Automatic protocol recognition method and system
A protocol identification and protocol technology, applied in the network field, can solve the problems of false negatives, false positives of IDS/IPS products, and inability to correctly identify the protocol type to which the packets belong, and achieve the effect of high accuracy and fast protocol identification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
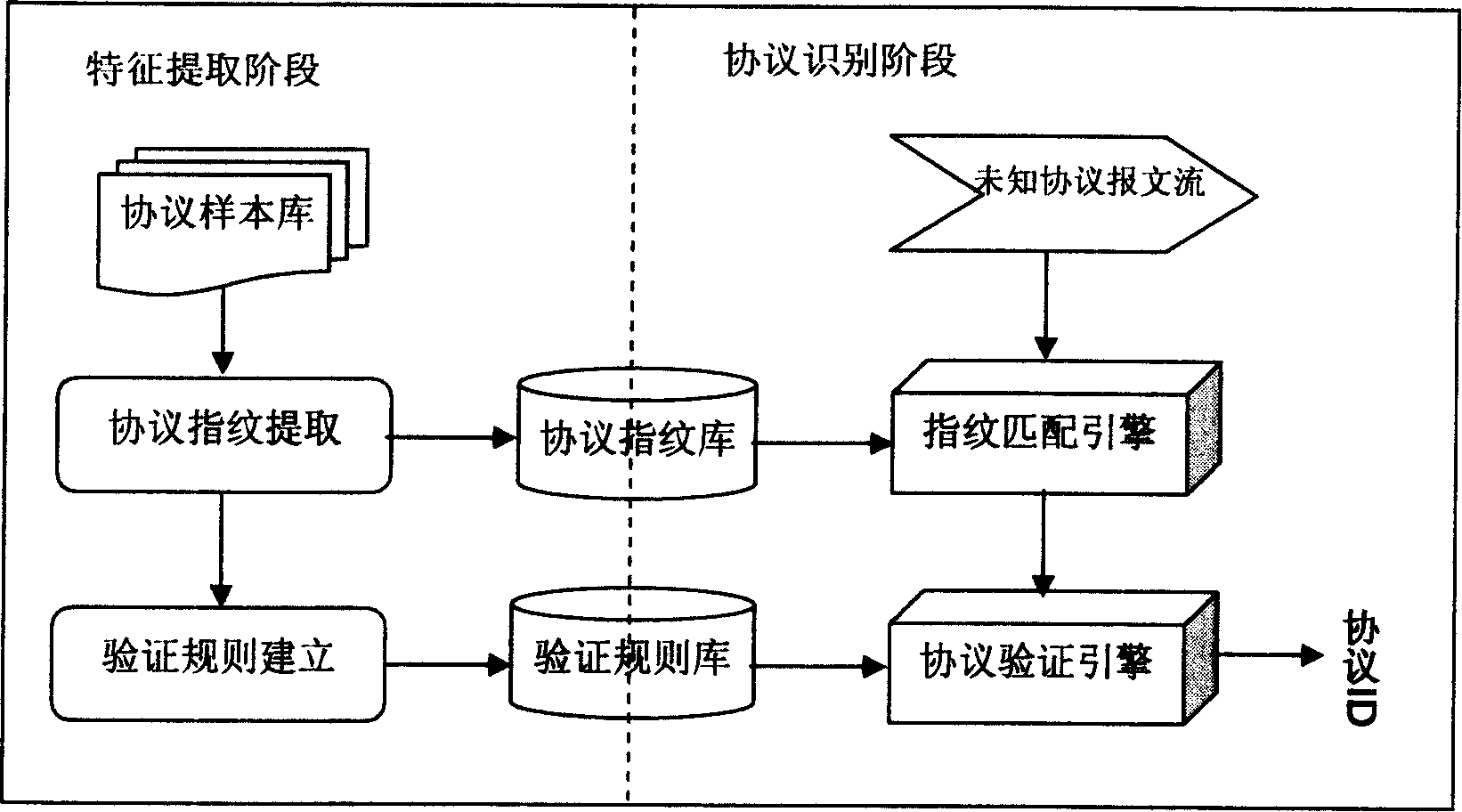
[0039] Embodiment 1; The protocol identification process method of the present invention comprises two working phases: early stage agreement sample feature extraction phase and online agreement identification phase, each phase step is as follows (see figure 1 ):
[0040] A. Protocol sample feature extraction stage;
[0041] According to the protocol fingerprint extraction method, the protocol fingerprint of this type of protocol is extracted from the protocol type sample (each type of protocol generally has multiple protocol fingerprints), and the corresponding verification rule set of this type of protocol is established.
[0042] The extracted protocol fingerprints and corresponding protocol verification rule sets are respectively stored in the protocol fingerprint library and the protocol verification rule library, which are used by the fingerprint matching engine and the protocol verification engine in the protocol identification stage.
[0043] B. On-line protocol identi...
Embodiment 2
[0064] Embodiment 2; The method for automatic protocol identification co-contains the following steps;
[0065] Protocol fingerprint extraction;
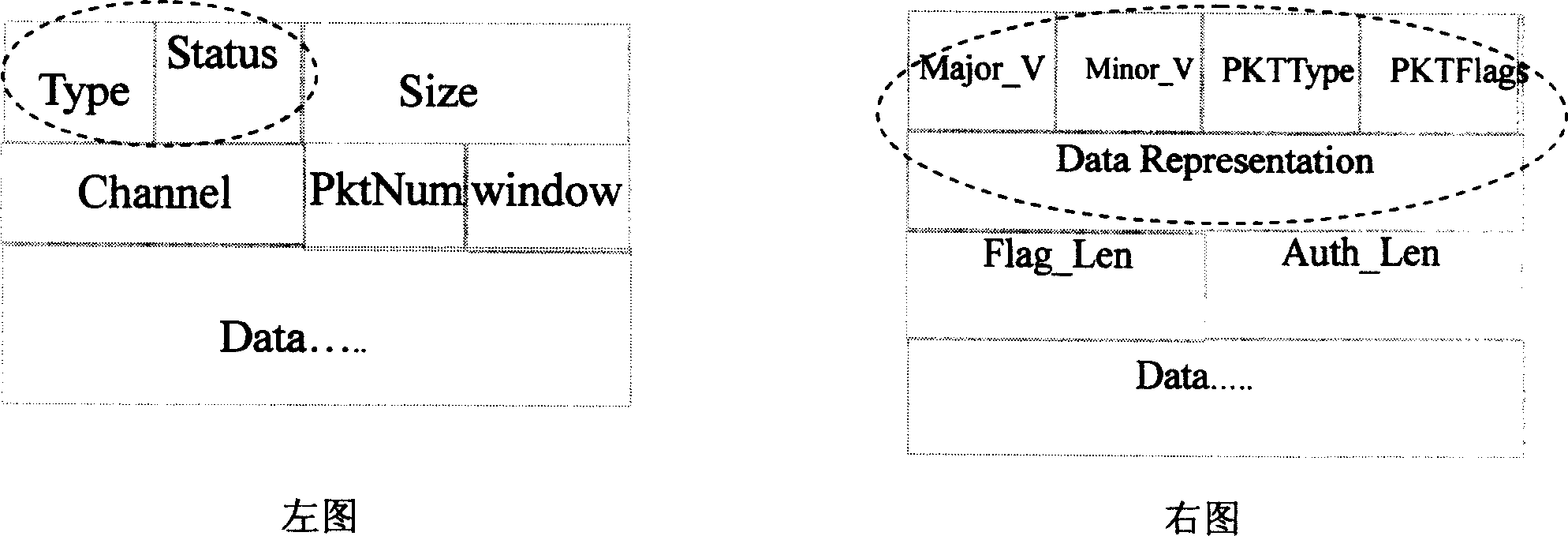
[0066] All protocols are divided into three categories: 1) text command format protocol; 2) fixed header format protocol; 3) no fixed format protocol. The fingerprint extraction methods of these three types of protocols are described below.
[0067] Text command format protocol;
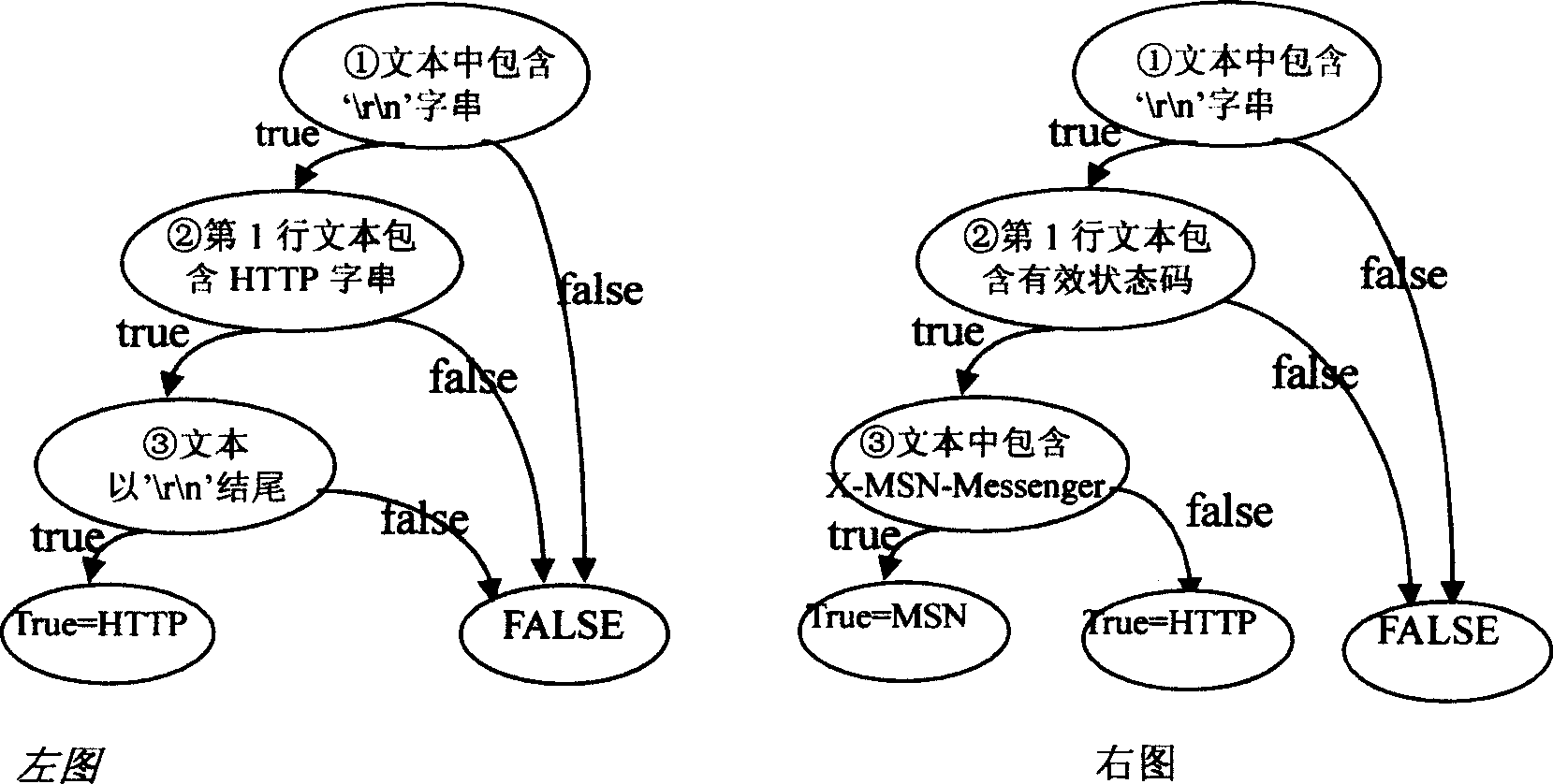
[0068] In the text command format protocol, all messages may be described in the form of {command + parameter}. The commands here include not only the usual protocol commands, but also the status code of the server response. There are many examples of text command format protocols, including POP3, SMTP, FTP, HTTP, etc. For such protocols, it is only necessary to extract protocol commands and protocol response status codes as protocol fingerprints. For example, for the HTTP protocol, the extracted HTTP protocol fingerprint set is {GET, POST, HEAD, HTTP / ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com