Patents
Literature
88 results about "Software work" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
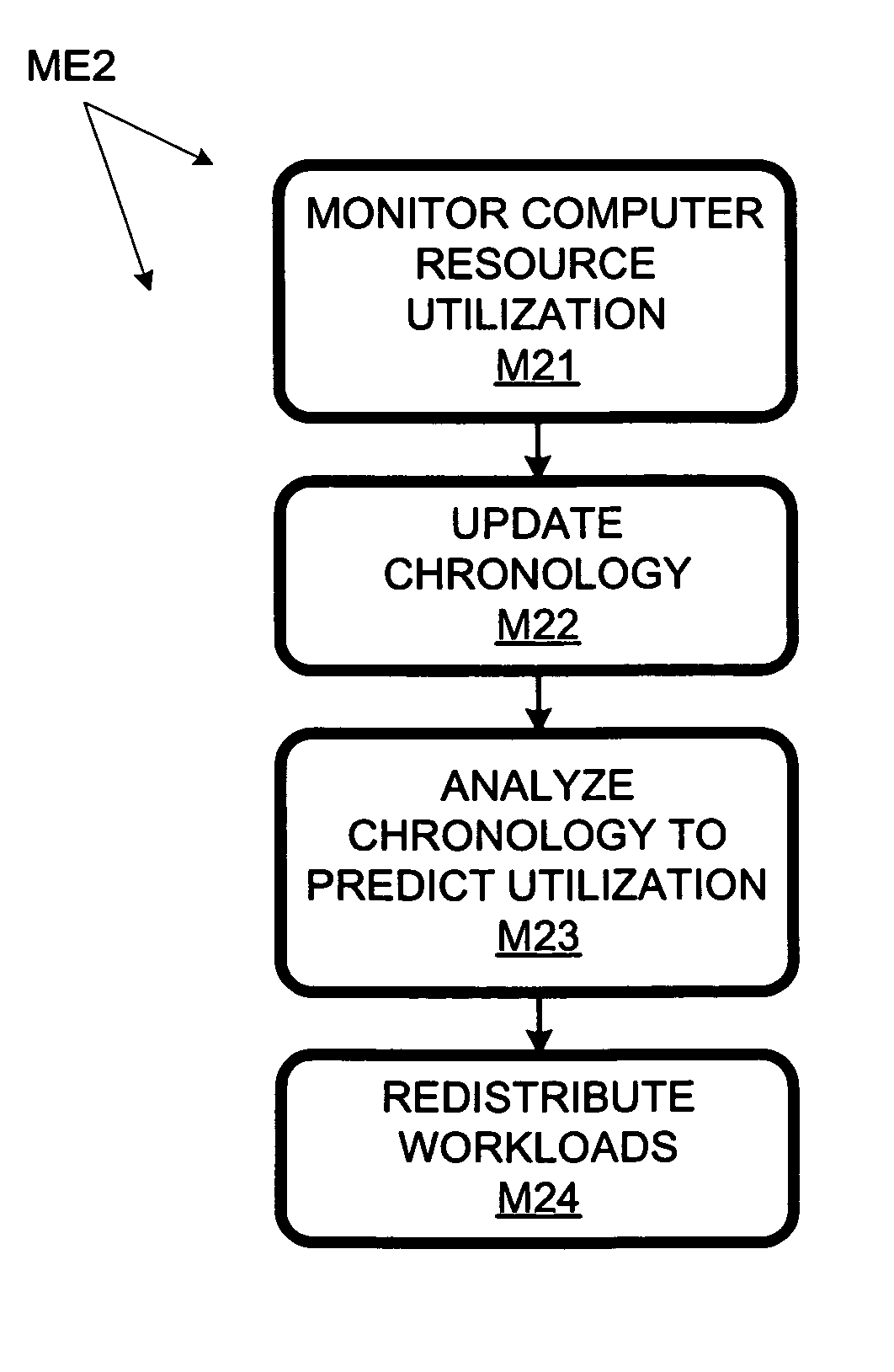
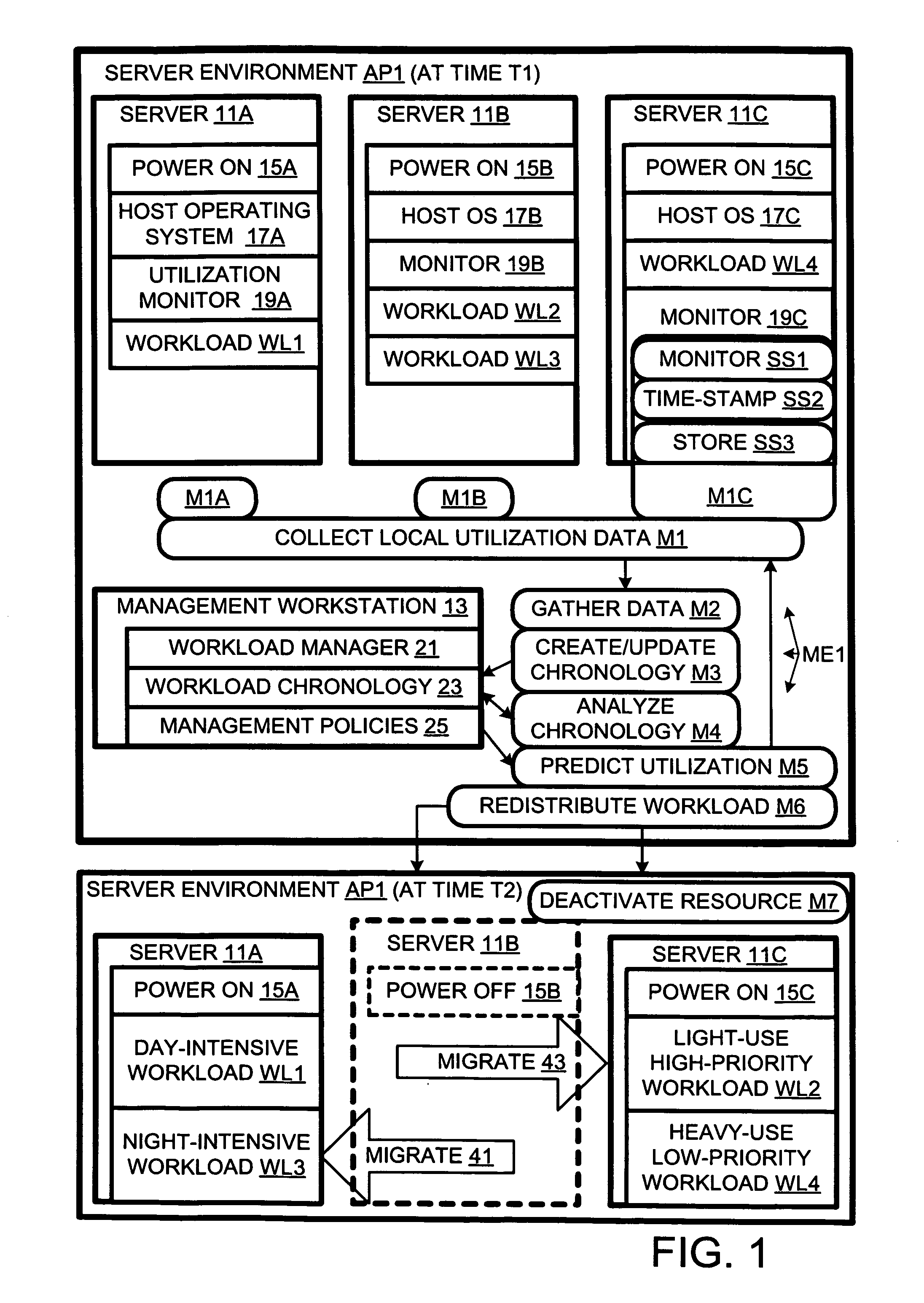
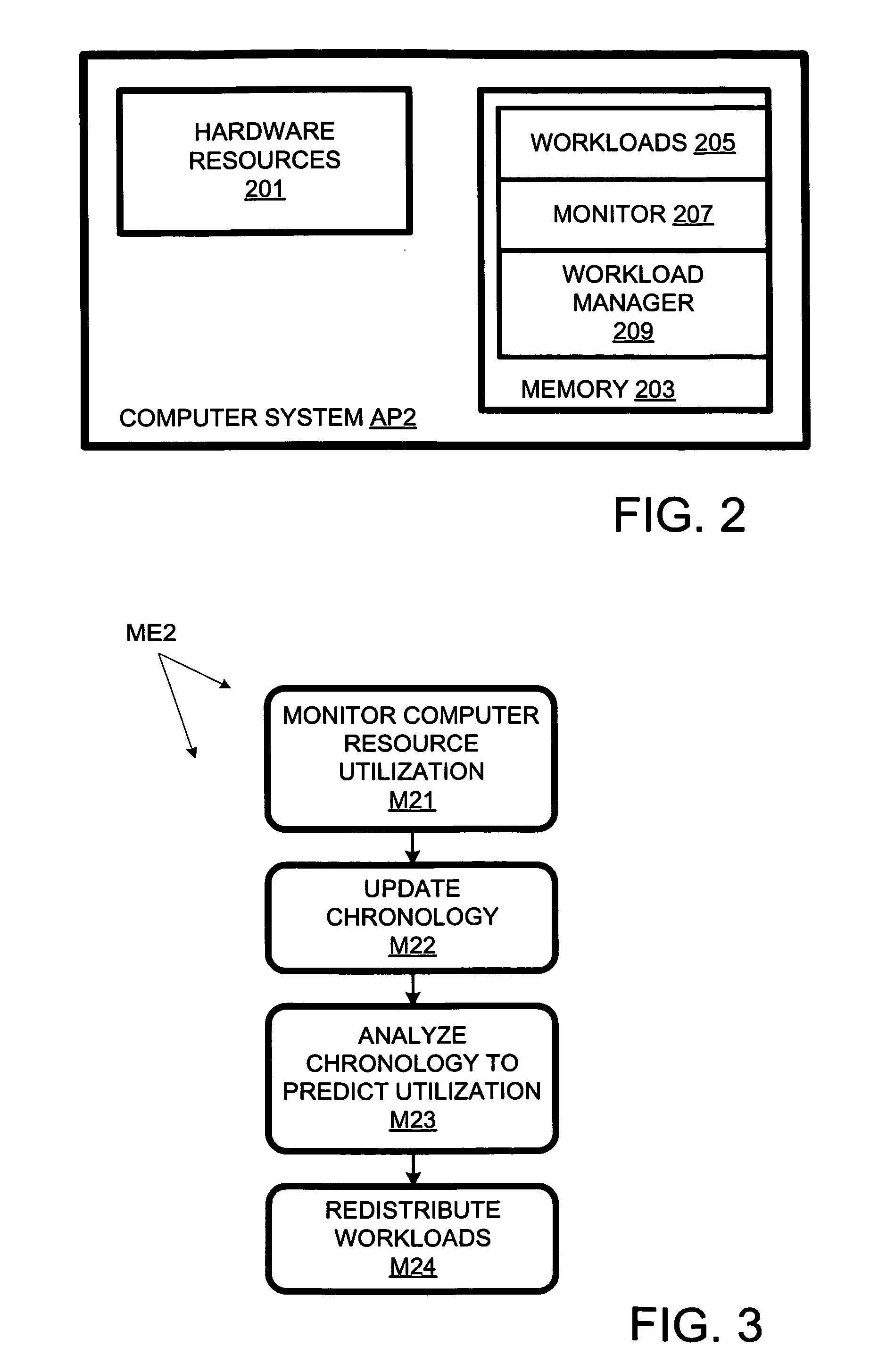
Computer workload redistribution
ActiveUS20070250838A1Error detection/correctionVolume/mass flow measurementComputer resourcesResource utilization
The present invention provides for redistributing workloads among computers to optimize resource utilization. Utilization by software workloads of computer resources is monitored to yield utilization data. A utilization chronology is updated using the utilization data. The chronology is analyzed to yield resource utilization predictions. The workloads are redistributed among the resources at least in part as function of said predictions.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
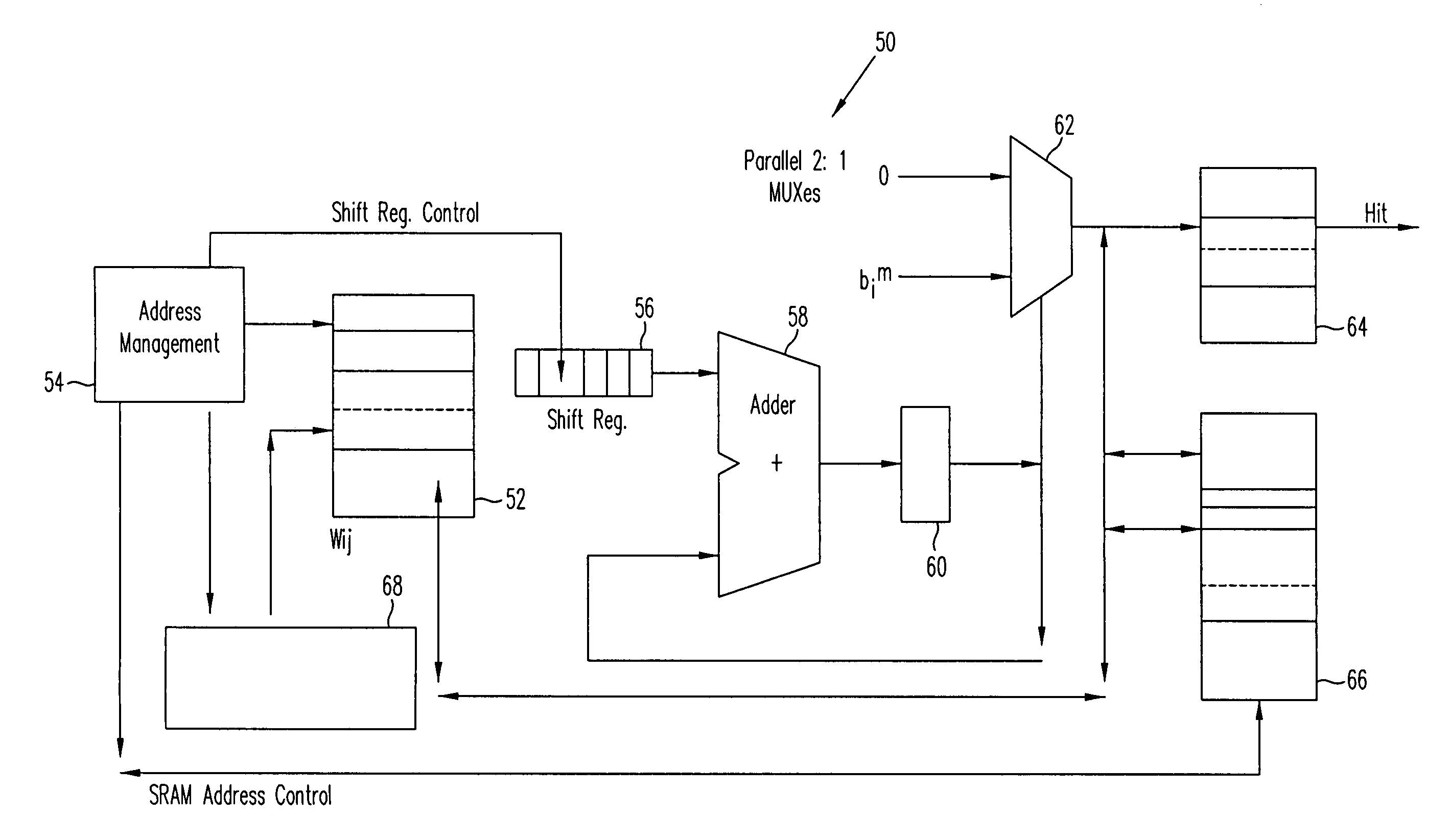
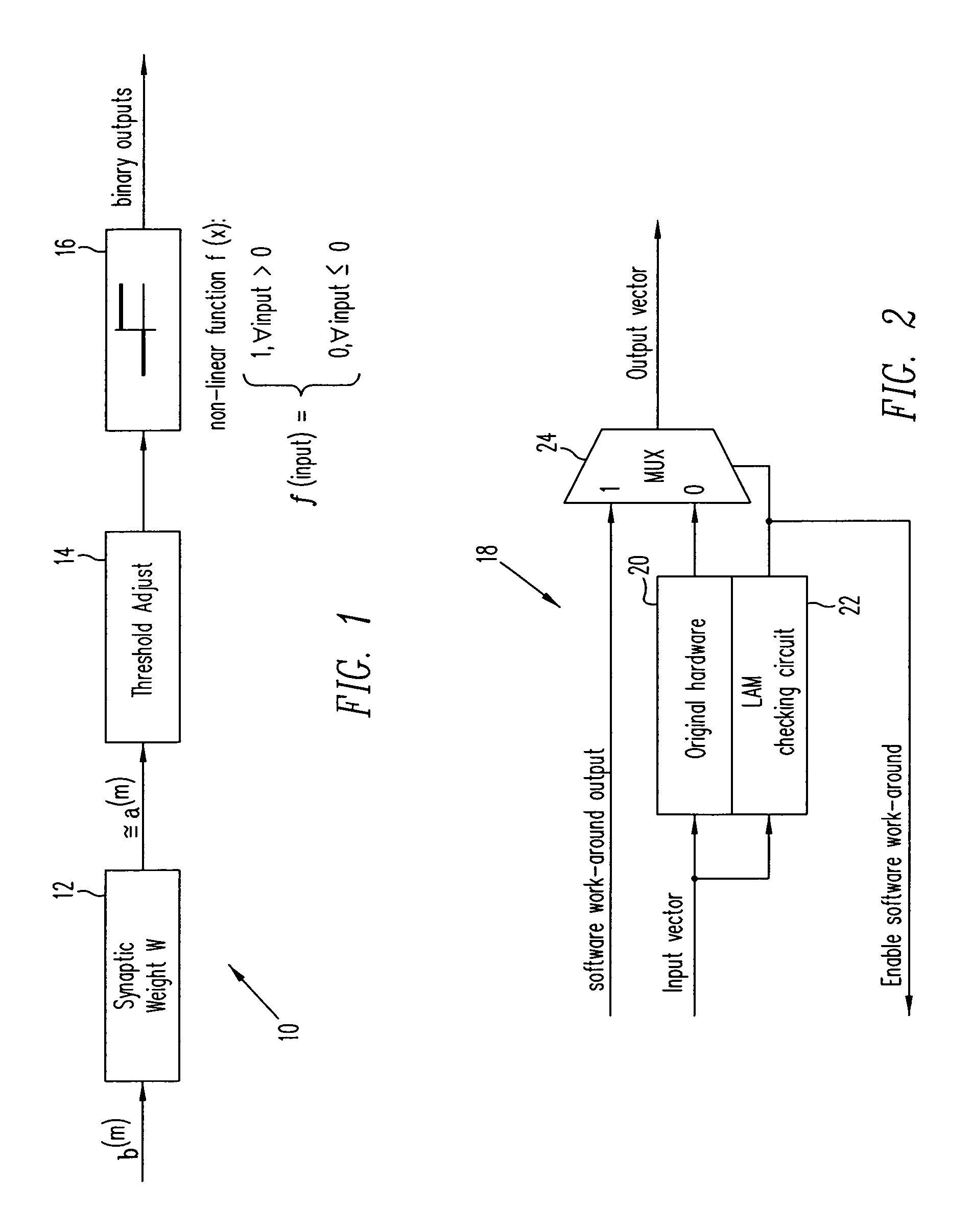
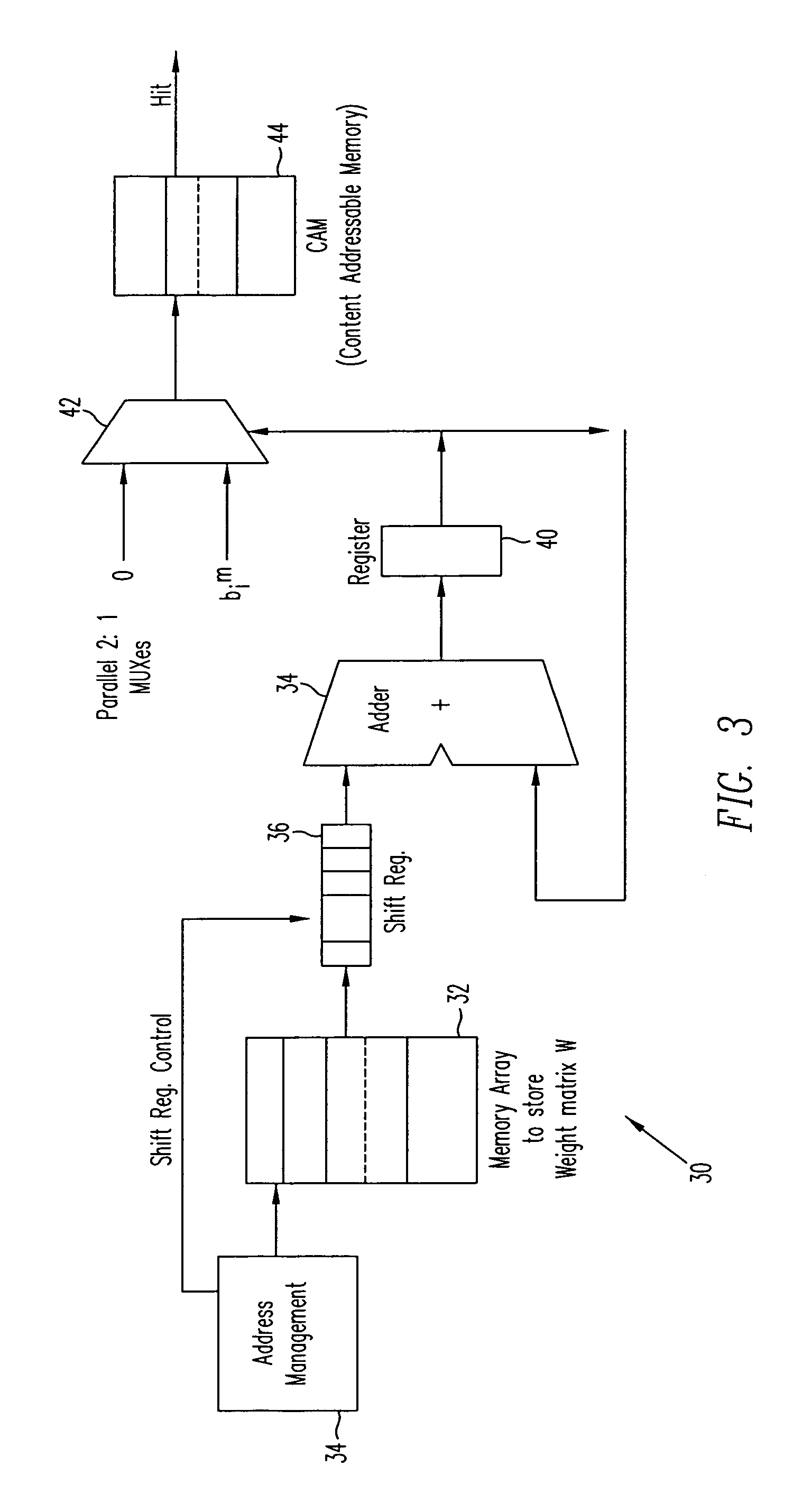
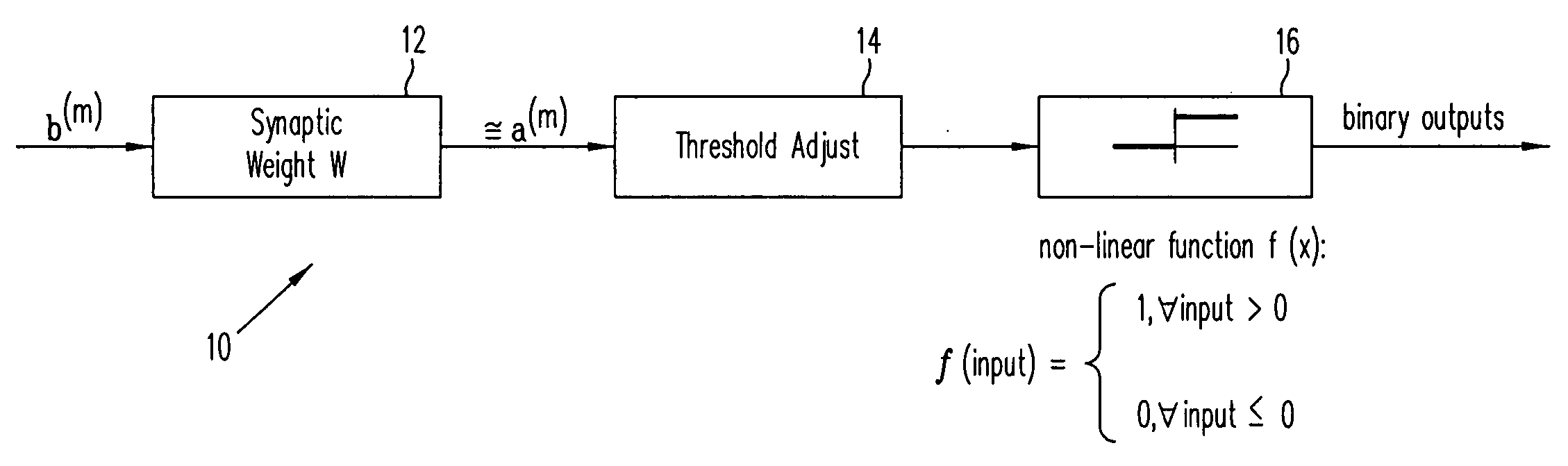
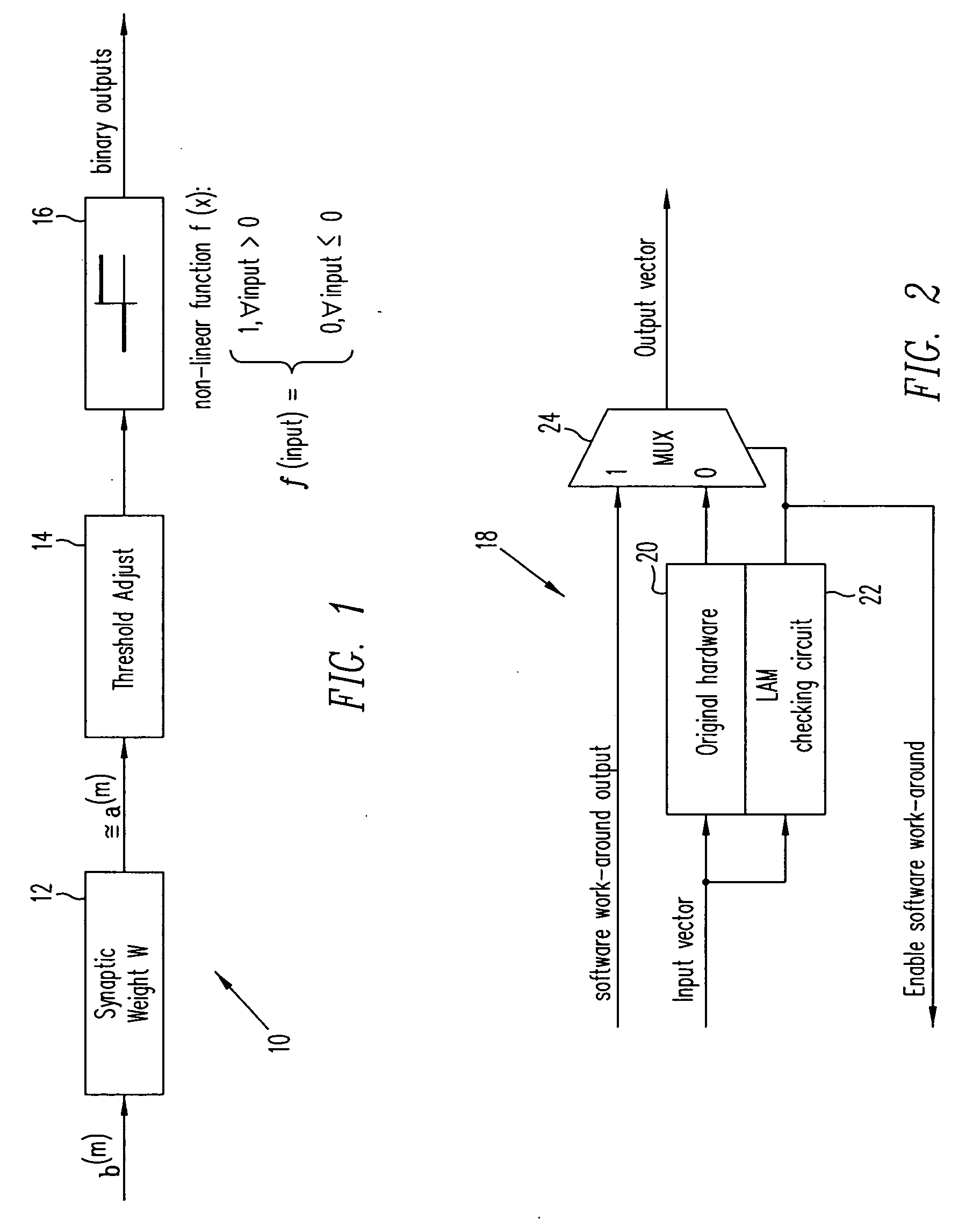
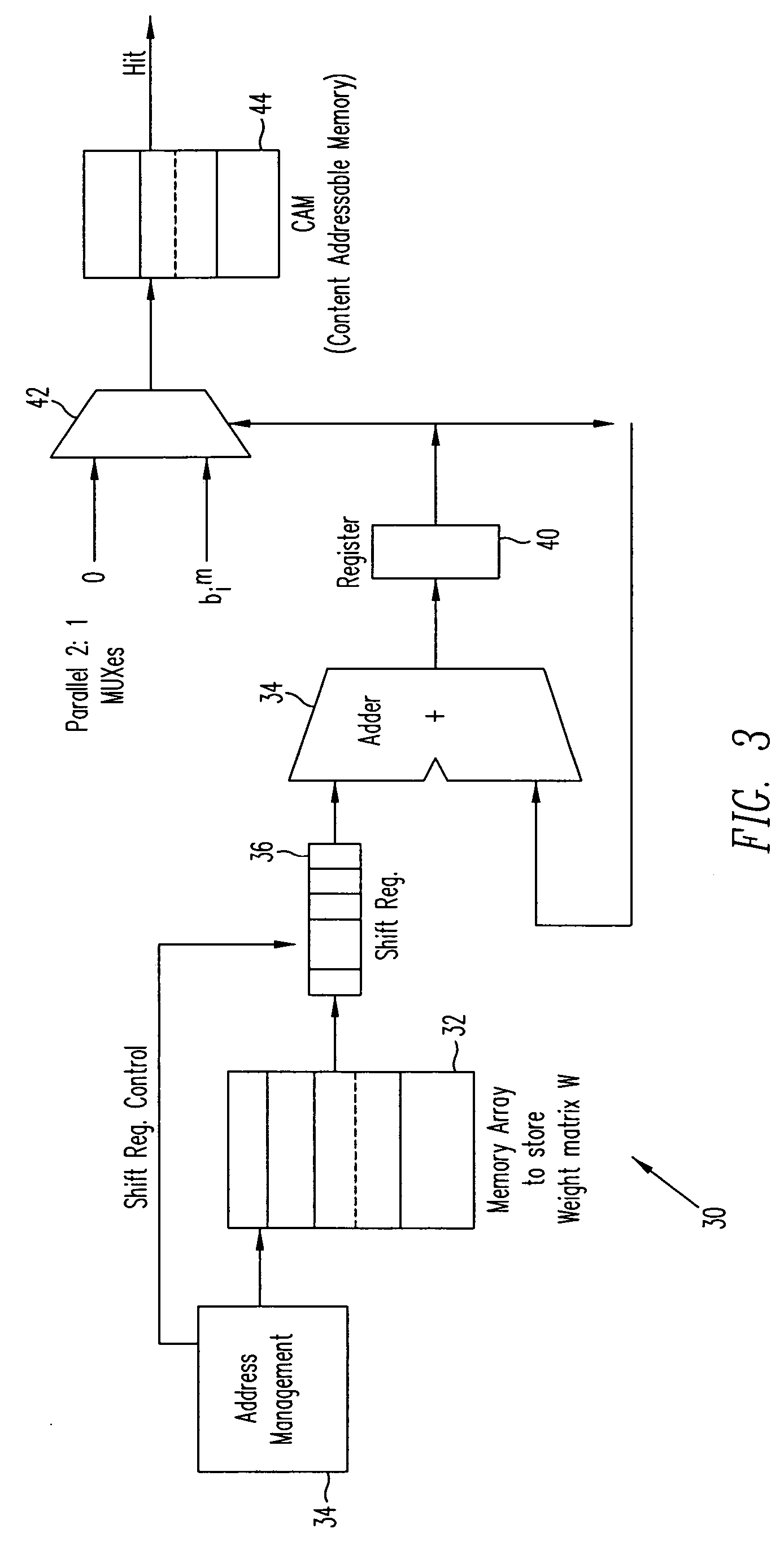
Linear associative memory-based hardware architecture for fault tolerant ASIC/FPGA work-around
A programmable logic unit (e.g., an ASIC or FPGA) having a feedforward linear associative memory (LAM) neural network checking circuit which classifies input vectors to a faulty hardware block as either good or not good and, when a new input vector is classified as not good, blocks a corresponding output vector of the faulty hardware block, enables a software work-around for the new input vector, and accepts the software work-around input as the output vector of the programmable logic circuit. The feedforward LAM neural network checking circuit has a weight matrix whose elements are based on a set of known bad input vectors for said faulty hardware block. The feedforward LAM neural network checking circuit may update the weight matrix online using one or more additional bad input vectors. A discrete Hopfield algorithm is used to calculate the weight matrix W. The feedforward LAM neural network checking circuit calculates an output vector a(m) by multiplying the weight matrix W by the new input vector b(m), that is, a(m)=wb(m), adjusts elements of the output vector a(m) by respective thresholds, and processes the elements using a plurality of non-linear units to provide an output of 1 when a given adjusted element is positive, and provide an output of 0 when a given adjusted element is not positive. If a vector constructed of the outputs of these non-linear units matches with an entry in a content-addressable memory (CAM) storing the set of known bad vectors (a CAM hit), then the new input vector is classified as not good.
Owner:CISCO TECH INC
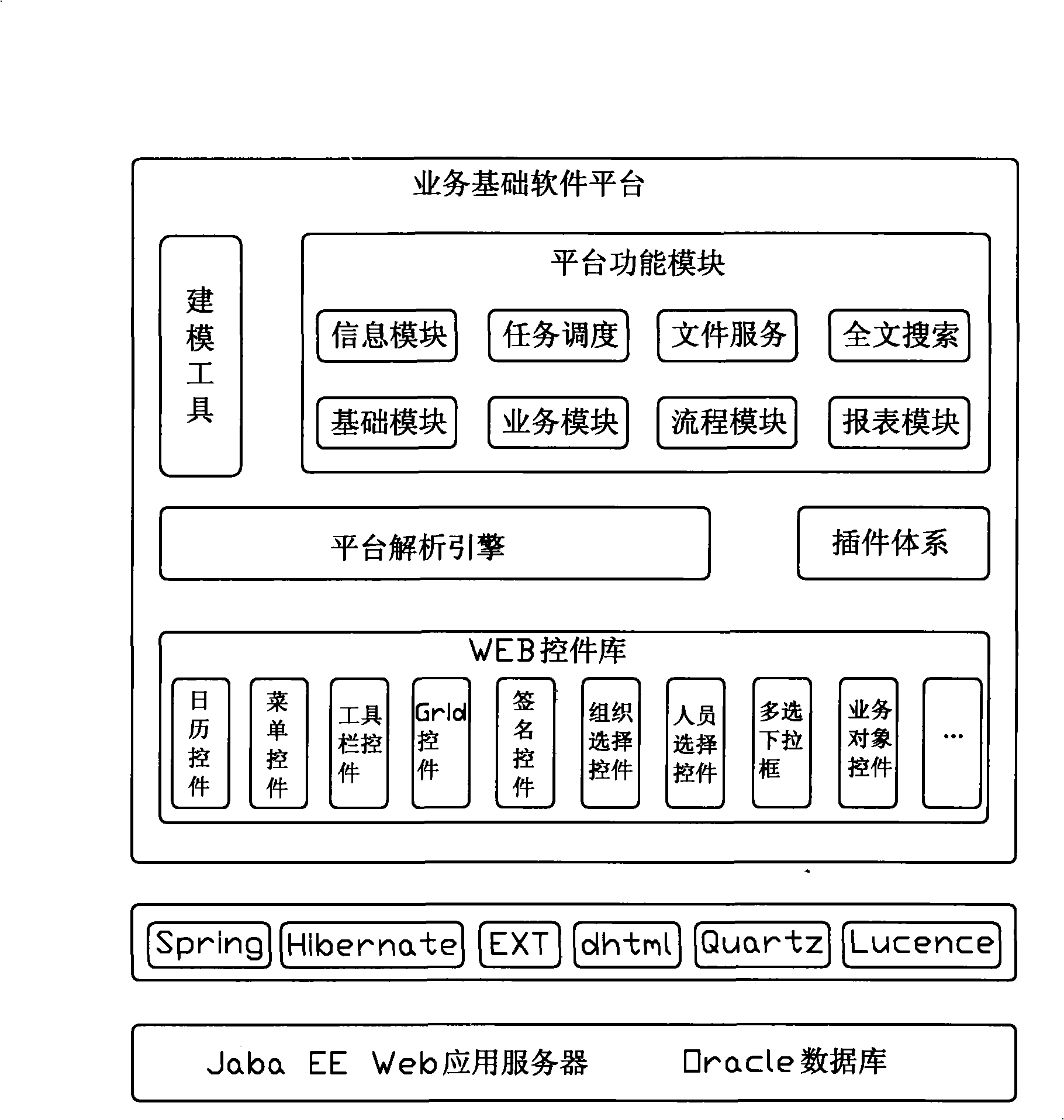
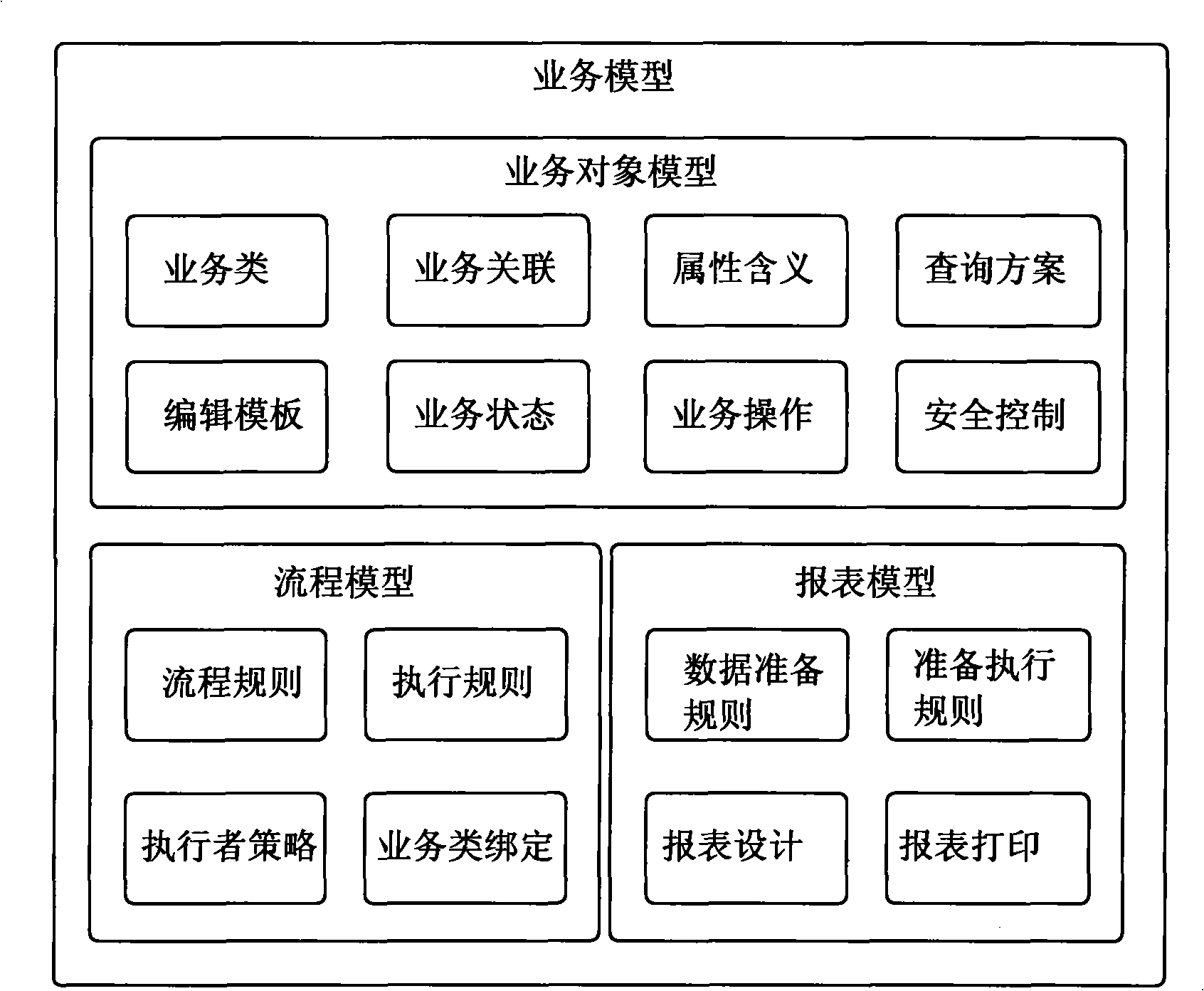
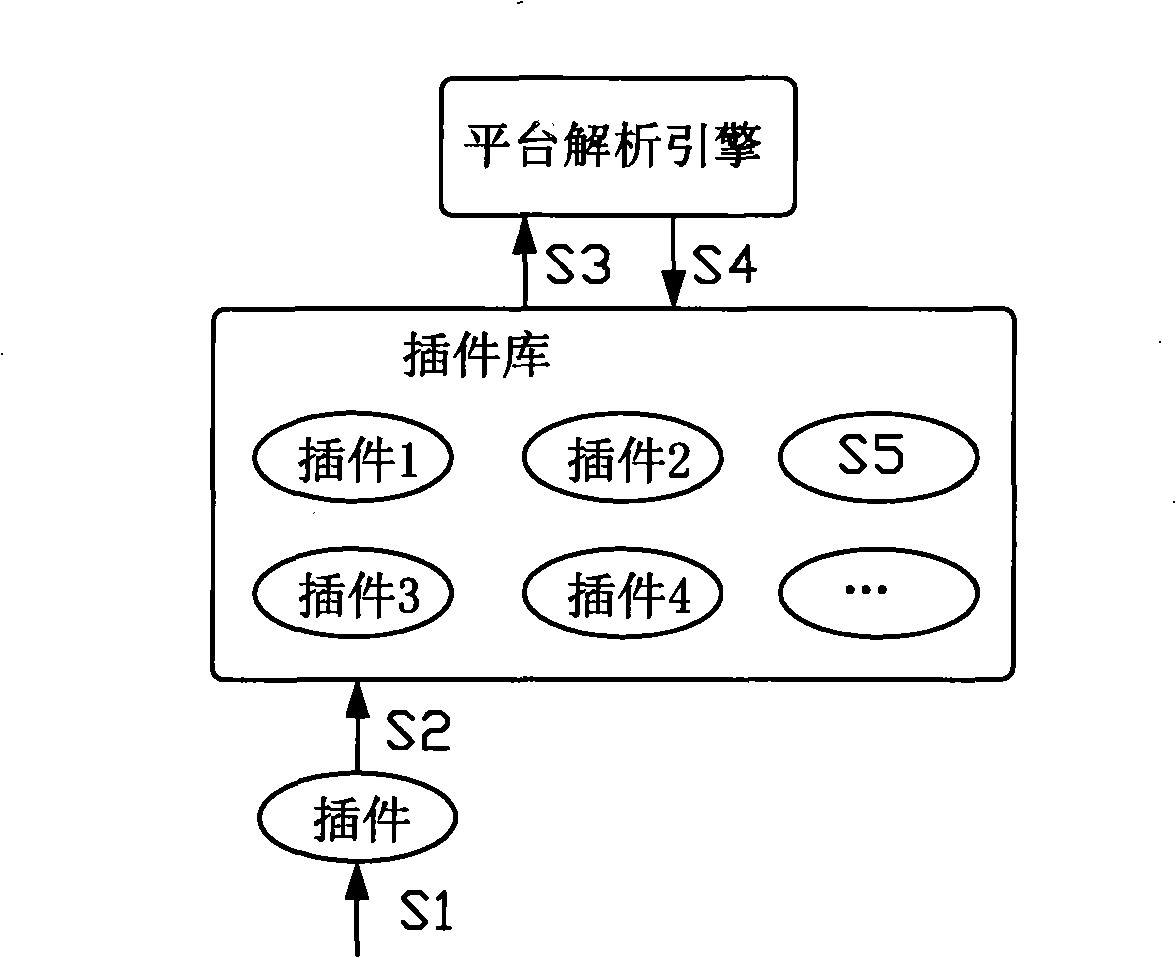
Service basic software platform
InactiveCN101539855AIncrease production capacitySpecific program execution arrangementsPersonalizationService model
The invention relates to a service basic software platform, which comprises a modeling tool, a service analysis engine and a plug-in unit system, wherein the modeling tool is used for processing service universal requirements, defines a service model through property configuration and graph configuration, and catties out high-speed buffer for the service model; the service analysis engine analyzes the buffered service model and instantiates a final service system; and the plug-in unit system writes a plug-in unit in native languages, and transfers a corresponding plug-in unit to process service personalized requirements in the process of analyzing the service model by the service analysis engine. On the basis of a point of view that the service basic software platform needs to serve for developers but not non-service personnel, the service basic software platform uses model drive to reach the service universal requirements, and uses a native code plug-in unit to achieve the service personalized requirements so as to ensure that the model drive logic and the plug-in unit code achievement logic are tightly integrated, and the software developers are released from complicated software works so as to pay close attention to development works which need personalized processing, and improve the software productivity.
Owner:XIAMEN GREAT POWER GEO INFORMATION TECH
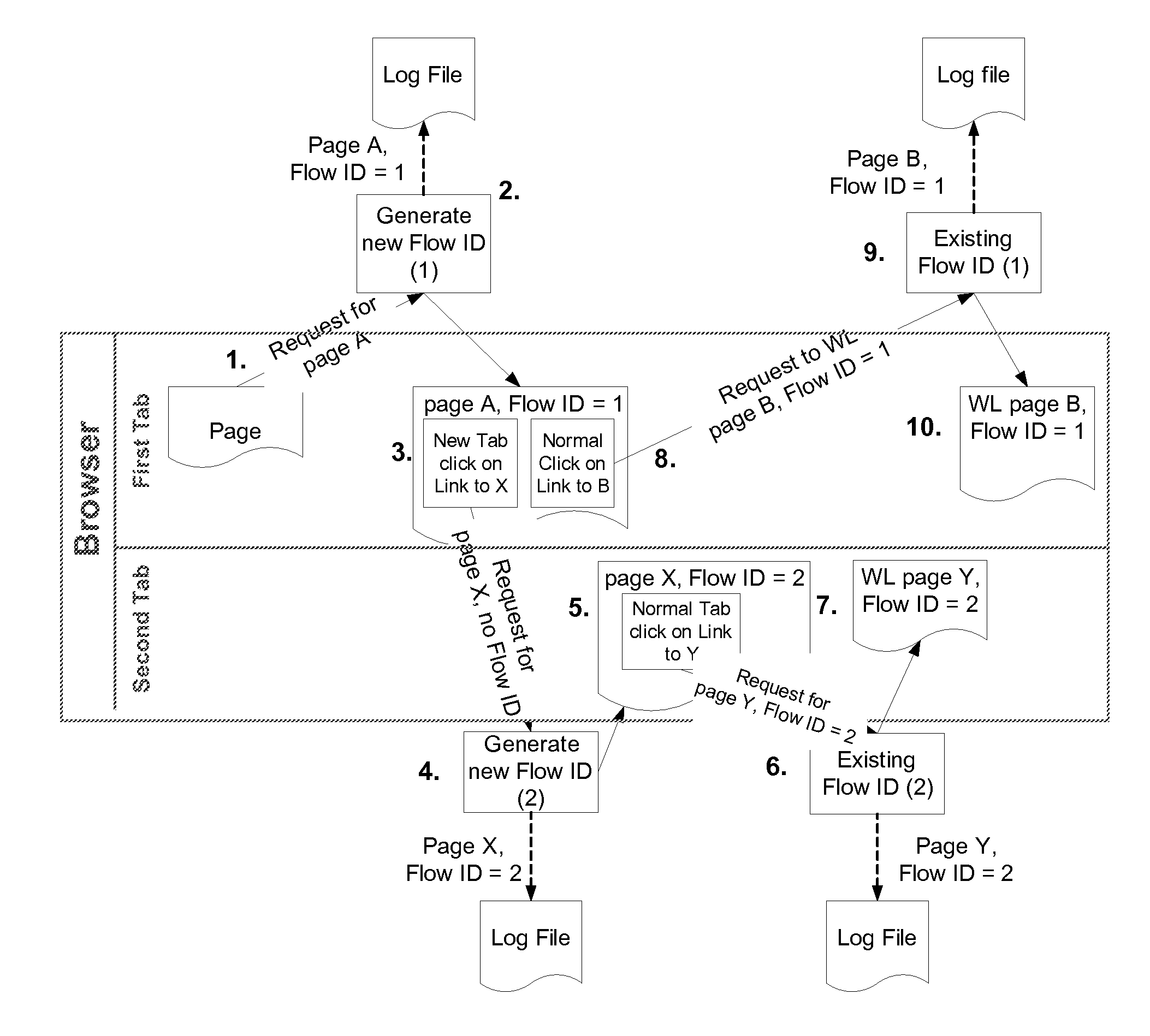
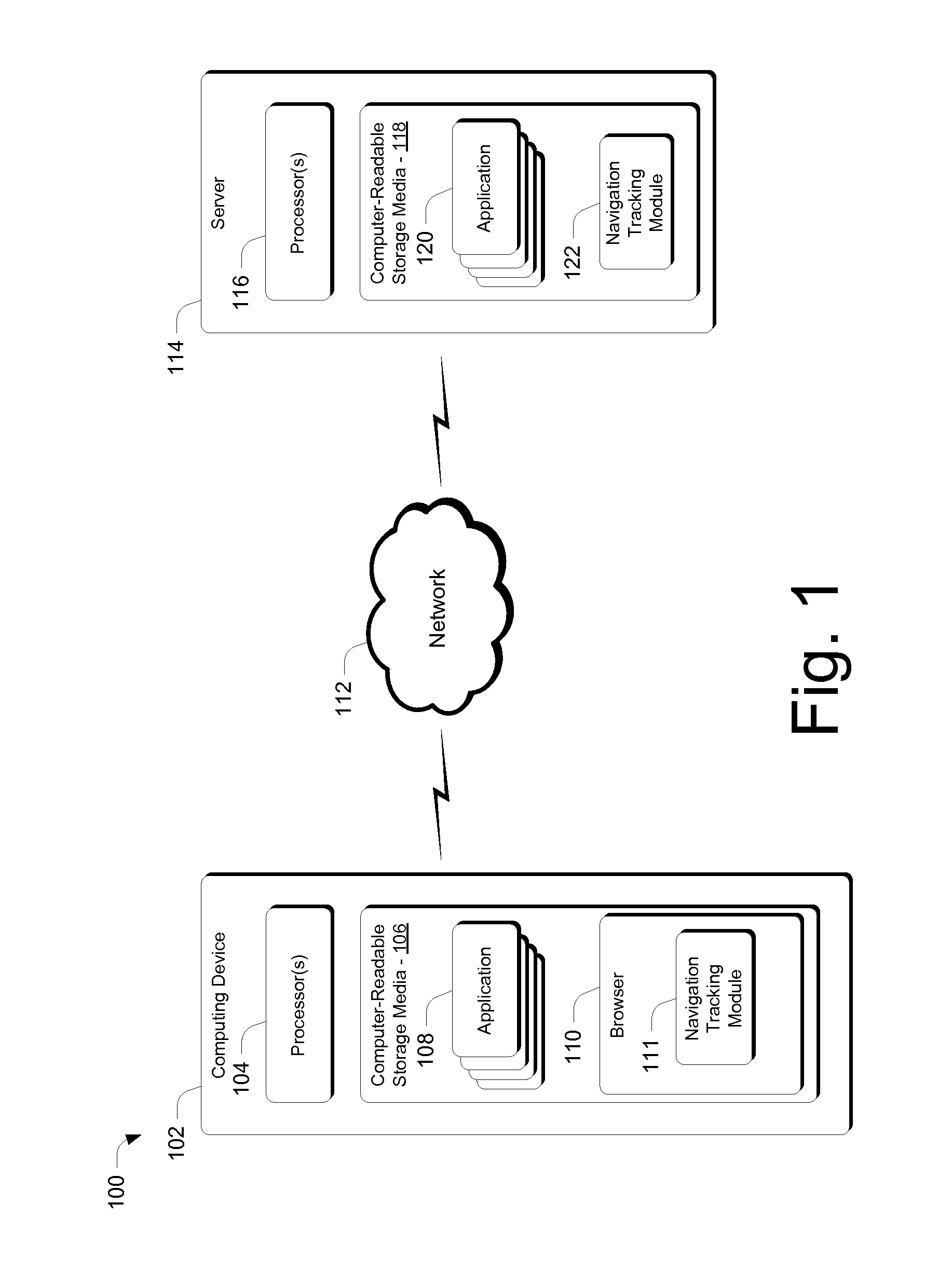
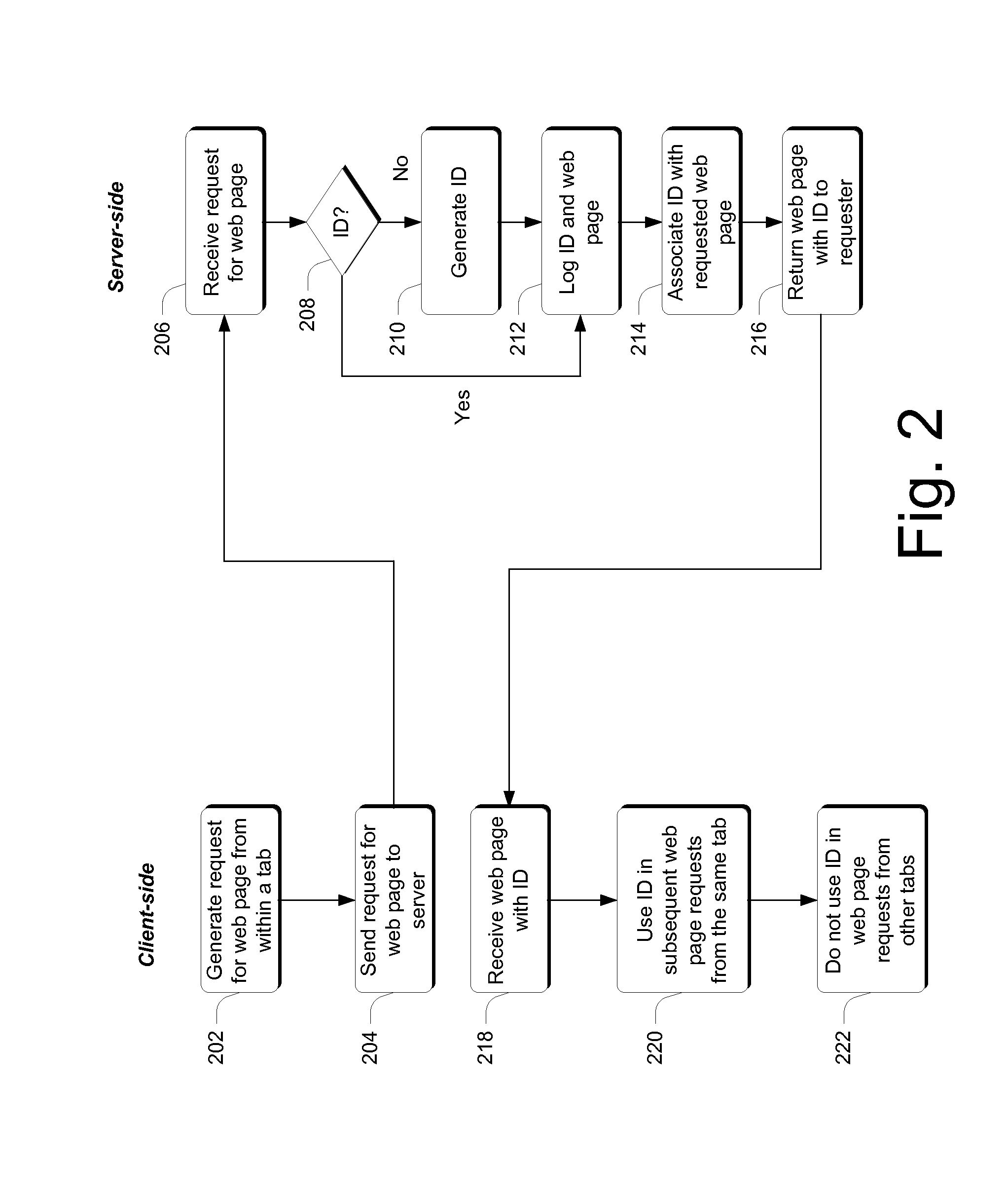
Tracking navigation flows within the same browser tab
ActiveUS20110239138A1Well formedMultiple digital computer combinationsWebsite content managementClient-sideWeb page
Various embodiments enable navigation flows that occur within a single tab to be tracked through the use of identifiers that are created and passed between client-side and server-side software. The client-side and server-side software work in concert to utilize these identifiers to track navigation within a particular tab. In at least some embodiments, a client can request a web page from within a tab and, responsive to that request, a server can create an identifier and associate the identifier with the web page. The web page and identifier can then be returned to the client. Subsequent web page requests from within the tab include the identifier so that the server knows that the request came from the same tab.
Owner:MICROSOFT TECH LICENSING LLC
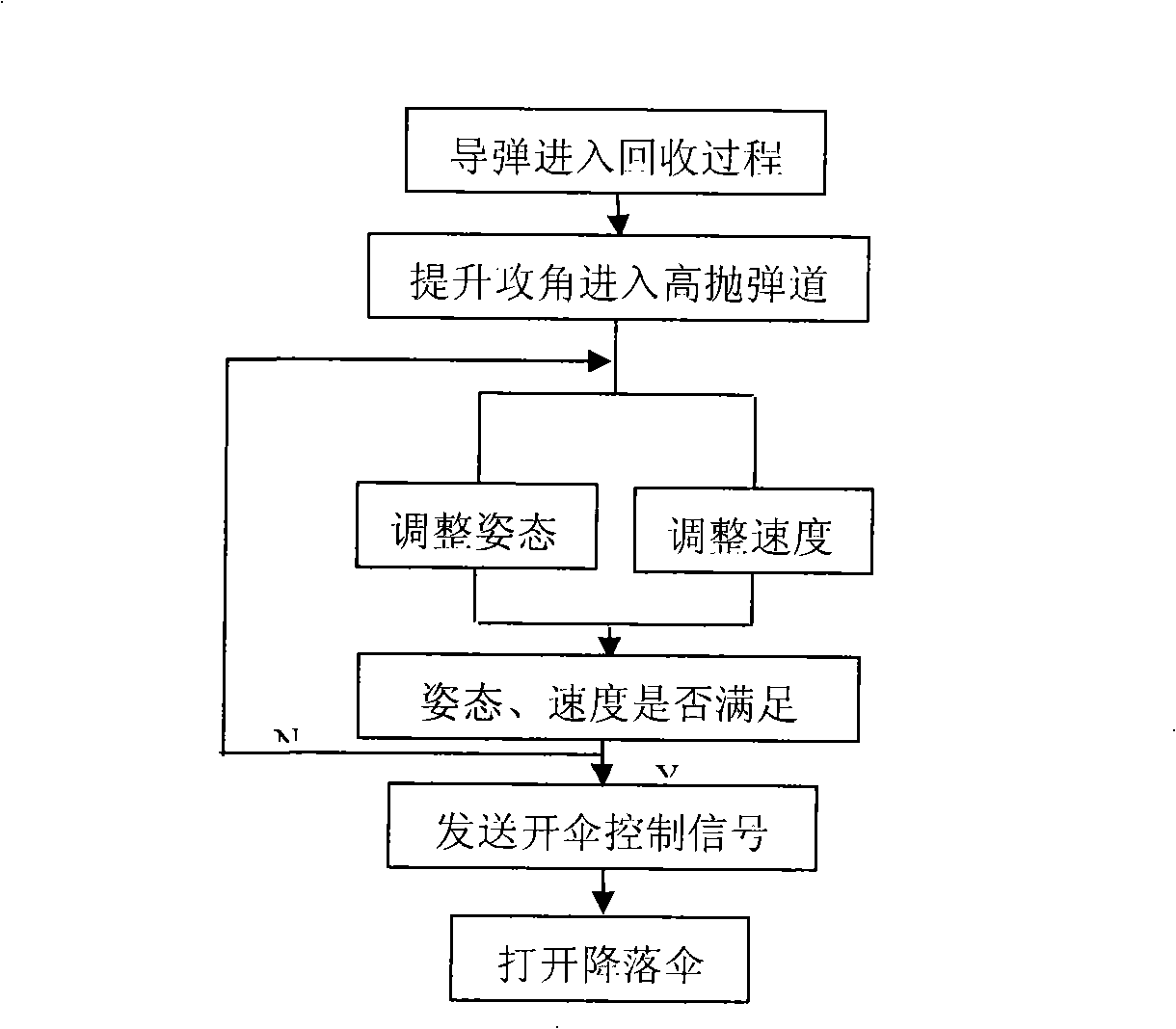
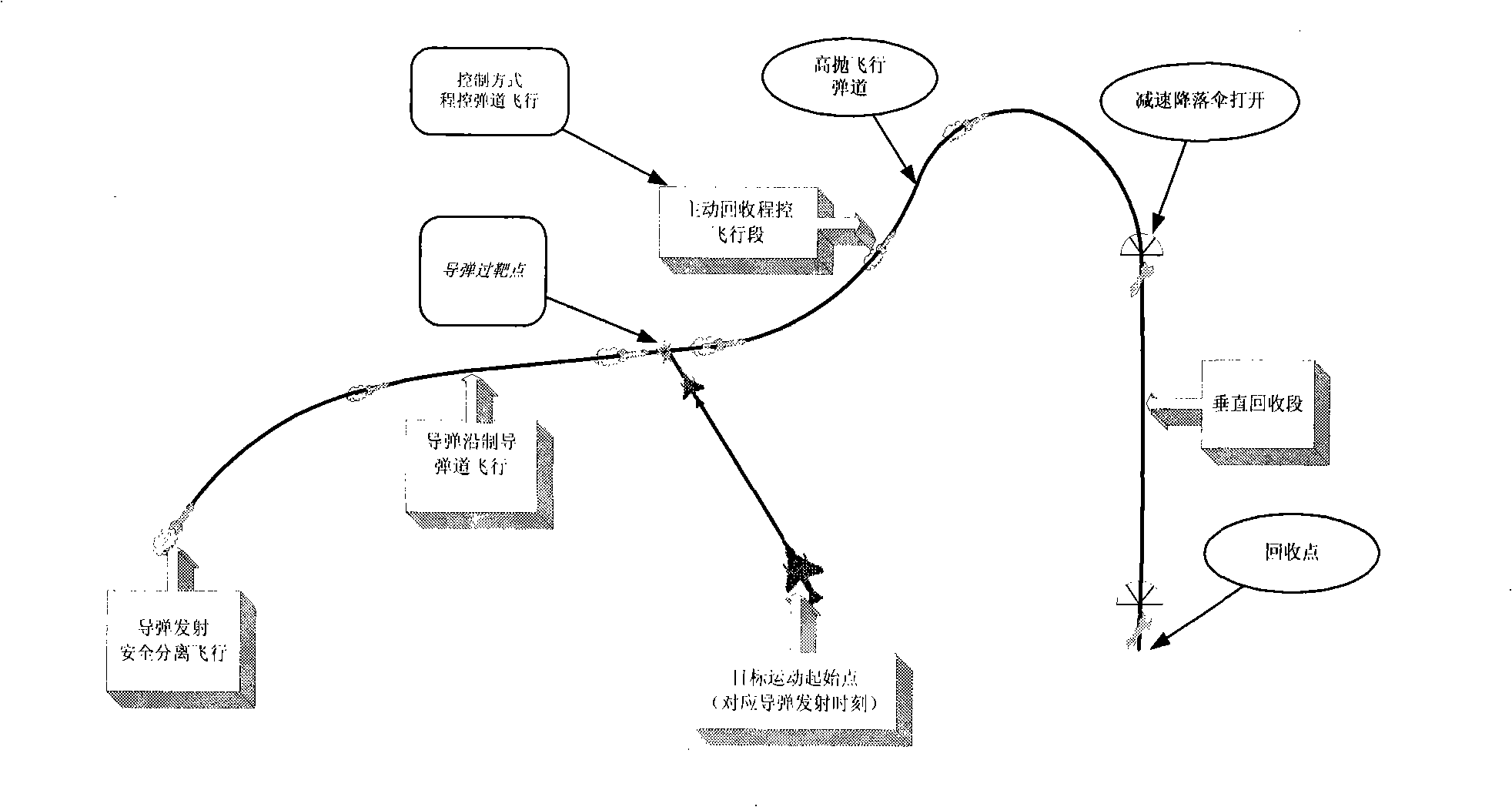
Active recycling control method of air-to-air missile experiment missile
ActiveCN101298974AAccelerate the development progressHigh research valueAmmunition testingSelf-propelled projectilesControl signalFailure analysis
The invention relates to an intiative reclaim control method of the air to air missile experiment missile. The method is added with an intiative reclaim control module and a built-in ballute in the inner of the missile, when the experiment occurs with fault or completes the flying test, the intiative reclaim control module is automatically started. The Control missile adopts the high dropping trajectory to reach the set deceleratatoin attitude-adjusting, then gives the parachute opening control signals, opens the deceleratatoin drag-parachute, completes the ntiative reclaim of the missile reclaim. After the missile reclaim control technology is adopted, the test personnel on the ground obtains the precious software working state and the flying test data in the flying, which realizes the effective utilization of the flying test missile. The technology advances the failure analysis and the zero adjustment work, which is of evident importance to accelerate the development speed of the missile.
Owner:CHINA AIR TO AIR MISSILE INST
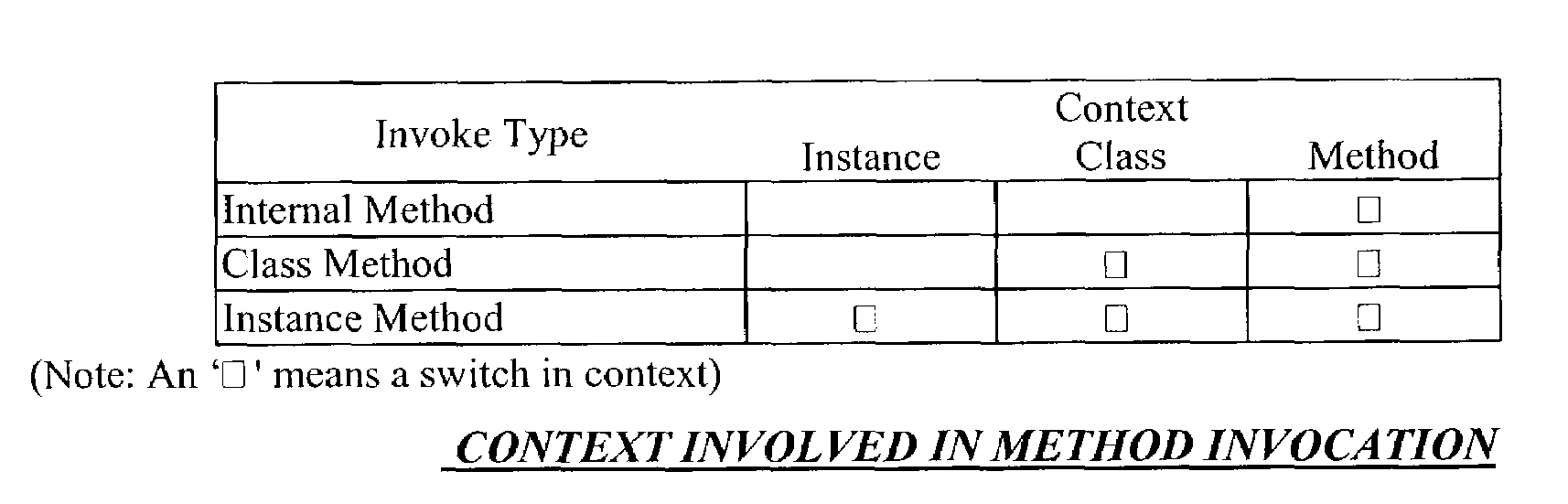
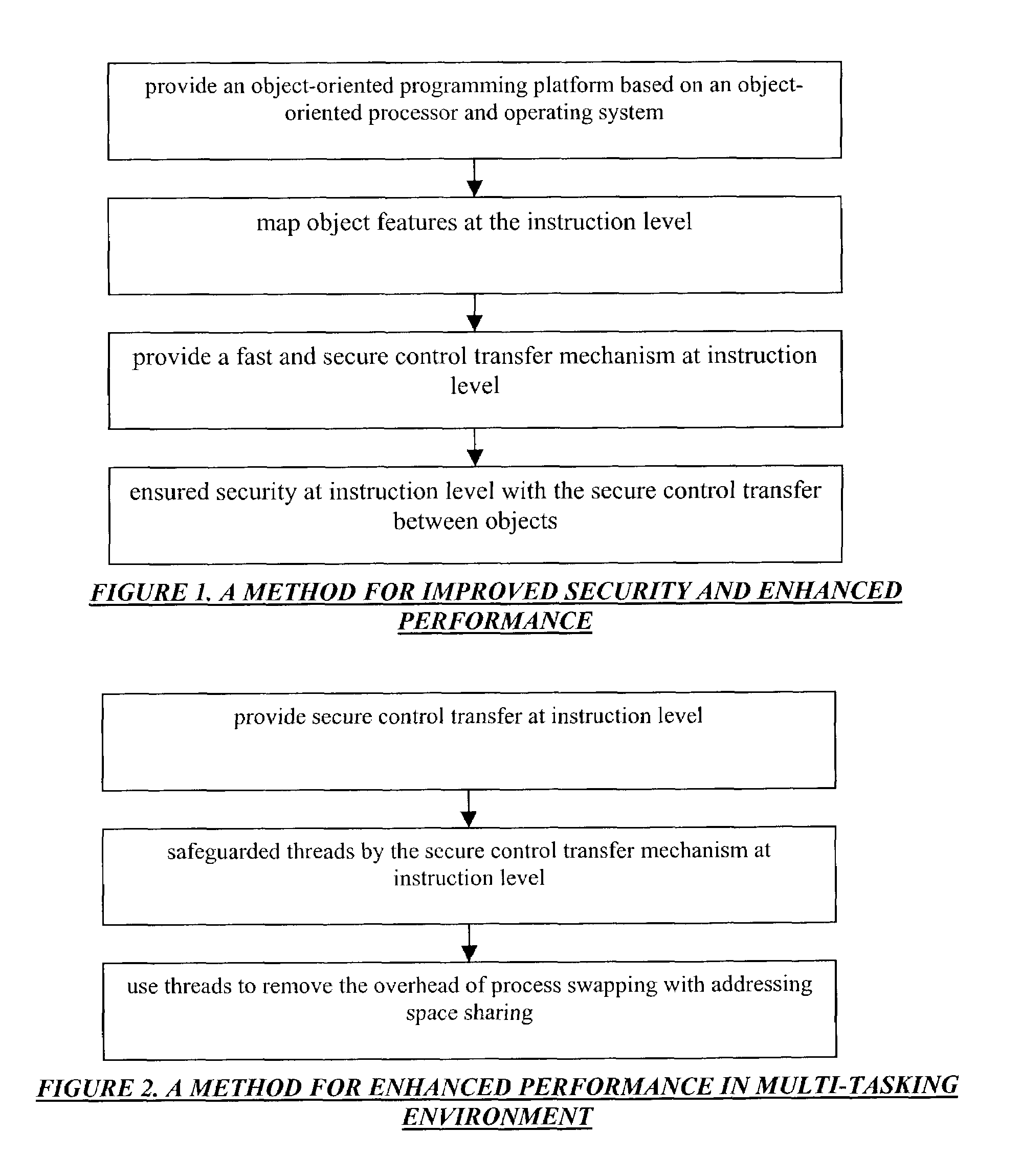
Secure control transfer in information system
ActiveUS7487507B1Overhead of context switching between processes can be avoidedAvoid overheadSpecific access rightsPlatform integrity maintainanceInformation processingControl transfer
Methods and / or systems and / or apparatus for improved security in information processing systems provide secure control transfer and object-oriented programming support at an architectural level using hardware readable data structures that represent different object structures in order to securely switch context. An architectural level Object-Oriented Programming (OOP) processor allows OOP software to be directly mapped into hardware and object security can be enforced not only in software, but also in hardware. The processor performs security checks for objects and eliminates most of the software work for access checking. In some embodiments, a hardware or hardware-like (e.g., firmware) device is used for communication and access control, to compute instructions, with a mapping mechanism of access control for object-oriented computing, through operand descriptor tables to describe the access control based on the object-orientation requirements, such as private, public, package, or protected, etc. The hardware emulates an object-orientation environment, to provide object management, object-oriented memory management, etc.
Owner:CITYU RES
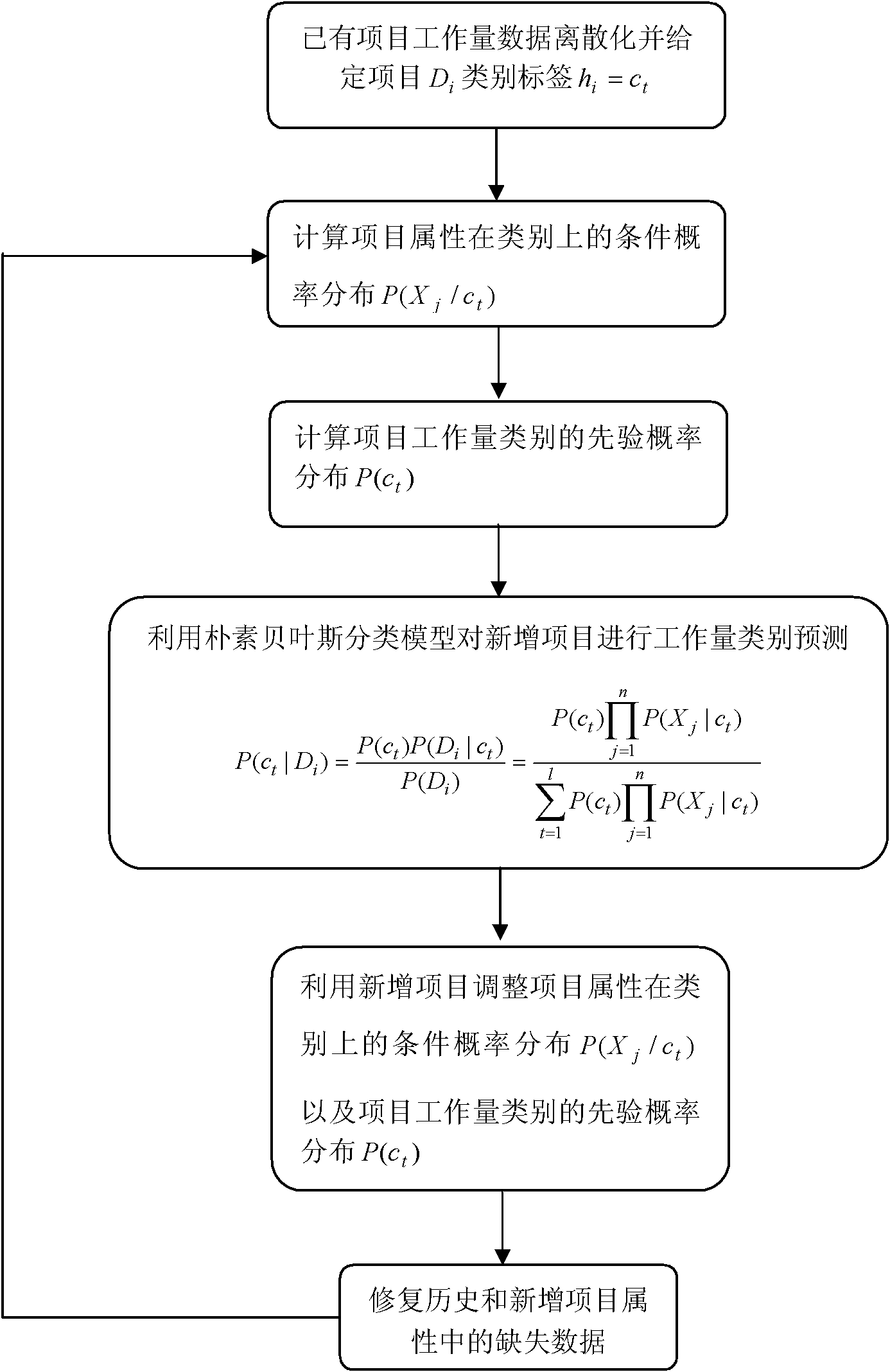
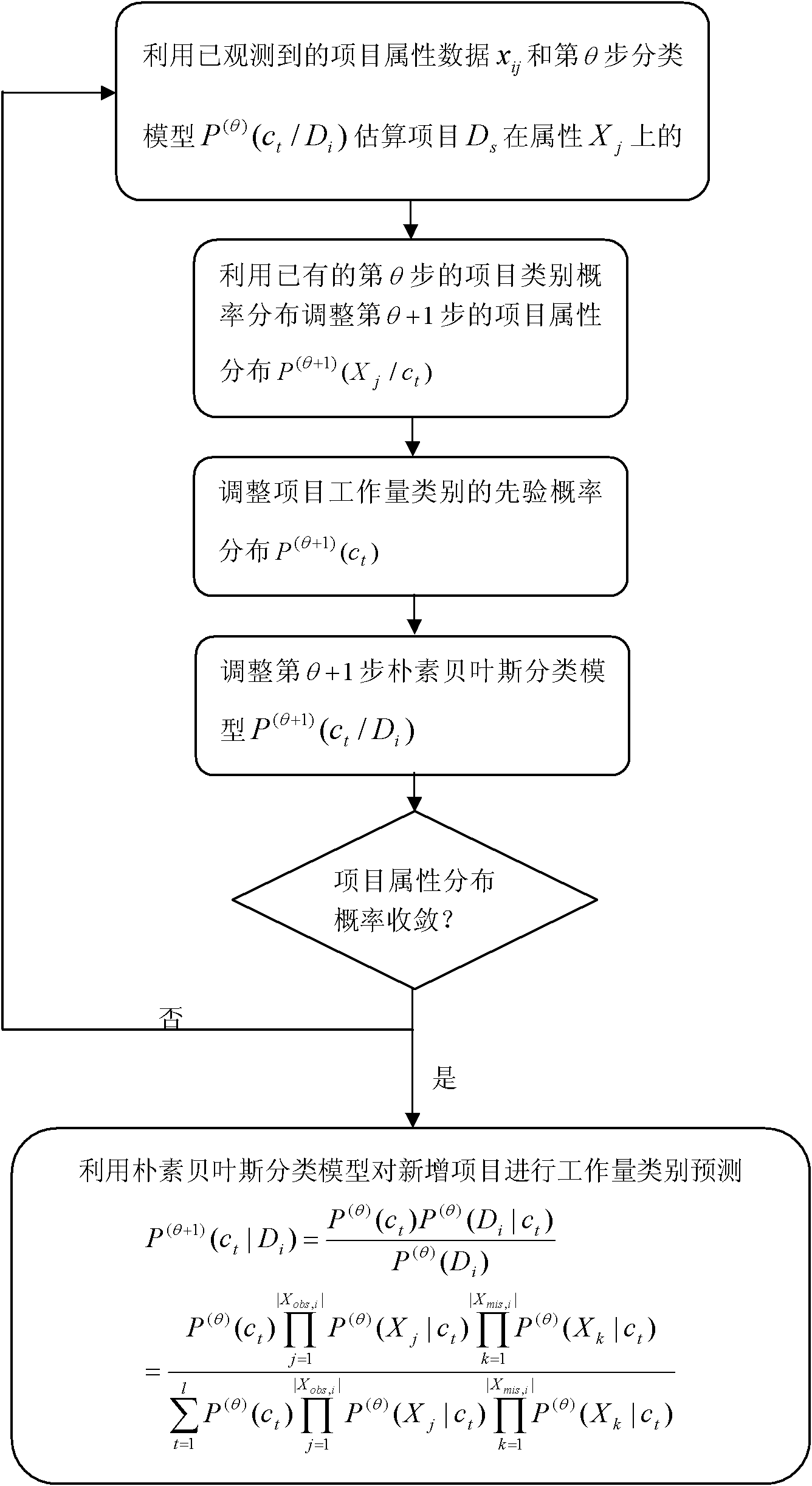
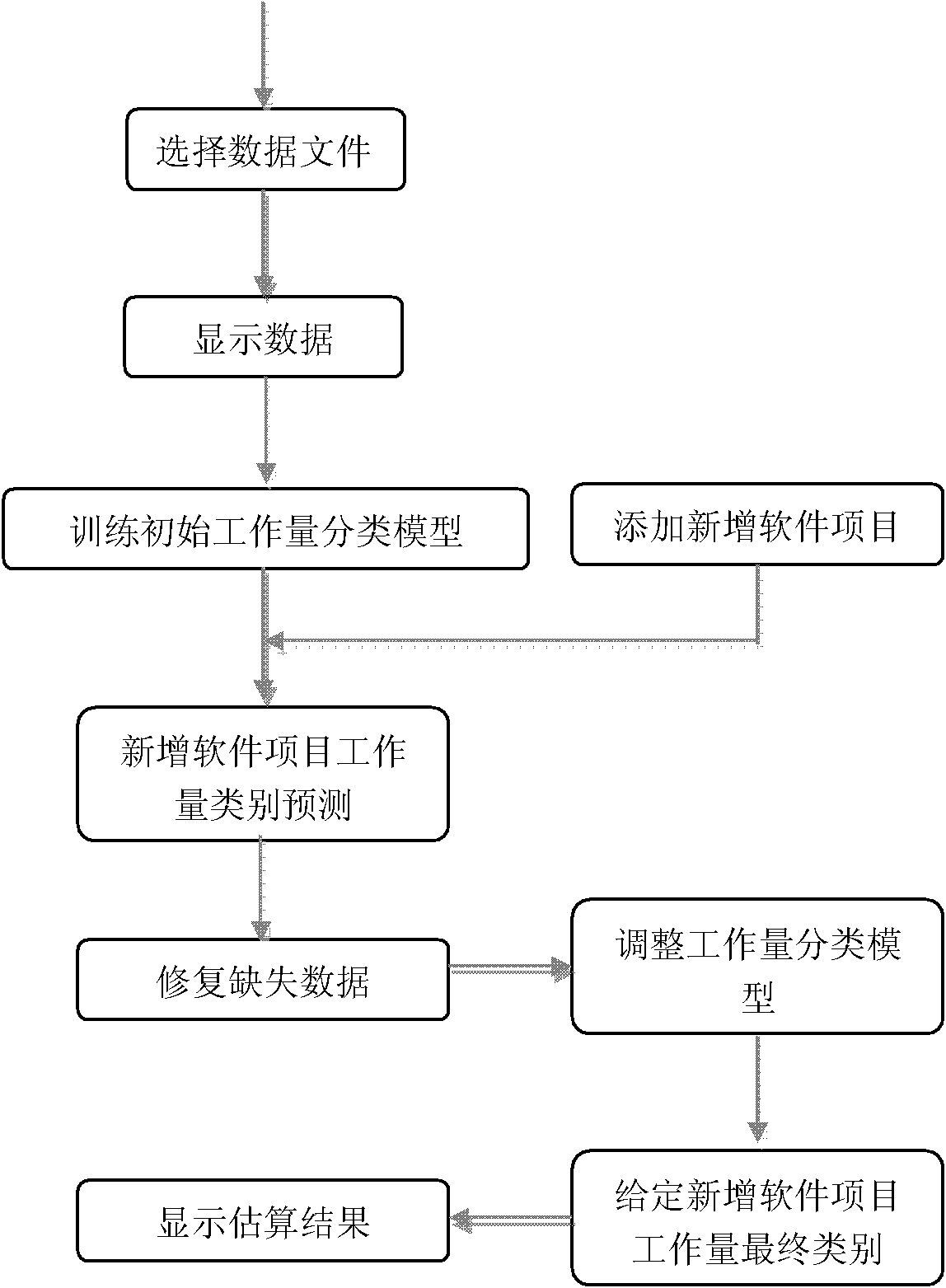
Method for predicting software workload of newly-added software project
InactiveCN102147727AImproving the Capabilities of Workload Prediction ModelsImprove abilitiesSpecific program execution arrangementsMissing dataPredictive methods
The invention discloses a method for predicting the software workload of a newly-added software project, belonging to the technical field of development of computer software. The method comprises the following steps of: discretizing the workload of history projects and dividing the history projects into project classes in designated number; calculating the condition probability and the priori probability of each project attribution in the classes of the project workload by using workload attribute data of the history projects; establishing a Bayes classification model and predicting the workload class of the newly-added project; adding the newly-added project subjected to workload classification prediction into history project data, repairing missing date, recalculating the condition probability of the project attribute on the project workload class and recalculating the priori probability of the project workload class, and repeatedly iterating until all probability distributions are converged; and finally predicting the workload of the newly-added software project by using the converged posterior probability distribution. Compared with the prior art, by using the method, the capability of a mode for predicting the workload of the software project is greatly improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Testing framework to highlight functionality component changes
InactiveUS20090037883A1Testing is superfluousError detection/correctionSpecific program execution arrangementsTest frameWork product
A computer program product stored on machine-readable media, the product including machine executable instructions for tracking a defect during development of a software work product, the computer program product including instructions for displaying the defect; identifying a component of the work product including the defect; displaying information related to the defect; and receiving input related to testing of the defect to update tracking information.
Owner:IBM CORP
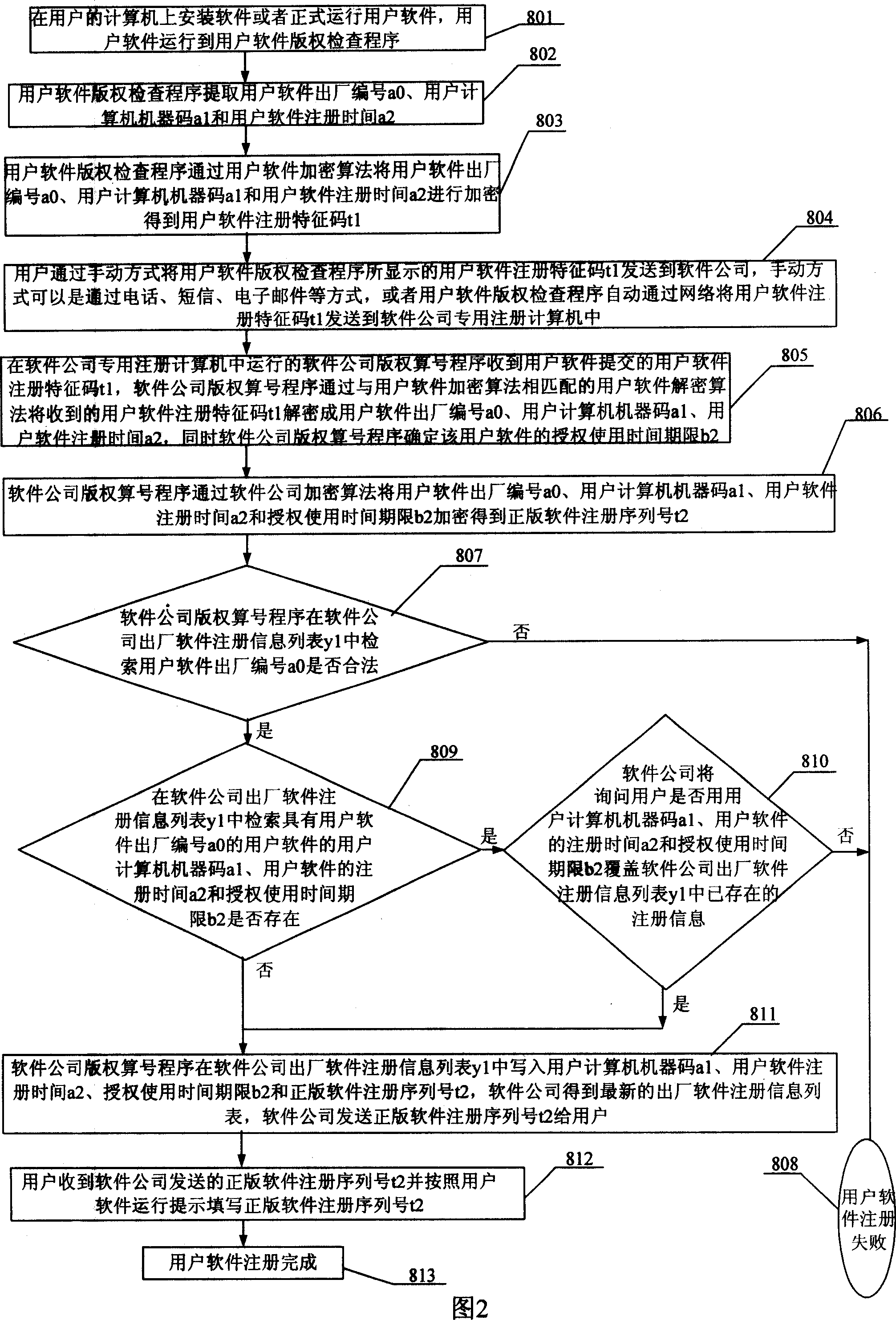
Interconnection network working software system antipirating method
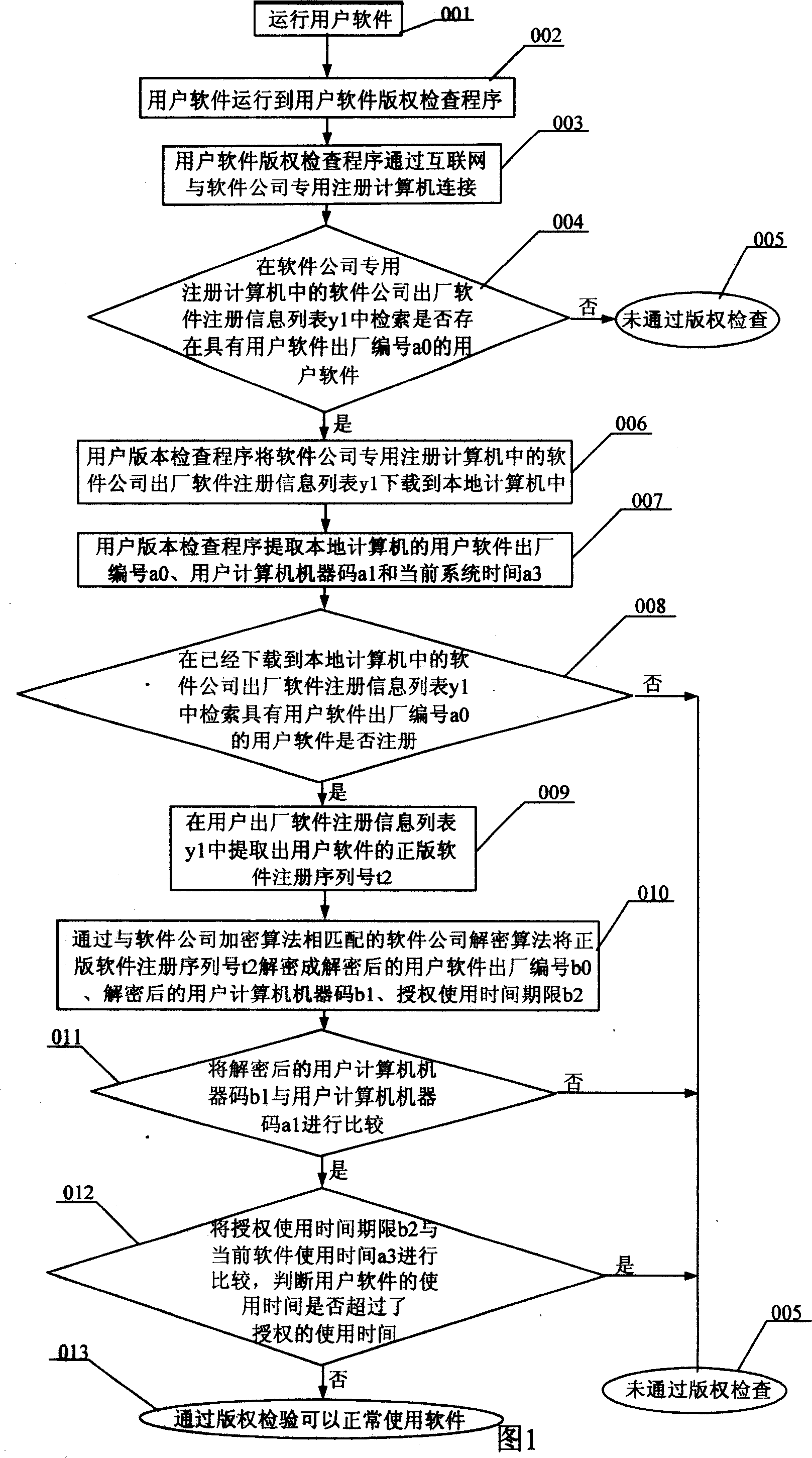
InactiveCN101067839AControlling License Runtime PeriodsEnhance anti-tracking and cracking capabilitiesProgram/content distribution protectionSoftware systemTime limit
This invention relates to an anti-pirating method for internet software system, which finishes anti-pirating by a copyright test process and a registration process suitable for networking operation system based on the internet environment and guarantees that the software house controls software volume of computers and authorized operation time period of each set working in the internet system, stops that a user mounts a set of software on multiple computers or the software works overtime and stops that a user applies for multiple registration numbers for a same set software using the software registration information list of the software house.
Owner:HARBIN INST OF TECH
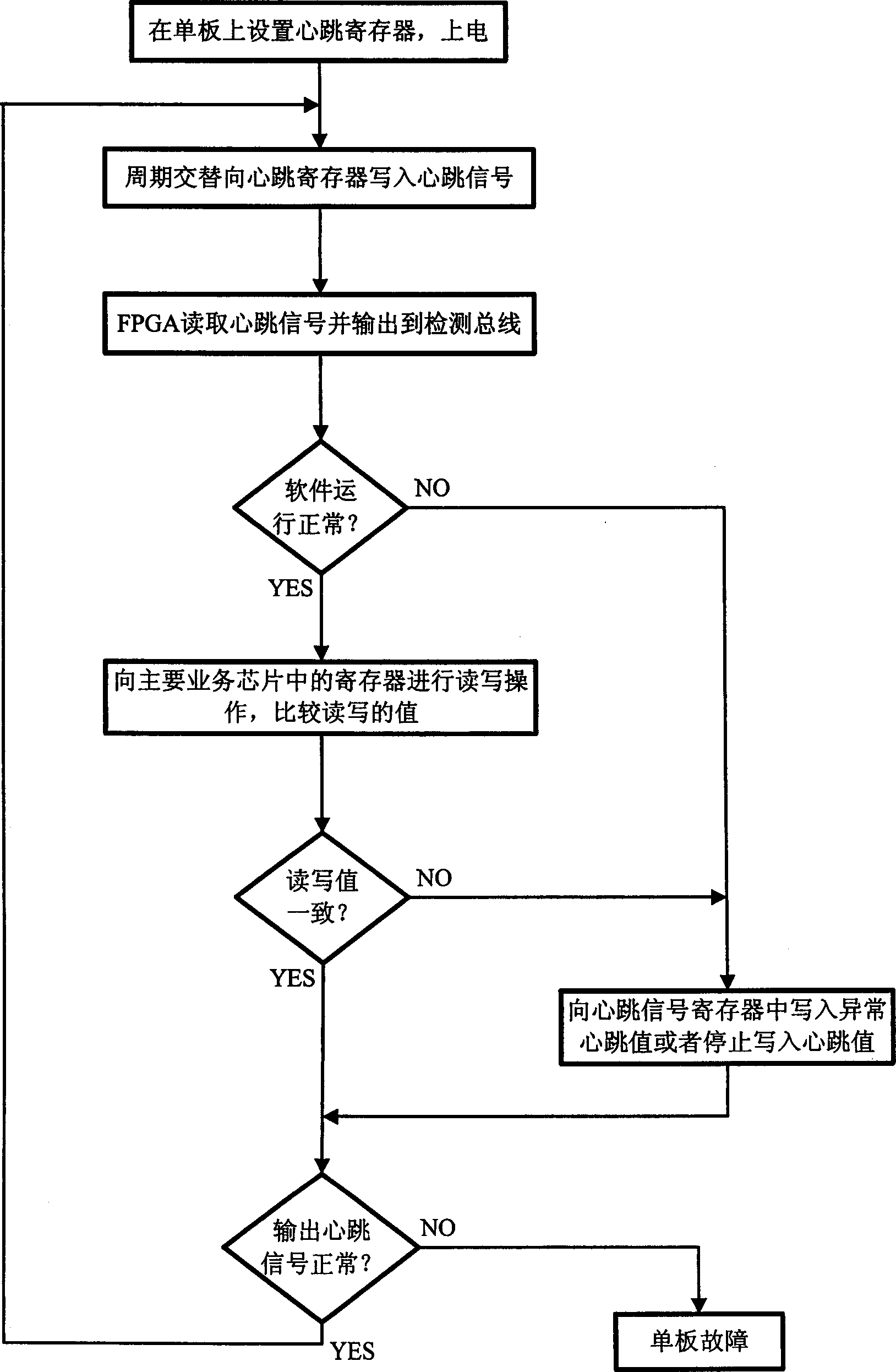
Method for detecting single board fault
InactiveCN1787410ADetect directlyReliable test resultsError detection/correctionData switching networksElectricityProcessor register
This invention discloses a method for testing errors of a single board including: 1, setting a heartbeat signal register on the board and operating on it on line, 2, writing specific heartbeat values alternatively in the register in a period of time, 3, FPGA fetches the heartbeat values and outputs the heartbeat signals to a test bus, 4, judging if the software works normally, if so, the work is continued, otherwise, it writes in abnormal heartbeat value or stops writing the value in the register to execute step 7, 5, carrying out writing and reading operation to the register in a main service chip and comparing if the values are consistent to judge if said chip works normally, 6, if so, the work is continued, otherwise, it writes the abnormal value or stops writing the value in the register, 7, judging if the signal is all right, if so, it returns to step 2, otherwise, the error of the single board is output.
Owner:ZTE CORP
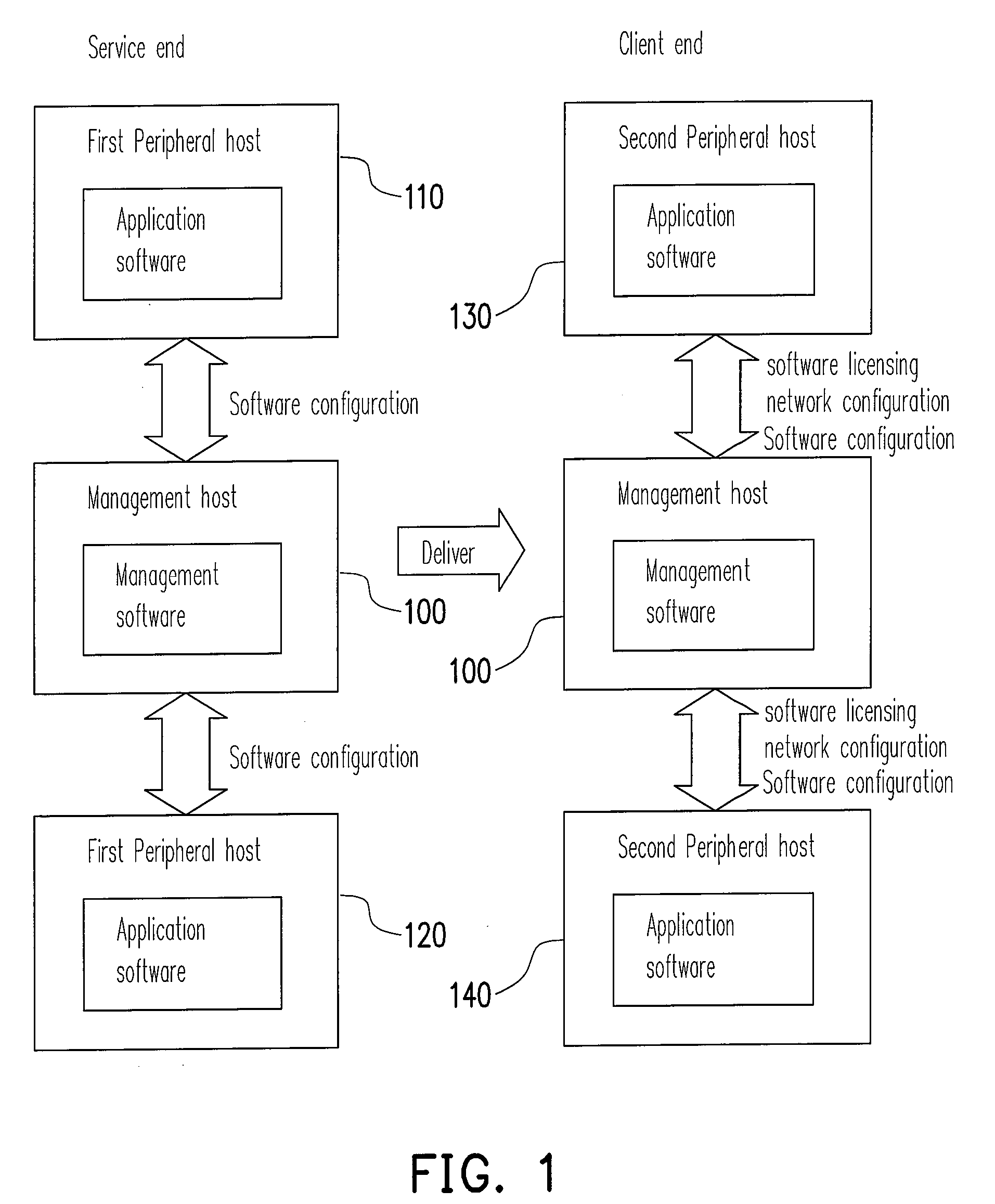
Verifying method for implementing management software
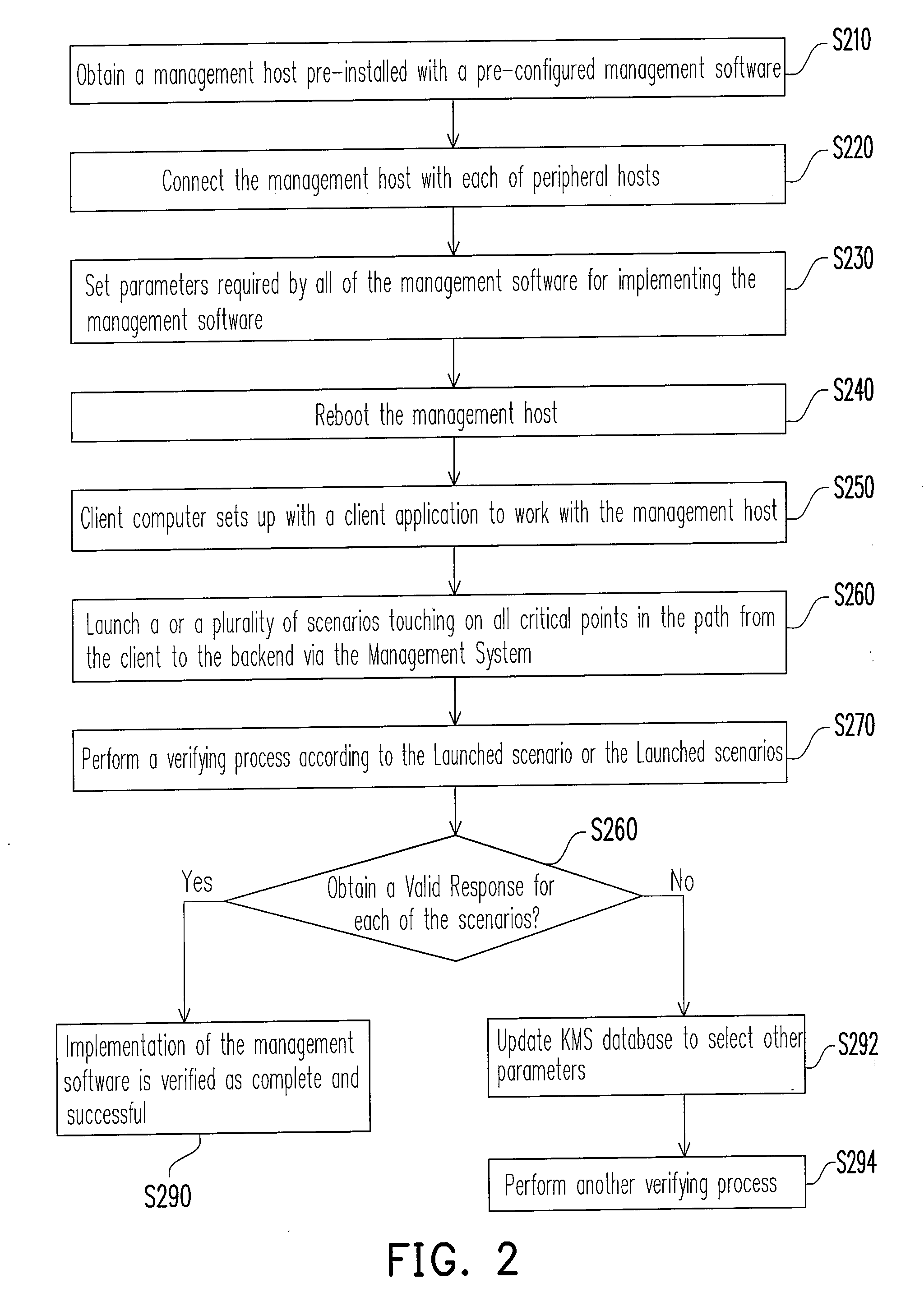
InactiveUS20080244064A1Simplified installation stepsShorten the timeDigital computer detailsTransmissionValidation methodsTest management
A verifying method for implementing management software at a client end is provided herein. The management software works for collecting, managing, and analyzing data of a plurality of peripheral hosts. In the verifying method, a management system fitting the requirements of the management software is established at a service end first. The management system includes a management host and a plurality of first peripheral hosts, and the management host is connected to each of the first peripheral hosts through a network, and the management software is installed in the management host. One or more verifying scenarios are provided herein for testing configuration and performance of the management software at a simulated environment of the client end. Each of the scenarios for testing may consider that a request form the client computer is validated through multiple authorization points and finally a valid and complete response to the client's request is returned.
Owner:INVENTEC CORP
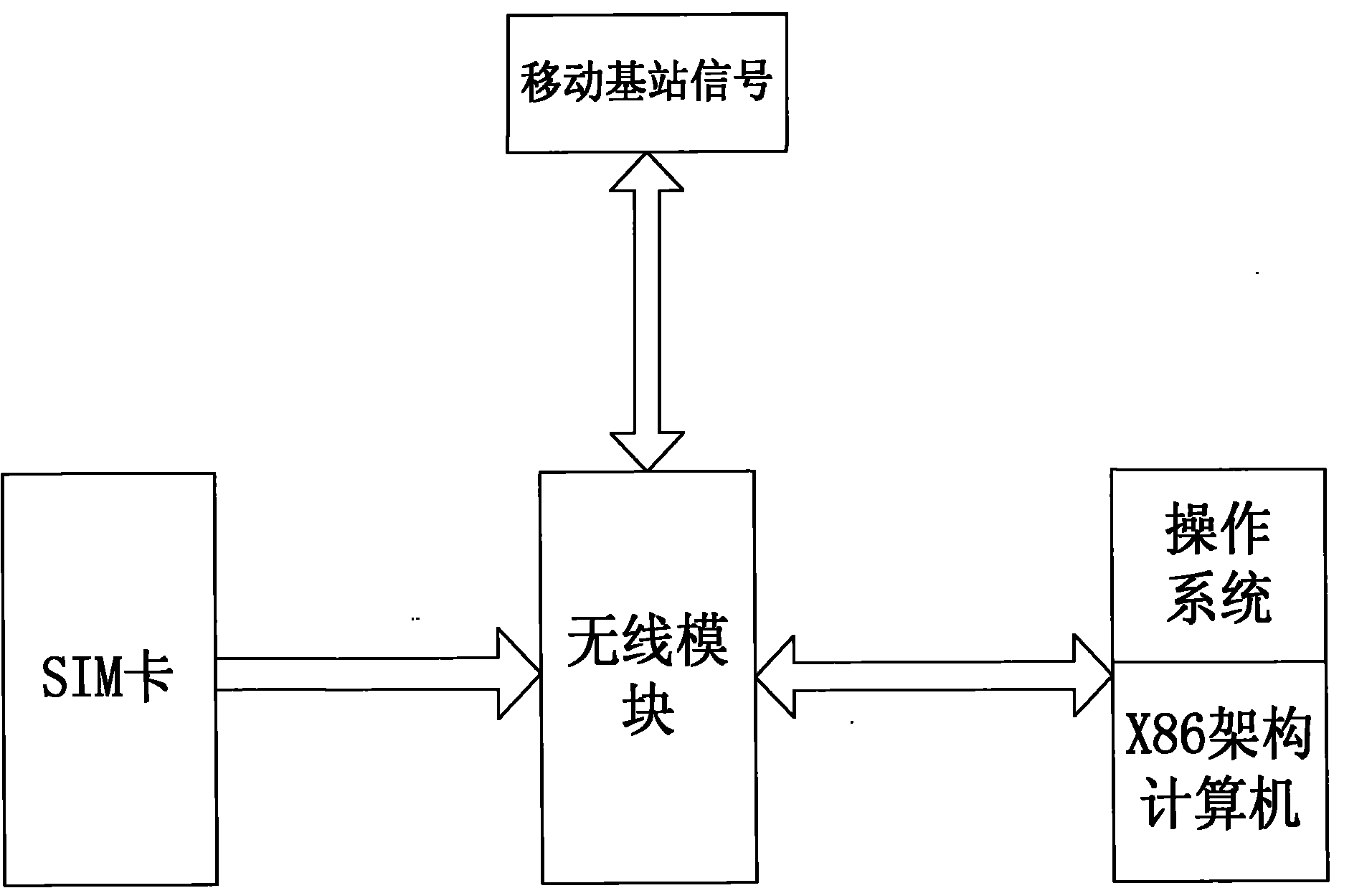
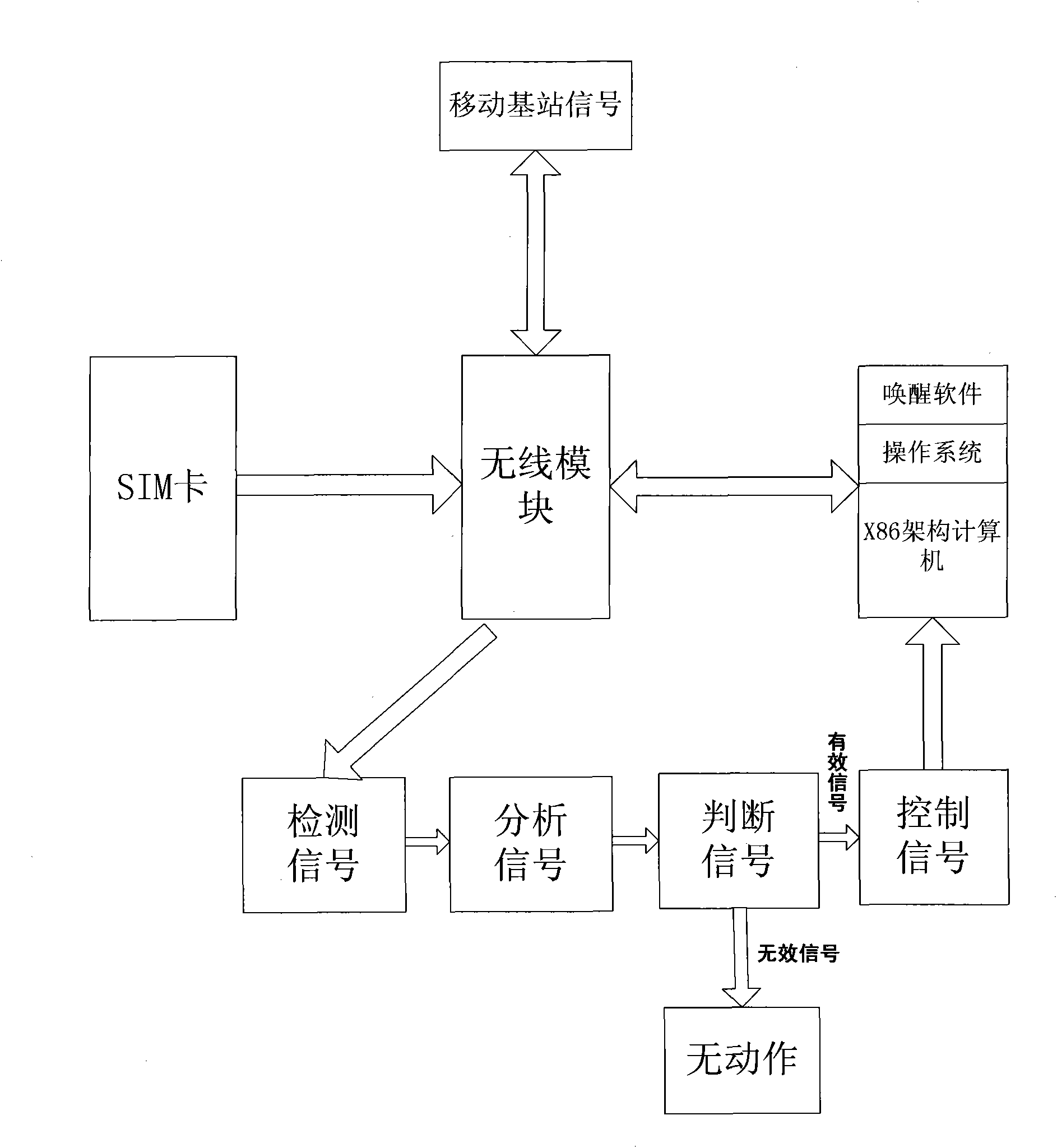
Computer built-in with wireless module and standby method and activation method thereof
InactiveCN101813963ASolve power consumptionIncrease power consumptionPower managementDigital data processing detailsActivation methodControl signal
The invention provides a computer built-in with a wireless module and a standby method and an activation method thereof. The activation method comprises: computer activation is started; the wireless module sends a signal which requests to activate the computer; a control circuit detects, analyses and determines the signal which requests to activate the computer and sends the control signal which activates the computer to the computer; and the computer responses the control signal and is activated. The invention can realize that the computer can continuously provide the power supply for the wireless module under the condition of standby; when voice or data is called in, the computer can detect a voice or data signal, analyzes the signal, judges the signal, automatically awakens a computer system in extremely short time after finding a correct signal, restores normal hardware and software work environment and makes corresponding ringing hint, and thus the computer can quickly answer the phone or receive and send short messages; the problem of computer power consumption can be solved, and standby time is improved to 5 days or even longer from 2-8 hours of the original battery power supply time.
Owner:深圳市四面信息科技有限公司
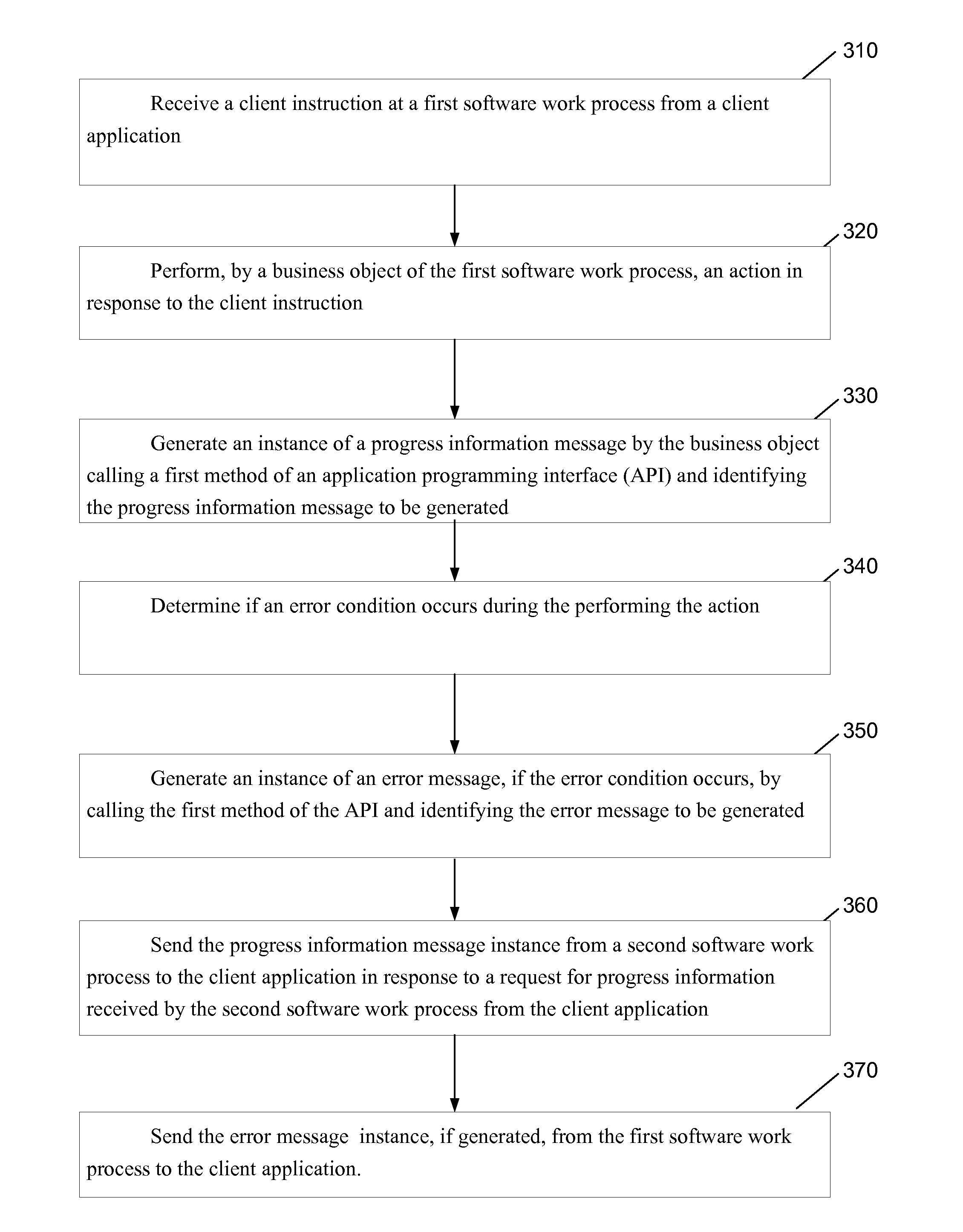
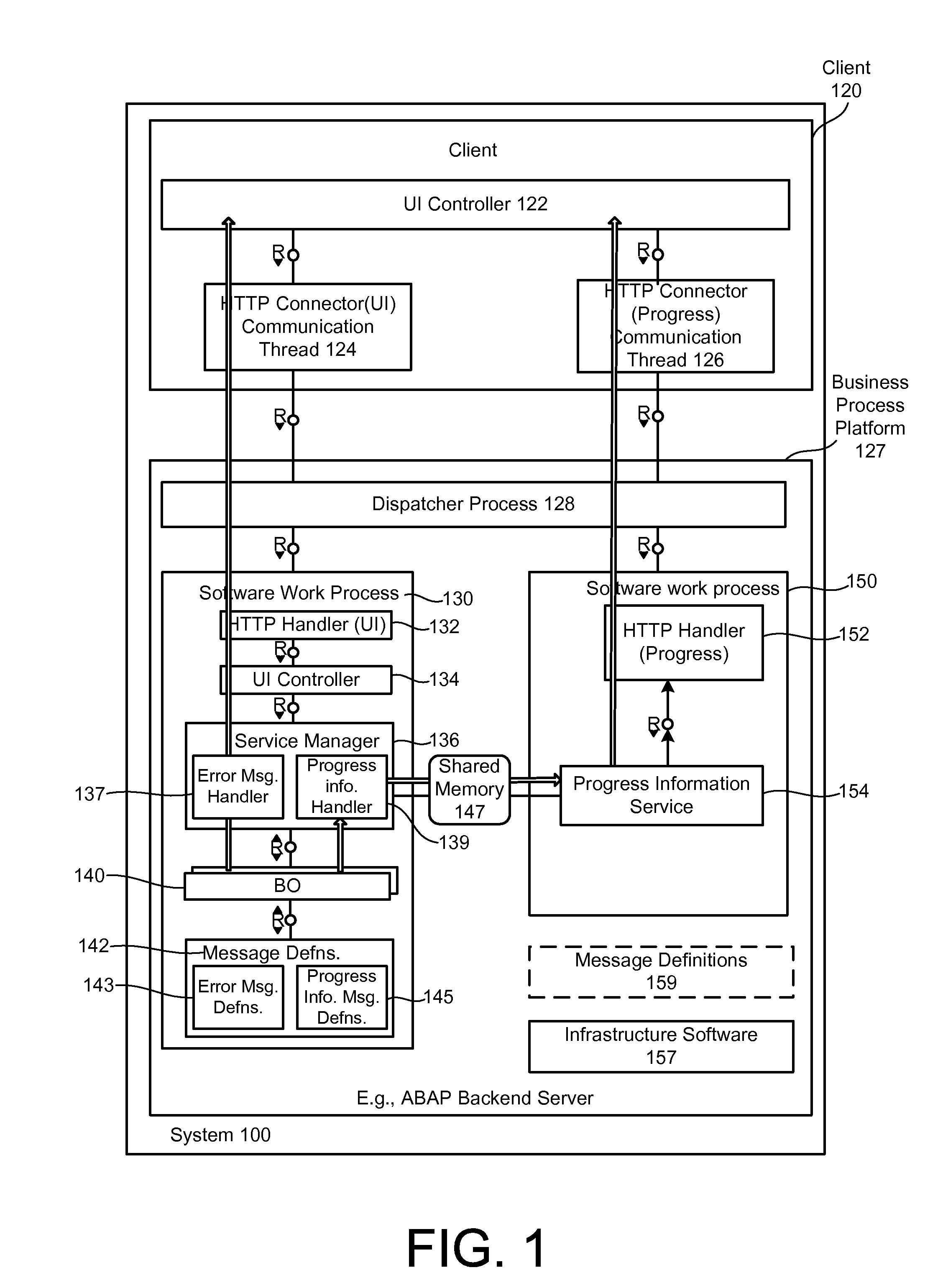
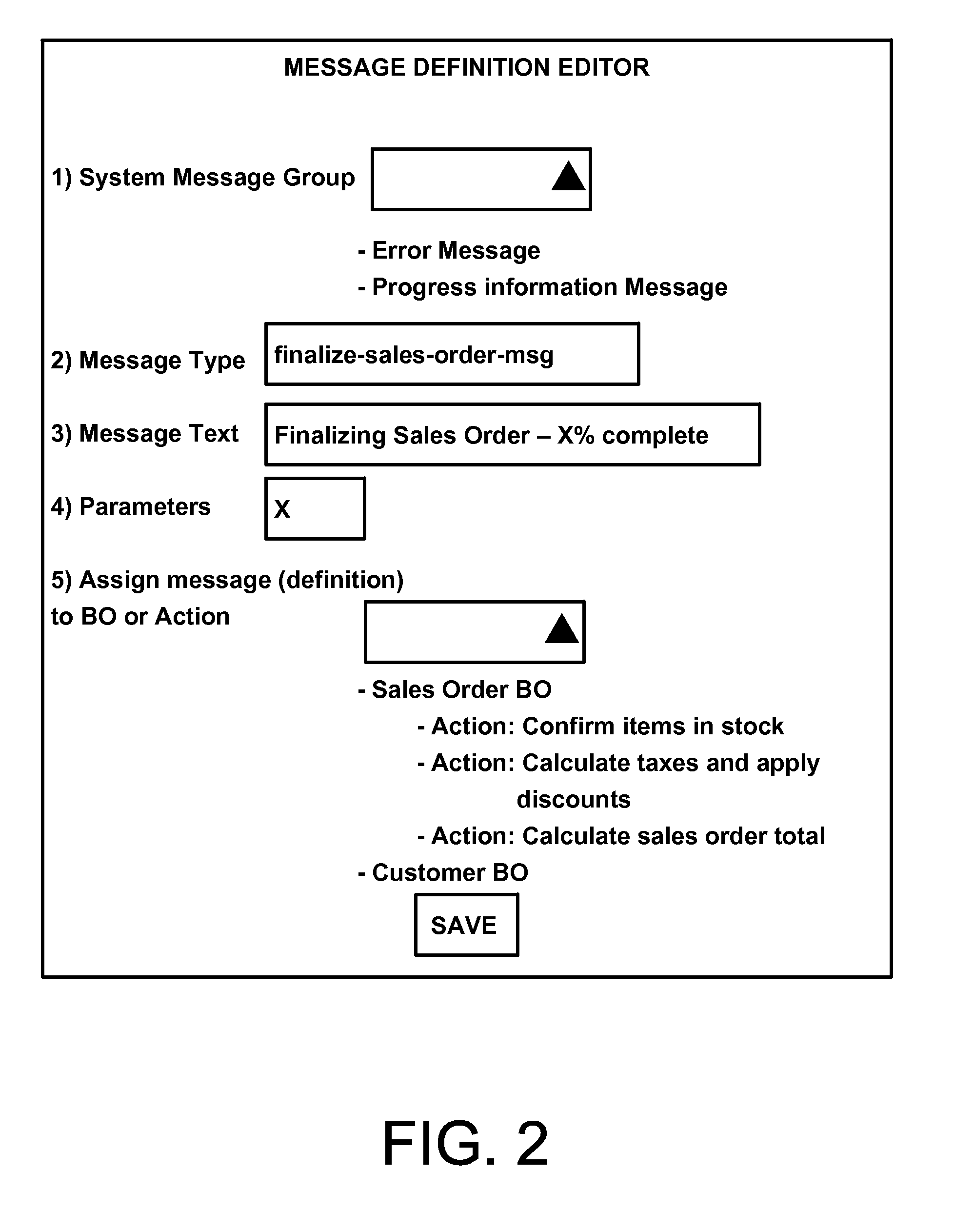
Generation of error messages and progress information messages via a common interface
The present description refers to a technique for receiving a client instruction, performing an action in response to the client instruction, generating an instance of a progress information message by the business object calling a first method of an API and identifying the progress information message to be generated, determining if an error condition occurs during the performing the action, generating an instance of an error message, if the error condition occurs, by calling the first method of the API, sending the progress information message instance from a second software work process to the client application in response to a request for progress information received by the second software work process from the client application, and sending the error message instance, if generated, from the first software work process to the client application.
Owner:SAP AG
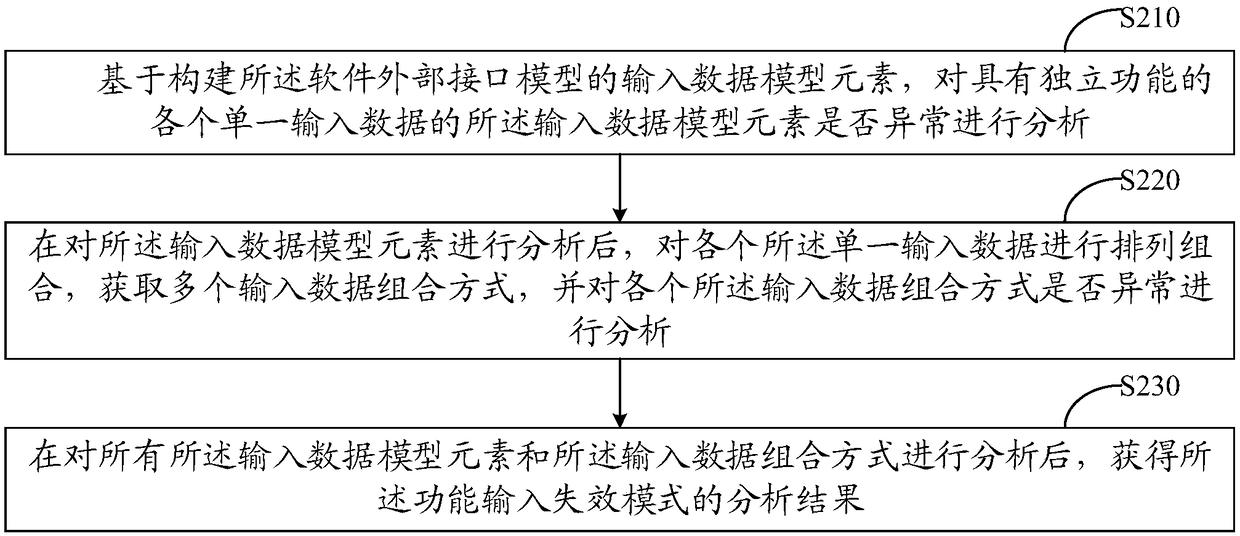
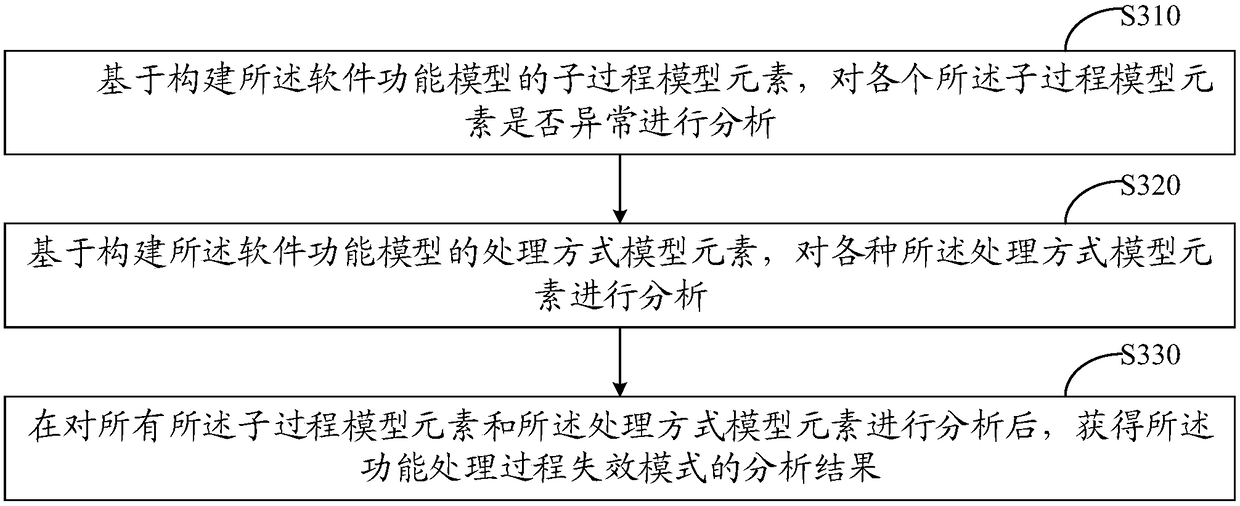
Method and device for identifying failure modes of software
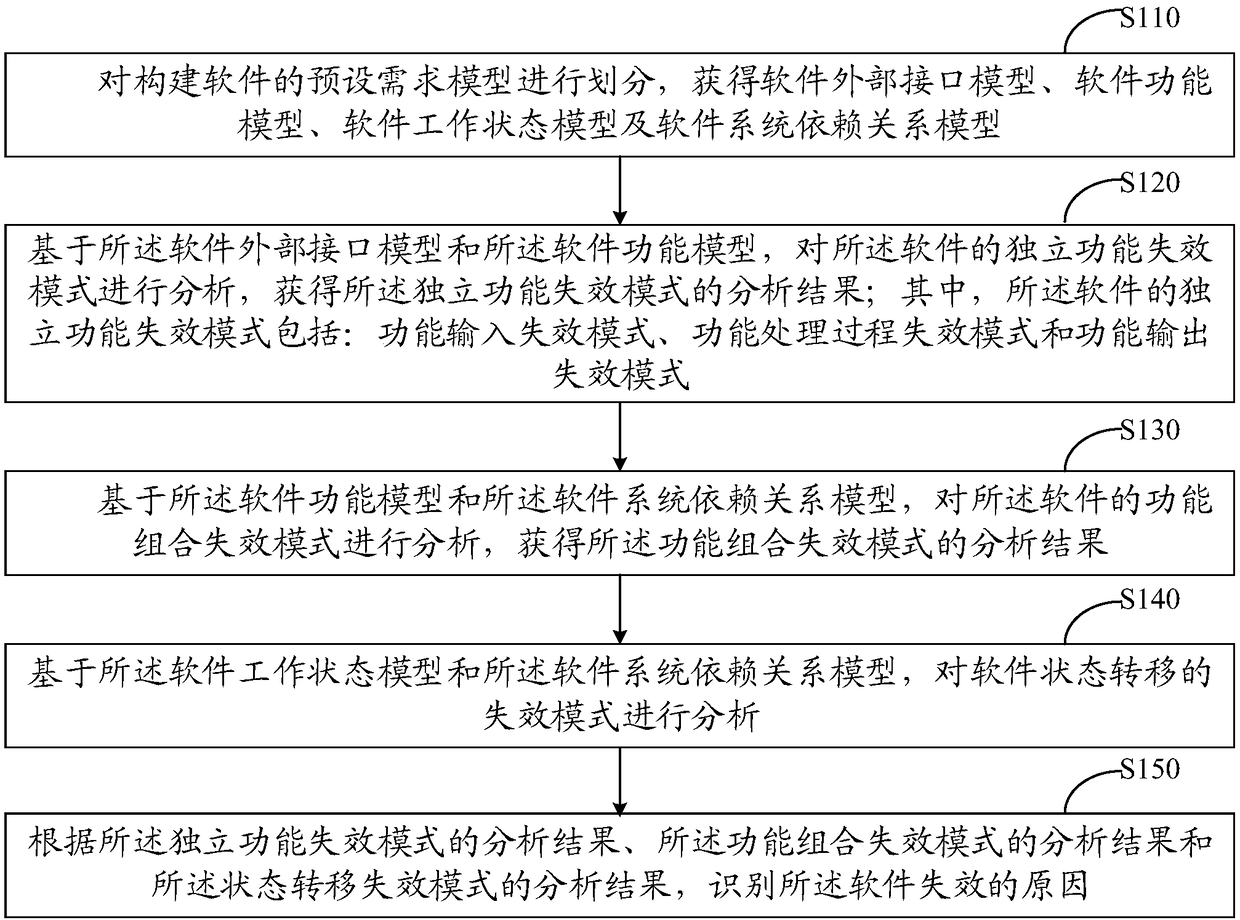
ActiveCN108255728AImprove securityIncreased level of safety designSoftware testing/debuggingSoftware development processRelational model
The invention discloses a method and device for identifying failure modes of software, and relates to the technical field of the internet. The method comprises the steps that a preset requirement model of the construction software is divided into a software external interface model, a software function model, a software working state model and a software system dependence relation model; the independent function failure mode of the software, the function combination failure mode of the software and the state transition failure mode of the software are analyzed on the basis of the models; software failures caused by software working state conversion and multiple function combinations are fully embodied, the software failure modes can be analyzed comprehensively, and the method has the advantages of being universal, easy to popularize and capable of being copied. Therefore, real causes and potential threats of the software failures are found in the software development process, the improvement of the safety design level in the software development stage is effectively promoted, the pertinence and the effectiveness of correction measures are enhanced, the safety of software products is improved, and the equipment damage caused by the software failures and the cost of the life cycle of the software are reduced.
Owner:CHINA ELECTRONICS PROD RELIABILITY & ENVIRONMENTAL TESTING RES INST
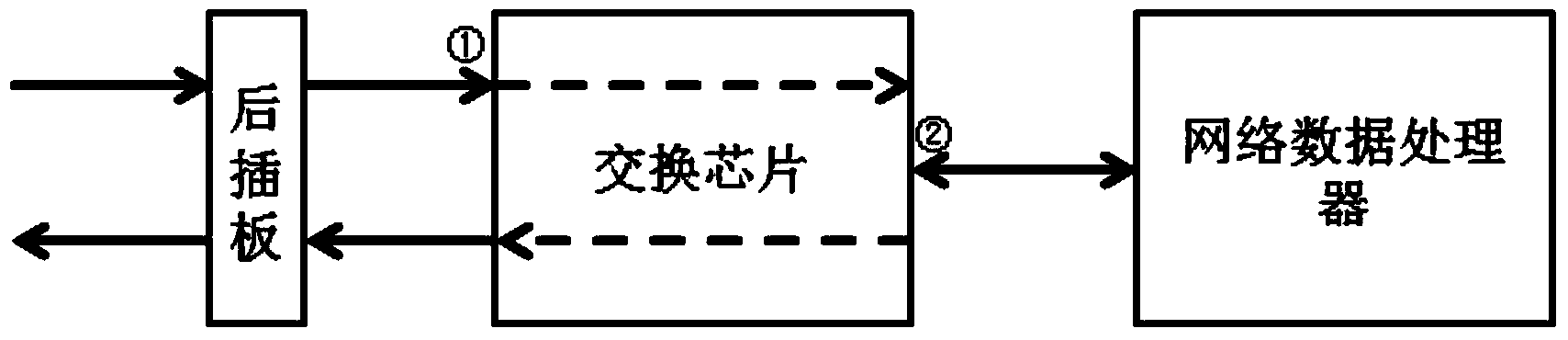
High-performance network data processing platform system
InactiveCN103812768AIncrease core business processing performanceMeet the needs of rapid developmentData switching networksComputer hardwareNetwork data
The invention discloses a high-performance network data processing platform system comprising a service board card with a Cavium processor, an X86 management board card and a 2-slot ATCA (Advanced Telecom Computing Architecture) case. The layer 2 address learning functions of a switch chip and the port of a network data processor are closed so that address learning conflict with the port of an inserted card can be prevented, and in the meantime, hardware shares one part of software work based on the enough strong performance of the switch chip in a software-hardware combined way and by virtue of distributed system deployment, and as a result, unnecessary expenditure of the network data processor is saved and the core service processing performance of the network data processor is enhanced.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
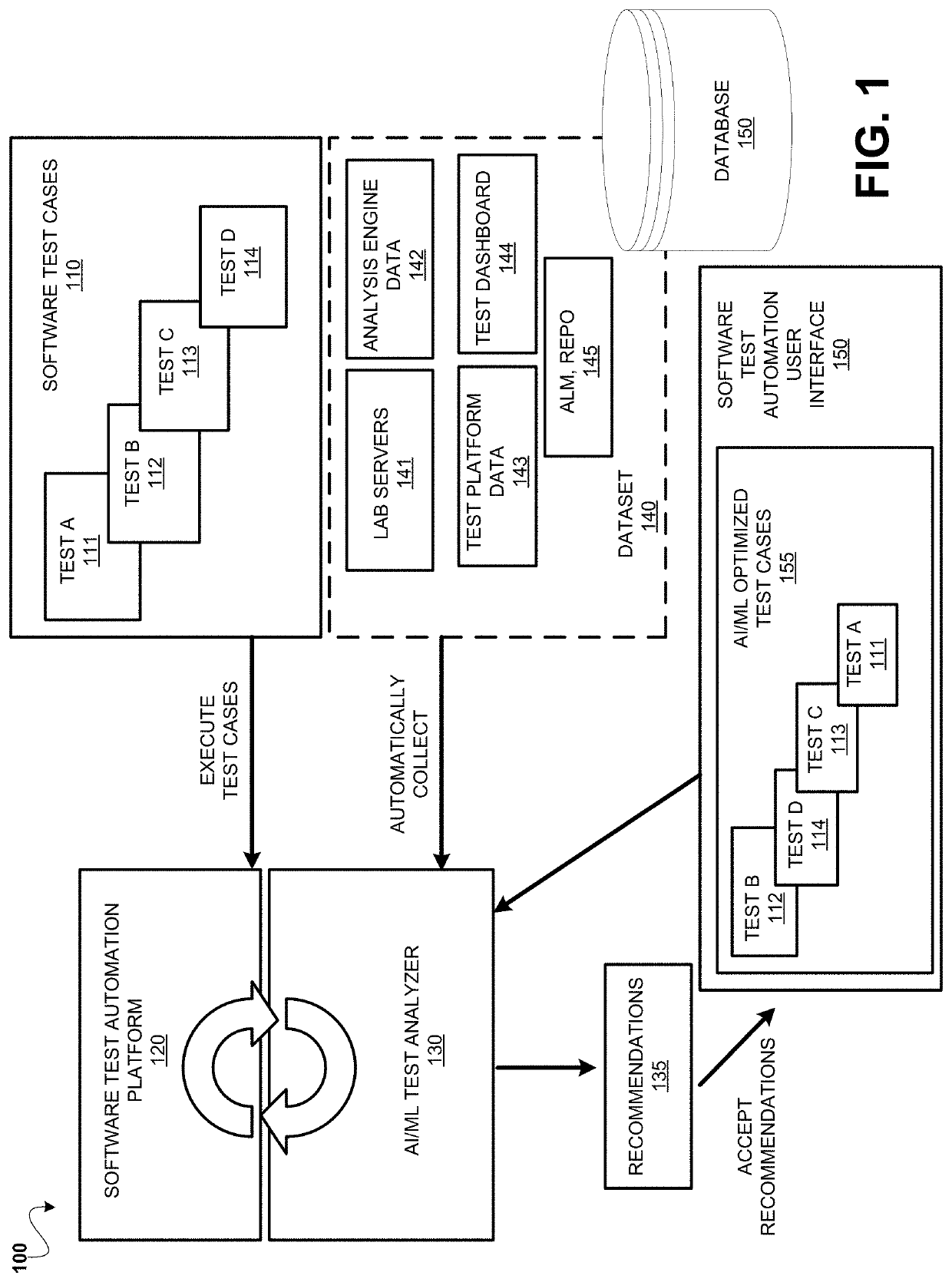
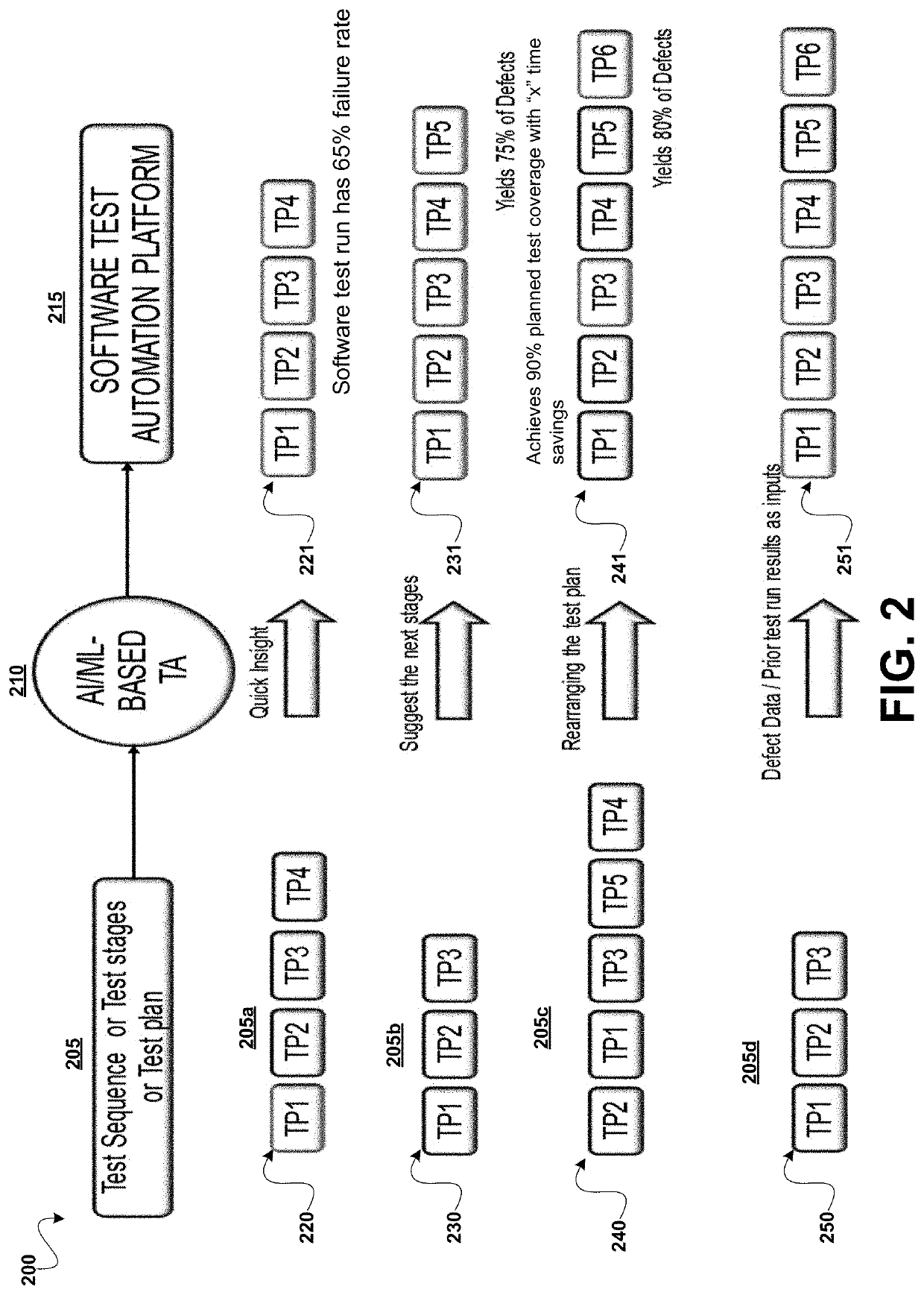
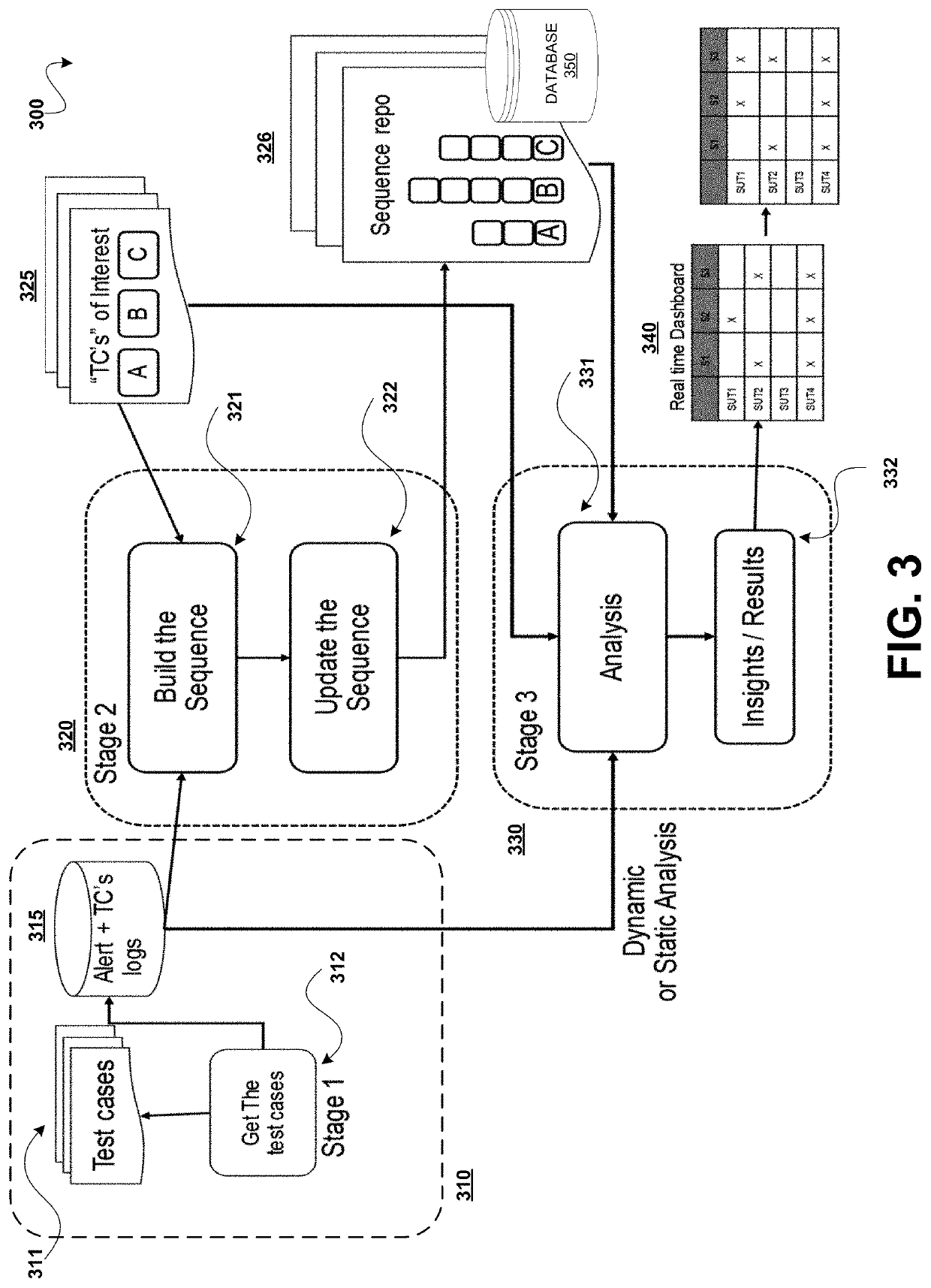
System and methods for amalgamation of artificial intelligence (AI) and machine learning (ML) in test creation, execution, and prediction
Systems and methods provided for a software test automation platform including an artificial intelligence (AO / machine learning (ML) test analyzer. The AI / ML test analyzer can be a computer device operating with the software testing automation platform that is programmed to obtain run-time data from executing multiple software test cases for a software workload; obtain log data from the one or more test logs, relating to previous executions of the tests cases for the software workload. The AI / ML test analyzer can then analyze the log data and the run-time data by applying ML / AI tools, concurrently with executing the test cases, for recognizing patterns associated with the executed tests cases over a period of time, and automatically predicting an optimized set of test cases and analytics related to execution of the test cases for the software workload.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
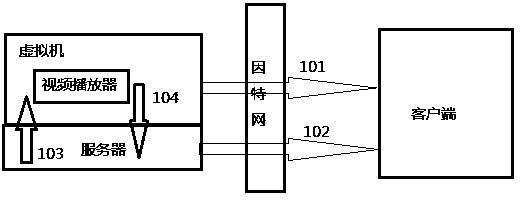
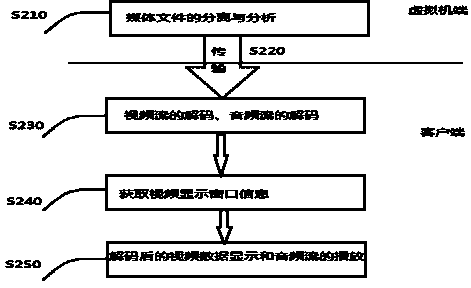
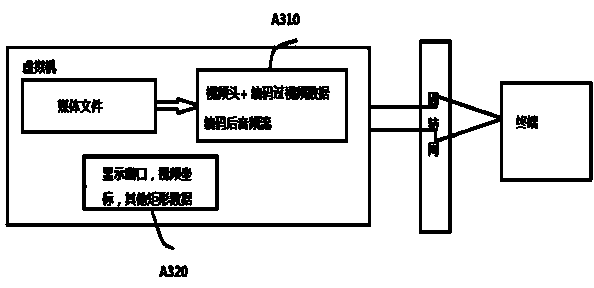
Video redirection method based on cloud computing
The invention discloses a video redirection method based on cloud computing. The video redirection method comprises the steps of analyzing and separating videos on a virtual machine, acquiring the IP address of a client, spreading the videos in a network, and decoding and displaying the videos at the client. According to the invention, a data channel transmits video heads, as well as video data and audio data of all frames, and coordinates and playback rate of a video display region are transmitted to the client through a main-control channel of the cloud desktop protocol; the video heads transmitted from the virtual machine are analyzed to initialize a decoder of the client, video data of all the frames are input into the decoder, and data capable of being directly displayed are output after being decoded; the audio time is utilized as the standard for audio-video synchronization, the positions of the coordinates transmitted to the client from the virtual machine are utilized to display the decoded video images at the client. A video player and remote desktop software work cooperatively to transmit the remotely played video data to the local place, and the video data are decoded to be fused with a desktop transmitted from the virtual machine to be displayed.
Owner:HUBEI UNIV OF EDUCATION
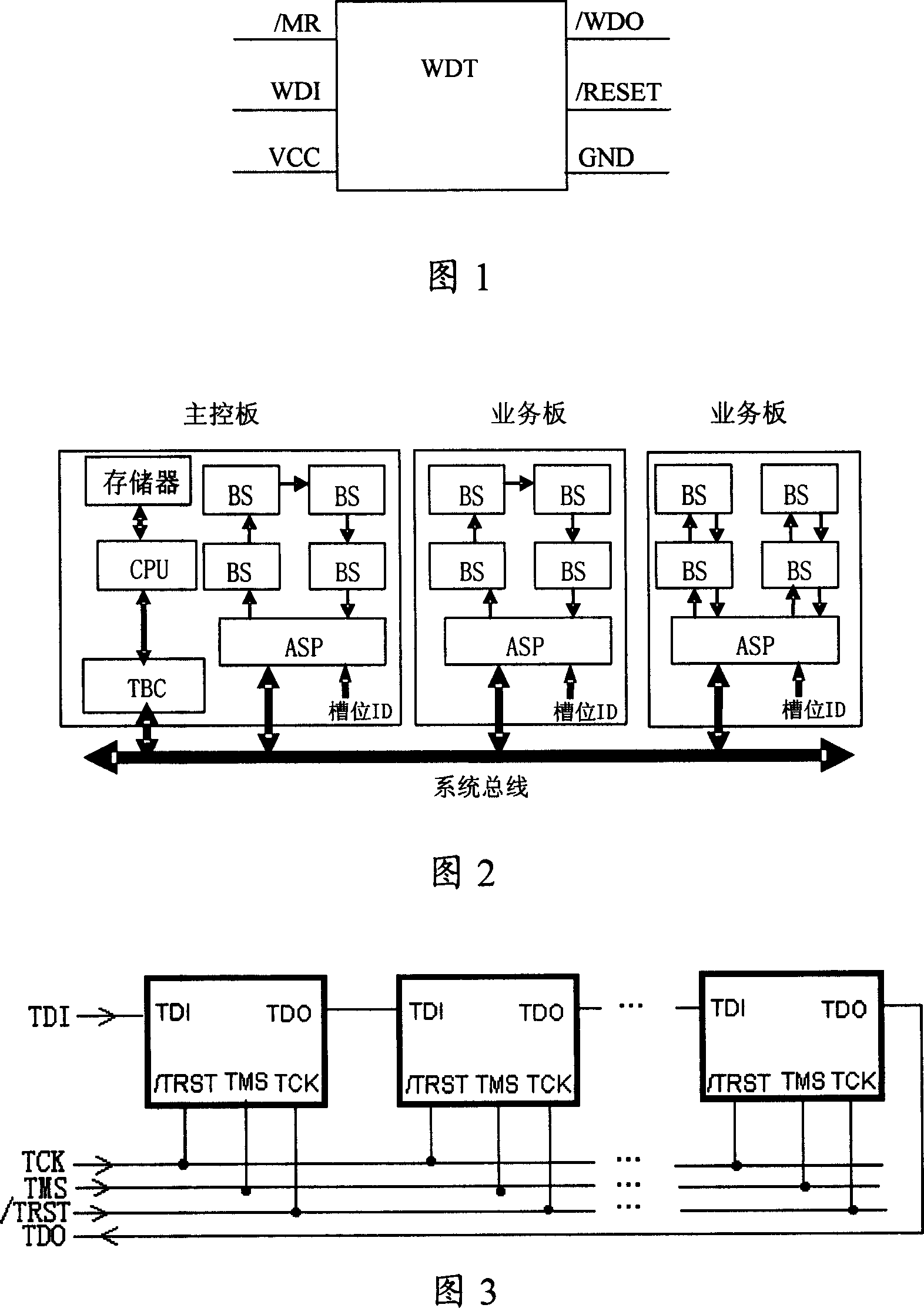
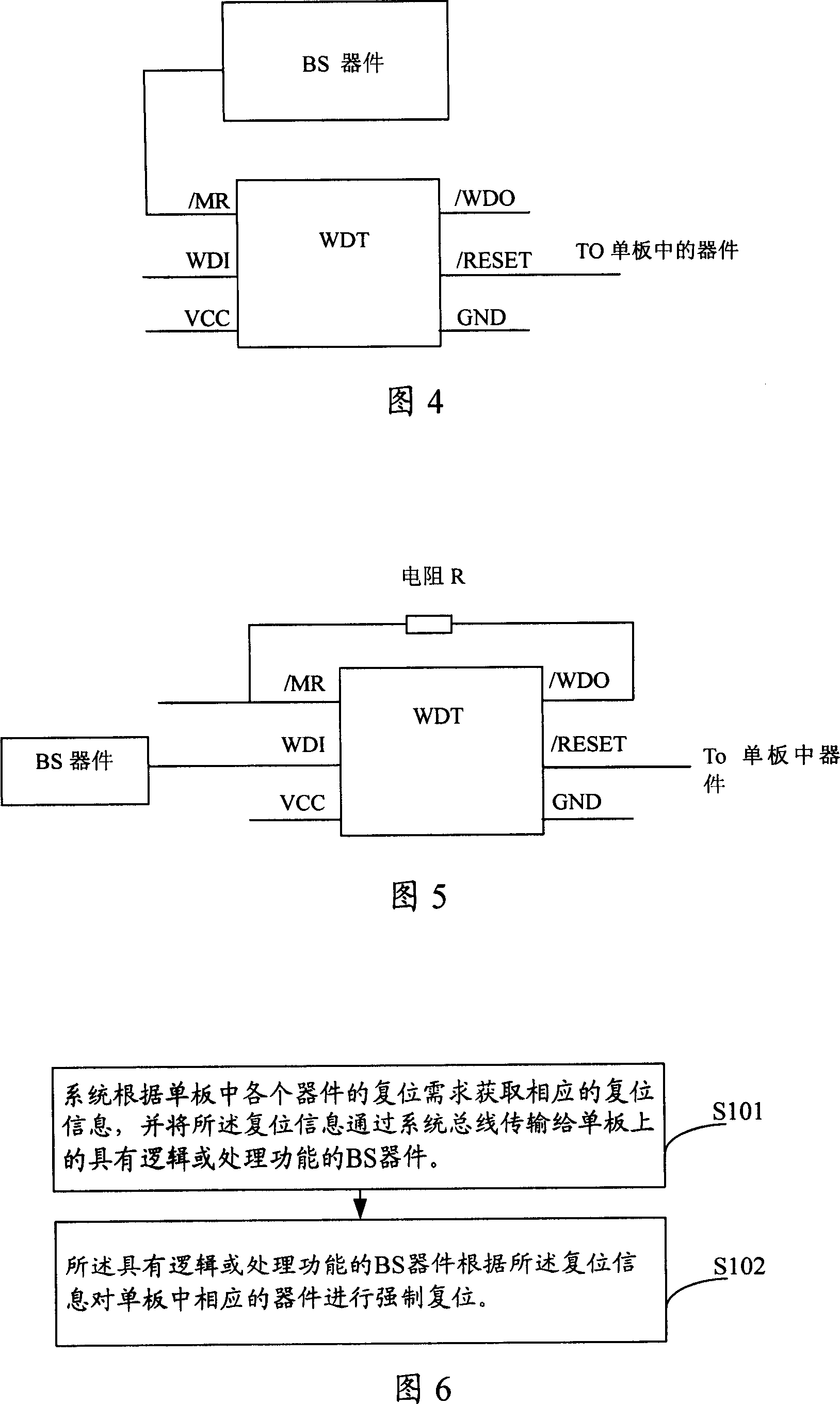
Method and system for realizing one board forced resetting
ActiveCN101021740AGuaranteed uptimeImplement a forced reset operationData resettingRequirements elicitationCanis lupus familiaris
The invention discloses a method and system to realize mandatory reduction of single-desk, which core is: a system acquires the corresponding reduction information according to the demands of different components, and transforms the information to boundary scan device BS in the single-desk with function of logic or dealing through system bus on the backplane. Based on the reduction information, the BS device takes induction on the corresponding device. Under the conditions of abnormal single-desk business and normal dog-software working, this invention can achieve the reduction of single-desk through standard system bus. Moreover, it's more flexible to achieve reduction through system bus, and doesn't need software support to take reduction when the single-desk appears unknown breakdown.
Owner:HUAWEI TECH CO LTD
Linear associative memory-based hardware architecture for fault tolerant ASIC/FPGA work-around
InactiveUS20060107153A1Electronic circuit testingError detection/correctionHardware architectureAlgorithm
A programmable logic unit (e.g., an ASIC or FPGA) having a feedforward linear associative memory (LAM) neural network checking circuit which classifies input vectors to a faulty hardware block as either good or not good and, when a new input vector is classified as not good, blocks a corresponding output vector of the faulty hardware block, enables a software work-around for the new input vector, and accepts the software work-around input as the output vector of the programmable logic circuit. The feedforward LAM neural network checking circuit has a weight matrix whose elements are based on a set of known bad input vectors for said faulty hardware block. The feedforward LAM neural network checking circuit may update the weight matrix online using one or more additional bad input vectors. A discrete Hopfield algorithm is used to calculate the weight matrix W. The feedforward LAM neural network checking circuit calculates an output vector a(m) by multiplying the weight matrix W by the new input vector b(m), that is, a(m)=Wb(m), adjusts elements of the output vector a(m) by respective thresholds, and processes the elements using a plurality of non-linear units to provide an output of 1 when a given adjusted element is positive, and provide an output of 0 when a given adjusted element is not positive. If a vector constructed of the outputs of these non-linear units matches with an entry in a content-addressable memory (CAM) storing the set of known bad vectors (a CAM hit), then the new input vector is classified as not good.
Owner:CISCO TECH INC
Embedded wireless Mesh network router
ActiveCN101296145AMeet the needs of useMeet other relevant performance requirementsData switching by path configurationWireless mesh networkSelf recovery
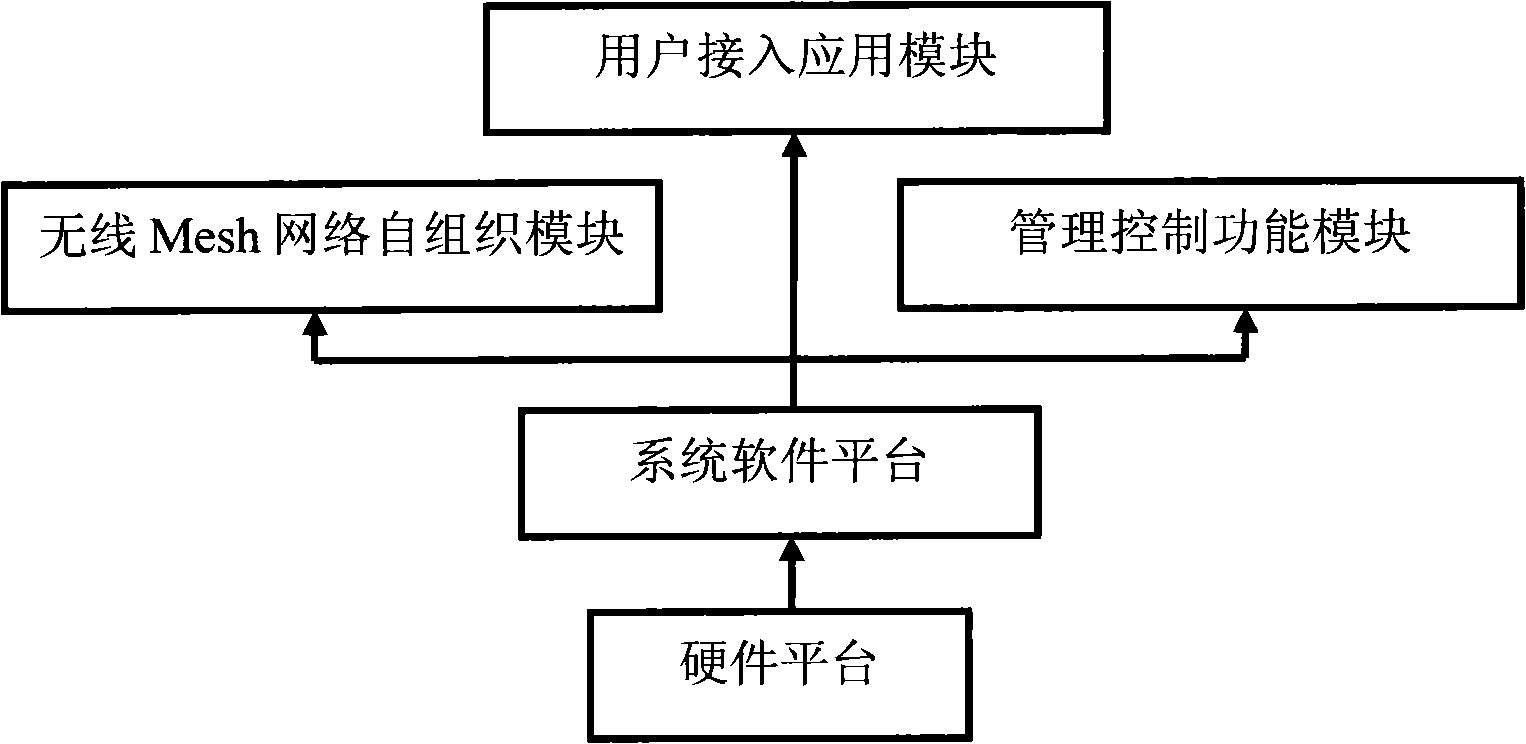
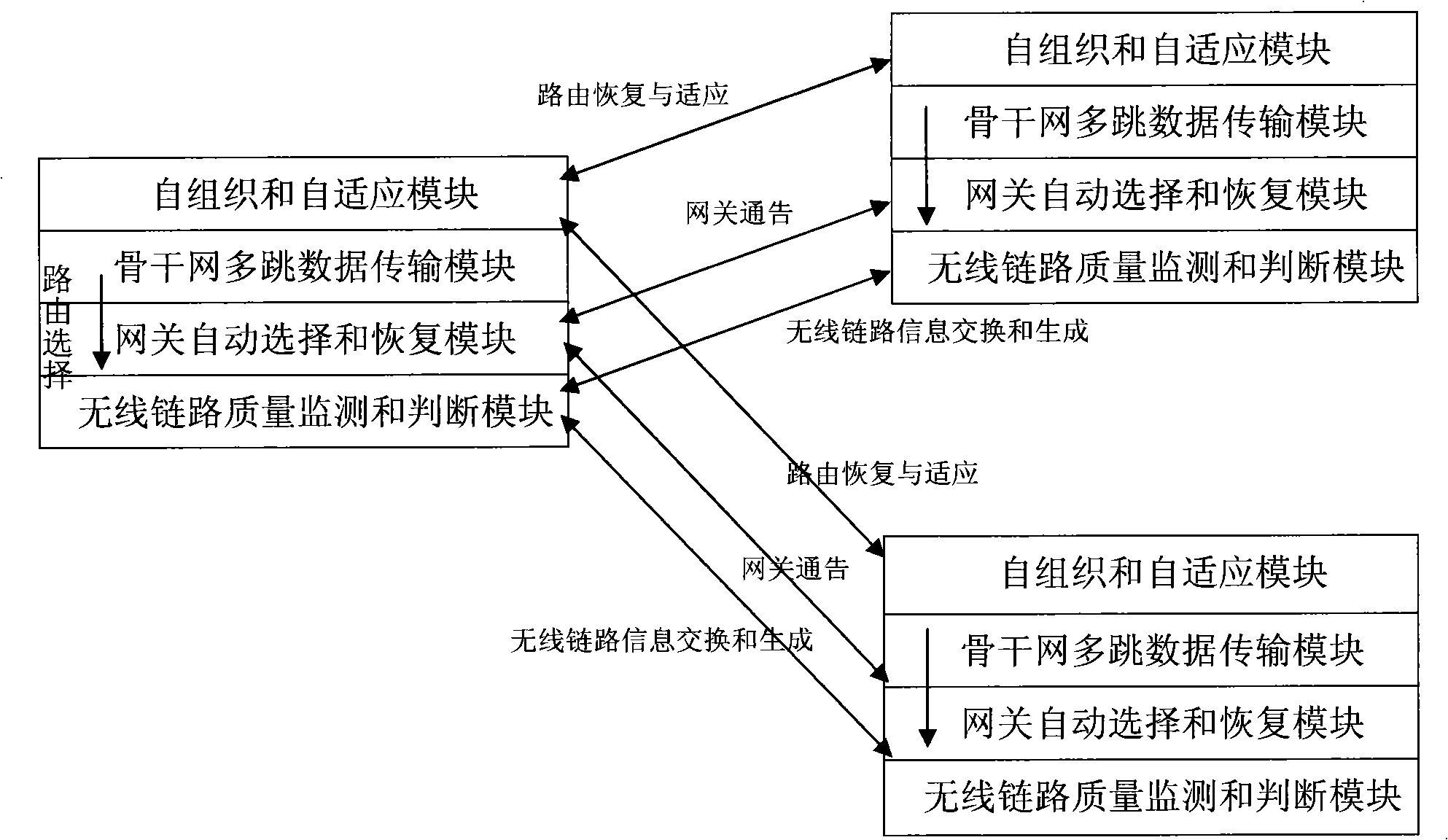
The invention discloses an embedded wireless Mesh network router in the technical field of wireless networks, which comprises a hardware platform, a system software platform, a wireless Mesh network self-organization module, a user access application module and a management control function module, wherein, the hardware platform adopts an embedded design and consists of a core processing module, a wire network communication module and a wireless communication module; the system software platform works on the hardware platform directly and obtains all hardware system information and interfaces to a software working module so as to realize the function of the router; the wireless Mesh network self-organization module provides the function of wireless Mesh network self-organization; the user access application module provides the functions of user access and network application; the management control function module provides administrators with functions of managing and controlling on other function modules. The router of the invention has the performances of self-organization and self-recovery based on the current 802.11g standard and can finish the establishment of Mesh networks independently.
Owner:SHANGHAI MAXTROPY DATA TECH
Locating software for smartphone and PC
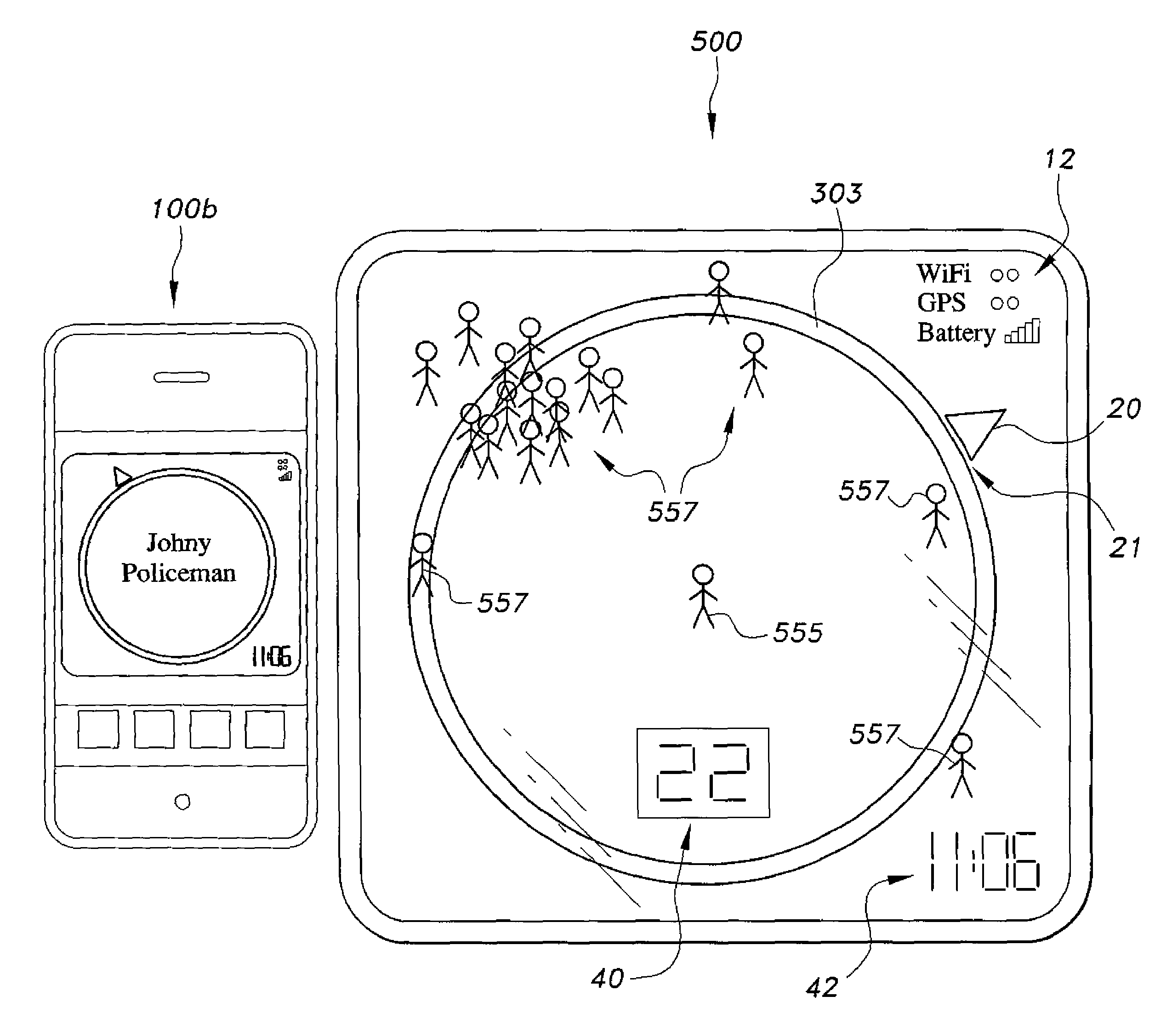
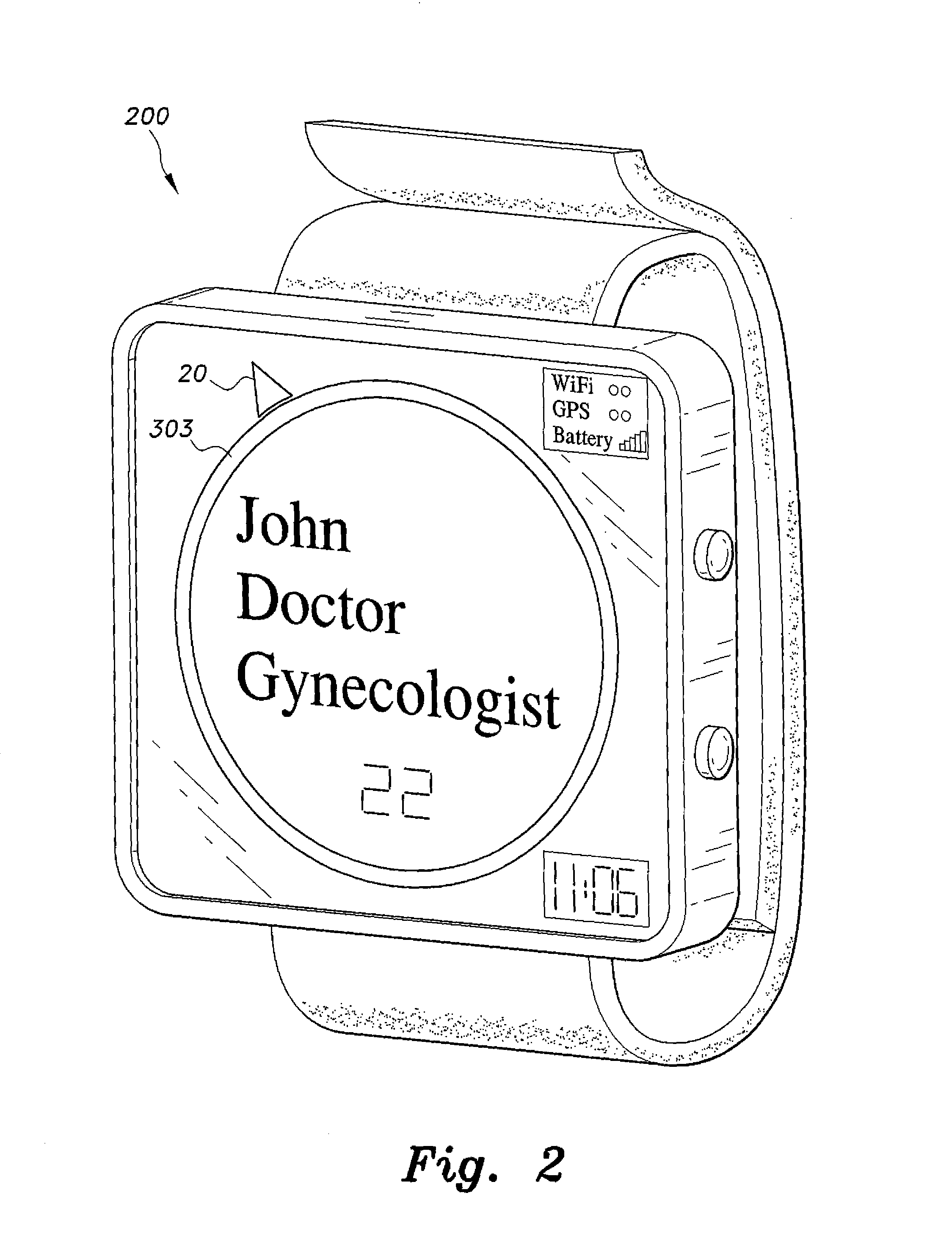
The locating software for smartphone and PC is a software application that lets people know other people's job during walking outside the house. The present software can be downloaded by a client or App store. All people can use it. It helps people to access nearby emergency services. Doctors, police, firemen and the like are immediately accessible using the present software. The present software may also be used for quickly seeking friends. The present software works with Bluetooth, Wi-Fi, 3G, GPS, and the like. The present software integrates with other communication technology that is used in smartphones and PCs. It works within Bluetooth range (about 100 feet), in homes, malls, parks, theaters, and the like.
Owner:BEHBEHANI FAWZI Q M A O A
Software tool configuration type integrated expansion calling method and system
InactiveCN103677842AImplement call handlingImprove scalabilitySpecific program execution arrangementsSoftware engineeringTechnology adaptation
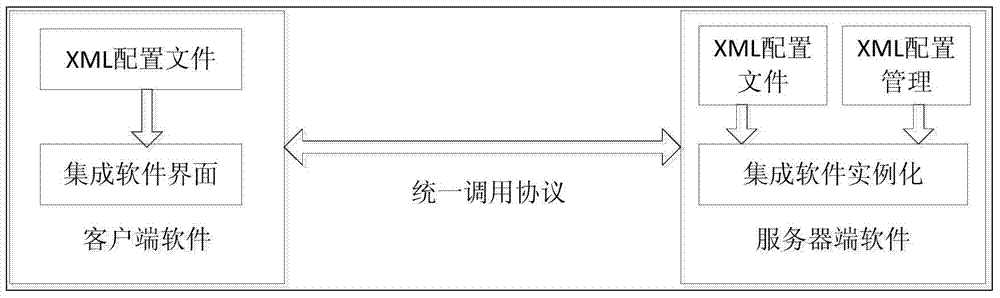
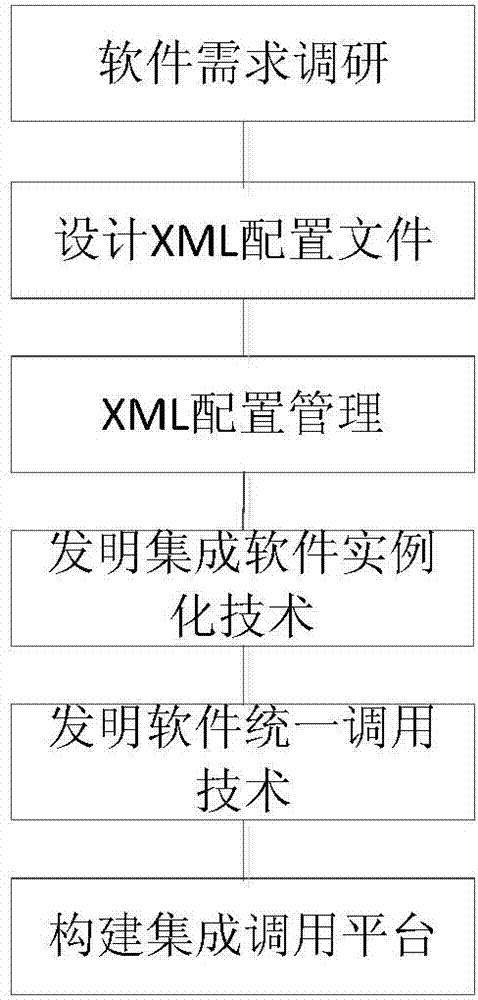
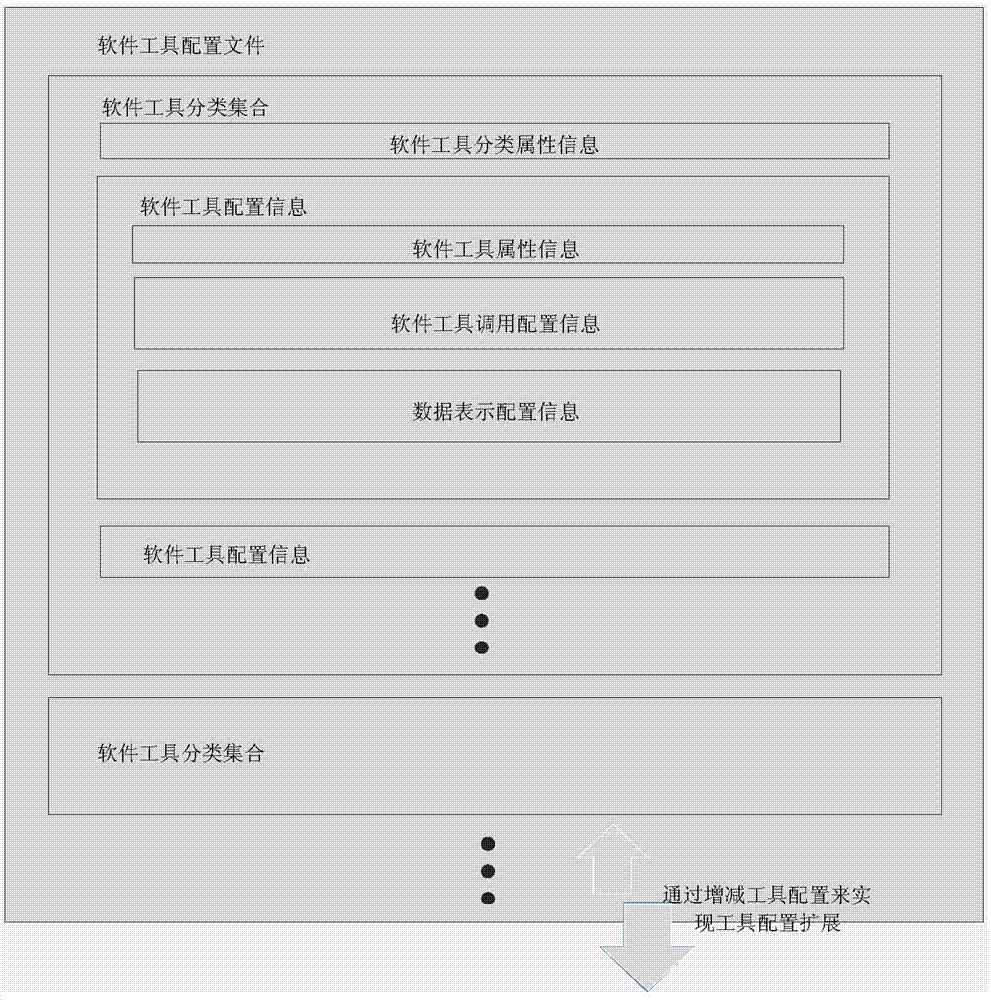
The invention discloses a software tool configuration type integrated expansion calling method and system. A whole set of software integration XML representation standards and uniform calling protocols are designed. By aid of the standards, the calling protocols and the object oriented technology, a series of processes of description, calling and deployment of different software tools are completed, and finally the configuration integration of software tools is realized. A uniform method is used for calling the software tools. The expandable design and the characteristic of supporting local and remote of the method and system can effectively reduce the cost for developing different software tools, and can reduce enterprise cost through deploying software on site to complete software work. The capability of promoting normalization and integration in the integration aspect of software is improved. The network type construction technology adopted by the method and system also enables the uniform calling technology to meet the increasingly developing requirements of network application and the cloud computing technology, and necessary basic protocols and component support are supplied for increasingly wide networks and cloud computing relevant software.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
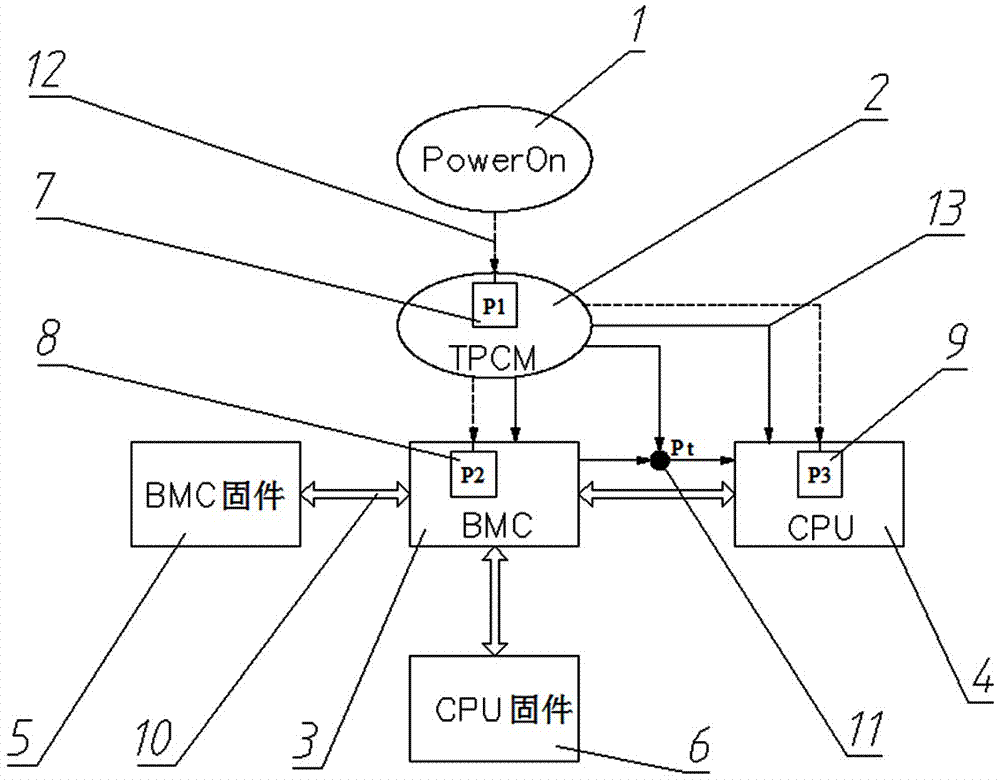
A Power platform-based trusted computer design method and control and operation method
ActiveCN106991327AAvoid security issuesReduce workloadPlatform integrity maintainanceElectricityTrusted Computing
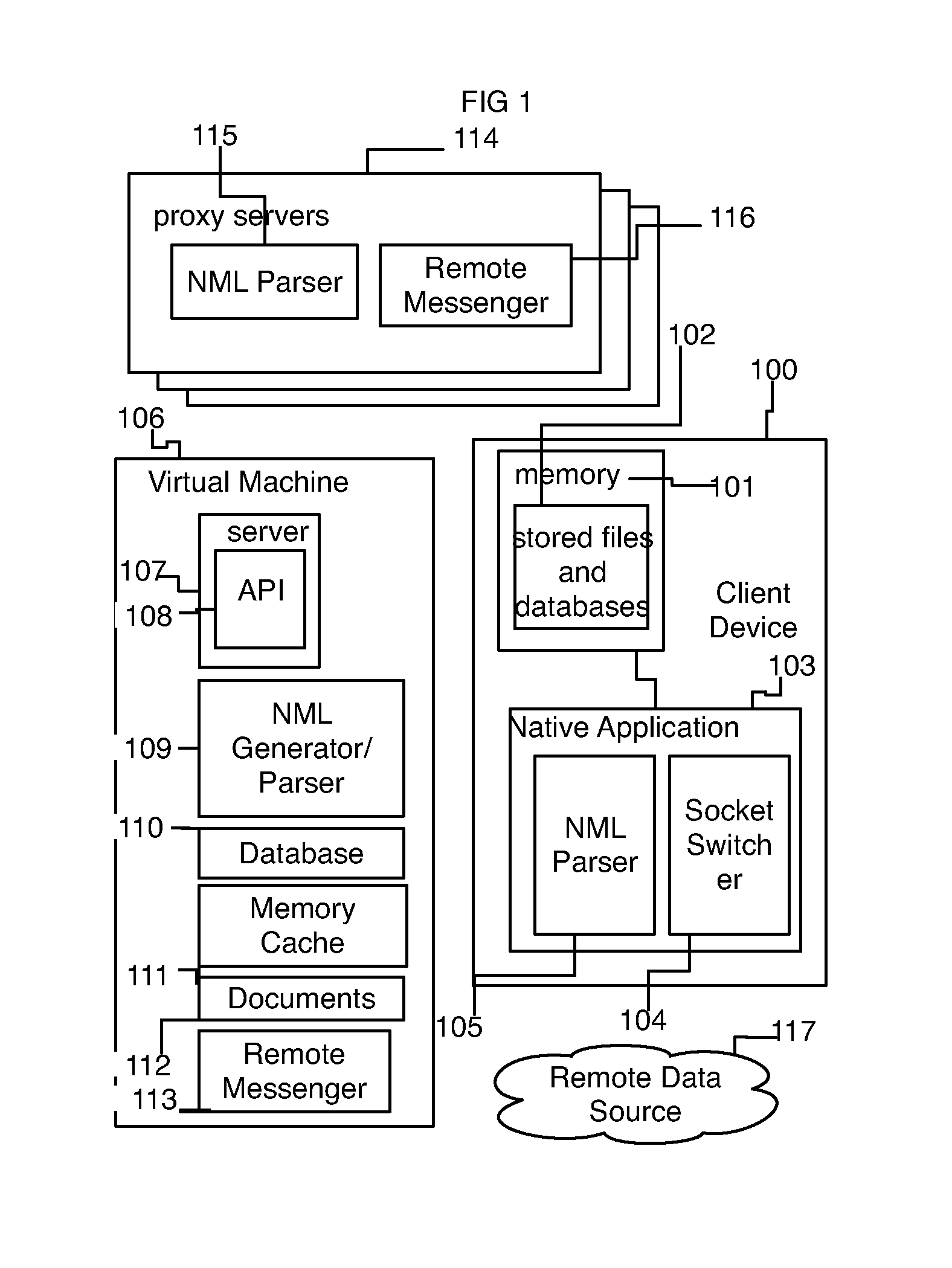
The invention provides a Power platform-based trusted computer design method and control and operation method. A trusted computer comprises a power source (PowerOn), a trusted platform control module (TPCM), a base-board management controller module (BMC), a central processing unit module (CPU), base-board management controller firmware (BMC firmware), and central processing unit firmware. When the system power source (PowerOn) is electrified, the trusted platform control module (TPCM) starts automatically and controls other module power sources of the system. By performing trust measurement on modules, measurement for the base-board management controller module (BMC) and the system PNOR and control to a power source of the base-board management controller module (BMC) and the system power source are achieved, so that problems about computer terminal and network security are solved from the bottom layer, the reliability is improved and workload of software is reduced.
Owner:SHANDONG INTELLIGENT OPTICAL COMM DEV
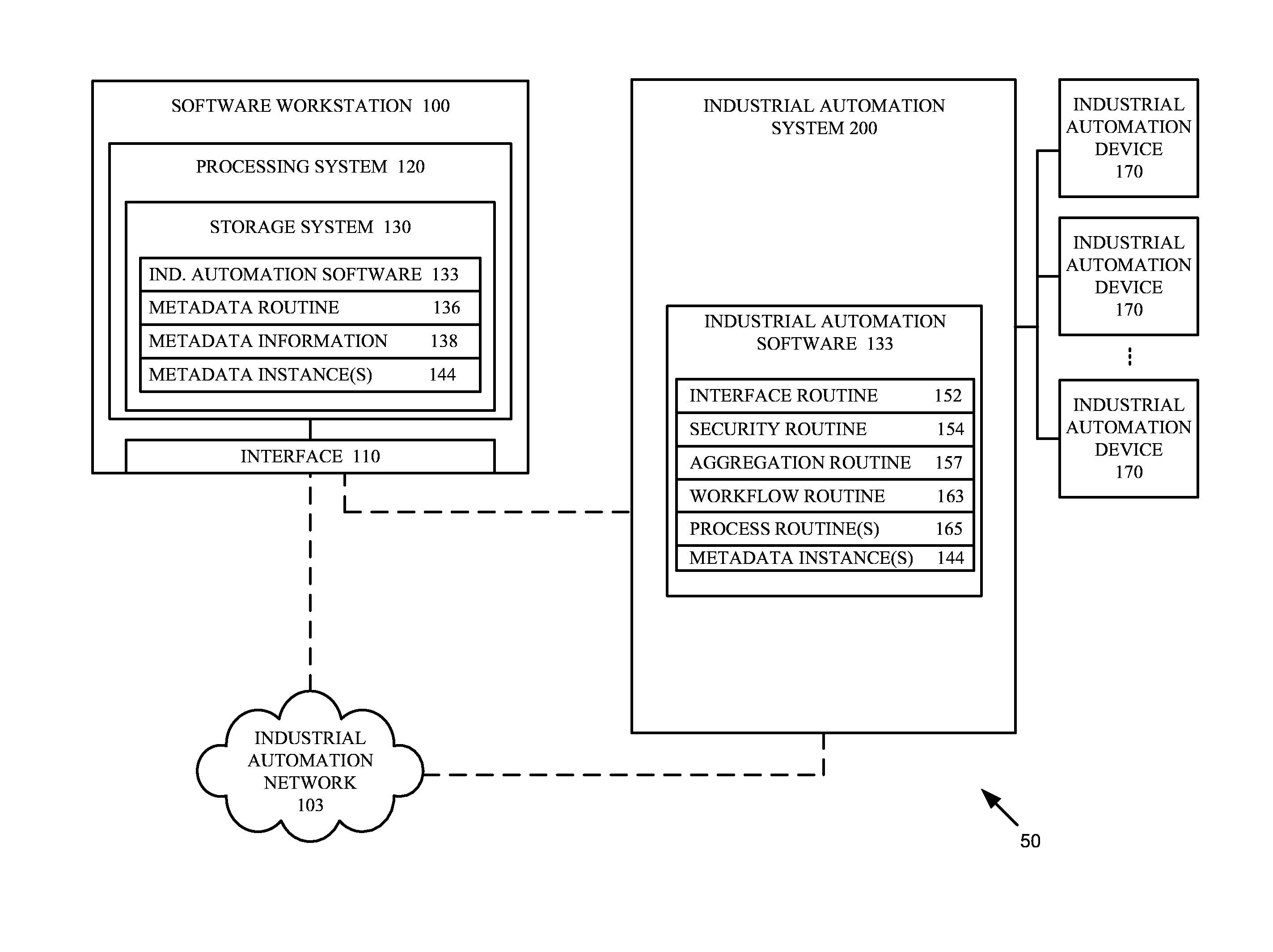
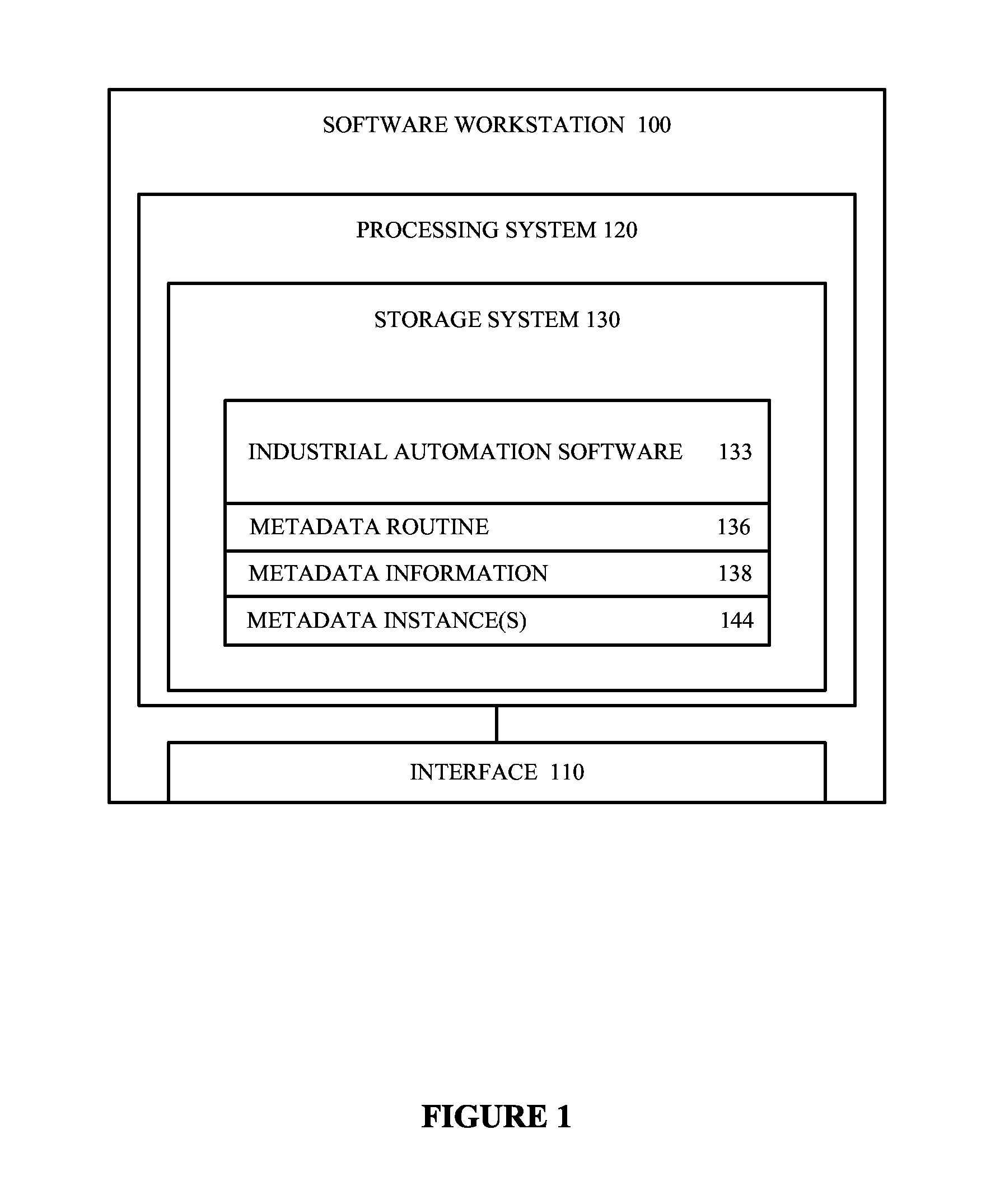
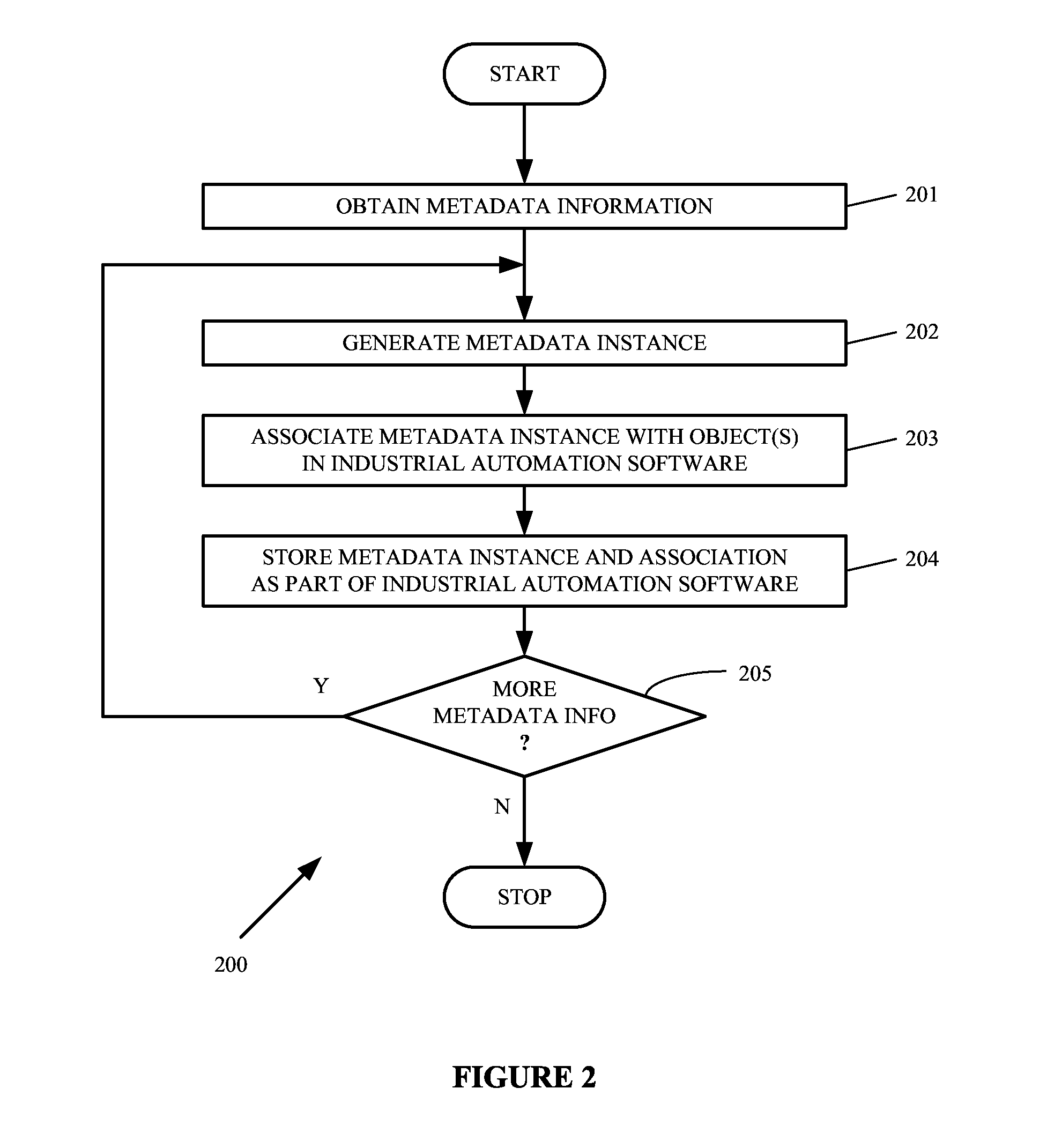
Software workstation and method for employing appended metadata in industrial automation software
A software workstation and method configured to employ appended metadata in an industrial automation software of an industrial automation environment are provided. The software workstation in one example includes an interface configured to interact with a user and communicate with an industrial automation system including the industrial automation software and a processing system coupled to the interface, with the processing system configured to obtain a metadata information, generate at least one metadata instance from the metadata information, associate the at least one metadata instance with one or more predetermined objects in the industrial automation software, and store the at least one metadata instance and the association as part of the industrial automation software.
Owner:ROCKWELL AUTOMATION TECH
Data Infrastructure For Providing Interconnectivity Between Platforms, Devices, and Operating Systems
ActiveUS20140330899A1Accurate estimateEasy to updateTransformation of program codeIntelligent editorsInterconnectivityOperational system
The present invention teaches methods for using a point-and-click interface to allow developers to create visual relationships between APIs and GUI components. Further, the present invention uses interactive machine learning to learn from developer actions. The present invention will assist developers by providing recommendations on how their application should compile to a target platform. Developers may then configure their app and its connection to APIs (device and remote) directly from the present invention's point-and-click interface. The invention also teaches methods for visual recognition of data structures to allow sections of data to be targeted by a system that matches targeted data to a GUI component. The visual recognition system allows any type of data to move between systems and have required protocols applied at run time instead of during development in the way traditional software works.
Owner:ORTIZ GABRIEL JOSHUA ORTI MR
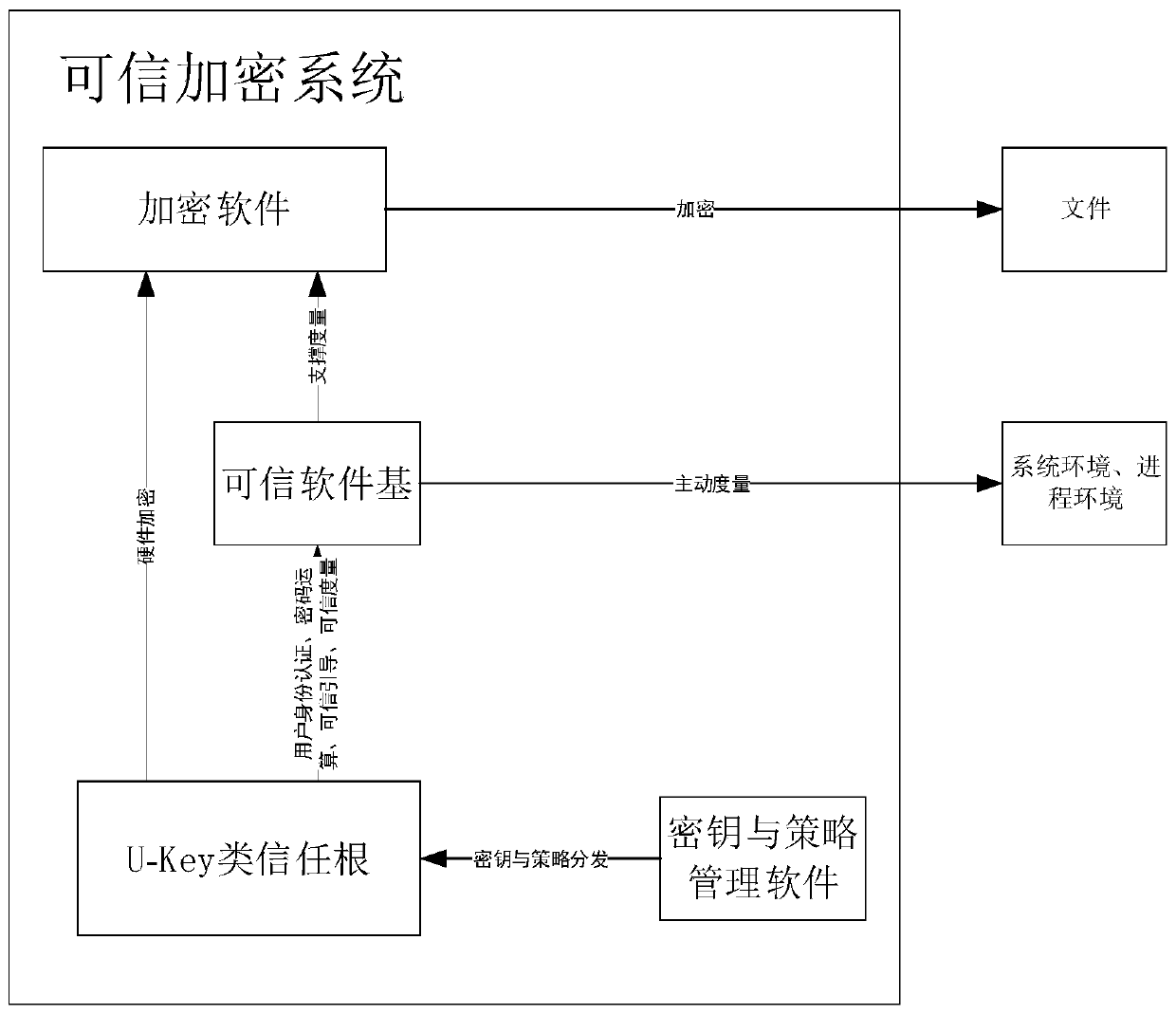
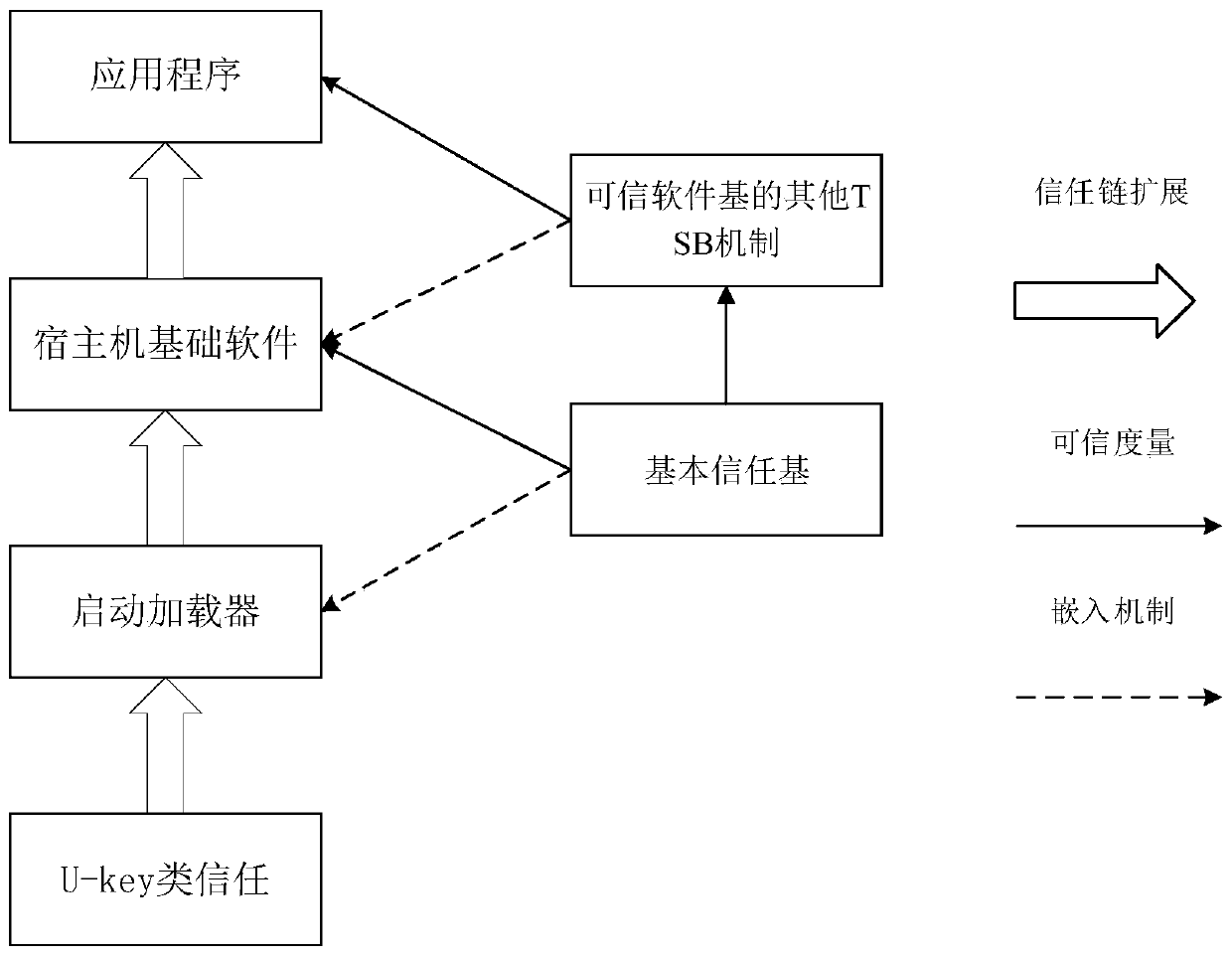
Credible encryption system and method
ActiveCN110188547AEnsure safetyDigital data protectionDigital data authenticationPlaintextTrusted Computing
The invention discloses a credible encryption system and method. The credible encryption system comprises a credible computing platform and a U-Key type trust root, the U-Key type trust root serves asa trust chain starting point of the credible computing platform and is used for supporting the credibility measurement work and the encryption and decryption work of the credible computing platform,and the trusted computing platform comprises a trusted software base and an encryption software. According to the credible encryption system and method provided by the invention, the security of dataduring the encryption and decryption process is ensured by adopting an active immune mechanism; the working security of the encryption software can be ensured; the security policy can be stored in theU-key type trust root, the U-key type trust root provides a secure storage area for secure storage, and the security protection of the virtual disk is provided for the encrypted plaintext, so that the security of the data during the encryption and decryption process can be ensured.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
Method to protect software against unwanted use with a "temporal dissociation" principle
ActiveUS7272725B2Protect normal useUnauthorized memory use protectionHardware monitoringData processing systemOperand
The invention concerns a process to protect a vulnerable software working on a data processing system against its unauthorized usage using a processing and memorizing unit. The process comprises creating a protected software by choosing in the source of the vulnerable software at least one algorithmic processing and by producing the source of the protected software so that during the execution of the protected software appear several distinct steps, namely 1) the placing of at least one operand at the processing and memorizing unit's disposal 2) the carrying out by the processing and memorizing unit, of the algorithmic processing's functionality on at least said operand 3) and possibly, the placing at the data processing system's disposal of at least one result by the processing and memorizing unit.
Owner:VALIDY NET
Information sharing platform for software workers and software demanders
InactiveCN107578814AEasy to shareImprove service capabilitiesHealthcare resources and facilitiesStatistical analysisSoftware requirements
The invention provides an information sharing platform for software workers and software demanders. The platform comprises a hospital information source, an emergency center terminal and a special line network system, the hospital information source and the emergency center terminal are both connected to the special line network system through data integrated security gateways, the special line network system is connected with a regional medical information data sharing platform, the regional medical information data sharing platform comprises a cloud platform application server, a cloud storage system, an encryption and decryption module, a statistical analysis system, a medical image main index and a patient treatment main index, and the cloud platform application server is connected with a mobile terminal, so that comprehensive system integration is conducted on different medical institutions to form the medical information sharing platform with unified standards, the sharing capability of medical information and the service capability of the medical information service platform can be improved, better regional medical services are achieved, and the platform has great superiority compared with traditional decentralized and independent construction modes.
Owner:南京荣膺软件科技有限公司
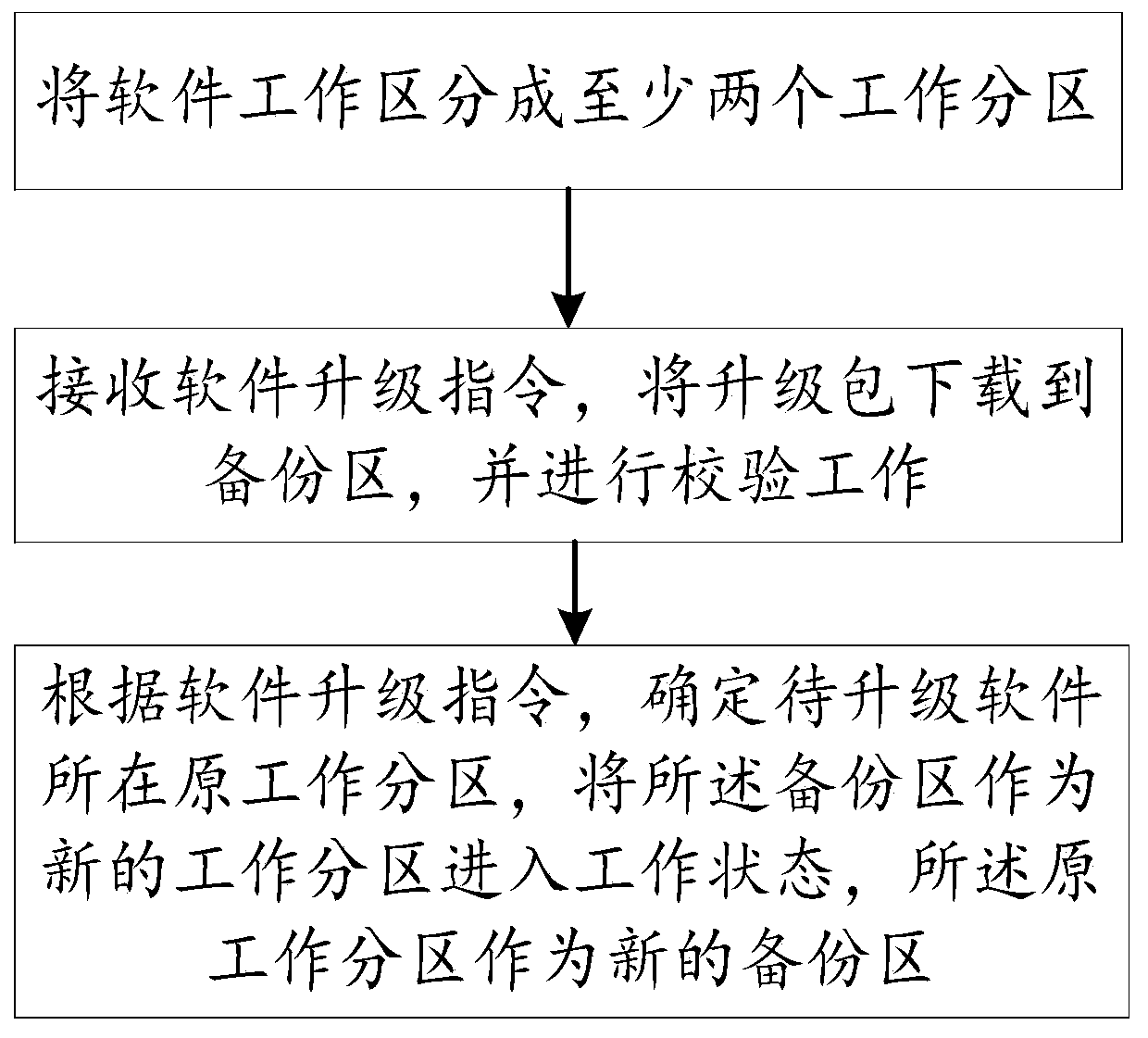
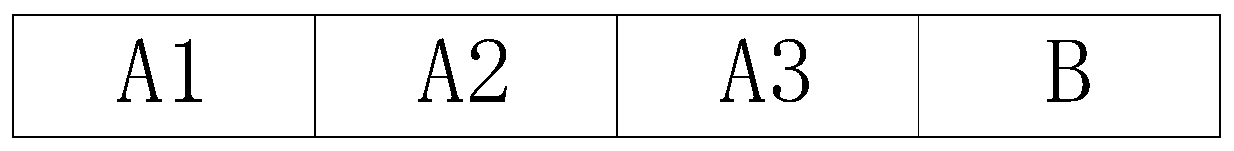
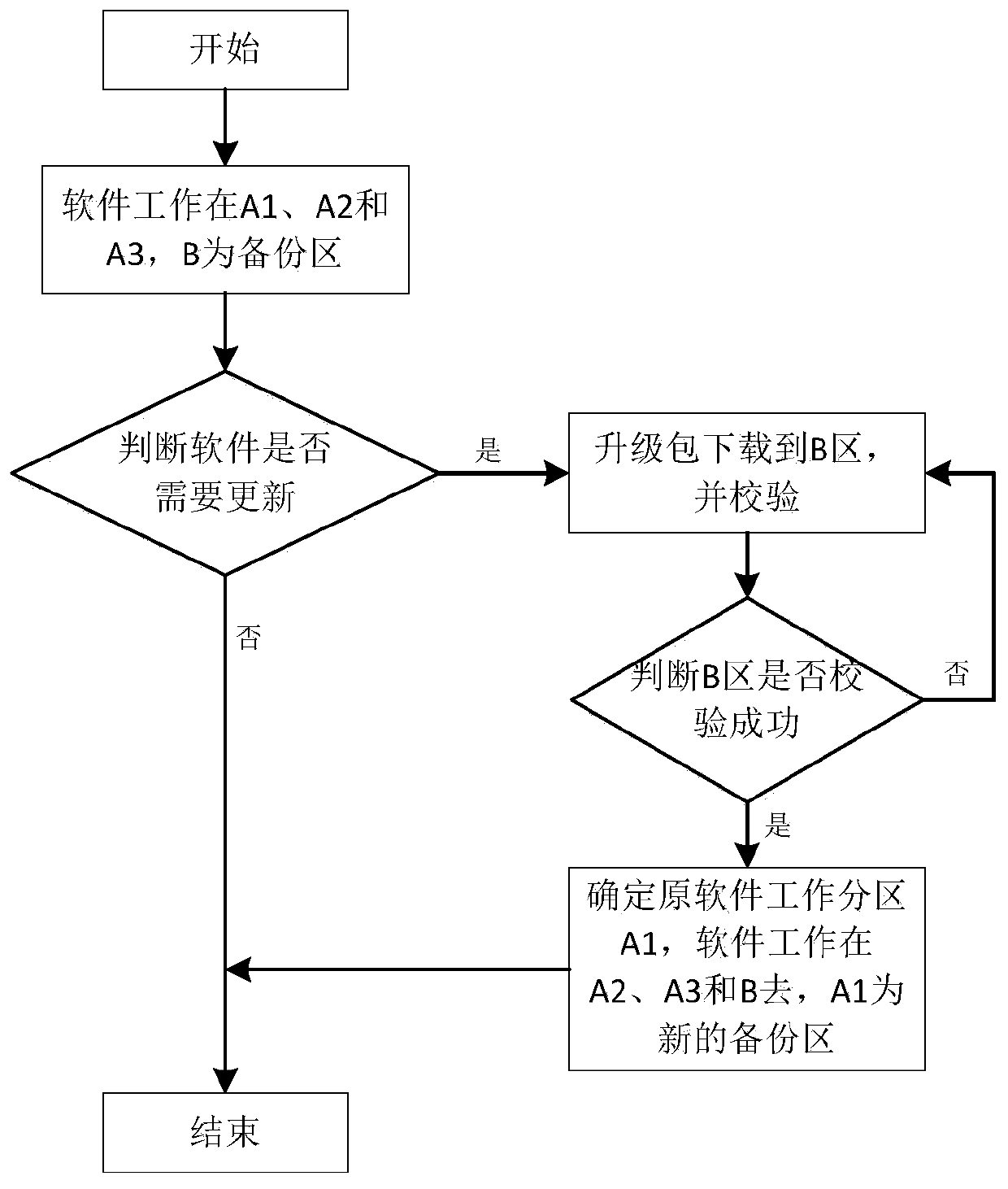
Software upgrading method and device, equipment and storage medium
ActiveCN110311960AReduce default capacityReduce storage space requirementsSoftware engineeringTransmissionSpace requirementsWork status
The invention discloses a software upgrading method and device, equipment and a storage medium. The method comprises: dividing a software working area into at least two working subareas; receiving a software upgrading instruction, downloading the upgrading package to a backup area, and performing verification work; according to the software upgrading instruction, determining the original working partition where the to-be-upgraded software is located, taking the backup area as a new working partition to enter the working state, and taking the original working partition as a new backup area. Byarranging the multiple working partitions, the preset capacity of the backup area can be reduced, so that the storage space requirement is reduced, and the cost is saved.
Owner:ZHEJIANG GEELY HLDG GRP CO LTD +1
Method to protect software against unwanted use with a "detection and coercion" principle
ActiveUS7174466B2Digital data processing detailsUser identity/authority verificationData processing systemSoftware work
The invention concerns a process to protect a vulnerable software working on a data processing system against its unauthorized usage using a processing and memorizing unit. The process comprises defining: 1) at least one software execution characteristic, liable to be monitored at least in part in a processing and memorizing unit 2) at least one criterion to abide by for at least one software execution characteristic 3) detection means to implement in a processing and memorizing unit and enabling to detect that at least one software execution characteristic does not abide by at least one associated criterion 4) coercion means to implement in a processing and memorizing unit and enabling to inform the data processing system and / or modify the execution of a software when at least one criterion is not abided by.
Owner:VALIDY NET
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com