Three-level secret key encryption system
An encryption system and secret key technology, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as file exposure and secret key security difficulties, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
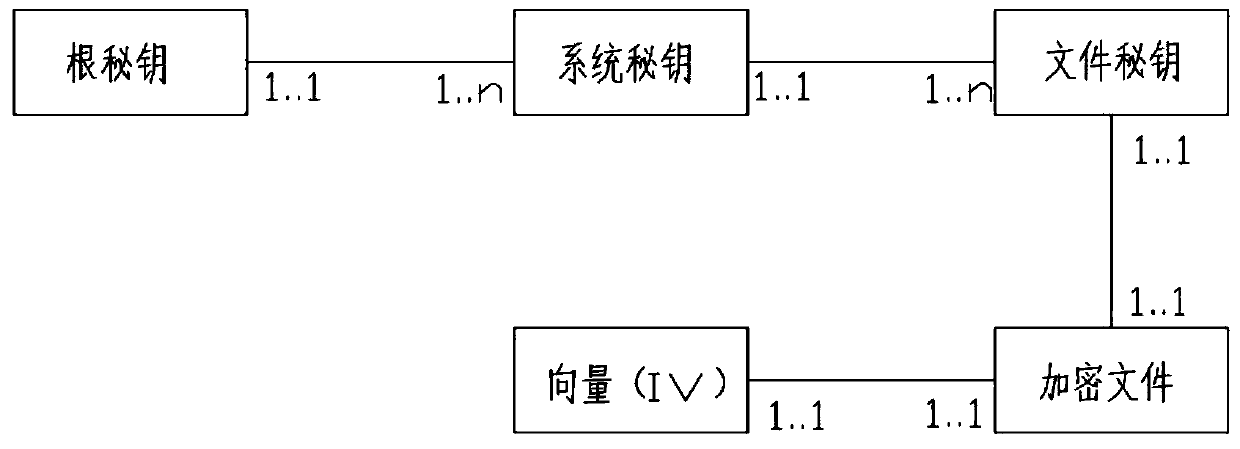
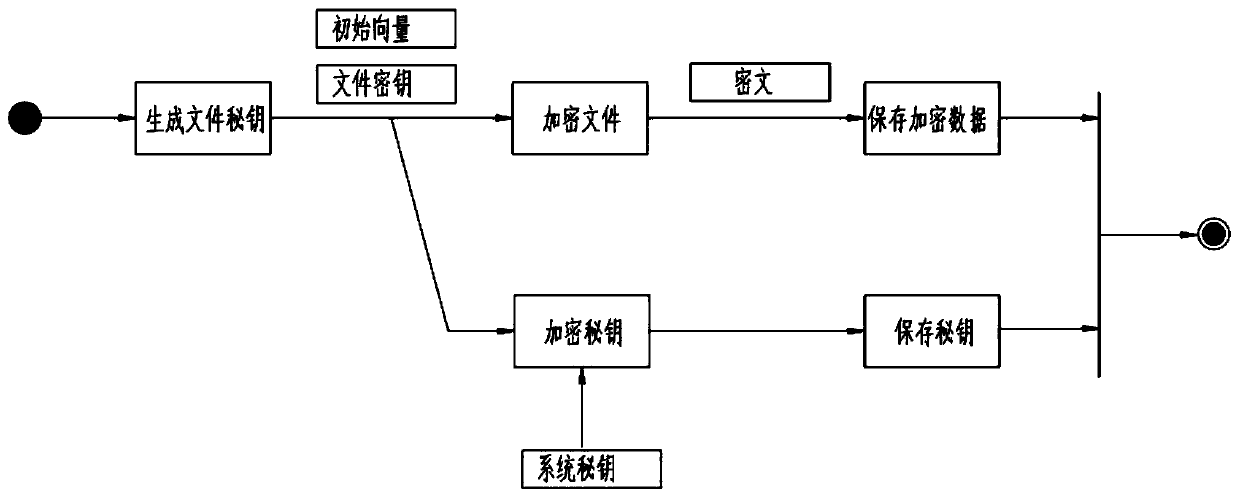
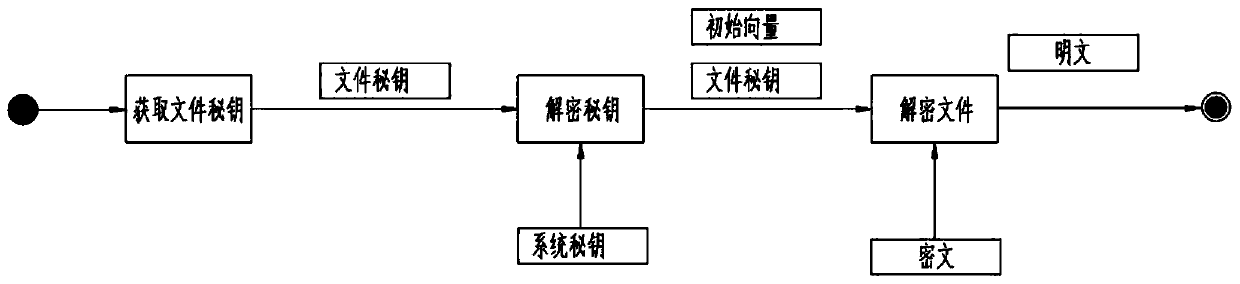
[0028] combined with Figure 1~3 , a three-level secret key encryption system, comprising the following steps:
[0029] S1. The third-level secret key includes the root secret key that is solidified in the program and is only used to encrypt the system secret key, the system secret key that can be dynamically modified, and the file secret key corresponding to the file produced by a random algorithm; the initialization of the system secret key and After the system goes online, the system administrator triggers the generation function through the interface. The server sets a random key and does not transmit it to the client. The operator cannot access the content of the key. The file key is generated using a secure random algorithm when encrypting files. The client cannot access the key content.
[0030] S2. File encryption: The encryption algorithm adopts a symmetric encryption algorithm, using a 256-bit secret key and CBC mode. Each file is configured with a file secret key a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com