Method for verifying security model of computer system
A computer system and security model technology, applied in computer security devices, computing, digital data authentication, etc., can solve the problems of model state explosion, inability to reflect the dynamic properties of security models, and lack of timing behavior determination of security models, and improve the degree of automation. , the effect of verification ability improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
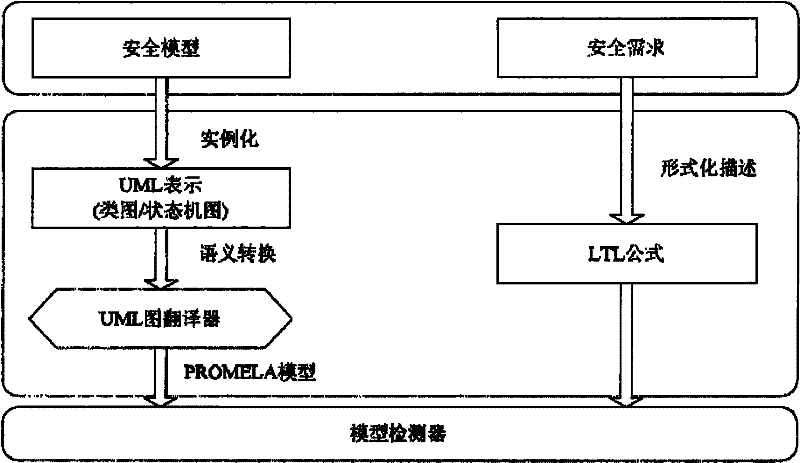
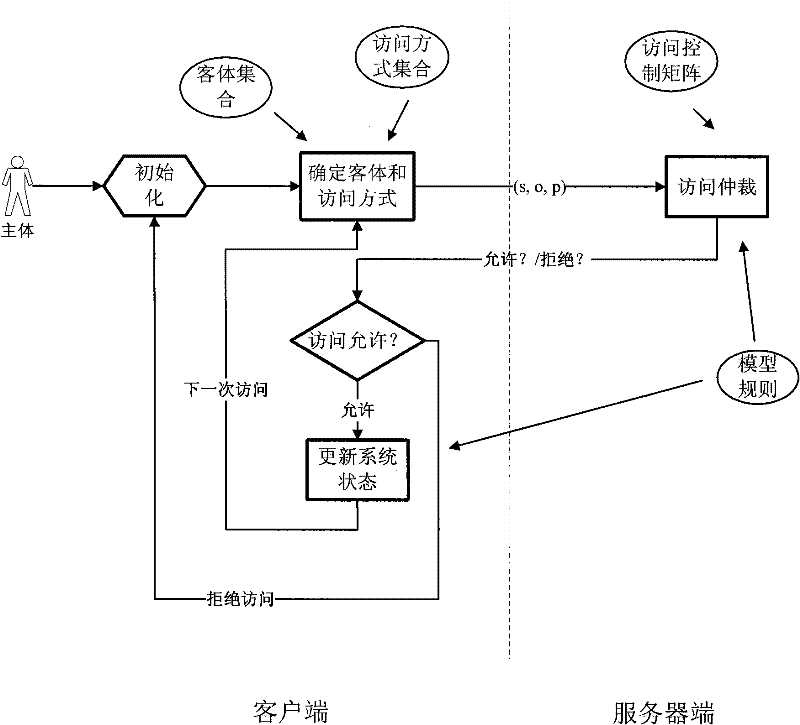
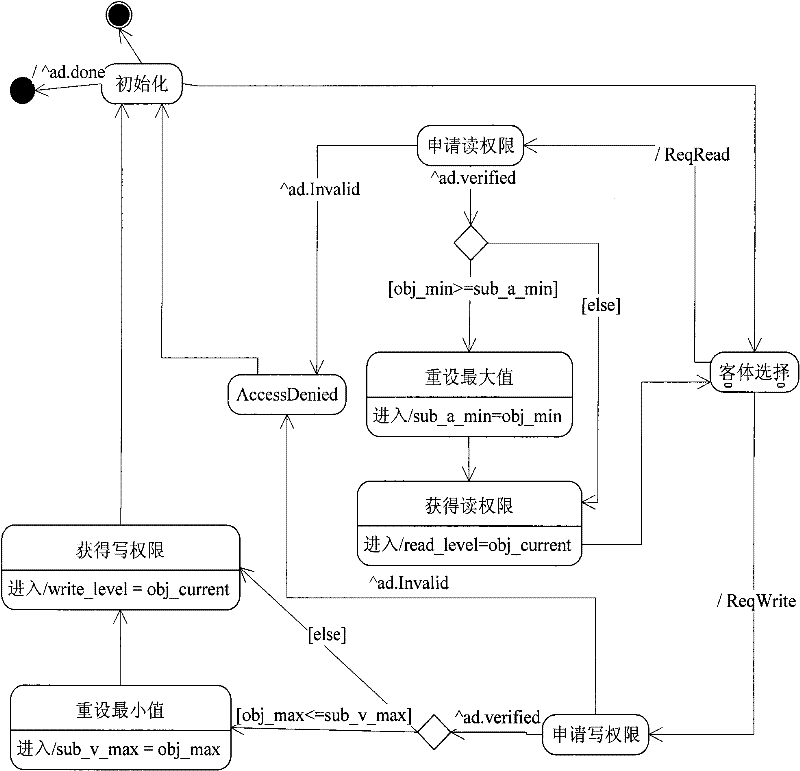
[0038] The input of the present invention is a computer system security model and security attributes to be verified. The input information is divided into two parts, one part comes from the computer system security model that will be implemented or has been implemented in development, it can come from any computer software system and equipment that needs security enhancement, such as hosts, servers, intrusion detection systems, routers, Firewall and so on. The input models obtained after formal abstraction and extraction of security mechanisms on these devices can be used as input information of the present invention. The other part comes from the security requirements of these systems and equipment or the security attributes that should be met, such as confidentiality and data integrity. The above information requirements are complete and comprehensive, the more complete the information, the more accurate the verification results. Through the layer-by-layer processing and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com