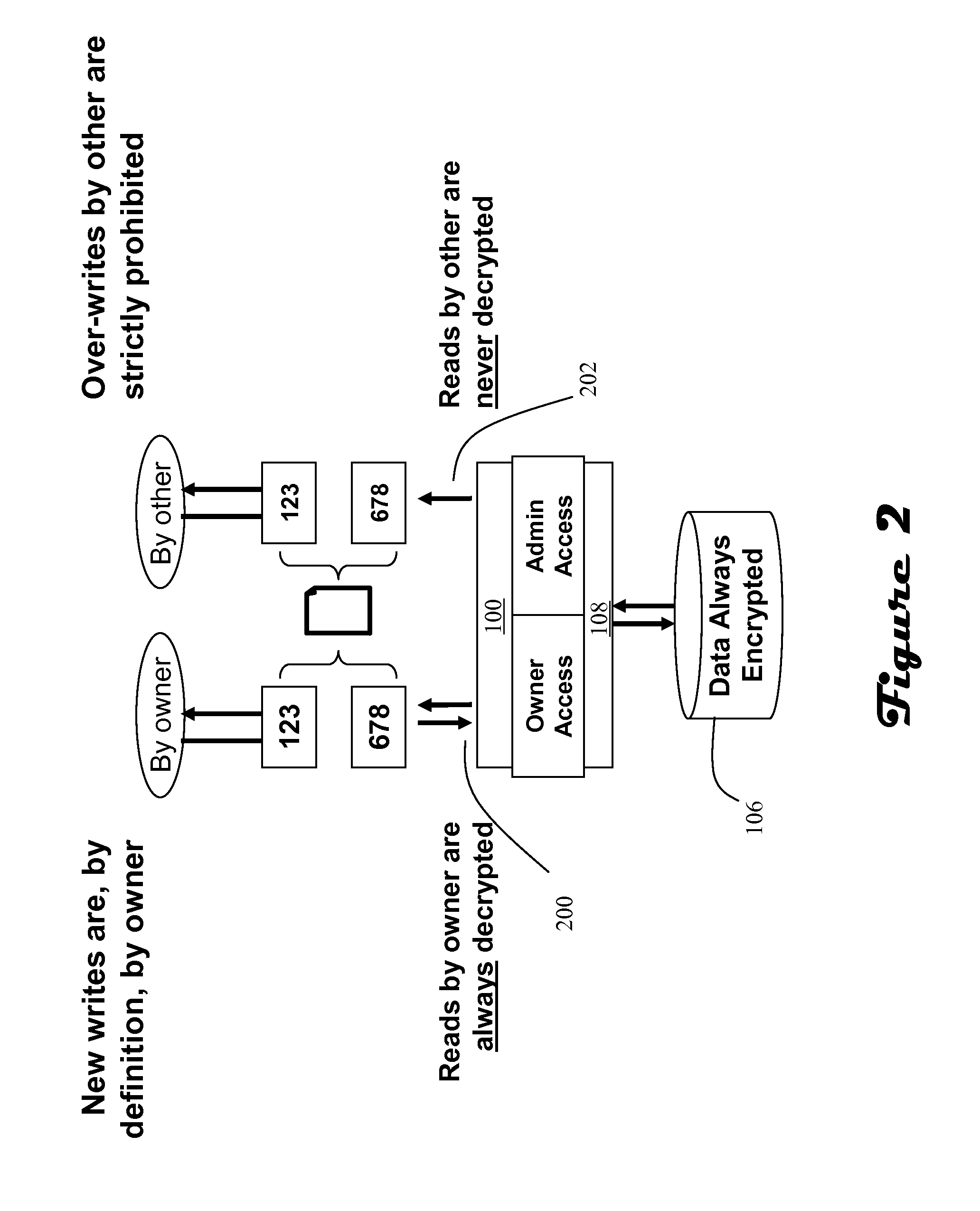
A data storage architecture for networked access by clients includes a file server capable of communication with the clients via the network, physical storage organized as a plurality of logical volumes, and an encryption device in communication with both the file server and the physical storage. The encryption device is operable in response to signaling from the file server to cause encryption of data being moved into the physical storage, and decryption of data being retrieved from storage. Two logical paths are provided for I / O operations. A first path is reserved for use by a first type of requestor, such as file owners. Data retrieved via the first path is decrypted by the encryption device, and Writes via the first path are allowed. A second path is employed for others than the owners, e.g., administrators. Data retrieved via the second path is not decrypted by the encryption device, and attempted Writes via the second first path are denied. Metadata may be delivered in-the-clear via both paths in response to a Read so that legitimate management tasks can be performed.
Owner:EMC IP HLDG CO LLC
Credit Data, Model Guarantee and Verification Method Based on Block Chain
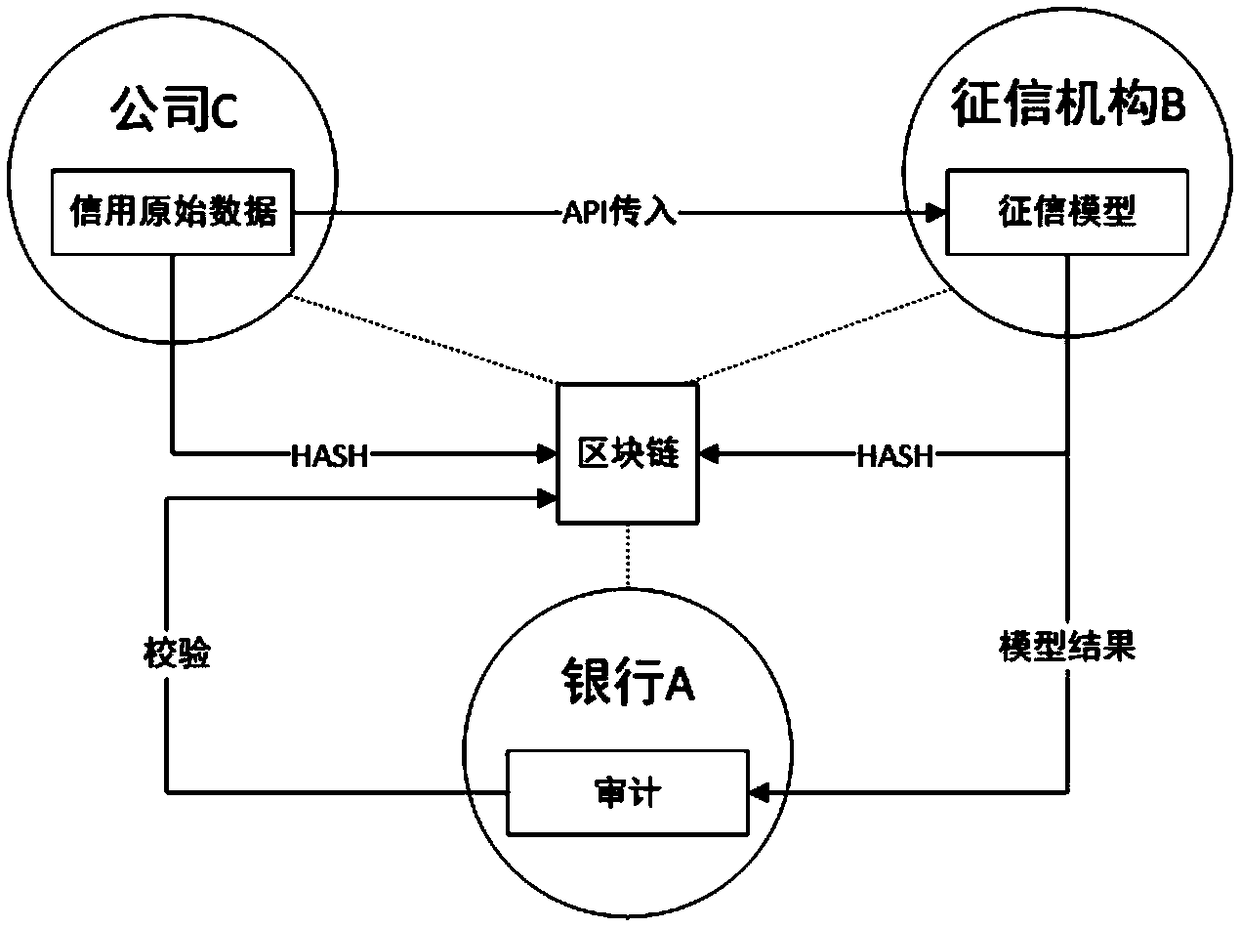
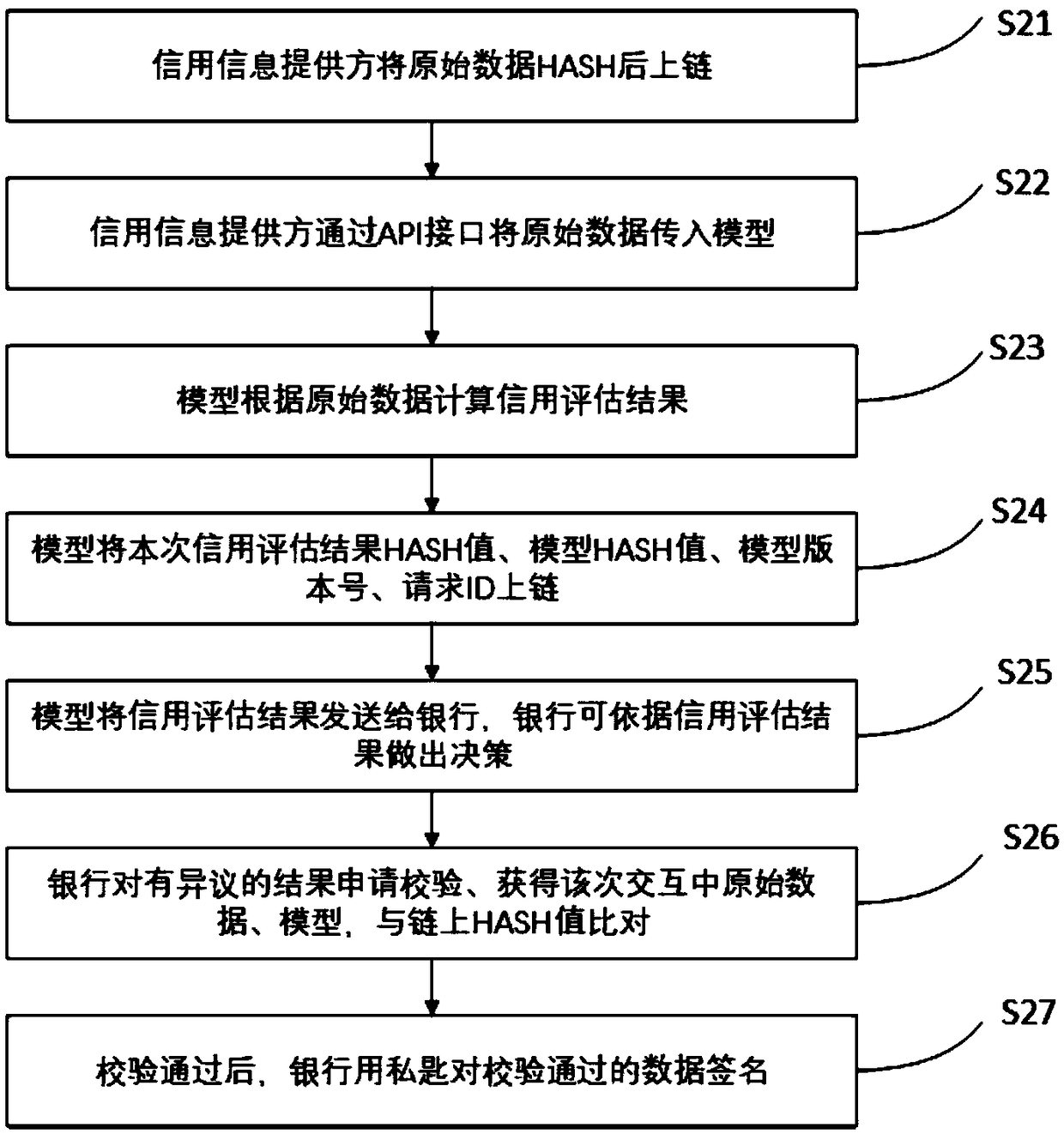
InactiveCN109118355AAvoid lostPrevent malicious tamperingFinanceDigital data protectionOriginal dataEvaluation data
The invention discloses a warranty and verification method of credit data and credit model based on block chain. The method comprises the following steps: (1) a provider of credit data links the HASHvalue of the original data; (2) the HASH value of the model, the HASH value of the model result data, the model version and the request ID are recorded on the link; (3) bank or other personal information users audit the data, that is, compare the data on the chain with the original data, audit and verify the evaluation data and model. The invention guarantees the safety, reliability, traceabilityand verifiability of the credit evaluation data, thereby effectively reducing the disputes caused by the information opacity in the credit investigation process, preventing the damage caused by malicious tampering of the credit investigation data, and meeting the actual use demand.
Owner:南京安链数据科技有限公司
Identifying and enforcing strict file confidentiality in the presence of system and storage administrators in a NAS system
ActiveUS8176319B2Improve data confidentialityDigital data processing detailsUnauthorized memory use protectionComputer hardwareConfidentiality
Owner:EMC IP HLDG CO LLC
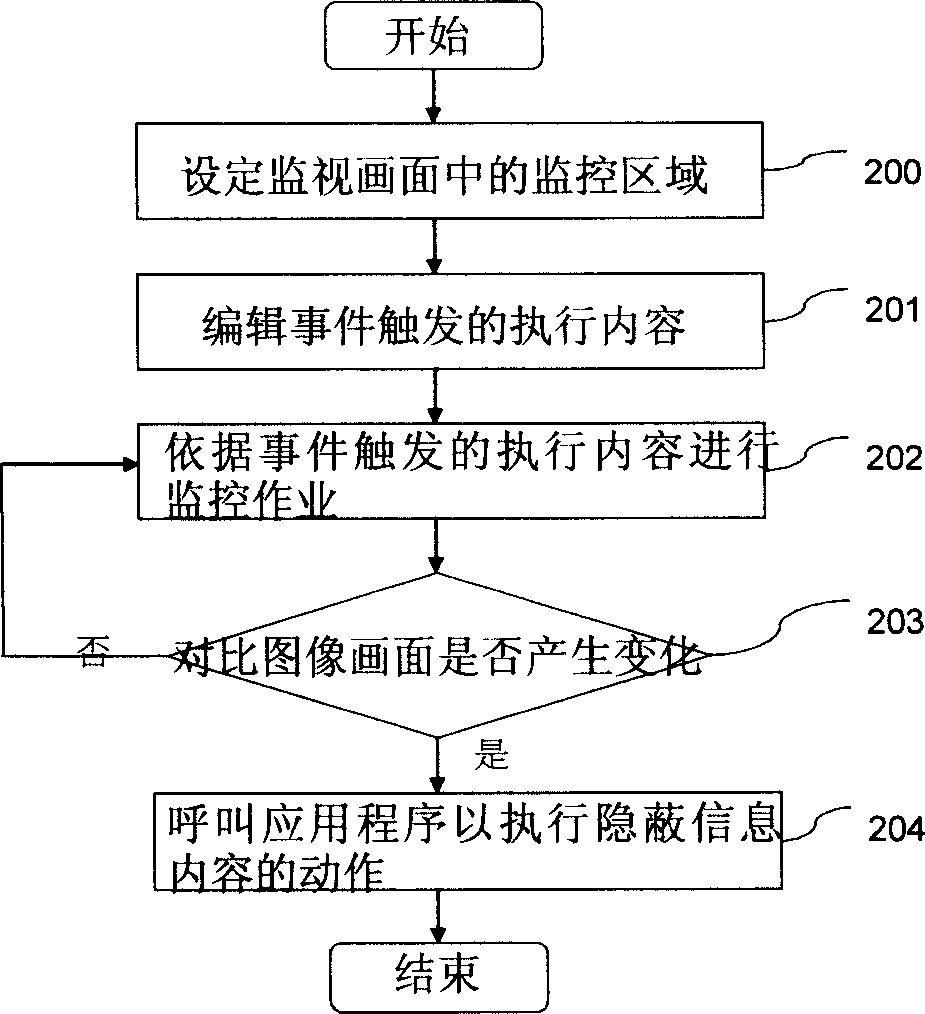
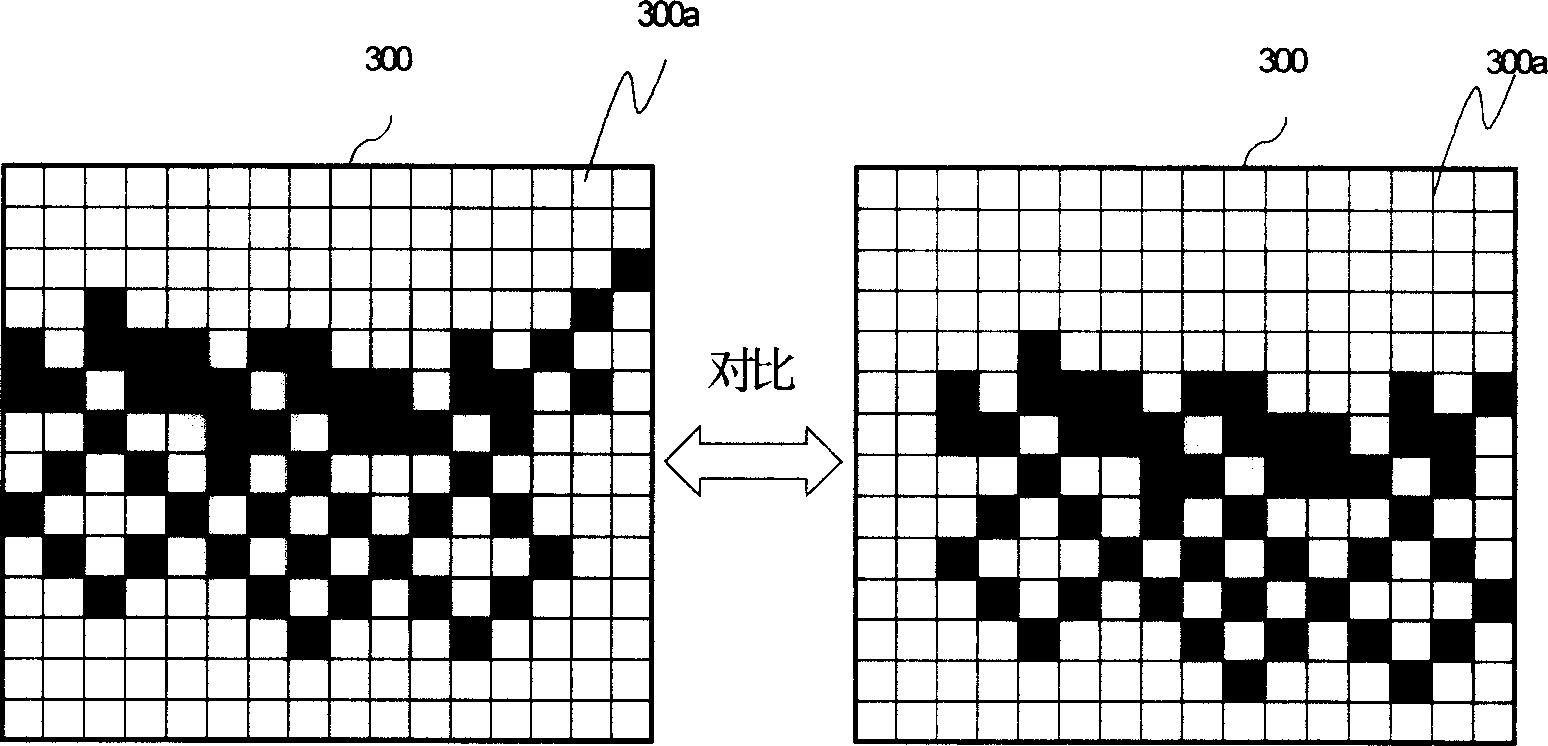
Image monitoring system and monitorng method and pattern operating interface thereof
ActiveCN1889682AImprove data confidentialityClosed circuit television systemsSpecific program execution arrangementsMonitoring systemApplication procedure
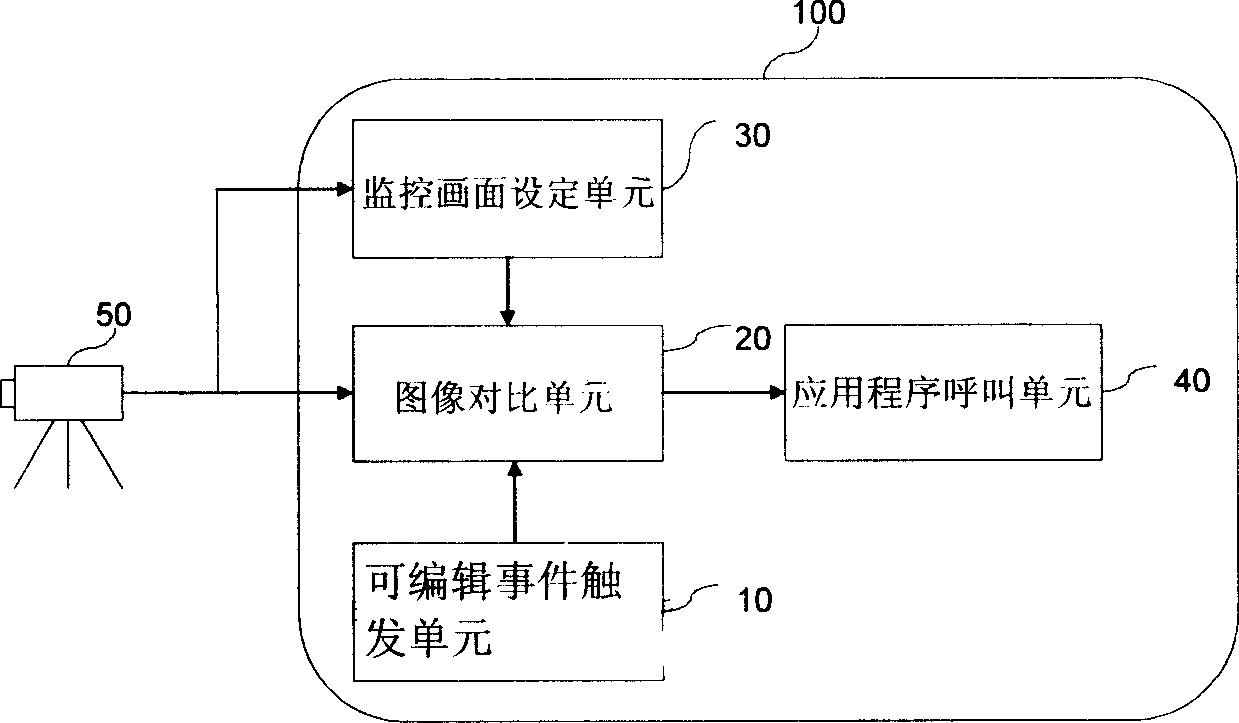
An image monitoring system comprises triggering unit of editable event for providing execution content of editing and starting up event trigger by user, image comparison unit for comparing variation of each image and for generating event triggering command corresponding to execution content of editing and starting up event trigger by user as well as application program calling unit for calling up application program corresponding to execution content according to event triggering command.
Owner:GIGA BYTE TECH CO LTD
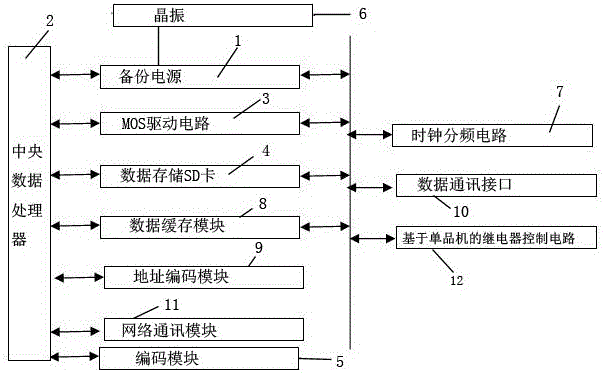
Automatic goods selling device control system and method based on blockchain foundation
InactiveCN106781008AEffective Encoding ProtectionImprove data confidentialityCoin-freed apparatus detailsTransmissionNetwork communicationElectrical bonding
The invention relates to an automatic goods selling device control system and method based on a blockchain foundation. The automatic goods selling device control system comprises a backup power, a central data processor, an MOS driving circuit, a data storage SD card, a coding module, a crystal oscillator, a clock frequency dividing circuit, a data caching module, an address coding module, a data communication interface, a network communication module and a relay control circuit based on a single chip microcomputer, wherein the central processing unit is electrically connected with the backup power, the MOS driving circuit, the data storage SD card, the data caching module, the address coding module and the network communication module; the MOS driving circuit is connected with the backup power, the data storage SD card, the clock frequency dividing circuit, the data caching module, the data communication interface and the relay control circuit based on the single chip microcomputer. On one hand, the requirements that product sales and sales information monitoring feedback work are remotely carried out through a network can be effectively met, and on the other hand, data security and safety in a data communication process is improved.
Owner:CHENGDU YUYA TECH
Method for the transmission of information with improved perenniality
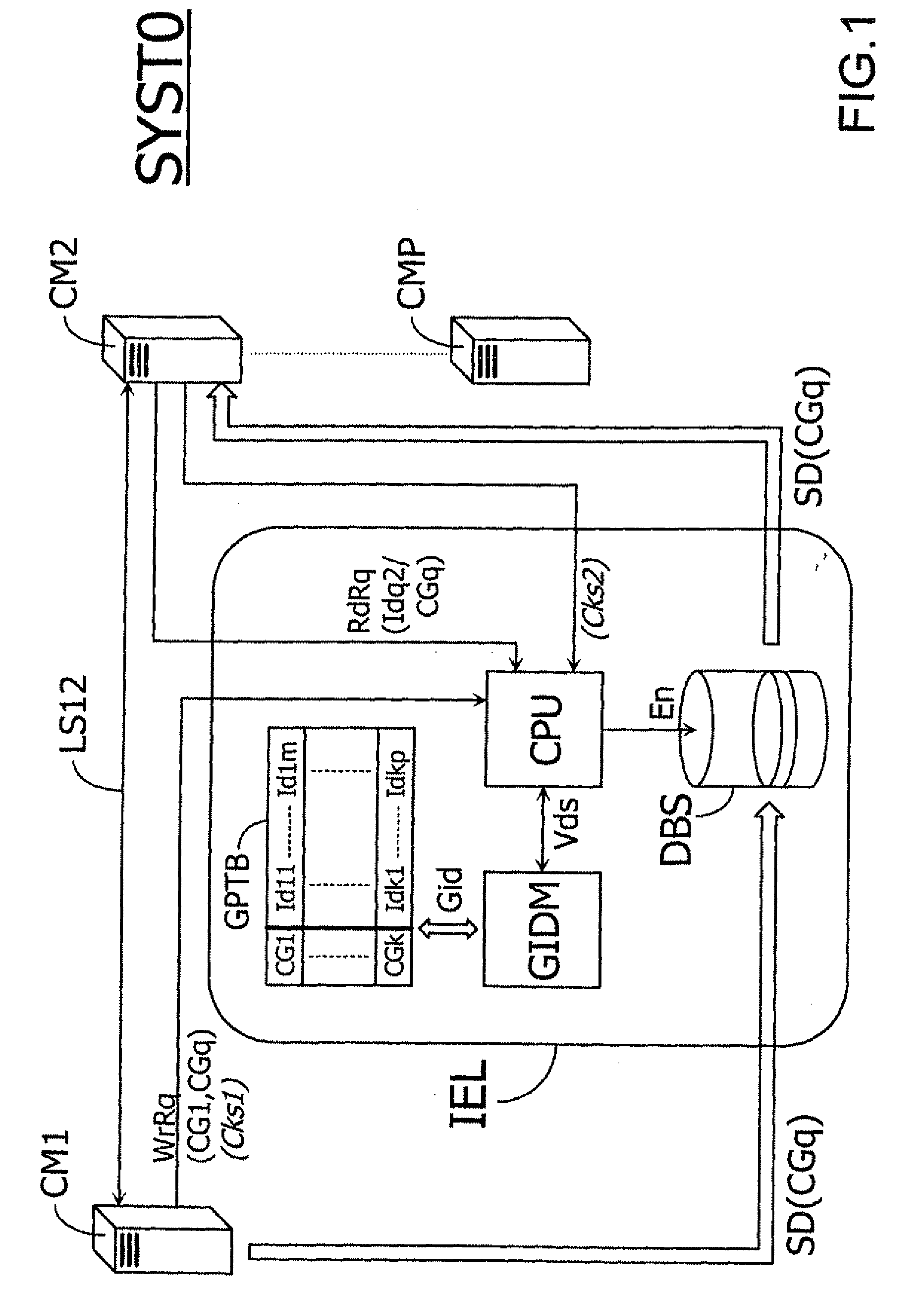
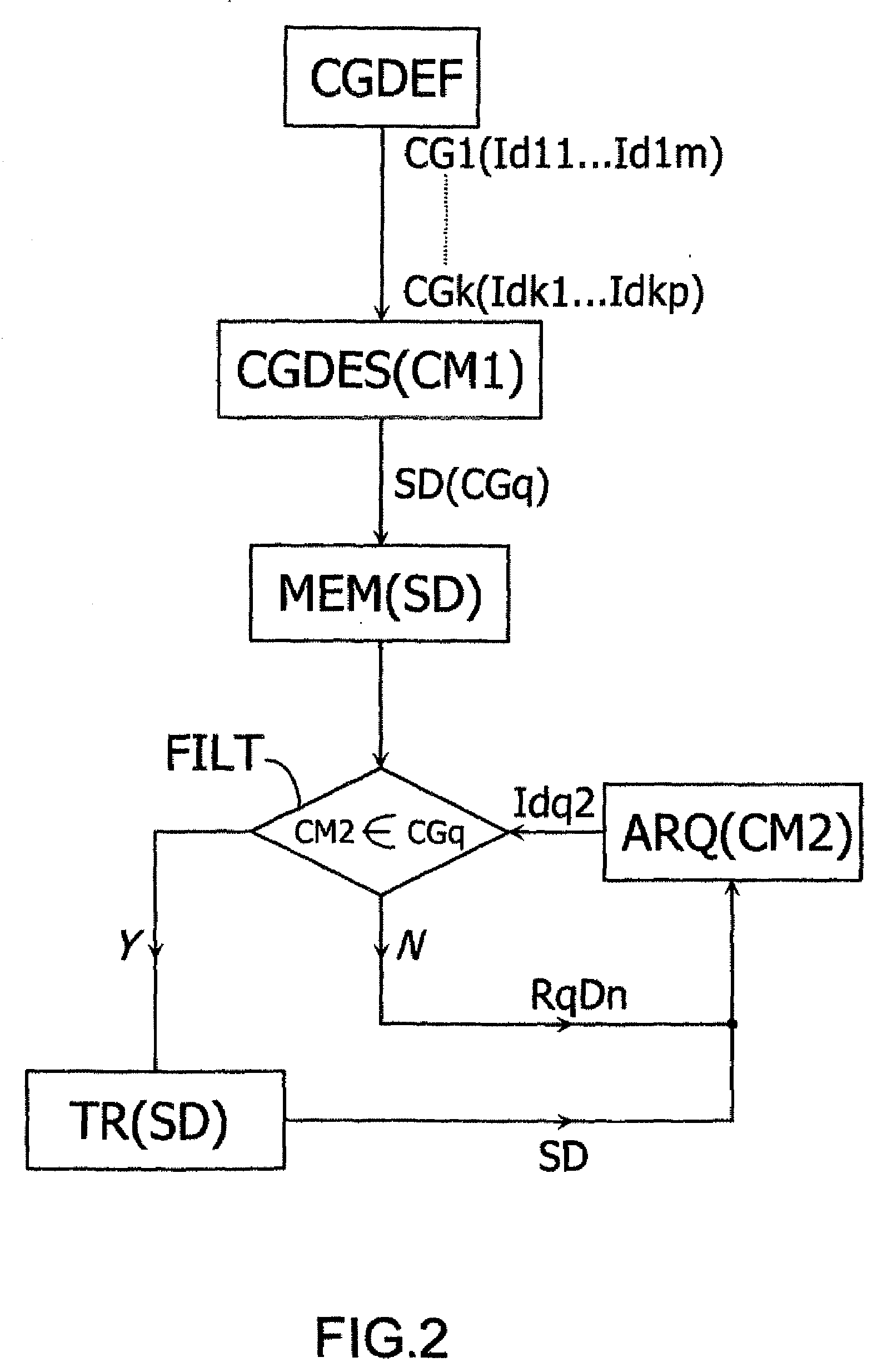
InactiveUS20090216890A1Multiple countImprove securityDigital data processing detailsMultiple digital computer combinationsClient-sideTelecommunications equipment
A method is provided for the transmissions of information between at least a first and a second communication means. The method includes in saving at least one set of information in an intermediate element. The method also includes defining a plurality of client groups, using an identifier in order to designate at least one group of clients that are authorized to access the information set, and at least one filtering step, which is intended to prevent a user that does not belong to the group from accessing the information. The method enables the integrity of the contained in the intermediate element to be substantially secured, by selecting clients that are authorized to access the information.
Owner:FRANCE TELECOM SA
Identifying and enforcing strict file confidentiality in the presence of system and storage administrators in a NAS system
ActiveUS8769271B1Improve data confidentialityDigital data processing detailsAnalogue secracy/subscription systemsConfidentialityClient-side
Owner:EMC IP HLDG CO LLC
Triple and quadruple churning security for 1G and 10G PON
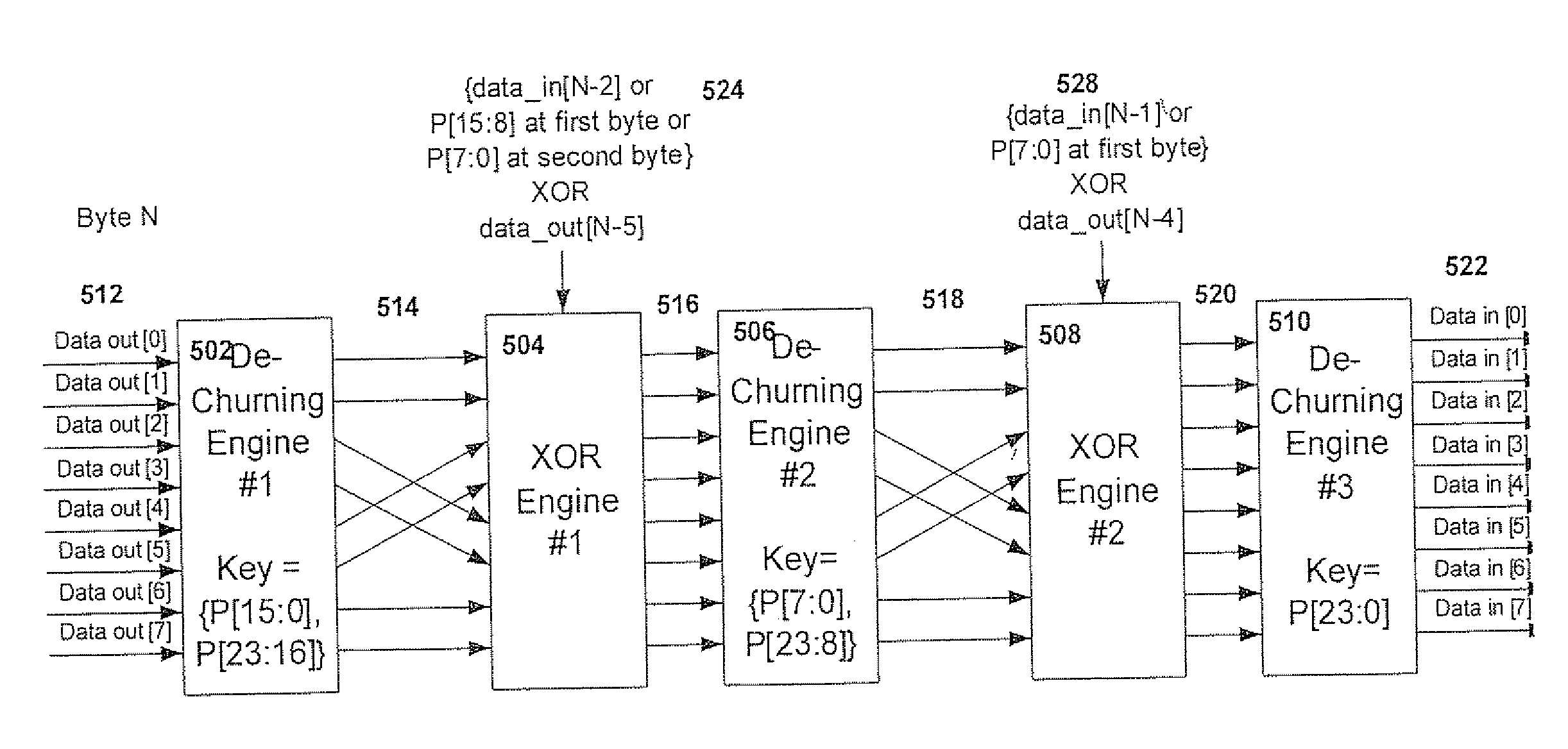
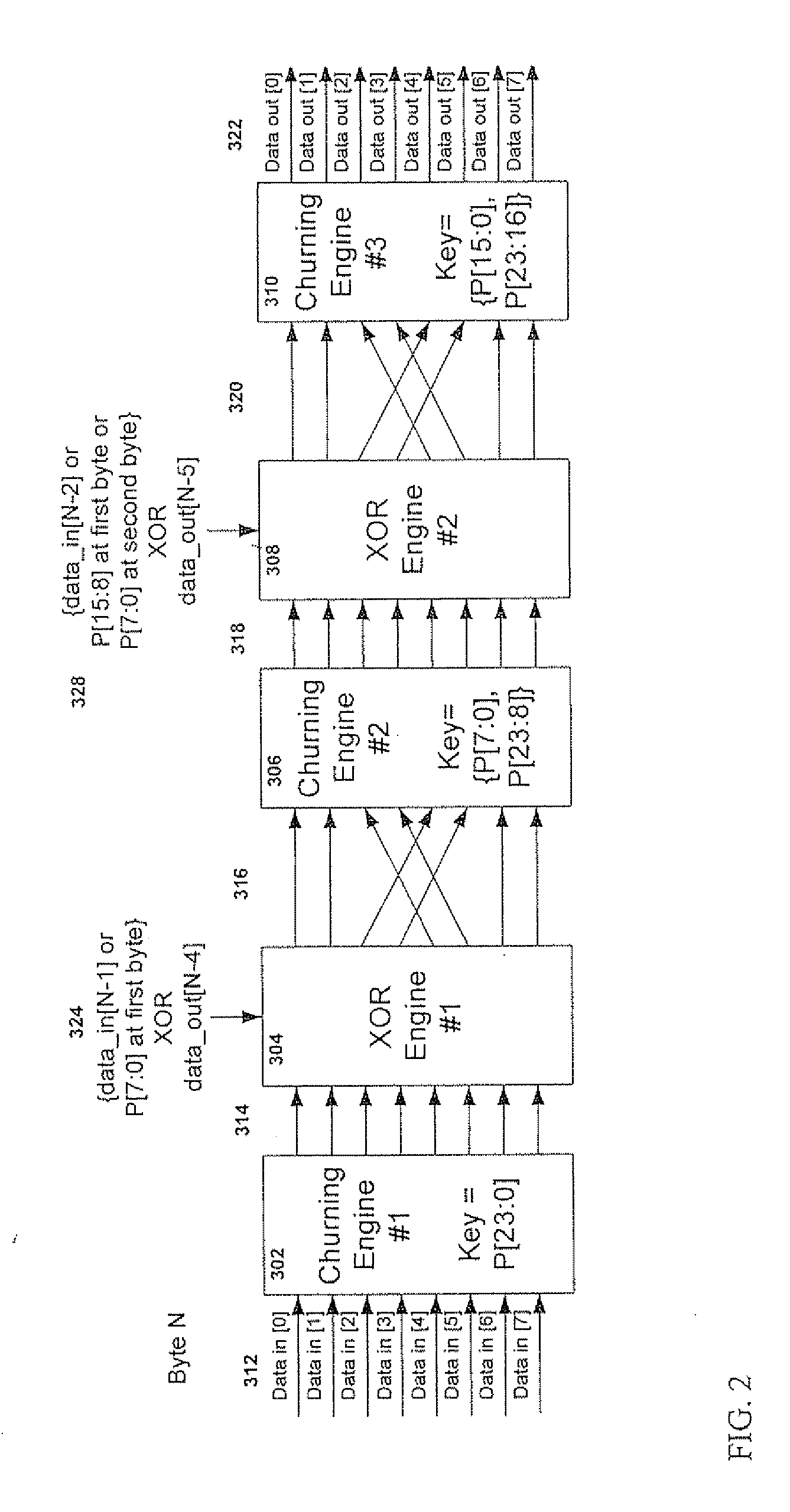
InactiveUS20100106959A1Improve confidentialityImprove data confidentialityData stream serial/continuous modificationTime-division multiplexConfidentialityEncryption decryption
A data encryption-decryption method for enhancing the confidentiality of data transmitted between two, first and second communication network entities including the steps of: at the first network entity, performing a quadruple-churning operation on a byte N to obtain an encrypted byte N, the quadruple-churning operation including: performing a first churning operation to obtain a first churned output; bit-wise XORing the first churned output with two values to obtain a first XOR result; bit-swapping the first XOR result; performing a second churning and XORing stages to obtain a second XOR result; performing a third churning and XORing stages to obtain a third XOR result; bit swapping the third XOR result; and performing a fourth churning operation on the third bit-swapped XOR result to obtain encrypted byte N; and transmitting the encrypted byte N to the second network entity.
Owner:PMC-SIERRA
Multi-area interconnected microgrid system decentralized coordination scheduling method and device
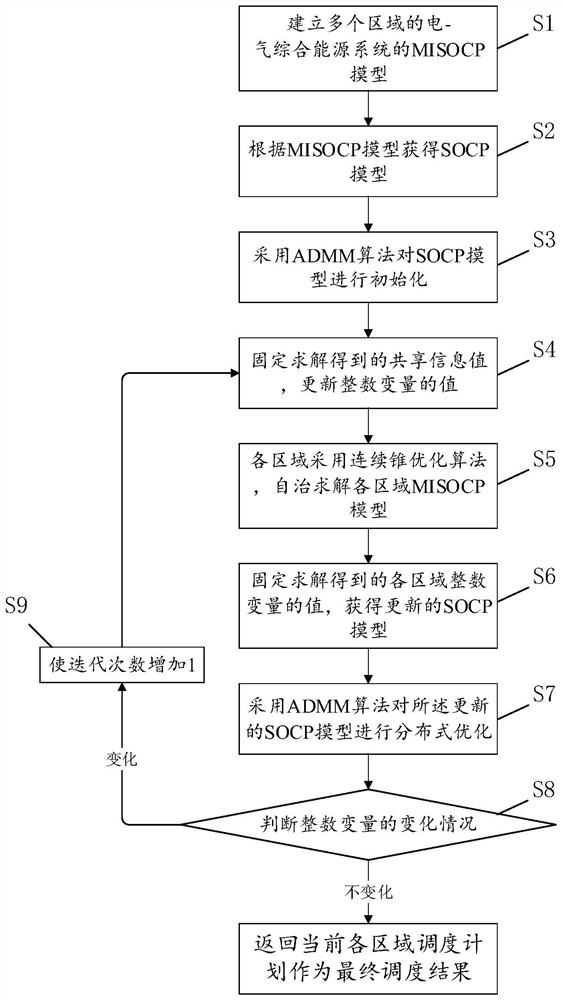
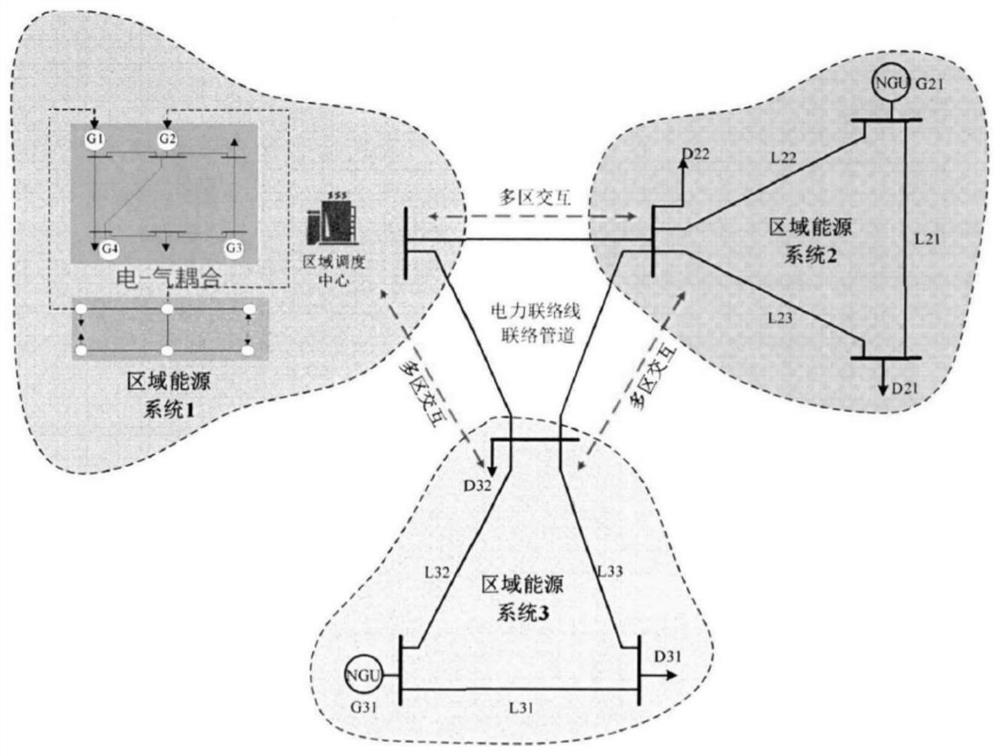
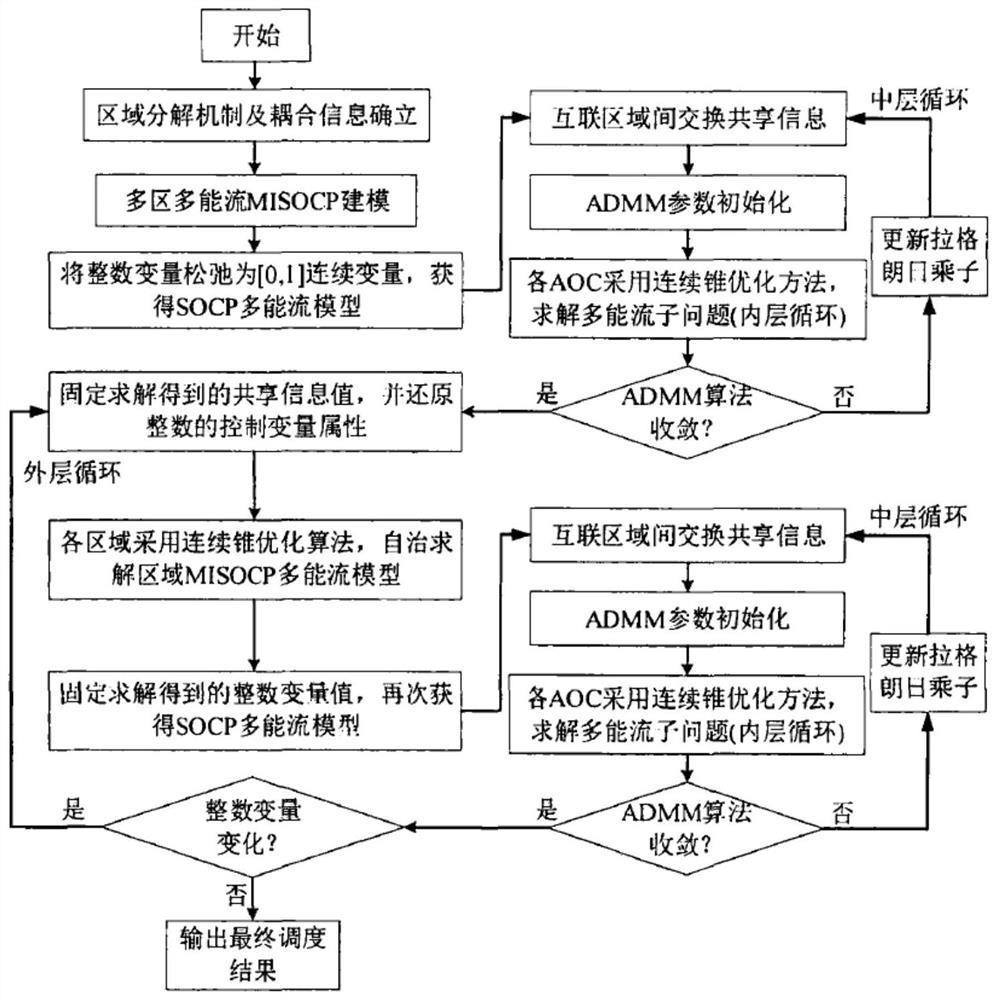
PendingCN112288283ALess exchangeImprove data confidentialityResourcesComplex mathematical operationsMicrogridIntegrated energy system
The invention provides a multi-area interconnected microgrid system decentralized coordination scheduling method and device. The scheduling method comprises the following steps: S1, establishing MISOCP models of electro-pneumatic integrated energy systems of multiple areas; S2, obtaining an SOCP model according to the MISOCP model; s3, adopting an ADMM algorithm to initialize the SOCP model; s4, fixing the solved shared information value, and updating the value of the integer variable; s5, adopting a continuous cone optimization algorithm for each area, and autonomously solving an MISOCP modelof each area; S6, fixing the solved value of the integer variable of each area to obtain an updated SOCP model; s7, adopting an ADMM algorithm to carry out distributed optimization on the updated SOCP model; s8, judging the change condition of the integer variable, and if the integer variable does not change any more, returning the current area scheduling plan as a final scheduling result, otherwise, executing the step S9; and S9, increasing the number of iterations by 1, and repeatedly executing the steps S4-S8. According to the scheduling method disclosed by the invention, the information exchange amount between the areas can be reduced, and the convergence efficiency in the solving process is improved.
Owner:XIAMEN ELECTRIC POWER SUPPLY COMPANY OF STATE GRID FUJIAN ELECTRIC POWER
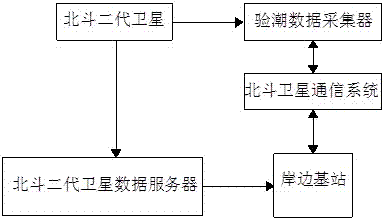
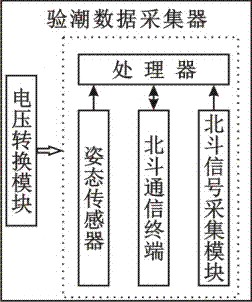
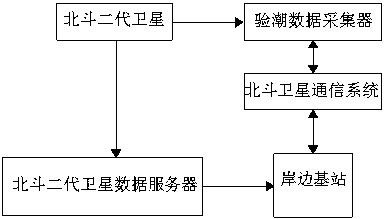
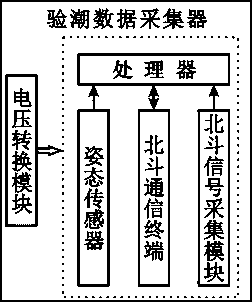
Whole-sea tidal observation system and tidal observation method based on Beidou
ActiveCN106908044AHigh precisionExpand the scope of workMeasuring open water movementSatellite radio beaconingNatural satelliteLongitude
The invention discloses a whole-sea tidal observation system based on Beidou. The whole-sea tidal observation system comprises a Beidou second-generation satellite navigation and positioning system, a Beidou satellite communication system, a shoreside base station, and a tidal observation data acquisition device positioned on a carrier in ocean; meanwhile, the invention discloses a tidal observation method for the tidal observation system; the tidal observation method comprises the following steps: determining a tide model of a sea area where the shoreside base station is located by the shoreside base station according to latitude and longitude coordinates of the tidal observation data acquisition device, determining a main tidal component type of the sea area where the shoreside base station is located, and carrying out trigonometric polynomial fitting on daylong tidal level data according to the period of the tidal component type to obtain a high-precision daily tide level curve. The whole-sea tidal observation system disclosed by the invention can be applied to any one sea area which can receive an electromagnetic wave signal of a Beidou second-generation satellite; the defect that a conventional tidal observation means only can be operated near shore is overcome, and the working range of marine tide measurement is widened; in addition, the Beidou satellite communication system is adopted for carrying out data transmission, so high data security is realized.
Owner:THE FIRST INST OF OCEANOGRAPHY SOA +1
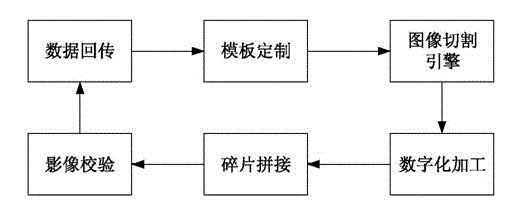
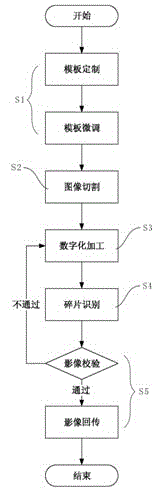
Image processing system and method based on fragmentation technique
InactiveCN104639950AReduce consumptionImprove data confidentialitySelective content distributionImage compressionData security
The invention discloses an image processing system and an image processing method based on fragmentation technique, which belongs to an image compression processing method. The system comprises a template customization module, an image cutting engine and a digital processing site, wherein the template customization module is used for inputting an image template and recording the size of the current image template by using a coordinate counting method; the image cutting engine is used for cutting an image picture which is uploaded to the system according to the image template and distributing cut fragments to each remote digital processing site at random; the digital processing site is used for digitizing the fragments of the image picture and transmitting the digitized fragments to a fragment splicing module and the like. An image picture file is fragmented by the fragmentation engine and then is distributed to each site so as to perform image digitalization processing, so that data security in a remote image processing field is effectively increased, and additionally, network resource consumption due to image transmission in a remote machining process is reduced.
Owner:BEIJING QUANTUM WEIYE INFORMATION TECH
Information dispersion method and system based on distributed object storage system security
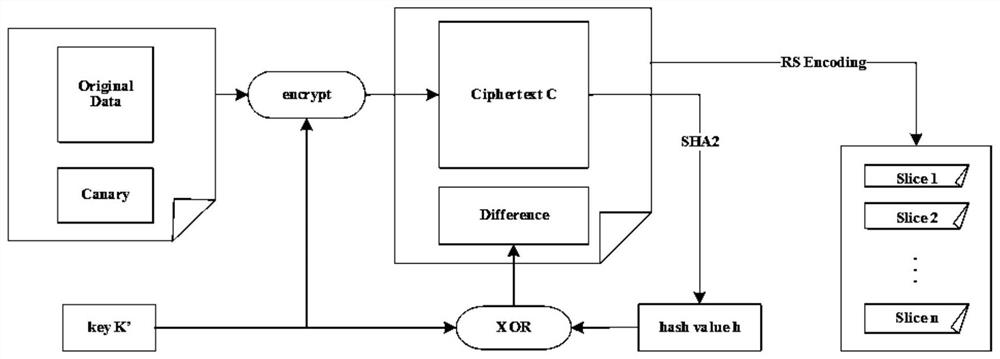
InactiveCN112486412AImprove data confidentialityIncrease the lengthInput/output to record carriersRedundant data error correctionHash functionAlgorithm
The invention is applicable to the field of data information distribution technology improvement, and provides an information dispersion method based on distributed object storage system security, which comprises the following steps: S1, calculating a data block hash value in a salting manner to resist collision attack of a hash function and improve the confidentiality of data; S2, improving the calculation efficiency by using an SHA2512 hash algorithm, and replacing the random key with the hash value of the original data; S3, inputting the data with the same content, and encoding the data through an AONTNZZD algorithm to generate data blocks with the same content so as to realize data deduplication. According to the AONTNZZD algorithm, the length of a data block is additionally selected as a salt value of hash operation when the hash value of the data block is calculated, and therefore an attacker can be prevented from carrying out hash function attack. According to the AONTNZZD algorithm, an NZZD code based on binary shift and exclusive-OR operation is adopted, and the relatively good encoding and decoding rate is achieved.
Owner:FOSHAN SAISICHAN TECH CO LTD +1
System and a method for management of confidential data
ActiveUS10354084B2Improve data confidentialityImprove confidentialityKey distribution for secure communicationDigital data protectionEncryptionSingle point
A system and a method for managing confidential data in a cloud service is provided. The system comprises a cryptographic key service comprising two or more cryptographic key servers, Si, each being arranged to compute file encryption keys, kj, on the basis of information regarding data and using one or more cryptographic keys, Kj. The cryptographic keys, Kj, are secretly shared among the cryptographic key servers, Si, and none of the cryptographic key servers, Si, possesses knowledge of all of the cryptographic keys, Kj. A single point of trust at the cryptographic key service is avoided.
Owner:KMAAS APS +1
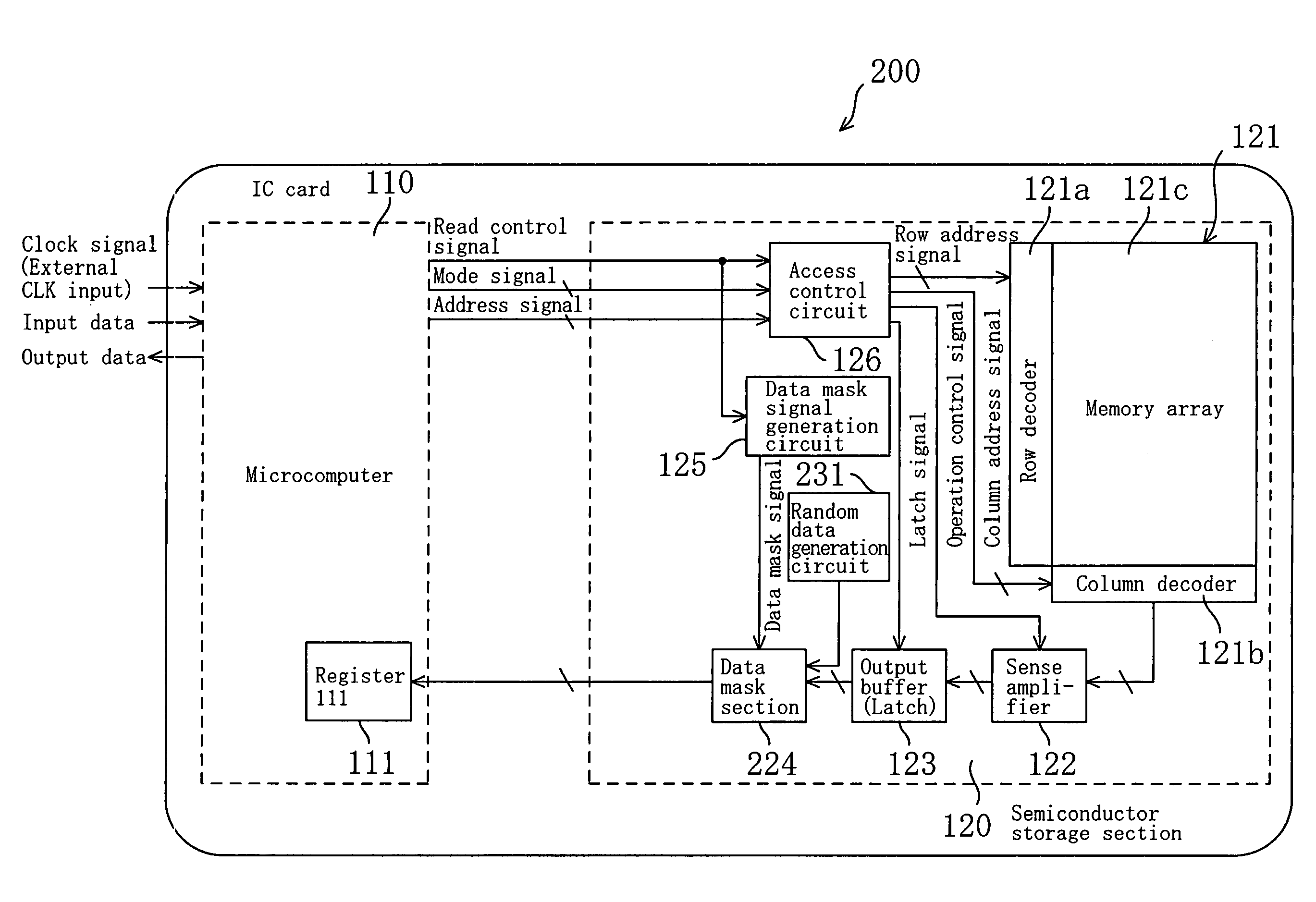
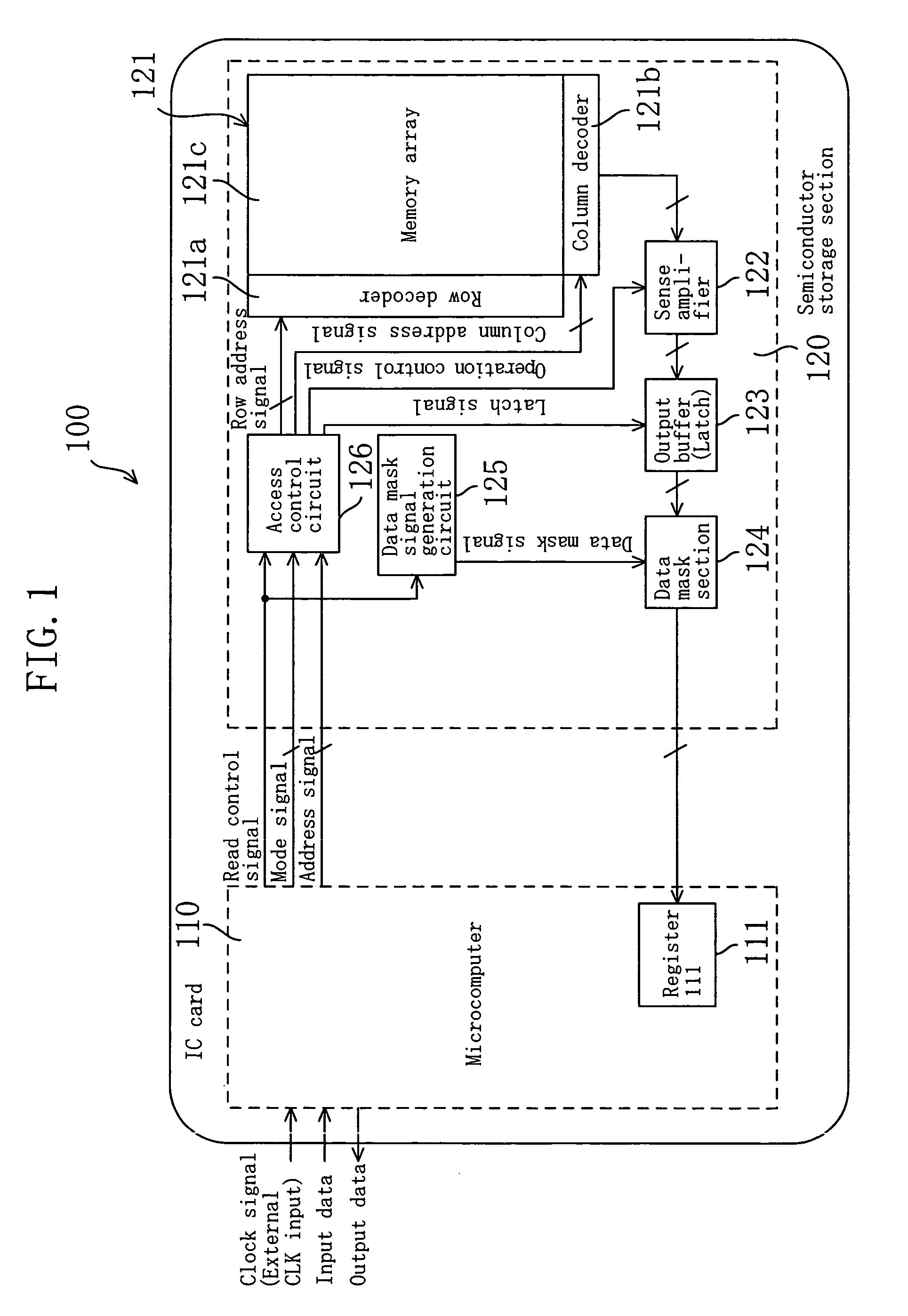
Storage device
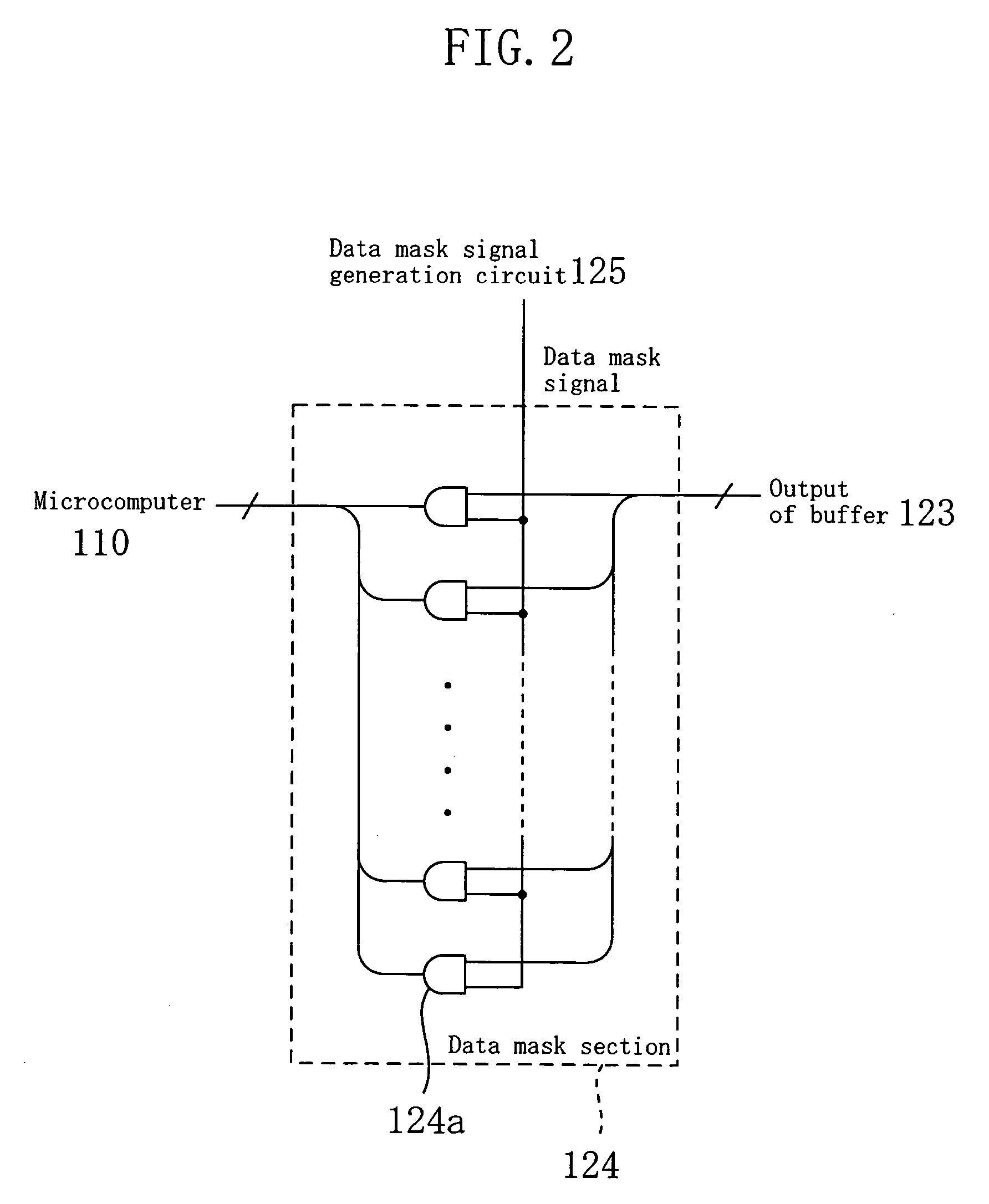
InactiveUS7171533B2Difficult to analyzeImprove confidentialityOther printing matterUnauthorized memory use protectionMicrocomputerConfidentiality
A data mask section outputs memory data read from a memory array unit for a predetermined time period that is shifted from an edge timing of a clock signal, while a microcomputer takes in the data output from the data mask section at the edge timing of the clock signal. Thus, the microcomputer is capable of appropriately taking in the memory data only when the frequency of the clock signal is within a predetermined range, and accordingly, it is difficult to fraudulently obtain the memory data. Furthermore, the data mask section may output random data, or the like, during a time period other than the predetermined time period. In such a case, it is difficult to analyze the memory data, and the confidentiality of the memory data is improved.
Owner:PANASONIC CORP
Method for the transmission of information with improved perenniality
InactiveUS7975004B2Multiple countImprove securityDigital data processing detailsMultiple digital computer combinationsClient-sideInformation transfer
A method is provided for the transmissions of information between at least a first and a second communication means. The method includes in saving at least one set of information in an intermediate element. The method also includes defining a plurality of client groups, using an identifier in order to designate at least one group of clients that are authorized to access the information set, and at least one filtering step, which is intended to prevent a user that does not belong to the group from accessing the information. The method enables the integrity of the contained in the intermediate element to be substantially secured, by selecting clients that are authorized to access the information.
Owner:FRANCE TELECOM SA
Printing system and data transmission method thereof
ActiveUS9041967B1Improve data confidentialityData transfer speed is fastDigitally marking record carriersDigital computer detailsData transmissionVIT signals
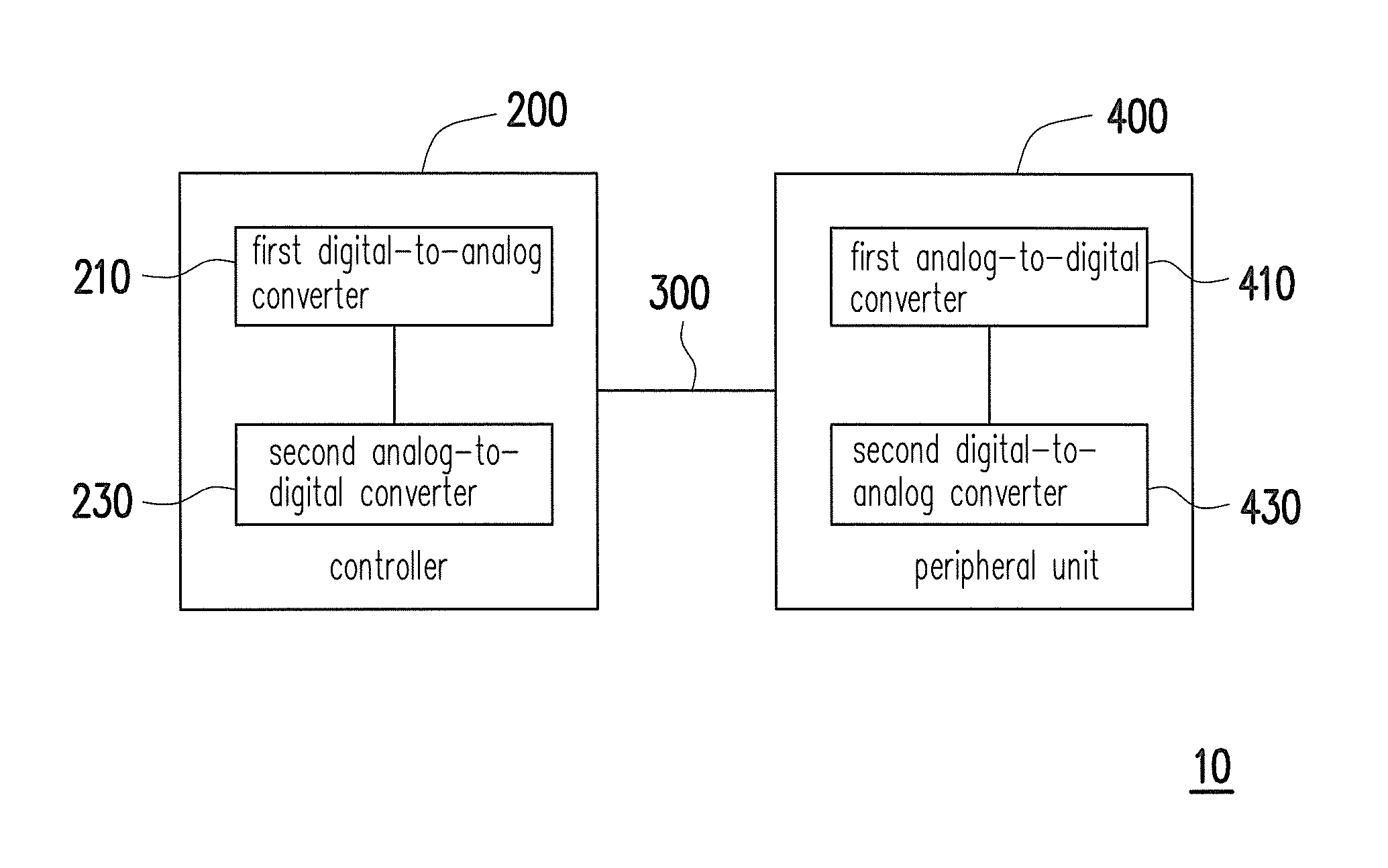
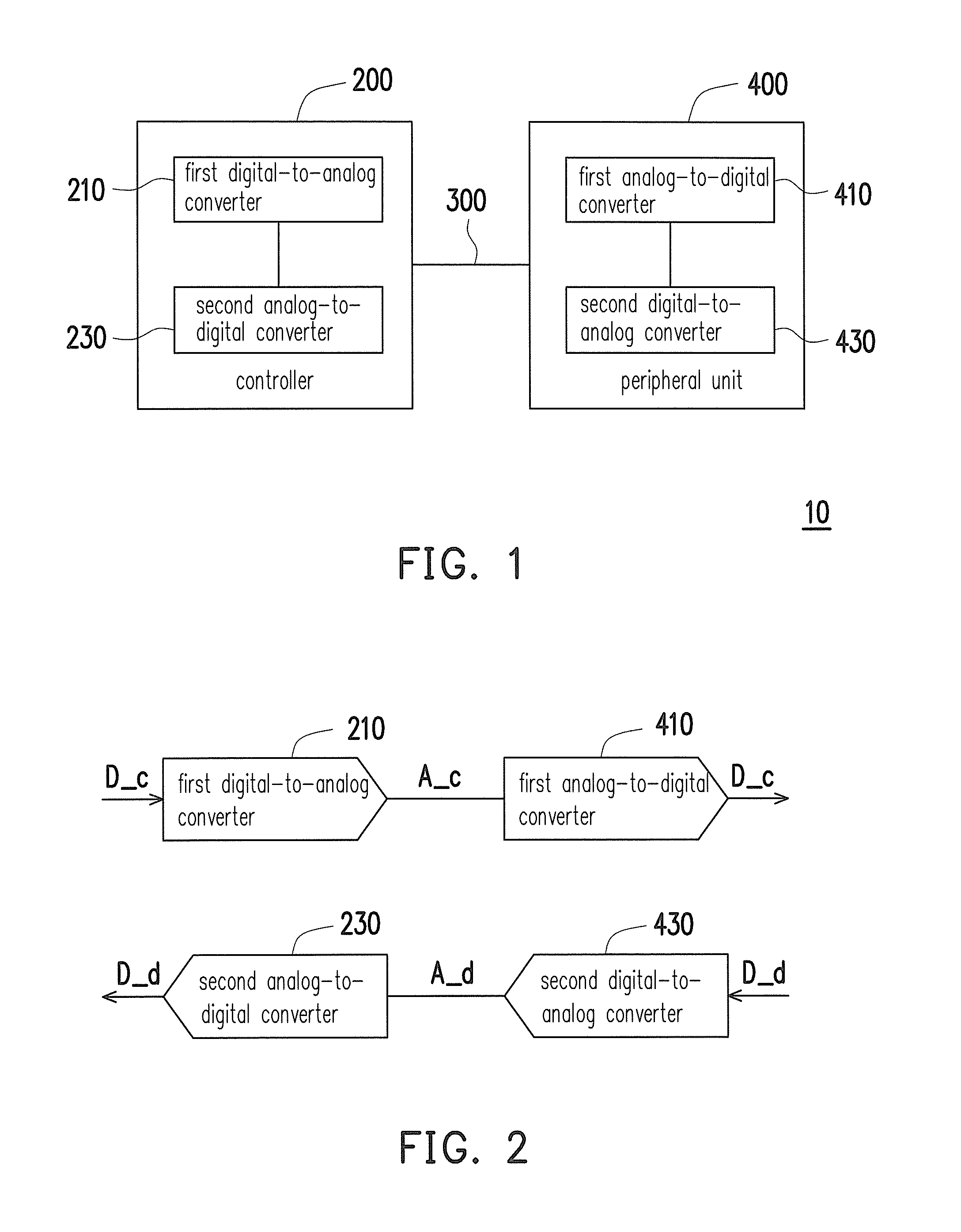
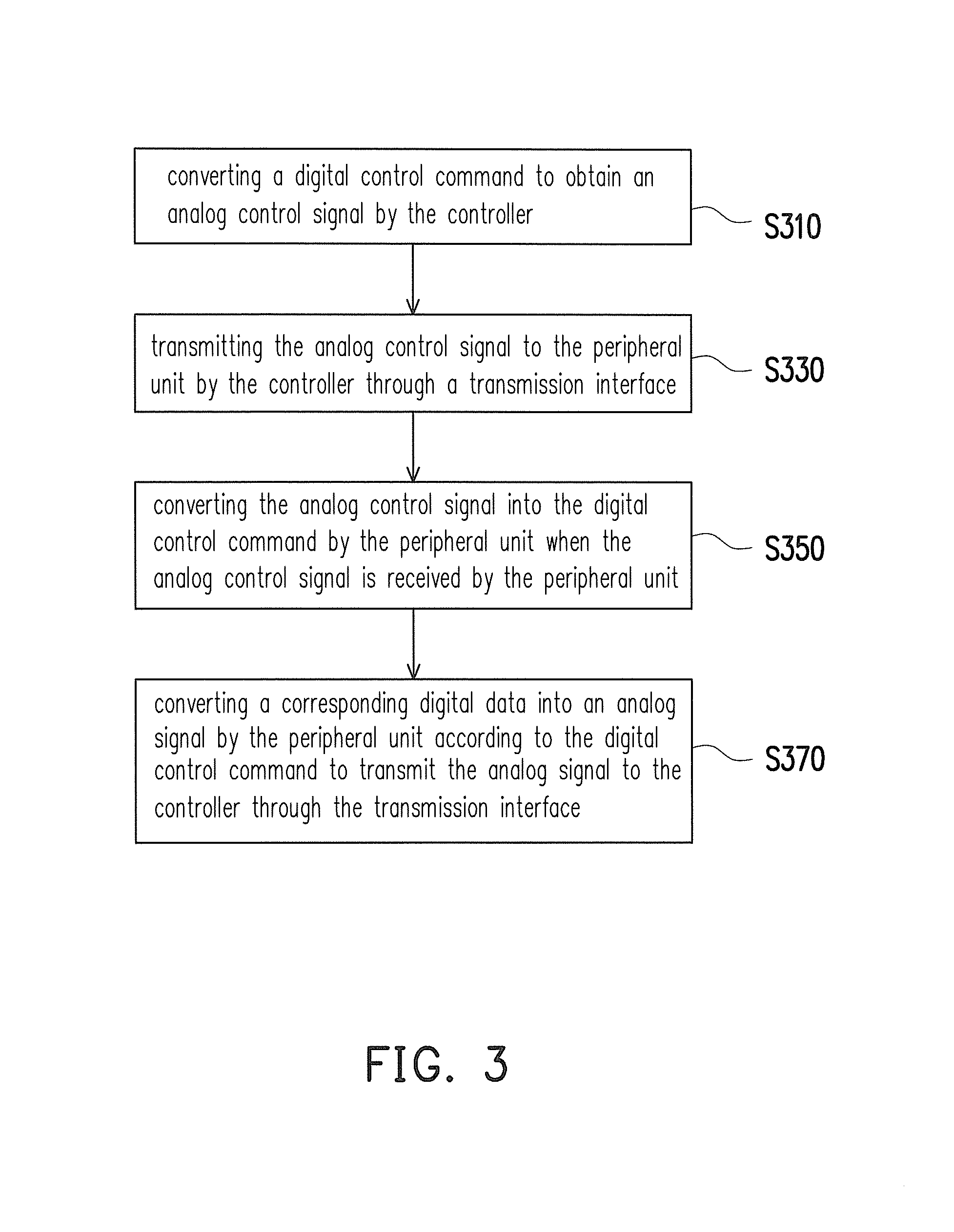
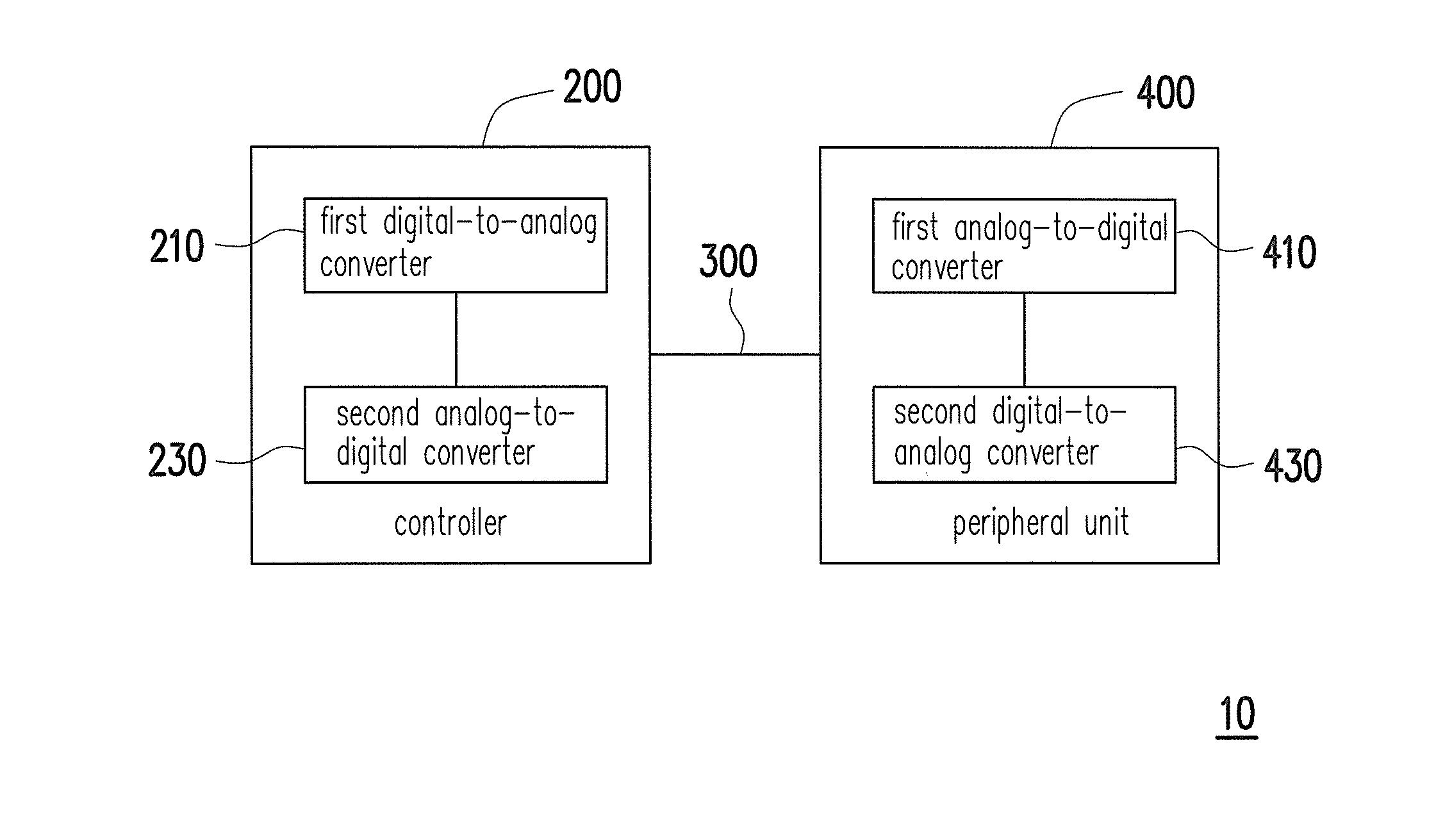
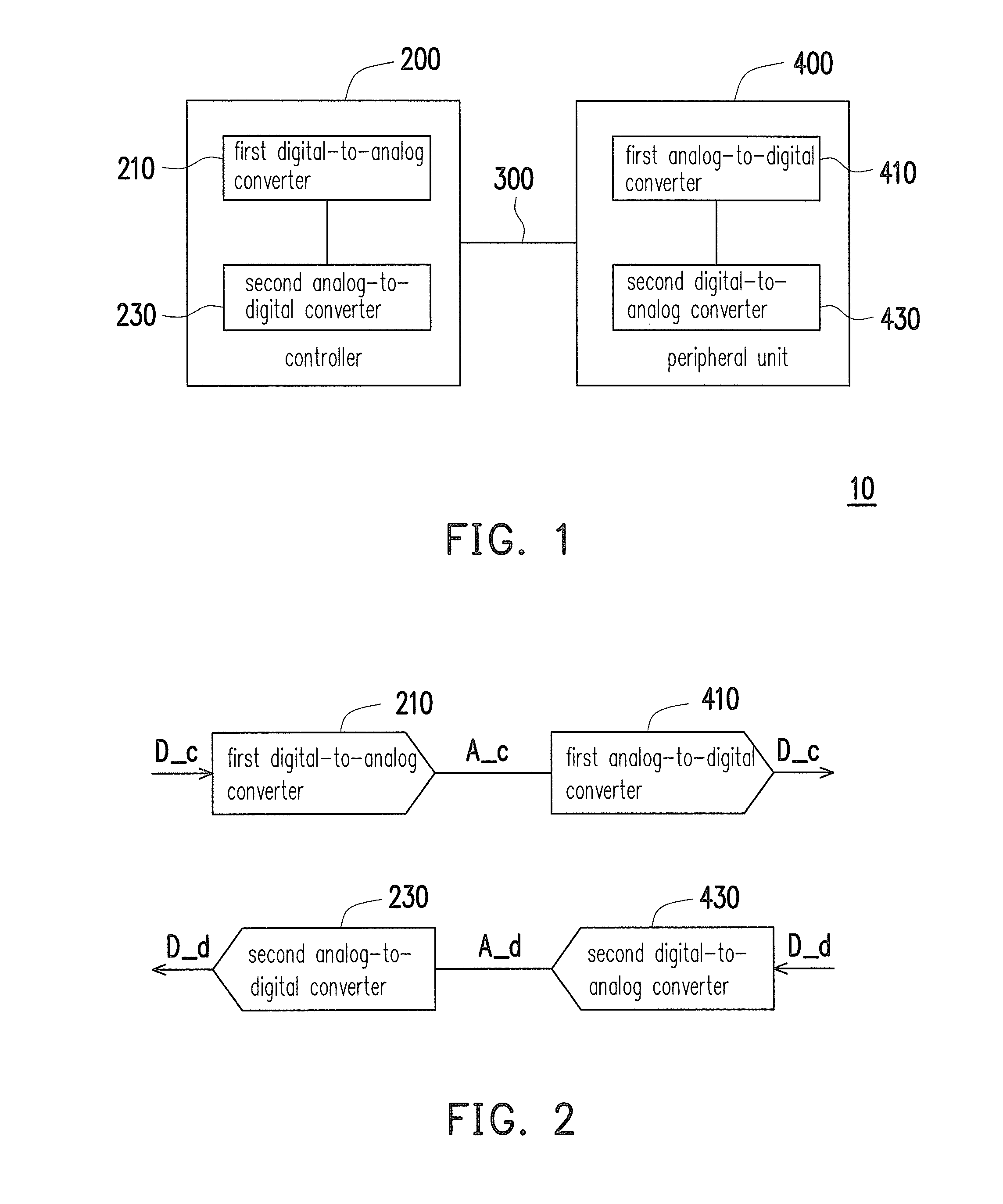
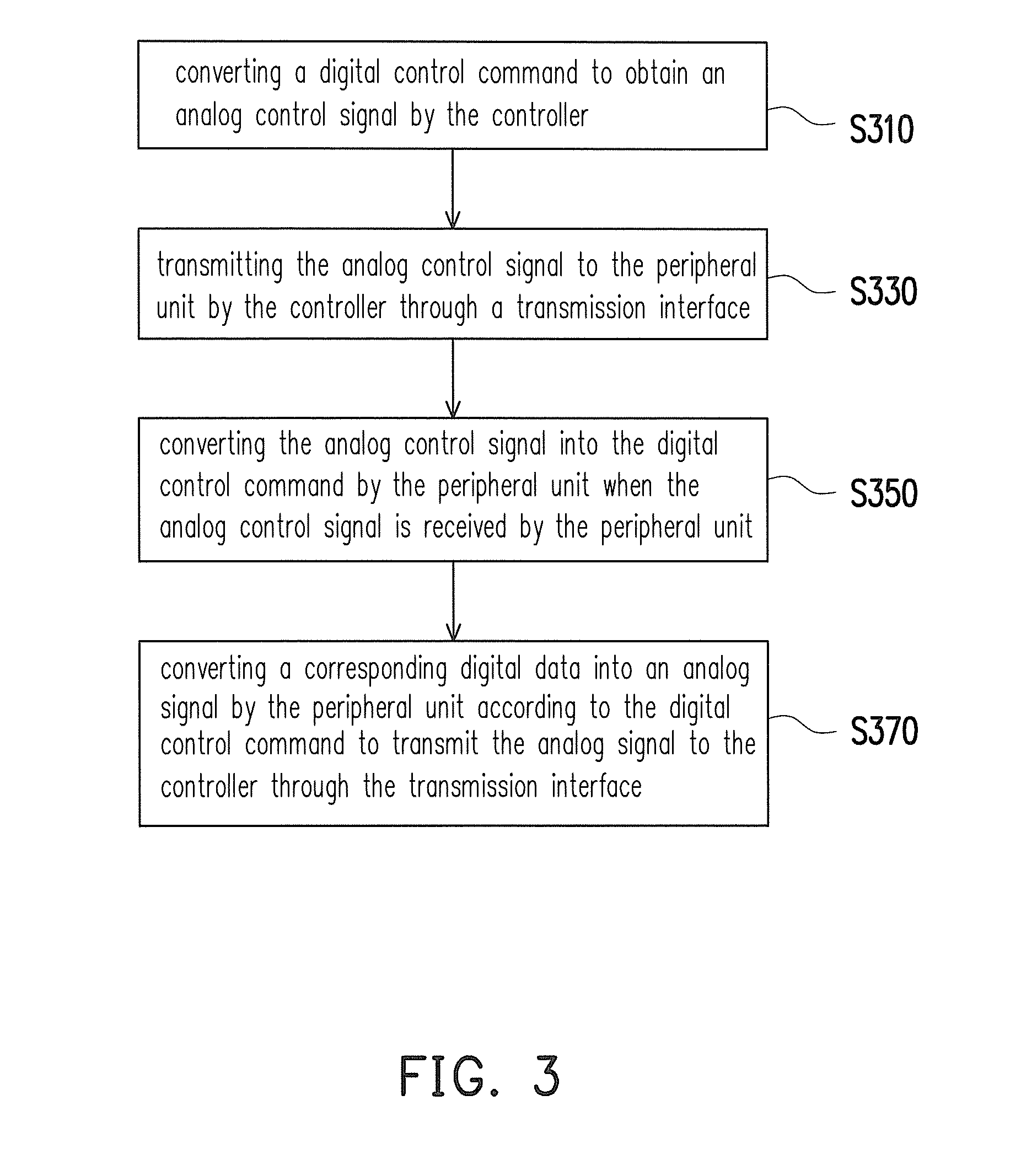
A printing system and a data transmission method thereof are provided. The printing system includes a peripheral unit and a controller. The peripheral unit is configured to execute a data printing function and includes a digital data. The controller is coupled to the peripheral unit. The controller converts a digital control command to obtain an analog control signal, and transmits the analog control signal to the peripheral unit. The peripheral unit converts the analog control signal into the digital control command when the analog control signal is received by the peripheral unit. The peripheral unit converts a corresponding digital data into an analog signal according to the digital control command to transmit the analog signal to the controller.
Owner:XYZPRINTING +2
Organic light emitting diode device and manufacturing method thereof
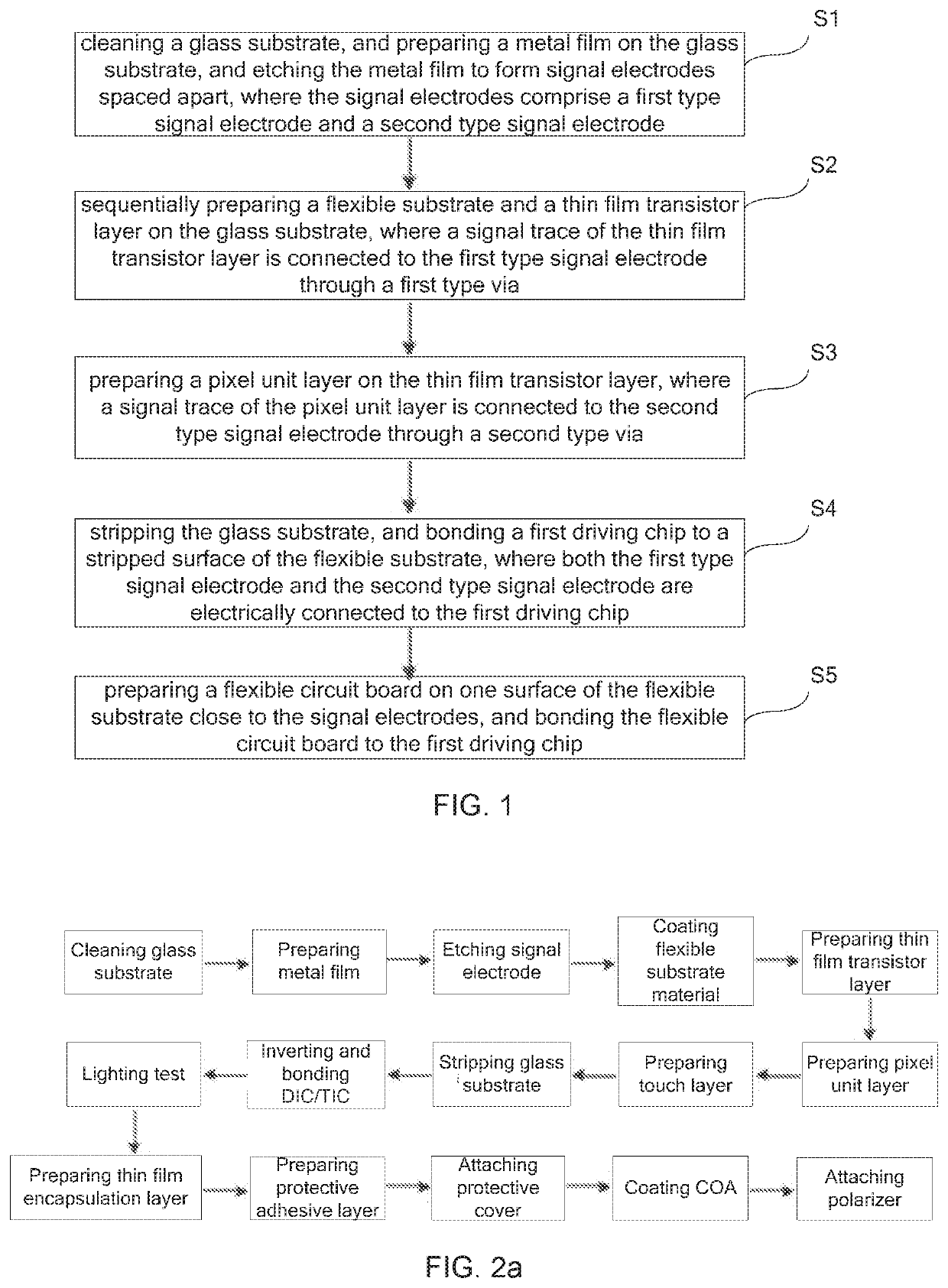
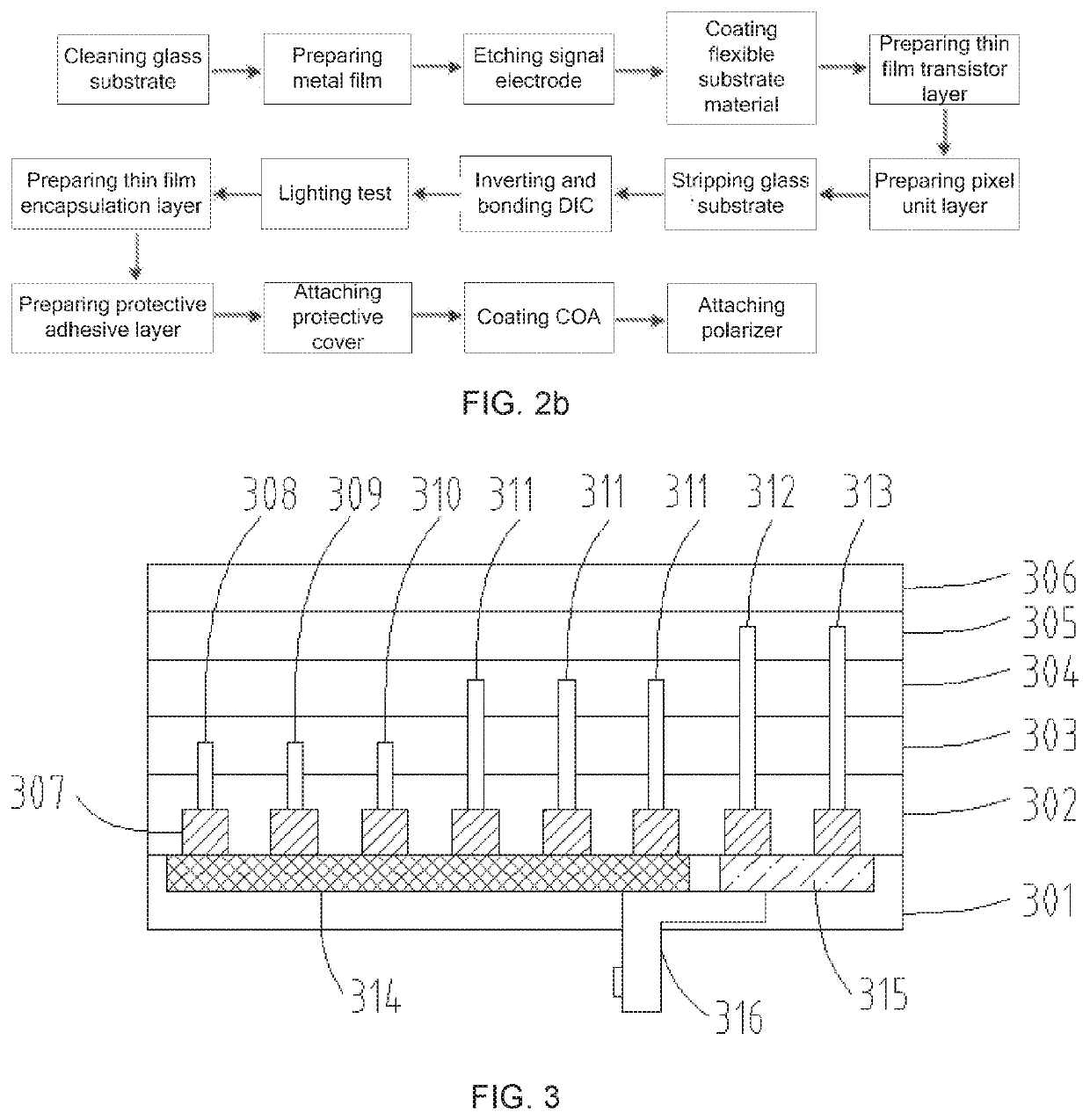
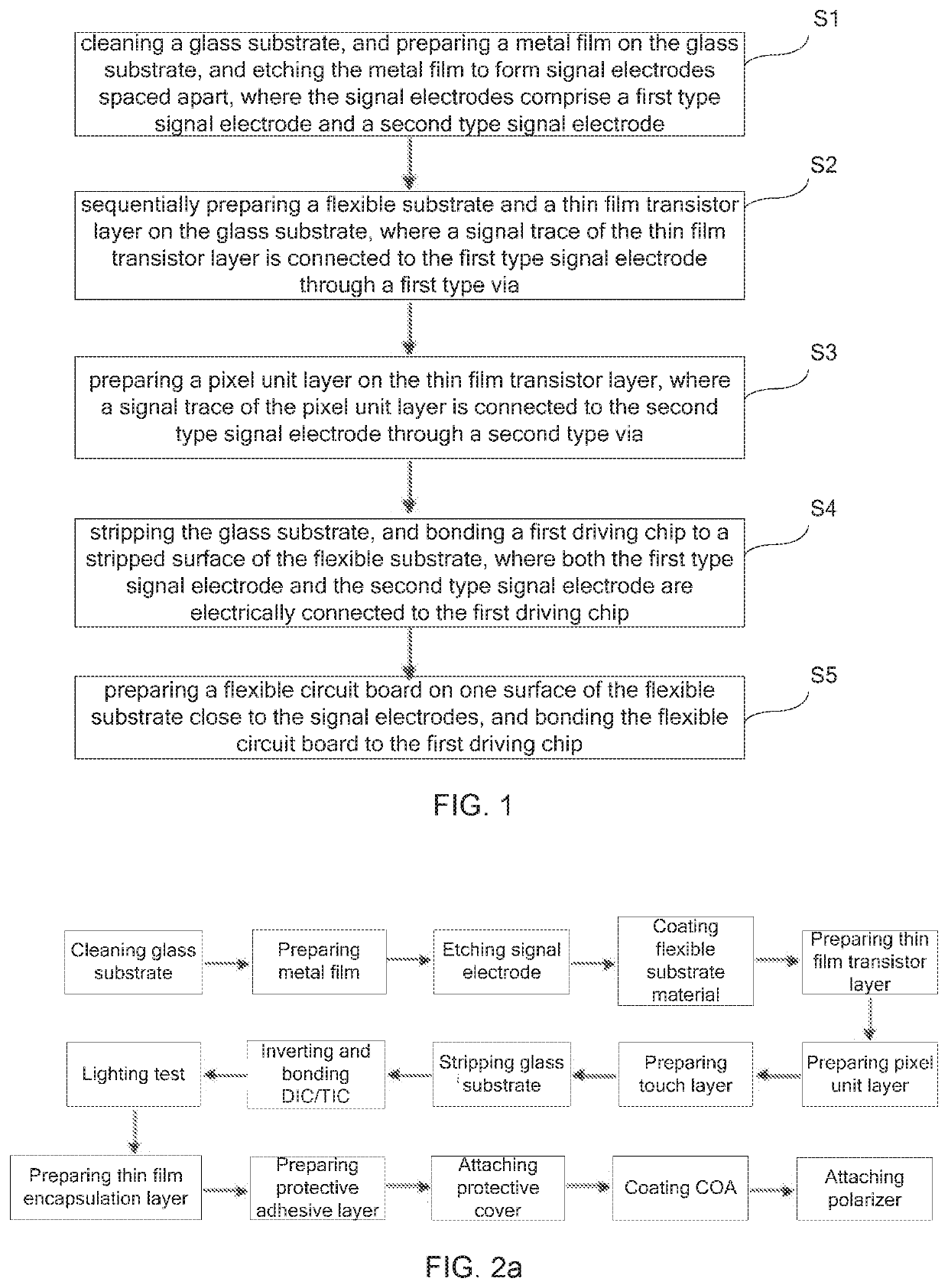
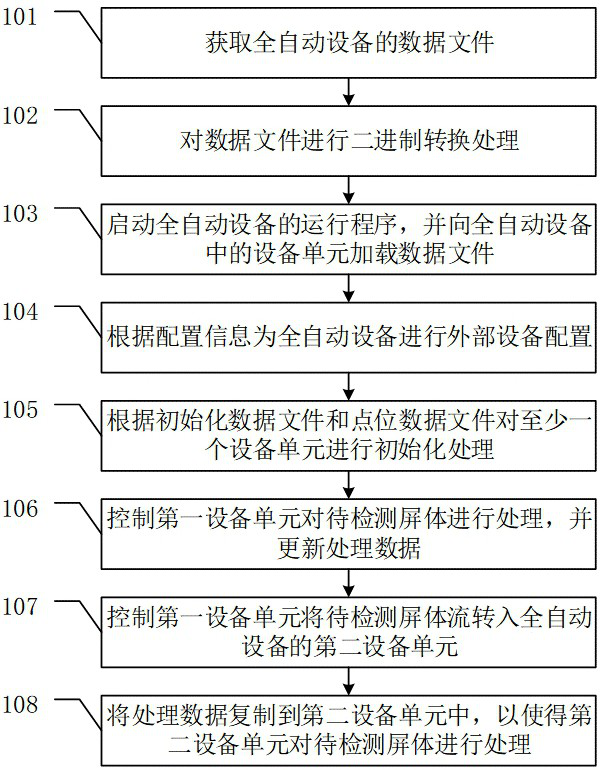
ActiveUS20200106029A1Increase the effective display areaHigh mechanical strengthFinal product manufactureSolid-state devicesFlexible circuitsEngineering
Provided is an OLED device and a manufacturing method thereof. The OLED device includes: a flexible substrate having signal electrodes embedded on a surface of one side of the flexible substrate and a thin film transistor layer and a pixel unit layer prepared on a surface of the other side; both a first driving chip and a flexible circuit board are disposed on a back surface of the flexible substrate; signal traces in the thin film transistor layer and the pixel unit layer are connected to corresponding signal electrodes through vias, and the signal electrodes are connected to the first driving chip.
Owner:WUHAN CHINA STAR OPTOELECTRONICS SEMICON DISPLAY TECH CO LTD
Printing system and data transmission method thereof
InactiveUS20150153974A1Improve data confidentialityData transfer speed is fastDigital output to print unitsDigital dataAnalog signal
A printing system and a data transmission method thereof are provided. The printing system includes a peripheral unit and a controller. The peripheral unit is configured to execute a data printing function and includes a digital data. The controller is coupled to the peripheral unit. The controller converts a digital control command to obtain an analog control signal, and transmits the analog control signal to the peripheral unit. The peripheral unit converts the analog control signal into the digital control command when the analog control signal is received by the peripheral unit. The peripheral unit converts a corresponding digital data into an analog signal according to the digital control command to transmit the analog signal to the controller.
Owner:XYZPRINTING +2
Organic light emitting diode device and manufacturing method thereof
ActiveUS10847731B2Increase the effective display areaHigh mechanical strengthFinal product manufactureSolid-state devicesFlexible circuitsLight-emitting diode
Provided is an OLED device and a manufacturing method thereof. The OLED device includes: a flexible substrate having signal electrodes embedded on a surface of one side of the flexible substrate and a thin film transistor layer and a pixel unit layer prepared on a surface of the other side; both a first driving chip and a flexible circuit board are disposed on a back surface of the flexible substrate; signal traces in the thin film transistor layer and the pixel unit layer are connected to corresponding signal electrodes through vias, and the signal electrodes are connected to the first driving chip.
Owner:WUHAN CHINA STAR OPTOELECTRONICS SEMICON DISPLAY TECH CO LTD
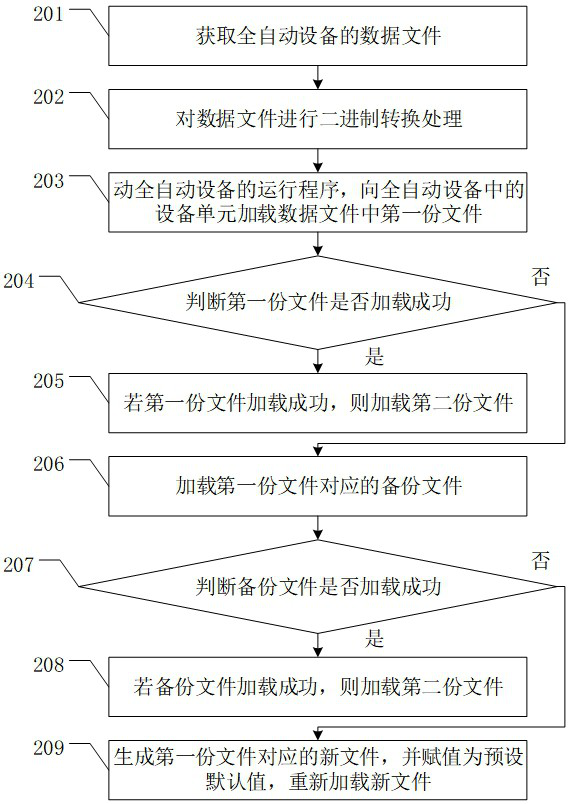
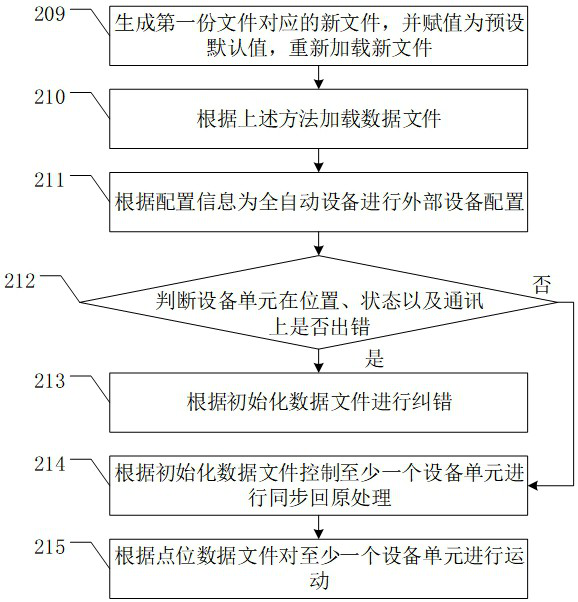
Data processing method of full-automatic equipment and related device
ActiveCN114721893AImprove data confidentialityDetecting faulty hardware by configuration testBootstrappingComputer hardwareConfidentiality
The invention discloses a data processing method of full-automatic equipment and a related device, which are used for improving the data confidentiality degree of traditional full-automatic equipment. The method comprises the following steps: acquiring a data file of the full-automatic equipment; performing binary conversion processing on the data file; starting a running program of the full-automatic equipment, and loading the data file to the equipment unit; performing external equipment configuration on the full-automatic equipment according to the configuration file; performing initialization processing on the at least one equipment unit according to the initialization data file and the point location data file; controlling the first equipment unit to process the to-be-detected screen body according to the equipment unit state file, the point location data file and the processing data, and updating the processing data; the second equipment unit is used for controlling the first equipment unit to transfer the to-be-detected screen body into the full-automatic equipment; copying the processing data into the second equipment unit to enable the second equipment unit to process the to-be-detected screen body; and updating and storing the data of the at least two equipment units into the data file.
Owner:SHENZHEN SEICHITECH TECHN CO LTD
A whole sea area tide gauge system and tide gauge method based on Beidou
ActiveCN106908044BExpand the scope of workOvercome the shortcoming that the means of tide measurement can only be operated near the shoreMeasuring open water movementSatellite radio beaconingData acquisitionLongitude
The invention discloses a whole-sea tidal observation system based on Beidou. The whole-sea tidal observation system comprises a Beidou second-generation satellite navigation and positioning system, a Beidou satellite communication system, a shoreside base station, and a tidal observation data acquisition device positioned on a carrier in ocean; meanwhile, the invention discloses a tidal observation method for the tidal observation system; the tidal observation method comprises the following steps: determining a tide model of a sea area where the shoreside base station is located by the shoreside base station according to latitude and longitude coordinates of the tidal observation data acquisition device, determining a main tidal component type of the sea area where the shoreside base station is located, and carrying out trigonometric polynomial fitting on daylong tidal level data according to the period of the tidal component type to obtain a high-precision daily tide level curve. The whole-sea tidal observation system disclosed by the invention can be applied to any one sea area which can receive an electromagnetic wave signal of a Beidou second-generation satellite; the defect that a conventional tidal observation means only can be operated near shore is overcome, and the working range of marine tide measurement is widened; in addition, the Beidou satellite communication system is adopted for carrying out data transmission, so high data security is realized.
Owner:THE FIRST INST OF OCEANOGRAPHY SOA +1
Device and method for analyzing performances of a web application
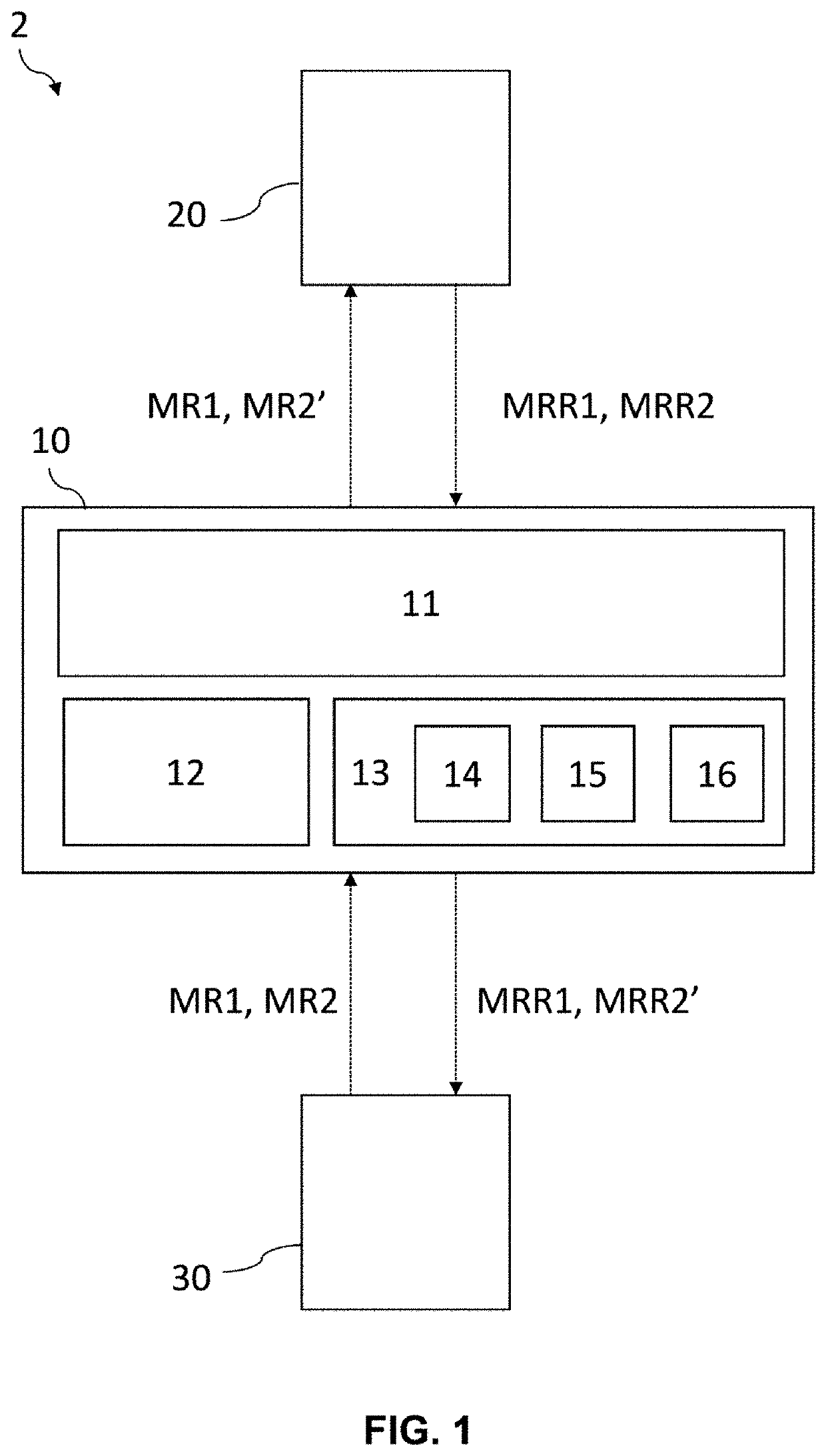
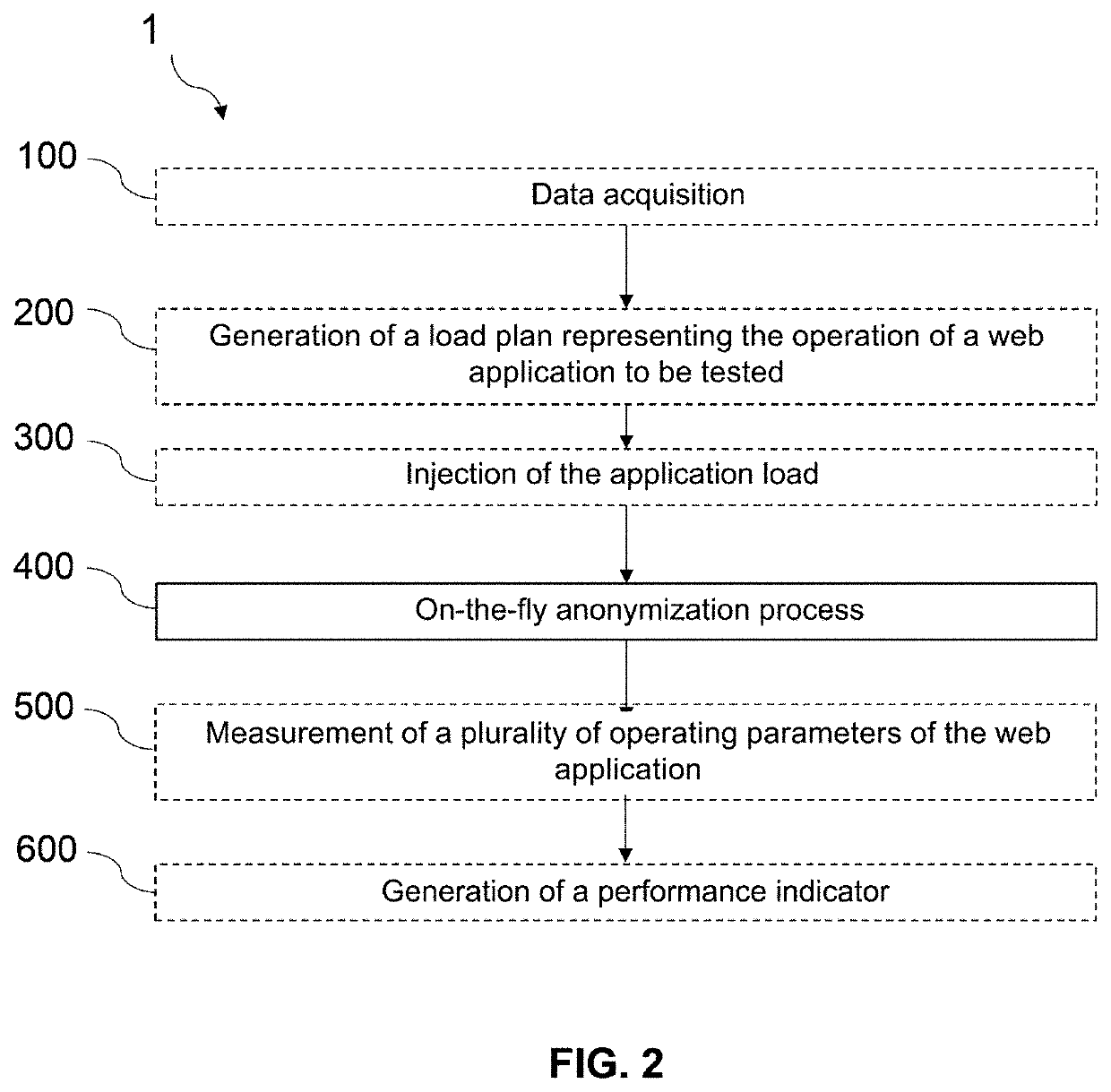
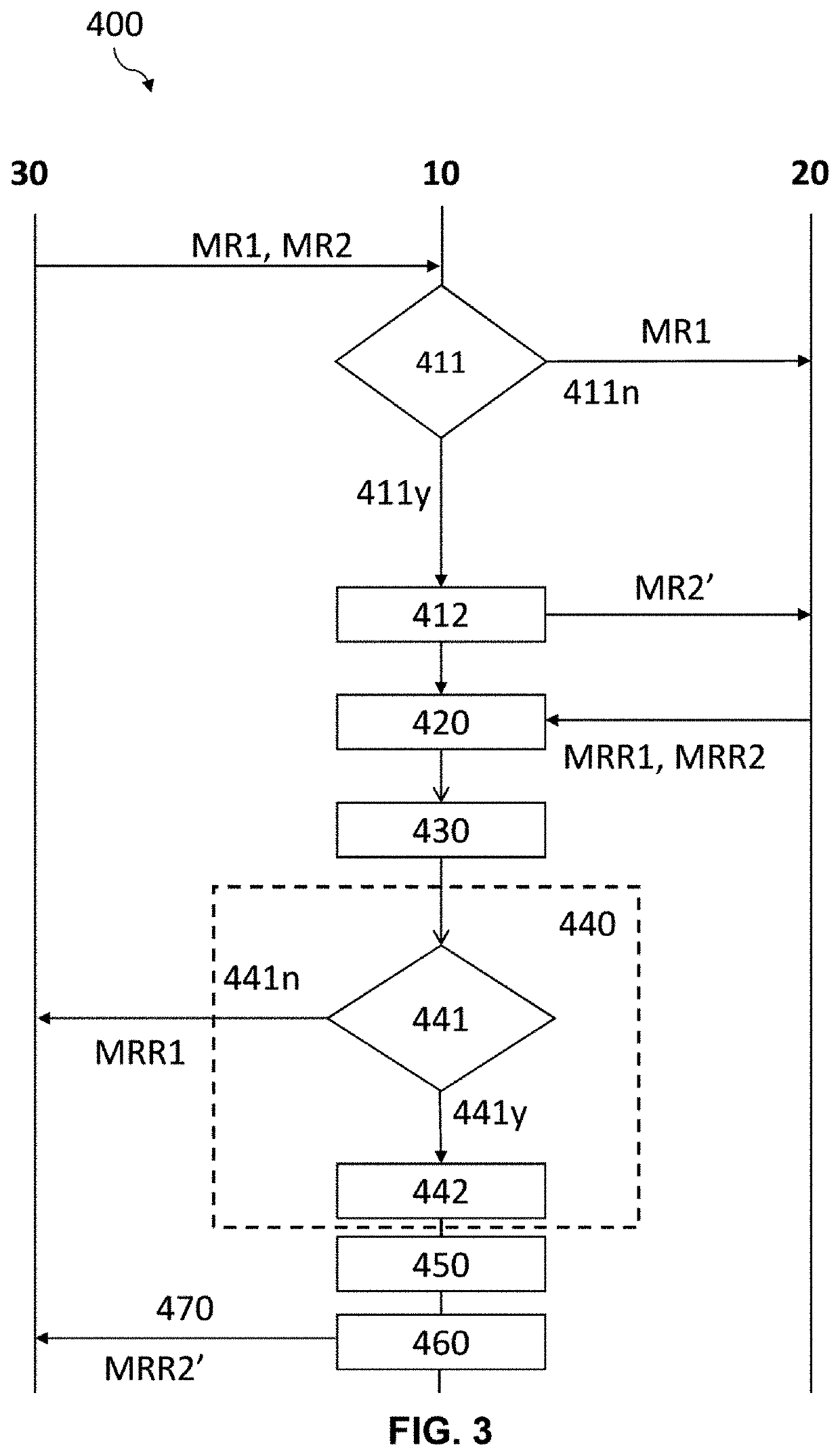
ActiveUS20210019446A1Save timeConserving data confidentialityError detection/correctionDigital data protectionElectronic communicationEngineering
The invention relates to a device and a method for analyzing performances of a web application capable of performing a process of on-the-fly anonymization (400) of production data, said production data being generated following a benchmark request message (MR1, MR2′) transmitted to said web application, said anonymization process (400) being carried out by a first electronic communication device (10) capable ofIdentifying, from a sensitive data identification repository (14), data to be anonymized in the response message (MRR1, MRR2);Generating, from an anonymization repository (15), anonymized data from previously identified data to be anonymized; andGenerating, from the anonymized data and from the response message (MRR2), an anonymized response message (MRR2′).
Owner:BULL SA
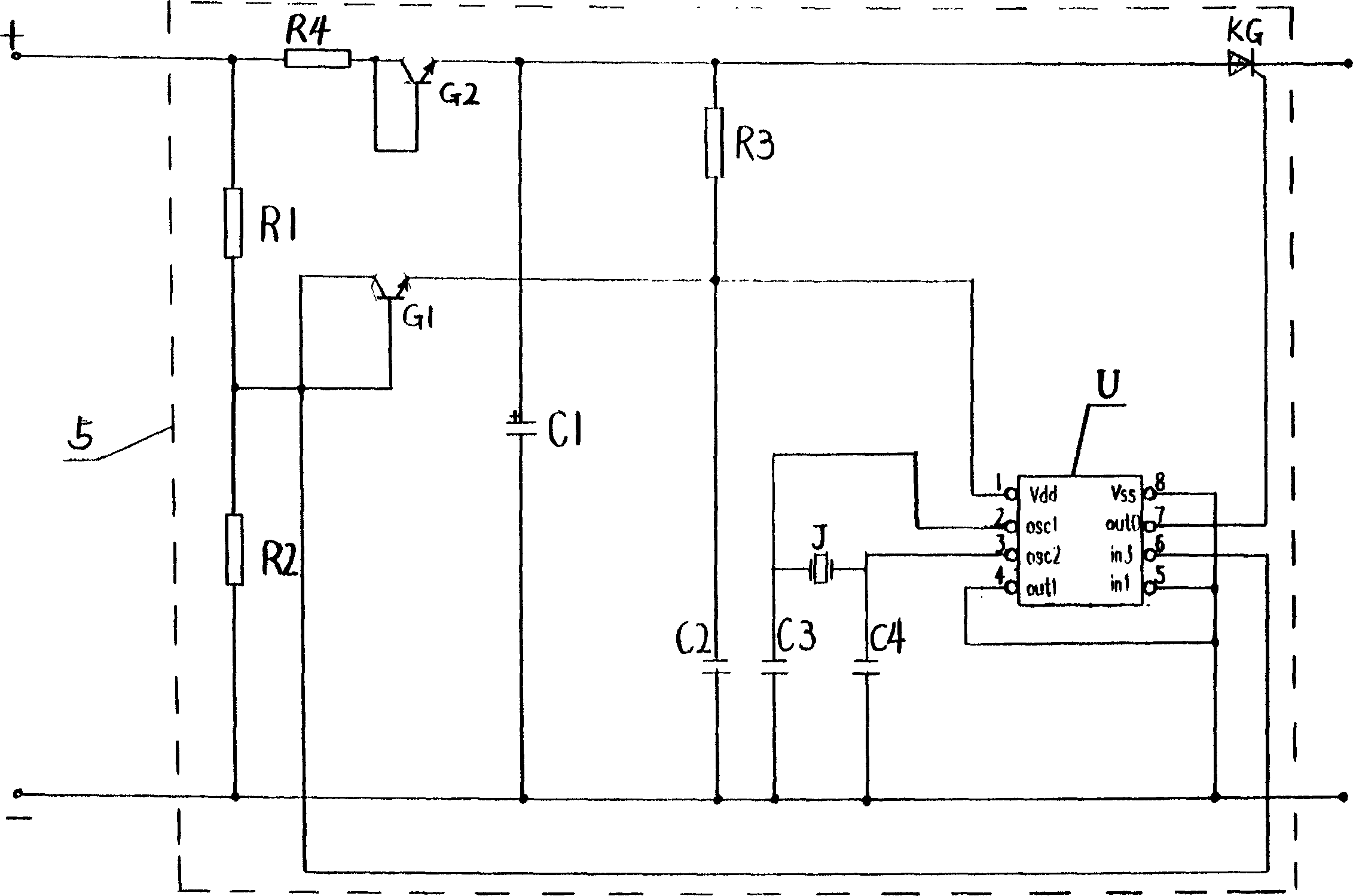
Safeety detonator
The prodn. method of safety detonator is that conducting wire is connected with detonator body, bottom explosive is put in bottom of detonator, force-end of conducting wire is encapsulated on top of the detonator by elastic PVC plastic plug, an electric time delay unit is connected with force-end of the conducting wire, igniting powder head is connected with out-end of the electric time delay unit. The delay time can be set to 1-30 section with equally interval 20 millisecond, delay error is less than 5 millisecond.
Owner:GUIZHOU JIULIAN IND EXPLOSIVE MATERIALS DEV
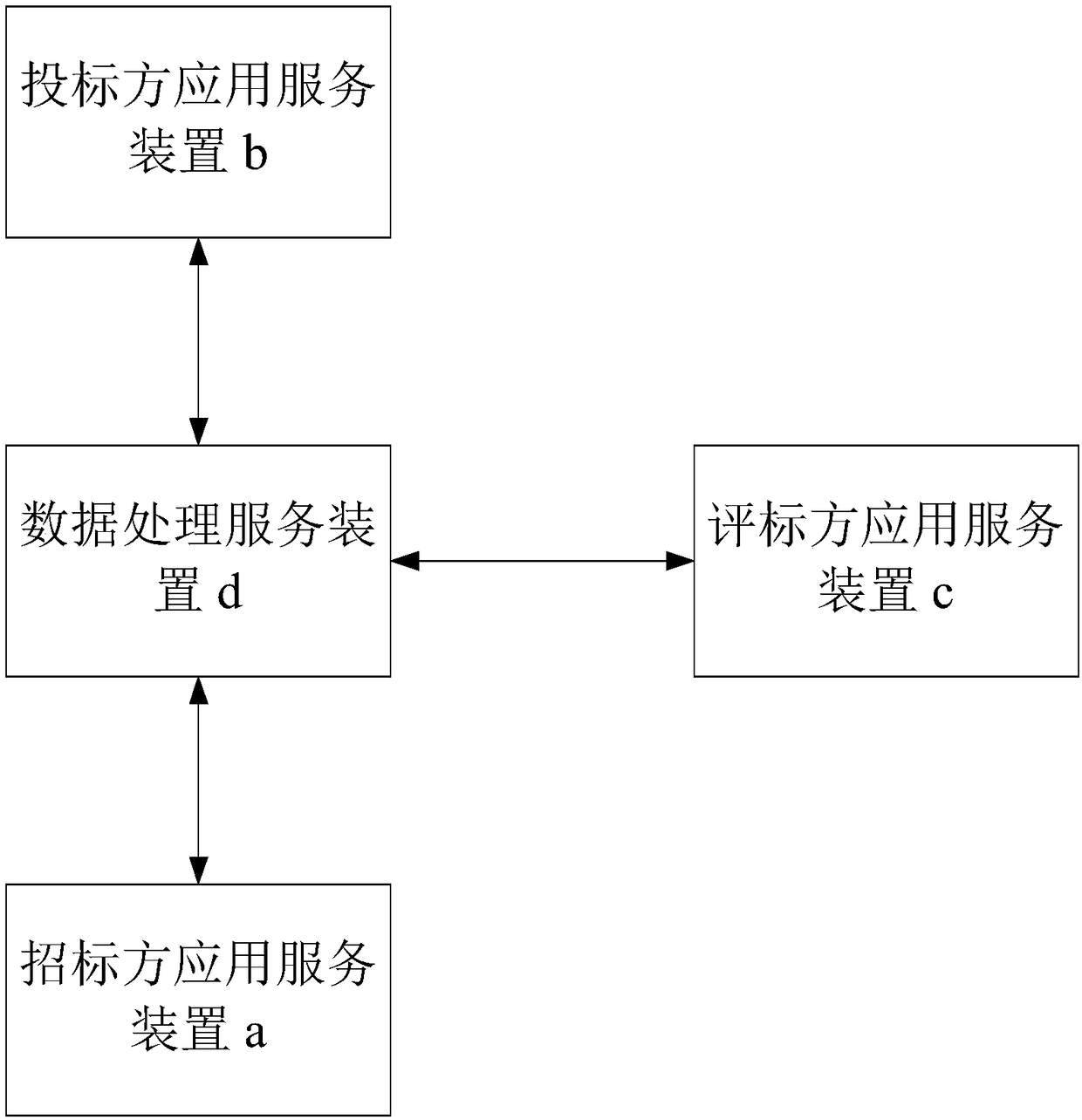
Data fragmentation processing method for bid invitation, tender and evaluation online transaction system
InactiveCN108280586AImprove controllabilityImprove data confidentialityBuying/selling/leasing transactionsResourcesConfidentialityNetwork connection
The invention relates to a data fragmentation processing method for a bid invitation, tender and evaluation online transaction system. The data fragmentation processing method includes the steps of S1, connecting a tenderer application service device, a bidder application service device, an evaluator application service device and a data processing service device through the network; S2, storing bid invitation data individually through the data processing service device; S3, responding to the bid invitation data one by one through the tender application service device; S4, data, divided into automatic calculated data and manual reviewed data, as well as results of the automatic calculated data , are stored individually through the data processing service device; S5, responding to the manual reviewed data one by one through the evaluator application service device; S6, storing evaluation response data individually through the data processing service device. As the bid invitation data, the response data and the automatic calculated data of the system are stored respectively to realize fragmentation data storage, data confidentiality of the whole bid invitation, tender and evaluationprocess is improved.
Owner:万盈摩比科技(深圳)有限公司
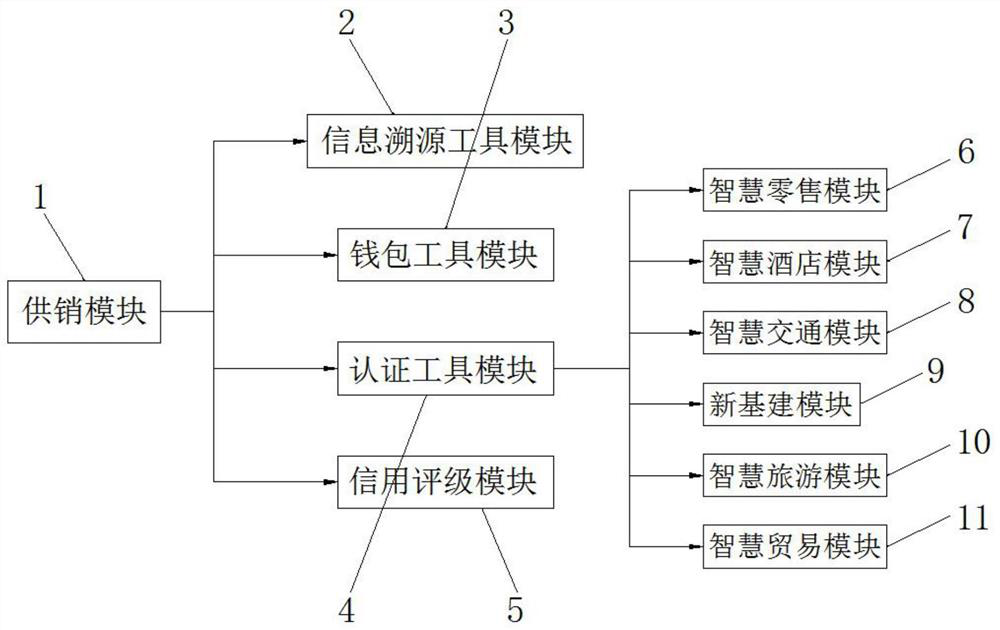
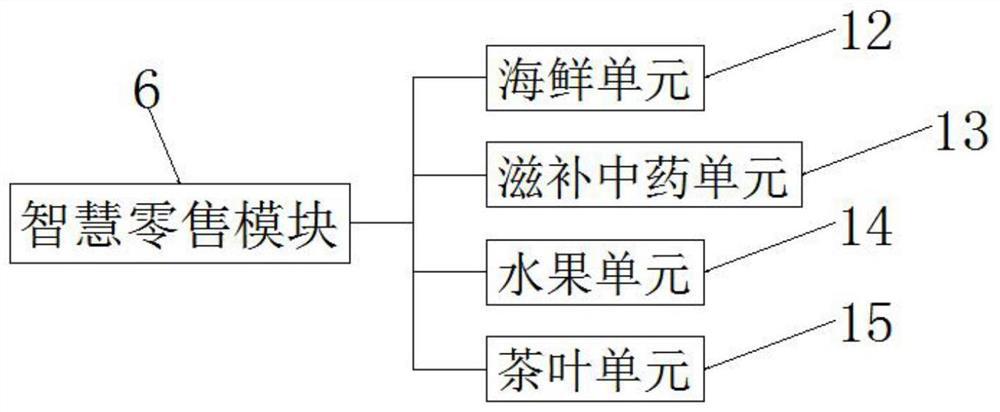
Supply and marketing system based on block chain technology
PendingCN112132590AReduce monitoring costsImprove data confidentialityFinanceBuying/selling/leasing transactionsBusiness enterpriseDatabase
The invention provides a supply and marketing system based on a block chain technology, which comprises a supply and marketing module, the supply and marketing module comprises an information traceability tool module, a wallet tool module, an authentication tool module and a credit rating module; the information traceability tool module can check detailed information of commodities through authorized users, and combined with geographic positions, the source of the product is traced, thus understanding the situation of the product from various aspects; the wallet tool module is used for payingand inquiring account information, and the authentication tool module is used for digital authentication of blockchain products and has the functions of inquiring and tracing a supply and marketing platform shop, authenticating information, confirming an authentication state and the like, so that a foundation is laid for building a supply and marketing platform consumption environment; and the credit rating module adopts an enterprise rating and scoring system and is based on enterprise basic information and basic indexes.
Owner:上海明寰科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com