File encryption and decryption methods and terminals
A file encryption and terminal technology, applied in the field of communications, to limit random dissemination or copying, strong confidentiality, and effective and reliable passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
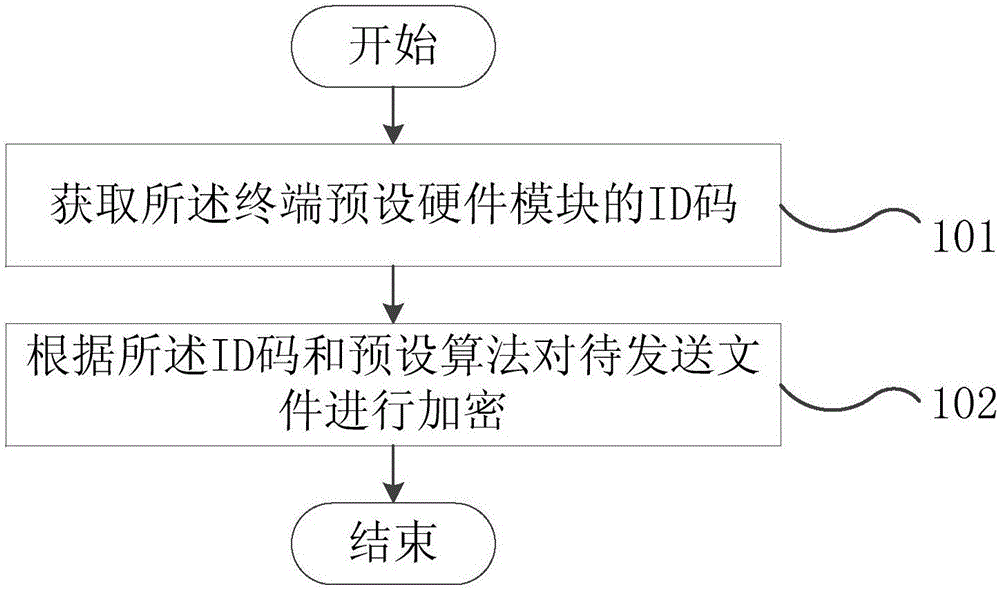
[0025] The implementation of the present invention provides a method for encrypting files, such as figure 1 shown, including:
[0026] Step 101, acquiring the ID code of the preset hardware module of the terminal.
[0027] In this step, the hardware module includes at least one of CPU, RAM, GPU, or CCM of the terminal. Before sending the encrypted file, the sender loads a control program module. The sender pre-sets at least one of the bound hardware modules through the loaded control program module. After the receiving terminal receives the file, the control program module automatically obtains the received The ID code corresponding to the bound hardware module in the terminal, and encrypts the file according to the ID code of the hardware module. Therefore, when decrypting, the encrypted file can only be decrypted according to the ID code of the hardware module of the receiving terminal, so when the recipient uses the receiving terminal to decrypt, the encrypted file can on...
no. 2 example
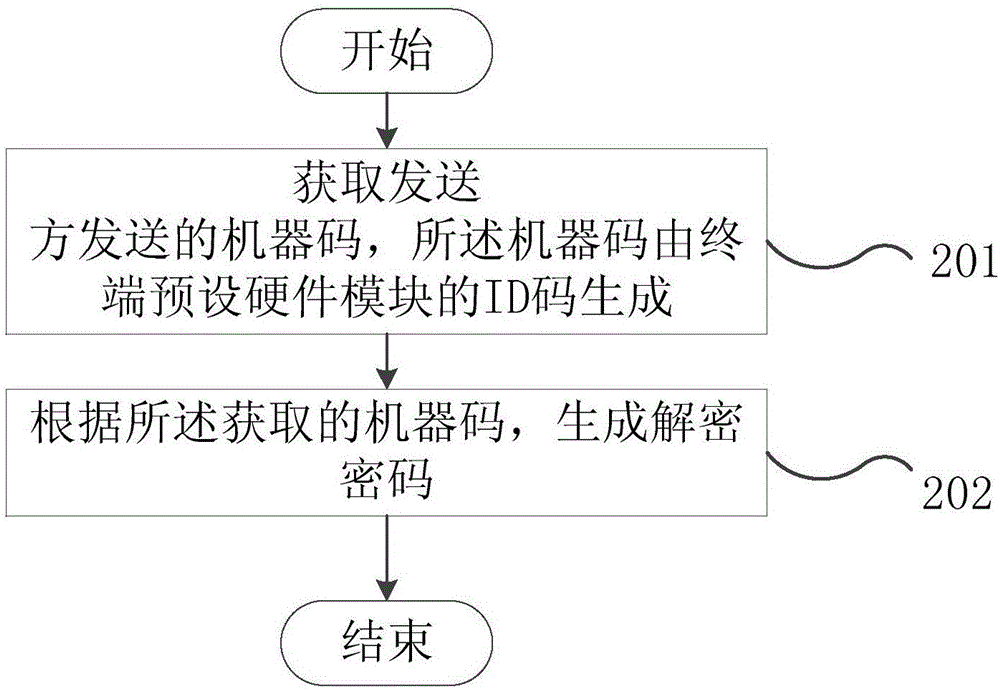
[0038] The embodiment of the present invention provides a method for file decryption, such as figure 2 As shown, the method includes:
[0039] Step 201, acquire the machine code sent by the sender, and the machine code is generated by the ID code of the terminal preset hardware module.
[0040] In this step, the hardware module includes at least one of CPU, RAM, GPU, or CCM of the mobile terminal. The ID code of the hardware module is the unique identification of the hardware module. When the recipient receives the encrypted file and decrypts it, a dialog box showing the machine code information of the receiving terminal and an input box asking for the decryption password pops up, and the recipient can complete the decryption operation only by inputting the decryption password in the decryption password input box. The machine code is generated by the control program module set by the sender according to the ID code of the hardware module of the receiving terminal, and sent ...
no. 3 example
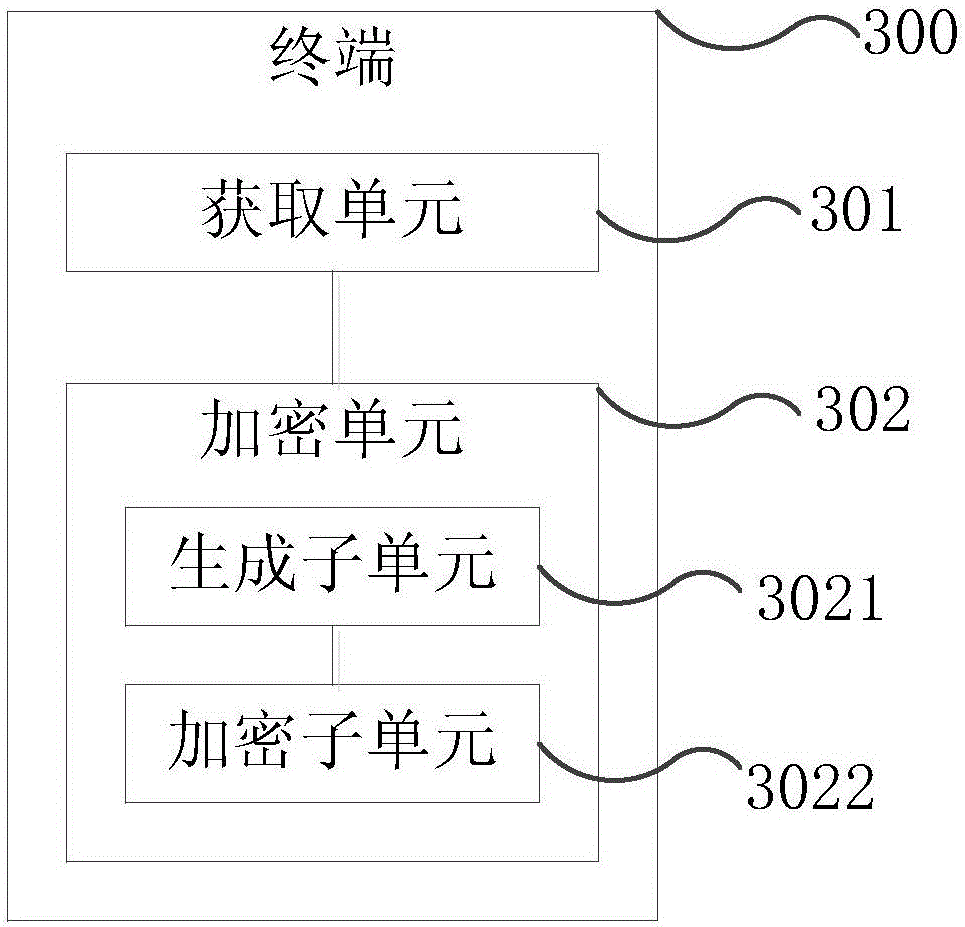
[0045] A kind of file encryption terminal provided by the implementation of the present invention, such as image 3 As shown, the terminal 300 includes:
[0046] An acquisition unit 301, configured to acquire the ID code of the preset hardware module of the terminal;
[0047] An encryption unit 302, configured to encrypt the file to be sent according to the ID code and a preset algorithm.
[0048] Wherein, the hardware module includes at least one of CPU, RAM, GPU, or CCM of the terminal.
[0049] Further, at image 3 On the basis of this, the terminal 300 also includes:
[0050] The encryption unit 302 includes:
[0051] generating subunit 3021, configured to generate a machine code according to the ID code;
[0052]The encryption subunit 3022 is configured to encrypt the file to be sent according to the machine code and a preset algorithm.
[0053] In the terminal provided in this embodiment, the ID code of the preset hardware module of the receiving terminal is obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com