Credible encryption system and method
An encryption system and reliable technology, applied in the field of encryption to achieve the effect of ensuring security and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
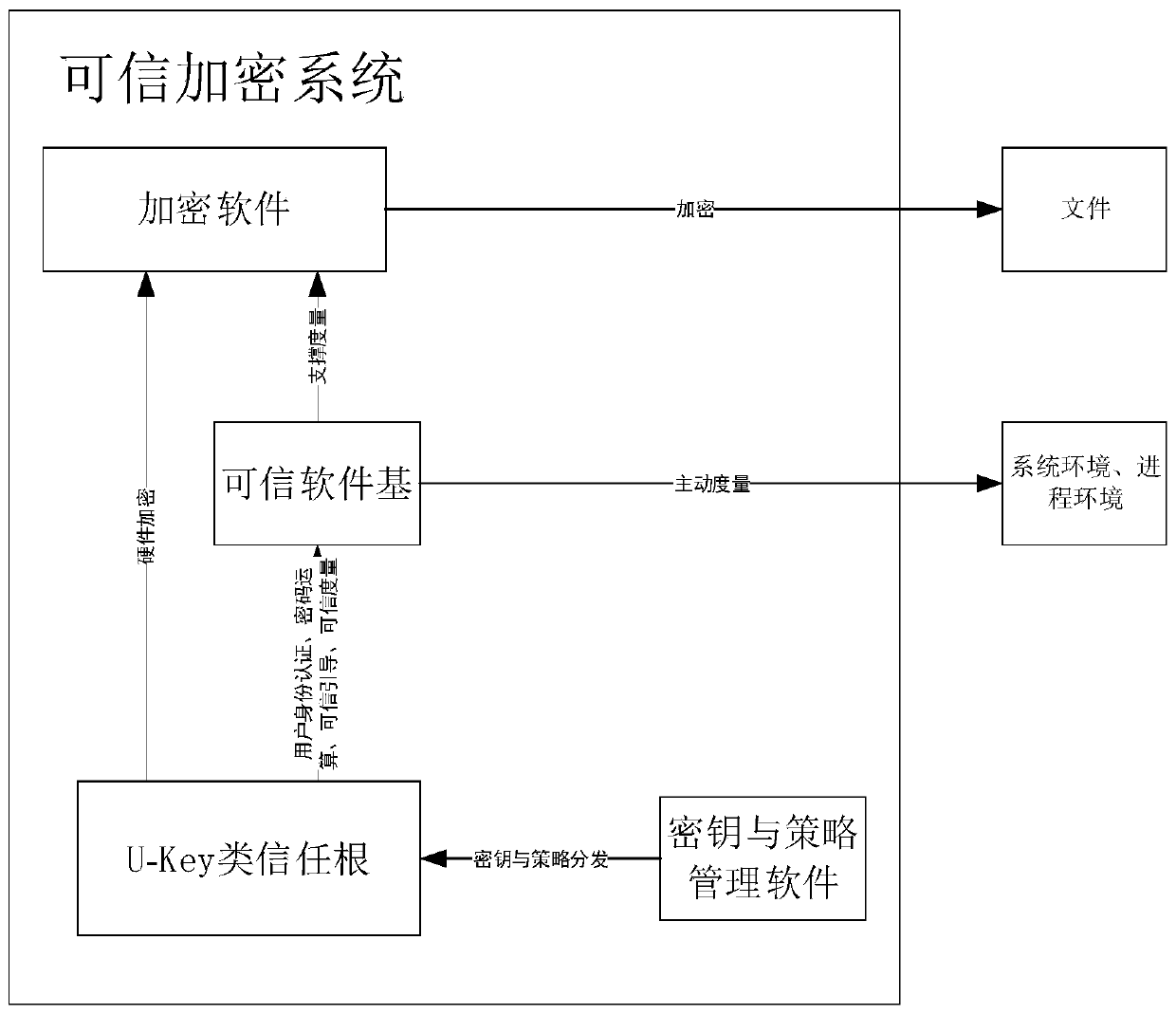
[0136] The trusted encryption method mainly includes a startup process and an encryption and decryption process.
[0137] Startup process:
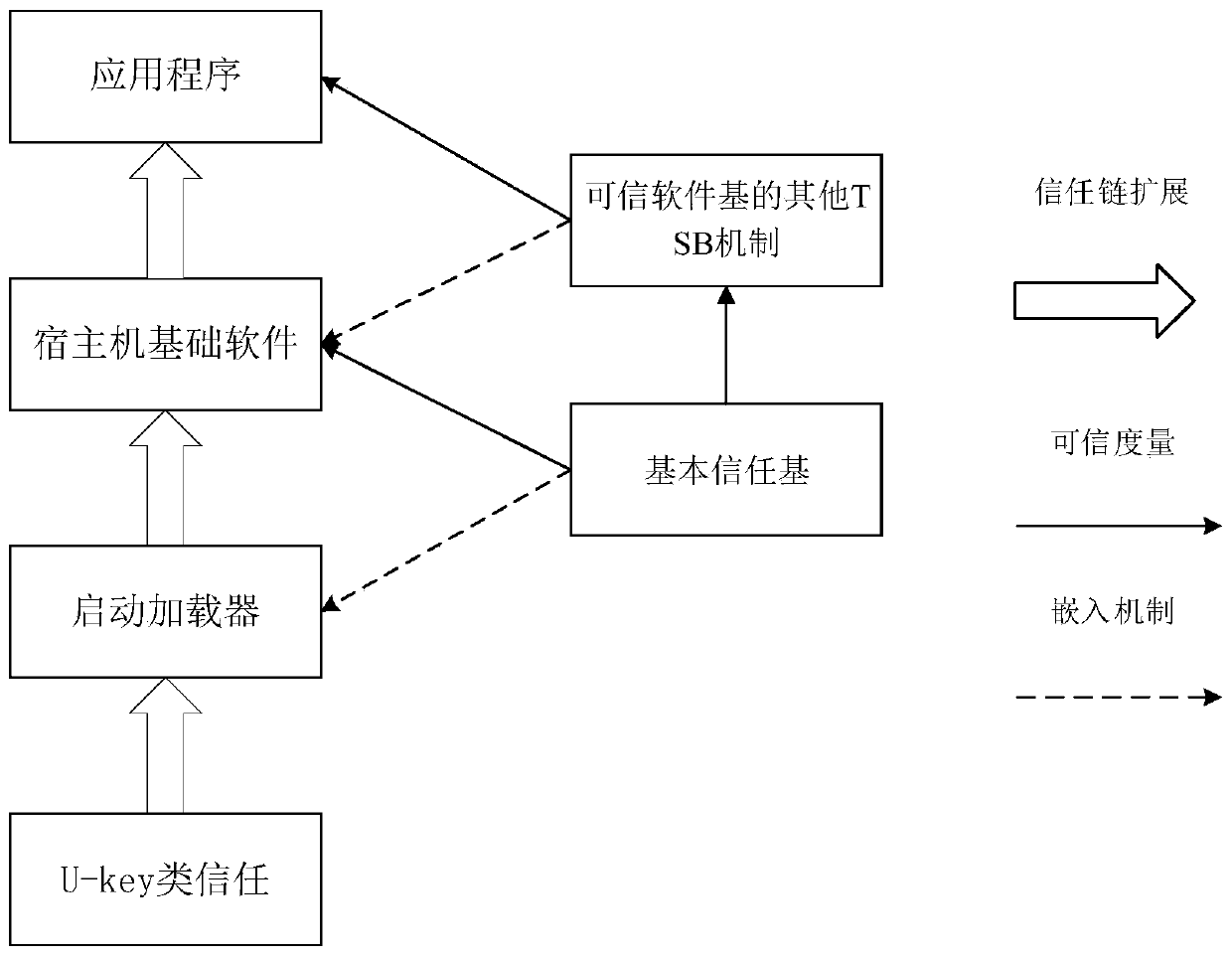
[0138] The start-up process is the pre-process of the encryption and decryption process. By restarting the computer and using the U-Key trust root to measure the credibility of the initial state environment of the system and applications, a trust chain is established to ensure that the next stage of trusted software base and explicit / Implicitly encrypts the security of software applications.
[0139] The startup process is to insert the root of trust->start the computer->root of trust boot measurement->trusted software base startup measurement environment->explicit / implicit encryption software startup.
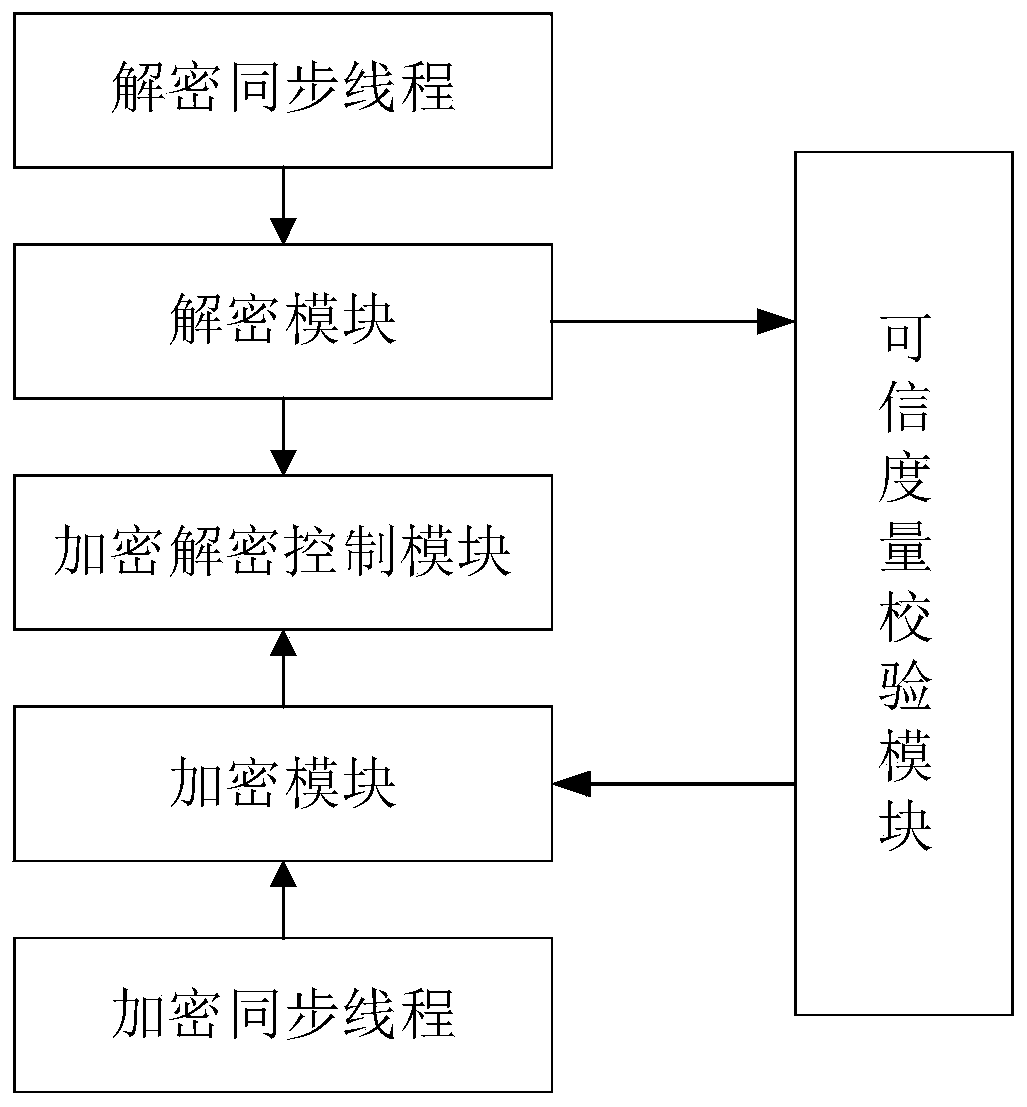
[0140] Encryption and decryption process:
[0141] The encryption and decryption process is the main process of encryption, which involves the mutual cooperation of multiple processes such as U-Key trust root, trusted software base, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com