FPGA-based multi-algorithm security encryption authentication system and method
A security encryption and authentication system technology, applied in the field of encryption authentication, can solve the problems of easy to be attacked to read important data, complex structure of traditional encryption chips, low selectivity, etc., to improve anti-counterfeiting and anti-attack capabilities, strong defense security Risk capability and the effect of improving the safety level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
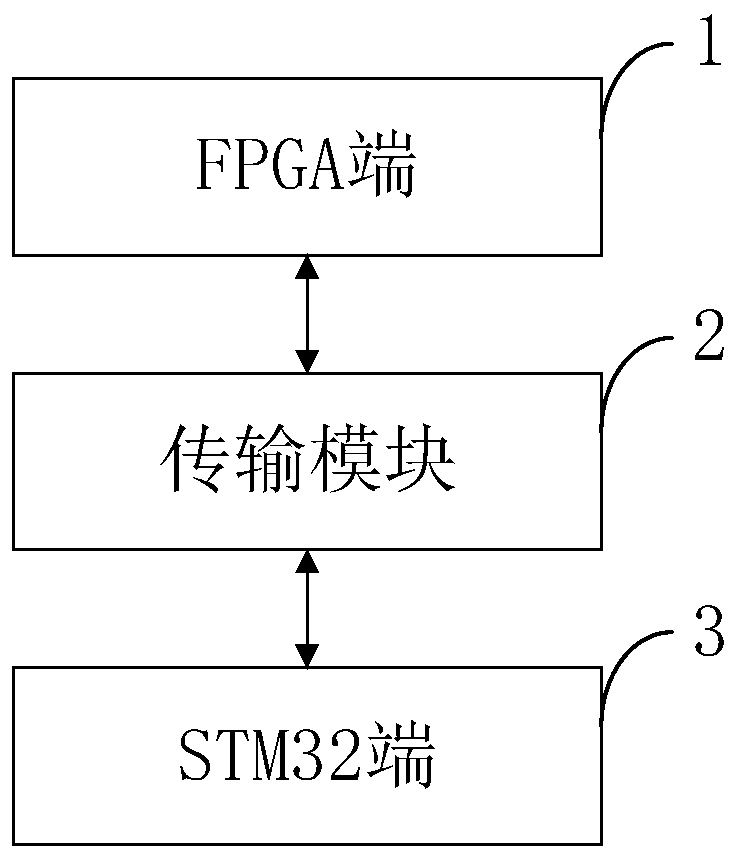
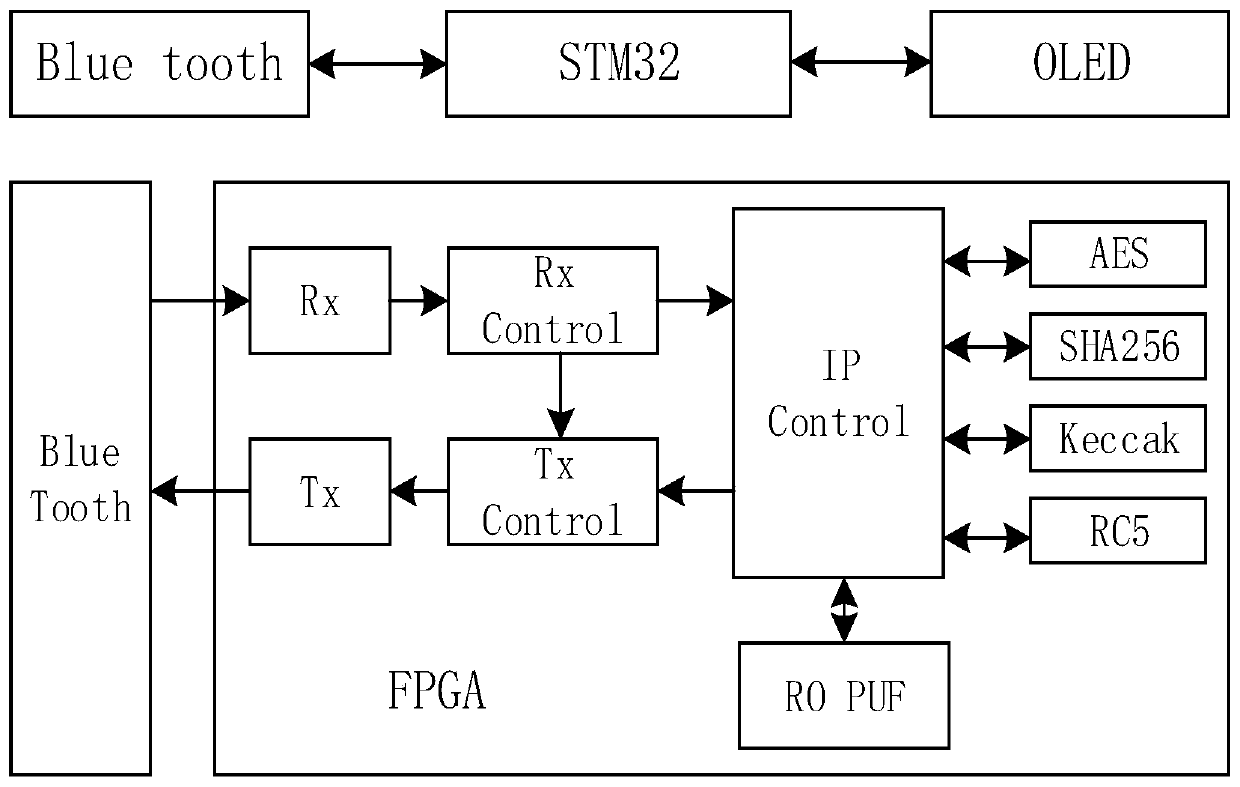
[0136] 1. The entire encryption authentication system is divided into two parts. The FPGA side is the implementation part of the encryption authentication chip, and the STM32 side is the configuration and verification part of the encryption authentication chip. The instructions and data are transmitted between the two parts through the serial port Bluetooth. Such as figure 2 As shown, the system hardware modules include: EES-303 FPGA core board, STM32F103C8T6 core board, 128*64 resolution OLED display and two HC-05 serial port Bluetooth modules.
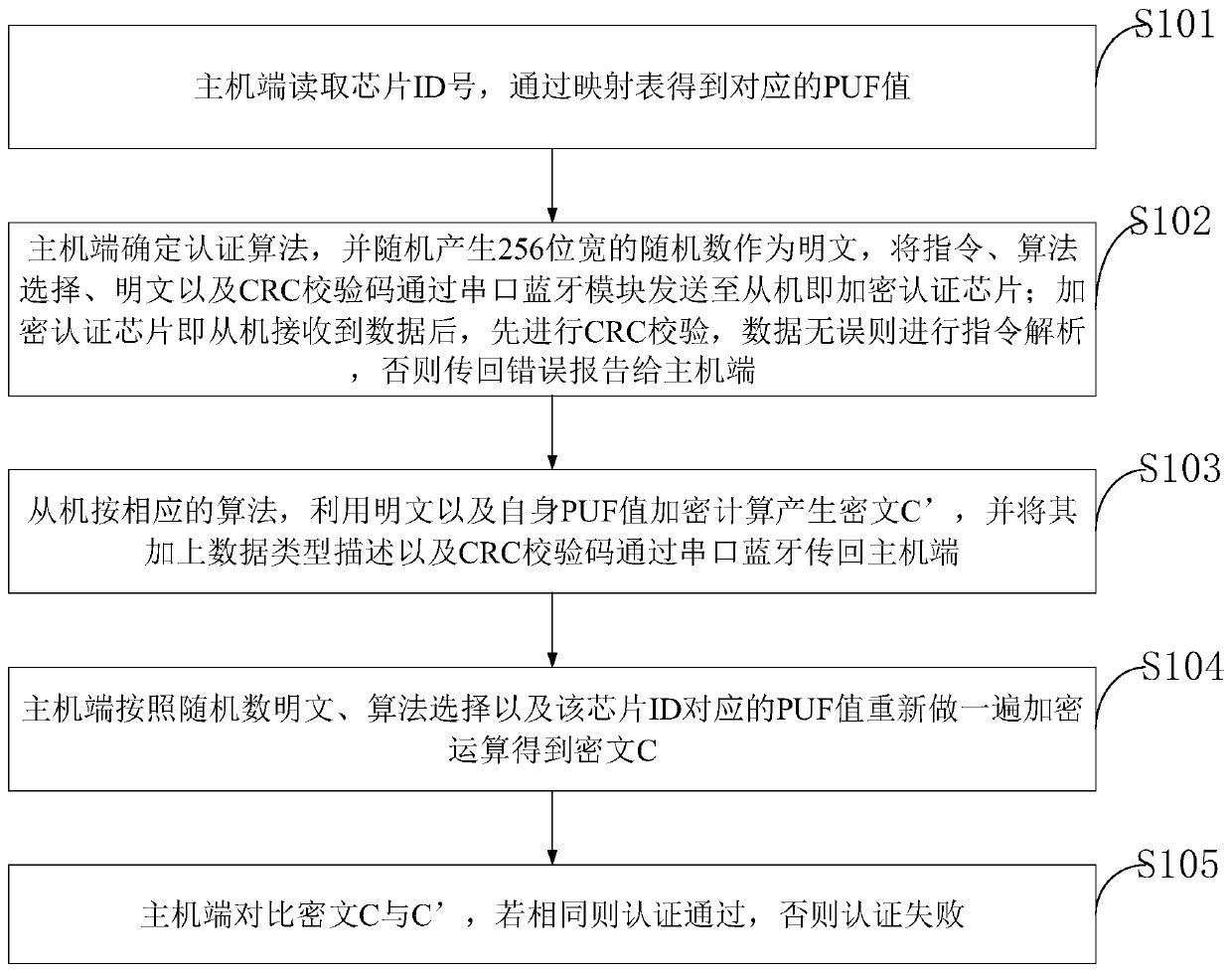
[0137] The FPGA design includes a serial port transceiver module, a serial port input control module, a serial port output control module, an algorithm control module, four algorithm IP modules, and a RO PUF module; chip configuration and certification programs are programmed in STM32. After the system is powered on, the RO PUF module is initialized, reads the DNA code in the Xilinx FPGA chip, and takes the last 32 bits as the ID of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com