Patents
Literature
163results about How to "Verify security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
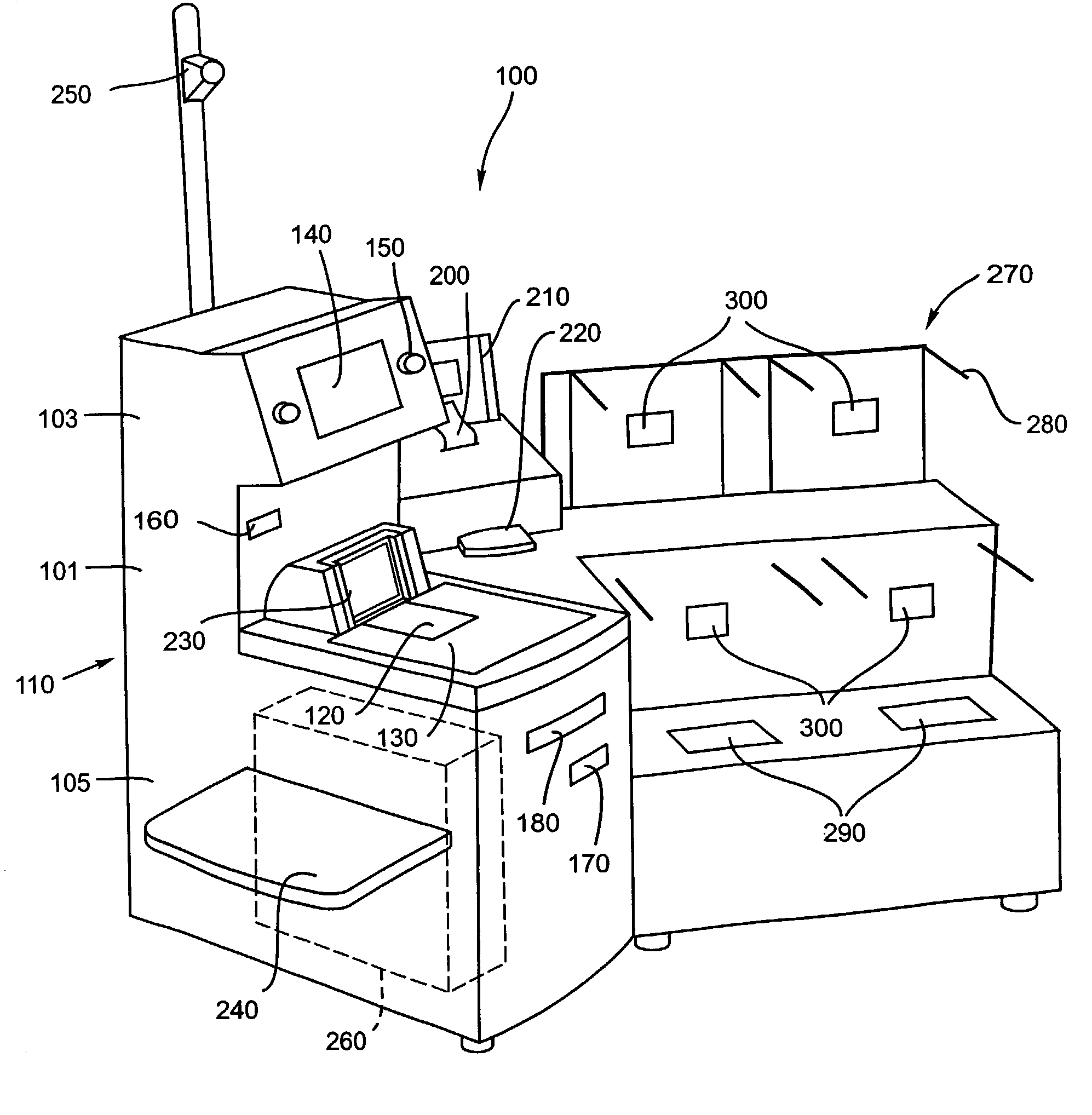
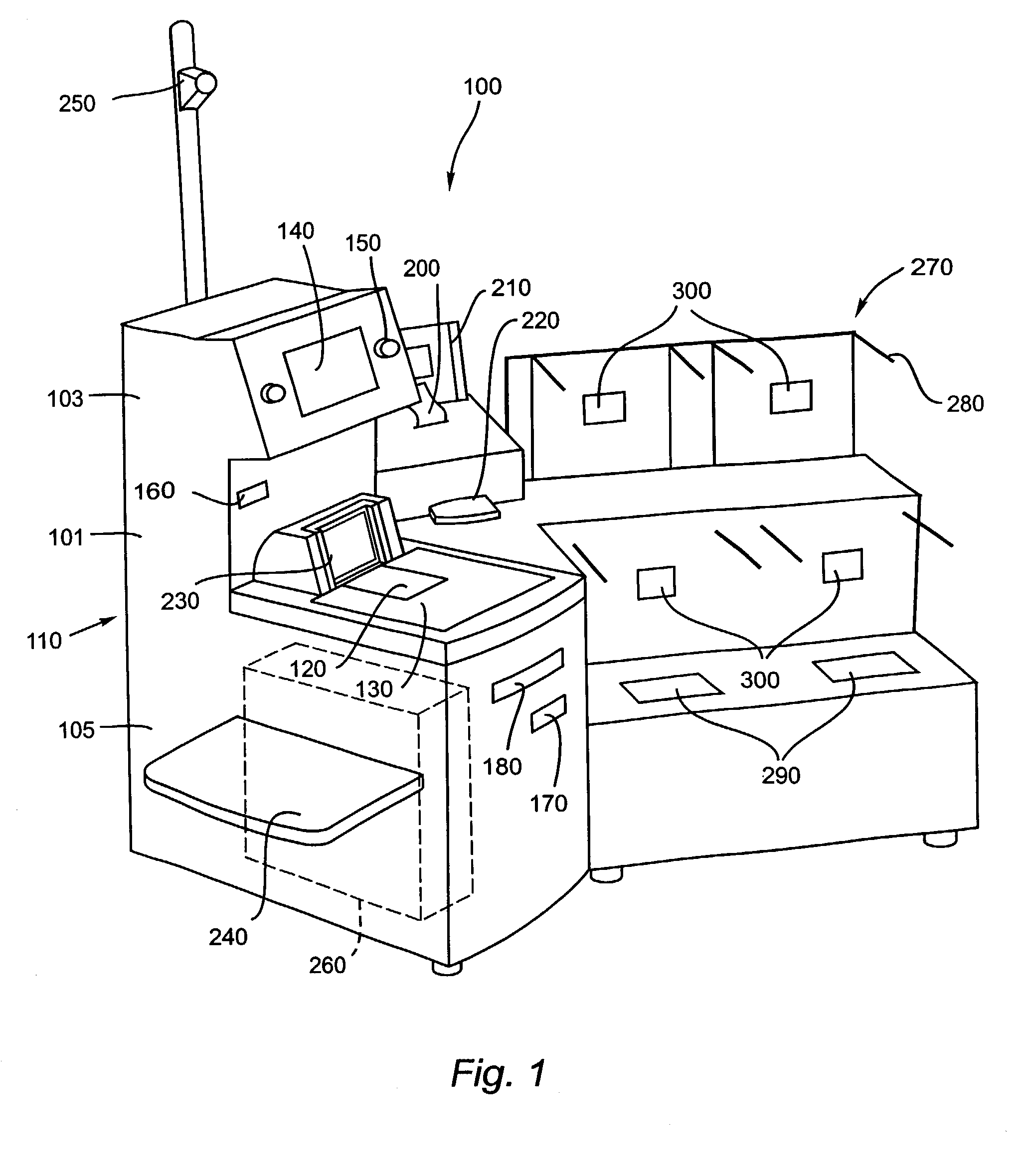
Checkout system with a flexible security verification system
InactiveUS7044370B2Verify securityCash registersAlarm indicatorsSecurity validationVerification system
A method and system for self-checkout of items from a retail or non-retail establishment is disclosed. The system verifies security by comparing a measured physical characteristic of an item with the stored security characteristic for that item and determining if the measured physical characteristic is within an operator-modifiable tolerance range. The operator-modifiable tolerance range is different for different of items in the store. Moreover, a stored security characteristic of an item can be updated automatically. In addition, the system includes a dynamic-weight scale that reports a measured weight before the scale settles.
Owner:ECR SOFTWARE CORP
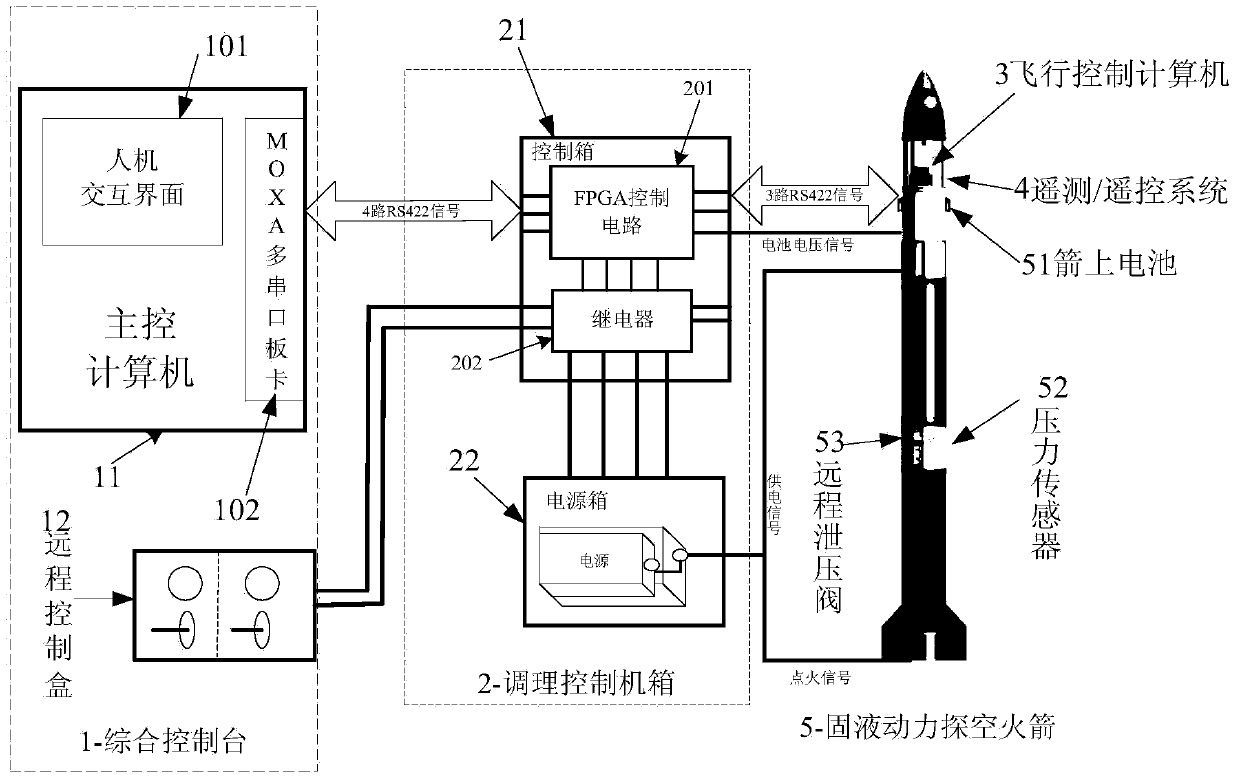
Solid-liquid power air vehicle ground test and launch control system of 422 bus
ActiveCN103558838ASafe and Efficient Ground Test Launch ControlRealize long-distance transmissionElectric testing/monitoringInteraction interfaceControl data
The invention relates to a solid-liquid power air vehicle ground test and launch control system of a 422 bus. The system comprises a ground integrated console, an adjusting control machine box, a flying control computer and a telemetering / telecontrol system. A main control computer of the ground integrated console uses a human-computer interaction interface, a CP-134U-I / DB9M board card of MOXA is used as a 422 node, orders are received and sent, and state information is displayed. The adjusting control machine box carries out ground and missile-borne power supply and distribution, signal forwarding, signal state monitoring and testing. The flying control computer receives orders sent by the main control computer and feeds the state information of an air vehicle back to the ground. According to the system, ground testing of the whole system, missile-borne system self detecting, result back transmitting, flying control data stapling, important parameter real-time detecting and system information back reading can be completed, and comprehensive monitoring of bus information, data real-time storage and displaying and safe protecting integration design are achieved.
Owner:BEIHANG UNIV
Construction verification method and device capable of verifying security two-dimensional code offline
ActiveCN106452756AEasy to useCannot be tampered withKey distribution for secure communicationUser identity/authority verificationInformation analysisEffective time
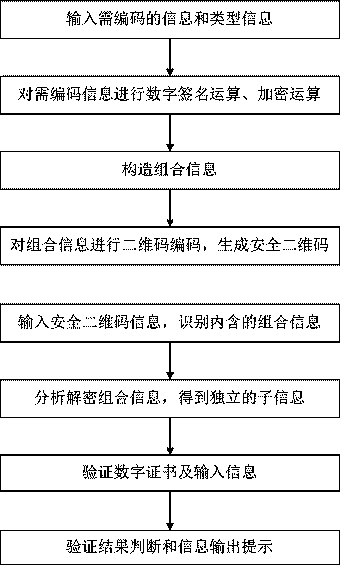
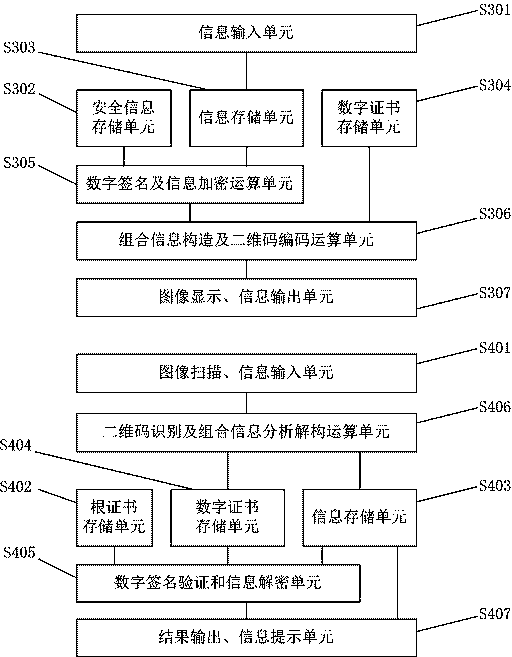
Embodiments of the invention provide a construction verification method and device capable of verifying a security two-dimensional code offline. The method comprises the following steps of inputting information that needs coding and type information, carrying out digital signature operation and encryption operation on the input information according to an information release type, constructing combination information, and encoding to generate a security two-dimensional code which can be verified off-line according to a two-dimensional code coding rule; inputting the information of the security two-dimensional code and identifying included combination information and type information, analyzing and decoding the combination information to obtain independent sub-information according to the type information of the two-dimensional code, and verifying digital certificate effectiveness information, a digital signature of the input information and an effective time limit of the input information; and if all verifications pass, showing that the offline verification of the security two-dimensional code is correct and the coding information source of the security two-dimensional code is credible, otherwise showing that the information release source of the security two-dimensional code is incredible. The method and the device have the beneficial effects that the security two-dimensional code cannot be tampered, counterfeited and denied, the public or private information can be released, and the integrity of the information of the security two-dimensional code and the authenticity of the source can be verified offline without a network connection.
Owner:王栋
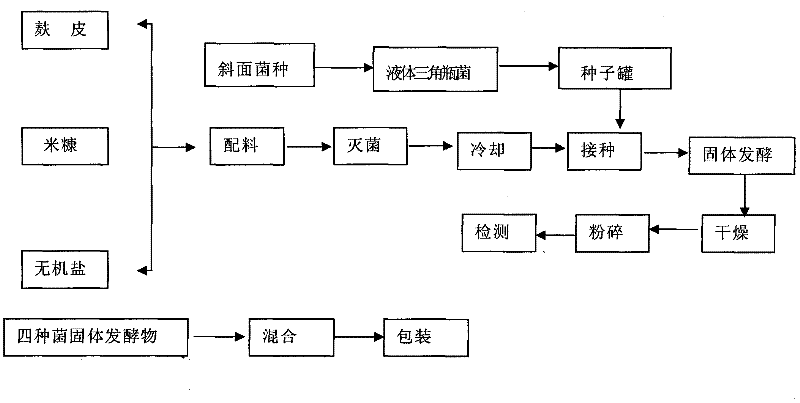
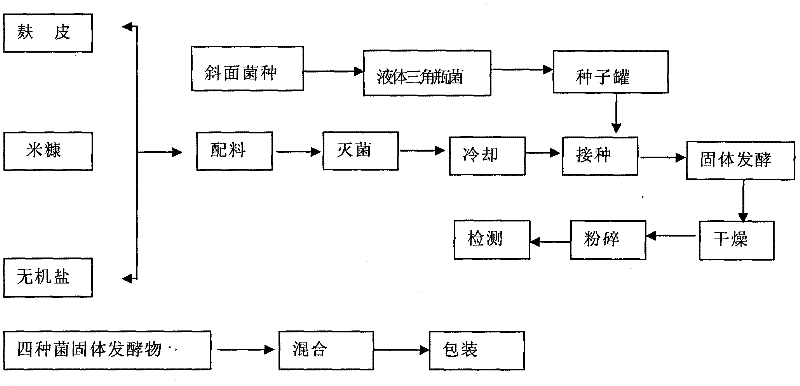
Microbial straw decomposition additive as well as preparation method and application thereof
InactiveCN102382768AAuxiliary Growth-Promoting BenefitsIncrease the ambient temperatureFungiBacteriaSporeMicroorganism
The invention discloses microbial straw decomposition additive, which belongs to the field of straw decomposition additive and is obtained through combining four bacteria: bacillus subtilis, aspergillus niger, trichoderma reesei and saccharomyces cerevisiae. The microbial straw decomposition additive utilizes the temperature rise benefit of the aspergillus niger spore enzyme activity for raising the environment temperature of decomposition, the further temperature rise benefit in the growth process of the bacillus subtilis is cooperated, and the temperature required by the decomposition is ensured, so the decomposition effect of straws is improved. The microbial straw decomposition additive has the obvious temperature rise benefit and can be used for the in-site field returning decomposition of the straws, the straw decomposition can be better accelerated in low-temperature and normal-temperature environment, the bottleneck problem of straw utilization is solved, the straw burning can be effectively reduced, the decomposition work procedure and the labor cost are saved, the fertilizer feeding is reduced, the soil structure is improved, and the planting benefit is improved.
Owner:武汉施瑞福生物技术有限公司
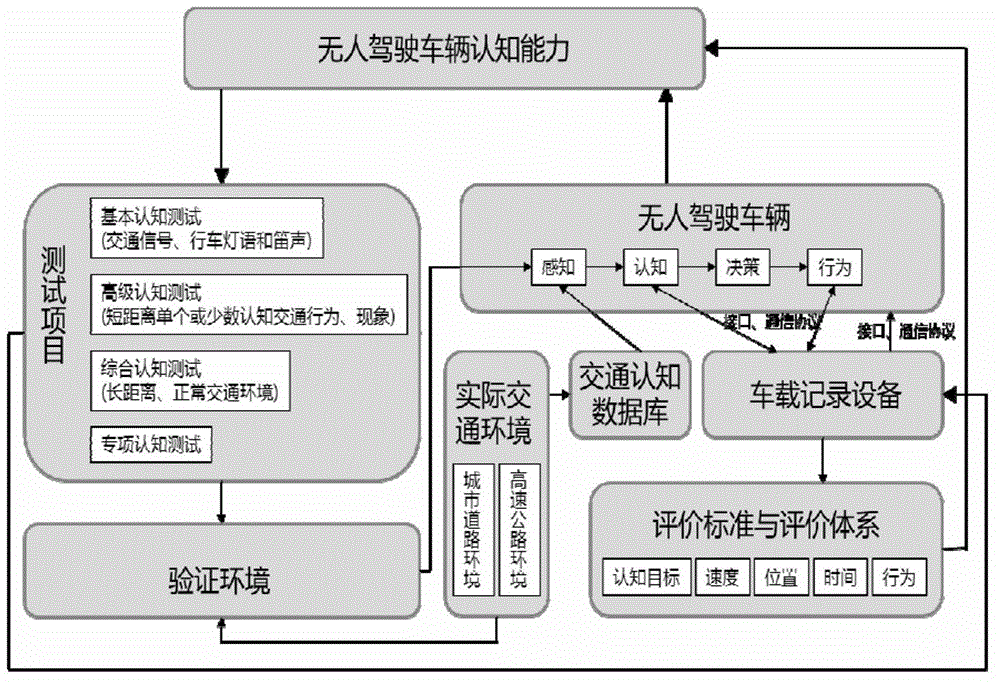
Unmanned driving vehicle cognitive competence testing system and method
ActiveCN103335853AVerify securityVerify reliabilityVehicle testingTesting/monitoring control systemsData transmissionData content
The invention discloses an unmanned driving vehicle cognitive competence testing system which comprises an unmanned driving vehicle and a vehicle-mounted recording unit, wherein the unmanned driving vehicle and the vehicle-mounted recording unit are in wired connection through a communication interface, the vehicle-mounted recording unit is used for inputting cognitive competence testing task to an unmanned driving vehicle, and receiving and storing data output by unmanned driving vehicle cognitive competence test; after receiving testing task through a testing task input program, the unmanned driving vehicle rebuilds serial port connection and starts corresponding program output test data to the vehicle-mounted record unit, the testing task input and the testing data output both of the unmanned driving vehicle cognitive competence test adopt the uniform interface, parameter and data transmission form, while the specific forms of the data contents are different; the communication interface adopts an RS-232 interface.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Data sharing method and system under cloud computing environment
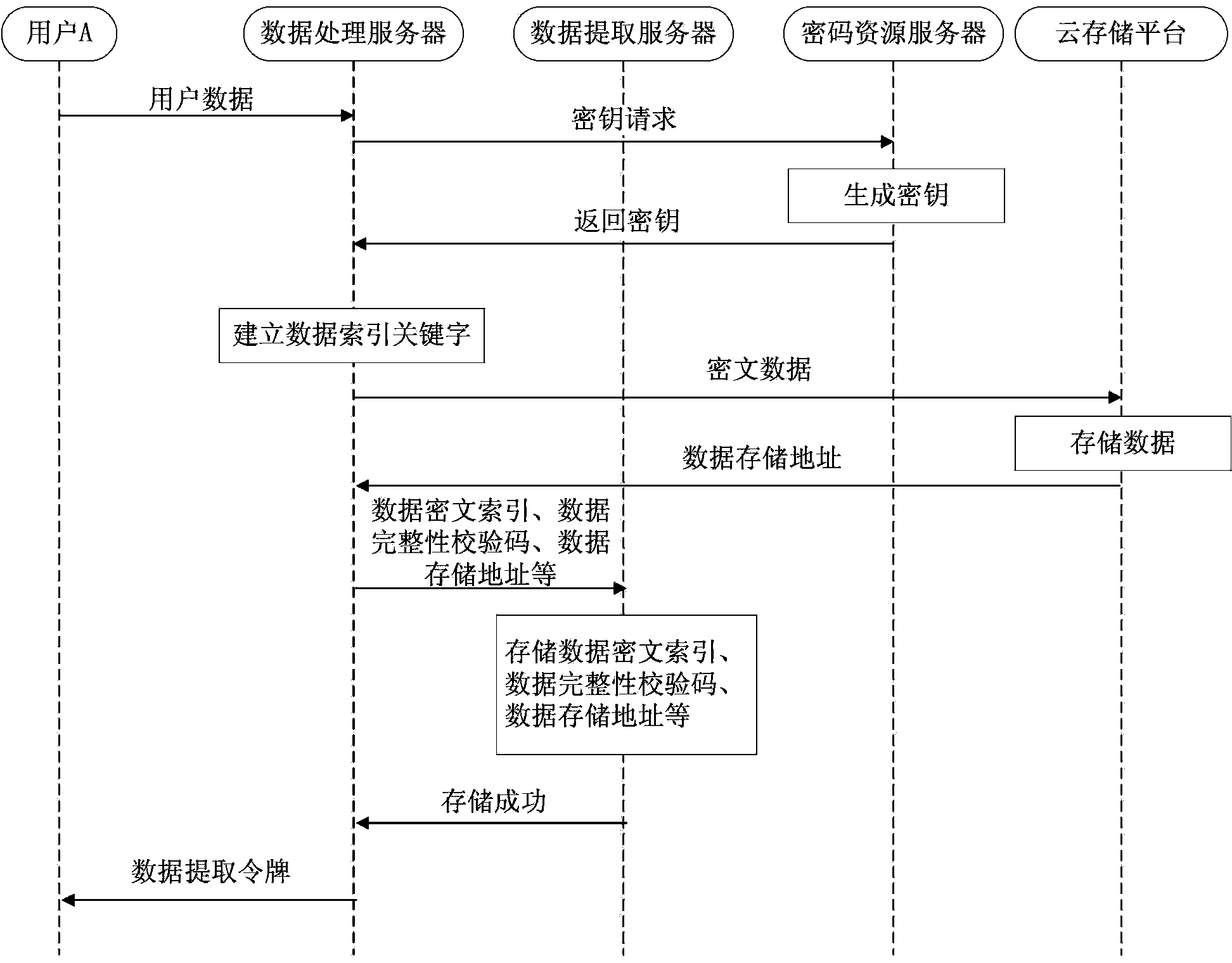
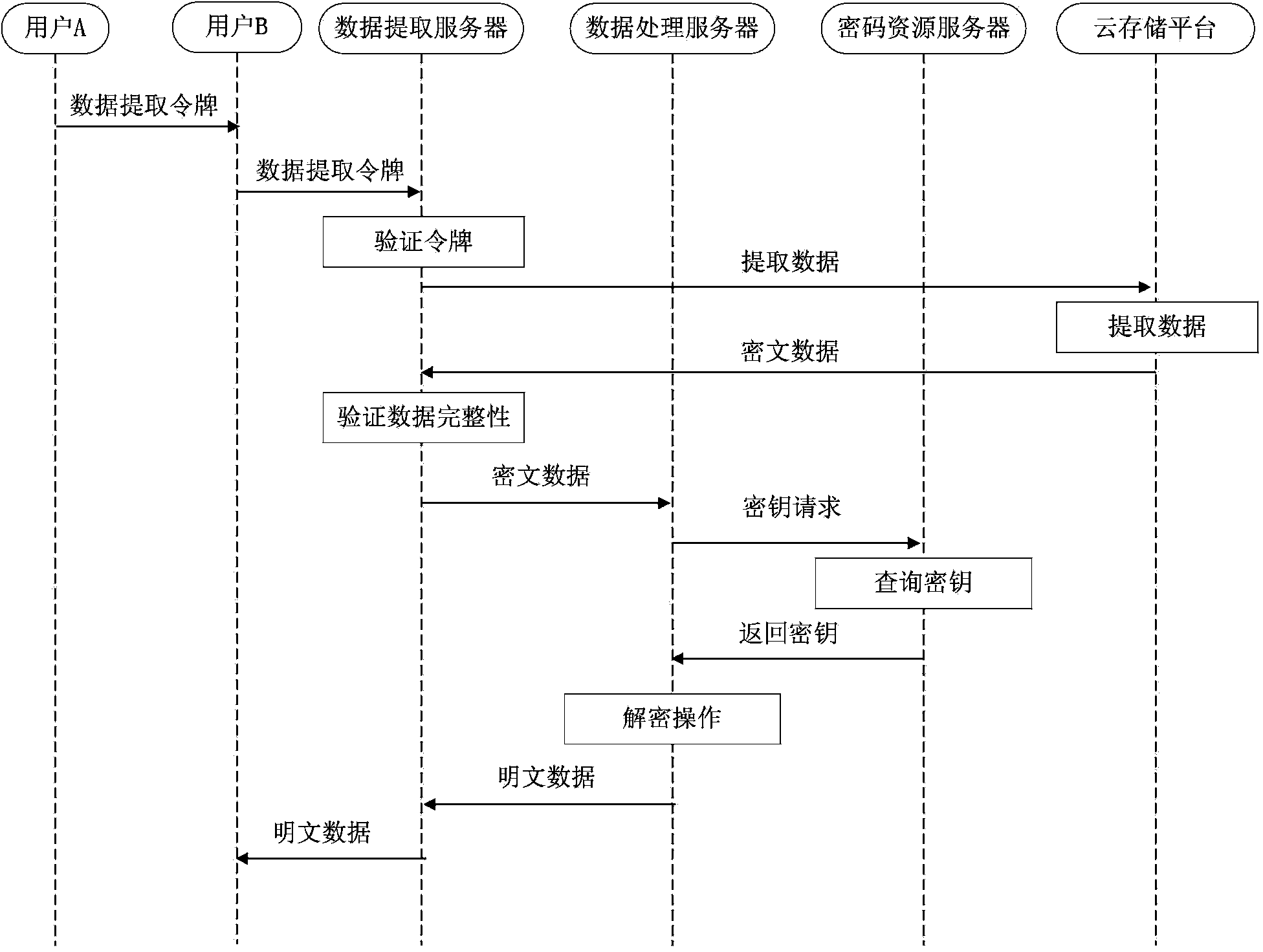
ActiveCN103457733AImprove securityReduce duplicationUser identity/authority verificationData ingestionCiphertext
The invention relates to a data sharing method and system under the cloud computing environment. The method comprises the user data encryption storage step and the user data extraction step. The user data encryption storage step comprises the particular steps that a data processing server sets up data index keyword information for user data and generates a matched data ciphertext index and a matched data extraction token, the user data are stored in a cloud storage platform after being encrypted, the data ciphertext index and a data storage address are stored in a data extraction server, and the data extraction token is transmitted to a user. The user data extraction step comprises the particular steps that after receiving the data extraction token, the data extraction server verifies the legality of the data extraction token, extracts data from the cloud storage platform according to the data storage address, and the data are returned to the user by the data extraction server after being decrypted by the data processing server. According to the data sharing method and system, the data storage safety under the cloud computing environment is ensured, and meanwhile the problem of user data sharing is conveniently solved.
Owner:CEC CYBERSPACE GREAT WALL
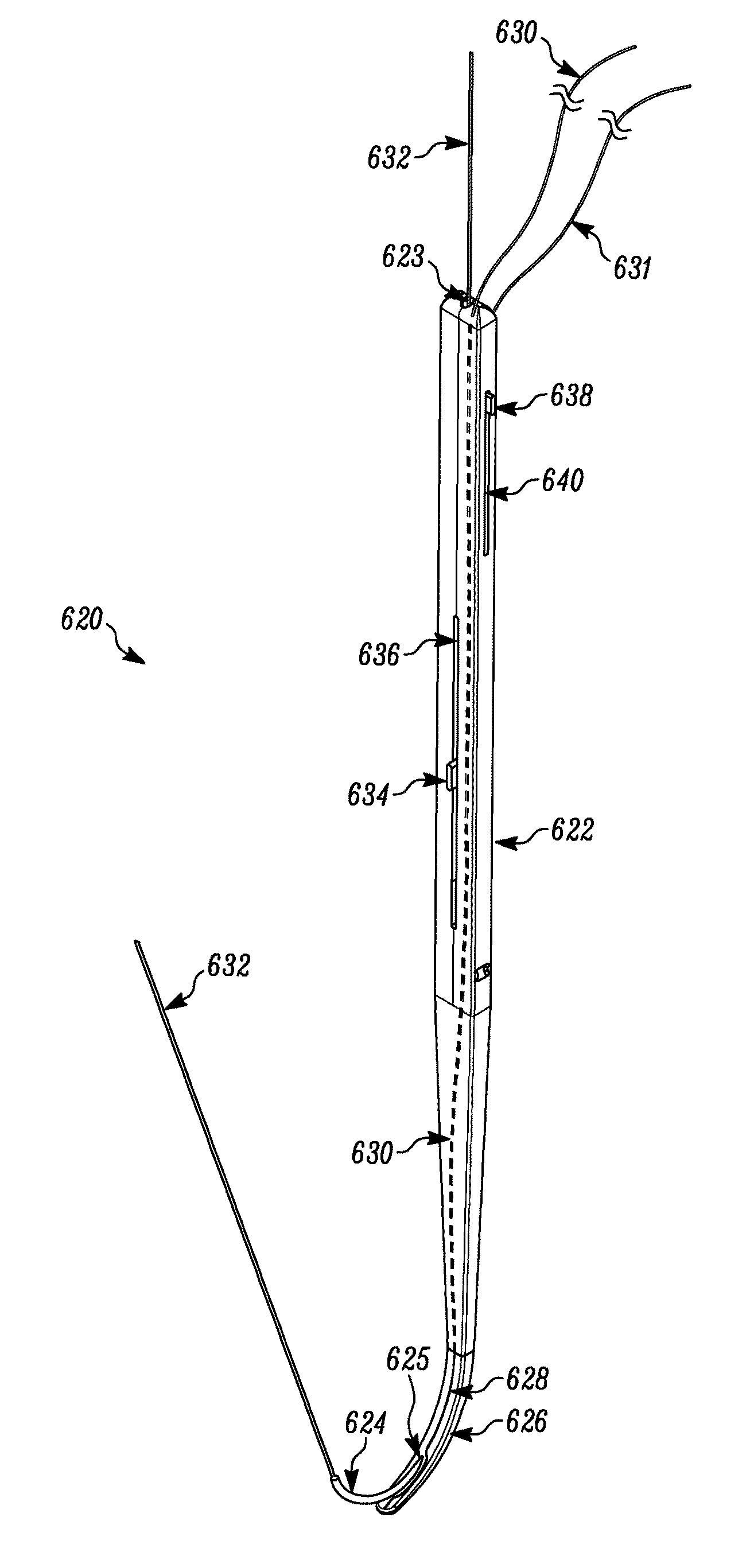
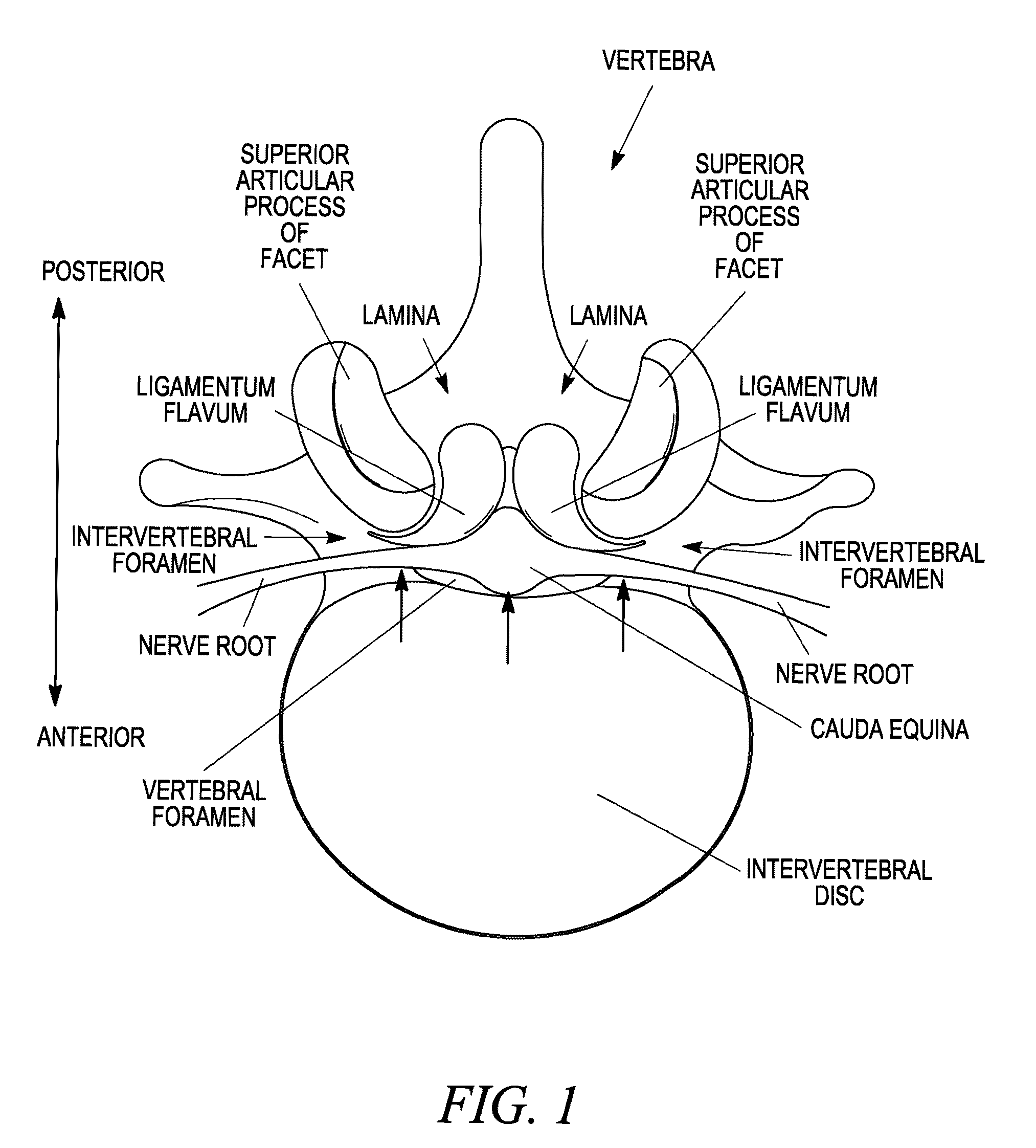
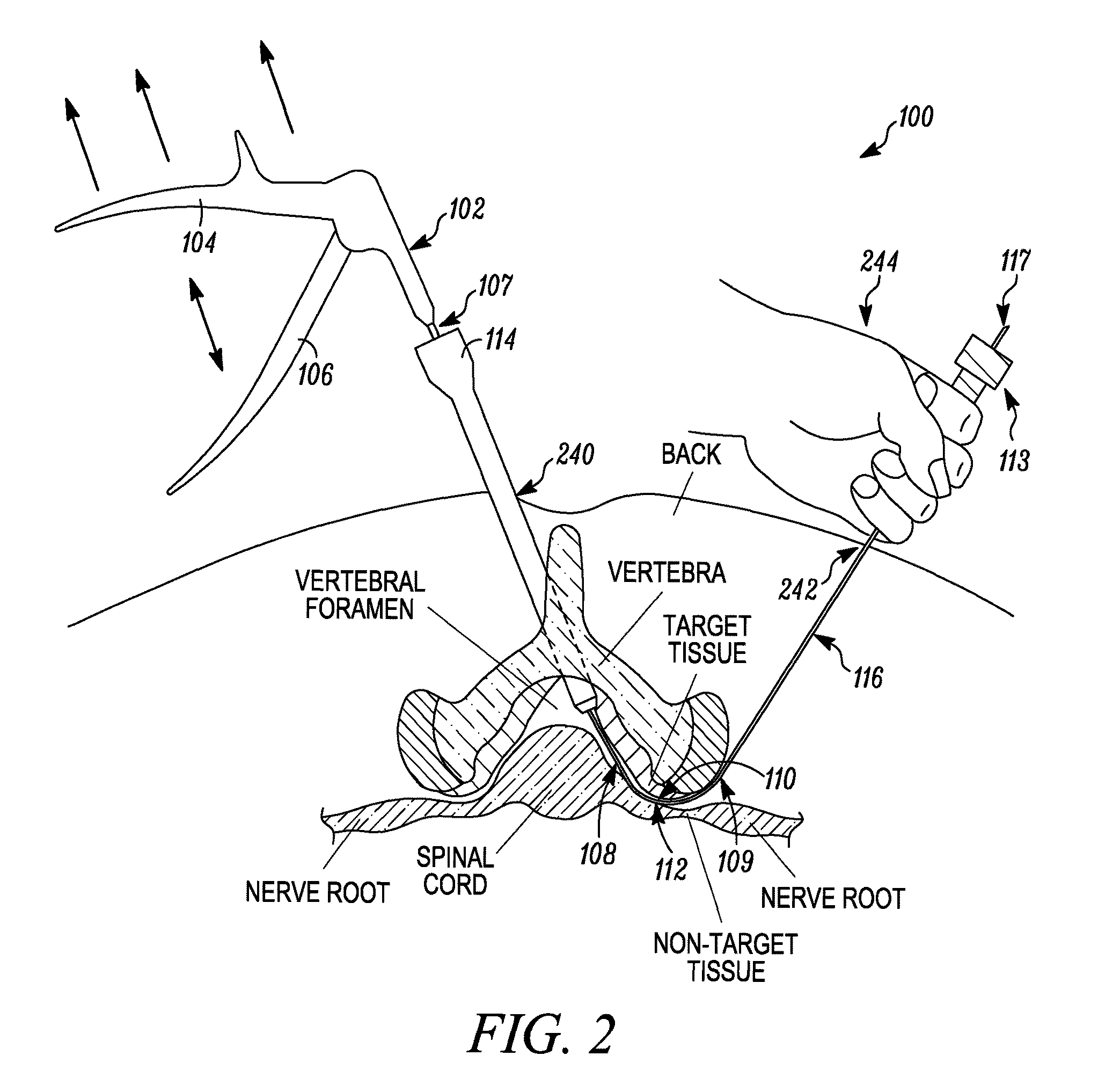
Spinal access and neural localization
A method for locating neural tissue in a patient body may involve: advancing a probe along a natural tissue interface between the neural tissue and another tissue in the body, the probe having a first surface oriented toward the neural tissue and a second surface oriented away from the neural tissue; delivering a first electrical current to a first electrode along the first surface of the probe; delivering a second electrical current to a second electrode along the second surface of the probe; and verifying that the first surface of the advanced probe remains oriented toward the neural tissue and the second surface remains oriented away from the neural tissue by monitoring neural response to the first and second electrical currents.
Owner:MIS IP HLDG LLC +1
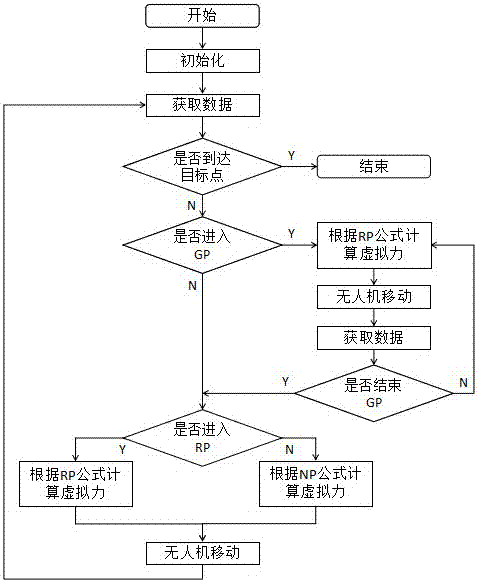
UAV dynamic path planning method suitable for high-speed environment
InactiveCN107102650AReduce complexitySimplify complexityPosition/course control in three dimensionsPotential fieldControl system
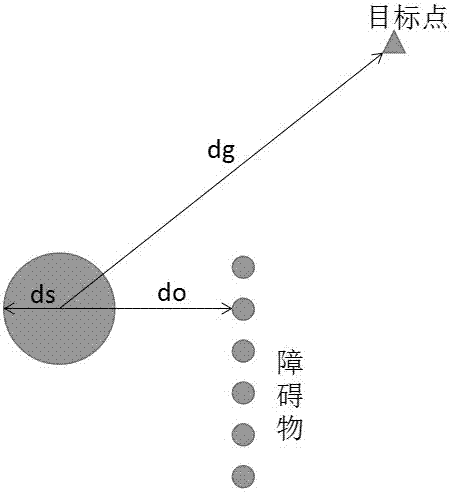
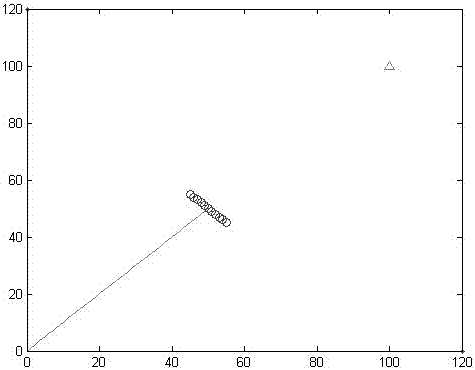
An UAV dynamic path planning method suitable for high-speed environment combines the theory of kinematic mechanics, establishes speed-dependent gravitational and repulsive functions, increases the virtual resistance, abandons the concept of "potential field", and directly calculates the resultant force born by the UAV through the virtual force function. The simulation experiments show that the method is effective and safe when the UAV is moving at high speed. The beneficial effect is that the method of the invention does not need to generate the motion path of the UAV, and only needs to calculate the expected resultant force of the UAV, not only reduces the complexity of the algorithm, but also substitutes the desired acceleration for the desired position as the input of the control system, so that one closed loop is omitted, the system complexity is lowered, the stabilizing time is greatly shortened, and the problem that the existing path planning method is not suitable for the high speed environment.
Owner:南通海嘉智能科技有限公司
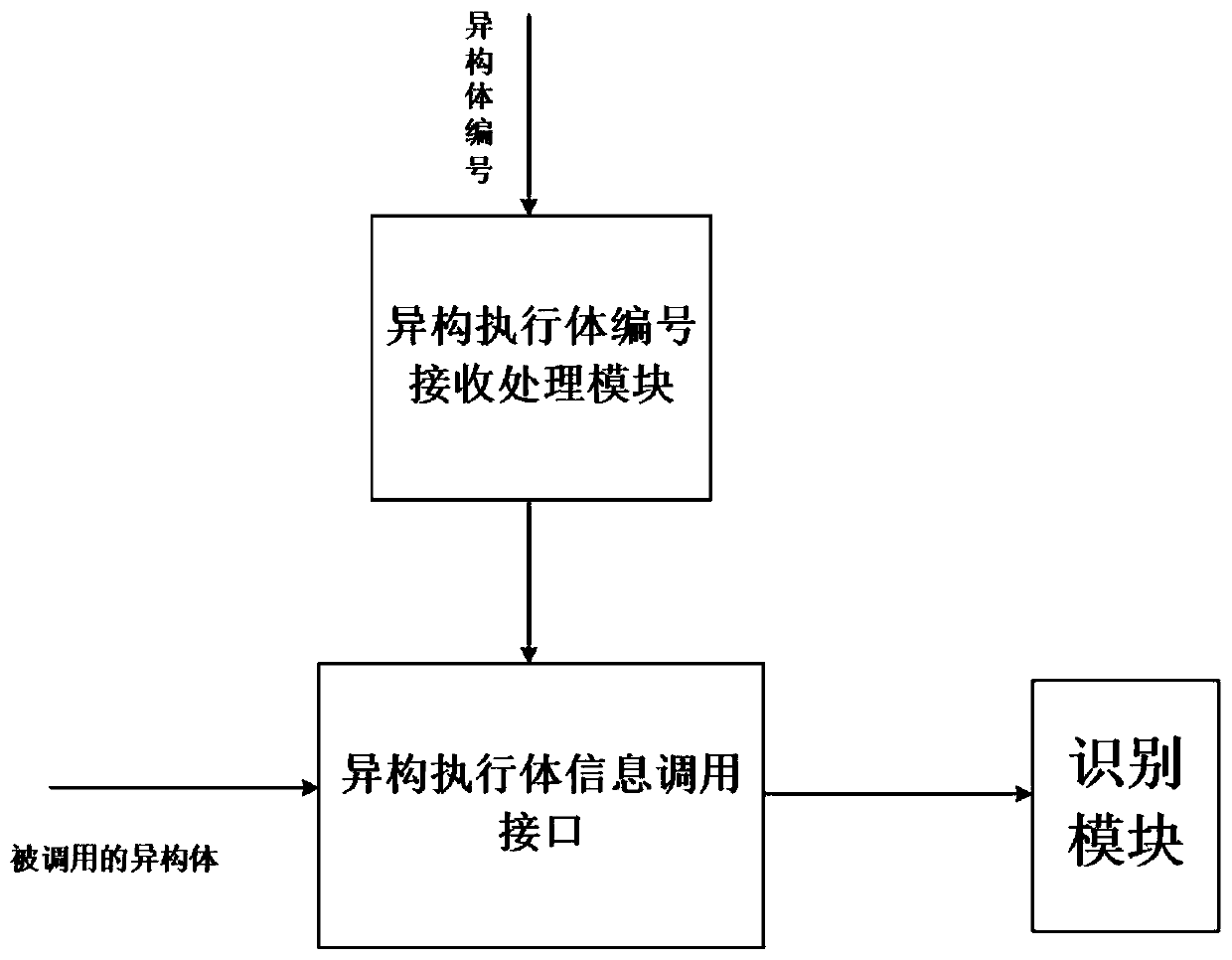
Heterogeneity testing device and method based on a DHR architecture mimicry defense platform
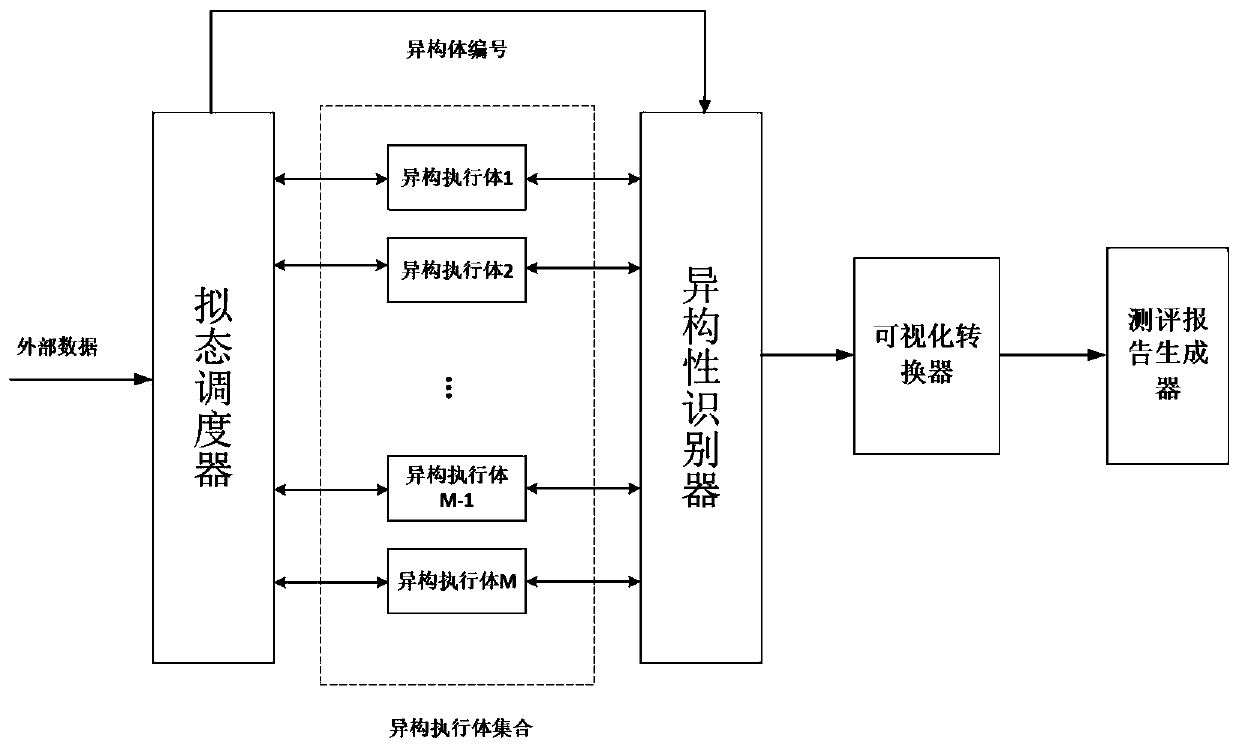
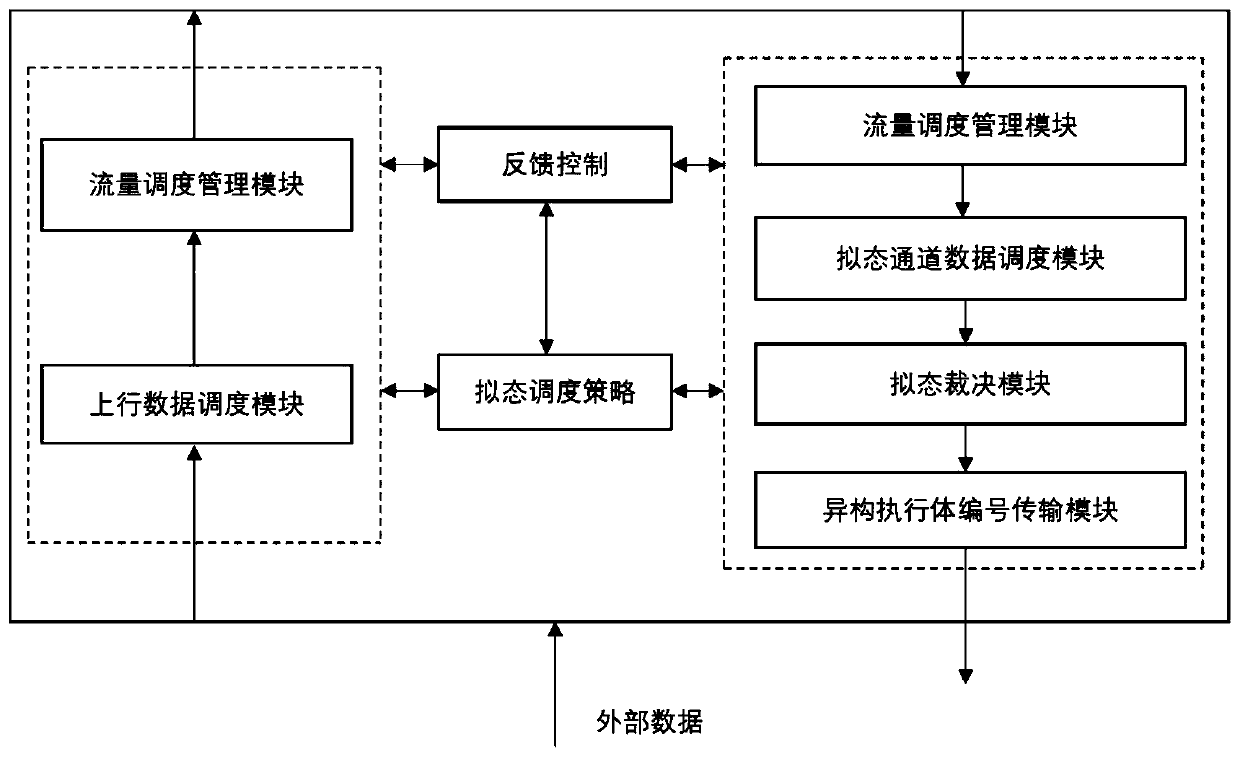
InactiveCN110445787AVerify securityEfficient and stableData switching networksTest fixtureComputer science
The invention provides a heterogeneity testing device and method based on a DHR architecture mimicry defense platform. The device part comprises a mimicry scheduler, a heterogeneity executor set and aheterogeneity recognizer. The device disclosed by the invention is based on the existing test method for verifying the characteristics of the mimicry system; verification and judgment for the types of the heterogeneous executors are added, the stability, safety and performance rationality of the heterogeneous executors can be verified more efficiently, and a detailed test report is automaticallygenerated, so that the requirement for evaluating the heterogeneity of the mimicry safety information system is met.
Owner:EAST CHINA INST OF COMPUTING TECH
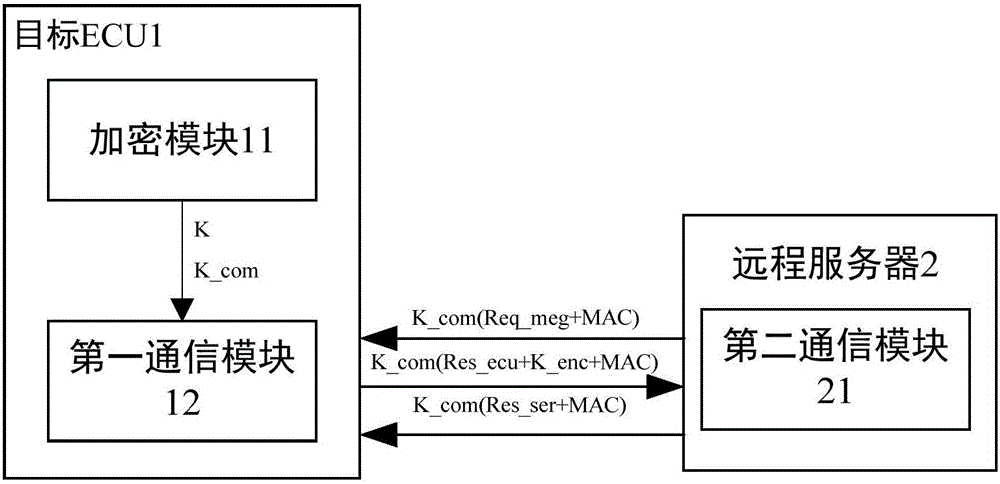
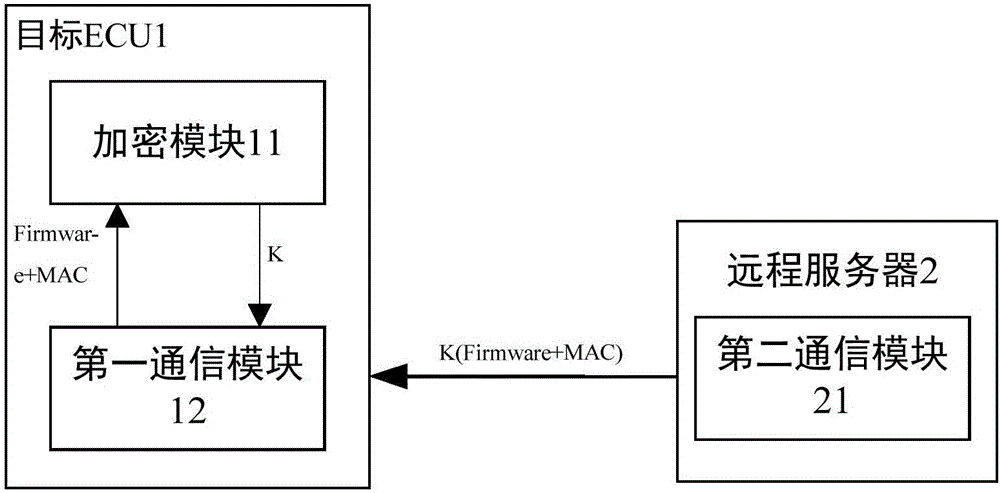
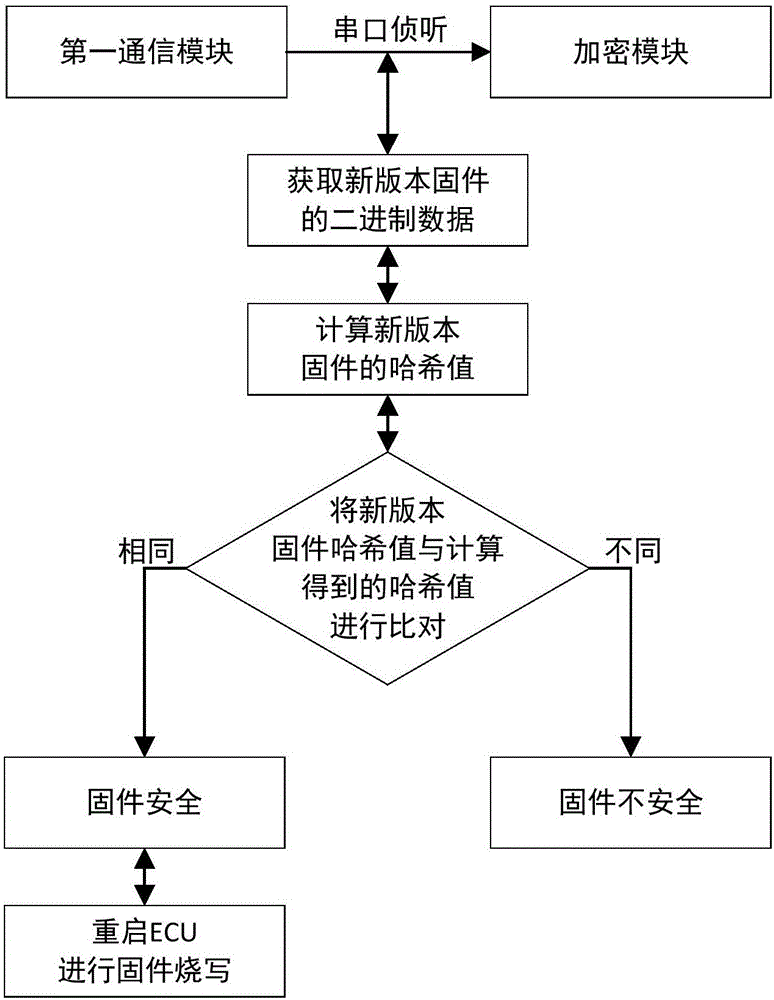
Vehicle remote firmware updating method and device based on information security technology
ActiveCN106685653AAccelerateSmall amount of calculationKey distribution for secure communicationUser identity/authority verificationInformation technologyEncryption
The invention relates to a vehicle remote firmware updating method and device based on an information security technology. The method comprises the following steps: generating a firmware updating request message by using a remote server, generating a first hash value according to a message digest of the firmware updating request message, and carrying out symmetric encryption packaging on the firmware updating request message and the first hash value to obtain a first message; carrying out symmetric decryption verification on the first message by using a target ECU; generating a secret key K by using the target ECU, carrying out symmetric encryption on the secret key K and then transmitting the secret key K to a remote server; encrypting a new firmware and a third hash value corresponding to the new firmware through the secret key K by using the remote server to generate a second message; decrypting the second message by the target ECU, calculating a fourth hash value, and judging whether the fourth hash value is the same as the third hash value or not; and programming the new firmware by the target ECU. Compared with the prior art, the vehicle remote firmware updating method has the advantages of high safety, convenience, reliability and the like.
Owner:TONGJI UNIV
High-pressure gas tightness detection system
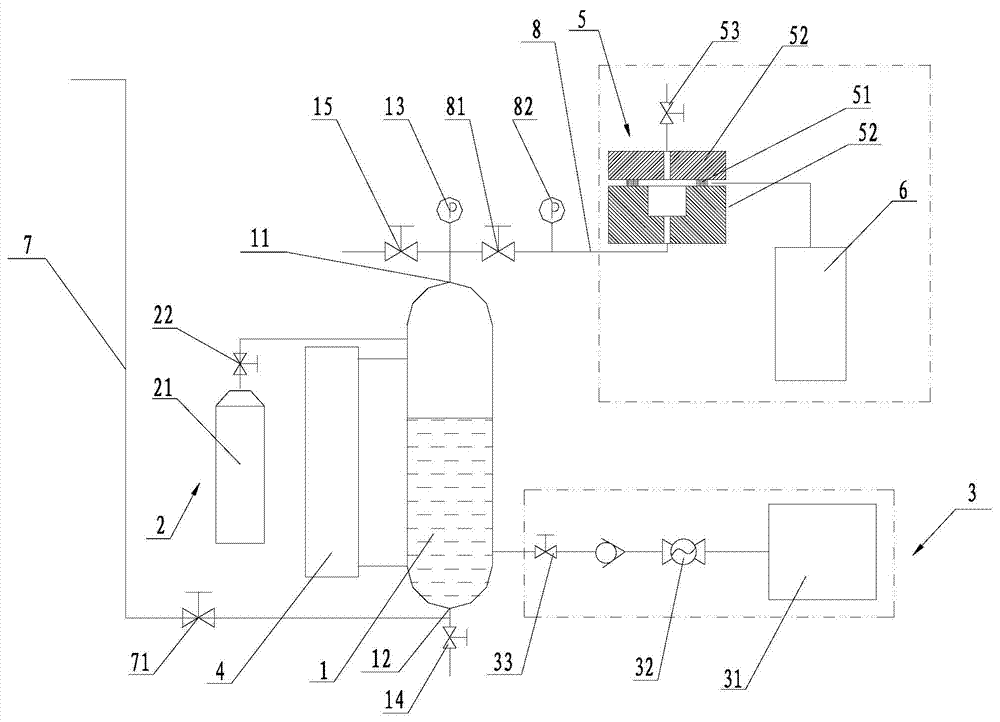
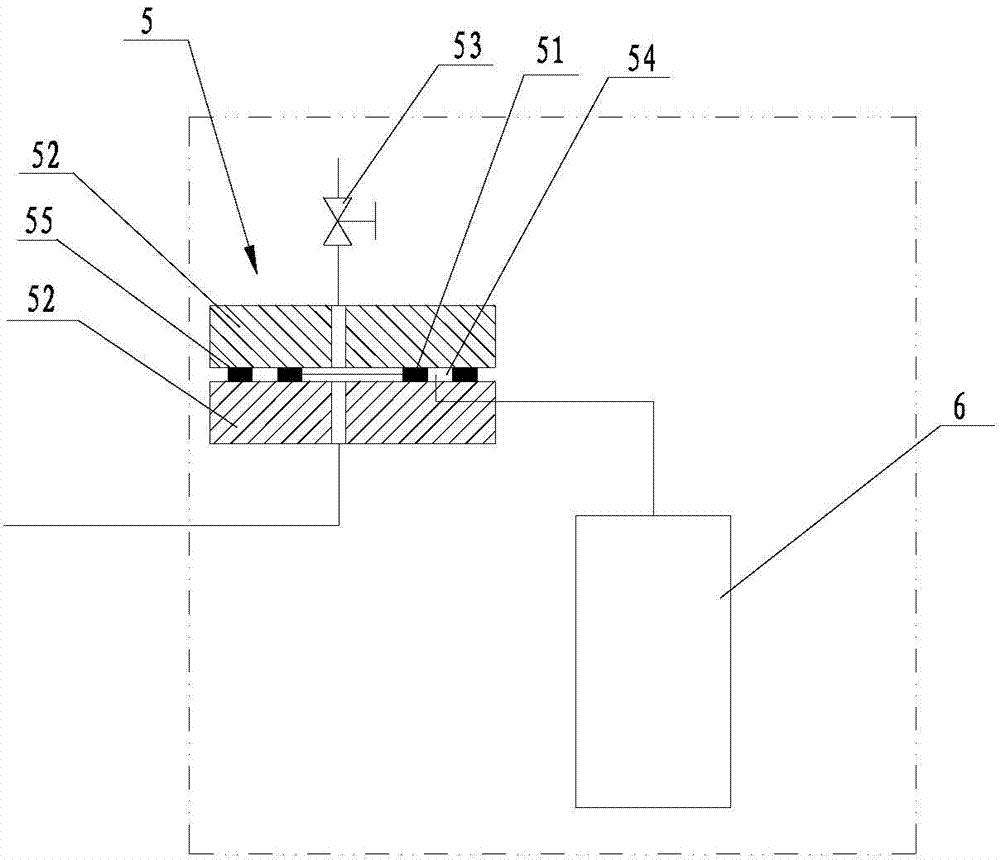
InactiveCN104122048AVerify rationalityVerify securityMeasurement of fluid loss/gain rateEngineeringMechanics
The invention discloses a high-pressure gas tightness detection system. The high-pressure gas tightness detection system is used for performing quantitative detection on the high-pressure gas tightness of a high-pressure sealing system, wherein a certain quantity of gas for detection is introduced into a high-pressure tank and then water is continuously injected into the high-pressure tank so that the gas pressure in the detection system is capable of meeting the test requirement, and quantitative detection is performed on the gas for detection leaking from the high-pressure sealing system under this circumference, and therefore, the sealing leakage quantity of the high-pressure sealing system under corresponding testing working conditions can be obtained. According to the result of the quantitative detection, the designed leakage quantity of a sealing element can be verified so that the reasonability and safety of the design of the sealing element can be verified, and the result of the quantitative detection also can be used for detecting the leakage quantity under variable working conditions, and therefore, the correspondence between the working conditions of the sealing element and the leakage quantity can be obtained, and furthermore, the leakage quantity under the working conditions of the sealing element can be determined; consequently, accurate data support can be provided for the design of the sealing element, the connecting part of the sealing element and the like.
Owner:SUZHOU BMC SEALING TECH CO LTD
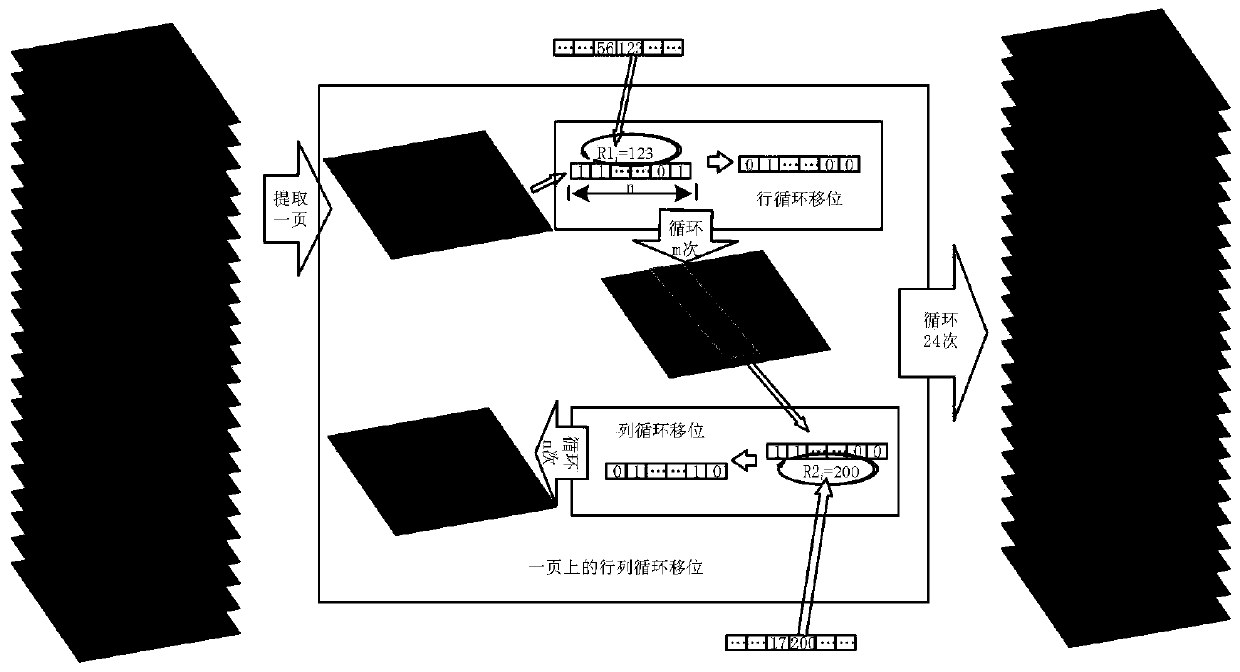
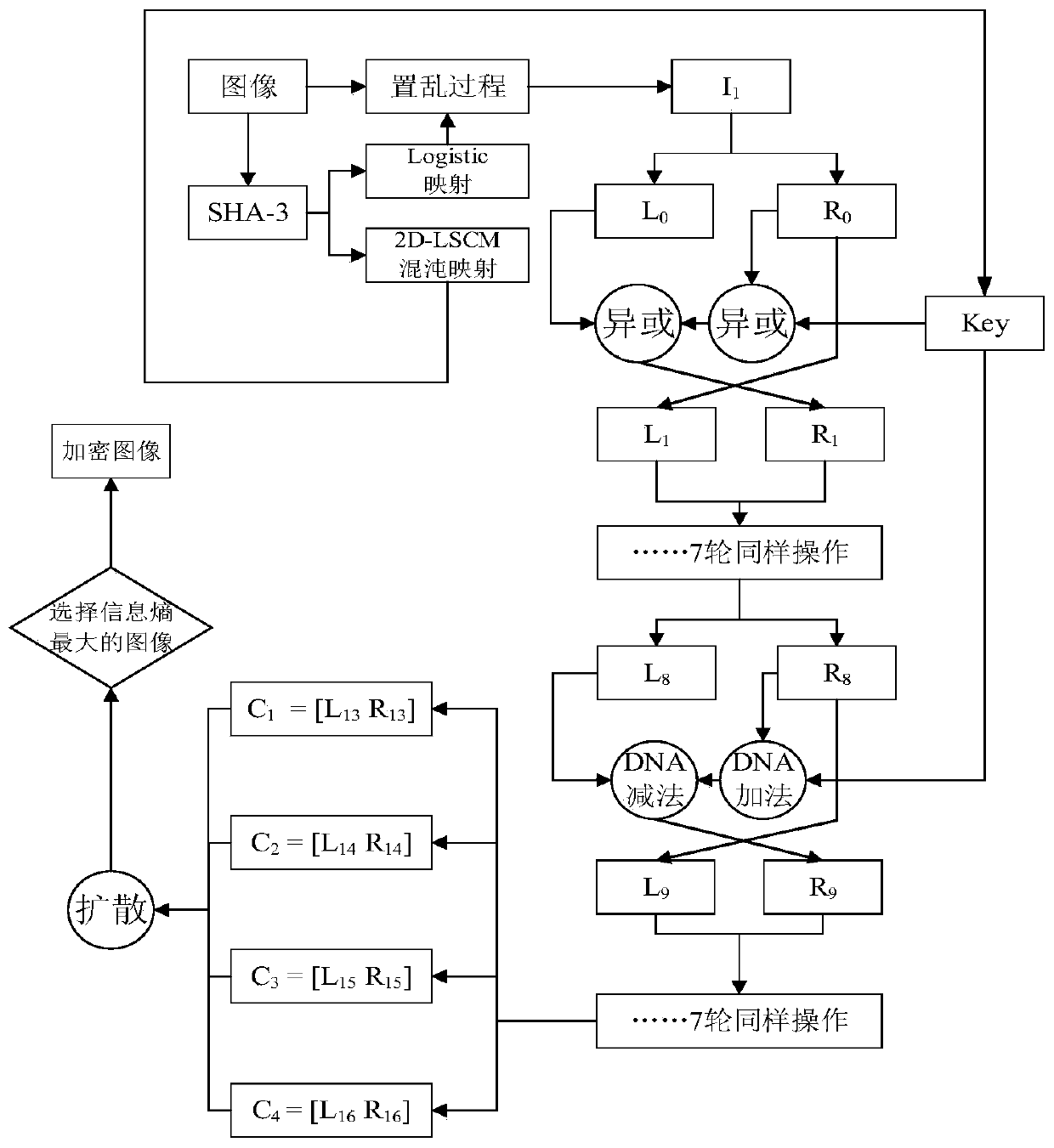
Image encryption method based on L-F cascade chaos and 3D bit scrambling
InactiveCN110889877AGuaranteed speedExpand the chaotic intervalImage codingDigital data protectionChosen-plaintext attackKey space
The invention discloses an image encryption method based on L-F cascade chaos and 3D bit scrambling. Image encryption is mainly divided into two steps: (1) 3D bit scrambling encryption and (2) diffusion operation. A novel L-F cascade chaos is constructed, the problem that a blank window exists due to uneven distribution of Logistic is solved while the rapidity of the Logistic is guaranteed, the chaos interval and number of parameters are increased, the secret key space is increased, and the exhaustion attack resistance of the system is improved. According to the method, the randomness of scrambled ciphertext is improved by adopting a 3D cyclic shift bit scrambling mode, and the problem that a bit scrambling sequence is insensitive is solved. According to the method, high-order informationcontaining a large amount of plaintext information and low-order information containing a small amount of plaintext information are separately scrambled, so that the noise attack resistance of the system is improved. According to the encryption system, the plaintext SHA-256 is used for carrying out strong association on the chaotic key, so that the plaintext sensitivity and the capability of resisting the attack of the selected plaintext are effectively improved.
Owner:QIQIHAR UNIVERSITY
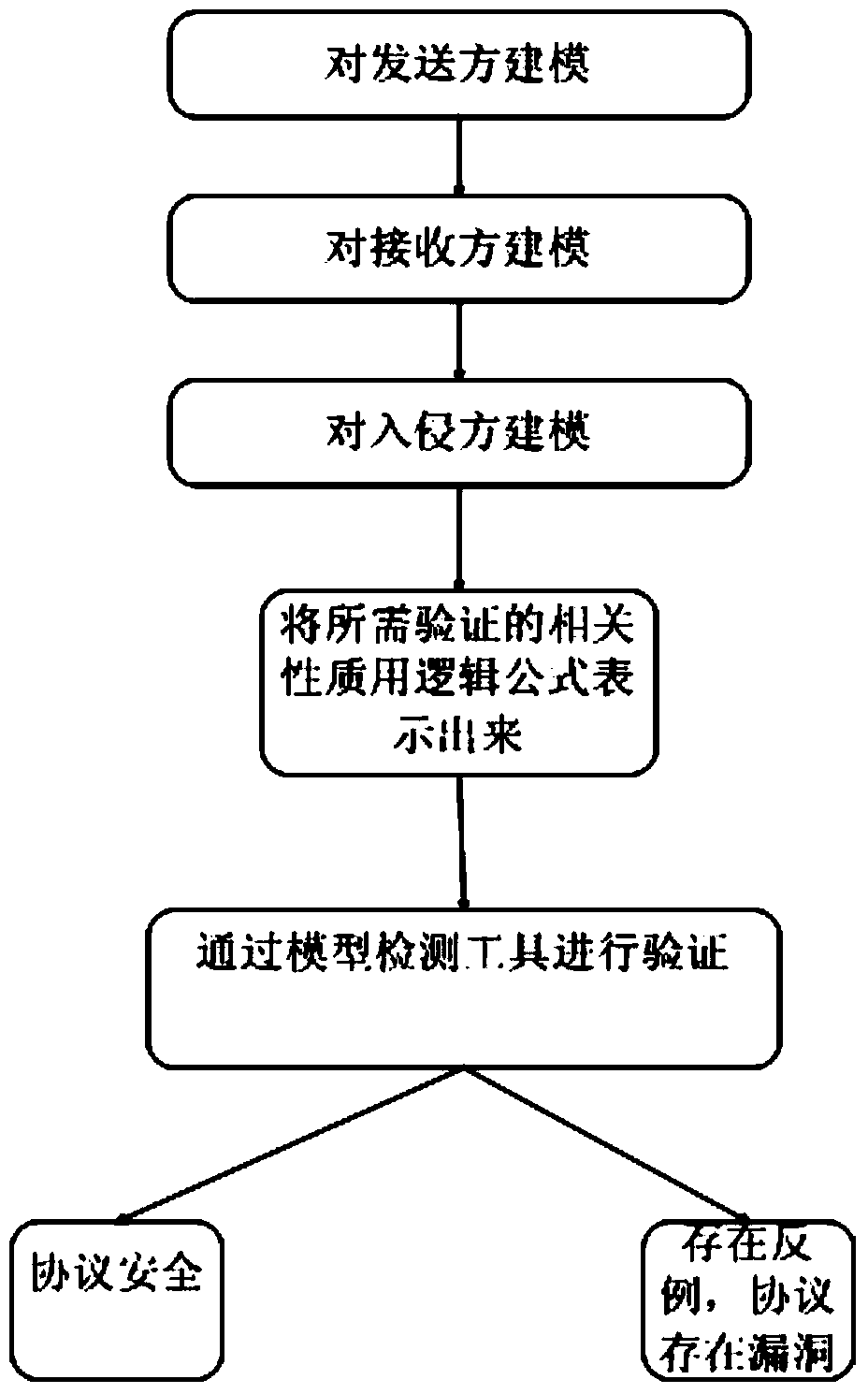
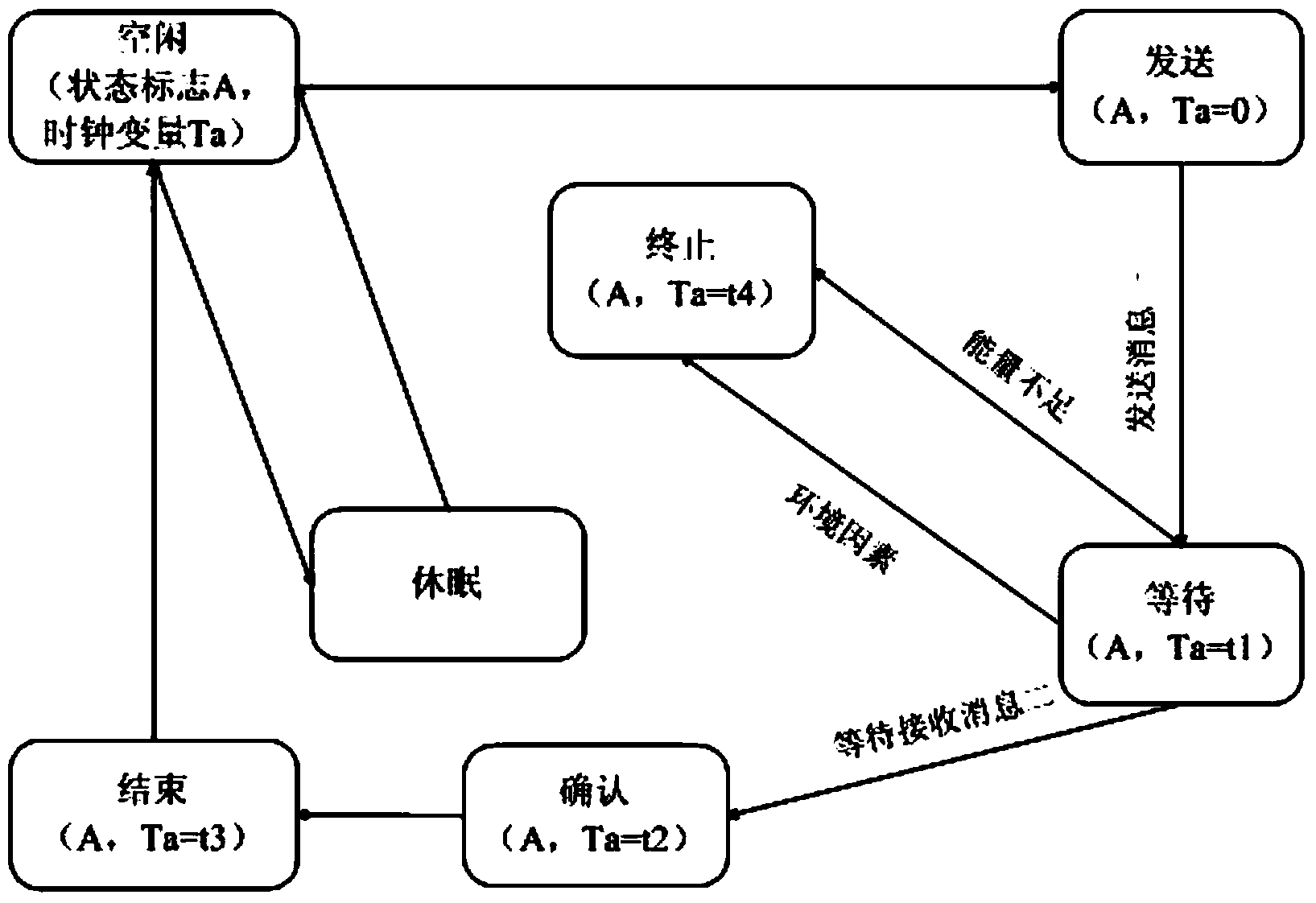
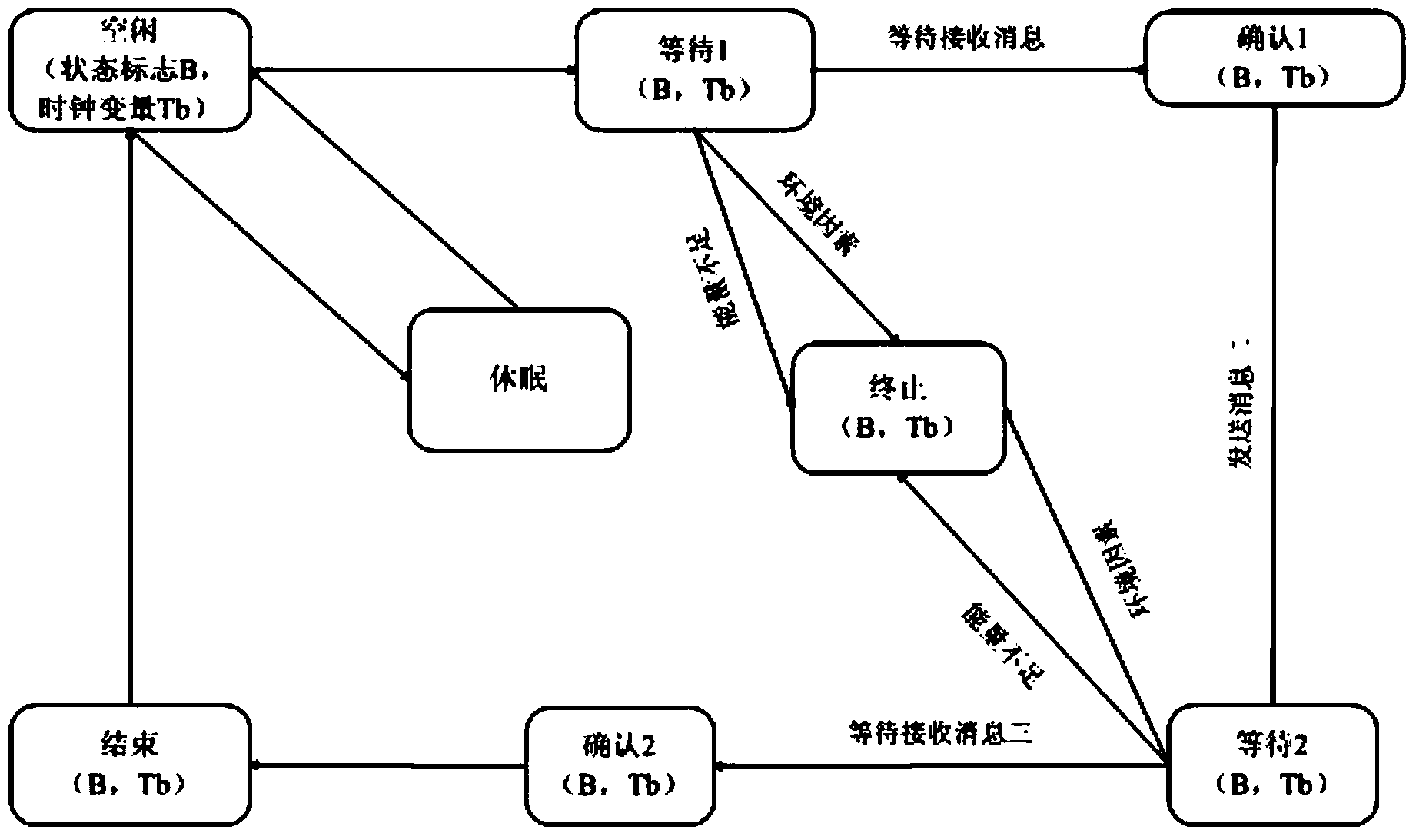
Wireless sensor network security protocol verification method based on model checking
ActiveCN103476033AVerify securityNetwork topologiesWireless network protocolsCryptographic protocolWireless sensor networking
The invention discloses a wireless sensor network security protocol verification method based on model checking. A state migratory system formed by a timed automata represents a wireless sensor network security protocol, a modal / time sequence logical formula represents the conditions which need to be met by the security protocol in the wireless sensor network, and the verification of the wireless sensor network security protocol is converted into a model carrying out verification that whether the state migratory system is a formula. According to the wireless sensor network security protocol verification method based on model checking, the characteristics of the wireless sensor network are sufficiently considered during the security protocol verification process, a clock restraint condition is added in the modal / time sequence logical formula, and comprehensive verification can be conducted on the wireless sensor network security protocol.
Owner:NANJING UNIV
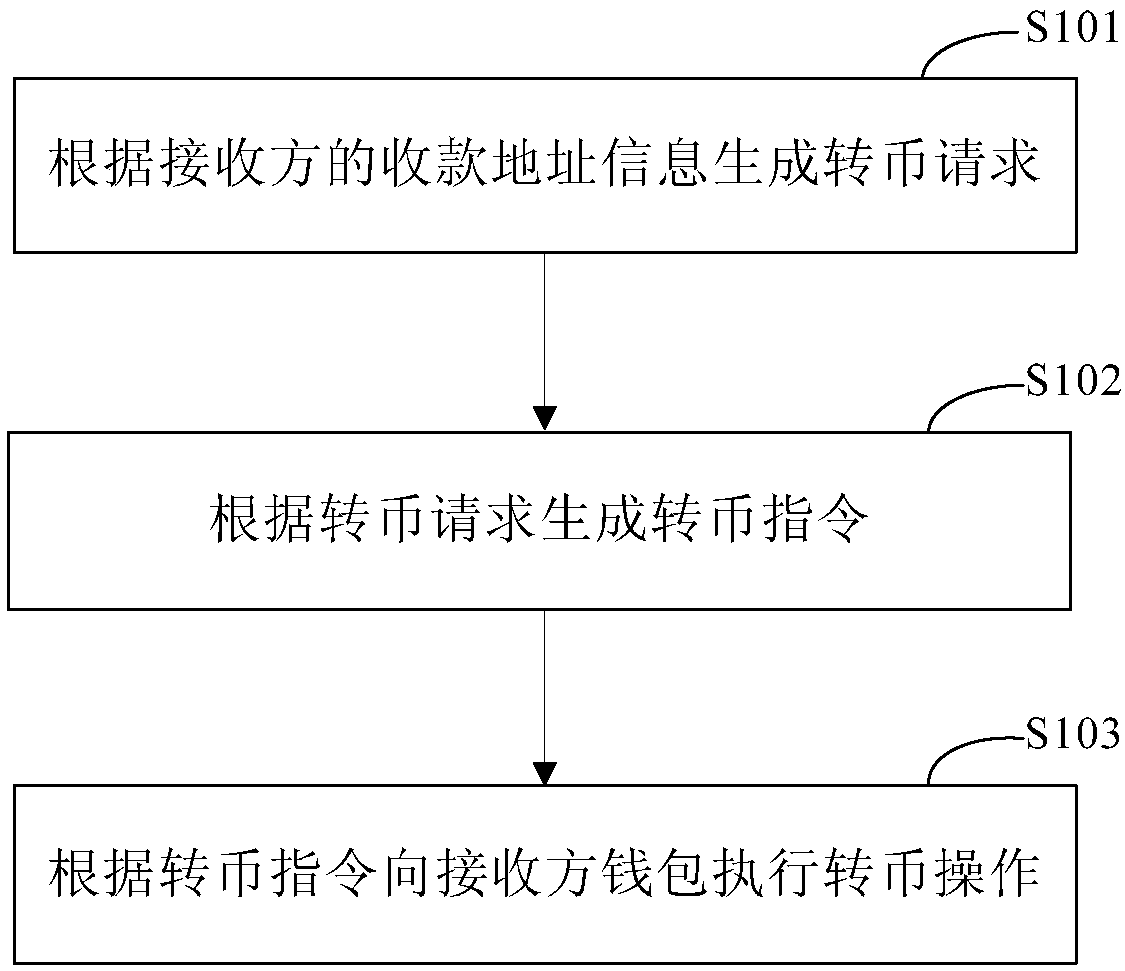
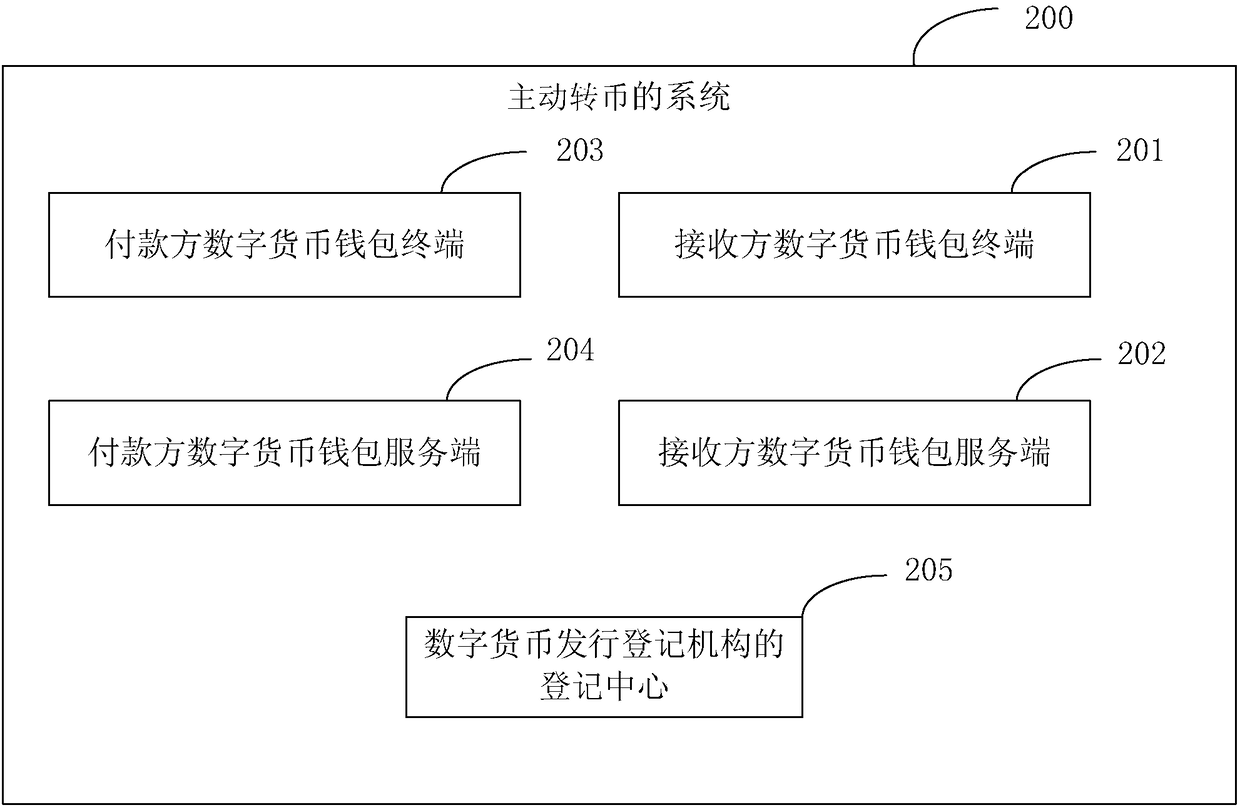
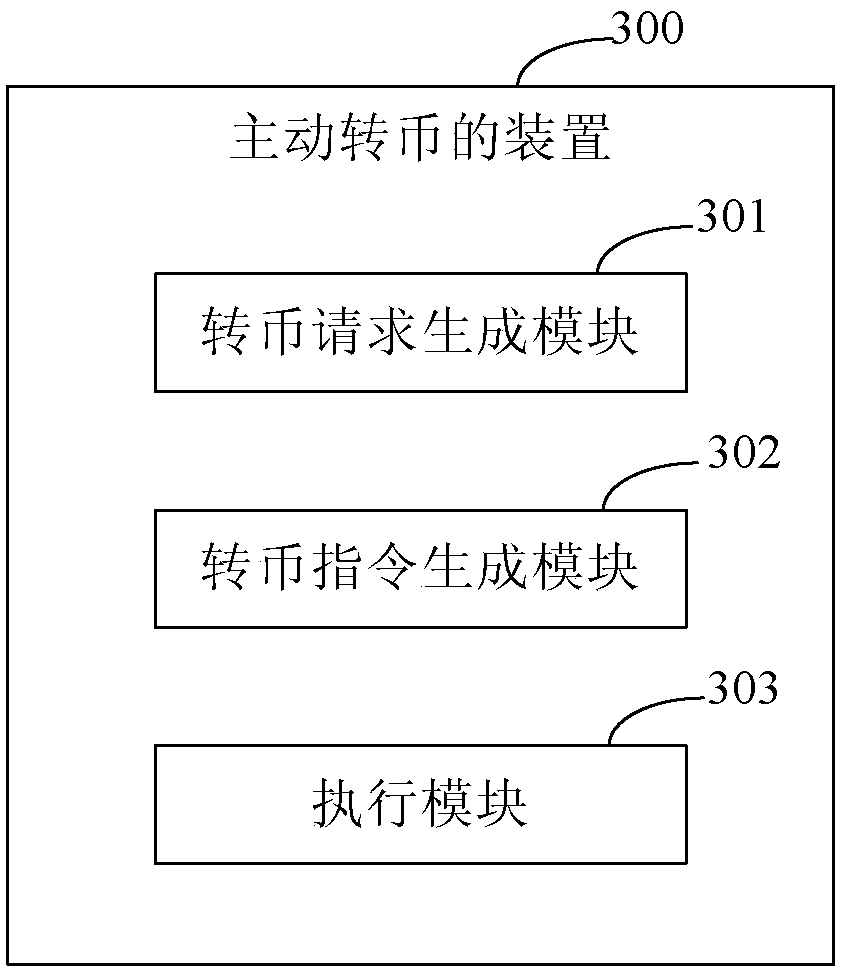
Method, apparatus, and system for active currency transferring
The embodiments of the invention provide a method, apparatus, and system for active currency transferring so that digital currency can be stored actually and a digital currency transferring mechanismthat is initiated by a payer between specific wallets can be realized. The method comprises: a currency transferring request is generated according to collection address information of a receiver; a currency transferring instruction is generated based on the currency transferring request; and according to the currency transferring request, currency transferring is carried out on a receiver walletbased on the currency transferring instruction.
Owner:THE PEOPLES BANK OF CHINA DIGITAL CURRENCY INST
Managing method for network equipment
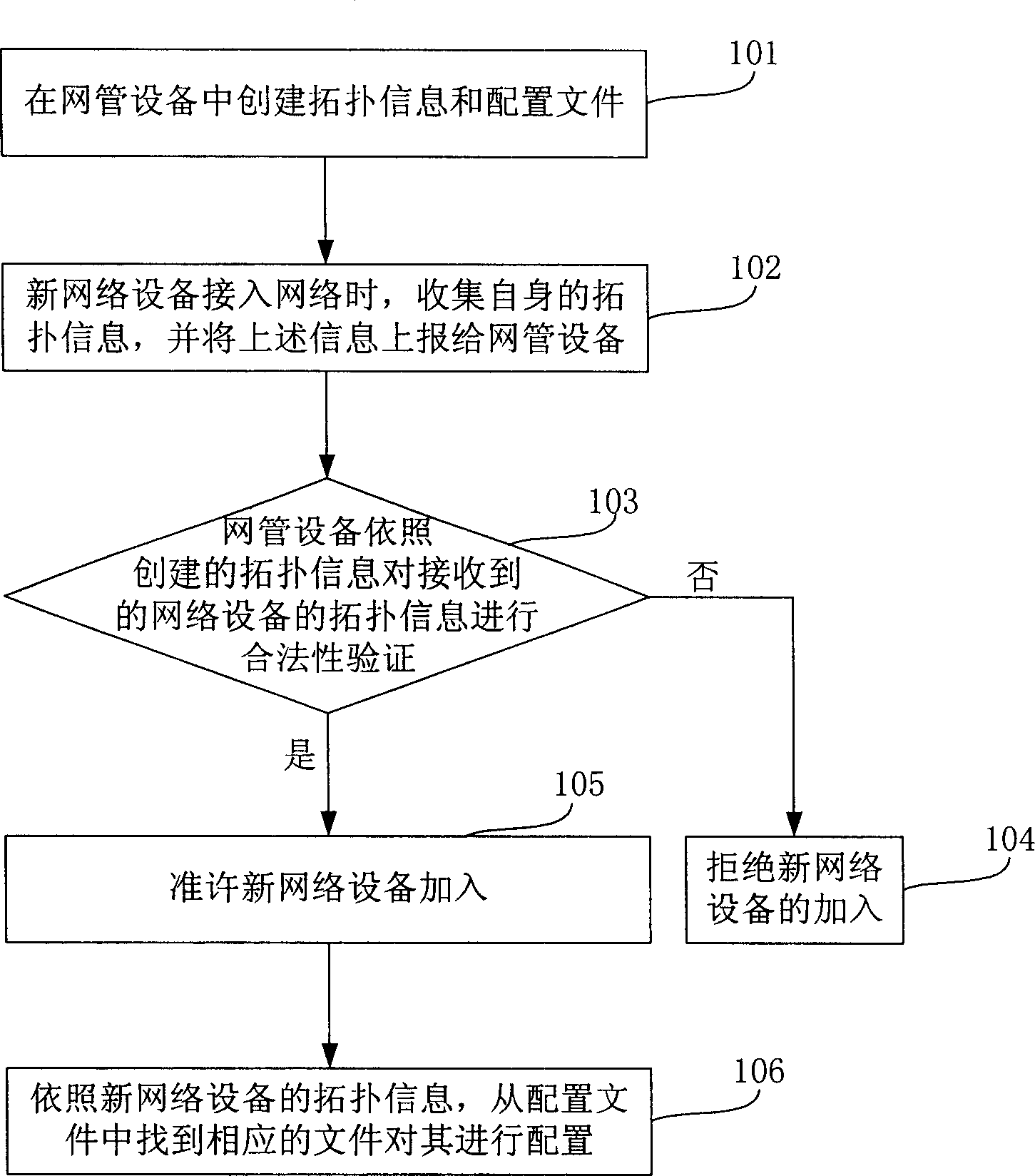
ActiveCN1859185AVerify securityIncrease flexibilityData switching networksAccess networkTopology information
The present invention discloses a network equipment management method, which contains to establish network equipment topology information and configuration files in network administrator equipment; network administrator equipment according to above-mentioned topology information identity authentication to accessed network equipment; network administrator equipment adding verified legal network equipment into administrative domain and according to above-mentioned configuration files configuring network equipment. The present invention ensures network administrator equipment network management security and raises network maintenance flexibility and expedience.
Owner:HUAWEI TECH CO LTD
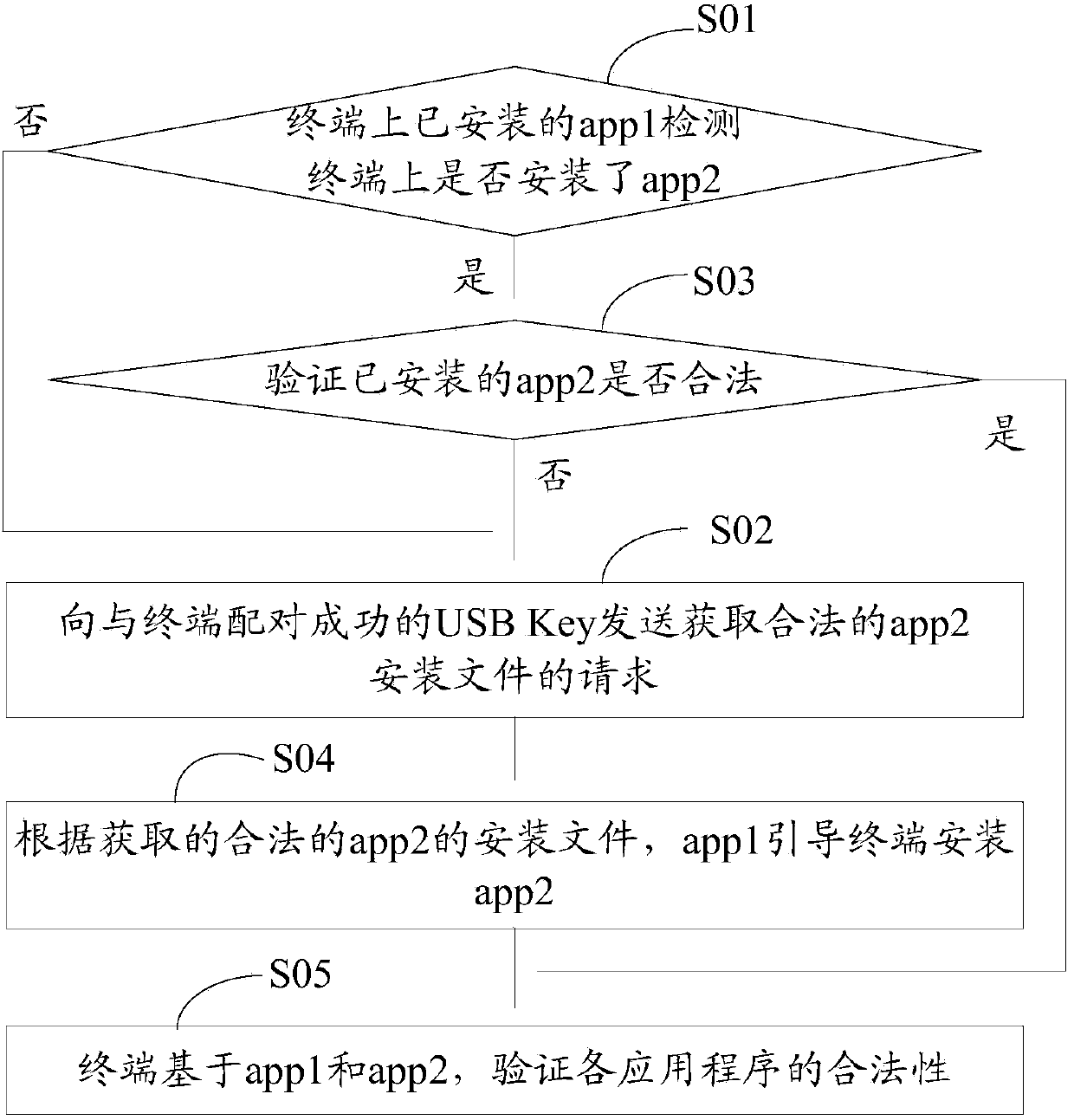
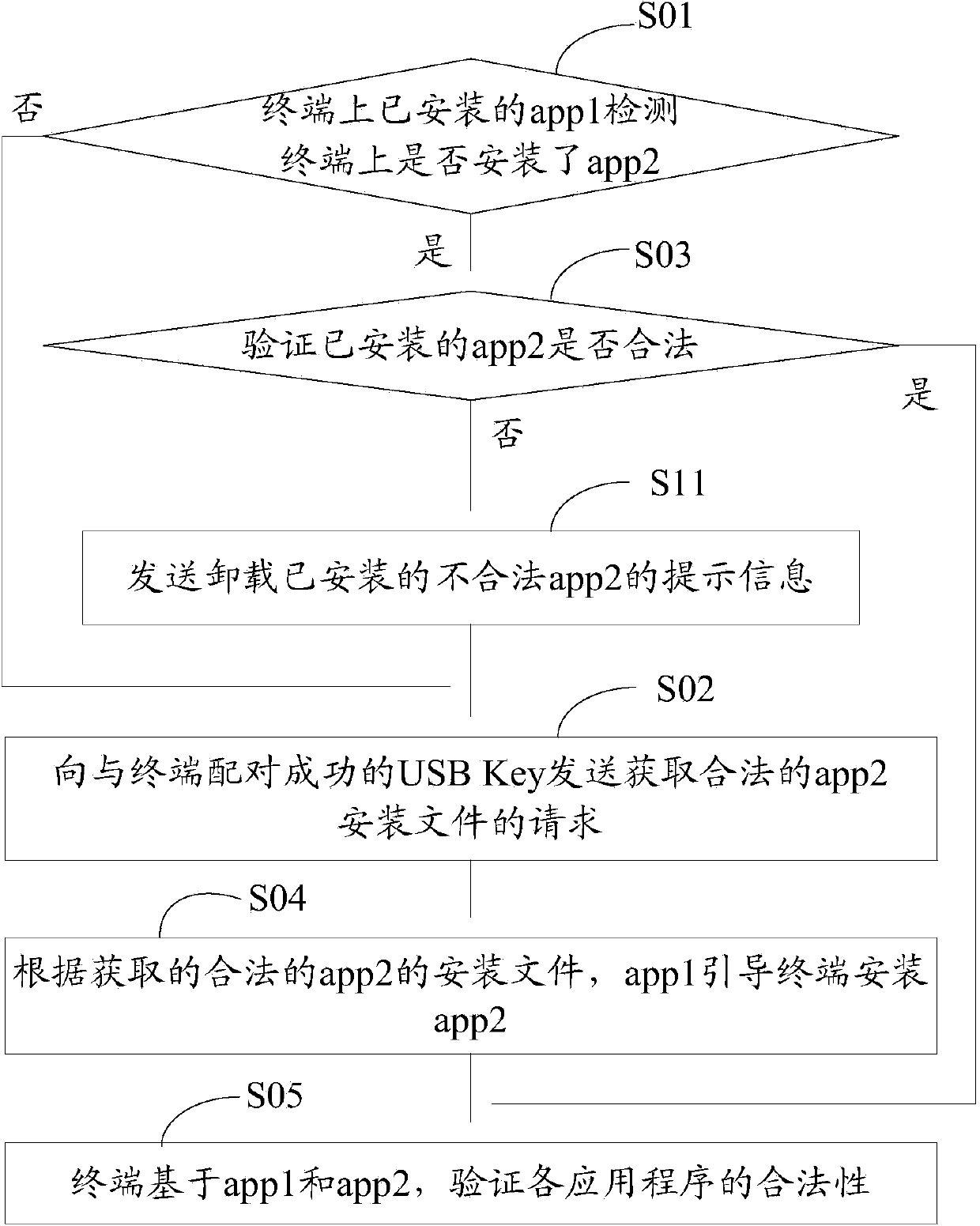
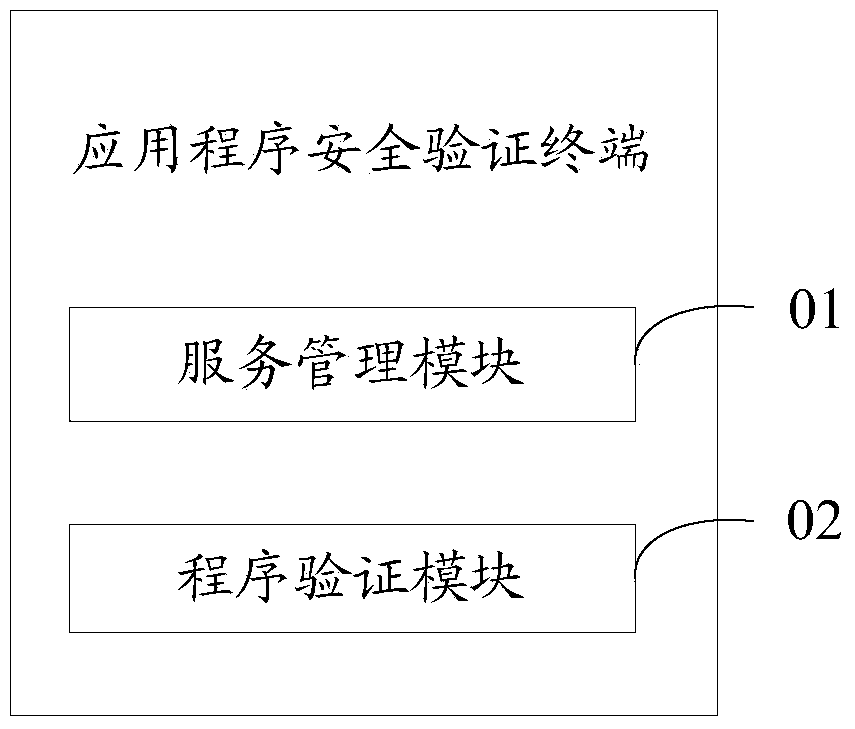
Application program security verification method and terminal
ActiveCN103473498AVerify legitimacyVerify securityDigital data authenticationTransmissionValidation methodsProgram security
The invention discloses an application program security verification method and a terminal. A reliable application program, namely a service management program is provided by a USB (universal serial bus) Key and used for verifying other application programs such as a security detection program on the terminal, so that validity and security of the application programs on the terminal are effectively verified, and the problem of security risks due to incapability of verifying validity of traditional application program download and installation is solved. The method has the advantages that security of the application programs on the terminal is improved, and further, security of personal information of users is ensured.
Owner:北京明华联盟科技有限公司
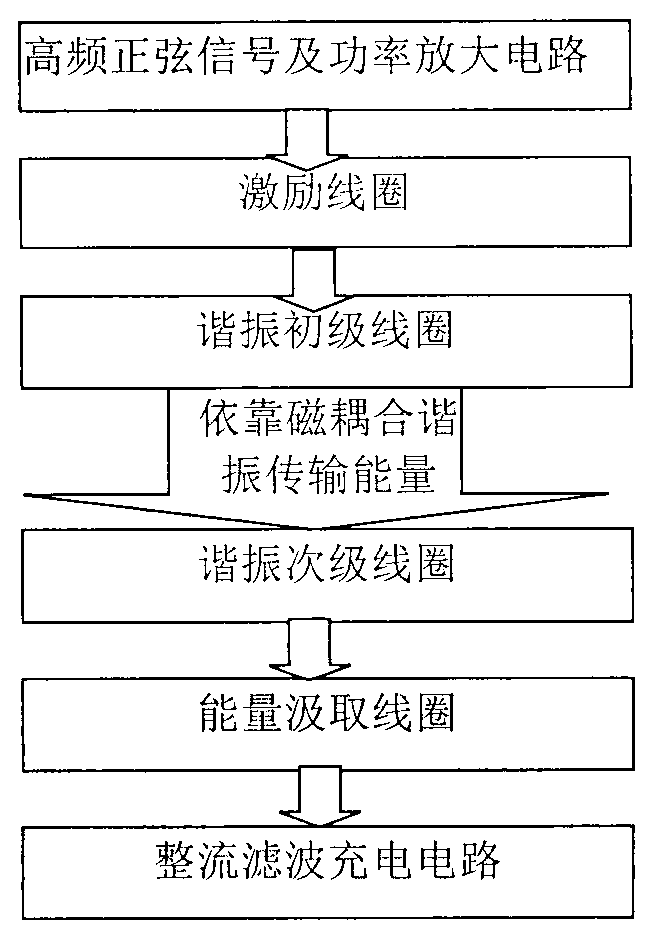
Small-size resonator and magnetic coupling resonance wireless energy transmission system
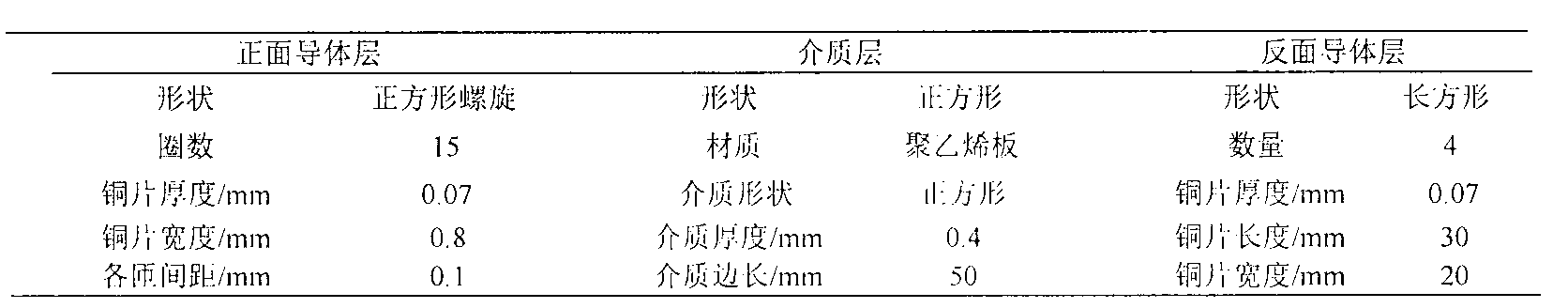
InactiveCN102983637ARaise the resonant frequencyVerify securityElectromagnetic wave systemTransformersCapacitanceElectrical conductor
Magnetic coupling resonance wireless energy transmission is a new technology which utilizing magnetic coupling resonance to achieve middle-distance electric energy wireless transmission, and has good application prospects. The invention provides a small-size plane-spiral resonance coil made by a printed board directly, the front face and the back face of the coil are all coated with copper, inductance generated on a front conductor layer and capacitance generated on an overlapped section of the front conductor layer and a back conductor layer form a needed resonator through a complex series-parallel connection circuit for energy transmission, and the size of the resonator is only 1.35 cm<3>. Through establishment of human head three-dimensional numerical model and implantation of a coil model into a body, a time-domain finite difference method is applied to the calculate head specific absorption rate and the electric-field magnetic field strength. Results show that when the magnetic coupling resonance wireless energy transmission technology is applied for the energy transmission of components implanted in the head, the I0g specific absorption rate (SAR) average value of the human head is 9.2627*10-6W / kg, the maximum value of root-mean-square of the electric-field magnetic field strength is respectively 4.64 V / m and 0.057 A / m, and the values are lower than the international safety limit standard.
Owner:HEBEI UNIV OF TECH
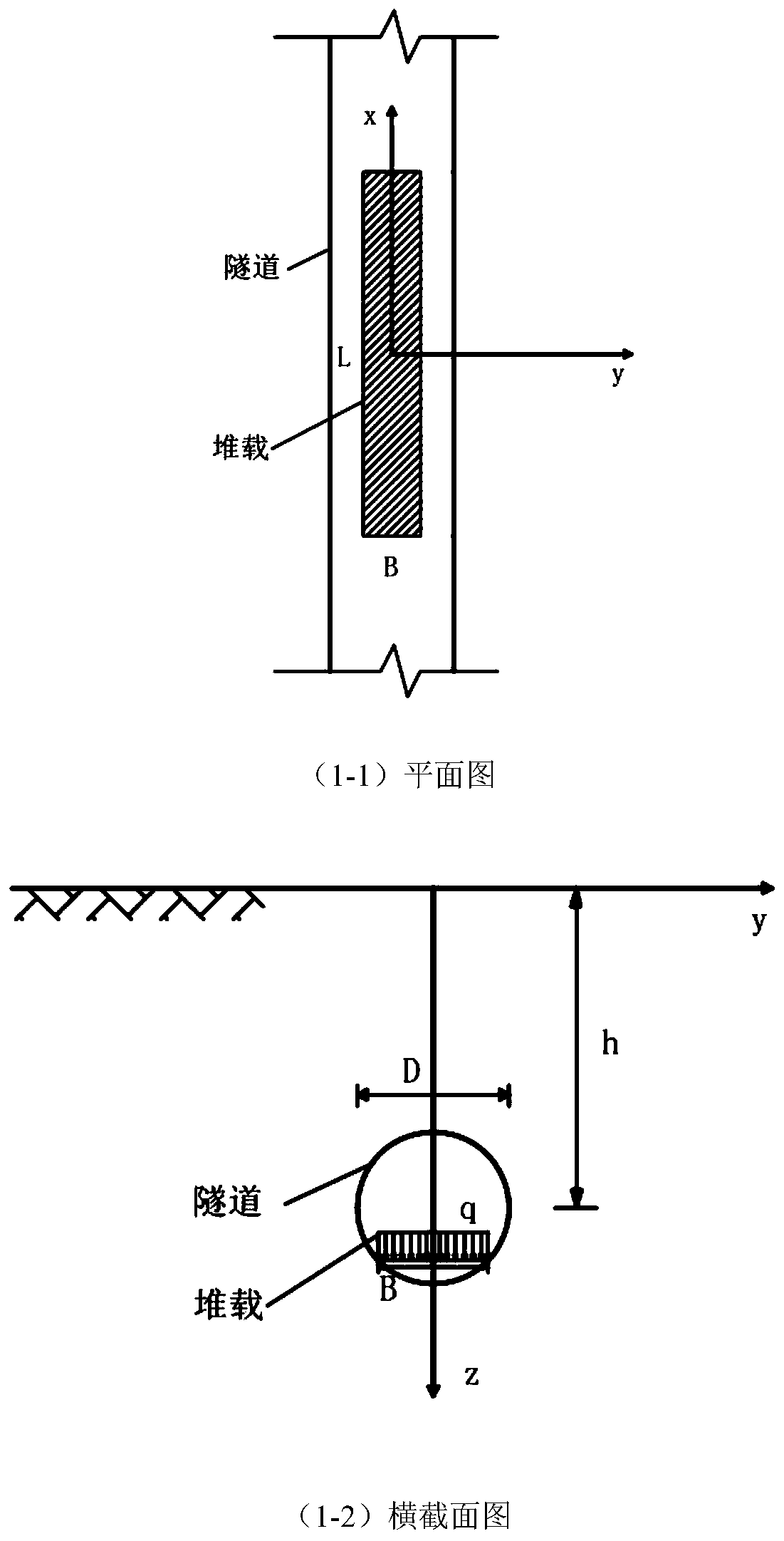
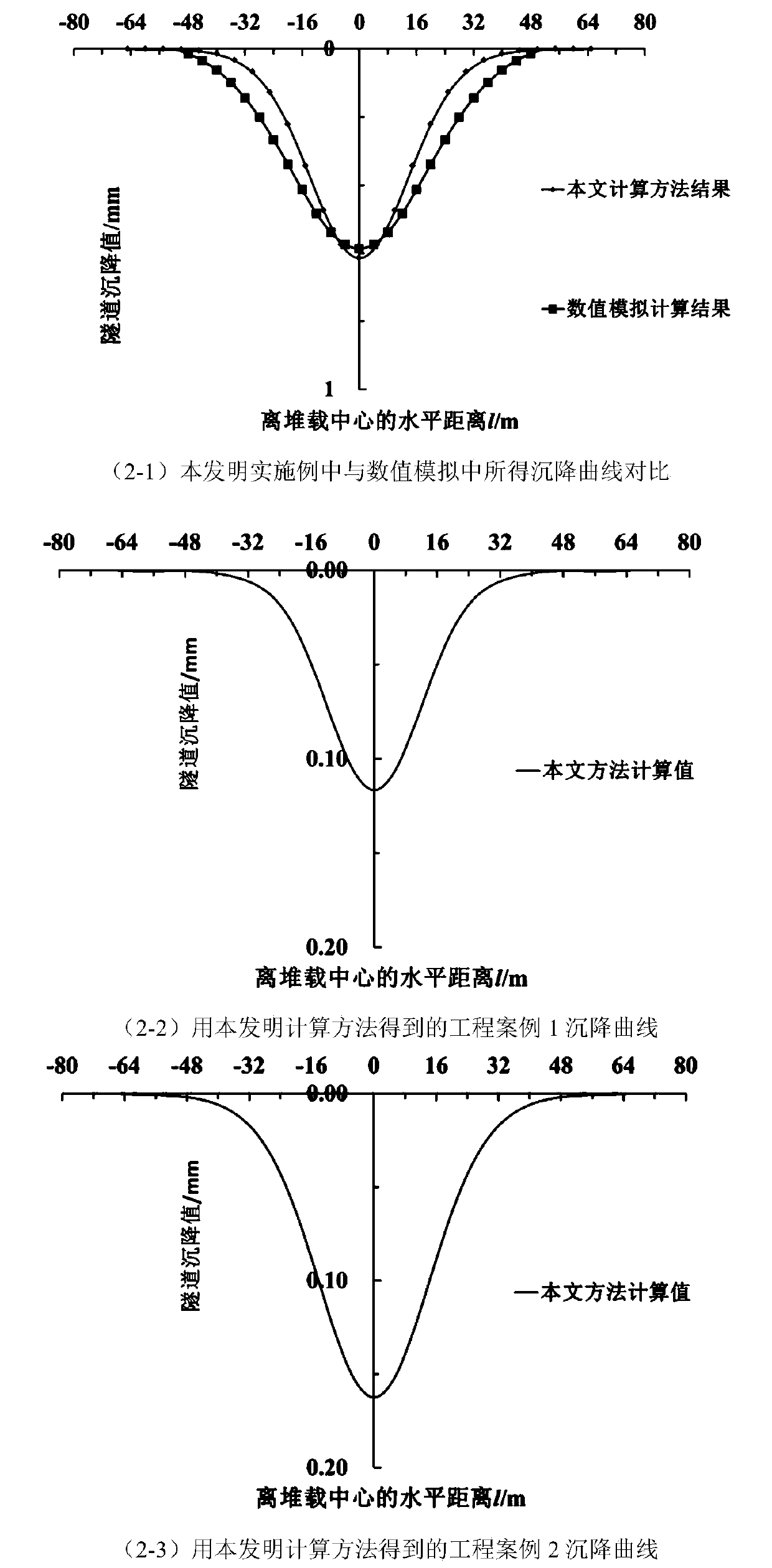
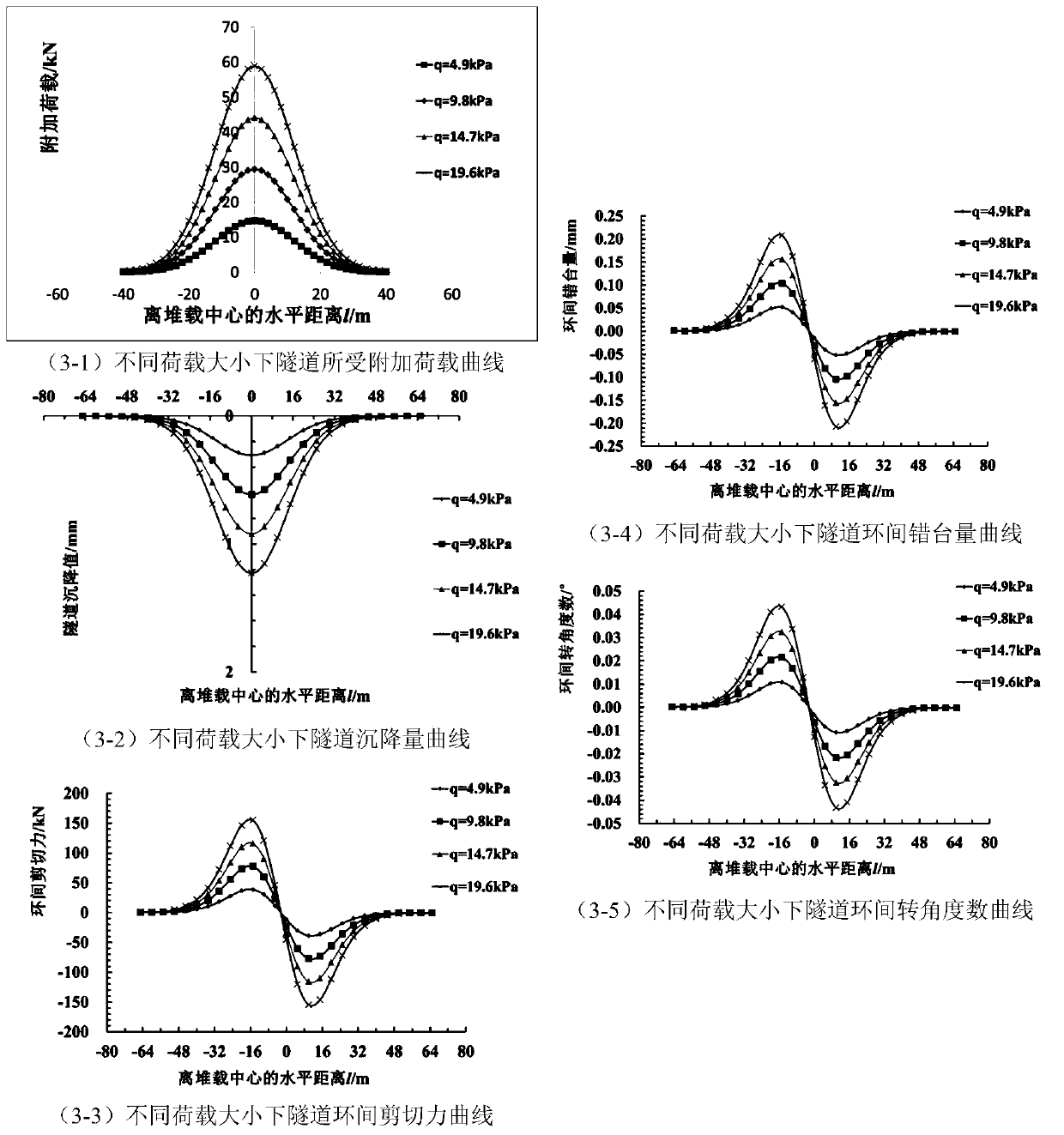
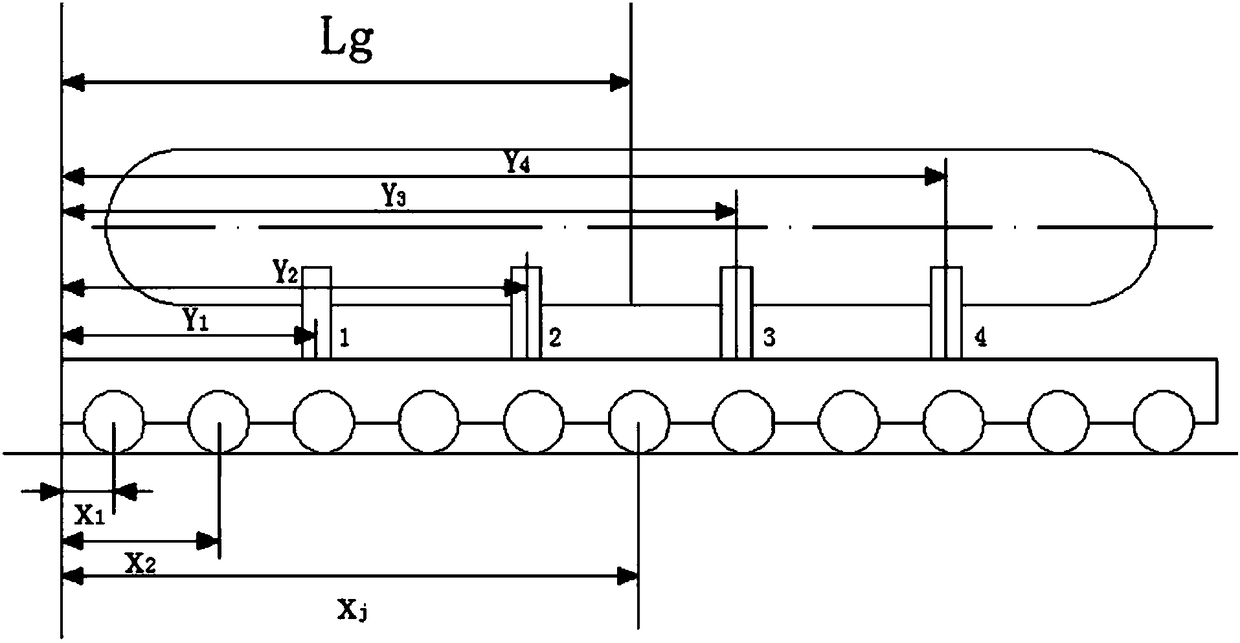
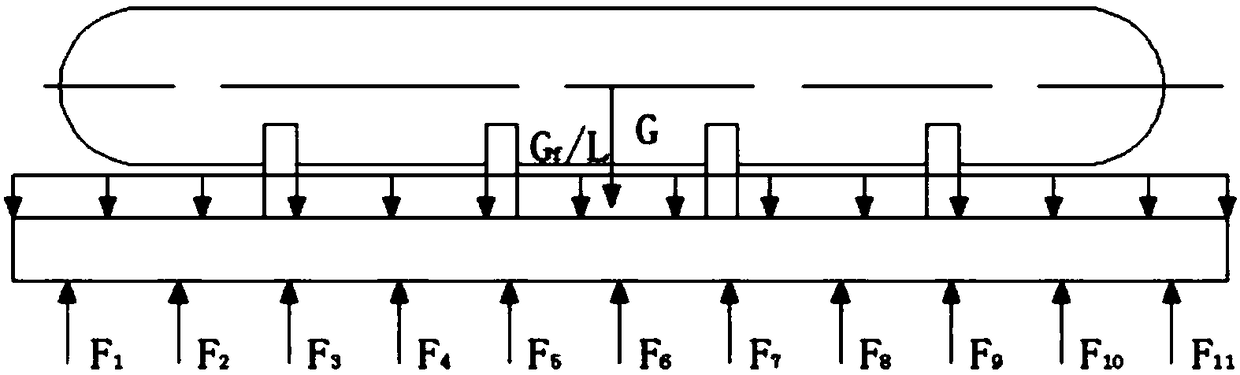
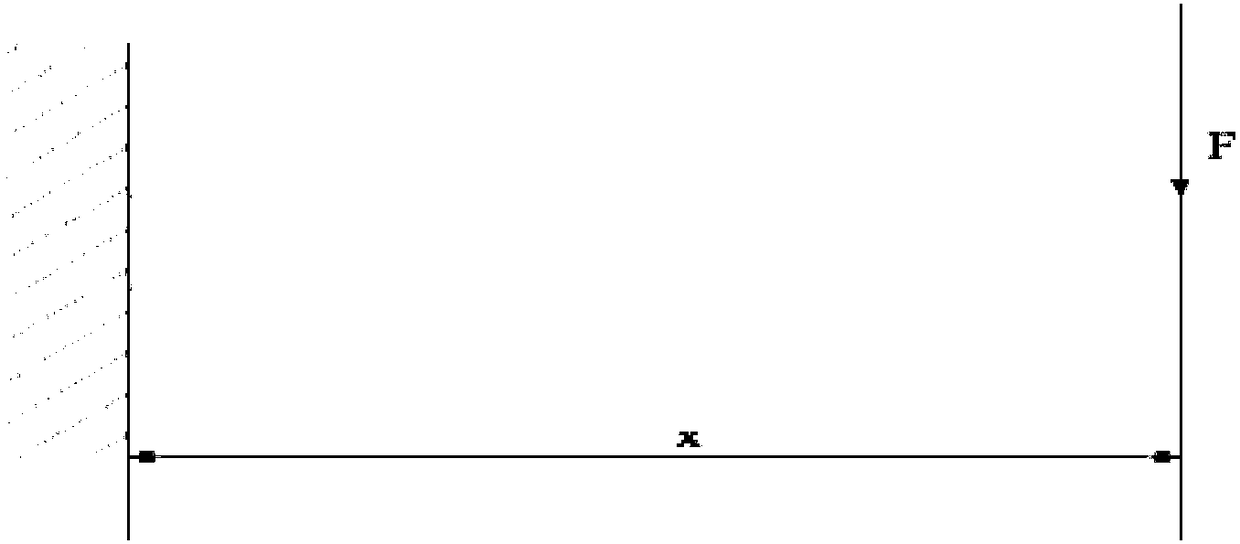
Calculation method for displacement deformation of existing tunnel caused by concentrated loads in tunnel
ActiveCN110147587AThe result is accurateSimple calculationSustainable transportationDesign optimisation/simulationMechanical modelsShearing deformation
The invention relates to a calculation method for displacement deformation of an existing tunnel caused by concentrated loads in the tunnel. The calculation method comprises the following steps: step1) establishing a mechanical model of heap loading in the tunnel; 2) calculating an additional load by adopting a derivation formula of a Peck formula; and 3) calculating tunnel settlement and deformation. The method has the beneficial effects that the joint effect between the tunnel rings is considered, a shear staggered platform model is introduced, meanwhile, shear deformation and staggered platform deformation between the tunnel rings are analyzed, the shear deformation and the staggered platform deformation are more consistent with an actual tunnel structure stress deformation mode, and atunnel settlement and deformation calculation result is more accurate; in the calculation method, the modeling is simple and clear; the calculation process of the soil body additional load is simpleand easy to understand, and the finally obtained load normal distribution function f (x) involves few parameters and is convenient to calculate and analyze.
Owner:ZHEJIANG UNIV CITY COLLEGE +1
Stress and formation analysis method for deep foundation pit engineering structure under complex conditions
The invention relates to a stress and formation analysis method for a deep foundation pit engineering structure under complex conditions. The analysis method mainly comprises the following aspects of: (1) stress and deformation analysis of a space enclosing structure during the construction stage; (2) stress and deformation analysis of an underground structure during the construction and using stage; (3) contrastive analysis of measured data during excavation of a foundation pit. Compared with the prior art, the stress and formation analysis method disclosed by the invention has the advantages of reasonable design, effective guide of site construction and abnormal situation treatment, good safety and reliability of the structure and the like.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +2
digital image encryption method based on a DES structure and DNA coding
ActiveCN109756322AResistant to Statistical AttacksResistance to Differential AttacksEncryption apparatus with shift registers/memoriesGenetic modelsComputation complexityCiphertext
The invention provides a digital image encryption method based on a DES structure and DNA coding. The method is used for solving the problems that when a traditional DES encryption algorithm is applied to image encryption, operation is complex, and clipping attack resistance is poor. According to the method, the structure of the DES encryption algorithm is used for reference, and methods such as DNA encoding operation, ciphertext output selection and key verification are used, so that the problems of high computational complexity, inconvenience in key management and the like when a traditionalcharacter encryption algorithm is applied to digital image encryption are well solved. According to the method, the security of the ciphertext is verified by analyzing indexes such as information entropy, pixel change rate and image correlation of the ciphertext; The method has a very good recovery capability when being attacked, has a relatively large key space to resist exhaustive attacks, canalso resist statistical attacks, differential attacks, clipping attacks, noise attacks and the like, and can be widely applied to secure transmission of image information.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Method for proving integrity of cloud data storage
ActiveCN106899406AVerify integrityVerify securityKey distribution for secure communicationComputation complexityData expansion
The invention discloses a method for proving the integrity of cloud data storage. The method for proving the integrity of cloud data storage comprises the following steps: the user processes a file to be uploaded, generates the private key, blocks the files, and calculates the label of each block; the user sends the pre-processed file to the cloud storage server, and only the private key is kept on local; when the verification of the integrity of cloud data storage is required, the user randomly selects a number of file blocks and launches a challenge to the cloud; the cloud generates a proof of having the file blocks and returns to the user; and the user performs the verification of the cloud data integrity by means of the proof of having the file blocks. Compared with the prior art, the positive effects of the invention comprise: the integrity of multiple file blocks can be verified at one time by means of the addition homomorphism of bitwise extraction of binary data, and the method has the characteristics of low data expansion rate and low computational complexity.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
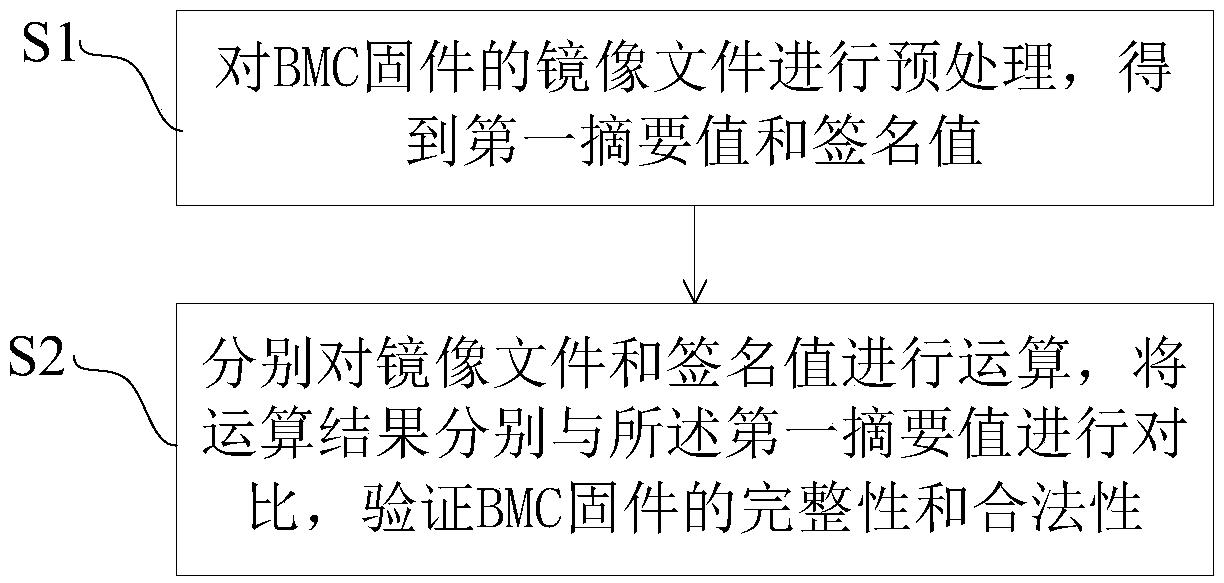
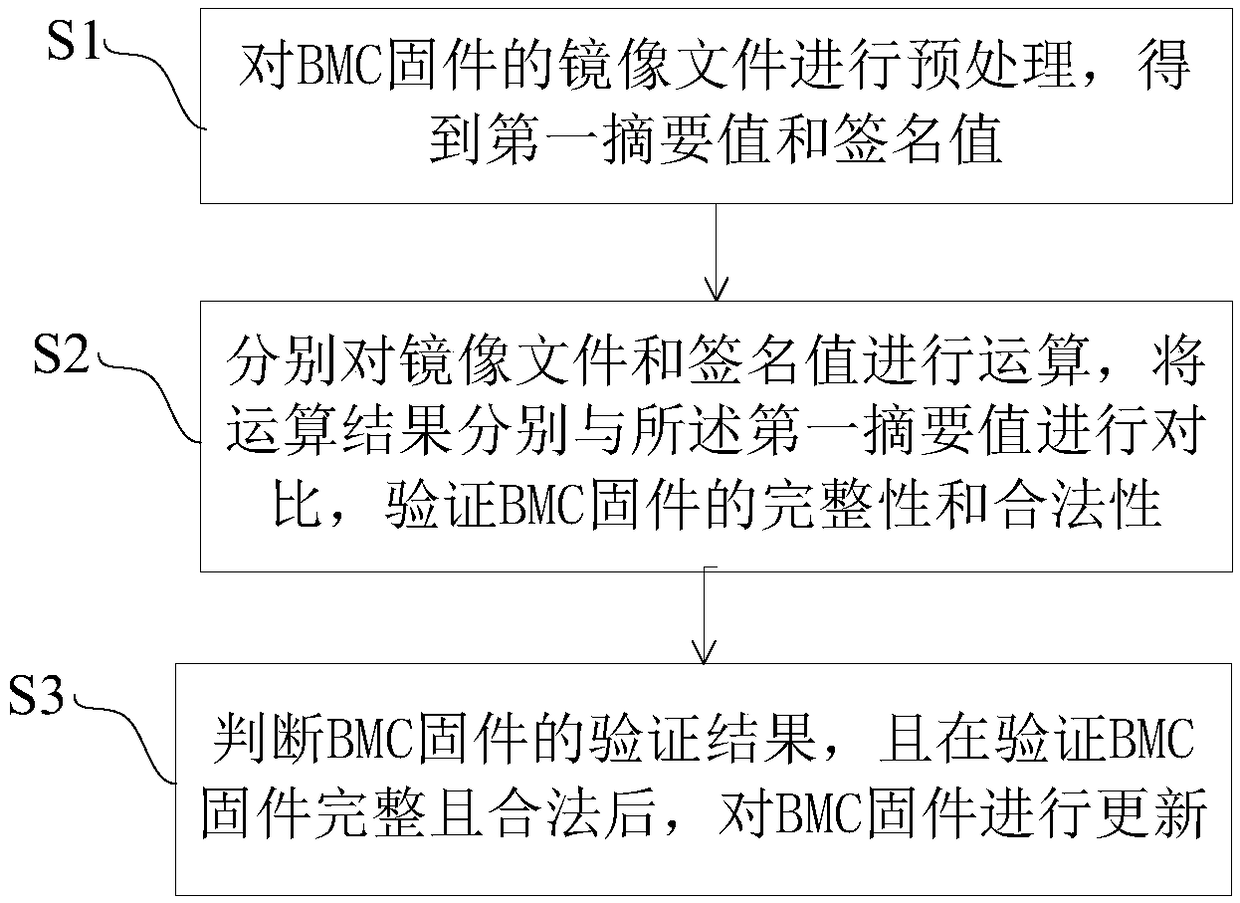
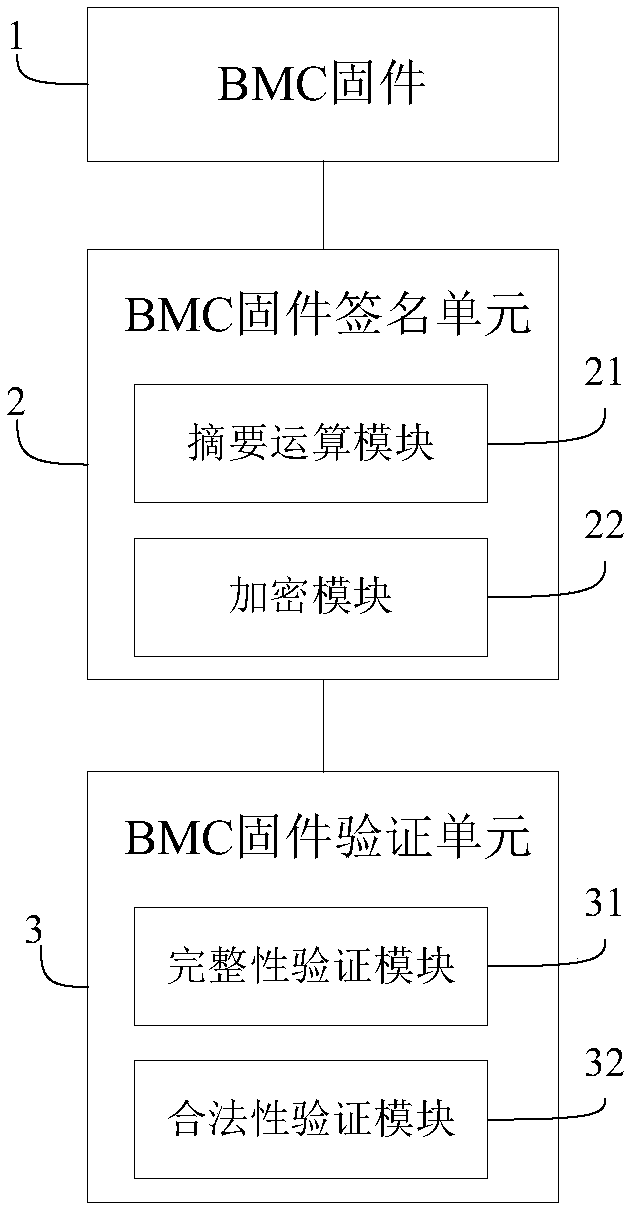
Security verification method and system of BMC firmware
InactiveCN109063470AVerify integrityVerify legitimacyPlatform integrity maintainanceSoftware deploymentComputer securityFirmware
The invention provides a BMC firmware security verification method and system. The method comprises the following steps: preprocessing a mirror image file of the BMC firmware to obtain a first digestvalue and a signature value; The image file and the signature value are calculated respectively, and the operation results are compared with the first digest value to verify the integrity and legitimacy of the BMC firmware. The system comprises a BMC firmware and a BMC firmware signature unit, which is used for preprocessing the mirror file of the BMC firmware to obtain a first digest value and asignature value; The BMC firmware verification unit calculates the image file and the signature value respectively, compares the operation result with the first digest value respectively, and verifiesthe integrity and legitimacy of the BMC firmware. At the same time, the invention verifies the integrity and legitimacy of the BMC firmware, and ensures the security of the BMC firmware to be updated.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
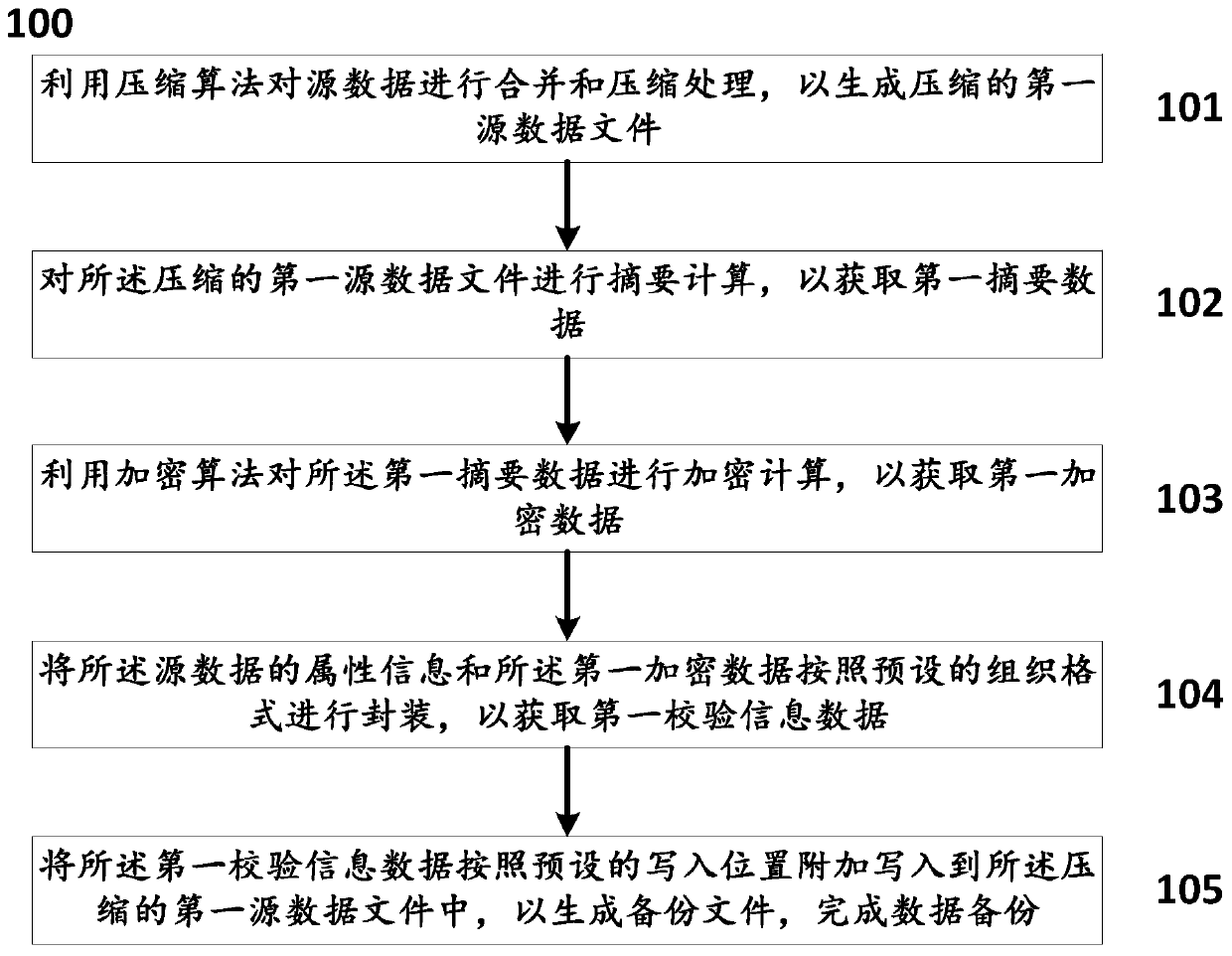
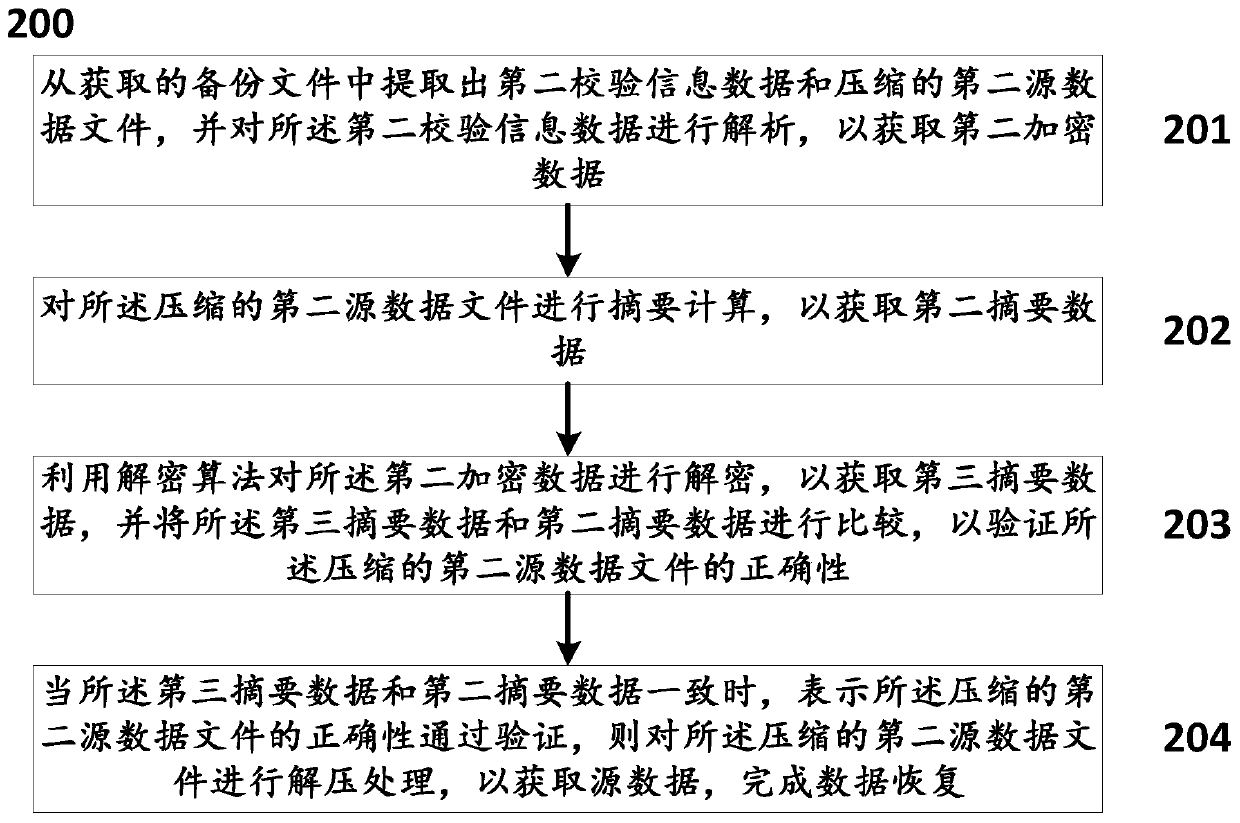
Data backup method and system, data recovery method and system and mobile terminal
PendingCN109871296AImprove securityVerify securityDigital data information retrievalDigital data protectionTamper resistanceSummary data
The invention discloses a data backup method and system, a data recovery method and system and a mobile terminal, and the method comprises the steps: carrying out the combination and compression of source data through employing a compression algorithm, generating a compressed first source data file, carrying out the summary calculation, and obtaining first summary data; performing encryption calculation on the first abstract data to obtain first encrypted data; packaging the attribute information of the source data and the first encrypted data to obtain first verification information data; andwriting the first verification information data into the compressed first source data file to generate a backup file, and finishing data backup. According to the method, the compressed backup file isabstracted and encrypted by adopting a compression algorithm and a digital abstract and encryption technology, and verification information and the compressed backup file are combined together, so that the backup file has good safety, is tamper-proof and forgery-proof, is convenient to manage, and guarantees the safety and integrity of recovered system data.
Owner:AEROSPACE INFORMATION
Safety analysis method of main longitudinal beam of highway heavy-goods transport trailer
ActiveCN108287957AAccurate calculation of bending momentVerify securityGeometric CADSpecial data processing applicationsVariable stiffnessStatically indeterminate
The invention discloses a safety analysis method of a main longitudinal beam of a highway heavy-goods transport trailer. The method includes the steps of statically-indeterminate mechanical analysis of main-beam stress of the large-goods transport axis vehicle; calculation of arbitrary-position deflection of a variable-stiffness cantilever beam under the action of single-form force; calculation ofarbitrary-position deflection of a variable-stiffness simply-supported-beam under the action of single-form force; calculation of arbitrary-position deflection of a vehicle frame under the action ofsingle-form force; solving of shear force, a bending moment and deflection of an arbitrary position of the vehicle frame; and arrangement of optimal support and reinforcement beams of the vehicle frame. The method has the advantages of: precisely calculating a bending moment, shear force and deflection on each point of the longitudinal beam of the vehicle frame, verifying safety thereof, and providing a method of goods bracket setting and vehicle-frame strength reinforcement position and size setting under support of calculated specific data.
Owner:XIHUA UNIV +1
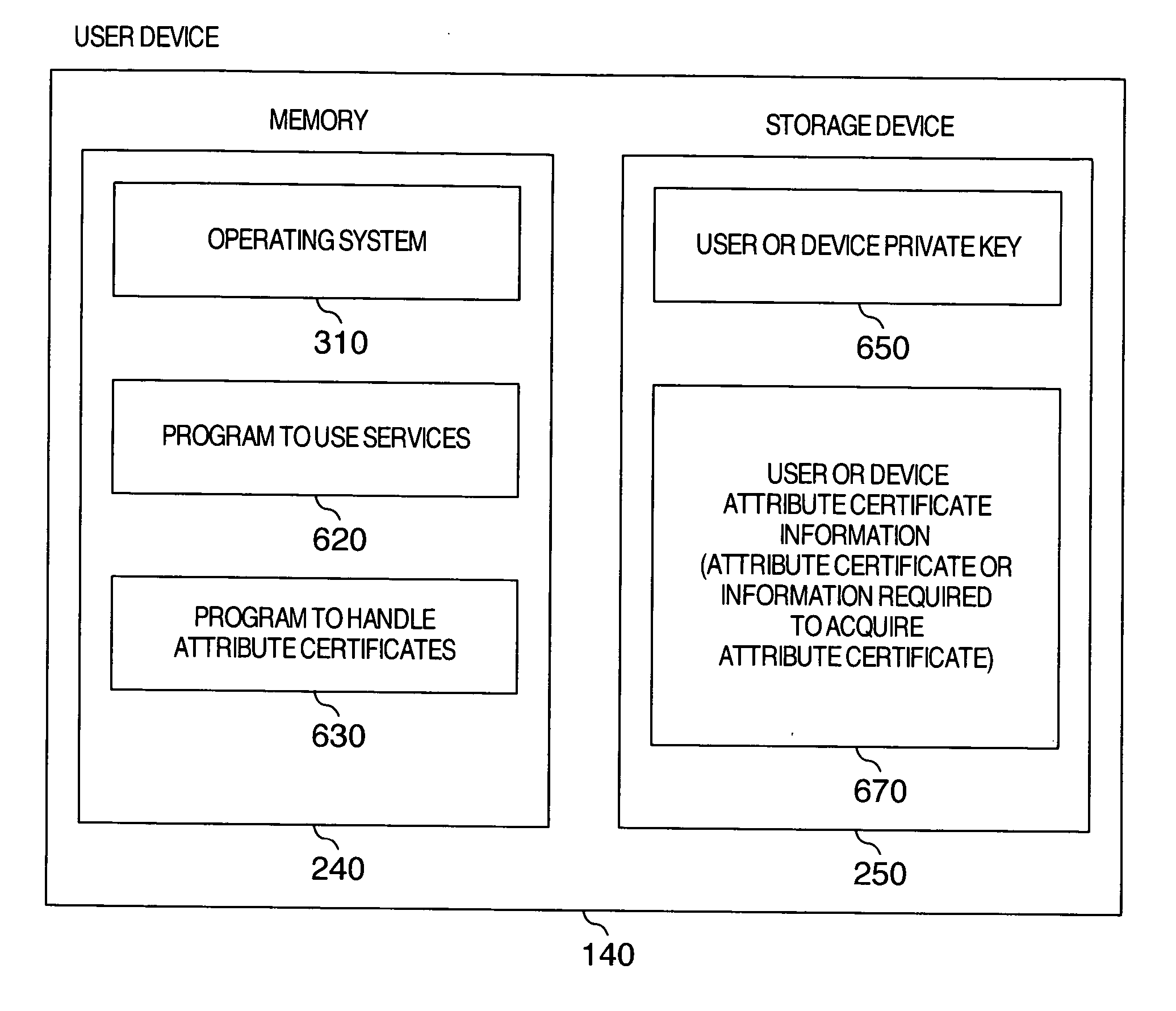
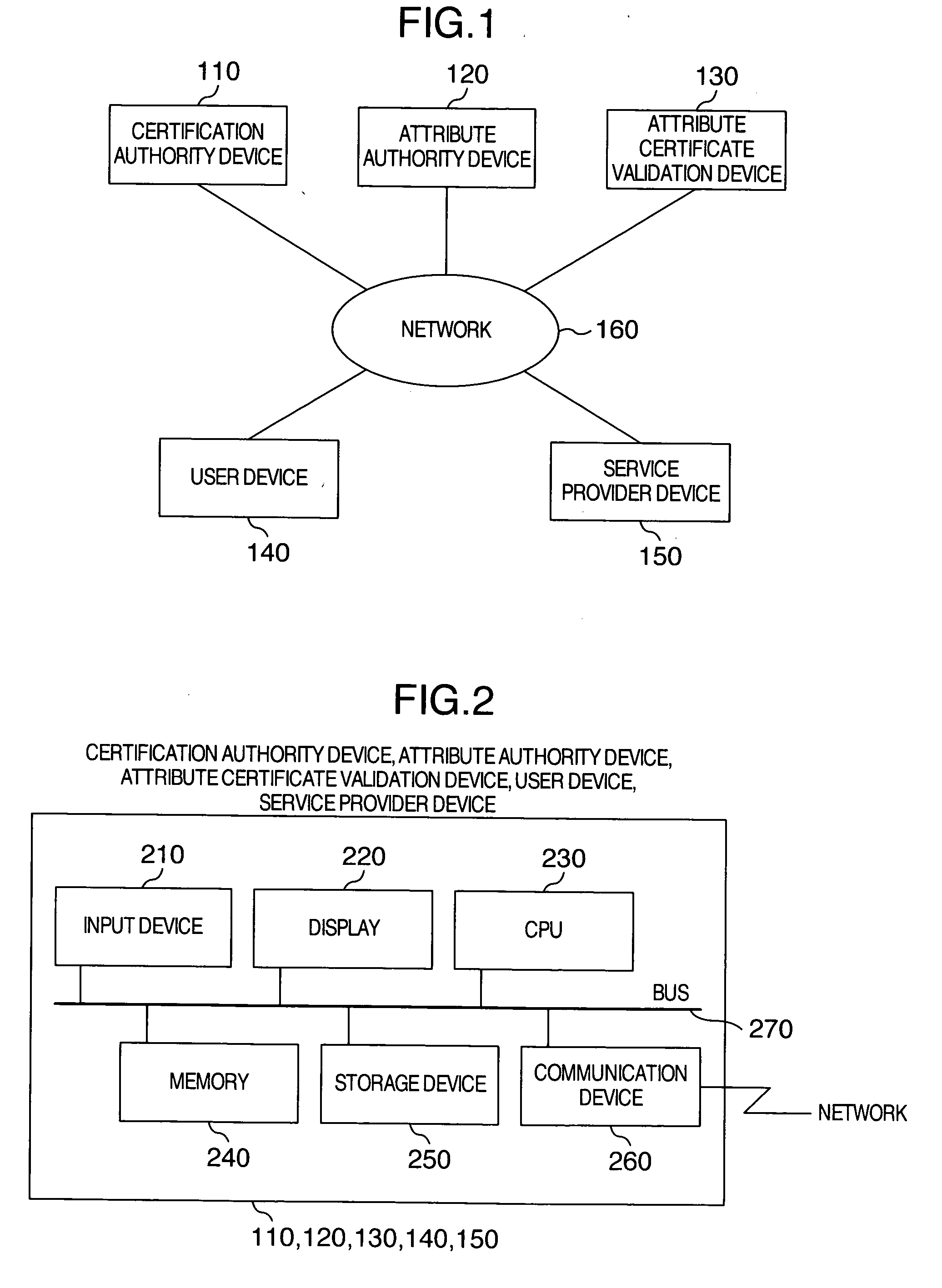
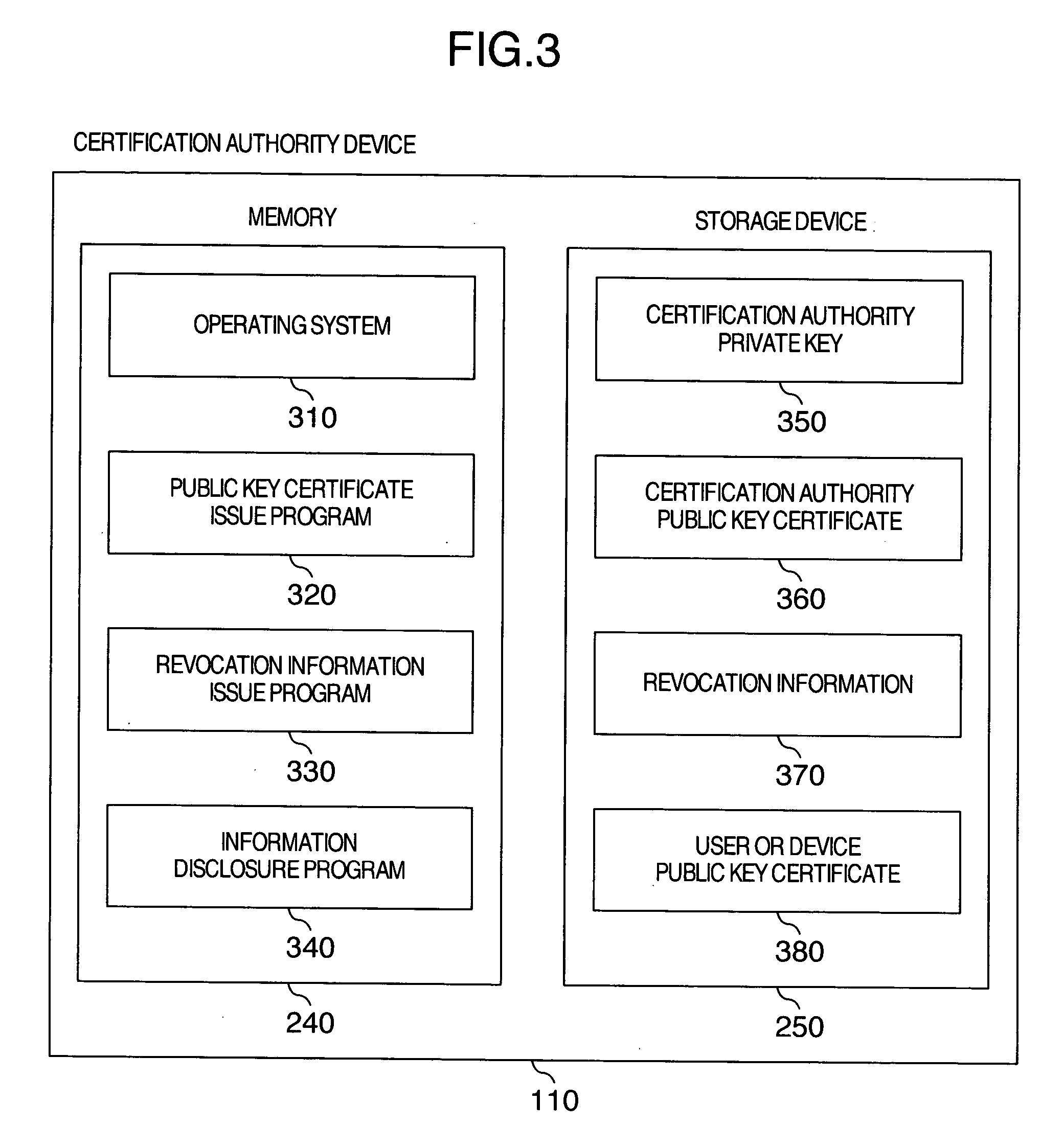
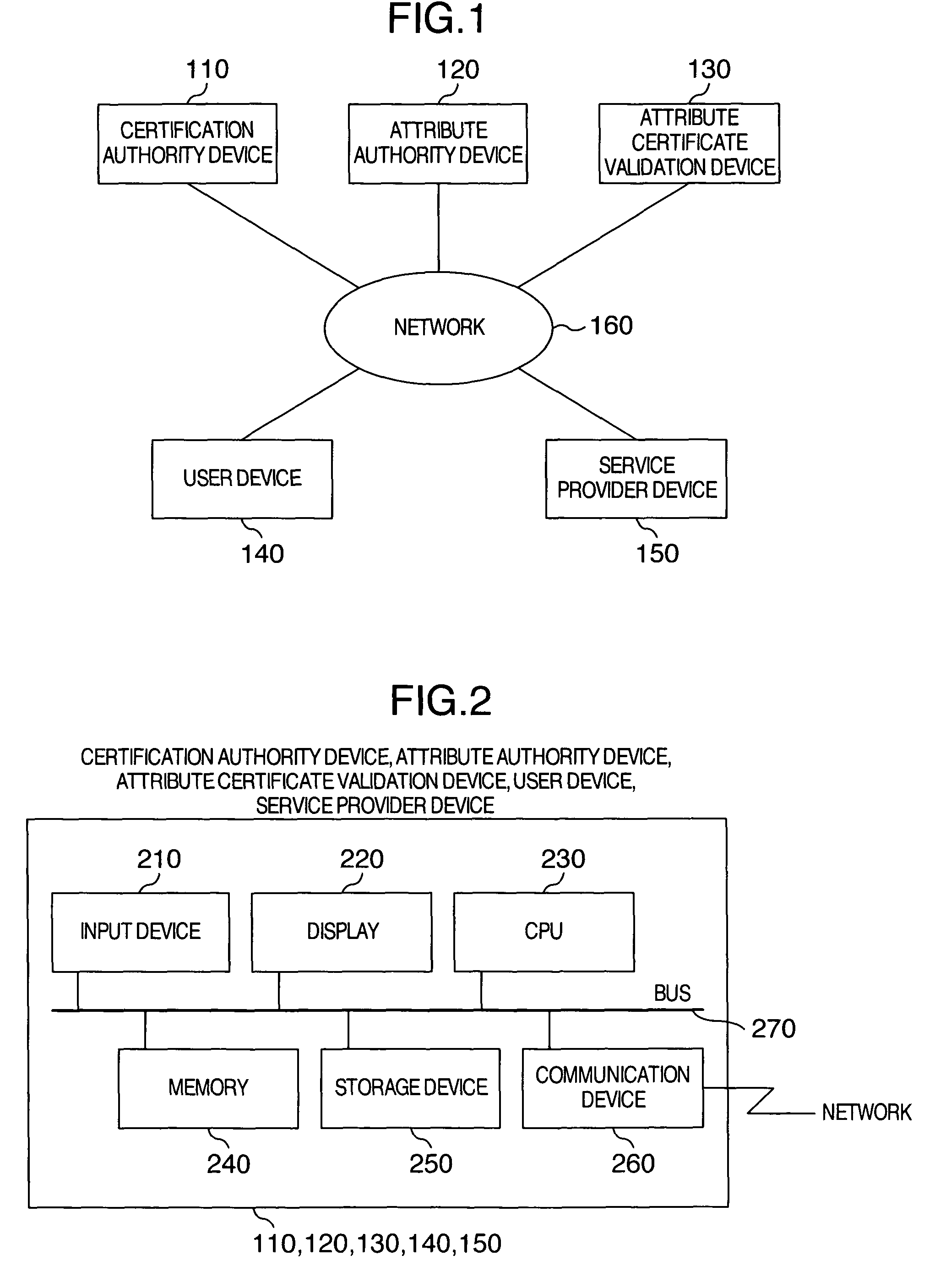
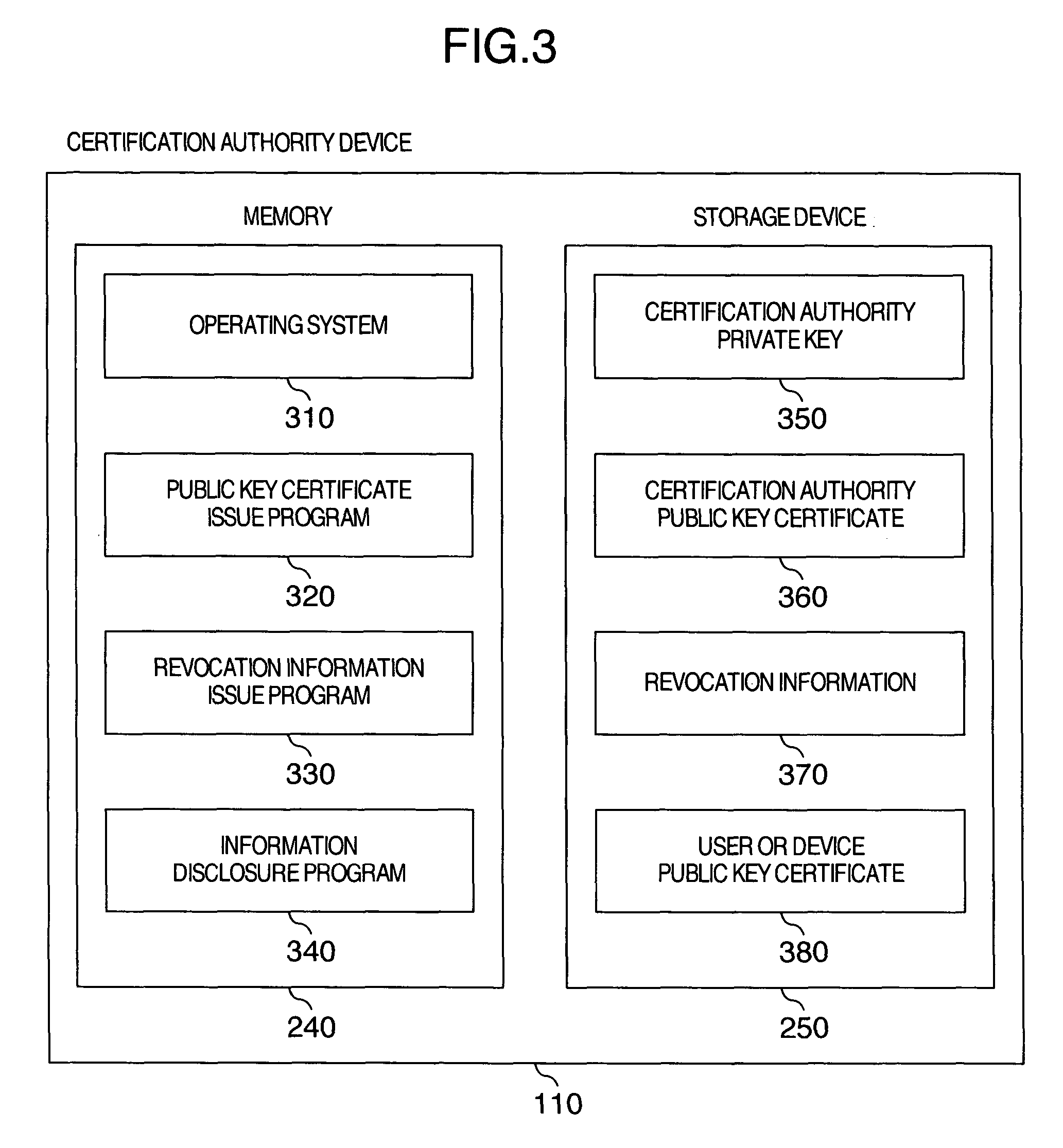
Attribute certificate validation method and device
InactiveUS20060277417A1Verify securityPrevention of identification and tracingKey distribution for secure communicationDigital data processing detailsValidation methodsTrusted third party
To verify a qualification on a network without notifying verifier privacy information that can identify as a subject of a public key certificate while keeping safety of the public key infrastructure technology. An attribute certificate validation method wherein by preparing an environment in which only an attribute certificate validation device operated by a trusted third party can access a user's public key certificate, the verifier transmits attribute certificate and signed data received from a user having presented a qualification, to the attribute certificate validation device to thereby request the device to make a check to confirm authenticity of the holder of the attribute certificate, thereby preventing the public key certificate (particularly, privacy information contained in the public key certificate) of the user from being passed to the verifier.
Owner:HITACHI LTD
Attribute certificate validation method and device
InactiveUS7840804B2Verify securityPrevention of identification and tracingKey distribution for secure communicationDigital data processing detailsValidation methodsTrusted third party
To verify a qualification on a network without notifying verifier privacy information that can identify as a subject of a public key certificate while keeping safety of the public key infrastructure technology. An attribute certificate validation method wherein by preparing an environment in which only an attribute certificate validation device operated by a trusted third party can access a user's public key certificate, the verifier transmits attribute certificate and signed data received from a user having presented a qualification, to the attribute certificate validation device to thereby request the device to make a check to confirm authenticity of the holder of the attribute certificate, thereby preventing the public key certificate (particularly, privacy information contained in the public key certificate) of the user from being passed to the verifier.
Owner:HITACHI LTD
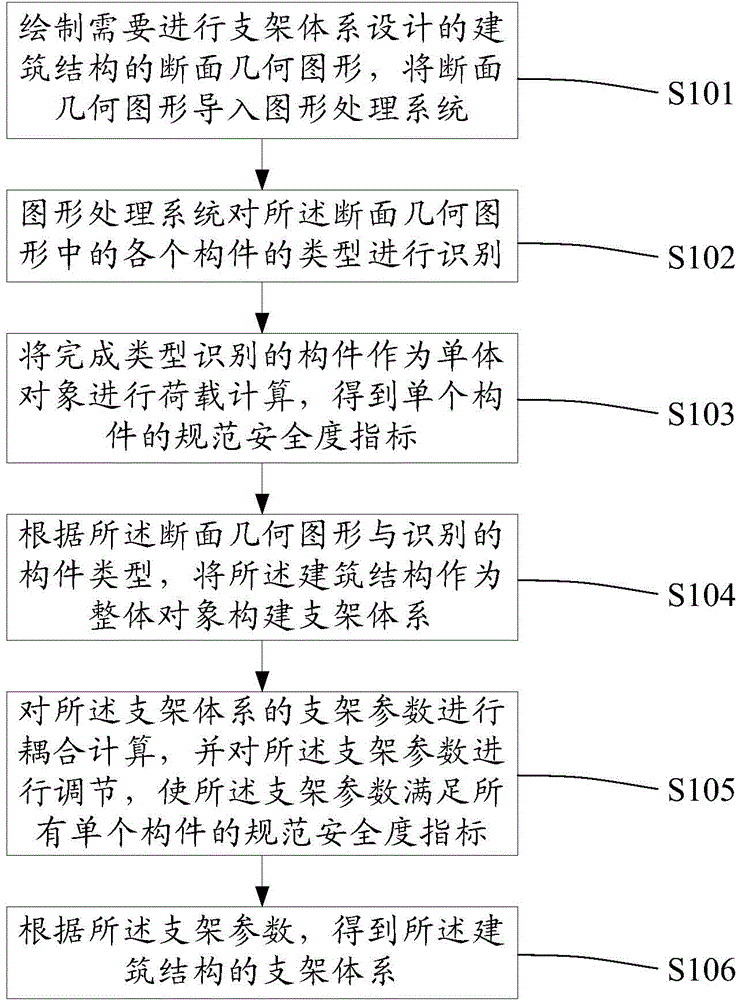
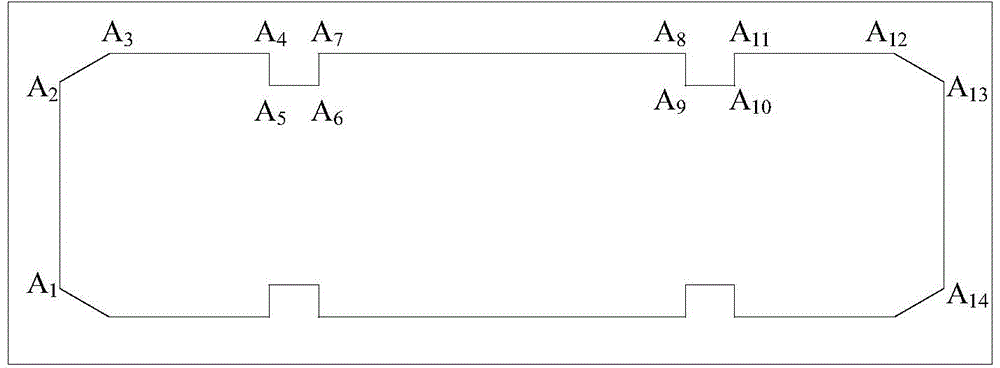
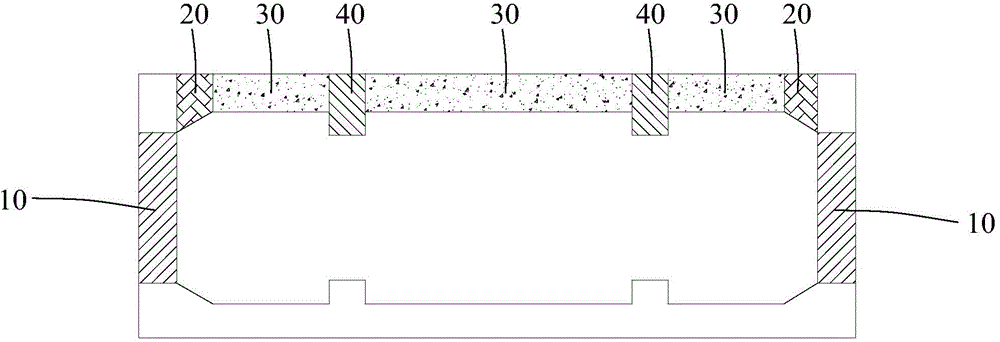
Integrated construction method of support system
ActiveCN104594627AAvoid design blind spotsEnsure construction safetyForms/shuttering/falseworksSpecial data processing applicationsGraphicsSupporting system
The invention provides an integrated construction method of a support system. The method includes the steps that a section geometric figure of a building structure with the support system design requirement is drawn and input to a figure processing system; the types of components in the section geometric figure are identified through the figure processing system; the loads of the components, with the types identified, serving as individual objects are calculated, so that standard safety degree indexes of the single components are acquired; according to the section geometric figure and the identified component types, the building structure serves as a whole object for establishing the support system; support parameters of the support system are coupled and calculated and adjusted, so that the support parameters meet the standard safety degree indexes of all the single components; according to the support parameters, the support system of the building structure is acquired. By the adoption of the method, the building structure serves as a whole for support design, all the components in different positions and different directions in a whole structure section are comprehensively considered, and therefore the support system can bear the load effect of the different components in different directions.
Owner:SHANGHAI TUNNEL ENG CO LTD +1
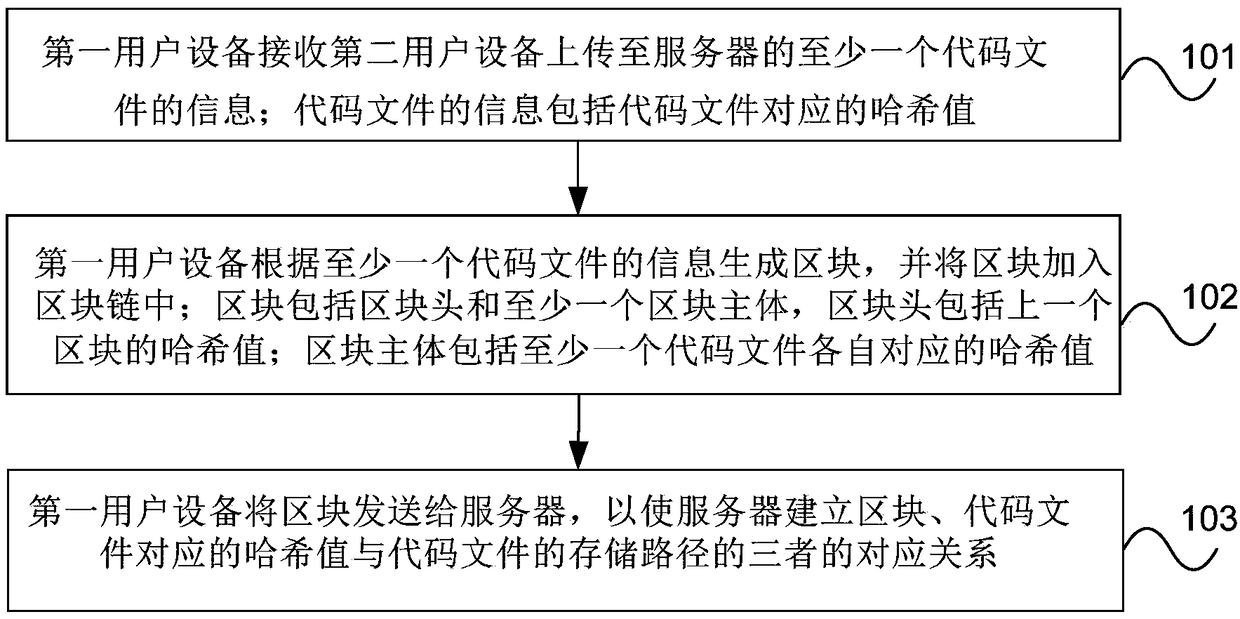
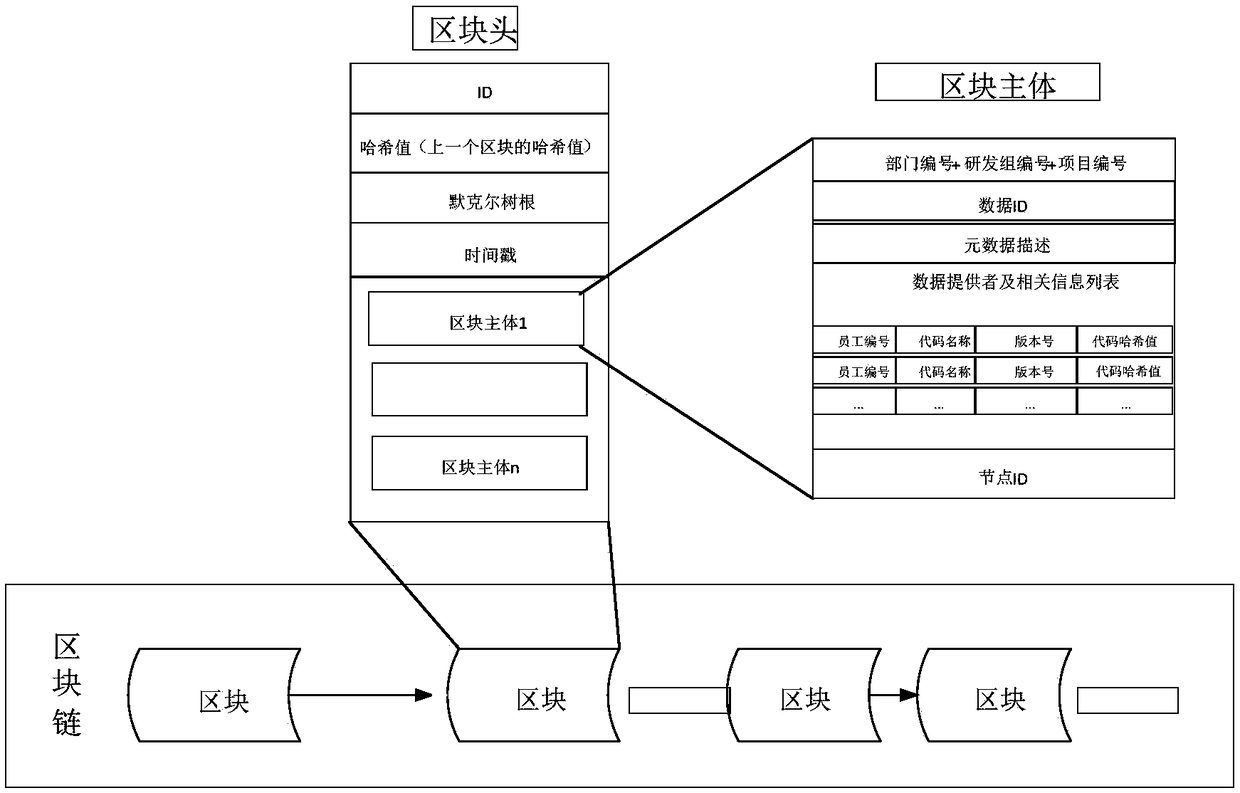
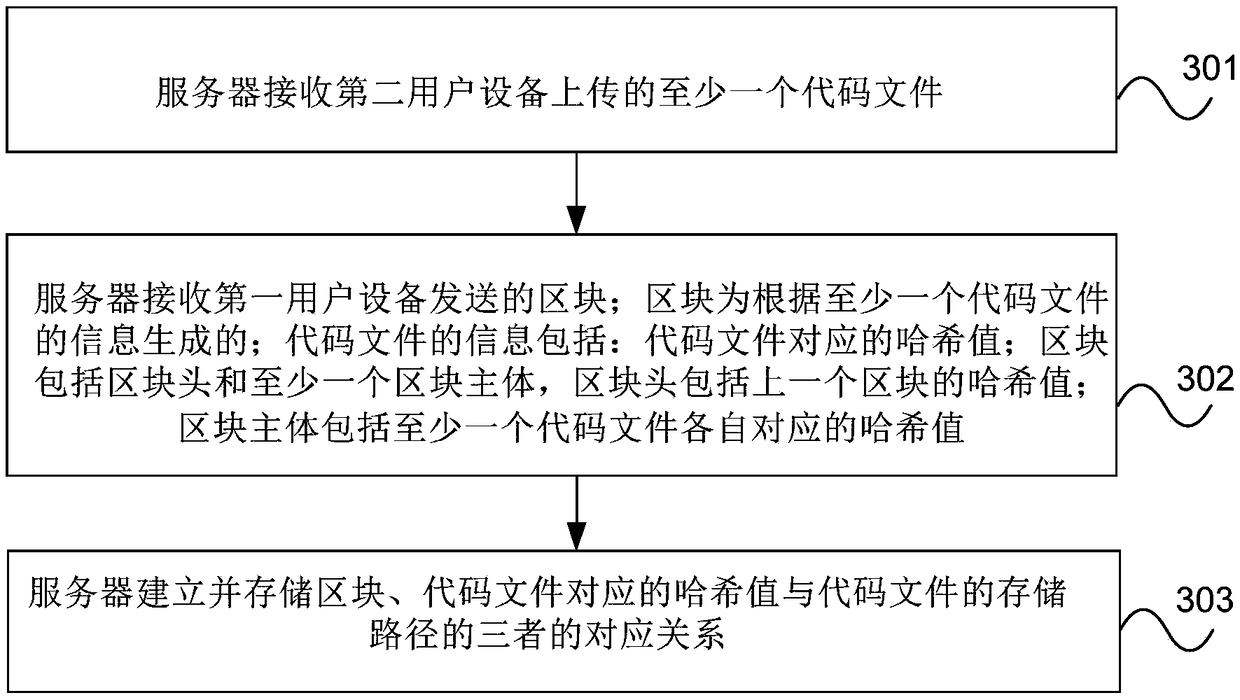
Code management method and device
ActiveCN108880820AVerify authenticityVerify securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationUser equipmentInformation storage
The invention provides a code management method and device. The method comprises the steps that first user equipment receives information of at least one code file which is uploaded to a server by second user equipment, wherein the information of the code files comprises hash values corresponding to the code files; the first user equipment generates a block according to the information of the at least one code file and adds the block to a block chain, wherein the block comprises a block head and at least one block body, the block head comprises the hash value of the last block, and the block body comprises the hash values corresponding to the at least one code file; and the first user equipment sends the block to the server, so the server establishes a corresponding relationship among theblock, the hash values corresponding to the code files and storage paths of the code files. According to the embodiment of the invention, the code files are stored to the server and the information ofthe code files is stored to the block chain, so the information of the code files is prevented from being tampered, and security of the code files is ensured.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Condom with antisepsis and anti-inflammation functions and preparation method thereof
ActiveCN105963807AEnhanced barrier functionImprove skin penetrationOrganic active ingredientsAntimycoticsDiseaseSophocarpidine
The invention belongs to the field of medical instruments, and particularly relates to a condom with antisepsis and anti-inflammation functions. A lubricant of the condom contains sophocarpidine, and the condom is subjected to plasma treatment before being coated with the lubricant. Under the condition of not changing the original production, detection and package technological process, sophocarpidine is applied to the lubricant of the condom, and therefore, the condom can be used for prevention and auxiliary treatment of such gynecological diseases as cervical erosion, leukorrhea with reddish discharge, trichomonas vaginitis and vaginal fungal infection.
Owner:ZHEJIANG XIANGBAN LATEX PROD
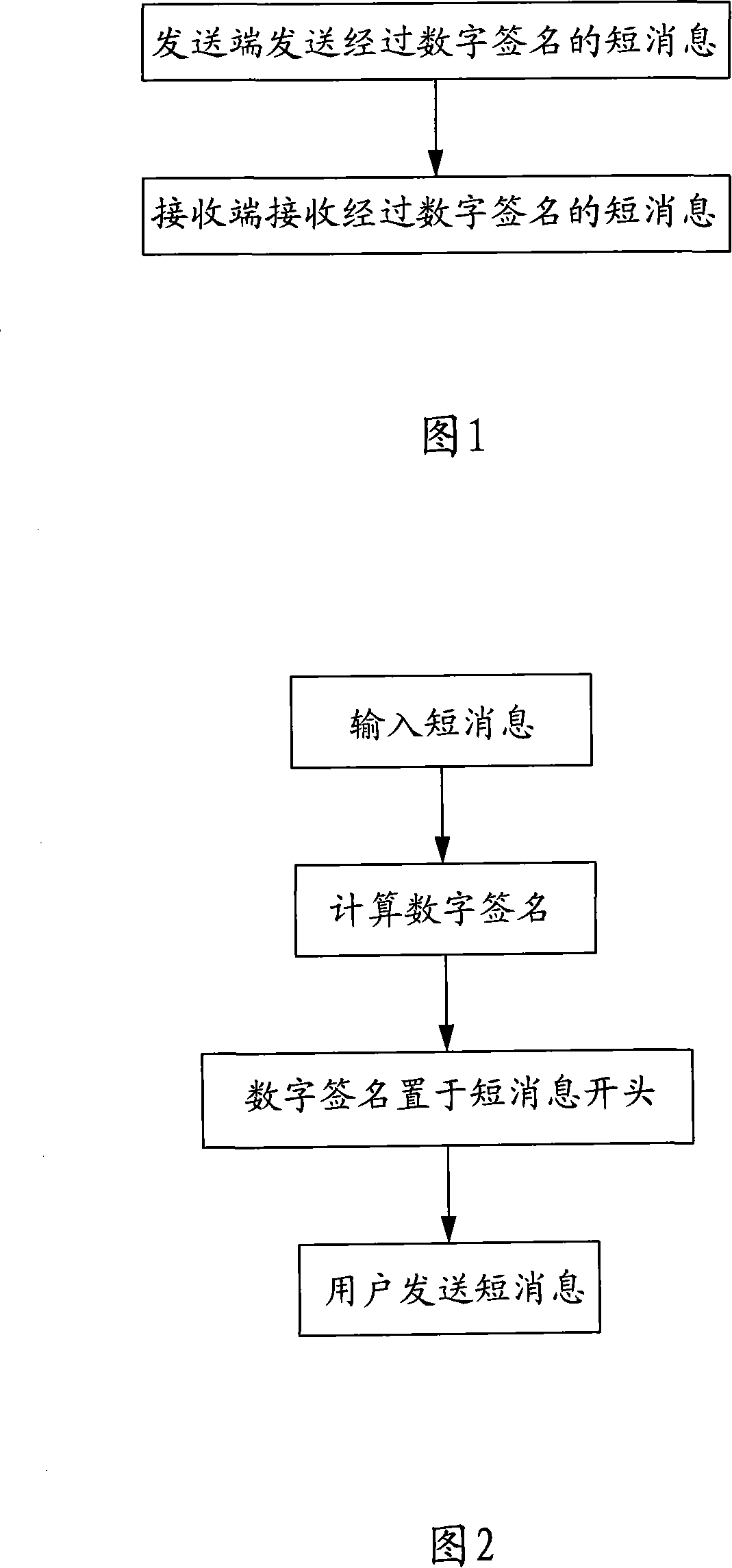
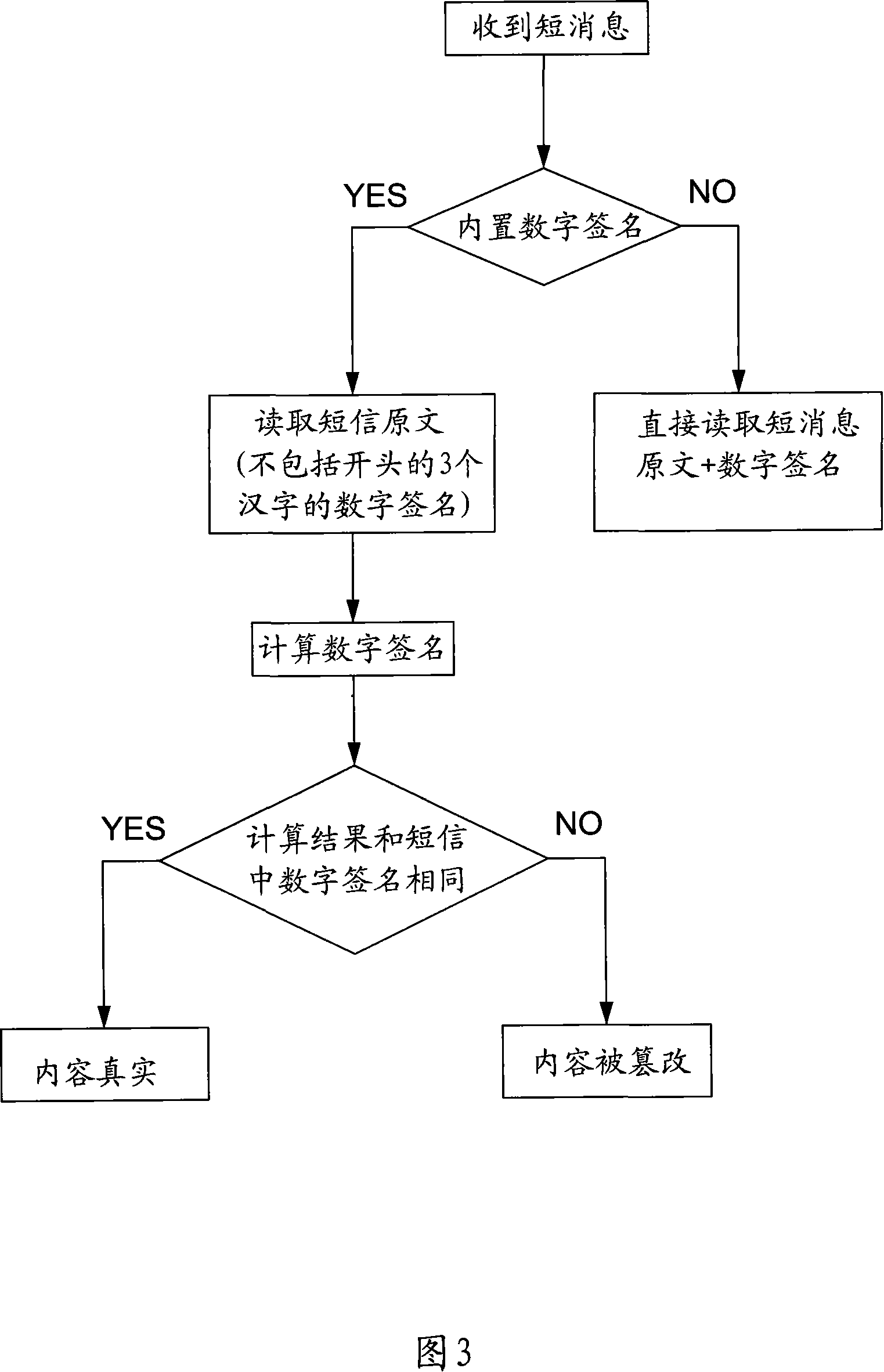
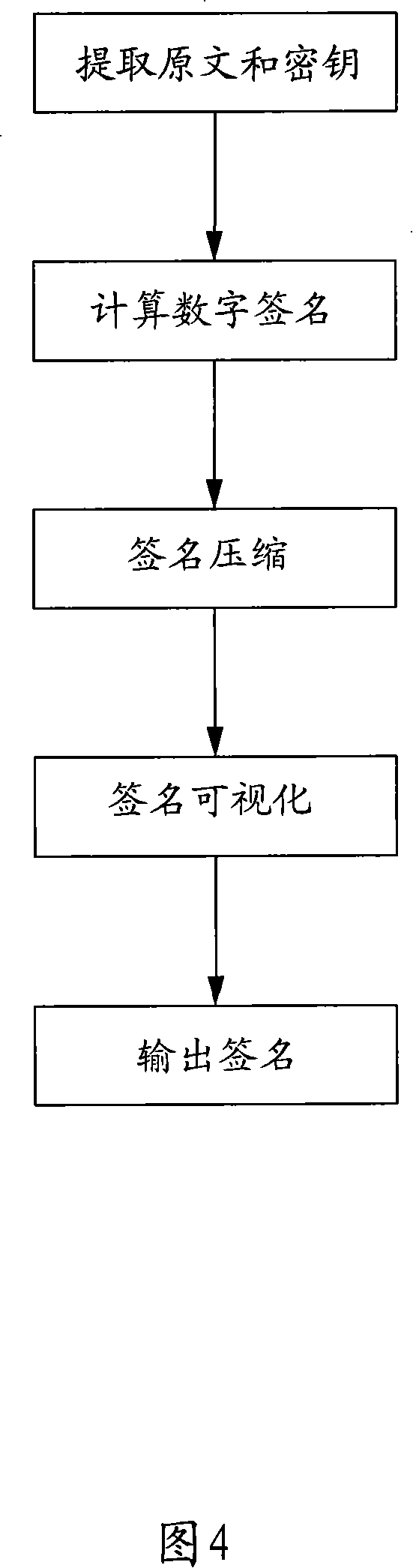
Short message content interpolation-preventing method
InactiveCN101072377AImprove securityVerify securityRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsDigital signatureSecret code
The method includes following steps: (1) when sending short message, the sending end sends short message with digital signature; (2) after receiving short message with digital signature, the receiving end checks correctness of the digital signature. Length of short message inputted is not limited. Using form of algorithm + secret key, the method possesses high security. Through secret key, the method guarantees security of signature even if algorithm is leaked. Features are: wide acceptable secret keys usable to the algorithm, convenience for remembrance, easy for maintaining secret key, high operating rate, and low requirement on hardware of terminal. The invention is suitable to embedded type terminal such as handset.
Owner:FUJIAN XINO COMM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com