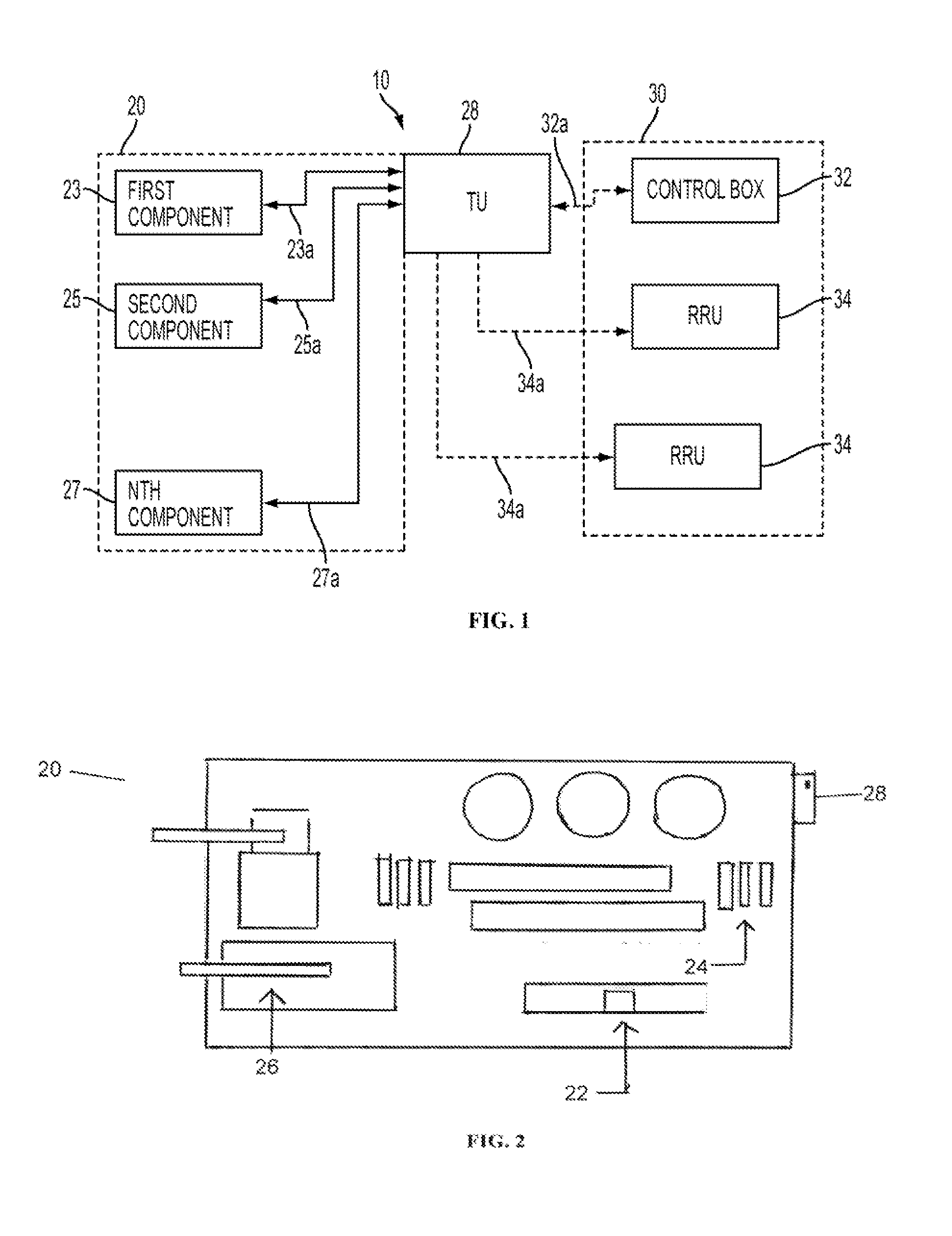
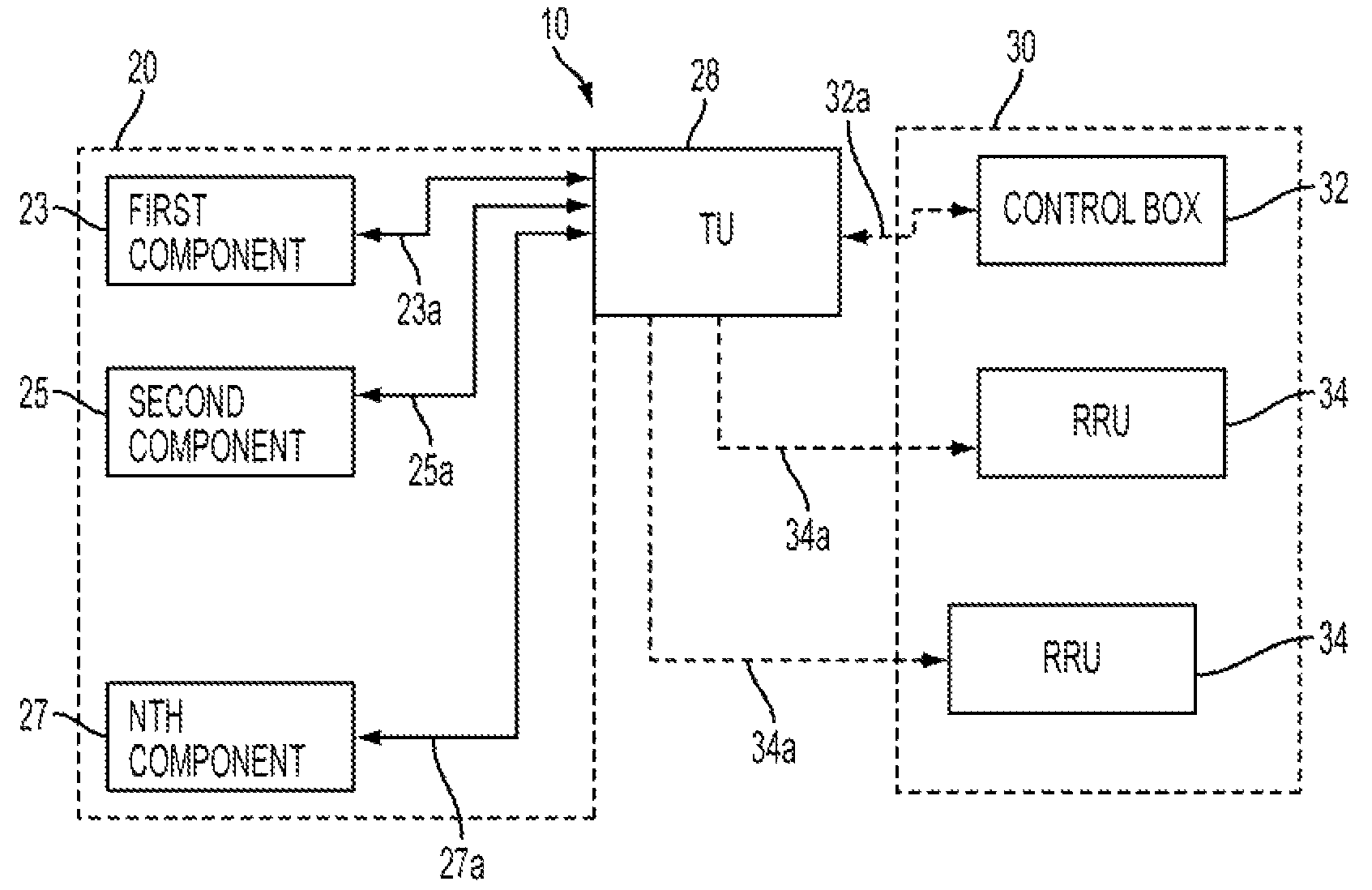
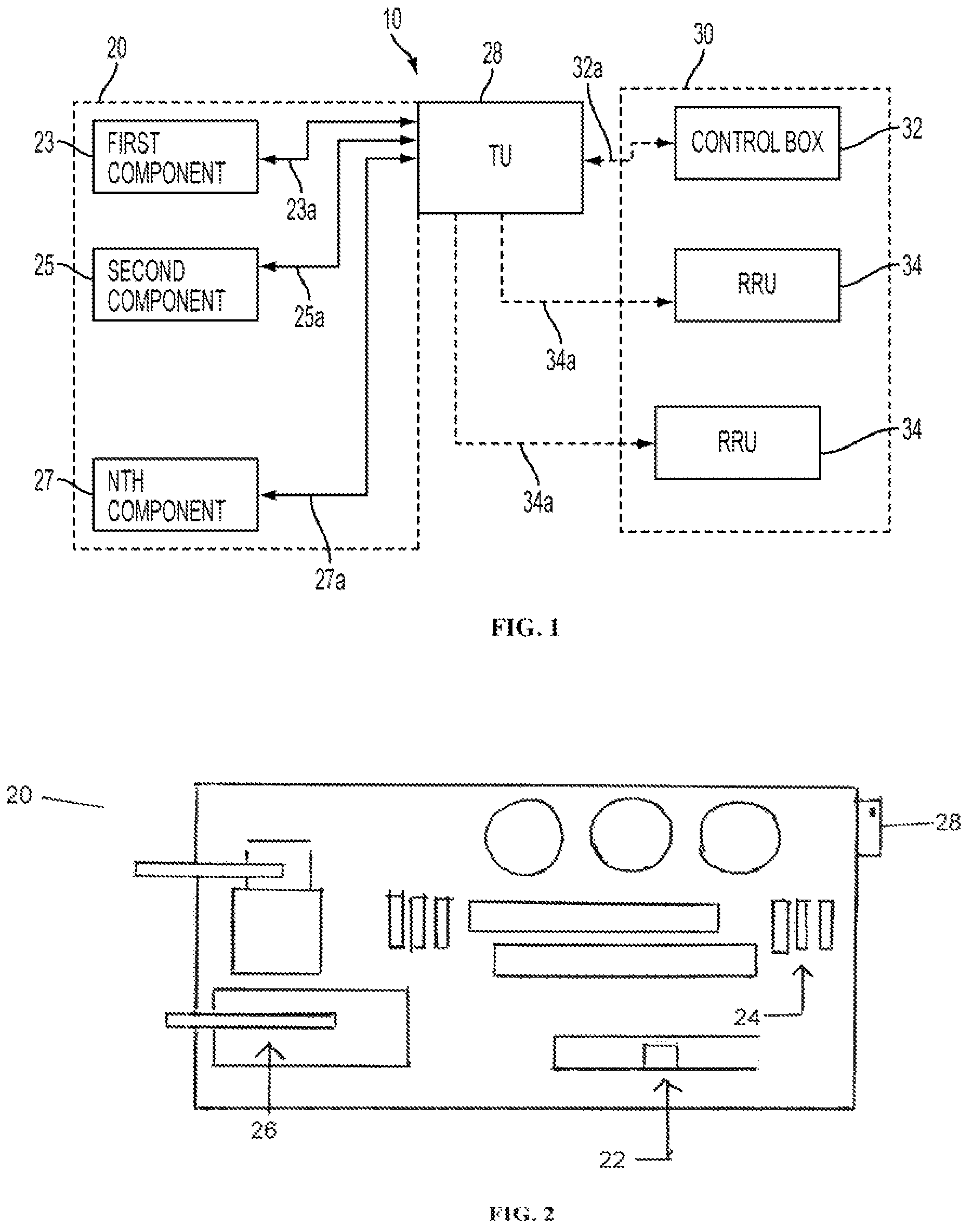
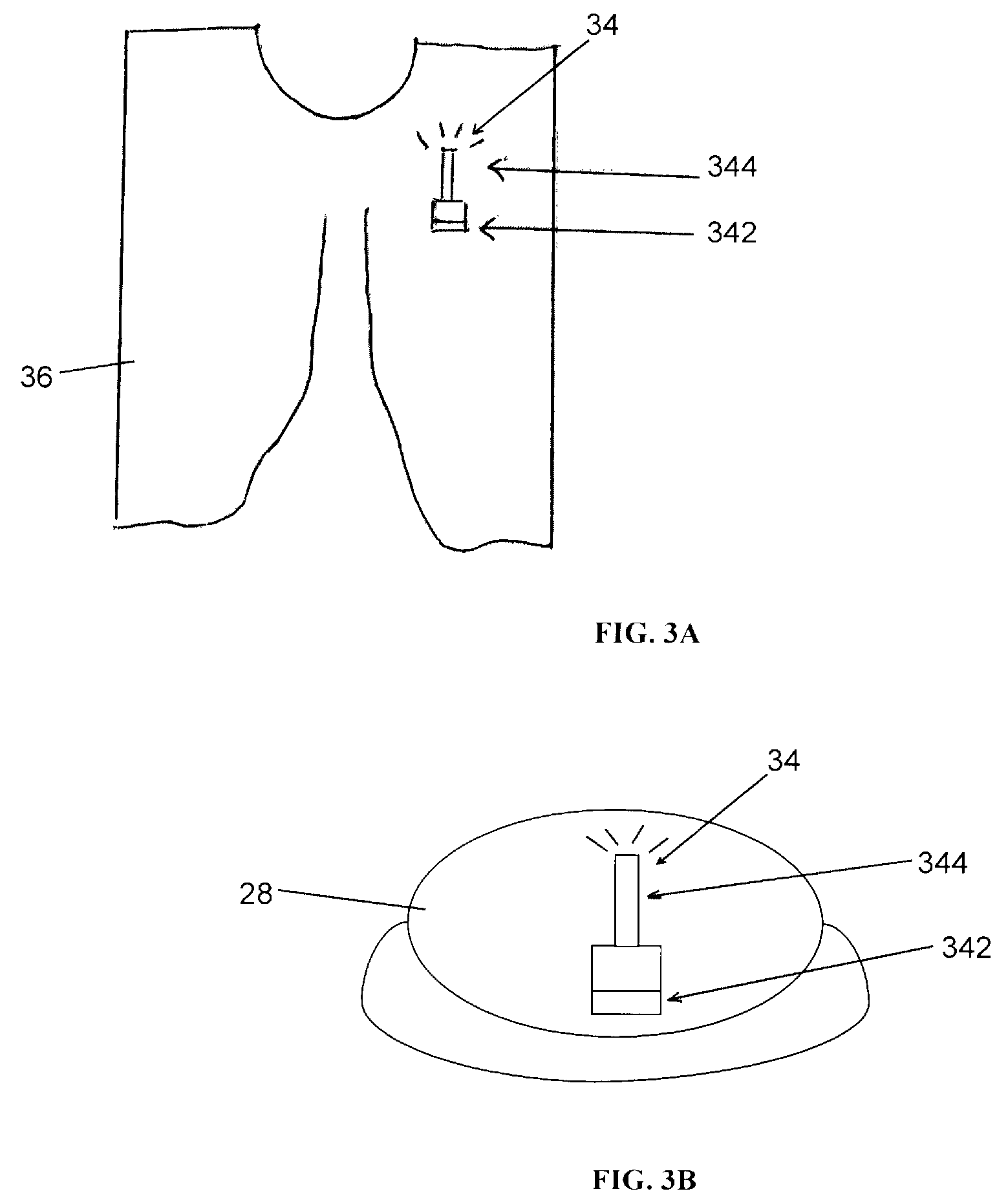
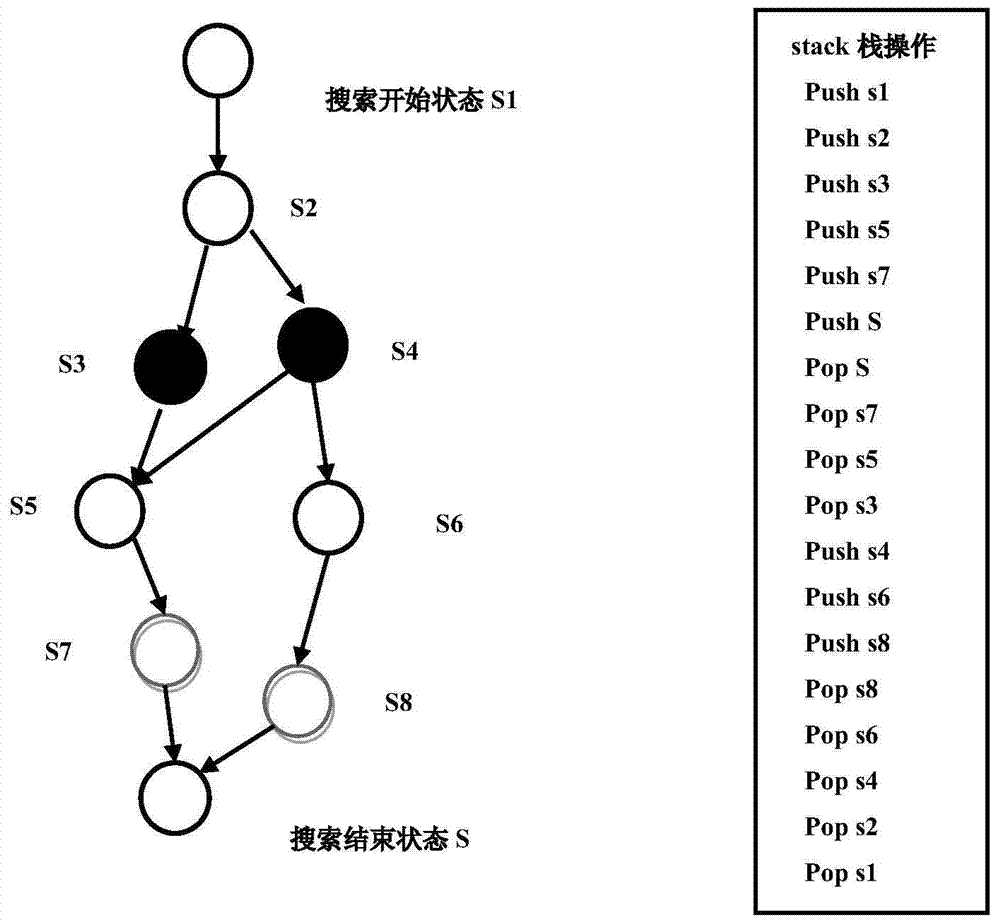
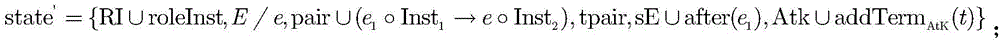Patents
Literature
75 results about "Protocol verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Verification Protocols. Verification protocols promoted uniform controlled testing for a class or category of technologies. They may have retained draft status until the testing was performed and were then finalized by building on the testing experience. In some cases, documentation of a robust test protocol allowed for the development...
Method and apparatus for authenticating a user using three party question protocol
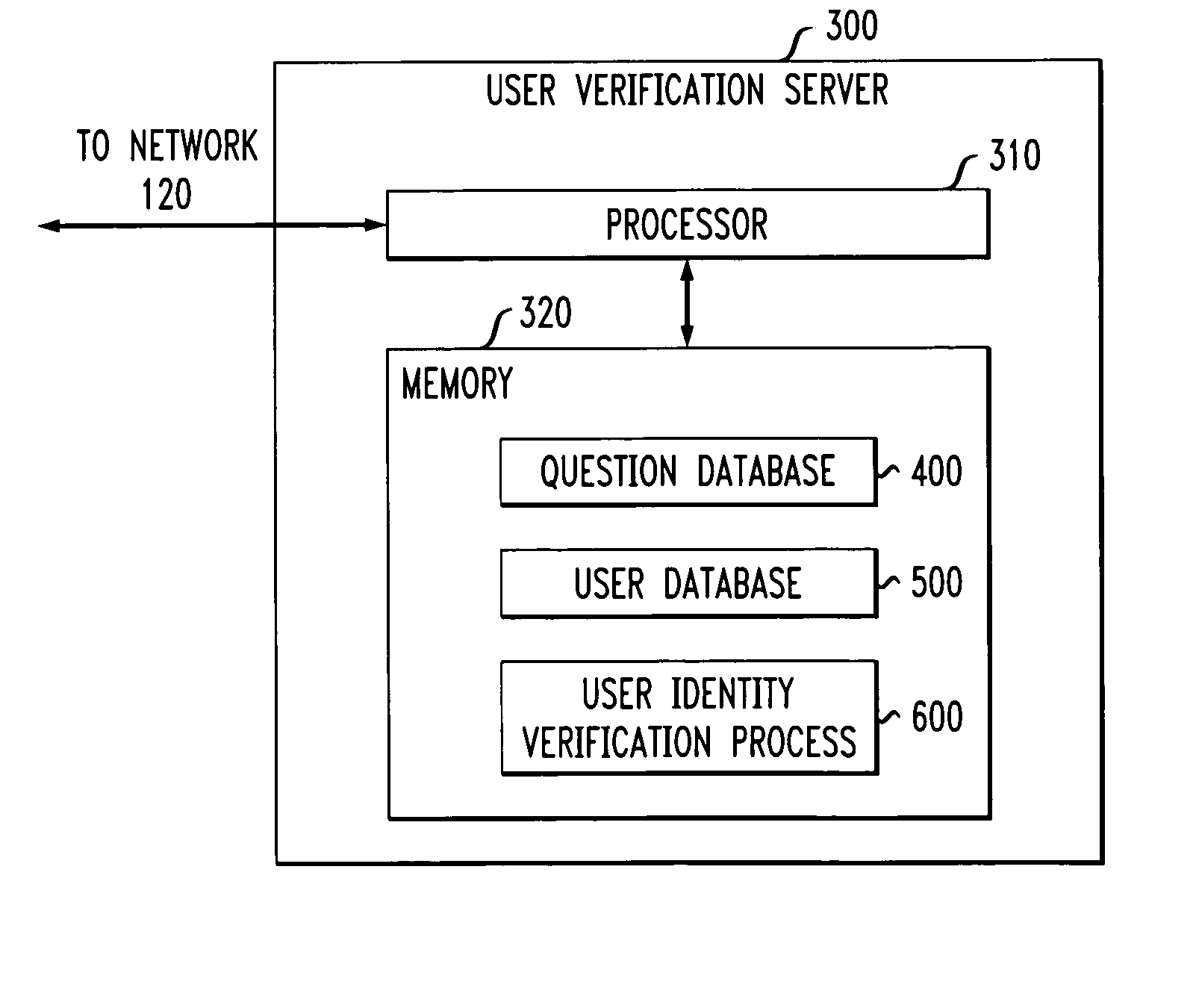
InactiveUS20050039056A1Digital data processing detailsSpecial service for subscribersUser verificationHuman agent
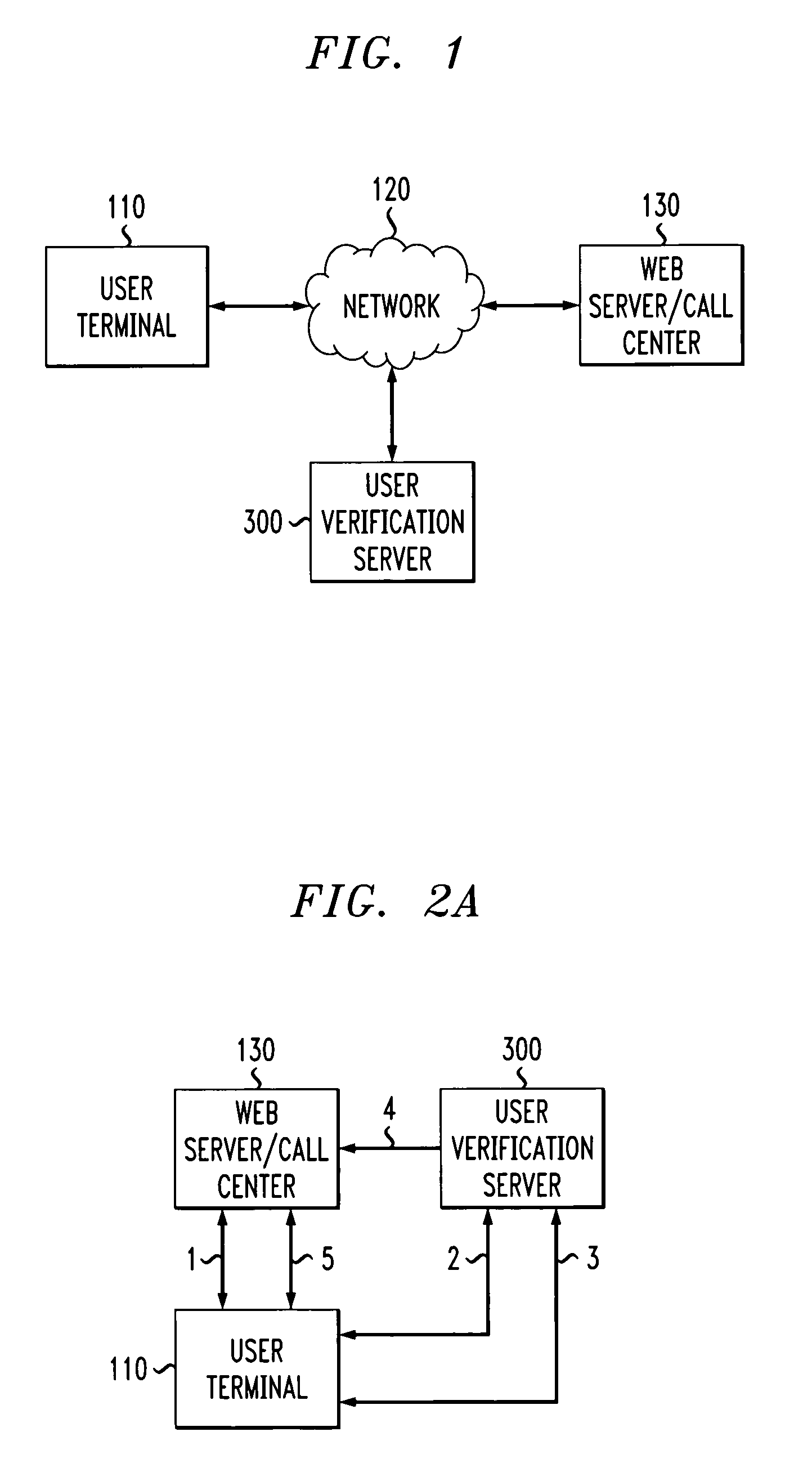
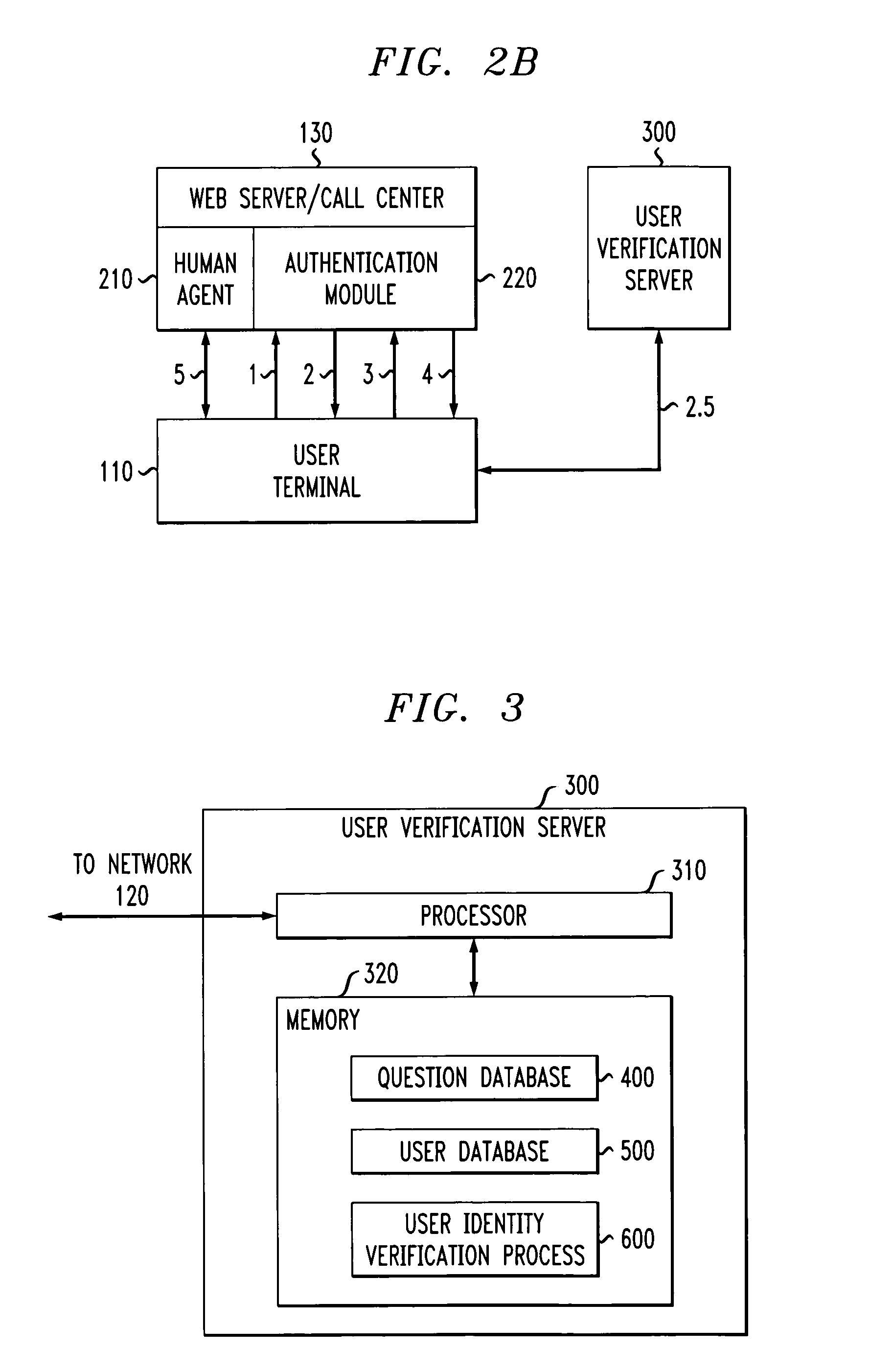
A three party authenticating protocol is disclosed. During an enrollment phase, a user contacts a call center and is directed to a user verification server. The user verification server instructs the user to select and answer a number of questions that will be used for verification. The selected questions along with identifying indices for each question are stored at the user's location and at the user verification server. The user verification server sends the question indices to the call center, which in turn sends these indices to the user to obtain answer indices for each question. During a verification phase, the user contacts the call center and an authentication module asks the user to provide an asserted identity. The authentication module provides a random selection of question indices from those selected by the user. The user provides answer indices for each question to the authentication module. If the number of correctly matching answers exceeds a threshold, then the user is verified. Otherwise, the user fails verification. After verification, the user is transferred from the authentication module of the call center to a human agent for further processing.
Owner:AVAYA INC
Automatic protocol recognition method and system
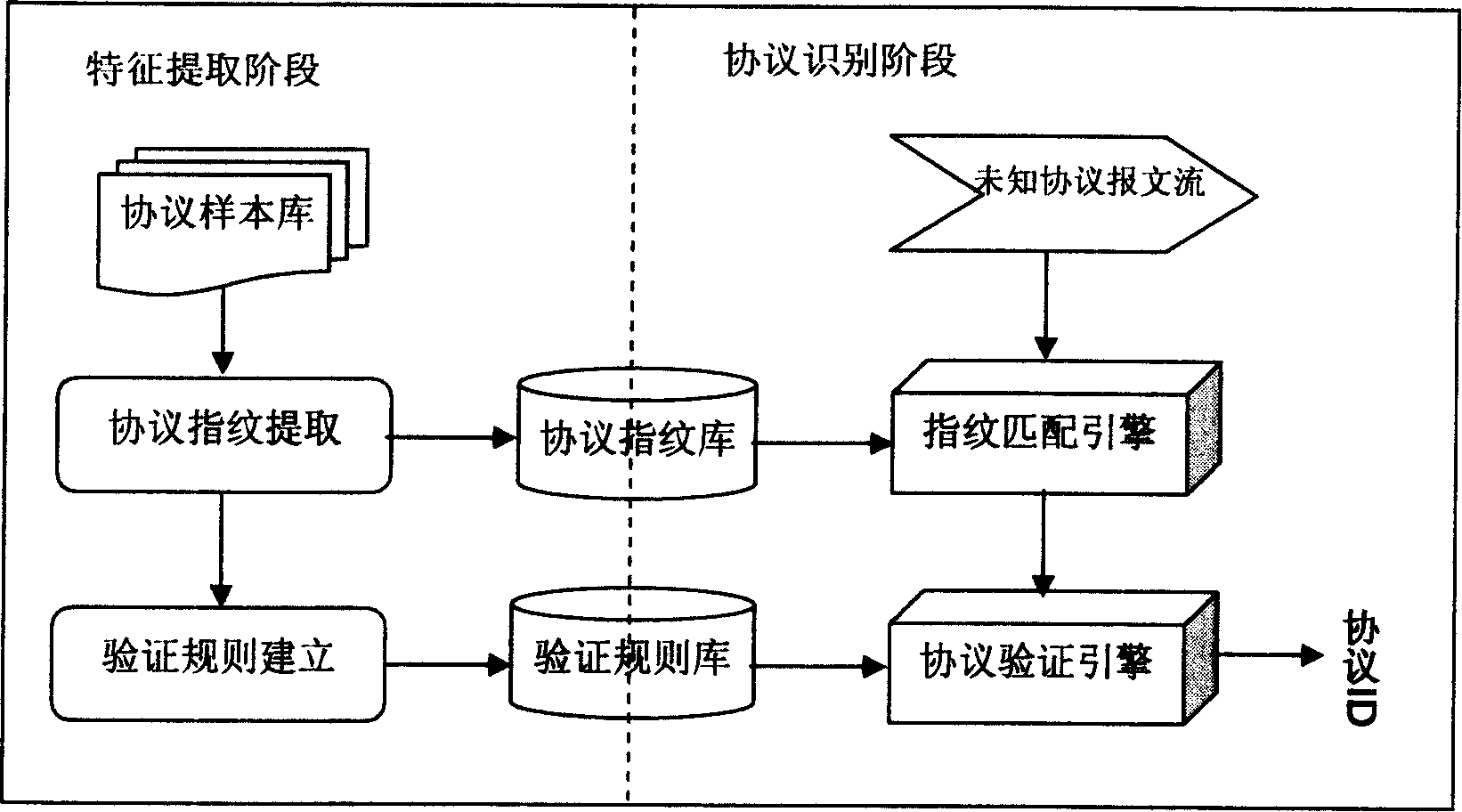
InactiveCN1845066ASolve the self-identification problemFast recognitionUser identity/authority verificationHardware monitoringFeature extractionNetworking protocol
The invention discloses an automatic protocol identification method and system used in inbreak defense detect (IDS / IPS) product. Wherein, it can automatically identify the protocol type according to the initial report character in the initial period of network protocol communication, and use protocol check rule to check the protocol identified result. Said method comprises two steps as initial protocol sample character extraction and on-line protocol identification, while the first step comprises: the protocol fingerprint extraction of protocol type sample and building relative protocol check rule; the second step comprises: protocol fingerprint quick matching and protocol identification result quick check. The inventive protocol identification system comprises protocol sample character base, protocol fingerprint match engine and protocol check engine, while the protocol fingerprint match engine is based on quick Haxi list method, and the protocol check engine is based on high-efficiency virtual mode.
Owner:BEIJING VENUS INFORMATION TECH +1
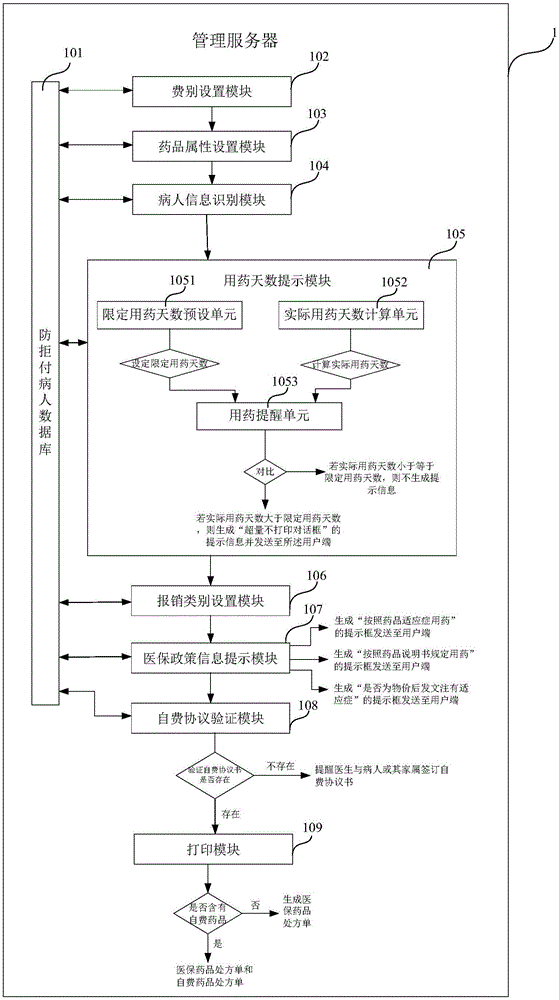
Hospital medical insurance expense nonpayment prevention auxiliary management information system and nonpayment prevention method
InactiveCN106530166AEasy to manageFacilitate communicationData processing applicationsPatient databaseEconomic benefits
The invention provides a hospital medical insurance expense nonpayment prevention auxiliary management information system, which comprises a management server and a user end, wherein the management server comprises a nonpayment prevention patient database, and an expense nature setting module, a drug attribute setting module, a patient information recognition module, a drug usage day prompt module, a reimbursement category setting module, a medical insurance policy information prompt module, a self-paying protocol verification module and a printing module communicating with the nonpayment prevention patient database. The drug usage days of the patient can be counted, a doctor is prompted when the drug usage days exceed, indication judgment can be carried out on drugs prescribed by the doctor, the drug usage indication is prompted to the doctor, the doctor can thus inform the patient or a family member, happening of the expense nonpayment possibility can be prevented from the source, convenience is provided for the doctor, medical disputes can be avoided, management by the hospital is facilitated, and obvious economic benefits are brought to the hospital.
Owner:FIRST HOSPITAL AFFILIATED TO GENERAL HOSPITAL OF PLA
Controlled exception-based routing protocol validation
InactiveUS7342892B2Improve reliabilityError preventionTransmission systemsMessage sizeAdverse conditions
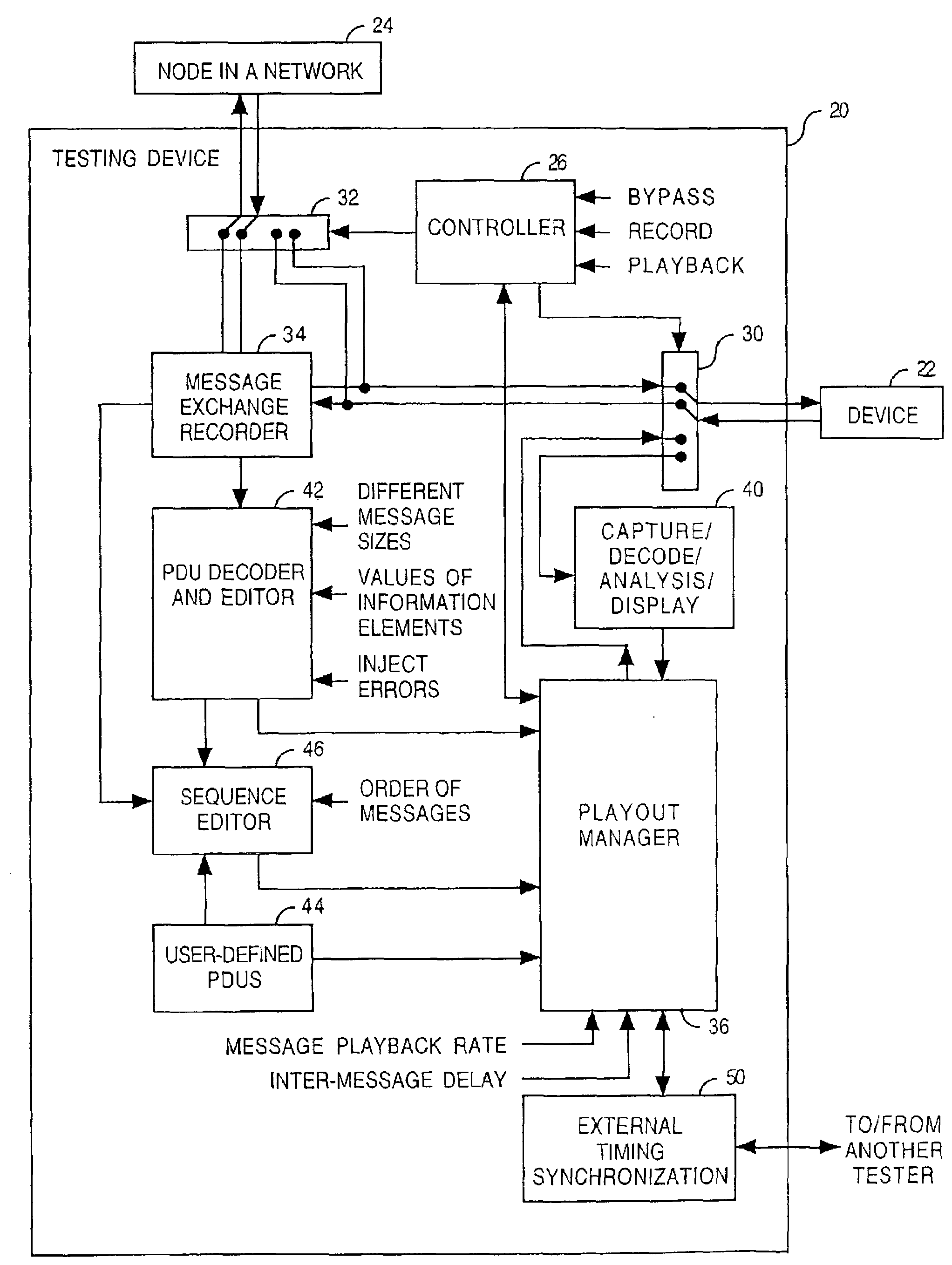
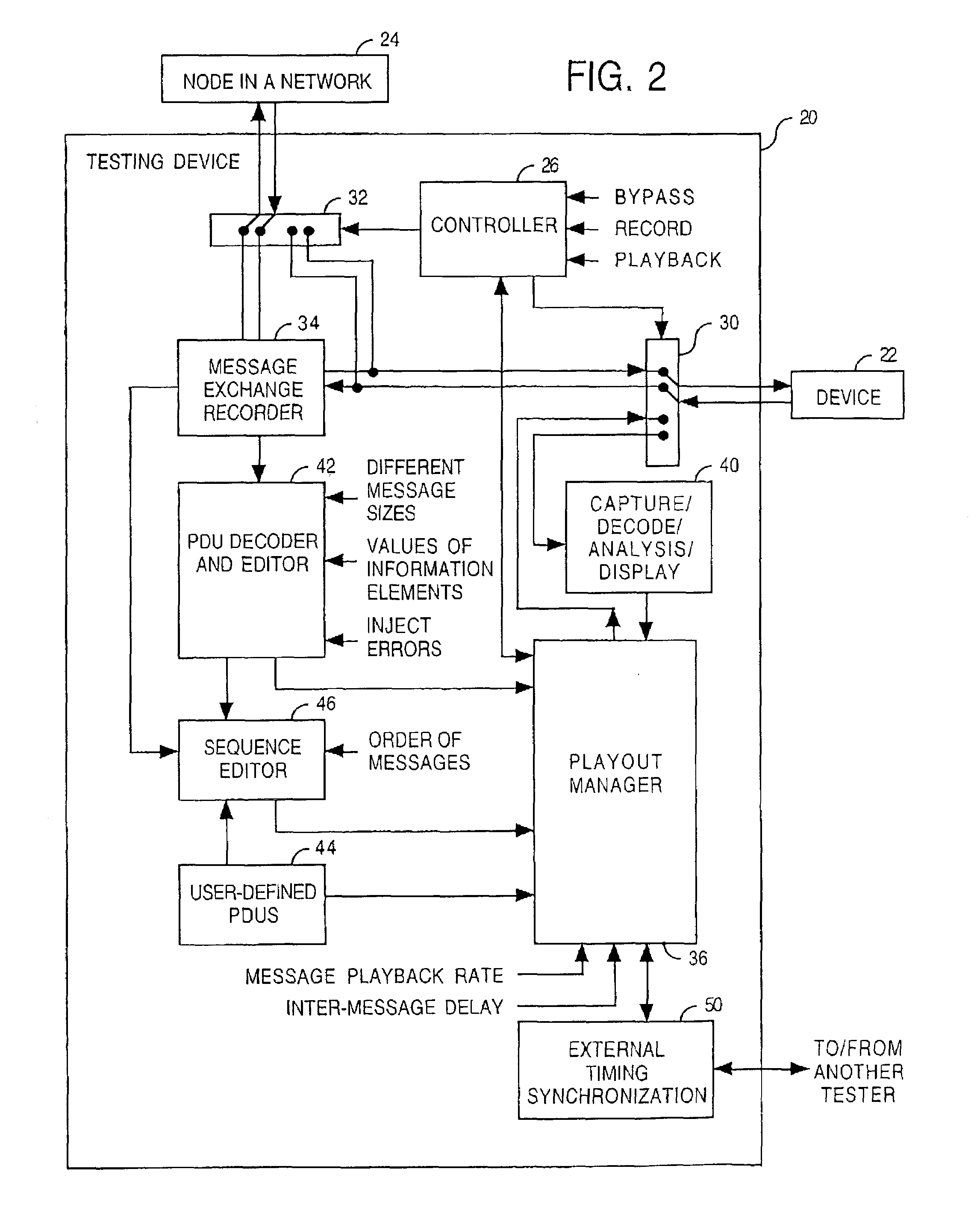
An implementation of a routing protocol in a device is tested by testing how the device reacts to messages and message sequences having potentially adverse conditions. Examples include messages either having a specified message size which is intentionally out-of-conformance with the routing protocol, having a repeated protocol field, absent a mandatory protocol field, or having an incorrect order of protocol fields. Examples also include message sequences having either a specific playback delay between at least one pair of adjacent protocol messages in the first sequence of protocol messages, a specific playback rate for the second sequence of protocol messages, or a modified message order.
Owner:AT&T INTPROP I L P
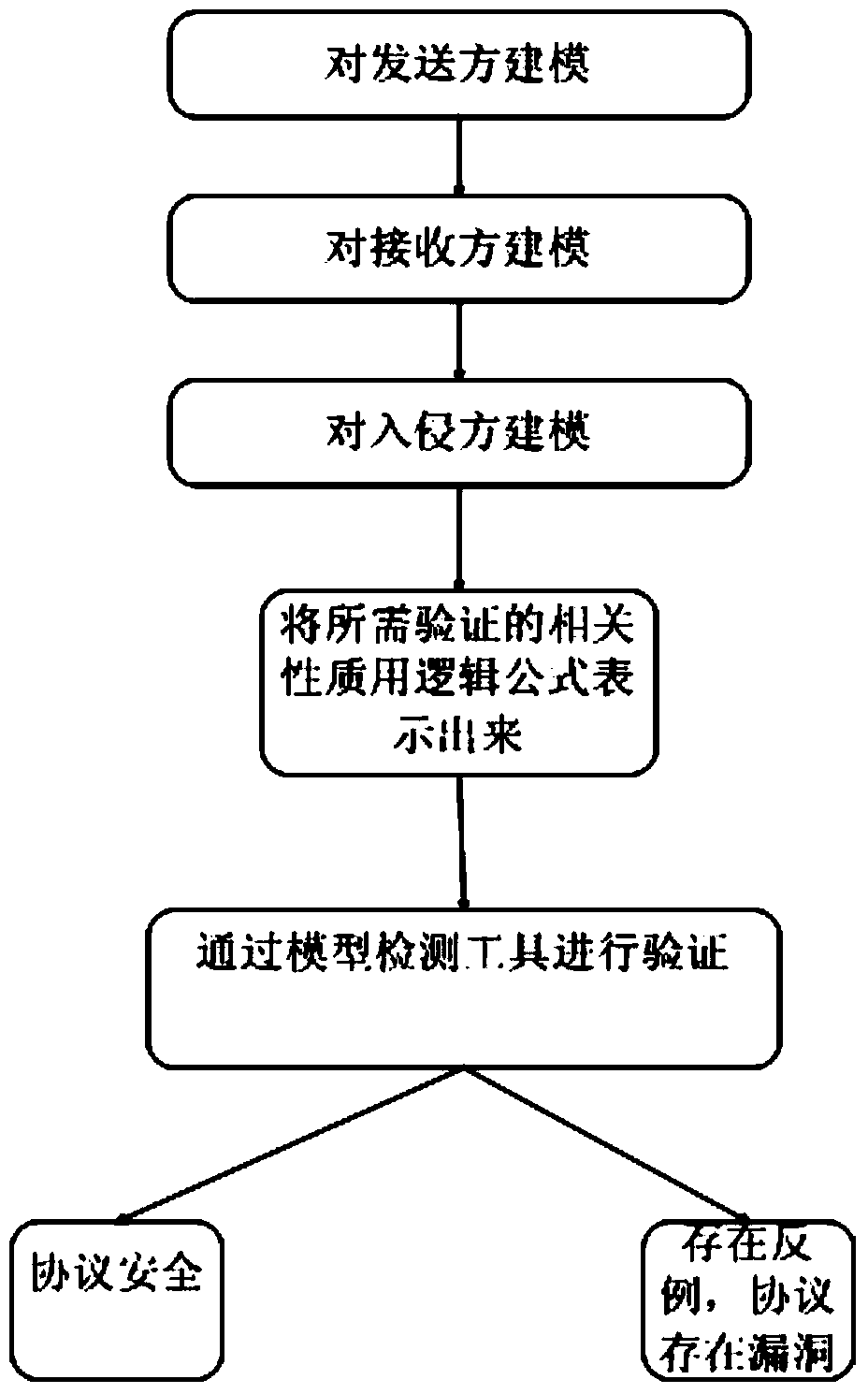
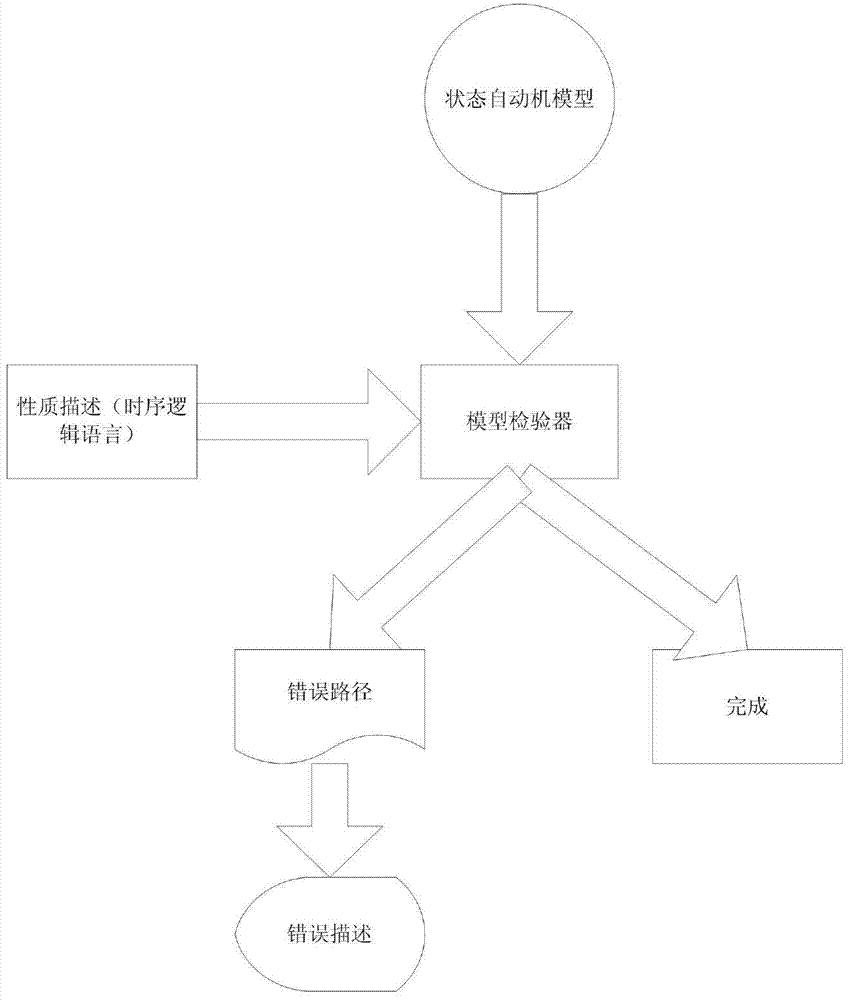
Safety protocol formal verification method based on model detection
InactiveCN109150833AReduce complexitySmall scaleData switching networksLogic modelingCryptographic protocol
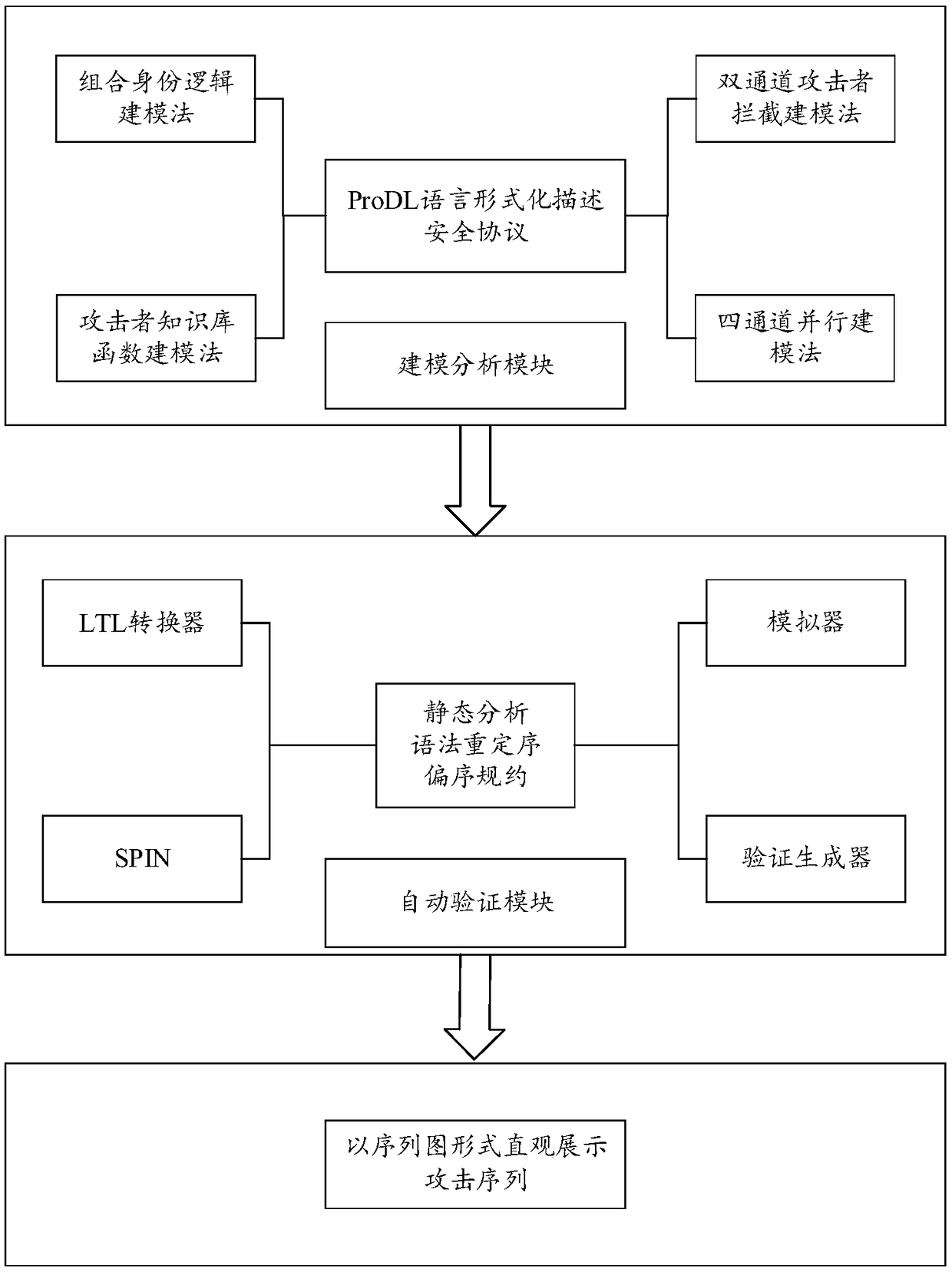
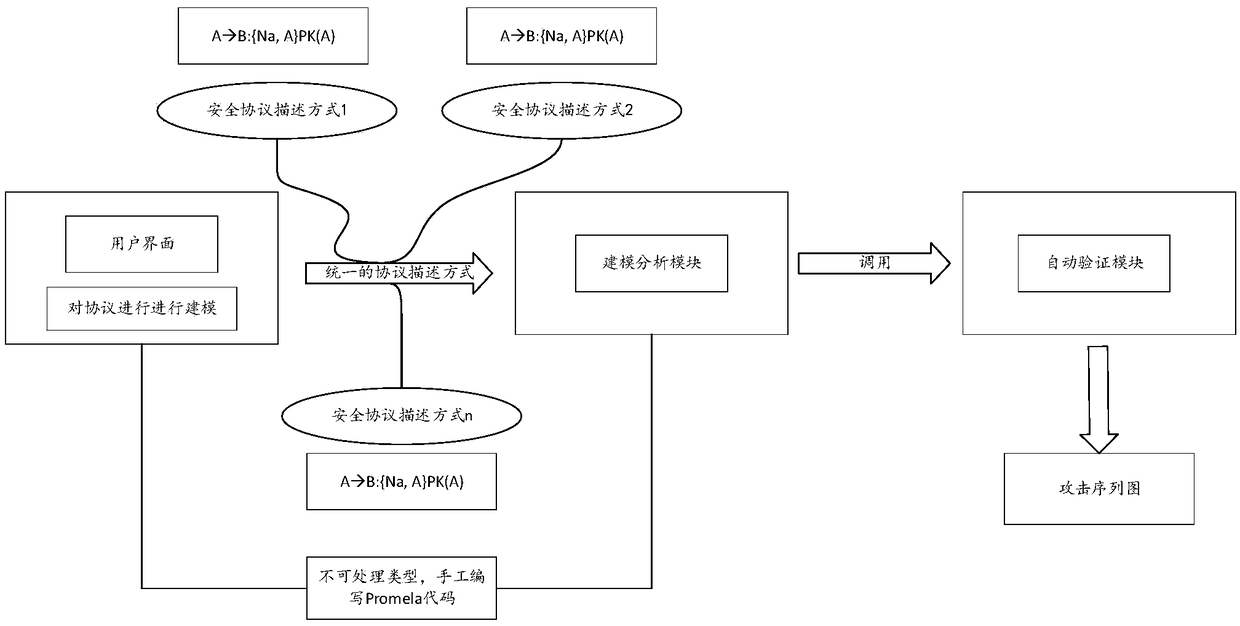
The invention provides a safety protocol formal verification method based on model detection. In the method, an intruder model based on algorithmic knowledge logic is taken as a theoretical basis, SPIN / Promela is used to model and analyze a large number of network safety protocols, and a model detection technology is used to design and realize a network safety protocol verification model generation system. In the system, for the different types of protocols, a corresponding modeling method is provided, such as a combined identity logic modeling method, a two-channel attacker interception modeling method, an attacker knowledge base function modeling method and a four-channel parallel modeling method; the method is used for the Promela modeling of the safety protocol; and the analysis requirements of several different types of safety protocols are effectively satisfied, and for the size of an attacker knowledge base in the safety protocol, a program enumeration method is used to construct. The three optimization strategies of static analysis, syntax reordering and partial order reduction are arranged in the system so that a state explosion problem in a safety protocol model detectionprocess can be effectively alleviated.
Owner:EAST CHINA JIAOTONG UNIVERSITY
Verification method of FPGA universal configurable UART protocol based on UVM
InactiveCN105718344AImprove verification efficiencyDetecting faulty computer hardwareComputer architectureValidation methods
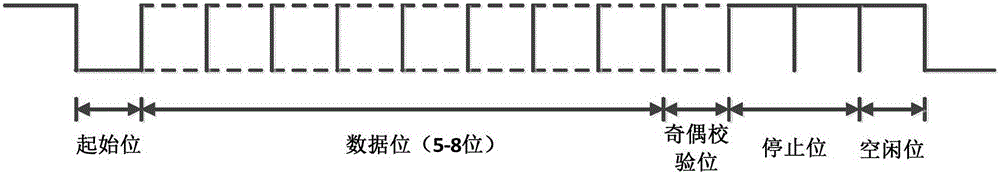
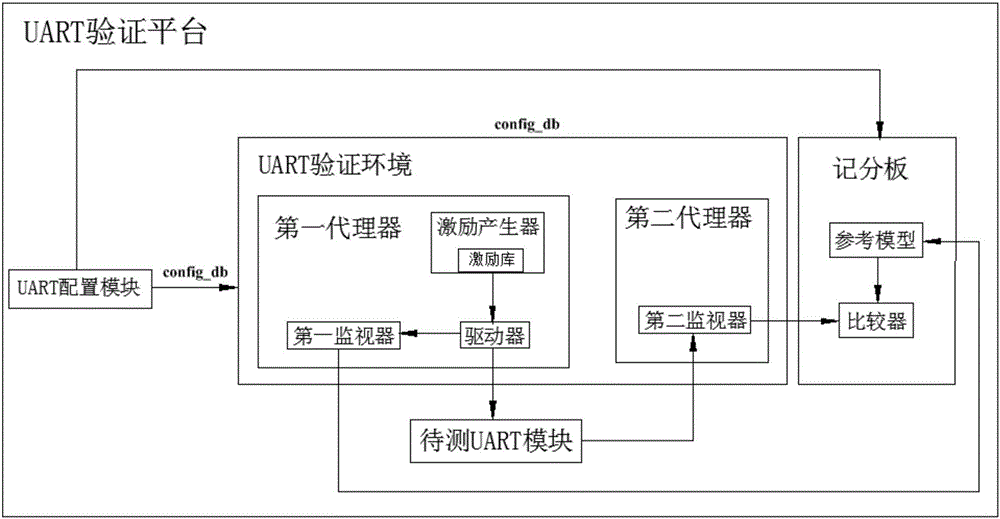
The invention relates to a verification method of an FPGA universal configurable UART protocol based on UVM. The verification method comprises the steps of finishing an overall framework of UART protocol verification by utilizing a UVM verification platform structure and a verification idea; and setting a UART configuration type in which all the parameter information of the UART protocol is packaged, and sending the UART protocol parameter information to related parts of platforms such as a driver, a monitor and a grade recording board through a config-db mechanism provided by the UVM. During instantiation of a top layer, a universal parameter-configurable UART protocol FPGA verification platform can be realized only by setting corresponding parameter information such as a Baud rate, a data bit, a stop bit and a verification mode based on protocol requirements of a to-be-tested UART by the user. The verification method of the FPGA universal configurable UART protocol based on the UVM has the advantages of being efficient and universal. A test case meeting requirements can be generated automatically only by setting corresponding UART parameters at the top layer by an FPGA design engineer or verification engineer, and a verification environment is unnecessary to develop again, so that the verification efficiency is improved greatly.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 38 RES INST
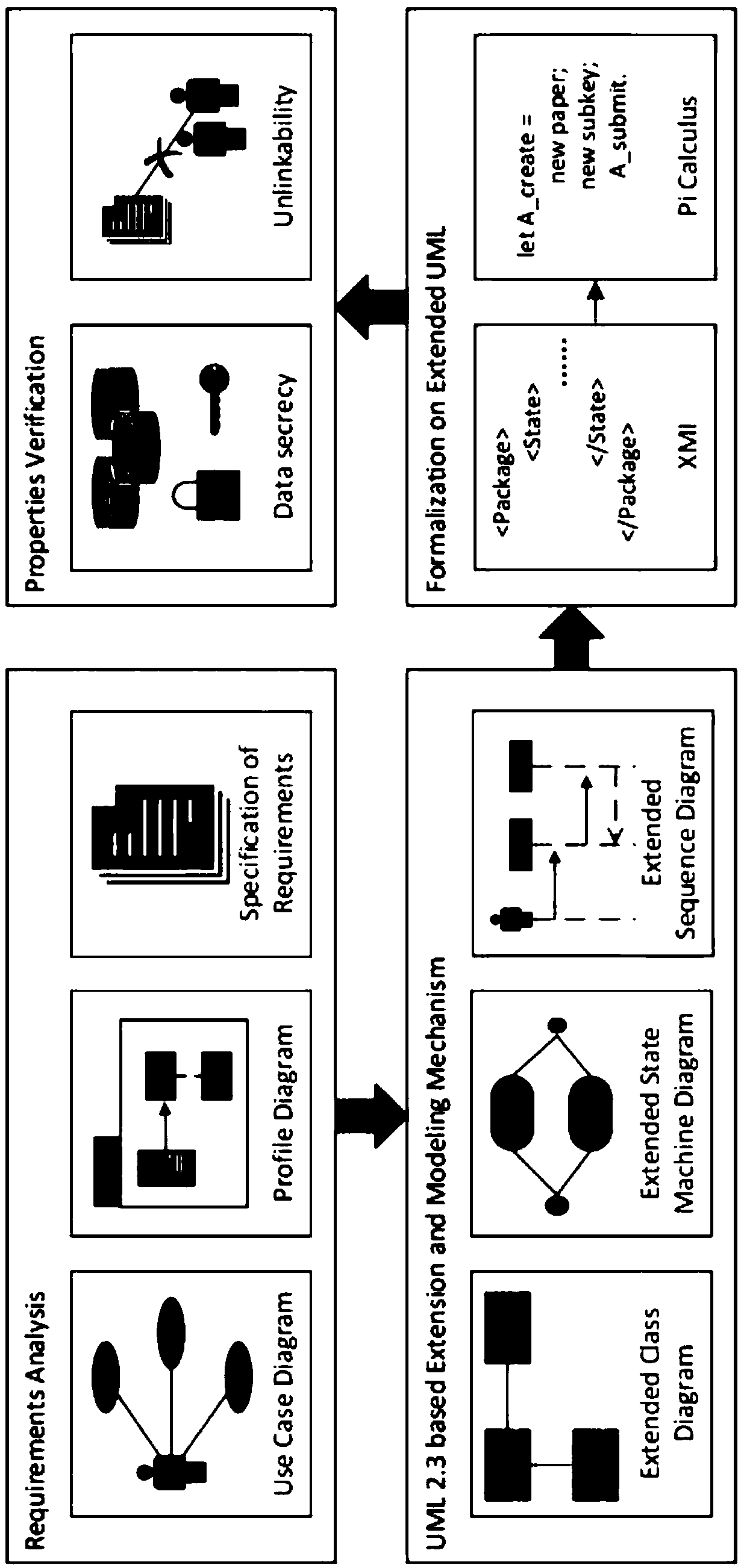
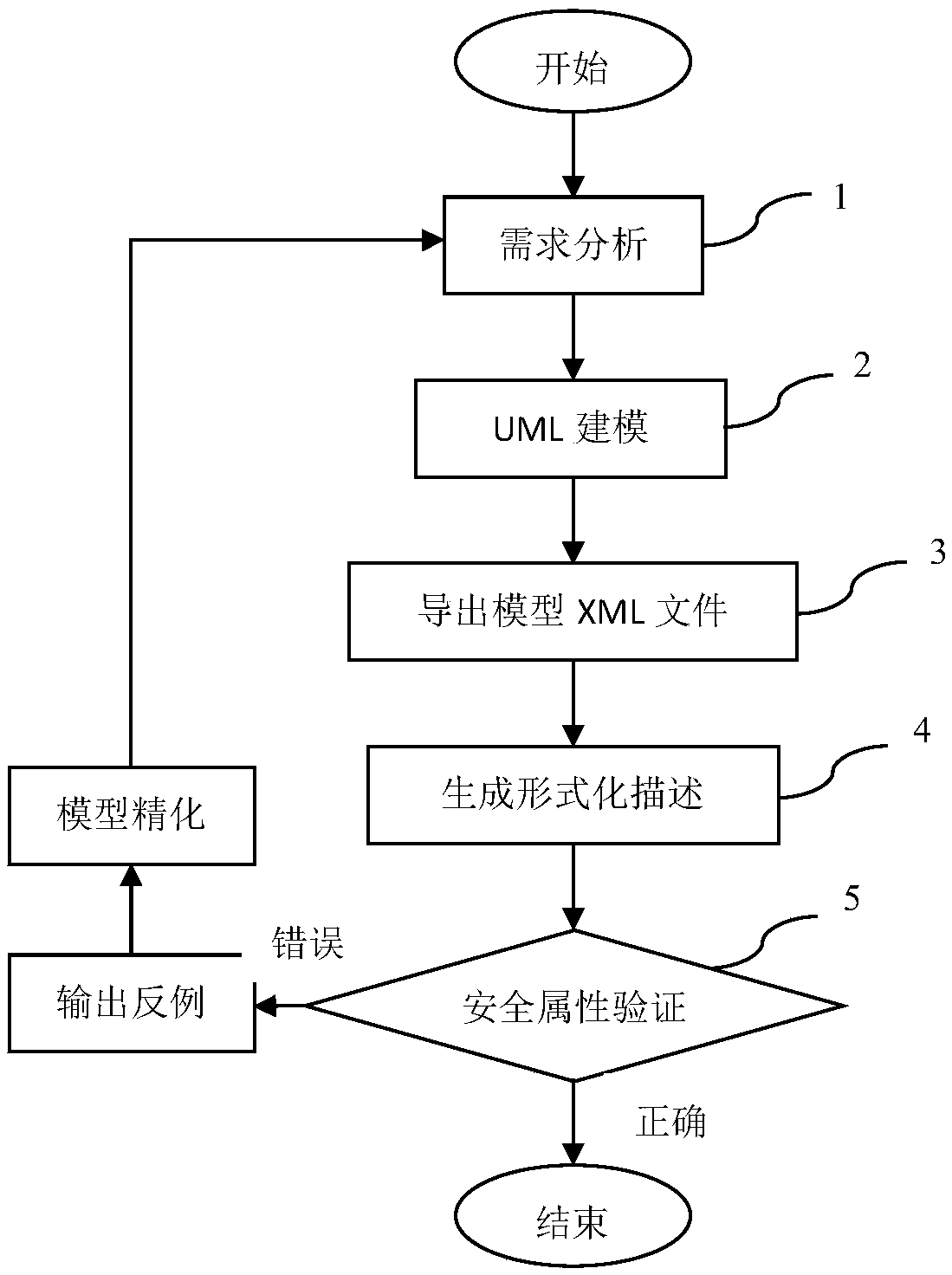
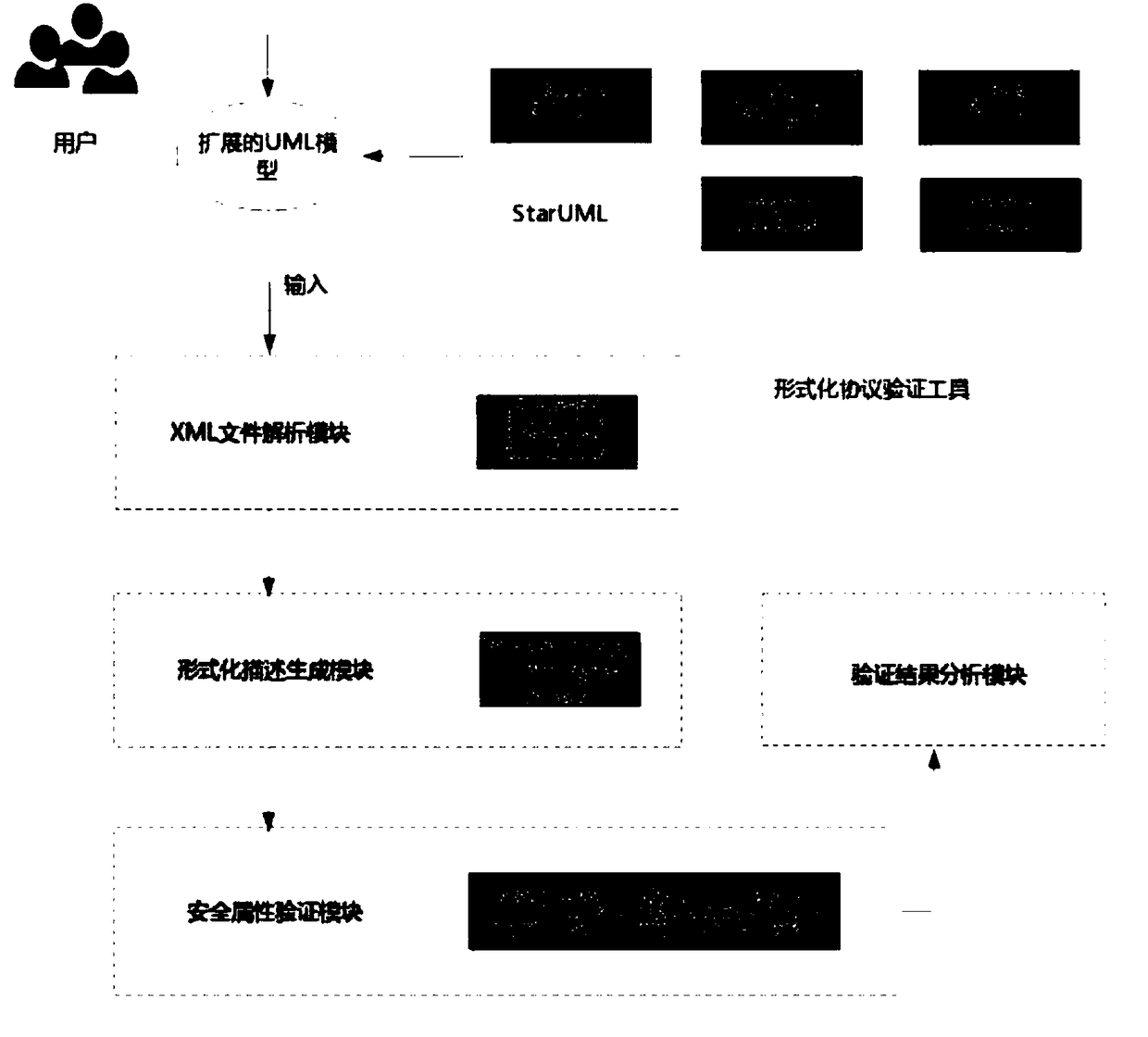
Extension UML-based Web application formalization modeling and verification method
InactiveCN108830085AGuaranteed designEnsure consistencyPlatform integrity maintainanceWeb applicationSoftware system
The invention discloses an extension UML-based Web application formalization modeling and verification method, which comprises the following steps: step (1), extracting functional demands of a software system to be designed, and performing demand analysis, step (2), performing UML modeling; step (3), using XML to represent the aforementioned UML2.3 model; step (4), generating formalization description; step (5), performing security attribute verification. The invention provides a feasible method for automatic conversion from the UML2.3 model to the formalization language to expand class diagram, sequence diagram and state diagram in the UML2.3 to implement protocol verification in Web application and implement automatic conversion from the UML model to pi calculation formalization language, and greatly reduces the difficulty of carrying out formalization modelling on the protocol directly; the formalization modeling verification tool is used, and the formalization verification model isrefined; the loophole of the formalization model is detected through display of the verification result and analysis of the attack path, which facilitates quick refining of the model and efficient defect detection.
Owner:TIANJIN UNIV
Method and apparatus for safety protocol verification, control and management
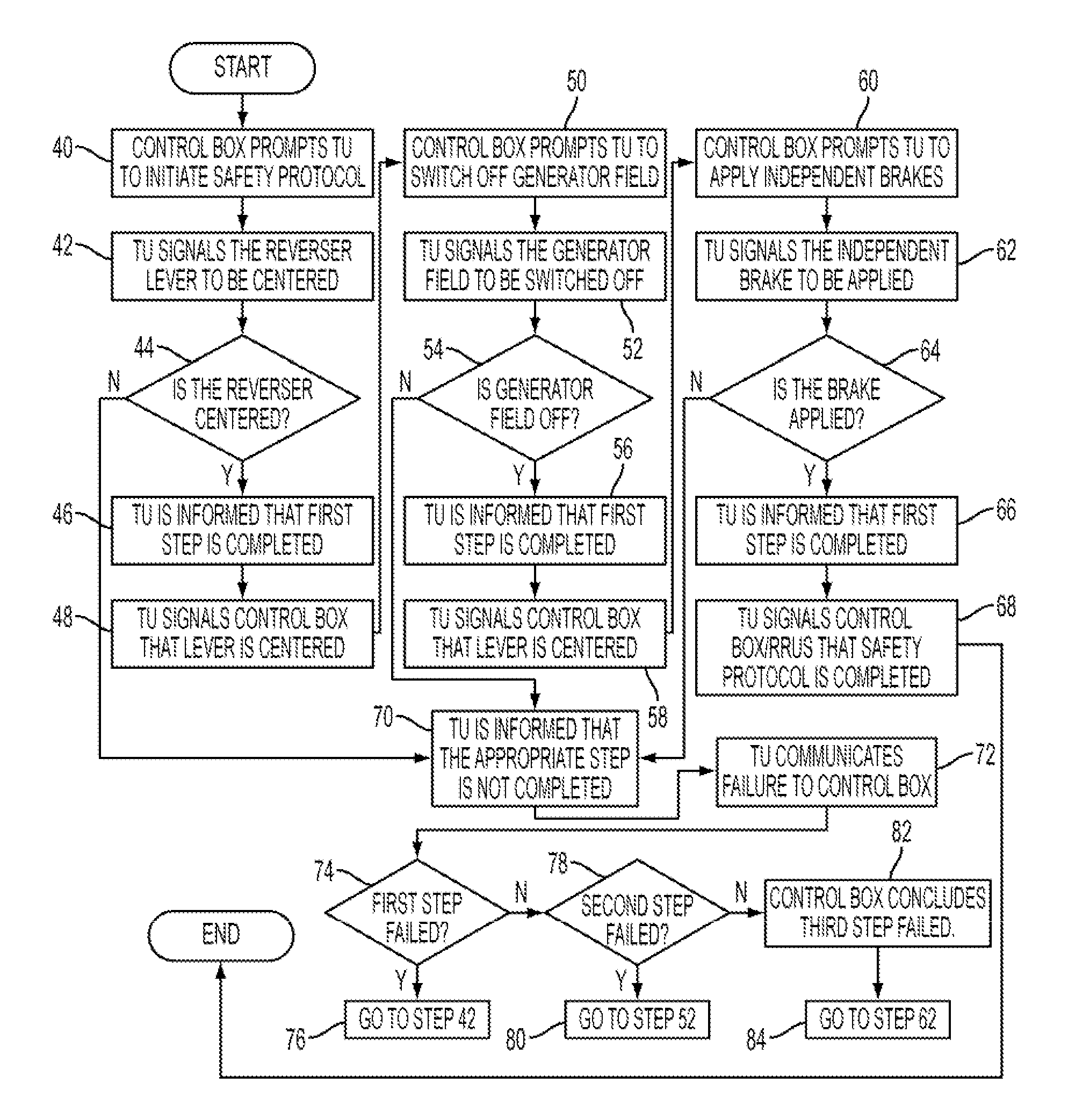
ActiveUS20130304286A1Serious deathSerious injuryDigital data processing detailsVehicle position/course/altitude controlVibratory signalCryptographic protocol
The present invention is an apparatus and a method for a safety verification system, or a safety verification management system. At railroads or construction sites, equipment, such as a piece of heavy machinery, or a locomotive engine, must be subjected to a safety protocol before authorized personnel are allowed to approach the equipment. It is essential to have independent, automatic confirmation that the safety protocol has been successfully completed. In railroad systems, a Three Step Protection Mode is often used to place a locomotive engine in safe mode. One embodiment of the present invention provides an independent, automatic verification that this safety protocol has been successfully completed and sends an audible, visual, audiovisual, or vibratory signal to remote personnel. Another embodiment tracks the relative positions of personnel and locomotives, and generates a warning when personnel are proximate to an equipment that is not in safe mode.
Owner:EHRLER ERIC +1
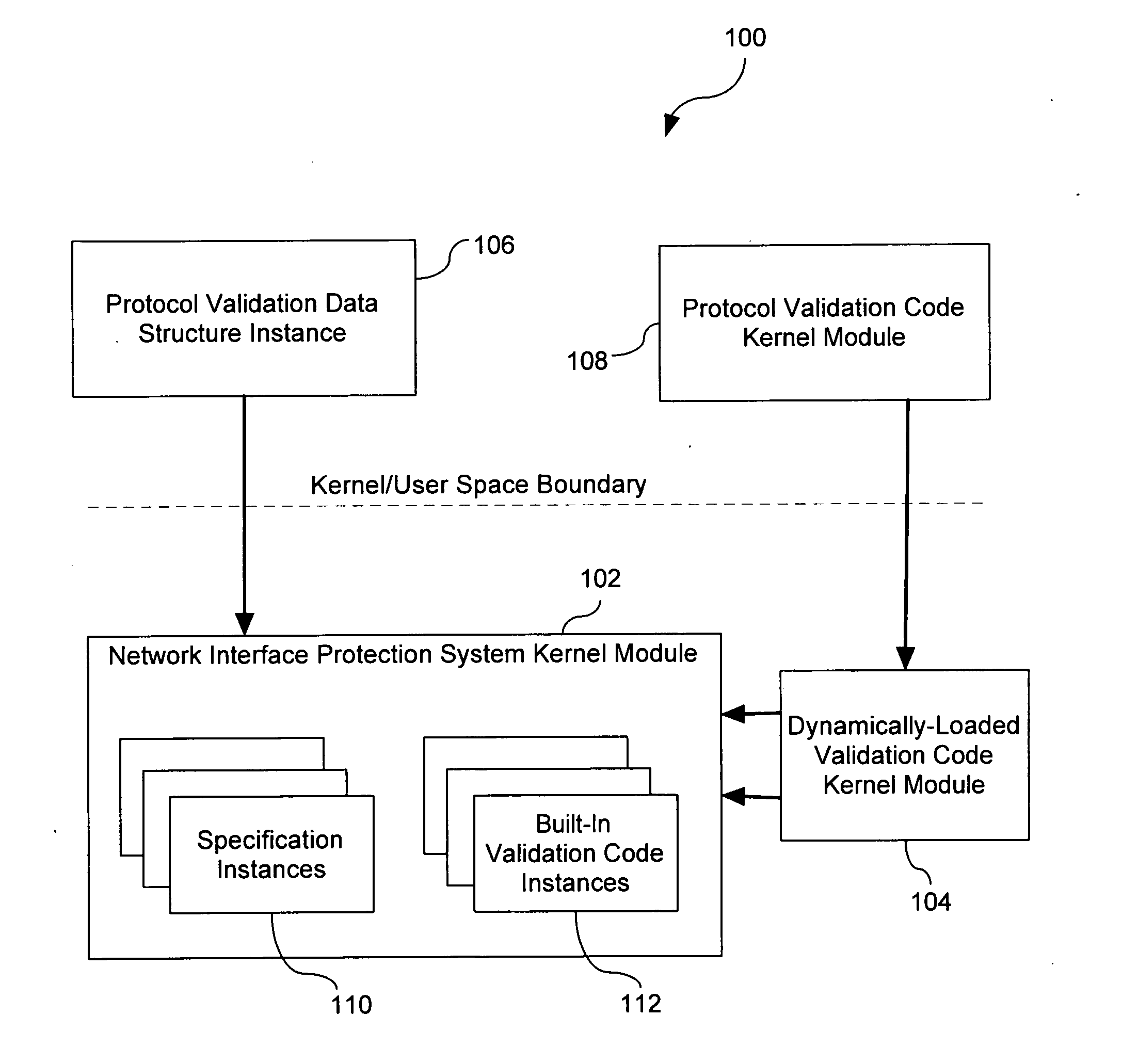
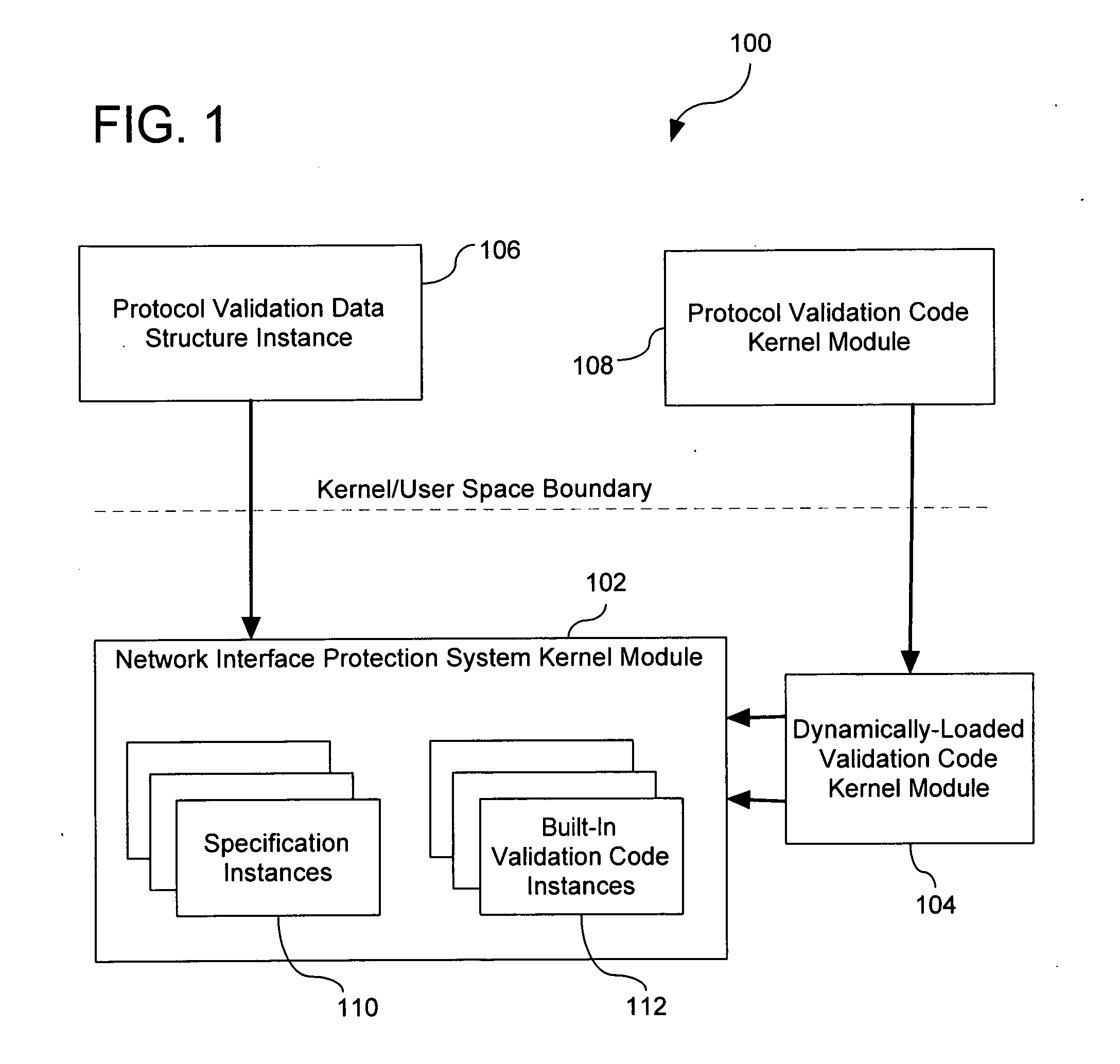
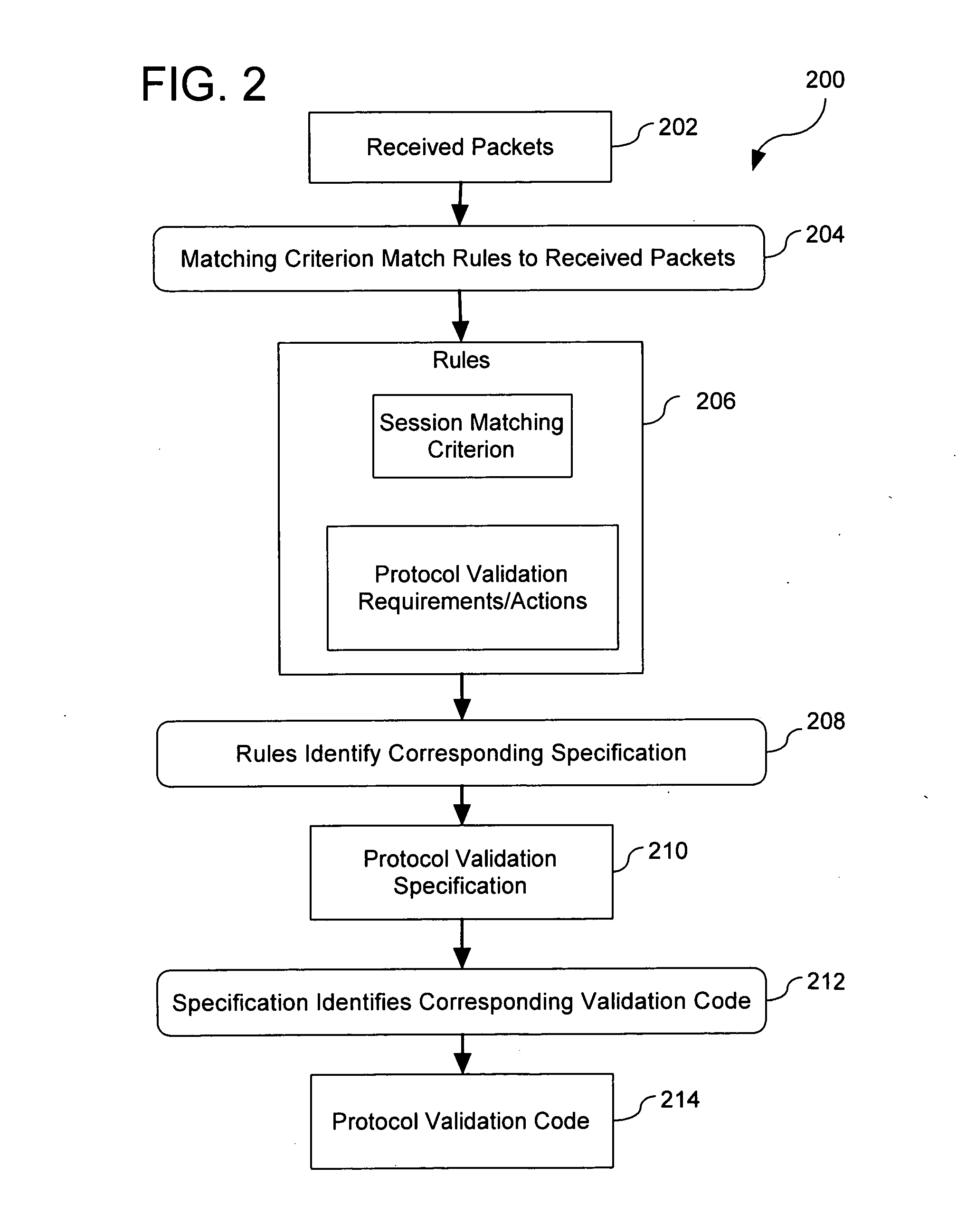
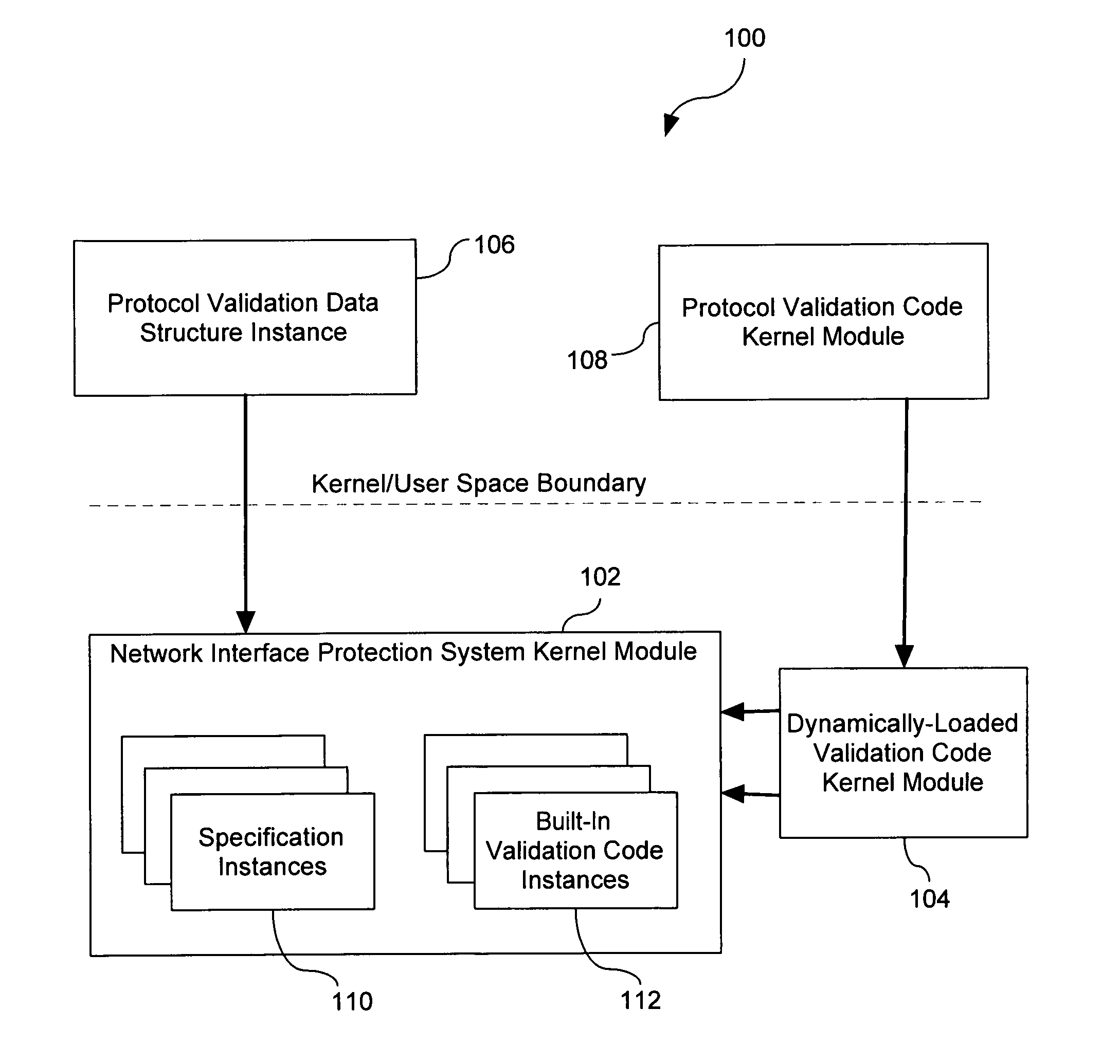
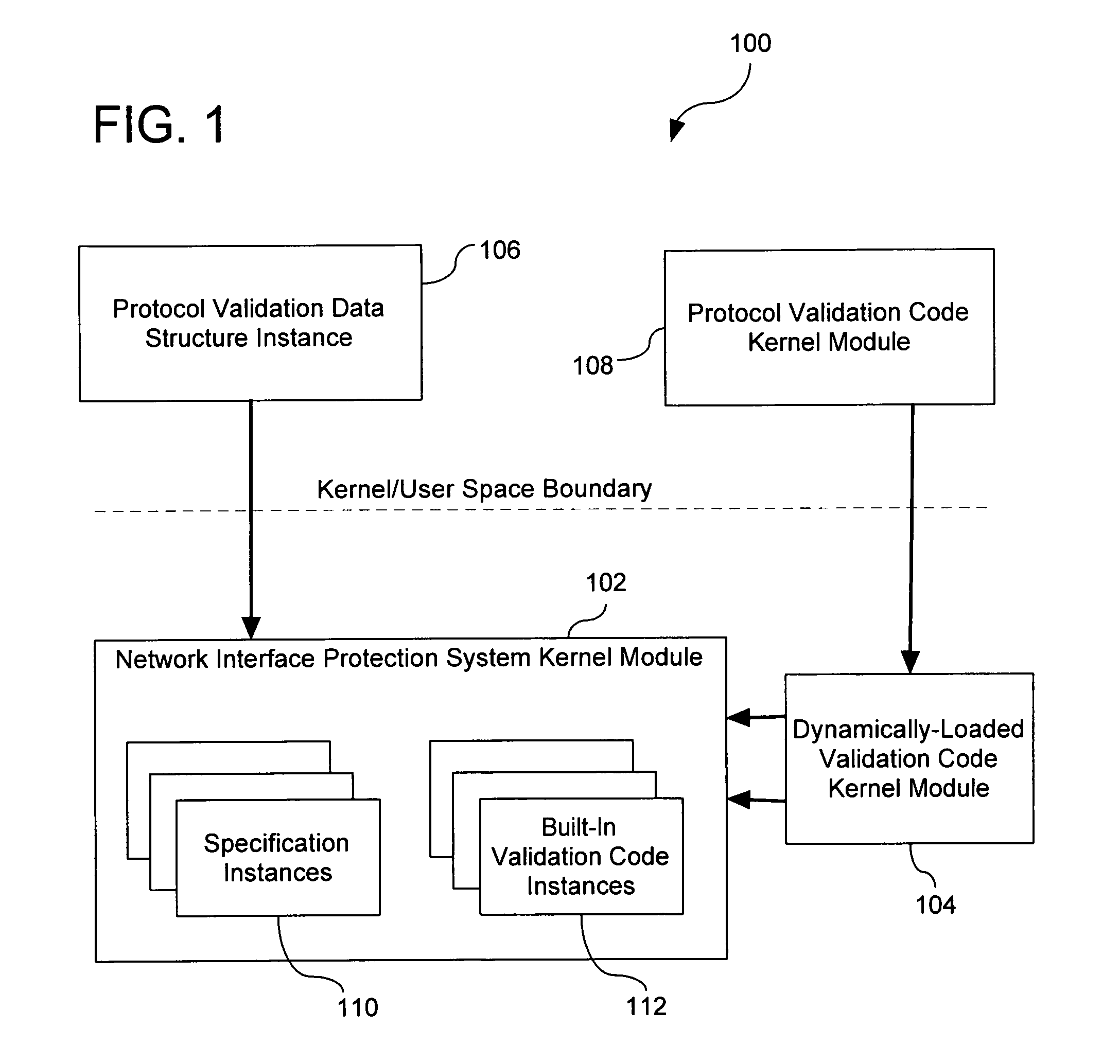
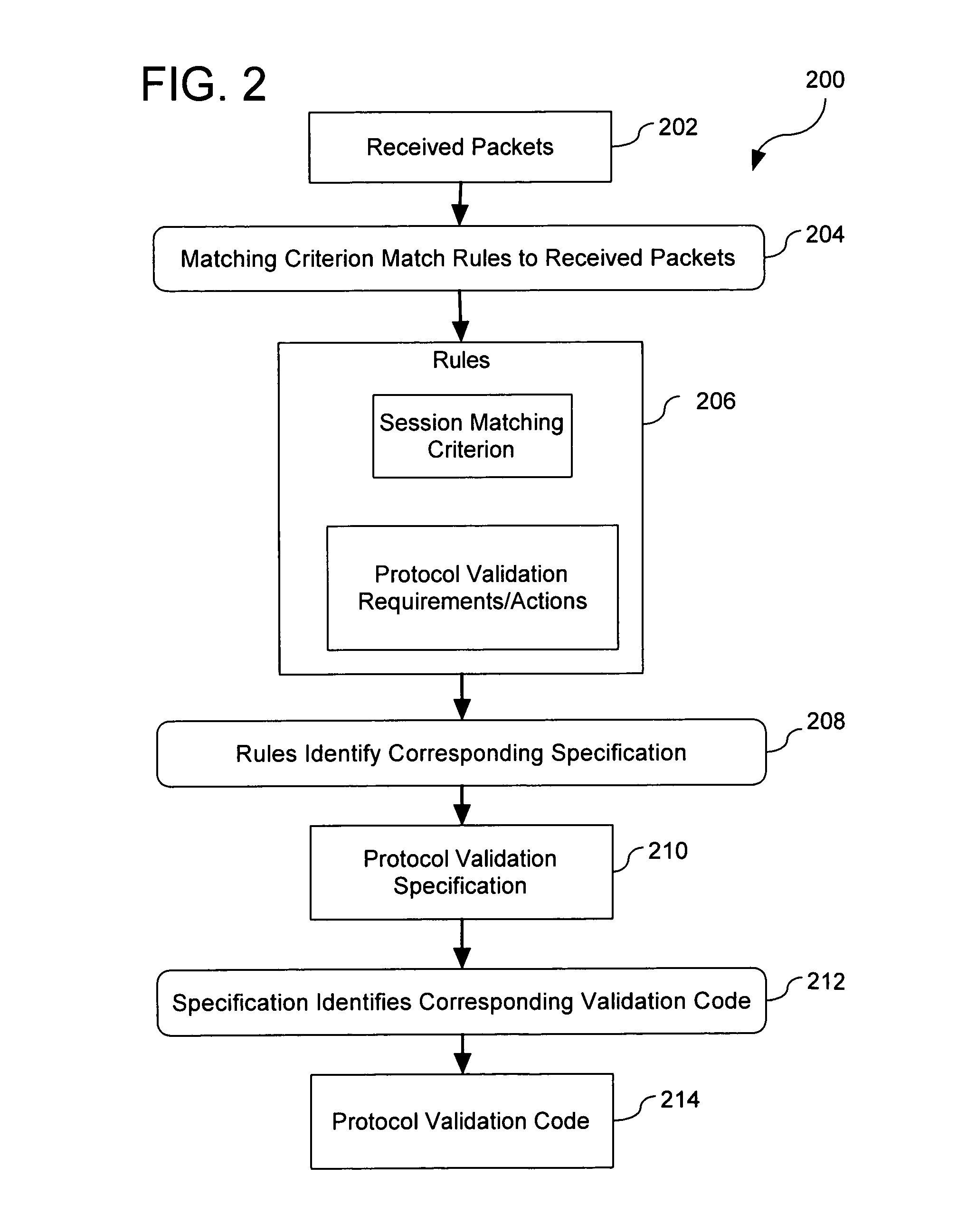
Extensible Protocol Validation
ActiveUS20110030028A1Readily apparentMultiple digital computer combinationsProgram controlData packNetwork packet
A method comprises operations for receiving a binary data structure including a portion representing a protocol validation specification expressed in a respective protocol validation specification language and for receiving a security policy rule having an action part specifying that the binary data structure is to be used for verifying that application protocol payload of network packets complies with the protocol validation specification. After receiving the binary data structure and the security policy rule, an operation is performed for verifying that application protocol payload of received network packets complies with the protocol validation specification. Such verifying is initiated in response to determining that the security policy rule applies to the received network packets and such verifying includes validating the application protocol payload of the received network packets against the binary data structure.
Owner:ALCATEL LUCENT SAS
Wireless sensor network security protocol verification method based on model checking
ActiveCN103476033AVerify securityNetwork topologiesWireless network protocolsCryptographic protocolWireless sensor networking
The invention discloses a wireless sensor network security protocol verification method based on model checking. A state migratory system formed by a timed automata represents a wireless sensor network security protocol, a modal / time sequence logical formula represents the conditions which need to be met by the security protocol in the wireless sensor network, and the verification of the wireless sensor network security protocol is converted into a model carrying out verification that whether the state migratory system is a formula. According to the wireless sensor network security protocol verification method based on model checking, the characteristics of the wireless sensor network are sufficiently considered during the security protocol verification process, a clock restraint condition is added in the modal / time sequence logical formula, and comprehensive verification can be conducted on the wireless sensor network security protocol.
Owner:NANJING UNIV
Method and apparatus for safety protocol verification, control and management
ActiveUS8630758B2Serious deathSerious injuryAudible signalsRoad vehicles traffic controlVibratory signalCryptographic protocol
The present invention is an apparatus and a method for a safety verification system, or a safety verification management system. At railroads or construction sites, equipment, such as a piece of heavy machinery, or a locomotive engine, must be subjected to a safety protocol before authorized personnel are allowed to approach the equipment. It is essential to have independent, automatic confirmation that the safety protocol has been successfully completed. In railroad systems, a Three Step Protection Mode is often used to place a locomotive engine in safe mode. One embodiment of the present invention provides an independent, automatic verification that this safety protocol has been successfully completed and sends an audible, visual, audiovisual, or vibratory signal to remote personnel. Another embodiment tracks the relative positions of personnel and locomotives, and generates a warning when personnel are proximate to an equipment that is not in safe mode.
Owner:EHRLER ERIC +1
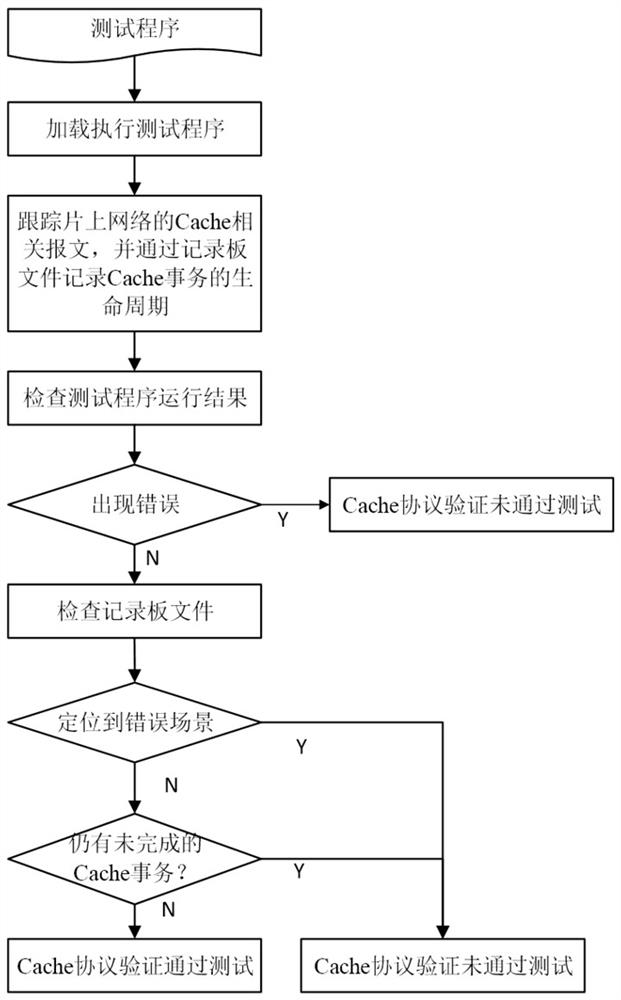
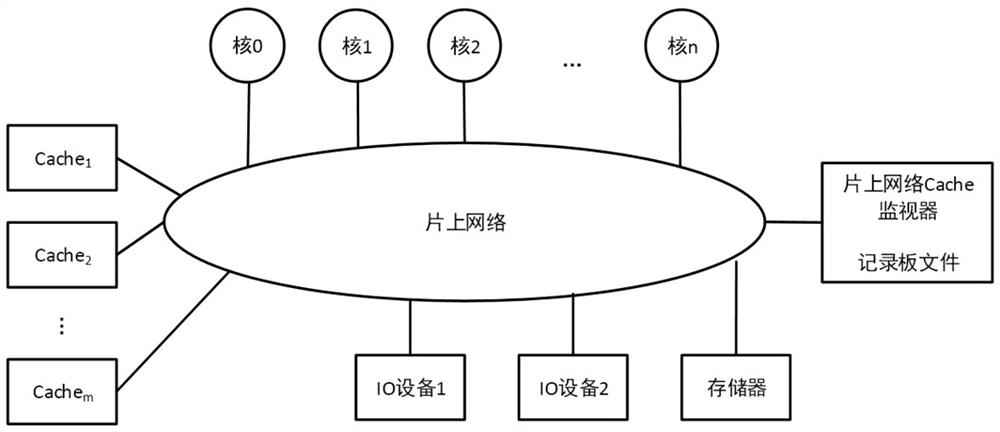
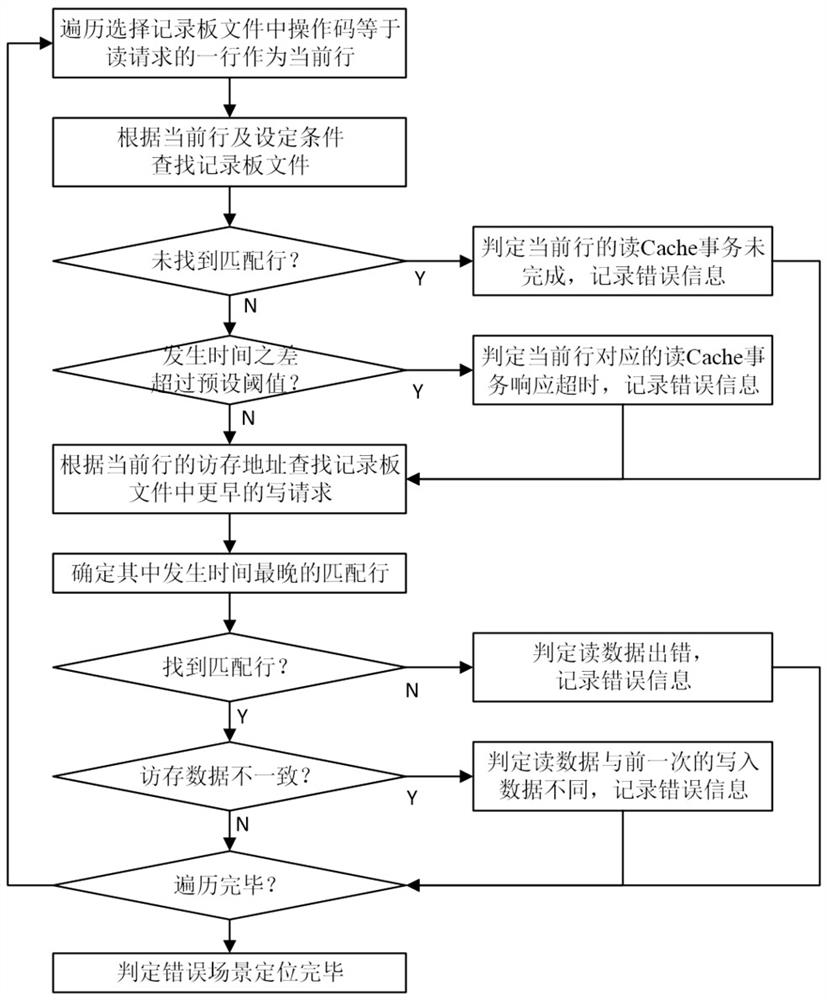
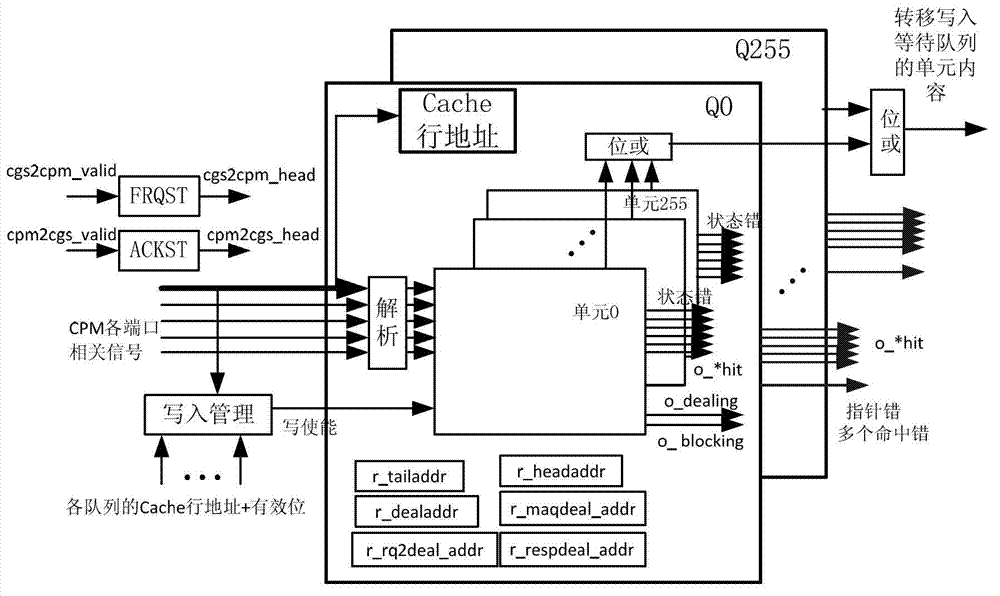
Cache consistency protocol verification method and system for on-chip multi-core processor, and medium
ActiveCN111611120APrecise positioningEasy to spot design errorsFaulty hardware testing methodsEnergy efficient computingCache consistencyNetworks on chip
The invention discloses a Cache consistency protocol verification method and system for an on-chip multi-core processor, and a medium. The method comprises the steps of loading and executing a test program for the on-chip multi-core processor executing a Cache protocol to be verified, tracking a Cache related message of an on-chip network, and recording the life cycle of a Cache transaction through a recording board file; checking whether the running result of the test program has an error or not, if so, judging that the Cache protocol verification does not pass the test, and exiting; otherwise, checking an error scene in the execution process of the record board file positioning test program, and if the error scene is found or the record board file still has an unfinished Cache transaction, judging that the Cache protocol verification does not pass the test; otherwise, judging that the Cache protocol verification passes the test. According to the invention, an error scene can be accurately positioned in a verification process, and design vulnerabilities and errors are easy to discover.
Owner:NAT UNIV OF DEFENSE TECH
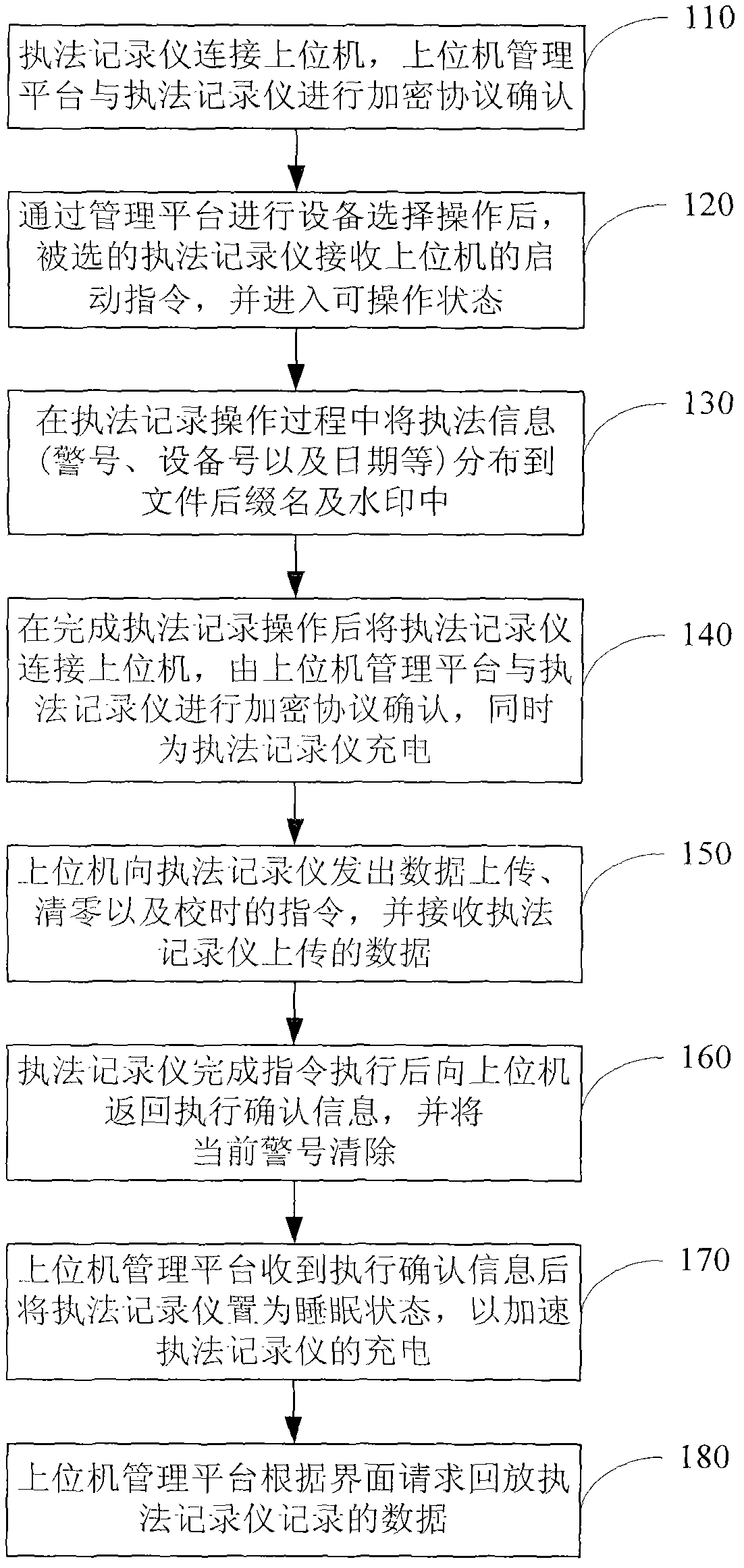
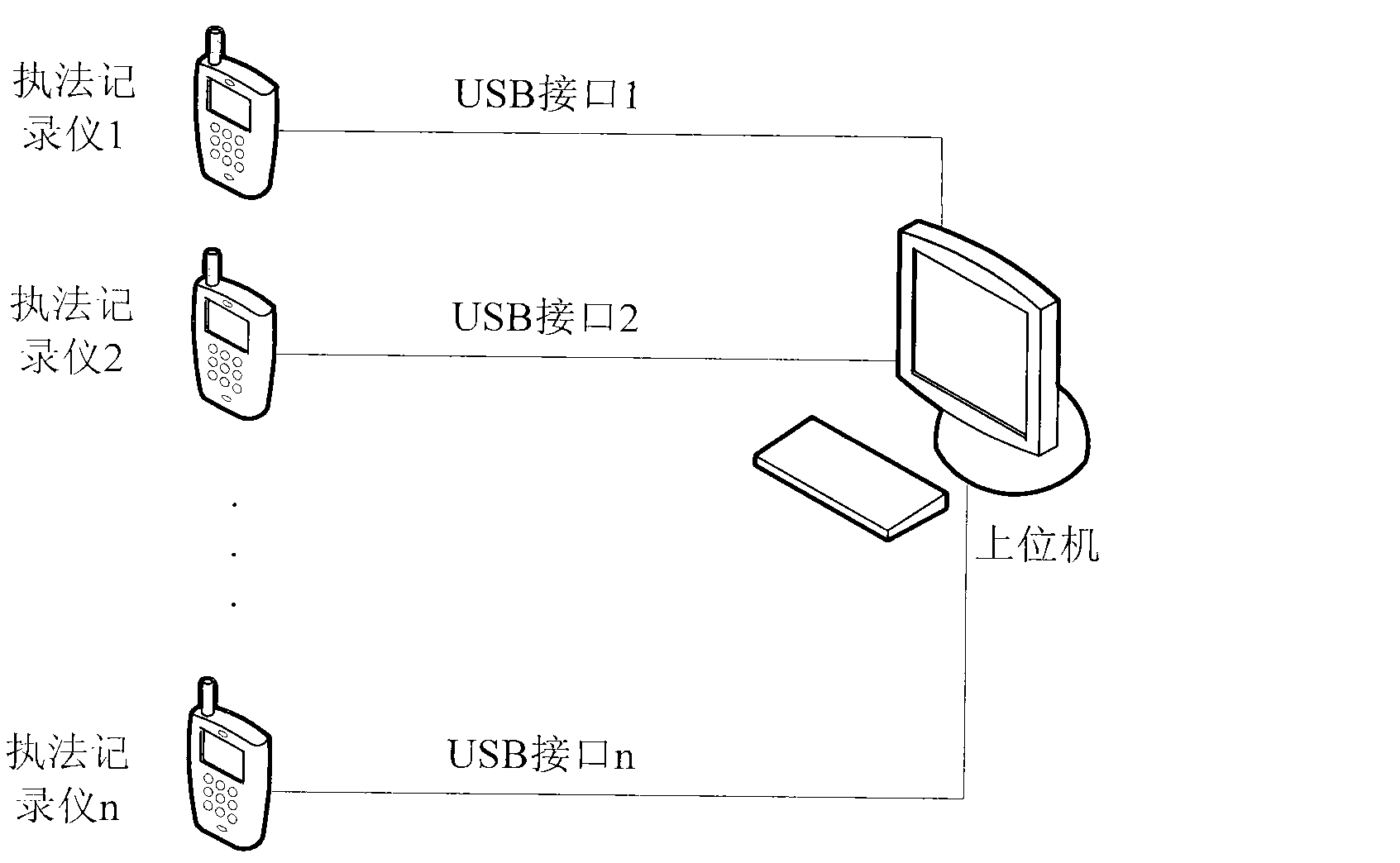
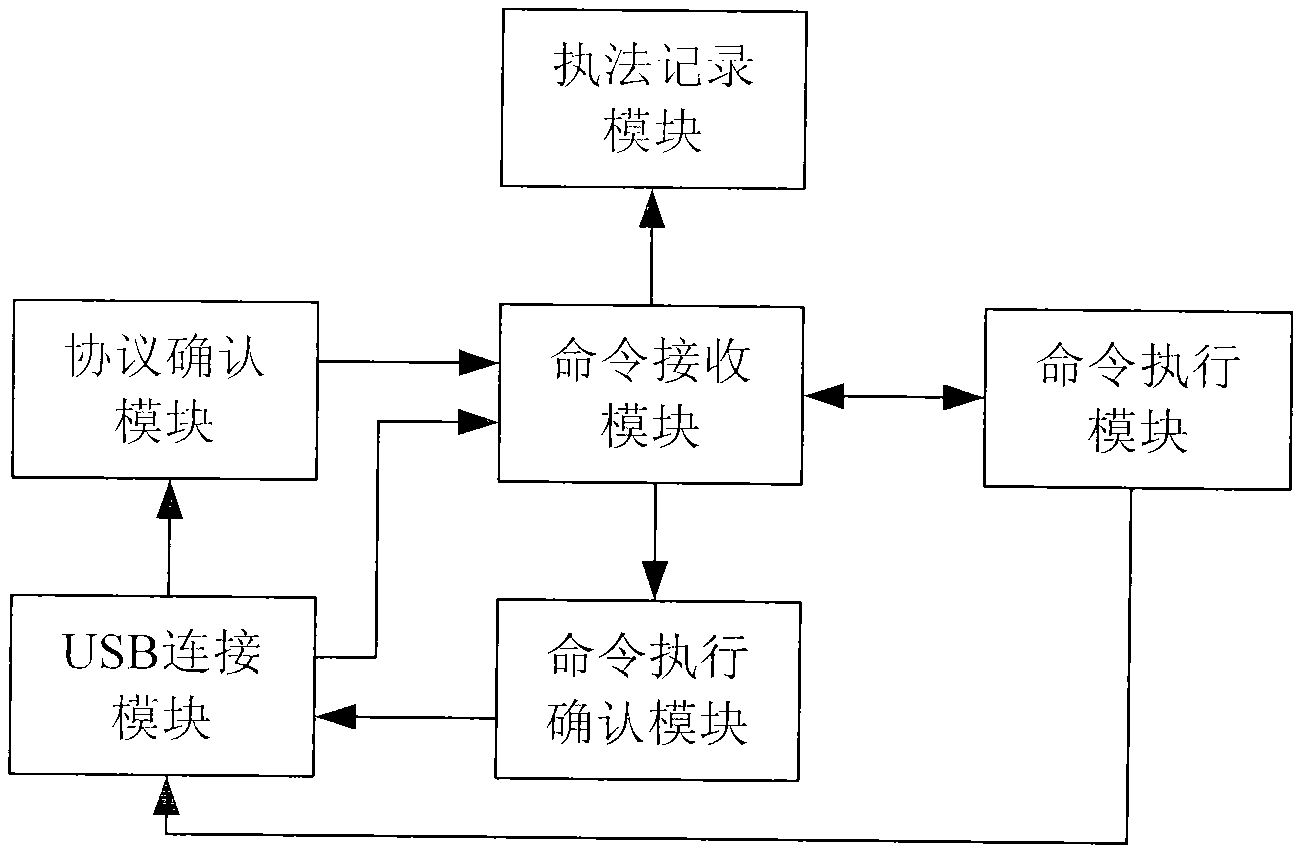
Law enforcement recording system, law enforcement recording device and law enforcement recording method
InactiveCN102841590ASimple and fast operationEasy to operate and learnTotal factory controlProgramme total factory controlComputer moduleManagement efficiency
The invention discloses a law enforcement recording system, a law enforcement recording device and a law enforcement recording method, wherein the system comprises an upper computer and a plurality of law enforcement recorders managed by the upper computer; by means of an installed management platform, the upper computer verifies the encryption protocol when a law enforcement recorder accesses the system, and provides a device selection interface for the law enforcement recorder; the law enforcement recorder verifies the encryption protocol by means of a protocol verification module when being connected with the upper computer; after the device selection interface of the management platform is selected, a command receiving module is utilized to receive the starting command of the upper computer, and a law enforcement operation command is outputted to a law enforcement recording module. The invention can use only one upper computer to manage a plurality of law enforcement recorders and then utilize the operating platform to automatically carry out various operations in batches, consequently, the management efficiency can be greatly increased, and meanwhile, the error rate also can be greatly decreased or prevented.
Owner:深圳众里飞扬科技有限公司
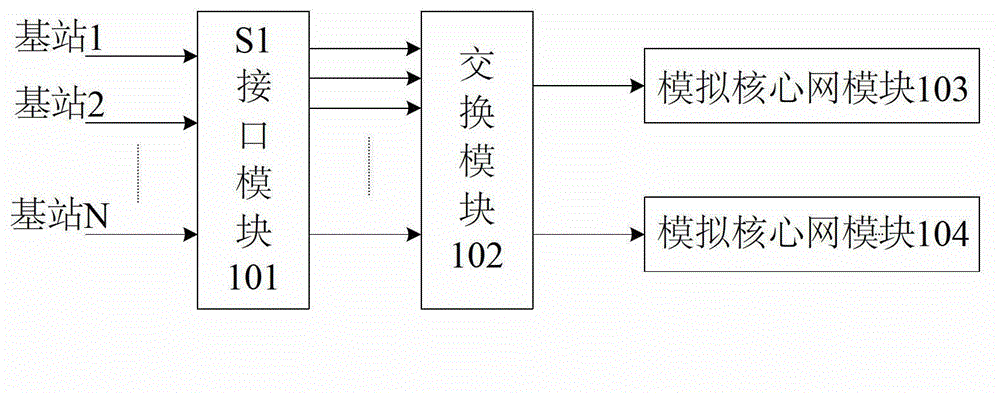
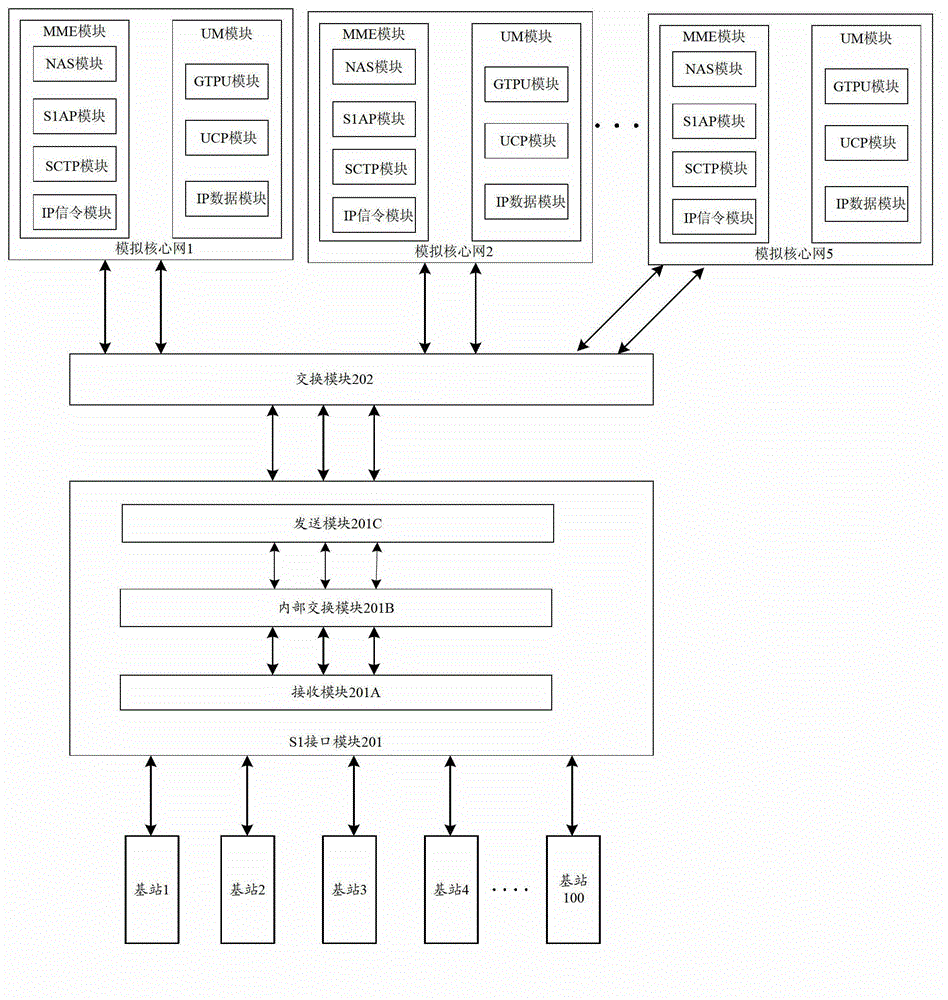
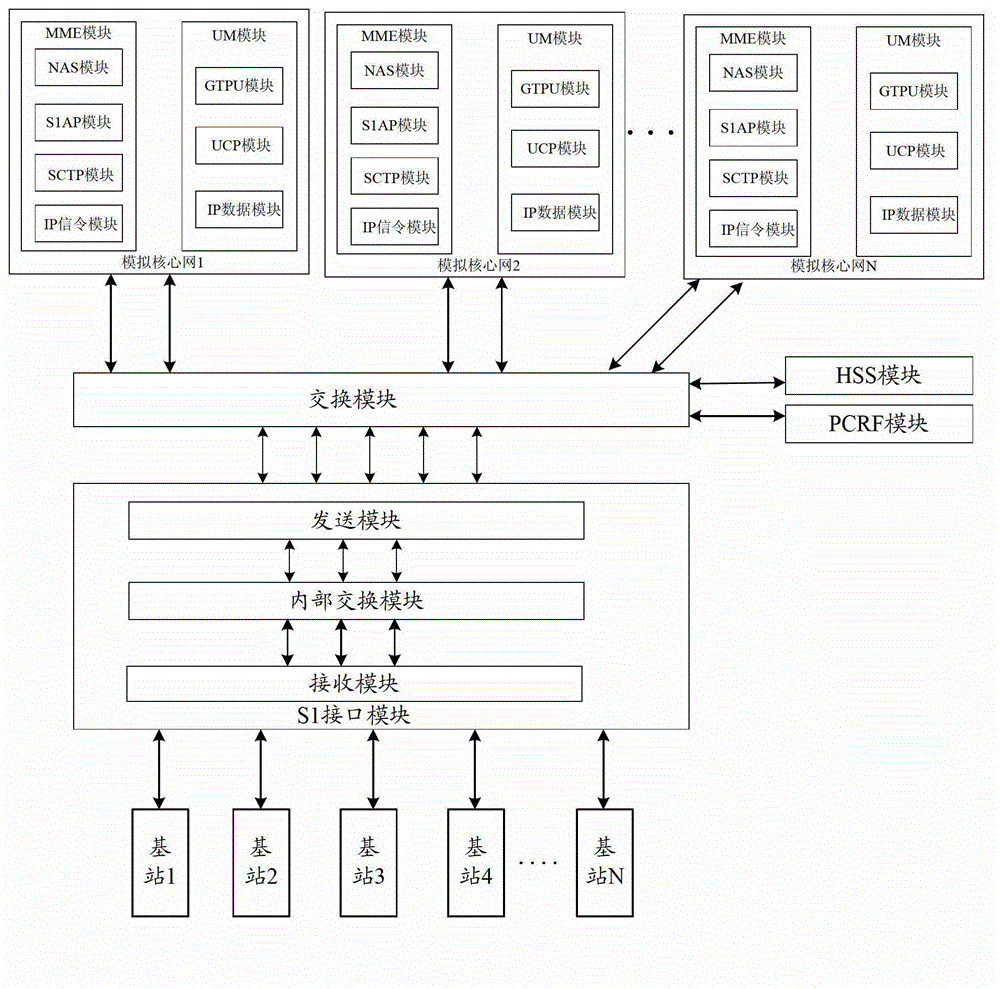
Device and method for consistency protocol verification of interfaces S1 of LTE (Long Term Evolution) wireless network
The embodiment of the invention discloses a device and method for consistency protocol verification of interfaces S1 of an LTE (Long Term Evolution) wireless network. The device comprises an interface S1 module, an exchange module and at least two analog core network modules, wherein the interface S1 module is used for simultaneously receiving interface S1 test data sent by different base stations, determining the corresponding relationship between the different base stations and the analog core network modules through exchange processing, and transmitting the interface S1 test data from the different base stations to respective corresponding analog core network modules through the exchange module; and the analog core network modules are used for simultaneously processing the interface S1 test data which is received from the exchange module and comes from the different base stations, and transmitting a first response signal to the interface S1 module through the exchange module. The device and the method have the advantages that the consistency protocol verification on the interfaces S1 between multiple base stations and multiple analog core network modules can be simultaneously carried out, and the requirements of LTE for rapid network deployment are met.
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
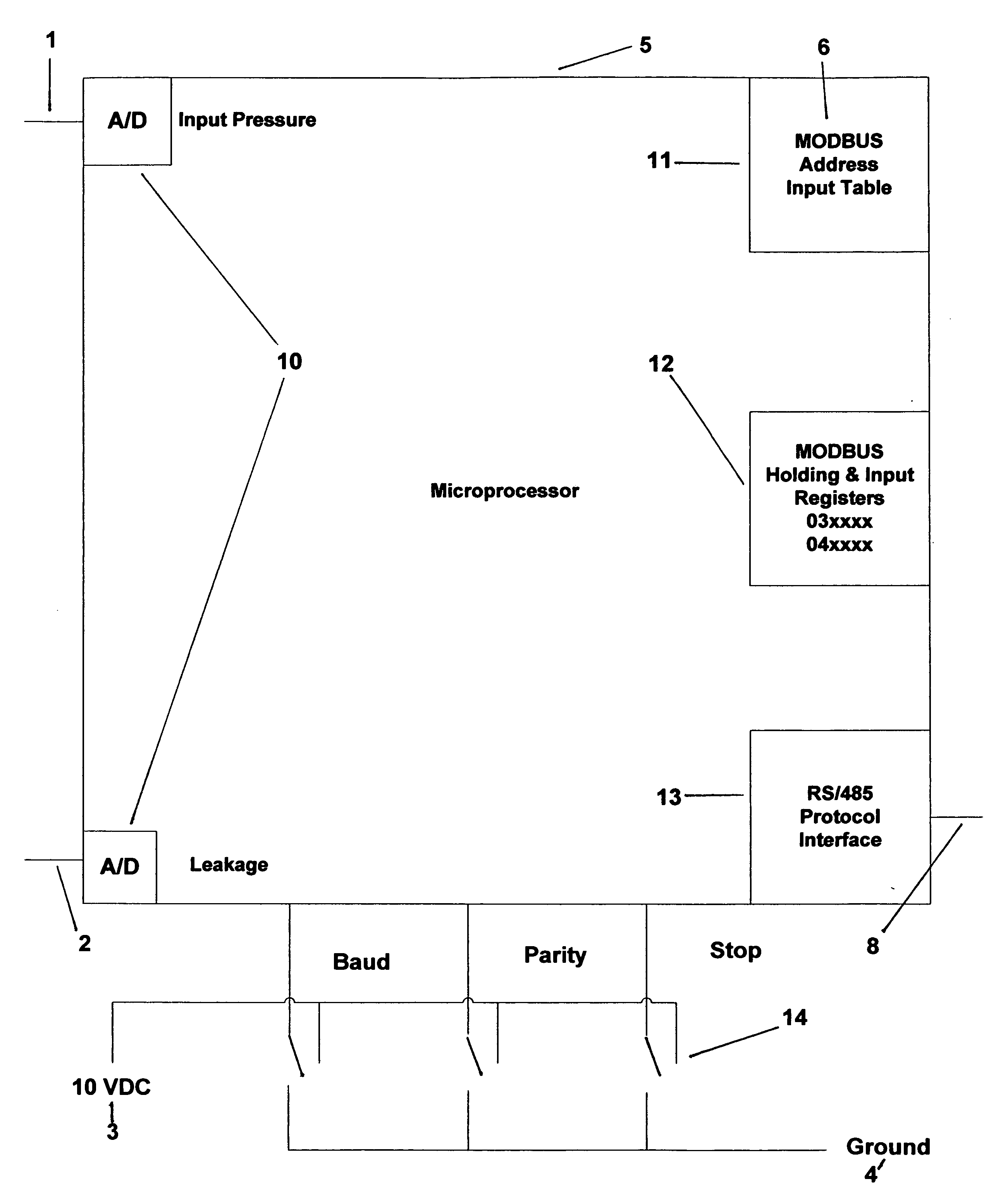
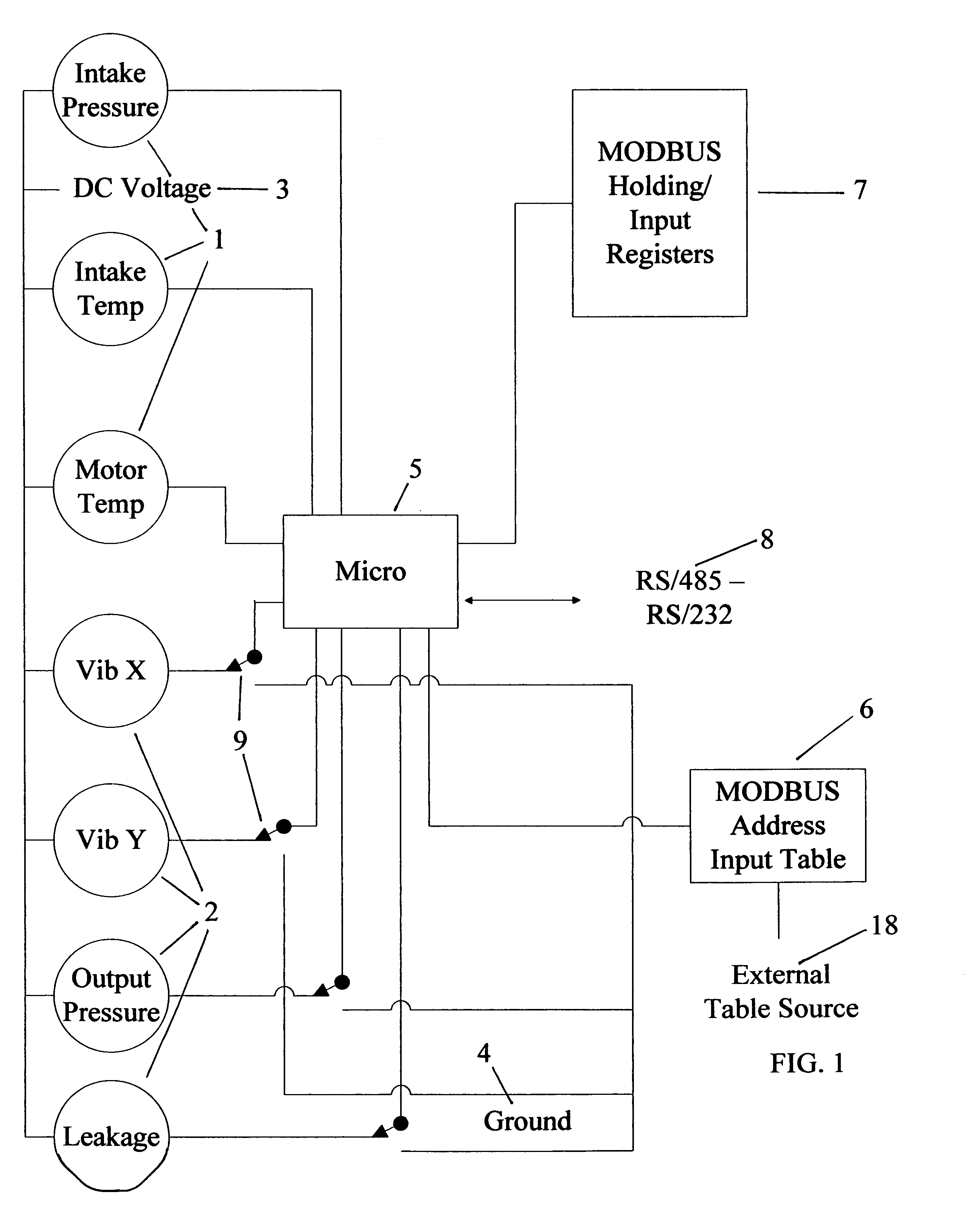
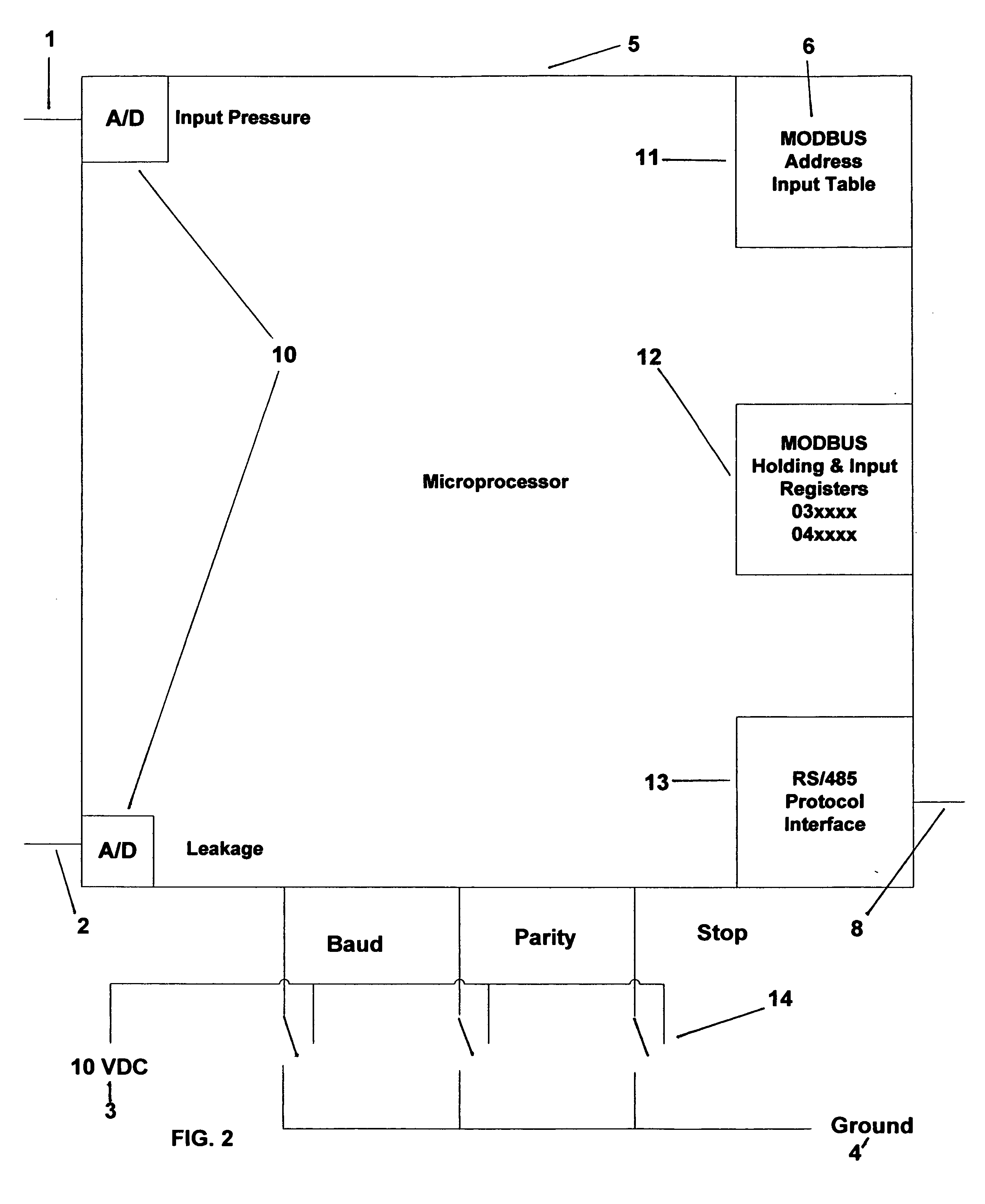
Downhole Sensor MODBUS Data Emulator
InactiveUS20120194351A1Simulator controlElectric/magnetic detectionNetwork Communication ProtocolsComputer science
In order to emulate the inputs from a DHS, RTD type sensors are typically employed, externally heated, and the input provided into an interface unit. At best such an approach provides a stop-gap solution that is cumbersome and not reliably repeatable. Such temporary inputs seldom provide the equivalent communications protocol verification between the surface controller of the DHS and the external communications device. Each DHS commercially available also uses different MODBUS register addresses for the requested data, as well as a variation in the number of parameters expected from the DHS itself, ranging from 3 to 7, depending on the vendor of choice. In this new design, a number of potentiometers are used to provide a variable signal level to the microprocessor, acting as variable parameters from the downhole sensor, the settings of which can be repeated for reliable test results.
Owner:FLOYD RAYMOND E
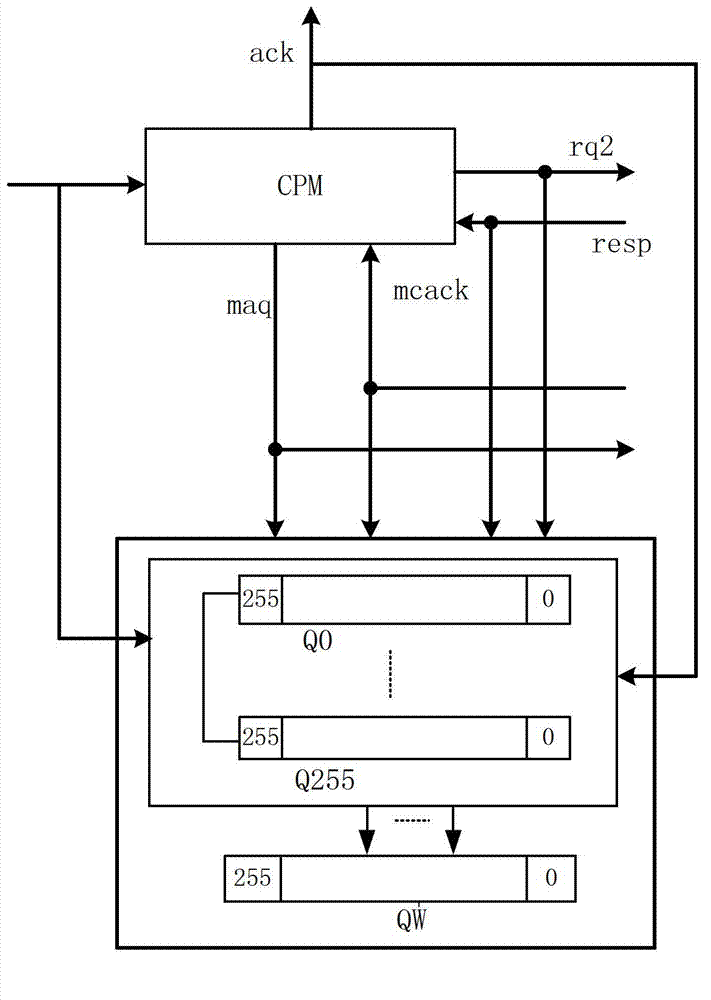
Method for verifying Cache coherence protocol and multi-core processor system
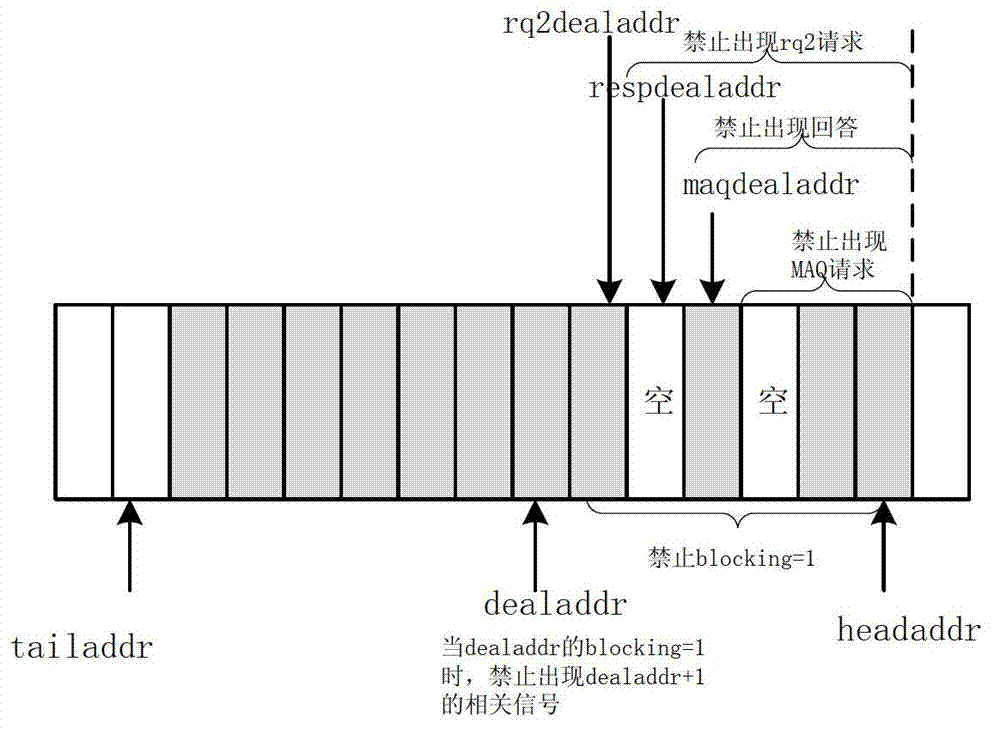
ActiveCN102880467ABehavior Accurate MonitoringDigital computer detailsSpecific program execution arrangementsBehavioral stateProcessing element
The invention provides a method for verifying a Cache coherence protocol and a multi-core processor system. The method for verifying the Cache coherence protocol comprises the following steps that: a plurality of queues are arranged in a monitor, every queue comprises a plurality of units, the units are used for recording all primary requests which are not processed completely, all the requests which are relevant to addresses are orderly stored in the units of the same queue according to the sequence in which the requests enter a coherence processing element, and every unit is used for tracking the performance status of recorded requests independently. According to the characteristic that the method for verifying the Cache coherence protocol based on the monitor in the invention can process the requests relevant to the memorized and accessed addresses in sequence according to the Cache coherence protocol, the monitor is used for monitoring the protocol-level behavior of the Cache coherence processing element accurately, and the behavior of every request package can be monitored accurately. Through adjusting the content in the monitor, the method for verifying the Cache coherence protocol is suitable for verifying various coherence protocols.
Owner:JIANGNAN INST OF COMPUTING TECH
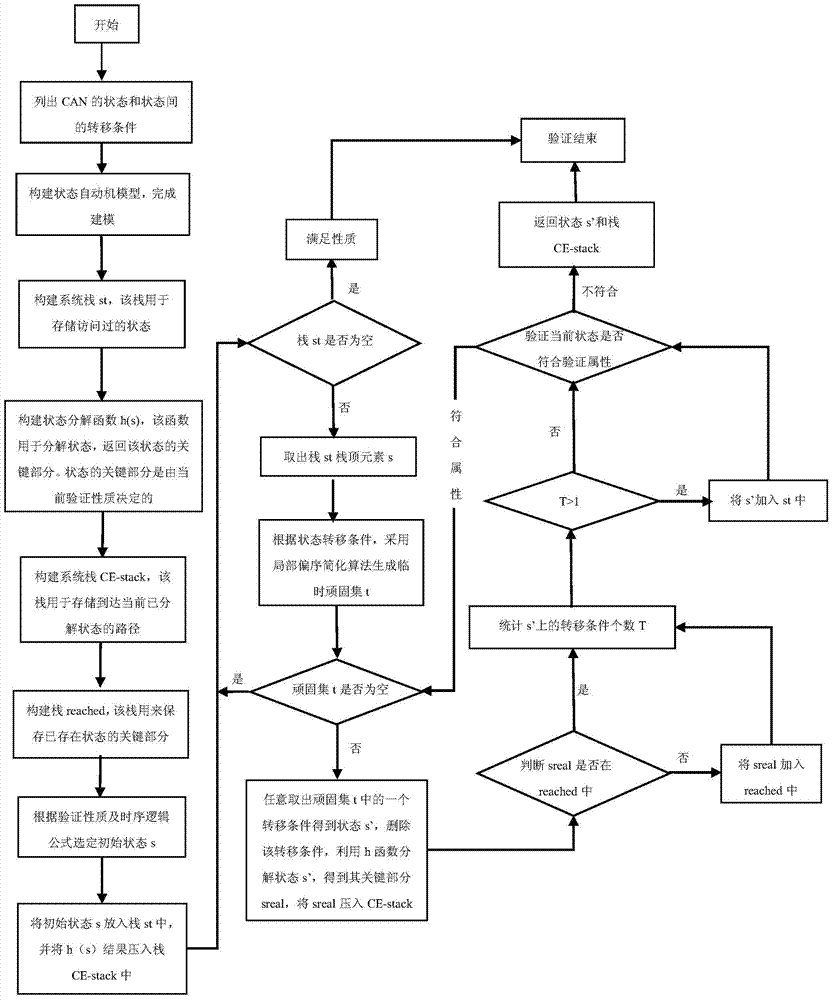
Controller local area network protocol verification method based on state space search
ActiveCN103888460ATime and Space Complexity OptimizationClear expressionTransmissionArea networkDynamic planning
The invention discloses a controller local area network protocol verification method based on state space search. The method comprises the steps of system modeling, model pre-processing and model verification. In the modeling process, an abstract time state automat model is constructed, a state transition diagram prevents, through the utilization of the idea of dynamic planning, a state spatial graph from being generated in a redundant state. In the verification of a controller load area network software model, the state search algorithm based on decomposition is used for further optimizing the state search space of the model, the verification process of the whole system is made to be further optimized in time and space complexity, and data processed through the algorithm are output and converted into a language form which can be understood by inspection personnel easily. The controller local area network protocol verification method can be used for effectively verifying whether relevant network protocols meet requirements, and relieves the problem of state space explosion in the verification process. The space-time complexity of the system in the verification process is low.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method for implementing Ethernet load-carrying point-to-point protocol authentication on very-high speed digital user loop
InactiveCN1477832ALow costReduce workloadData switching by path configurationSelection arrangementsPoint-to-Point ProtocolTerminal equipment
The present invention provides a method for implementing Ethernet loaded point-to-point (PPPoE) protocol verification on the very-high speed digital user loop. The equipment distribution of terminal PPPoE can be simultaneously downward-moved, and the control message of PPPoE is processed by CPU, the service message can be processed by ASIC or FPGA. The adoption of said invented technical scheme can effectively reduce equipment cost for supporting PPPoE, at the same time the PPPoE equipment distribution can reduce the group-transmitting message copy work capacity of every PPPoE terminal equipment, so that the practical group transmission under the PPPoE mode also can be implemented.
Owner:HUAWEI TECH CO LTD
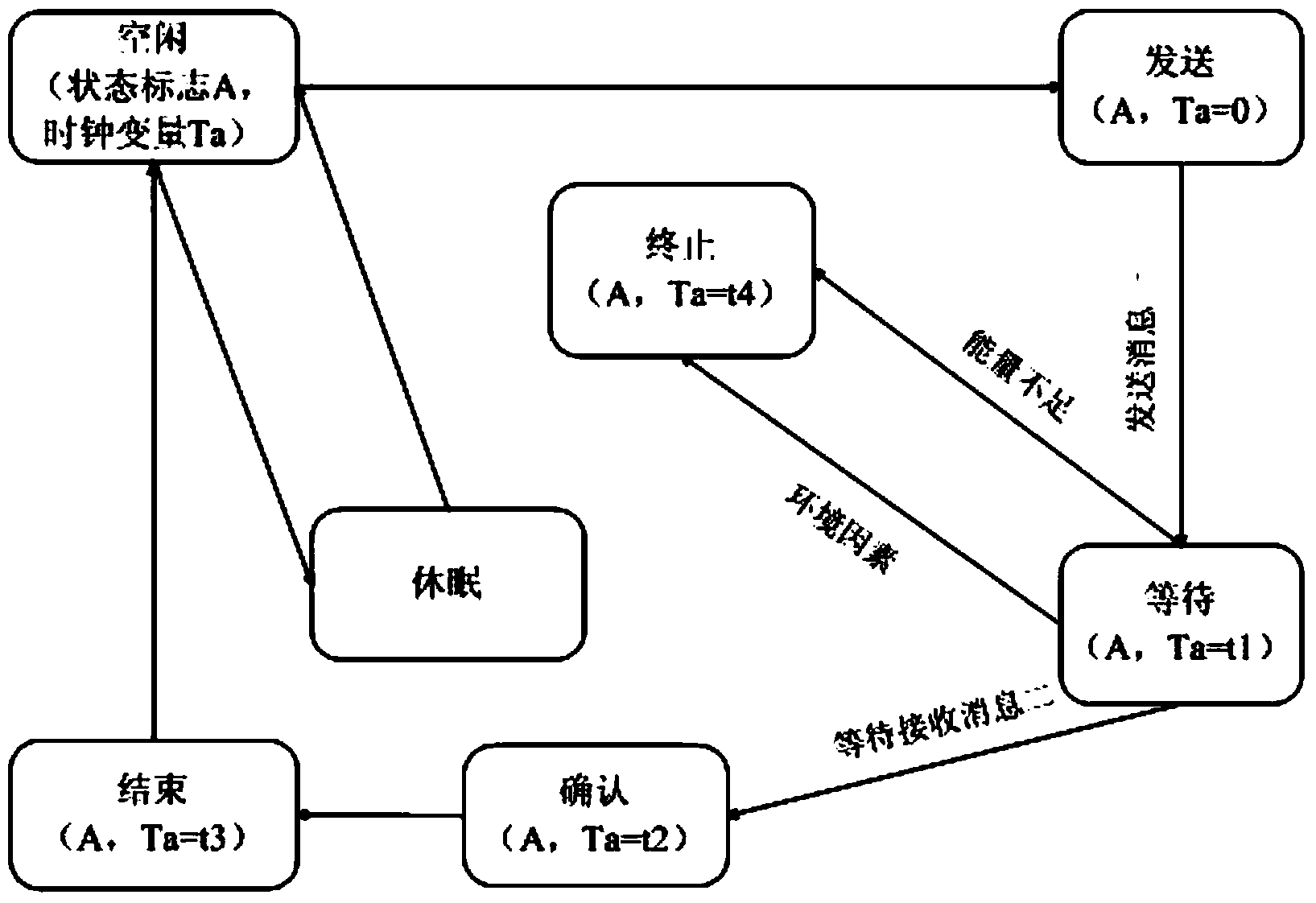
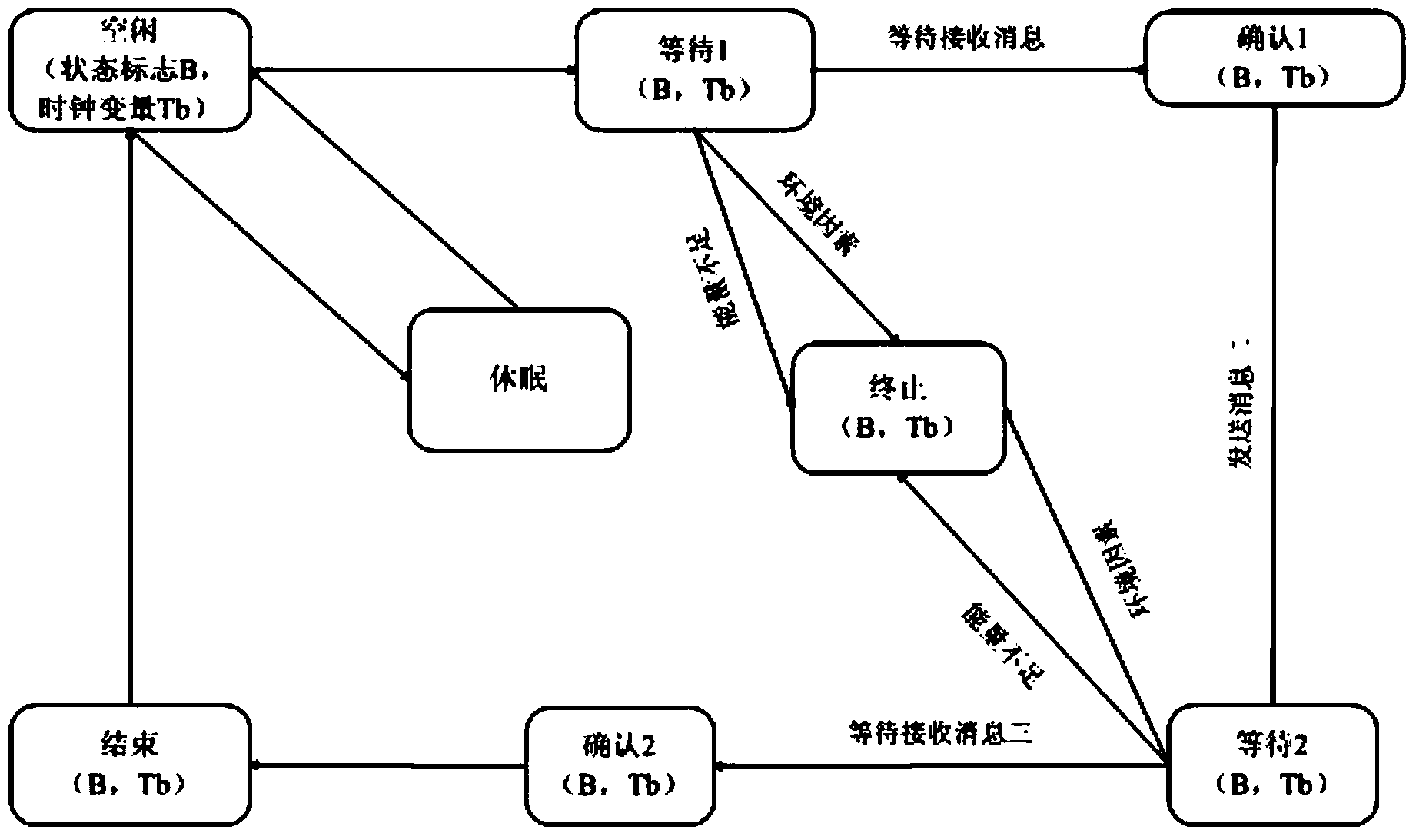
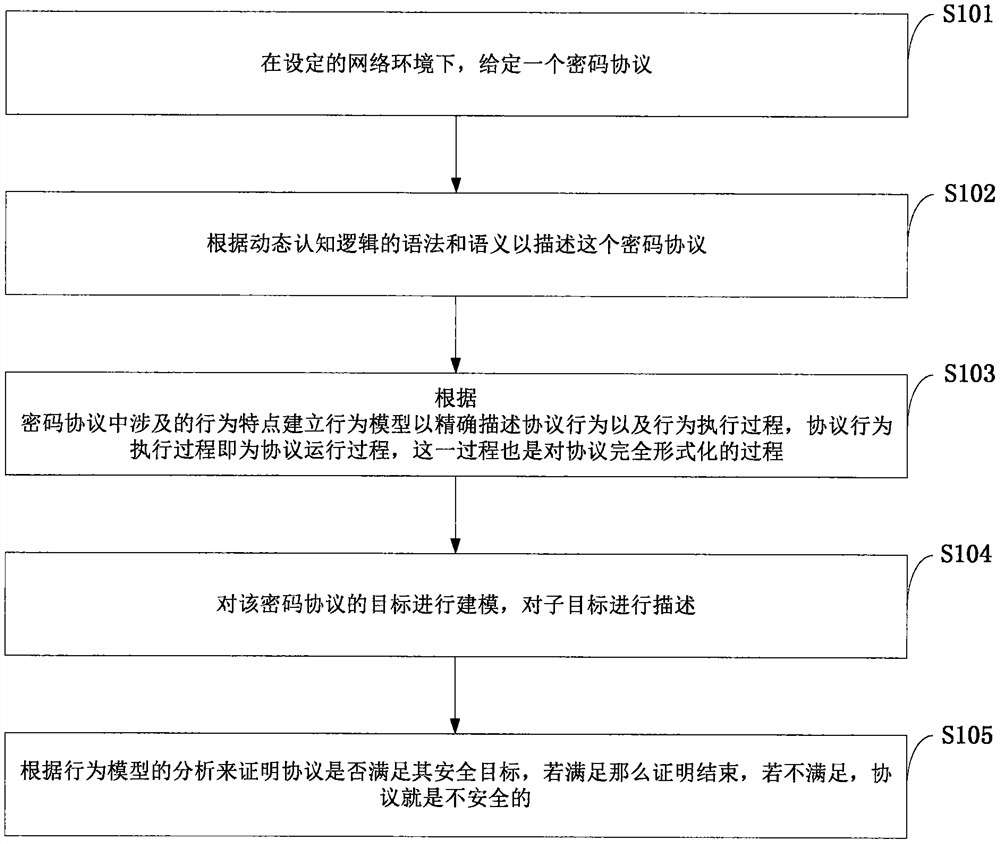
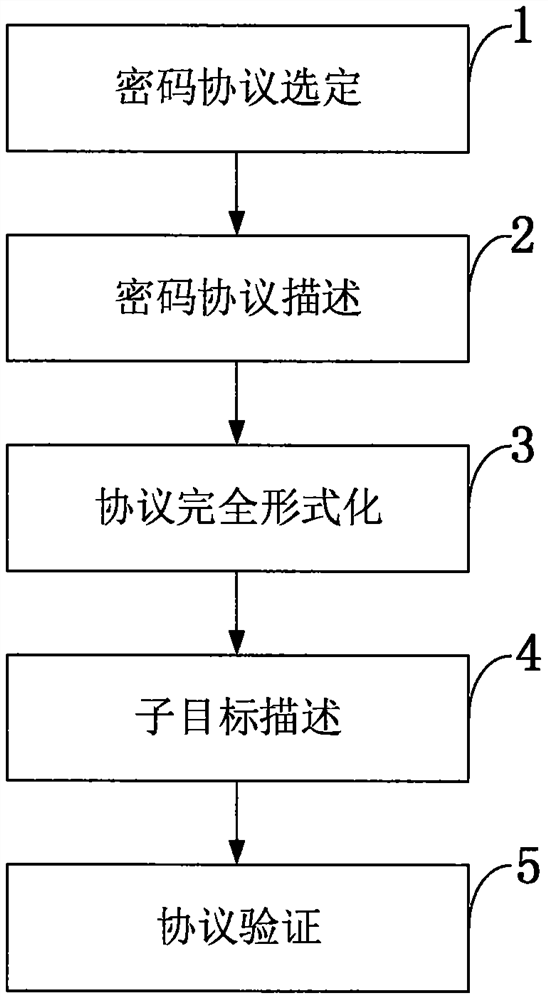
Cryptographic protocol verification method
PendingCN111756704ASimple and clear descriptionReduce complexityTransmissionAlgorithmCryptography protocols
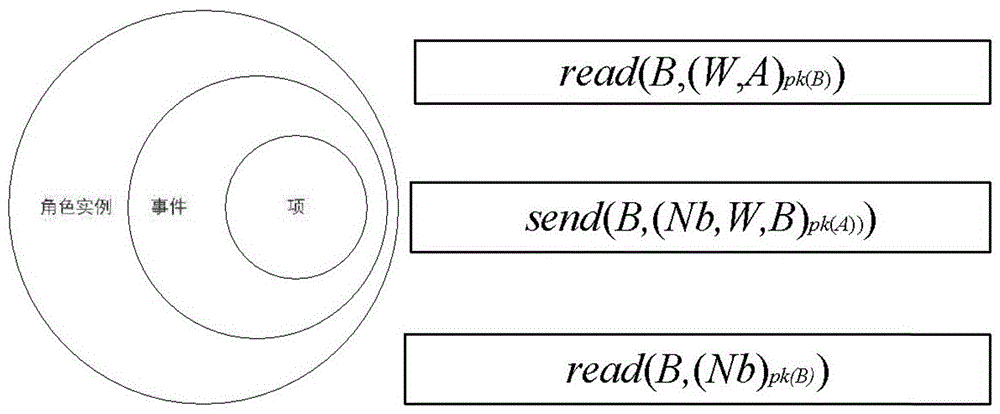
The invention belongs to the technical field of information security, and discloses a cryptographic protocol verification method. The method comprises: in a set network environment, giving a cryptographic protocol; describing a cryptographic protocol according to the grammar and semantics of the dynamic cognitive logic; establishing a behavior model according to behavior characteristics involved in the cryptographic protocol to accurately describe protocol behaviors and a behavior execution process, wherein the protocol behavior execution process is a protocol operation process, and the process is also a process of completely formalizing the protocol; modeling a target of the cryptographic protocol, and describing a sub-target; determining whether the protocol meets the safety target or not according to analysis of the behavior model, if so, ending the protocol, and indicating that the protocol is safe. According to the invention, knowledge owned by participants in the protocol is clearly described, and the logic expression method can accurately describe each step of protocol execution; and meanwhile, the behavior model is described simply and clearly, so that the proving process is rigorous and perfect.
Owner:SOUTHWEST UNIVERSITY
Attribute-driven security protocol symbolization model detection method and system
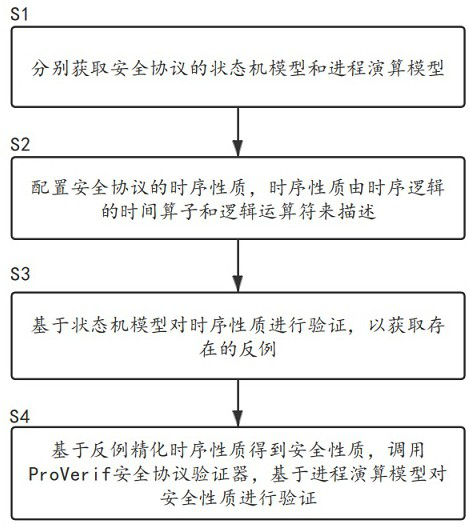
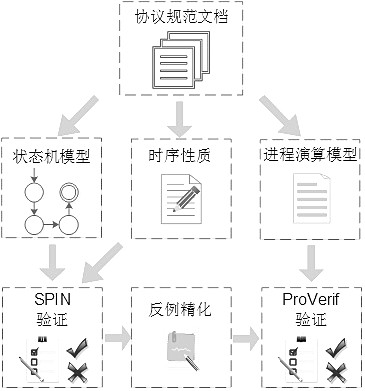
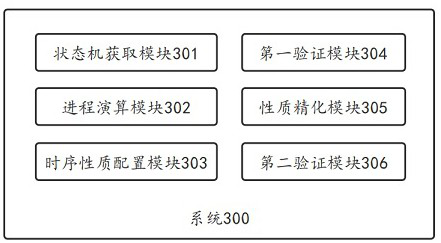
ActiveCN112818569AImplementing Automatic Formal VerificationSolving the problem of spurious counterexamplesDigital data protectionDesign optimisation/simulationSecurity propertiesSequential logic
The invention provides an attribute-driven security protocol symbolization model detection method and system and a medium. The method comprises the following steps: S1, respectively acquiring a state machine model and a process calculation model of the security protocol; S2, configuring a time sequence property of the security protocol, wherein the time sequence property is described by a time operator and a logic operator of time sequence logic; S3, verifying the time sequence property based on the state machine model to obtain an existing counter example; and S4, refining the time sequence property based on the counter example to obtain a security property, calling a ProVeif security protocol verifier, and verifying the security property based on the process calculation model. According to the method, the correctness of traditional model detection in the aspect of security protocol time sequence verification can be improved, the condition of false counter examples is effectively avoided, and the problem that a security protocol formal verification tool cannot perform time sequence modeling and analysis is solved.
Owner:军事科学院系统工程研究院网络信息研究所
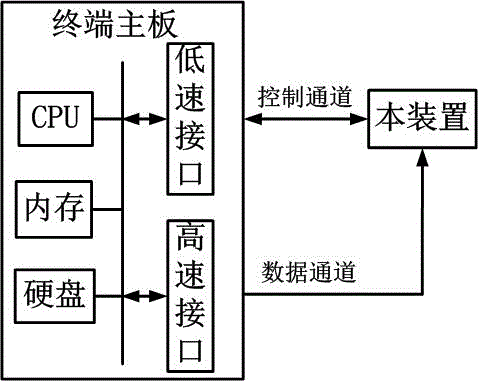
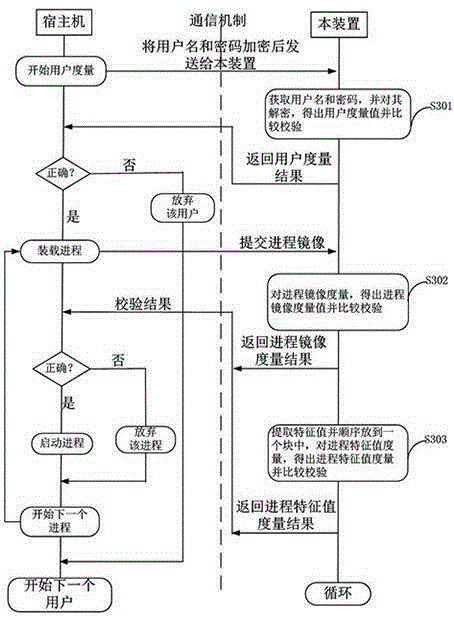
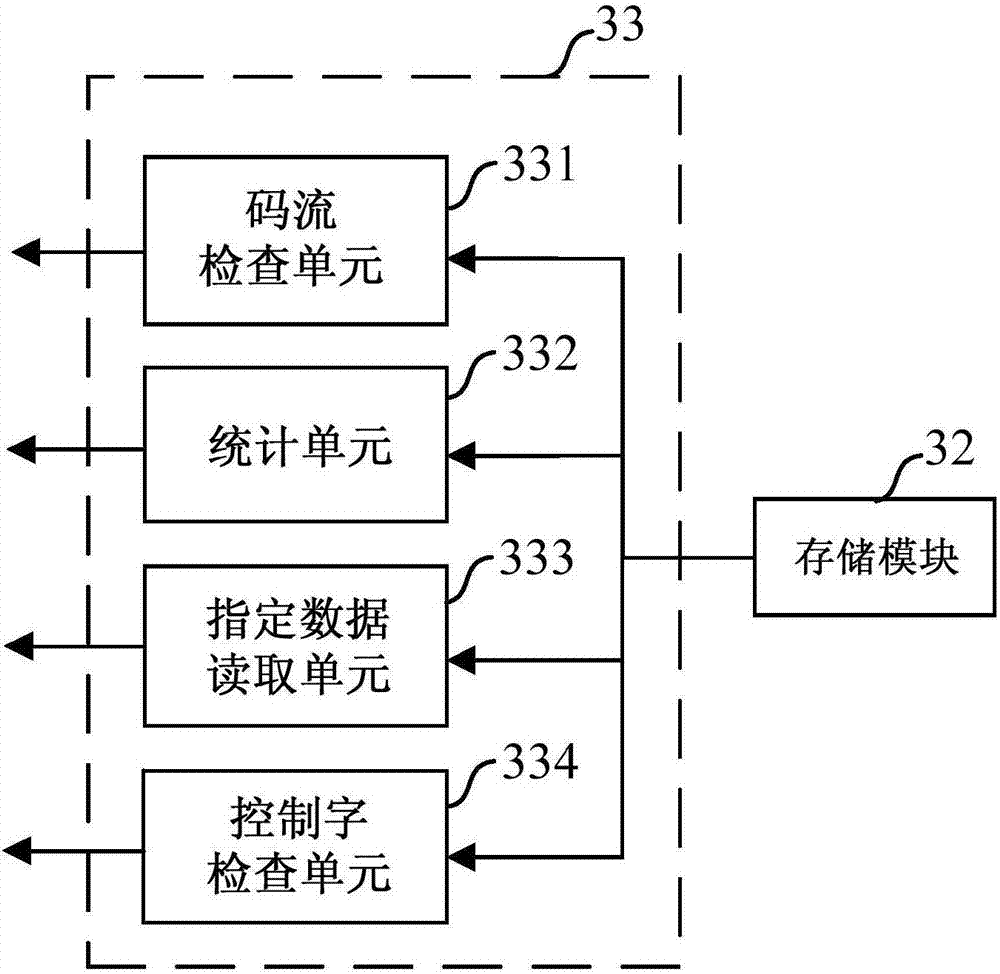
Encryption module and process trusted measurement method
The invention relates to a trusted computing technology, in particular to an encryption module and a process trusted measurement method. The encryption module includes interfaces, an algorithm module, a protocol verification module, a process verification module, and a storage module. The encryption module is mainly arranged on a terminal main board of a host machine such as a PC terminal or a mobile terminal, and is used for performing trusted measurement on an application process of a host system, and monitoring the integrity of the application process by verification and comparison of the a process user measurement value, a process image measurement value, and a process feature measurement value. The host machine uses the verification and comparison result of the process measurement value as a basis so as to determine whether a process is loaded or operated, virus processes and virus infection processes cannot pass trusted measurement and will not be loaded, processes which are infected by a virus will be stopped, and virus spread and attacks can be avoided.
Owner:深圳耀东安全科技有限公司
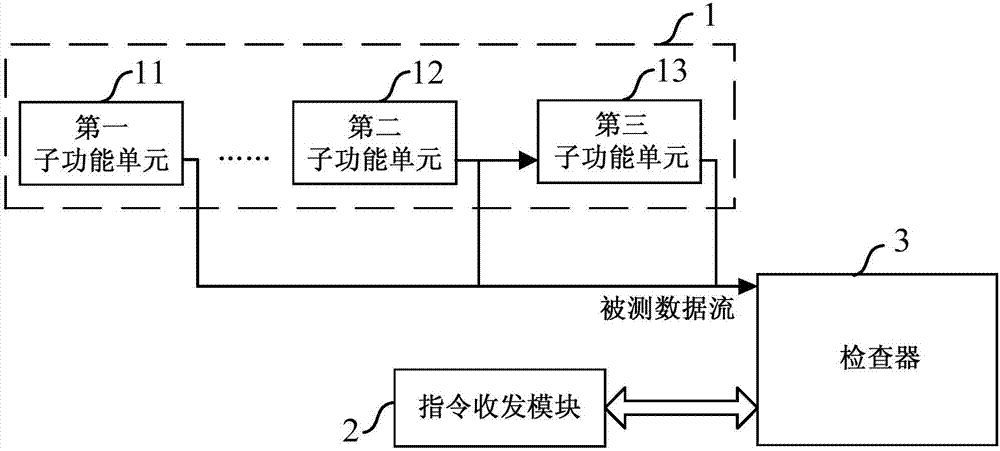
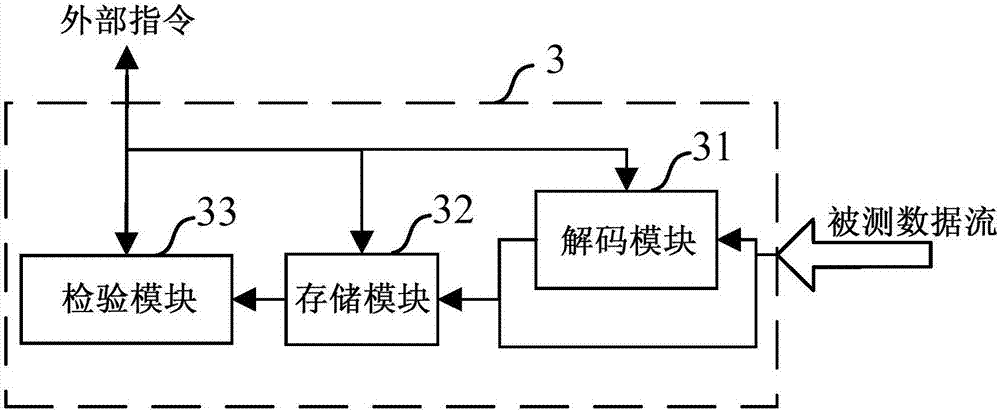
Checker based on SERDES protocol verification and functional verification system and method
ActiveCN106991027AIncrease flexibilityImprove the reusability of different designsError detection/correctionData streamNetwork packet
The invention provides a checker based on SERDES protocol verification and a functional verification system and method. The checker comprises a design module to be checked, an instruction receiving and sending module for sending instructions, a decoding module for decoding a coded data stream to be checked, a storage module for storing non-coded data, and a check module for reading the non-coded data and conducting functional verification. The method includes the steps that a data stream to be checked is received, if the data stream is coded data, decoding is conducted to obtain non-coded data and control word information contained in the code stream is output, and if the data stream is non-coded data, the data stream is directly received; the non-coded data is stored; the non-coded data is read, and functional verification is conducted on the non-coded data according to an external instruction. The checker can be reused in the data output port of any design module to be checked, supports verification of various code stream sequences or data packages in different frame formats and supports verification of coded / non-coded functional modules, the verification flexibility and different-design reusability are improved, the cost is reduced, and the function coverage of verification is increased.
Owner:SHANGHAI ADVANCED RES INST CHINESE ACADEMY OF SCI +1
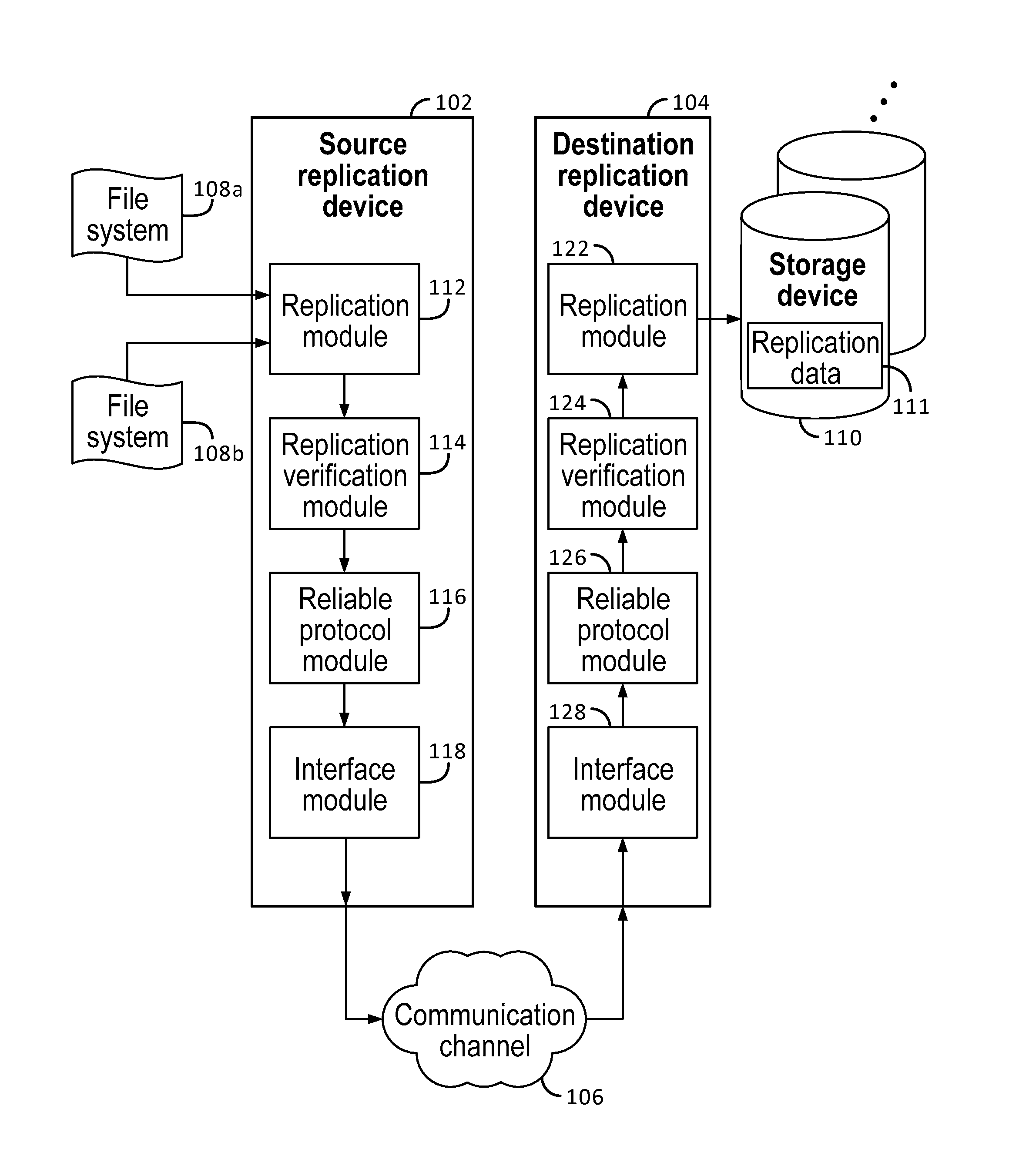
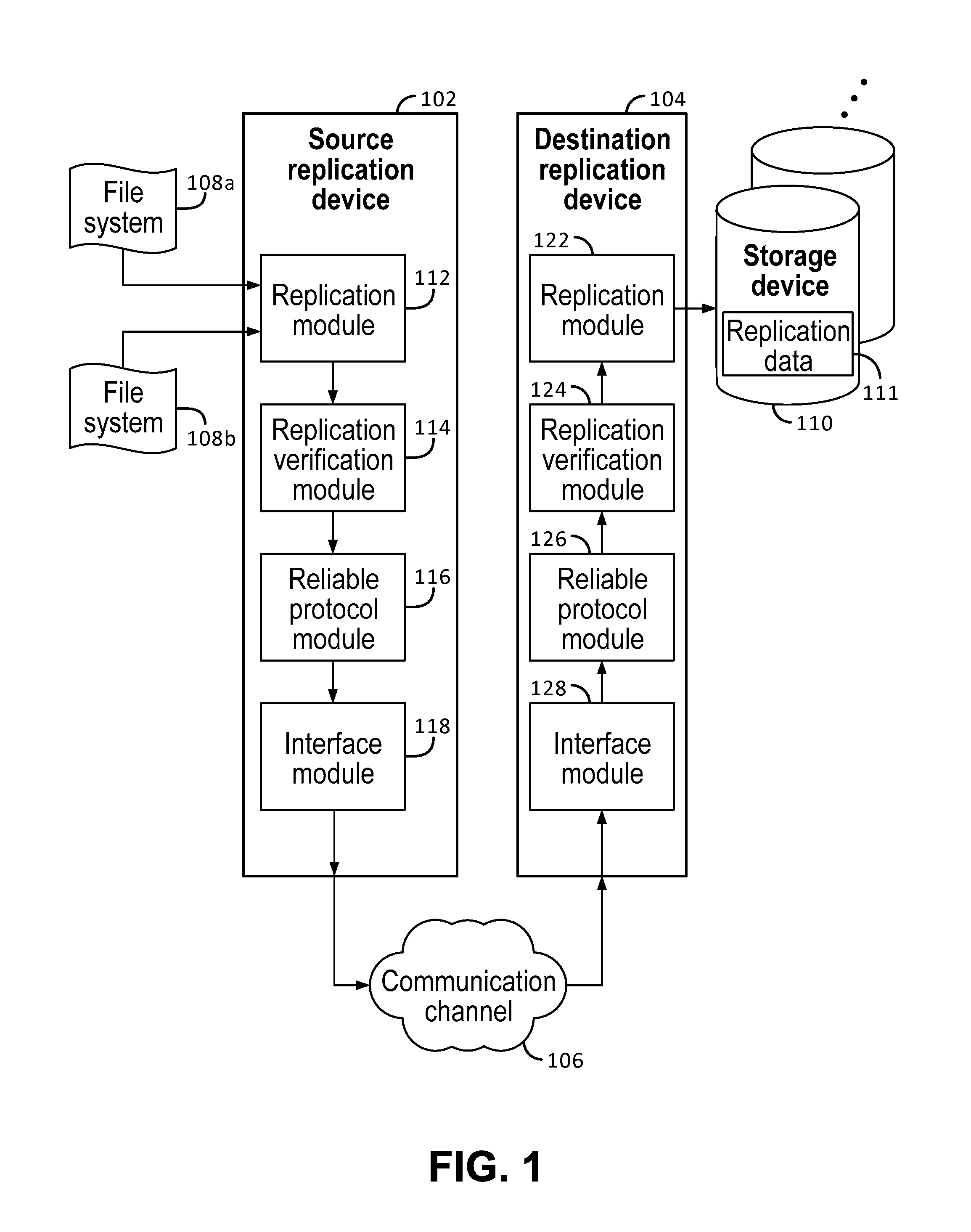
System and method for highly reliable data replication
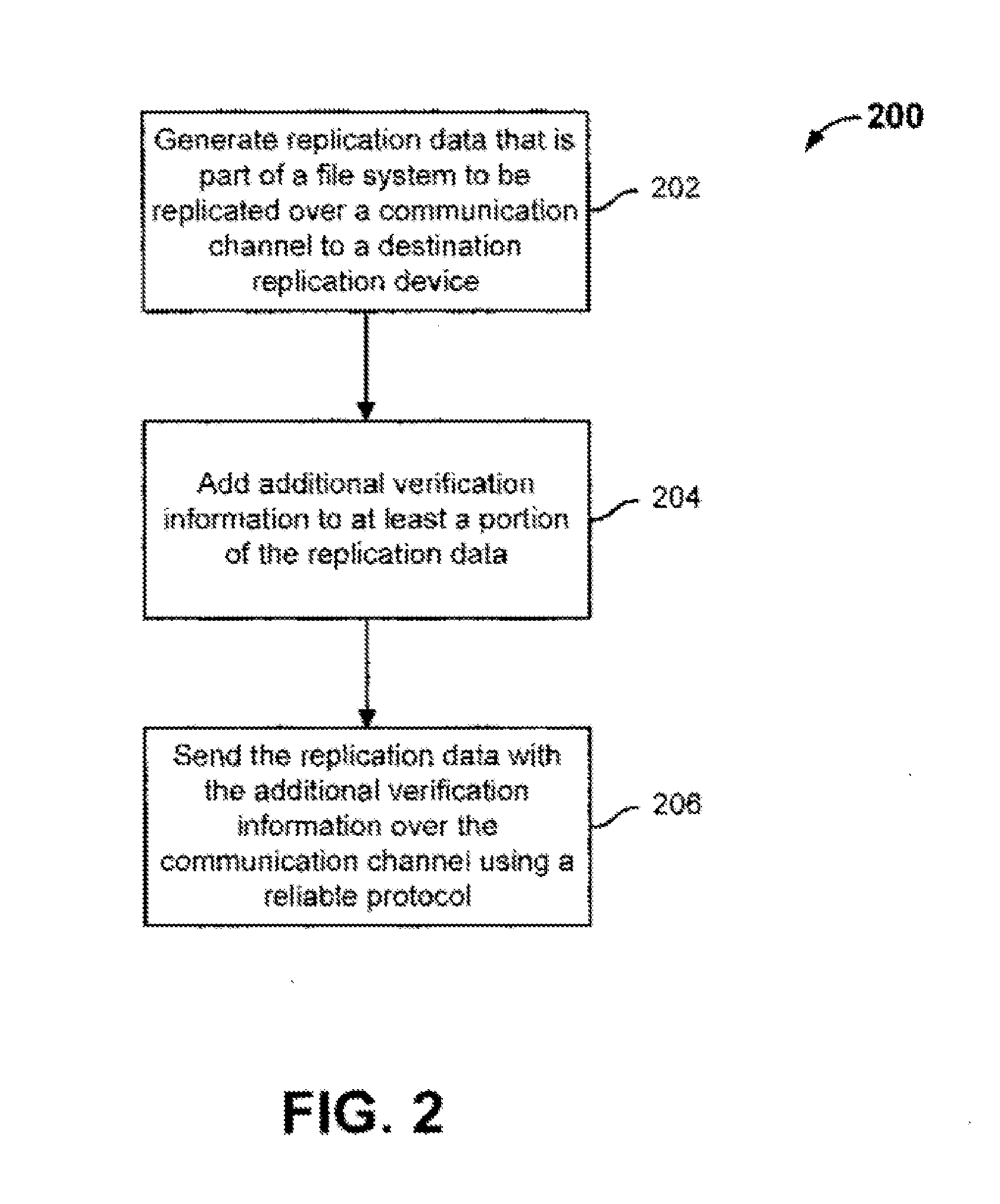
ActiveUS20120239778A1Data processing applicationsDigital data information retrievalFile systemData Corruption
Data replication includes generating replication data that is part of a replicated file system to be sent over a communication channel to a destination replication device; adding additional verification information to at least a portion of the replication data to prevent data corruption; and sending the replication data and the additional verification information over the communication channel to the destination replication device. The replication data with additional verification information is sent over the communication channel using a reliable protocol that allows the replication data to be verified by the reliable protocol at the destination replication device. The reliable protocol is a protocol capable of detecting most but not all data corruption introduced by the communication channel. The additional verification information includes information for verifying that replication data sent using the reliable protocol does not include data corruption that was introduced by the communication channel and undetected by the reliable protocol.
Owner:EMC IP HLDG CO LLC
Universal receiving method of communication data packets of online monitoring device
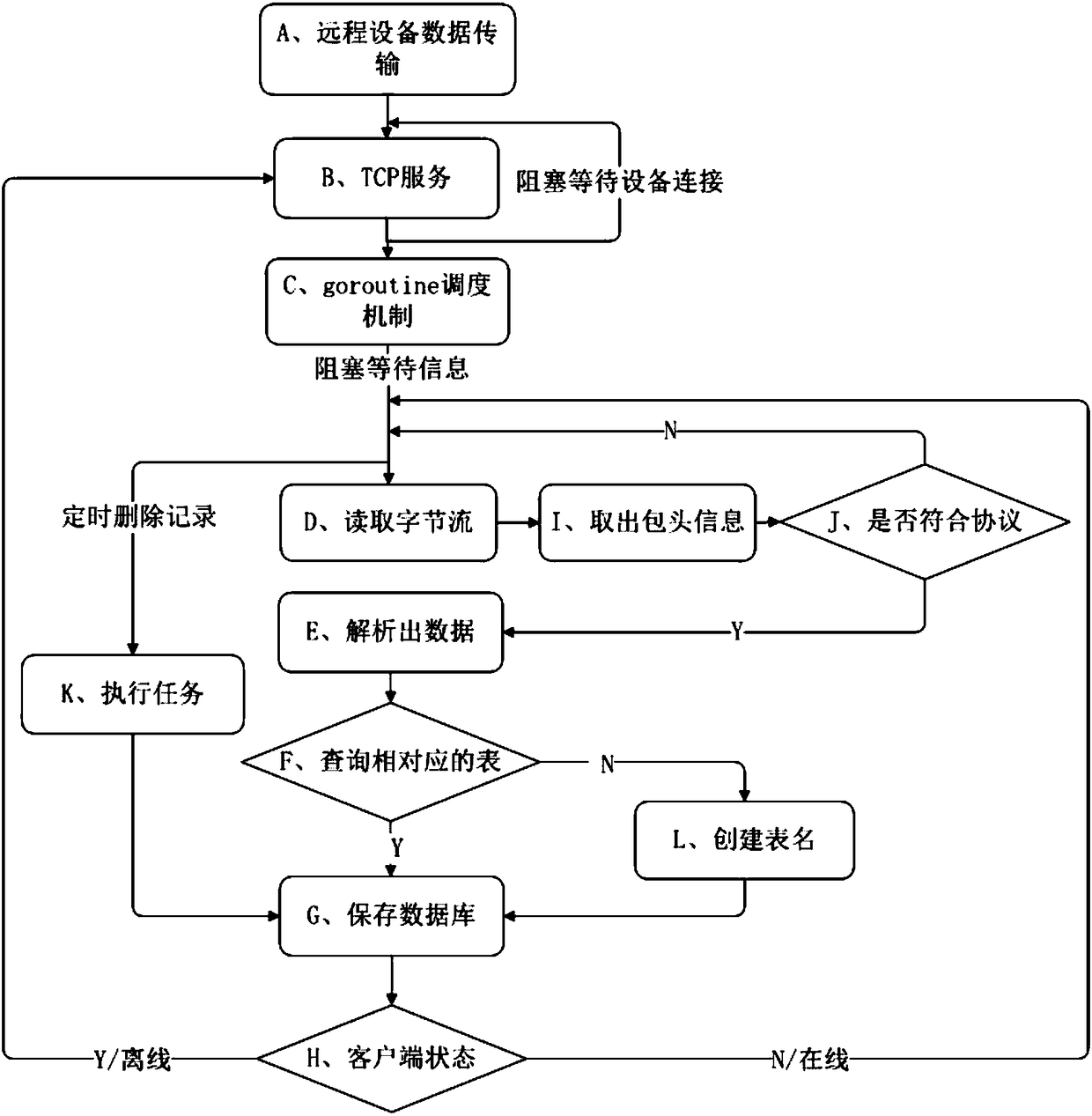
The invention discloses a universal receiving method of communication data packets of an online monitoring device. The method comprises the following steps: blocking TCP service, and waiting for the connection of a remote device; opening a goroutine mechanism, blocking the reading of data packet information, parsing a data packet, performing data transmission protocol verification, parsing data, performing database table check, and storing the data; and executing a timed task, and destroying an offline client.
Owner:广州恩业电子科技有限公司
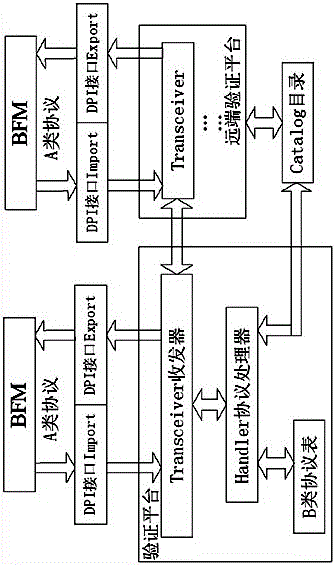
BFM (Bus Function Model)-based method for SystemVerilog to build protocol verification platform
ActiveCN105930299AEasy to handleImprove throughputDigital computer detailsElectric digital data processingArray data structureTransceiver
The invention discloses a BFM (Bus Function Model)-based method for SystemVerilog to build a protocol verification platform. The method comprises the following implementation process: building a Transceiver which is in charge of transceiving and disassembling / assembling an A-class protocol message; building a Catalog structure which is in charge of recording consistency information; realizing a protocol table model which is in charge of realizing protocol conversion; and building a Handler which is in charge of processing the protocol. The method simplifies a protocol processing process, adopts a one-by-one way, does not relate to a resource dispatching problem, improves protocol conversion communication among multiple clumps, and fully utilizes the verification characteristics of sv, the handling capacity of the protocol message is enlarged by a queue and a dynamic associative array, the Catalog structure is visible on the whole platform, and communication between the Transceiver and the BFM adopts a simple DPI interface.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
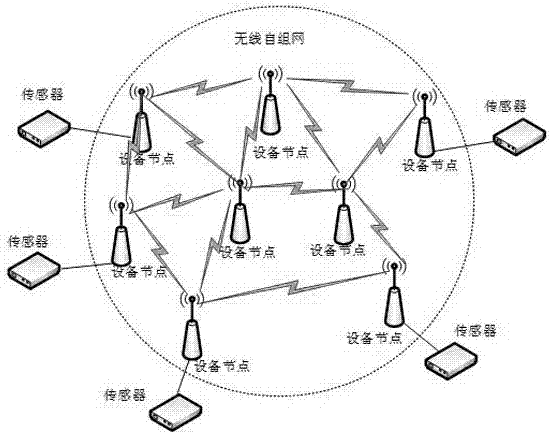
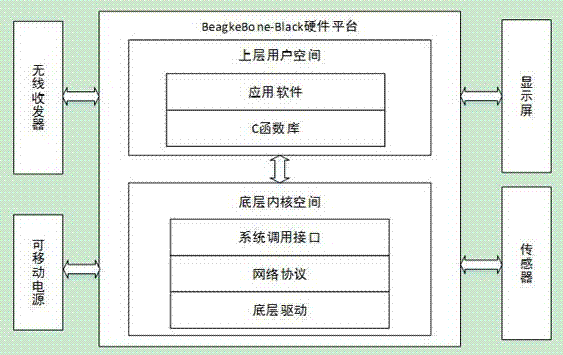
Ad-Hoc routing protocol verification method based on BeagleBone-Black
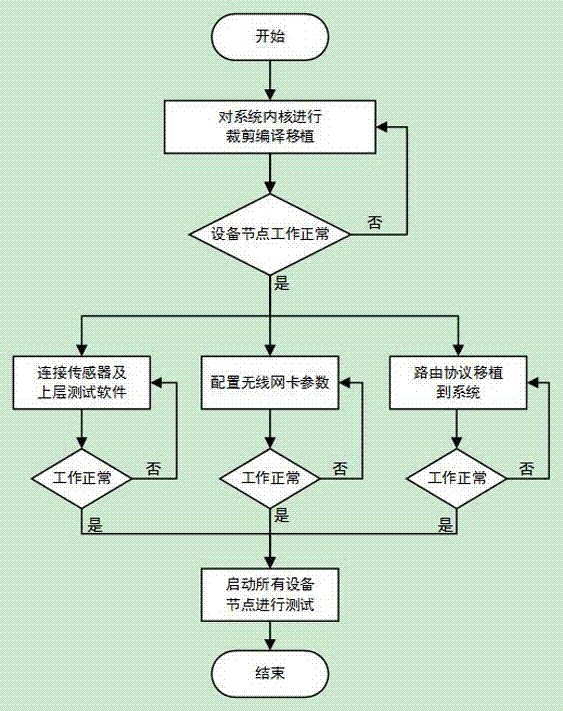
InactiveCN107086957AWork lessQuickly know the end-to-end delayData switching networksPacket loss rateDependability
The invention provides an Ad-Hoc routing protocol verification method based on BeagleBone-Black. The method comprises the following steps that step 1 the system core of a useless module component is removed to be transplanted to the BeagleBone-Black system of each equipment node; step 2 a routing protocol requiring verification is transplanted to the system, and external network card parameters are configured so that the node is enabled to normally receive and transmit data; step 3 multiple equipment nodes are started to operate the routing protocol in the outdoor onsite scene, the working mode is configured as Ad-Hoc, the external sensor of the system also searches signals, the customized software is started on one node to search and forward a target host in the network, and the end-to-end transmission delay and the packet loss rate of the data are observed at the target host side through the customized software; and step 4 all the equipment nodes are started to perform testing so as to obtain the verification result. With application of the technical scheme, the equipment nodes can be brought to the onsite scene so that the authenticity and the reliability of the experimental data can be further enhanced, and the system is enabled to have great application prospect by the simple and rapid networking mode.
Owner:GUILIN UNIV OF ELECTRONIC TECH
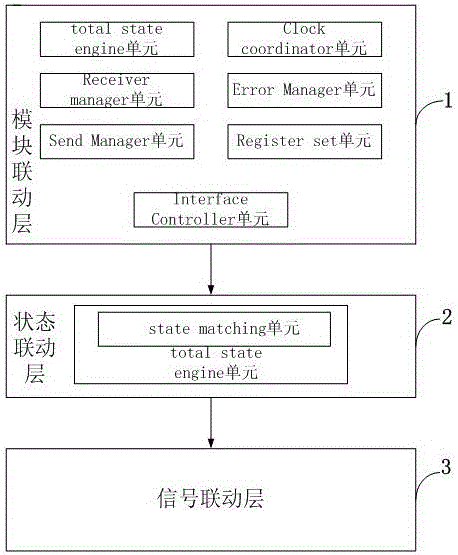
CAN FD communication protocol verification system
InactiveCN106209841AGuaranteed CompatibilityGuaranteed stabilityTransmissionComputer moduleDependability
The invention discloses a CAN FD communication protocol verification system. The system comprises a module linkage layer, a state linkage layer and a signal linkage layer. According to the system, a CAN FD soft kernel that realizes a whole protocol frame by a three-layer architecture model is adopted, so that a protocol can be conveniently improved for a specific application need while complete compatibility with a standard CAN FD protocol is ensured; the stability of the whole CAN FD protocol is guaranteed and any property of the CAN FD protocol can be quickly modified through a VHDL, so that the CAN FD protocol can be immediately verified through the verification system; an FPGA-based CAN FD star-type electric signal switching node soft kernel is originally created, so that transmission mediums such as twisted-pair wires, optical fibers and the like are removed, the verification cost is reduced, the verification process is simplified, and the reliability of a verification result is improved; and CAN FD controller nodes can be directly connected with CAN FD star-type electric signal switching nodes through pins.
Owner:SICHUAN UNIV
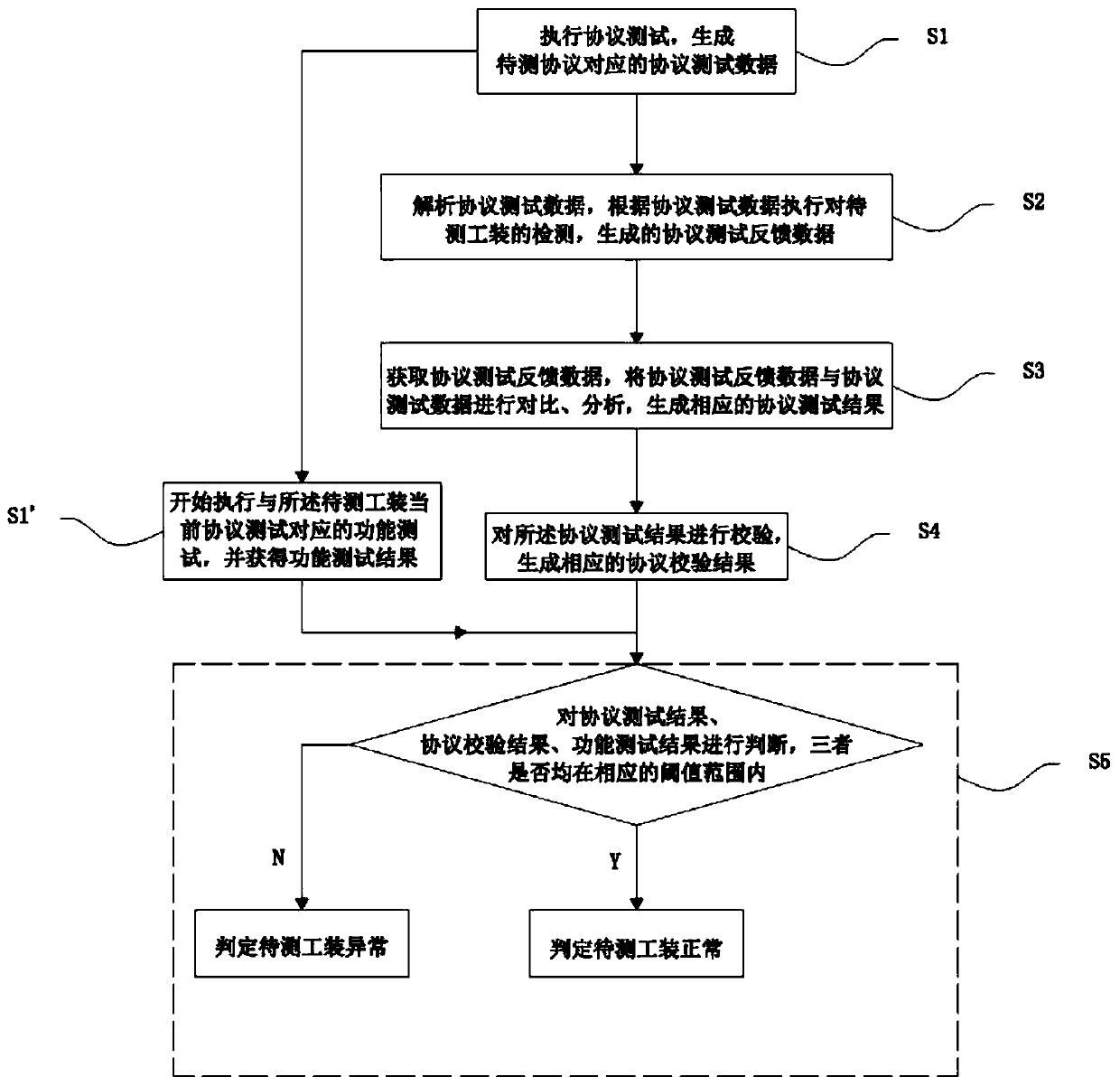
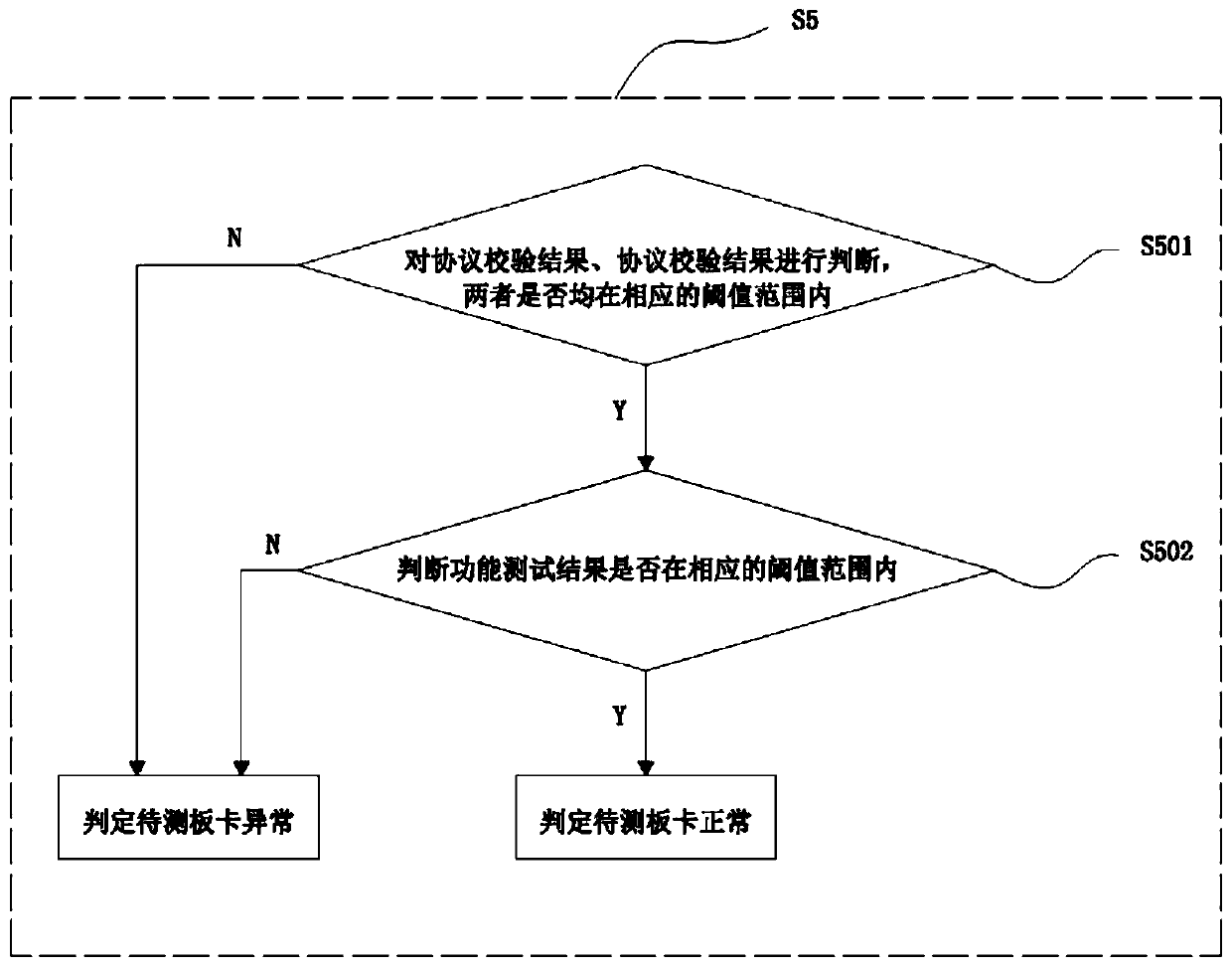
Automatic tool testing method, equipment and system
InactiveCN109831348AReduce the burden onAvoid manual operationStructural/machines measurementData switching networksComputer hardwareFunctional testing
The embodiment of the invention discloses an automatic tool test method, device and system, and the method comprises the following steps: executing a protocol test, and generating protocol test data corresponding to a to-be-tested protocol; analyzing the protocol test data, detecting the to-be-tested tool according to the protocol test data, and generating protocol test feedback data; obtaining protocol test feedback data, comparing the protocol test feedback data with the protocol test data, and analyzing the protocol test feedback data to generate a corresponding protocol test result; verifying the protocol test result to generate a corresponding protocol verification result; when the protocol test data corresponding to the to-be-tested protocol is generated, starting to execute a function test corresponding to the current protocol test of the to-be-tested tool, and obtaining a function test result; and judging the protocol test result, the protocol verification result and the function test result, and judging that the to-be-tested tool is normal if the protocol test result, the protocol verification result and the function test result are all within corresponding threshold ranges.
Owner:北京航天晨信科技有限责任公司
Extensible protocol validation
ActiveUS8356332B2Multiple digital computer combinationsProgram controlNetwork packetSpecification language
A method comprises operations for receiving a binary data structure including a portion representing a protocol validation specification expressed in a respective protocol validation specification language and for receiving a security policy rule having an action part specifying that the binary data structure is to be used for verifying that application protocol payload of network packets complies with the protocol validation specification. After receiving the binary data structure and the security policy rule, an operation is performed for verifying that application protocol payload of received network packets complies with the protocol validation specification. Such verifying is initiated in response to determining that the security policy rule applies to the received network packets and such verifying includes validating the application protocol payload of the received network packets against the binary data structure.
Owner:ALCATEL LUCENT SAS
Security protocol verification method taking attacker as center
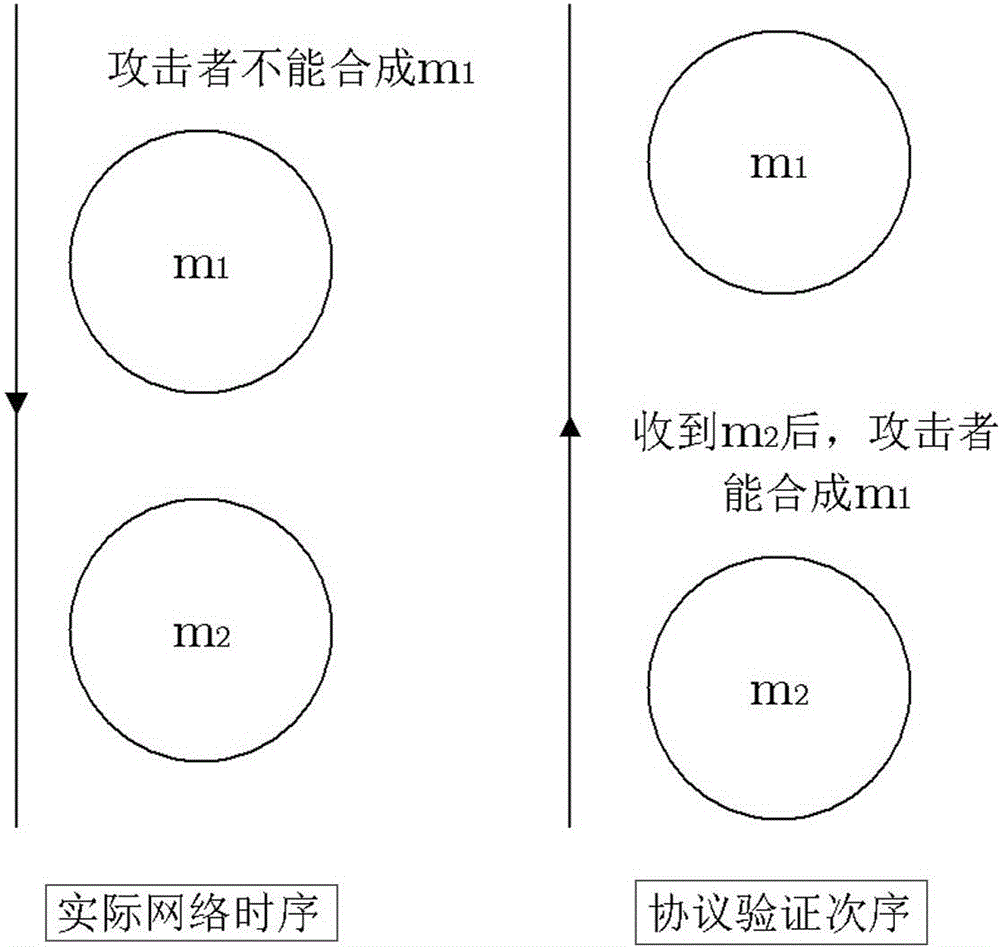
InactiveCN106411940AReduced number of intermediate statesReduce the numberTransmissionComputer hardwareProtocol design
The invention belongs to the field of computer security protocol verification methods, and specifically relates to a security protocol verification method taking an attacker as the center. The security protocol verification method comprises the steps of 1, setting an initial state according to a protocol verification target; 2, extracting an event to be handled in the state, sequentially judging whether the current state and the event conform to TRules or not; and performing judgment on states in a Resultstate, wherein if a certain state that attacker knowledge contains parameters required to be kept secret of a protocol exists, the state is secrecy abnormal state, and if a certain state that a protocol session scene is abnormal exists, the state is an authentication abnormal state, otherwise, the protocol design is secure. The security protocol verification method aims to consider time sequence contradiction in the state extension process, a back tracking mechanism is introduced into state extension, extended branches of invalid states do not appear in the state searching process, and the number of intermediate states is reduced; and state extension is driven by requirements of the attacker, the mode is not fixed, the number of branches is less, and the number of state spaces is reduced.
Owner:THE PLA INFORMATION ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com