Message source verification method, device and system and message sending method and device
A verification method and source technology, applied in the field of communication, can solve the problems of property loss, difficulty for users to identify the authenticity of news sources, forgery and counterfeiting of news sources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
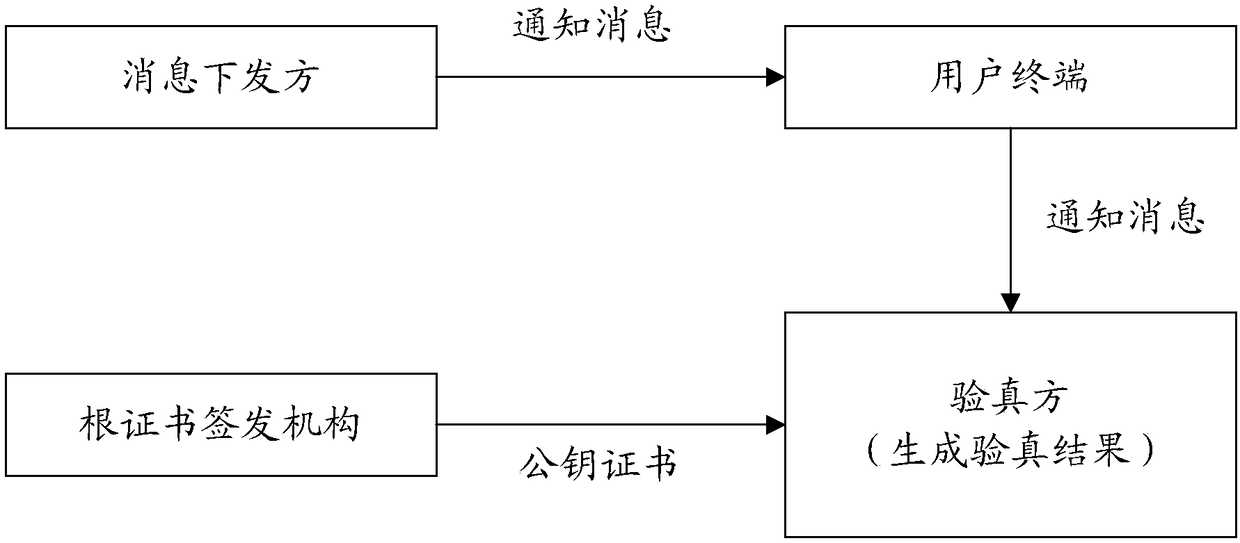
[0193] figure 1 An application scenario diagram of message source verification according to Embodiment 1 of the present application is shown. It can be seen from the figure that in the message verification scenario of the embodiment of the present application, there are a message issuer, a user terminal, an authenticity verifier and a root certificate issuing authority.
[0194] Among them, the sender of the message may be a trusted base station, a message server of an official organization, or other user terminals trusted by the message receiver, or a fake base station that sends notification messages containing fraudulent or false content, or other untrustworthy The sender of malicious messages such as user terminals.
[0195] Specifically, the message issuer may request a message issue certificate from the root certificate issuing authority, and the root certificate issuer may return a corresponding message issue certificate according to the message issuer. The message is...
Embodiment 2
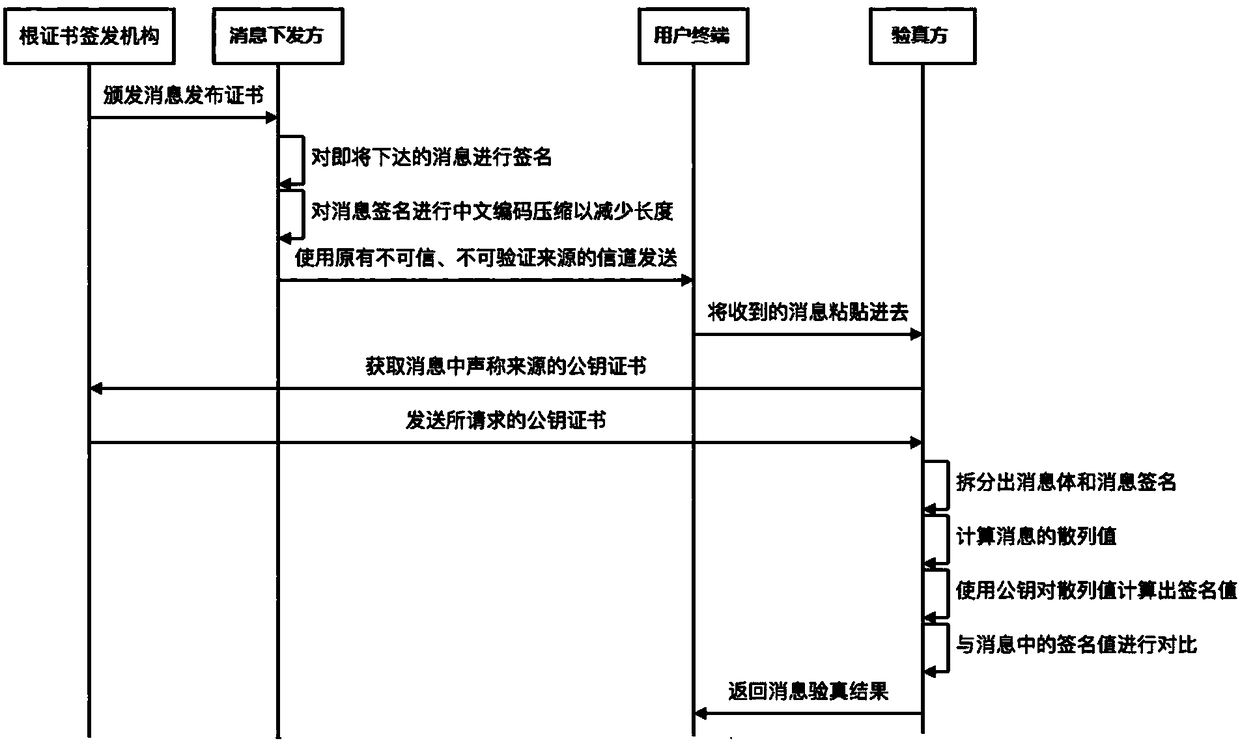
[0203] figure 2 A schematic diagram of information exchange for message source verification according to Embodiment 2 of the present application is shown. It can be seen from the figure that information exchange is performed among the message sender, user terminal, authenticity verifier and root certificate issuing authority to complete the verification of the source of the message.
[0204] Specifically, the root certificate issuing authority can issue a message release certificate to the message sender, and the message sender uses the message release certificate to sign the content of the message to be sent, and compresses the message signature in Chinese encoding to shorten the The length of the message signature. The sender of the message composes the message content and the message signature into a notification message, and sends the notification message to the user terminal using a conventional untrusted and unverifiable channel of the message source. For example, not...
Embodiment 3
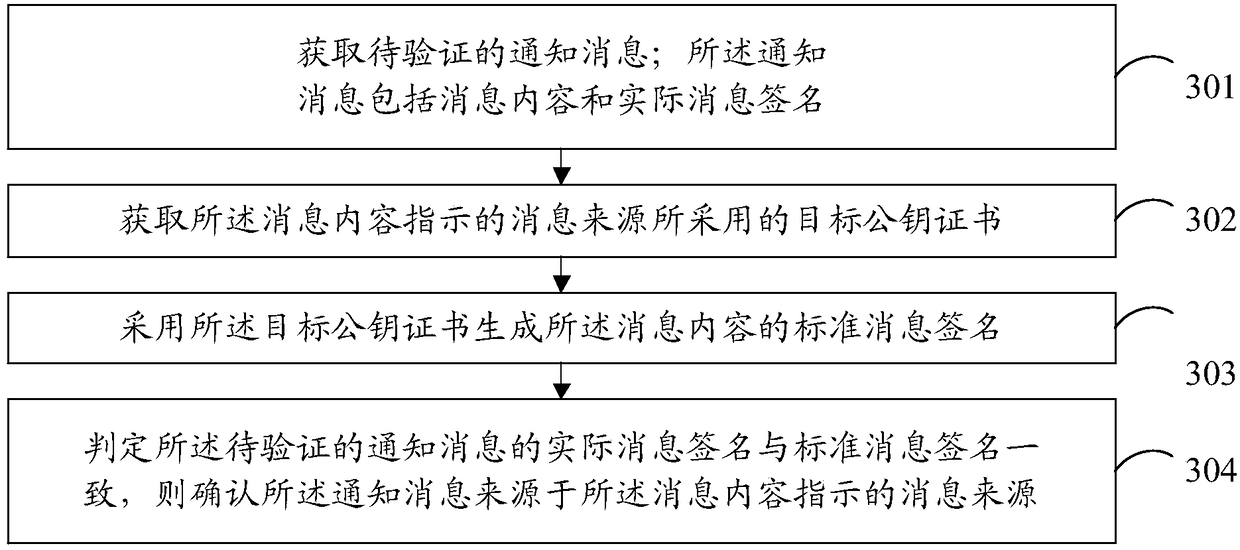
[0207] image 3 It shows a flow chart of the steps of a message source verification method in Embodiment 3 of the present application, which may specifically include the following steps:
[0208] Step 301, obtain a notification message to be verified; the notification message includes message content and an actual message signature.
[0209] In practical applications, when sending a notification message to a certain target client, the message source end used to send the notification message may, according to the source identifier of the message source end, select from, for example, PKI (Public Key Infrastructure, public key infrastructure), The certificate issuing platform such as CA (Certificate Authority, certification center) obtains the corresponding target public key certificate.
[0210] In practical applications, the target public key certificate can also be pre-stored in the message source, and the target public key certificate can be obtained locally when a notificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com