Short message content interpolation-preventing method
A short message, anti-tampering technology, applied in the direction of messages/mailboxes/notifications, safety devices, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
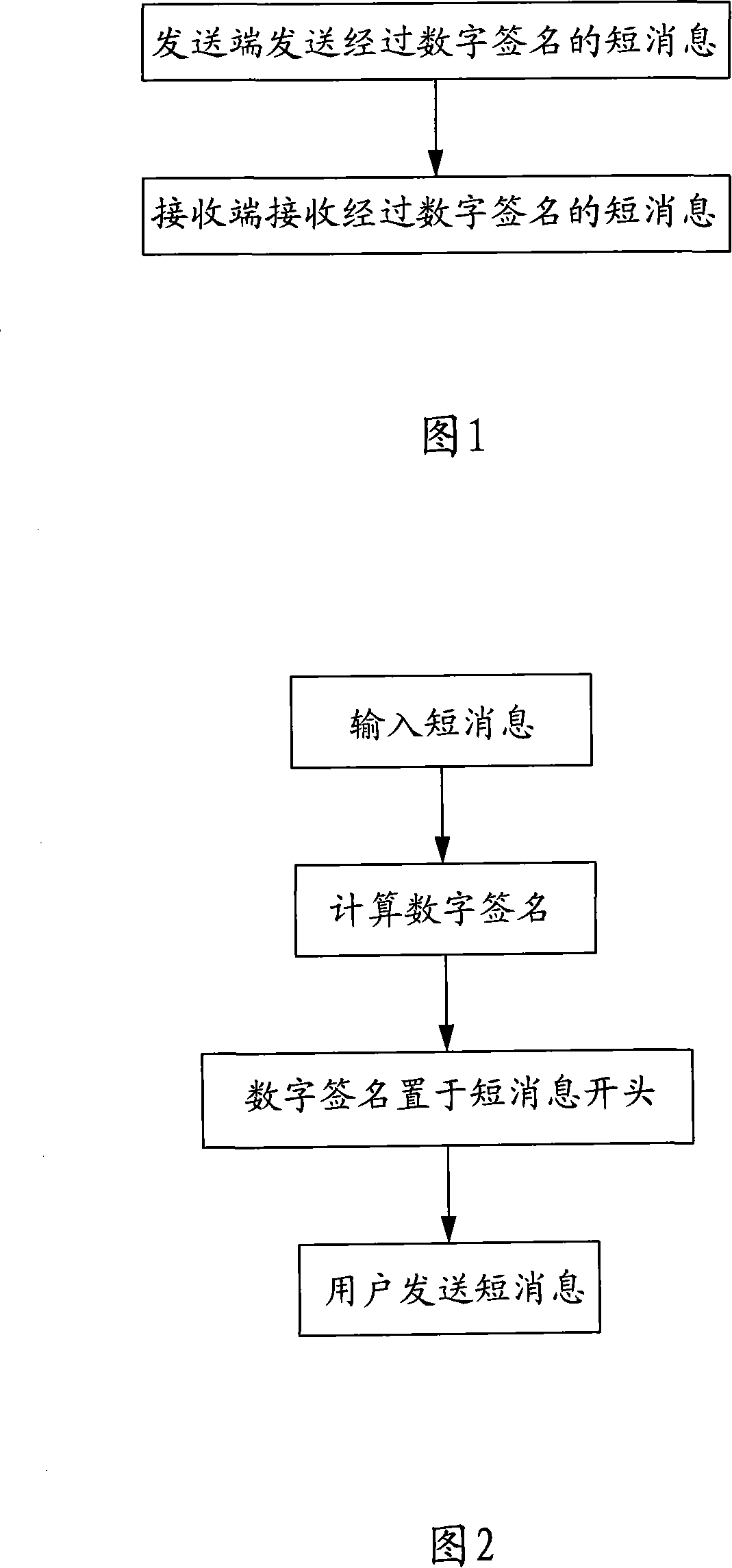
[0046] Please refer to Fig. 1, the present invention is a kind of short message content anti-tampering method, comprises following two steps:
[0047] 1. When the sender sends a short message (SMS-SUBMIT), send a digitally signed short message;
[0048] 2. After receiving the digitally signed short message (SMS-DELIVER), the receiving end checks the correctness of the digital signature.
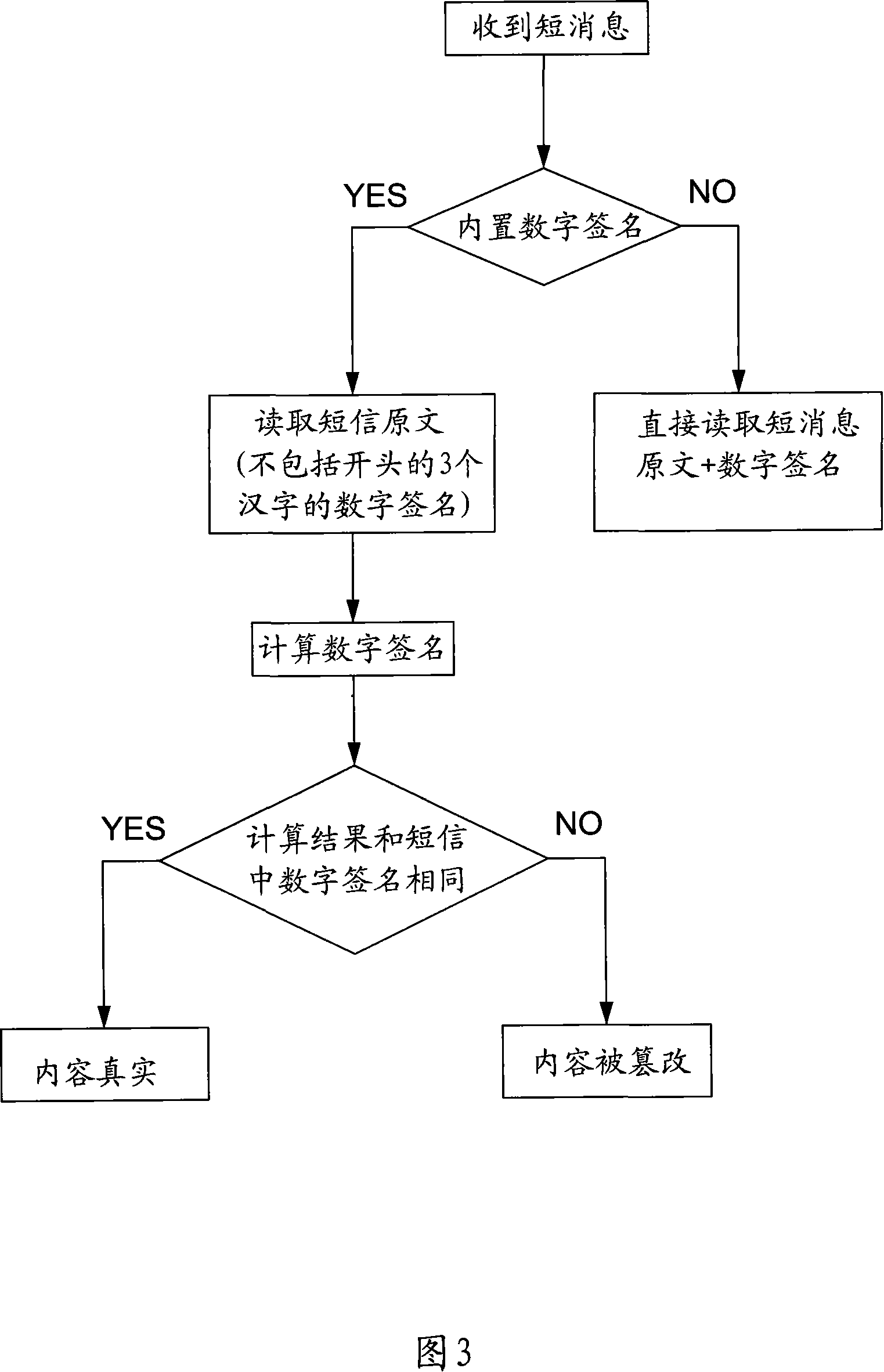
[0049] Referring to Figure 2, the step 1 specifically includes the following steps:
[0050] 11. The user enters a short message at the sending end;
[0051] 12. Calculate the digital signature;
[0052] 13. The sender places the digital signature at the beginning of the SMS;
[0053] 14. The sending end sends out the short message with the digital signature added (SMS-SUBMIT).
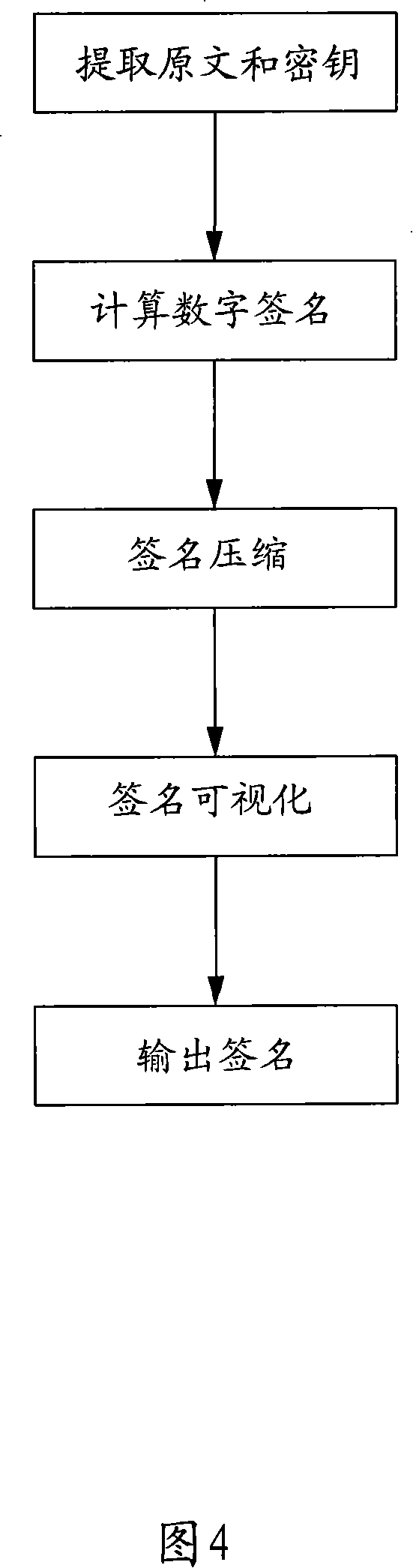
[0054] Referring to Figure 3, the step 2 specifically includes the following steps:
[0055] 21. The recipient receives the short message, and the beginning of the short message contains a digital signature with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com