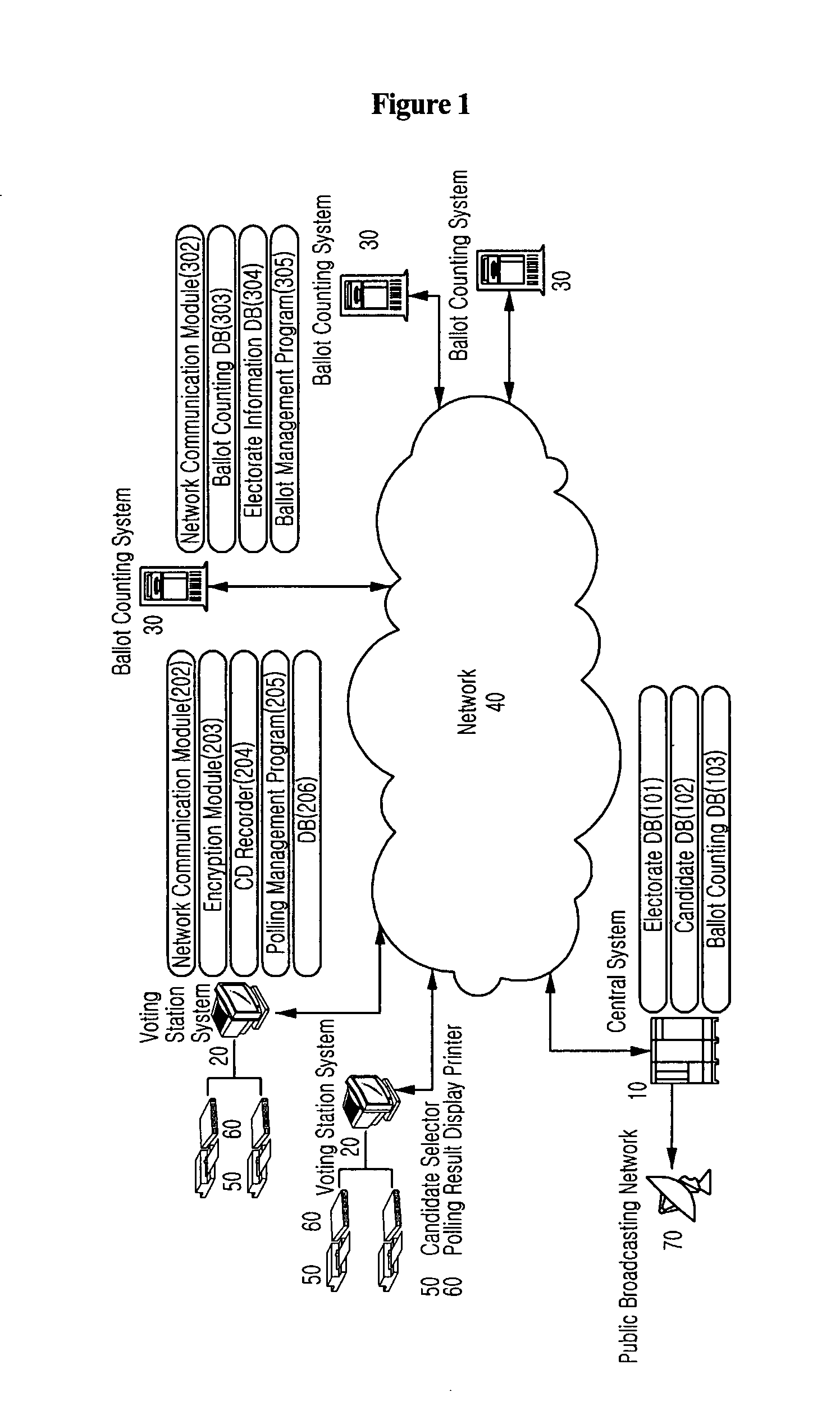
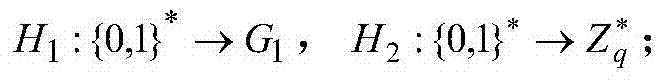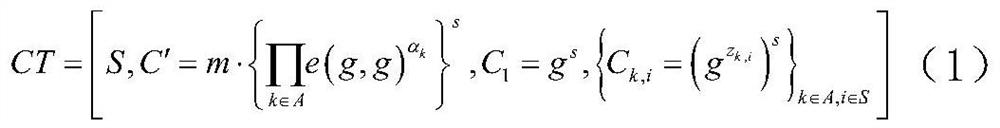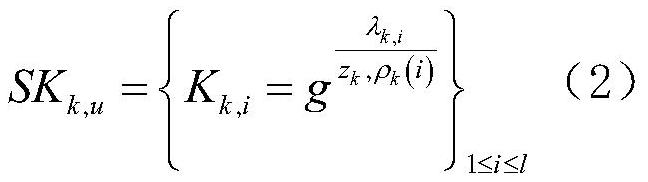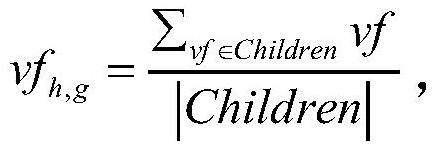Patents
Literature
46 results about "Verifiable encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
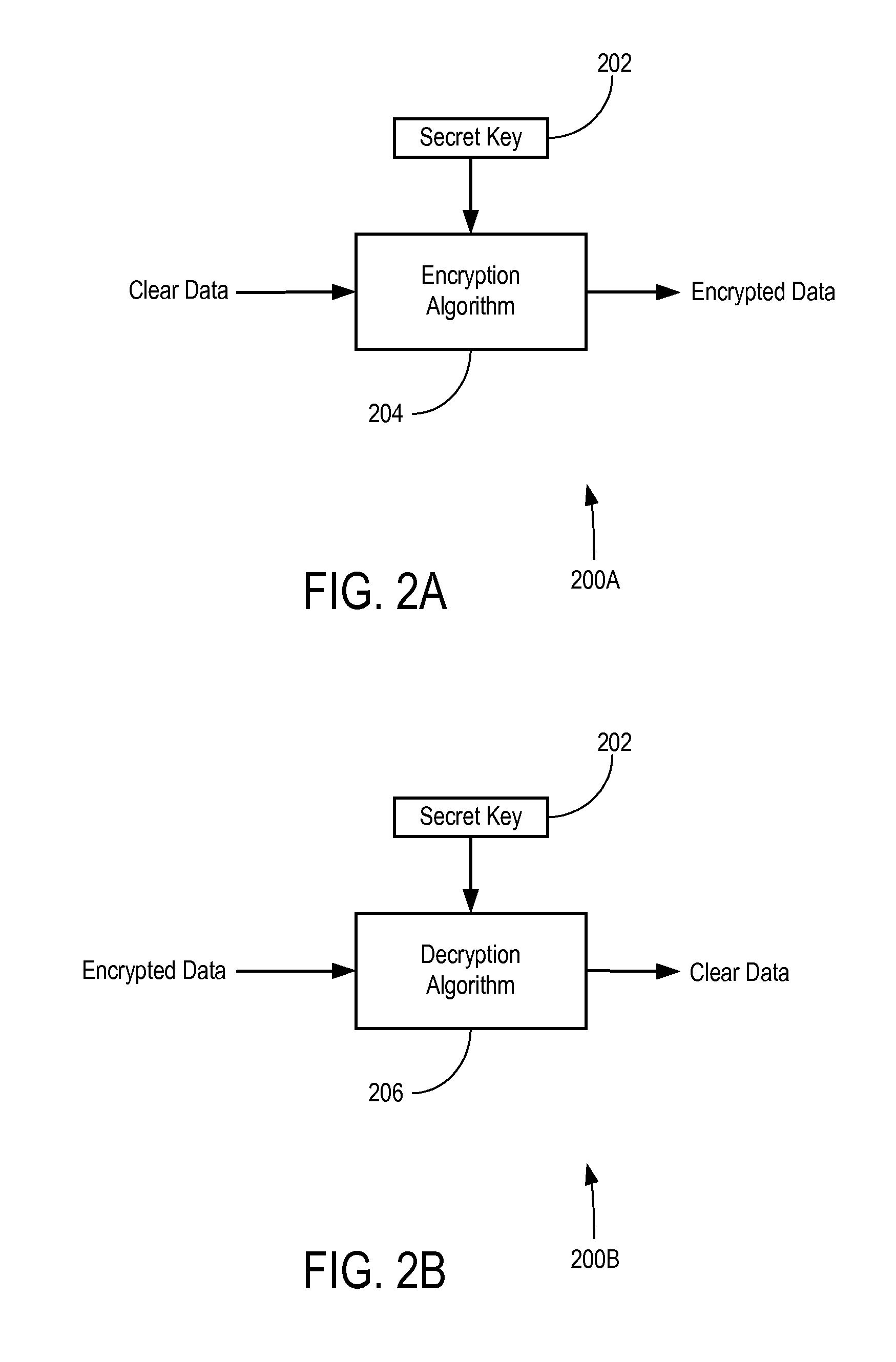
Verifiable encryption is an encryption scheme where one can prove some property of a message m, while the message is given in an encrypted form. When an encryption scheme is secure, the encryption E(m) should reveal no information regarding m.
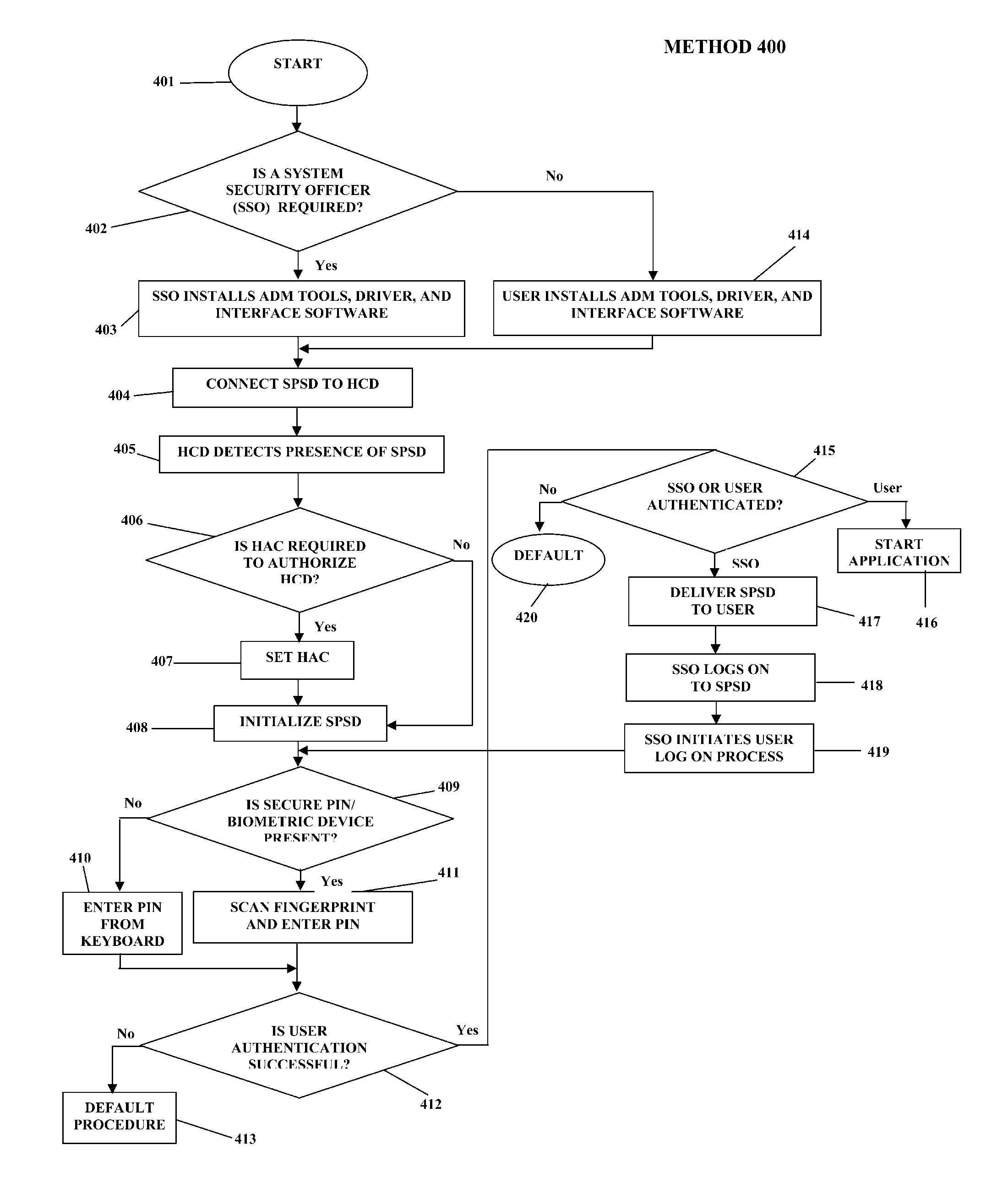
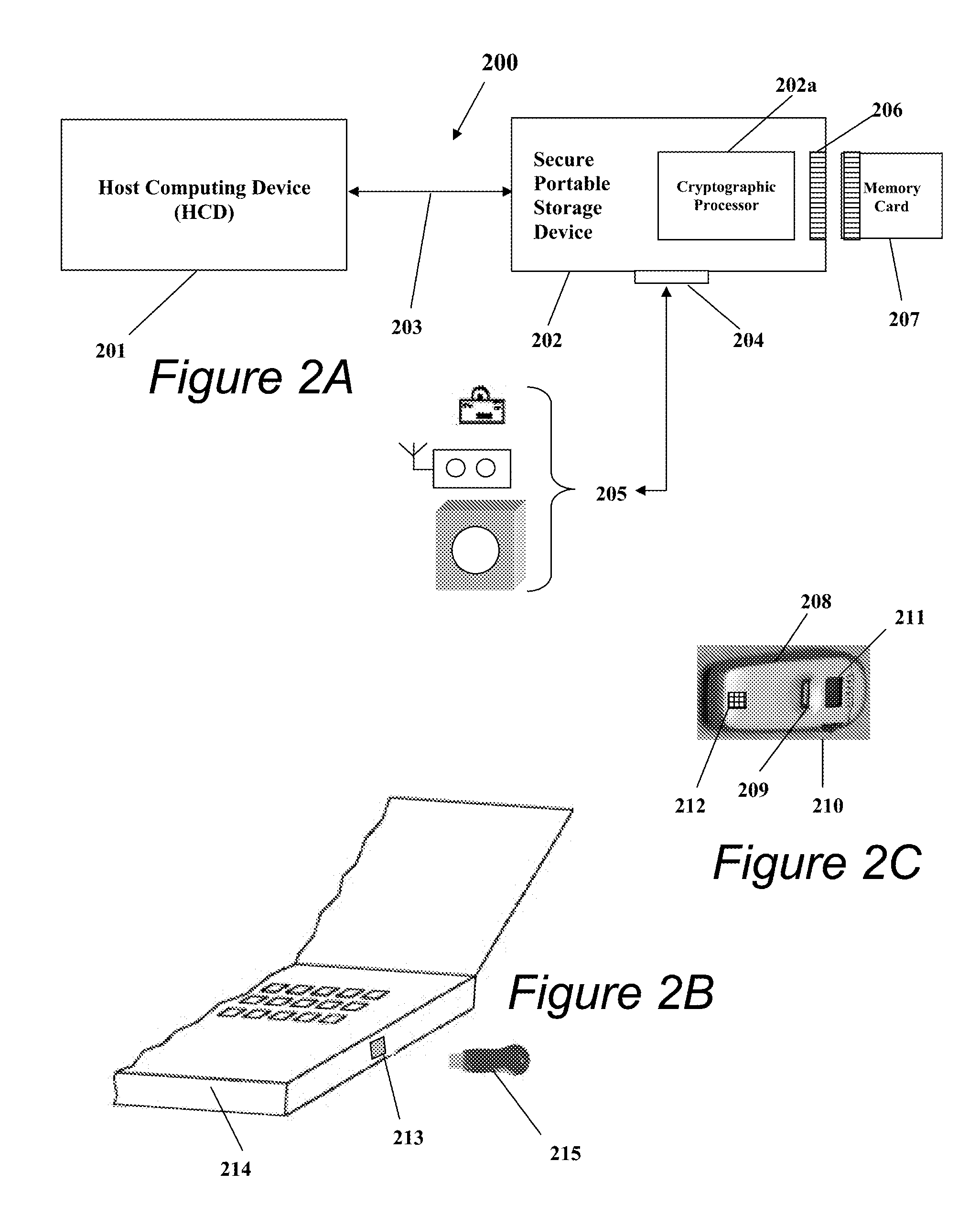
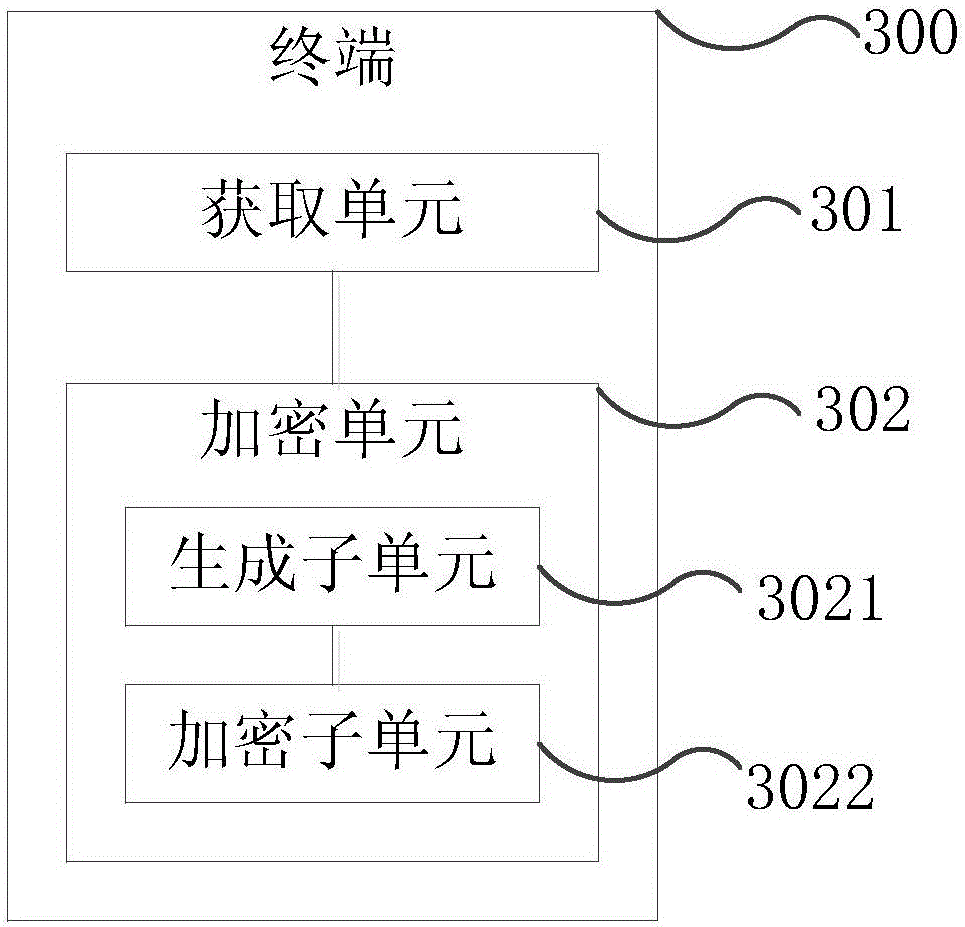
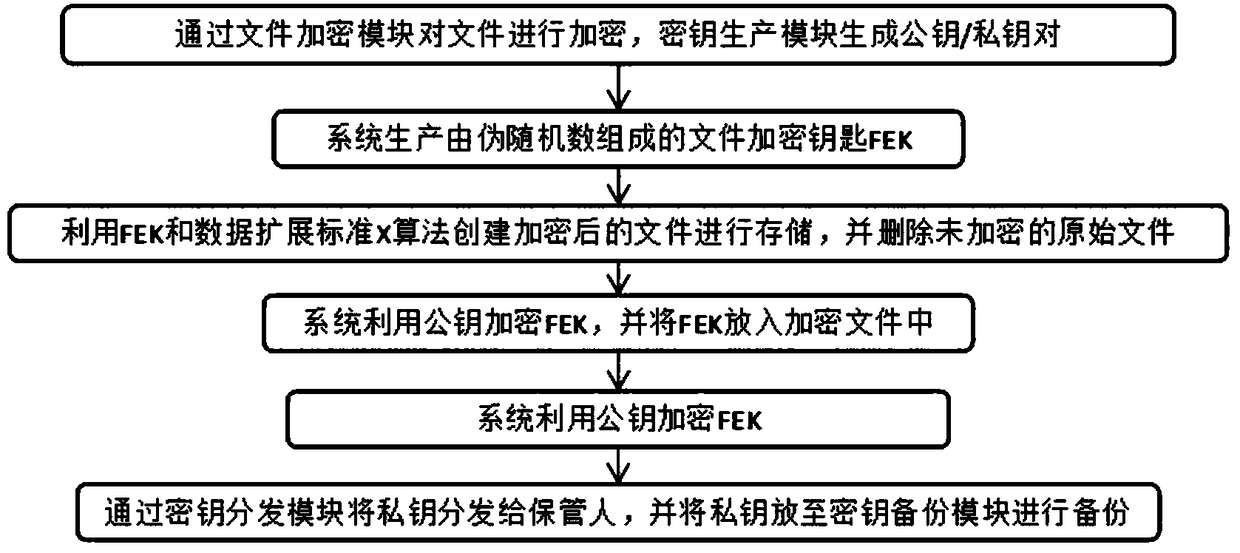
Portable data encryption device with configurable security functionality and method for file encryption
ActiveUS9049010B2Mitigates and eliminates vulnerabilityKey distribution for secure communicationUser identity/authority verificationPlaintextComputer hardware
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
Cryptographic encoding and decoding of secret data
InactiveUS20100142704A1Secret communicationSecuring communicationData processing systemVerifiable encryption
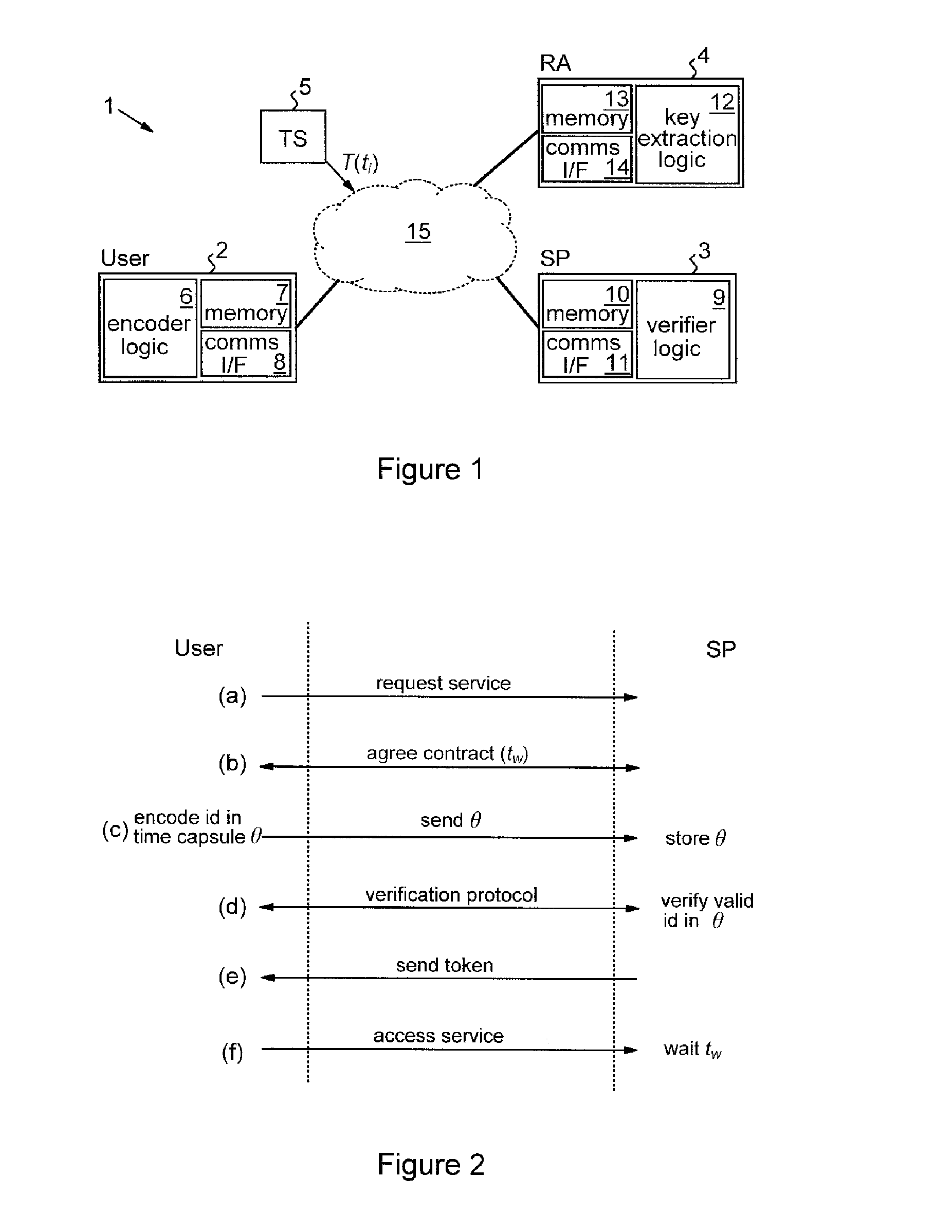
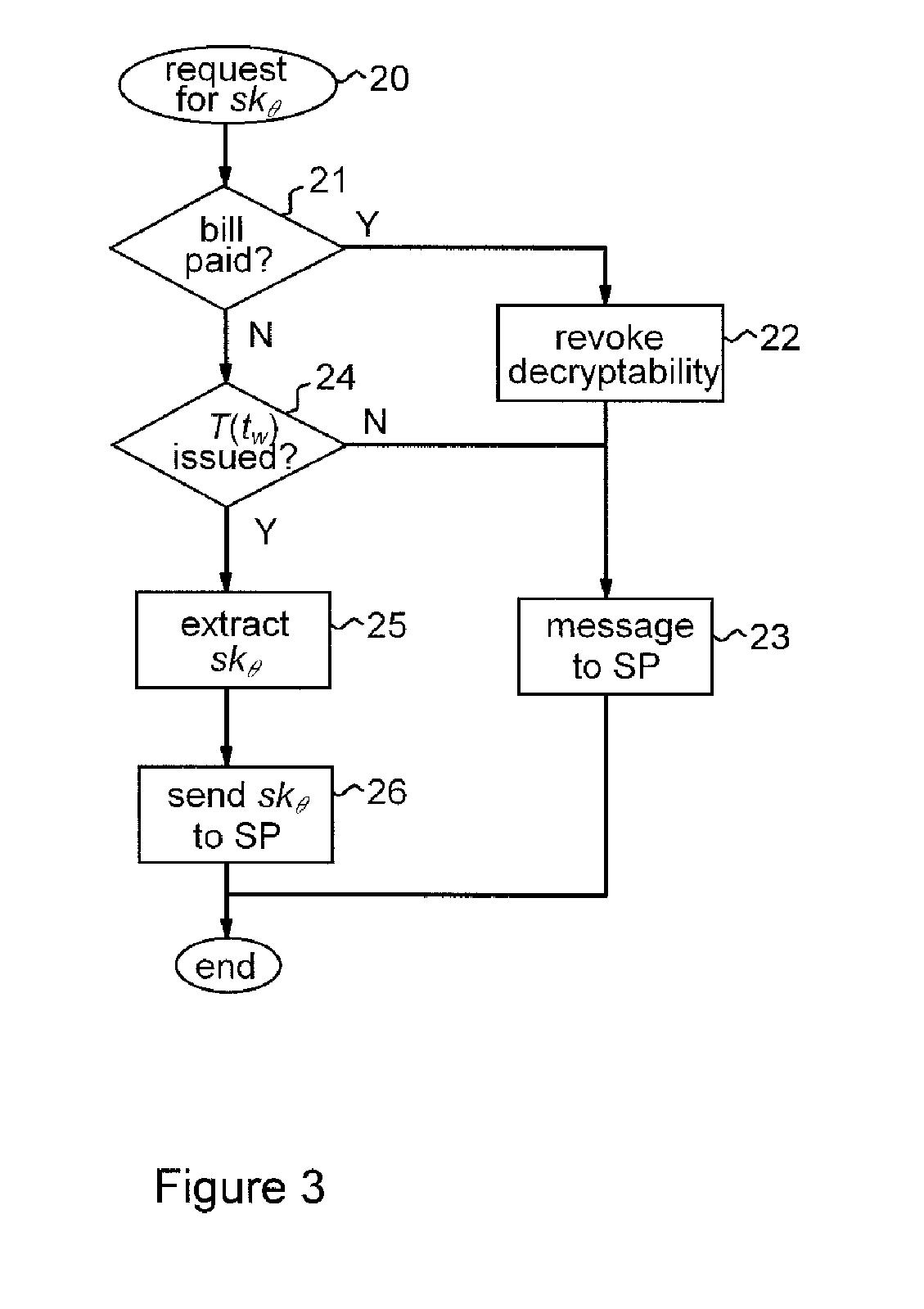
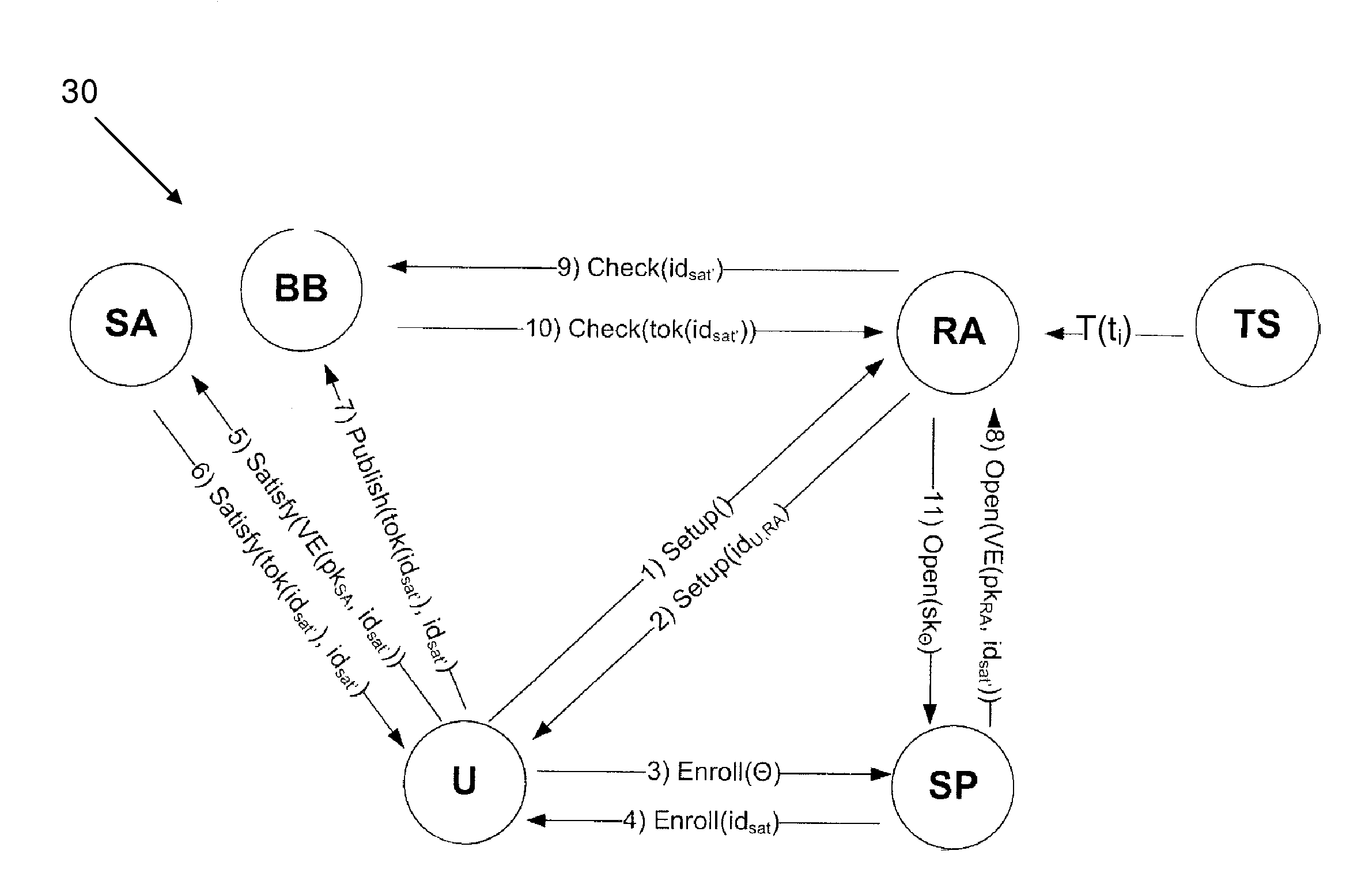
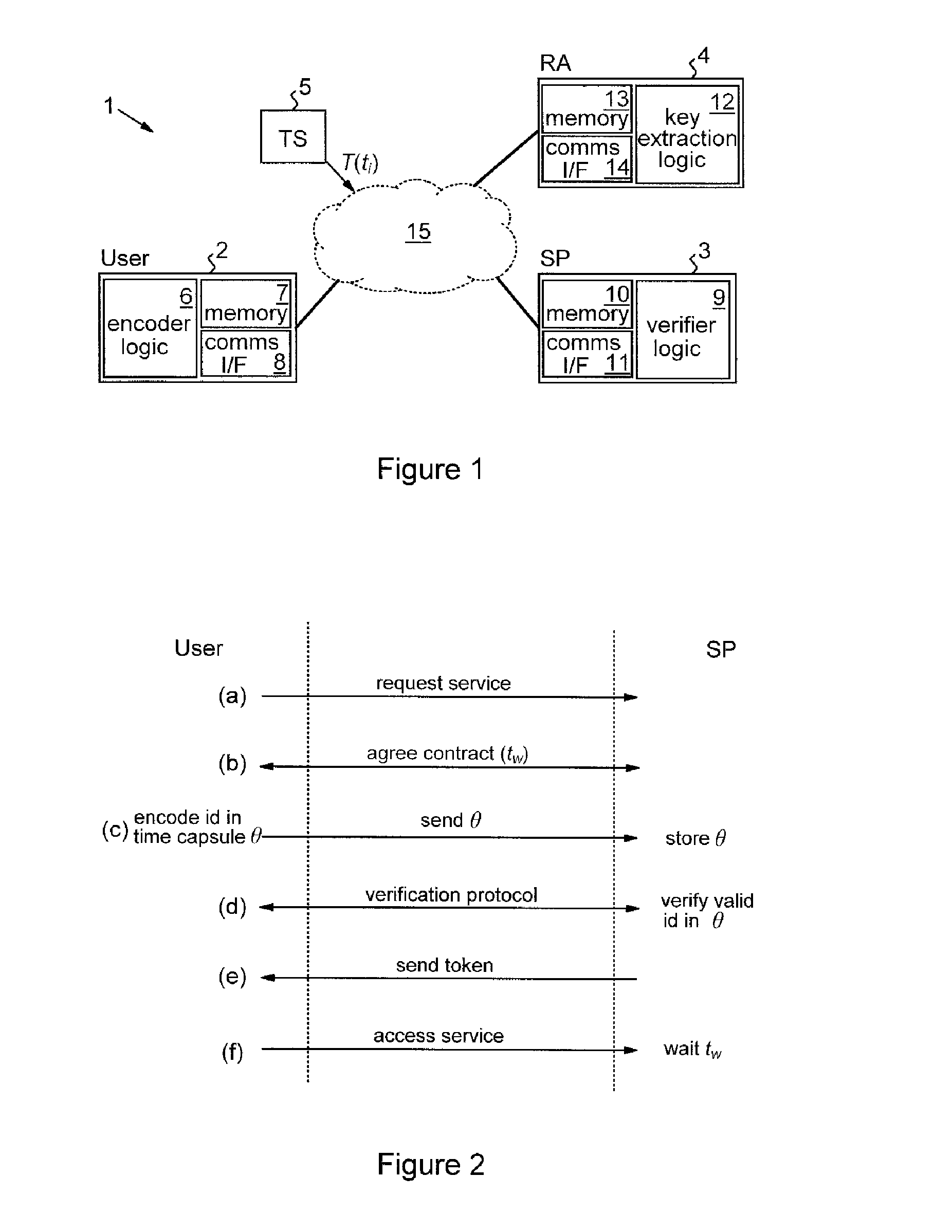
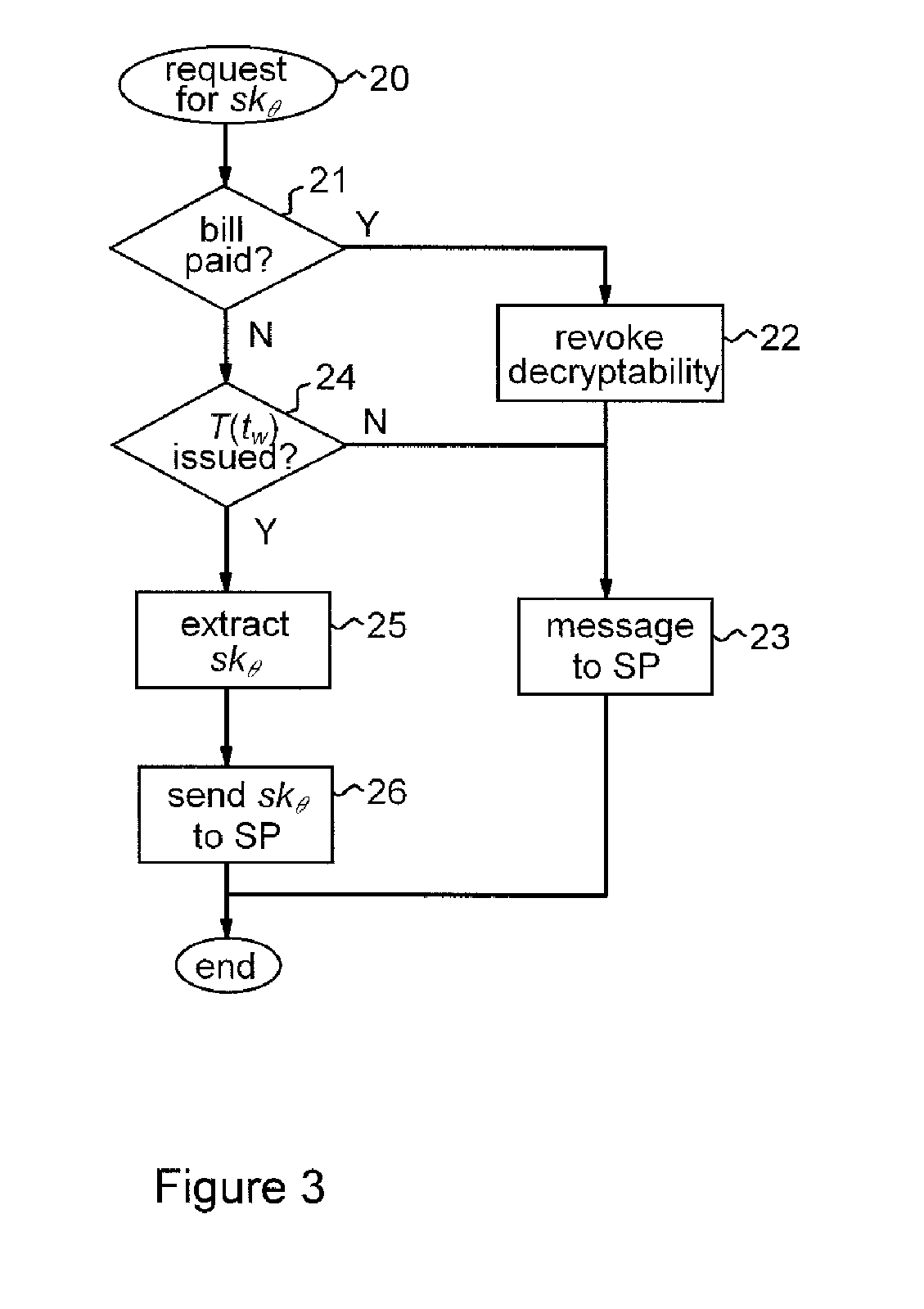
Methods and apparatus are provided for cryptographically encoding secret data in a data processing system. The secret data is encoded in accordance with a verifiable encryption process to produce a cryptographic construction (θ) having a decryption constraint dependent on the occurrence of a predetermined event. An event-dependent decryption constraint is thereby built into the cryptography, so that there is an intrinsic restriction on the ability to decrypt the encoded secret data which is dependent on occurrence of the predetermined event. Decoding apparatus for such a cryptographic construction is also provided, as well as distributed trust data processing systems providing accountable privacy based on use of such cryptographic constructions.
Owner:IBM CORP
System and method for file encryption and decryption
InactiveUS20080104417A1Public key for secure communicationUser identity/authority verificationData decryptionDisk encryption
There is disclosed a system and method for file encryption and decryption. In an embodiment, a method of encrypting a file on backup media involves encrypting clear data using a data encryption key applied to a data encryption algorithm and outputting encrypted data; storing the encrypted data on the backup media; encrypting the data encryption key using a reference cryptographic key applied to a key encryption algorithm and outputting an encrypted data encryption key; and storing the encrypted data encryption key and reconstitution data in a header of the backup media. The encrypted data may be subsequently decrypted by identifying the reference cryptographic key using the reference cryptographic key name; applying the reference cryptographic key to a key decryption algorithm to decrypt the encrypted data encryption key; and applying the decrypted data encryption key to a data decryption algorithm to decrypt the encrypted data.
Owner:IBM CORP
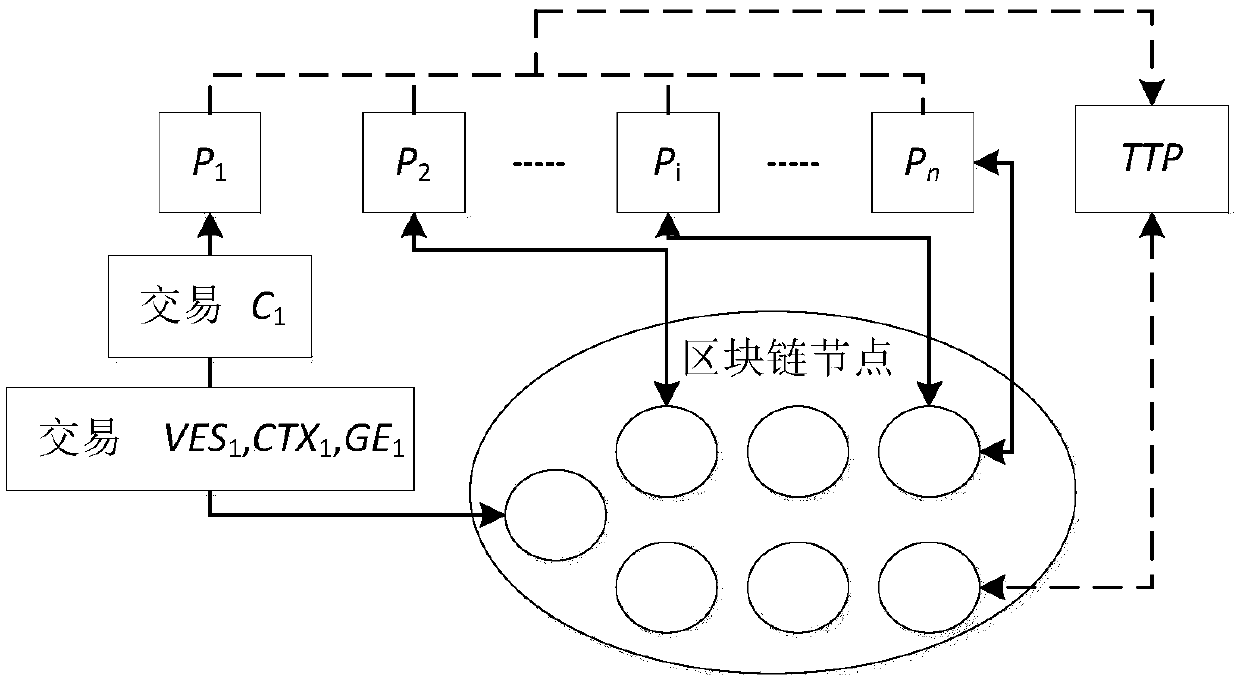
Multiparty fair PDF contract signing method based on block chain
ActiveCN108833115AKey distribution for secure communicationData processing applicationsDigital signatureCiphertext
The invention relates to a multiparty fair PDF contract signing method based on a block chain. Participants comprise a plurality of contract signers P<1>,... and P<n>, a trusted third party (TTP) andblock chain nodes. The method comprises the steps that the P<1> generates a verifiable encryption signature VES<1> of a contract, calculates a hash context CTX<1> of contract content, generates elements GE<1> of a group key negotiation agreement GKA, packages the VES<1>, the CTX<1> and the GE<1> into block chain transaction and sends the block chain transaction to any block chain node; a P verifies VES<i-1> of a P<i-1>, wherein the i is greater than 1 and is smaller than or equal to the n, after the verification is successful, the P generates a new VES, CTX and GE, and sends theVES, CTX and GE to any block chain node through transaction; after the P<n> finishes operation, a P<j> calculates a group encryption key GK, wherein the j is greater than or equal to 1 and is smaller than or equal to the n, the P<j> encrypts a digital signature of a PDF document to form a ciphertext C<j>, packages the C<j> into the transaction and sends the transaction to the block chainnode; the P<j> queries block chain data, decrypts the block chain data through utilization of the GK and then combines the block chain data into a complete PDF contract; and if the P<j> does not obtain the block chain data after the P<j> is overtime, the P<j> communicates with the TTP to process an exception. According to the method, the dependence on the TTP is relatively weak, and the efficiency is relatively high.
Owner:信睿吉科技(北京)有限公司
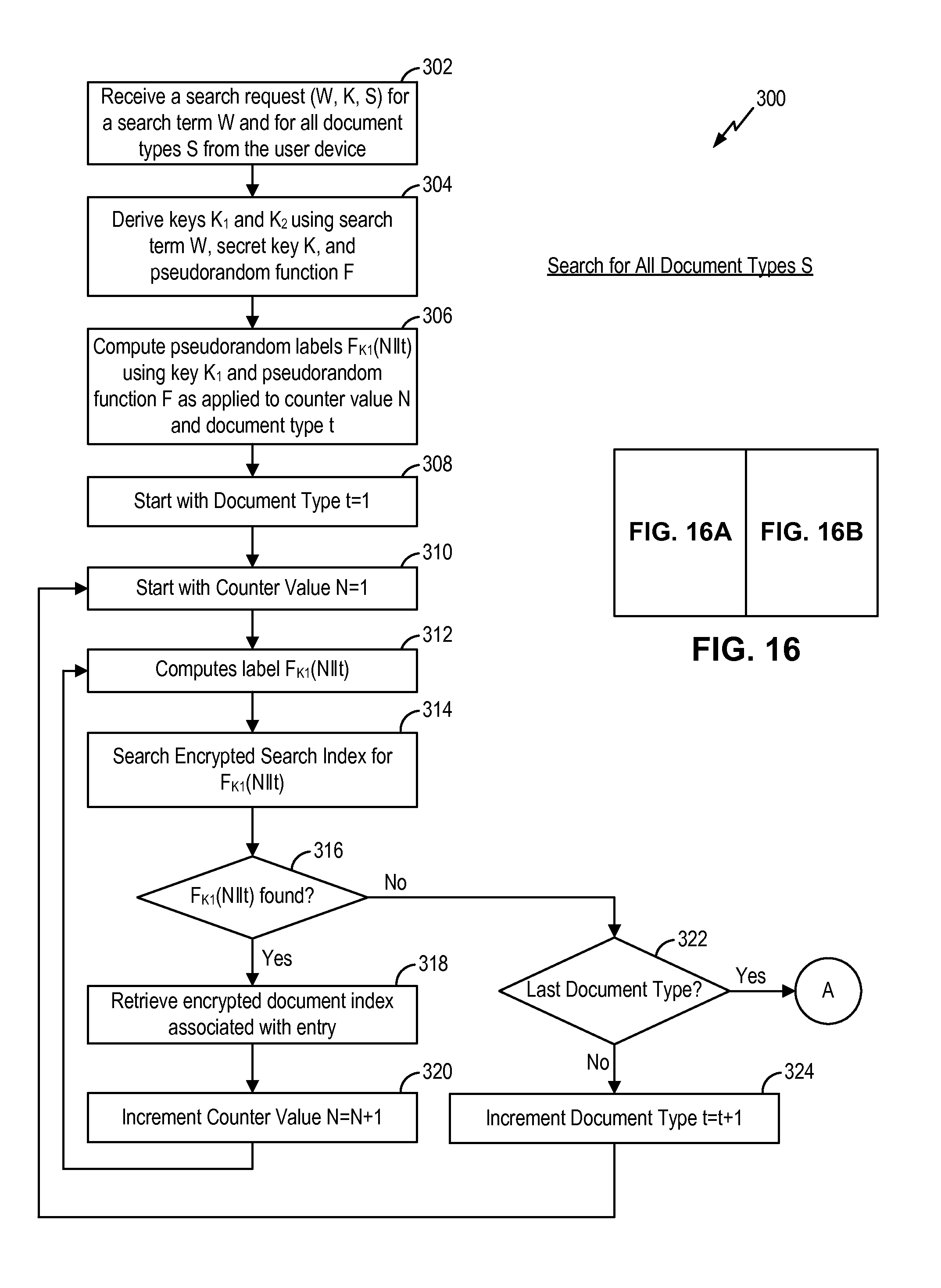
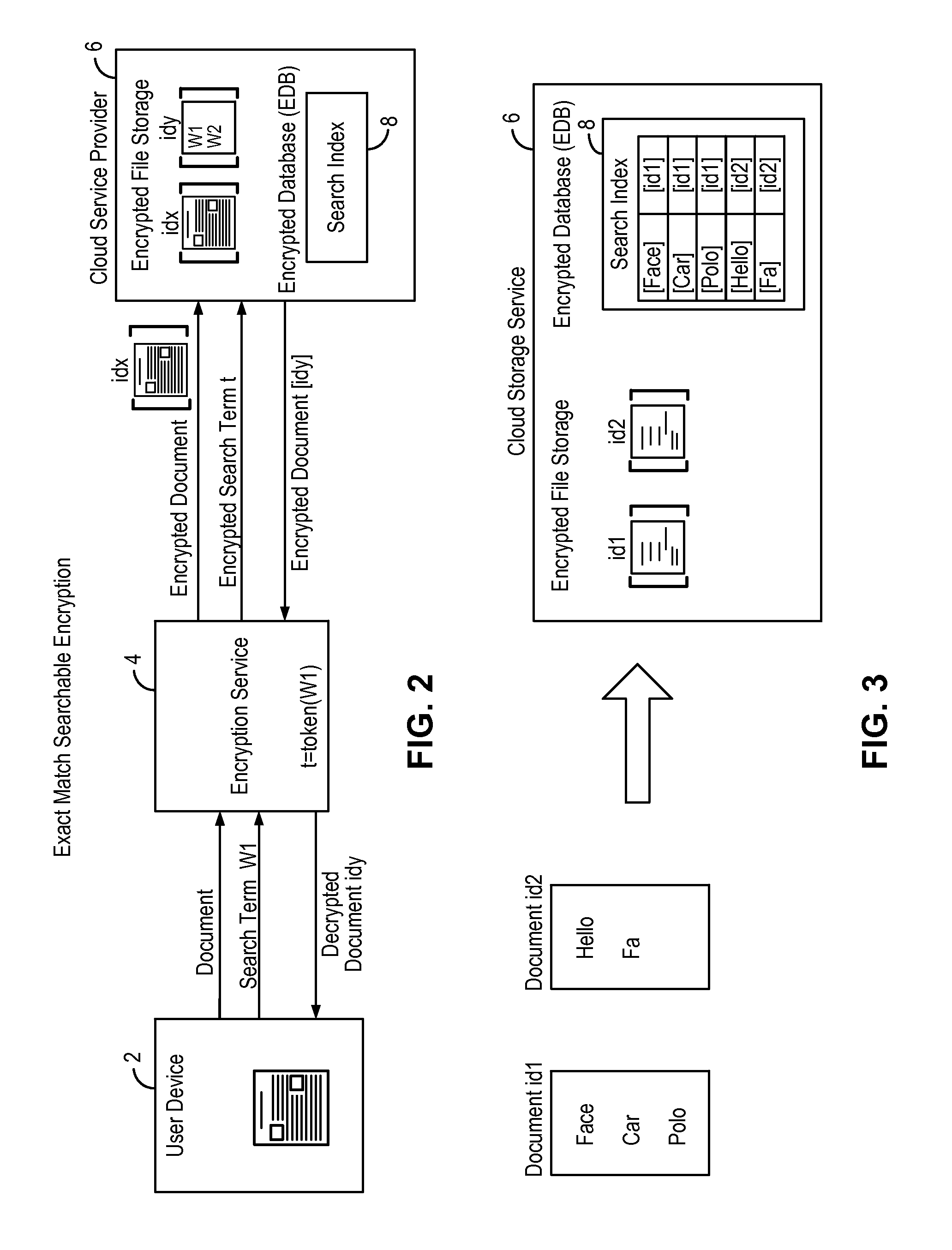
Searchable encryption enabling encrypted search based on document type
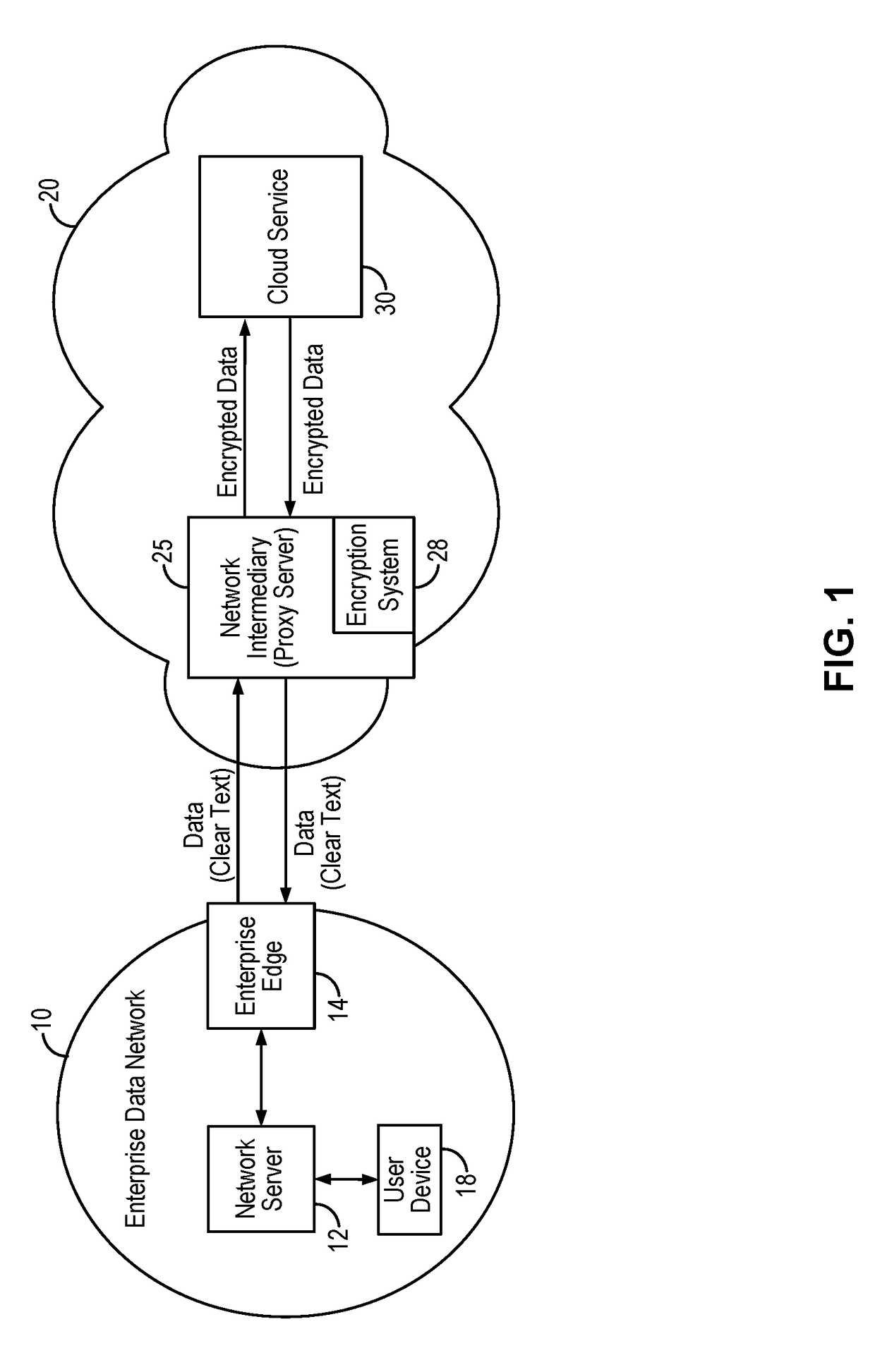
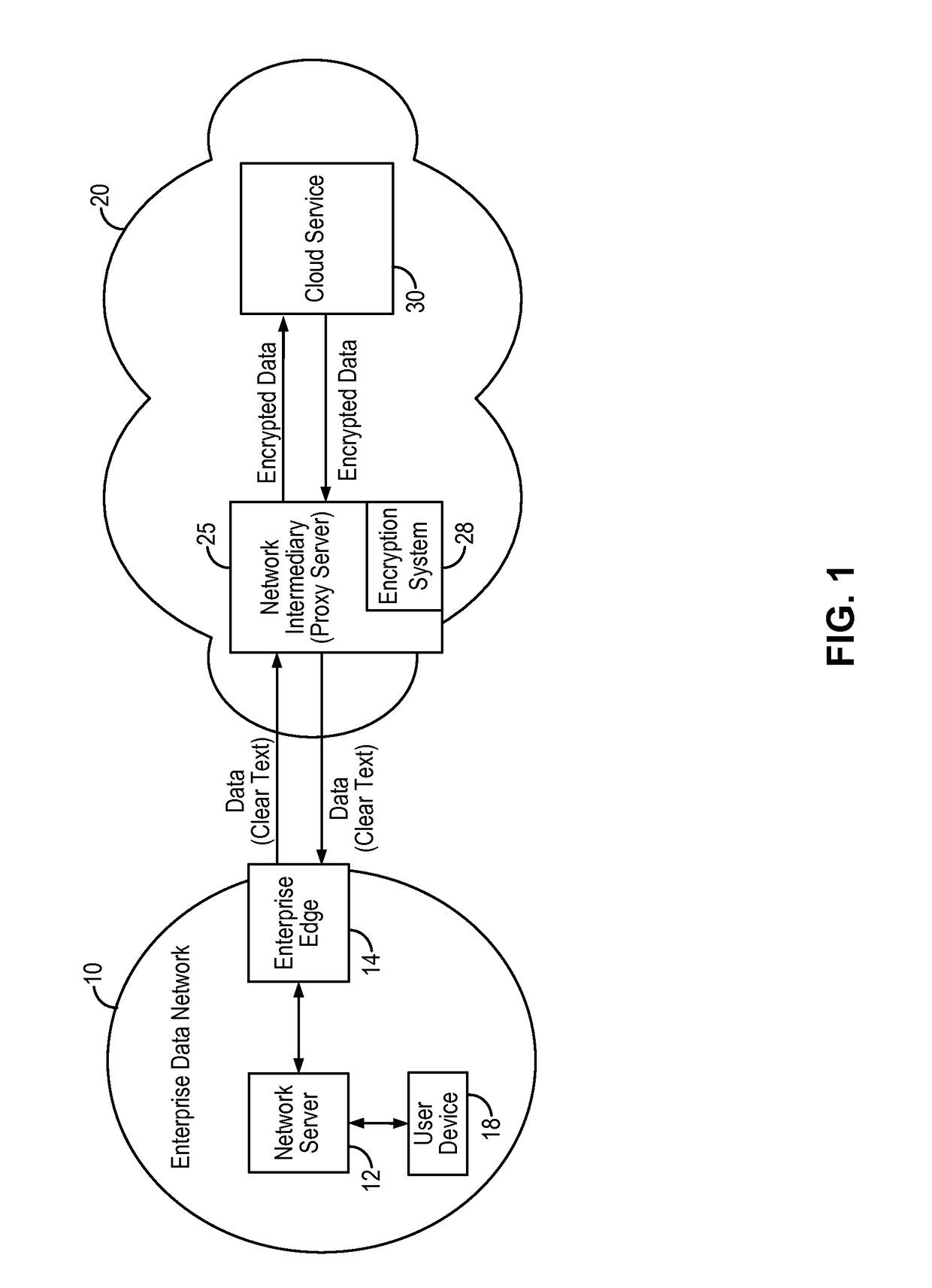
ActiveUS20170026350A1Computer security arrangementsSpecial data processing applicationsProxy serverDocumentation
A searchable encryption method enables encrypted search of encrypted documents based on document type. In some embodiments, the searchable encryption method is implemented in a network intermediary, such as a proxy server. The network intermediary encrypts documents on behalf of a user or an enterprise destined to be stored on a cloud service provider. The searchable encryption method encodes document type information into the encrypted search index while preserving encryption security. Furthermore, the searchable encryption method enables search of encrypted documents using the same encrypted index, either for a particular document type or for all encrypted documents regardless of the document type.
Owner:SKYHIGH SECURITY LLC
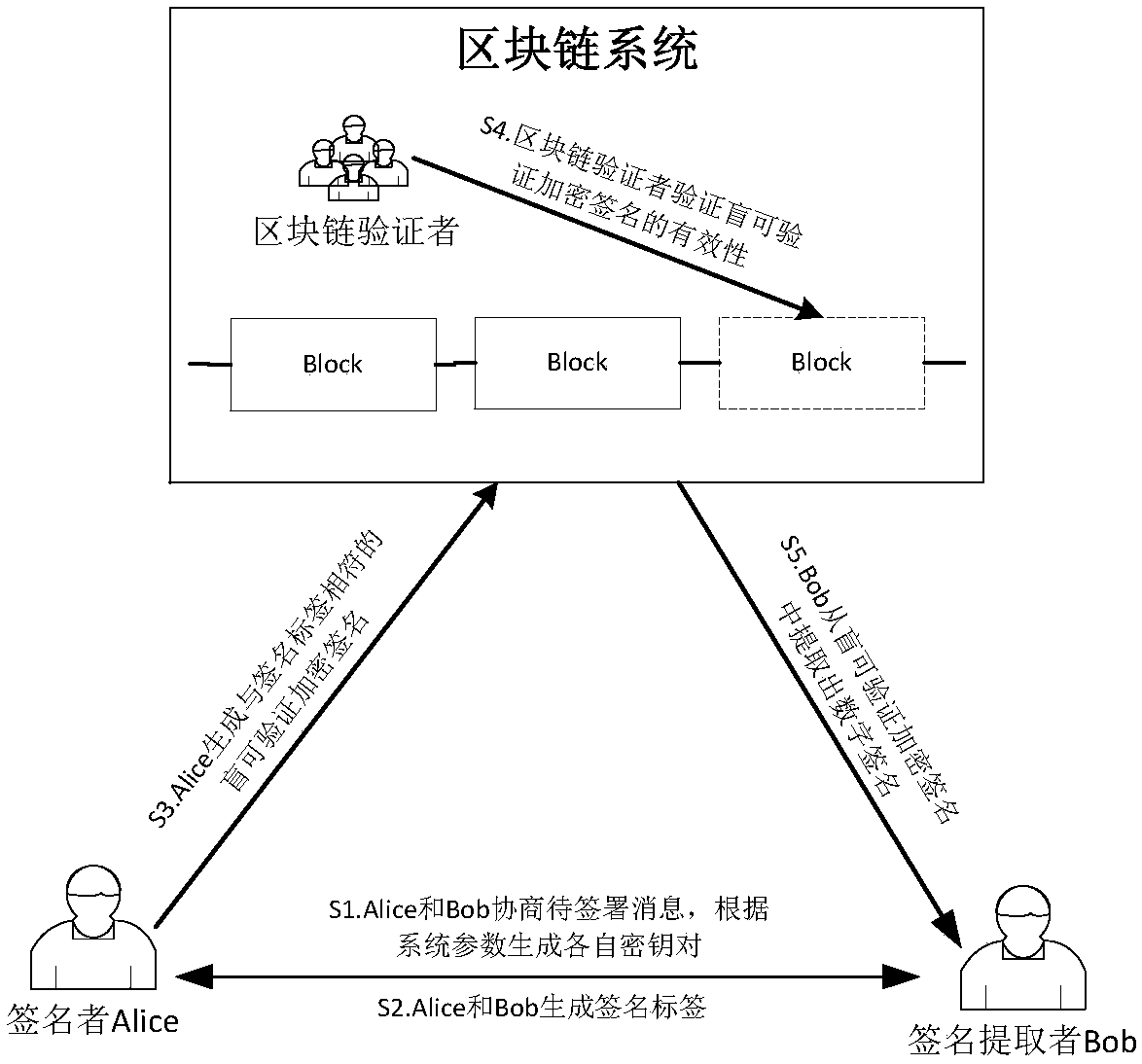
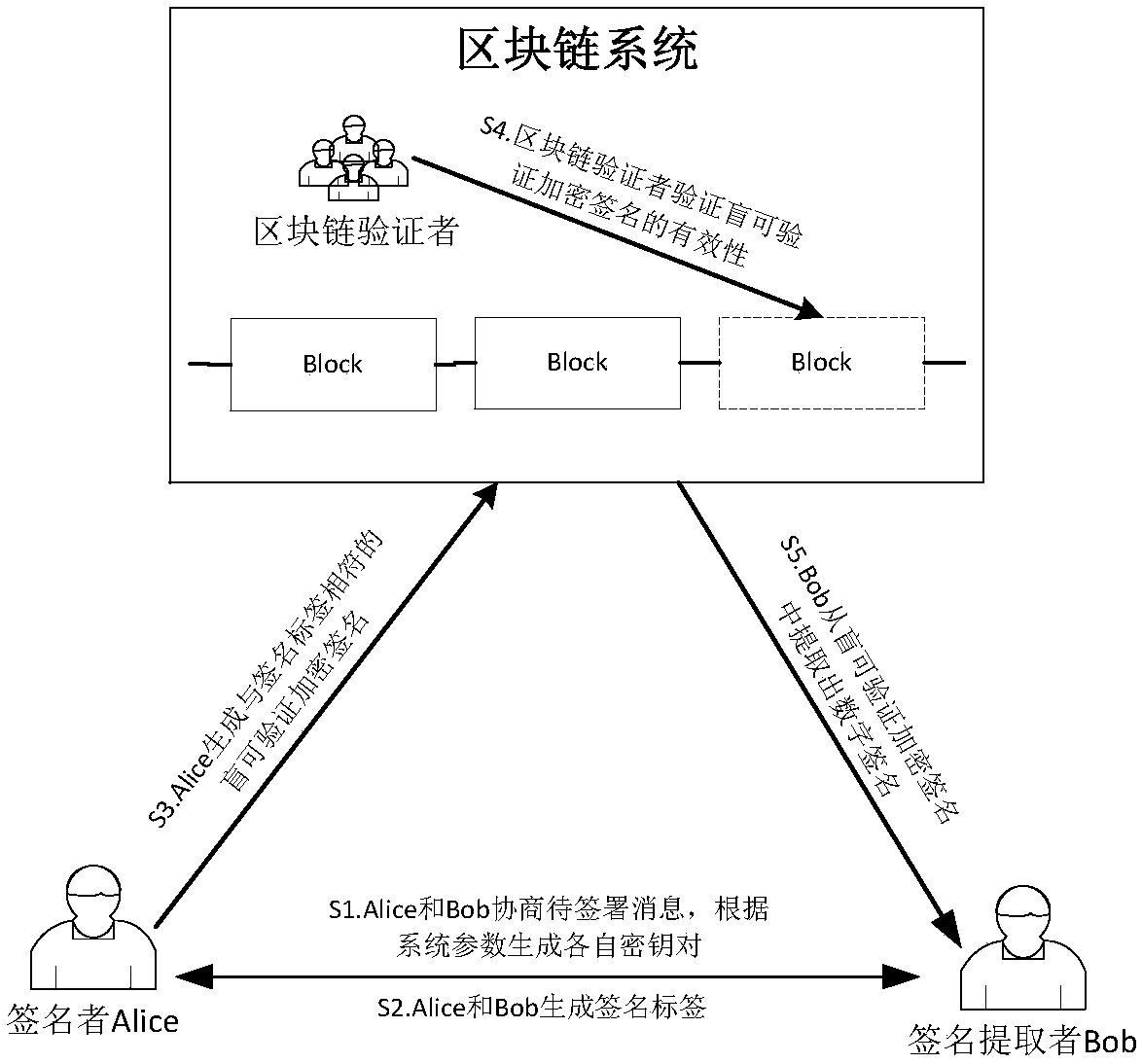
Blind verifiable cryptographic signature method based on block chain
InactiveCN107040383APrivacy protectionPublic key for secure communicationUser identity/authority verificationAlice and BobDigital signature
The invention relates to a blind verifiable cryptographic signature method based on a block chain. The method includes three parties: a signer Alice, a signature extractor Bob, and a block chain verifier. The method is implemented in the following steps: Alice and Bob negotiate a message to be signed and generate their own key pairs respectively according to system parameters; Alice and Bob generate signature tags; Alice generates a blind verifiable cryptographic signature that matches the signature tag; the block chain verifier verifies the validity of the cryptographic verifiable cryptographic signature; and Bob extracts a digital signature from the blind verifiable cryptographic signature. The method can be used to construct a fair digital signature exchange protocol that protects privacy in a public block chain environment. The method blindens the public key information of the signer so that a node on a block chain cannot obtain the real digital signature and the public key of the signer aside from verifying the validity of the signature, and the privacy protection for the signer is achieved.
Owner:深圳市数峰科技有限公司
Verification method for operation of encryption apparatus and its application to electronic voting
InactiveUS20080059791A1Increase probabilitySimple methodVoting apparatusError detection/correctionPlaintextValidation methods
A verification method for encrypter operation and an electronic voting verification system using the same, which can verify the operation of the encrypter without having to execute corresponding decryption. In the verification method, the encrypter creates a plurality of ciphertexts corresponding to the plain text and presenting the ciphertexts to a user. The user selects one of the ciphertexts, the encrypter dispenses a certificate where information used by the encrypter during encryption is recorded, in response to the ciphertexts which are not selected by the user; and the user creates a ciphertext in person and verifies whether or not the user-created ciphertext is identical with the user-selected ciphertext. Then, the user can verify the encryption results inside and outside a polling booth.
Owner:RES & BUSINESS FOUND SUNGKYUNKWAN UNIV
Searchable encryption enabling encrypted search based on document type
ActiveUS20180124026A1Computer security arrangementsSpecial data processing applicationsDocument Type CodeDocumentation
A searchable encryption method enables encrypted search of encrypted documents based on document type. In some embodiments, the searchable encryption method is implemented in a network intermediary, such as a proxy server. The network intermediary encrypts documents on behalf of a user or an enterprise destined to be stored on a cloud service provider. The searchable encryption method encodes document type information into the encrypted search index while preserving encryption security. Furthermore, the searchable encryption method enables search of encrypted documents using the same encrypted index, either for a particular document type or for all encrypted documents regardless of the document type.
Owner:SKYHIGH SECURITY LLC
A fair contract signing method with privacy protection based on a block chain
ActiveCN109815728AReduce riskFair Contract Signing AgreementDigital data protectionElectronic contractsRing signature
The invention discloses a fair contract signing method with privacy protection based on a block chain. Conventional electronic contract signing needs to use a centralized trusted third party to coordinate the signature process. However, a single-point fault is easy to occur in centralization, and sensitive information is leaked due to internal or external attacks. The blockchain may implement decentration. However, although an existing contract signing protocol based on the block chain can achieve fair contract signing and hide contract content and a digital signature of a contract, the identity of a signer cannot be completely hidden, and a transaction initiator can still be traced through a signing script of the block chain transaction. The identity of a signer is protected to the maximum extent. The identity of the participant is confused by using a disposable ring signature technology, and a stronger privacy protection fair contract signing protocol is designed in combination witha blind verifiable encryption signature scheme, so that a plurality of signers complete fair contract signing, contract content hiding, digital signature and identity information of the signers through a block chain.
Owner:JINAN UNIVERSITY
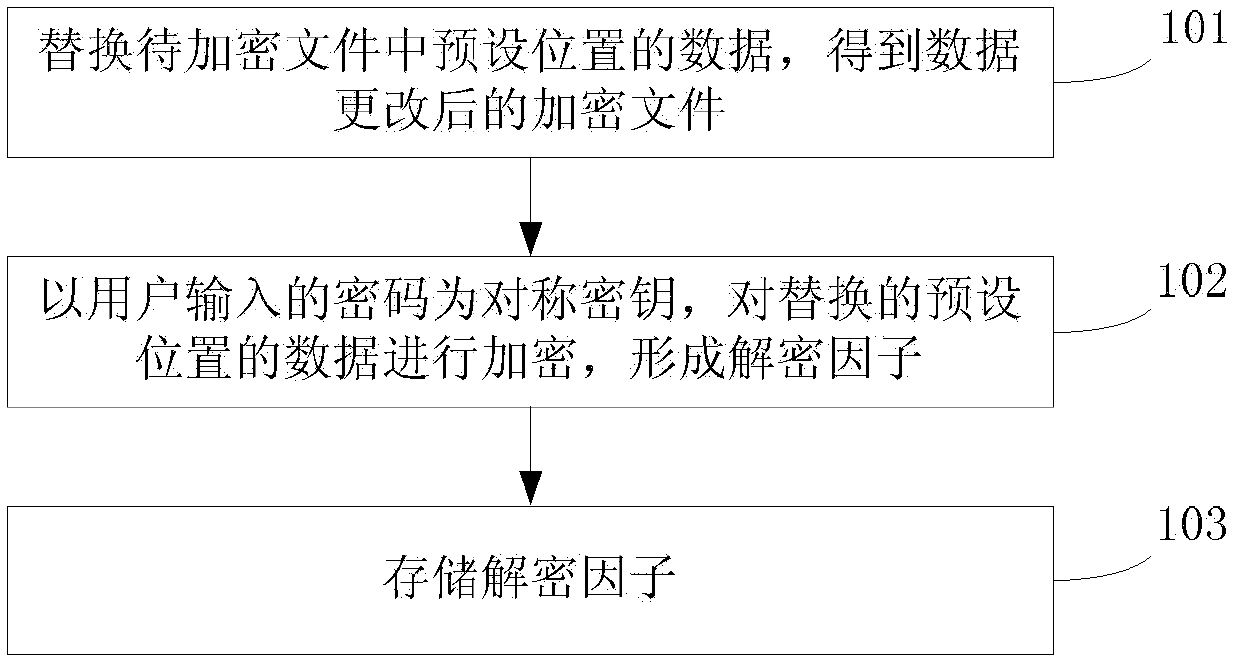
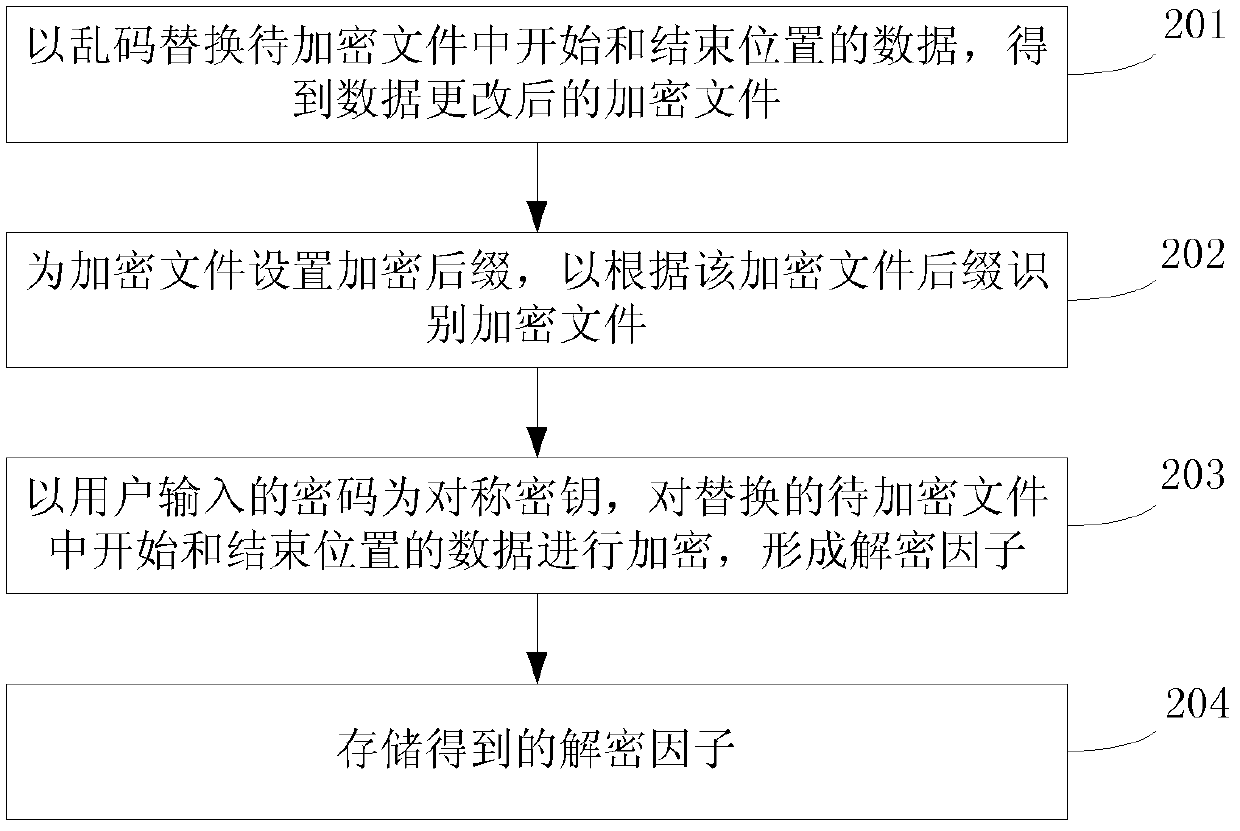
File encryption and decryption method and device
ActiveCN103377347AReduce processing timeImprove processing efficiencyDigital data protectionComputer hardwareUser input
The invention discloses a file encryption and decryption method and device and belongs to the technical field of data processing. The file encryption method comprises the steps of replacing data at a preset position in a to-be-encrypted file, and obtaining an encryption file with data modified; enabling a password input by a user to serve as a symmetric key to encrypt the replaced data at the preset position, and forming a decryption factor; and storing the decryption factor. The file decryption method comprises the steps of obtaining the password input by the user and the decryption factor corresponding to the encryption file; decrypting the decryption factor according to the password input by the user, and obtaining decrypted data; and replacing the data at the currently preset position of the encryption file with the decrypted data to obtain the decrypted file. By replacing the data at the preset position of the file and only performing encryption and decryption treatment on the data at the preset position, compared with encryption and decryption treatment on a whole file in the prior art, the file encryption and decryption method and device can effectively reduce treatment time and improve treatment efficiency.
Owner:TENCENT TECH (SHENZHEN) CO LTD
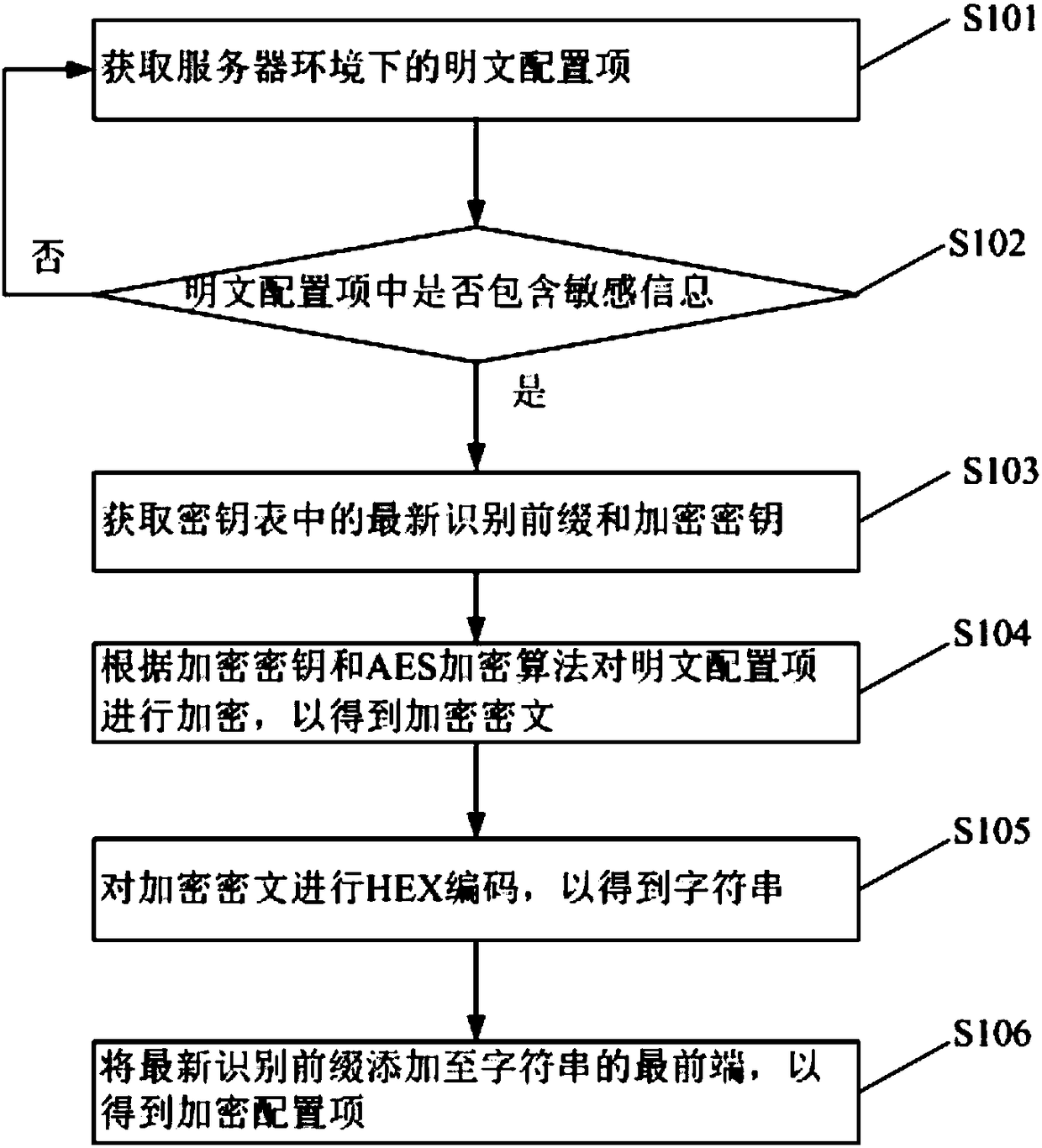
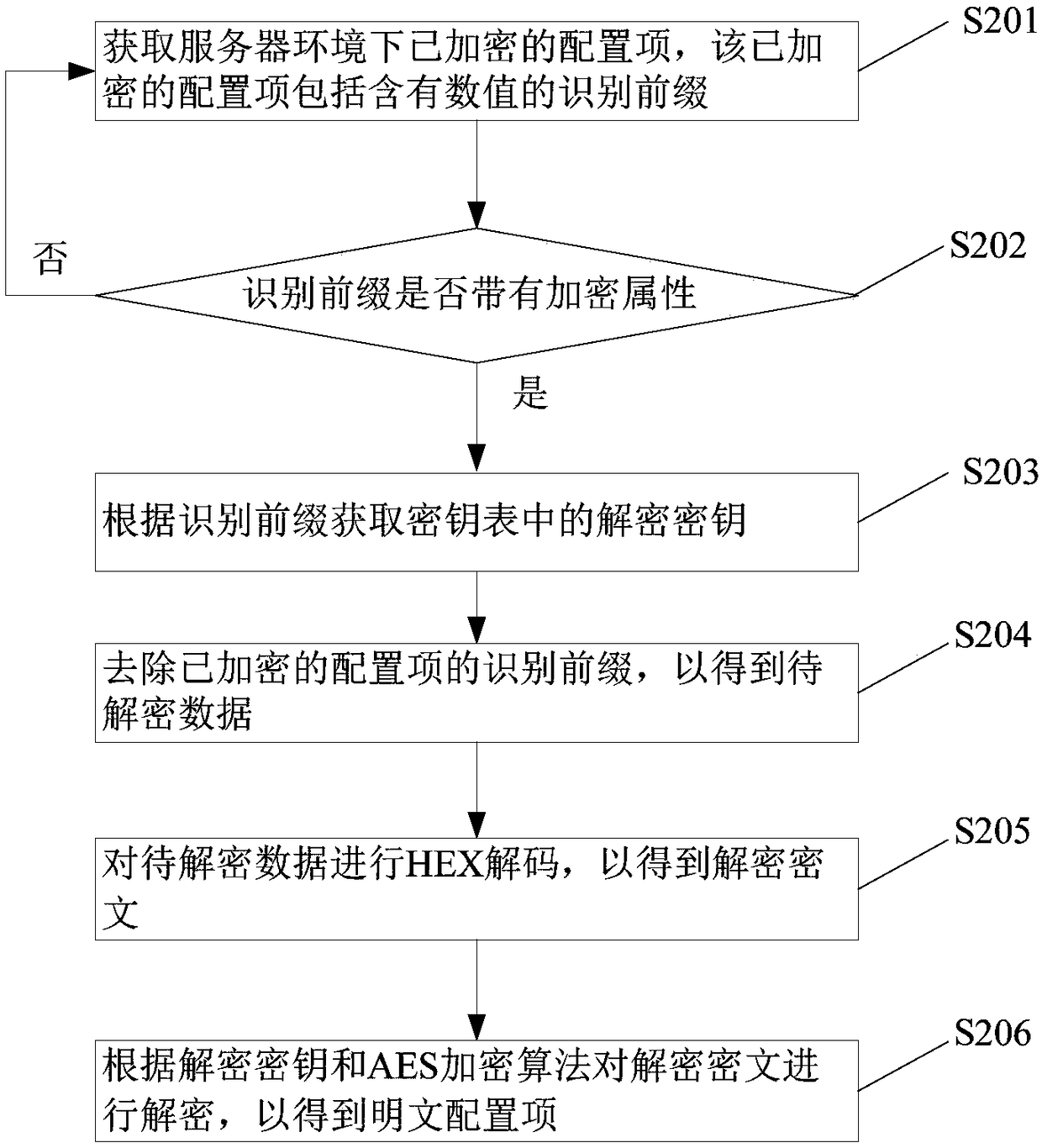
File encryption and decryption method and device, processing terminal and computer readable storage medium
ActiveCN108280356AFulfil requirementsFlexible configurationDigital data protectionPlaintextConfiguration item
The embodiment of the invention discloses a file encryption and decryption method and device, a processing terminal and a computer readable storage medium. The encryption method comprises the steps that a plaintext configuration item under a server environment is obtained; if the plaintext configuration item comprises sensitive information, a latest recognition prefix and an encryption key in an encryption key table are obtained; the plaintext configuration item is encrypted according to the encryption key and an AES encryption algorithm, and encryption ciphertext is obtained; according to theencryption ciphertext and the latest recognition prefix, the encryption configuration item is obtained. Accordingly, in the encryption process, the encryption item is flexibly configured according tothe encryption key table, and the user requirements are met; in the decryption process, the decryption process is implemented rapidly and easily according to the encryption key table.
Owner:吉浦斯信息咨询(深圳)有限公司
Certificateless verifiable encrypted signature method with forward security
InactiveCN104780047AResistant to Substitution AttacksHigh degree of associationUser identity/authority verificationHash functionTimestamp
The invention provides a certificateless verifiable encrypted signature method with forward security, and belongs to the technical field of computer network and information security. According to the method, the timestamp is embedded into secret values of a certificateless signature algorithm, secret values which are not used is safely deleted, and signature key evolution and digital signature are really combined; a traditional certificateless signature algorithm sequence is changed, the set secrete values are generated before part of private keys are generated, meanwhile, public keys are bound to a Hash function, the parameter correlation degree in the signature algorithm is increased, and two types of enemy attacks of the certificateless environment are resisted; a generated verifiable encrypted signature comprises the user secret values and has the forward security; the computation burden of a signature scheme is small, the signature is short, and the whole performance is advantageous. The certificateless verifiable encrypted signature method with the forward security has very high security and fairness.
Owner:NANJING UNIV OF POSTS & TELECOMM
Cryptographic encoding and decoding of secret data
InactiveUS8744077B2Secret communicationSecuring communicationData processing systemVerifiable encryption
Methods and apparatus are provided for cryptographically encoding secret data in a data processing system. The secret data is encoded in accordance with a verifiable encryption process to produce a cryptographic construction (θ) having a decryption constraint dependent on the occurrence of a predetermined event. An event-dependent decryption constraint is thereby built into the cryptography, so that there is an intrinsic restriction on the ability to decrypt the encoded secret data which is dependent on occurrence of the predetermined event. Decoding apparatus for such a cryptographic construction is also provided, as well as distributed trust data processing systems providing accountable privacy based on use of such cryptographic constructions.
Owner:IBM CORP
Credible encryption system and method
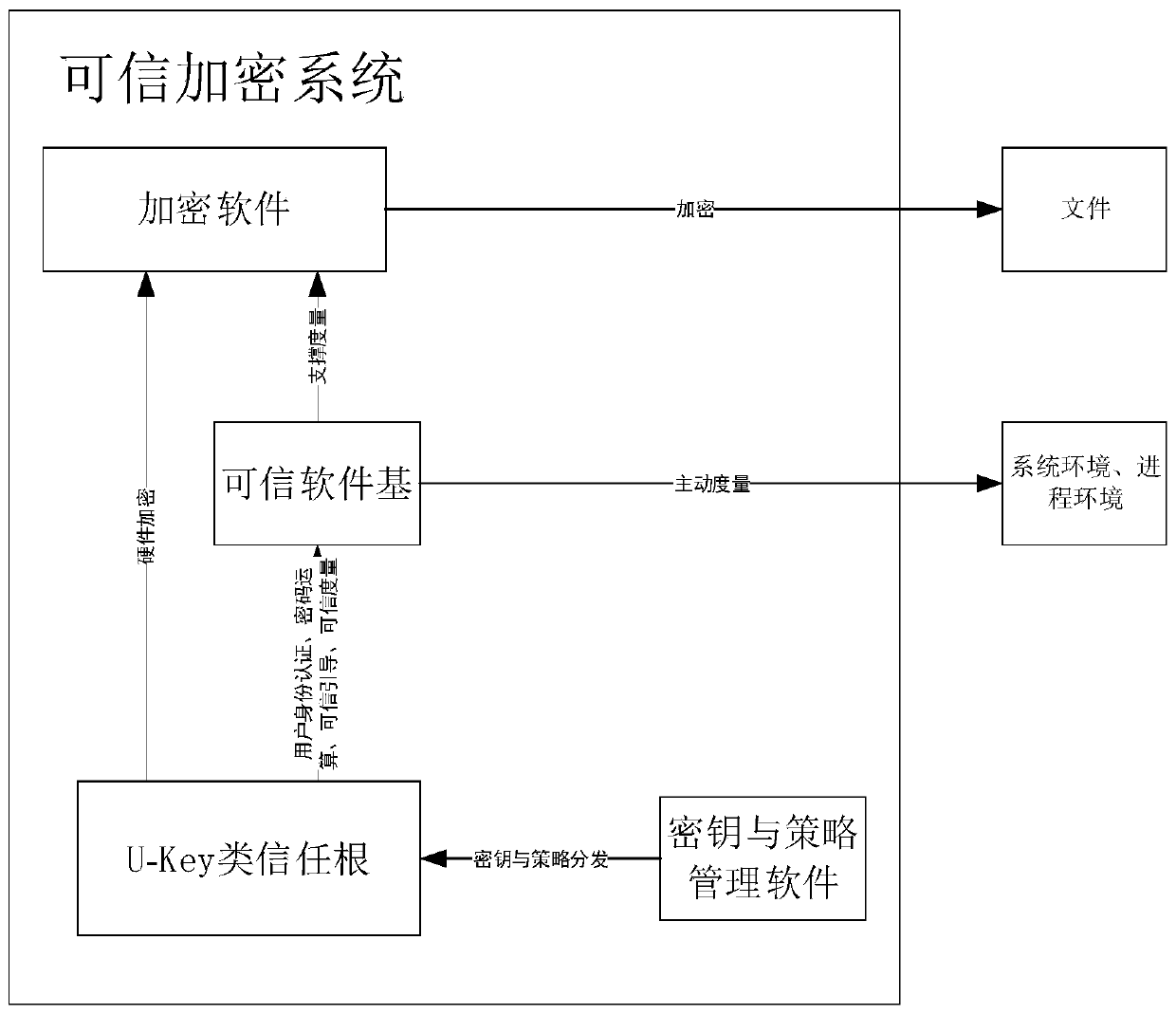
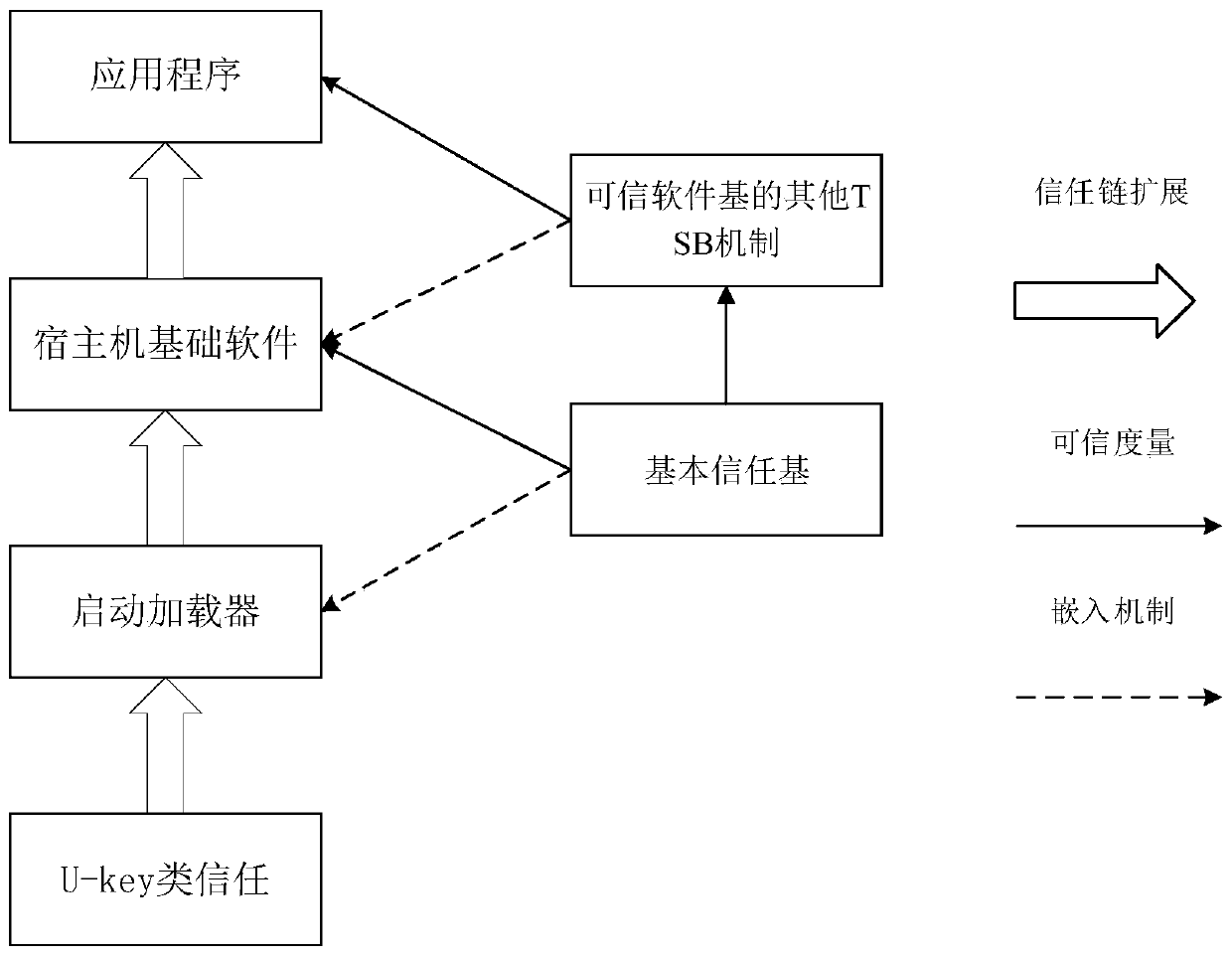
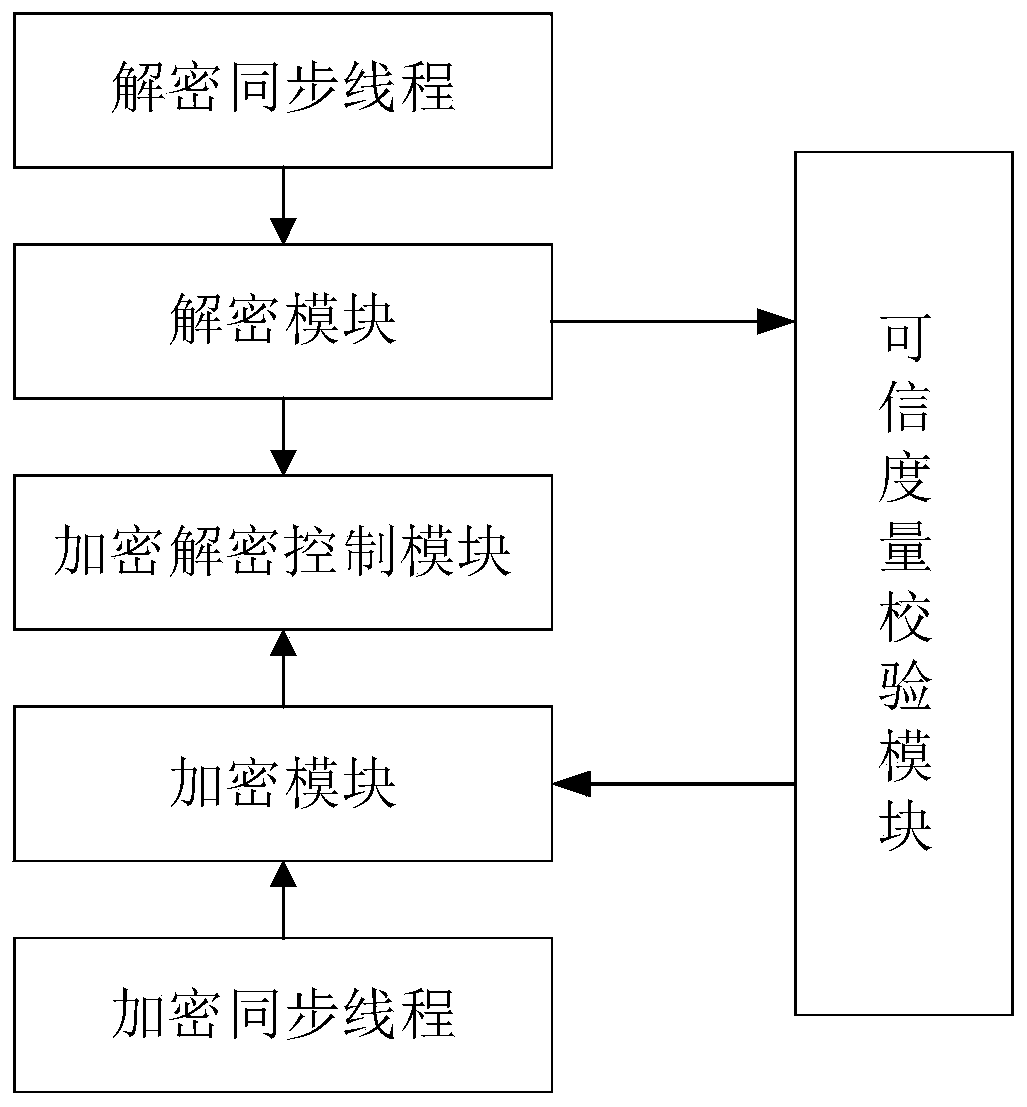
ActiveCN110188547AEnsure safetyDigital data protectionDigital data authenticationPlaintextTrusted Computing
The invention discloses a credible encryption system and method. The credible encryption system comprises a credible computing platform and a U-Key type trust root, the U-Key type trust root serves asa trust chain starting point of the credible computing platform and is used for supporting the credibility measurement work and the encryption and decryption work of the credible computing platform,and the trusted computing platform comprises a trusted software base and an encryption software. According to the credible encryption system and method provided by the invention, the security of dataduring the encryption and decryption process is ensured by adopting an active immune mechanism; the working security of the encryption software can be ensured; the security policy can be stored in theU-key type trust root, the U-key type trust root provides a secure storage area for secure storage, and the security protection of the virtual disk is provided for the encrypted plaintext, so that the security of the data during the encryption and decryption process can be ensured.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
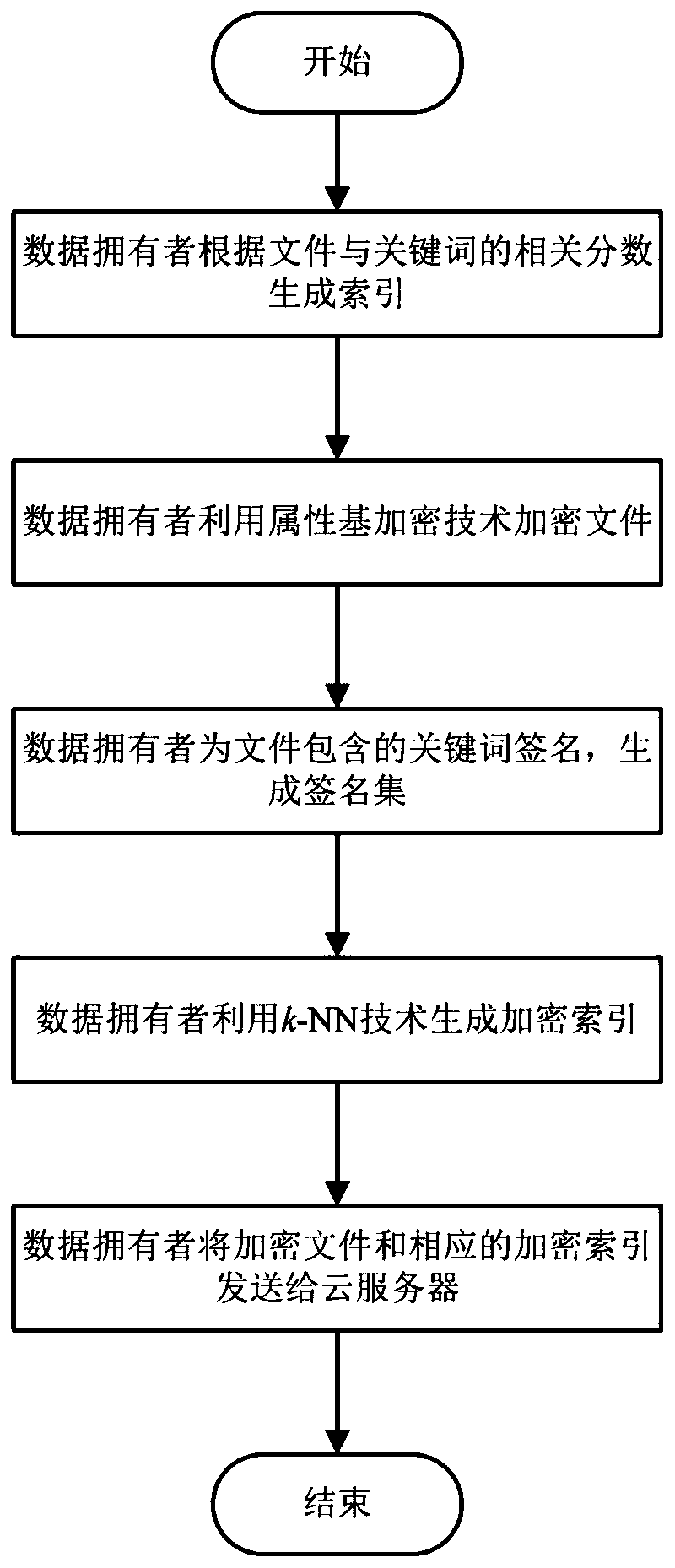
Verifiable encryption and decryption method supporting multi-keyword weighted retrieval and result sorting
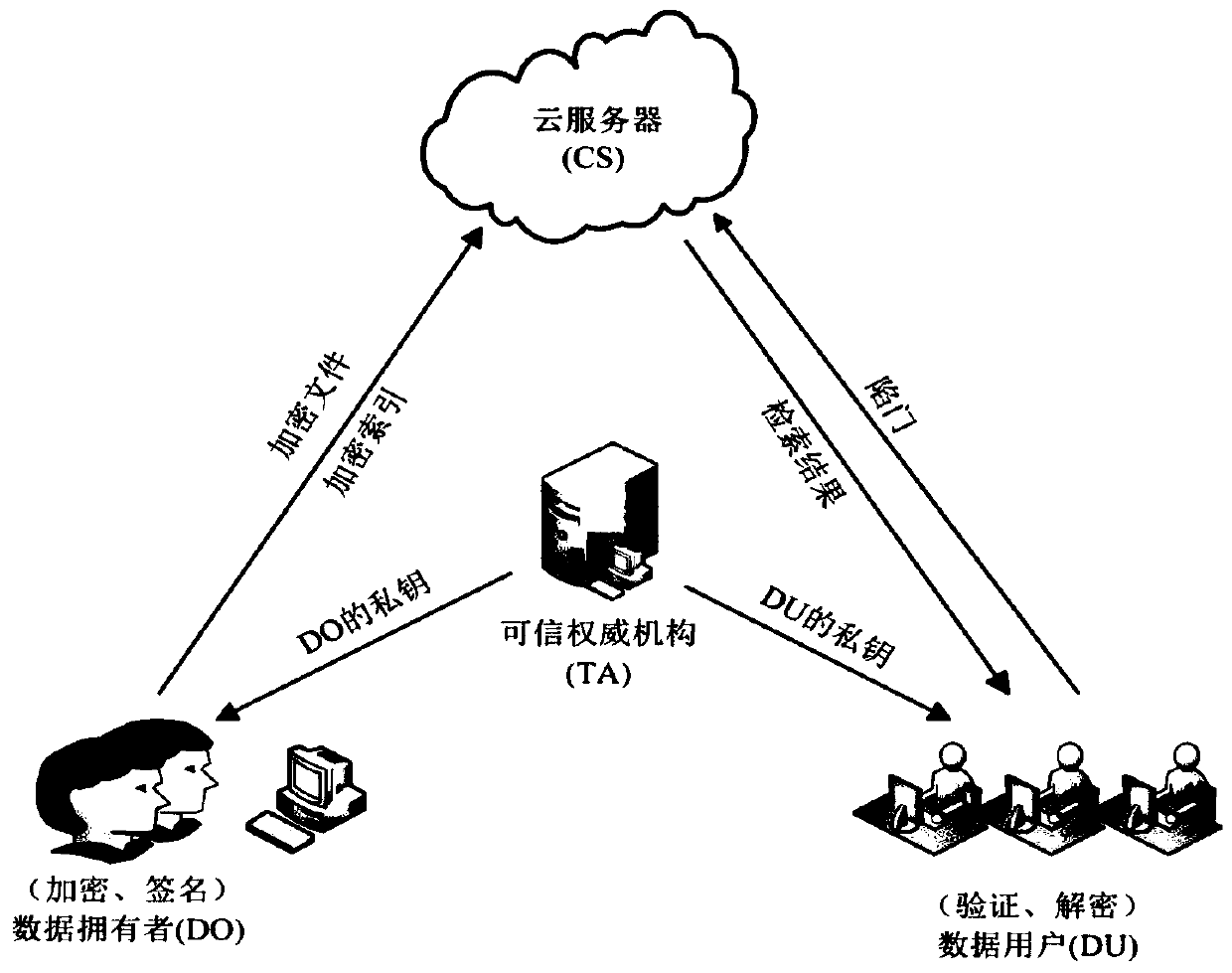
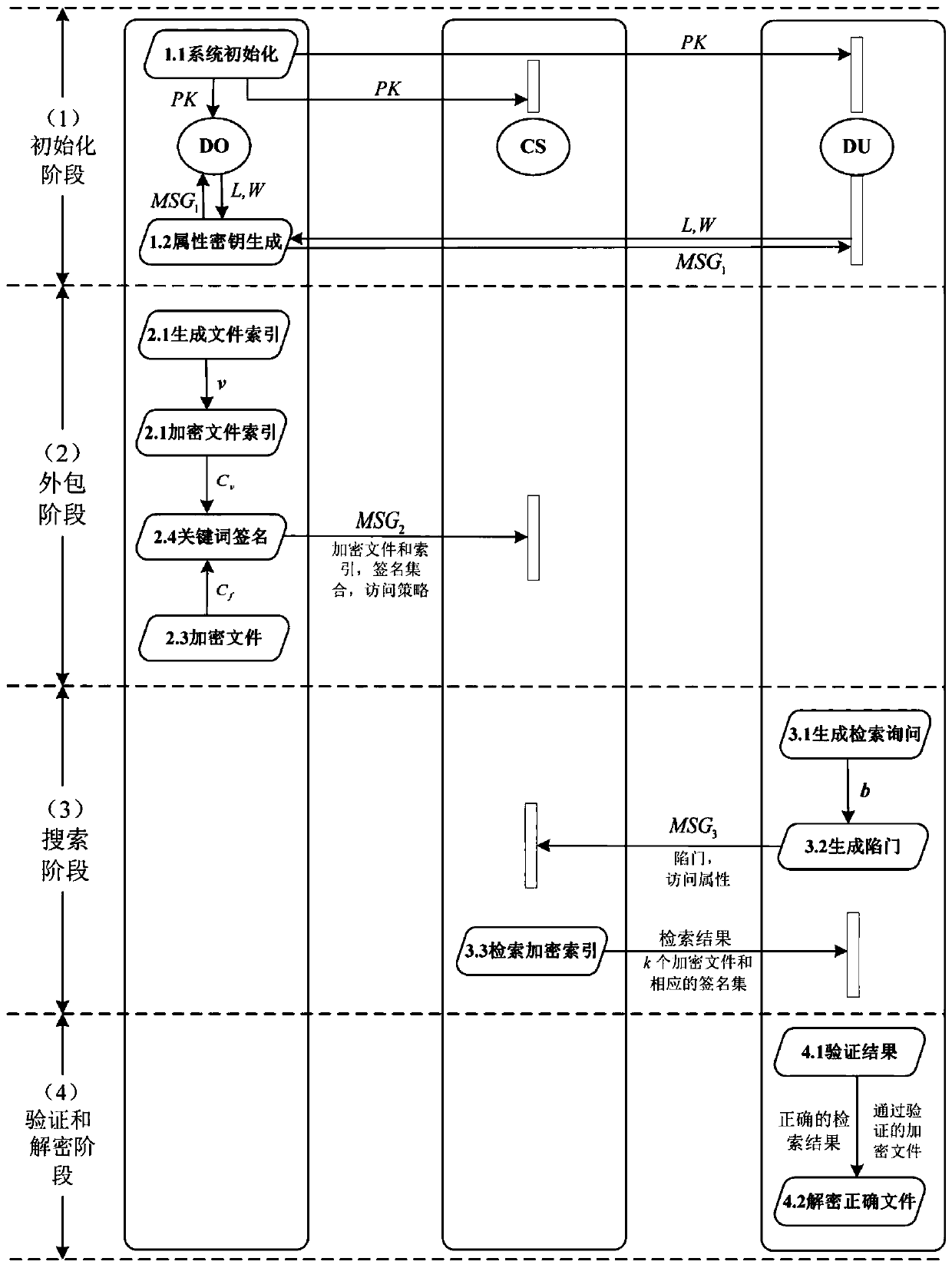
ActiveCN111159352AHigh precisionImplement weighted retrievalDigital data protectionText database queryingTheoretical computer scienceEngineering
The invention relates to a verifiable encryption and decryption method supporting multi-keyword weighted retrieval and result sorting. Firstly, an outsourcing file is encrypted based on an attribute-based encryption idea, so that the access permission of a data user is preset, and the data user meeting the attribute requirement can directly decrypt a retrieved file. Secondly, a k-nearest neighbor(k-NN) technology is improved, so that communication burden caused by the fact that a data owner and a data user need to share a splitting factor in advance is reduced and avoided, and meanwhile, theaccuracy of multi-keyword retrieval is also improved. Thirdly, although the cloud server is supposed to be not completely credible, most of existing retrieval schemes do not consider verification of retrieval results returned by the cloud server, and in the method, a data user can verify whether a retrieval result file contains all queried keywords or not, so that correctness of the retrieval fileis verified.
Owner:山东齐鲁知识产权交易中心有限公司
File encryption and decryption method and terminal
InactiveCN108334785AImprove securityIncrease the difficultyDigital data protectionComputer hardwareEncrypted function
Owner:HUAWEI TECH CO LTD
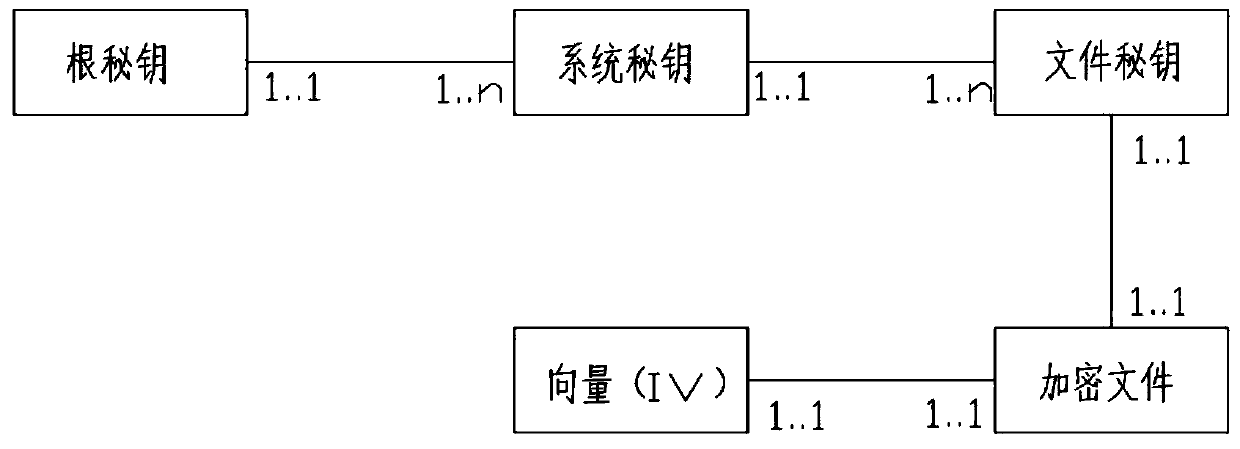
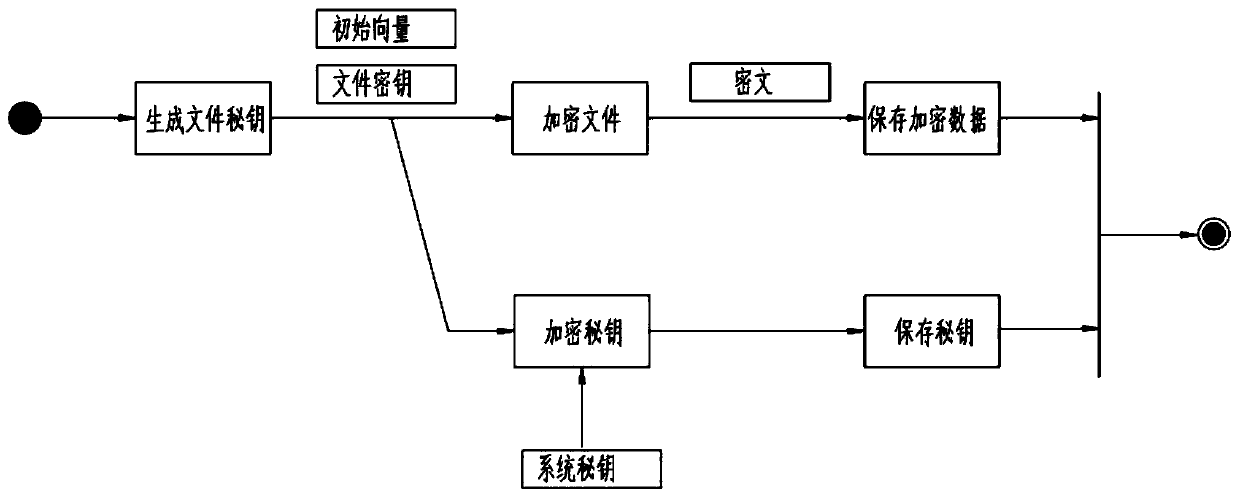
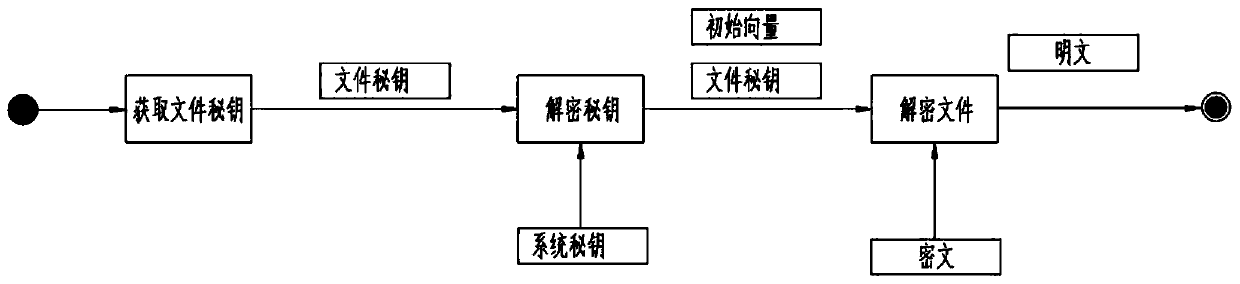
Three-level secret key encryption system
ActiveCN110166458AEnsure safetyKey distribution for secure communicationComputer hardwareThree level
The invention discloses a three-level secret key encryption system. The method comprises the following steps of secret key classification, file encryption, file decryption and secret key management. All secret keys cannot be independently obtained in all links of system development, maintenance and use through three-level secret key encryption, a new encryption algorithm is not needed through a secret key classification method, and the safety of encrypted files is ensured.
Owner:王怀尊
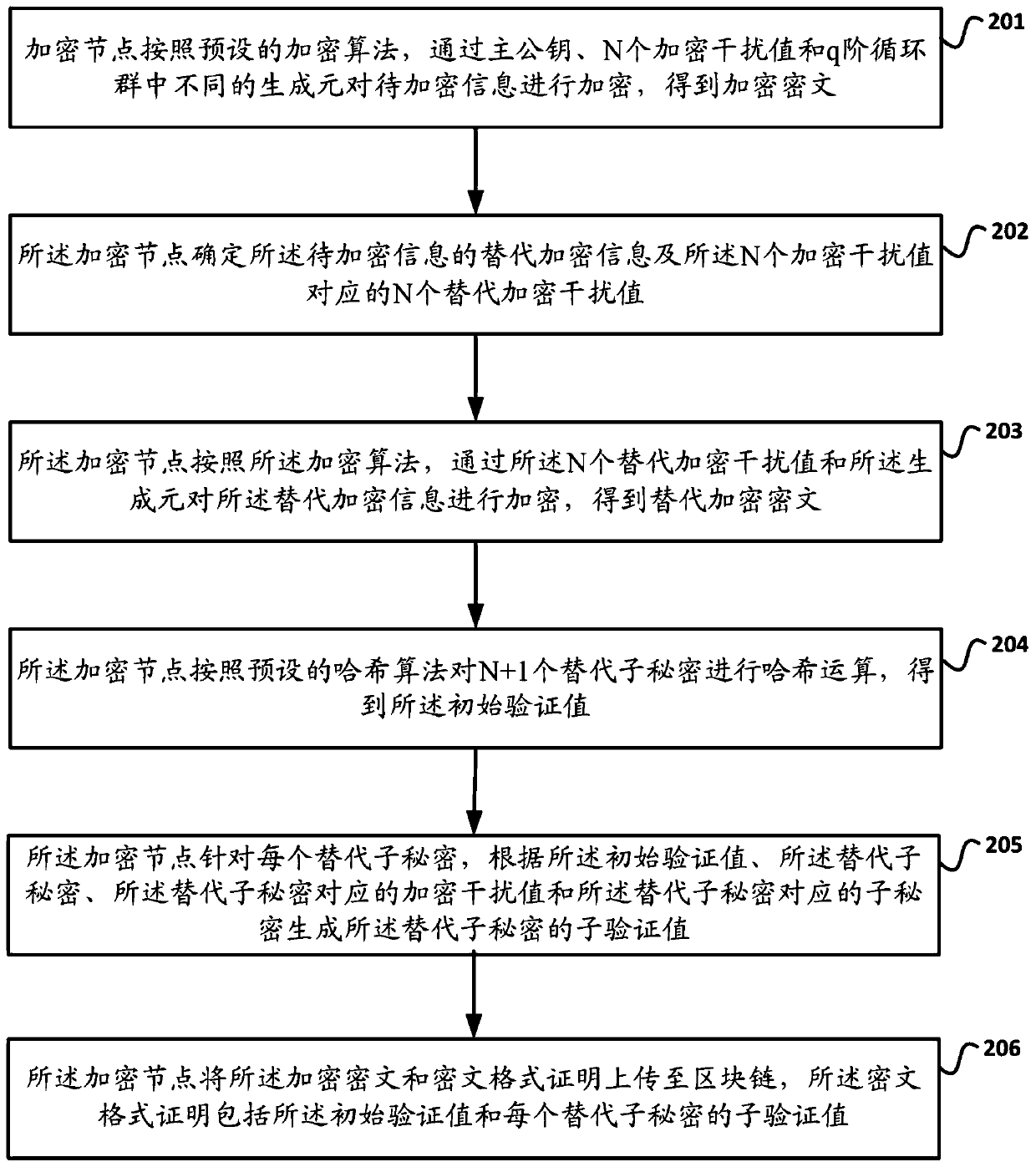
Verification method and device suitable for blockchain
The invention discloses a verification method and device suitable for blockchain, and the method comprises the steps that an encryption node encrypts to-be-encrypted information through a main publickey, N encryption interference values and different generators in a q-order cyclic group according to a preset encryption algorithm, and obtains an encrypted ciphertext; and the encryption node encrypts the alternative encryption information through the N alternative encryption interference values and the generators according to the encryption algorithm to obtain an alternative encryption ciphertext, and the encryption node uploads the encryption ciphertext and the ciphertext format proof to a block chain. When the method is applied to the Fintech, it is proved through a ciphertext format thatthe encryption correctness of the encrypted ciphertext can be verified on the basis that the information to be encrypted and the N alternative encryption interference values are not exposed.
Owner:WEBANK (CHINA) +1
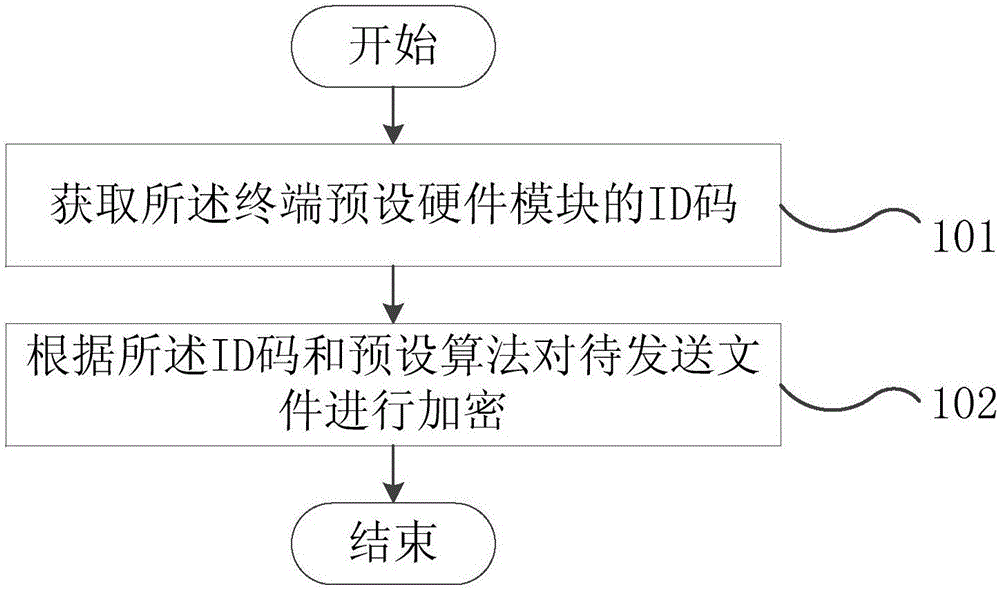
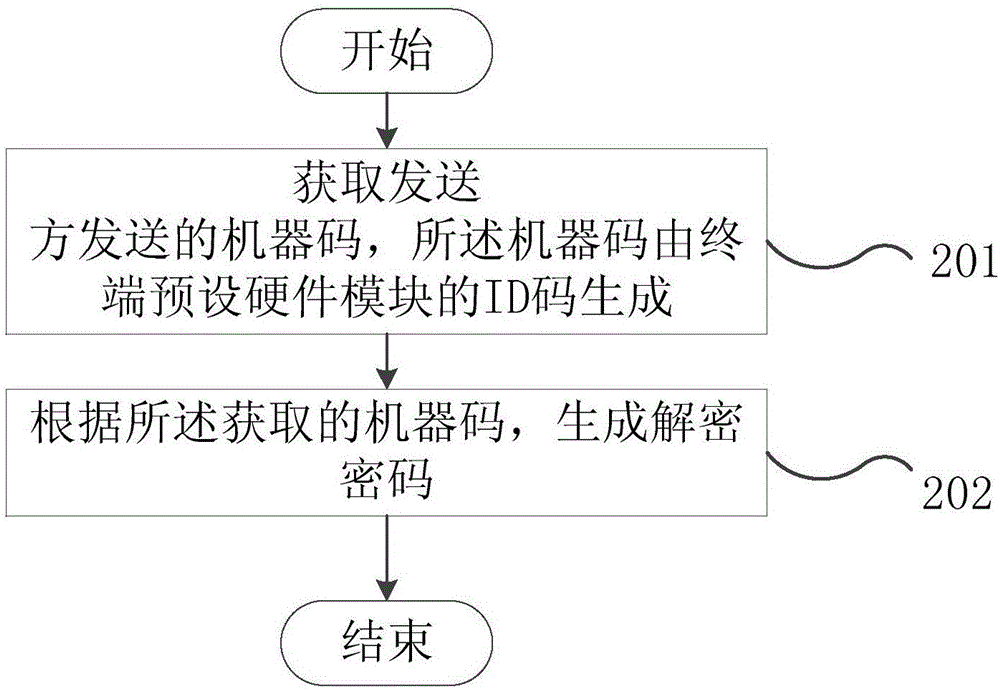
File encryption and decryption methods and terminals
InactiveCN106656485AImprove confidentialityKey distribution for secure communicationXML EncryptionComputer terminal
The embodiment of the invention provides file encryption and decryption methods and terminals. The encryption method comprises the following steps: acquiring an ID (Identity) code of a preset hardware module of a terminal; and encrypting a file to be transmitted according to the ID code and a preset algorithm. In the file encryption and decryption methods provided by the invention, the file is encrypted in conjunction with hardware ID information of the terminal, so that decoding needs to be performed according to the ID code of the hardware module of the terminal during decoding; use of a decoded file in other terminals is limited; and a receiver is effectively prevented from randomly copying and transmitting the decoded file.
Owner:VIVO MOBILE COMM CO LTD
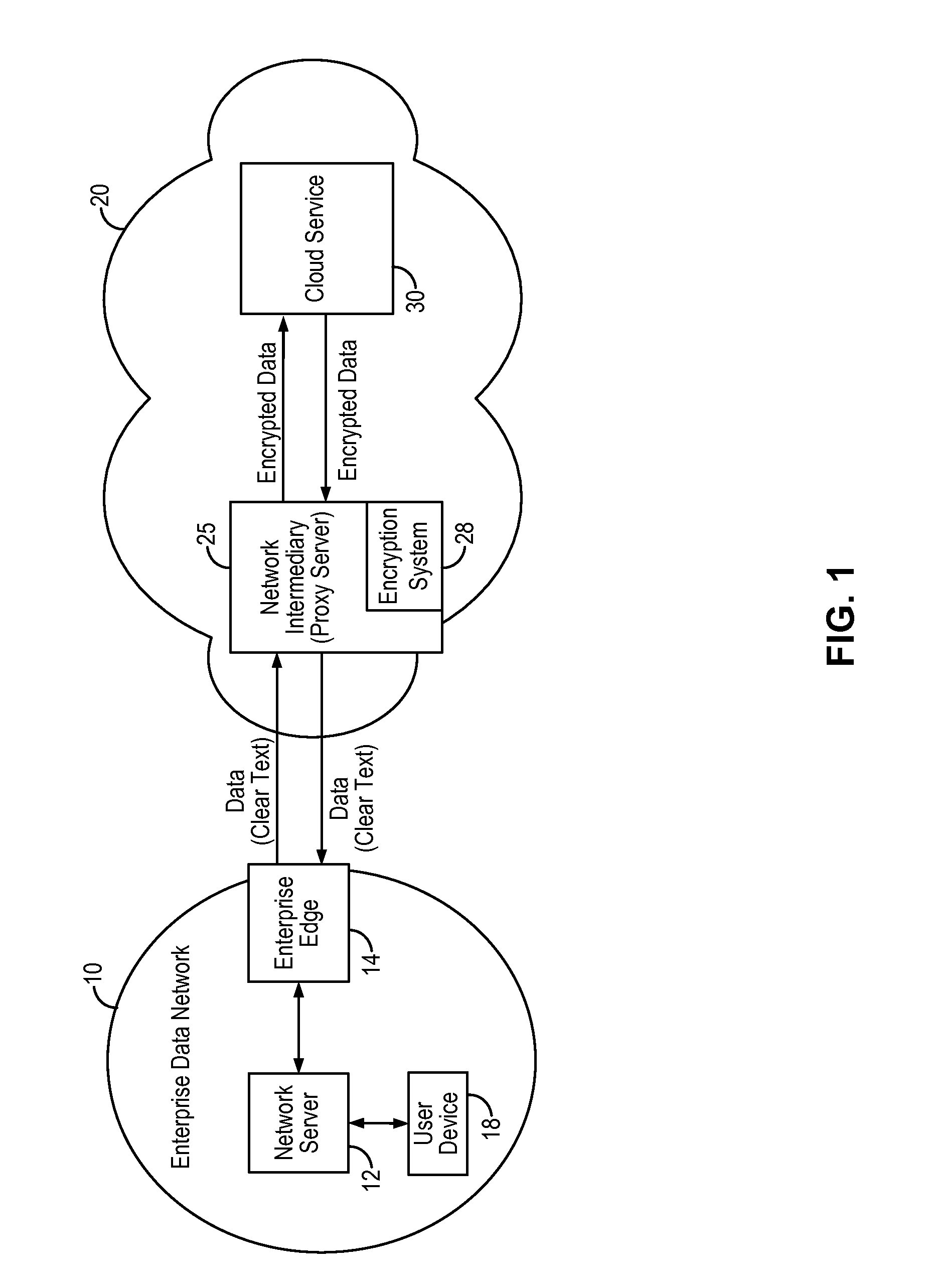
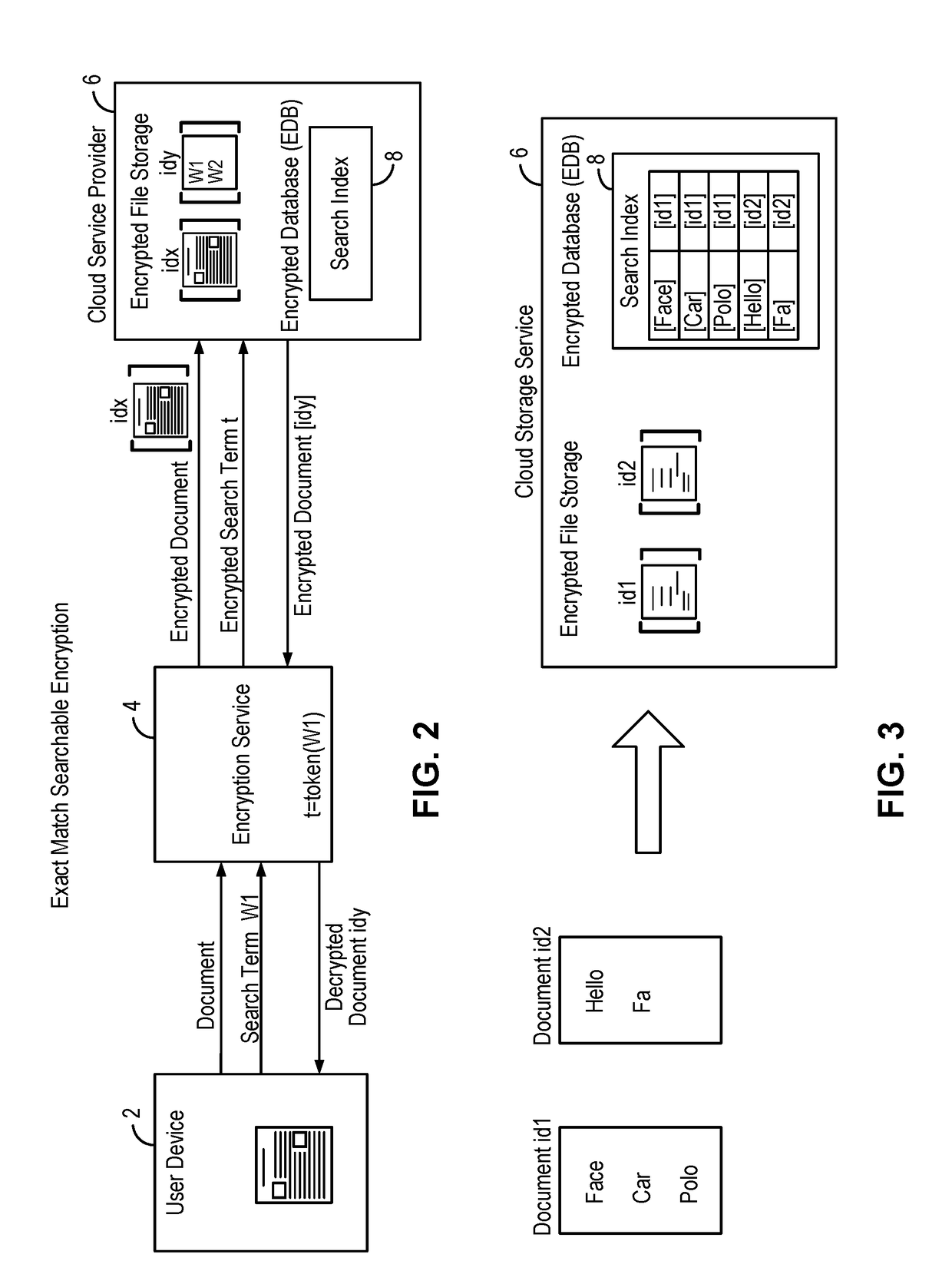
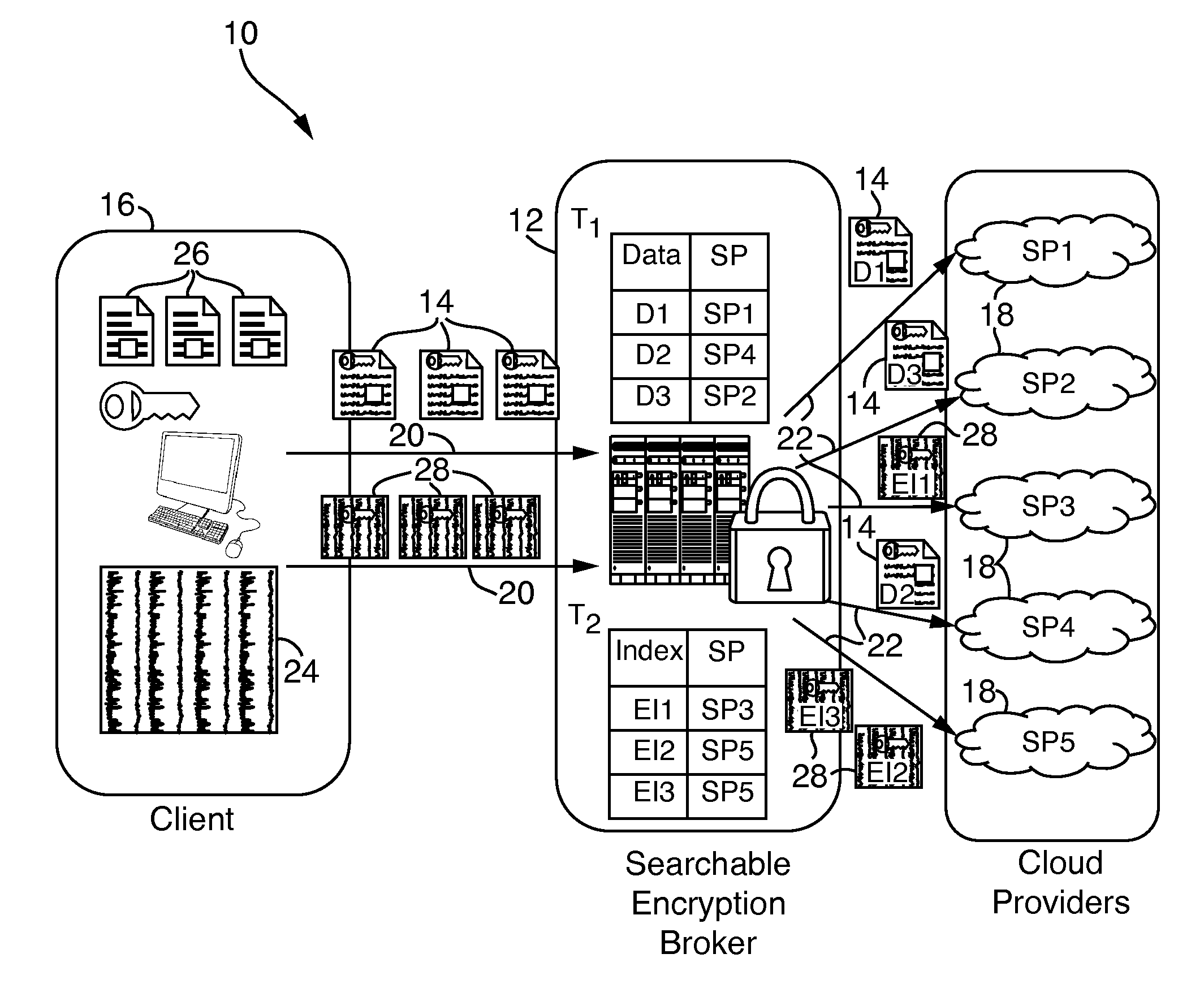
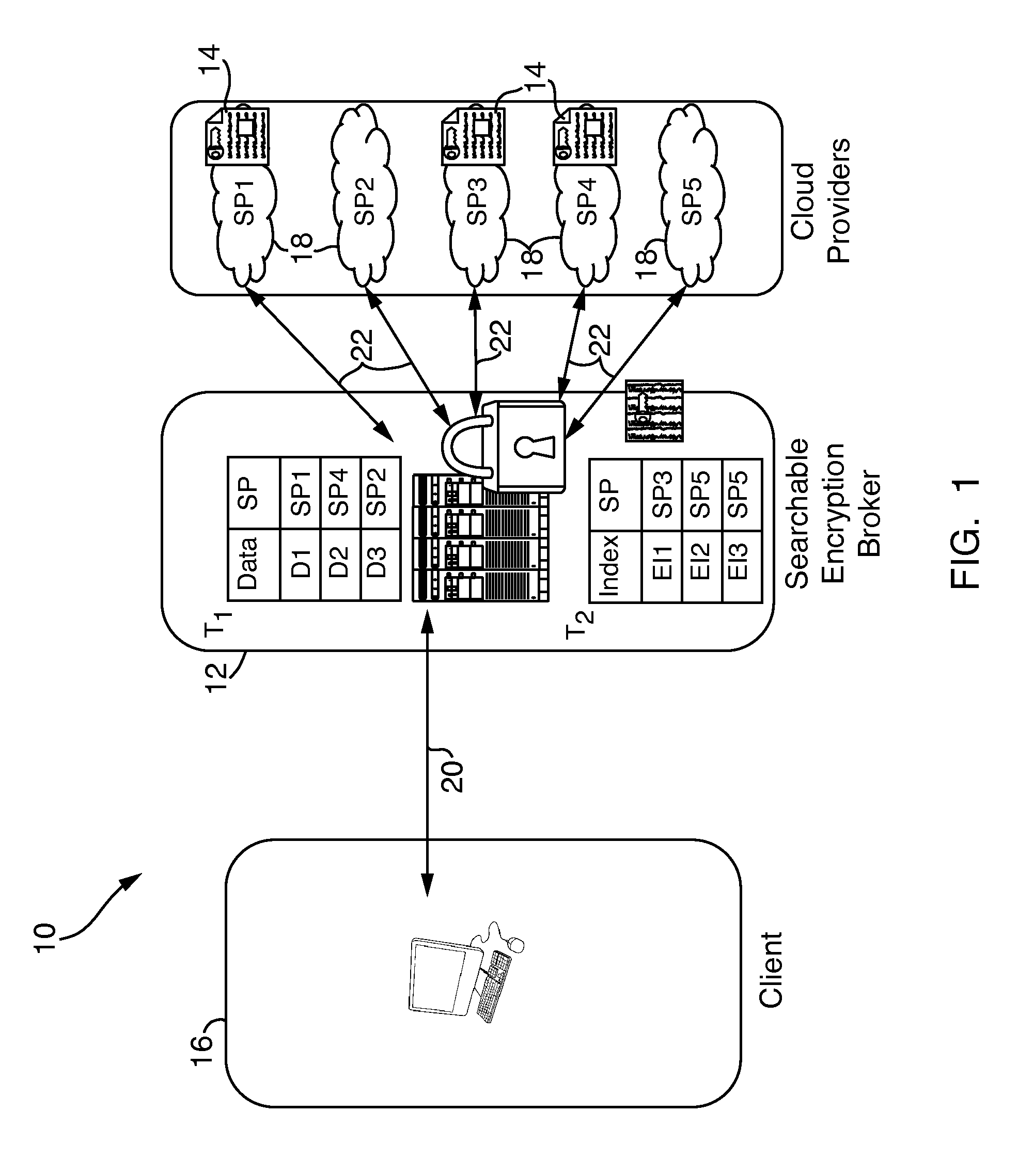
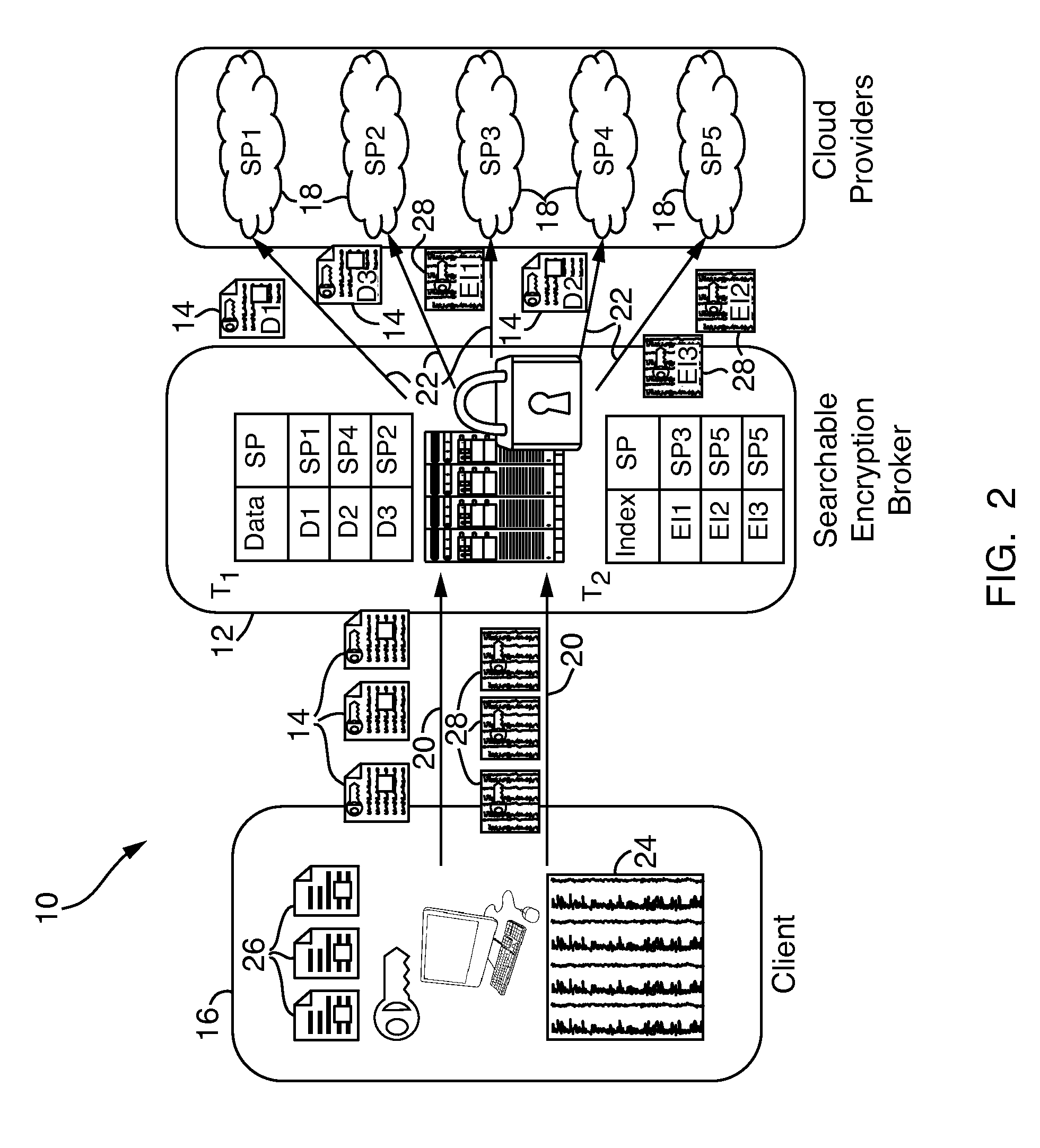
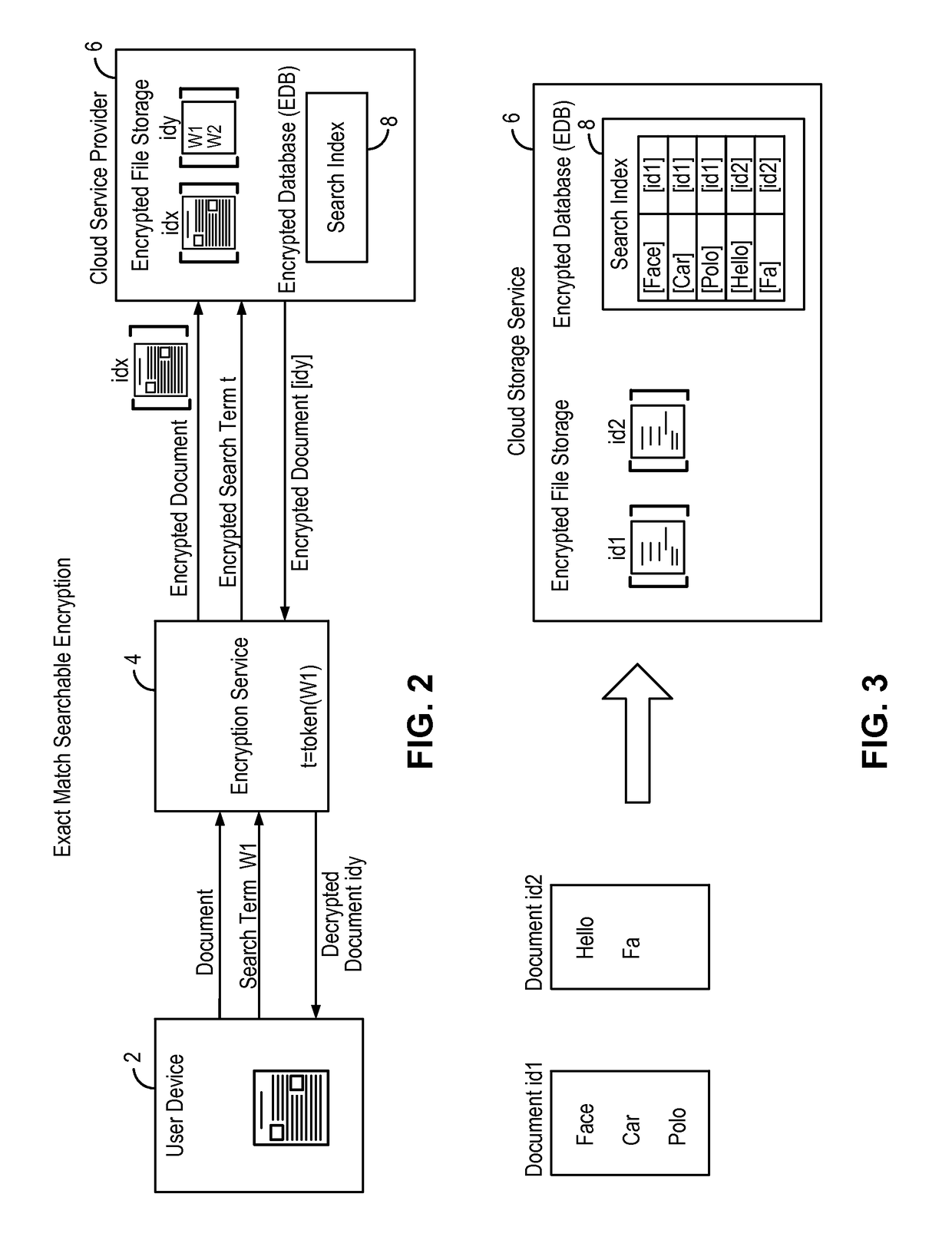
Systems and methods for enabling searchable encryption
A system and method for enabling searchable encryption of encrypted documents stored by a client on one or more storage providers includes a broker server in communication with the client and the one or more storage providers. The broker server is adapted to transfer the encrypted documents between the client and the one or more storage providers and to maintain information indicating where the encrypted documents are transferred. The broker server further stores information for at least one encrypted index for the encrypted documents and a test function for a searchable encryption mechanism used to encrypt the at least one encrypted index.
Owner:ALCATEL LUCENT SAS
Searchable encryption enabling encrypted search based on document type
ActiveUS9894042B2User identity/authority verificationComputer security arrangementsProxy serverDocumentation
A searchable encryption method enables encrypted search of encrypted documents based on document type. In some embodiments, the searchable encryption method is implemented in a network intermediary, such as a proxy server. The network intermediary encrypts documents on behalf of a user or an enterprise destined to be stored on a cloud service provider. The searchable encryption method encodes document type information into the encrypted search index while preserving encryption security. Furthermore, the searchable encryption method enables search of encrypted documents using the same encrypted index, either for a particular document type or for all encrypted documents regardless of the document type.
Owner:SKYHIGH SECURITY LLC
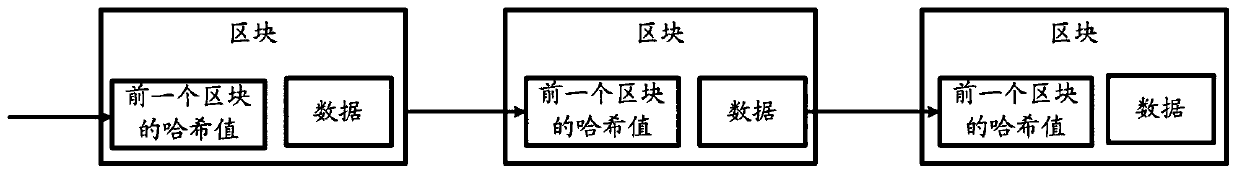
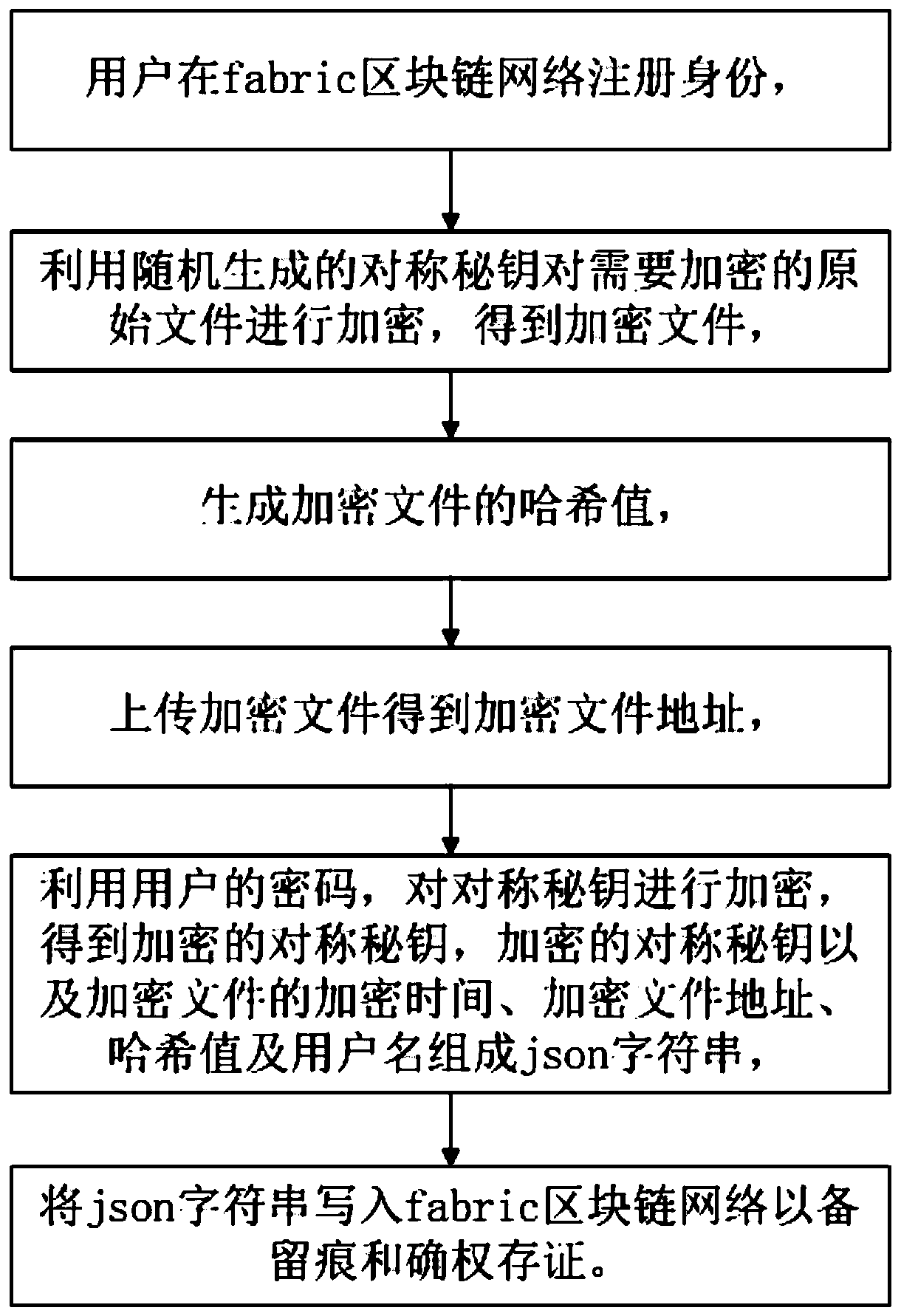
File encryption storage method based on block chain
The invention discloses a file encryption storage method based on a block chain, and relates to the technical field of file encryption. The file encryption storage method includes the steps: a user registers the identity in a Fabric block chain network, and encrypts an original file needing to be encrypted by utilizing a randomly generated symmetric key to obtain an encrypted file and generate a hash value of the encrypted file; the encrypted file is uploaded to obtain an encrypted file address; and the symmetric key is encrypted by utilizing a password of the user to obtain the encrypted symmetric key, forming a json character string by the encrypted symmetric key, the encryption time of the encrypted file, the address of the encrypted file, the hash value and the user name, and writing the json character string into the Fabric block chain network to reserve a mark and confirm a right certificate.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
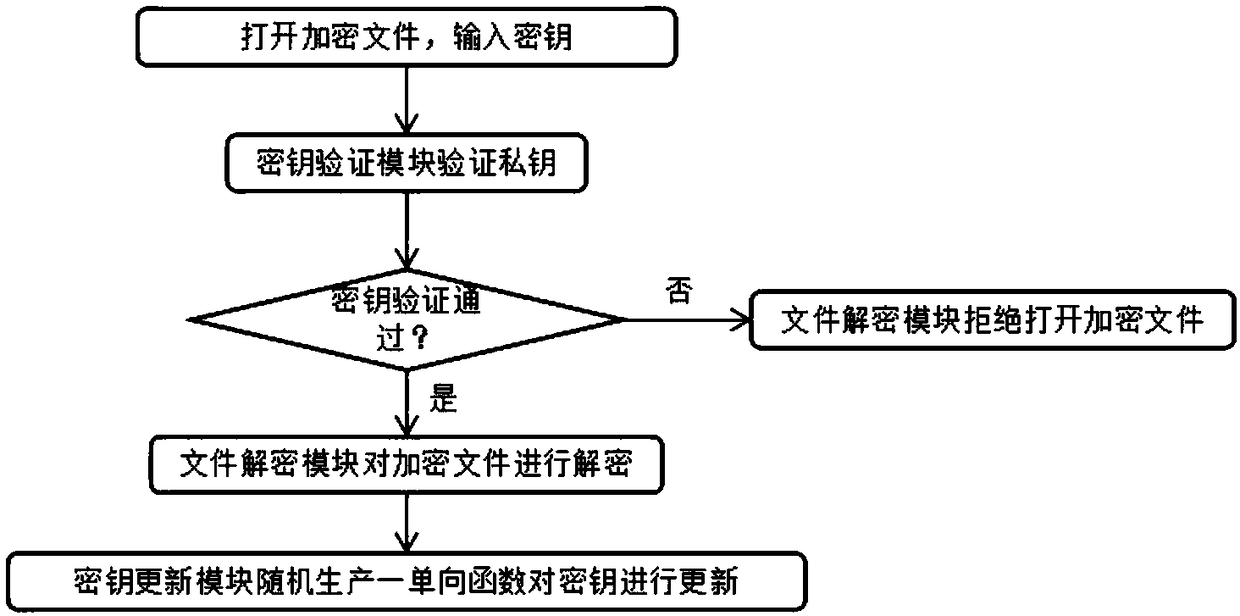
Method and device for file encryption and decryption
InactiveCN106022147AThe encryption process is simple and fastDecryption is flexibleDigital data protectionComputer hardwareEncryption
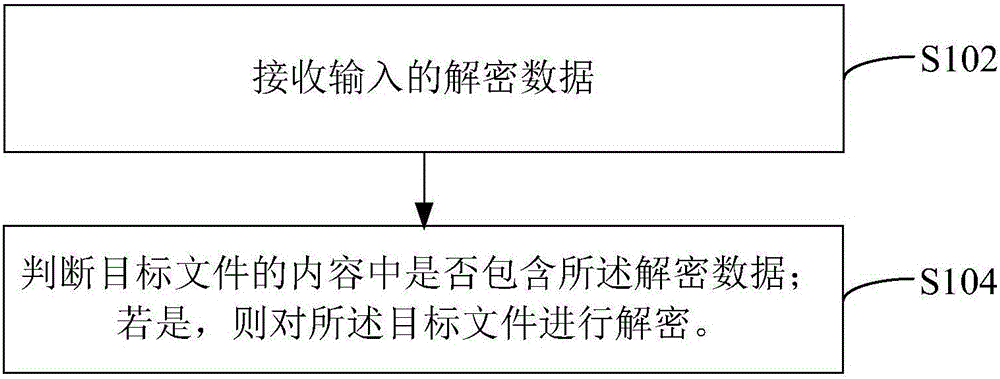
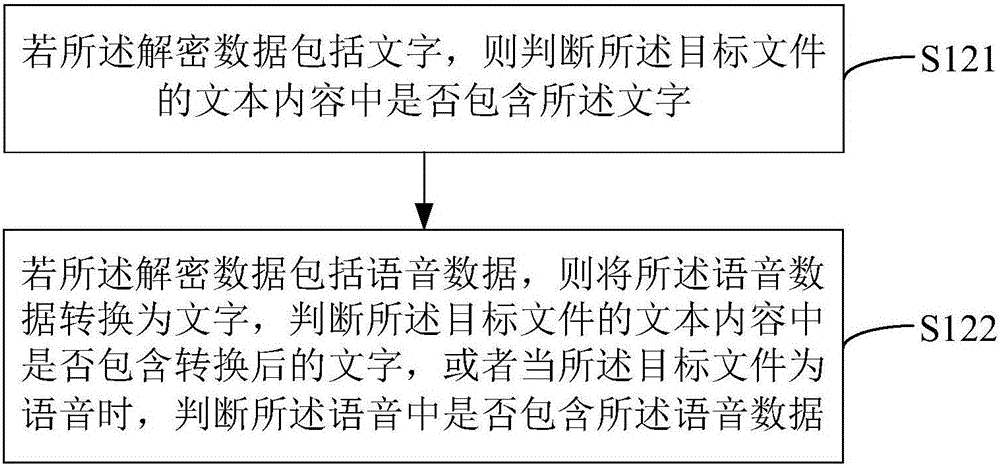
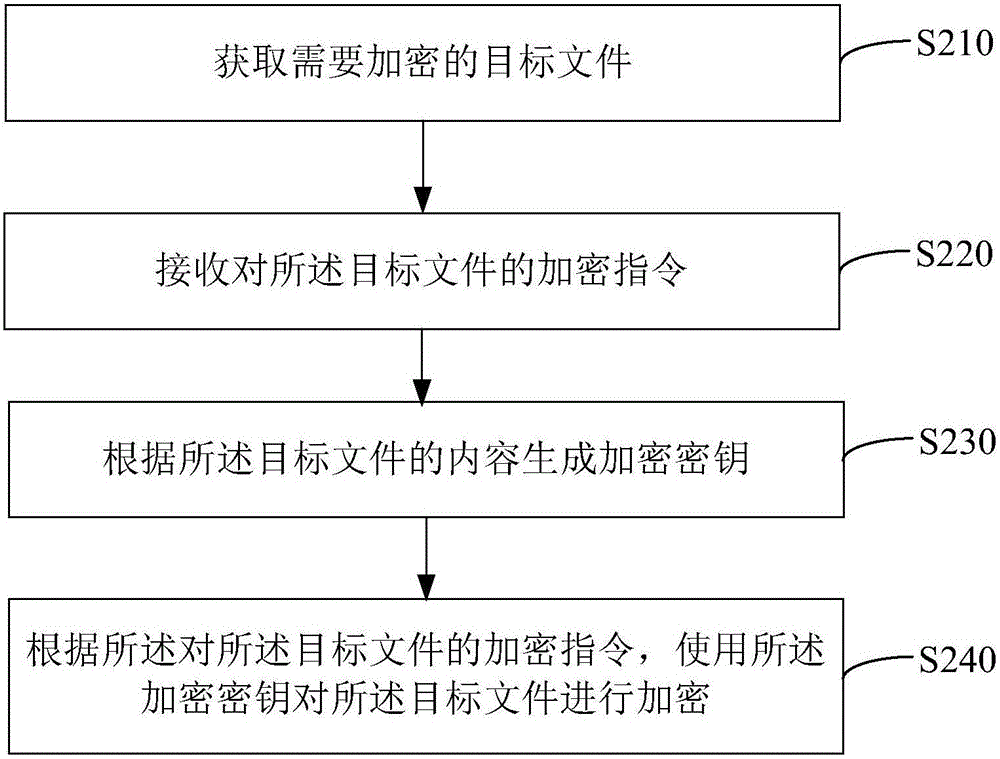
The present invention relates to a file encryption and decryption method and device. The decryption method includes: receiving input decryption data; judging whether the content of the target file contains the decryption data; and if so, decrypting the target file. The encryption method includes: obtaining a target file to be encrypted; receiving an encryption instruction for the target file; generating an encryption key according to the content of the target file; according to the encryption instruction for the target file, using the The encryption key is used to encrypt the target file. Using the above method, the encryption operation is simpler and faster, and the decryption is more flexible. Additionally, a device is provided.
Owner:MEIZU TECH CO LTD
File encryption system based on third party key management
ActiveCN108173880AReduced risk of crackingSolve security encryption problemsTransmissionThird partyXML Encryption
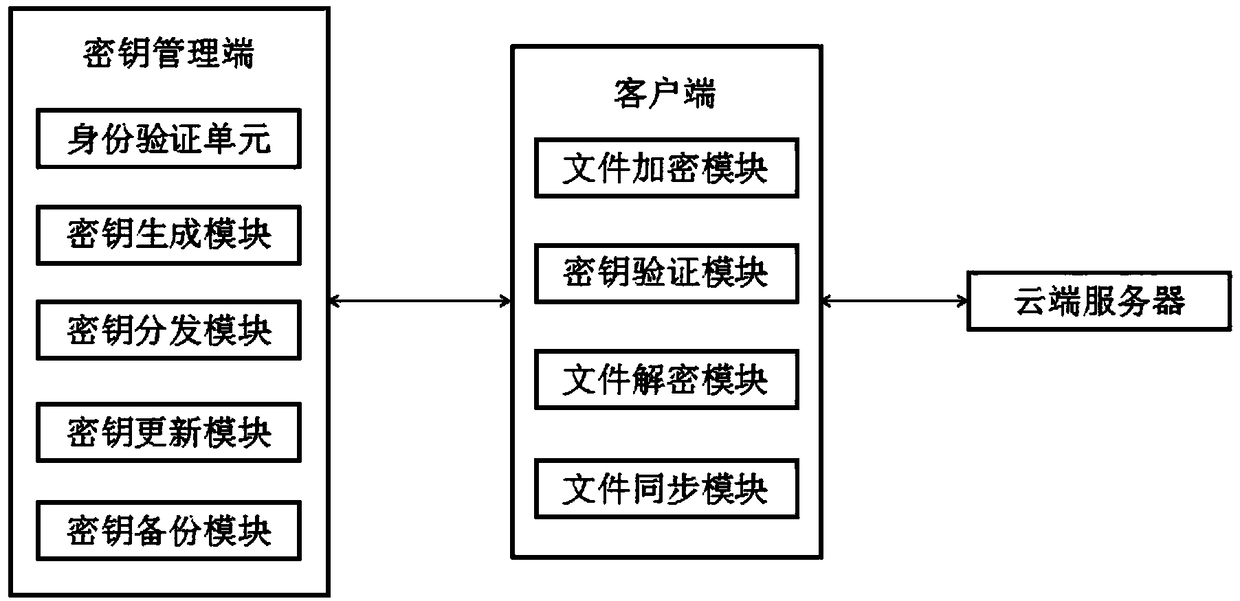
The invention discloses a file encryption system based on third party key management, which relates to the technical field of information security. The file encryption system comprises a key manager used for managing keys, a client used for file encryption / decryption and synchronization, and a cloud server used for storing and backing up encrypted files. The client and the cloud server carry out information interaction through the Ethernet. The client encrypts / decrypts files, and transmits the files to the cloud server for storage and backup. According to the invention, keys are managed by theindependent third party key manager, an encrypted file can be opened only when the key is obtained, and it is ensured that only the user himself or herself can see the file being decrypted and opened. Moreover, the file is encrypted / decrypted and synchronized to the cloud server by the client. The problem on how to encrypt a file securely is well solved. A key is updated by a key update module after the key is verified by a key verification module, and therefore, the risk of key cracking is reduced.
Owner:合肥图久智能科技有限公司
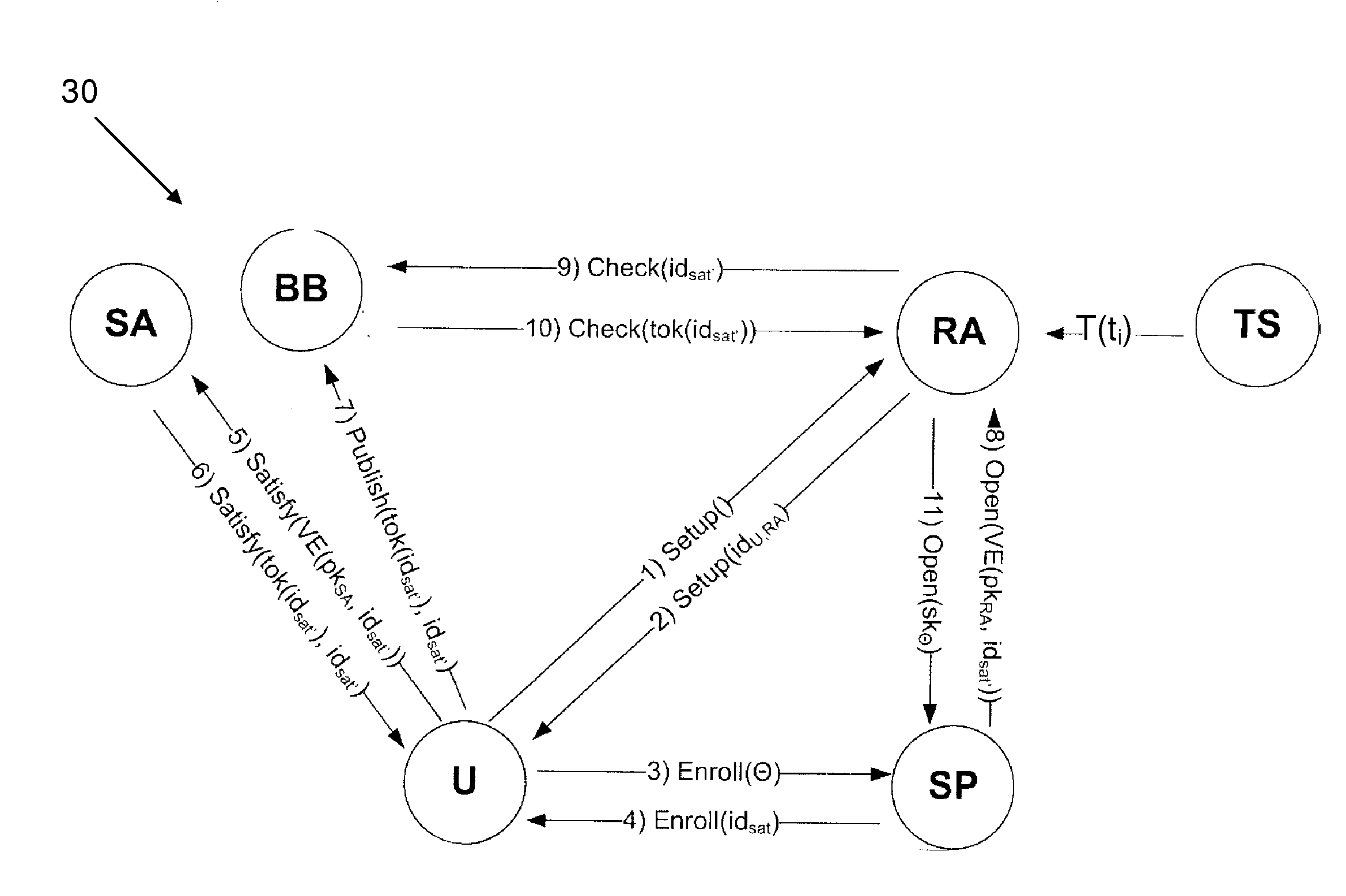
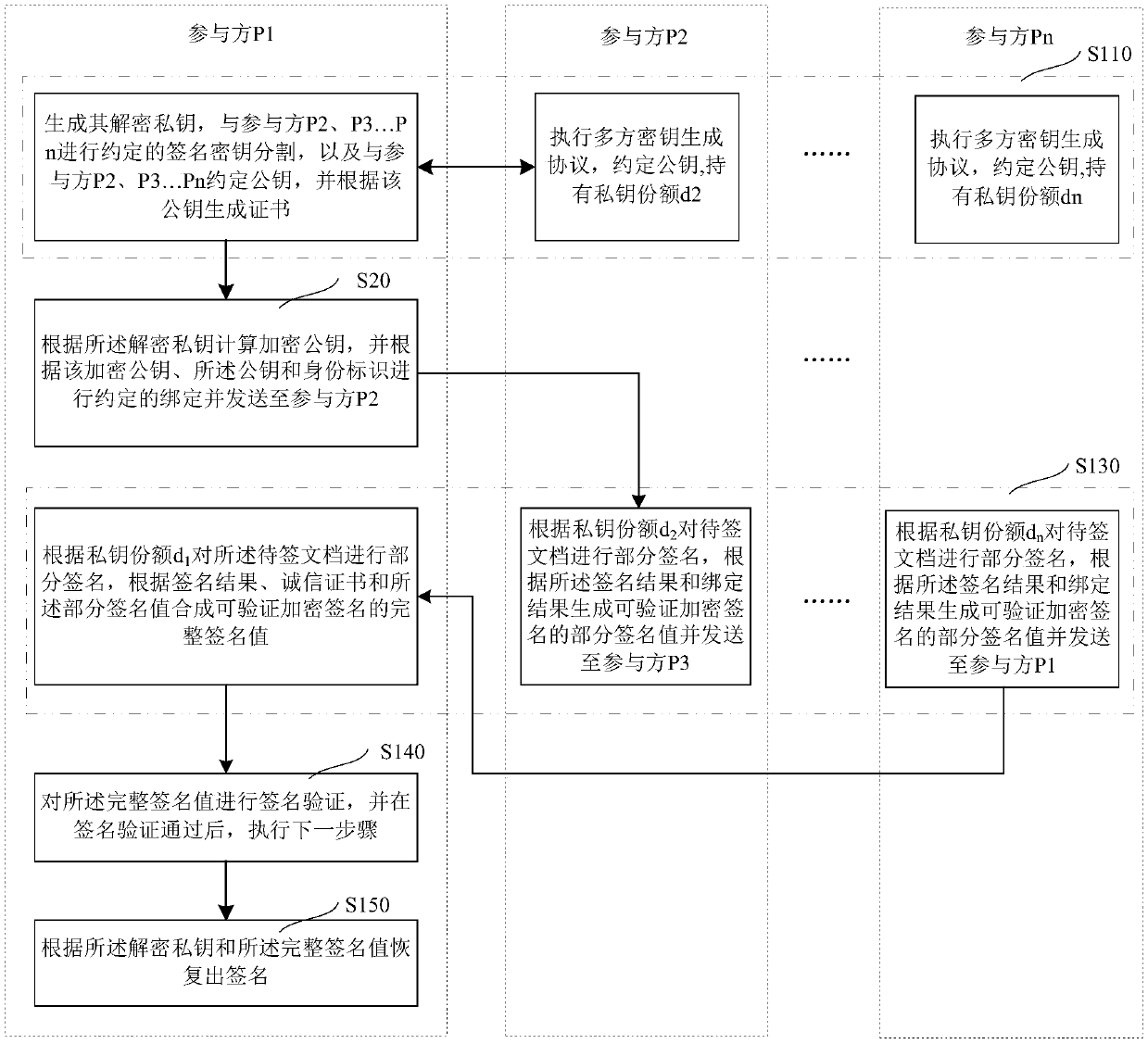
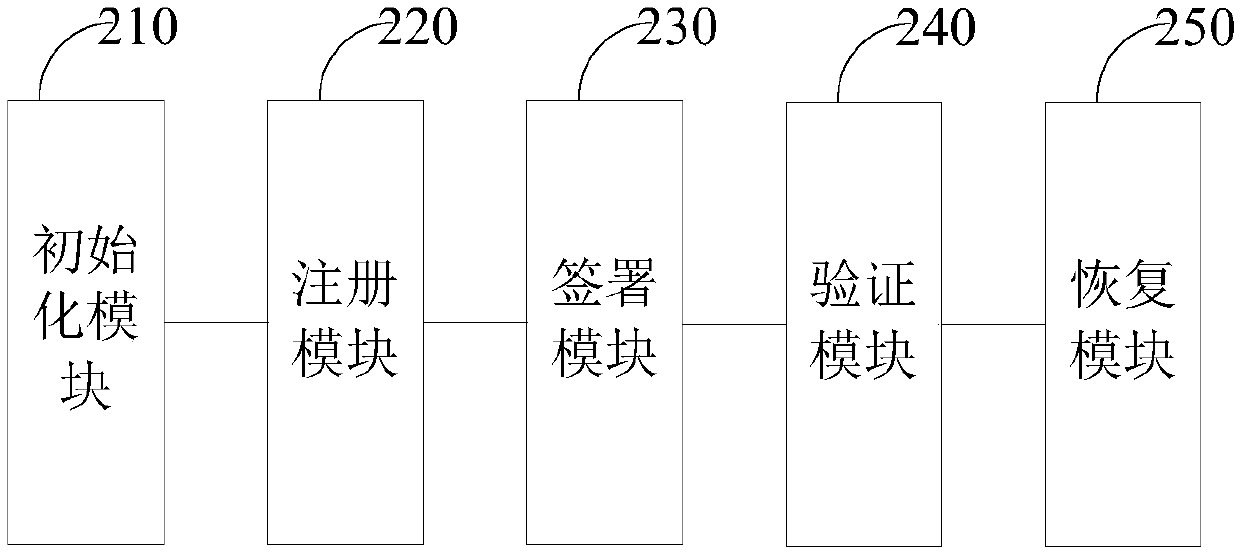
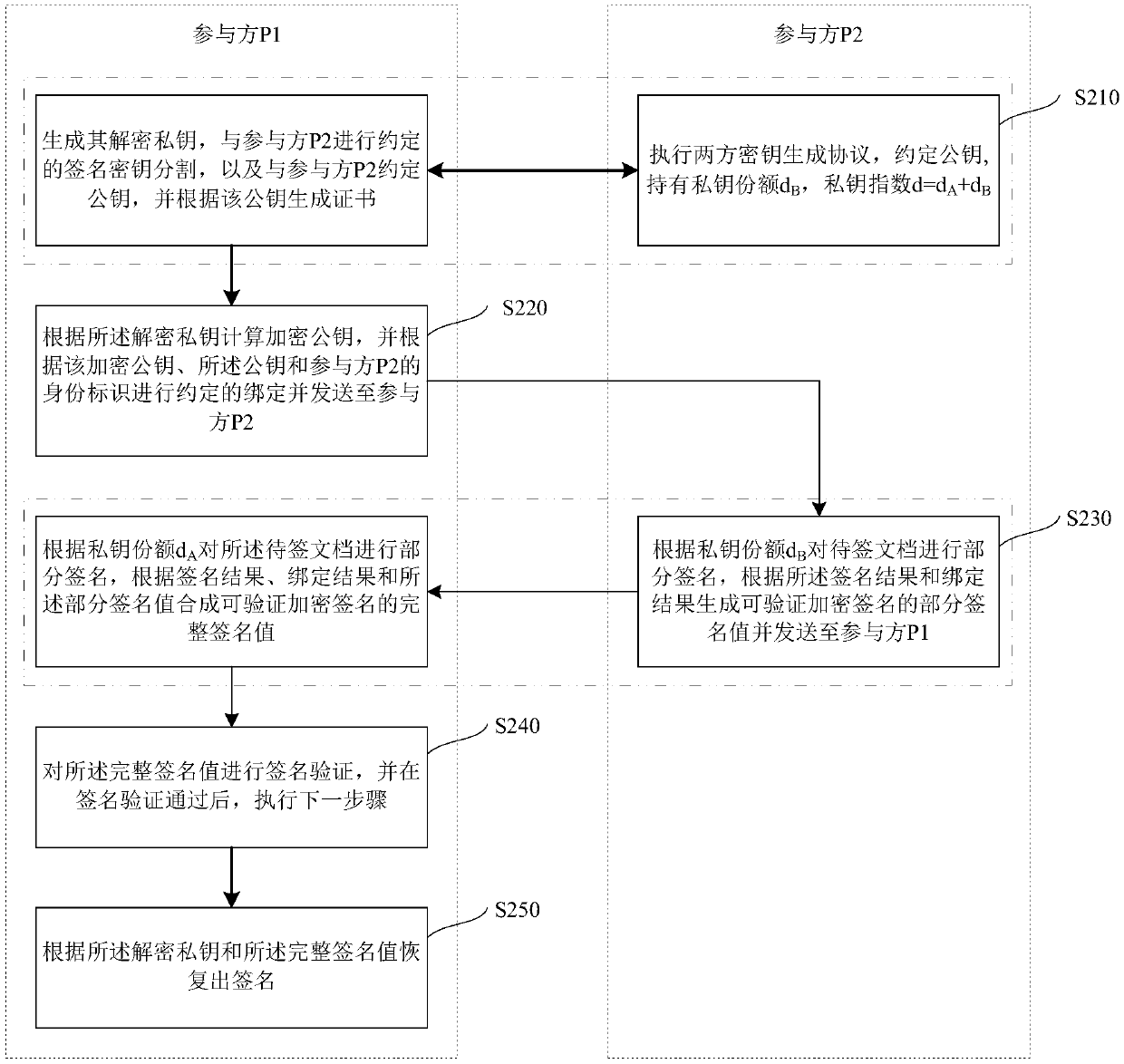
Verifiably encrypted signature generation method and system
ActiveCN108768634AEnsure safetyImprove securityKey distribution for secure communicationMultiple keys/algorithms usageGeneration processVerifiable encryption
The invention relates to a verifiably encrypted signature generation method and system. The method comprises the following steps that n participants P1, P2 to Pn are arranged; an identity (ID) is agreed by the participant according to a preset rule; and the n participants participate in a verifiably encrypted signature generation process in the form of a ring in sequence. According to the method and the system, the participants participate in generation of a verifiably encrypted signature together on the premise that each private key share is not leaked, , and the safety of the generated verifiably encrypted signature can be ensured.
Owner:GUANGDONG CERTIFICATE AUTHORITY
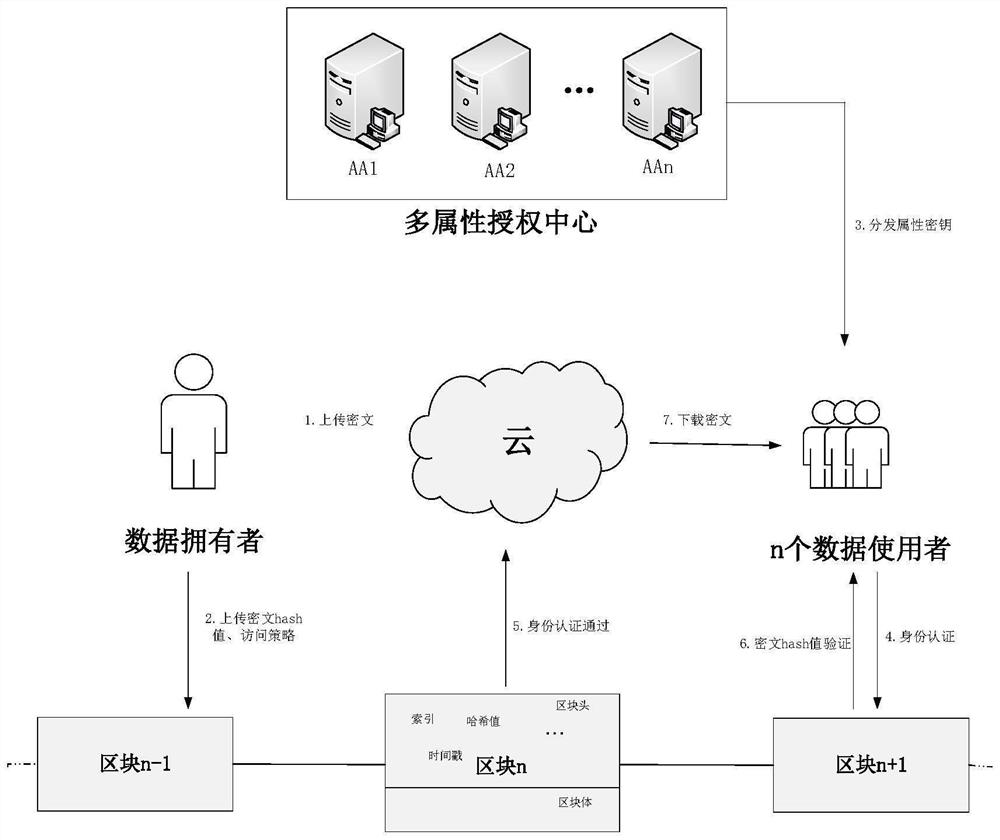
Multi-authorization attribute-based verifiable encryption method based on block chain
InactiveCN114143094AIncrease the difficultyIncrease costSecuring communicationData privacy protectionEngineering
The invention discloses a multi-authorization attribute-based verifiable encryption method based on a block chain, belongs to the technical field of block chain data privacy protection security, and is suitable for one-to-many data sharing and fine-grained access control. The method comprises the following steps: firstly, a data owner uploads encrypted data to a cloud end by using a system public key, and uploads a data ciphertext hash value and an access strategy to a block chain; and the cloud storage server is responsible for receiving and storing the ciphertext. Secondly, the data user receives the attribute key distributed by the multi-attribute authorization center and can verify the correctness of the key; and the block chain performs identity authentication on the data user, and returns an authentication result to the cloud server. And finally, only the legal user whose attribute private key accords with the access strategy can download the data from the cloud and verify whether the data is tampered or not.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
File encryption and decryption method and system
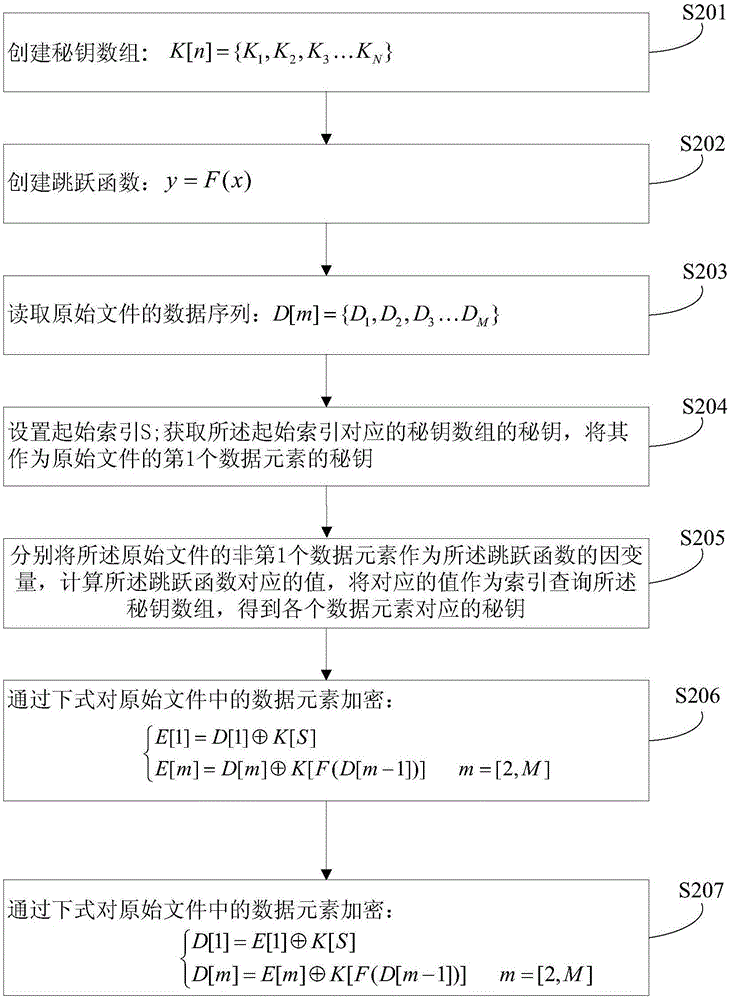
ActiveCN106372529ARealize encryption and decryptionDigital data protectionArray data structureJumping function
The invention relates to a file encryption and decryption method and system. The method comprises the following steps of: creating a secret key array and a jump function; reading data elements of an original file; respectively taking the data elements of the original file as dependent variables of the jump function, calculating a value corresponding to the jump function, and taking the corresponding value as an index to query the secret key array so as to obtain secret keys corresponding to the data elements; carrying out XOR on the data elements of the original file and the corresponding secret keys to obtain an encrypted file; and carrying out XOR restoration on the data elements of the encrypted file and the corresponding secret keys to obtain the original file. According to the method and system provided by the invention, the jump function is created on the basis of reversibility of XOR, so that the secret keys corresponding to the data elements of the original file are indexed in a jump manner, XOR is carried out on the data elements of the original file and the corresponding secret keys to obtain the encrypted file, and XOR restoration is carried out on the data elements of the encrypted file and the corresponding secret keys to obtain the original file, thereby well realizing the encryption and decryption of the file on embedded devices with small memories.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD
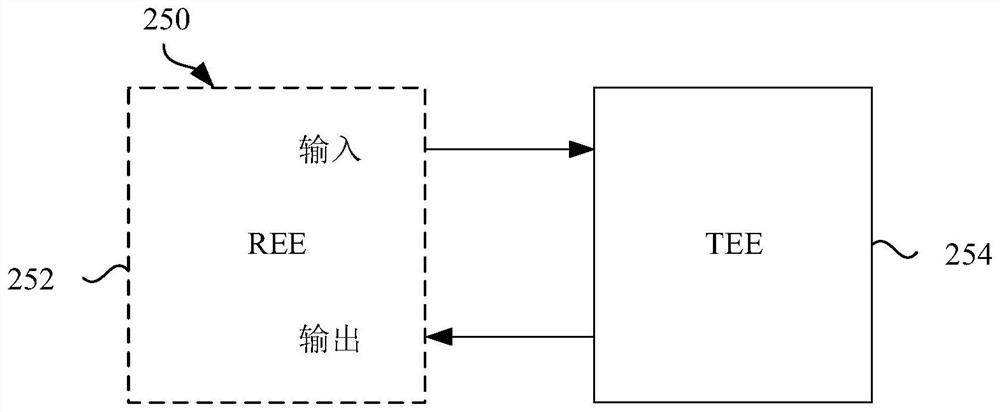
Verifiable encryption based on trusted execution environment
ActiveCN112438034AMultiple keys/algorithms usagePlatform integrity maintainancePlaintextInternet privacy
A method for verifying a property of plaintext using ciphertext is disclosed. In an embodiment, a computing device may receive the ciphertext at a trusted execution environment (TEE) of the computingdevice. The TEE may decrypt the ciphertext to generate the plaintext using a private encryption key of an encryption key pair. The encryption key pair comprises a public encryption key and the privateencryption key. The TEE may generate a digitally signed validation result by encrypting the validation result using a private signing key of a signing key pair. The signed key pair comprises a publicsigning key and the private signing key. The private key is retrieved from secure memory of the computing device, and the secure memory may only be accessible by the TEE. The computing device may then transmit the digitally signed validation result.
Owner:HUAWEI TECH CO LTD
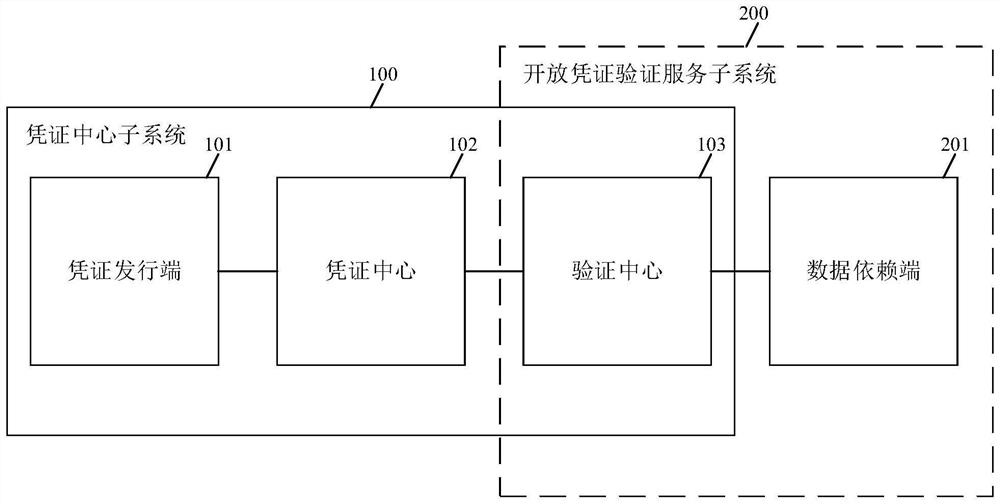
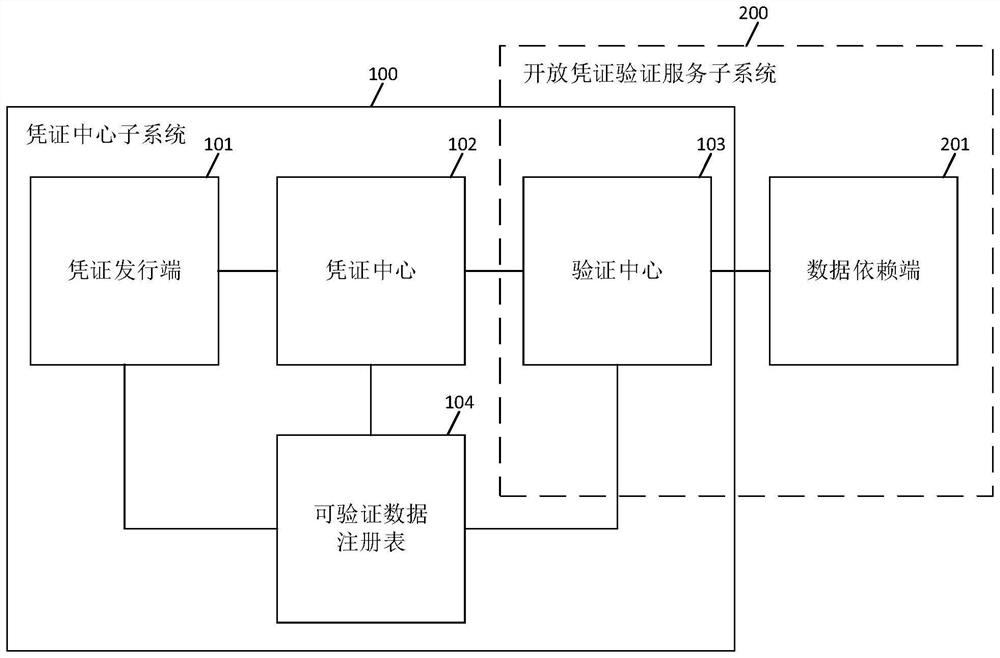
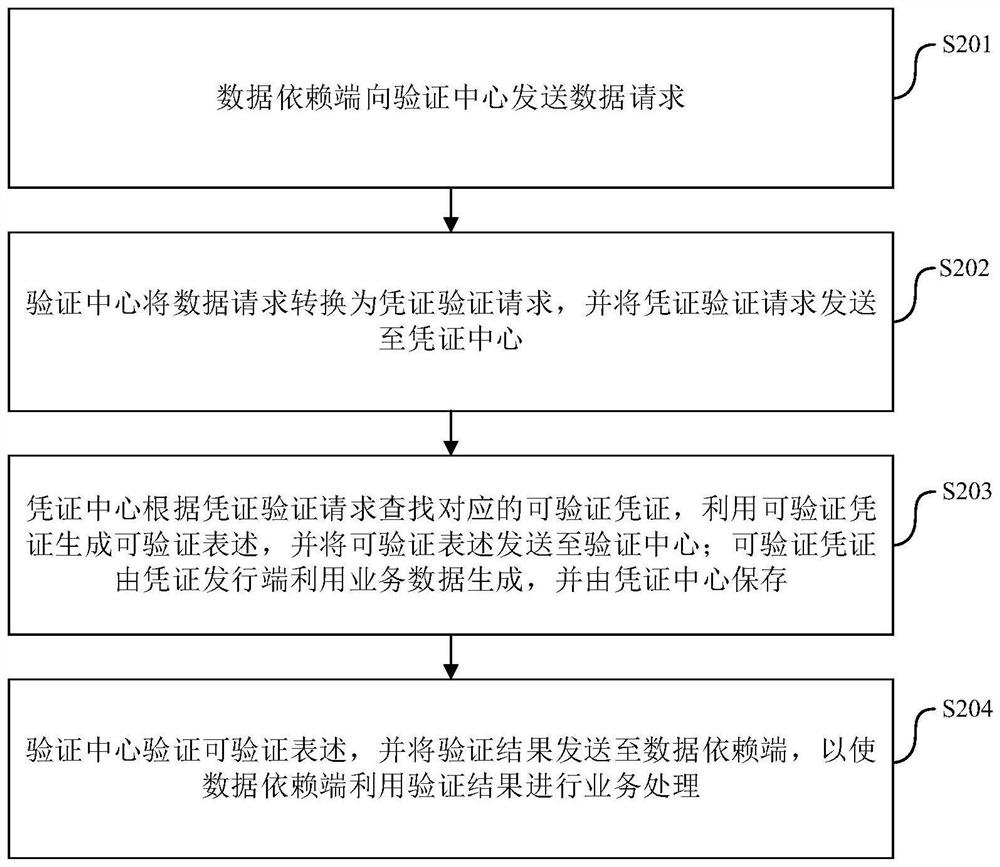
Data sharing method and system and computer readable storage medium
PendingCN114491449AAvoid circulationAvoid buttDigital data protectionDigital data authenticationData connectionPrivacy protection
The invention discloses a data sharing method, which is applied to a data sharing system, and comprises the following steps of: firstly, setting a data end as a certificate issuing end, and respectively deploying the certificate issuing end and a data dependence end in a certificate center subsystem and an open certificate service subsystem; direct data connection between a certificate issuing end and a data dependence end can be effectively avoided, and then the safety problem possibly caused by direct data connection can be avoided; in addition, data of a data party can be subjected to credential transformation, so that a data sharing and using process is converted into a request and verification process of an encrypted credential; and the machine-readable and verifiable encryption certificate can effectively solve the security and privacy protection problems in the current data circulation and use process, and can prevent the data from being copied and then circulated, thereby facilitating the promotion of data opening and sharing. The invention also provides a data sharing system and a computer readable storage medium, which have the above beneficial effects.
Owner:ZHONGCHAO CREDIT CARD IND DEV +1
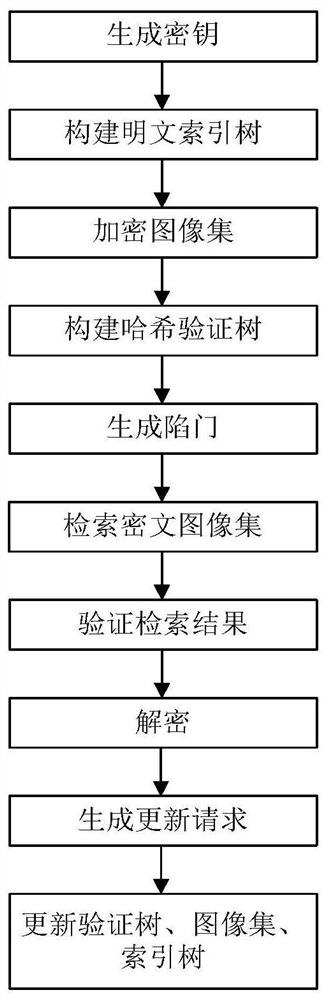
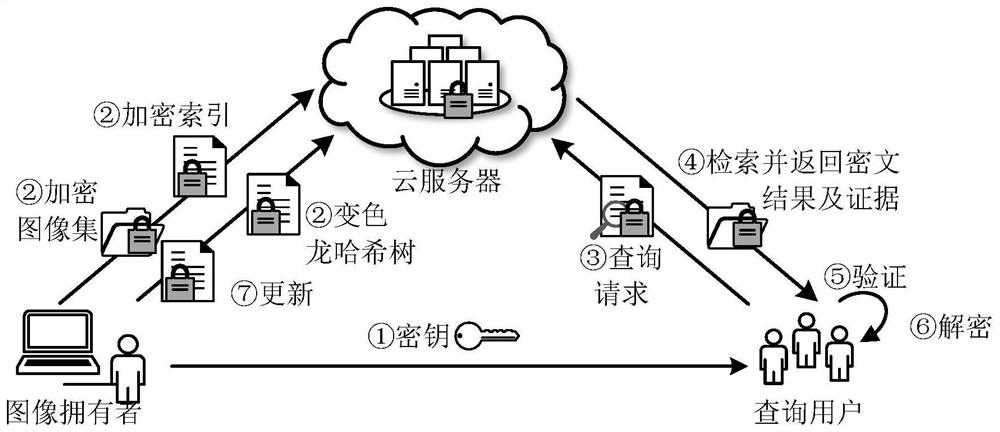
Verifiable encrypted image retrieval method supporting dynamic updating
PendingCN113569280ARealize dynamic updateImprove retrieval accuracyStill image data indexingDigital data protectionCiphertextImage retrieval
The invention discloses a verifiable encrypted image retrieval method supporting dynamic updating. An image owner initializes a system to generate a key and distributes the key to a query user; a data owner encrypts an image set, constructs an encryption index, generates a chameleon hash verification tree, and stores the encrypted image set, the encryption index and the chameleon hash verification tree to a cloud server; a query user generates a query request and submits the query request to the cloud server; when the cloud server receives a query request, the cloud server finds the first k image data ciphertexts with the maximum relevancy value based on the encryption index and the query request and generates corresponding evidences, and a ciphertext image retrieval result and the corresponding evidences are returned to a query user together; the correctness of a retrieval result in a dynamic environment is verified by using a chameleon-based Hash verification tree, and if verification succeeds, a query user to decrypt a plaintext image; and the image owner sends the information needing to be updated to the cloud server so as to realize dynamic updating of the image set.
Owner:XIDIAN UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com