File usage authority defining system and method
A setting method and permission technology, applied in the field of file usage permission setting system, can solve the problems of wrong permission setting, heavy burden on bosses and supervisors, inefficiency of file management process, etc., and achieve the effect of improving efficiency and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
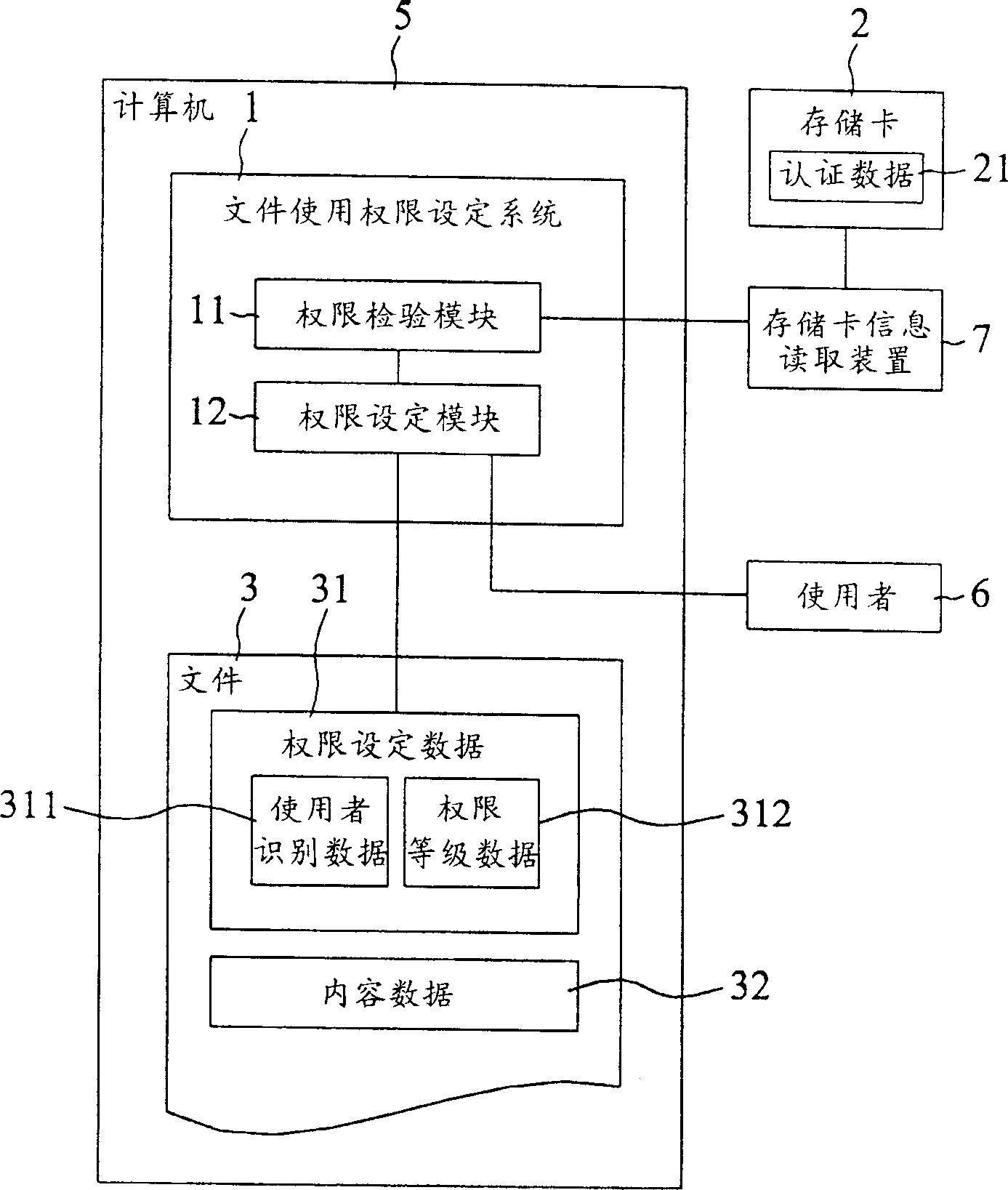
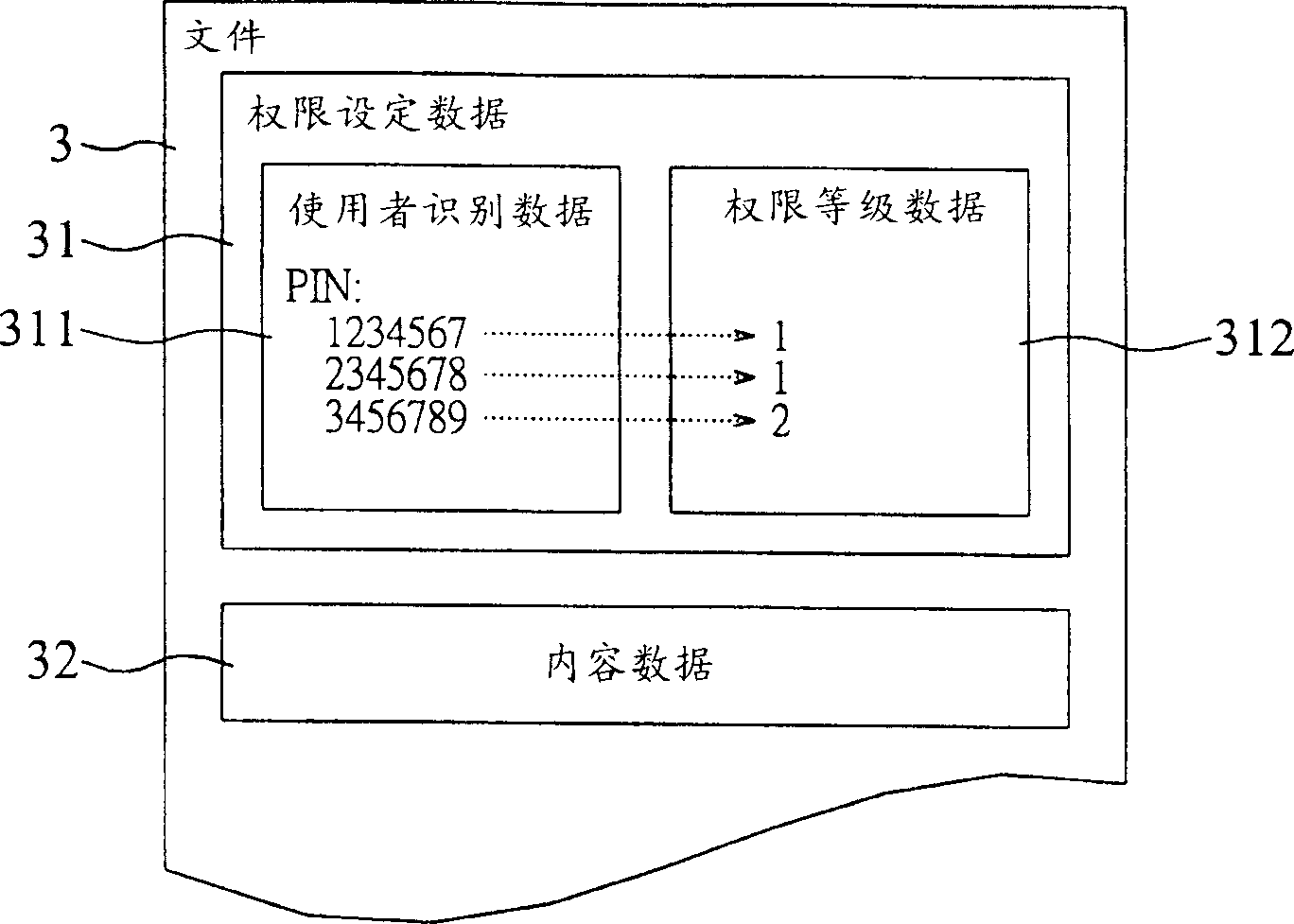
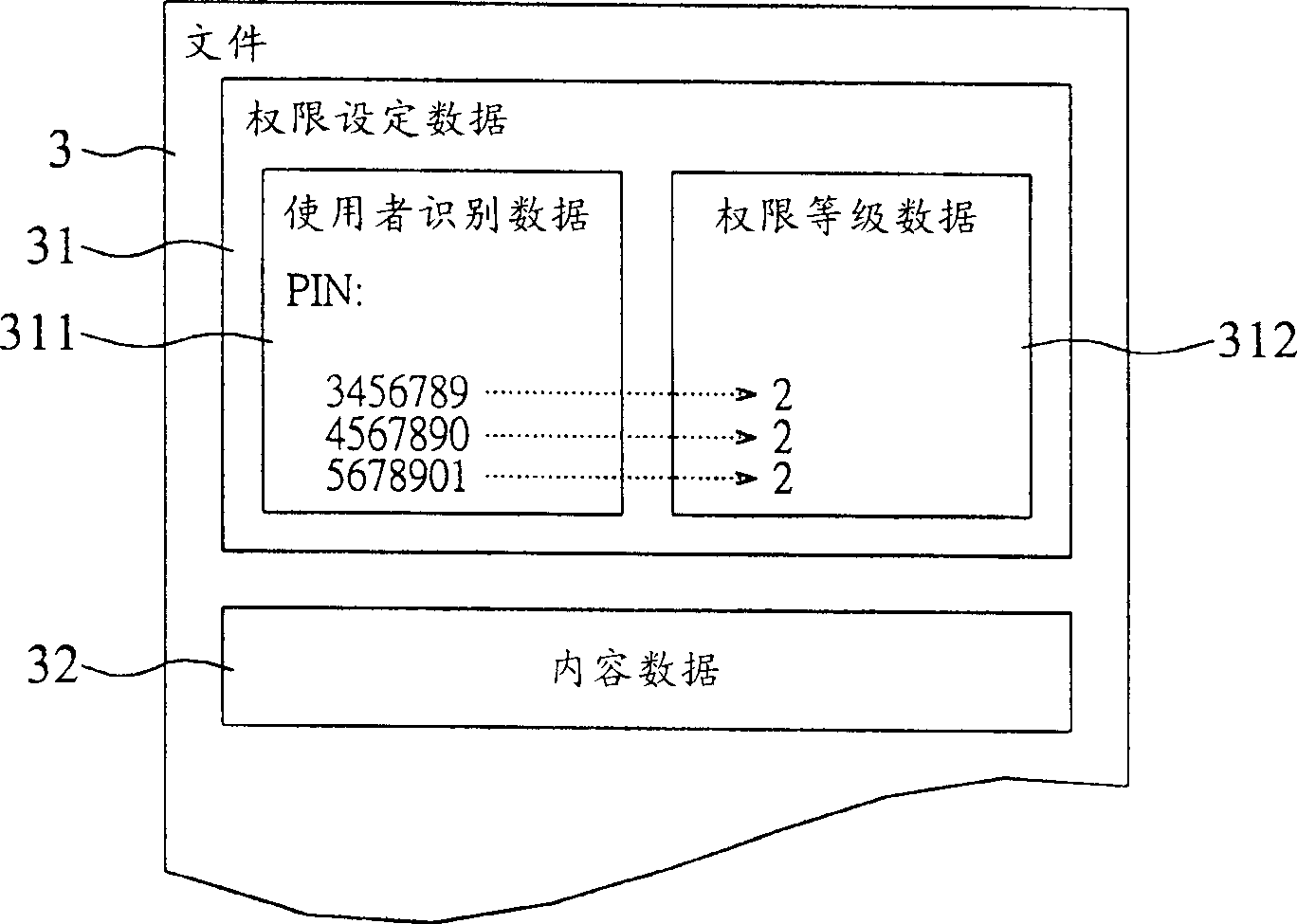
[0025] Please refer to figure 1 According to the preferred embodiment of the present invention, the file use authority setting system 1 is implemented in a computer 5 and includes an authority checking module 11 and an authority setting module 12 . In the computer 5, a file 3 including authority setting data 31 and content data 32 is stored. The authority setting data 31 includes user identification data 311 and authority level data 312 . In addition, the computer 5 cooperates with a memory card information reading device 7 to read the authentication data 21 stored in the memory card 2 . The user 6 sets the authority setting data 31 in the file 3 through the authority setting module 12 .
[0026] In this embodiment, the computer 5 at least includes a central processing unit, a computer-readable storage device, and other peripheral devices required to complete its functions, such as input devices such as keyboards and mice, and are connected to each other. An electronic sign...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com