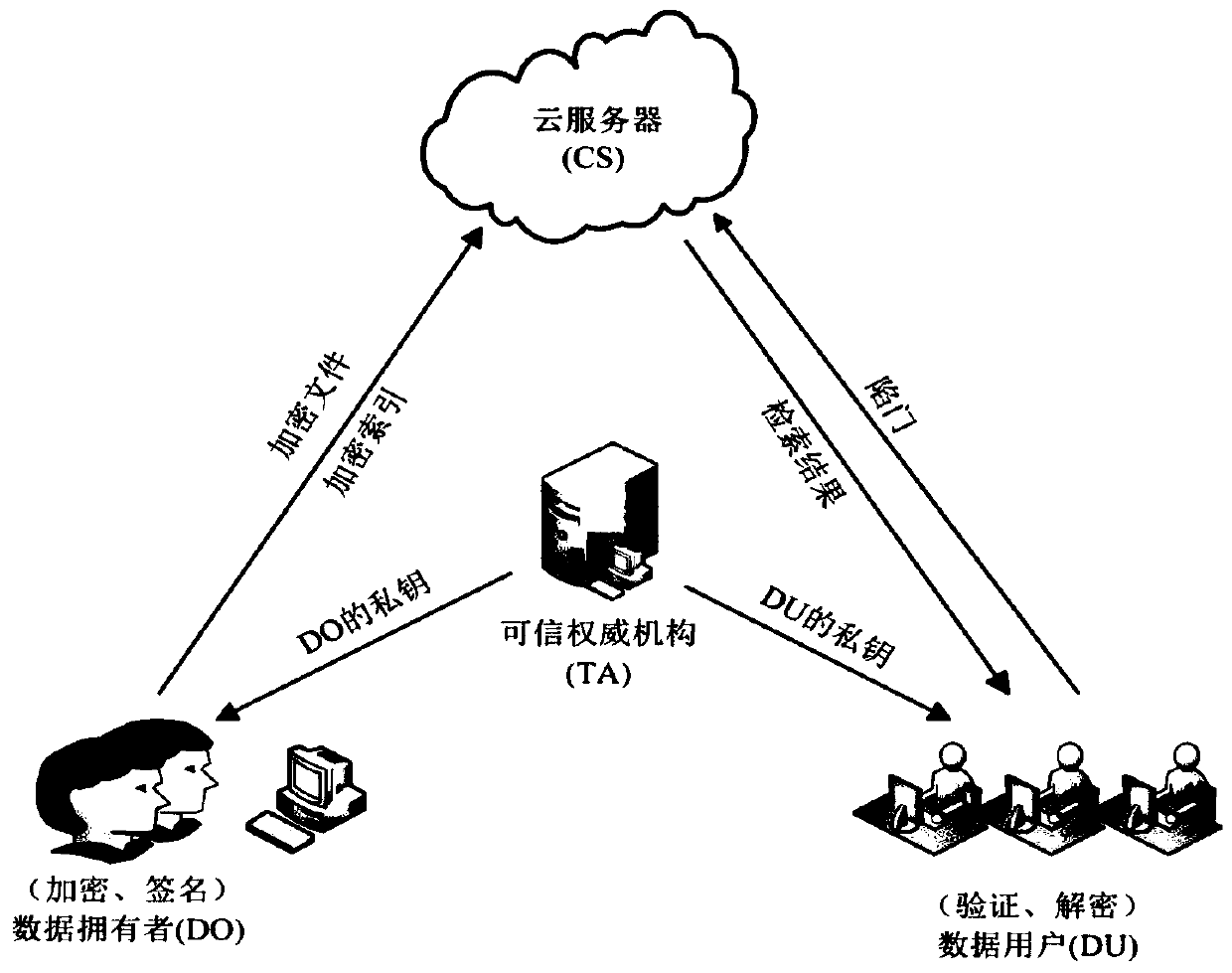
Verifiable encryption and decryption method supporting multi-keyword weighted retrieval and result sorting
A keyword, encrypted file technology, applied in digital data information retrieval, unstructured text data retrieval, special data processing applications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
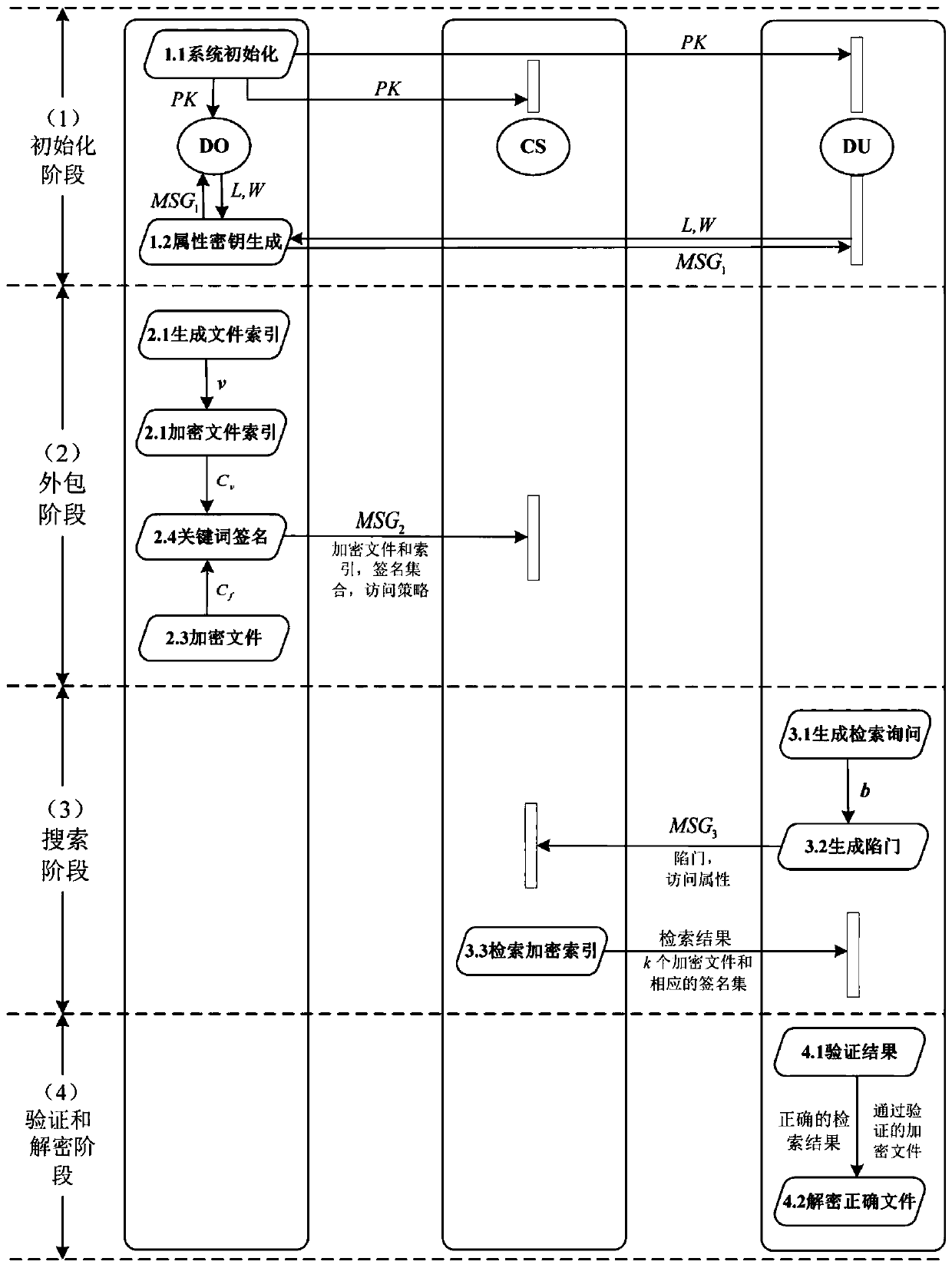
[0081] Support multi-keyword weighted retrieval and result sorting and verifiable encryption and decryption methods, such as figure 2 As shown, it specifically includes the following steps:
[0082] 1) System establishment
[0083] 1.1) Generate keyword dictionary and attribute set
[0084] First, the trusted authority TA pre-defines the system keyword dictionary K={k 1 ,k 2 ,k 3 ,k 4 ,k 5 ,k 6} and attribute set Att={att 1 ,att 2 ,att 3 ,att 4 ,att 5 ,att 6}, where k 1 Indicates cloud storage technology, k 2 Indicates deduplication technology, k 3 Indicates the retrieval technique, k 4 Indicates the audit technique, k 5 Indicates blockchain technology, k 6 Represents machine learning techniques. att 1 Indicates the user's country, att 2 Indicates the province to which the user belongs, att 3 Indicates the city to which the user belongs, att 4 Indicates user gender, att 5 Indicates whether the user is married, att 6 Indicates the user's graduation sch...
Embodiment 2
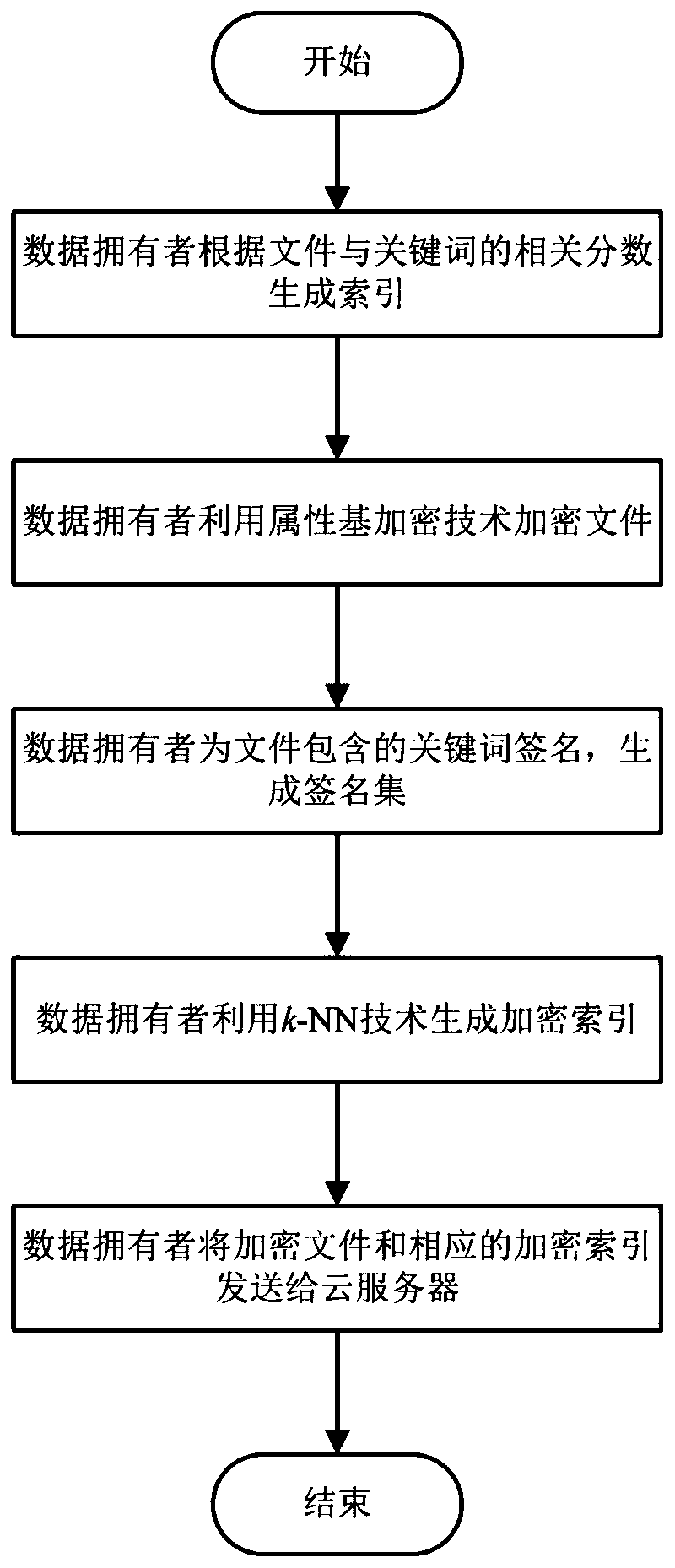
[0114] Such as image 3 As shown, on the basis of Embodiment 1, when the data owner DO needs to store files, the encrypted file, encrypted file index and file keyword signature set are uploaded. Data owner DO of uploaded file f 1 For example, the specific steps are as follows:
[0115] 2.1) Generate file index
[0116] Data Owner DO 1 Generate d(d=6) dimension keyword index u=(u according to file f 1 , u 2 ,...,u 6 ), where u i (1≤i≤6) means keyword k i The correlation score Score(k j ,f)=TF j ×IDF j ,1≤j≤6, where (wherein the term frequency TF shows the frequency of the keyword in the file, and the inverse document frequency IDF shows the importance of the keyword in the entire file set, specifically, n j Indicates the keyword k j Frequency of occurrence in file f; |f| means {n j}; N represents the number of files in the entire collection; N j Indicates that it contains the keyword k j number of files);
[0117] 2.2) Encrypted file index
[0118] Data Own...
Embodiment 3
[0128] On the basis of Embodiment 1, when a data user DU needs to retrieve a file, he needs to Figure 4 Steps to generate a trapdoor and send it to the cloud server CS; the cloud server CS then according to Figure 5 Steps to retrieve the files in the cloud through the trapdoor, and finally return the retrieved files to the data user DU. Data User DU 1 For example, the specific steps are as follows:
[0129] 3.1) Generate search query
[0130] data user DU 1 According to the keyword dictionary K of the system, generate a multi-keyword set K' to be asked, and then generate keyword weights a=(a 1 ,a 2 ,...,a 6 ),in
[0131] For example, DU 1 Need to retrieve keywords containing k 3 (retrieval technique) and k 6 (Machine learning technology) For files with two keywords, the weighted values corresponding to the two keywords are 0.4 and 0.6 respectively. The larger the weight value, the more important the keyword, and the data user DU 1 The weighted search query for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com