Wireless sensor network security protocol verification method based on model checking
A network security protocol and wireless sensor technology, applied in the field of security protocol verification, can solve the problems that the end-to-end encryption mechanism cannot be used in wireless sensor networks, digital signatures cannot be performed, sensor nodes have weak processing capabilities, storage capabilities, and communication capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] Certain embodiments of the accompanying drawings of the present invention are described in more detail below.
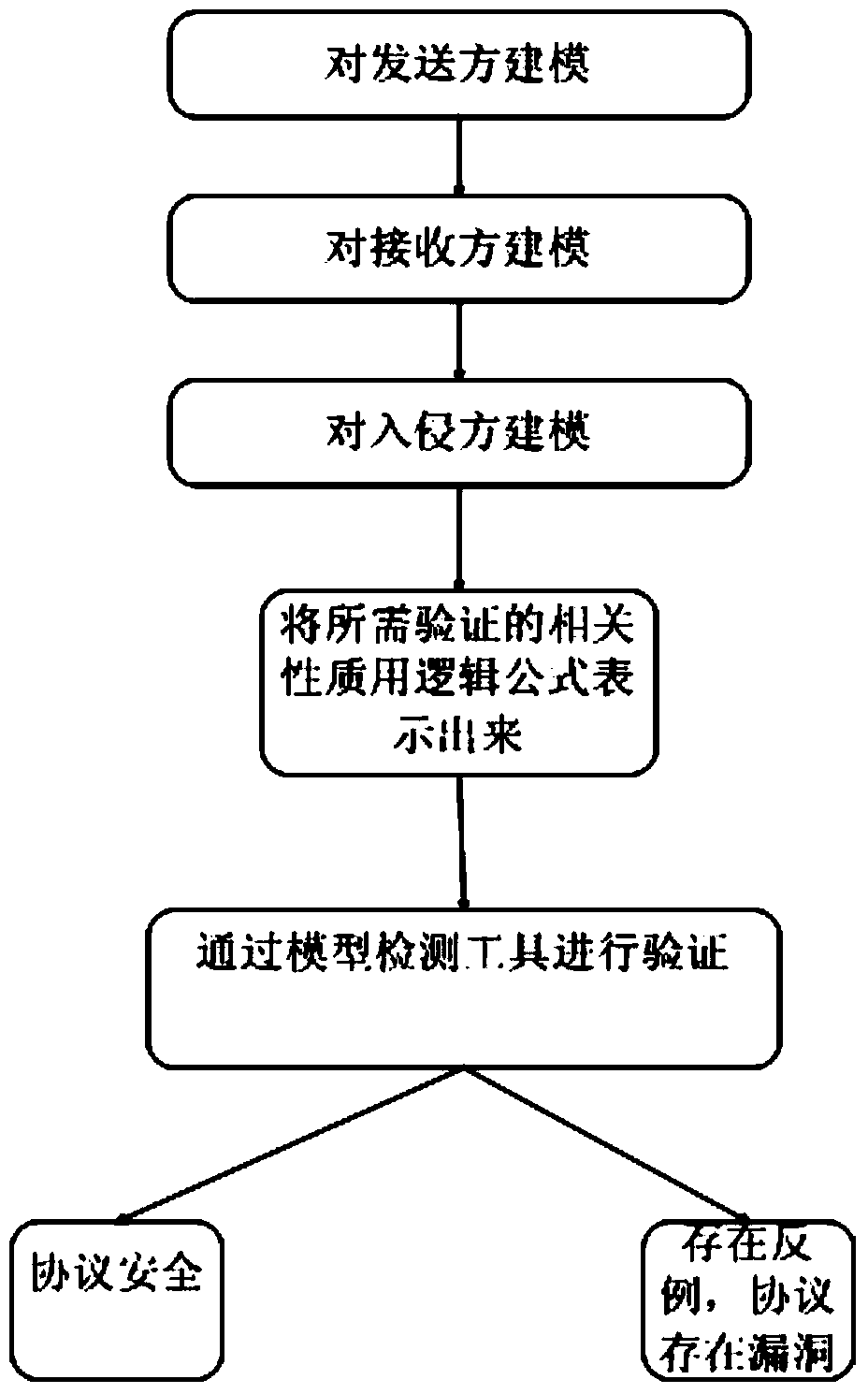
[0055] according to figure 1 , the present invention is built on the basis of model checking technology, and the specific implementation mode is:
[0056] 1. Establish a state transition system based on time automata
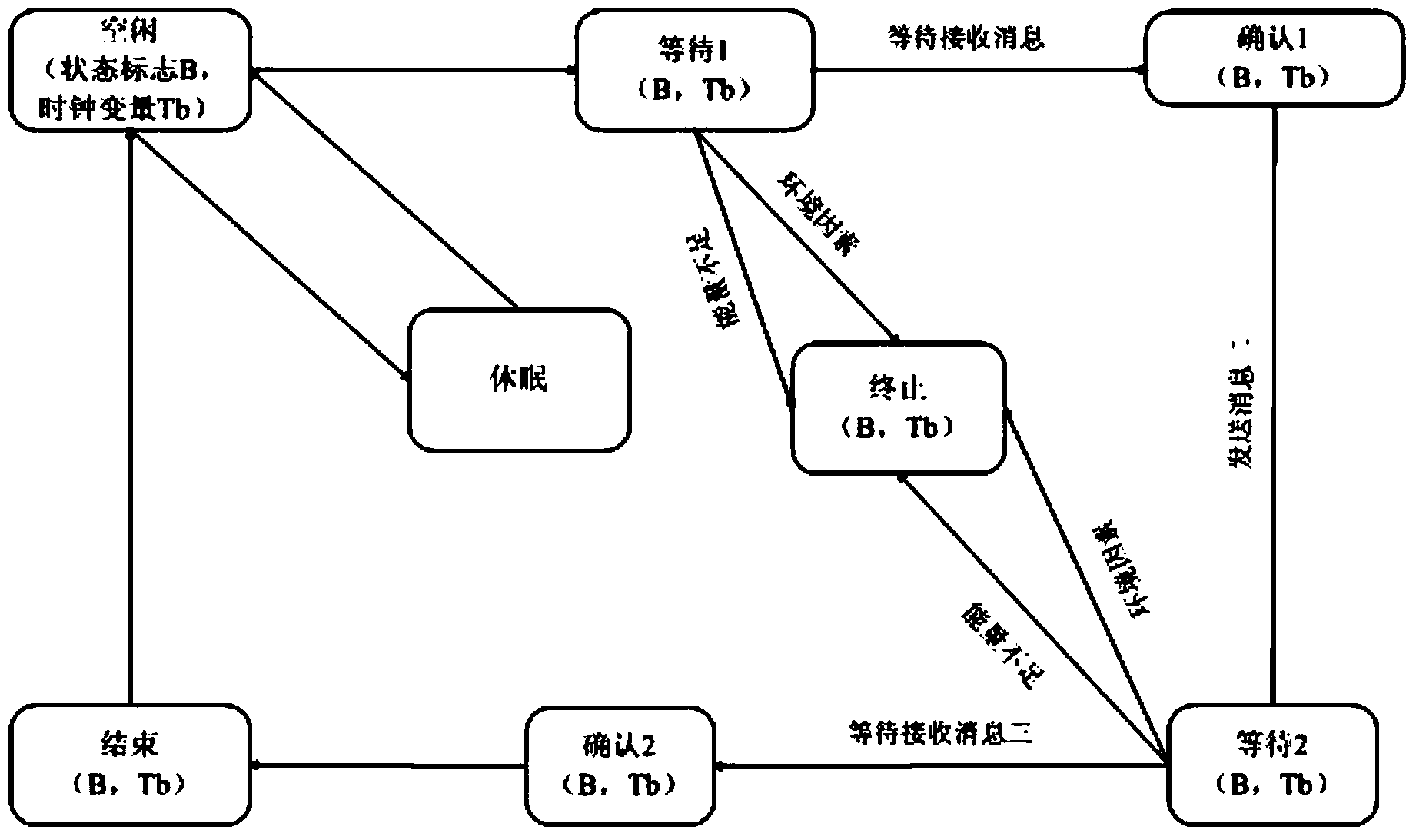
[0057] The state transition system based on timed automata described in the present invention uses timed automata modeling to describe the possible states of the protocol during operation for the sender, receiver and intruder involved in the protocol respectively.
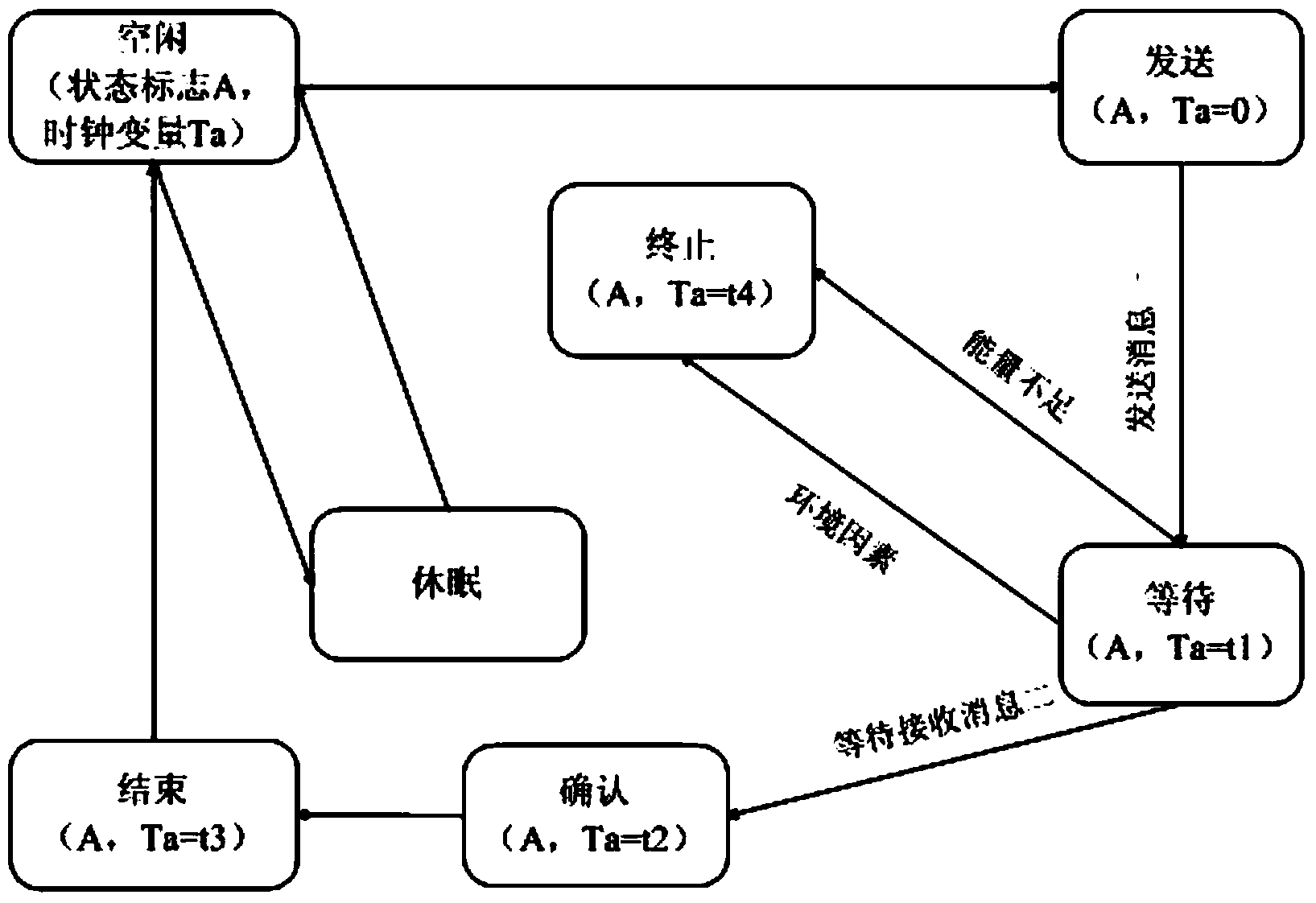
[0058] For the sender, a timed automaton is used to describe the state process of executing the protocol. When the sender communicates securely with the receiver, the protocol starts to execute. First, the sender enters the idle state from the dormant state, sets up a status flag, denoted as A, and sets up a clock variable Ta at the same time. A and Ta change continuously with the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com