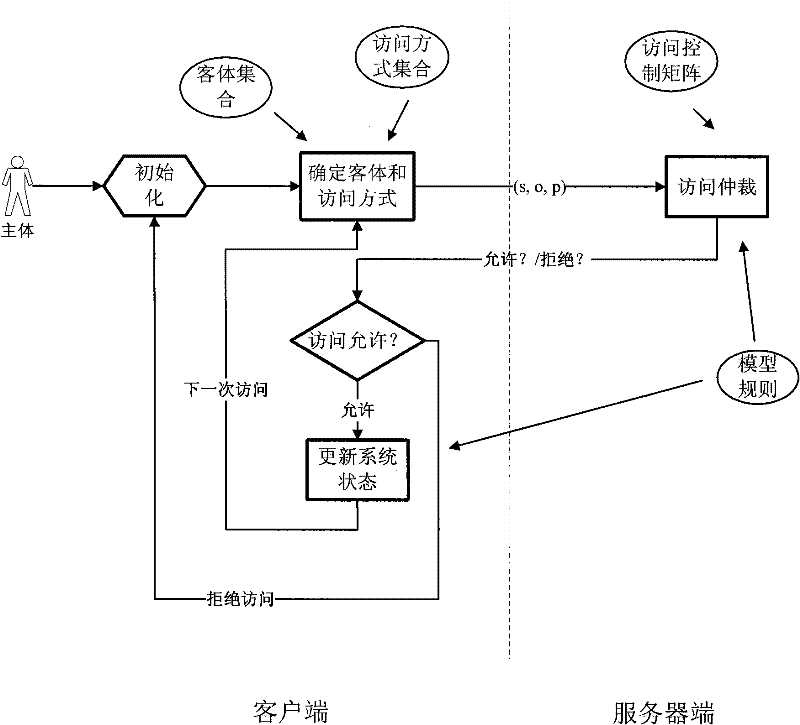
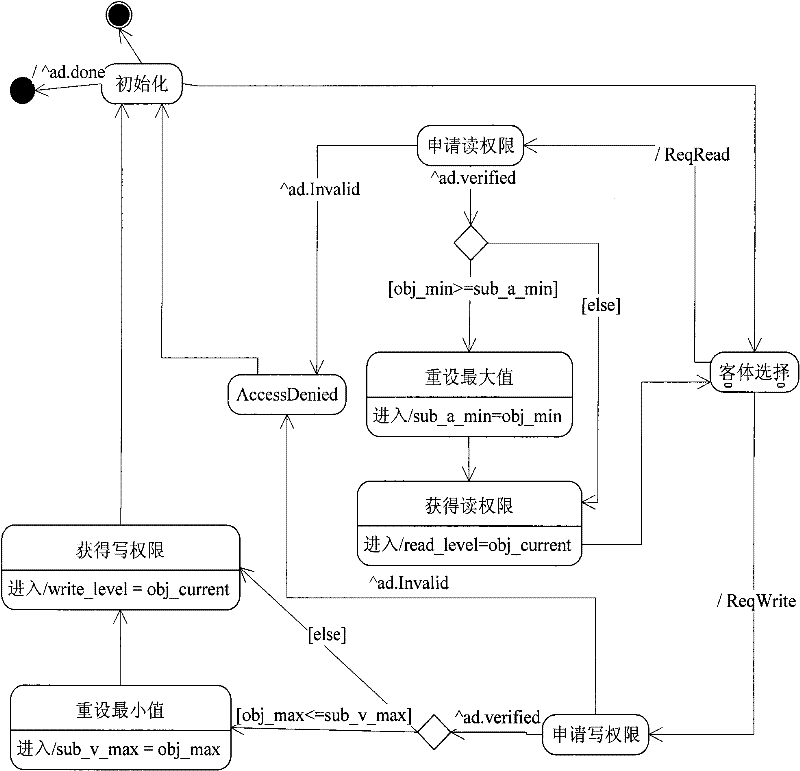
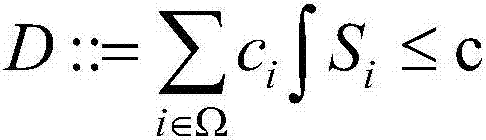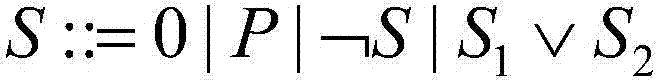Patents
Literature
60 results about "Logical formula" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System for Enterprise Knowledge Management and Automation
ActiveUS20080097748A1Easy to useDigital data information retrievalSemantic analysisFirst-order predicateSoftware design
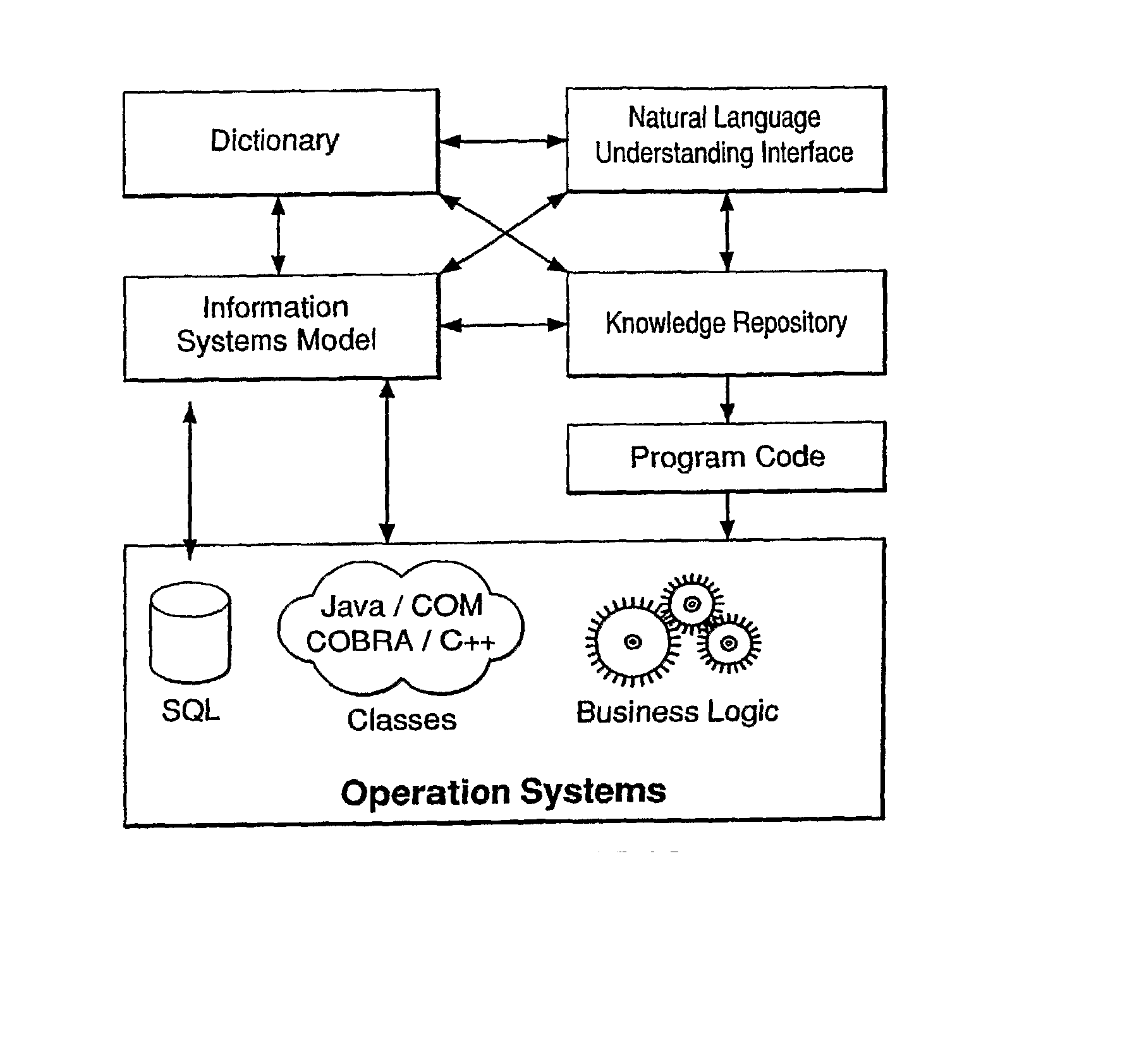
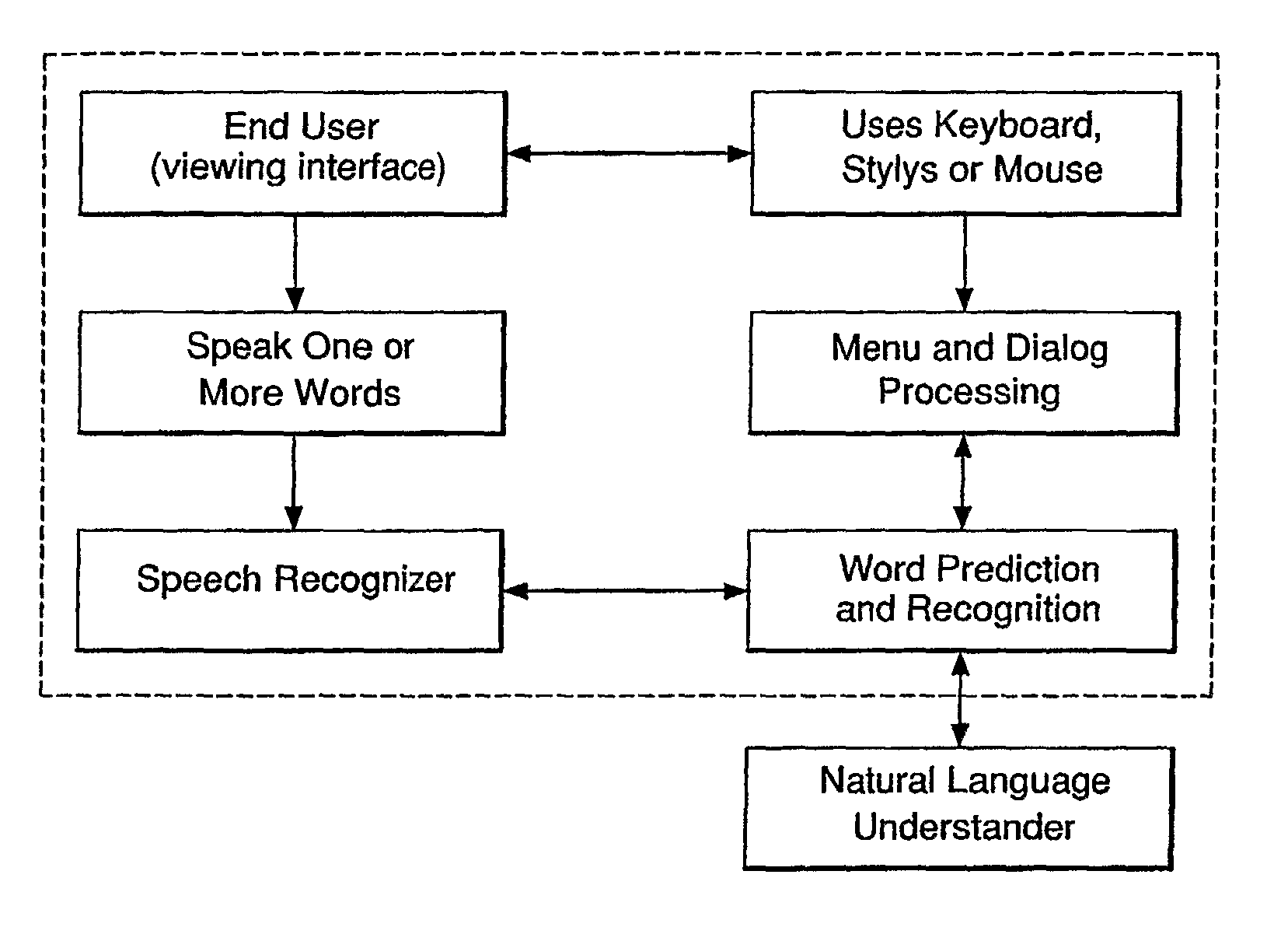
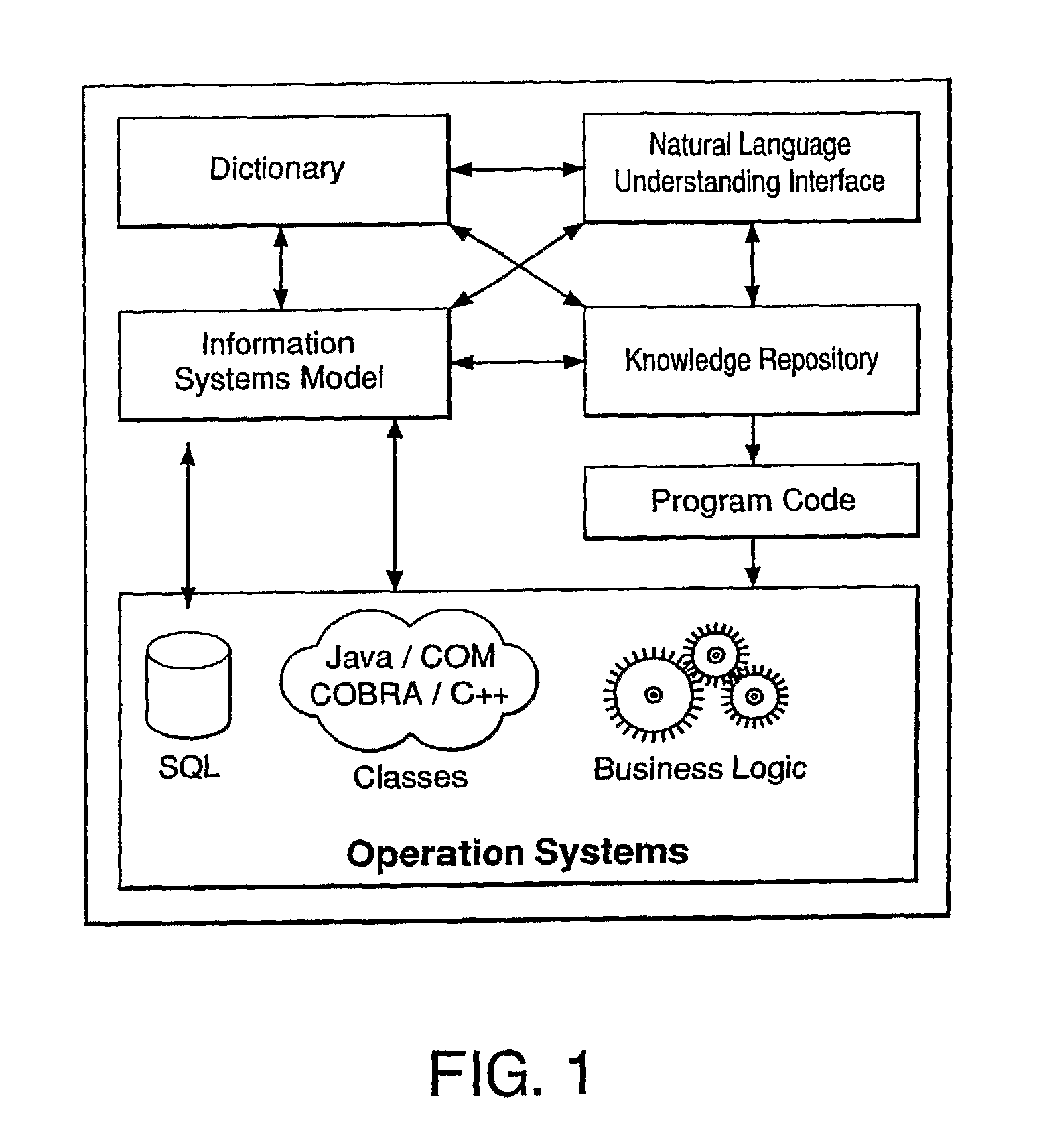
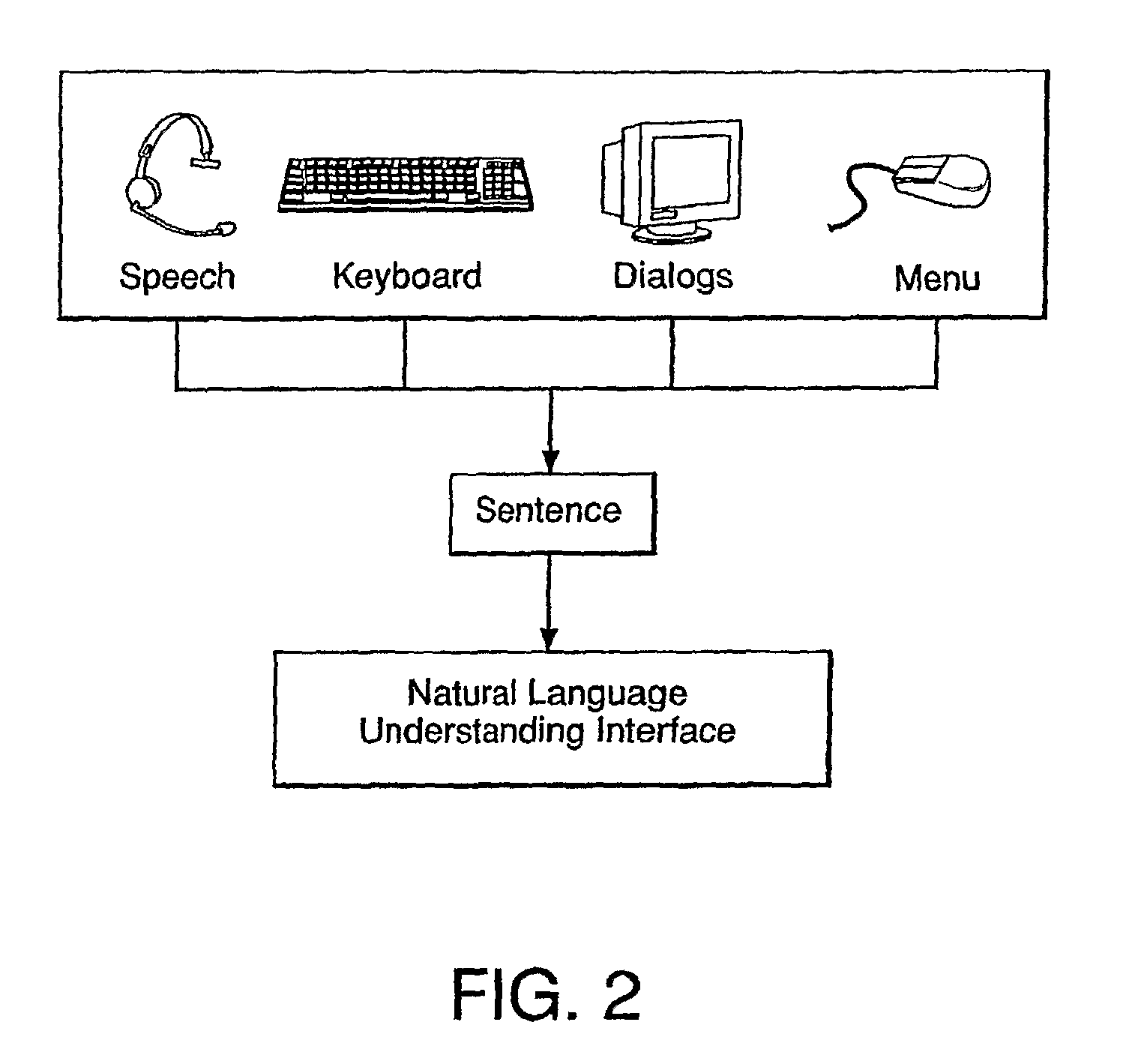
The present invention is directed to a system for managing business knowledge expressed as statements, preferably sentences using a vocabulary, where such statements may be automated by the generation of programming language source code or computer program instructions. As such, the present invention also manages software design specifications that define, describe, or constrain the programming code it generates or programs with which it or the code it generates is to integrate. The present invention facilitates the creation of composite sentences. In one embodiment, the present invention also interprets a composite sentence as a logical formula in first order predicate calculus or similar logic formalism supporting conjunction, disjunction, and negation as well as existentially and universally quantified variables. The invention further interprets natural language, including singular common count noun phrases and connectives, as variables in formal logic. Further, the invention then implements the logical interpretations as rules.
Owner:ORACLE INT CORP
Systems, methods and apparatus for distributed decision processing
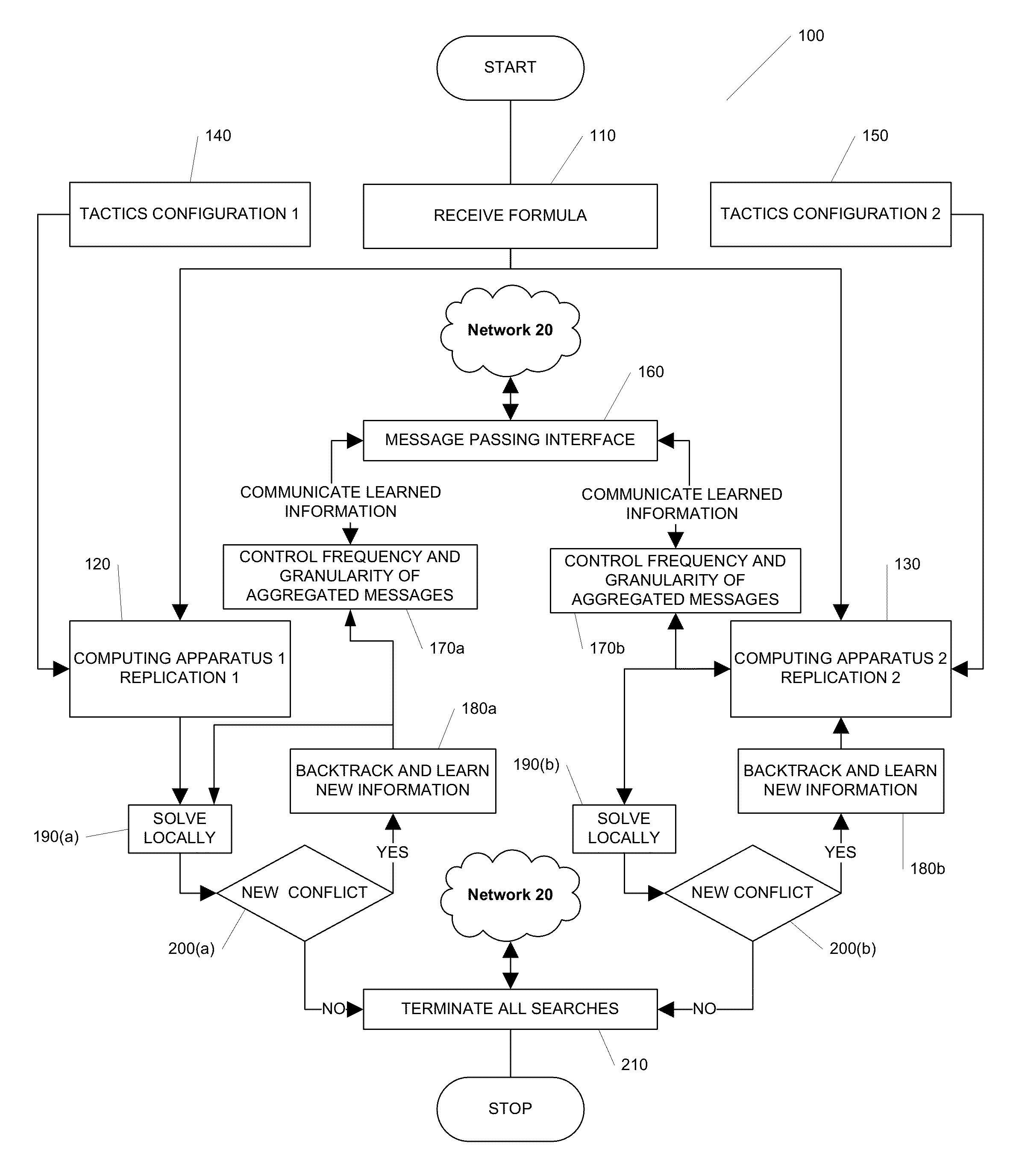
Methods, apparatus, and computer software product for making a decision based on the semantics of formal logic are provided. In an exemplary embodiment, two custom computing apparatuses are used to resolve the satisfiability of a logical formula and provide an example. In this embodiment, the two custom computing apparatuses operate in concert to explore the space of possible satisfying examples. This Abstract is provided for the sole purpose of complying with the Abstract requirement rules. This Abstract is submitted with the explicit understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:QUALCOMM TECHNOLOGIES INC
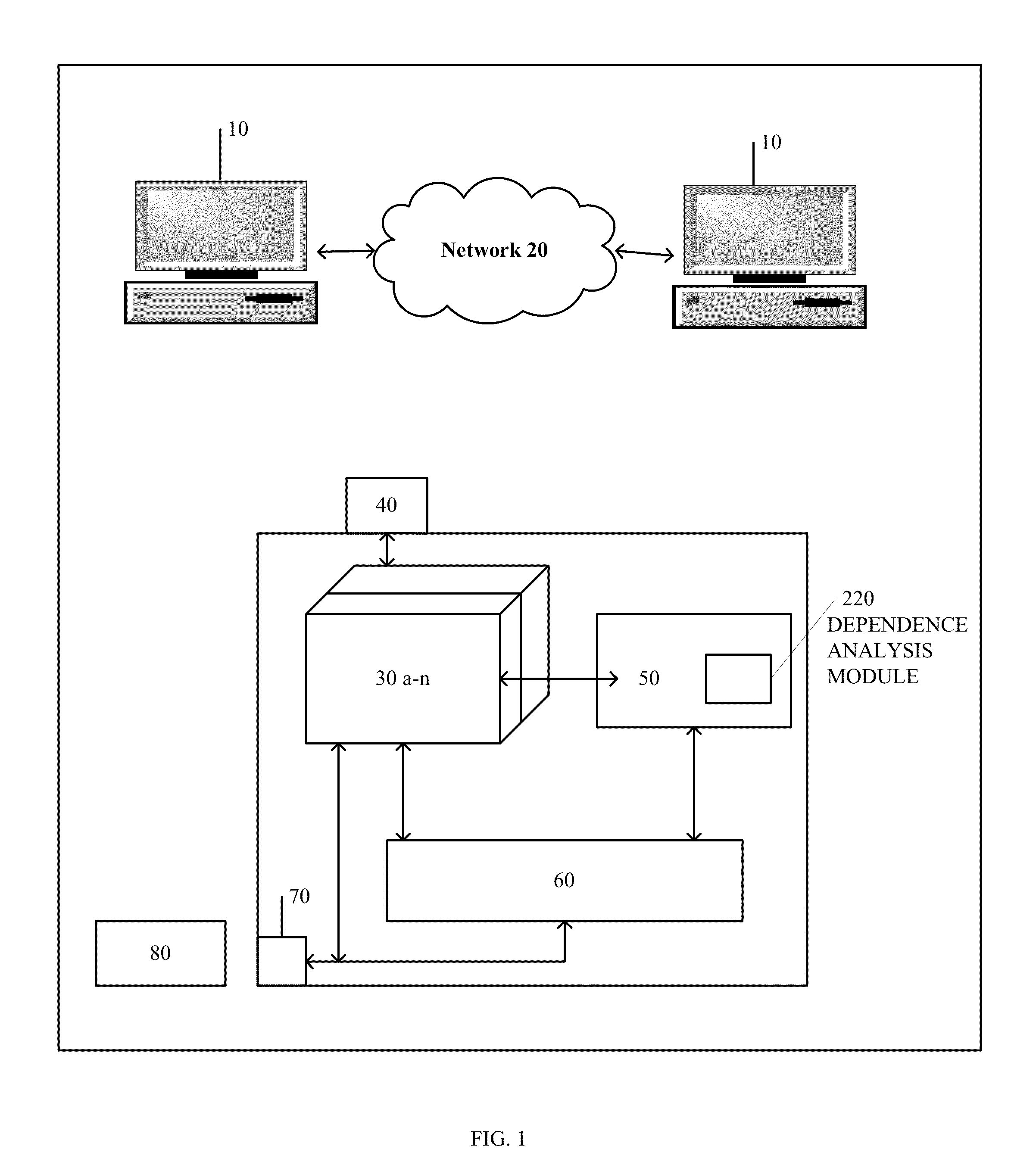
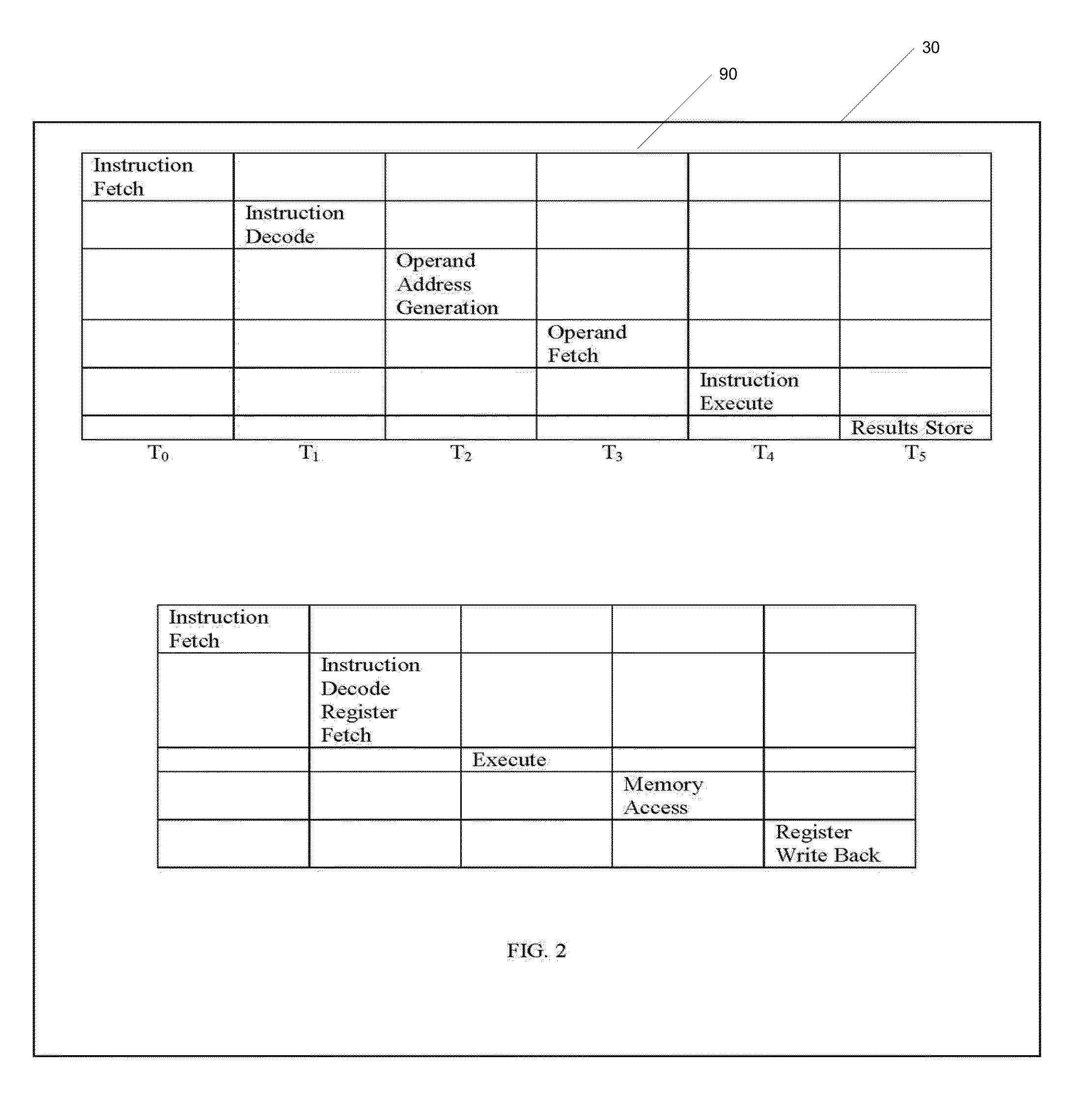
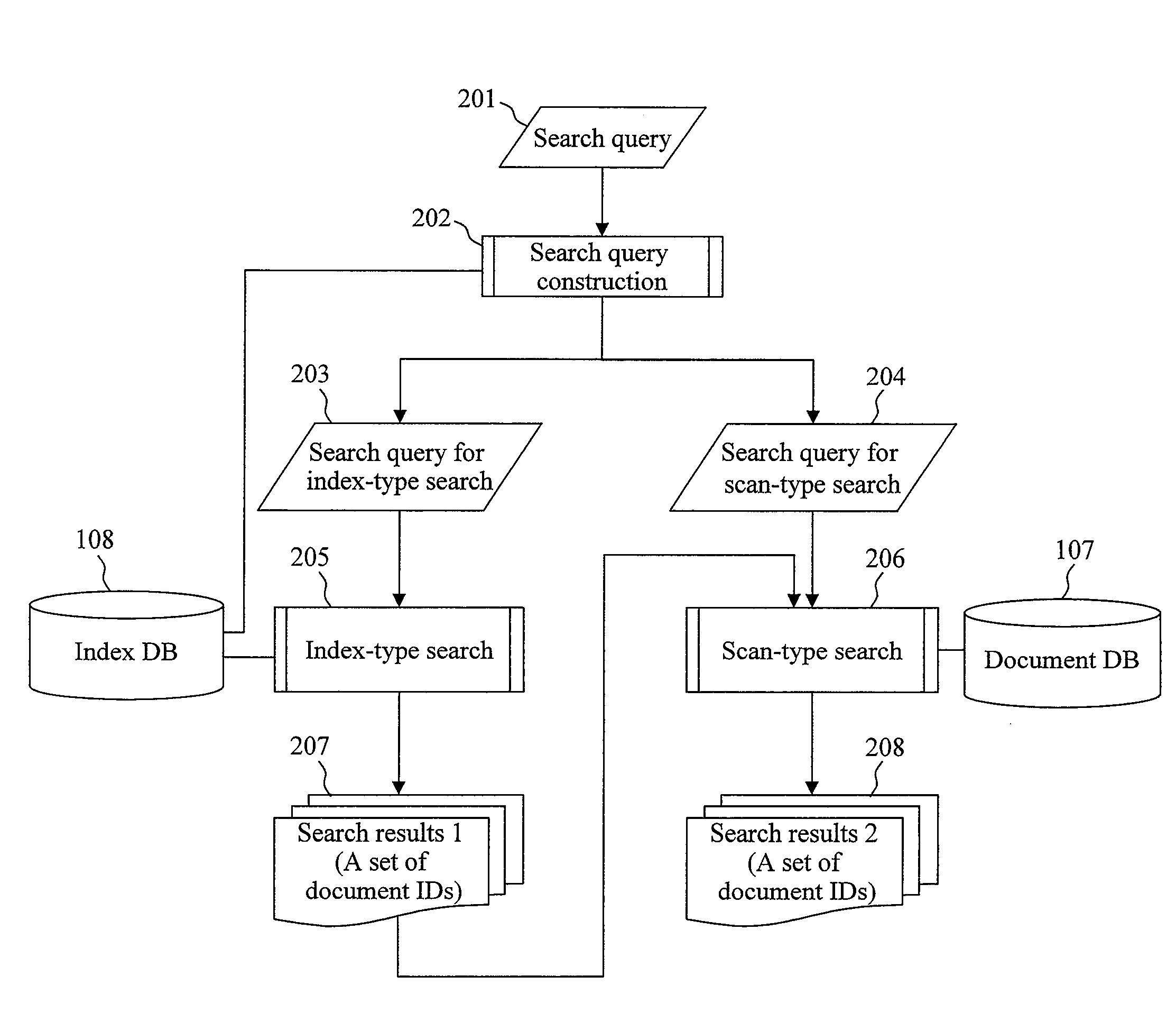
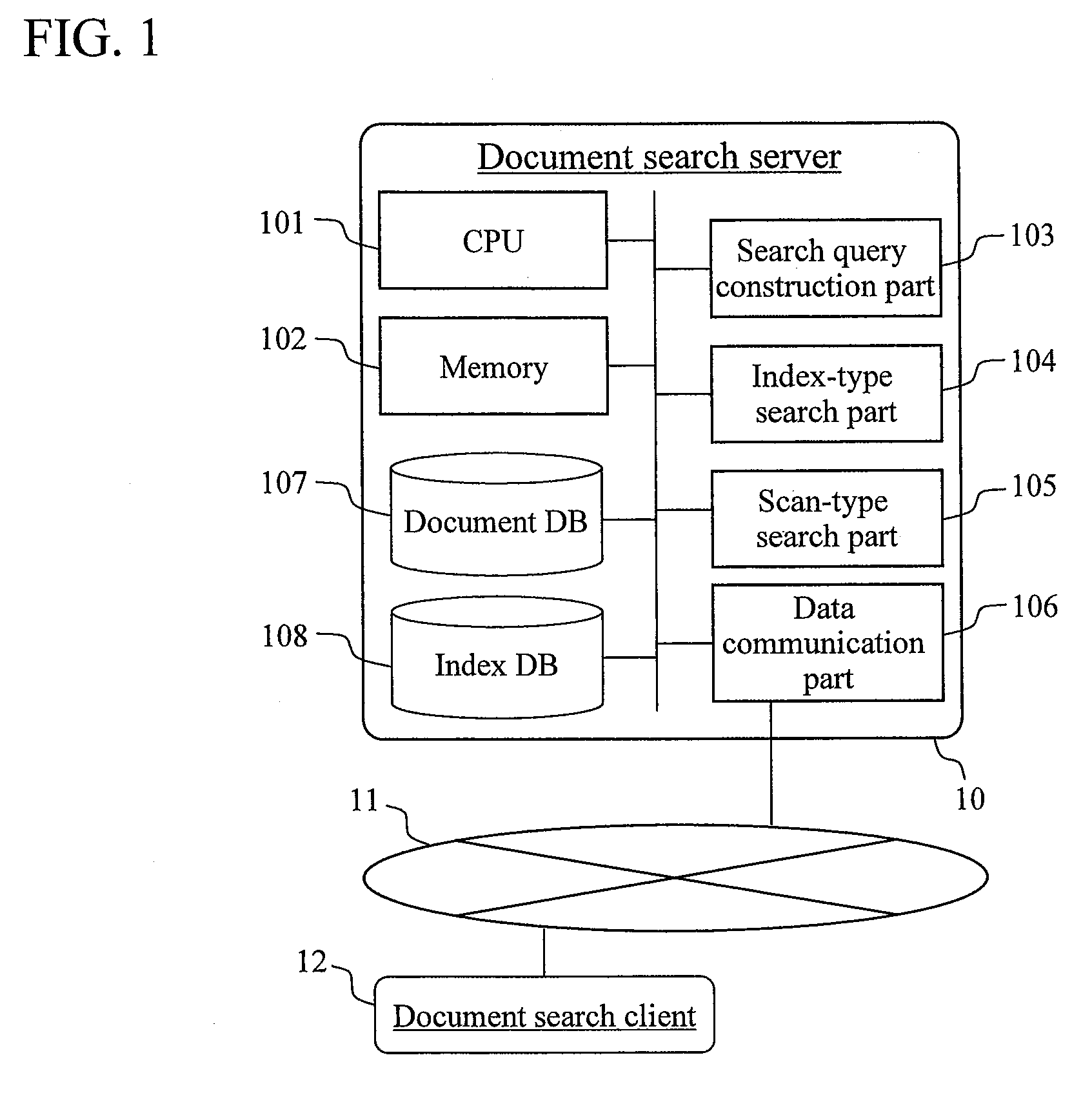
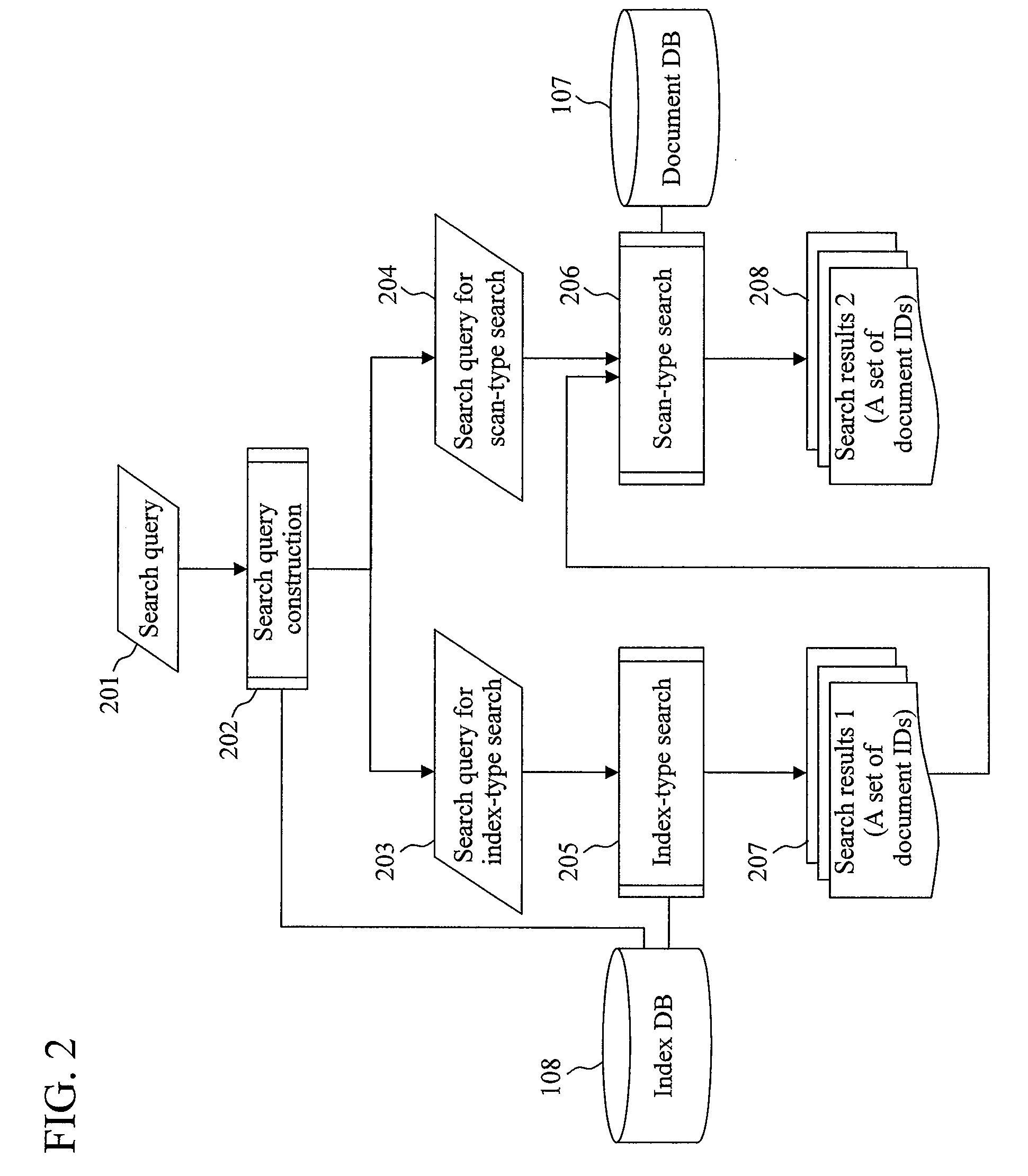
Document search method
InactiveUS20080306919A1Increase speedGood effectDigital data information retrievalDigital data processing detailsGramWeb search query
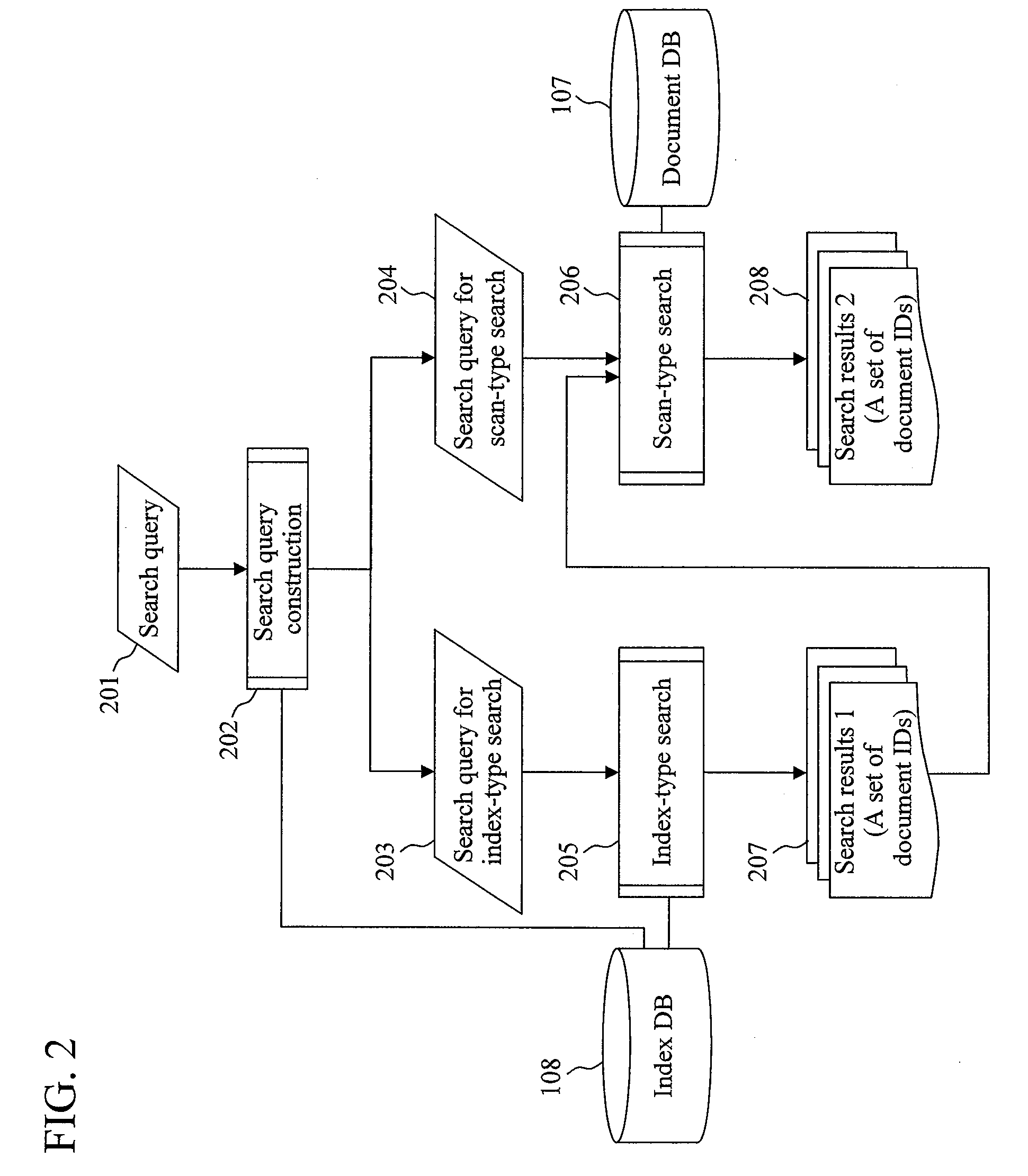
A document search apparatus capable of an index-type search and a scan-type search performs a search in a combination of the two search types while compensating for the disadvantages of the two search types with each other. A search query for index-type search and a search query for scan-type search are constructed based on a search query consisting of a logical formula of keywords. Then, a character 2-gram for performing an index search is set to shorten the whole search time, and the index-type search is performed. Finally, a scan-type search is performed on this search result of the index-type search.
Owner:HITACHI LTD
Automated bid decision technique
InactiveUS7346571B1Large possible profitEasy constructionFinancePayment architectureDecision systemData memory
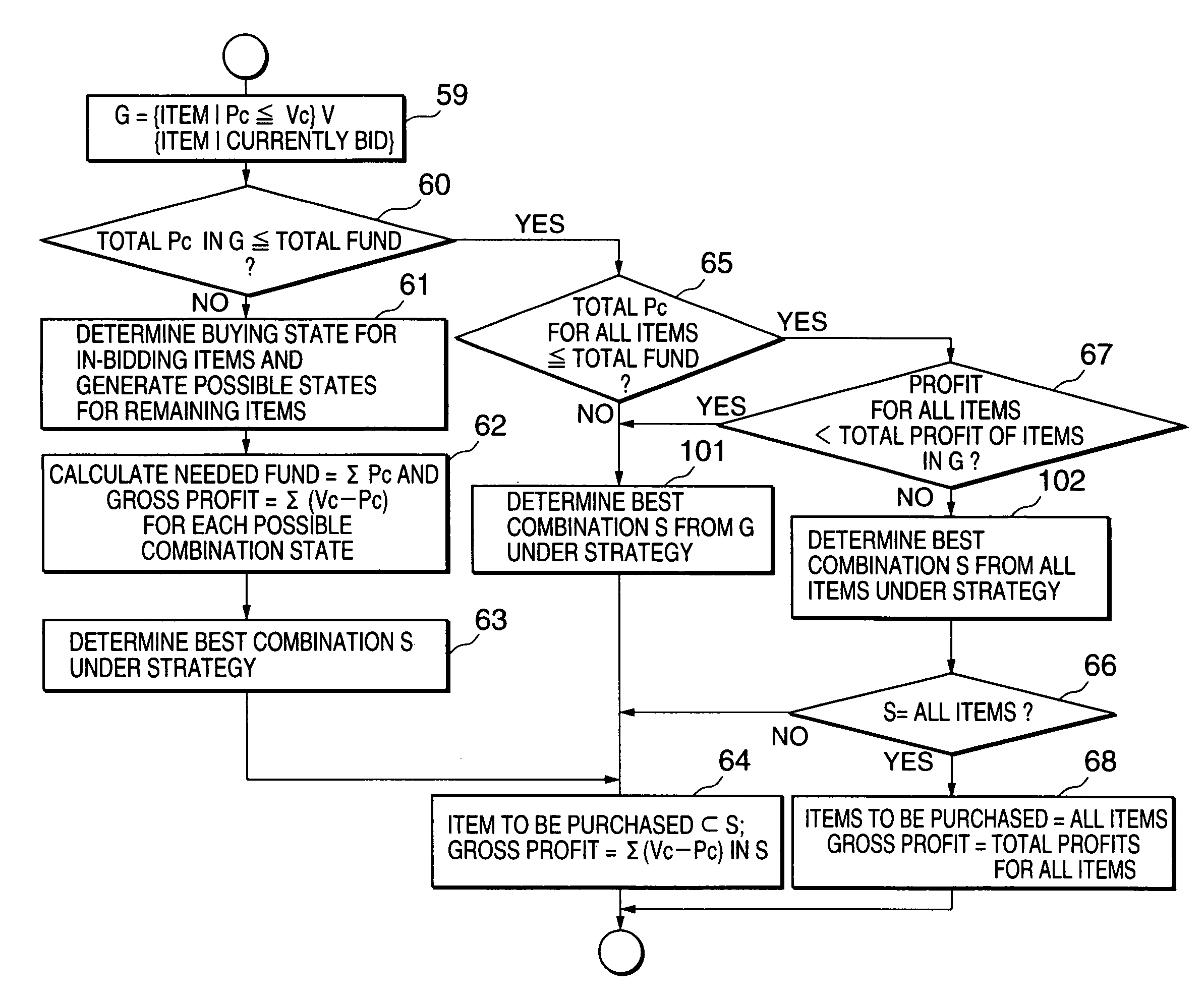
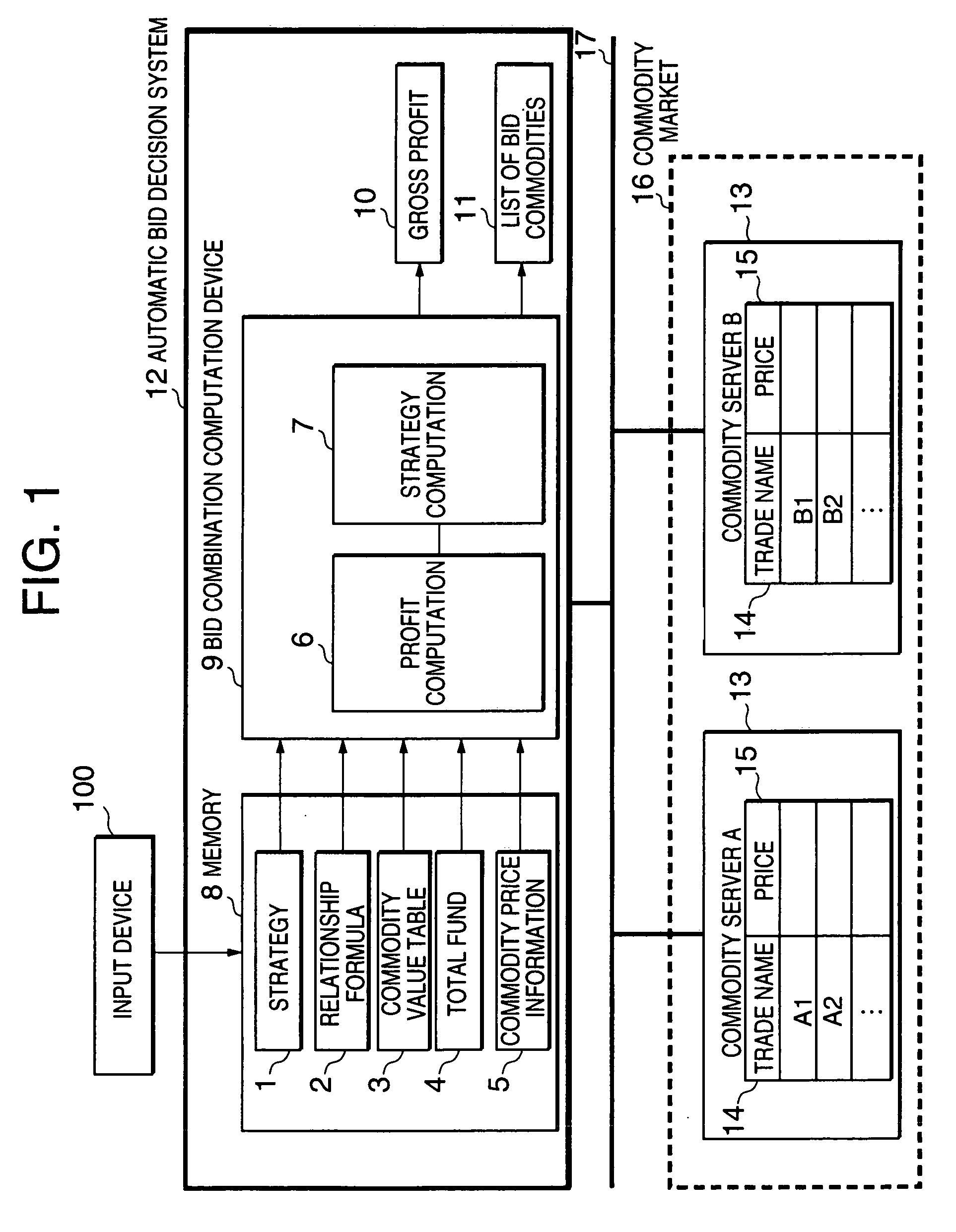
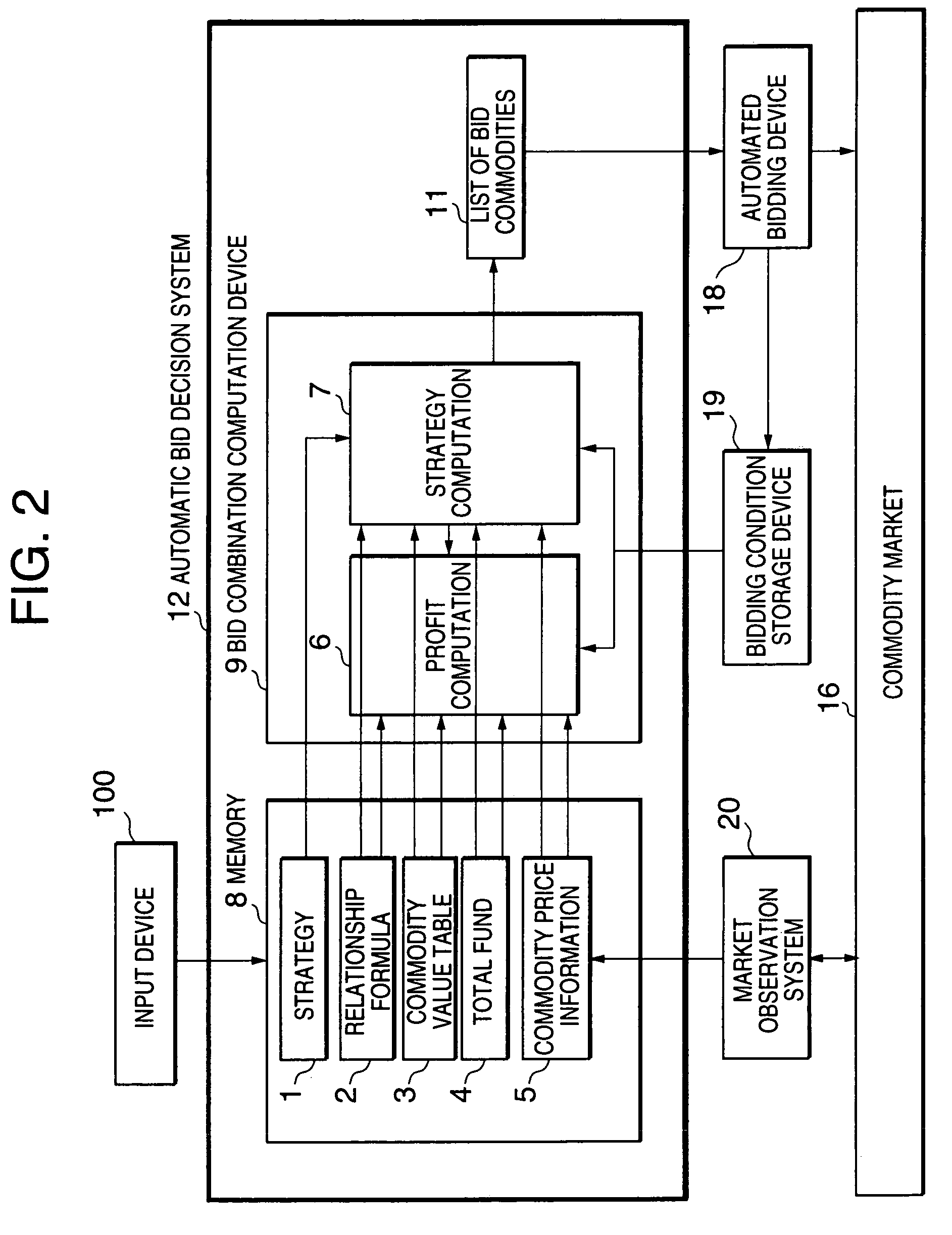
An automated bid decision system allowing a bidder to make a bidding for plural commodity items over a plurality of markets is disclosed. A data memory stores a logical formula representing a relationship among a plurality of bid items, a value table of the bid items, price information of the bid items in at least one market, a total purchasing fund, and a bidding strategy. A profit computation section computes a profit obtainable when at least one bid item arbitrary selected from the bid items is purchased, based on the value and the price information. A strategy computation section determines a list of bid items for which a bid should be made and a gross profit obtainable therefrom. A combination candidate is selected from the bid items based on the relationship formula and a possible profit obtainable from the selected combination candidate is computed. The final list of bid items are determined so as to maximize the possible profit within the total purchasing fund.
Owner:NEC CORP
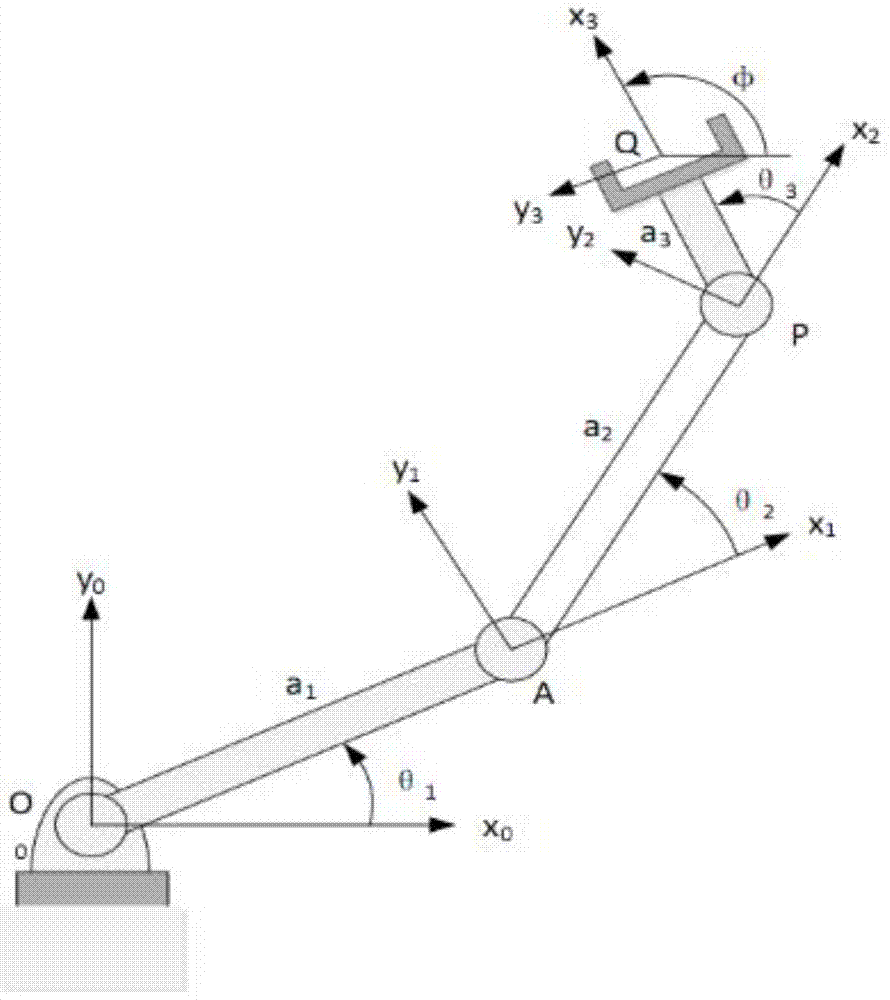
Mechanical arm kinematics formal analysis method
ActiveCN104772773AReduce difficultySimple form of expressionManipulatorHigher-order logicKinematic chain
The invention relates to a mechanical arm kinematics formal analysis method. The method comprises the steps of 1, determining structural parameters of a mechanical arm mechanism; 2, using high-order logical language for building a mechanical arm kinematics logical model; 3, using a logical formula for describing kinematics constraints or attributes needing to be verified; 4, enabling the mechanical arm mechanism kinematics logical model and the kinematics constraints or attributes needing to be verified to form a logical proposition; 5, utilizing a logical reasoning engine for proving whether the logical proposition is true or not; if the logical proposition is true, it represents that the model meets the kinematics constraints or have the attributes; if not, it represents that the model does not meet the kinematics constraints or does not have the attributes. According to formal verification, on the basis of system formal specifications or attributes, the correctness of the system is verified by using the mathematical method, and the verified attributes are precise and complete.
Owner:CAPITAL NORMAL UNIVERSITY
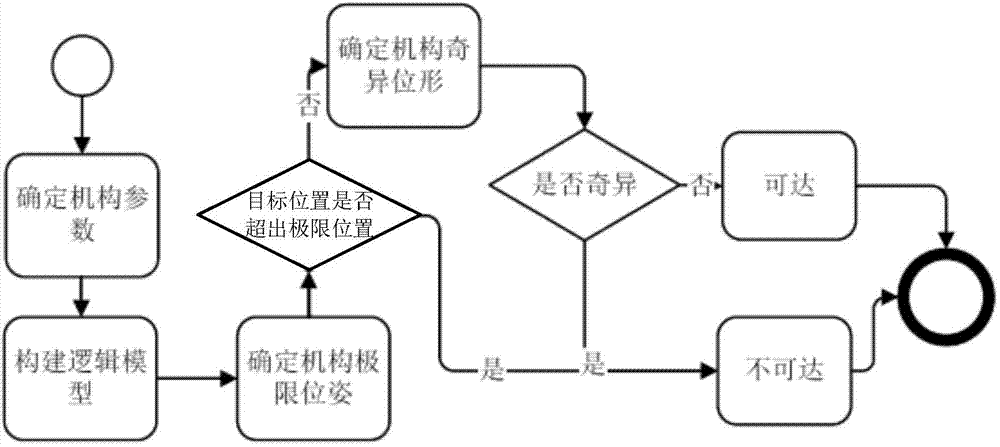
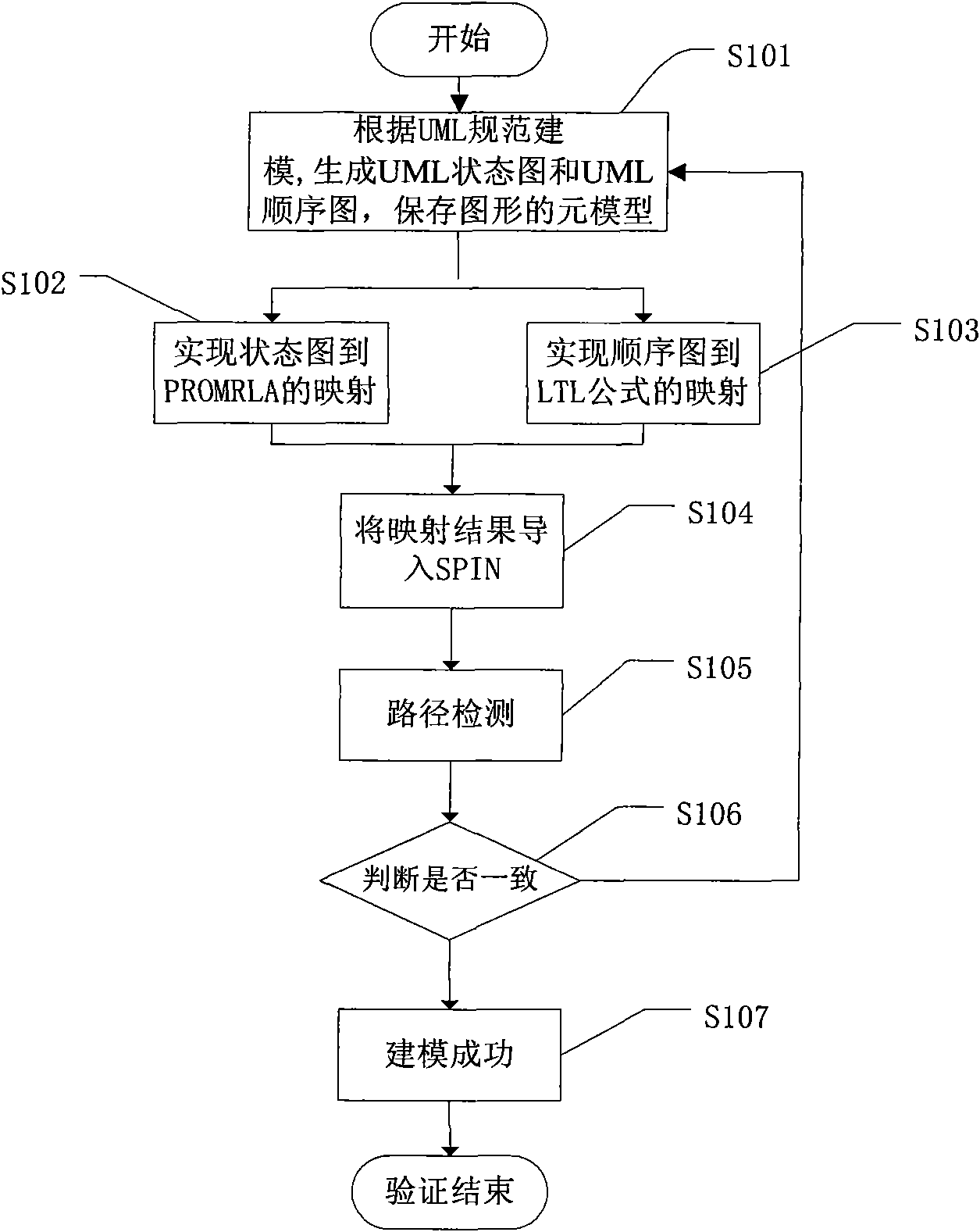
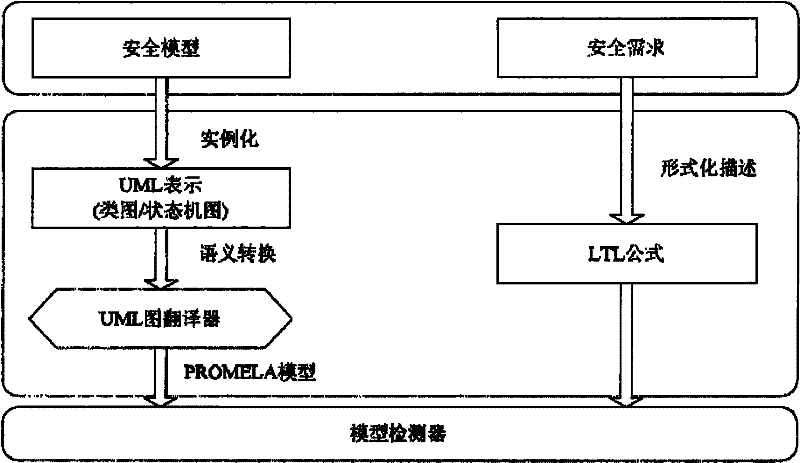
Method for verifying consistency of dynamic behavior in UML model and time-sequence contract
InactiveCN101673198AGuaranteed accuracyGuaranteed reusabilitySpecific program execution arrangementsGraphicsPromela
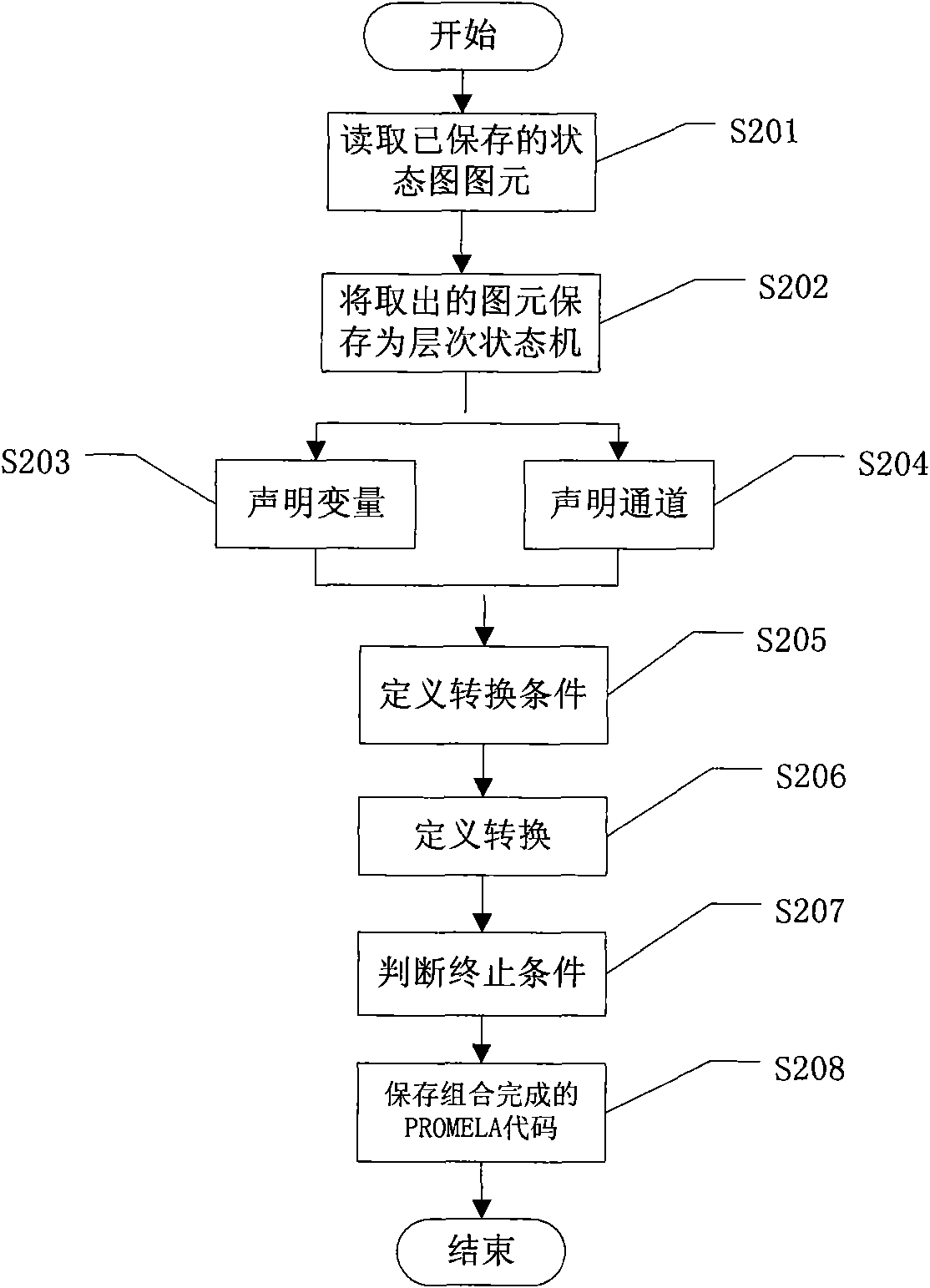
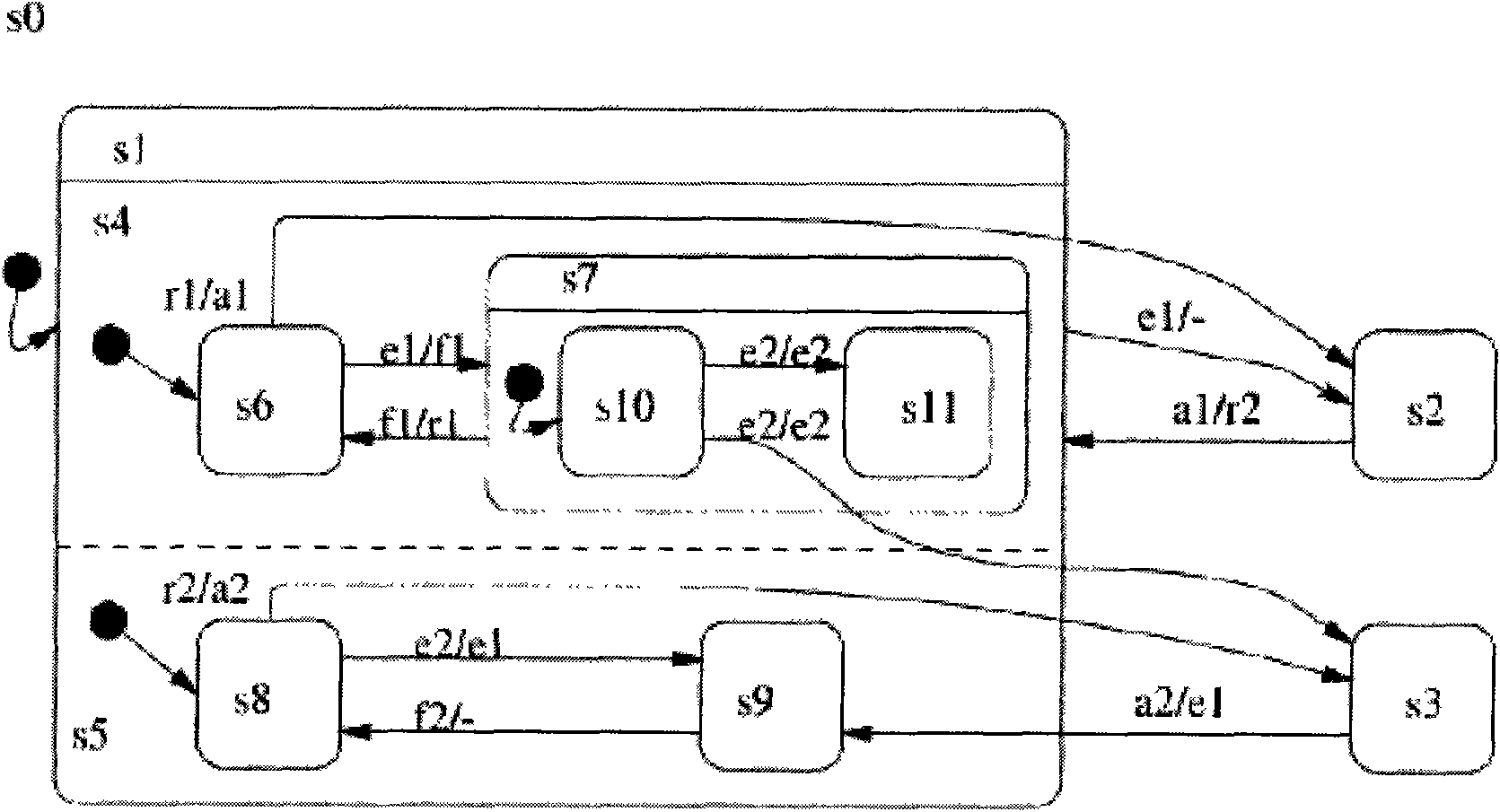
The invention relates to a method for verifying the consistency of a dynamic behavior in a unified modeling language (UML) model and a time-sequence contract. The method is characterized by comprisingthe following steps: modeling according to the UML standard, including generating a UML state diagram and a UML sequence diagram, and then saving the metamodels of the diagrams; mapping the UML statediagram to a PROMELA code for the dynamic behavior of the model; establishing the time-sequence contract of the model to map the UML sequence diagram to an LTL temporal logical formula; utilizing a model verifying tool SPIN to verify the PROMELA code and the LTL temporal logical formula; and analyzing the returned SPIN verifying result. The technical scheme of the invention associates the unifiedmodeling language (UML) and the verifying tool together, solves the problem of model inconsistency arisen in the requirement and design stage of soft engineering and provides an effective basis for the subsequent development of model driving type software.
Owner:EAST CHINA NORMAL UNIV
Control system of nuclear power unit, automatic diagnostic method and subsystem thereof
InactiveCN101158874AQuick actionProvide quicklyElectric testing/monitoringNuclear powerControl system
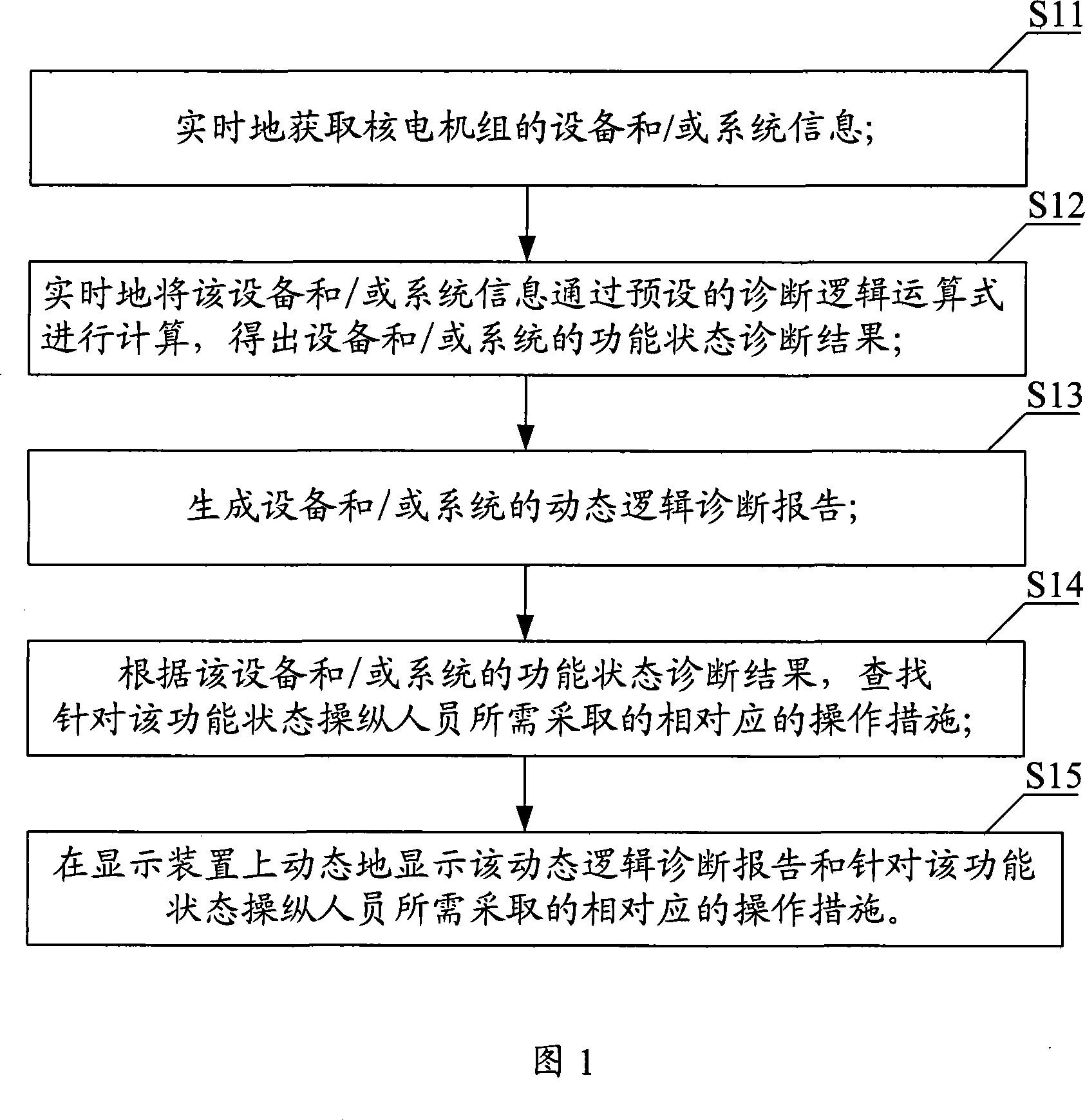
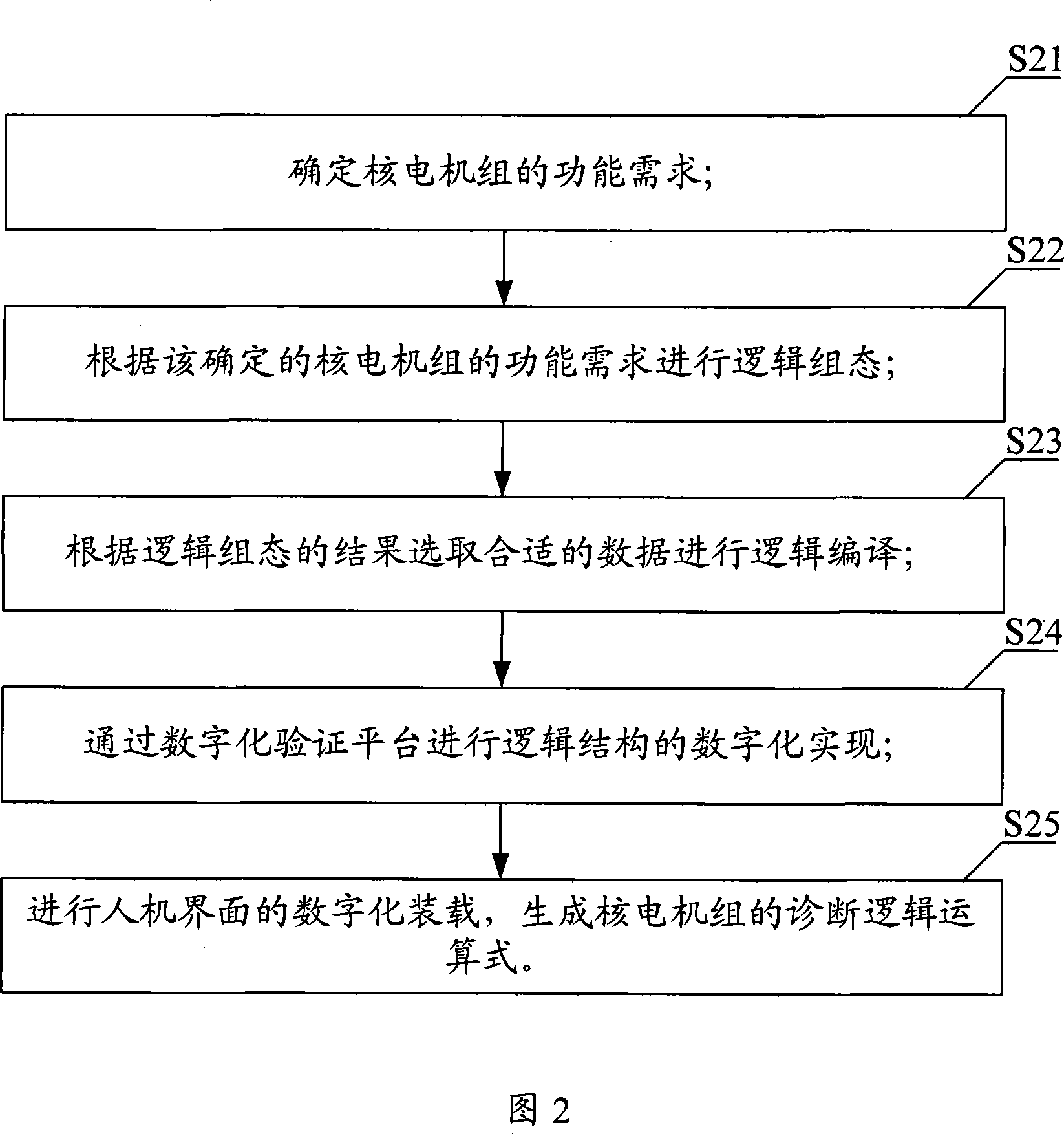
The inventive embodiment discloses a control system of a nuclear power generating unit and an automatic diagnostic method and a subsystem thereof. The method comprises the following steps that the equipment and / or system information of the nuclear power generating unit is obtained; the equipment and / or system information is calculated through a preset diagnosis logical formula to obtain the function state diagnosis result of the equipment and / or system; in accordance with the function state diagnosis result of the equipment and / or system, the operator needs to adopt corresponding operation measure aiming to the function state; the corresponding operation measure aiming to the function state adopted by the operator is displayed on a display device. The inventive embodiment is able to provide the operator with the function state diagnosis result of the equipment and / or system quickly and accurately, and is able to guide the operator to adopt the corresponding measure.
Owner:DAYA BAY NUCLEAR POWER OPERATIONS & MANAGEMENT
System for enterprise knowledge management and automation
ActiveUS8135576B2Facilitates productive useDigital data information retrievalSemantic analysisFirst-order predicateSoftware design
Owner:ORACLE INT CORP
Methods for automatically generating assertions
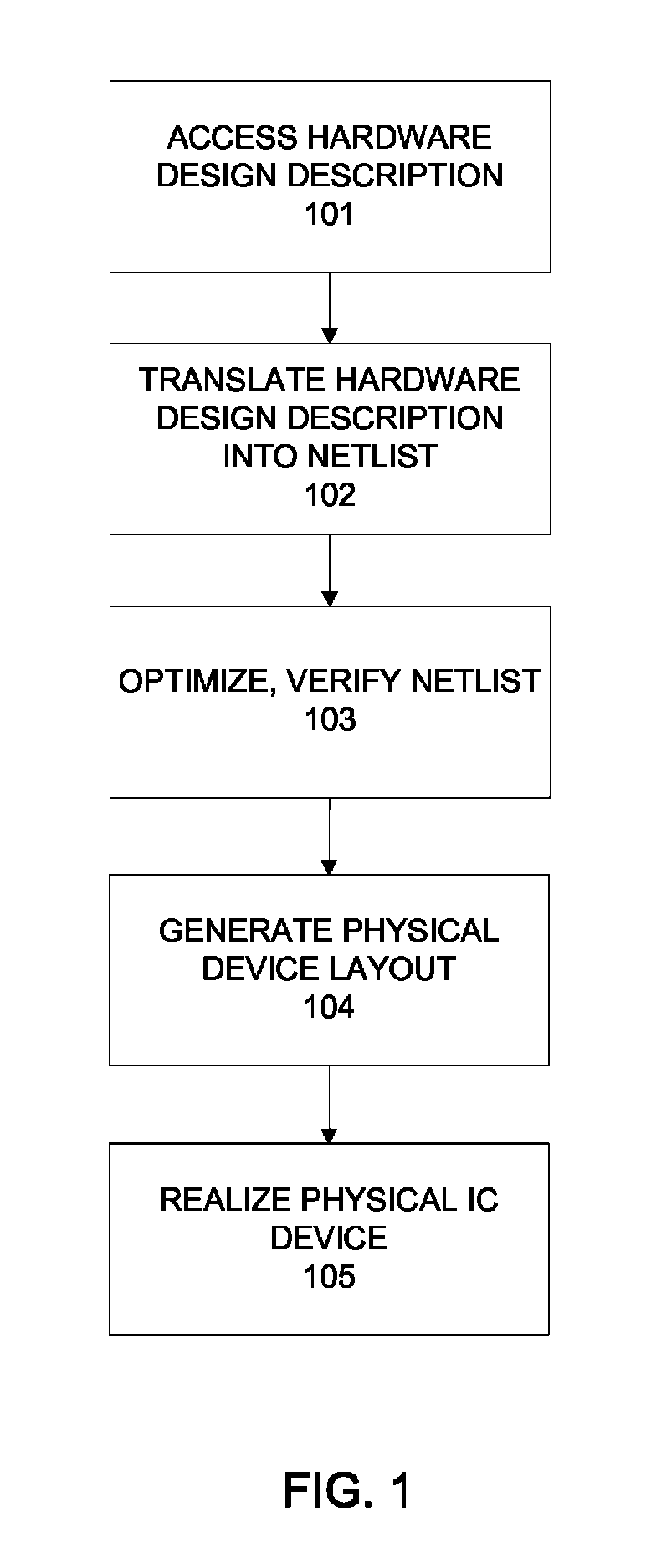
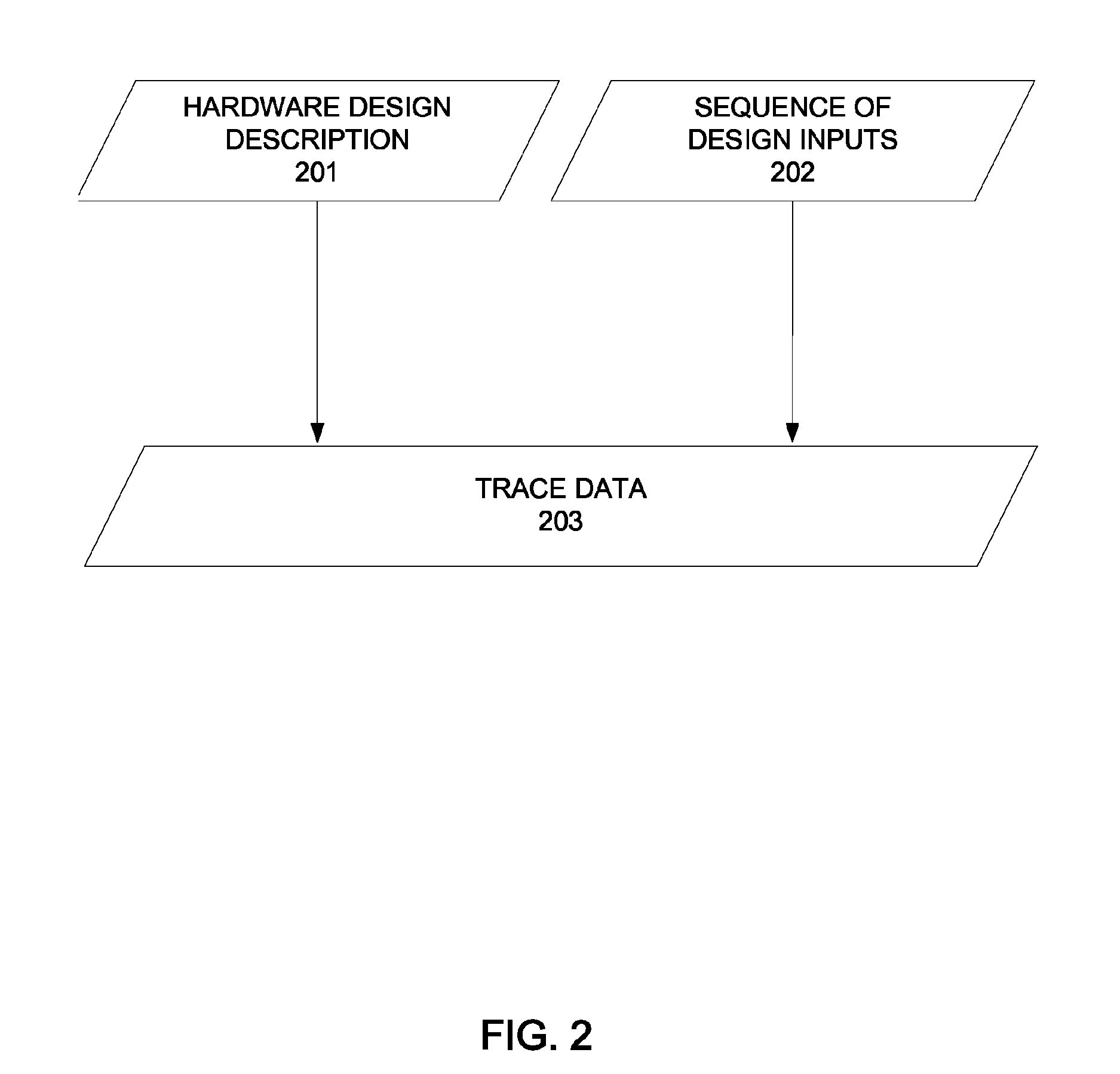
ActiveUS7926020B1Detecting faulty computer hardwareCAD circuit designLogic optimizationTheoretical computer science
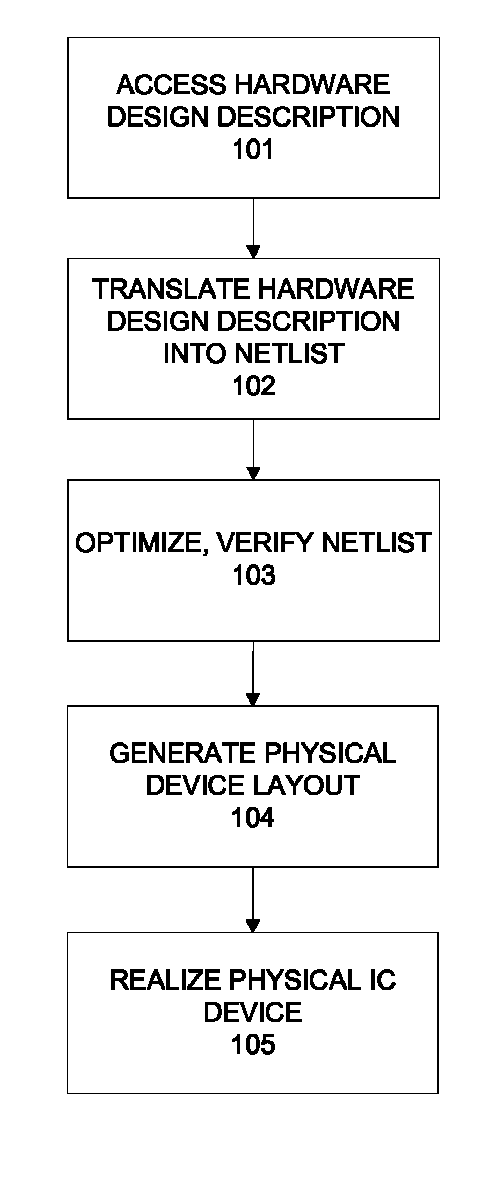
One embodiment of the present invention provides a method that automatically generates assertions of a hardware design. The method includes accessing a trace and a set of predicates of the hardware design. Then, the trace is projected over the set of predicates to generate a second trace. Then, a new set of states of the second trace is computed and the result is represented as a logical formula. The formula is reduced by logic optimization techniques. And finally, a set of logical consequences of the logic formula is produced and each logical consequence is enumerated as an assertion.
Owner:SYNOPSYS INC
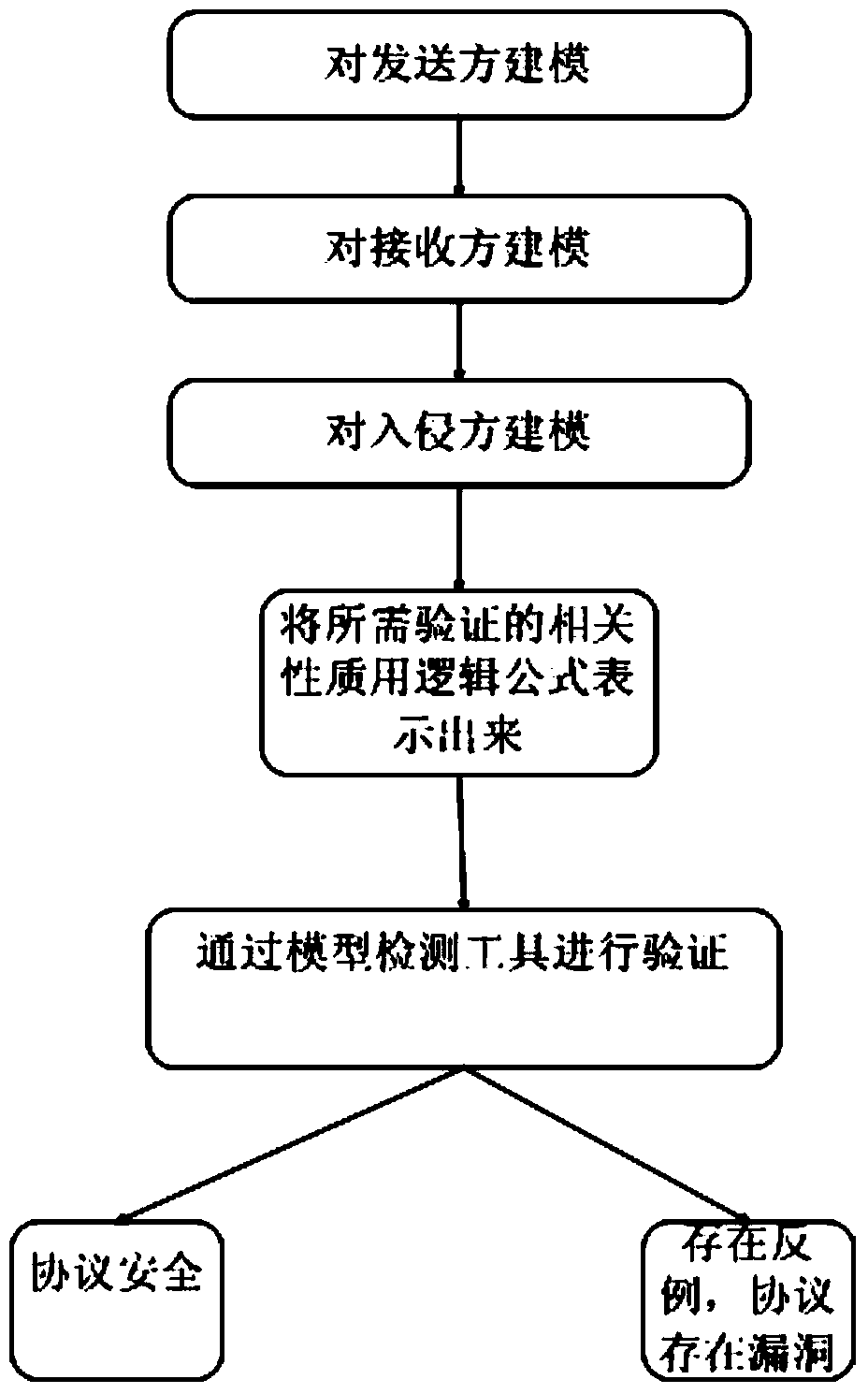
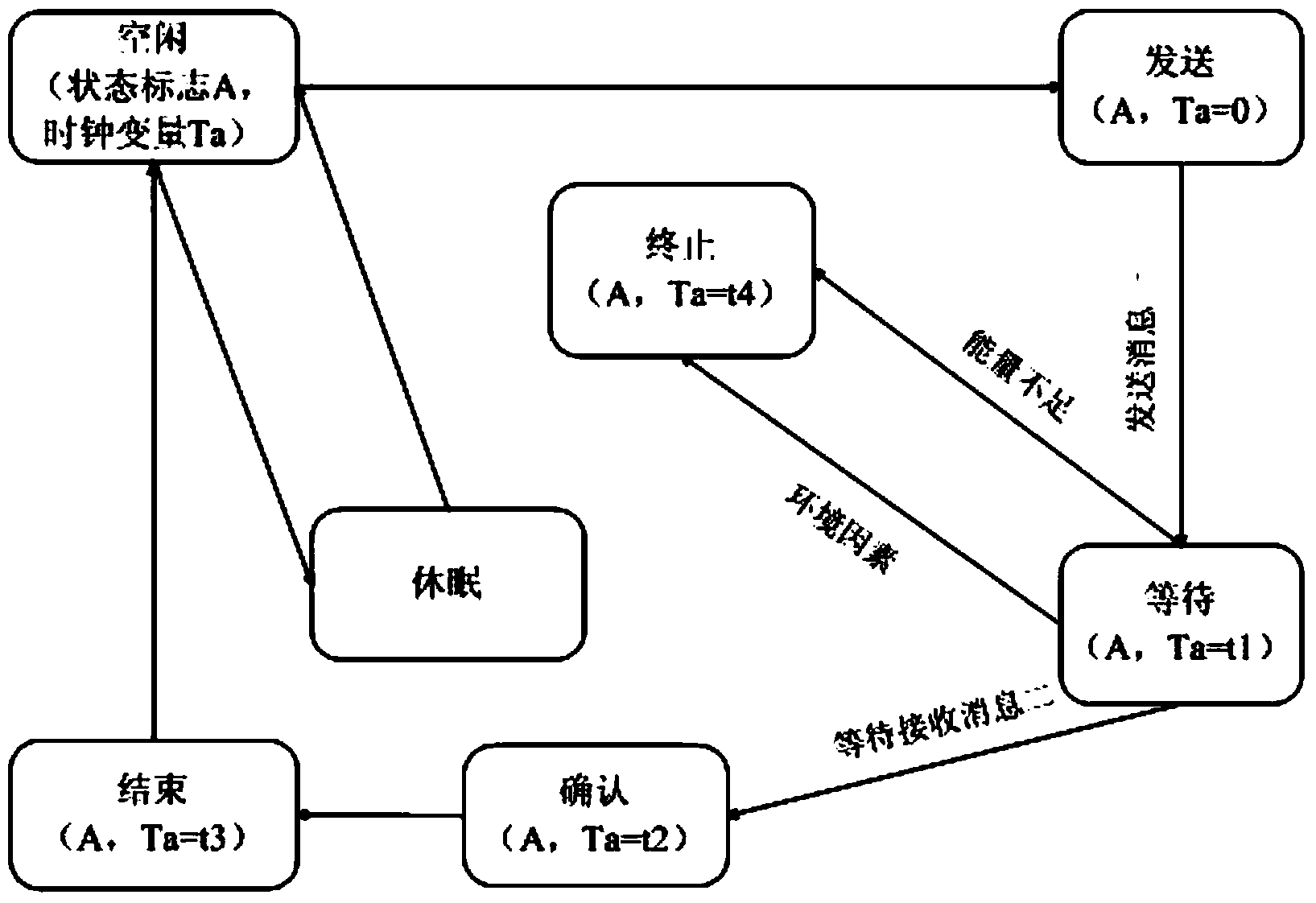
Wireless sensor network security protocol verification method based on model checking
ActiveCN103476033AVerify securityNetwork topologiesWireless network protocolsCryptographic protocolWireless sensor networking
The invention discloses a wireless sensor network security protocol verification method based on model checking. A state migratory system formed by a timed automata represents a wireless sensor network security protocol, a modal / time sequence logical formula represents the conditions which need to be met by the security protocol in the wireless sensor network, and the verification of the wireless sensor network security protocol is converted into a model carrying out verification that whether the state migratory system is a formula. According to the wireless sensor network security protocol verification method based on model checking, the characteristics of the wireless sensor network are sufficiently considered during the security protocol verification process, a clock restraint condition is added in the modal / time sequence logical formula, and comprehensive verification can be conducted on the wireless sensor network security protocol.
Owner:NANJING UNIV
Target domain knowledge base generation method and device and question answering method and device
ActiveCN111538844ARealization of logic operationsRealize logical derivationNatural language data processingSpecial data processing applicationsAlgorithmTheoretical computer science
The invention discloses a target domain knowledge base generation and question answering method and device, and the method comprises the steps: determining a concept graph, a reason graph and a predicate logic formula of target domain knowledge according to the knowledge type of the target domain knowledge; and generating a target domain knowledge base, wherein the concept map is used for representing a static relationship among the concept words, the factorial map is used for representing the sequence between the events and the factorial relationship between the events, and the predicate logic formula is used for representing business rules in the target domain knowledge. The question answering method comprises the steps that M events triggered by N word segmentation phrases of a questionare determined from an affair graph, and slot position values of slot positions of the M events are determined according to K word segmentation phrases, matched with a concept graph, in the N word segmentation phrases; a predicate logic formula corresponding to the consulting object of the question is calculated according to the M events and the slot values of the slots of the M events; an answerto the question is determined.
Owner:HUAWEI TECH CO LTD
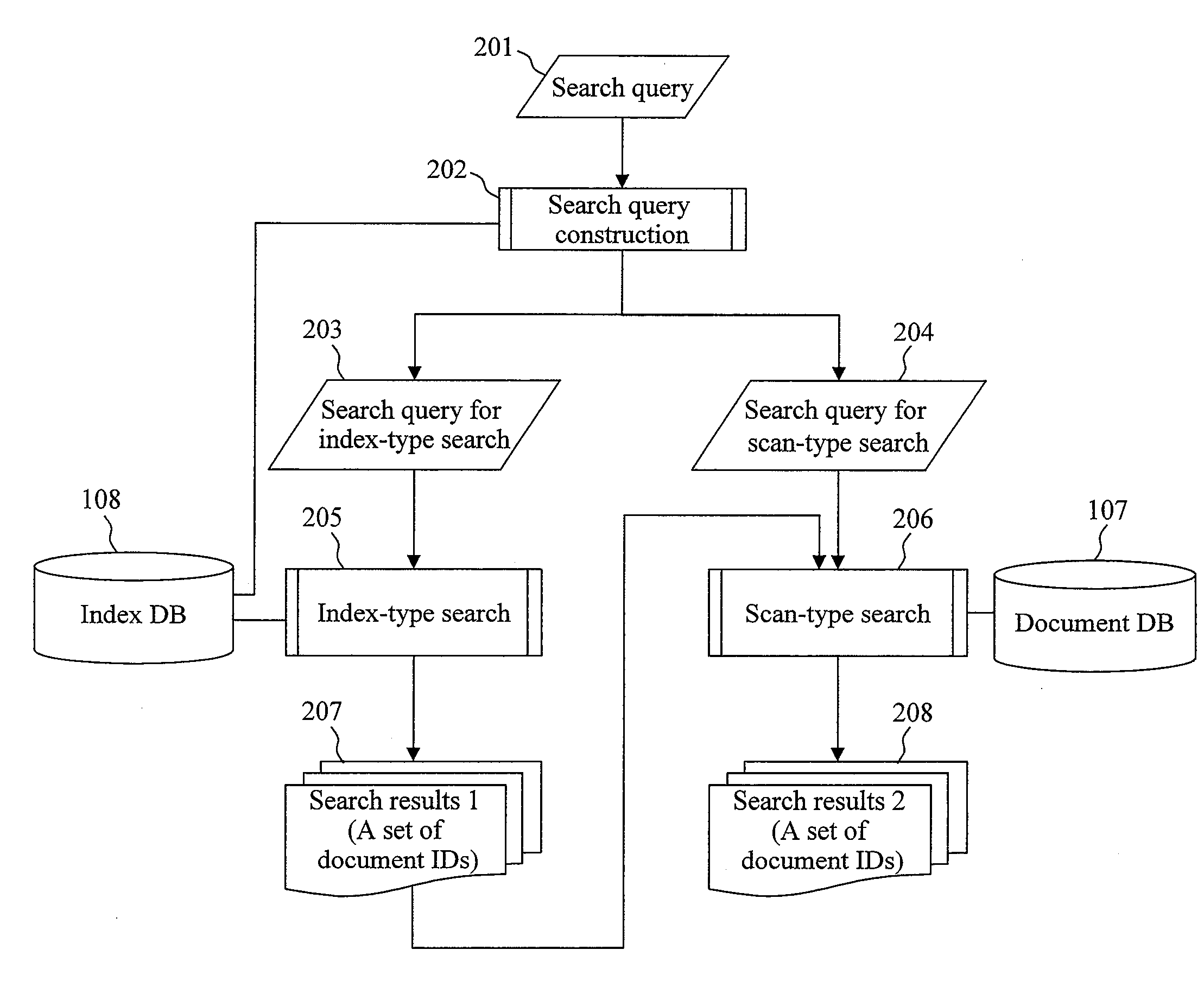
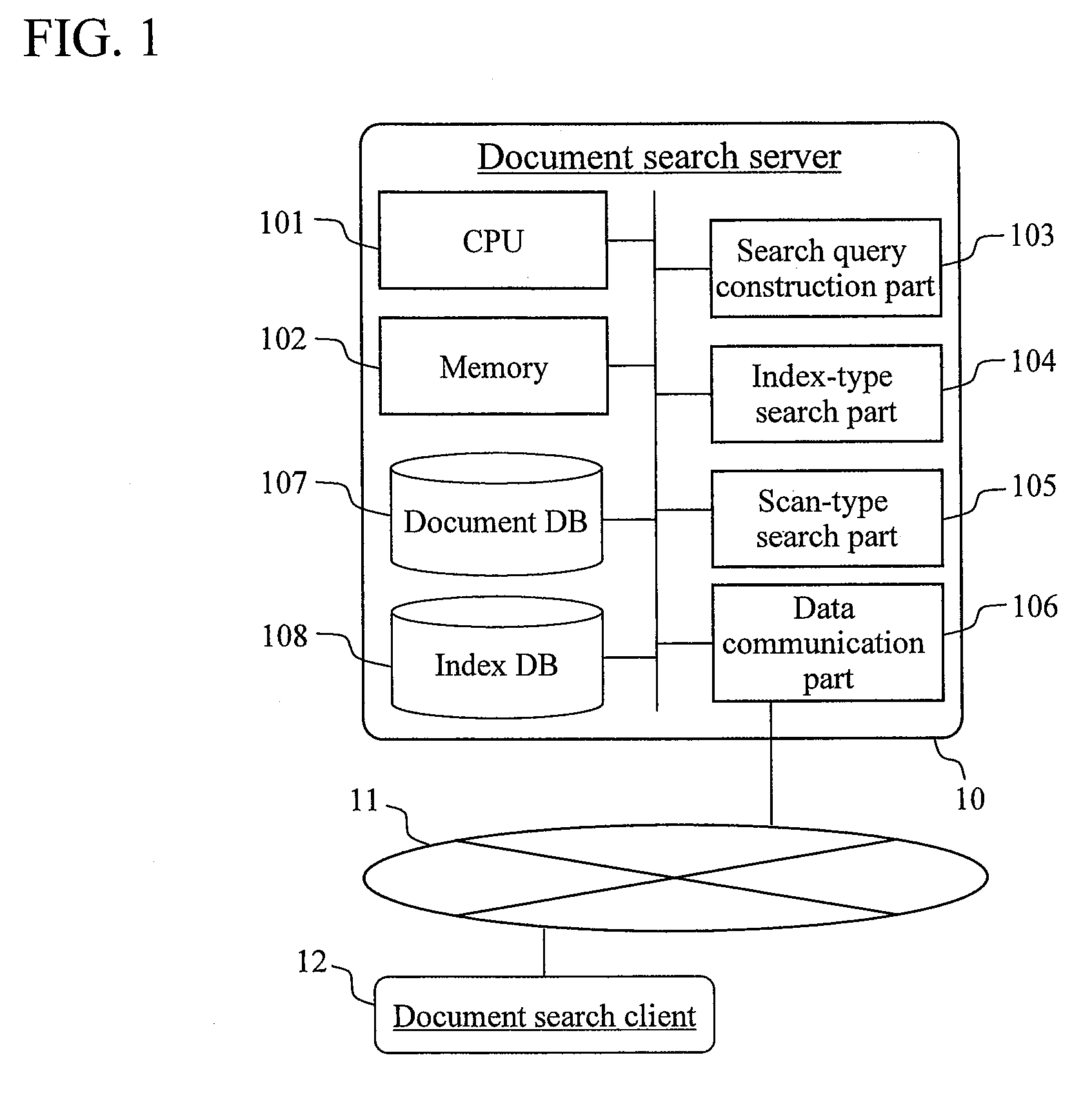
Document search method and document search apparatus that use a combination of index-type search and scan-type search
InactiveUS7966307B2Increase speedGood effectDigital data information retrievalDigital data processing detailsGramLine search
A document search apparatus capable of an index-type search and a scan-type search performs a search in a combination of the two search types while compensating for the disadvantages of the two search types with each other. A search query for index-type search and a search query for scan-type search are constructed based on a search query consisting of a logical formula of keywords. Then, a character 2-gram for performing an index search is set to shorten the whole search time, and the index-type search is performed. Finally, a scan-type search is performed on this search result of the index-type search.
Owner:HITACHI LTD
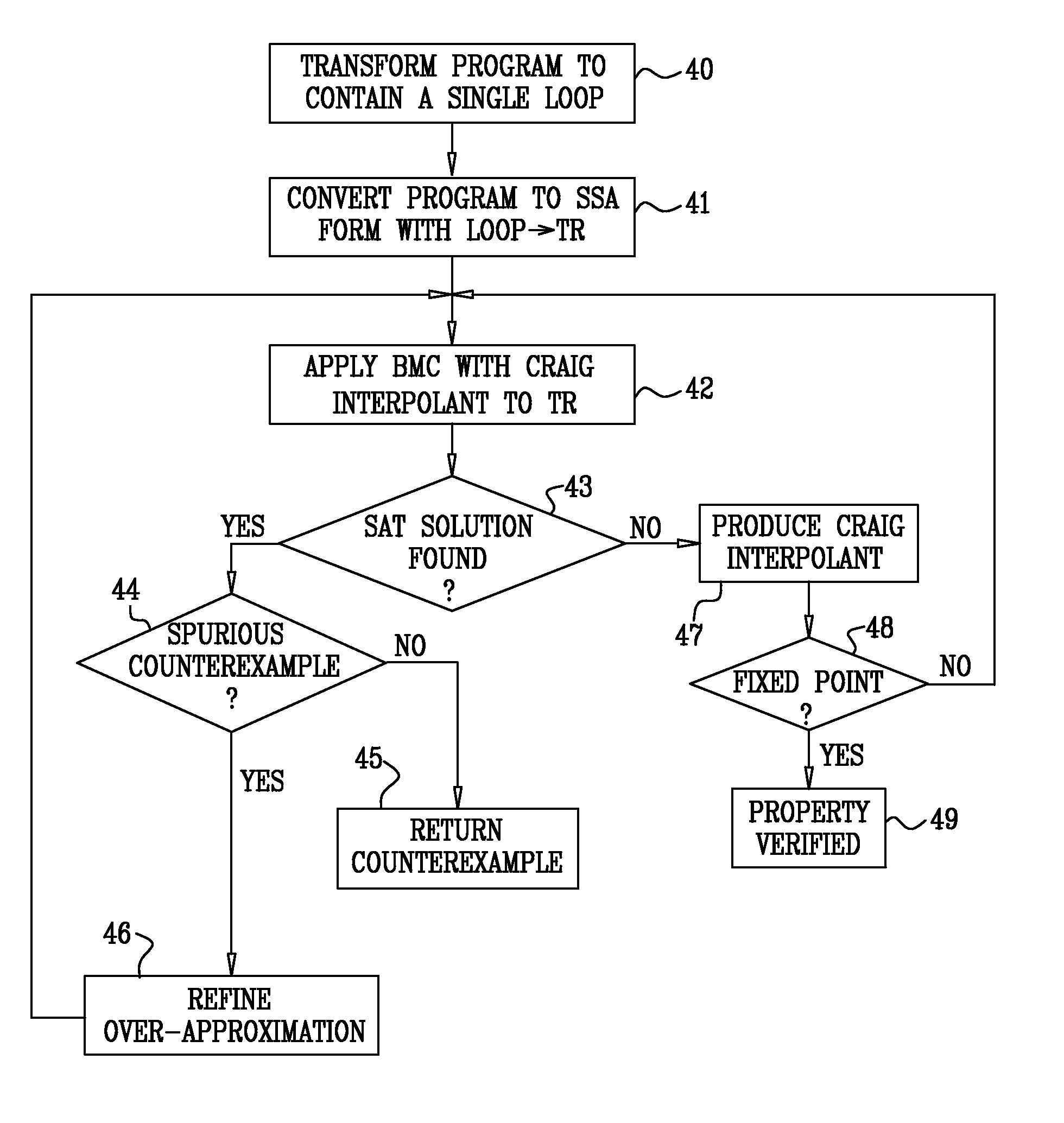
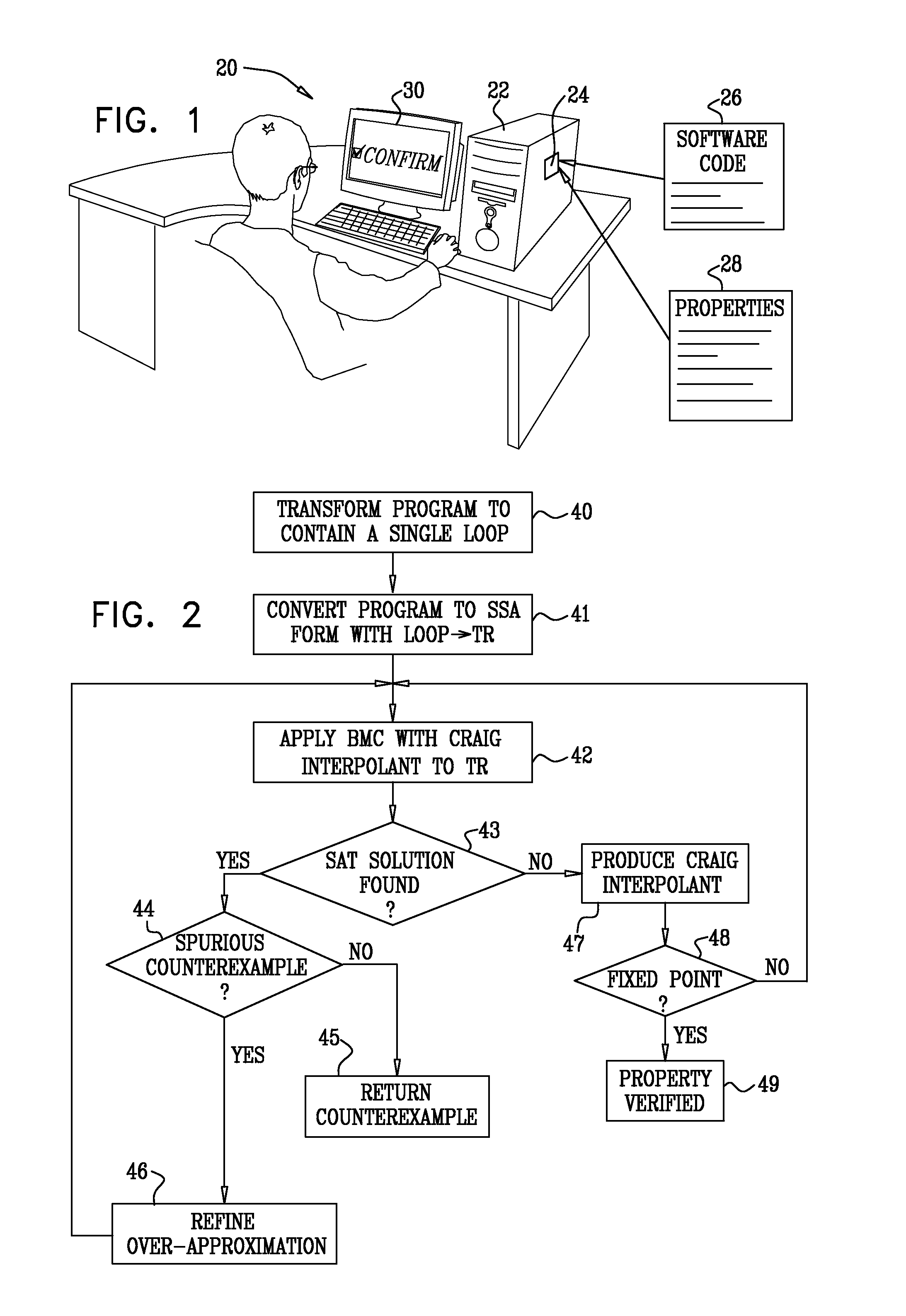
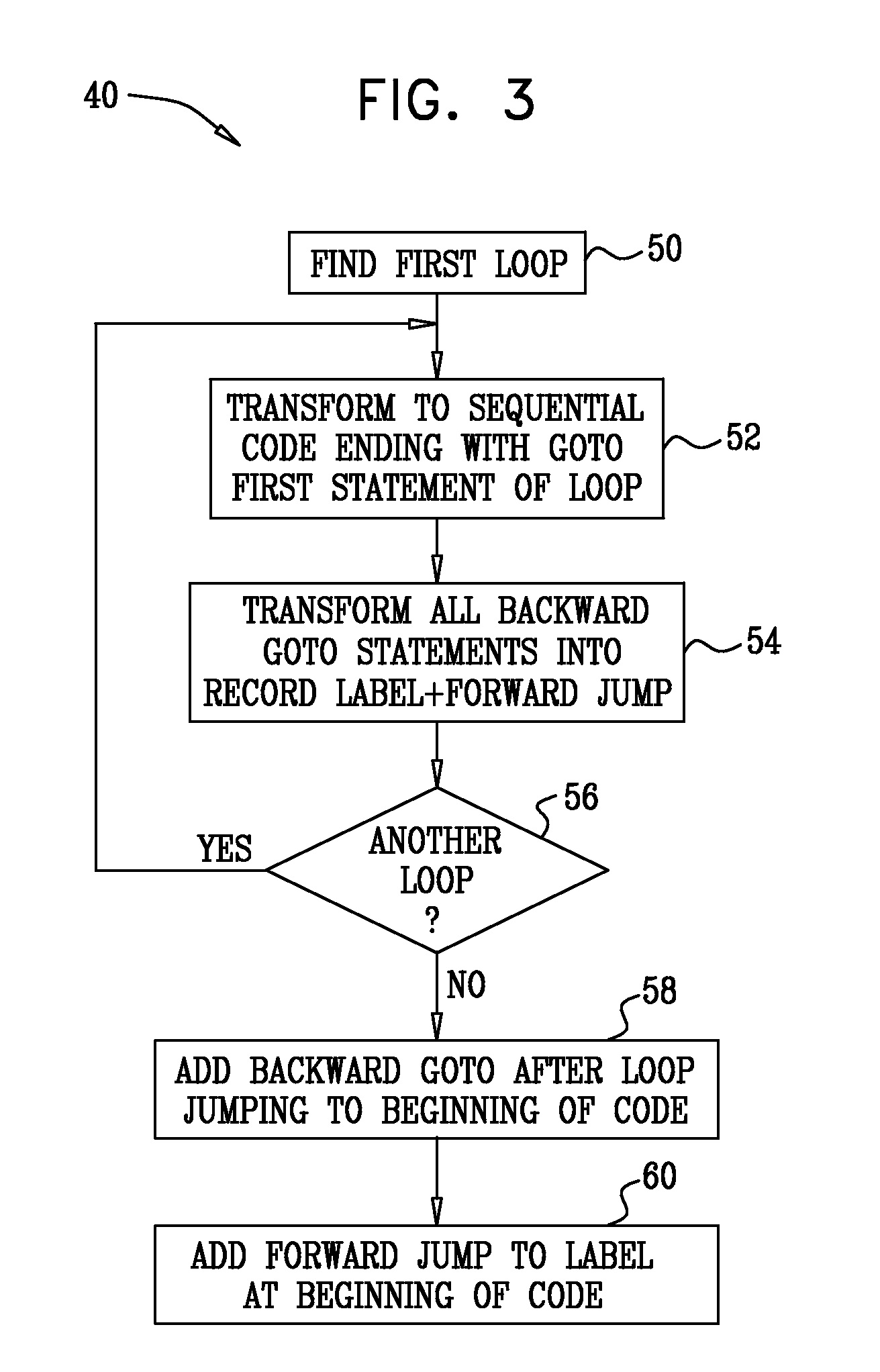
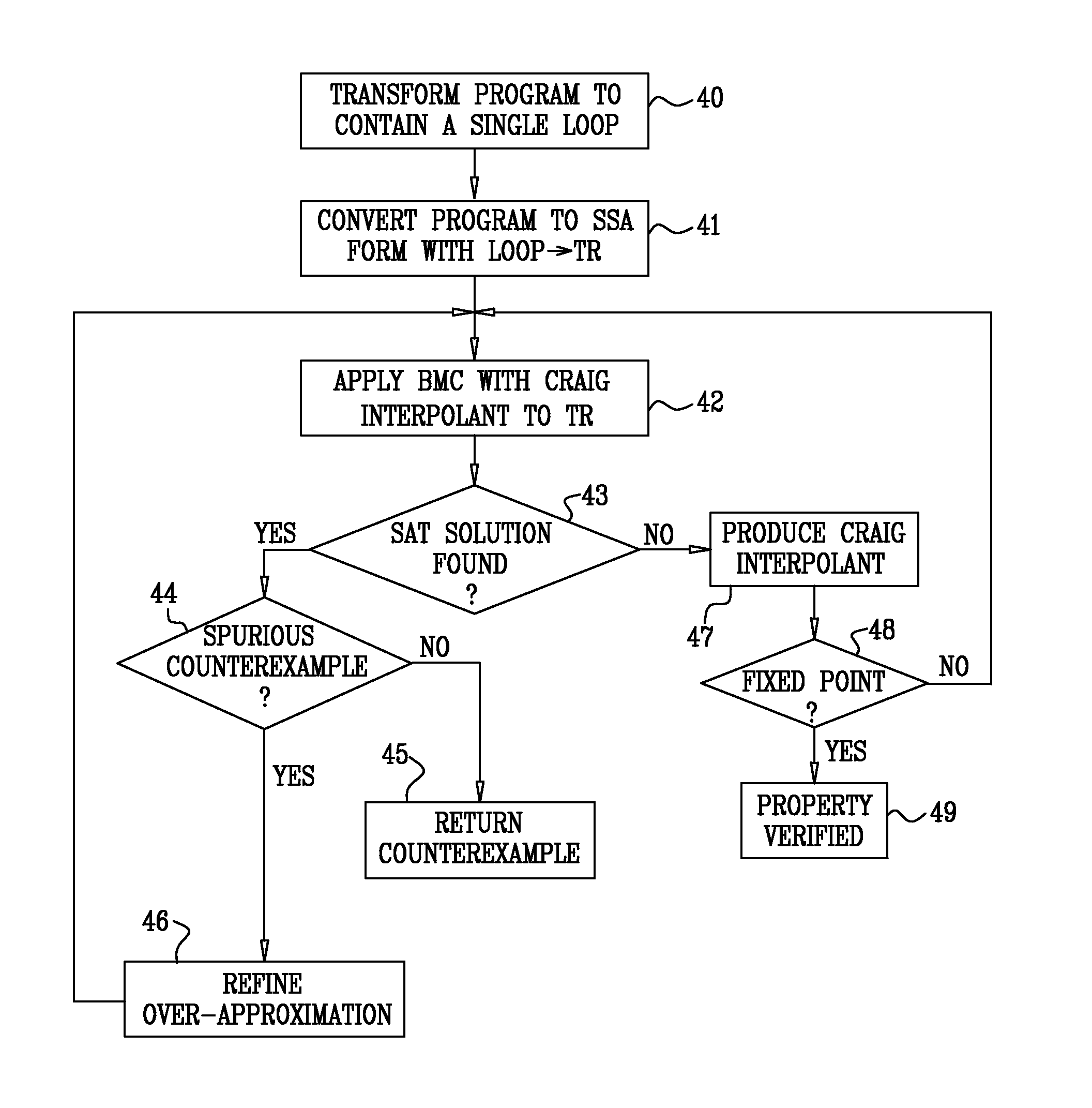
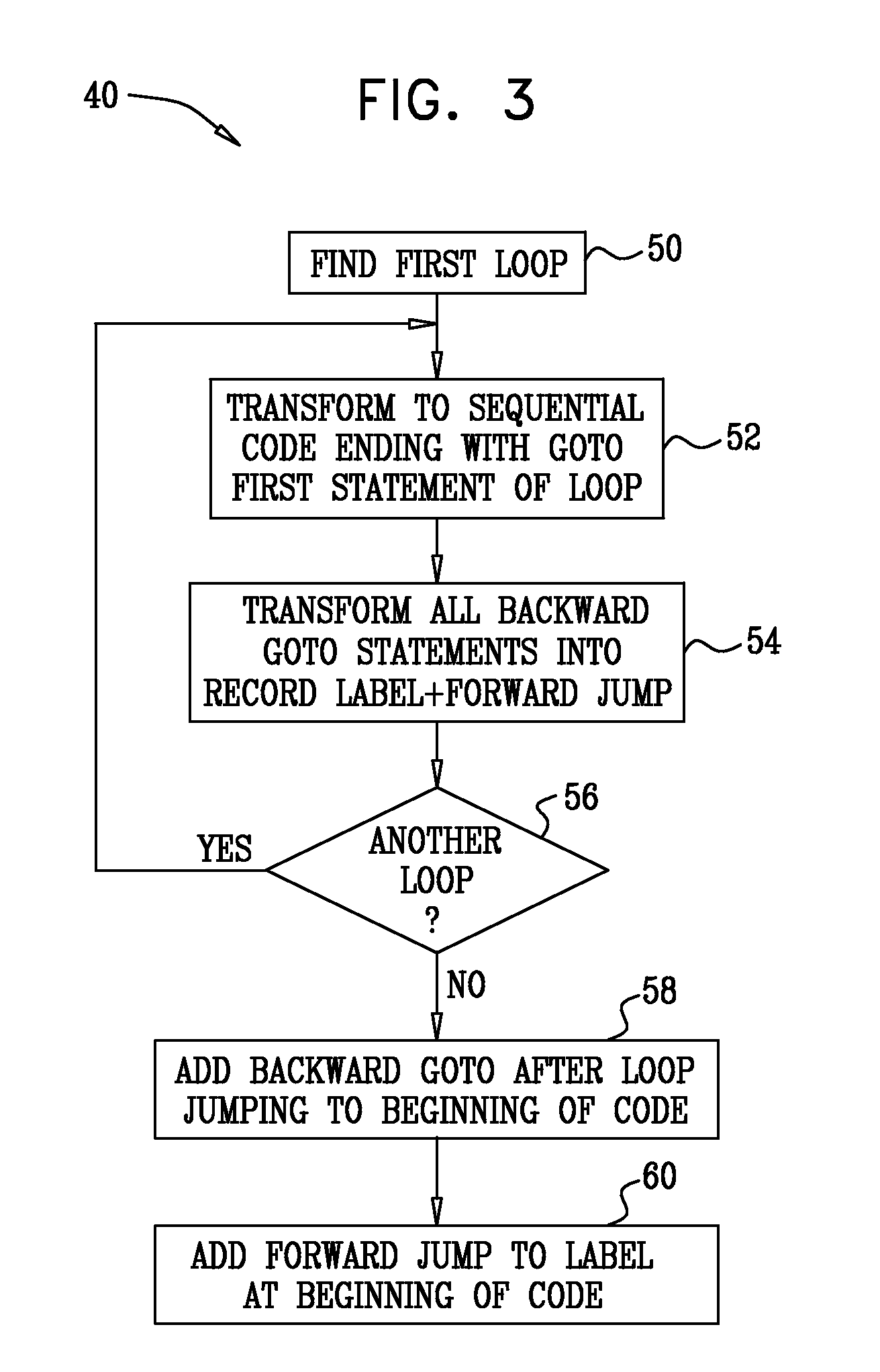
Model Checking of Non-Terminating Software Programs
InactiveUS20080098347A1Requirement analysisSpecific program execution arrangementsSingle assignmentLogical formula
Owner:IBM CORP
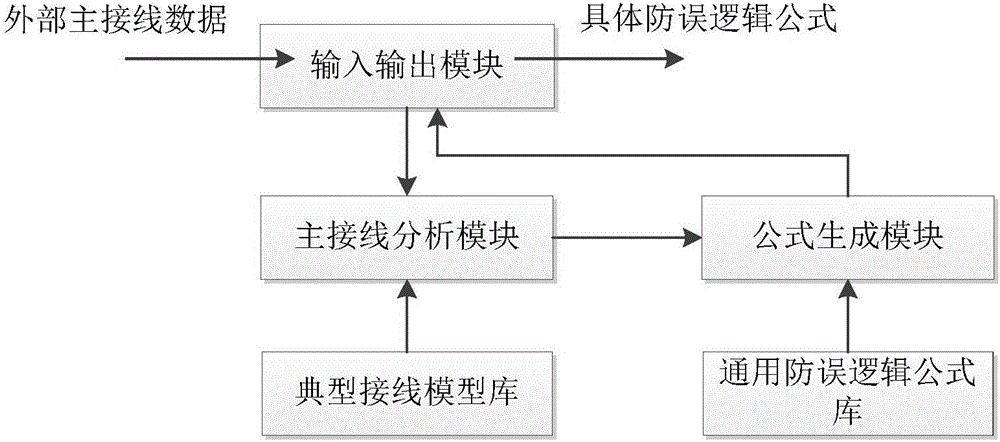
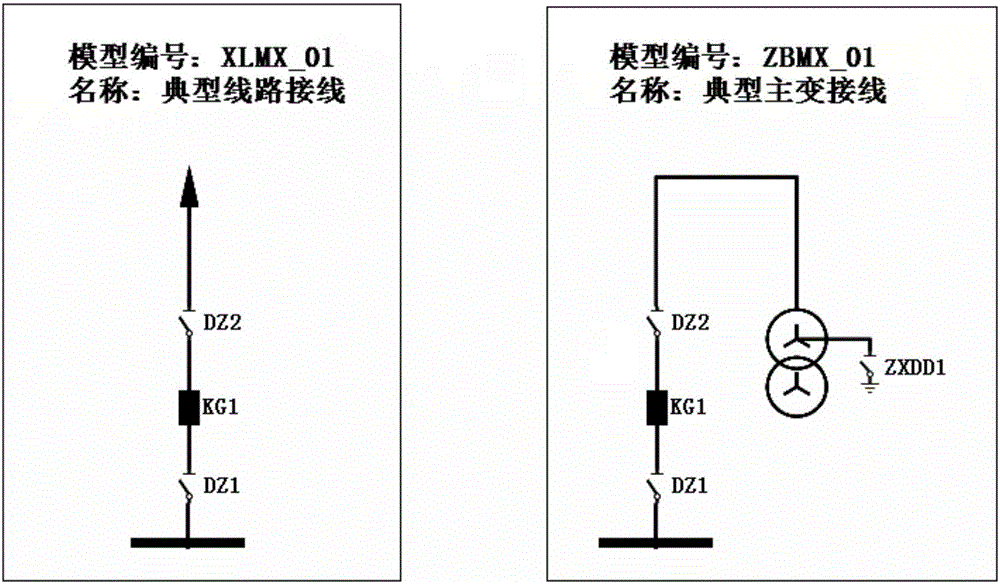
Automatic generating system and method for electrical-device error-preventing logical formulas
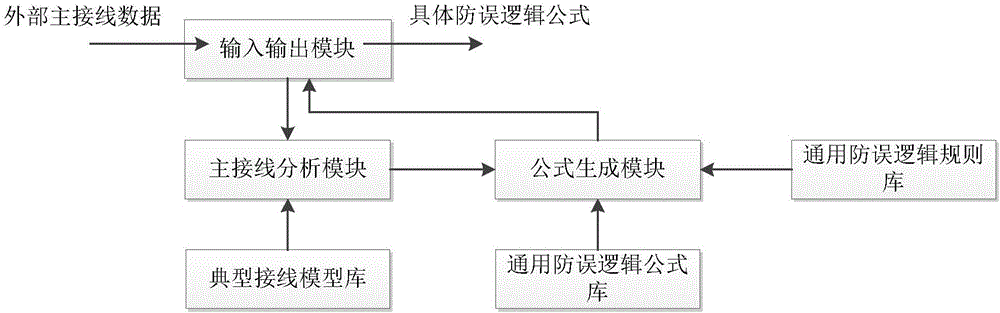
ActiveCN106843041AQuick buildImprove writing efficiencyProgramme controlComputer controlComputer moduleDependability
The invention discloses an automatic generating system and method for electrical-device error-preventing logical formulas. The automatic generating system comprises an input-output module, a typical wiring model base, a main wiring analysis module, a common error-preventing logical formula base, a formula generating module, a formula verifying module and the like. According to the automatic generating system, all kinds of typical wiring modules and common error-preventing logical formulas of a plant station are internally arranged; after main wiring information of a specific plant station is read, the wiring information can be matched with system-internally-arranged typical device wiring modules, then the common error-preventing logical formulas under a matching module are replaced into actual device information to be output, and therefore specific error-preventing logical formulas are obtained; further, automatically-generated logical formulas and written logical formulas can be verified, and therefore the problems that current plant-station error-preventing logical formulas are low in writing efficiency and verifying efficiency and insufficient in reliability are solved.
Owner:ZHUHAI UNITECH POWER TECH CO LTD
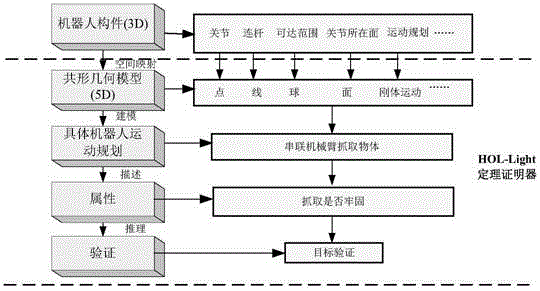
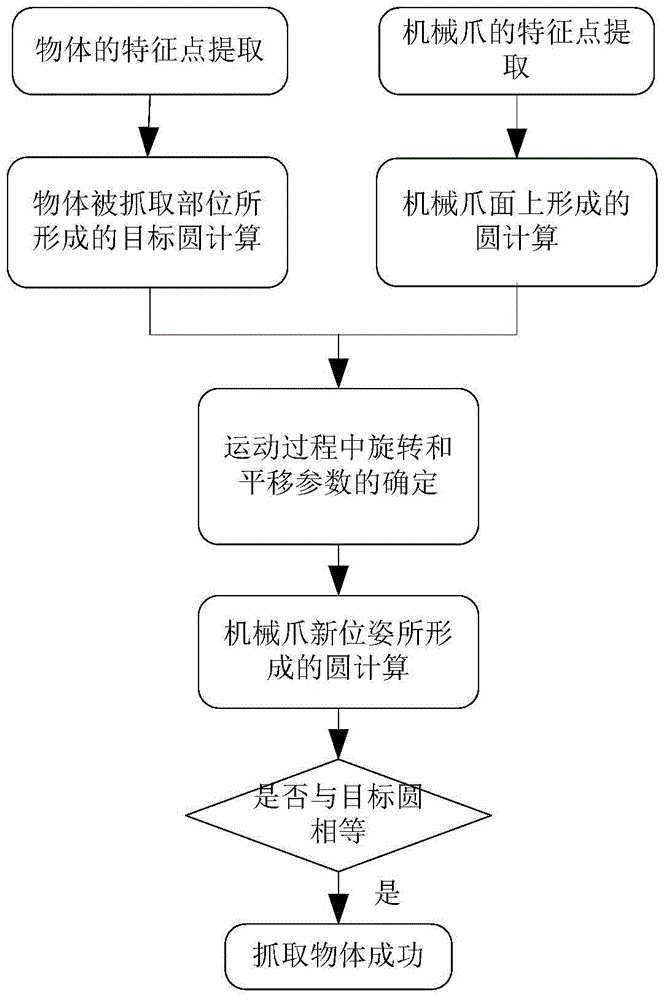
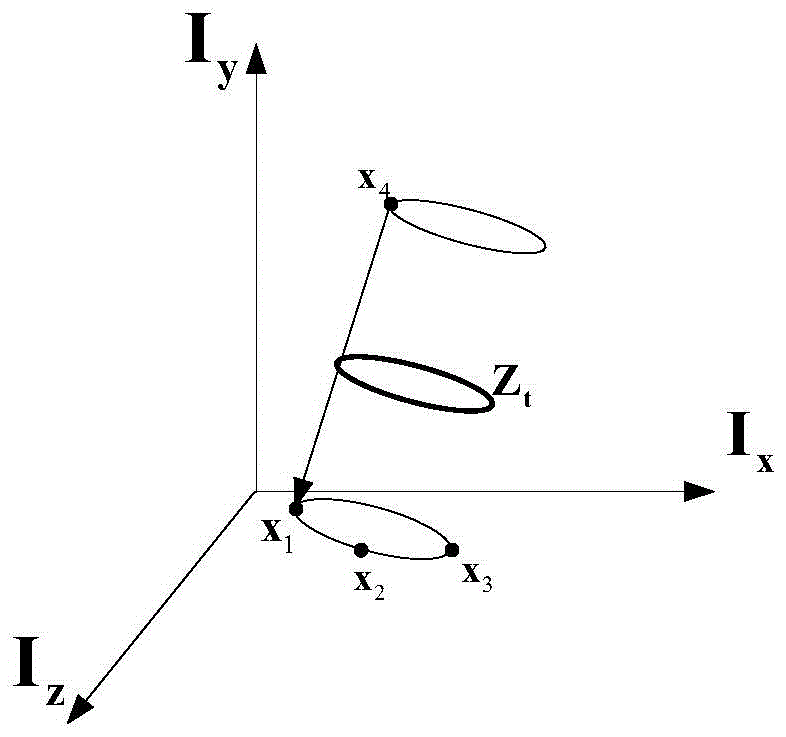
Formalized analyzing method and system for mechanical arm motion planning on basis of conformal geometric algebra
InactiveCN105760576AEnhanced couplingAdd dimensionProgramme controlProgramme-controlled manipulatorSimulationModel system
The invention discloses a formalized analyzing method and system for mechanical arm motion planning on the basis of conformal geometric algebra.The method comprises the steps that corresponding geometric models are built for basic elements and motion planning constrains of a robot on the basis of a conformal geometric algebra theory, and the built geometric models are described with a high-order logical language to form a basic geometric logical model system of the robot; specific structure parameters and motion planning parameters of the robot are determined; formalized modeling is performed on the specific robot motion process on the basis of the basic geometric logical model system to obtain a geometric relationship logical model of the specific robot motion process; the robot motion process constraints or attributes needing to be verified are described with a logical formula; the geometric relationship logical model of the specific robot motion process and the motion process constraints or attributes to be verified form a logical proposition; whether the logical proposition is valid or not is proved through a logical inference engine.
Owner:CAPITAL NORMAL UNIVERSITY
Model checking of non-terminating software programs
InactiveUS7921411B2Requirement analysisSpecific program execution arrangementsSingle assignmentLogical formula
A method for verifying software program code includes specifying a property that the software program code is expected to satisfy. The software program code and the property are transformed into an initial logical formula in a static single assignment (SSA) form, the formula including variables. A loop in the software program code is identified. Successive over-approximations are applied to a portion of the initial logical formula corresponding to the loop in order to produce a modified logical formula in the SSA form that represents a finite over-approximation of a set of states that are reachable by the loop. It is verified that the software program code satisfies the specified property by determining whether there is an assignment of the variables that satisfies the modified logical formula.
Owner:IBM CORP
Method for verifying security model of computer system
InactiveCN102194061AImprove verification effectVerify violationsDigital data authenticationOperational systemOperating system security
The invention discloses a method for verifying a security model of a computer system, and belongs to the technical field of security of an operating system. The method provided by the invention comprises the steps: (1) an ML (modeling language) modeling module describes the dynamic and the static attributes of a security model of a computer system by adopting of a UML (unified modeling language) description language to obtain the UML model of the security model of the computer system; (2) a security attribute to be verified is described through a mathematical logical formula adopted by a preset formal verification tool; (3) the UML model is converted into an input model, capable of being processed by the preset formal verification tool, through a UML model conversion module; and (4) state traversal is performed on the input model through the preset formal verification tool, the satisifiability of the formula obtained in the step (2) on each state is calculated, and verified results are output. By means of the invention, the automation degree of verification and the verification capability are improved, and at the same time, the structural defects of the security model per se and the condition of violation of a time sequence attribute can be verified.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
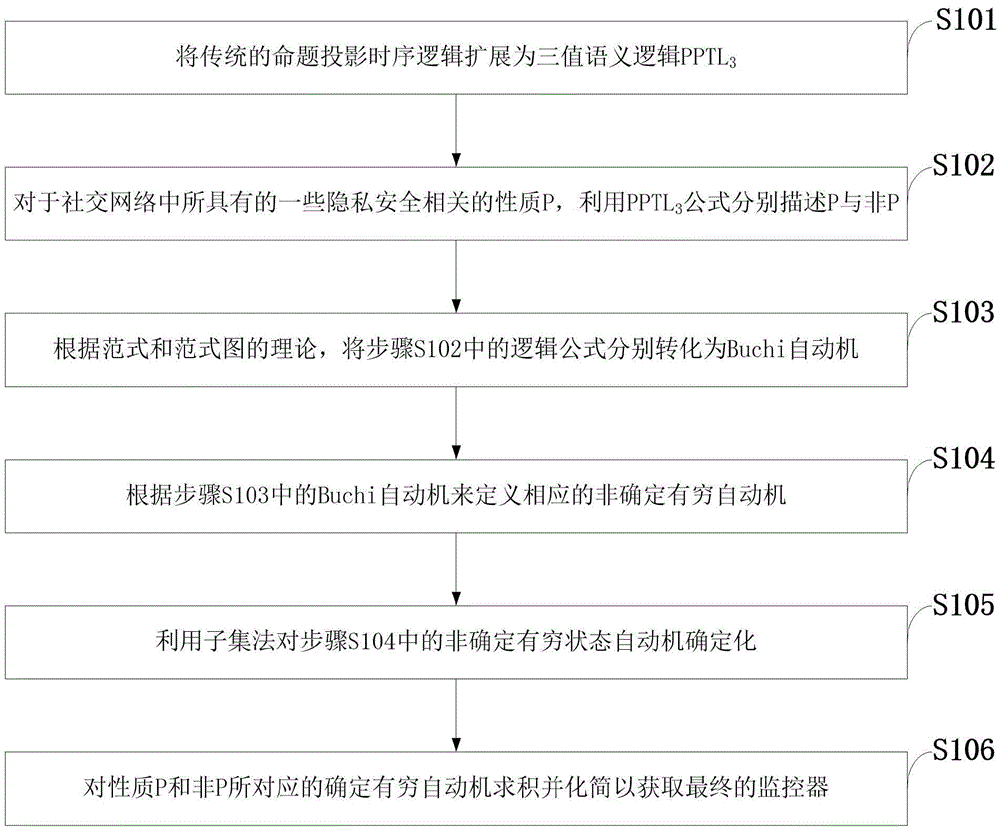
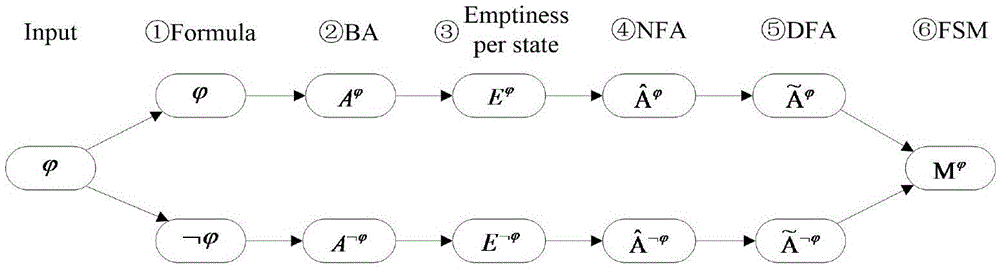
Social networking system privacy security runtime verification method based on PPTL3
ActiveCN105653935ATargetedExtended VerifiabilityPlatform integrity maintainanceRuntime verificationNetworked system
The invention discloses a social networking system privacy security runtime verification method based on PPTL3. The method comprises the steps that the property P to be verified is described with a PPTL3 formula, then logical formulas corresponding to P and non P are converted into normal formulas and further converted into normal form graphs and normal form graphs with marks, a corresponding Buchi automaton can be obtained according to the latter, a finite automaton is defined and determined by changing a receiving set, and finally quadrature is carried out on the finite automaton to build a monitor. On the basis, the invention further discloses application of runtime verification in a social networking system, the property needed by the social networking system is described through the PPTL3 formula, and a corresponding monitor is built and monitors the running system to judge whether current running meets the property or not.
Owner:XIDIAN UNIV
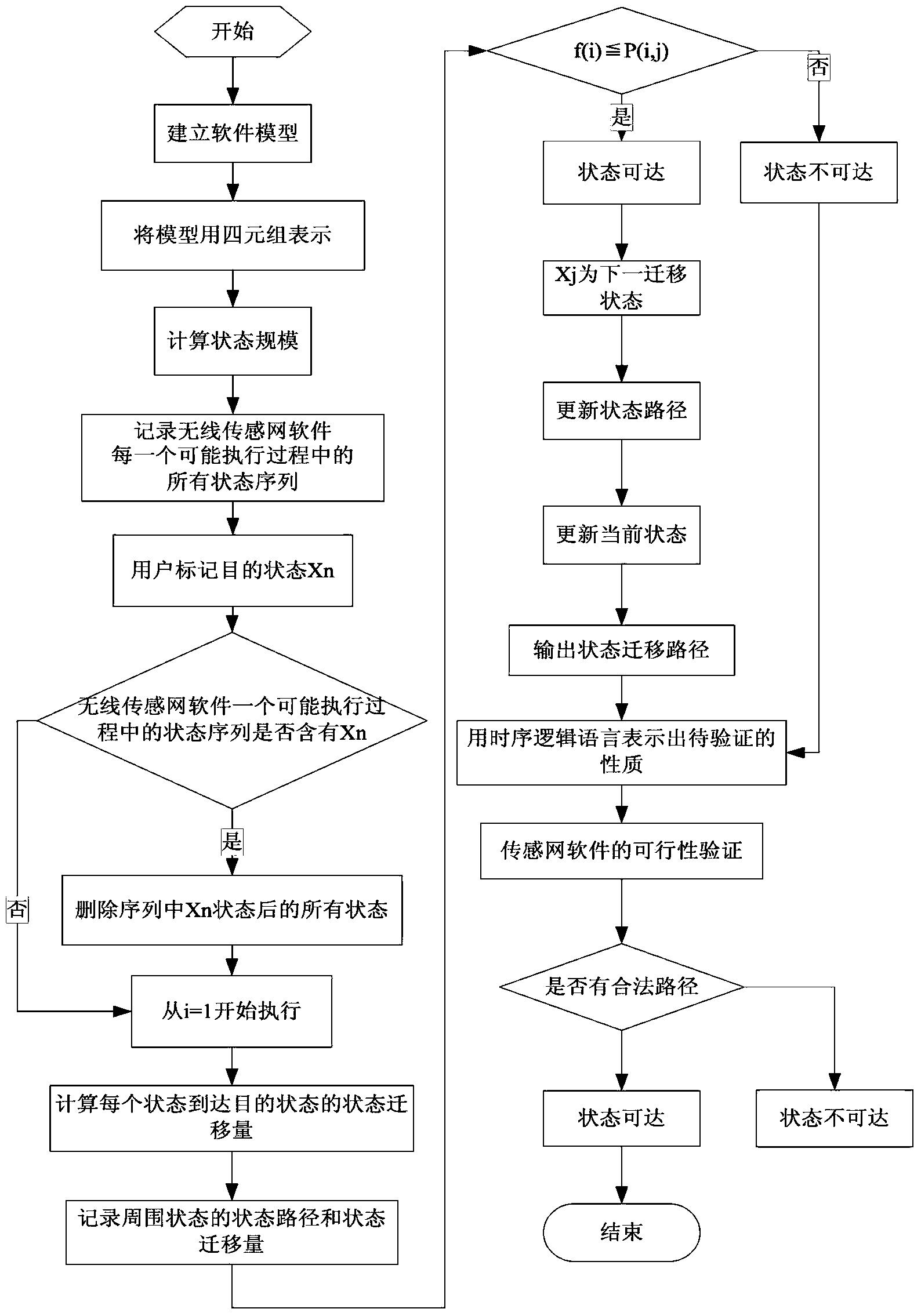
Sensor network software accessibility verification method
InactiveCN103970653AIncrease flexibilityImprove the efficiency of reachability verificationSoftware testing/debuggingValidation methodsReachability
The invention provides a sensor network software accessibility verification method. In the method, firstly, wireless sensor network software is represented through a model, the model is used for describing nodes and state transition among the nodes, then the software model is optimized through the particle swarm optimization, the property or quality which the wireless sensor network software needs to meet is represented through a sequential logical formula during specific implementation, and verification of the wireless sensor network software is converted into the mode that the property of a system is judged by verifying whether the software model meets the formula. According to the method, by optimizing the accessibility verification route, accessibility verification can be effectively performed on the sensor network software, and high flexibility is kept.
Owner:NANJING UNIV OF POSTS & TELECOMM
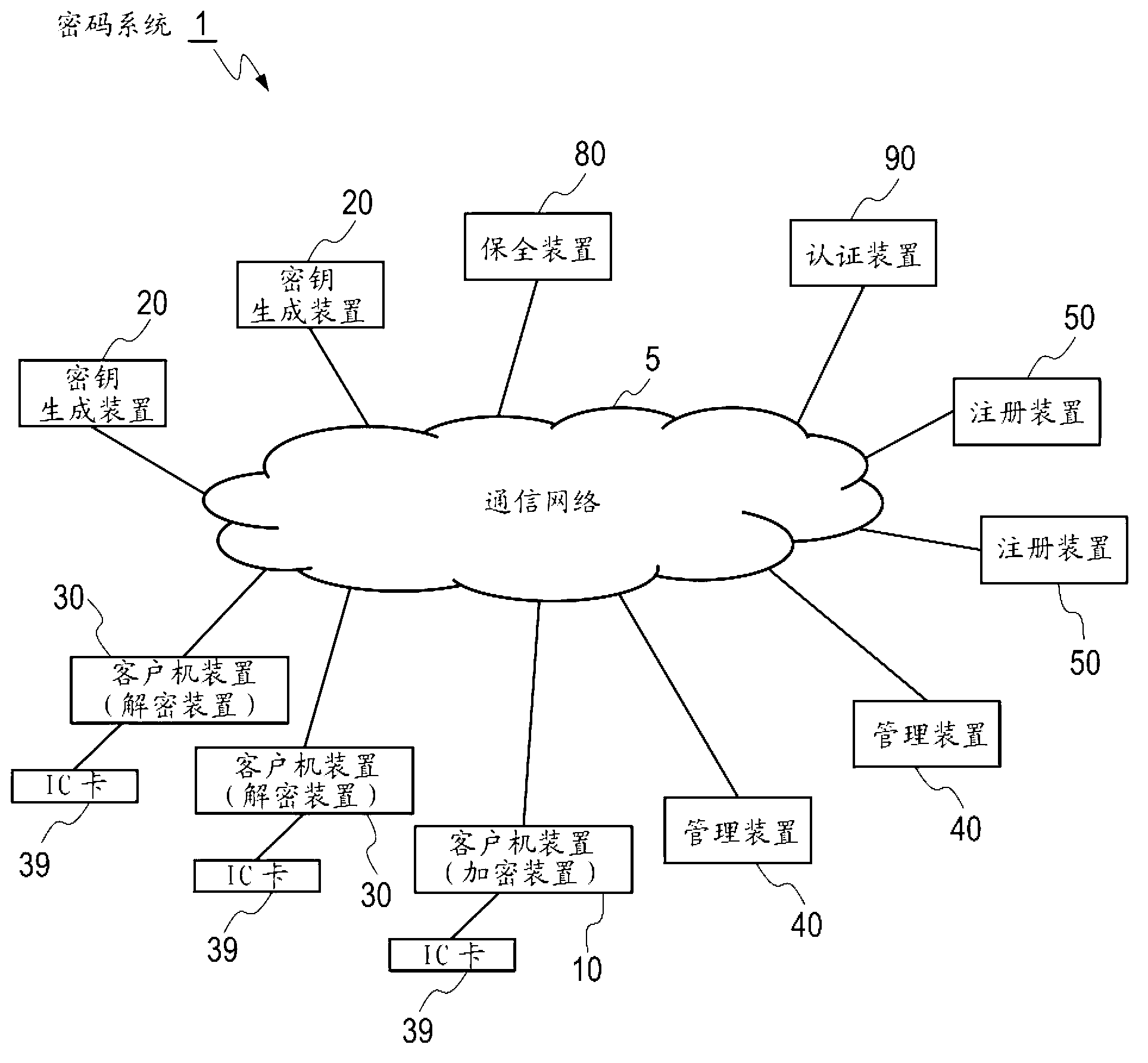
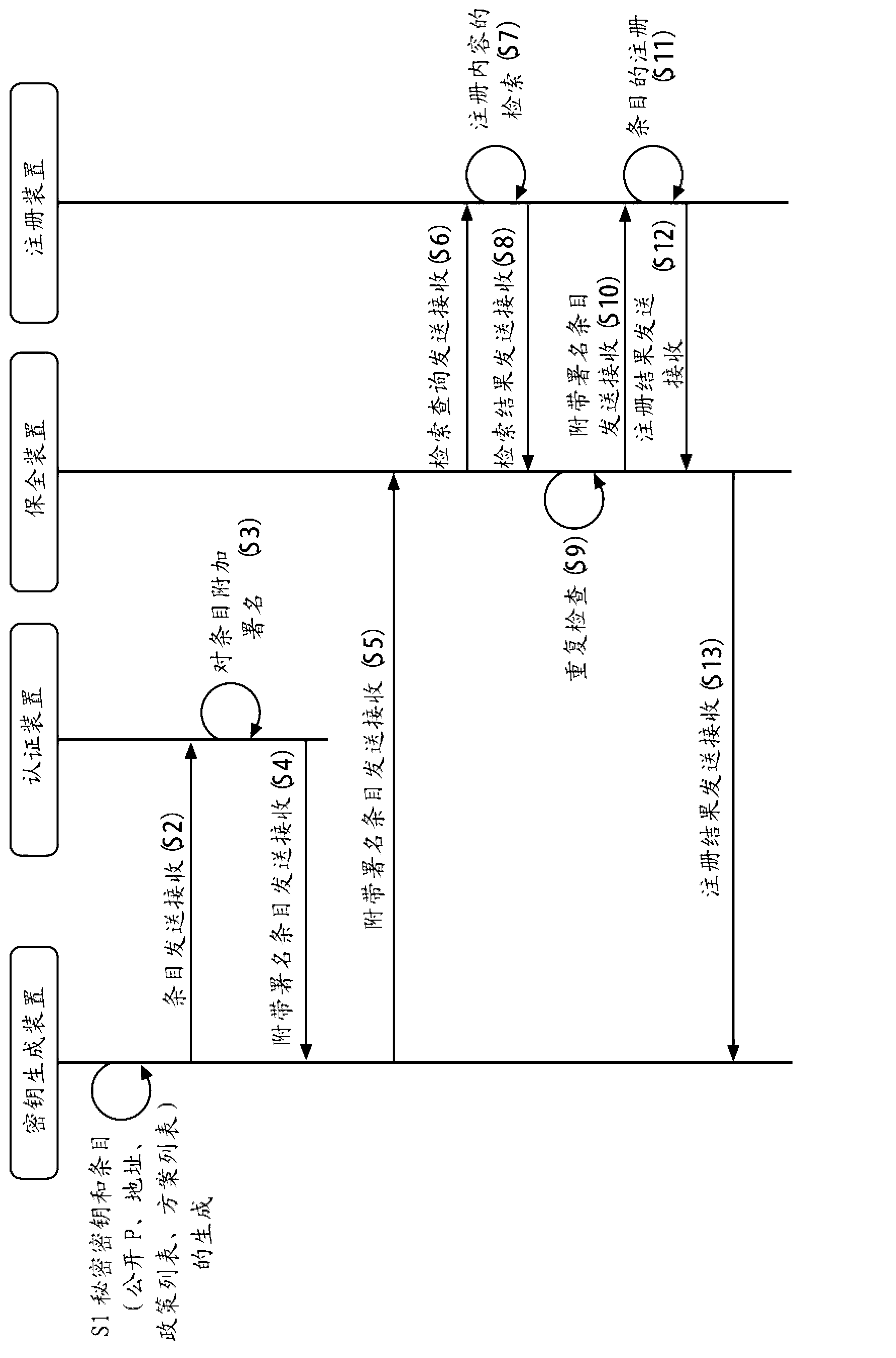
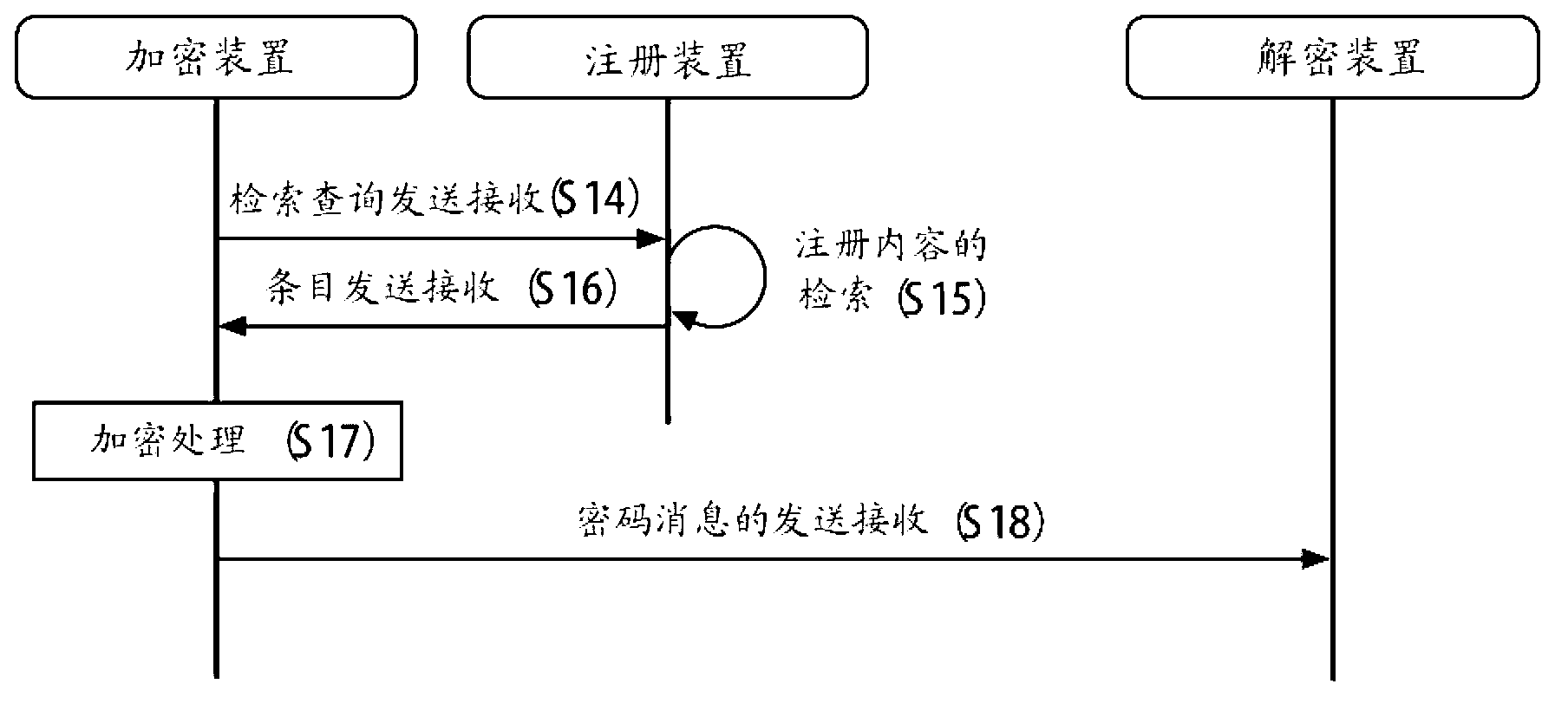
Cryptosystem, cryptographic communication method, encryption device, key-generating device, decryption device, content server device, program, and recording medium
ActiveCN103004130AKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareCryptosystem
Disclosed is a cryptographic communication technique that depends on a function cipher and that can be operated flexibly. A conversion rule information pair is prescribed ahead of time, said pair being the pair of: attribute conversion rule information that stipulates conversion rules for converting attribute assignment information to attribute information used in a function encryption algorithm; and logical formula conversion rule information that stipulates conversion rules for converting logical formula assignment information to logical information used in the function encryption algorithm. Using one of the sets of conversion rule information contained in the conversion rule information pair, first attribute information or first logical information is obtained from input information. This information is used in encryption processing. In decryption processing, decryption processing of encrypted information is performed using a decryption key produced using second attribute information or second logical information obtained from user information using the other set of conversion rule information.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Method and apparatus for judging necessity of performing integration test
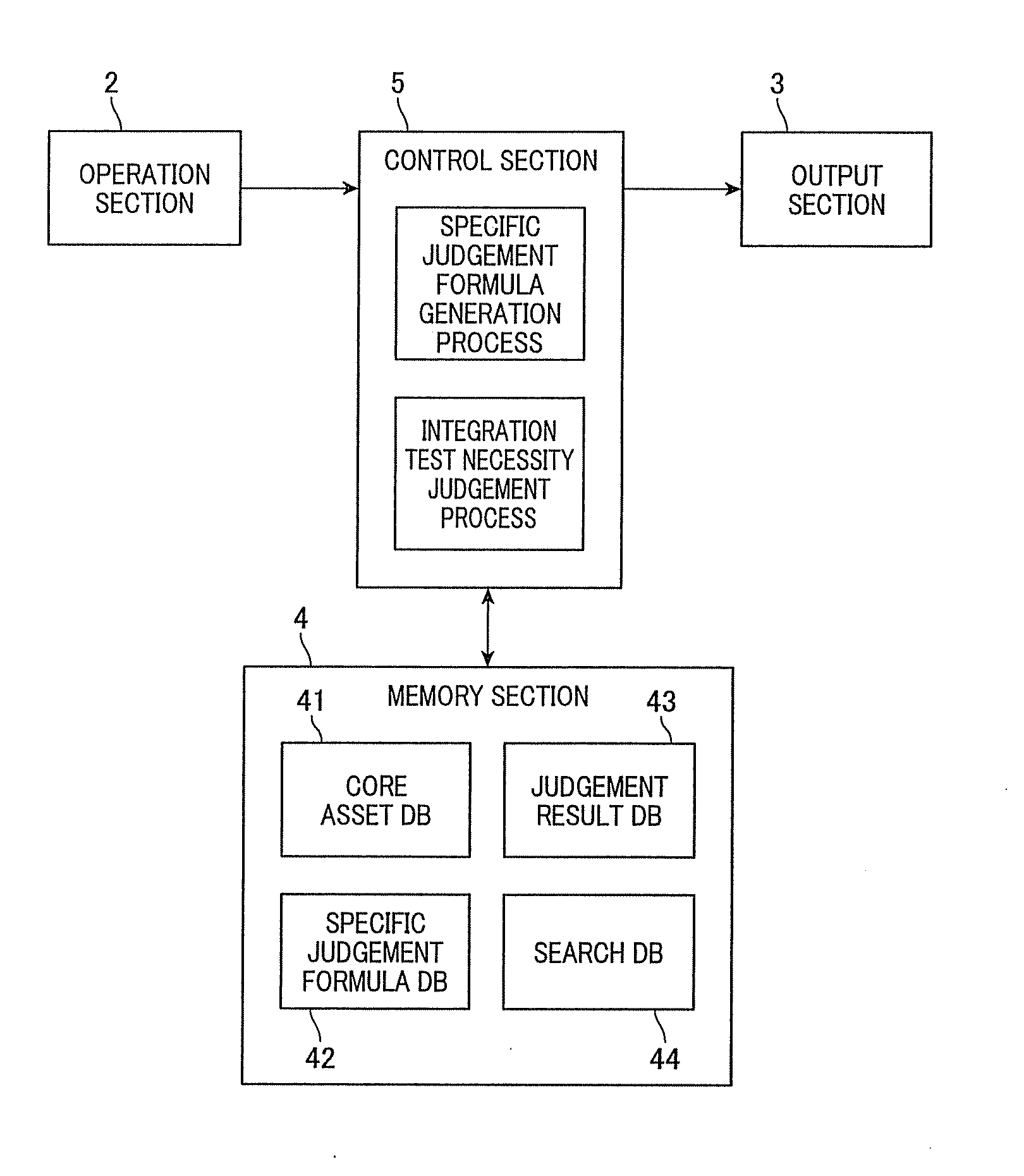
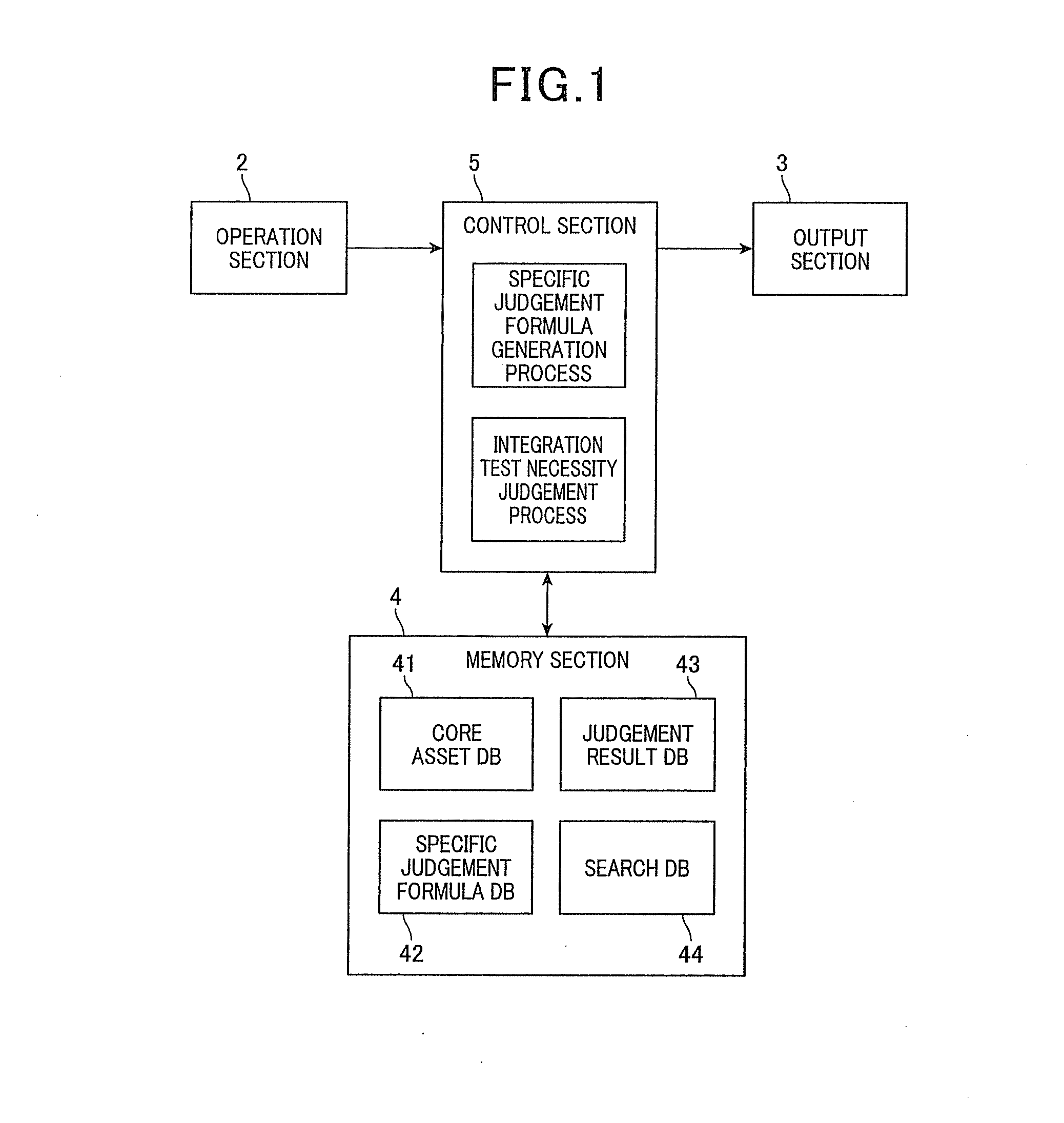
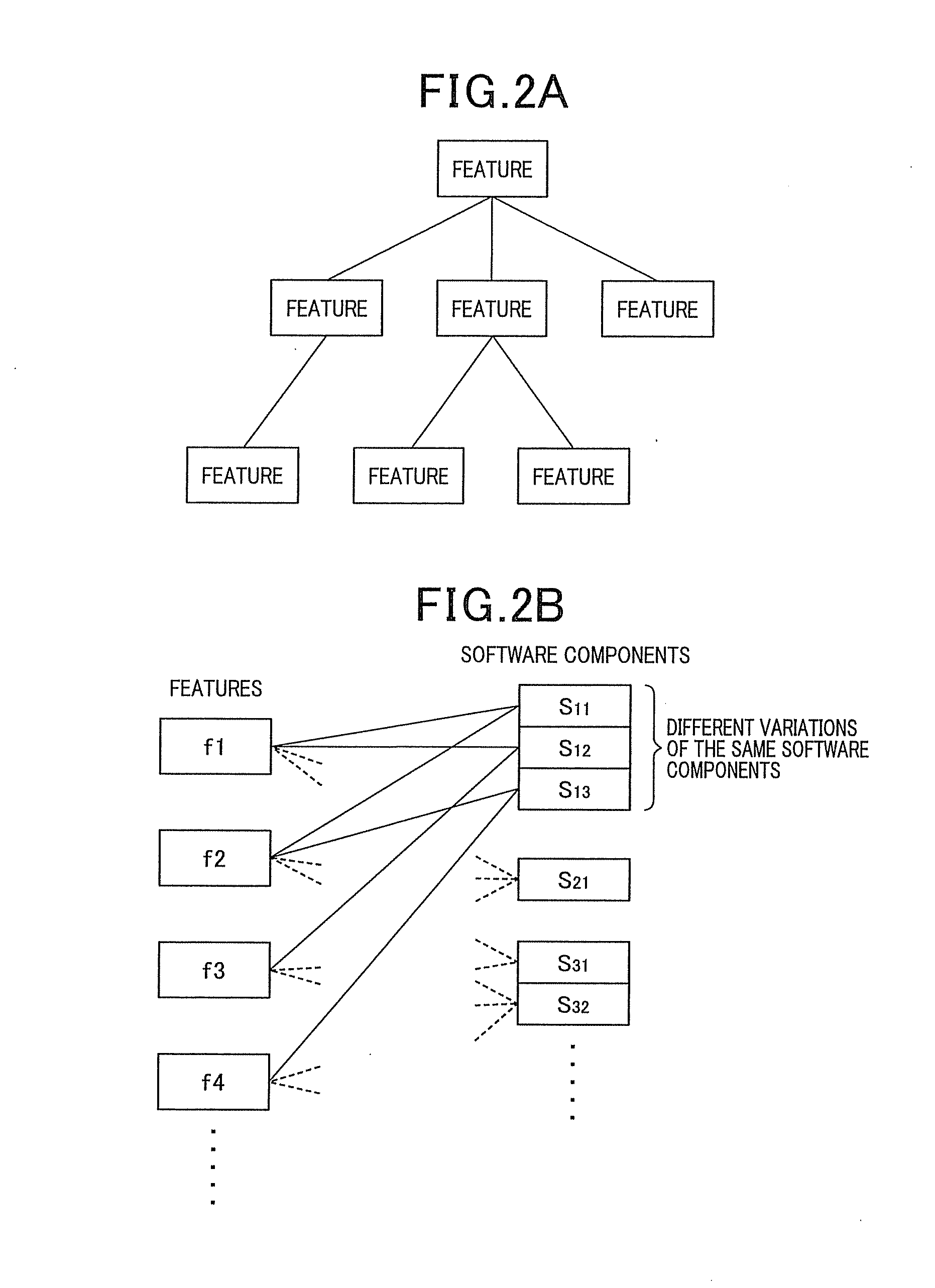
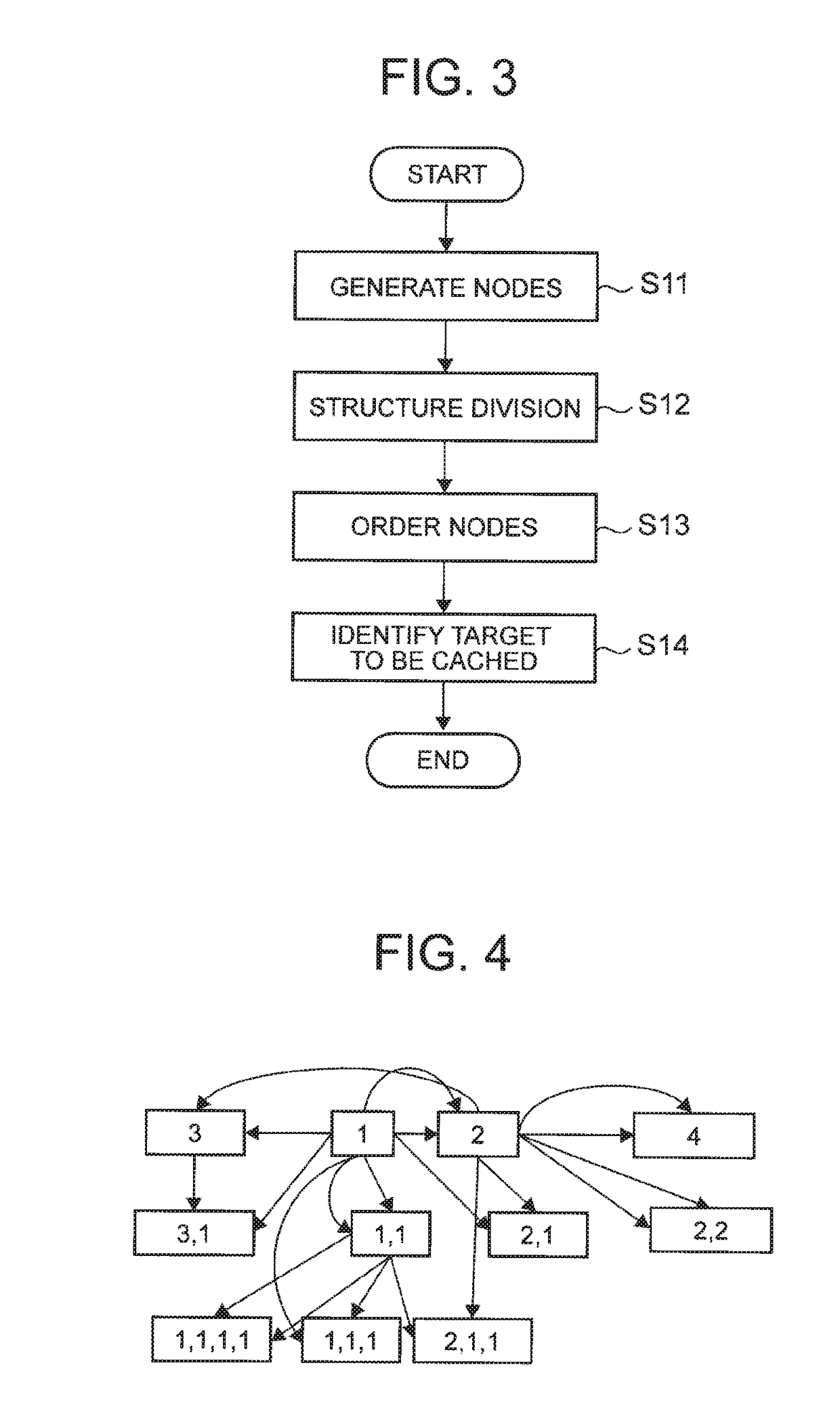
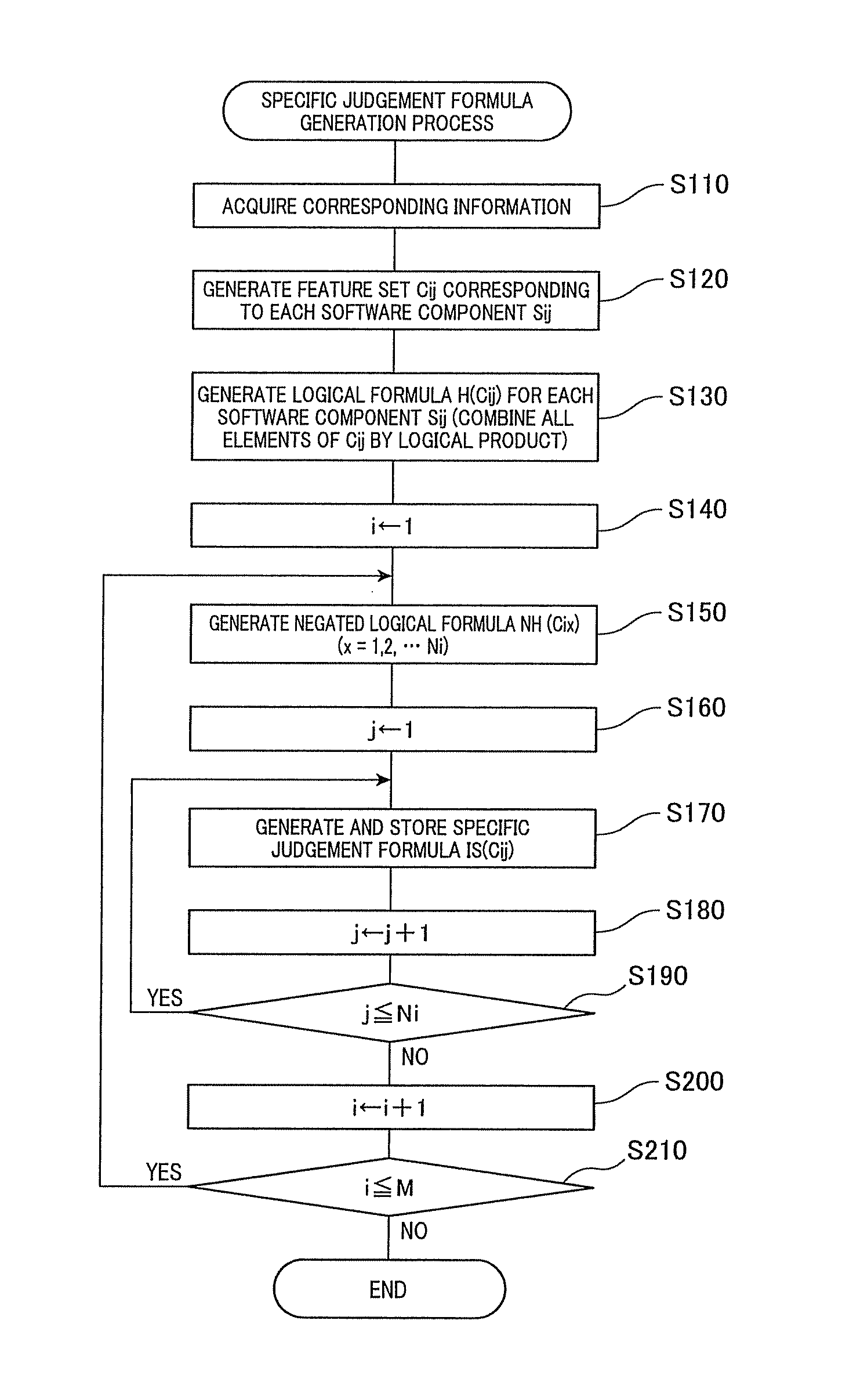
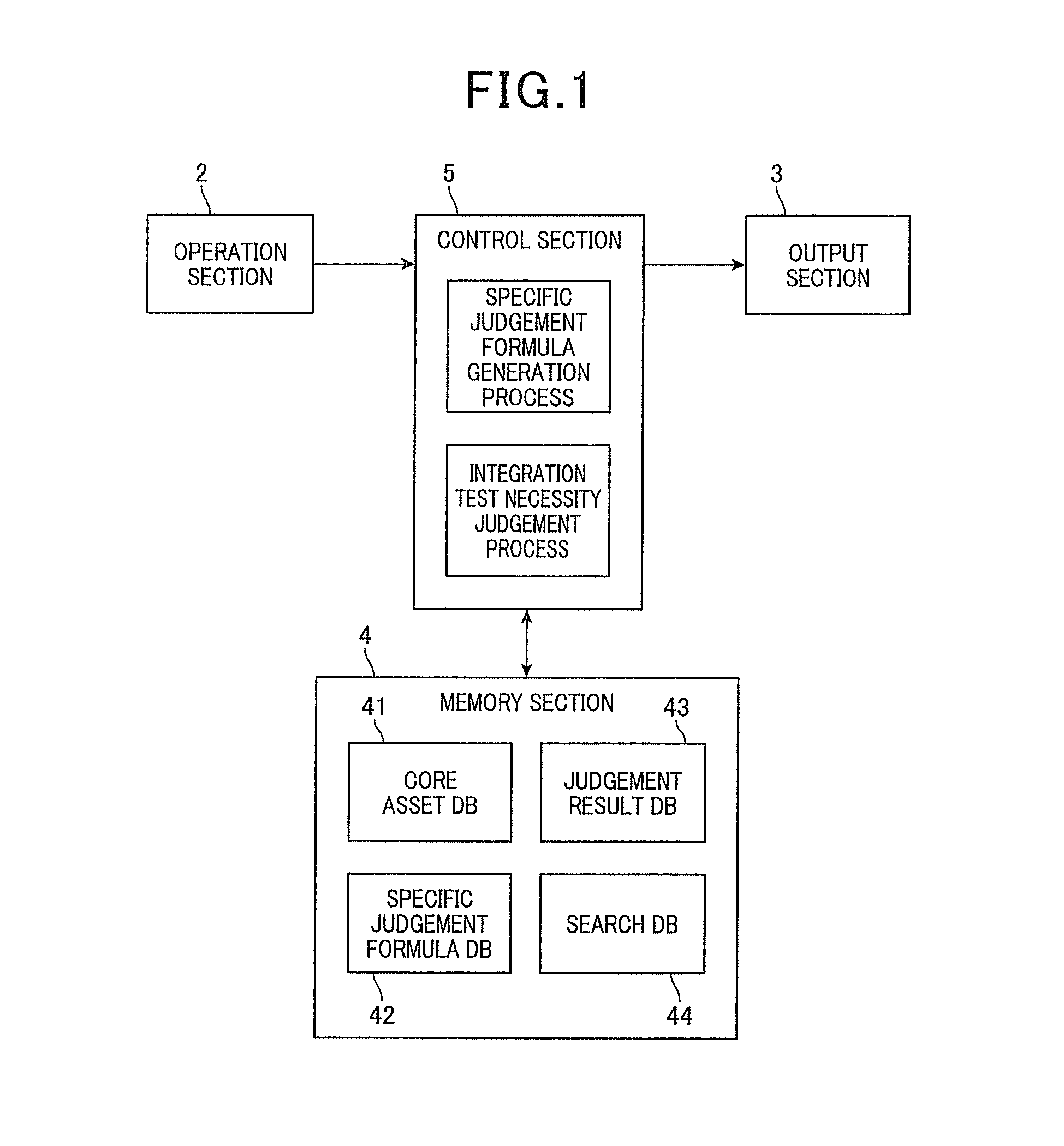
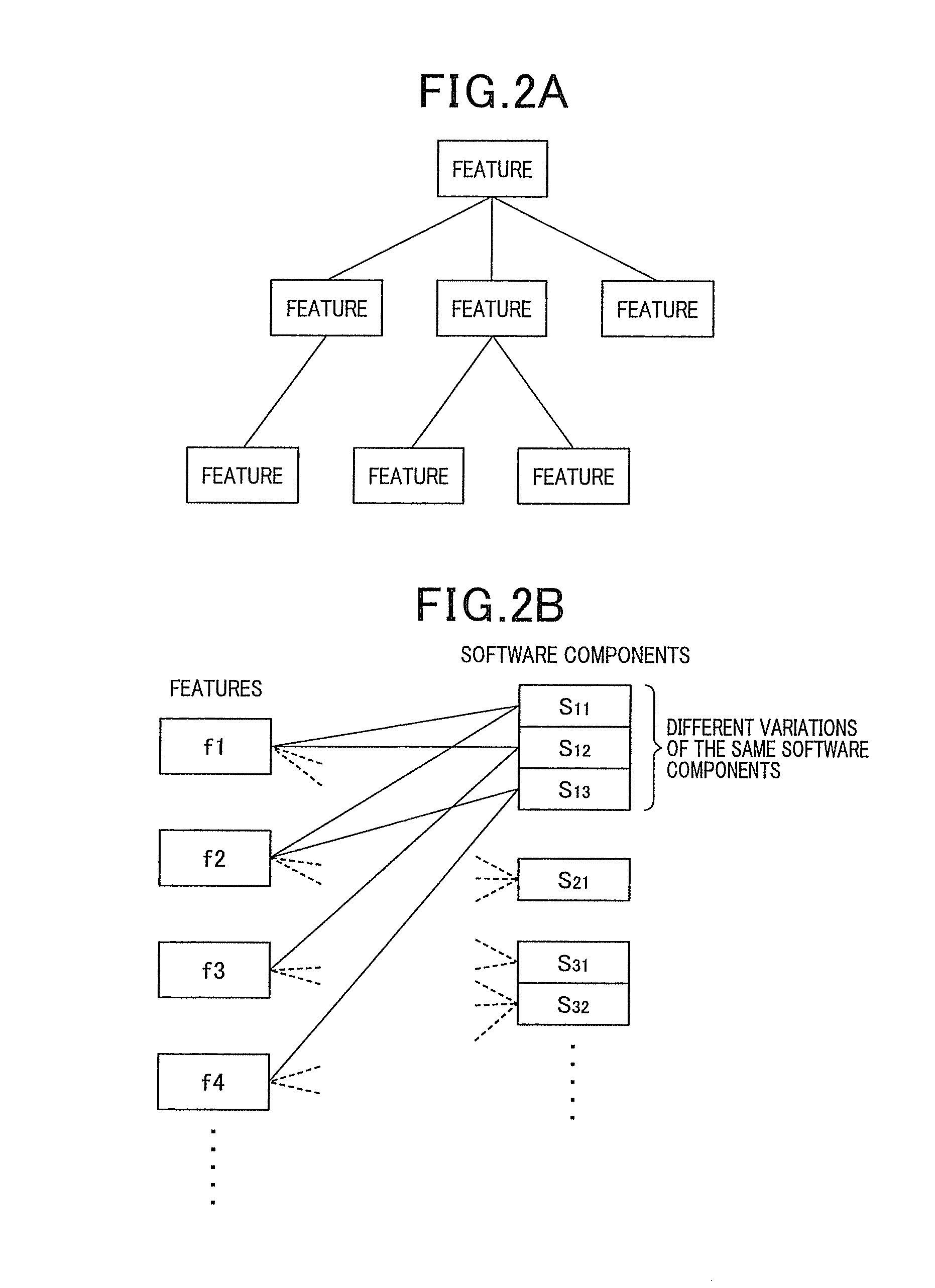
ActiveUS20140019938A1Reduce laborEasy to judgeHardware monitoringReverse engineeringState variableIntegration testing
Whether or not an integration test between or among software components is necessary is judged. Corresponding information between features is acquired, which configures a feature model expressing characteristics of a group of products produced by the software product line, and a type and variations of each software component. For each software component, a set of state variables of all of the features corresponding to the software components is produced based on the corresponding information. For each software component, a specific logical formula is produced. Two or more software components are designated. A necessity judgment formula is produced by logical-product combining all the specific judgment formulas, for the software components designated. It is judged that the integration test is necessary when the necessity judgment formula always shows FALSE (inconsistent formula) and not necessary when the necessity judgment formula shows unclearness as to TRUE or FALSE, or always shows TRUE (valid formula).
Owner:DENSO CORP
Automatic generation method for busbar parametrized material bill and process route
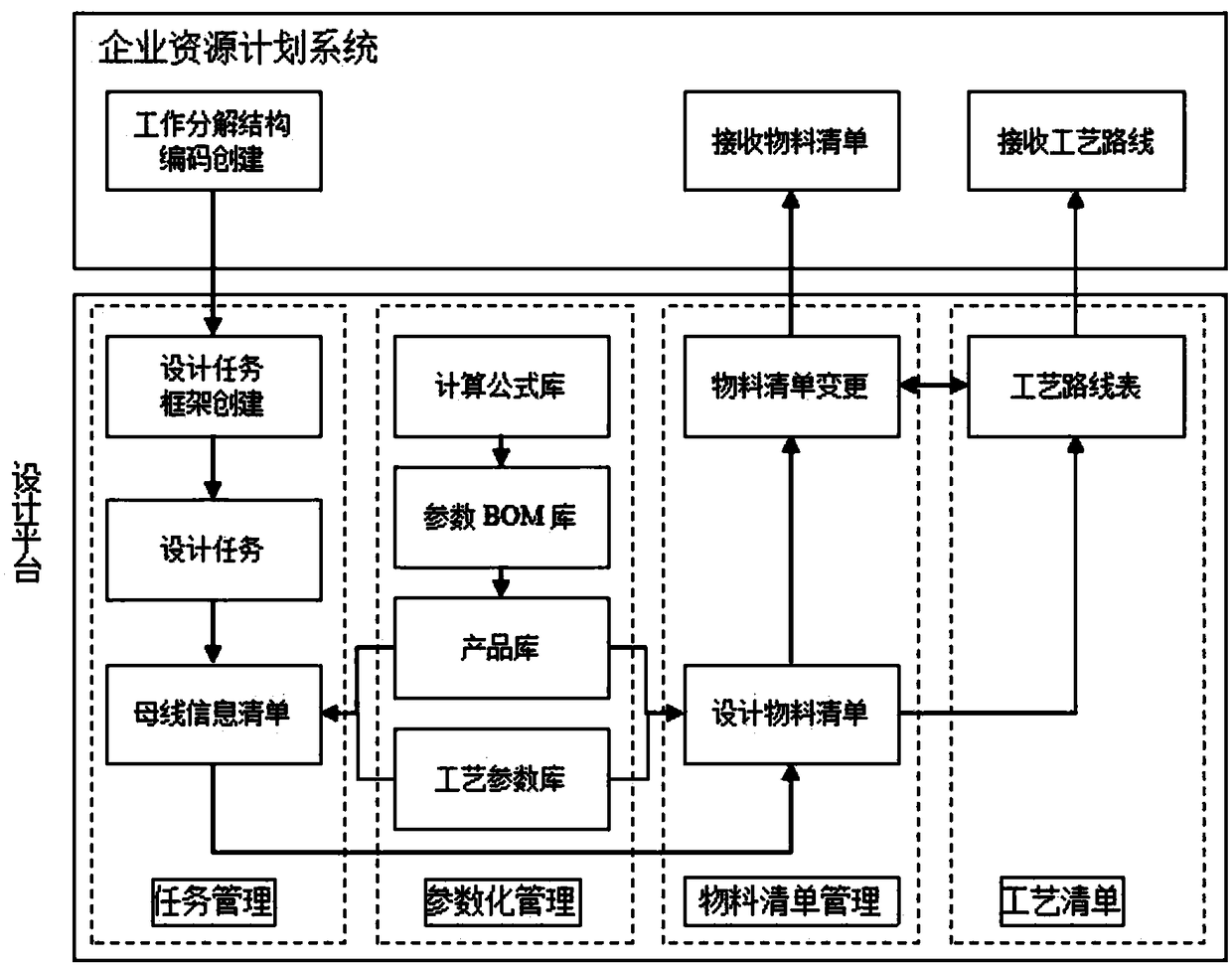
InactiveCN108121874AMeet individual needsAchieve sharingForecastingDesign optimisation/simulationBill of materialsComputer science
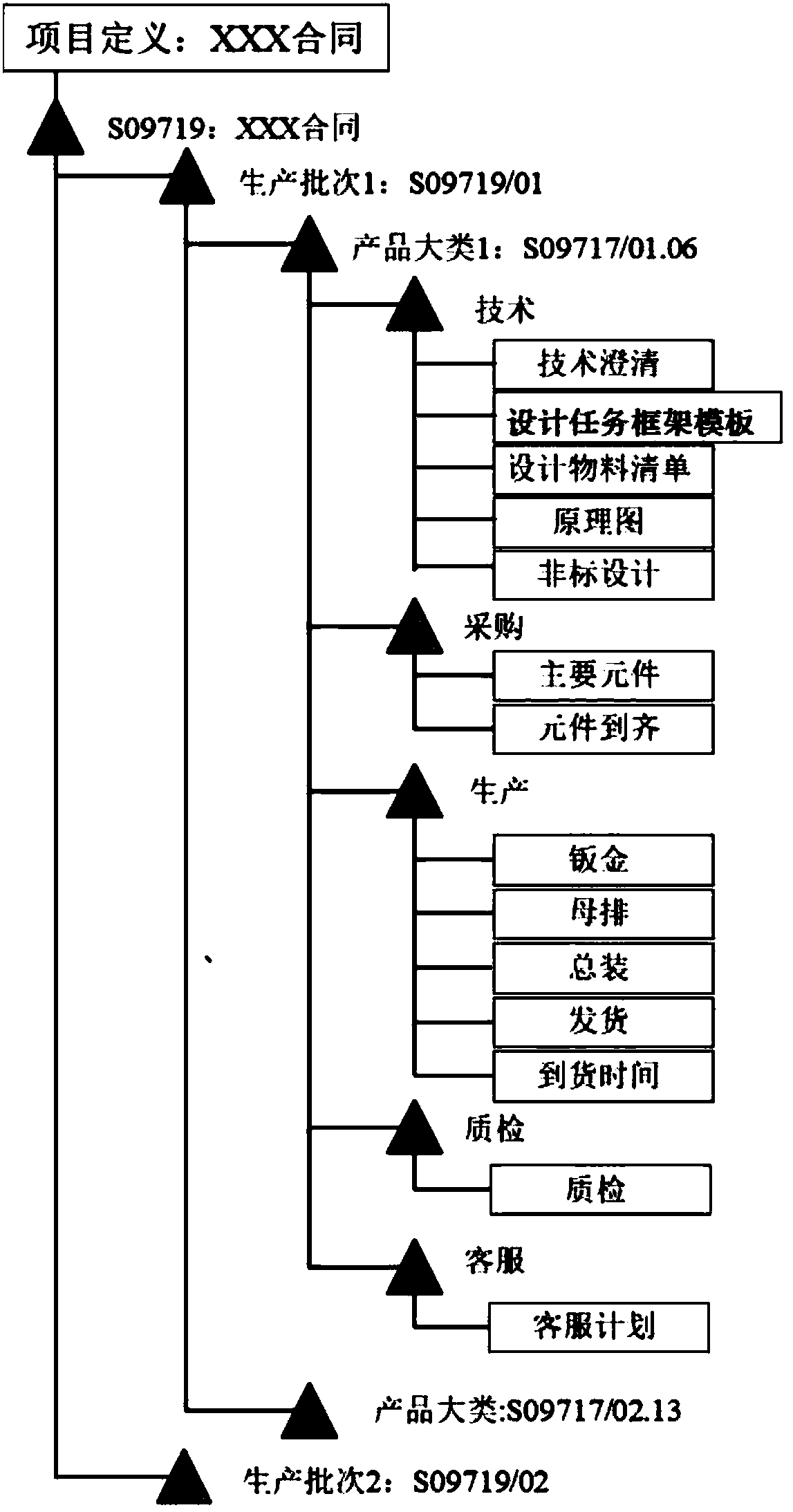
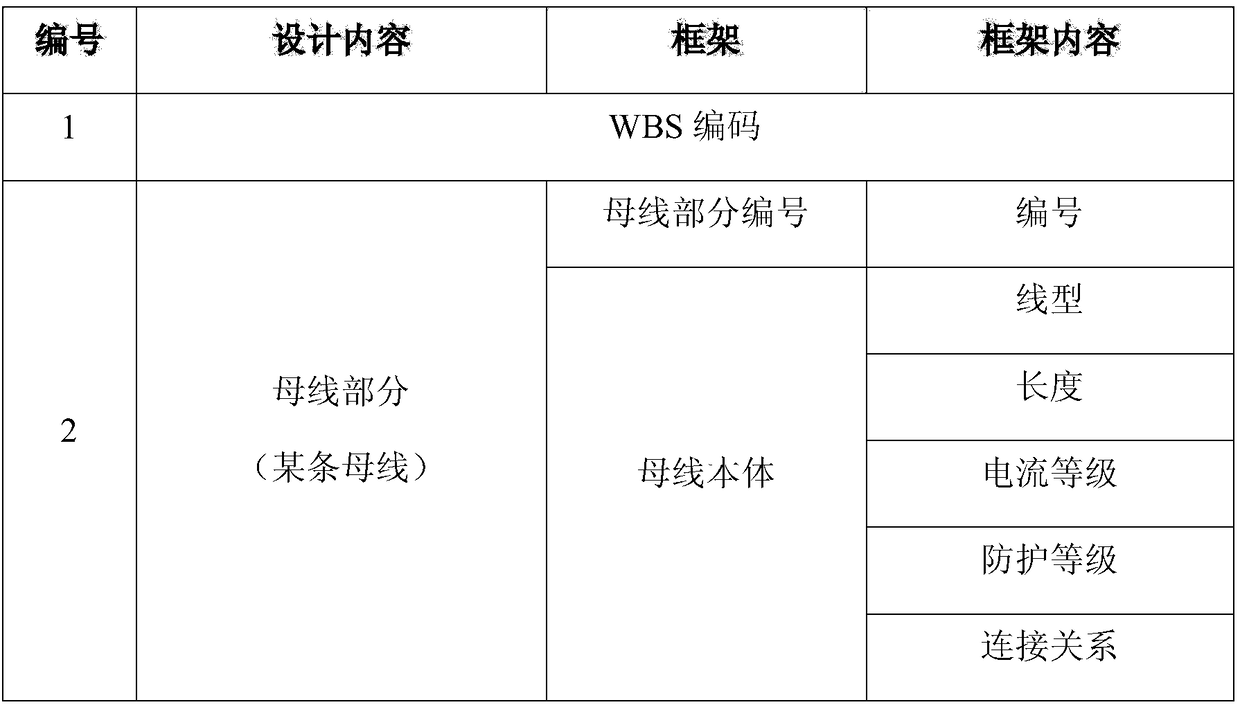
The invention discloses an automatic generation method for a busbar parametrized material bill and a process route, and belongs to the technical field of IT information. The method comprises the following steps: 1) according to a design task framework template of a work breakdown structure in a busbar design production process, creating a design task framework; 2) according to the design task framework, substituting into a logical formula corresponding to a design material bill item for calculating, and generating the busbar design material bill; and 3) according to the design material bill, substituting into a process route formula for calculating, and generating the process route. The method is capable of supporting the parametrized design, rapidly generating the material bill, supporting the need change of a customer, integrally completing the design change, the material bill change and the process route change, and seamless-connecting with the busbar production process.
Owner:DAQO GROUP CO LTD
Traceability method for determining moisture of solid material
ActiveCN104568648ARealize automatic generationEnsure reliabilityWeighing by removing componentData acquisitionMoisture
The invention relates to a traceability method for determining moisture of a solid material. The method comprises the following steps: writing a logical formula for determining moisture of the solid material into a computer program; connecting a computer, an electronic scale, a ticket printer and a bar code scanning gun through a data line; entering a main program interface, and setting the determined solid material information, alarm prompt tone and measurement accuracy; respectively weighing and scanning an empty sample plate, a sample plate with a sample and a sample plate for a dried sample; and finally printing the determined solid material information, weighing time, operation personnel information, weighing data and calculation result by virtue of a printer so as to finish the determination process. Compared with the prior art, the traceability method has the beneficial effects that human disturbance factors in the determination process are avoided by automatic information data collection and automatic data generation technologies; automatic generation, direct printing and information storage of each batch of material inspection data are achieved; and the reliability and the traceability of the determination result are ensured on the basis of strictly executing the national standard.
Owner:ANSTEEL GRP CHAOYANG ANLING STEEL & IRON
Bounded model inspection method based on expanded linear time invariance
InactiveCN107292027AReduce complexityImprove efficiencyConstraint-based CADSpecial data processing applicationsSemanticsAutomaton
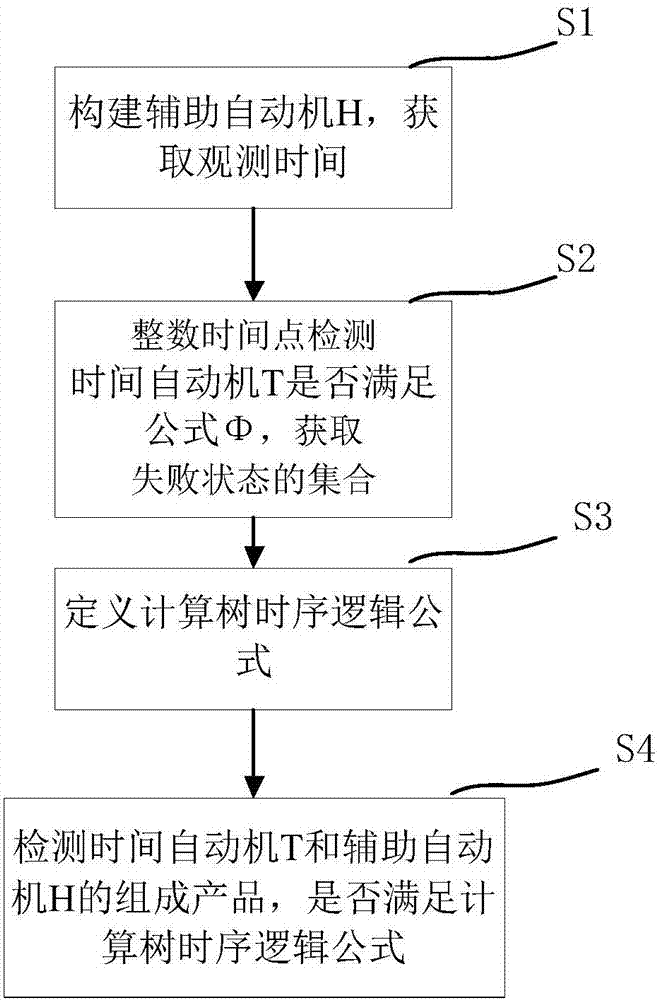
The invention relates to a bounded model inspection method based on an expanded linear time invariance, which includes steps of S1, structuring an assistant automat H according to a time automat T under a given discrete time semantics and an expanded linear time invariance formula phi; S2, detecting if the time automat T of every integer time point meets the formula phi within the setting scale of the observation time, and acquiring a set which disagrees with the state of the formula phi; S3, defining a logical formula of a calculating tree for describing the characteristics of the set; S4, detecting if the constituting product of the time automat T and the assistant automat H can meet the logical formula of the calculating tree; if it does not meet, the time automat T meets the an expanded linear time invariance formula phi; otherwise, the automat T does not meet the expanded linear time invariance formula phi. Compared with the prior art, the bounded model inspection method has better efficiency and lower algorithm complexity.
Owner:TONGJI UNIV
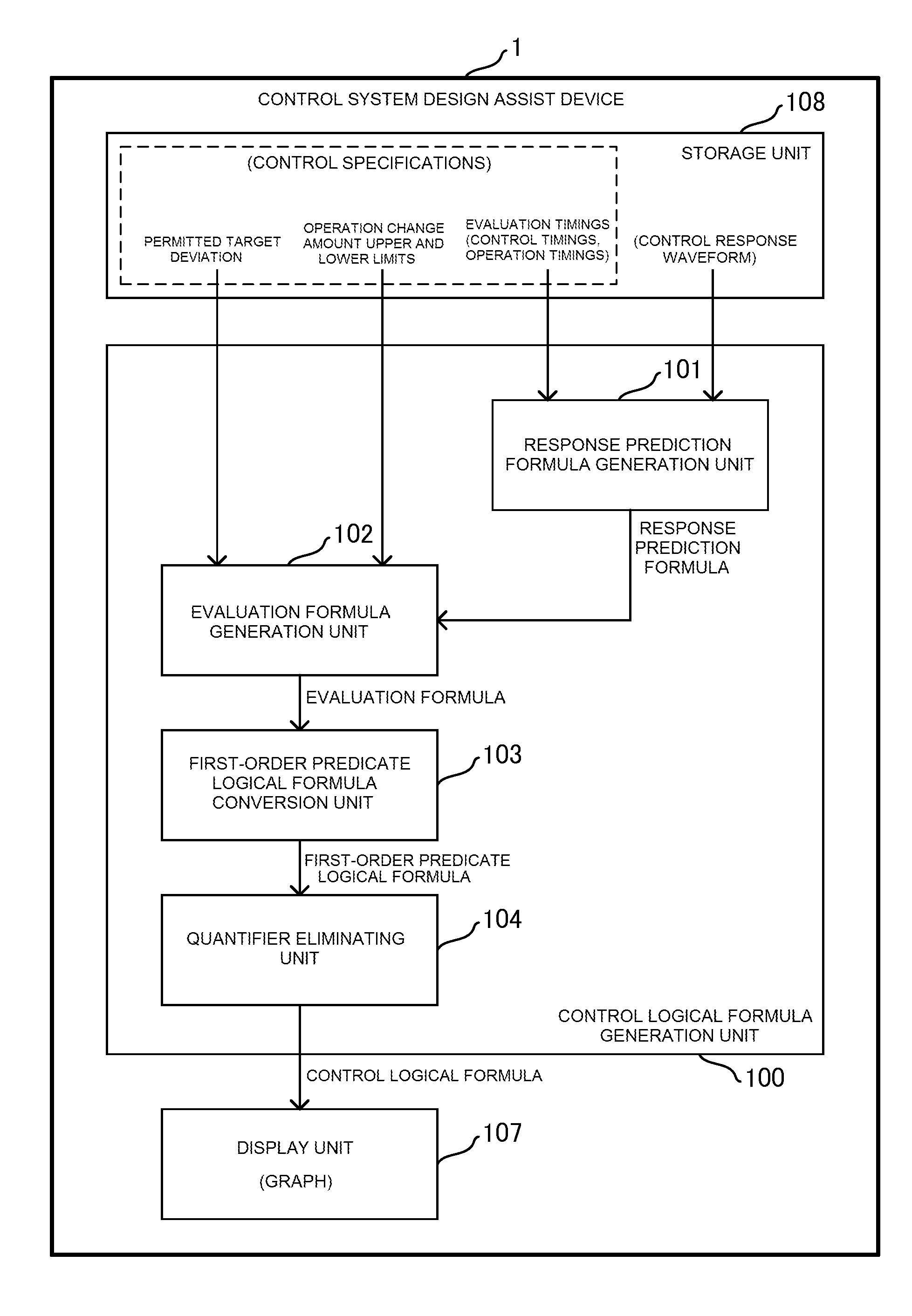
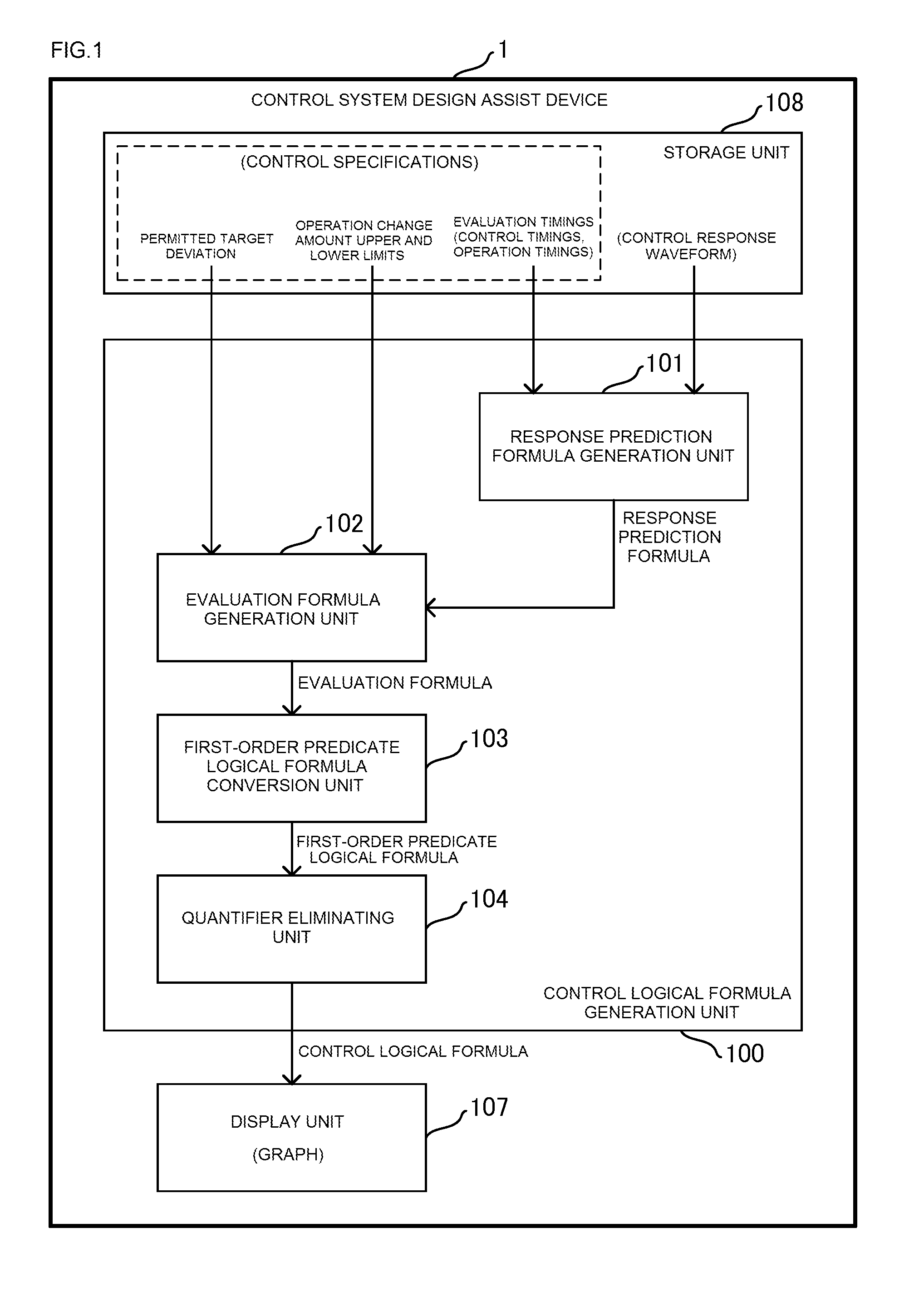
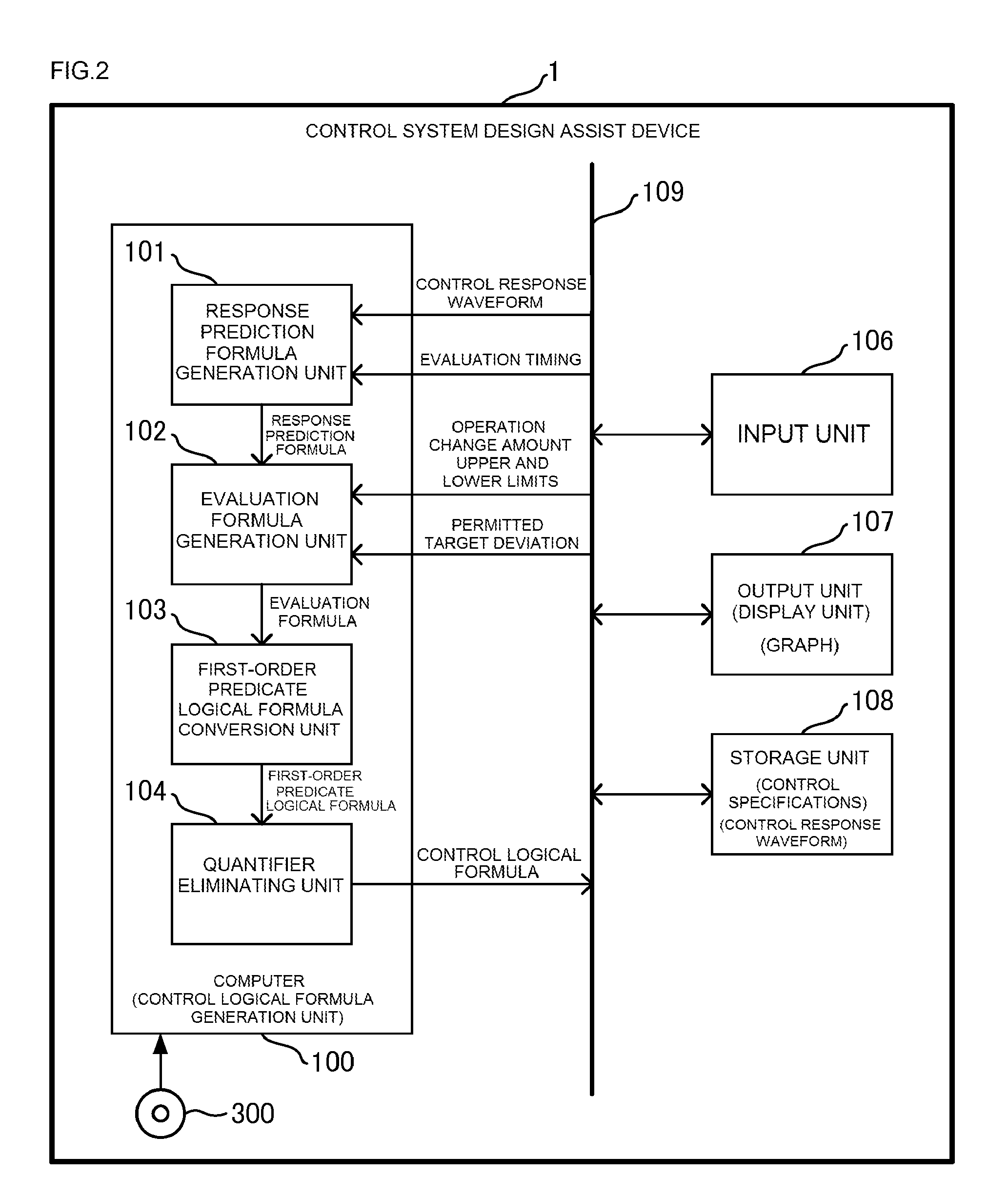
Control system design assist device, control system design assist program, control system design assist method, operation change amount calculation device and control device
ActiveUS20160063142A1Improve controlLow costComputation using non-denominational number representationControllers with particular characteristicsControl system designLogical formula
A control system design assist device which assists design of a control system that controls a control object such that the control object outputs a control amount according to a target value. The design assist device generates a response prediction formula predicting a variation value of the control amount at each control timing included in the sequence of control timings by using an amount of change of the operation amount at each operation timing included in the sequence of operation timings; generates evaluation formulas; and converts a logical product formula into a first first-order predicate logical formula. The design assist device generates a control logical formula indicating a relationship between the current value of the target deviation and the change amount of the operation amount.
Owner:FUJI ELECTRIC CO LTD
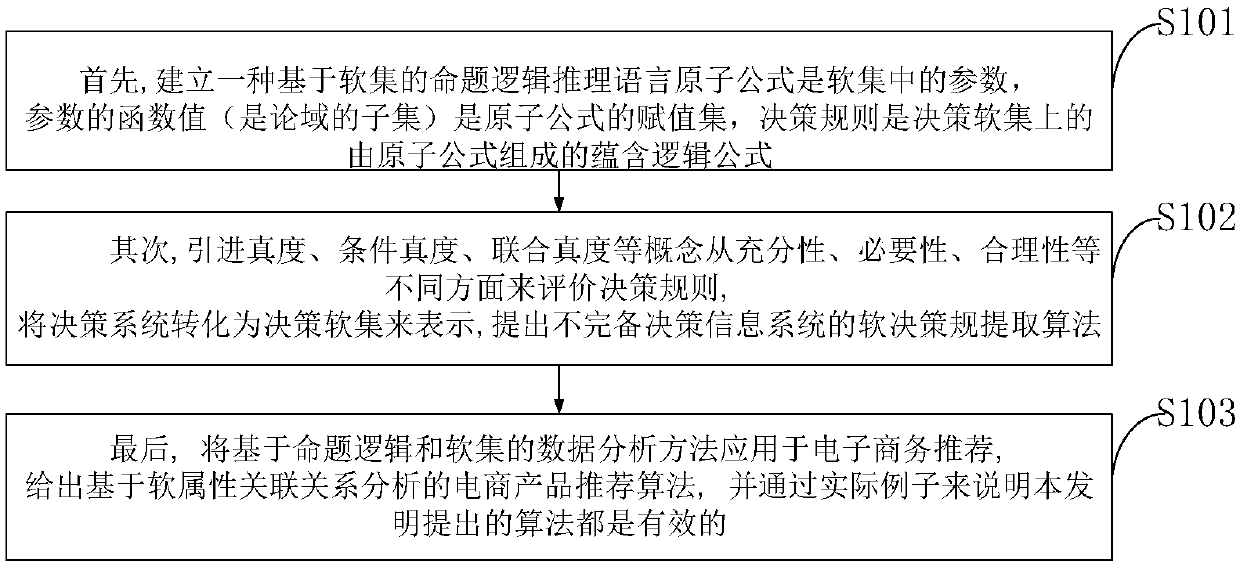
E-commerce recommendation technology and system based on soft-set decision rule analysis
ActiveCN108133407AInnovativeNovel method constructionVisual data miningStructured data browsingValue assignmentHuman language
The invention belongs to the technical field of computers, and discloses an e-commerce recommendation technology and system based on soft-set decision rule analysis. A propositional logical reasoninglanguage based on soft sets is established, and in the reasoning language, an atomic formula is a parameter e in a soft set, a function value F(e) of the parameter e is a value assignment set of the atomic formula e, and a soft decision rule is an implicit logical formula formed by atomic formulas on a decision soft-set; quantitative indexes of soft truth degrees, conditional soft truth degrees, joint soft truth degrees, soft similarity degrees, logical soft degrees and the like are introduced to evaluate soft decision rules from different aspects of adequacy, necessity and rationality; a decision system is transformed into the decision soft set, and a soft-decision-rule extraction method of the incomplete decision system is provided; and a data analysis method based on propositional logicand the soft set is applied to e-commerce recommendation. Through practical examples of the invention, it is illustrated that the methods provided by the invention are all effective; and theoreticalanalysis of the technology has innovativeness, method construction novelty and technical-means practicability.
Owner:XIANGNAN UNIV
Networked online monitoring method based on multi-stage combination
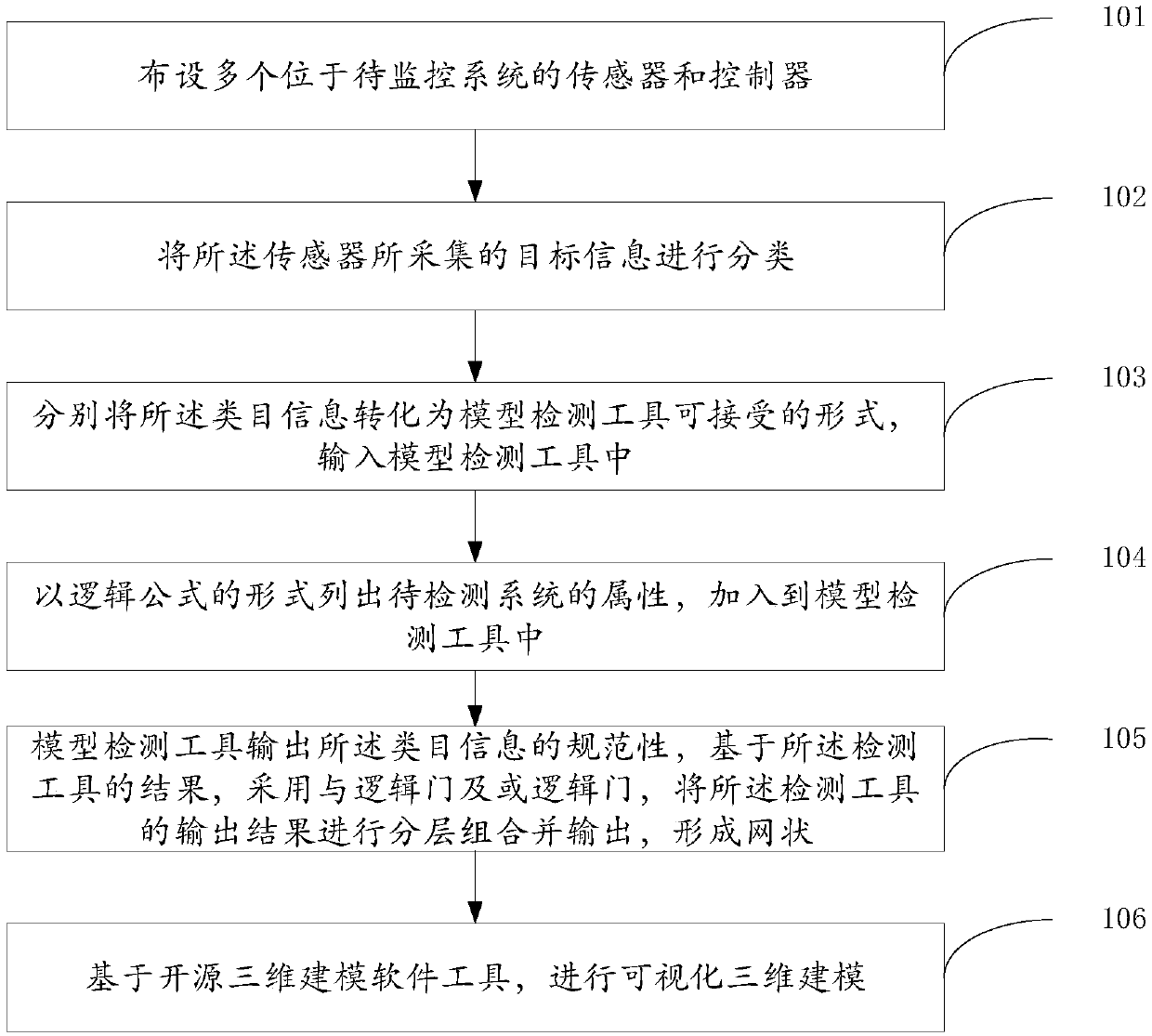
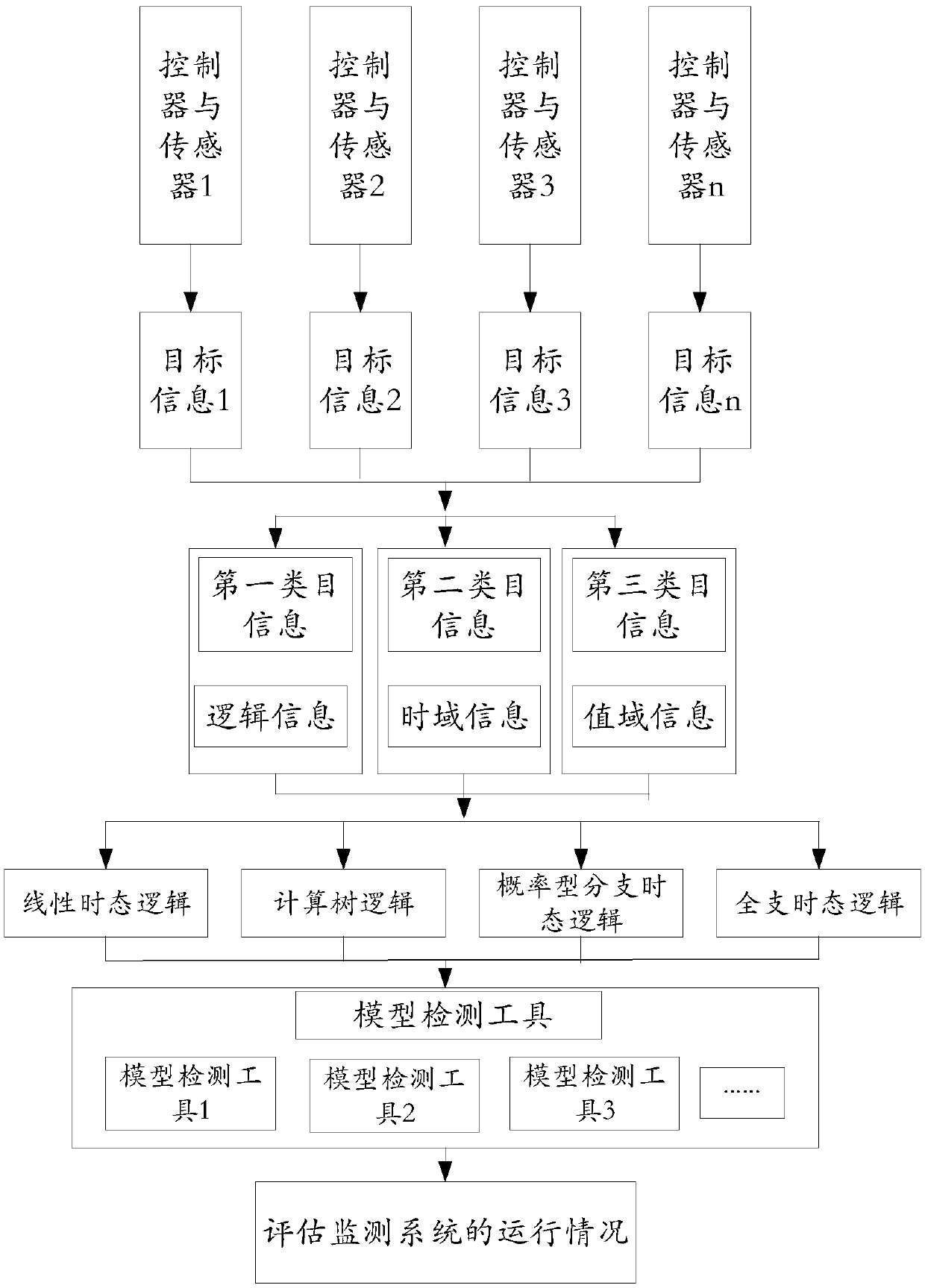
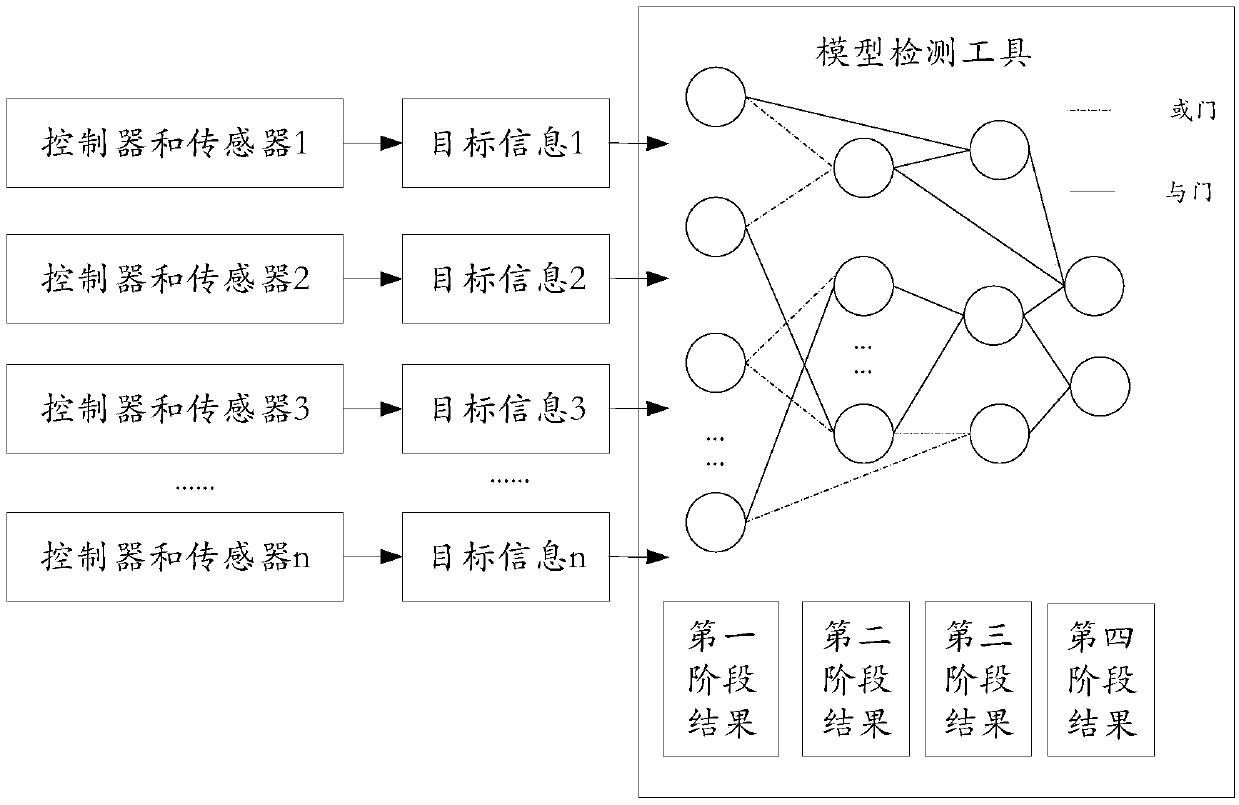
ActiveCN109613851ATo achieve the purpose of combination analysisSolve problems that cannot be quickly identifiedProgramme controlComputer controlMultiple sensorDimensional modeling
The invention discloses a networked online monitoring method based on a multi-stage combination. The networked online monitoring method based on the multi-stage combination comprises the following steps that multiple sensors and controllers which are located in a to-be-monitored system are arranged; target information collected by the sensors is classified; the category information is converted into a form capable of being accepted by a model detection tool and input into the model detection tool; the attributes of the to-be-detected system are listed in the form of logical formulas and addedinto the model detection tool; the model detection tool outputs specifications for the category information, and output results of the detection tool are combined in a layered mode and output to forma net shape by adopting an AND logic gate and an OR logic gate on the basis of the results of the detection tool; and visualized three-dimensional modeling is conducted on the basis of an open-sourcethree-dimensional modeling software tool. Through the steps, the purpose of combining and analyzing multiple kinds of detection information is achieved, and then a feasible analysis method is providedfor overall grasping of technical personnel on state information of the monitored system and local updating of rules.
Owner:BEIHANG UNIV
Feature enumeration system, feature enumeration method and feature enumeration program
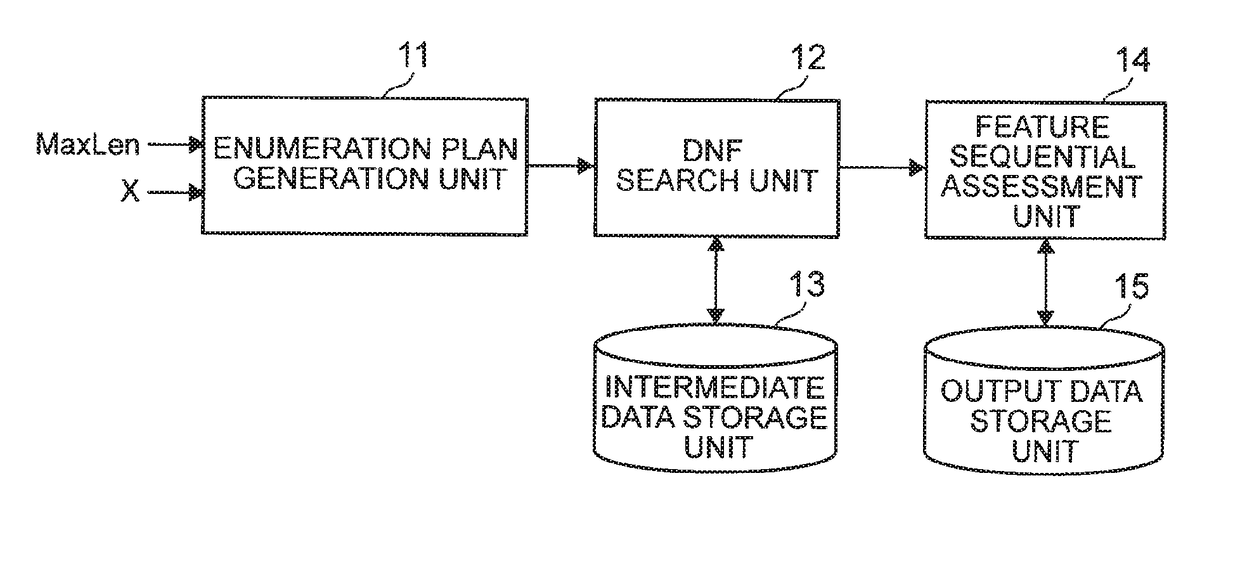
ActiveUS20170109629A1Avoid wastingBiostatisticsKnowledge representationProgramming languageLearning data
An enumeration plan generation unit 81 generates a set of logical formula structures each representing a way of combining logical formula expressions each representing a combination of features by use of the features of learning data items and the maximum number of features to be combined, and generates partial logical formula structures by dividing a logical formula expression included in each of the generated logical formula structures into two, and generates an enumeration plan in which the partial logical formula structures are linked to the logical formula structure from which the partial logical formula structures are divided. The feature generation unit 82 generates a new feature that is a combination of the features corresponding to the generated partial logical formula structures. Furthermore, the enumeration plan generation unit 81 divides the logical formula structure into two such that the numbers of the features included in the two partial logical formula structures generated from each of the logical formula structures are substantially equal.
Owner:NEC CORP
Method and apparatus for judging necessity of performing integration test
ActiveUS8959487B2Reduce laborEasy to judgeHardware monitoringReverse engineeringState variableIntegration testing
Whether or not an integration test between or among software components is necessary is judged. Corresponding information between features is acquired, which configures a feature model expressing characteristics of a group of products produced by the software product line, and a type and variations of each software component. For each software component, a set of state variables of all of the features corresponding to the software components is produced based on the corresponding information. For each software component, a specific logical formula is produced. Two or more software components are designated. A necessity judgment formula is produced by logical-product combining all the specific judgment formulas, for the software components designated. It is judged that the integration test is necessary when the necessity judgment formula always shows FALSE (inconsistent formula) and not necessary when the necessity judgment formula shows unclearness as to TRUE or FALSE, or always shows TRUE (valid formula).
Owner:DENSO CORP
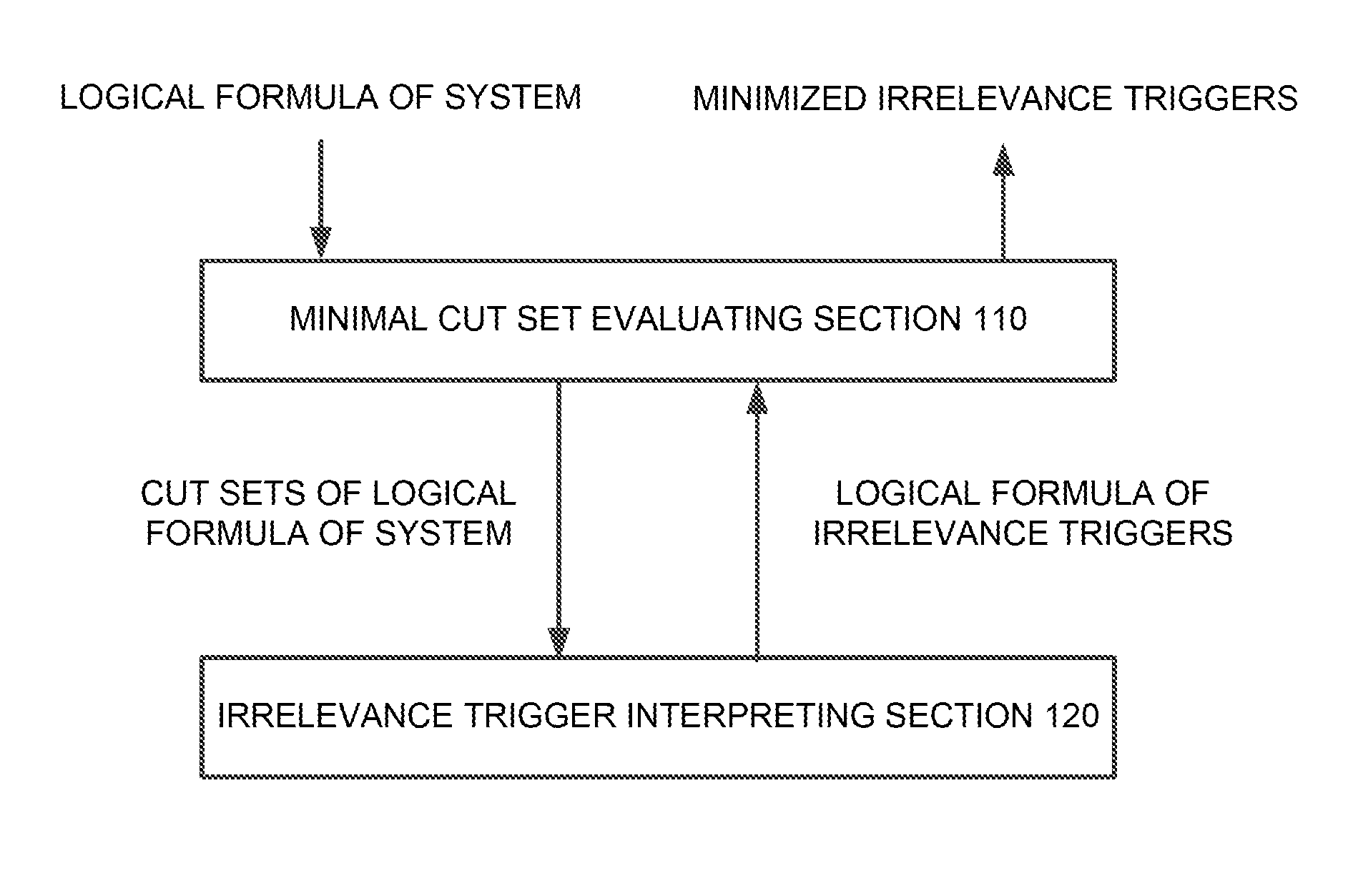
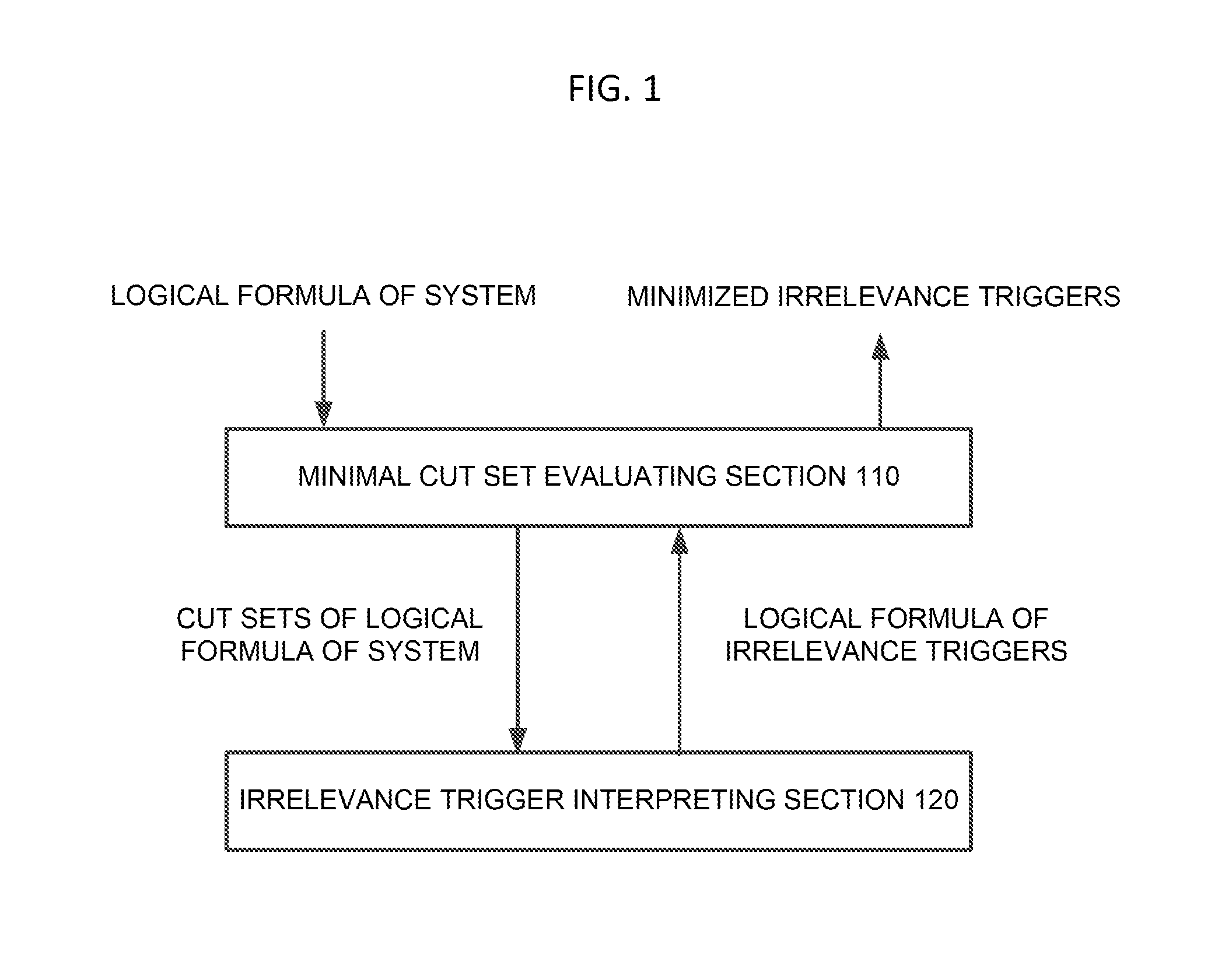
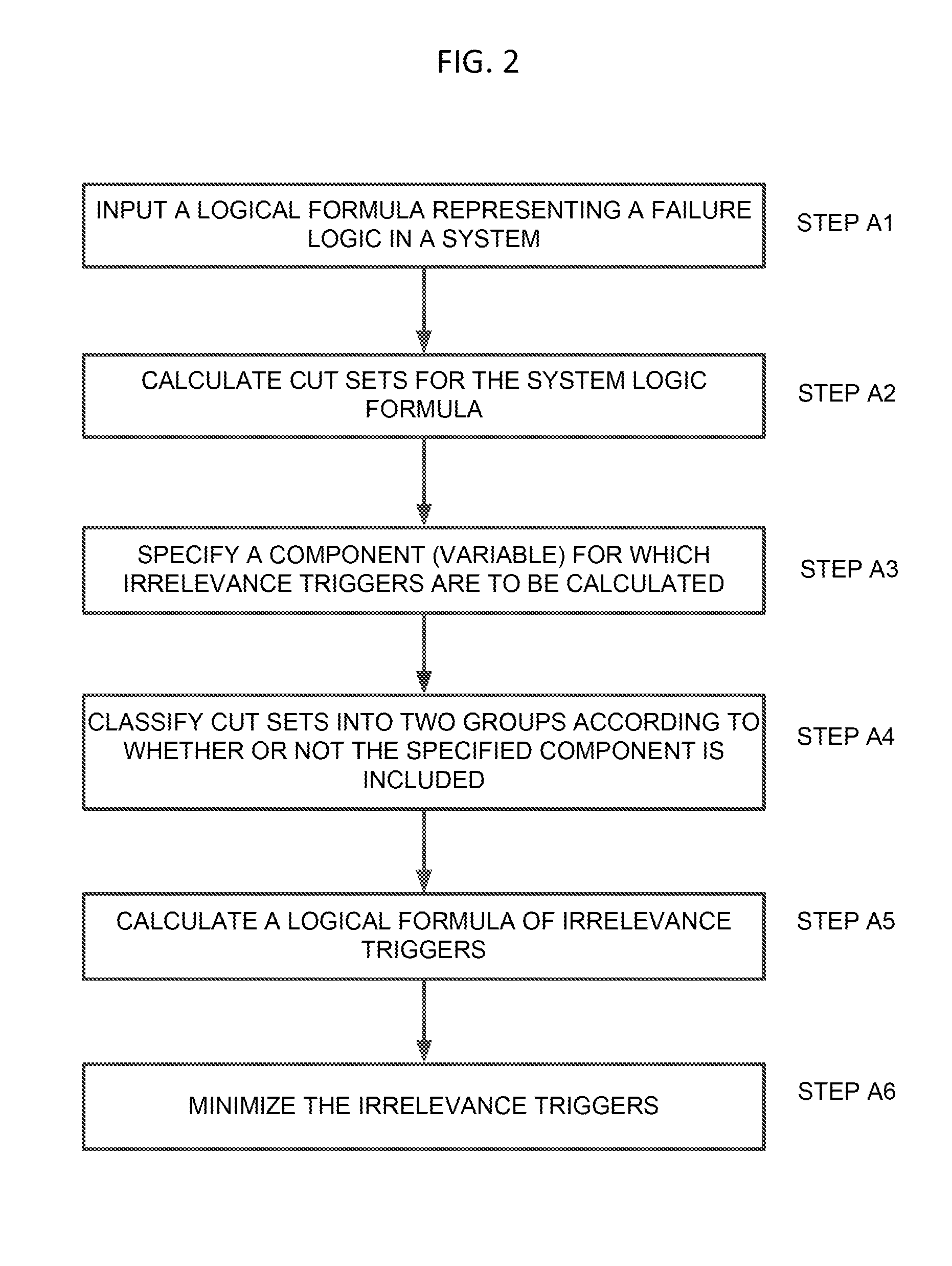
Identification system, identification method, and program
The present invention is an identification system comprising: an irrelevance trigger interpreting section for calculating a logical formula of irrelevance triggers for a component in a system from a cut set logical formula f of a system failure; and minimal cut set evaluating means for minimizing the logical formula of the irrelevance triggers, which has been calculated by said irrelevance trigger interpreting section, to calculate the irrelevance triggers for said component.
Owner:NEC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com