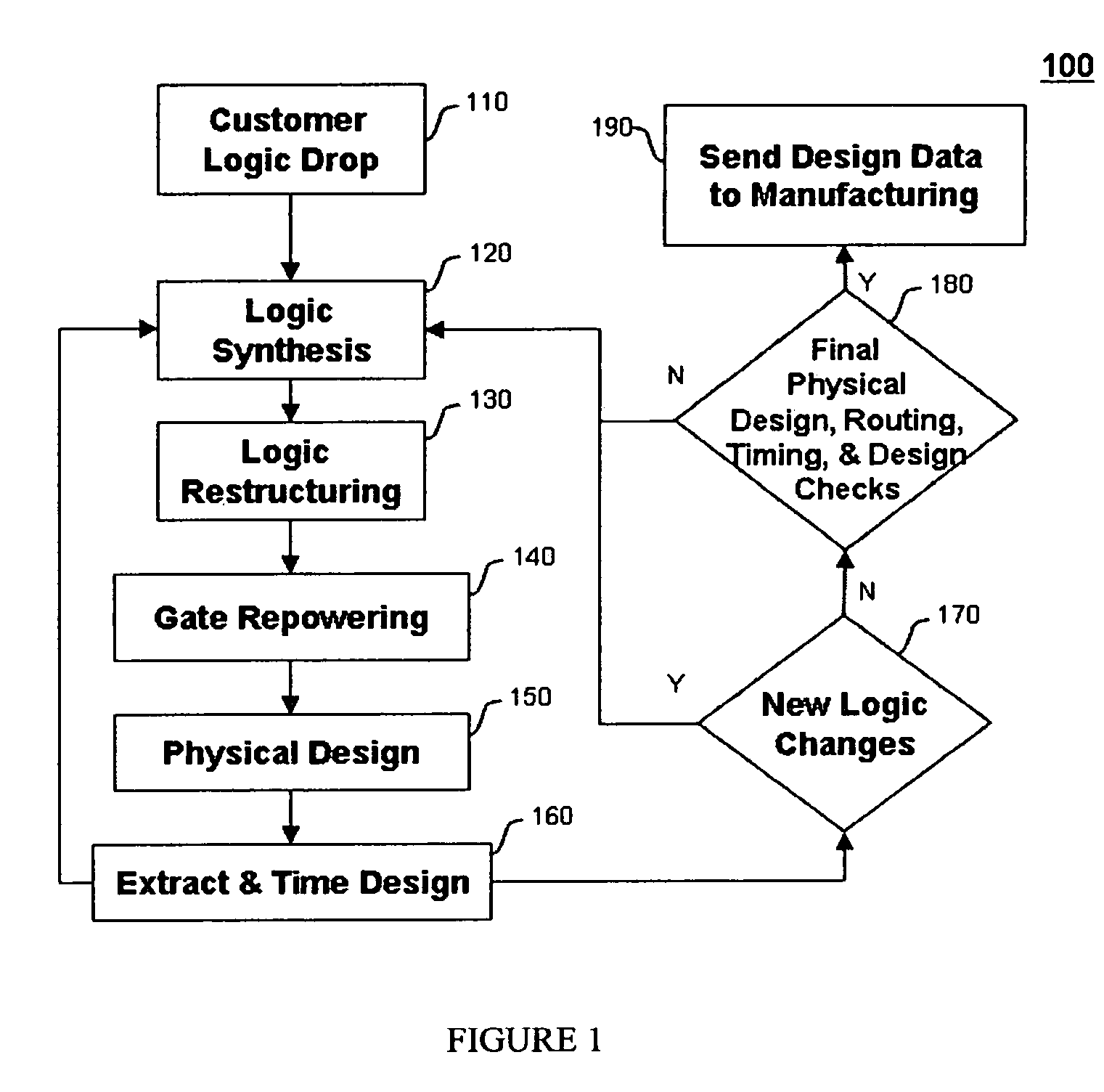
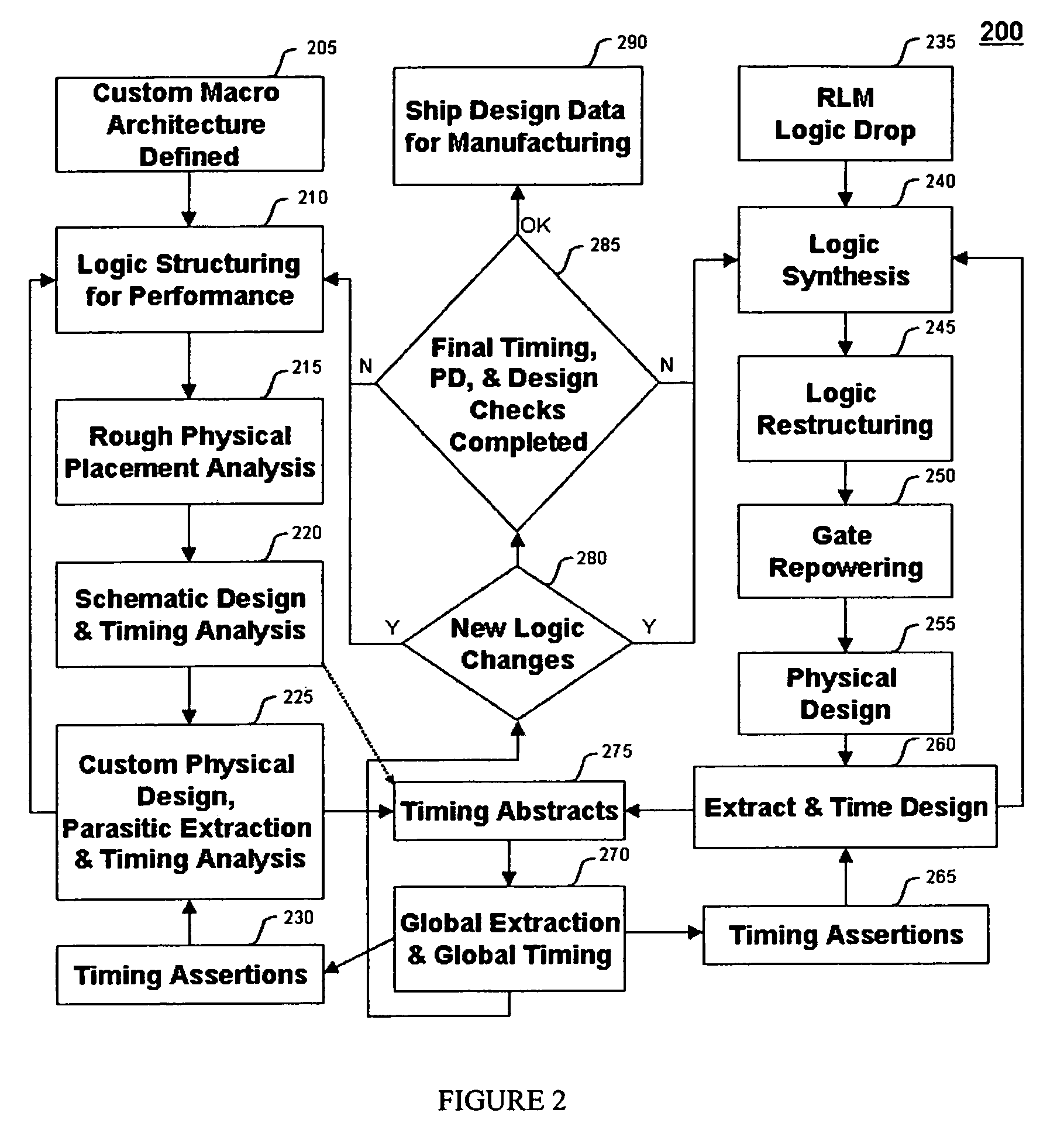
Patents
Literature
4019 results about "Logisim" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
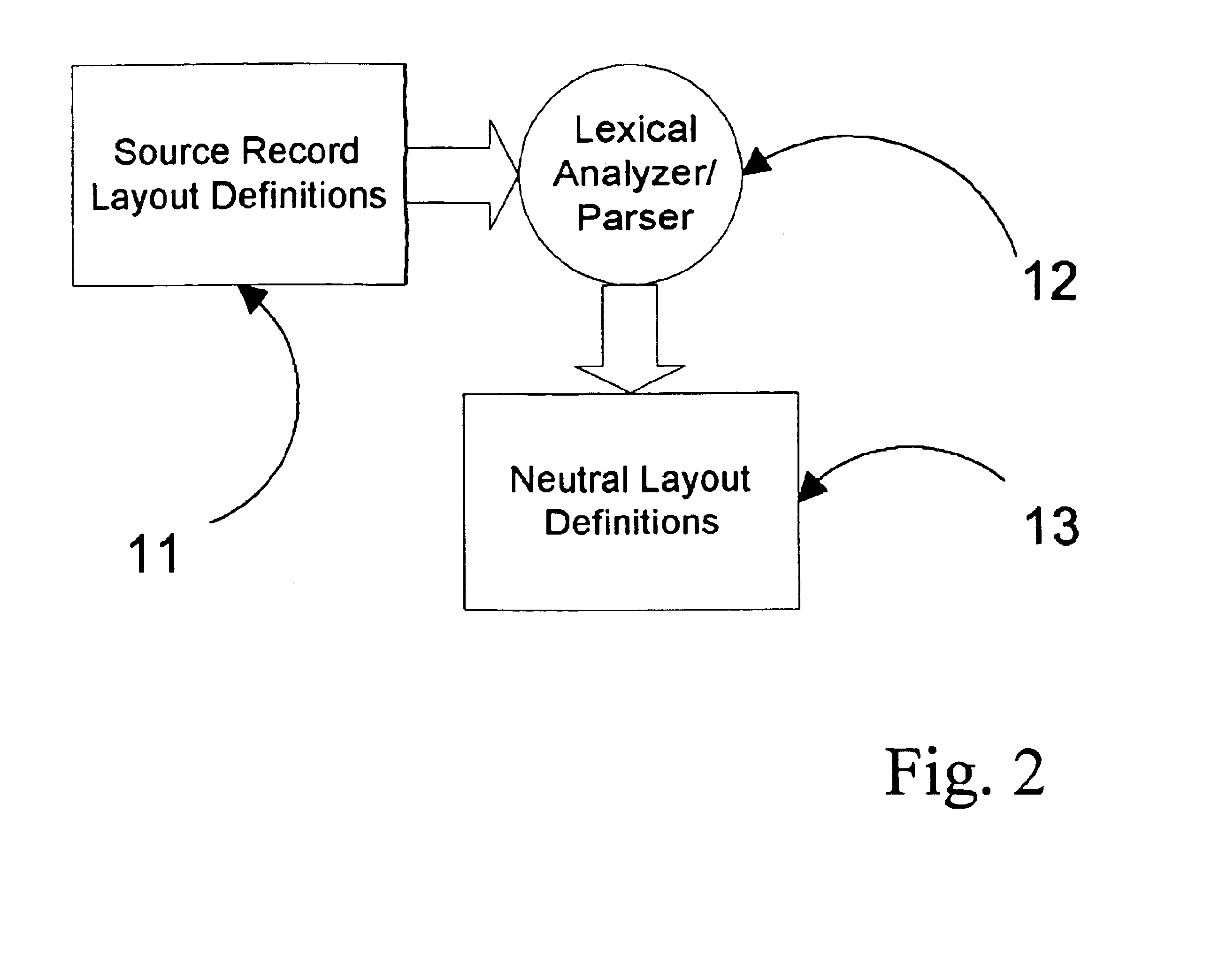
Logisim is a logic simulator which permits circuits to be designed and simulated using a graphical user interface. Released under the GNU Public License, Logisim is free software designed to run on the Windows, macOS, and Linux operating systems. Its code is Java using the Swing graphical user interface library. The primary developer, Carl Burch, worked on Logisim from 2001 to 2011. On October 11, 2014, Burch announced that he was suspending development of Logisim indefinitely.
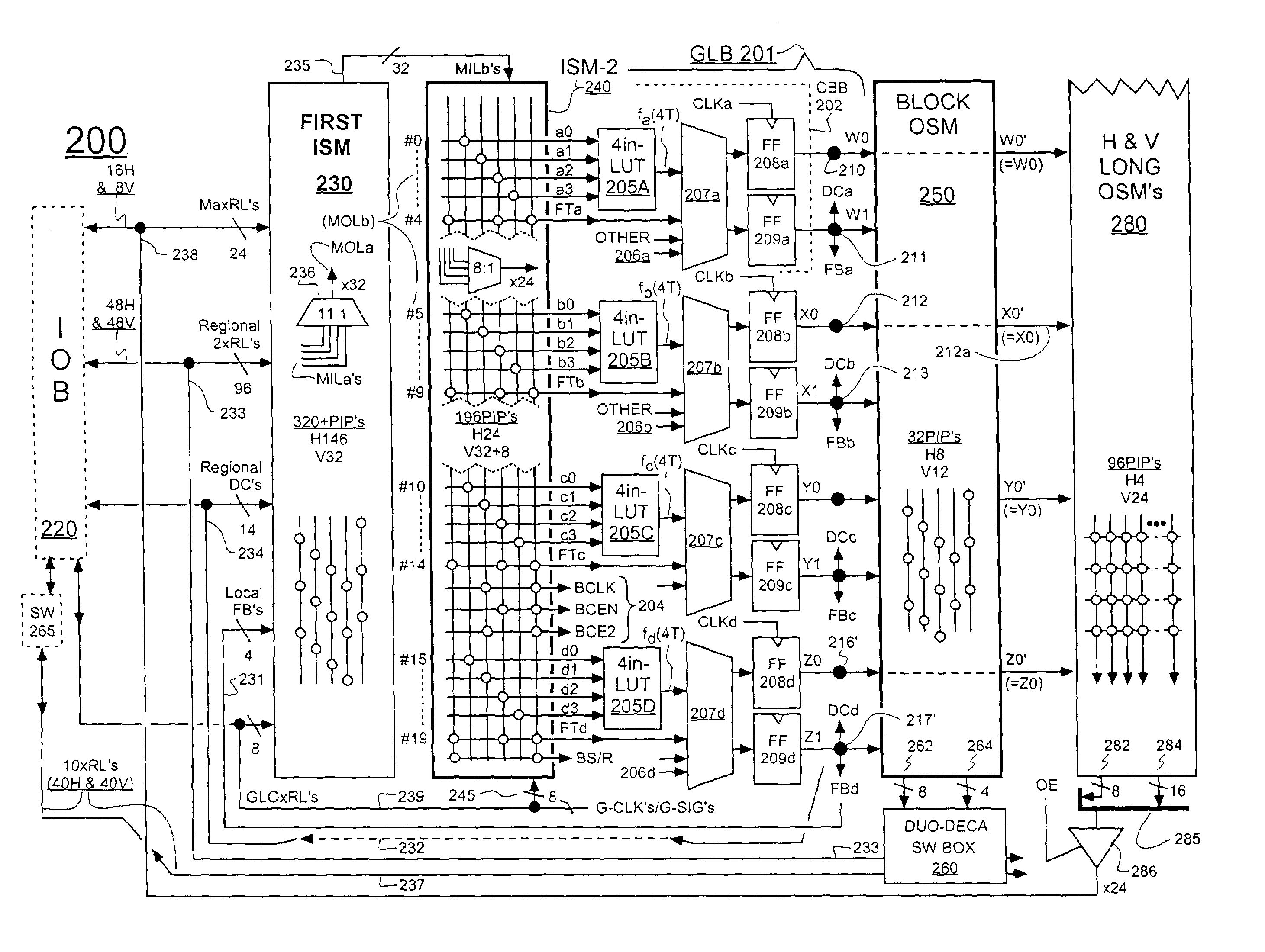
FPGA with register-intensive architecture
ActiveUS7028281B1Minimize resourceReduce consumptionSolid-state devicesCAD circuit designProcessor registerMultiplexer
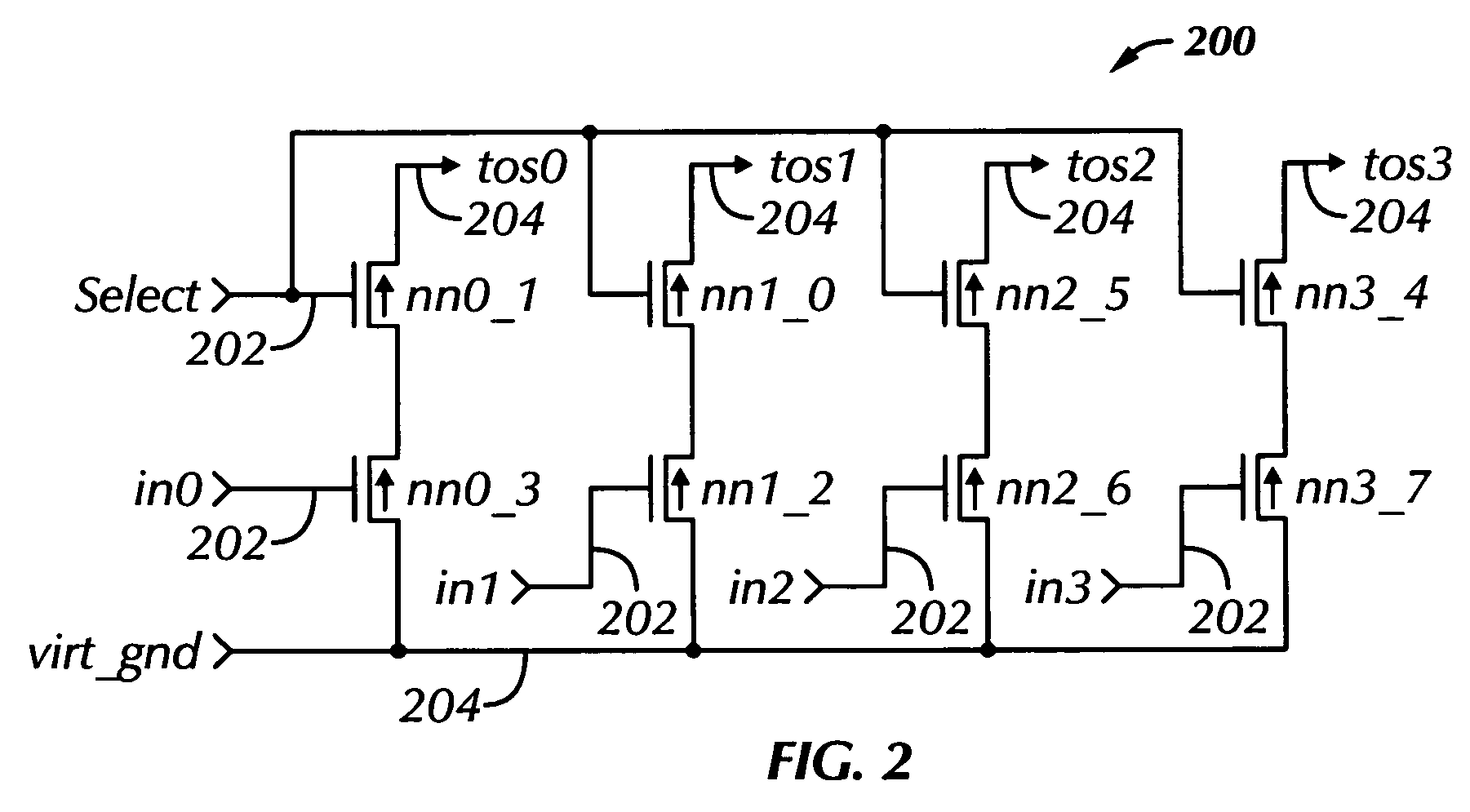
Field programmable gate arrays (FPGA's) may be structured in accordance with the disclosure to have a register-intensive architecture that provides, for each of plural function-spawning LookUp Tables (e.g. a 4-input, base LUT's) within a logic block, a plurality of in-block accessible registers. A register-feeding multiplexer means may be provided for allowing each of the plural registers to equivalently capture and store a result signal output by the corresponding, base LUT of the plural registers. Registerable, primary and secondary feedthroughs may be provided for each base LUT so that locally-acquired input signals of the LUT may be fed-through to the corresponding, in-block registers for register-recovery purposes without fully consuming (wasting) the lookup resources of the associated, base LUT. A multi-stage, input switch matrix (ISM) may be further provided for acquiring and routing input signals from adjacent, block-interconnect lines (AIL's) and / or block-intra-connect lines (e.g., FB's) to the base LUT's and / or their respective, registerable feedthroughs. Techniques are disclosed for utilizing the many in-block registers and / or the registerable feedthroughs and / or the multi-stage ISM's for efficiently implementing various circuit designs by appropriately configuring such register-intensive FPGA's.
Owner:LATTICE SEMICON CORP
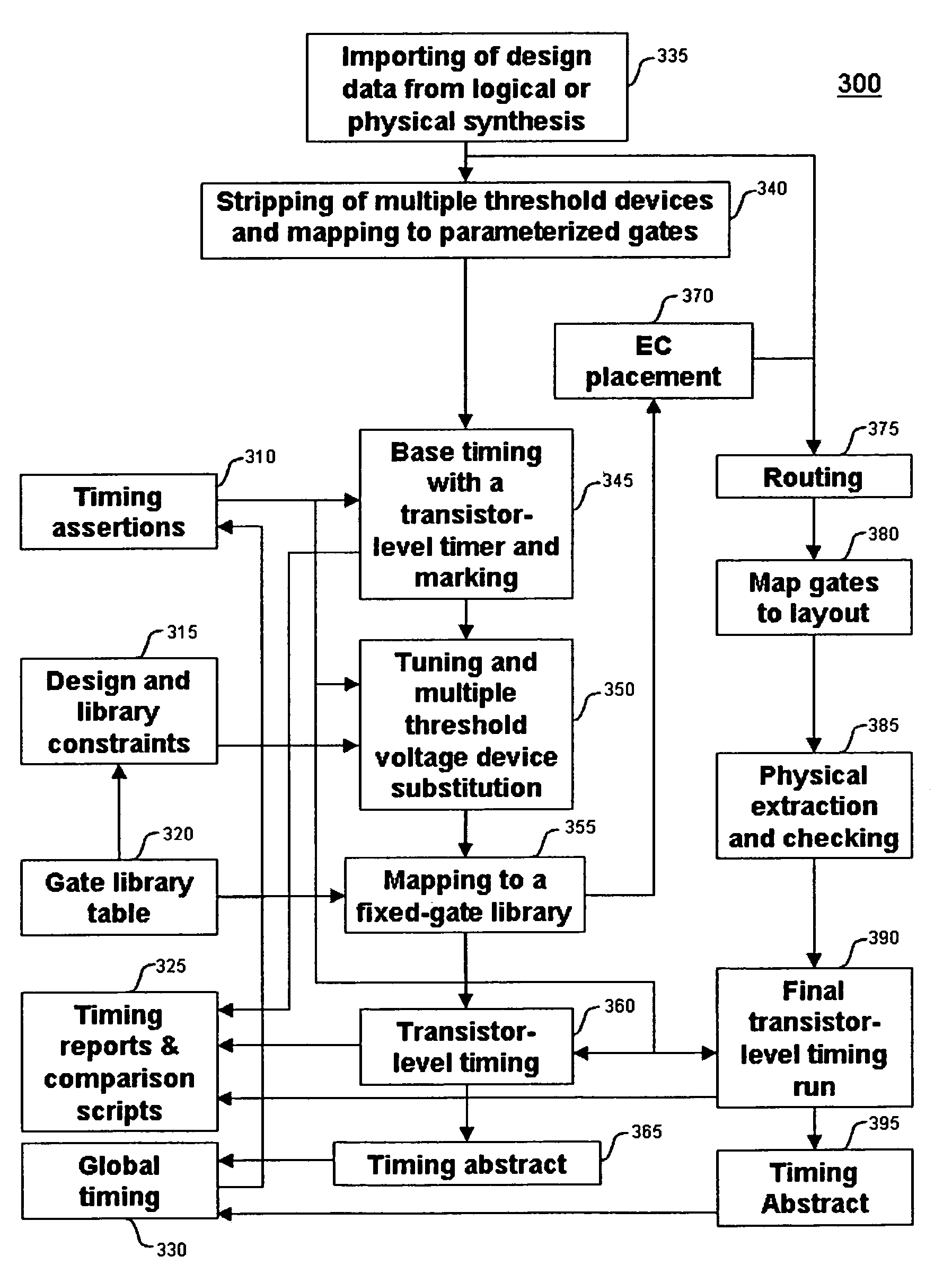
Method for tuning a digital design for synthesized random logic circuit macros in a continuous design space with optional insertion of multiple threshold voltage devices
InactiveUS7093208B2Efficient and effective methodologyError minimizationDigital storageComputer aided designContinuous designCritical section
A Digital Design Method which may be automated is for obtaining timing closure in the design of large, complex, high-performance digital integrated circuits. The methodincludes the use of a tuner on random logic macros that adjusts transistor sizes in a continuous domain. To accommodate this tuning, logic gates are mapped to parameterized cells for the tuning and then back to fixed gates after the tuning. Tuning is constrained in such a way as to minimize “binning errors” when the design is mapped back to fixed cells. Further, the critical sections of the circuit are marked in order to make the optimization more effective and to fit within the problem-size constraints of the tuner. A specially formulated objective function is employed during the tuning to promote faster global timing convergence, despite possibly incorrect initial timing budgets. The specially formulated objective function targets all paths that are failing timing, with appropriate weighting, rather than just targeting the most critical path. Finally, the addition of multiple threshold voltage gates allows for increased performance while limiting leakage power.
Owner:GLOBALFOUNDRIES INC
System and method for developing software applications using an extended XML-based framework
InactiveUS6845499B2Developing software applications have been substantially reduced or eliminatedShort development cycleSoftware designSpecific program execution arrangementsRequest - actionSoftware engineering
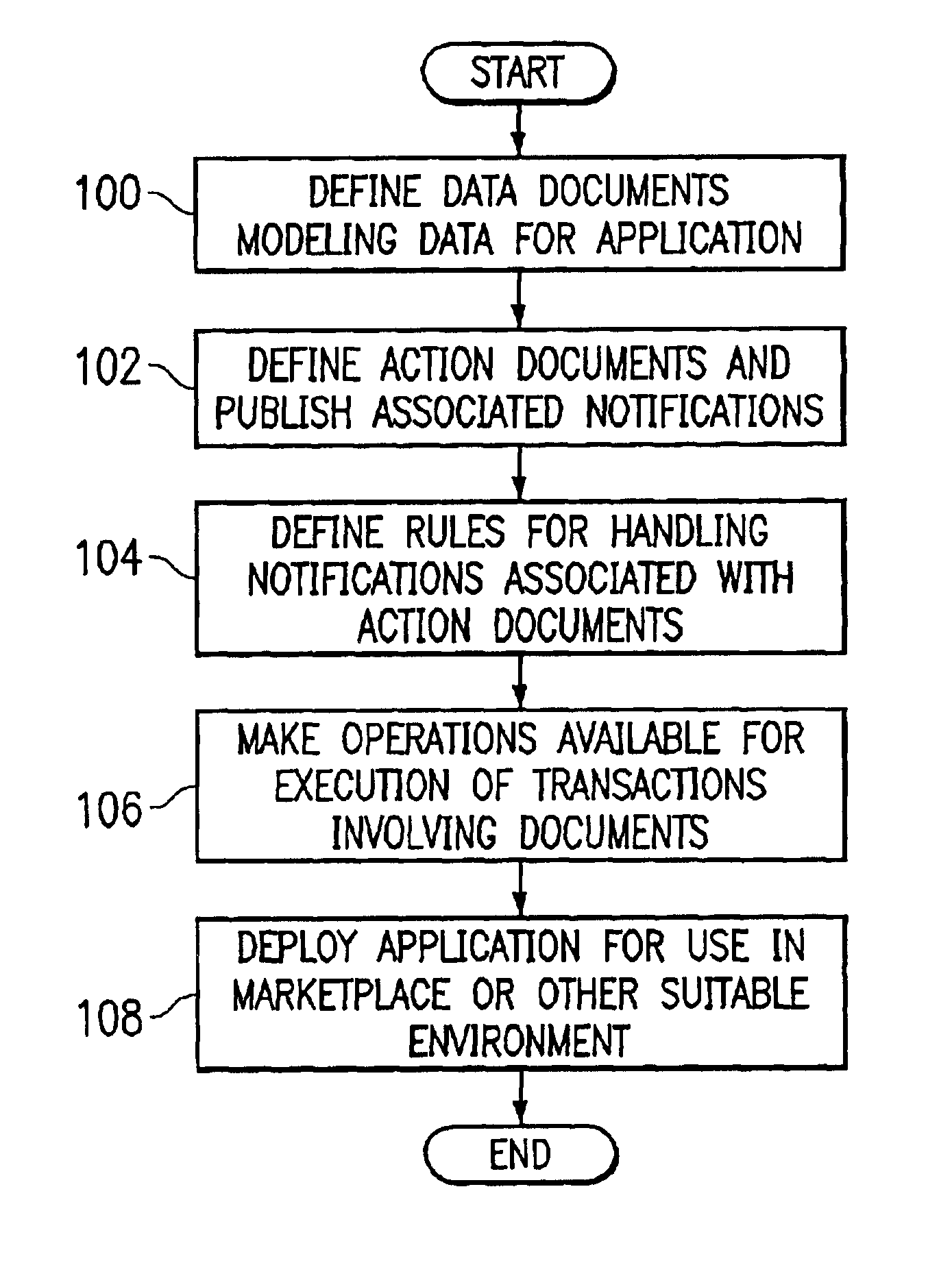
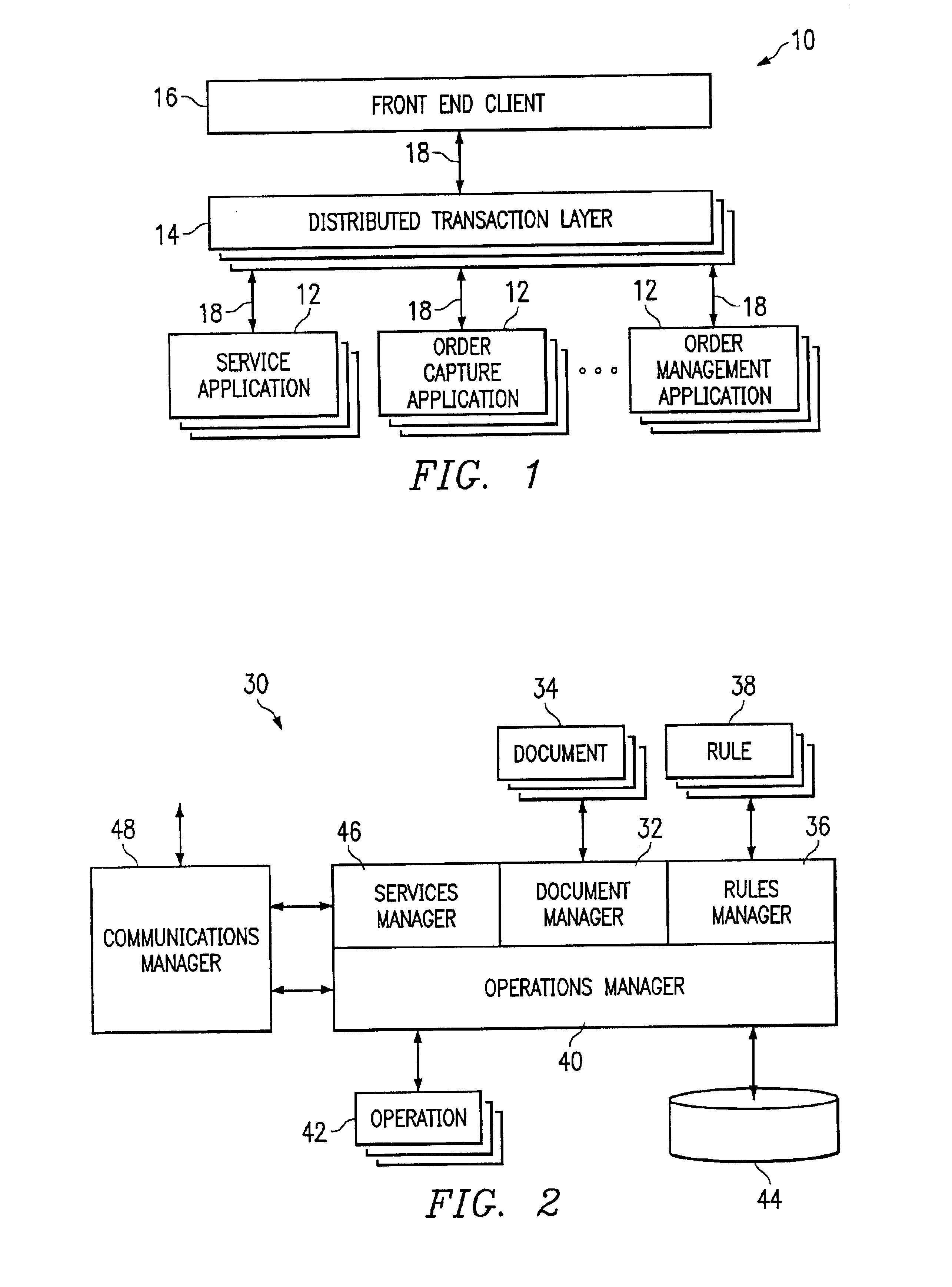
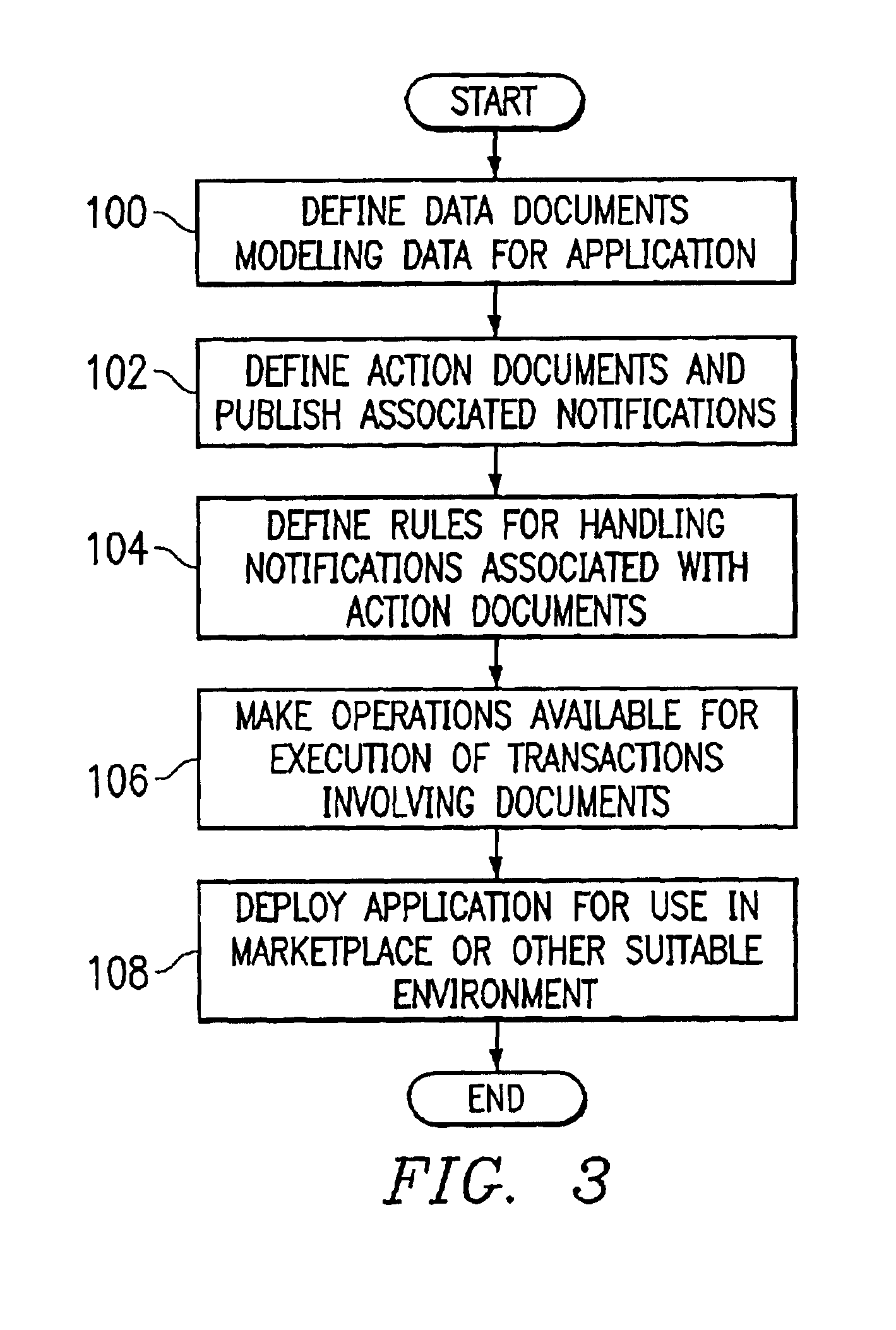
An XML-based framework (30) for developing software applications (12) includes a document manager (32) to manage activities relating to one or more XML-based data documents (34) associated with an application (12), each data document (34) modeling data associated with the application (12) and representing relationships between the data document (34) and one or more other data documents (34). The framework (30) includes a rules manager (36) to manage rules (38) specifying logic for handling notifications associated with XML-based action documents (34) received at the application (12), the notifications requesting actions involving data documents (34). The framework (30) also includes an operations manager (40) to manage the execution of transactions involving data documents (34) based on operations (42) defined for the application (12) during its development. The framework (30) provides a generic XML-based transaction engine, the application (12) being one of a plurality of distributed applications (12) each being an instance of the generic transaction engine. An electronic marketplace with a distributed transaction layer may include such a plurality of distributed applications (12), where the applications (12) interact with one another using the distributed transaction layer (14) to conduct electronic commerce within the marketplace.
Owner:JDA SOFTWARE GROUP
Method to locate logic errors and defects in digital circuits
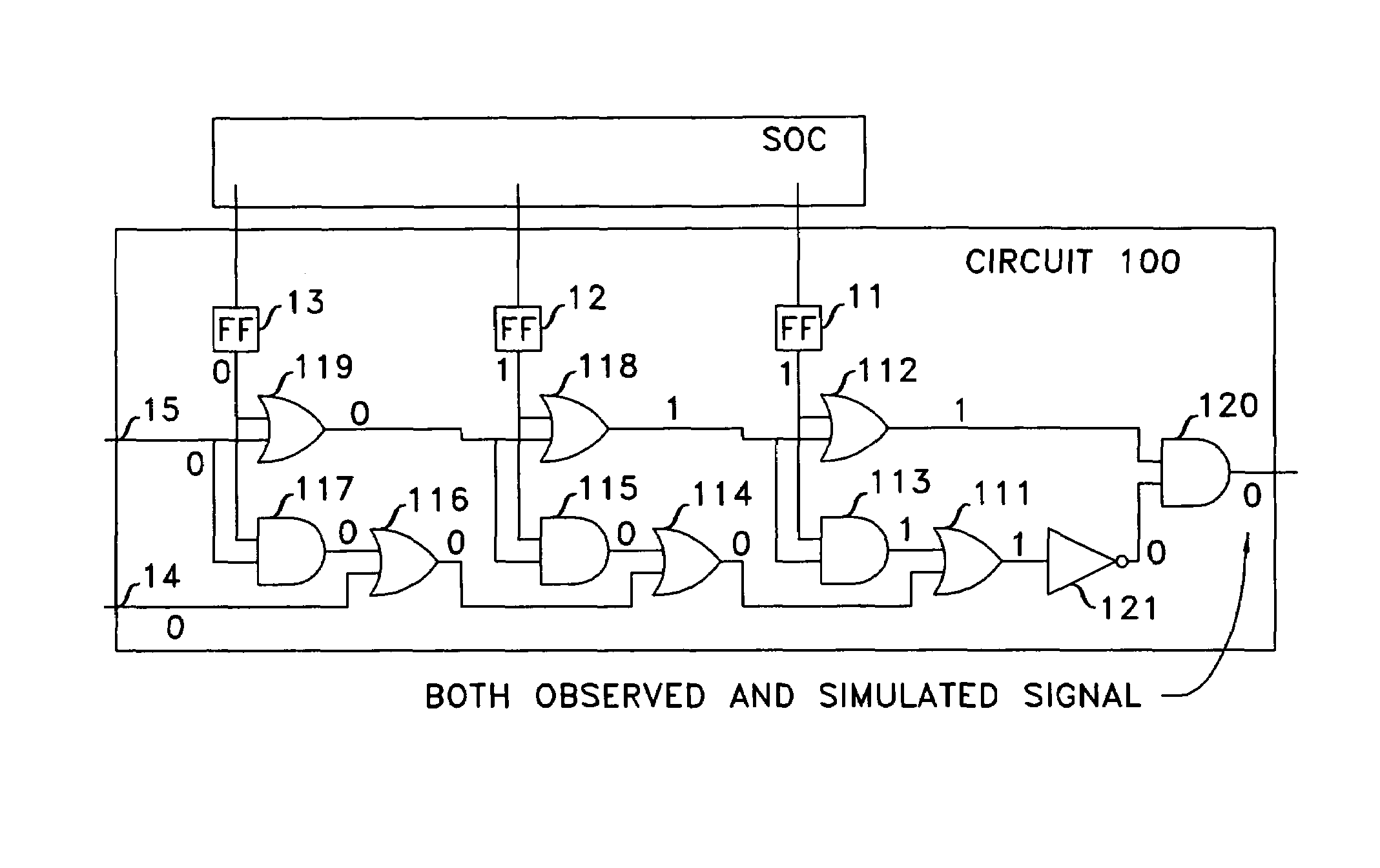
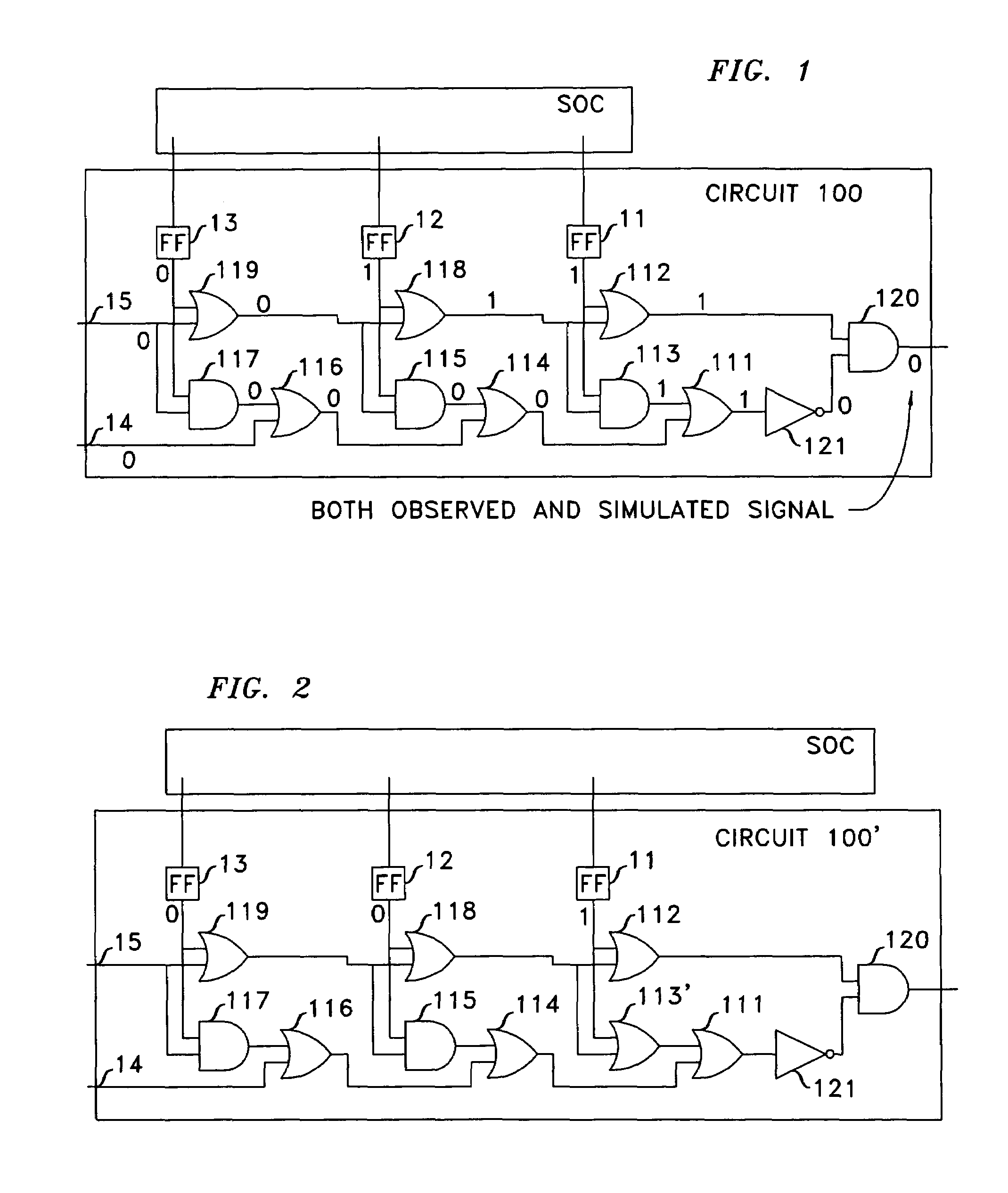
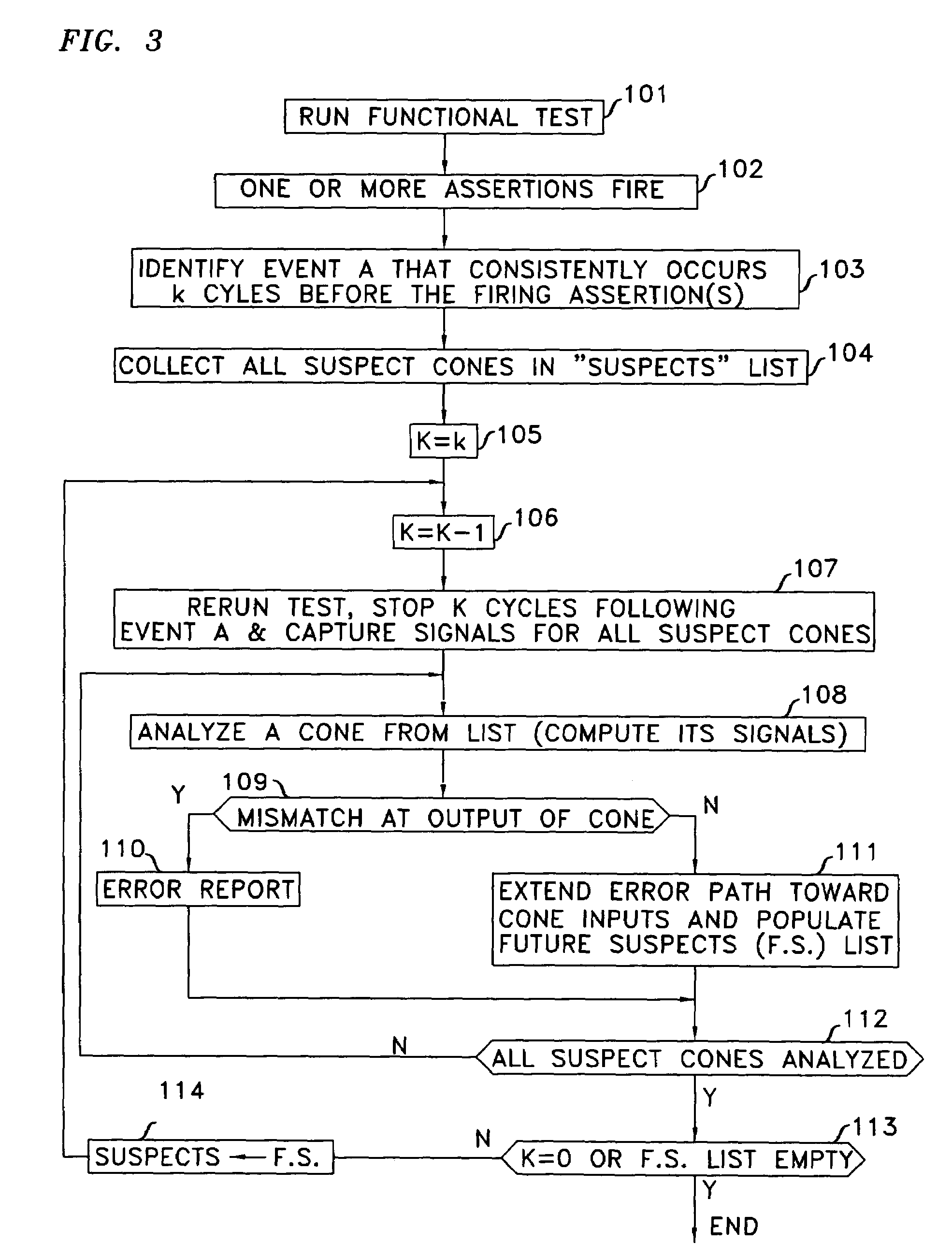
When, in the course of an integrated circuit's functional test an assertion fires at clock k, the operational clock is stopped, the sequence is reapplied to capture inputs to the assertion circuit that fired, signals within the assertion circuit are computed, and the error is backtraced. Once one or more inputs of the assertion circuit are identified as potentially the source of the error, the process of backtracing is performed for each such input. When the input that is potentially the source of the error emanates from a memory circuit, the fanin cone of the memory circuit is identified and the process of backtracing through the last-identified fanin cone is undertaken for clock k−1. This is repeated iteratively until either a module of the integrated circuit is found to be the source of the error, or the error is extended to inputs of the SoC.
Owner:DAFCA
Physical realization of dynamic logic using parameterized tile partitioning
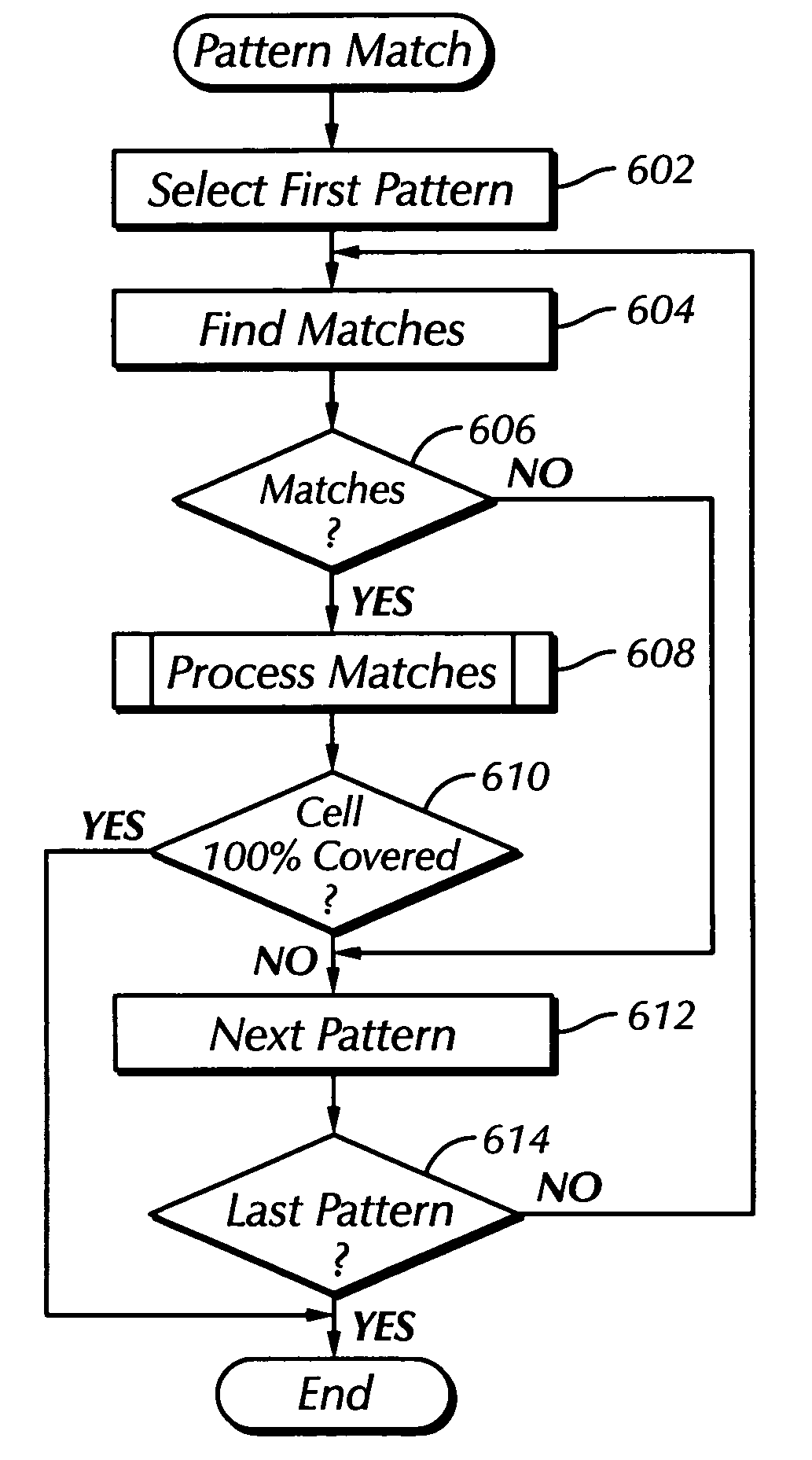
The matching algorithm of the layout synthesis method and apparatus disclosed locates transistor pattern matches in a design, links a parameterized tile to each identified match, and adjusts certain variable parameters of the linked parameterized tile to meet the physical design requirements of each located match. Each transistor pattern corresponds to a parameterized tile, which is an actual physical representation of the corresponding pattern and includes variable parameters, which may include transistor size. The matching algorithm locates matches in the design for an ordered list of patterns, names each located match, links the proper parameterized tile to each named match, and adjusts the tile's variable parameters as required. Transistors in the design are included in one and only one named located match.
Owner:APPLE INC
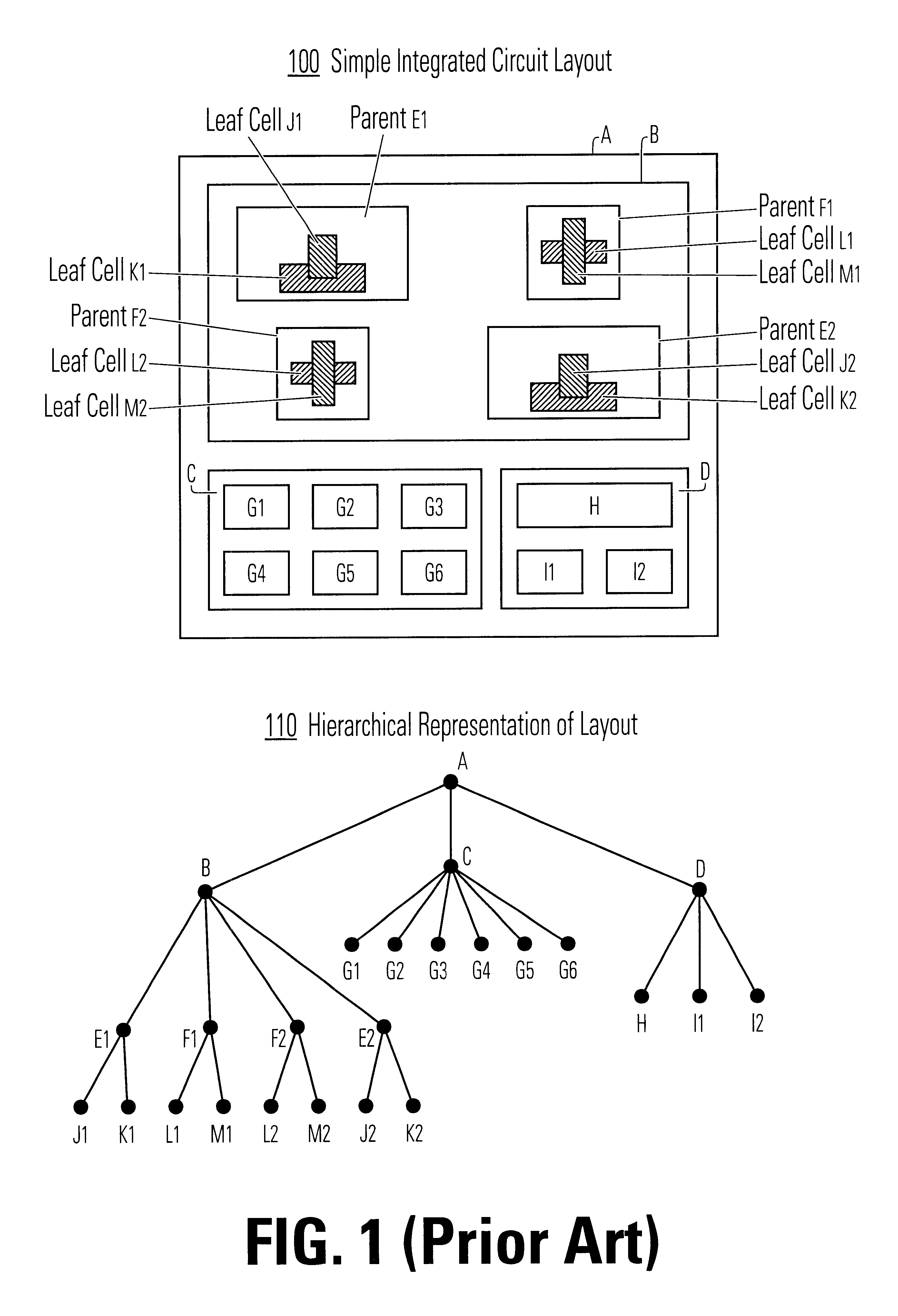
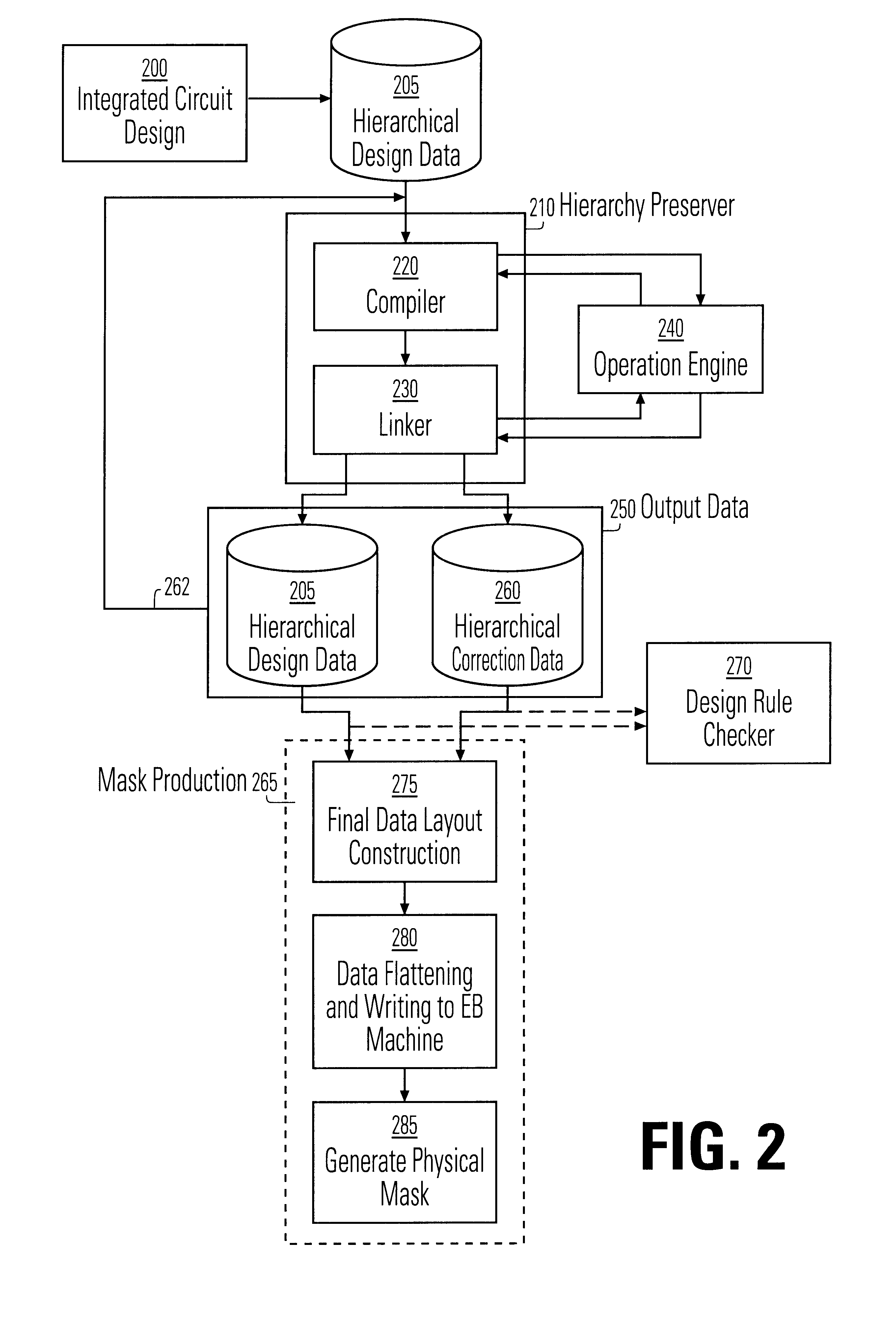
Method and apparatus for data hierarchy maintenance in a system for mask description
InactiveUS6453452B1Data augmentationReduce processing speedCAD circuit designProgram controlComputer architectureLogical operations
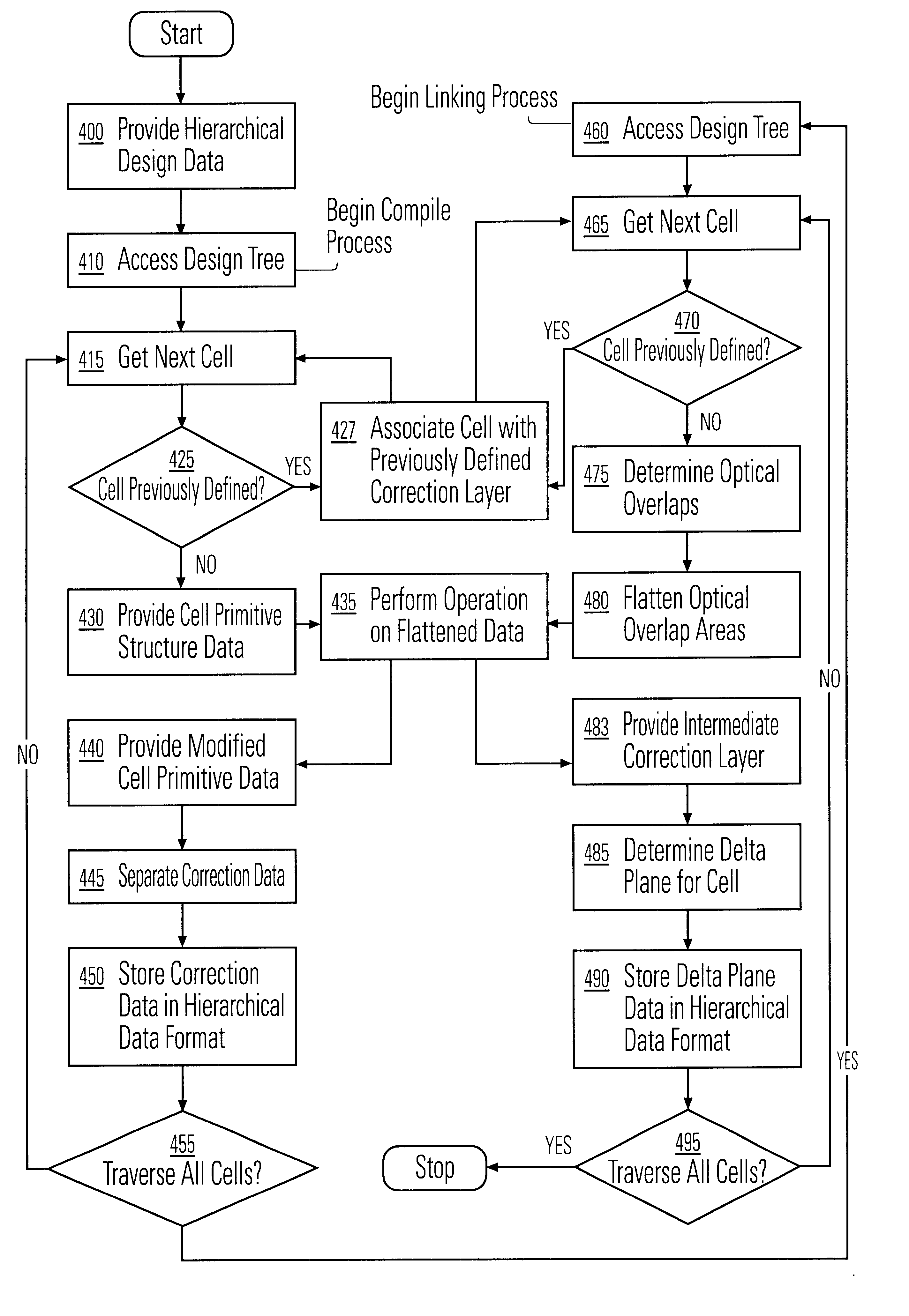
A method and apparatus for performing an operation on hierarchically described integrated circuit layouts such that the original hierarchy of the layout is maintained is provided. The method comprises providing a hierarchically described layout as a first input and providing a particular set of operating criteria corresponding to the operation to be performed as a second input. The mask operation, which may include operations such as OPC and logical operations such as NOT and OR, is then performed on the layout in accordance with the particular set of operating criteria. A first program data comprising hierarchically configured correction data corresponding to the hierarchically described layout is then generated in response to the layout operation such that if the first program data were applied to the flattened layout an output comprising data representative of the result of performing the operation on the layout would be generated. As the first program data is maintained in a true hierarchical format, layouts which are operated upon in accordance with this method are able to be processed through conventional design rule checkers. Further, this method is capable of being applied to all types of layouts including light and dark field designs and phase shifting layouts.
Owner:SYNOPSYS INC
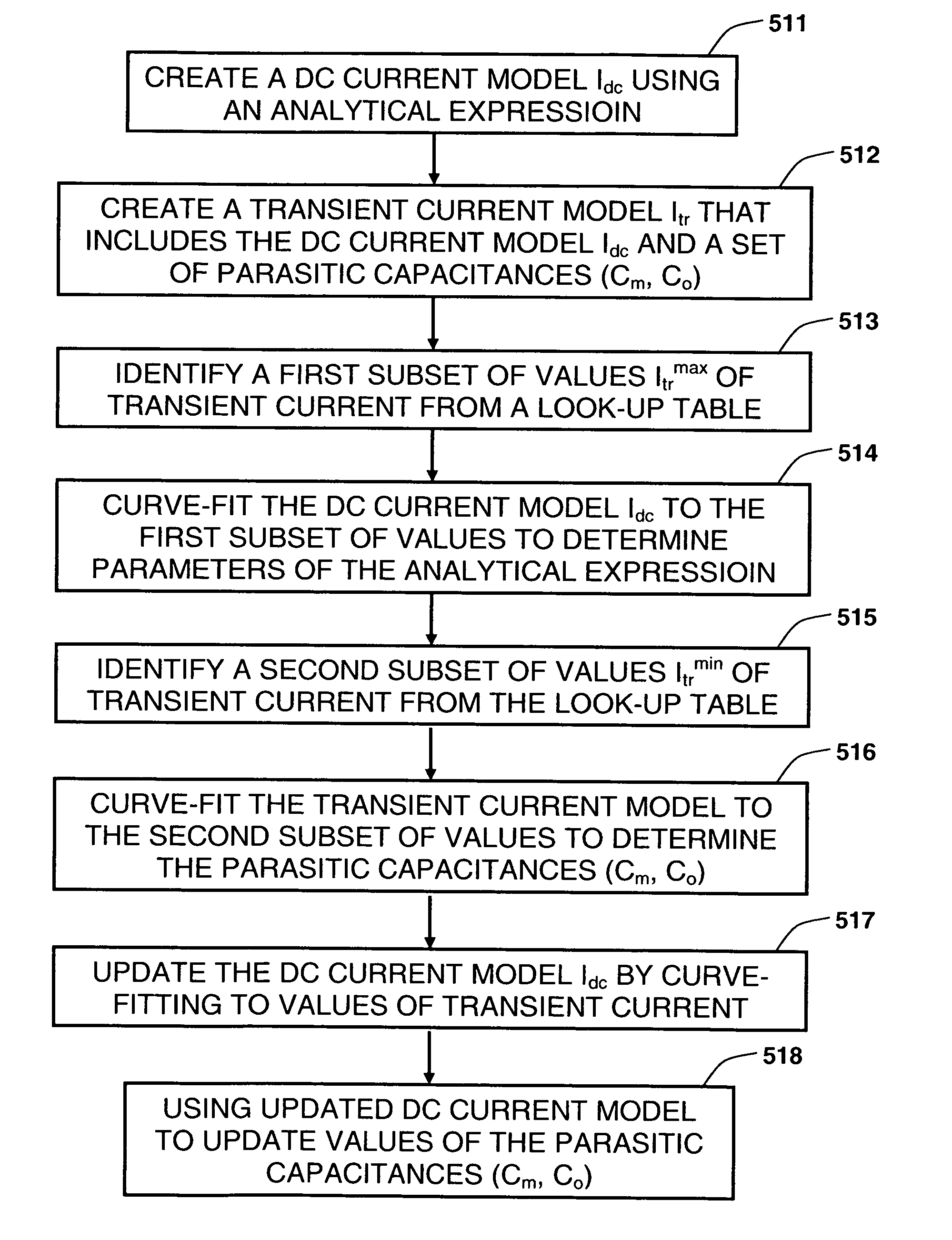
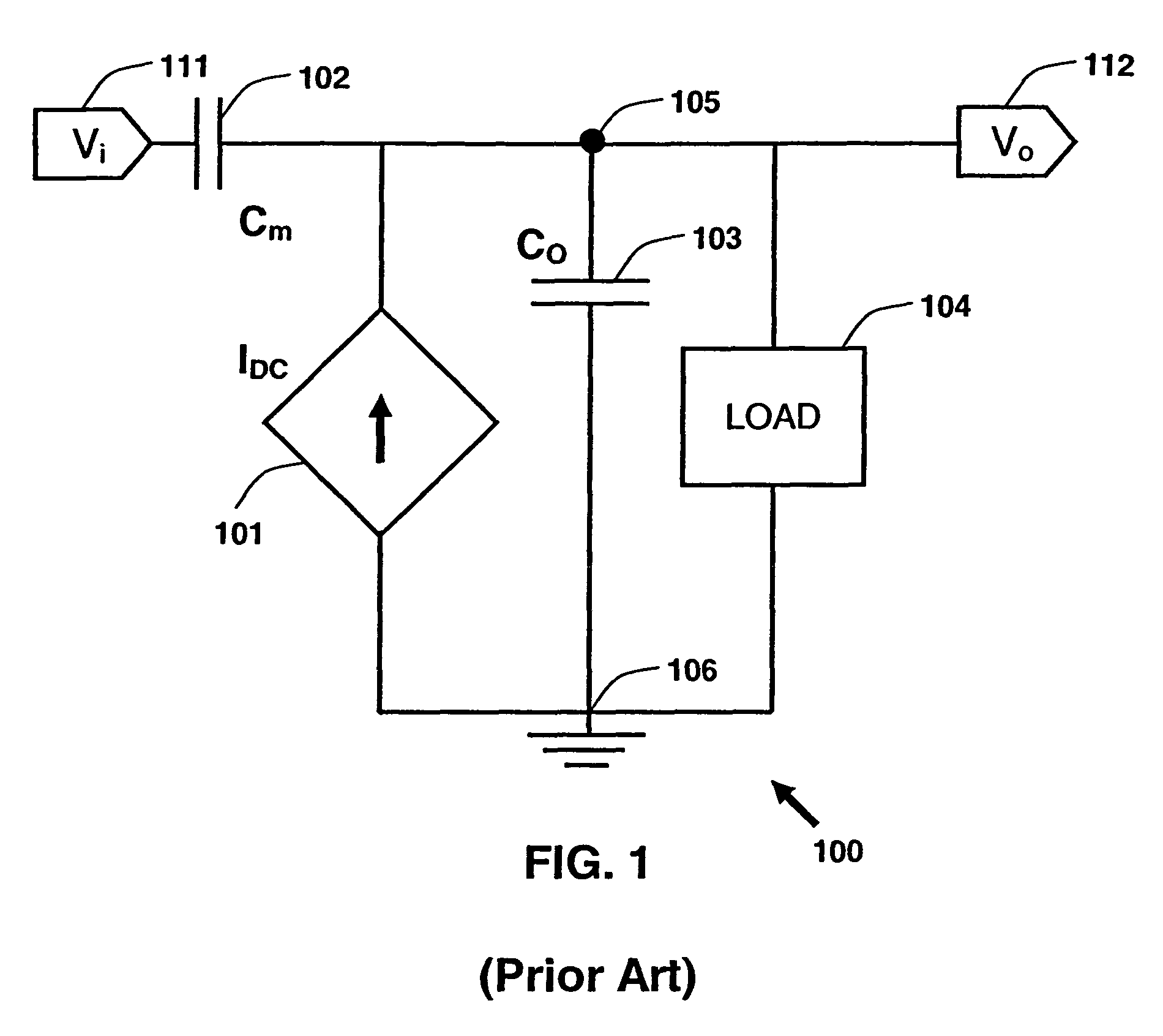
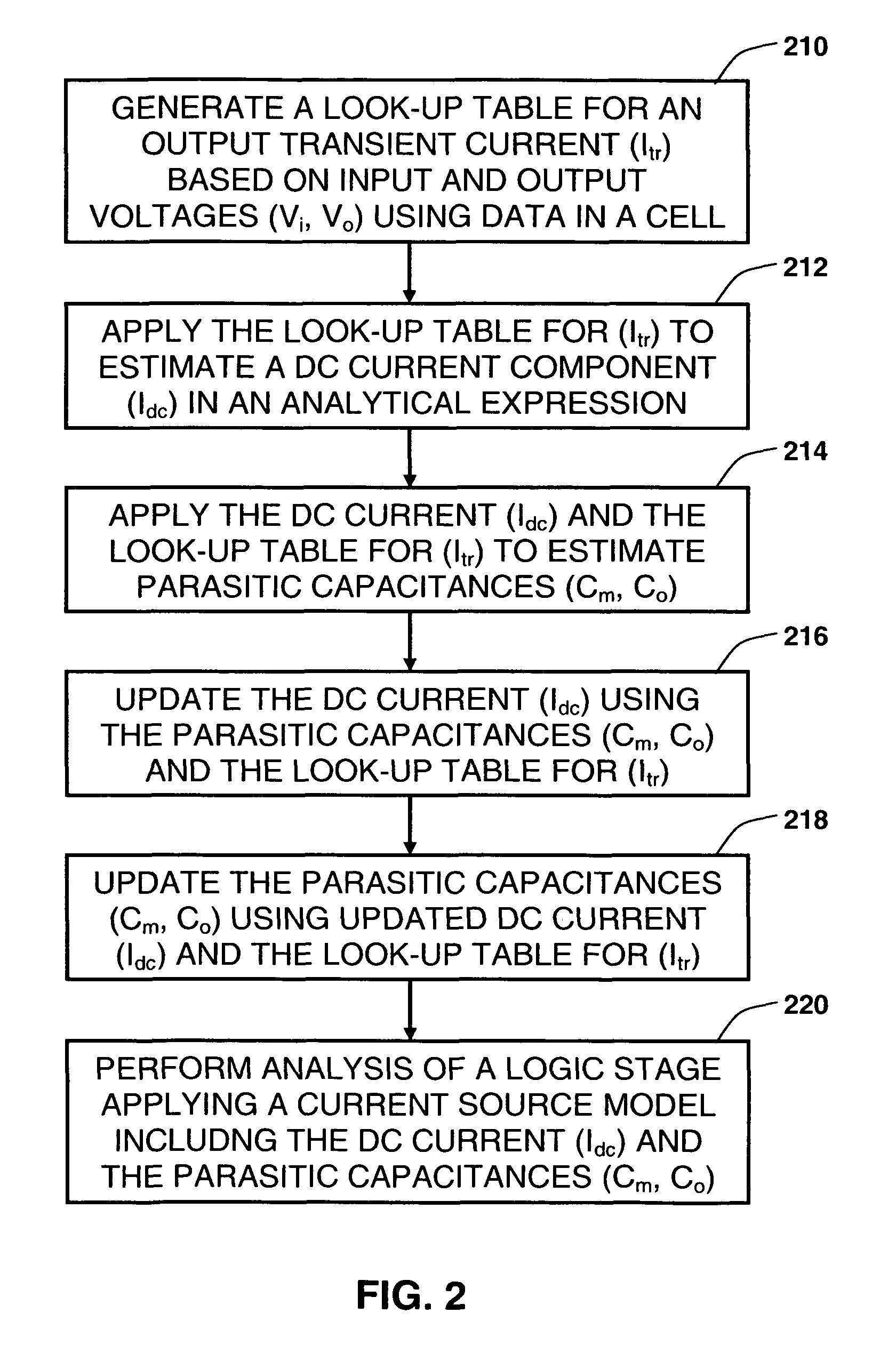
Synthesizing current source driver model for analysis of cell characteristics
InactiveUS7761275B2Analogue computers for electric apparatusCAD circuit designParasitic capacitanceEngineering
A method for performing an analysis of at least one logic stage in a netlist, which include one or more drivers, is provided. The method includes operations of generating at least one look-up table for an output transient current to be based on values of input and output voltages using data available from a cell library; synthesizing analytically at least one current source model, which includes a DC component and a plurality of parasitic capacitances, using the look-up table; simulating the logic stage using the current source model to model the drivers; and obtaining characteristics of the simulated logic stage. A system and a machine-readable medium for performing the method are also provided.
Owner:INT BUSINESS MASCH CORP
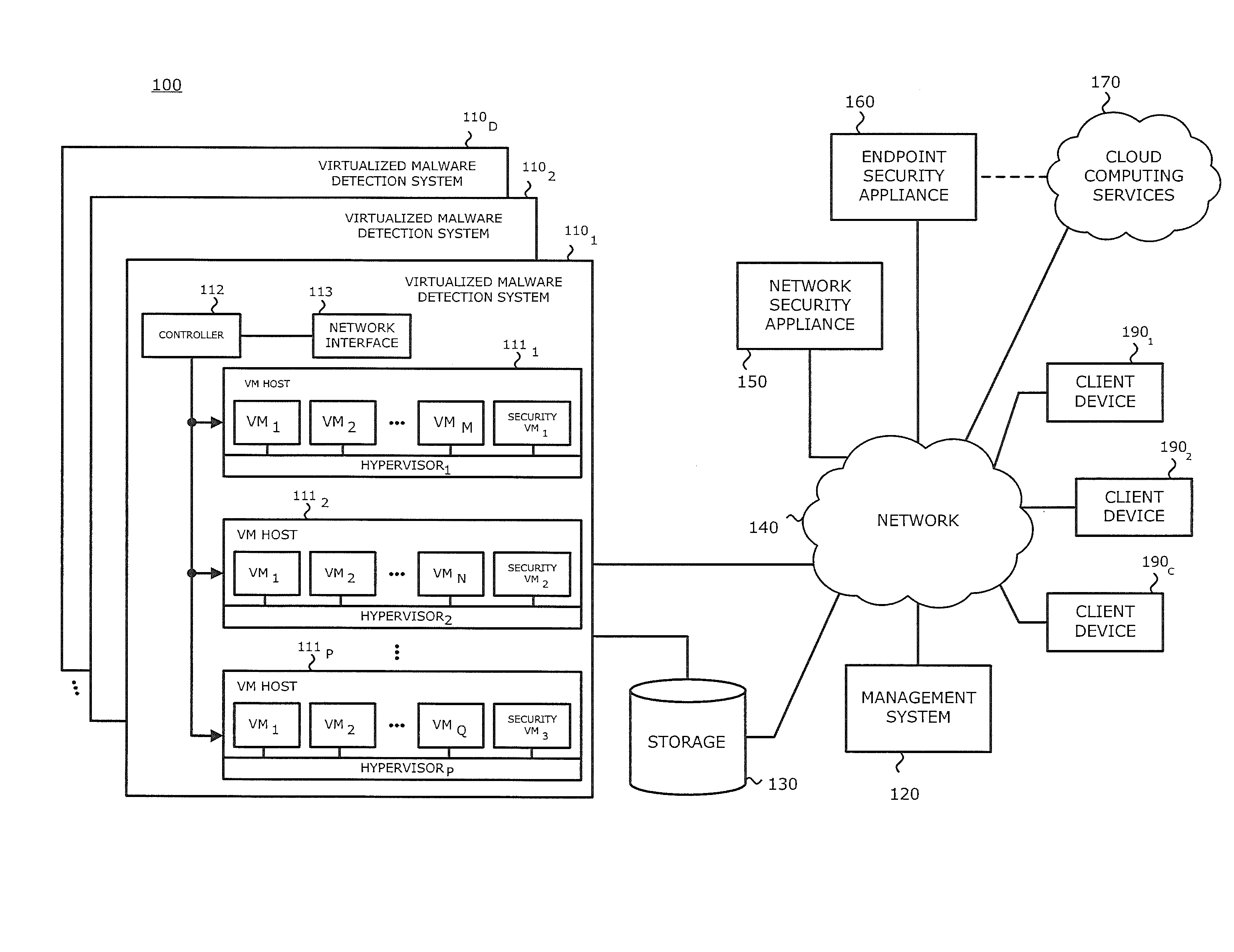
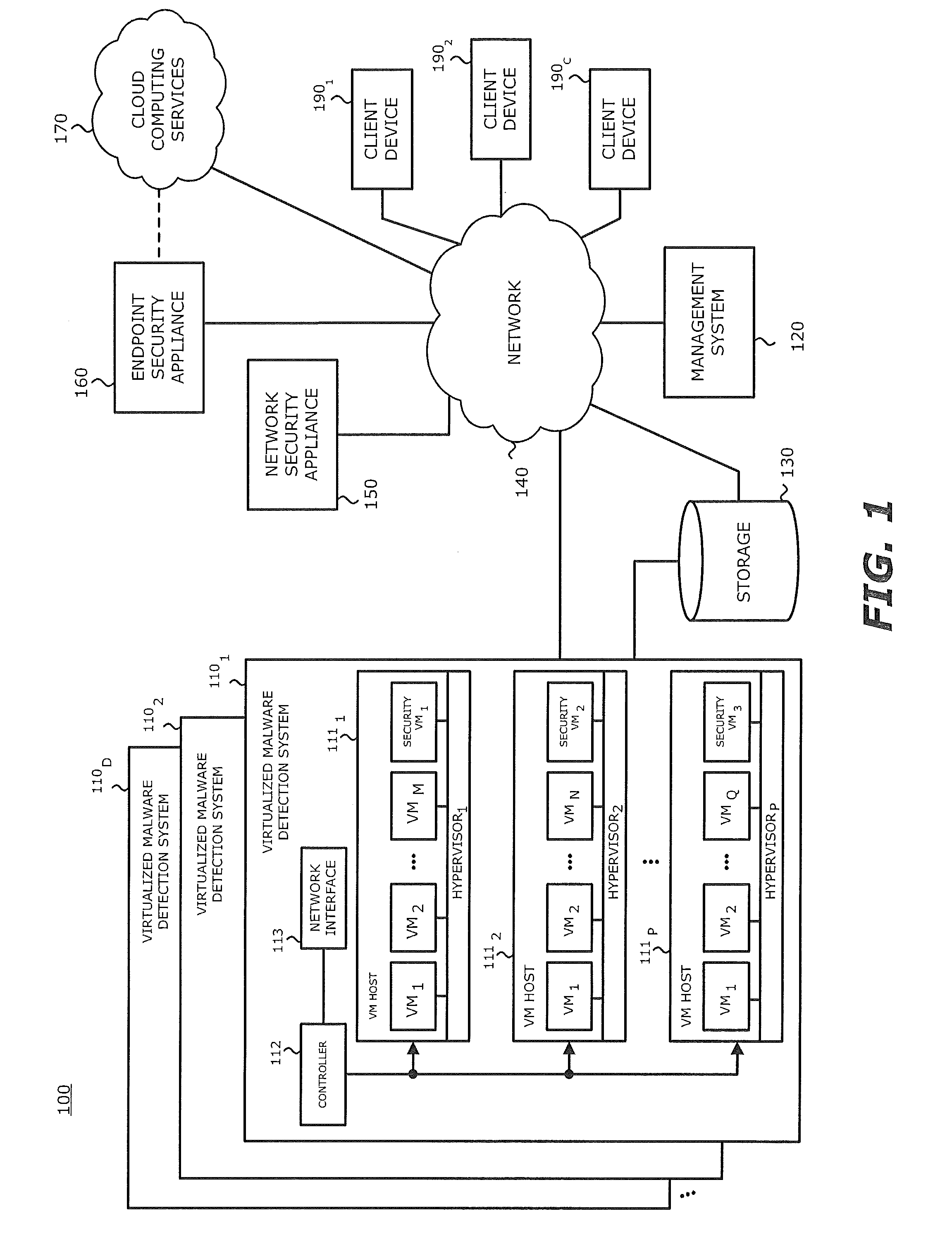
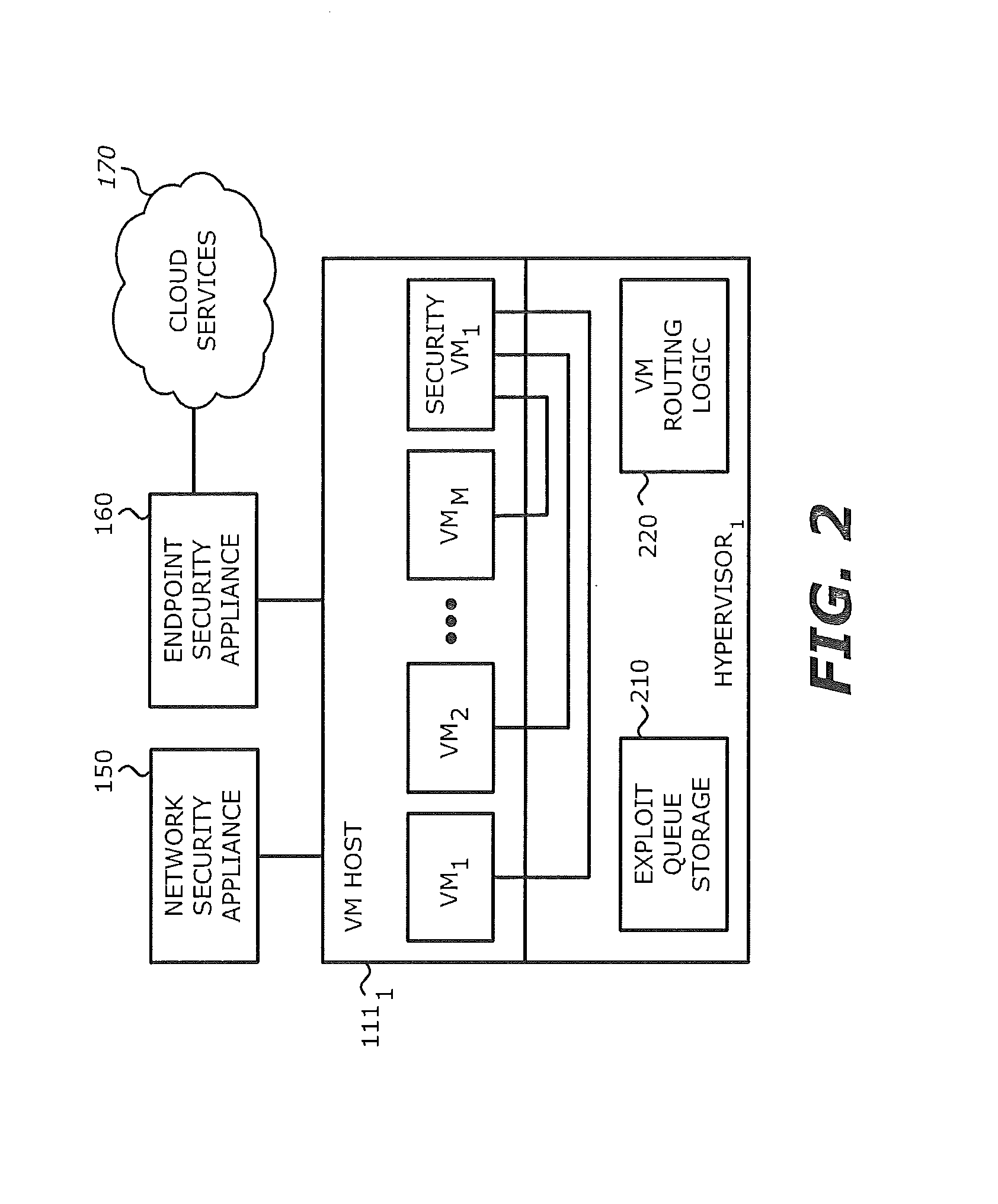
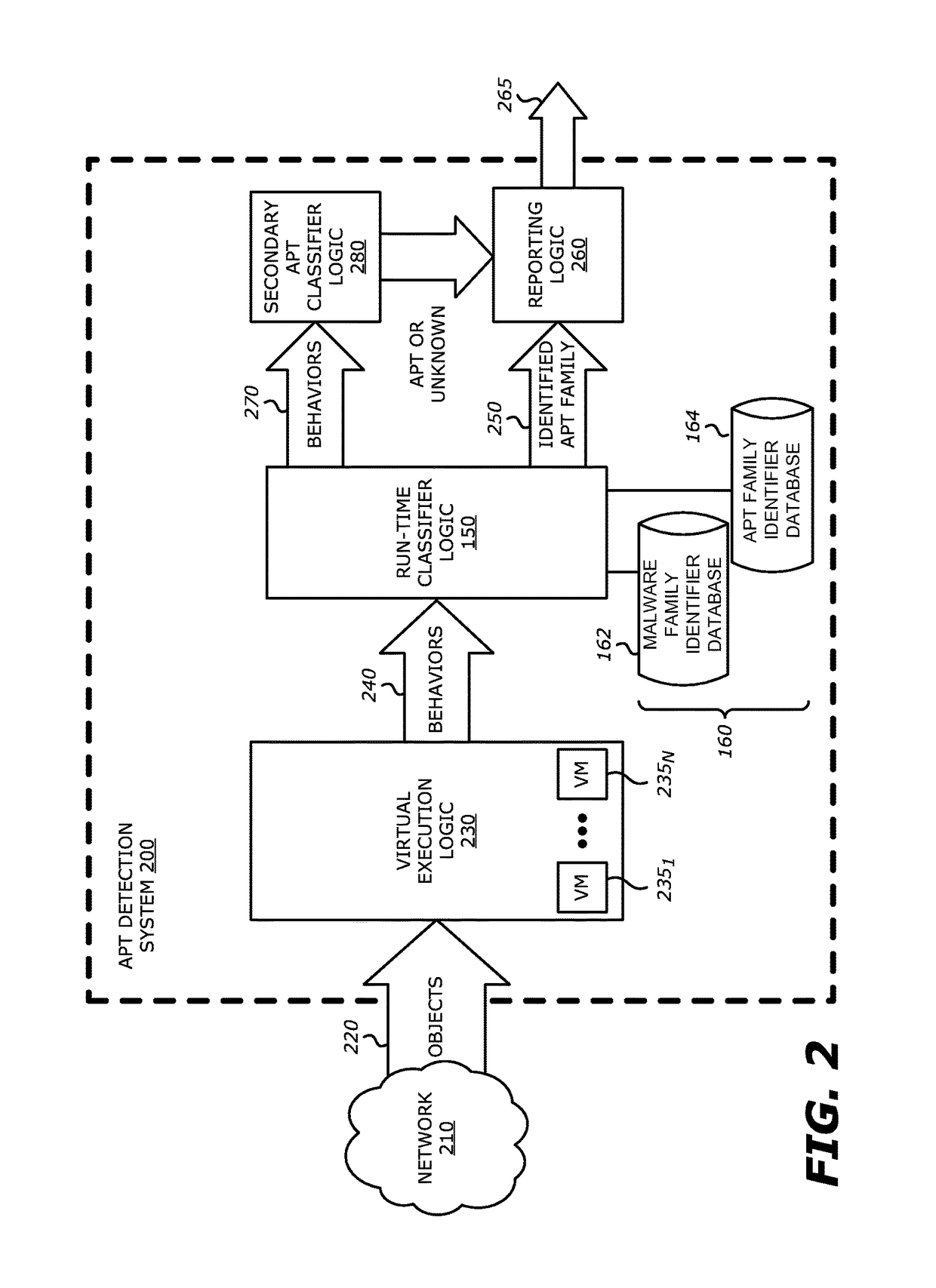
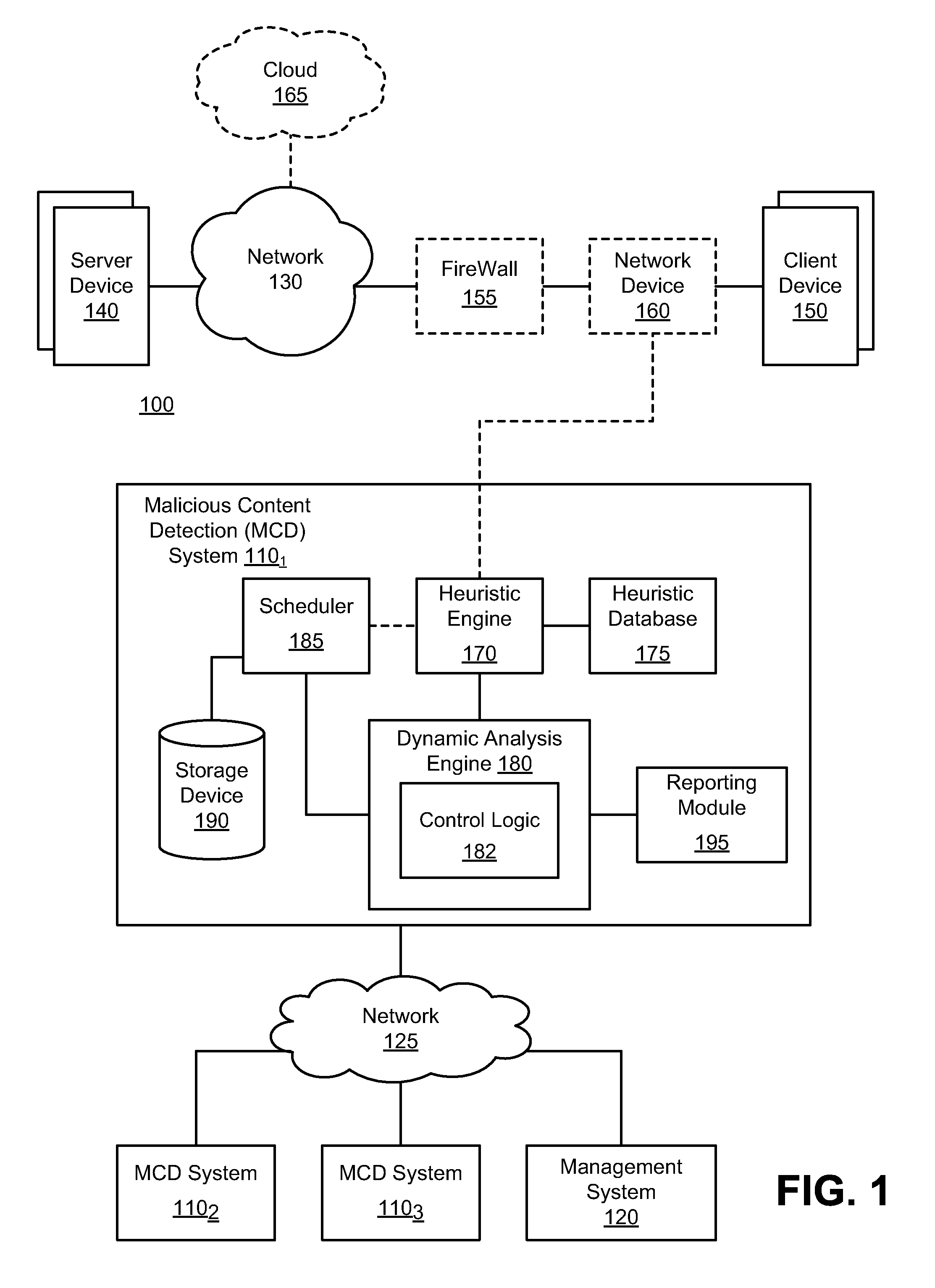
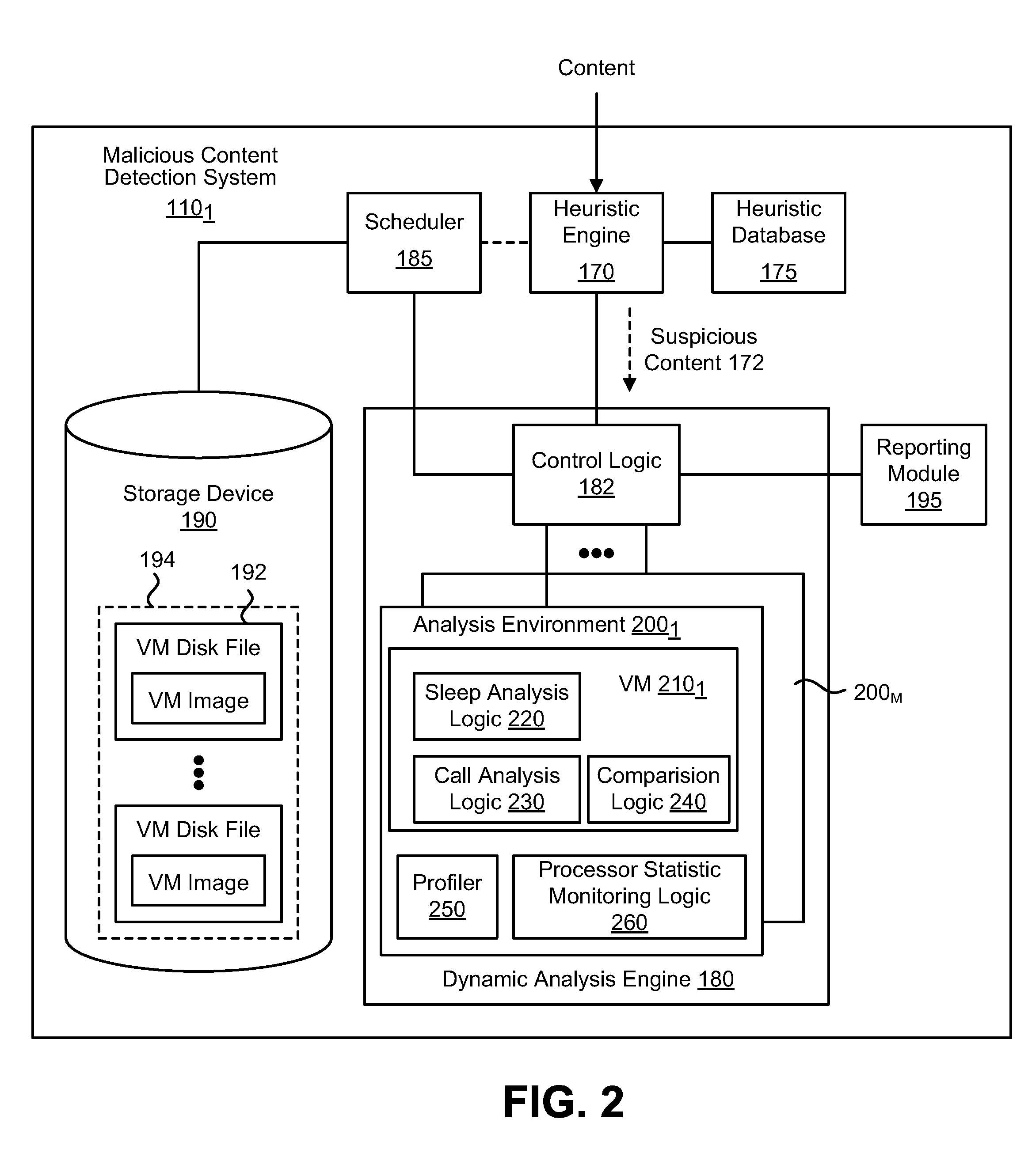
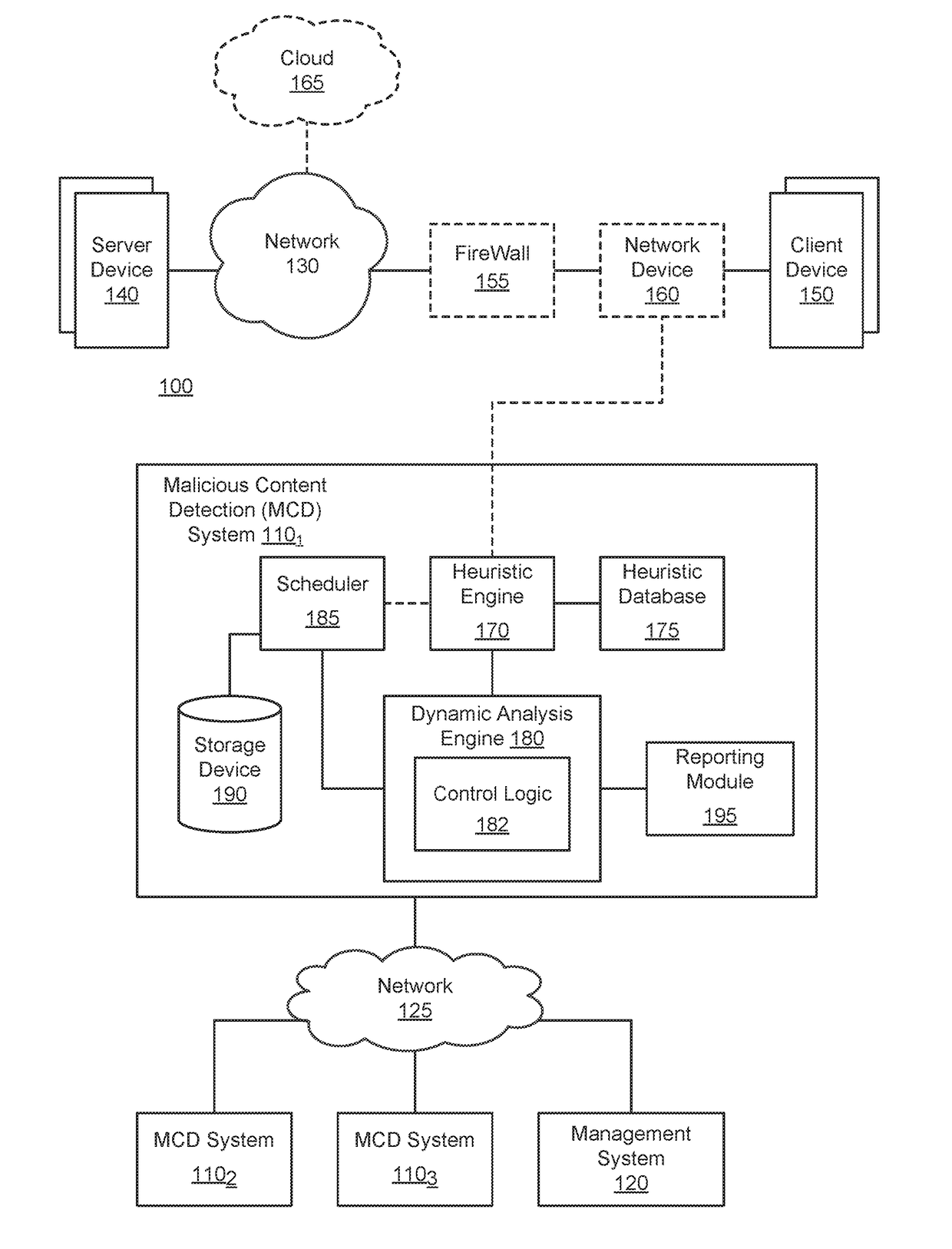
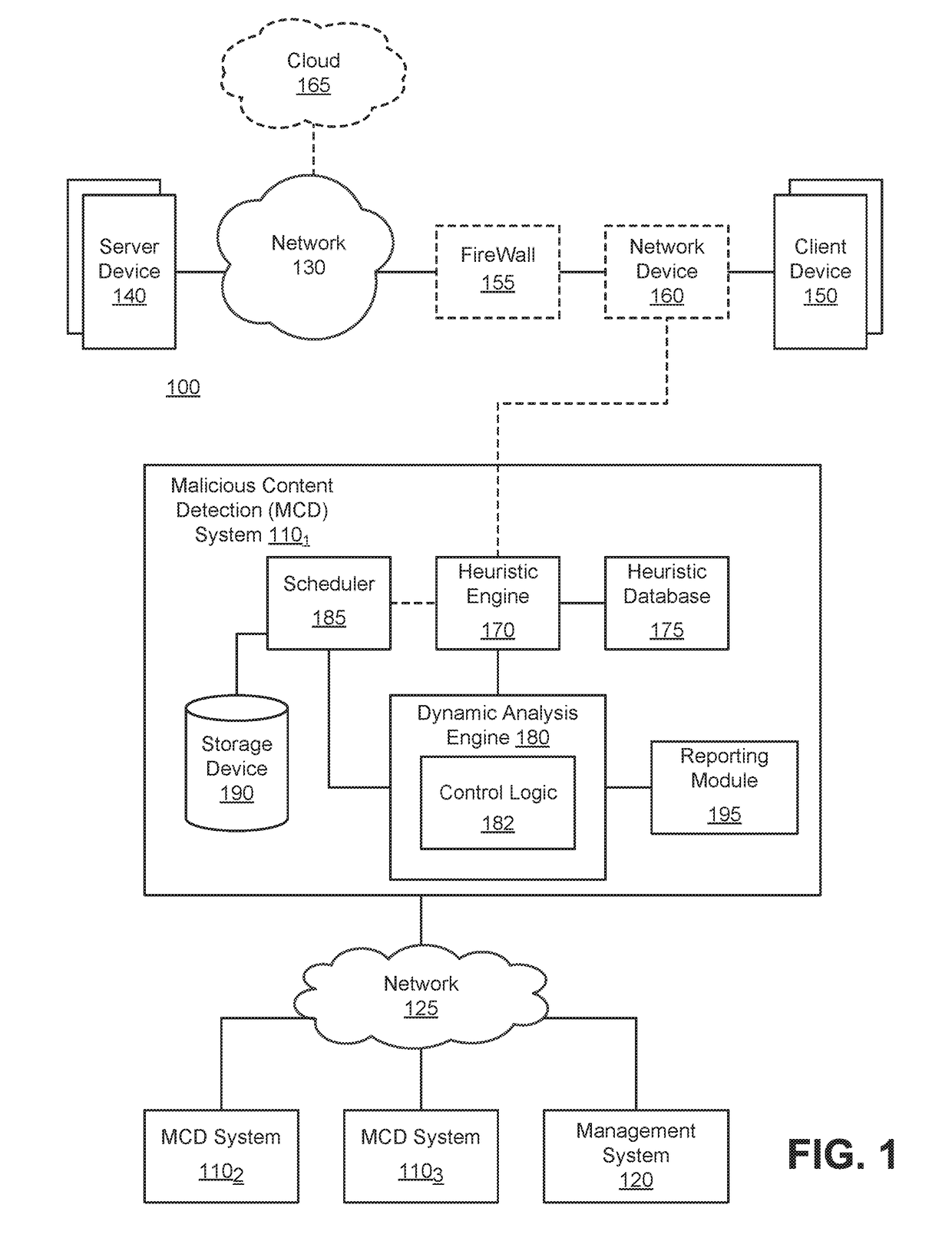
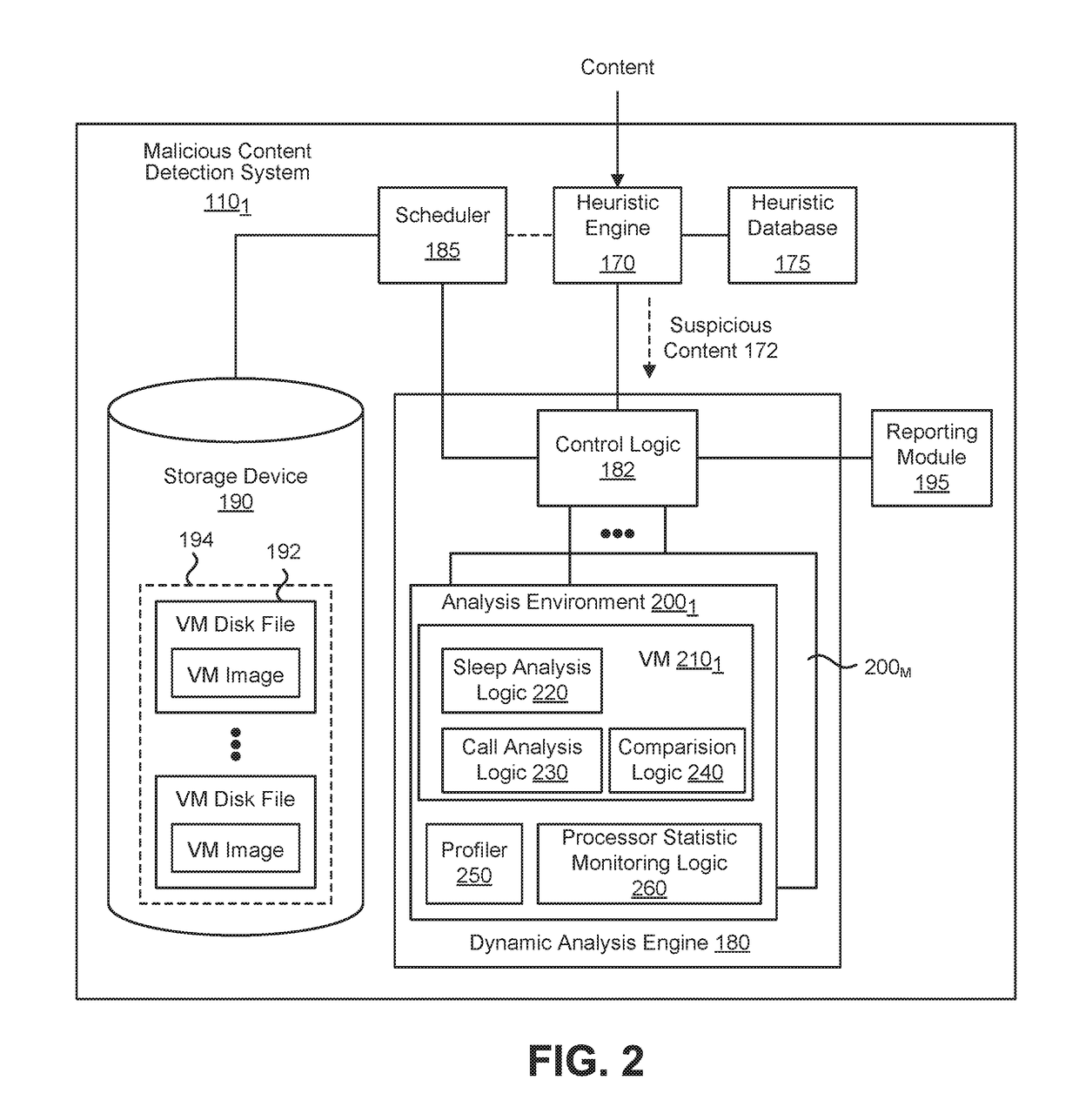
Exploit detection system
According to one embodiment, a virtualized malware detection system is integrated with a virtual machine host including a plurality of virtual machines and a security virtual machine. Logic within the virtual machines are configured to perform a dynamic analysis of an object and monitor for the occurrence of a triggering event. Upon detection of a triggering event within a virtual machine, the logic within the virtual machine provides the security virtual machine with information associated with the triggering event for further analysis. Based on the further analysis, the object may then be classified as “non-malicious,” or “malicious.”
Owner:FIREEYE SECURITY HLDG US LLC
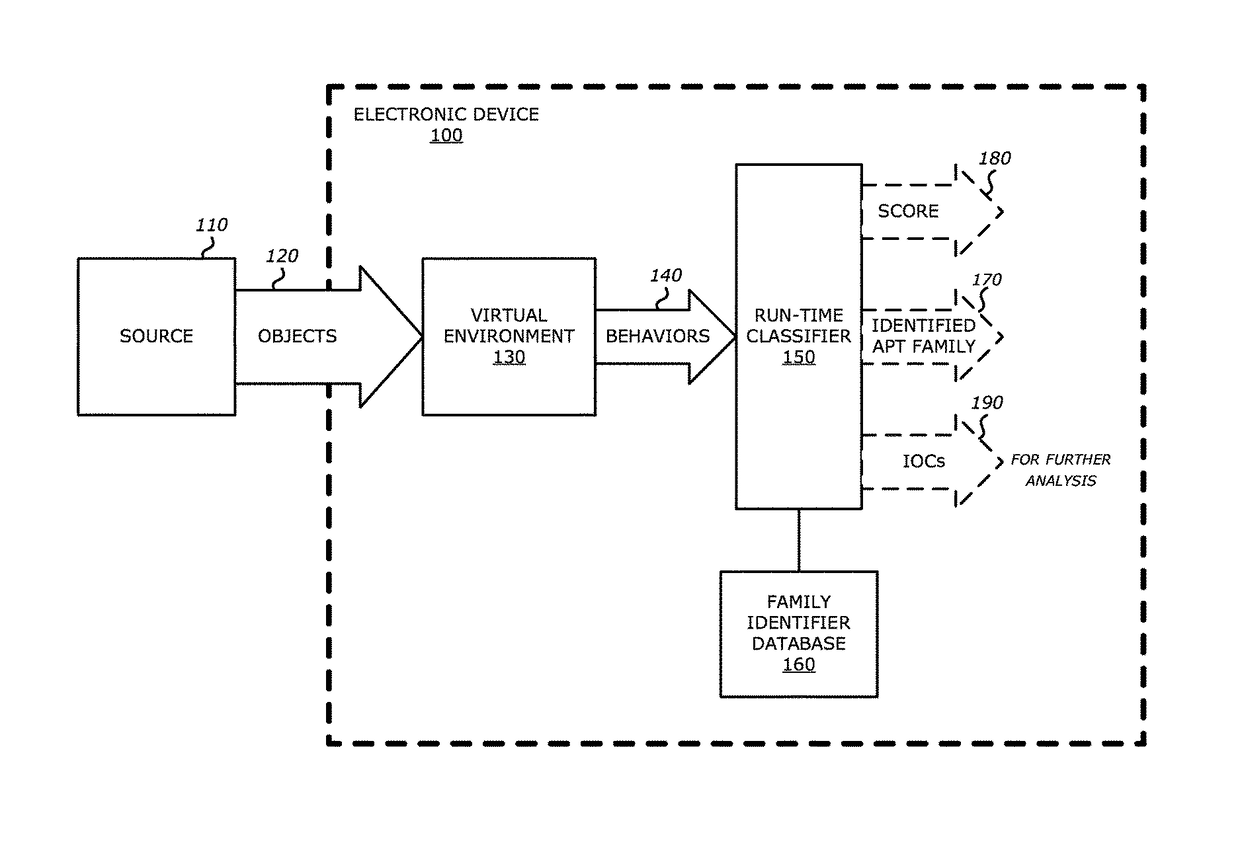
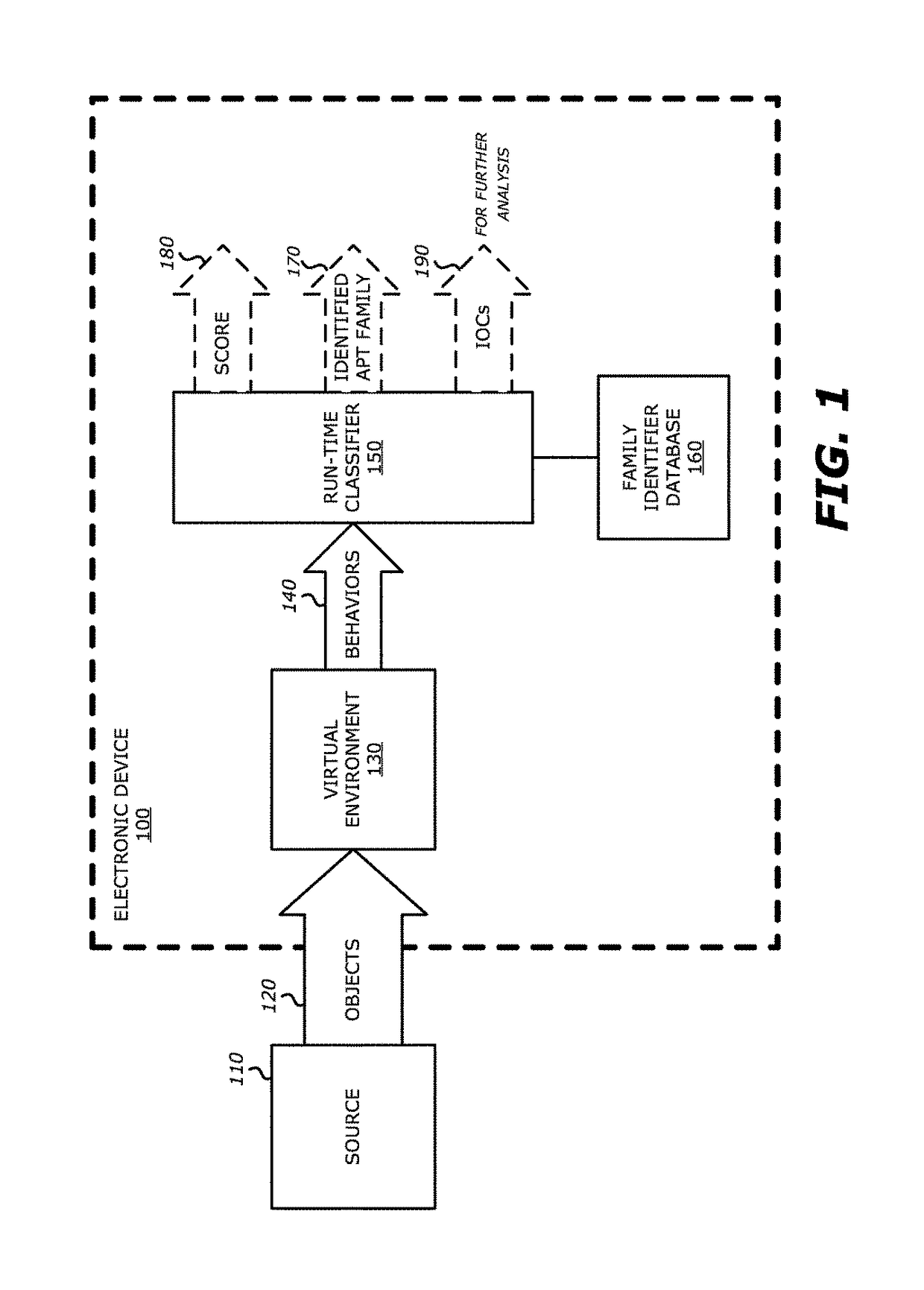
System and method for run-time object classification
One embodiment of an electronic device comprises a processor and a memory accessible by the processor. The memory comprises virtual execution logic and run-time classifier logic. The virtual execution logic includes at least one virtual machine that is configured to virtually process content within an object under analysis and monitor for anomalous behaviors during the virtual processing that are indicative of malware. The run-time classifier logic performs, during run-time, a first analysis on the monitored anomalous behaviors and a pre-stored identifier to determine if the monitored anomalous behaviors indicate that the object is malware belonging to a classified malware family. The pre-stored identifier is a collection of data associated with anomalous behaviors that uniquely identify the malware family.
Owner:FIREEYE SECURITY HLDG US LLC +1
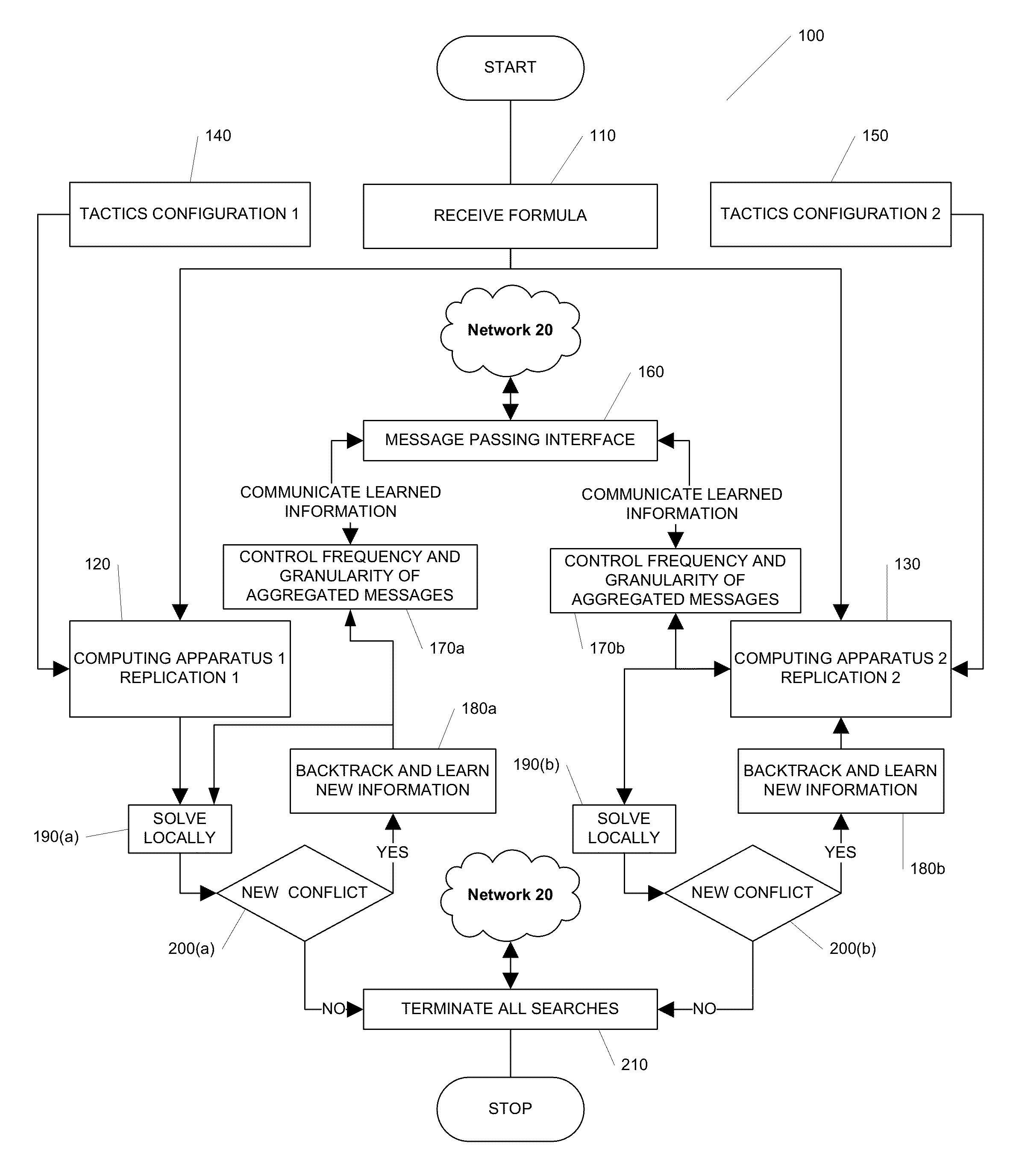
Systems, methods and apparatus for distributed decision processing
Methods, apparatus, and computer software product for making a decision based on the semantics of formal logic are provided. In an exemplary embodiment, two custom computing apparatuses are used to resolve the satisfiability of a logical formula and provide an example. In this embodiment, the two custom computing apparatuses operate in concert to explore the space of possible satisfying examples. This Abstract is provided for the sole purpose of complying with the Abstract requirement rules. This Abstract is submitted with the explicit understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:QUALCOMM TECHNOLOGIES INC
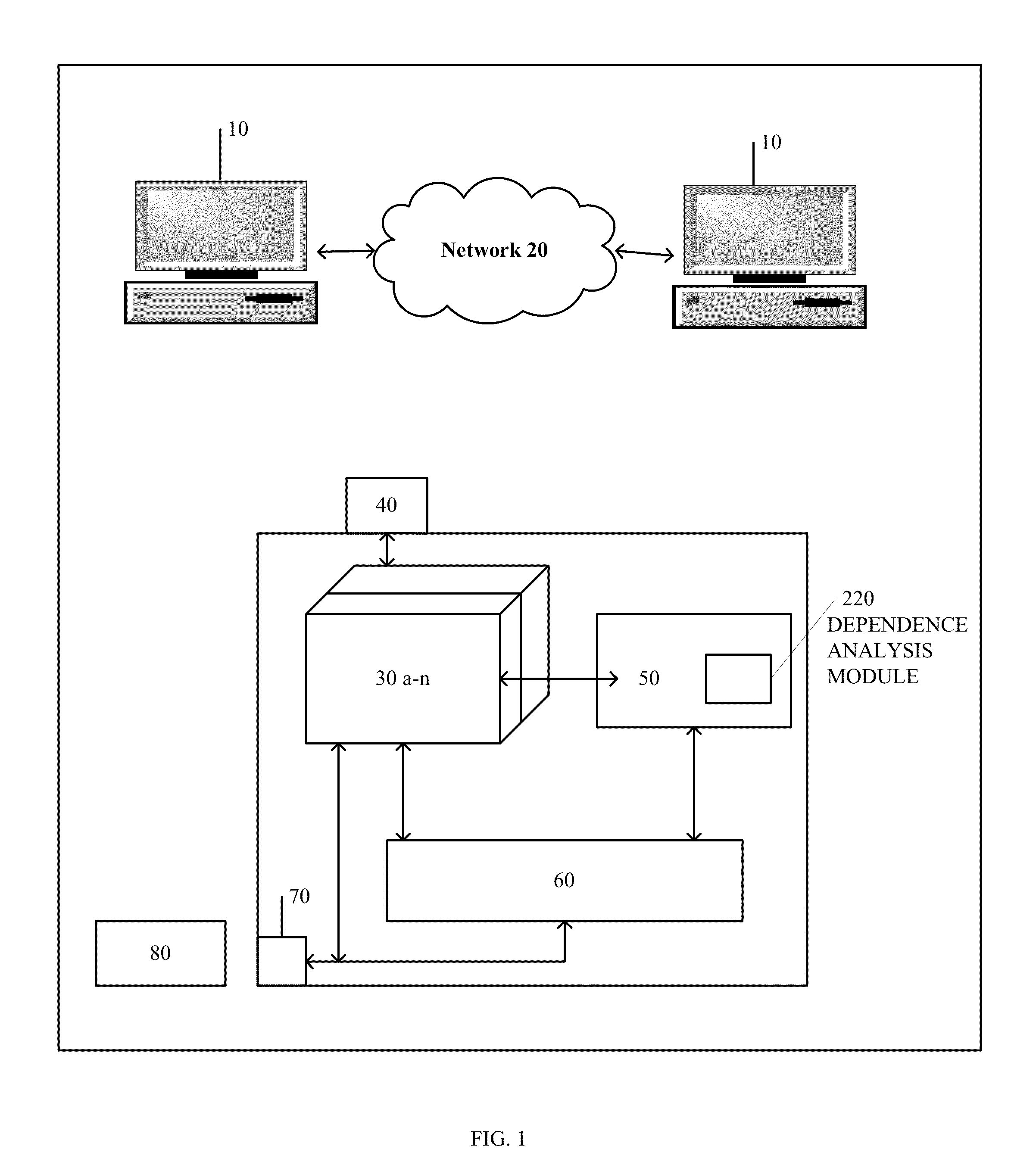
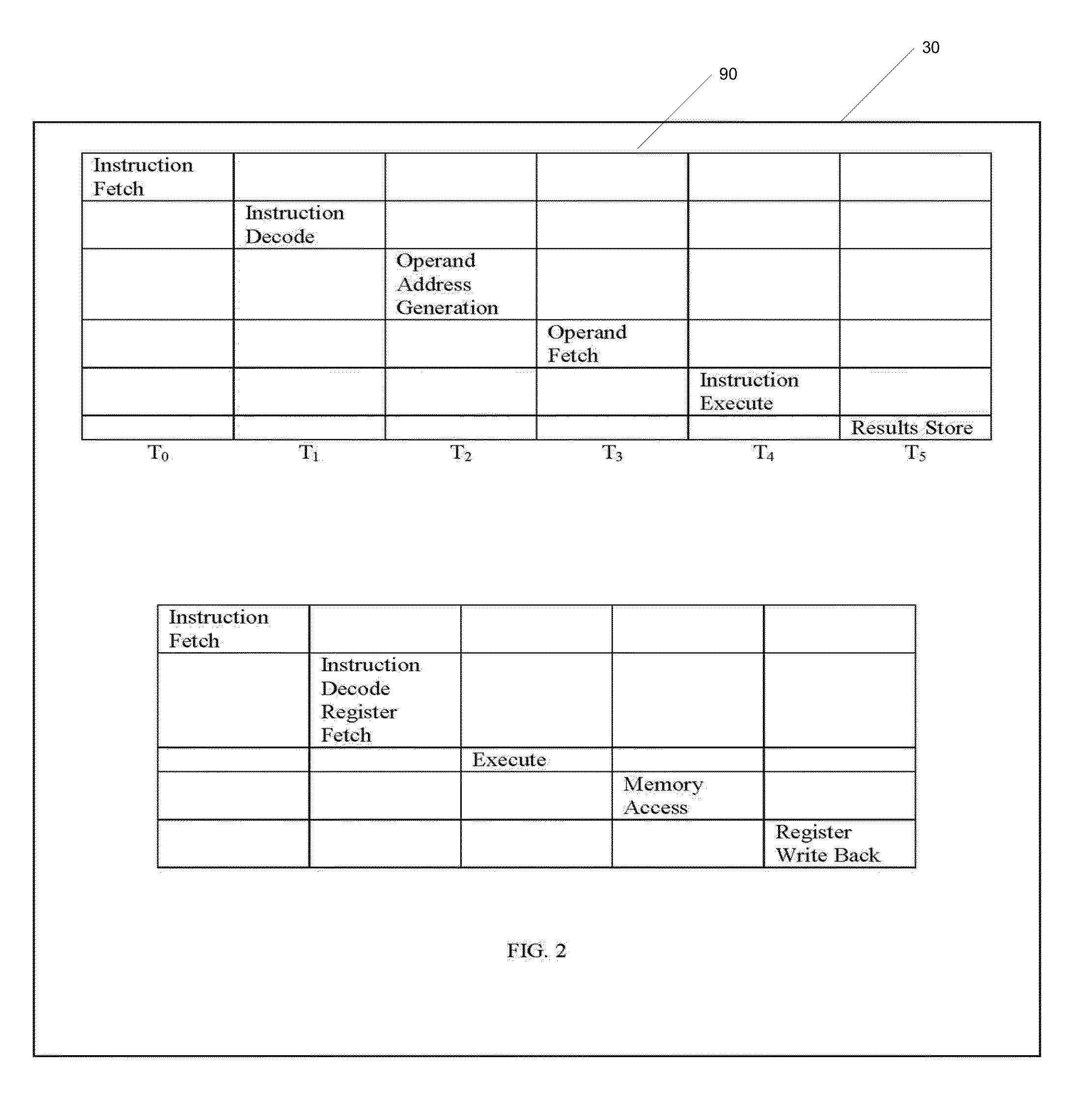
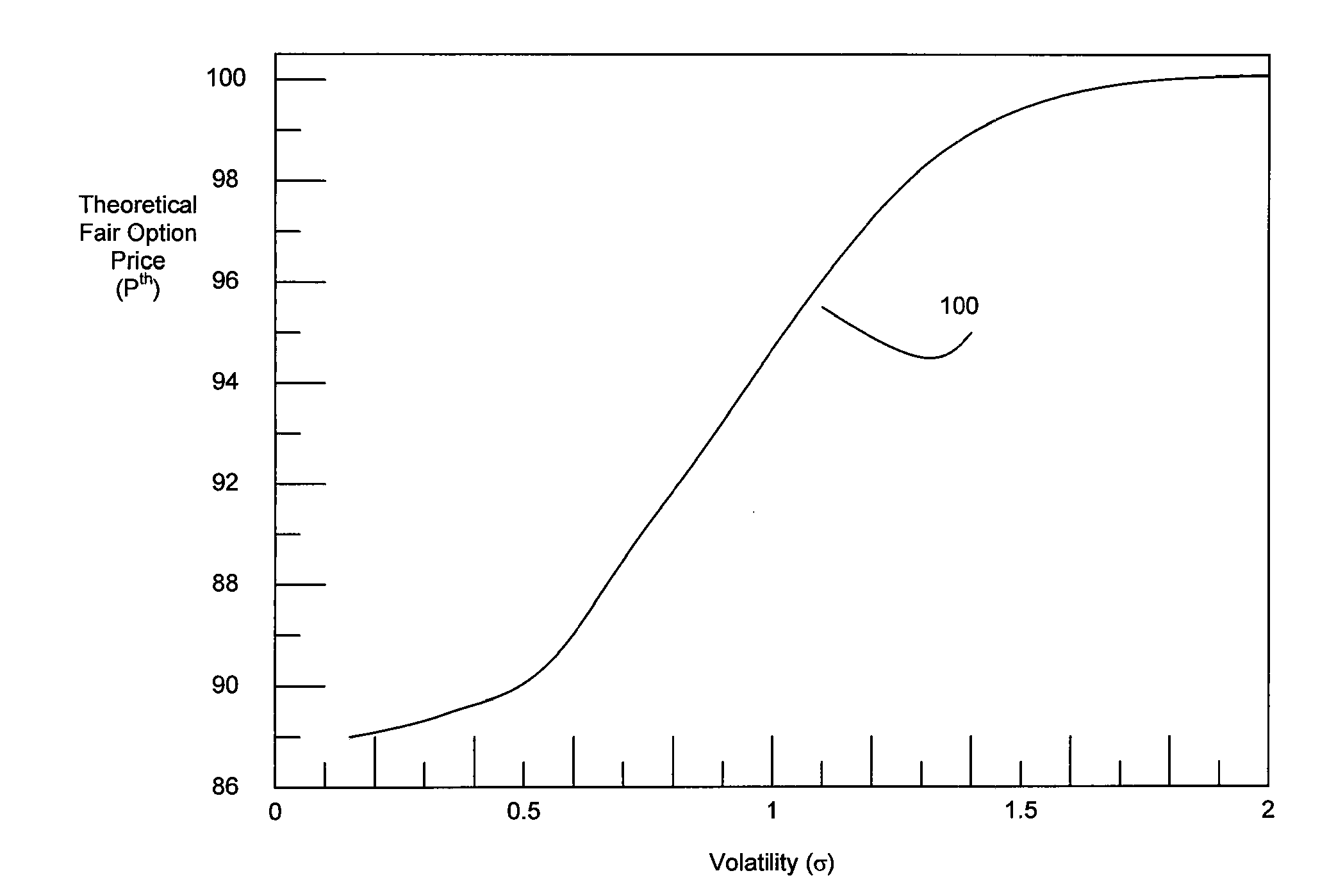
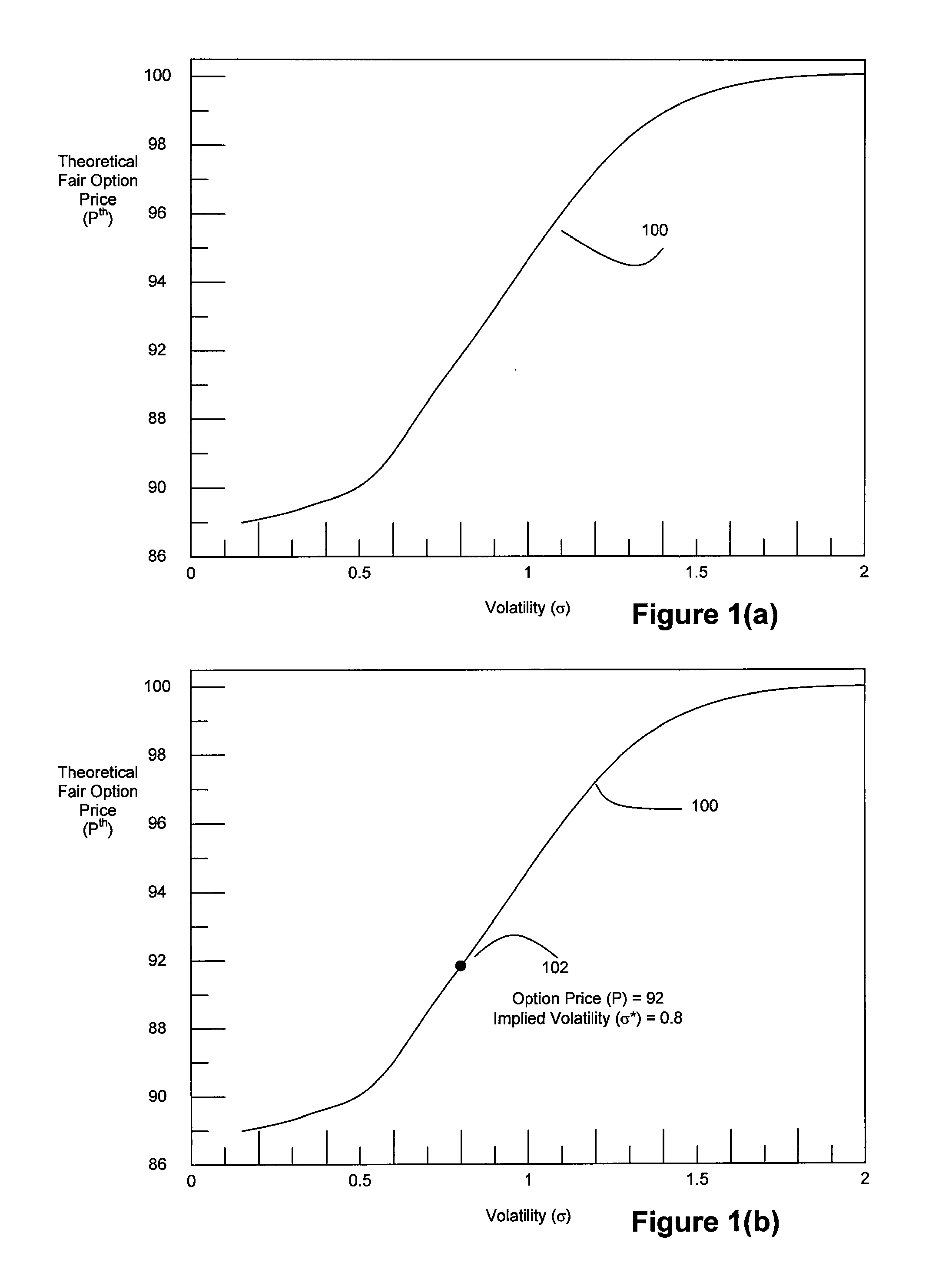
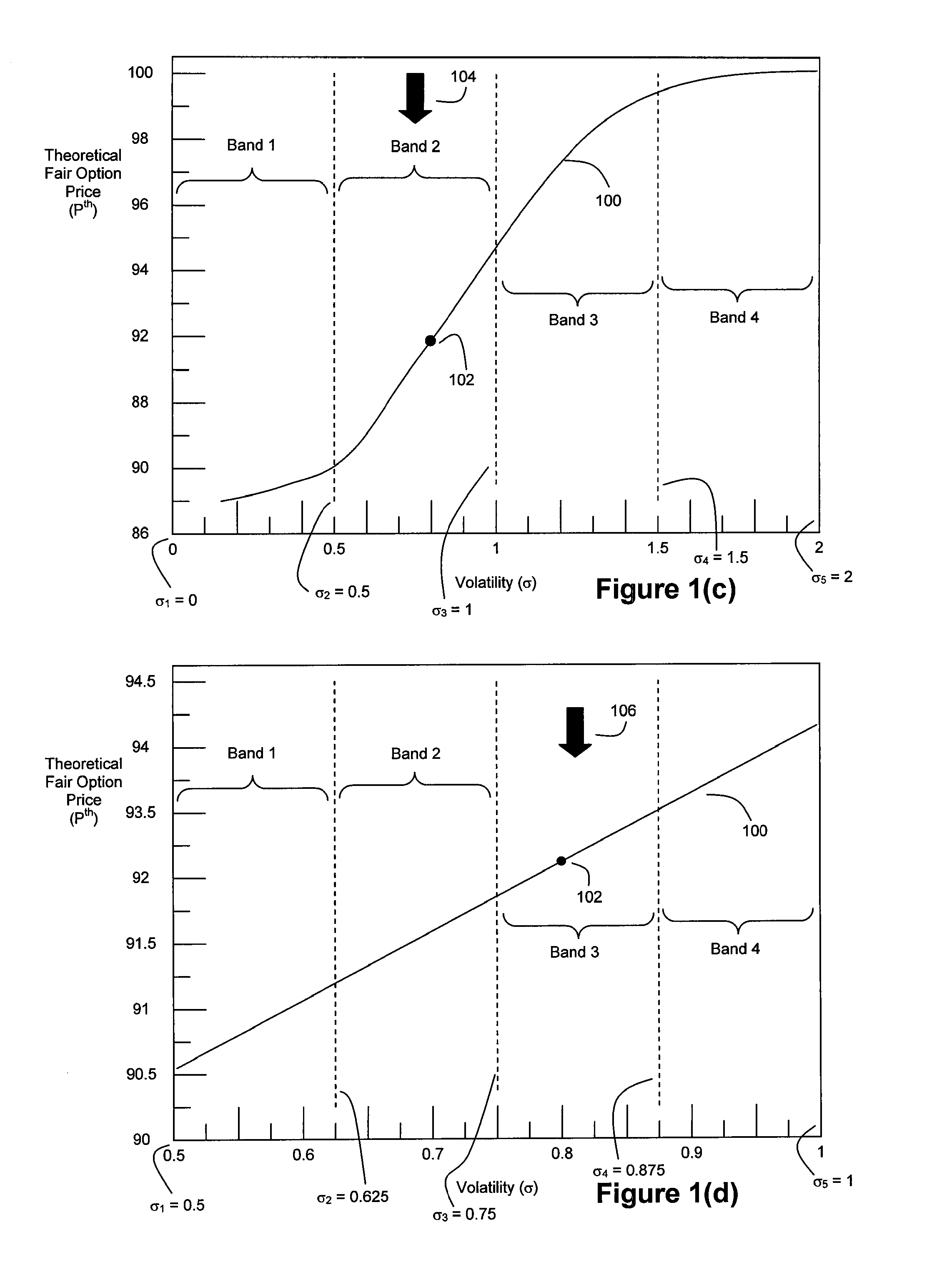
Method and System for High Speed Options Pricing
ActiveUS20070294157A1SpeedReduction of informationFinanceTheoretical computer scienceLatency (engineering)
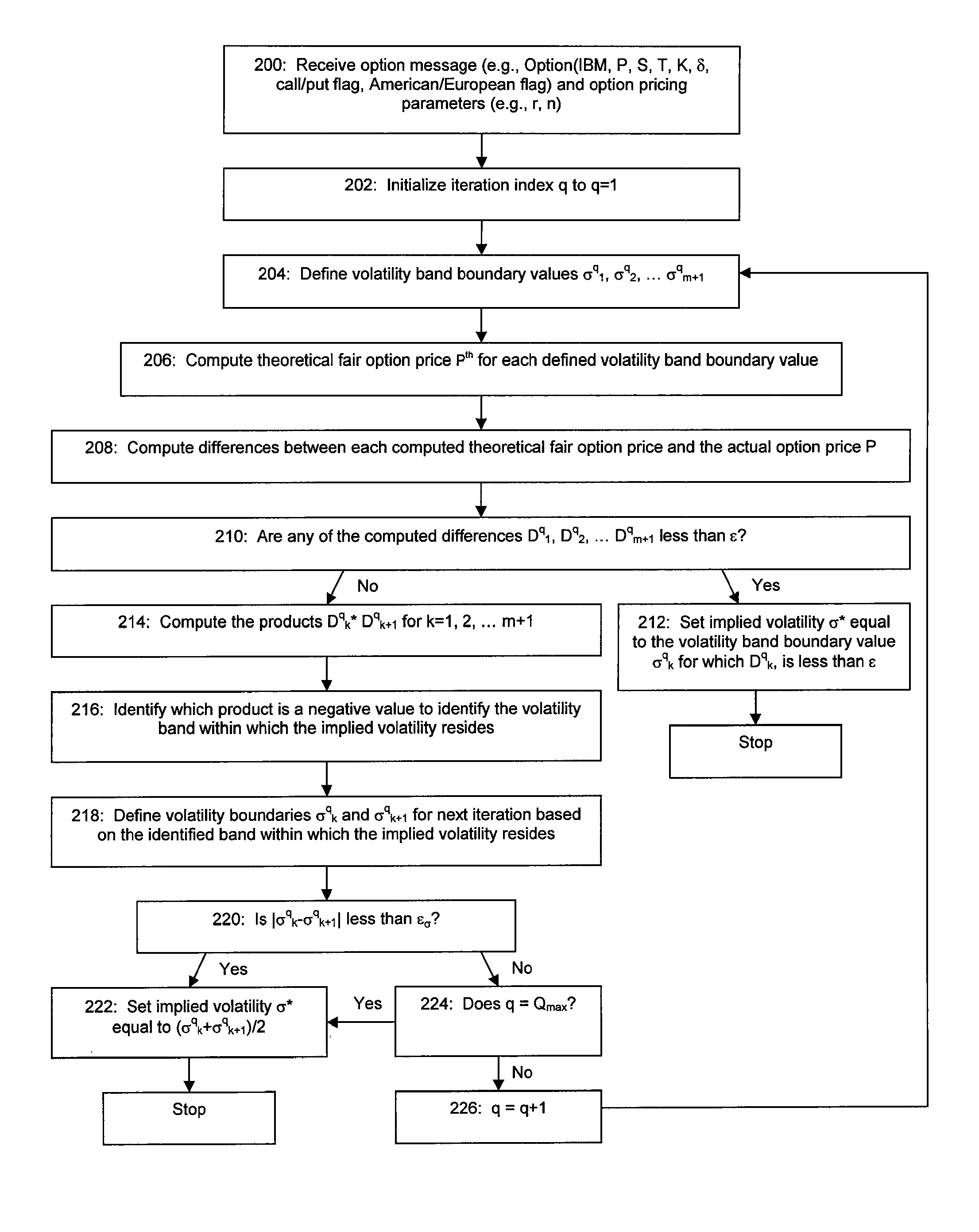
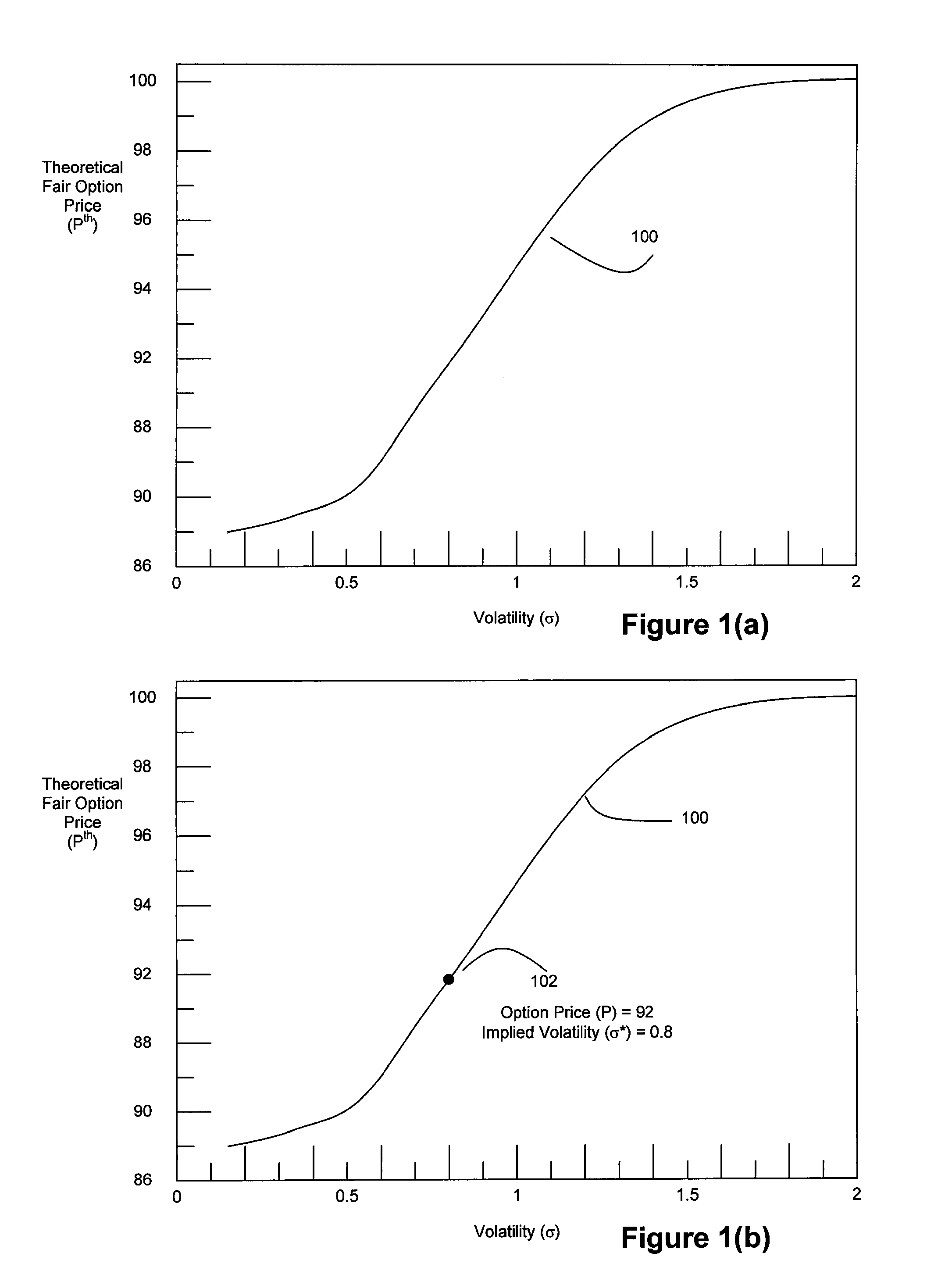
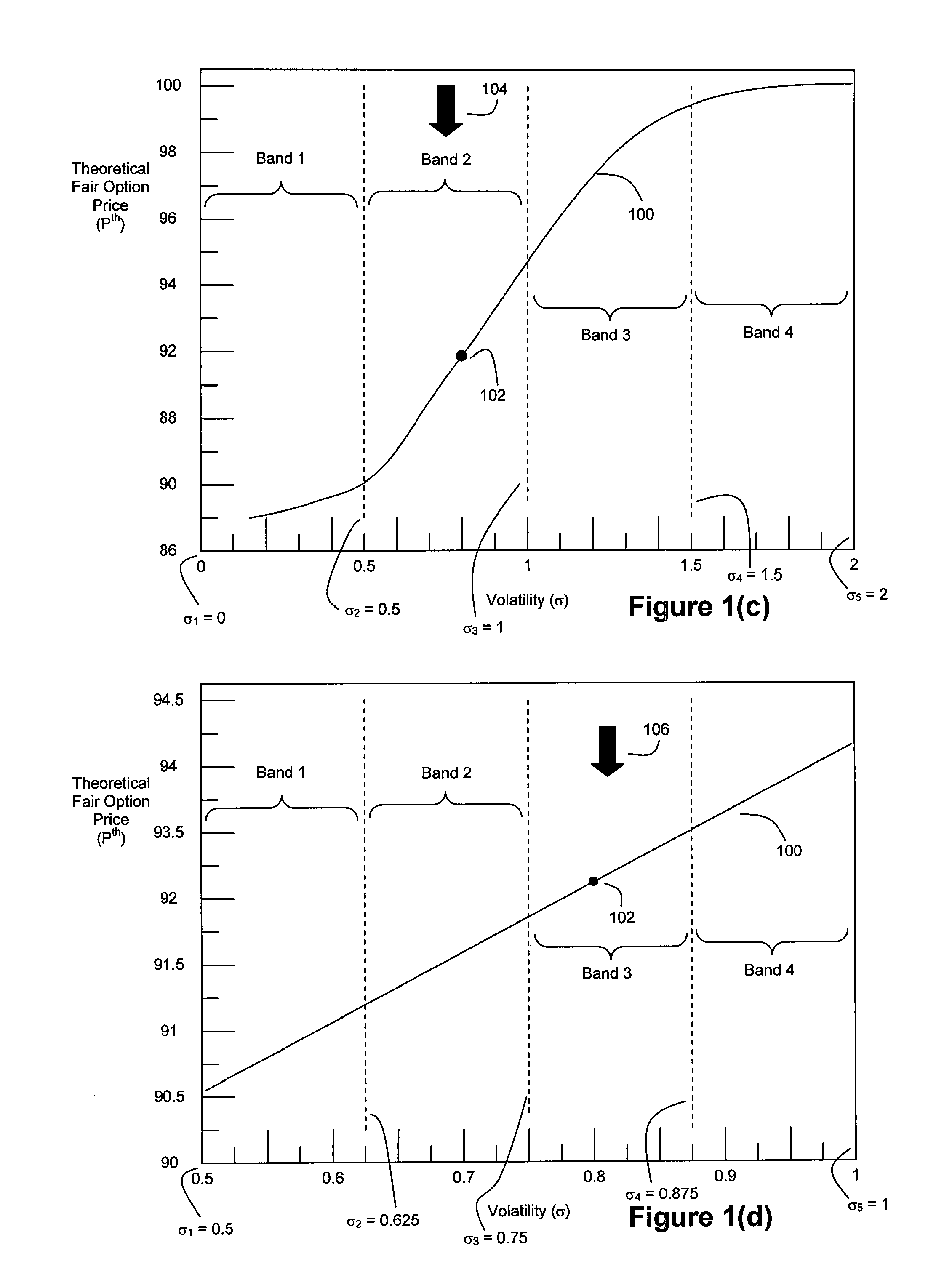
A high speed technique for options pricing in the financial industry is disclosed that can provide both high throughput and low latency. A parallel / pipelined architecture is disclosed for computing an implied volatility in connection with an option. Parallel / pipelined architectures are also disclosed for computing an option's theoretical fair price. Preferably these parallel / pipelined architectures are deployed in hardware, and more preferably reconfigurable logic such as Field Programmable Gate Arrays (FPGAs) to accelerate the options pricing operations relative to conventional software-based options pricing operations.
Owner:EXEGY INC
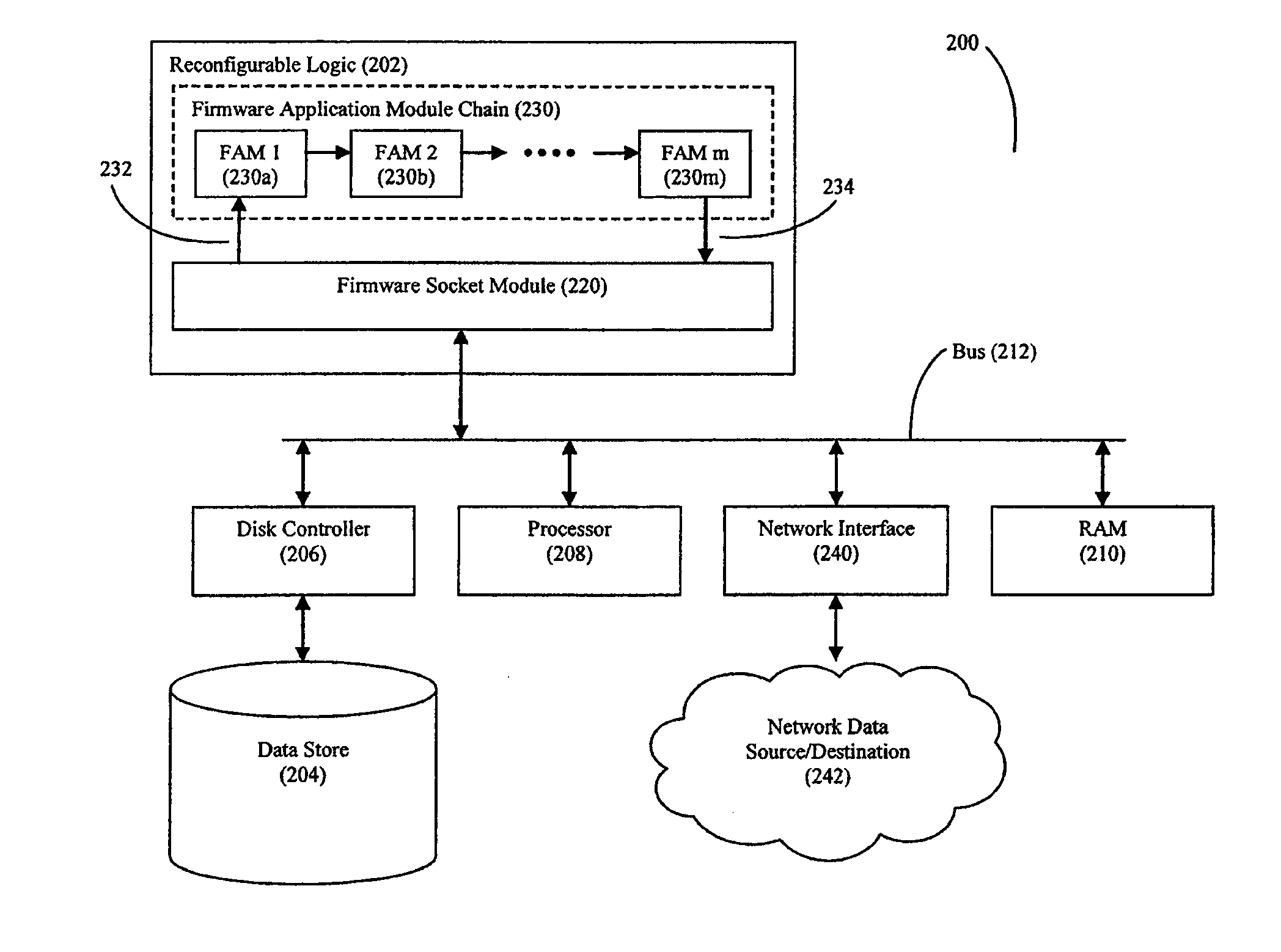
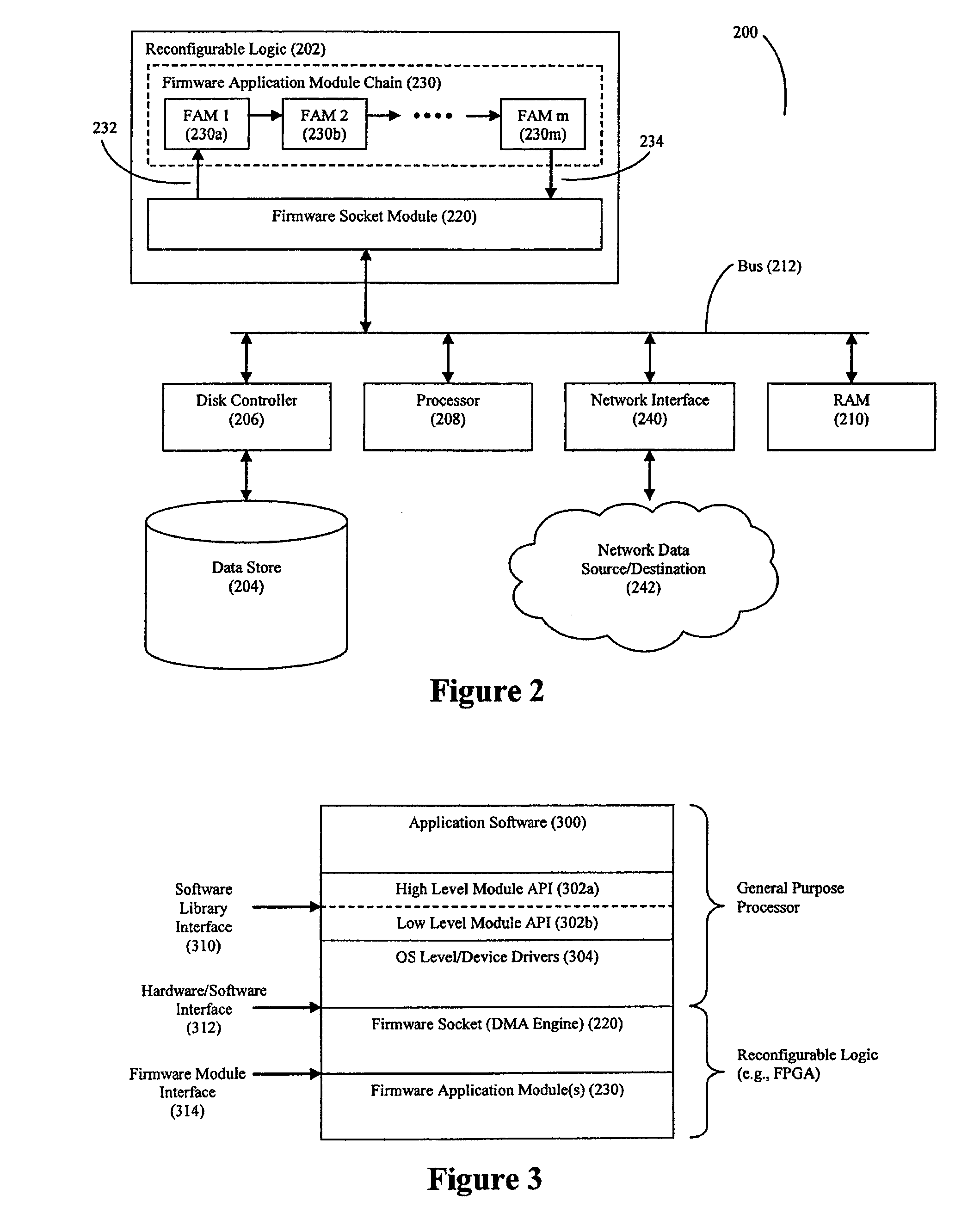
High Speed Processing of Financial Information Using FPGA Devices
Methods and systems for processing financial market data using a reconfigurable logic device are disclosed. Various operations such as basket calculation and volume weighted average price (VWAP) operations can be performed on the financial market data using firmware logic deployed on the reconfigurable logic device to accelerate the speed of processing.
Owner:EXEGY INC
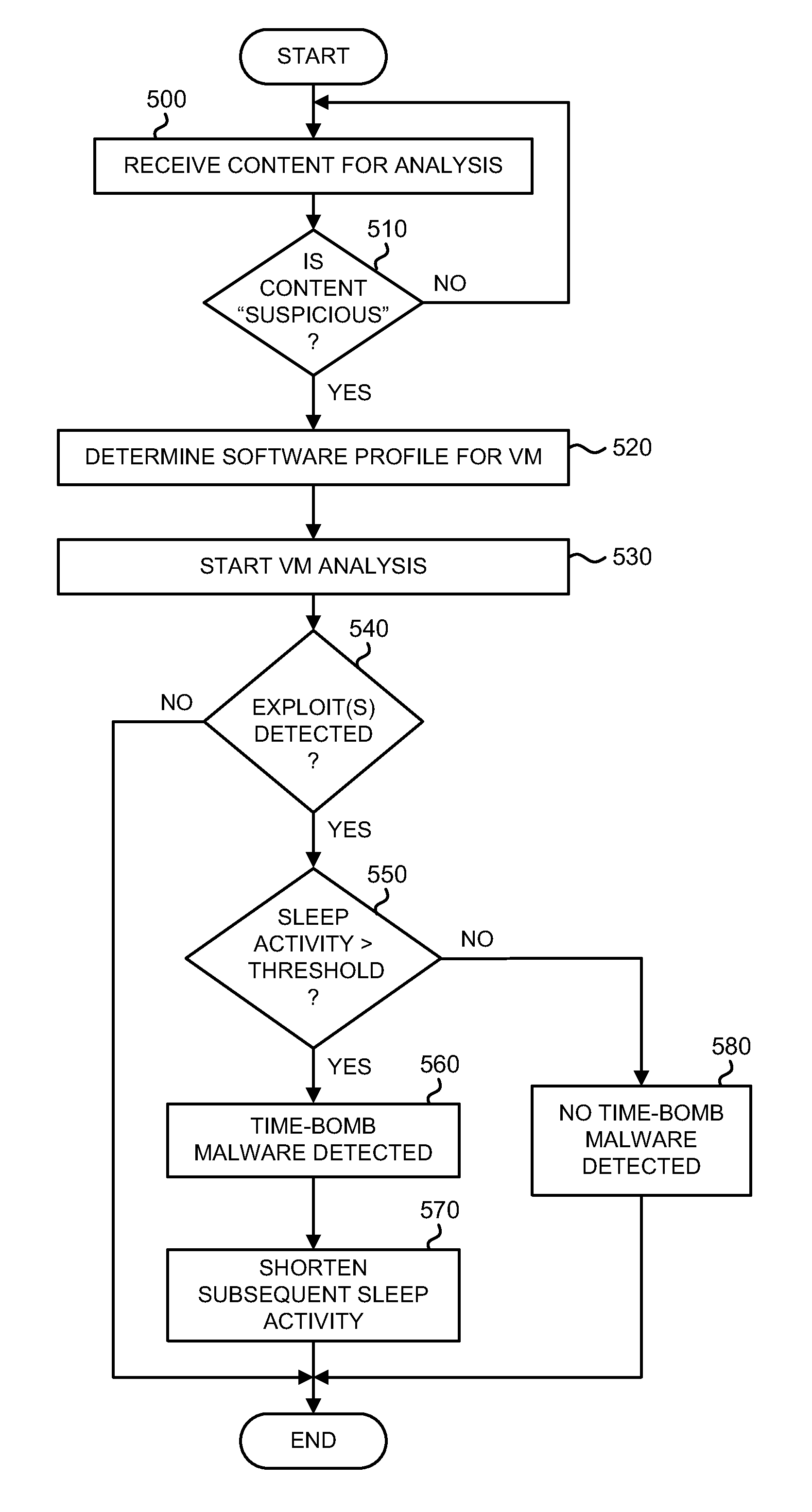
System and method for detecting time-bomb malware
According to one embodiment, a system comprises one or more counters; comparison logic; and one or more hardware processors communicatively coupled to the one or more counters and the comparison logic. The one or more hardware processors are configured to instantiate one or more virtual machines that are adapted to analyze received content, where the one or more virtual machines are configured to monitor a delay caused by one or more events conducted during processing of the content and identify the content as including malware if the delay exceed a first time period.
Owner:FIREEYE SECURITY HLDG US LLC
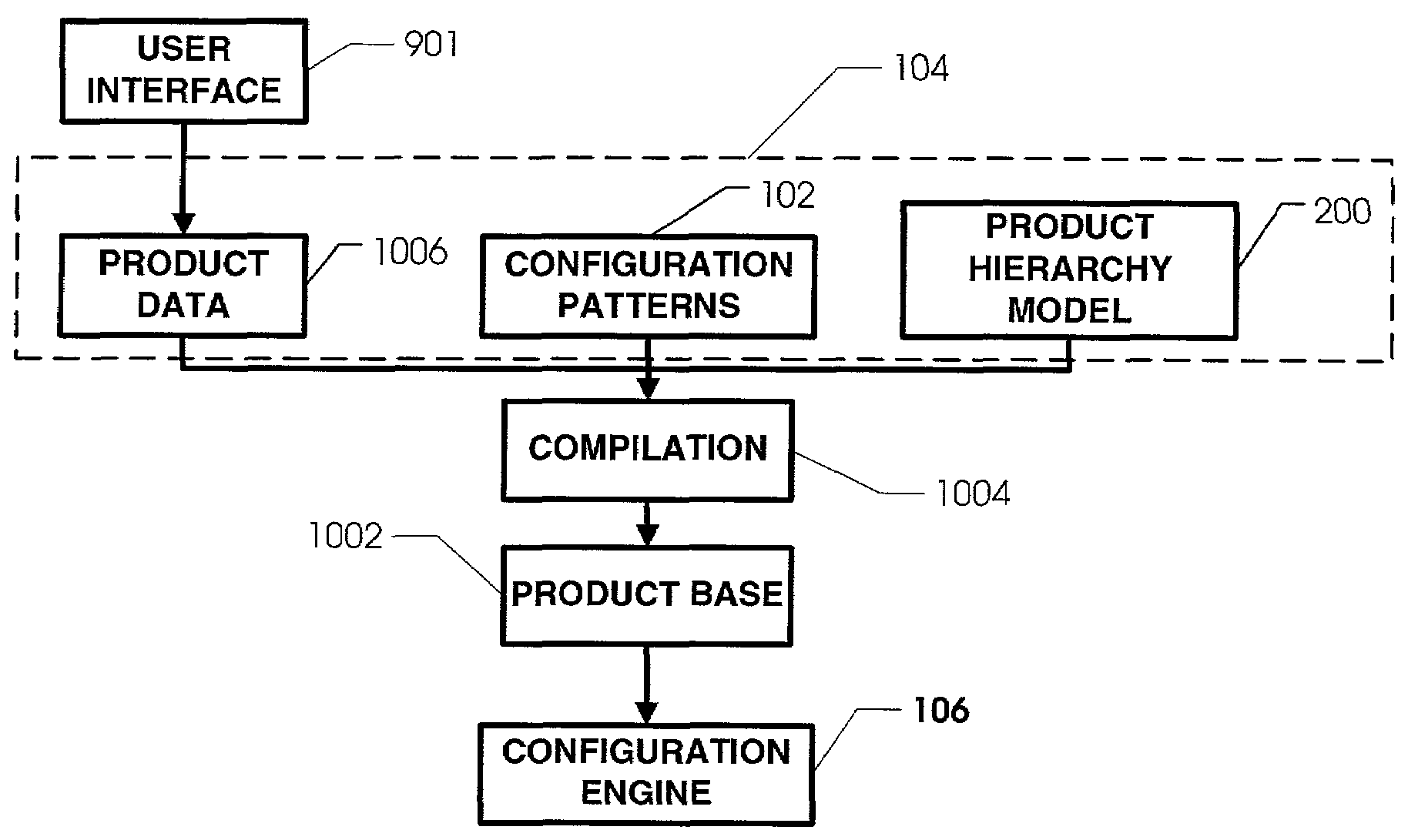
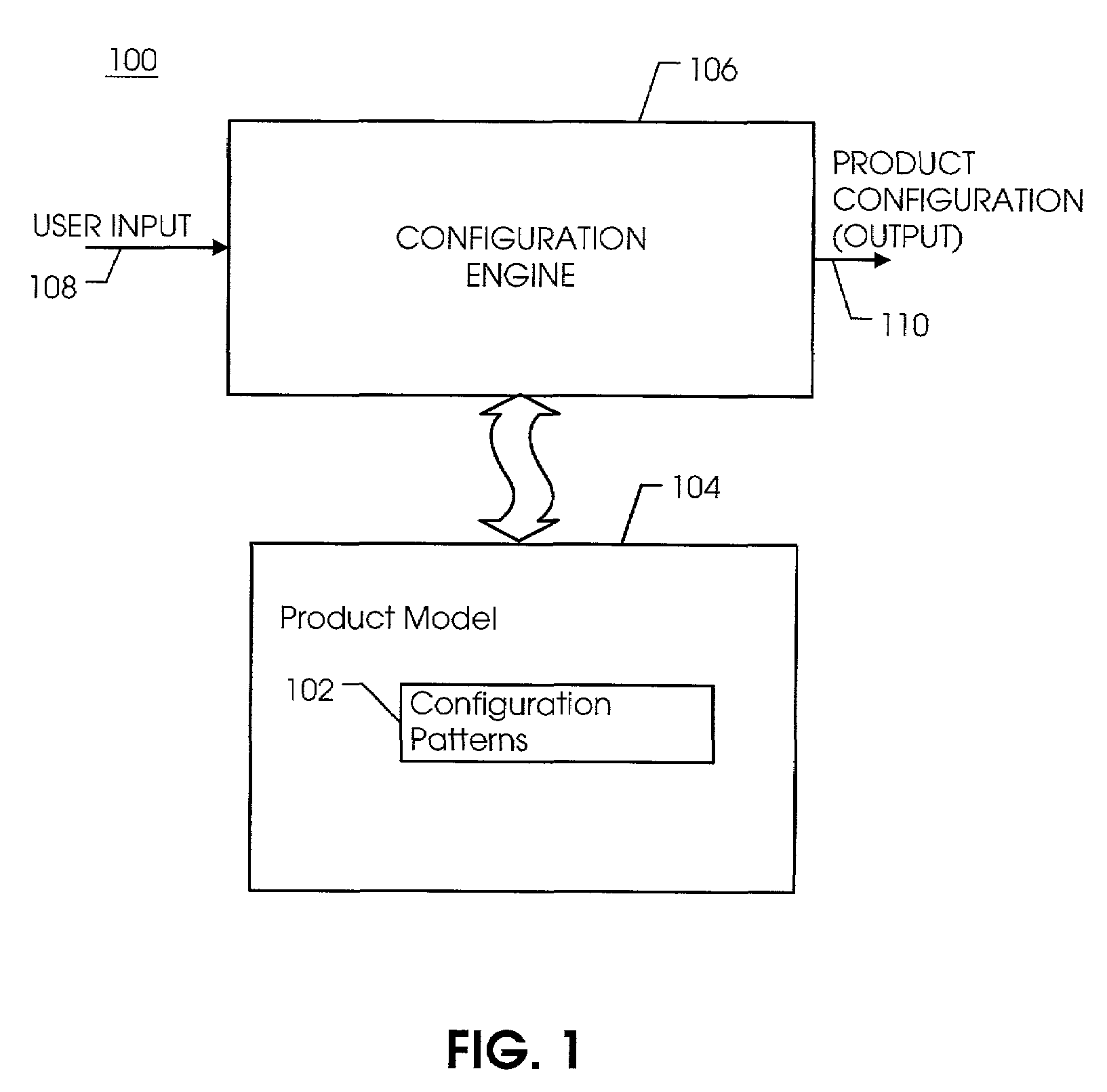
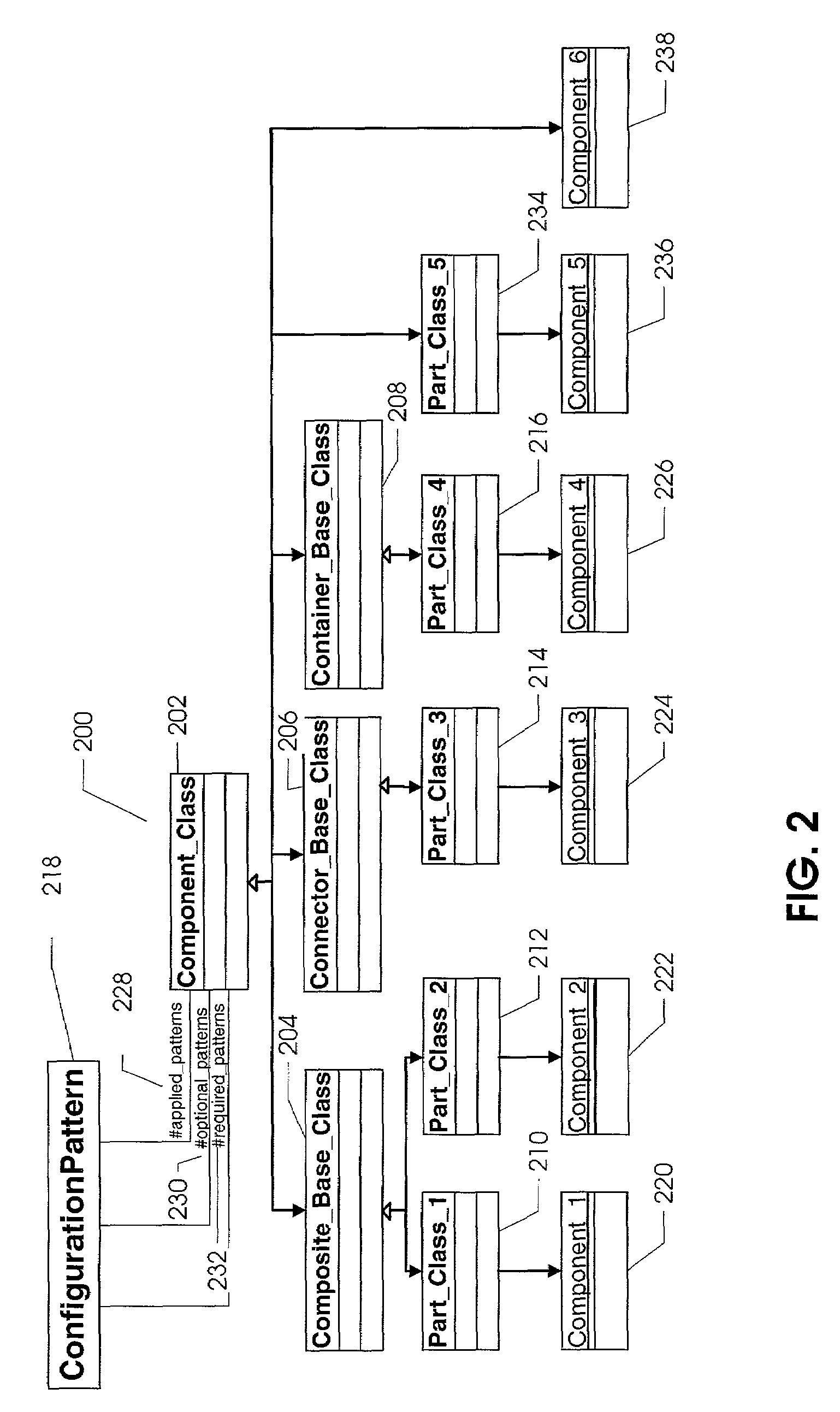
Product configuration using configuration patterns
ActiveUS7188335B1Requirement analysisSpecific program execution arrangementsData-drivenProduct family
In a particular embodiment, configuration patterns are used to provide solutions to configuration problems that repetitively occur. Use of configuration patterns in connection with a configuration model has many benefits. A configuration patterns is a parameterized or otherwise easily extensible solution to that problem, such that the solution is reusable by modifying the parameters of the pattern or extending the pattern in pre-defined ways. Configuration patterns are inherently data-driven and provide improved maintenance for data and logic as well as reduced programming effort. Configuration patterns can be reused within and across different product families and can be specialized from other patterns. Thus, the use of configuration patterns facilitates reduced maintenance cost and reduced programming effort for product configuration data and logic systems.
Owner:VERSATA DEV GROUP
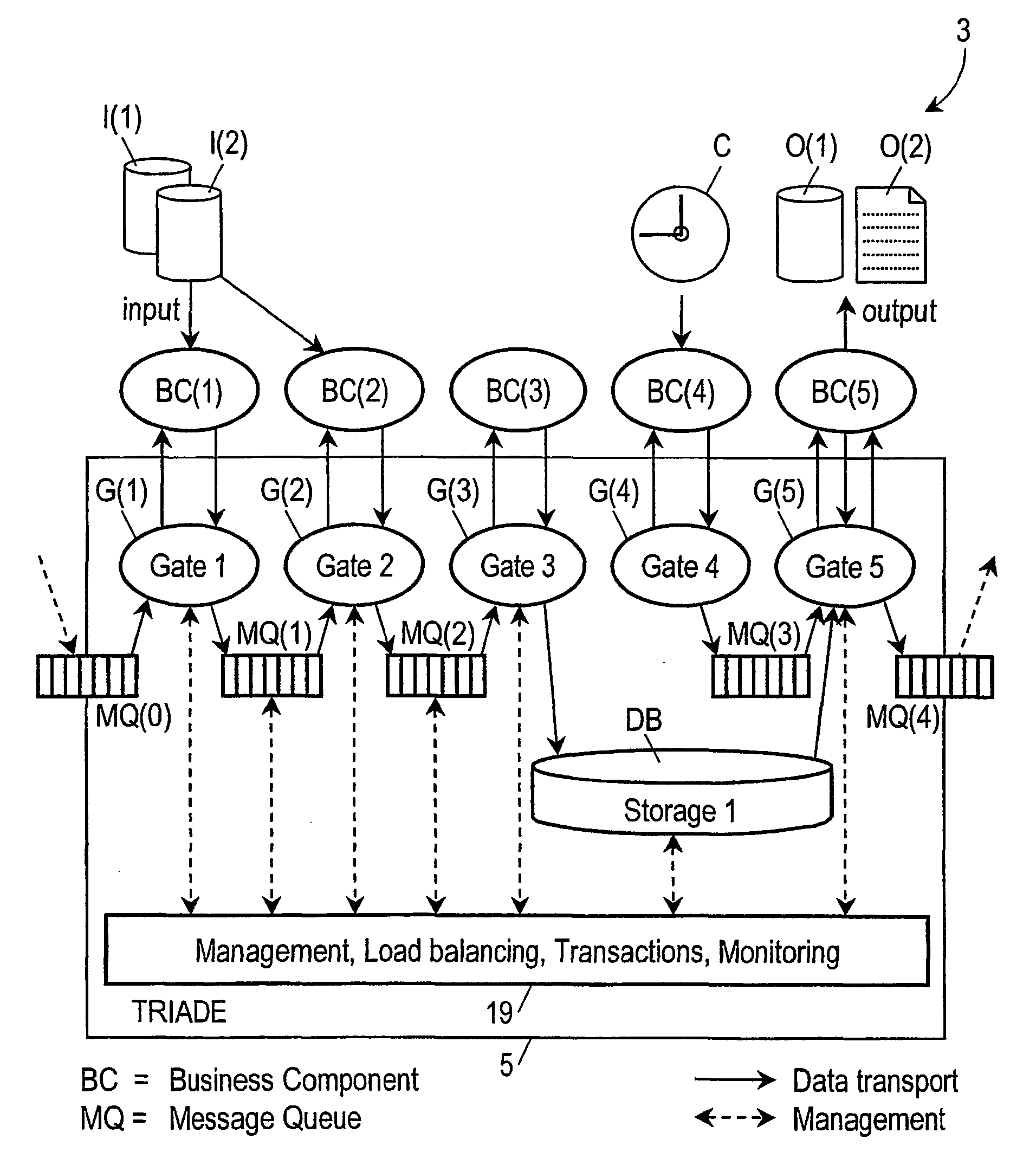
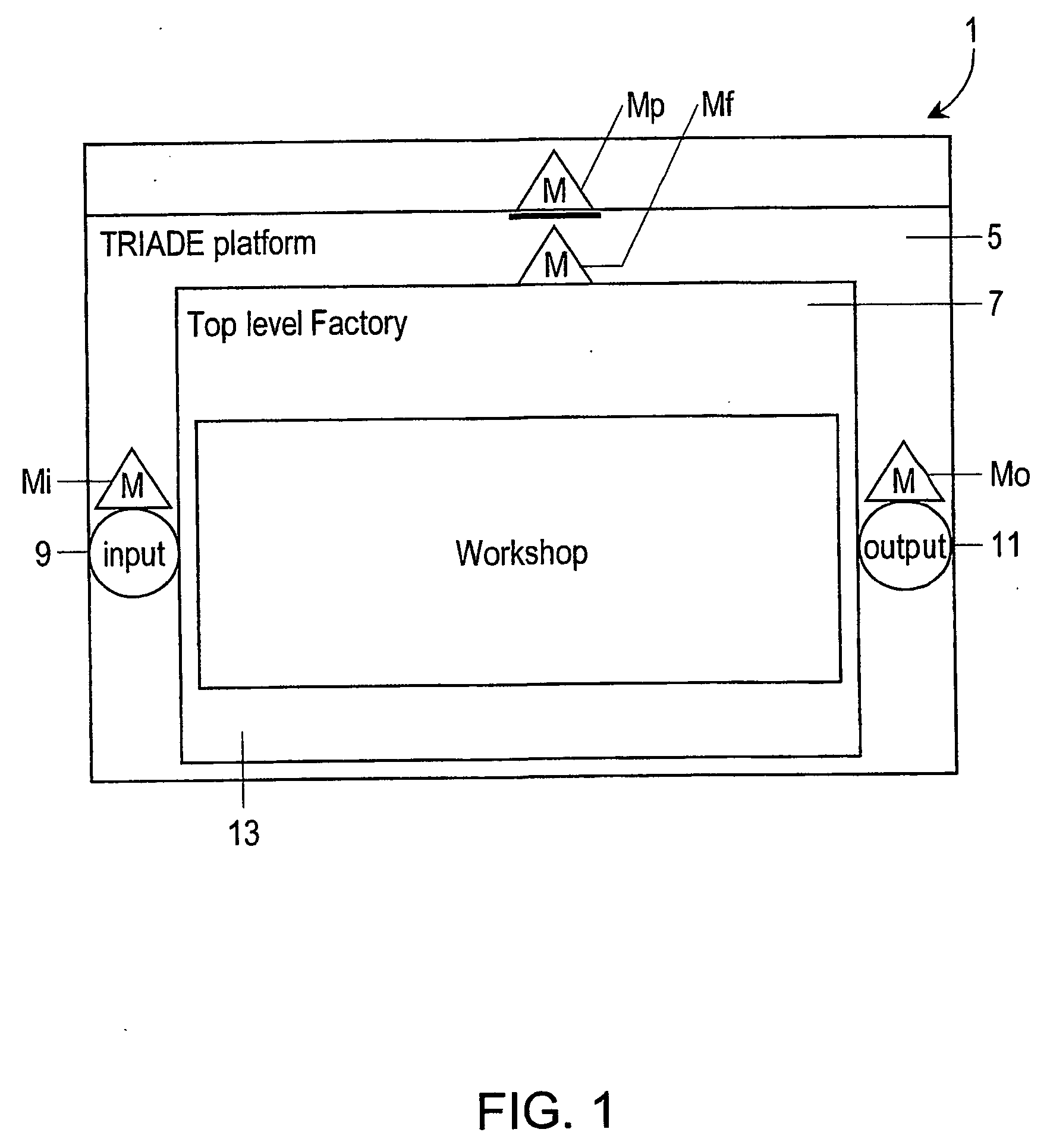
System and method for processing transaction data
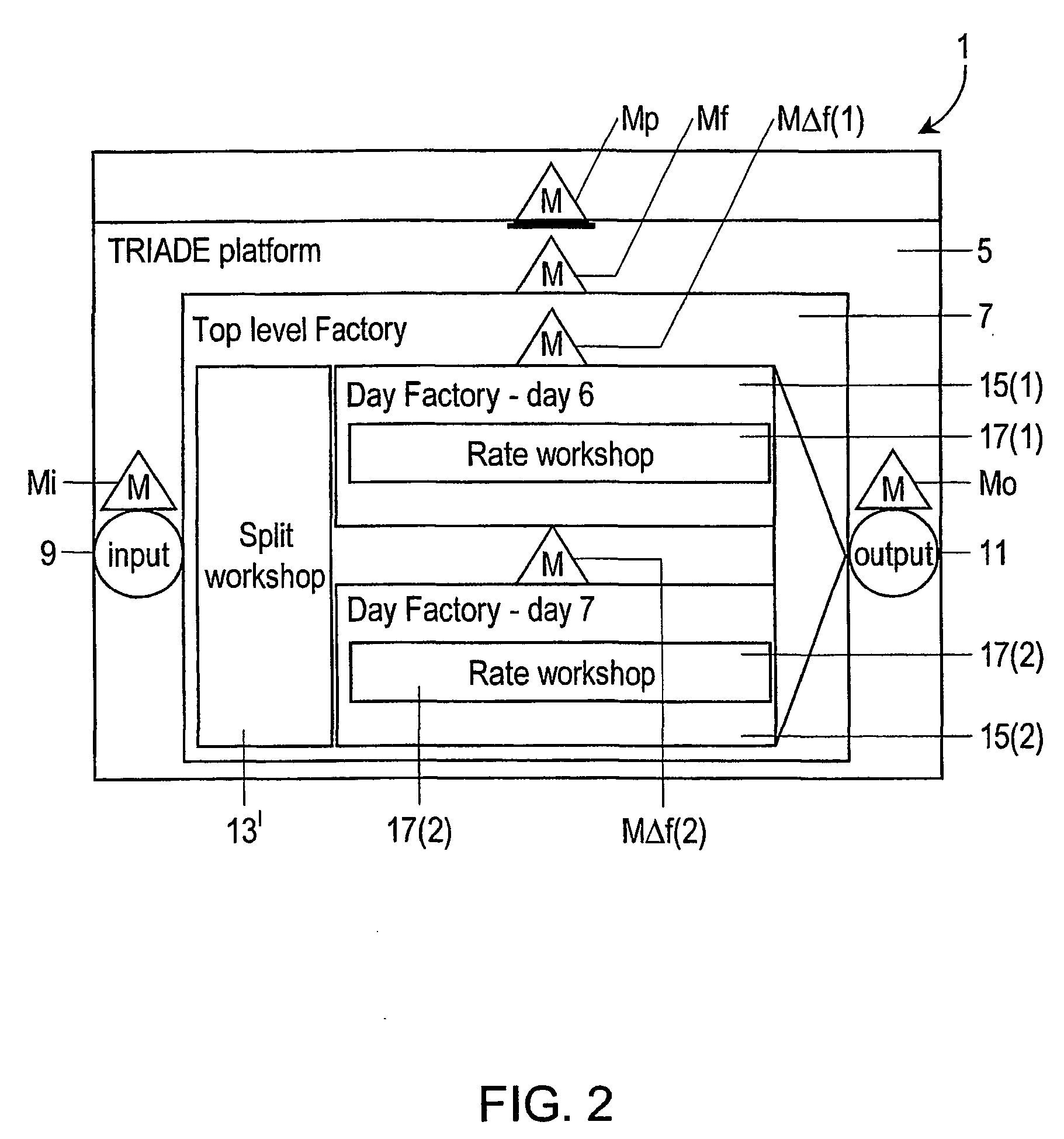
InactiveUS20040024626A1FinanceMultiple digital computer combinationsMessage queueSoftware architecture
Computer system provided with a software architecture for processing transaction data which comprises a platform (5) with at least one logical processing unit (21) comprising the following components: a plurality of gates (G(k)); one or more message queues (MQ(k)), these being memories for temporary storage of data; one or more databases (DB); a hierarchical structure of managers in the form of software modules for the control of the gates (G(j)), the messages queues (MQ(k)), the one or more databases, the at least one logical processing unit (21) and the platform (5), wherein the gates are defined as software modules with the task of communicating with corresponding business components (BC(j)) located outside the platform (5), which are defined as software modules for carrying out a predetermined transformation on a received set of data.
Owner:NEDERLANDSE ORG VOOR TOEGEPAST-NATUURWETENSCHAPPELIJK ONDERZOEK (TNO)
System and method for detecting time-bomb malware
Owner:FIREEYE SECURITY HLDG US LLC +1
Method and apparatus for previewing GUI design and providing screen-to-source association
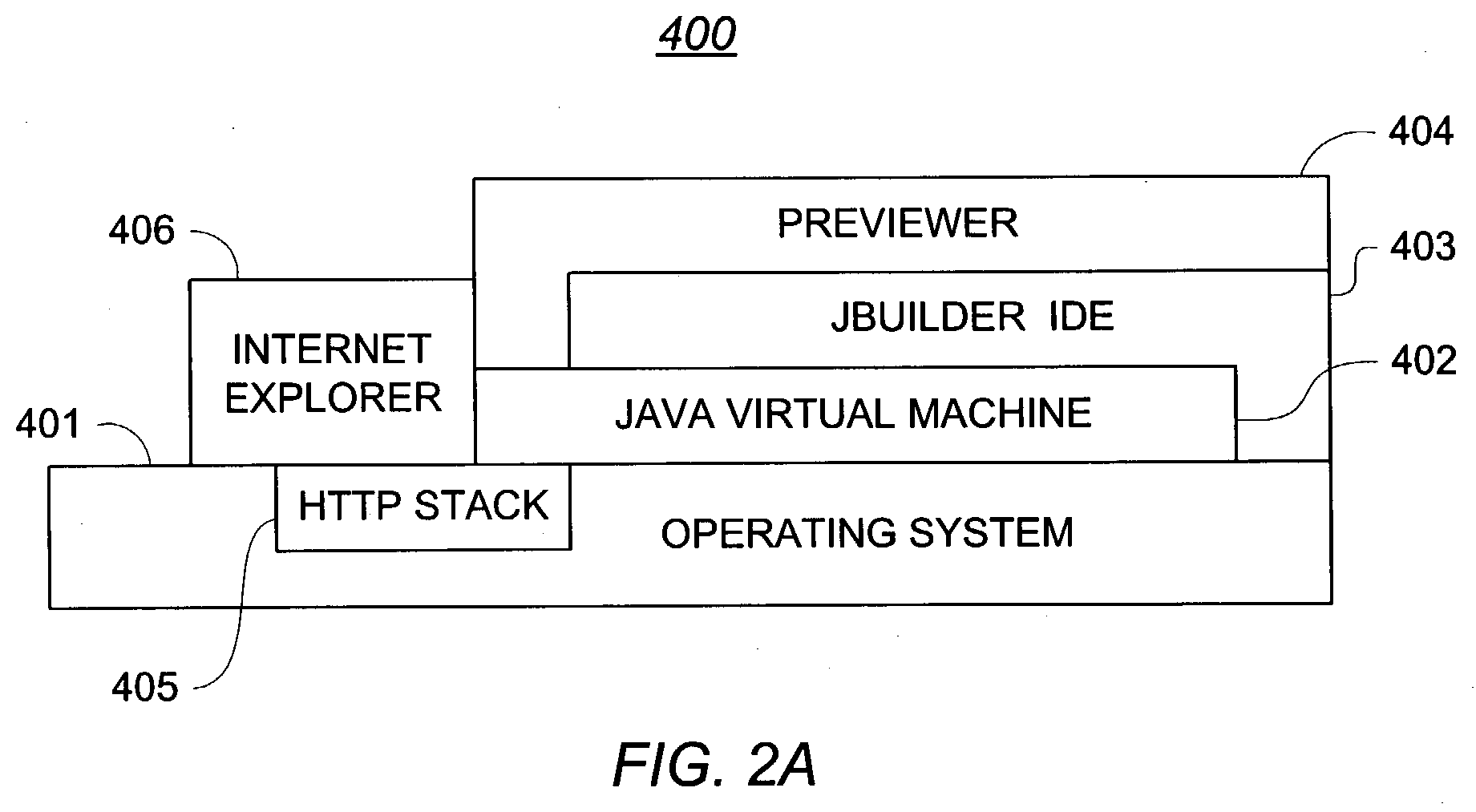
InactiveUS20040090458A1Eliminate dependenciesSoftware engineeringCathode-ray tube indicatorsConfiguration itemLogisim
A method and apparatus for previewing resulting screens of UI scripts of client-server information systems and providing screen-to-source association of those UI scripts. The process includes translating UI scripts into UI instructions to be displayed in the clients without executing the scripts in a server or modifying the clients, prompting a user to provide inputs for configuration items so that UI components with conditional logic can be properly previewed and inserting extra logic and data into the generated UI instructions so that when a user selects a location on a screen the corresponding section of a UI scripts will be displayed and highlighted.
Owner:SCIOWORKS TECH
Methods and systems for safe execution of guest code in virtual machine context
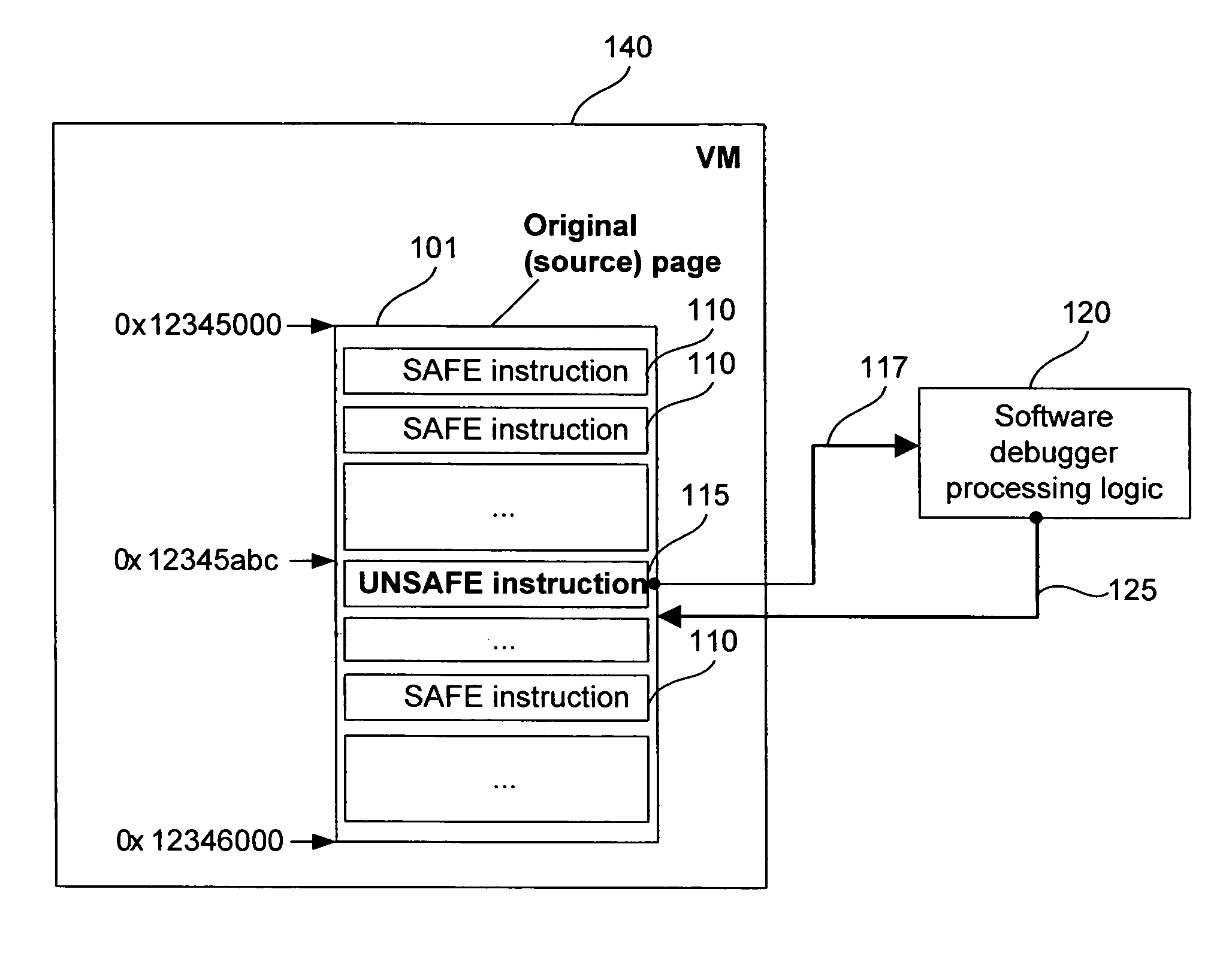
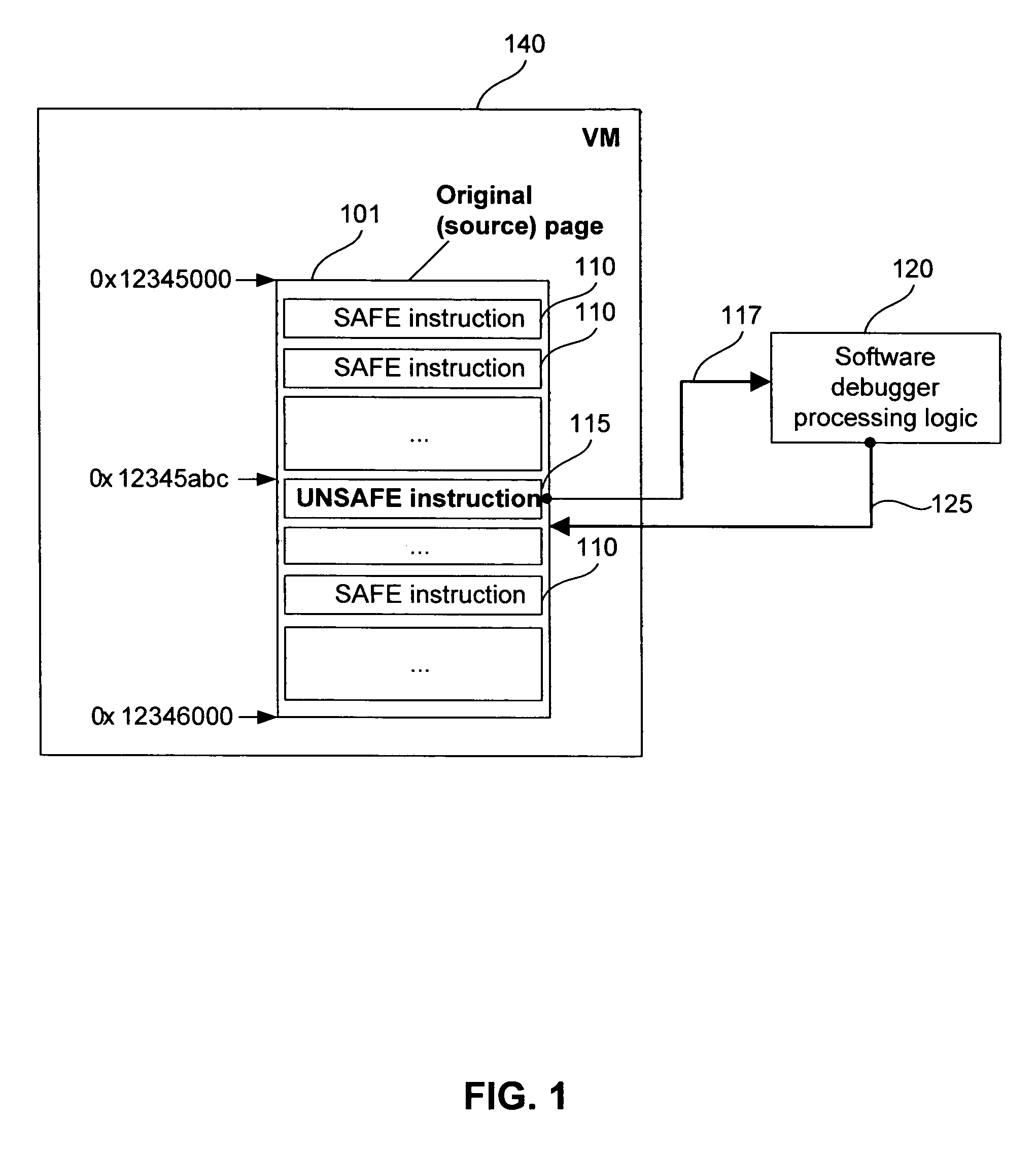
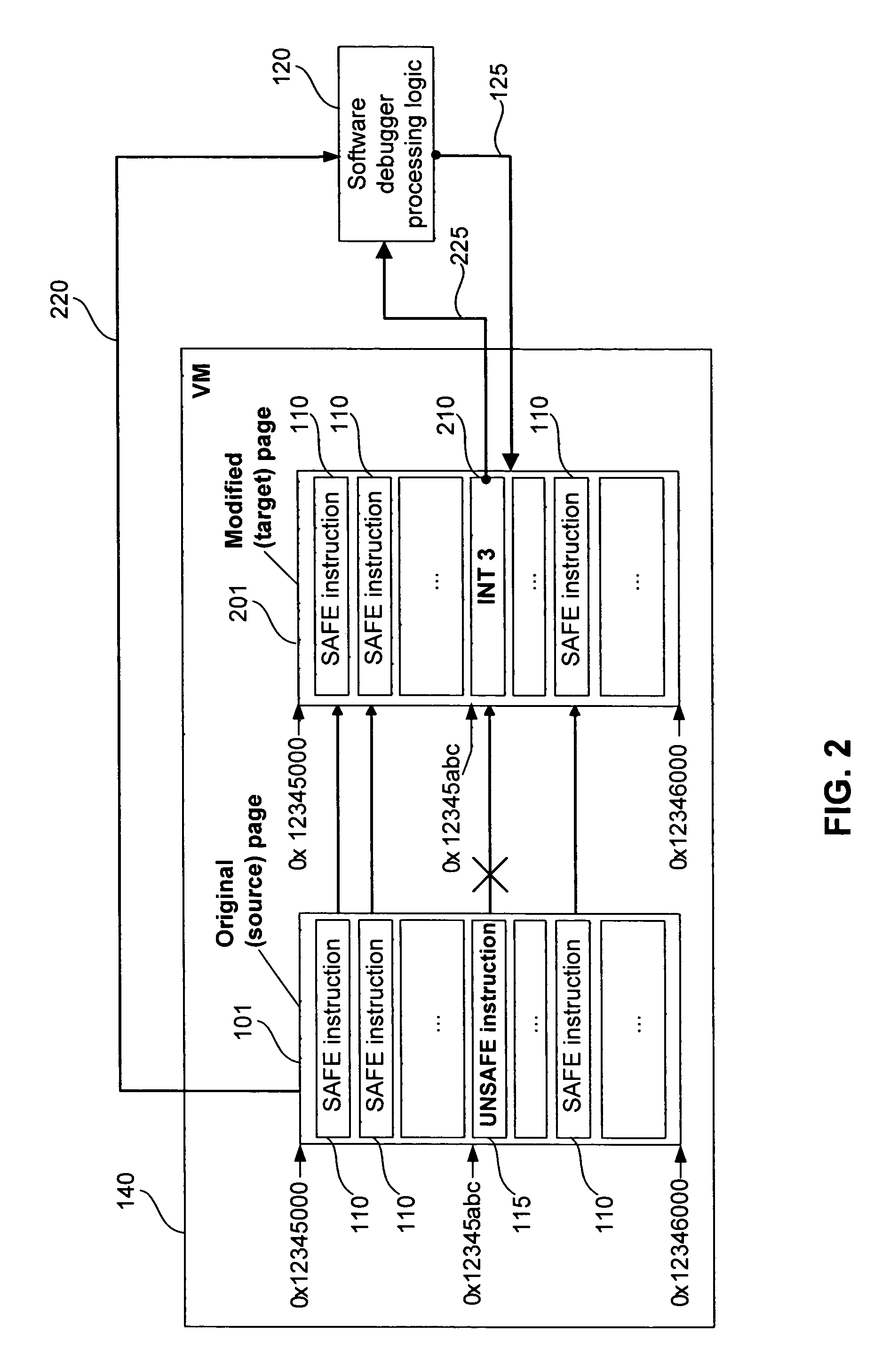
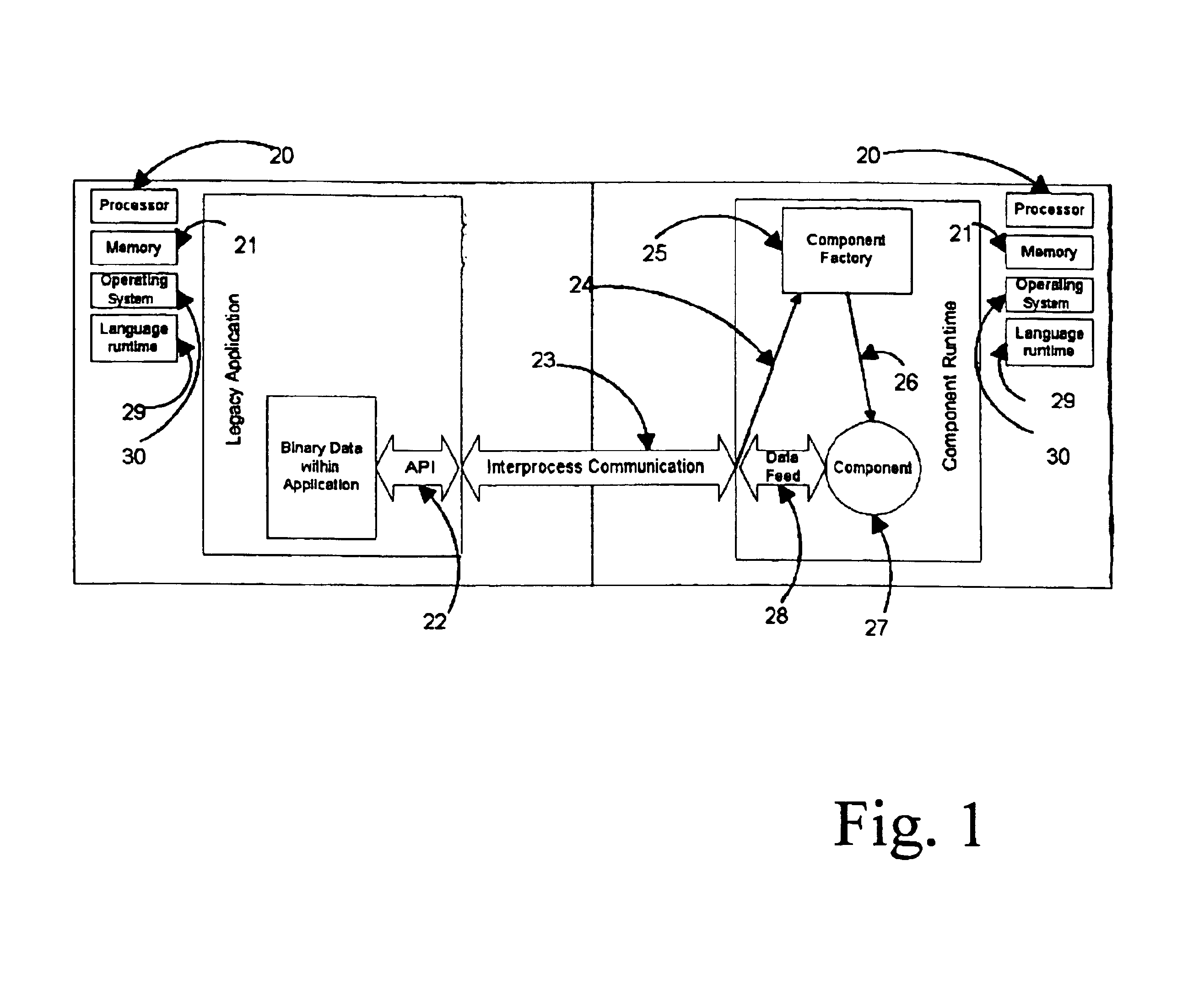
ActiveUS7647589B1Ensuring Safe ExecutionError detection/correctionPlatform integrity maintainanceSoftware engineeringLogisim
Methods and systems for safe execution of guest code in virtual machine context are presented. A method for running a virtual machine in a computing system includes (a) launching a virtual machine monitor (VMM) that uses a software debugger; (b) launching a virtual machine (VM) that can natively run safe instructions; (c) determining, at runtime, if the instruction is safe or potentially unsafe; (d) executing safe instructions in a native mode; and (e) activating control logic to process potentially unsafe instructions in the software debugger. The software debugger can bypass at least one of the potentially unsafe instructions. The potentially unsafe instructions include instructions that cannot be safely executed in the context of the VM, and instructions that can cause unpredictable results in the context of the VM.
Owner:PARALLELS INT GMBH
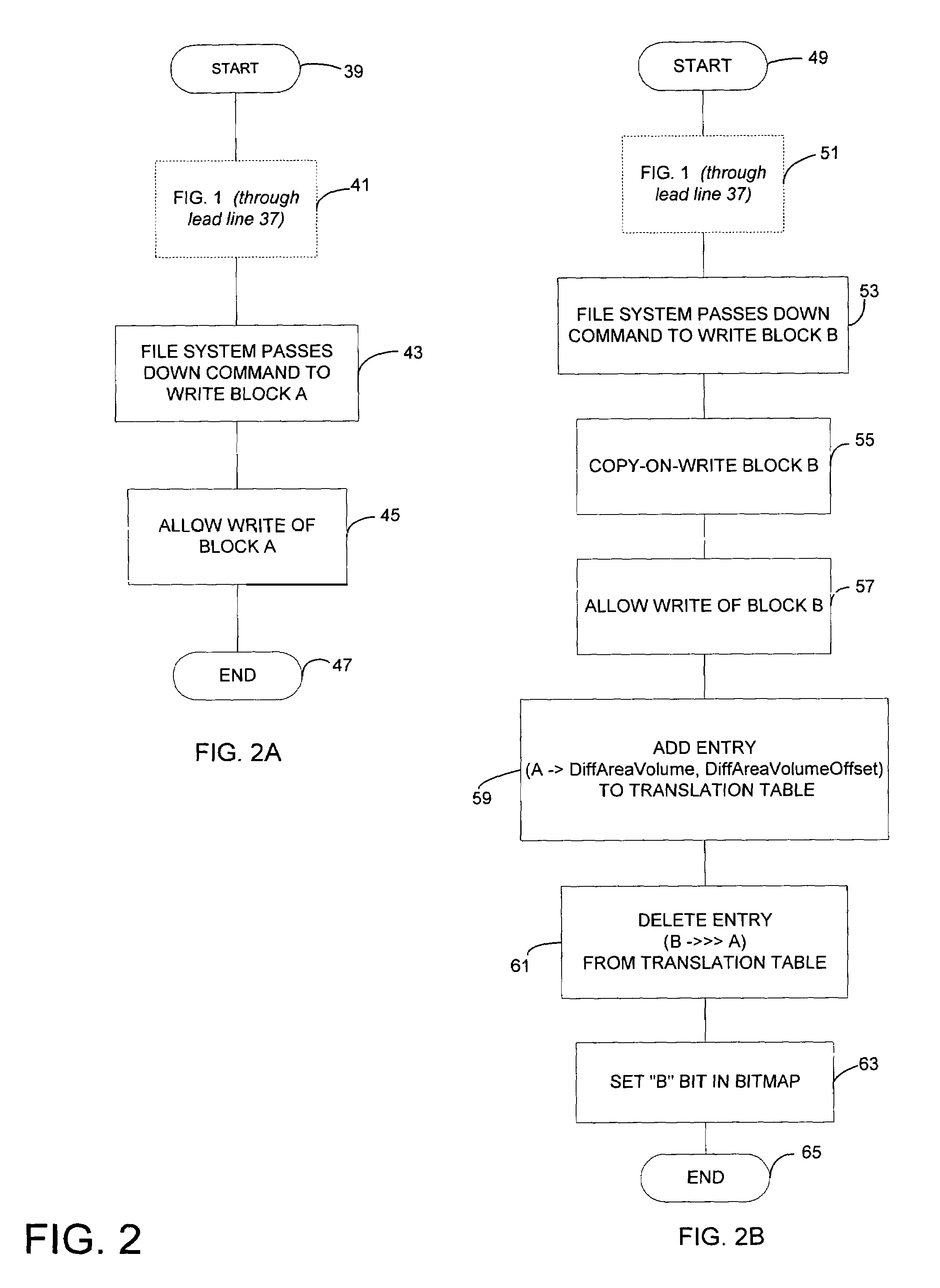
Optimizing defragmentation operations in a differential snapshotter
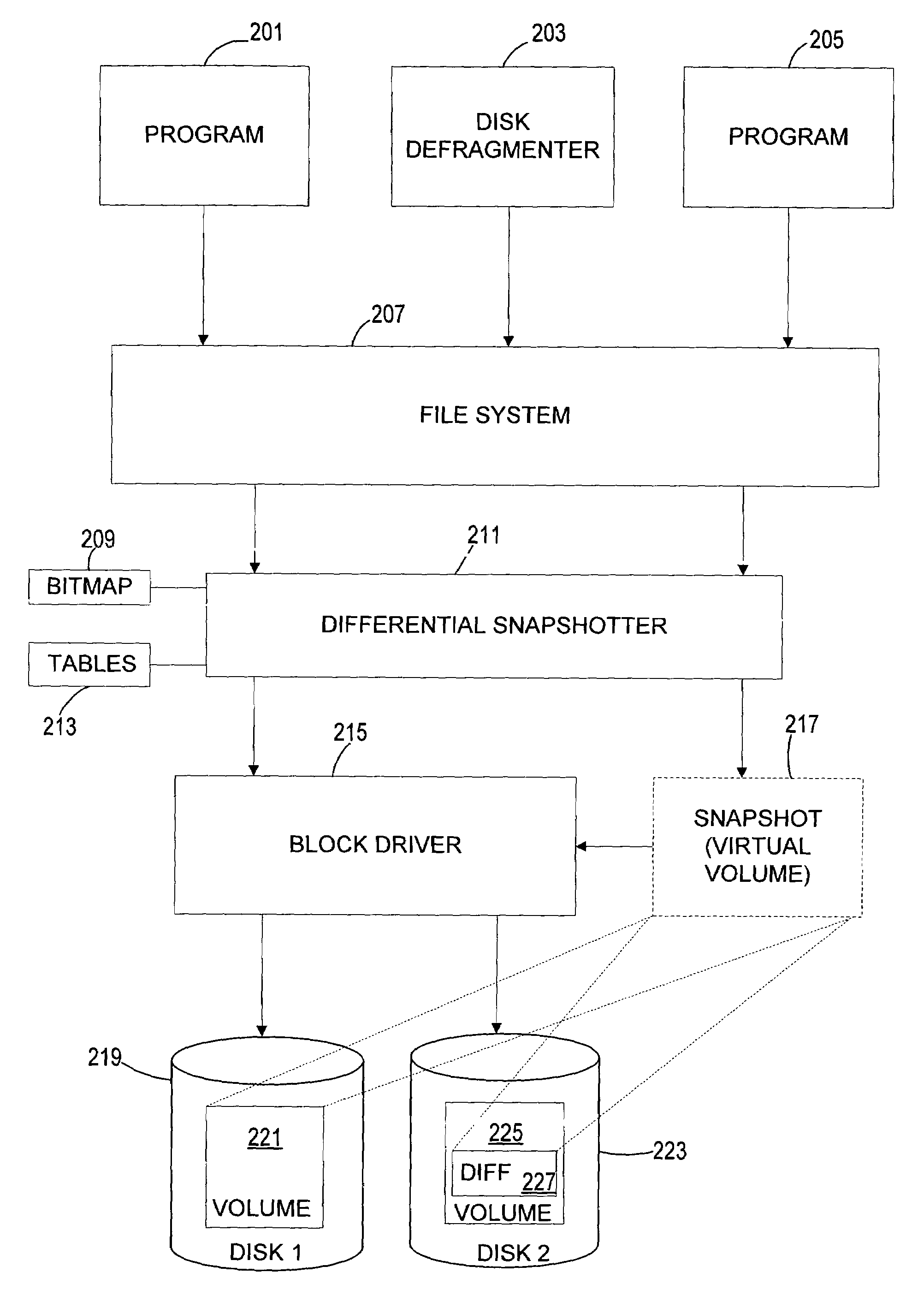
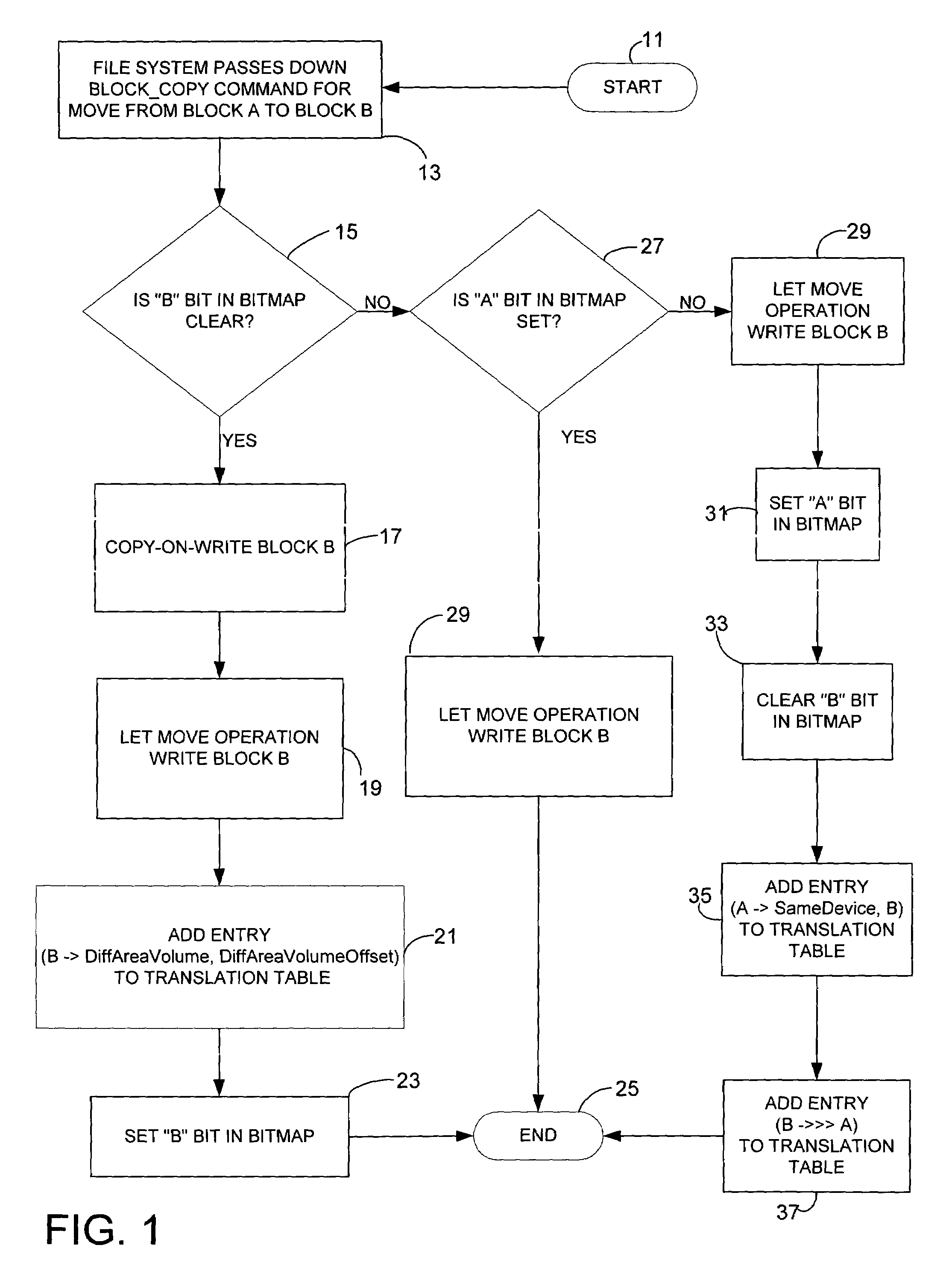
InactiveUS7664771B2Avoid unnecessary copy-on-write operationInput/output to record carriersDigital data processing detailsFile systemTranslation table
A differential snapshot is established and maintained for a set of files stored on a volume. Copy-on-write operations are avoided for logically insignificant moves of blocks, such as the block rearrangements characteristic of defragmentation utilities. A file system passes a block copy command to lower-level drivers that are to inform the snapshotter that a block move operation is not logically meaningful. When the logically insignificant move is of a block whose data forms part of the data captured in the snapshot virtual volume, and when the move is to a block location that is functioning as logical free space, the snapshotter can simply modify its block bitmap and update translation table entries without needing to perform a copy-on-write.
Owner:MICROSOFT TECH LICENSING LLC
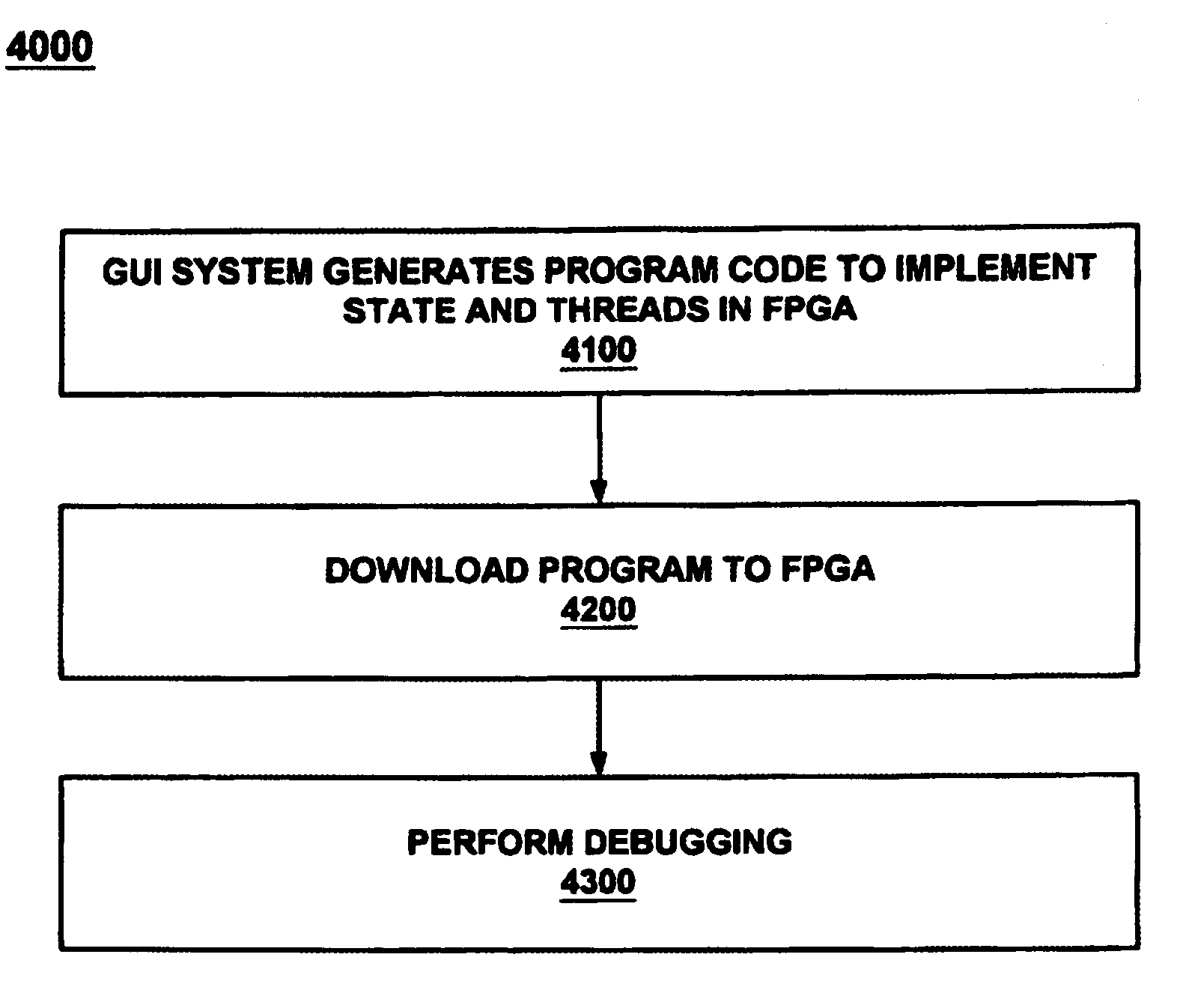
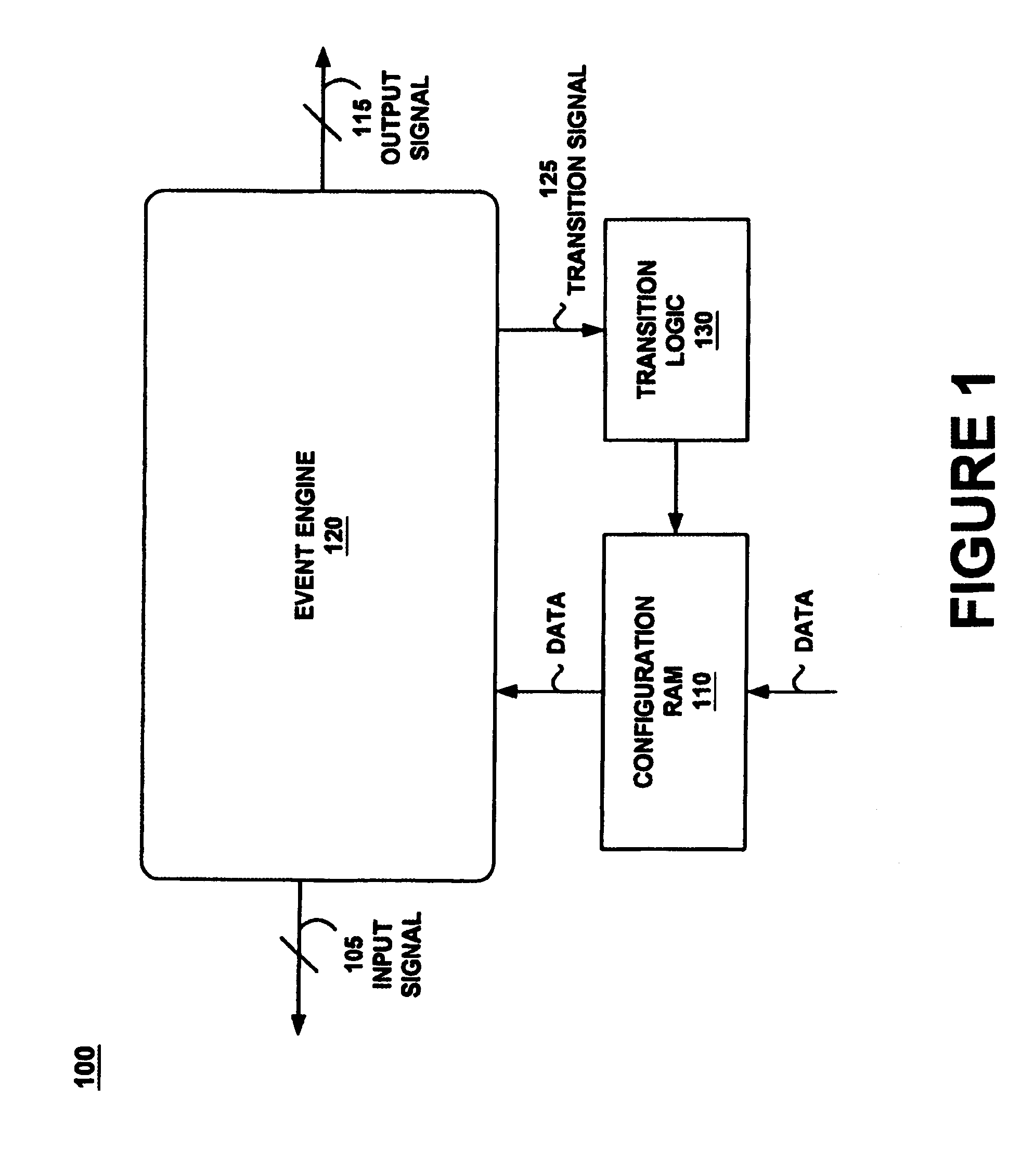
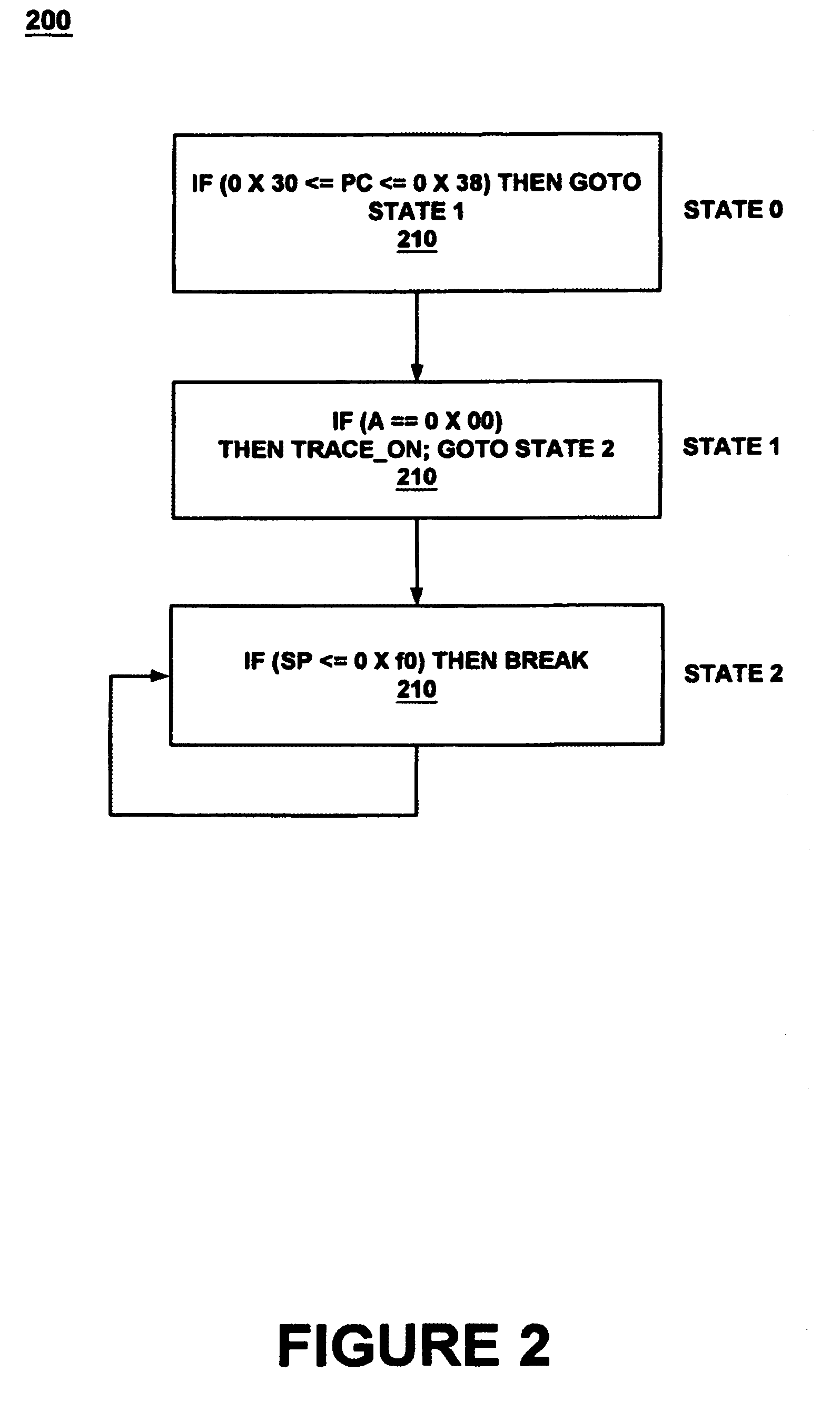
Graphical user interface with logic unifying functions
ActiveUS7150002B1Easy programmingError detection/correctionSpecific program execution arrangementsGraphical user interfaceSoftware engineering
Programming a plurality of states having respective threads is achieved by an event engine and a computer controlled GUI causing the event engine to monitor a signal and execute an action based thereon. The GUI programs an event and several states and causes the event engine to traverse between the states upon reaching the event. The GUI further programs a logic chain which unifies the threads. A method unifies several threads by selecting and executing a logic operation. The method further configures several states and causes traversing between them. The GUI may be deployed co-functionally with debuggers, logic analyzers, scopes, utilities, and software development tools. The results of the GUI are automatically transformed into program code which programs the event engine to operate during debug of a device under test by monitoring for events and taking action based thereon.
Owner:MONTEREY RES LLC
Method and System for High Speed Options Pricing
A high speed technique for options pricing in the financial industry is disclosed that can provide both high throughput and low latency. Parallel / pipelined architectures are disclosed for computing an option's theoretical fair price. Preferably these parallel / pipelined architectures are deployed in hardware, and more preferably reconfigurable logic such as Field Programmable Gate Arrays (FPGAs) to accelerate the options pricing operations relative to conventional software-based options pricing operations.
Owner:EXEGY INC
Method of and system for designing an N-tier software architecture for use in generating software components
InactiveUS6854107B2Low costMultiple digital computer combinationsSoftware designSoftware architectureSoftware engineering
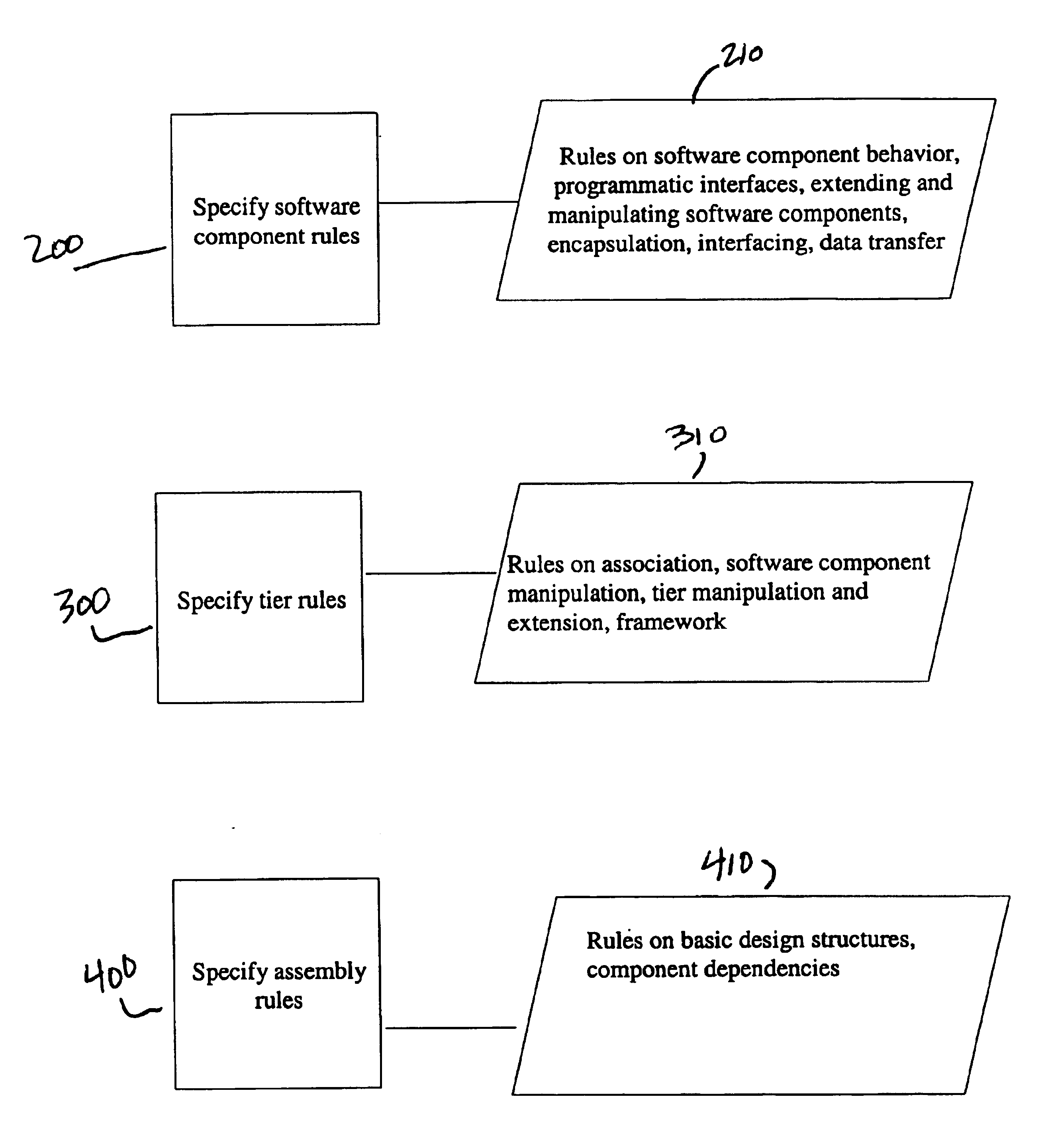
A system and method for designing a software architecture for utilizing software components in building extensible N-tier software applications is described, the method comprising specifying a set of software component rules for creating software components; specifying a set of tier rules for creating tiers; and specifying a set of assembly rules further comprising association rules by which each tier may be associated with at least one software component and linkage rules by which each tier may be linked to at least one other tier. The tier rules may further comprise a set of association rules by which each tier created with the set of tier rules may be associated with at least one software component created using the software component rules; a set of tier framework rules to provide an architected context for software components within a tier; and a set of package rules to provide for logical grouping of interfaces within a framework defined by the tier framework rules to provide a set of specific behaviors for the tier.
Owner:BAKER HUGHES INC
Method of accessing data and logic on existing systems through dynamic construction of software components
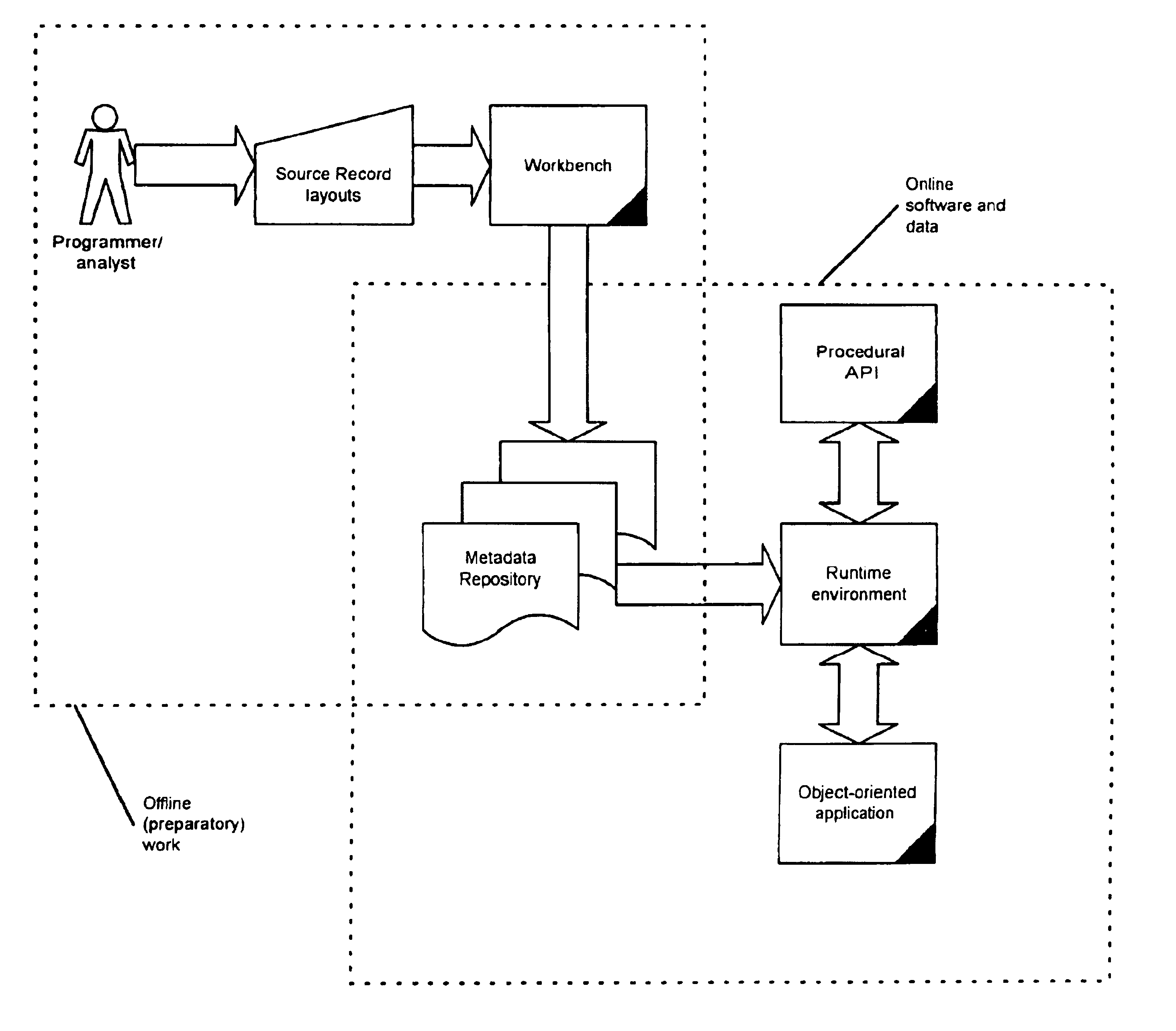
InactiveUS6931623B2Easy to reuseMultiprogramming arrangementsSoftware maintainance/managementBinary informationApplication software
A record layout in a legacy application is defined by the record definition in the source code of the language in which the application was written. For each record in a legacy application, the layout of the record is saved in a language-neutral and architecture neutral format in preparation for a runtime invocation. During runtime, for each record, the legacy application can send architecture-specific binary information as it exists in memory on the legacy computer to a component runtime environment that will construct a compatible object-oriented instance of a class to manipulate the information. Once the information is manipulated, the updated information can be represented to the original legacy application in an architecture-specific binary record layout.
Owner:TOUCHNET INFORMATION SYST
Shared FP and SIMD 3D multiplier
InactiveUS6490607B1Computations using contact-making devicesRuntime instruction translationComputerized systemTheoretical computer science
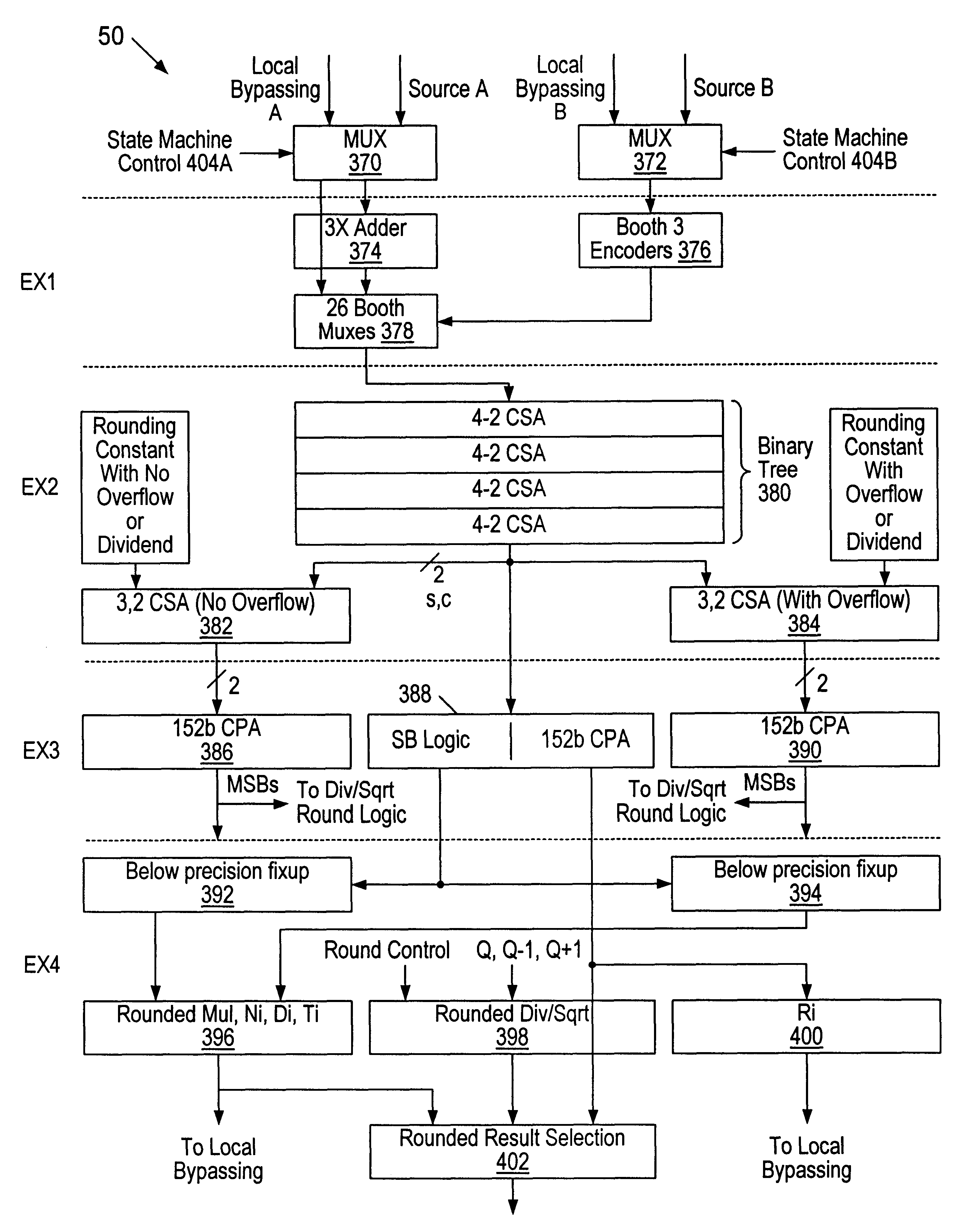
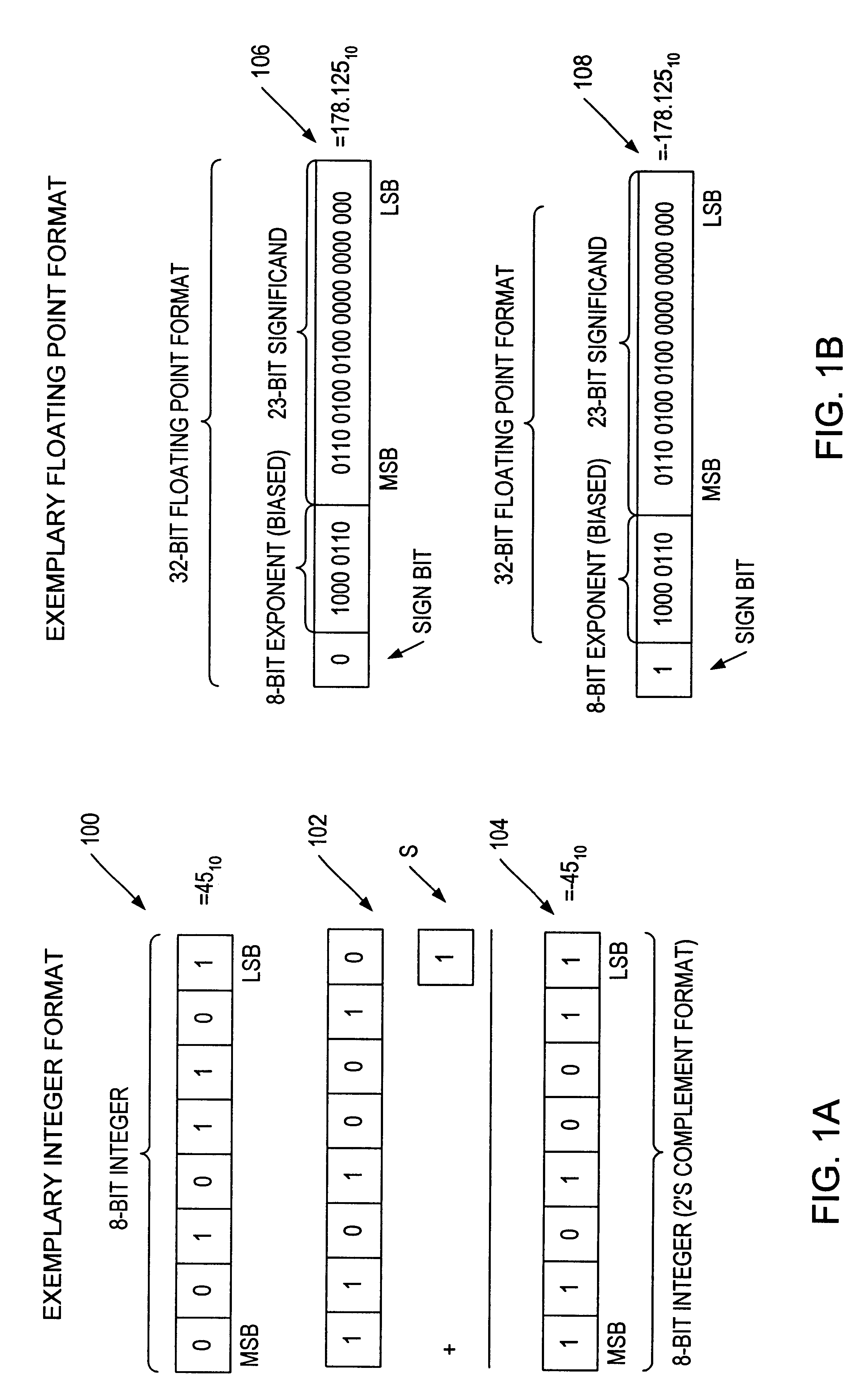
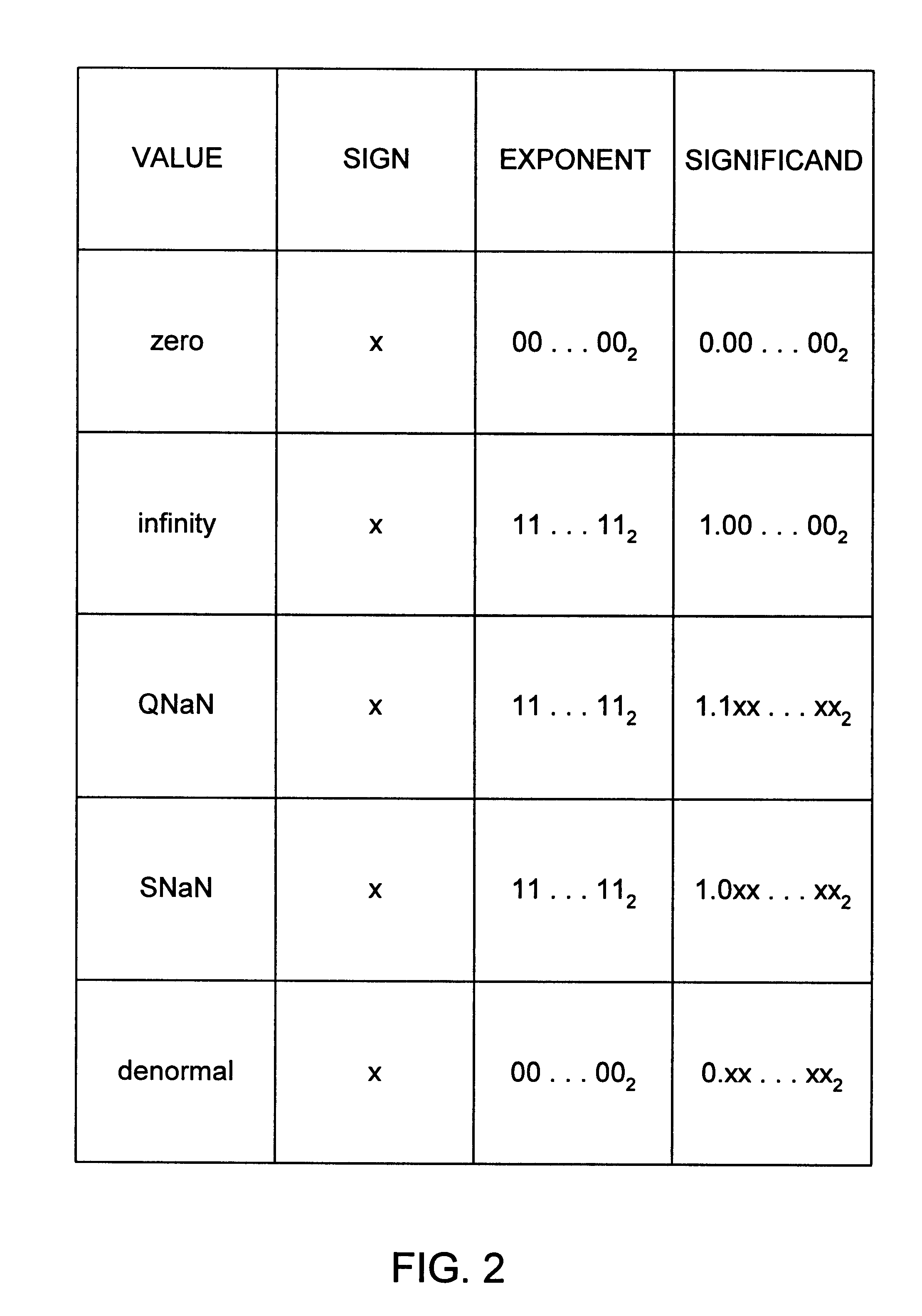
A multiplier configured to perform multiplication of both scalar floating point values (XxY) and packed floating point values (i.e., X1xY1 and X2xY2). In addition, the multiplier may be configured to calculate XxY-Z. The multiplier comprises selection logic for selecting source operands, a partial product generator, an adder tree, and two or more adders configured to sum the results from the adder tree to achieve a final result. The multiplier may also be configured to perform iterative multiplication operations to implement such arithmetical operations such as division and square root. The multiplier may be configured to generate two versions of the final result, one assuming there is an overflow, and another assuming there is not an overflow. A computer system and method for performing multiplication are also disclosed.
Owner:ADVANCED SILICON TECH
Storing and restoring snapshots of a computer process
InactiveUS7383538B2Maintain abilitySoftware testing/debuggingSpecific program execution arrangementsMemory operationComputer program
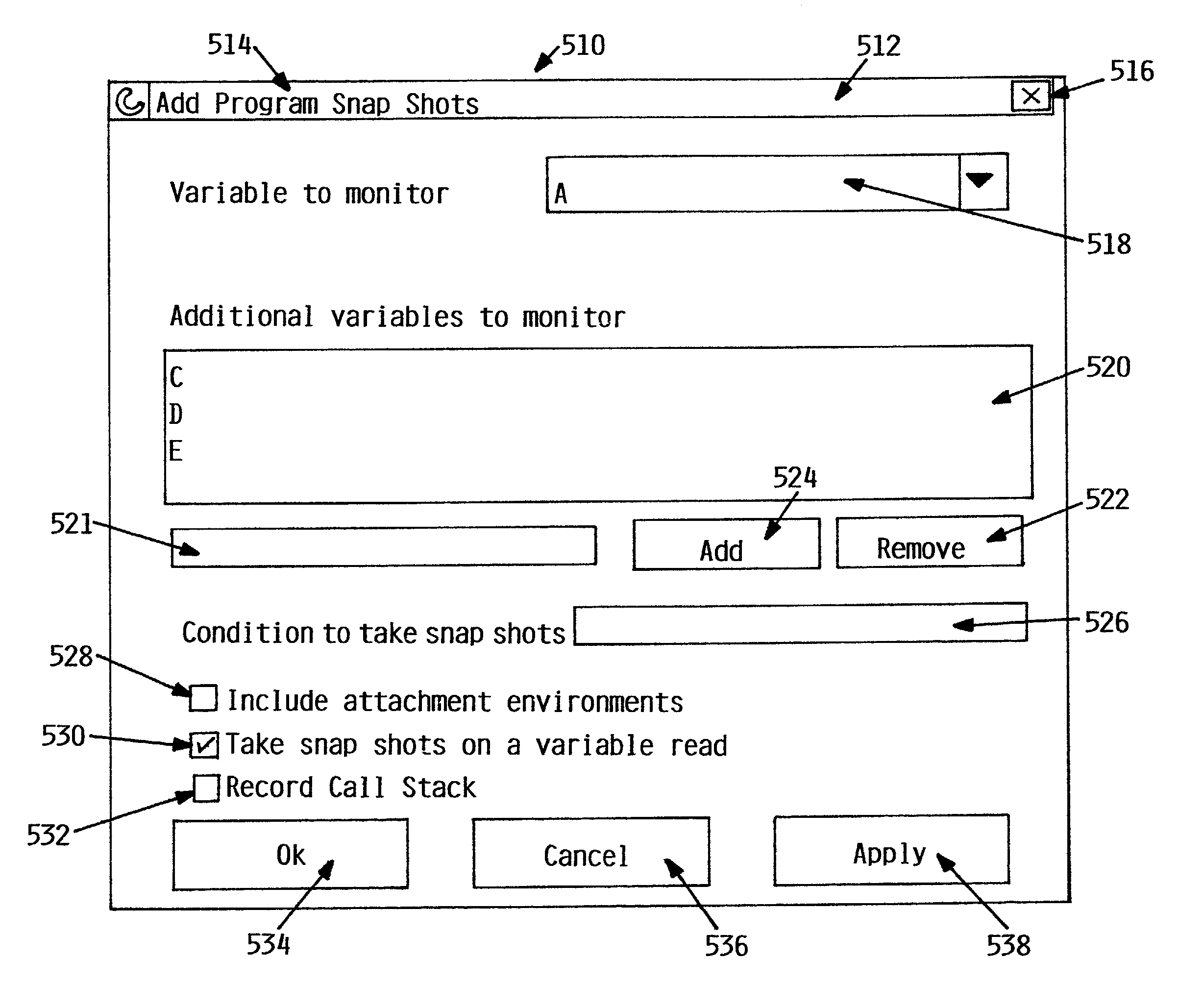
A method to trace a variable or other expression through a computer program is disclosed. A user determines the variable and the conditions upon which activity of the variable will be monitored. As a result of the invention, every time that variable is referenced in a memory operation or other activity by the program and the conditions set forth by the user are satisfied, the state of that variable is saved as a snapshot without interrupting or stopping execution of the program. The snapshots are accumulated in a history table. The history table can be retrieved and the state of the variable in any given snapshot can be restored. Other variables and expressions can be attached to the trigger variable and the states of these other variables at the time of the activity of the trigger variable may also be saved in the snapshot. The method may be incorporated into a program as a tracing device or a program product separate from the logical processing device executing the program.
Owner:IBM CORP
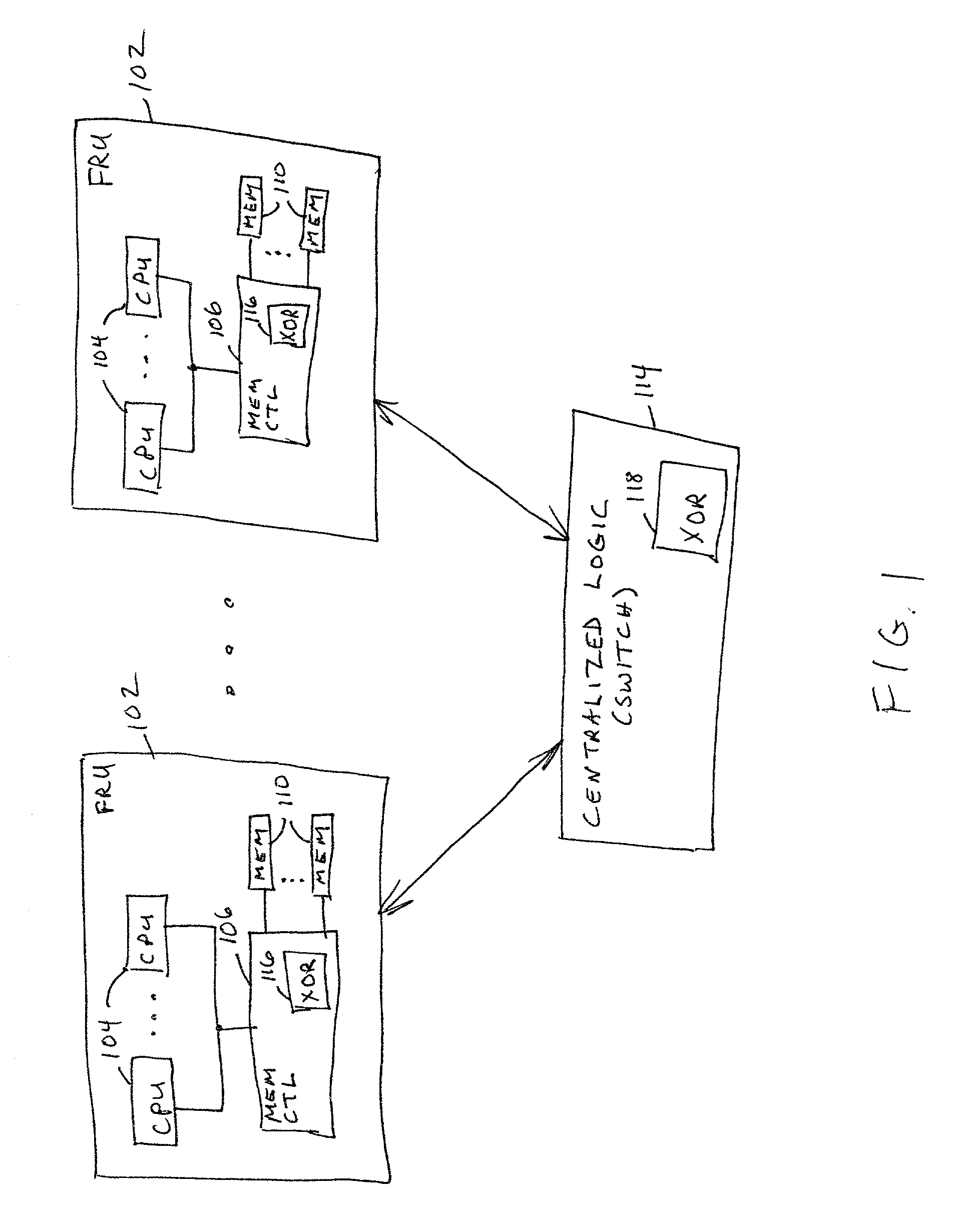
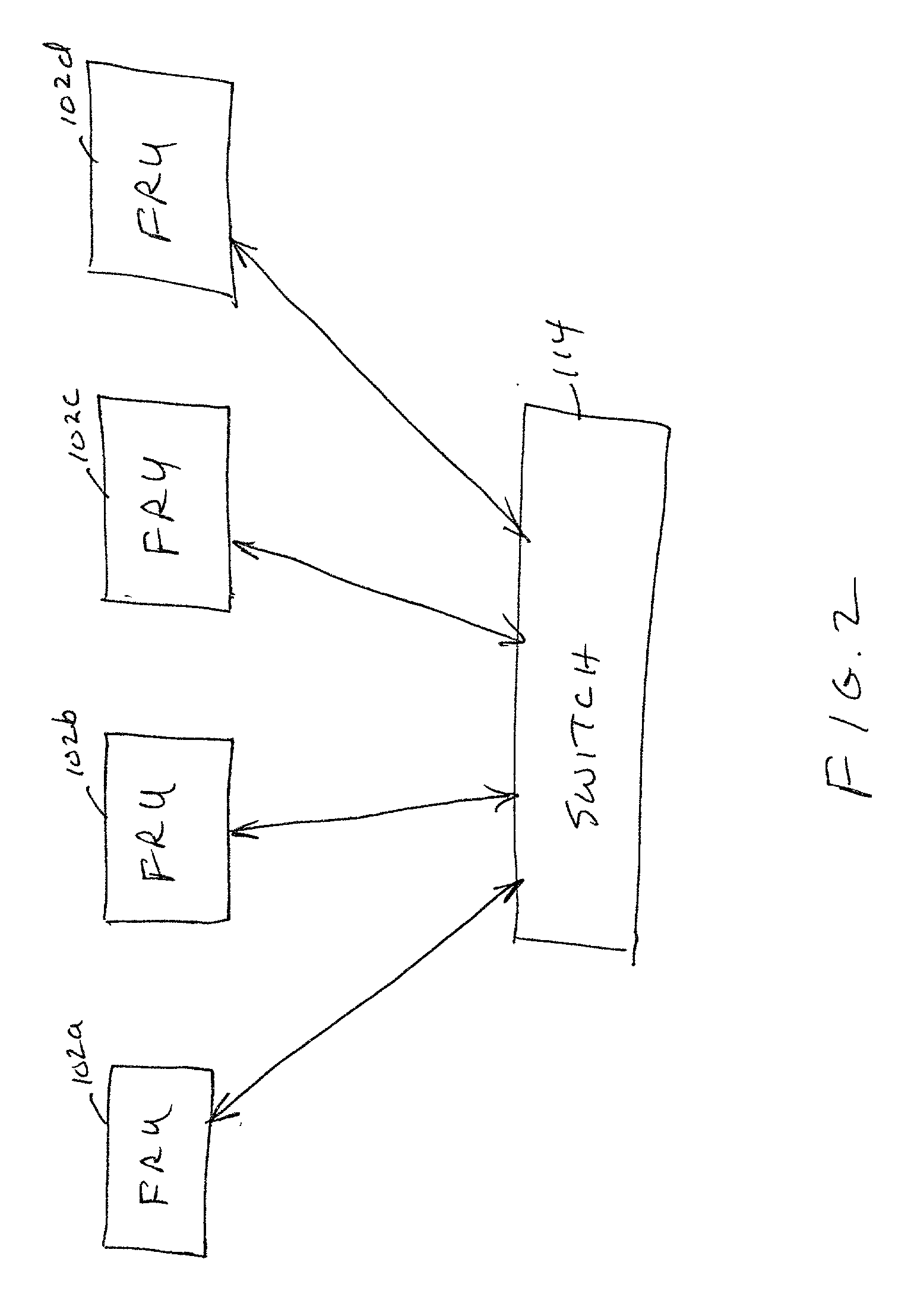
Data redundancy in a hot pluggable, large symmetric multi-processor system
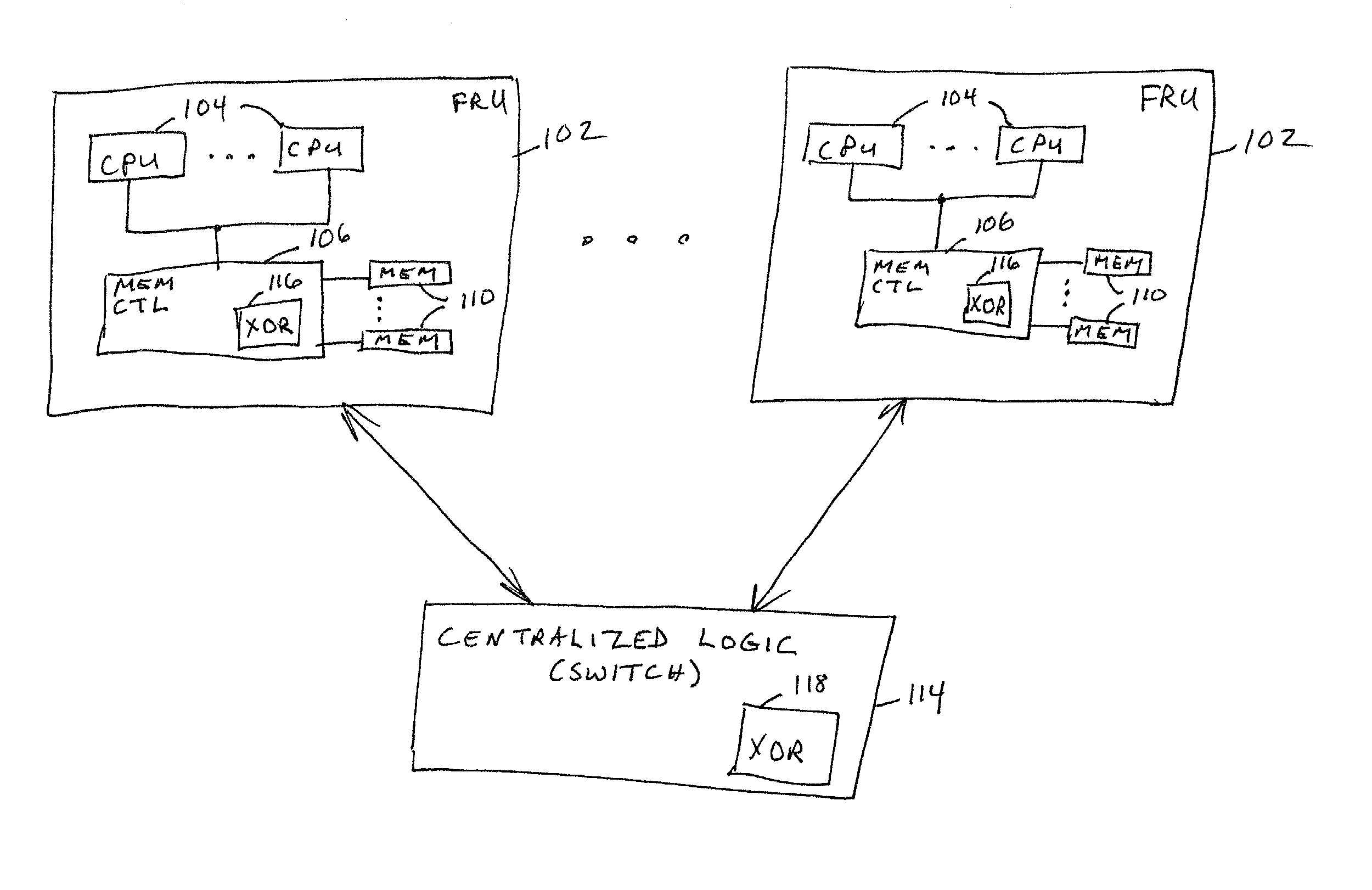
ActiveUS20030172330A1Fault toleranceReduce the numberStatic storageRedundant data error correctionFault toleranceRAID
A computer system includes a plurality of field replaceable units, each having volatile memory and at least one CPU. The FRUs communicate with each other via centralized logic. A RAID data fault tolerance technique is applied to the system so that an FRU can be lost or removed without loss of its data. An exclusive OR engine is included in the centralized logic or distributed among the FRUs. The RAID logic can restripe itself upon removal or addition of a FRU.
Owner:CONVERSANT INTPROP MANAGEMENT INC
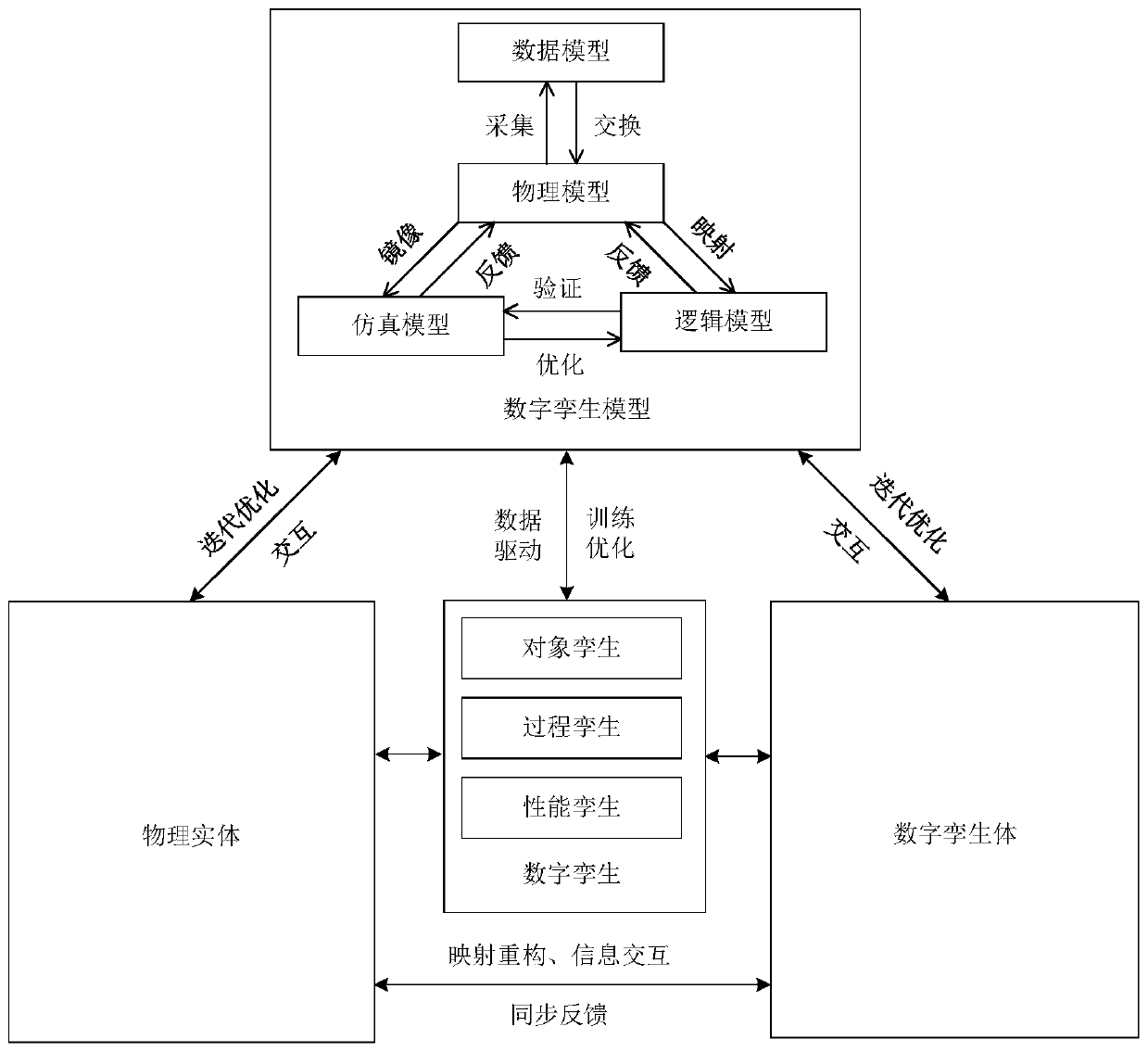
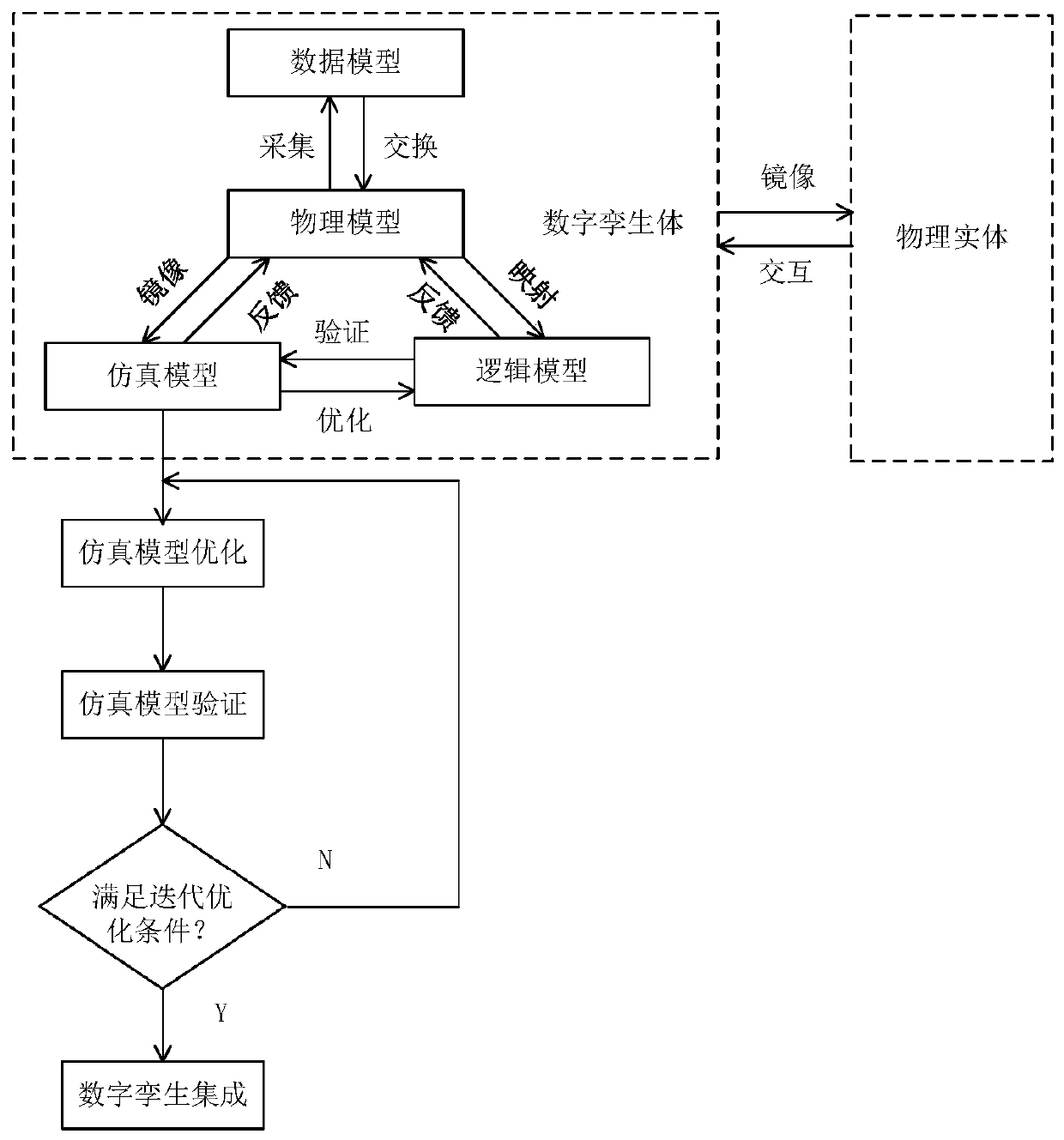
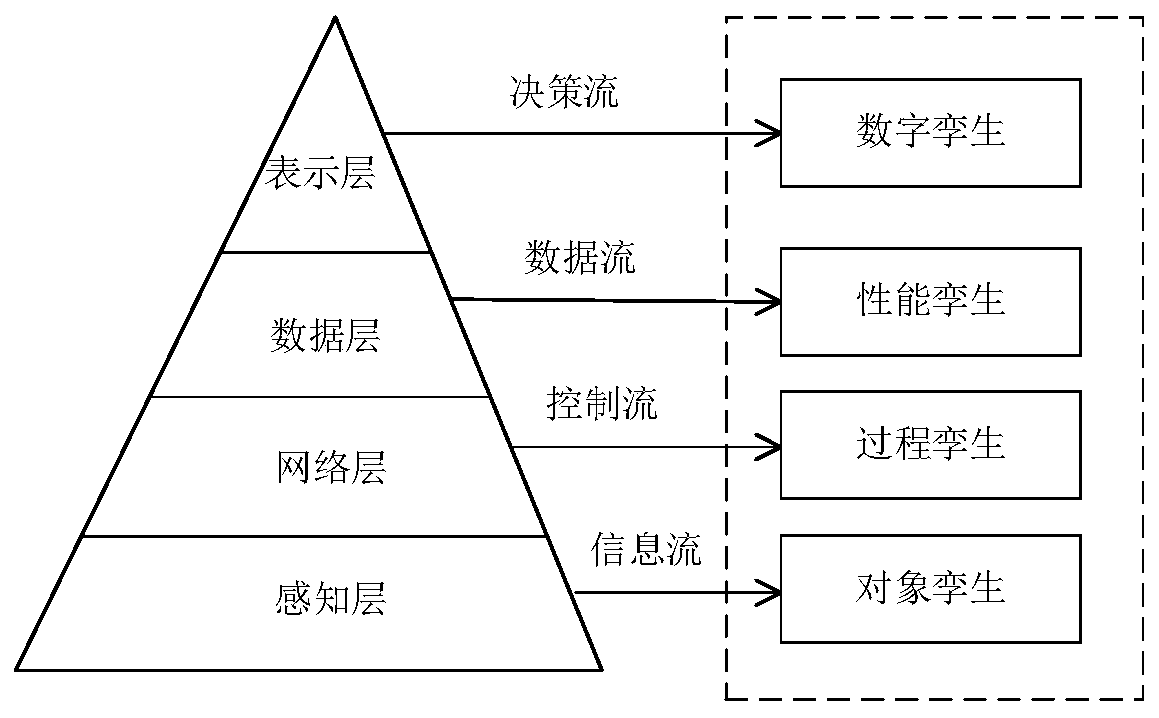
Mine digital twinning model and construction method thereof
The invention discloses a mine digital twinning model and a construction method thereof. The digital twinning model is formed by mutual coupling and evolution integration of a physical model, a logicmodel, a simulation model and a data model, and the construction method comprises the following steps: (1) constructing a physical model; (2) representing a logic model; (3) establishing a simulationmodel; (4) optimizing a simulation model; (5) verifying the simulation model; (6) constructing a data model; (7) performing digital twin representation. The method is based on a machine vision and deep learning algorithm, and by constructing a digital twinning model, object twinning, process twinning and performance twinning of a physical space physical entity and a virtual space digital twinningbody, and data mirroring and information interaction between the digital twinning body and the physical entity are realized; through a digital twinning model and a construction method thereof, remotevisual monitoring of a physical space mine scene, intelligent perception, real-time monitoring, accurate positioning and health prediction of the mine scene are realized in a virtual space mine scene.
Owner:CHINA UNIV OF MINING & TECH (BEIJING)
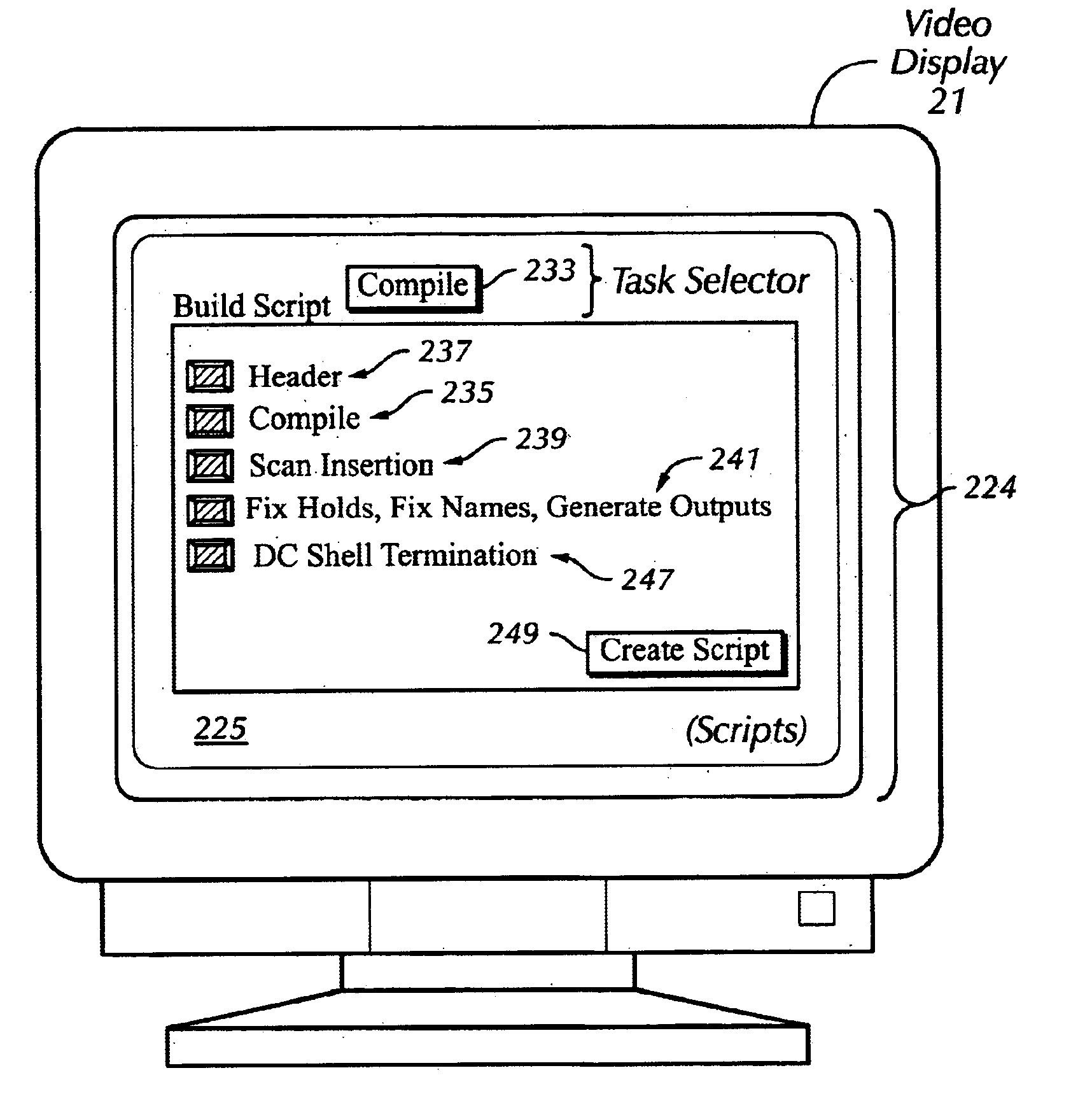
Methodology and graphical user interface for building logic synthesis command scripts using micro-templates
InactiveUS6697880B1Shorten the compositing timeSoftware engineeringSpecific program execution arrangementsGraphicsGraphical user interface
A template for a logic synthesis command script is broken into smaller and functionally independent templates termed "micro-templates." Using micro-templates, logic synthesis time may be significantly reduced. Each micro-template may correspond to a particular synthesis operation and may be enabled or disabled. Where synthesis of a particular set of synthesis operations is desired, the micro-templates corresponding to those synthesis operations are enabled.
Owner:GLOBALFOUNDRIES INC
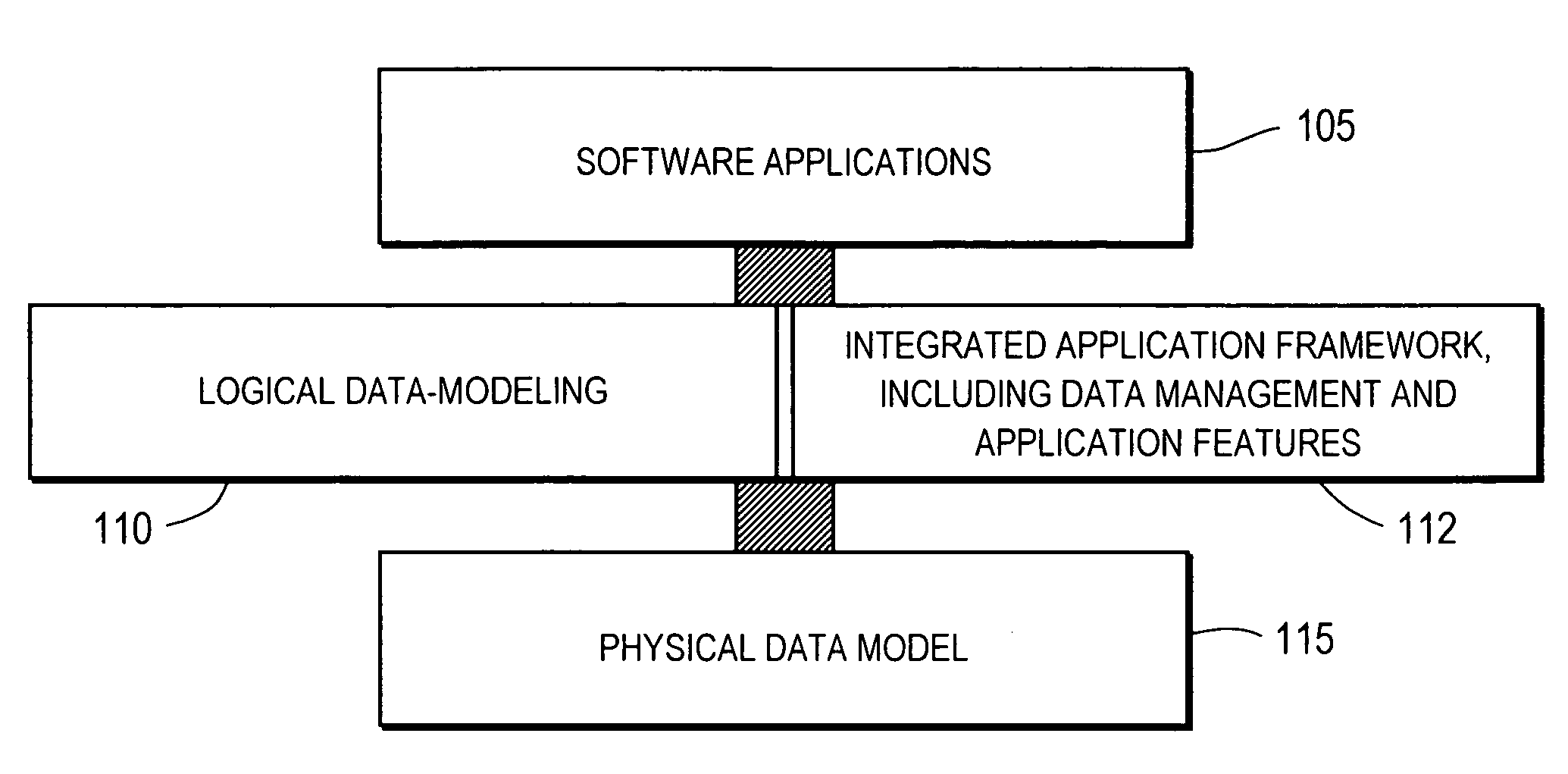
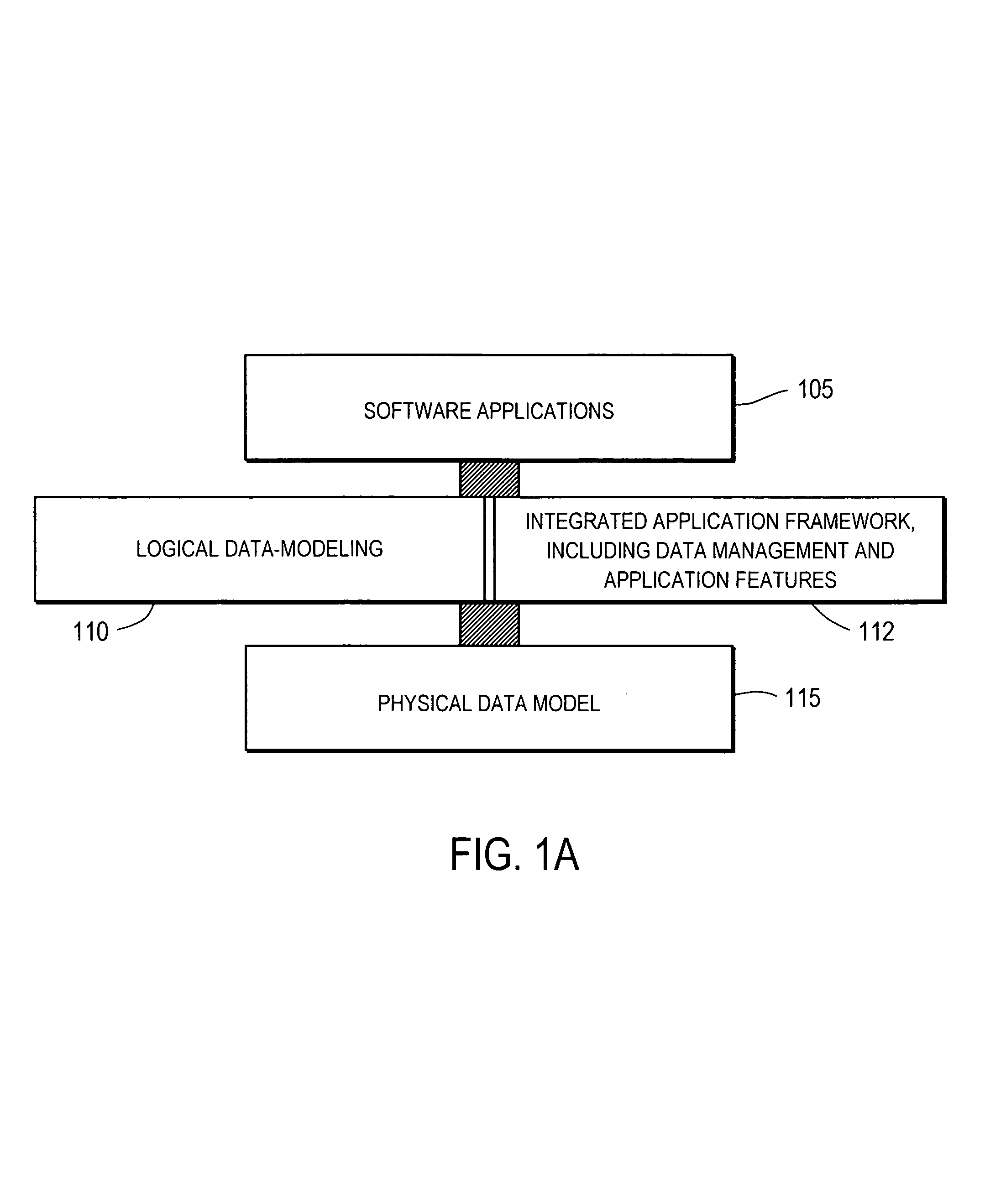
Logical data modeling and integrated application framework
ActiveUS7185317B2Visual/graphical programmingSpecific program execution arrangementsTheoretical computer scienceEngineering
A logical data model is defined using a data-modeling framework. The data-modeling framework enables a user to define the logical data model using a series of graphical user interfaces (GUI) or an application-programming interface (API). The data-modeling framework dynamically translates the logical data model into a corresponding physical data model. The logical data model can be changed using the GUI or API and the physical data model is automatically adjusted to accommodate the changes to the logical data model. The logical data model extends capabilities of the physical data model and automatically allows these capabilities to be available to software developers using an application framework integrated with the data-modeling framework. The application framework enables the developer to configure various application features and data management operations using GUI or API. The application framework is tightly coupled with the data-modeling framework such that changes in the logical data model is automatically reflected in the applications.
Owner:THOMSON REUTERS ENTERPRISE CENT GMBH
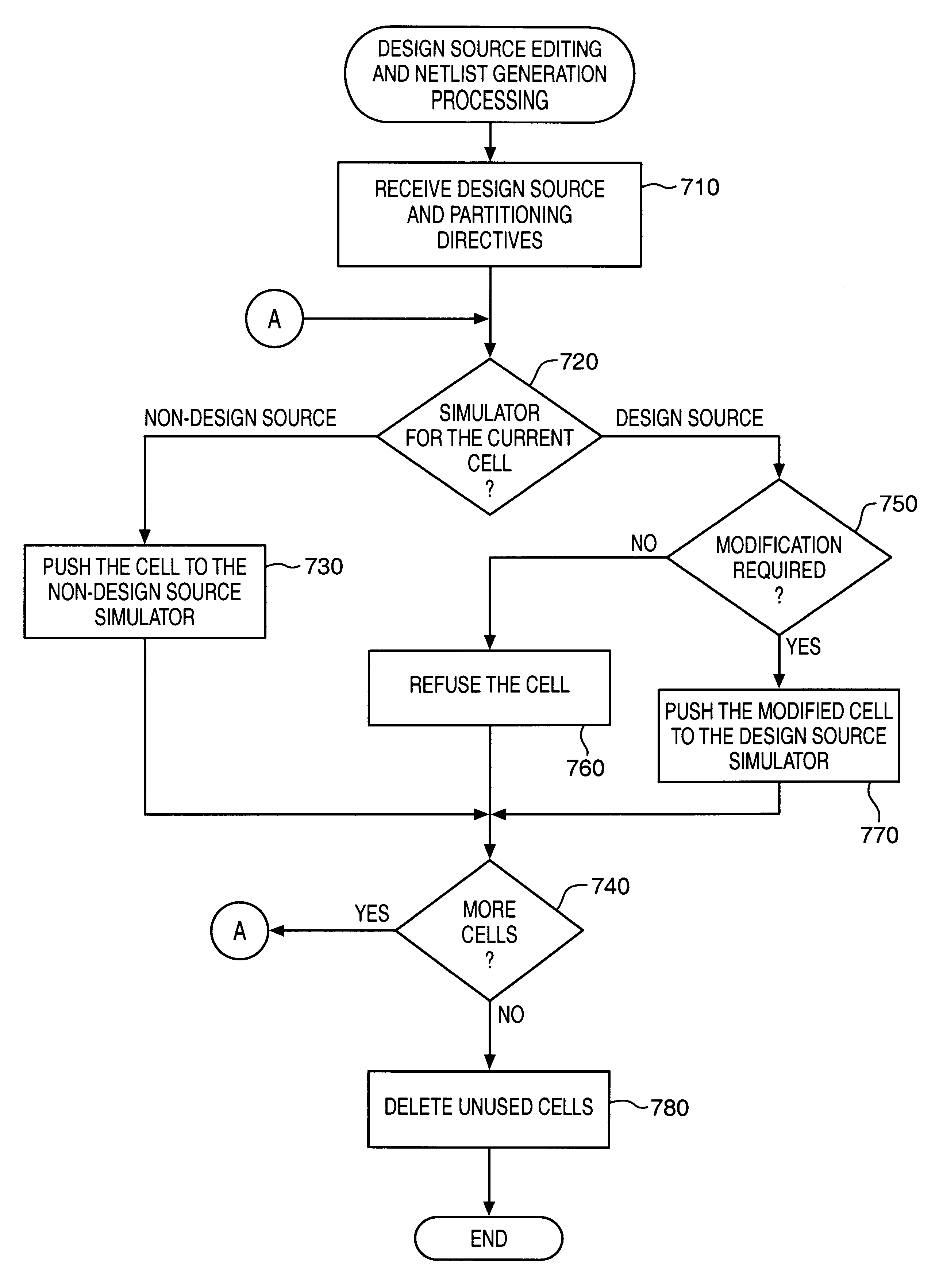
Automated design partitioning
InactiveUS6339836B1Detecting faulty computer hardwareCAD circuit designTheoretical computer scienceNetlist
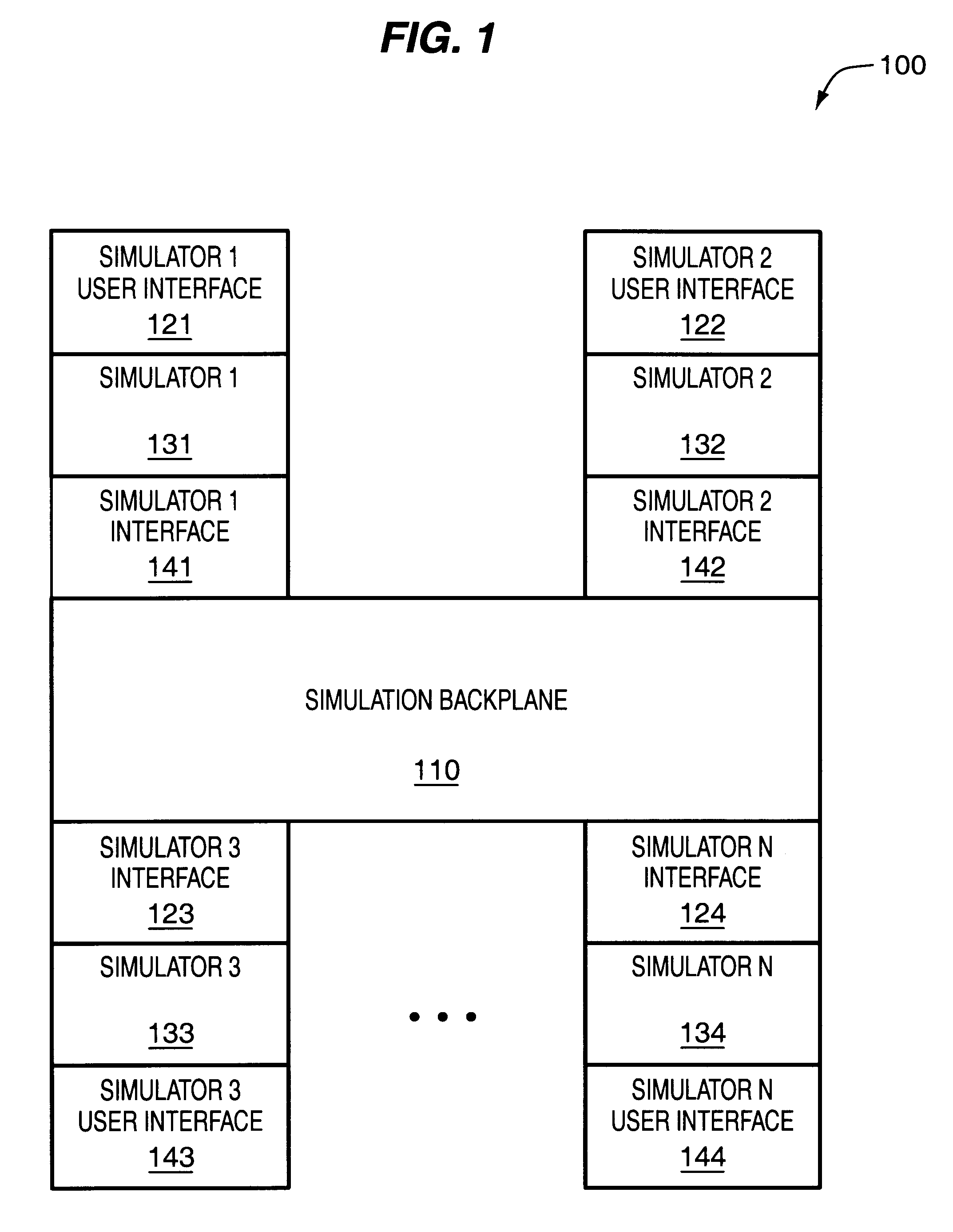
A flexible and extensible automated design partitioning mechanism that facilitates simulation sessions employing two or more simulators is provided. A simulation backplane includes partitioning logic that identifies the design blocks of an overall design pertaining to each of a plurality of simulators. Once the partitions have been identified, nets that cross simulator boundaries (e.g., mixed nets) are determined and inter-simulator connectivity information is generated for the simulators. According to one aspect of the present invention, the partitioning logic is able to accomodate arbitrary (e.g., instance-based) partitioning. A design source expressed in a design representation upon which a first simulator may operate is received. Design blocks to be partitioned to each of a plurality of solvers are identified based upon one or more partitioning directives and the design source. A first instance of a cell is assigned to a first solver and a second instance of the cell is assigned to a second solver. Netlist like information is generated for those of the design blocks that are partitioned to a non-design source solver. To accomodate a folded representation of a design block containing the first or second instance of the cell, one or more additional cells are created. According to another aspect of the present invention, name space mapping is retained across all simulators. A design source upon which a first simulator may operate is read. Based upon a set of rules, a primary partition that is to be simulated by a first solver is identified. The primary partition includes a top cell of the design representation. Additionally, a secondary partition that is to be simulated by a second solver is identified. Subsequently, netlist information is generated for the second solver while retaining name space mapping in the secondary partition by adding one or more levels of hierarchy so as to include information about the top cell in the secondary partition.
Owner:MENTOR GRAPHICS CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com