Patents
Literature
62results about How to "Non-reproducible" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
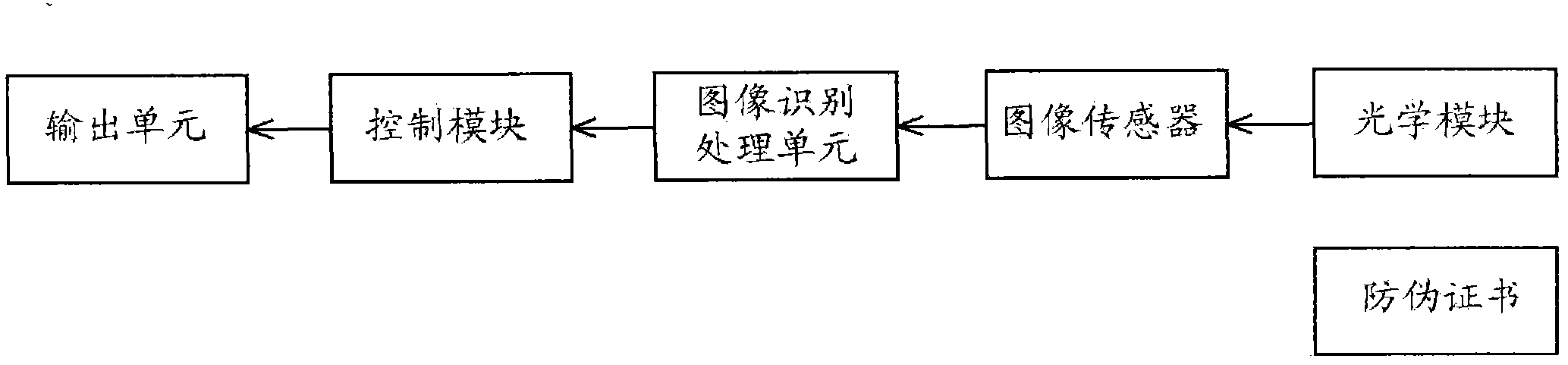
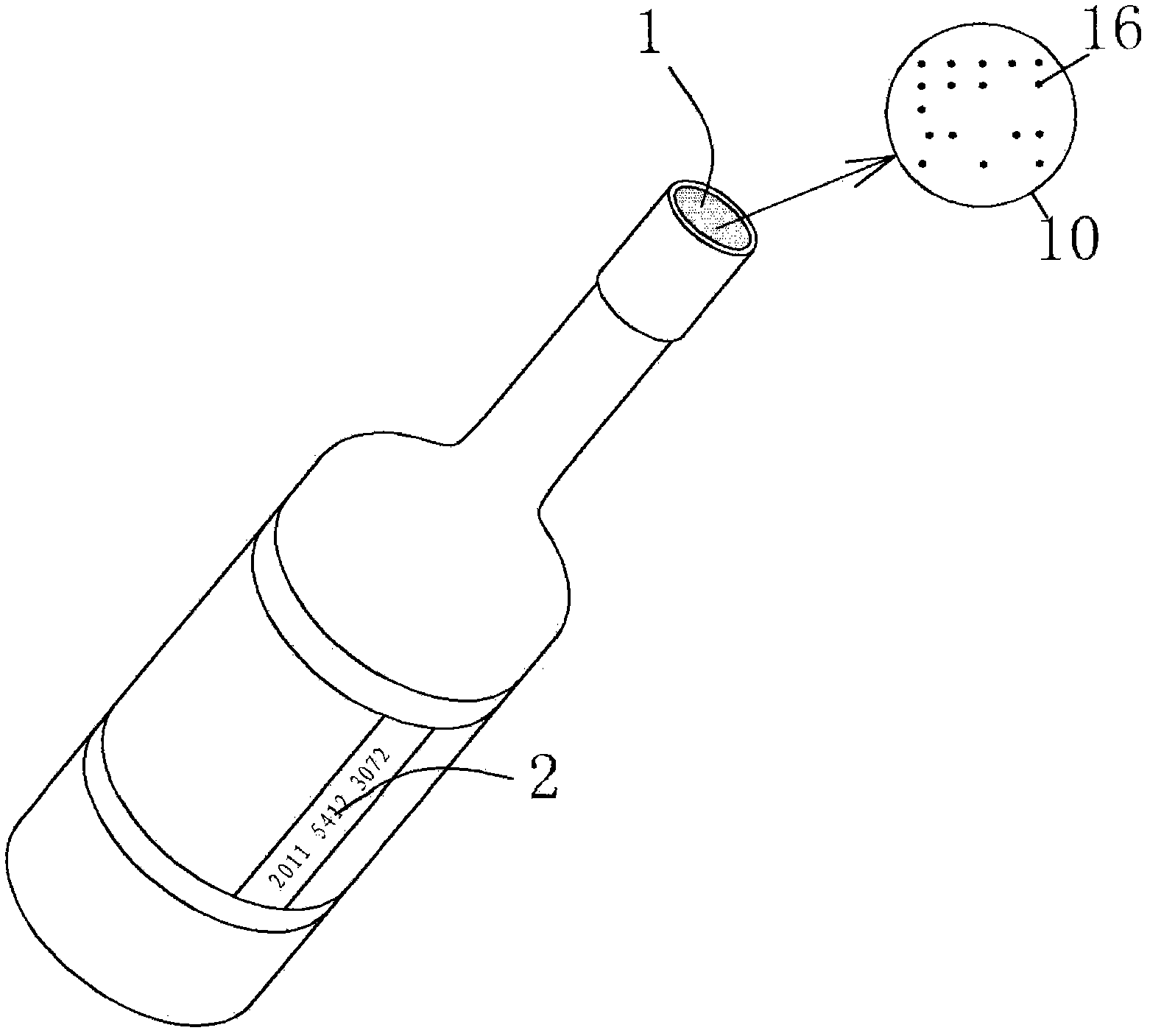
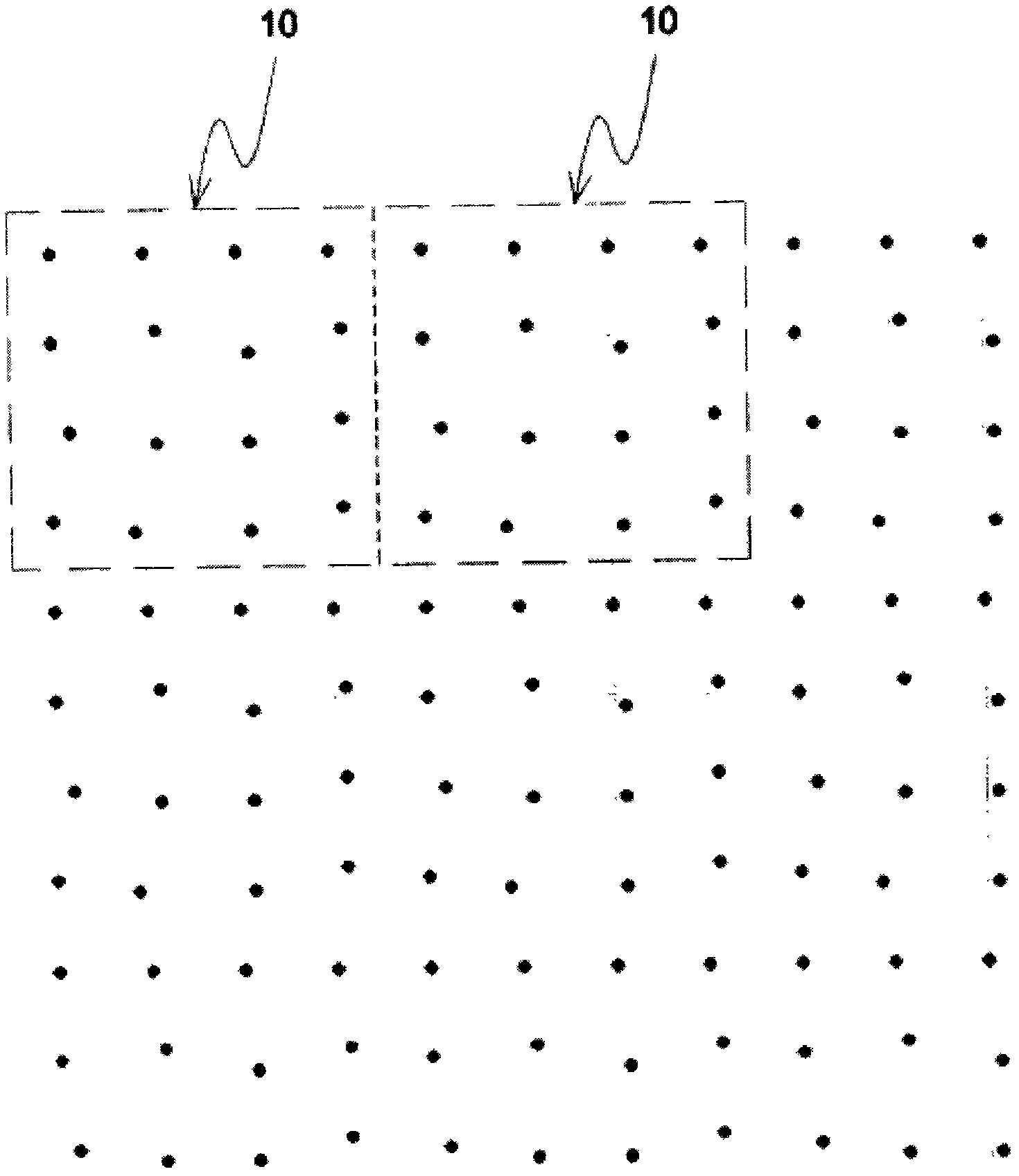
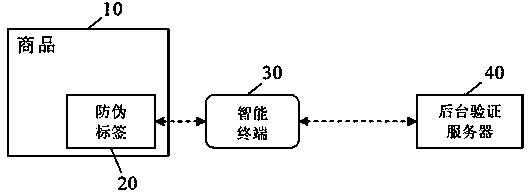
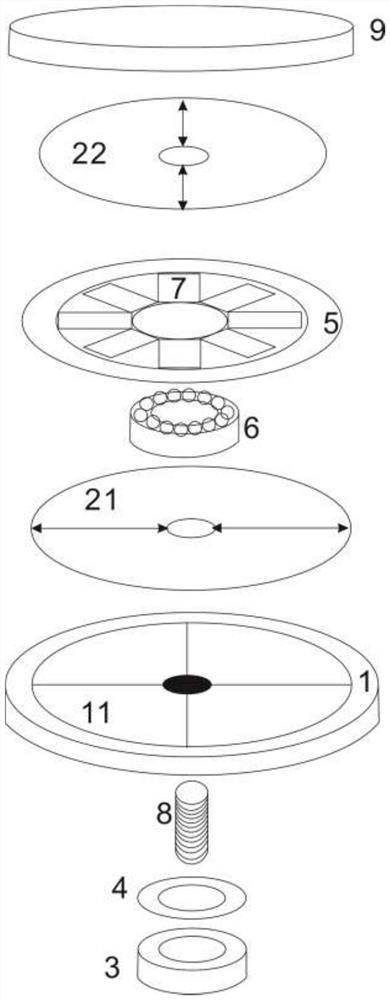
Construction verification method and device capable of verifying security two-dimensional code offline
ActiveCN106452756AEasy to useCannot be tampered withKey distribution for secure communicationUser identity/authority verificationInformation analysisEffective time
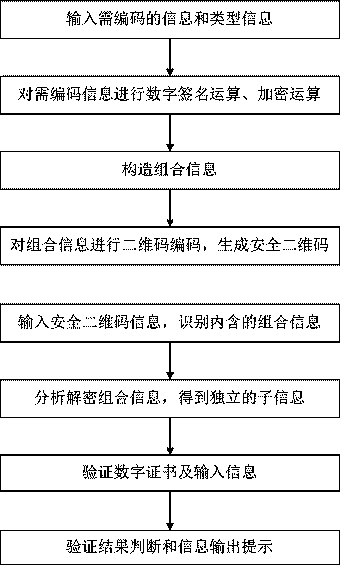
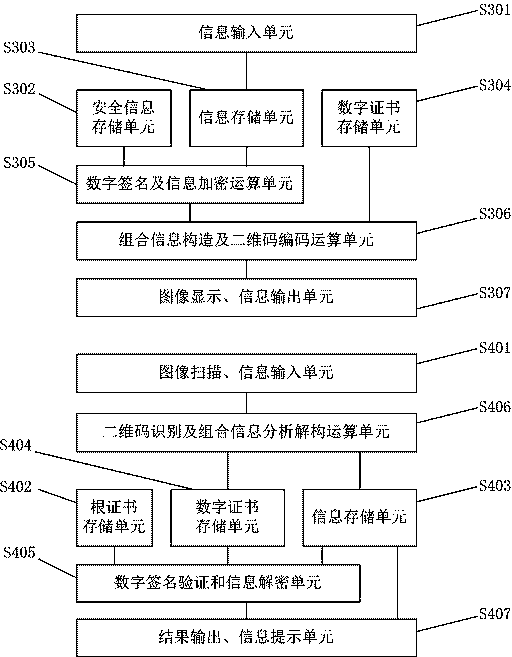
Embodiments of the invention provide a construction verification method and device capable of verifying a security two-dimensional code offline. The method comprises the following steps of inputting information that needs coding and type information, carrying out digital signature operation and encryption operation on the input information according to an information release type, constructing combination information, and encoding to generate a security two-dimensional code which can be verified off-line according to a two-dimensional code coding rule; inputting the information of the security two-dimensional code and identifying included combination information and type information, analyzing and decoding the combination information to obtain independent sub-information according to the type information of the two-dimensional code, and verifying digital certificate effectiveness information, a digital signature of the input information and an effective time limit of the input information; and if all verifications pass, showing that the offline verification of the security two-dimensional code is correct and the coding information source of the security two-dimensional code is credible, otherwise showing that the information release source of the security two-dimensional code is incredible. The method and the device have the beneficial effects that the security two-dimensional code cannot be tampered, counterfeited and denied, the public or private information can be released, and the integrity of the information of the security two-dimensional code and the authenticity of the source can be verified offline without a network connection.
Owner:王栋
Commodity anti-counterfeiting verification method
ActiveCN103295143ASolve the disadvantages of taking pictures and copyingTo achieve the purpose of real anti-counterfeitingCommerceValidation methodsComputer engineering
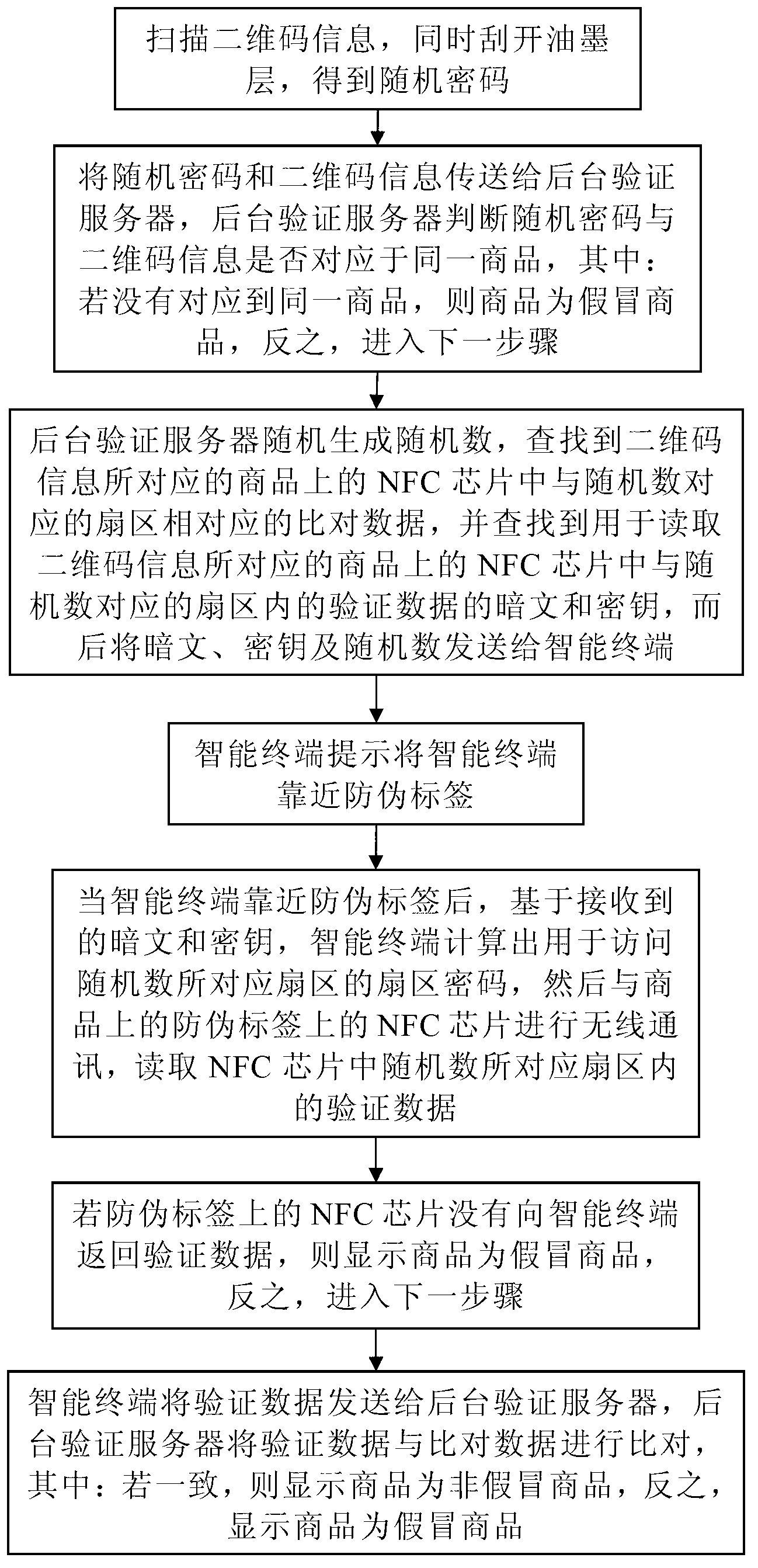
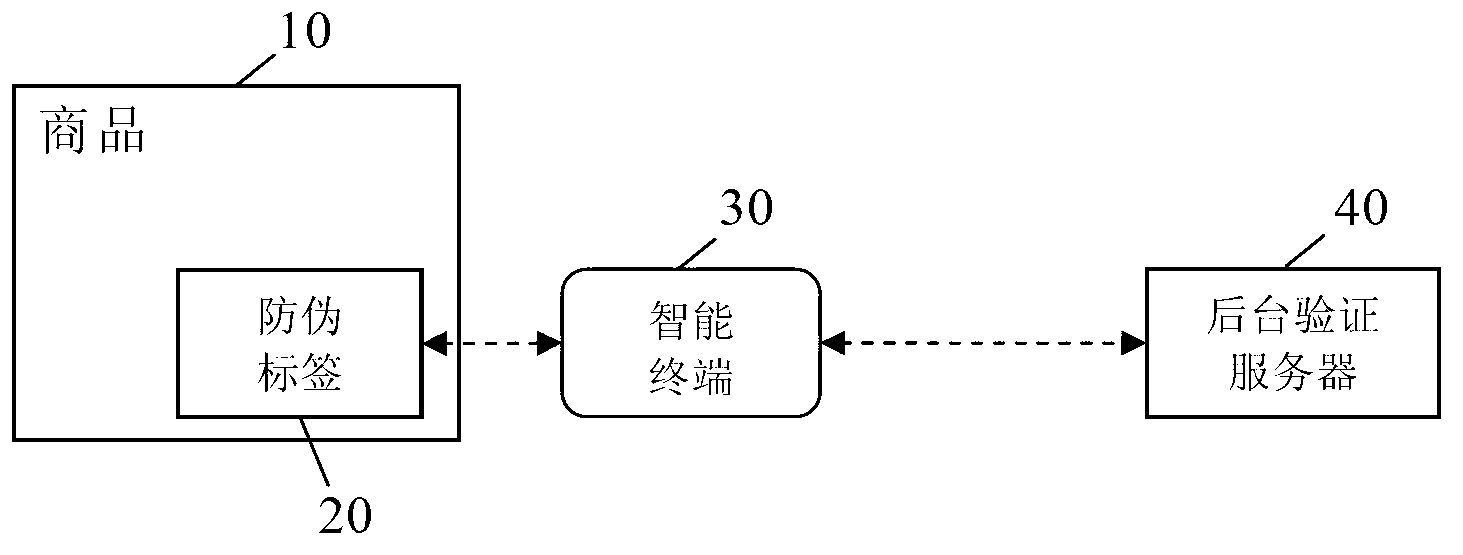
The invention discloses a commodity anti-counterfeiting verification method which includes: scanning two-dimensional codes, and opening an ink layer to obtain random ciphers; enabling a background verification server to judge whether the random ciphers and the two-dimensional codes correspond to the same commodity, judging the commodity to be fake if the random ciphers and the two-dimensional codes do not correspond to the same commodity and ending the verification, and otherwise entering the next step; enabling the background verification server to generate random numbers, referring to contrast data, dark patterns and secret keys and transmitting to an intelligent terminal; reminding the intelligent terminal to be close to an anti-counterfeiting label; after that, enabling the intelligent terminal to visit verification data in a sector area corresponding to the random numbers based on sector area ciphers calculated according to the dark patterns and the secret keys; judging the commodity to be fake if the intelligent terminal did not receive the data, ending the verification, and otherwise entering the next step; enabling the background verification server to compare the verification data with the contrast data, judging the commodity to be authentic if the verification data are in accordance with the contrast data, and otherwise judging the commodity to be fake and ending the verification. By means of the commodity anti-counterfeiting verification method, the actual anti-counterfeiting aim can be achieved through combination of various anti-counterfeiting technologies, and non-replicability, safety and reliability can be achieved.
Owner:重庆汉朗精工科技有限公司
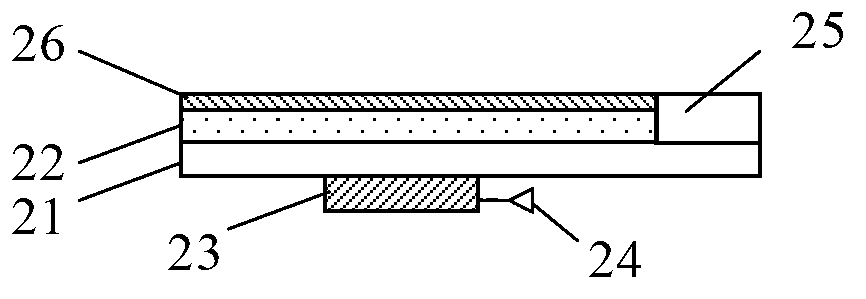
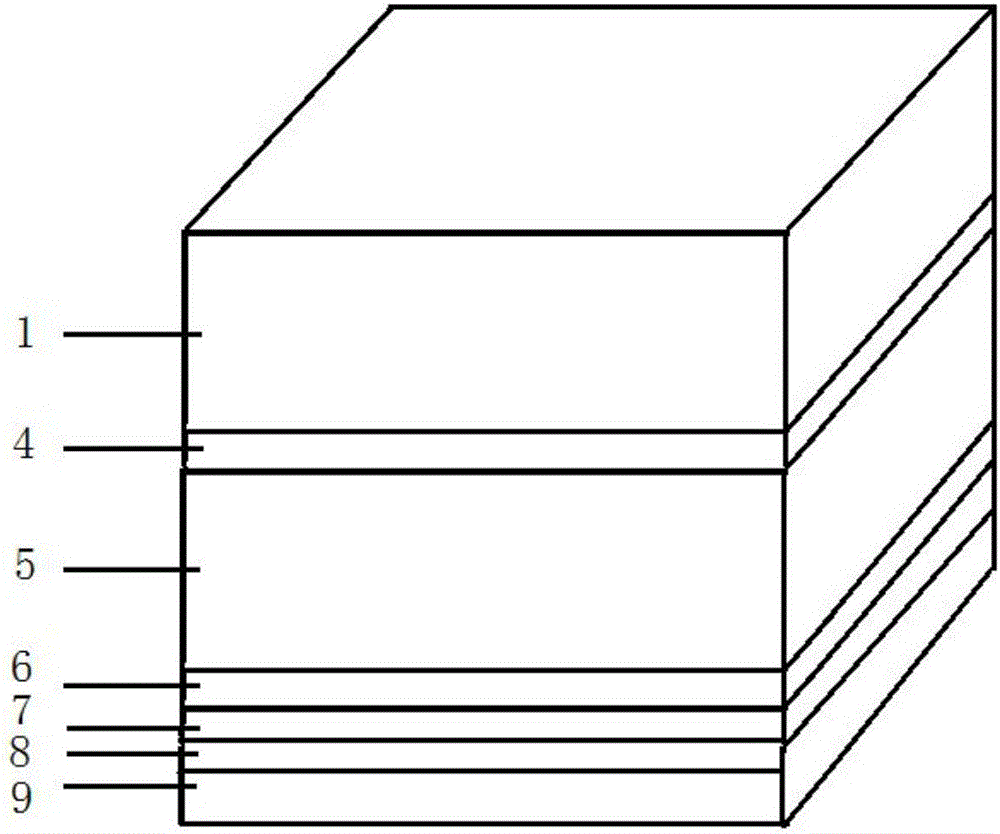
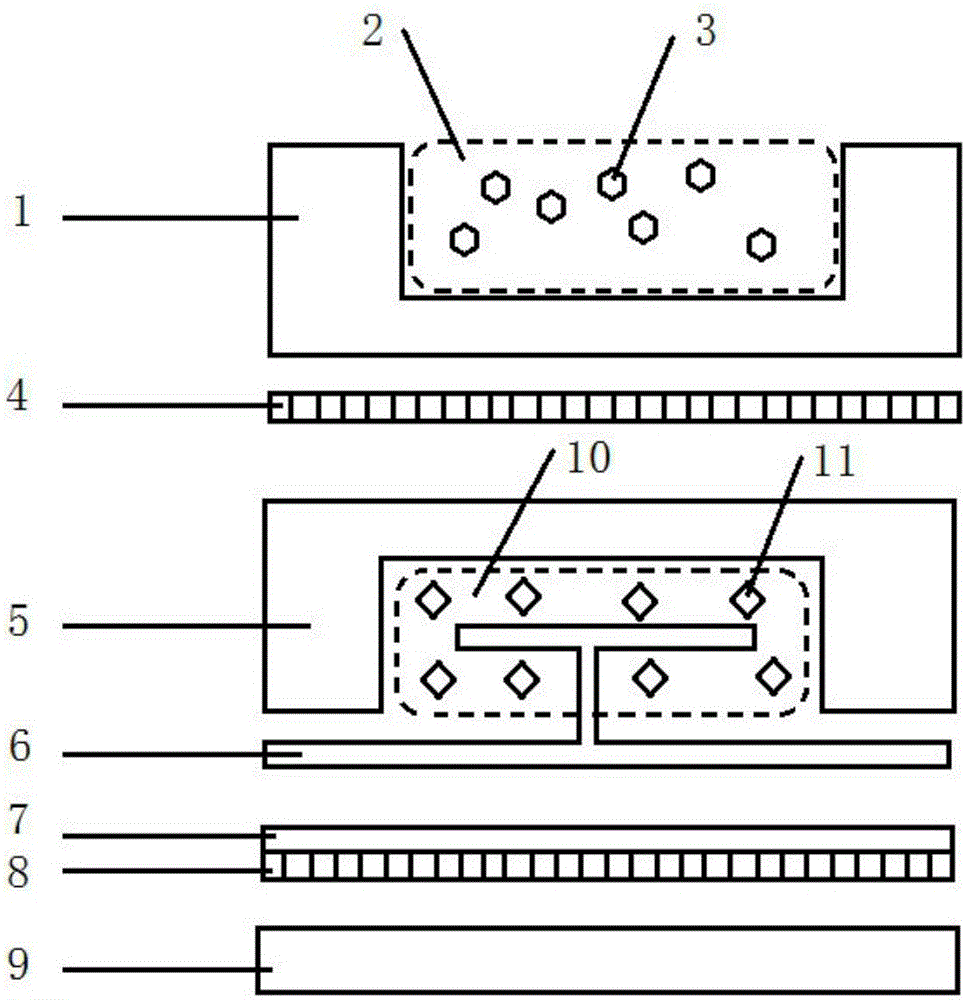
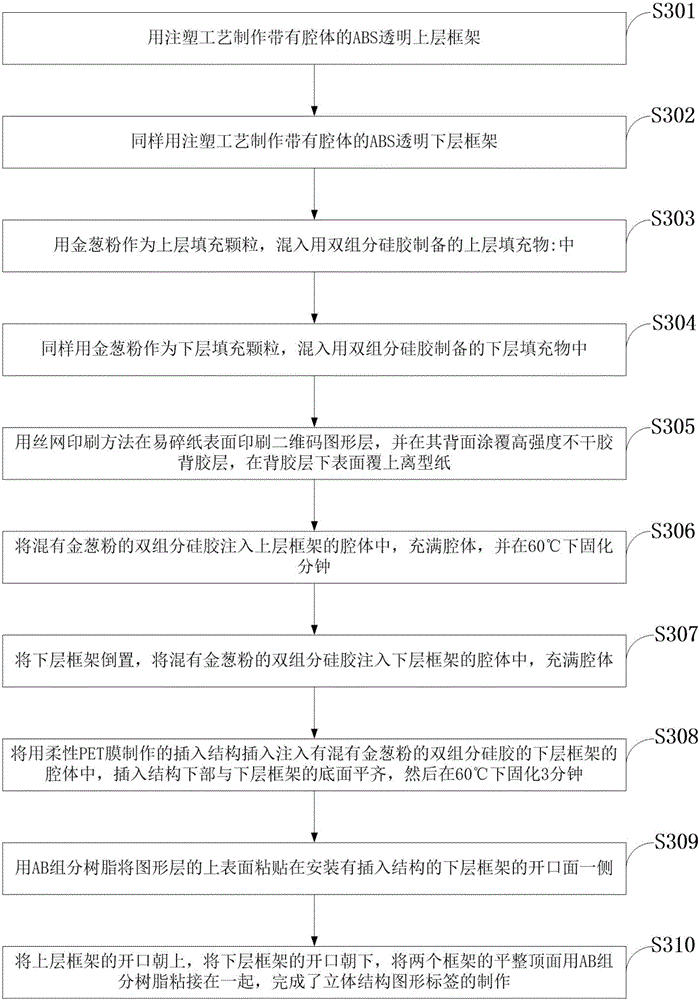
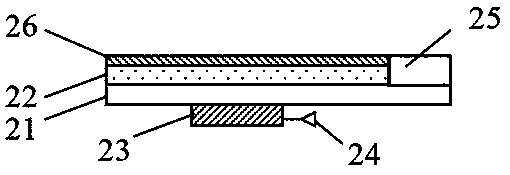
Three-dimensional graphic anti-counterfeit label and method for making same
The invention discloses a three-dimensional graphic anti-counterfeit label and a method for making the same. The method comprising making an upper layer frame and a lower layer frame; mixing upper layer filling particles into an upper layer filler, and mixing lower layer filling particles into a lower layer filler; printing a graph layer, coating a back glue layer, and attaching protective paper to the lower surface of the back glue layer; injecting the upper layer filler containing the upper layer filling particles into a chamber of the upper frame to solidify, injecting the lower layer filler containing the lower layer filling particles into a chamber of the lower frame to solidify after putting into an inserting structure; bonding flat top surfaces of the upper layer frame and the lower layer frame by glue layers; adhering the graph layer, the back glue layer and the side having the graph layer of the protective paper to one side where an opening is of the lower layer frame of the combination of the upper and lower frames. Accordingly, the three-dimensional graphic anti-counterfeit label is made. Problems in the prior art that a present graphic label is easy to copy, forge and transfer, the recognition is tedious and a high-quality users are needed can be solved by adopting the three-dimensional anti-counterfeit label.
Owner:HANGZHOU WOPUWULIAN SCI & TECH
Multi-wavelength fluorescent quantum dot anti-counterfeiting method
The invention discloses a multi-wavelength fluorescent quantum dot anti-counterfeiting method, comprising the following steps of (1) selecting a plurality of fluorescent quantum dots with various grain diameter types, wherein the fluorescence emission spectrums of the fluorescent quantum dots are evenly distributed within a near-infrared area; moreover, no wave bands overlap; and the type of the selected quantum dots is in a number equal to that of the ink boxes of a selected printer, and further is corresponding to the ink boxes of the selected printer one to one; (2) coding a plurality of fluorescent quantum dots of various types in each black bar according to bar codes through the utilization of the presence or absence of the fluorescence peaks of the fluorescent quantum dots of various type within a given wave band; (3) evenly mixing the quantum dots with ink in the corresponding printer ink box; and (4) printing an anti-counterfeiting marker with the ink containing the quantum dots in the step (3) so as to realize the highly anti-counterfeiting of commodities. The anti-counterfeiting marker made by such an anti-counterfeiting method has the advantages of high precision, good hiddenness and large information capacity, and further can be set and assigned by a manufacturer.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Secondary screening printing anti-counterfeiting method
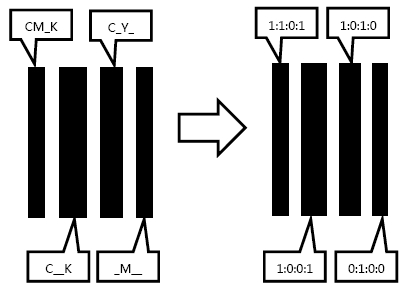
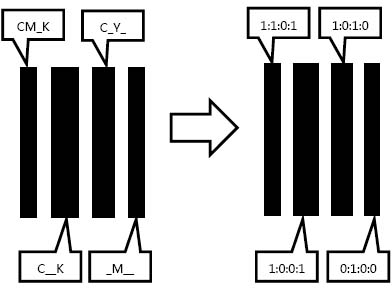
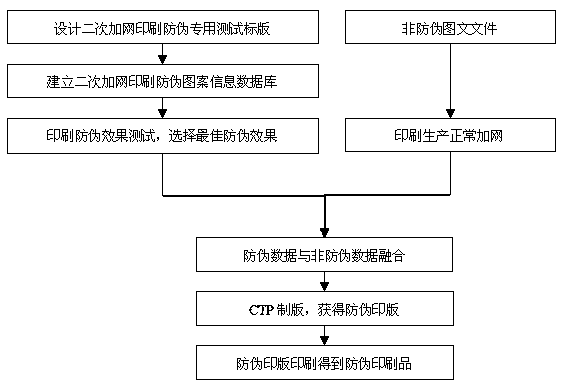
ActiveCN103722921ALow costNon-reproduciblePattern printingImage data processing detailsHydrogenComputer to plate
The invention provides a secondary screening printing anti-counterfeiting method. The method specifically includes: firstly, establishing a secondary screening printing anti-counterfeiting pattern information database; secondly, printing and testing secondary screening printing anti-counterfeiting patterns; thirdly, acquiring printing production data with secondary screening anti-counterfeiting pattern information; fourthly, establishing a digital CTP (computer to plate) output process control system to realize digital control of plate chamber temperature, humidity, developing solution concentration, solution compensation dosage, flush temperature, flush time, solution conductivity and PH (potential of hydrogen) value and guarantee accurate output of anti-counterfeiting data on a printing plate and repeatability of repeated output. Non-reproducible special anti-counterfeiting patterns are obtained by means of data fusion operation of screening data, and a mode of software and hardware combination and precise flow process control is adopted to realize extremely low anti-counterfeiting cost and excellent printing anti-counterfeiting effect.
Owner:HANGZHOU DAILY PRESS GRP SHENGYUAN PRINTING CO LTD
Digital content intelligent playing device and its controllable playing method
InactiveCN1815601ANon-reproducibleUnauthorized memory use protectionDigital recording/reproducingData scienceContent server
The playing back equipment includes one or more intelligent terminals as well as one or more intelligent keys in use for security. At least one intelligent key is as a security module, which is not possible to be replicated completely. Intelligent keys are divided into user type intelligent keys to denote usersí»ID and / or internal intelligent keys to denote ID of intelligent terminals. At least one intelligent terminal is connected to one or more intelligent keys. In condition of intelligent key is presented, intelligent terminal can process, transfer data or plays data of program. Intelligent key controls playing program. Content server has designed perfect methods for controlling display of local program, display of down loaded networked program, and display of online network program. The invention provides technical safeguard for further networked programs in multimedia.
Owner:BEIJING K CITY HIGH DEFINITION ELECTRONICS TECH
Intelligent desk and digital signal processing method
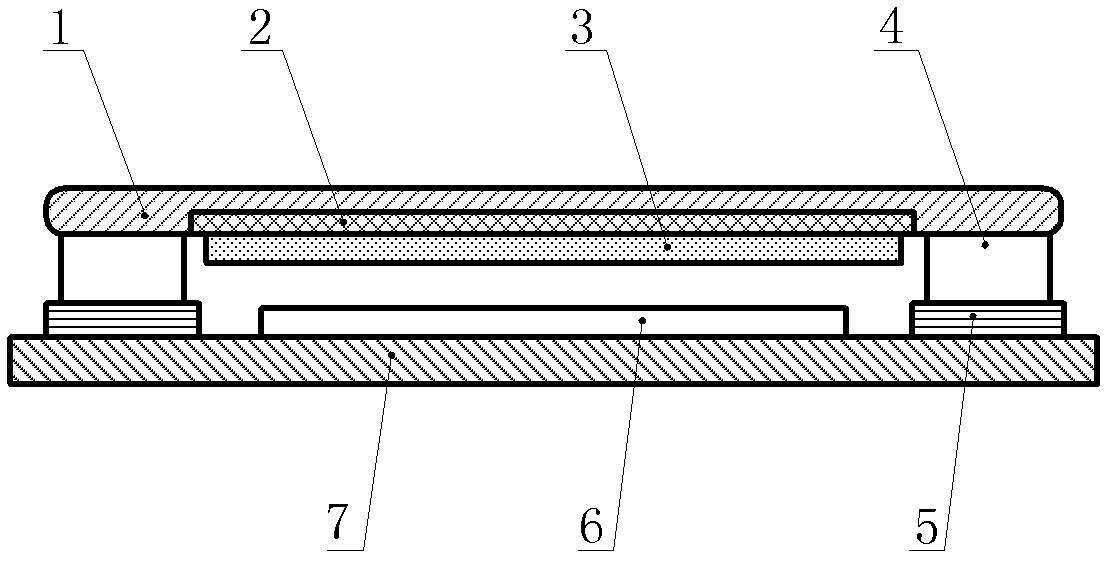
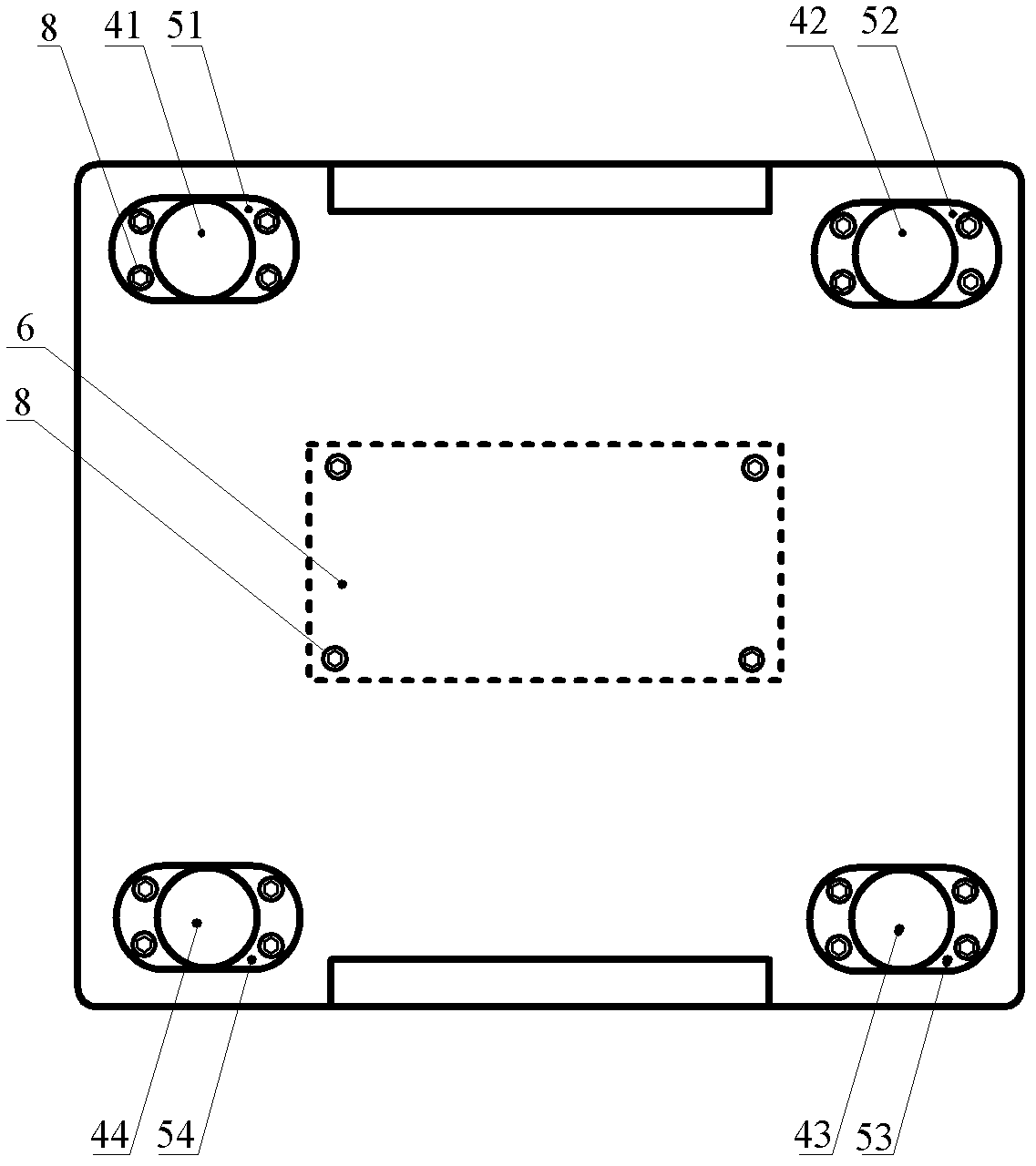
ActiveCN102411444AHigh positioning accuracyQuick responseInput/output processes for data processingDigital signal processingStructure of Management Information
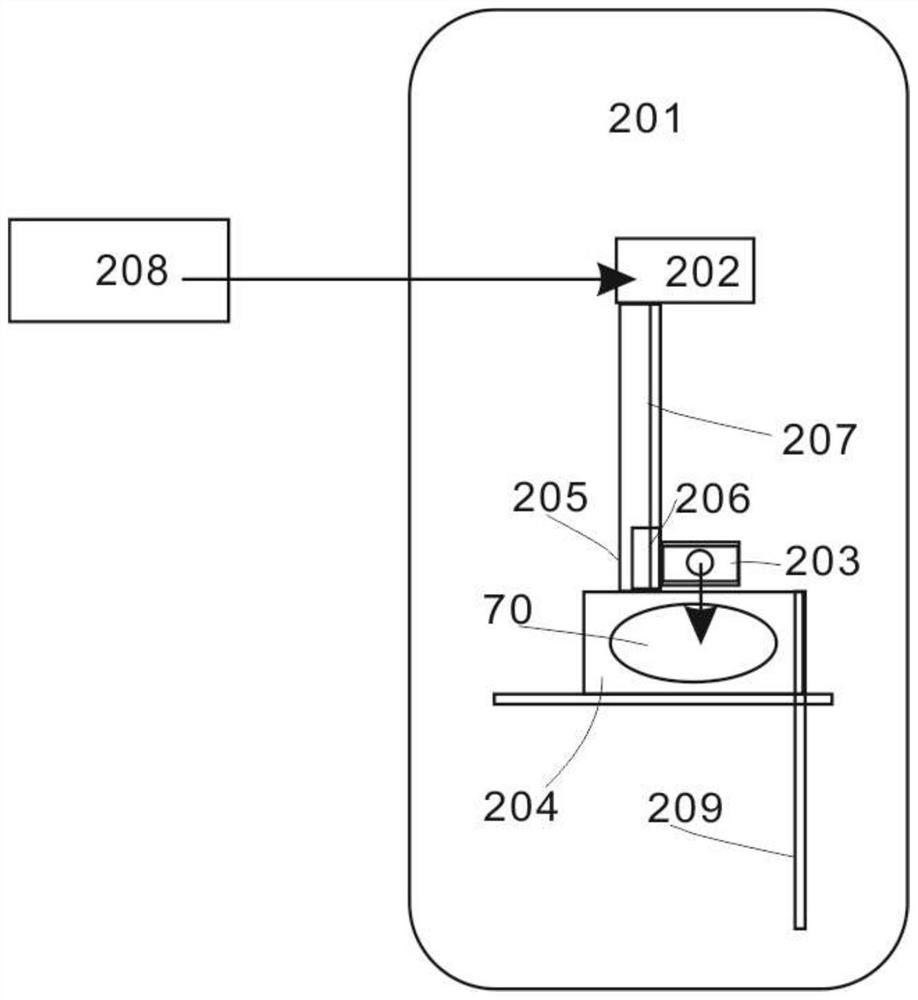
The invention relates to an intelligent desk and a digital signal processing method. The structure of the intelligent desk is that: a signature flat panel (1) is arranged on the intelligent desk; a liquid crystal flat panel display (2) and a liquid crystal display drive board (3) are sequentially arranged below the intelligent desk; four three-dimensional force sensors (4) are fixed at four corners below the signature flat panel (1) through four fixing adapter plates (5); and a digital signal processing plate (6) is fixed above the central position of a base flat panel (7) by internal hexagonal positioning holes (8) on two sides. In the digital signal processing method for the intelligent desk, the digital signal processing plate (6) digitally processes acquired analogue three-dimensional force information, performs digital smooth filtering processing to reduce the influence of interference noises, and performs data fusion processing on data to obtain the three-dimensional force vector information and real-time track coordinates of a contact point of a pen point; and calculated coordinate information is displayed to achieve the real-time visual feedback effects of a writing process.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
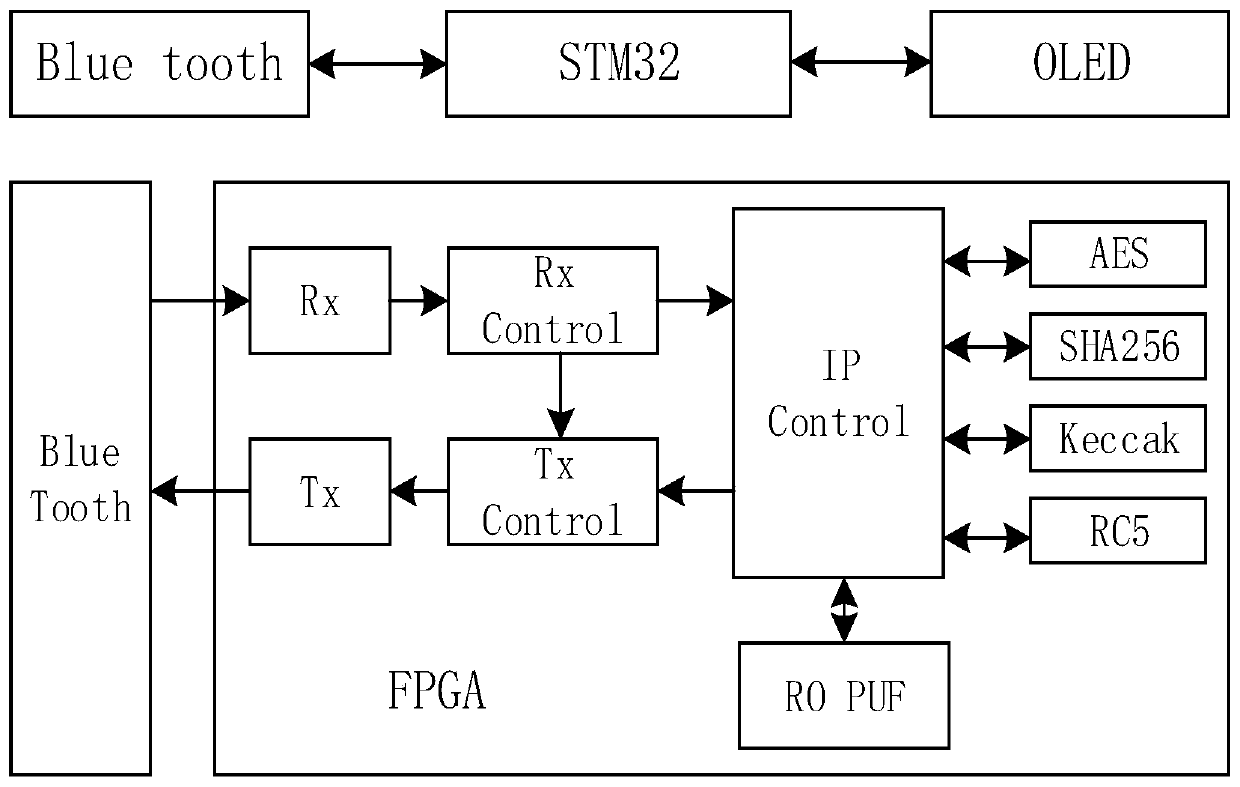
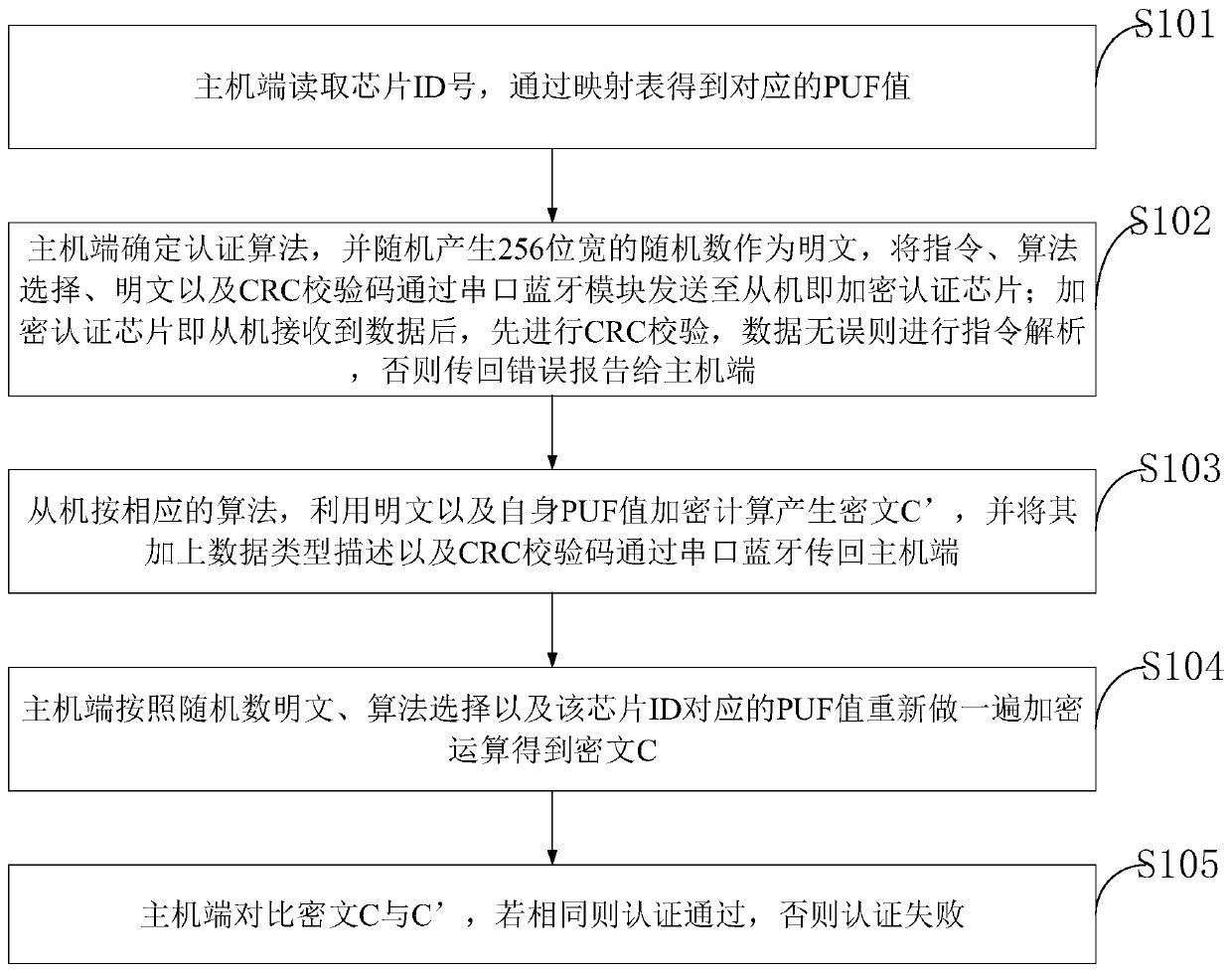
FPGA-based multi-algorithm security encryption authentication system and method
InactiveCN111259416AImprove anti-counterfeiting and anti-attack capabilitiesNon-reproducibleDigital data protectionInternal/peripheral component protectionAuthentication systemEmbedded system
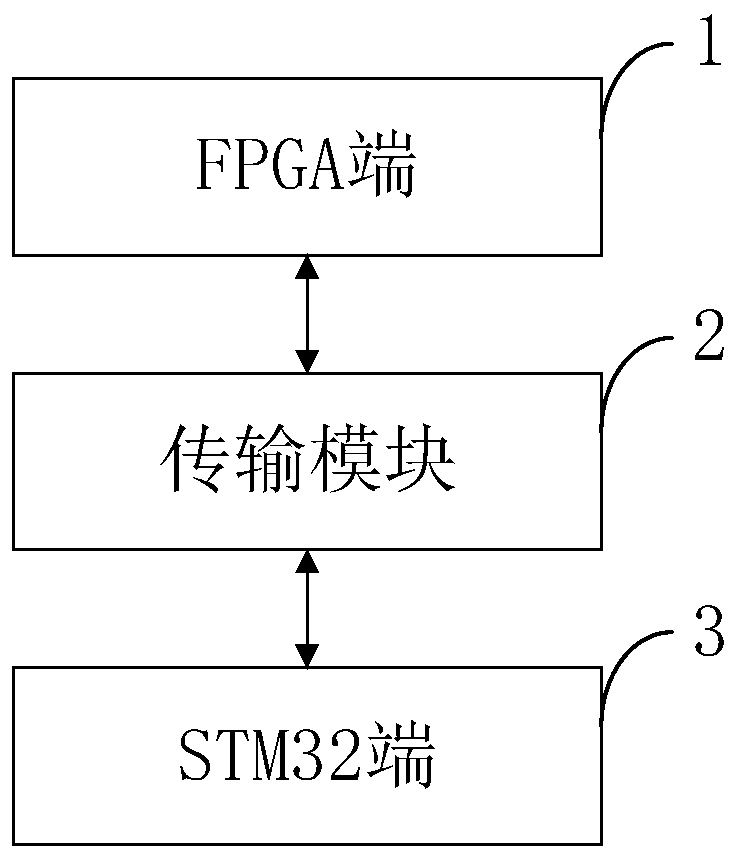
The invention belongs to the technical field of data encryption authentication, and discloses an FPGA-based multi-algorithm security encryption authentication system and method. The FPGA-based multi-algorithm security encryption authentication system comprises: an FPGA terminal, i.e., an encryption authentication chip, used for encryption authentication; a transmission module used for transmittinginstructions and data through a serial port protocol; and a host end used for configuring and verifying the encryption authentication chip. According to the security encryption authentication system,multiple different encryption algorithms can be selected during identity authentication, and compared with a single algorithm authentication system, the security encryption authentication system hasthe advantages that the cracking difficulty is increased, and the security coefficient is improved. According to the invention, the RO PUF is constructed by utilizing random difference generated during manufacturing of an integrated circuit to generate a chip key, so that the chip key cannot be re-etched, and is safer than a key stored in a nonvolatile memory. According to the method, the value ofeach bit of the PUF is generated and compared for many times to confirm the final value, so that the stability of the PUF value is improved.
Owner:HUBEI UNIV
Manufacturing method of optical anti-fake membrane, optical anti-fake membrane label, optical anti-fake label and optical anti-fake system
InactiveCN103177654AImprove anti-counterfeiting performanceSave money on counterfeitingStampsRecord carriers used with machinesChemistryDopant
The invention provides a manufacturing method of an optical anti-fake membrane. The method comprises: nontransparent dopant is added to curable transparent or partially transparent liquid materials; the dopant and the liquid materials are mixed so that mixed liquor is manufactured; and the mixed liquor is manufactured to the optical anti-fake membrane. The manufacturing method of the optical anti-fake membrane can solve the problem of counterfeit products troubling enterprises for a long time fundamentally, anti-fake cost is saved greatly, huge market shares occupied by the counterfeit products can be recaptured, and therefore economic benefit of the enterprises is greatly enhanced.
Owner:杜浩燕 +2
Preparation method of cellulose nanocrystal cholesteric liquid crystal texture anti-counterfeiting mark
InactiveCN105199150AWide variety of sourcesUniform sizeStampsIdentification meansMicroscopeCholesteric liquid crystal
The invention relates to a preparation method of a cellulose nanocrystal cholesteric liquid crystal texture anti-counterfeiting mark. The preparation method comprises the following processing steps: a) preparing nanocrystal suspension with microcrystalline cellulose; b) observing a cholesteric liquid crystal texture pattern through a polarizing microscope; c) preparing a texture anti-counterfeiting mark. The prepared cholesteric liquid crystal texture anti-counterfeiting mark has clear lines and unduplicatedness and has application value in the package anti-counterfeiting field.
Owner:NANJING FORESTRY UNIV
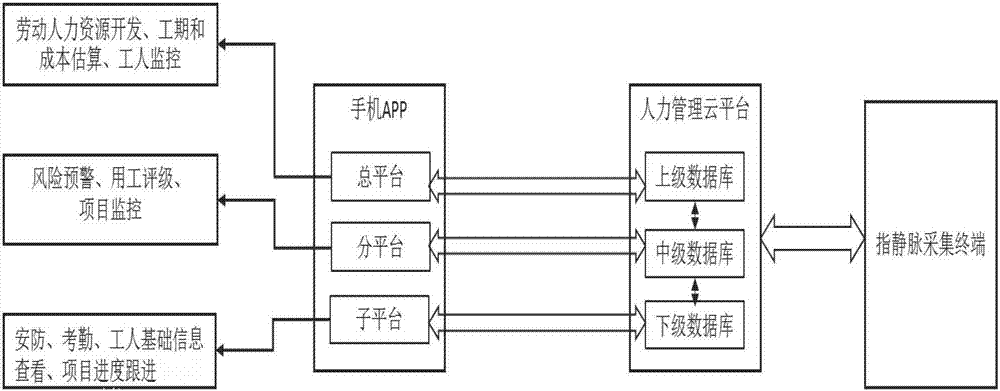
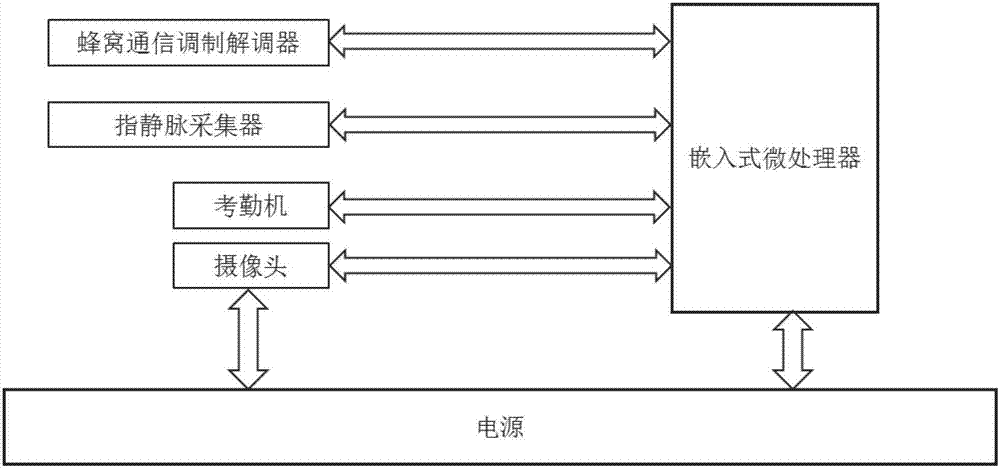
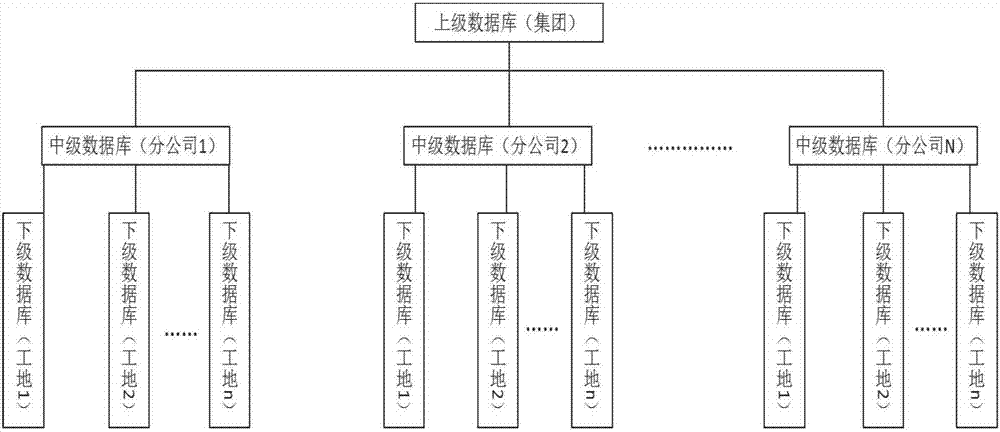
Labor service big data management system based on finger vein recognition and application method thereof
InactiveCN107451797AReduce management costsUniqueOffice automationAcquiring/reconising fingerprints/palmprintsVeinFinger vein recognition
The present invention discloses a labor service big data management system based on finger vein recognition and an application method thereof, belonging to the computer information management field. The system comprises a plurality of finger vein collection terminals, a manpower management cloud platform and a plurality of mobile management terminals; the finger vein collection terminals are configured to perform primary collection of work basic information for forming a primary archive and perform subsequent collection of the worker work attendance case and the construction period completion condition for forming a subsequent archive; the manpower management cloud platform is arranged in a background cloud server and is configured to store the primary archives and the subsequent archives uploaded by all the finger vein collection terminals so as to establish a labor service big database; and the mobile management terminals are arranged on a mobile device and are configured to obtain work basic information in the labor service big database to realize remote construction management. The labor service big data management system based on finger vein recognition and the application method thereof realize sharing of worker basic information with no need for repeatedly recording worker basic information, the permission setting allows the labor service data to be more safe, and the system can perform assessment of the construction period to help managers to perform human resource analysis.
Owner:上海荷福人工智能科技(集团)有限公司 +1
Anti-counterfeiting certificate capable of distinguishing truth and falsity through checking micro image codes and verification codes
InactiveCN102673220ALow costRealize anti-counterfeiting functionOther printing matterInformation cardsComputer hardwareGraphics
The invention relates to an anti-counterfeiting certificate capable of distinguishing truth and falsity through checking micro image codes and verification codes. The verification codes for verifying the truth and the falsity of articles to be verified and the micro image codes corresponding to the verification codes are printed on the surface of the anti-counterfeiting certificate; each micro image code comprises a content data part and a header part and consists of a plurality of micro image units, the different micro image codes are distinguished in a combined manner of the plurality of micro image units in each micro image code, and the combination of the micro image units forms a small graph incapable of being distinguished by human eyes; and the micro image codes can obtain information codes uniquely corresponding to the micro image codes through being decoded. The anti-counterfeiting certificate adopts a manner of directly reading the micro image codes printed on the surface of the anti-counterfeiting certificate to verify, therefore, the distinguishing speed is quick, and the verification work of a large quantity of articles to the verified can be finished within a shorter time.
Owner:AIGO DIGITAL TECHNOLOGY CO LTD
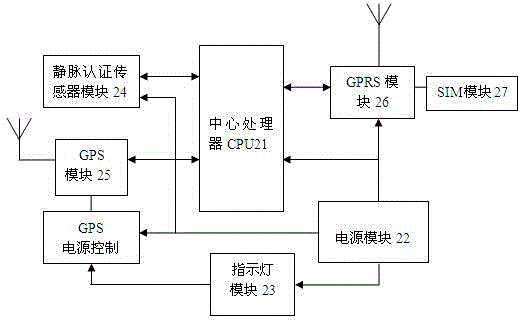
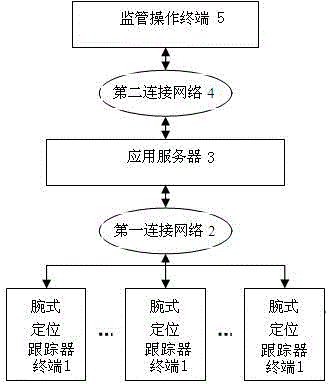
Vein authentication wrist wireless positioning tracker
ActiveCN104459718ALong-term effective recognition ratePrevent leakageSatellite radio beaconingMatching and classificationGps satellitesApplication server
Owner:无锡优辰电子信息科技有限公司
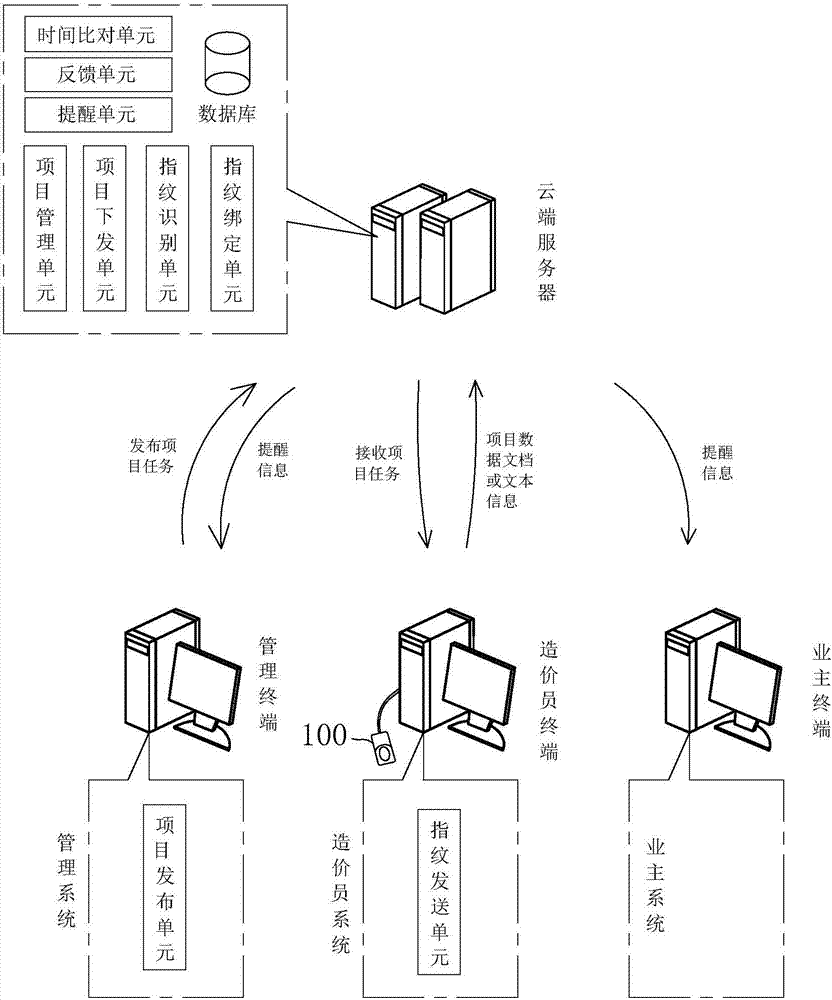
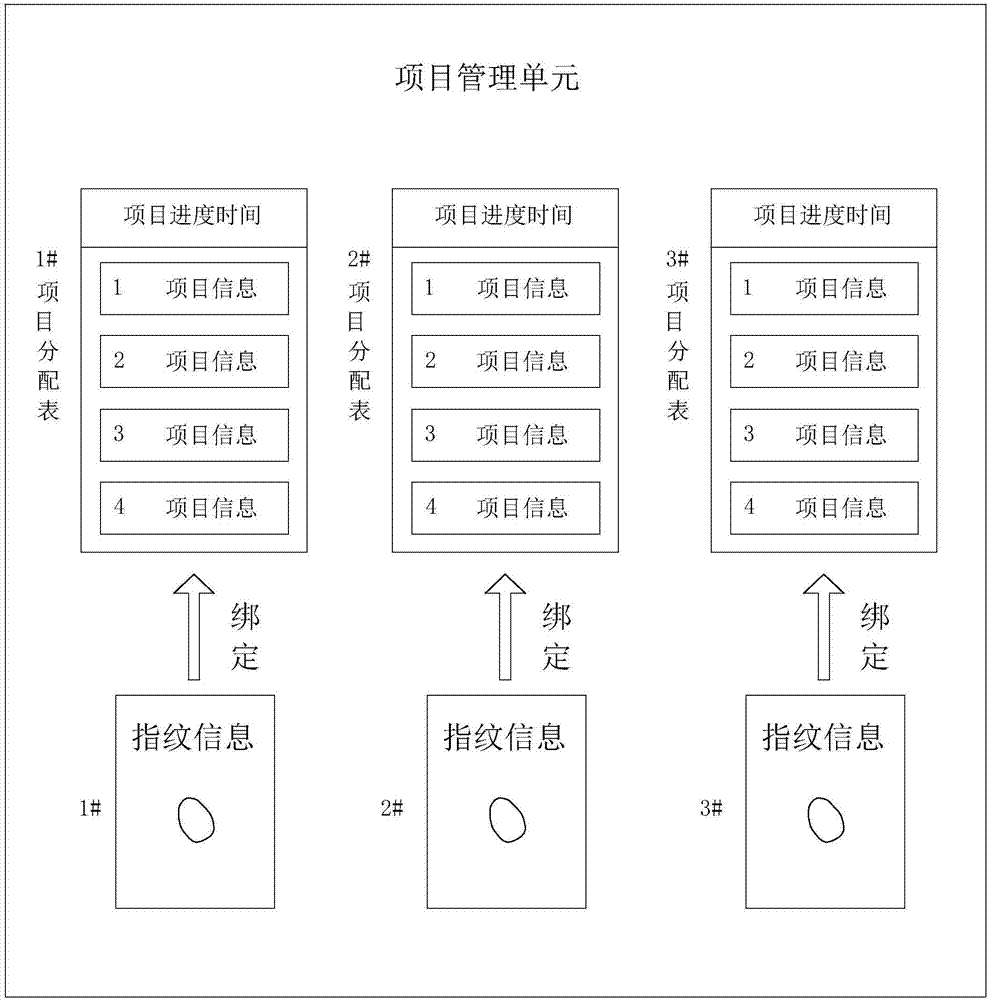
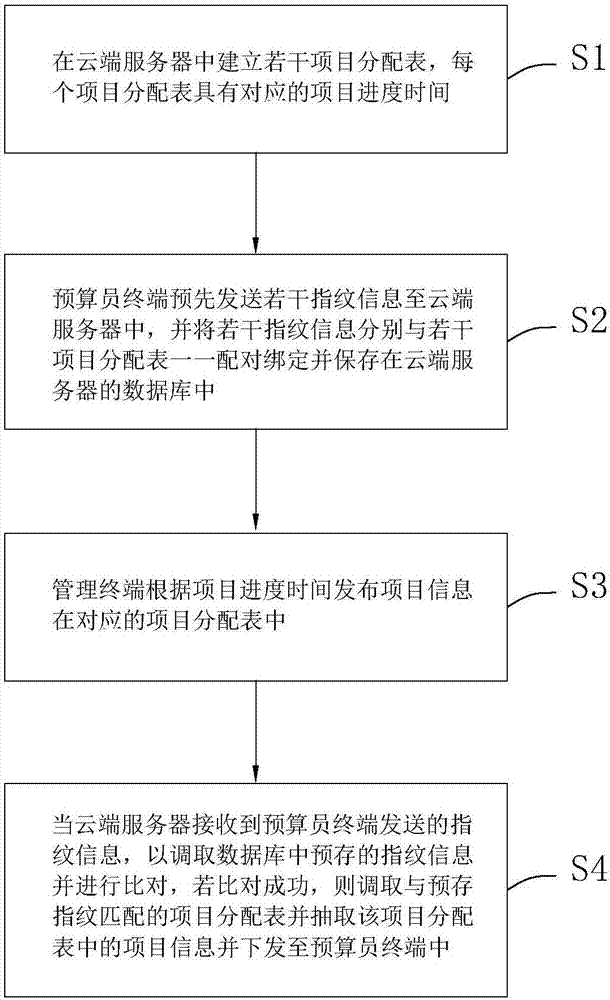
Engineering cost project distribution system and method
InactiveCN107067236AImprove processing efficiencyNon-reproducibleOffice automationDistribution systemFingerprint
The invention discloses an engineering cost project distribution system and a method. The technical schemes of the invention comprise: a project management unit comprises a plurality of project distribution sheets with each project distribution sheet provided with progress time corresponding to project; a project publishing unit is used to publish the project information in the corresponding project distribution sheet according to the project progress time; a fingerprint sending unit transmits the fingerprint information to a cloud server according to the fingerprint information recorded by a fingerprint input unit wherein the cloud server further comprises a fingerprint identification unit and a project delivery unit. The fingerprint identification unit is used to receive the fingerprint information so as to call and compare the fingerprint information pre-stored in a database. If the fingerprint information is successfully matched, then, the project delivery unit calls the project distribution sheet that matches the pre-stored fingerprint information, randomly extracts the project information in the project distribution sheet and delivers the project information to the cost maker system.
Owner:浙江华域高宇项目管理有限公司
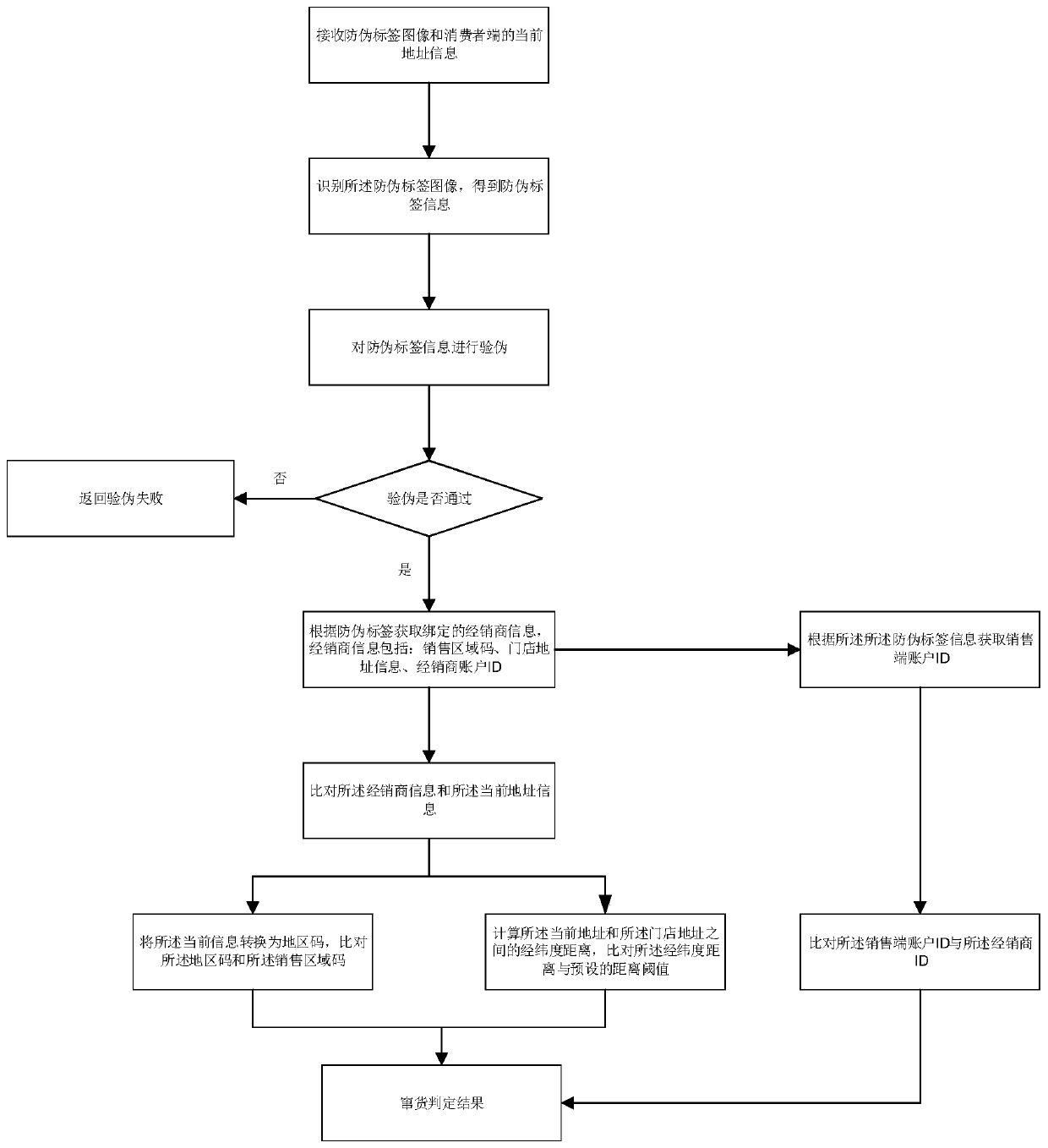
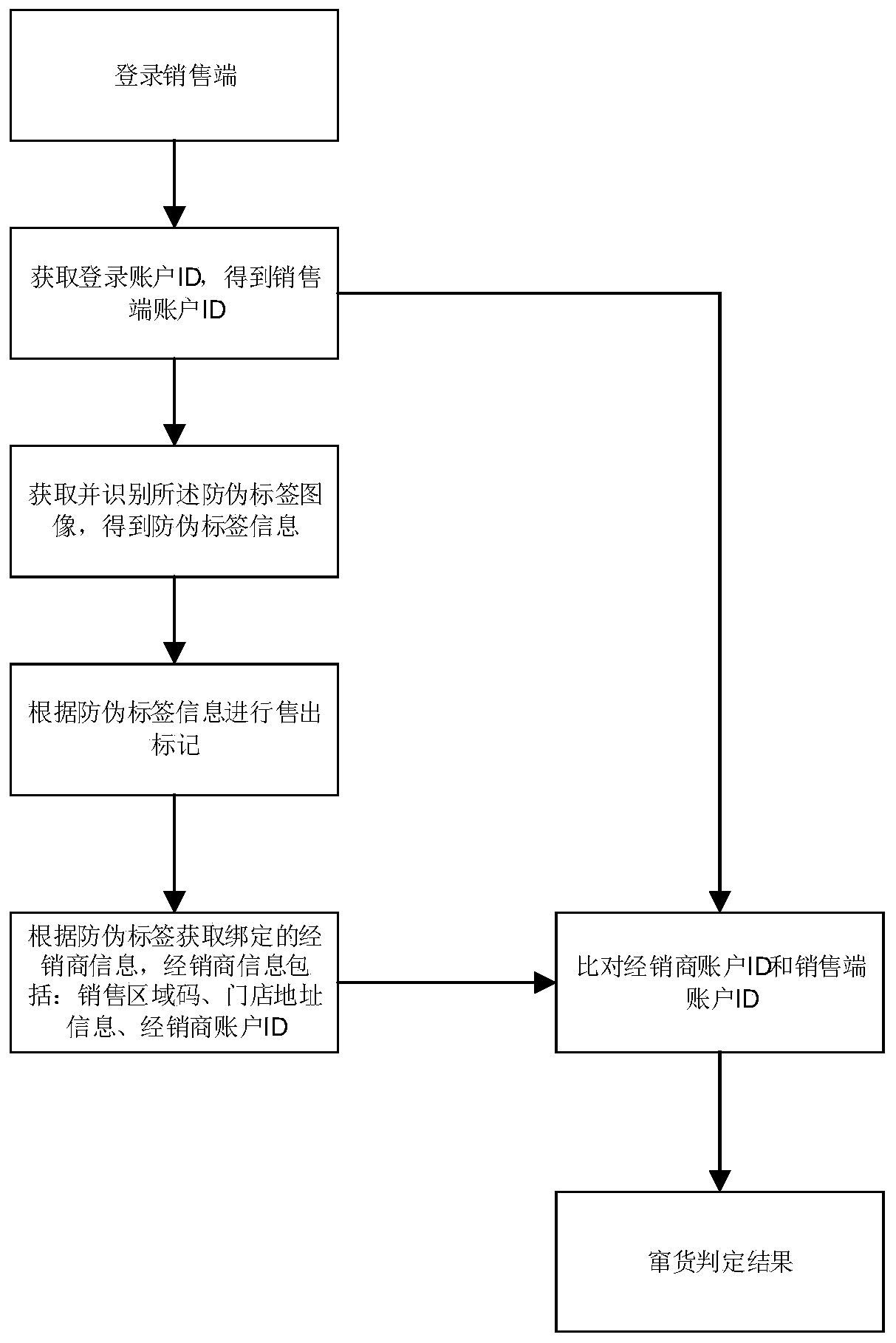
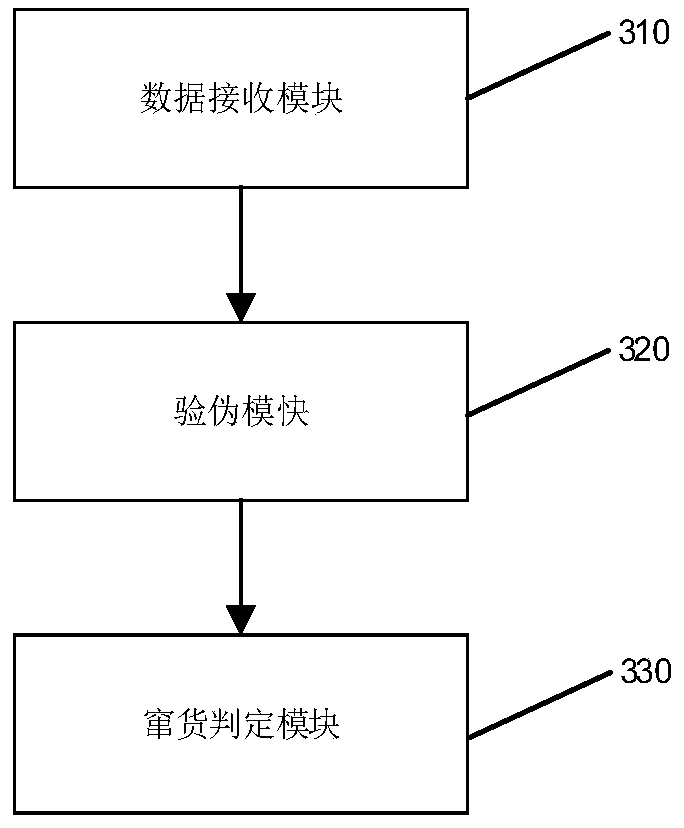
Commodity fleeing judgment method, device and equipment and medium
ActiveCN111242641ANon-reproducibleGuaranteed accuracyCo-operative working arrangementsCommerceInformation acquisitionData science
The invention discloses a commodity fleeing judgment method, which relates to the technical field of Internet of Things, and aims to improve the accuracy of commodity fleeing judgment. The method comprises the following steps of: receiving an anti-counterfeit label image and the current address information of a consumer terminal, and recognizing the anti-counterfeit label image to obtain the anti-counterfeit label information, performing counterfeit detection on the anti-counterfeit label information, and if the counterfeit detection is passed, obtaining bound dealer information according to the anti-counterfeit label information, and comparing the dealer information with the current address information to obtain a commodity fleeing judgment result. The invention further discloses a commodity fleeing judgment device, electronic equipment and a computer storage medium.
Owner:HANGZHOU WOPUWULIAN SCI & TECH
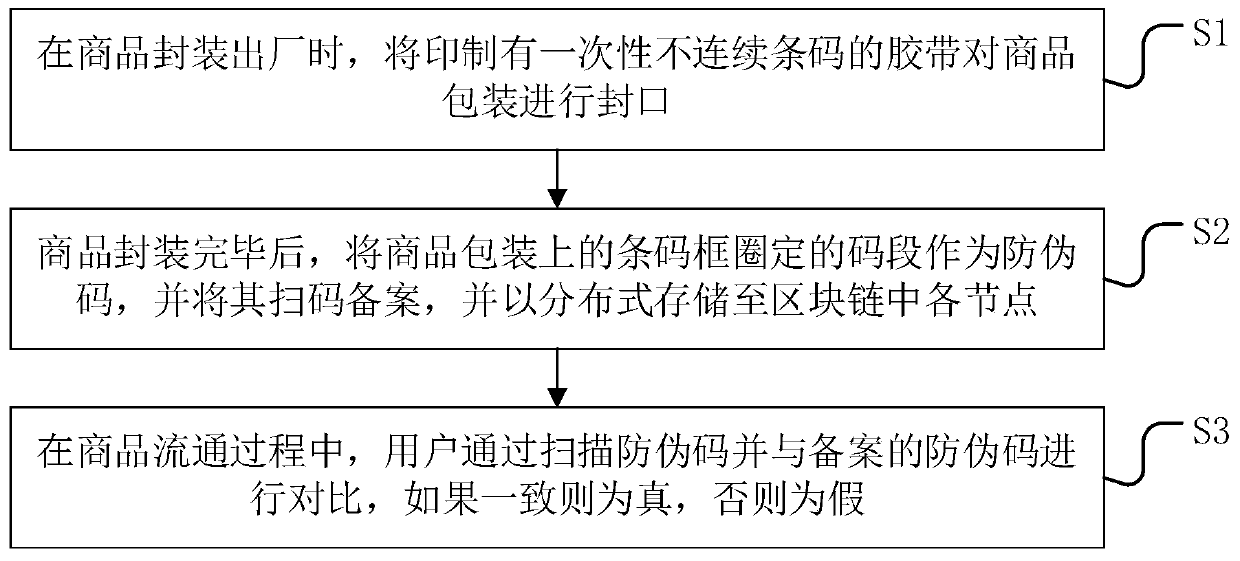
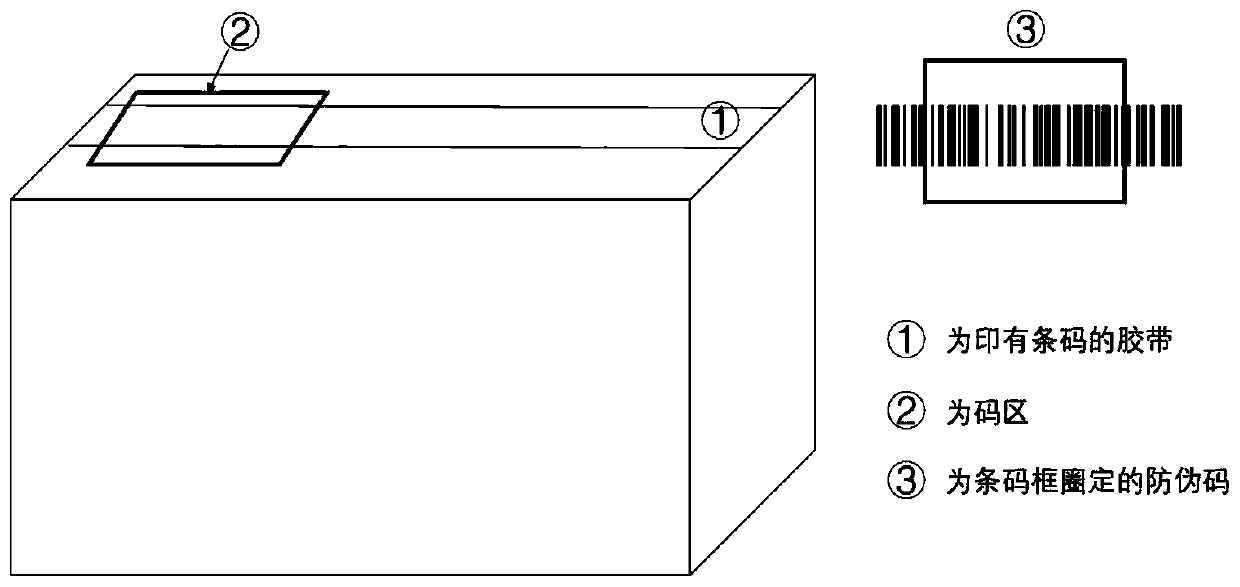
Certified product packaging anti-counterfeiting method and system based on discontinuous bar code adhesive tape
InactiveCN110232579AImprove effectivenessPrevent tamperingDatabase distribution/replicationCo-operative working arrangementsBlockchainDuctility
The invention provides a certified product packaging anti-counterfeiting method and system based on a discontinuous bar code adhesive tape. According to the invention, a plurality of characteristics of size difference of an outer package, a packaging angle, ductility of an adhesive tape, one-time property, discontinuity and non-repeatability of an adhesive tape bar code are utilized; the bar codeframe is arranged on the outer package, the bar code in the bar code frame is scanned to serve as the anti-counterfeiting code, so that the anti-counterfeiting code on each outer package has uniqueness, a counterfeiter difficultly reproduces the recorded anti-counterfeiting code of the certified product through the intersection of the adhesive tape and the bar code frame in the case sealing process, the threshold of successful reckoning and copying is high, and replicability is achieved. In addition, a block chain technology is applied to perform distributed storage on the anti-counterfeitingcodes, so that the anti-counterfeiting codes are prevented from being tampered, and the uniqueness of the anti-counterfeiting codes and logistics information is ensured.
Owner:青岛车智品信息科技有限公司
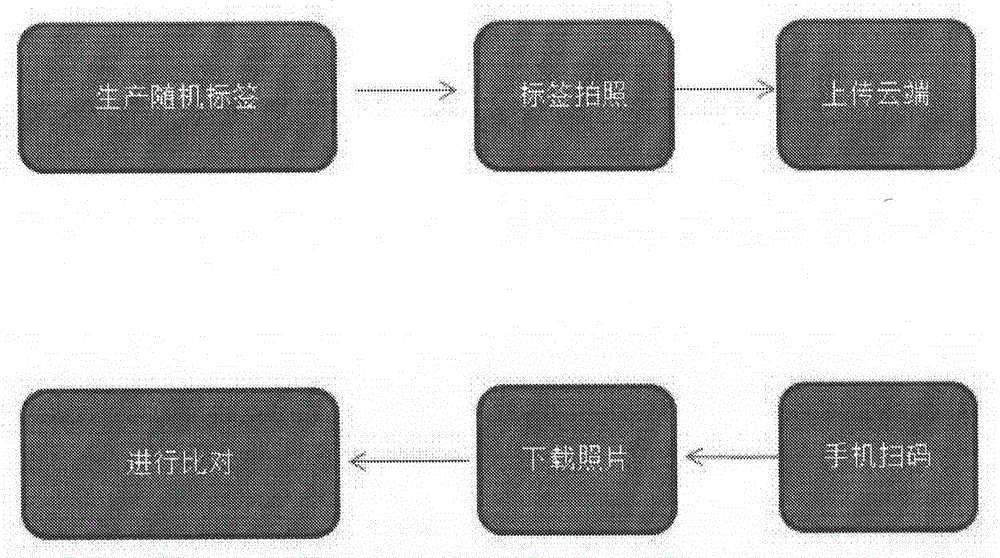
Anti-fake method based on random technology
InactiveCN105702154ASolve the lack of professional knowledge of the productSolve the incomparable problemsStampsIdentification meansComputer graphics (images)Algorithm
The invention relates to an anti-fake method based on the random technology, in particular to an anti-fake method in which a logo is made by means of the randomness, uniqueness and unduplicatedness of an object. The method mainly comprises the steps of making a random logo firstly, taking a picture of the logo, and then uploading the picture to the cloud side. A user can verify authenticity by downloading the picture from the cloud side and comparing the picture with a real logo. Due to the fact that the randomly made logo can not be duplicated substantially, authenticity verification can be easily conducted.
Owner:张玲
Application of electronic card applying hardware internal identification code and identification method thereof
InactiveCN101540079AAvoid confusionSimple consumer behaviorComplete banking machinesCharacter and pattern recognitionPaymentSecret code
The invention relates to an application of an electronic card based on a MAC address of a network chip; the electronic card is bound with the MAC address of a user, thus increasing the safety for using the electronic card which can realize automatically recording the consumption habit, providing the address of consumers and the like in e-business; the electronic card holder can be bound with an internal and external read-write head of the electronic card and an electronic card code by a home side network card and the MAC address of the internal network chip which is arranged in a set-top cable box to read and write required data safely, which realizes the function of e-business home payment side. When applying other electronic cards (social security card), the electronic card can be bound with the internal and external read-write head of the electronic card and an electronic card code by the home side network card and the MAC address of the network chip which is arranged in the set-top cable box, thus realizing the function of safe reading and writing.
Owner:谢经良 +2
Anti-counterfeiting system used for anti-counterfeiting by matching relationship between micro image code and verification code
InactiveCN102682269ALow costRealize anti-counterfeiting functionOther printing matterInformation cardsGraphicsParallel computing
The invention relates to an anti-counterfeiting system used for anti-counterfeiting by matching the relationship between a micro image code and a verification code. The system comprises a micro image code recognition device and an anti-counterfeiting certificate, wherein the micro image code for representing an article to be verified and the verification code corresponding to the micro image code are printed on the surface of the anti-counterfeiting certificate; the micro image code is formed by a plurality of micro image units, different micro image codes are distinguished according to combination manners of the plurality of micro image units in each micro image code, and the micro image units are combined to form a micro graphic which cannot be recognized by human eyes; and a unique information code obtained after decoding the micro image code by the code recognition device is matched with and corresponds to the verification code printed on the surface of the anti-counterfeiting certificate.
Owner:AIGO DIGITAL TECHNOLOGY CO LTD
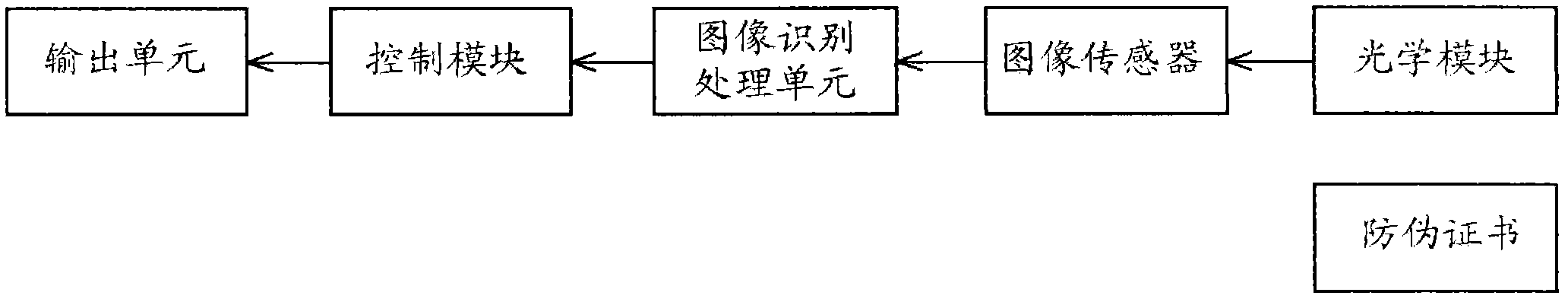
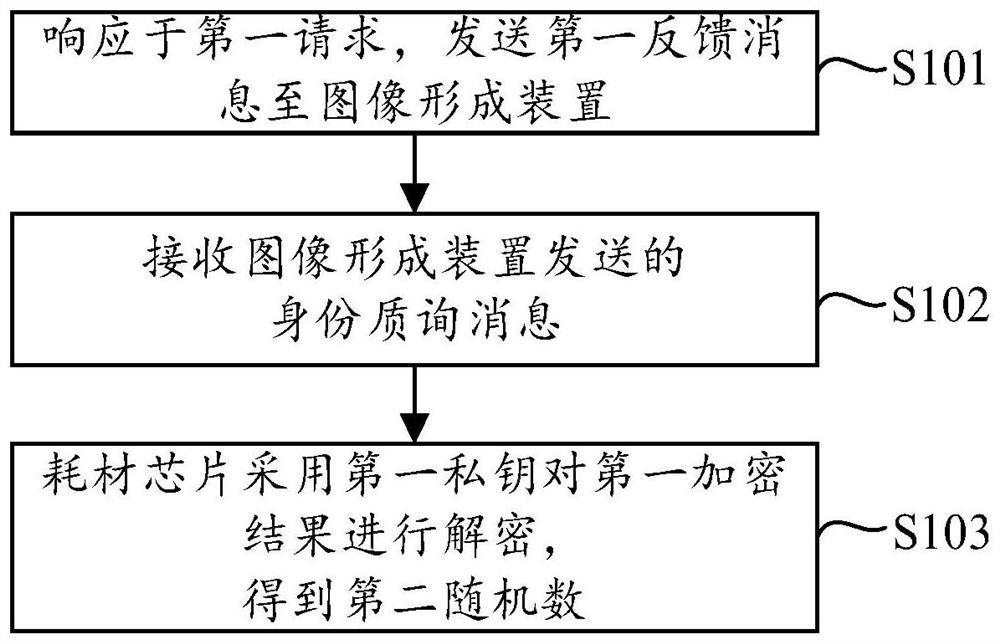
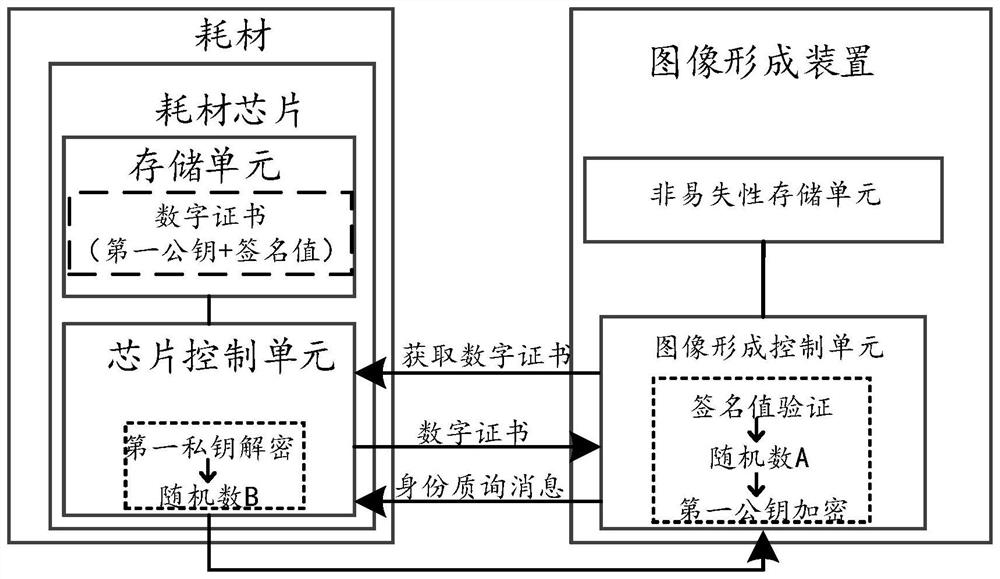
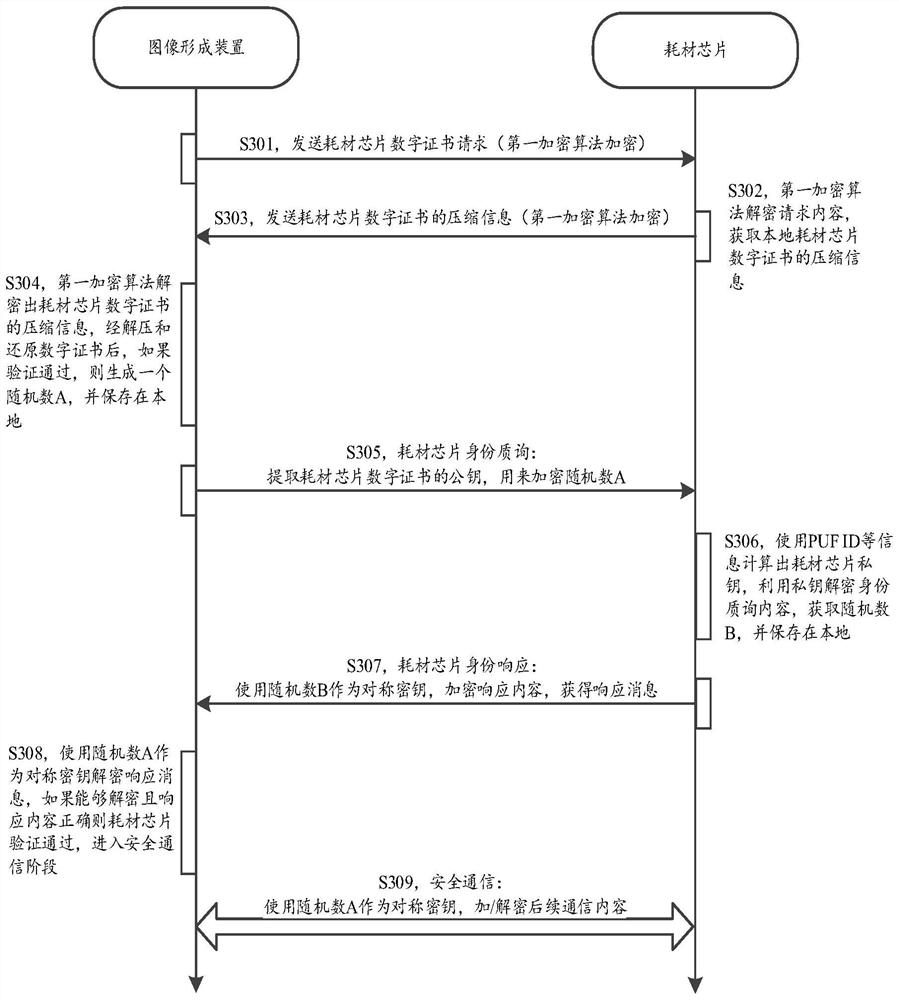
Verification method, consumable chip, consumable and image forming device
ActiveCN114236994ADoes not affect verificationImprove reliabilityDigital data protectionElectrographic process apparatusComputer hardwareImage formation
The invention relates to the technical field of image forming, in particular to a verification method, a consumable chip, a consumable and an image forming device, and the validity of the consumable chip can be accurately verified. The method comprises the steps that the consumable chip responds to a first request and sends a first feedback message to the image forming device; wherein the first feedback message carries digital certificate information, and the digital certificate information at least comprises a first public key; the first public key is generated based on a unique hardware identifier PUF ID of the consumable chip; the consumable chip receives an identity inquiry message sent by the image forming device; the identity inquiry message comprises a first encryption result, and the first encryption result is obtained by encrypting the first random number by using a first public key; the first random number is generated by the image forming device; the consumable chip decrypts the first encryption result by using a first private key to obtain a second random number; the second random number is used for obtaining a verification result of the consumable chip.
Owner:ZHUHAI PANTUM ELECTRONICS
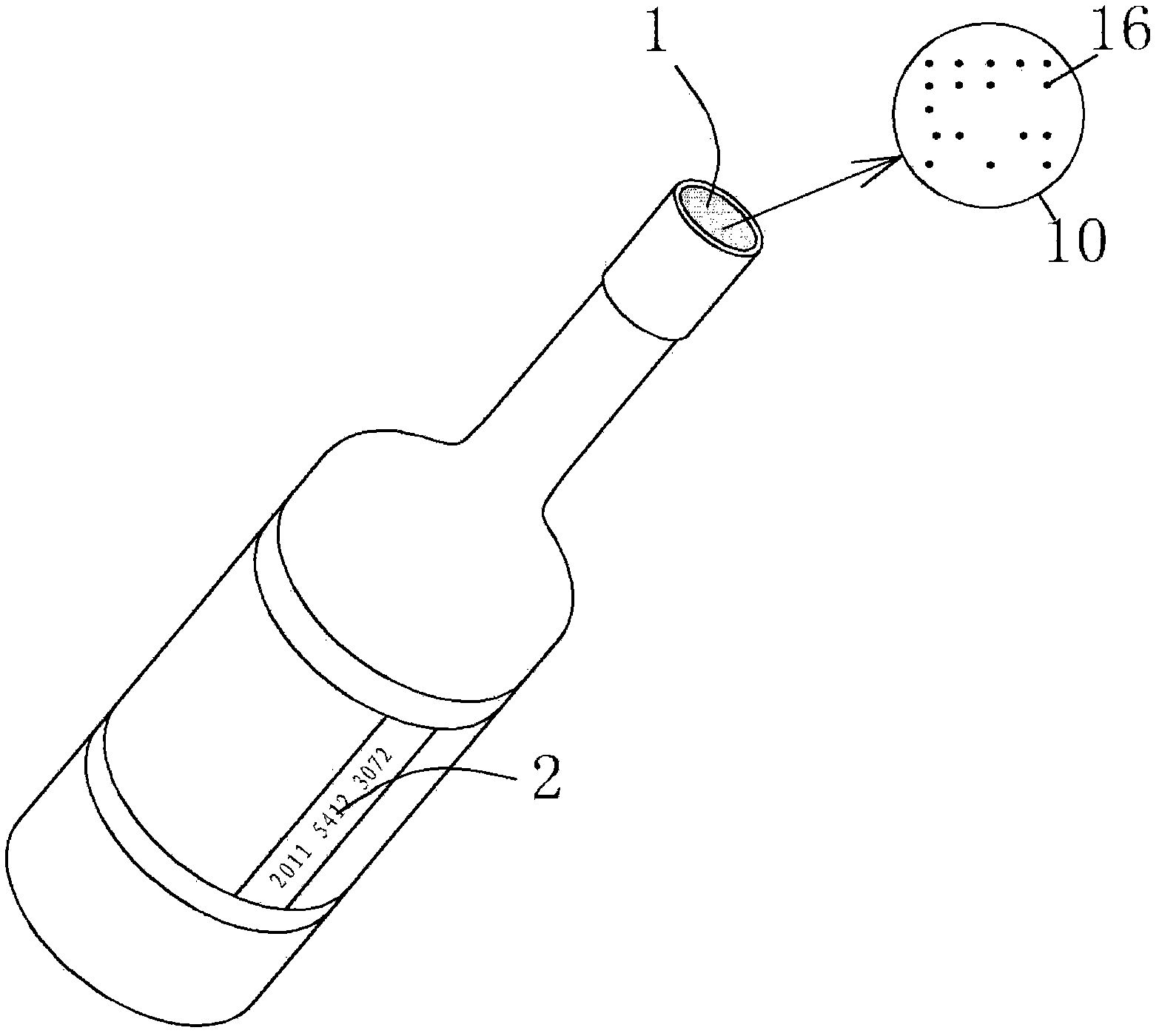
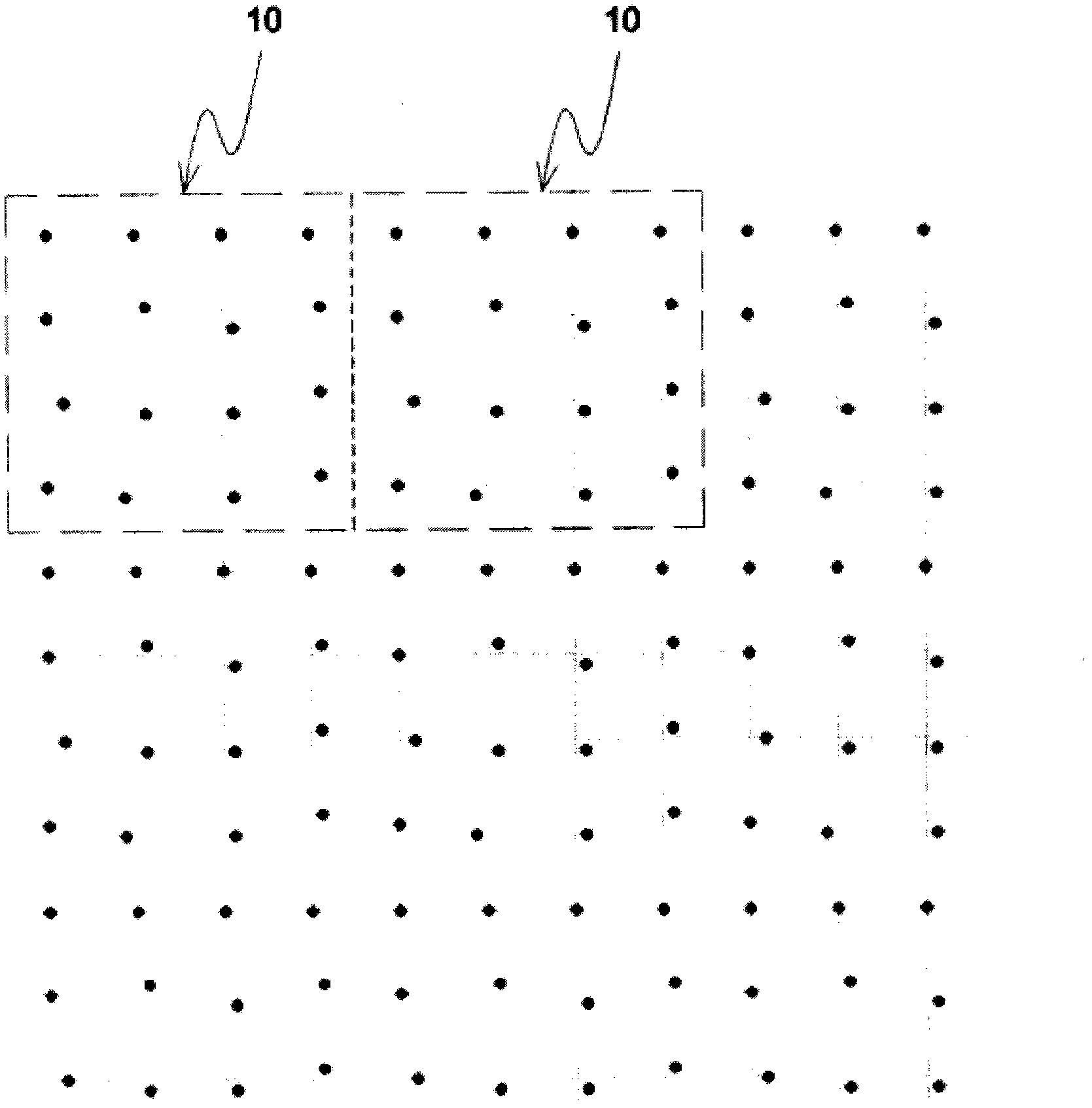
Anticounterfeit seal, and its manufacturing method and complete detecting film
InactiveCN1815494ANon-reproducibleThe effect of preventing forgeryStampsDigitally marking record carriersSheet filmNormal conditions
The disclosed stamper of guiding against false includes handle and surface of stamper. There is pattern of containing information of enterprise or individual on surface of stamper. There is dot chart on stamper, and the dot chart contains information of guiding against false. The invention also discloses an inspection film. Characters are that besides the said information, which is identical to information on stamper, distributed on the film, lines in use for distinguishing true / false of stamper are also distributed on the film. Being matched to the dot chart, the said lines are in use for distinguishing whether a stamper is true or false by sheathing the inspection film on die plate. The invention also discloses method for manufacturing stamper of guiding against false. Features are: simple scheme, low technique nonreproducibility of die plate, impossible to present invisible image under normal condition, except special dedicated inspection film.
Owner:陈锦昌
Novel method for security verification of commodities
InactiveCN108921578ASolve the disadvantages of taking pictures and copyingTo achieve the purpose of real anti-counterfeitingMemory record carrier reading problemsCommercePasswordCiphertext
The invention discloses a novel method for security verification of commodities. The method comprises the following steps of: scanning a two-dimensional code and scraping an ink layer to obtain a random password; judging whether the random password and two-dimensional code correspond to a same commodity or not by a background verification server, if the judging result is negative, judging the commodity as a fake commodity and ending the verification, and otherwise, entering the next step; generating a random number by the background verification server, searching comparison data, a ciphertextand a secret key, and sending the comparison data, the ciphertext and the secret key to an intelligent terminal; prompting the intelligent terminal to approach to an anti-fake label; after approachingto the anti-fake label, accessing verification data in a sector corresponding to the access number by the intelligent terminal on the basis of a sector password calculated by the ciphertext and the secret key; if the intelligent terminal does not receive the data, judging the commodity as a fake commodity and ending the verification, and otherwise, entering the next step; and comparing the verification data with the comparison data by the background verification server, if the verification data is consistent with the comparison data, judging the commodity as a non-fake commodity, and otherwise, judging the commodity as a fake commodity and ending the verification.
Owner:HEFEI LANGJIN ANTI COUNTERFEITING TECH CO LTD
Payment system and payment method thereof
InactiveCN102542450ARealize cardless consumptionWide applicabilityPayment architectureInformation transmissionComputer terminal
A payment system comprises user terminals, an information transmission system and a finance system. The user terminals and the information transmission system are respectively communicated with the finance system in a wired or wireless manner, each user terminal consists of a finance service terminal and a mobile communication terminal which are jointly arranged in mobile communication equipment, the finance service terminals are used for recording personal finance information of users, the mobile communication terminals are used for recording personal communication information of the users, the personal communication information is bound with the corresponding personal finance information, and when one of the finance service terminals is successfully communicated with the finance system and transaction payment is completed, the finance system feeds transaction completion information back to the corresponding mobile communication terminal. The invention further provides a payment method. The payment system and the payment method not only are convenient in use, but also are high in transaction security, and the problem that expense cards are stolen for transaction is stopped fundamentally.
Owner:蔡显强
Halftone information dual anti-fake method for microstructure websites
ActiveCN109572270ARealize multiple anti-counterfeitingNon-reproducibleInformation cardsAlgorithmInformation hiding
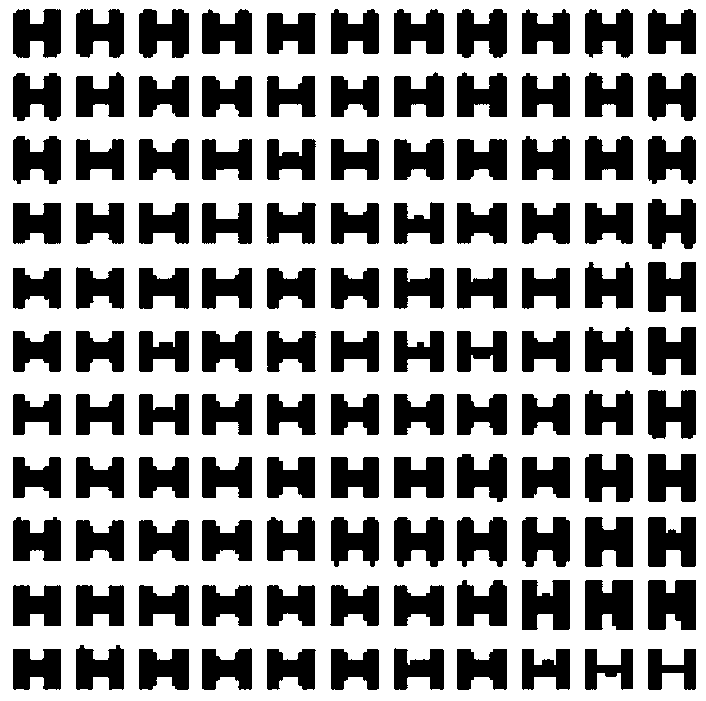
The invention provides a halftone information dual anti-fake method for microstructure websites. The method comprises the steps of: (S1) design of microscopic letter H-shaped website and circular website threshold matrixes; (S2) chaos scrambling encryption of anti-fake information; (S3) preprocessing of the anti-fake information after scrambling; (S4) halftone processing of carrier images and information hiding; and (S5) authentication of the anti-fake information. The method realizes multiple anti-fake of halftone images; the websites have non-repeatability, so that the multiple anti-fake isrealized, even if extracted information still has security; the hidden information occupies no breadth; the detecting method is various; and the anti-fake performance is higher.
Owner:NANJING FORESTRY UNIV
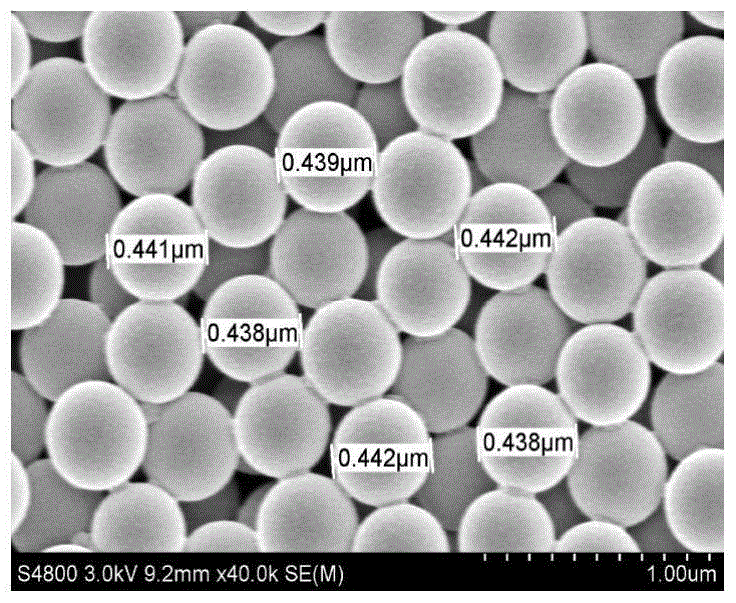
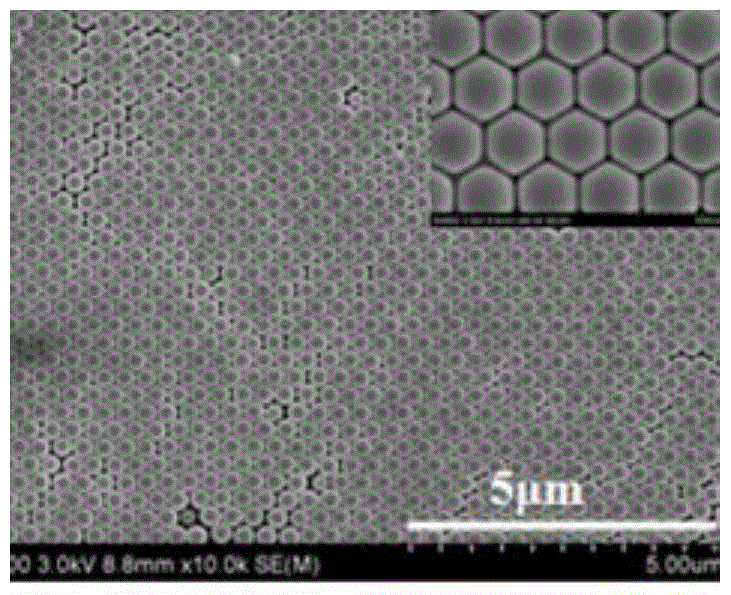
Preparation method of low-angle-dependence red polystyrene colloidal crystal film
InactiveCN105713214AImprove reflectivityReduce reflectivityVacuum evaporation coatingSputtering coatingAngle dependenceCarbon film
The invention relates to a preparation method of a low-angle-dependence red polystyrene colloidal crystal film, and belongs to the technical field of photonic crystal structure color preparation.The method comprises the steps that a mother solution of PS microspheres with the average particle size of 440+ / -10 nm is taken and diluted into an emulsion with the PS microsphere concentration of 0.1 wt%-0.5 wt% by taking deionized water as solvent, and the emulsion is put in a glass ware to be subjected to ultrasonic dispersion for 30-60 min; a cleaned substrate is vertically fixed in the dispersed PS emulsion, then the PS emulsion is put into a drying oven to be slowly dried, and the drying temperature is controlled to range from 40 DEG C to 65 DEG C; the surface of an assembled PS colloidal crystal film is plated with a carbon film with the thickness of 5-10 nm through a steaming plating instrument, a light absorption background is provided, the reflectivity in a photonic forbidden band is enhanced, the reflectivity to wavelengths beyond the forbidden band is reduced, and stray light is absorbed; color generation on a macro level shows low angle dependence, and the single red color not the rainbow color is presented.
Owner:SHAANXI UNIV OF SCI & TECH
Rock polarizing sheet base material storage medium as well as manufacturing method and application thereof
ActiveCN111679452ANon-reproducibleEasy to manufactureDigital storageNon-linear opticsLaser etchingIdentity recognition
The invention provides a rock polarizing sheet base material storage medium and a manufacturing method and application thereof. The rock polarizing sheet base material storage medium comprises a storage medium and jewelry which are manufactured by using gem and jade leftover materials and part of rock specimen sheets in a geology research process as raw materials, and a manufacturing method and application thereof. Rotation discoloration of jewelry in polarized light is achieved through the first polaroid, the fixing layer, the bearing, the rock slice, the second polaroid and other components,data storage is achieved through a laser etching method, and comprehensive utilization of rock leftover materials is achieved. Moreover, no two identical rocks exist in the world, so that the productprovided by the invention cannot be counterfeited; the polarized jewelry disclosed by the invention can be used for identity recognition without additionally implanting electronic equipment into thejewelry, and an unexpected identity recognition effect is generated on the basis of the decoration effect of the jewelry. When used as a black box or a space detector storage medium, the storage medium can be more resistant to high temperature, corrosion and radiation than a conventional storage medium.
Owner:INST OF GEOCHEM CHINESE ACADEMY OF SCI
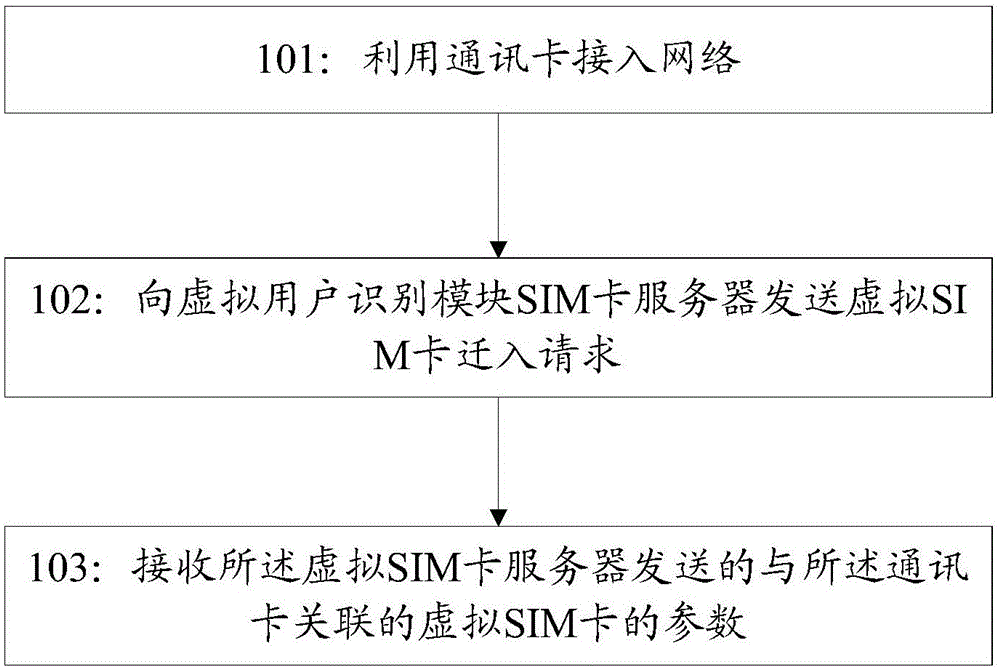
Migration method and system for virtual subscriber identity module (SIM) card, terminal and server
ActiveCN106535156AImprove experienceNon-reproducibleSecurity arrangementNetwork data managementSubscriber identity moduleComputer module
The invention discloses a migration method and system for a virtual subscriber identity module (SIM) card, a terminal and server. The method comprises the following steps: accessing a network by a communication card; sending a virtual SIM card immigration request to a virtual SIM card server; after identity authentication of the communication card of the terminal by the virtual SIM server passes, allocating a virtual SIM card associated with the communication card; and receiving parameters, which are transmitted by the virtual SIM card server, of the virtual SIM card associated with the communication card.
Owner:ZTE CORP
Random texture anti-counterfeiting mark structure and anti-counterfeiting method
PendingCN109427240ANon-reproducibleImprove reliabilityStampsIdentification meansFibrous bodyPattern recognition
Owner:BEIJING KESIYUAN TECH
Tool and method for weaving weft arc fabric of sample weaving machine
The invention discloses a tool and a method for weaving weft-direction arc-shaped fabrics for small prototypes, belonging to the technical field of textiles. On the prototype machine frame; input the pattern board diagram, after starting the working state, the warp yarn will automatically form a shed according to the pattern board data, and then manual weft insertion and beating can be performed; after the weft yarn is introduced into the shed, the beating wood knife is put into the shed. The reed is parallel to the reed. As the reed beats to the front of the machine, the wavy side of the wooden knife pushes the introduced weft to the loom; the reed is reset, and the pattern plate data is changed to the next weft through the induction system, thereby forming a new weft. the shed. Compared with the prior art, in the present invention, the warp and weft yarns are continuously interwoven, and the weft yarns are fixed in a wavy shape, and are arranged with different colors and wefts, so as to weave a characteristic fabric with wavy weft yarns, so that each piece of fabric has an inexhaustible texture. Reproducibility, clean fabric surface, clear texture, great style.
Owner:ZHEJIANG TEXTILE & FASHION COLLEGE
Payment method and payment system
InactiveCN102682381AImprove securityImprove precision and safetyProtocol authorisationInformation deliveryFingerprint database
The invention relates to a payment system, comprising a user terminal, an information transmitting system, a fingerprint input system, a financial system and a fingerprint database; the user terminal and the information transmitting system are respectively communicated with the financial system in a wire or wireless mode; the fingerprint input system also is communicates with the fingerprint database in the wire or wireless mode, wherein the user terminal comprises a financial service terminal for recording personal financial information of users and a mobile communication terminal for recording personal communication information of users, which are commonly contained in a mobile communication device; the personal communication information is bound with corresponding personal financial information and / or fingerprint information; when the financial service terminal is communicated with the financial system successfully, and trading payment is finished, the financial system feeds trading finish information back to the mobile communication terminal. The invention further provides a payment method. The payment system and the payment method have convenience for use and also have high security for trading so as to fundamentally eliminate phenomenon that cards are embezzled.
Owner:王涛
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com