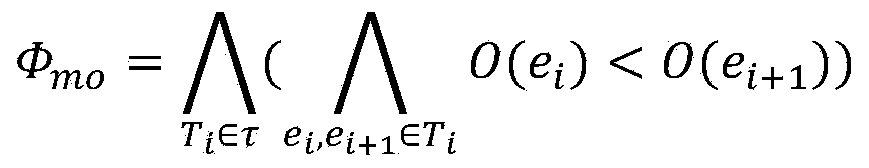Patents
Literature
173 results about "Verification problem" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Hash tree-based data dynamic operation verifiability method
InactiveCN103218574AReliable communication channelShorten the timeDigital data protectionThird partyData file
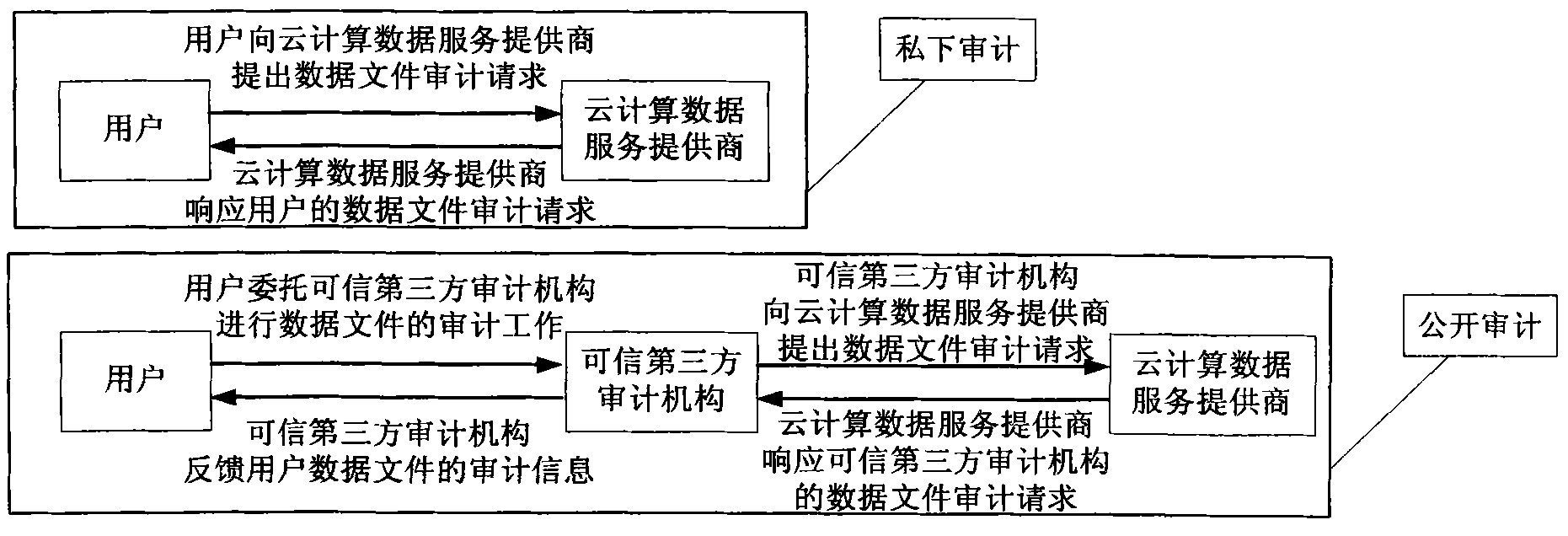
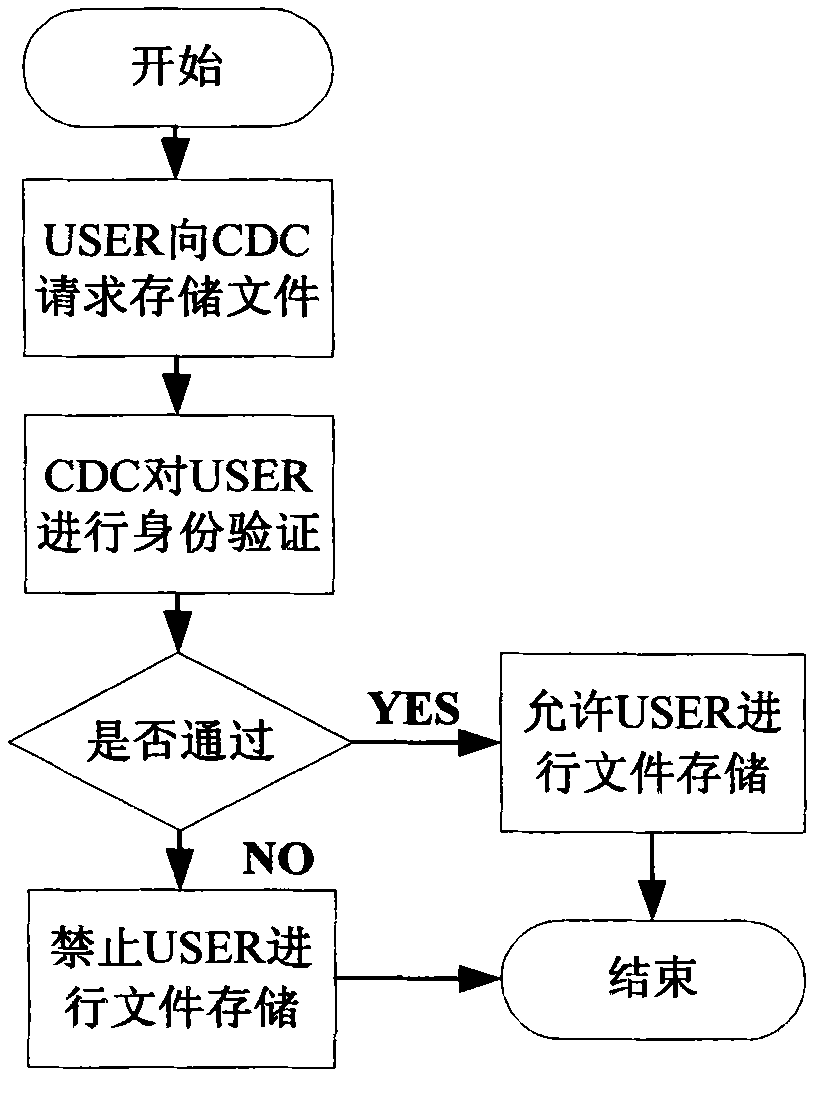
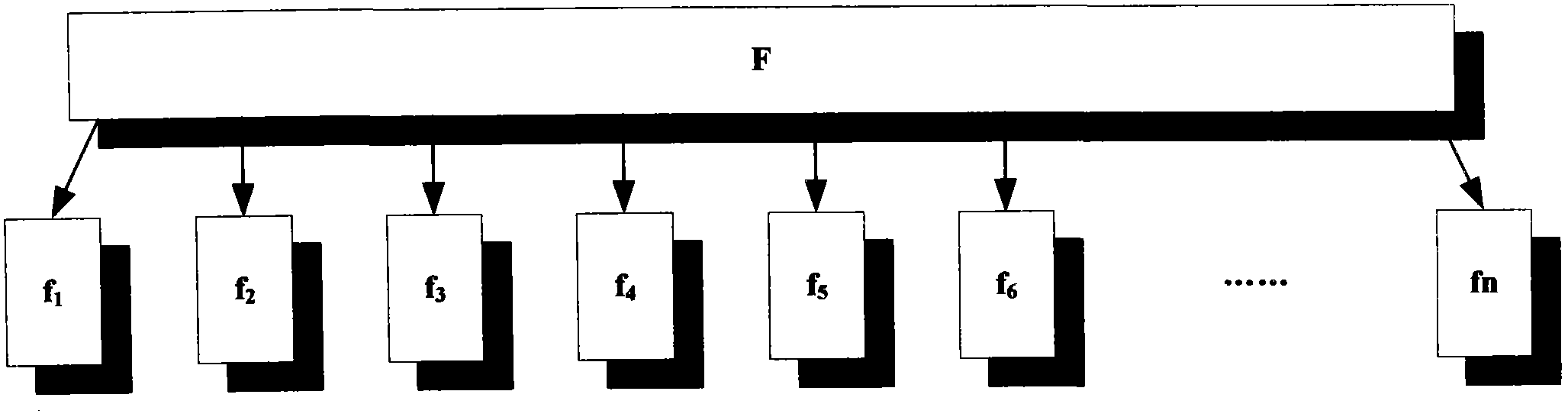
The invention discloses a hash tree-based data dynamic operation verifiability method, which consists of three parts, i.e., a USER, a cloud data center (CDC) and a third party administrator (TPA) connected through a communication network, wherein the USER is used as a party of making a data memory service request, who hopes to store a data file owned by the party into a cloud storage space of the cloud data center, and can be both a personal user and an enterprise user; the CDC is used for responding to the data storage service request of the USER, storing the data file of the USER into the huge data center of the CDC according to a certain rule and managing and maintaining the data file; and the TPA is used as a reliable TPA and is commissioned by the USER to check the completeness and the consistency of the data file stored in the CDC data center. According to the hash tree-based data dynamic operation verifiability method, the verification problem of the completeness and the consistency of the user data file under a cloud computing environment is solved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
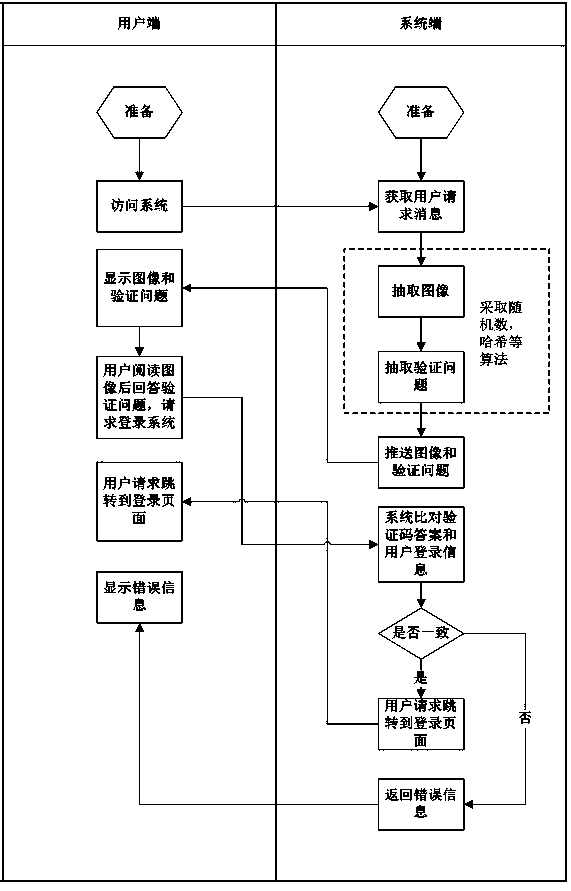
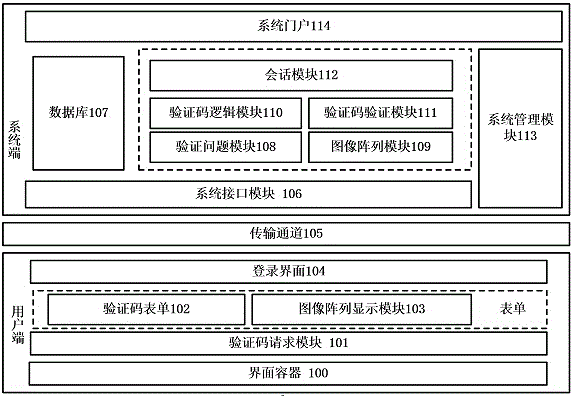
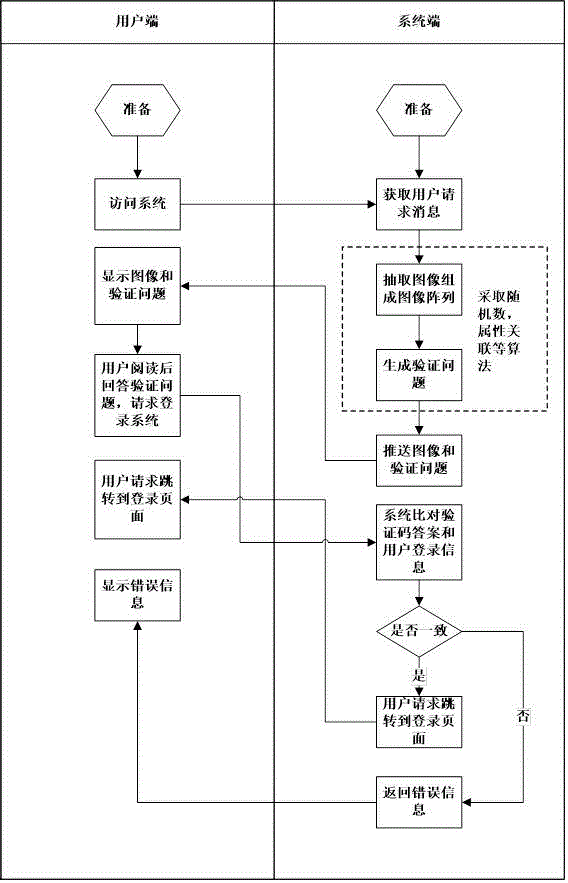
Verification code based on image content
InactiveCN103428163AClear imagingEasy to readDigital data authenticationTransmissionProgramming languageUser verification
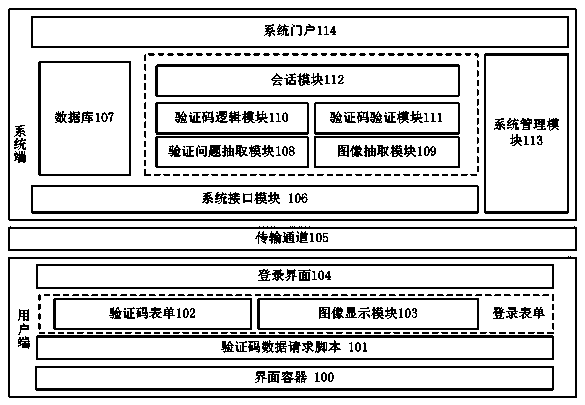
The invention discloses a verification code based on image content. A verification code system comprises a verification code module, a service logic module, a database and the like. According to the verification code, images are selected through the system according to selection rules, verification questions based on image content semantics are selected from content based on image targets, the verification questions are displayed at a user access terminal, a user is required to answer the verification questions as the verification code, the user reads the images and the verification questions to fill in the verification code, the system compares verification answers filled in by the user with corresponding answers of the verification questions corresponding to the selected images, and if the verification answers filled in by the user are consistent to the corresponding answers, the verification code of the user is correct. By means of the verification questions generated on the basis of the image semantics and the corresponding verification code serving as the answers, safety of the verification system is improved, and automatic identification of a machine program is effectively prevented.
Owner:SHANGHAI BOLU INFORMATION TECH
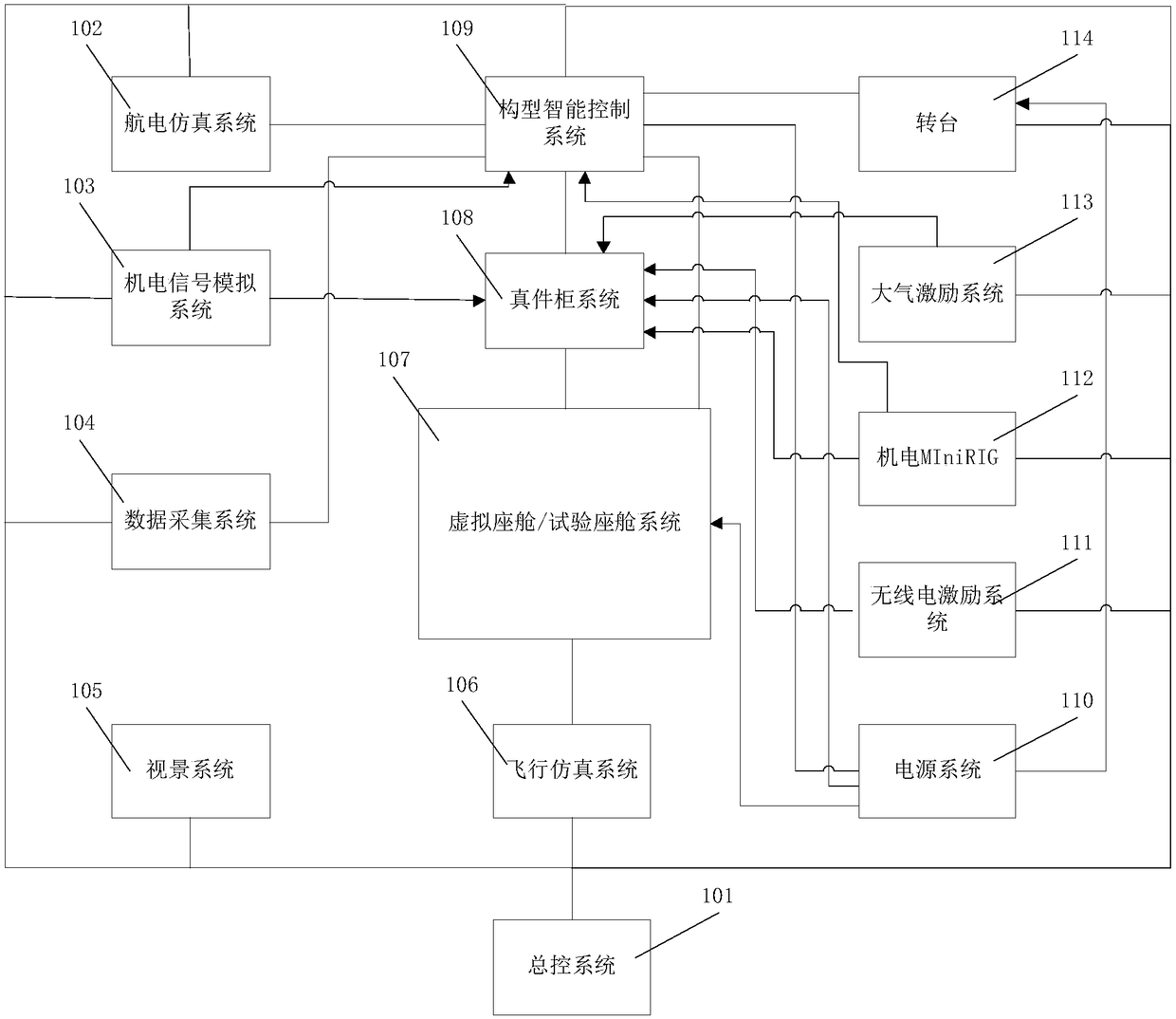
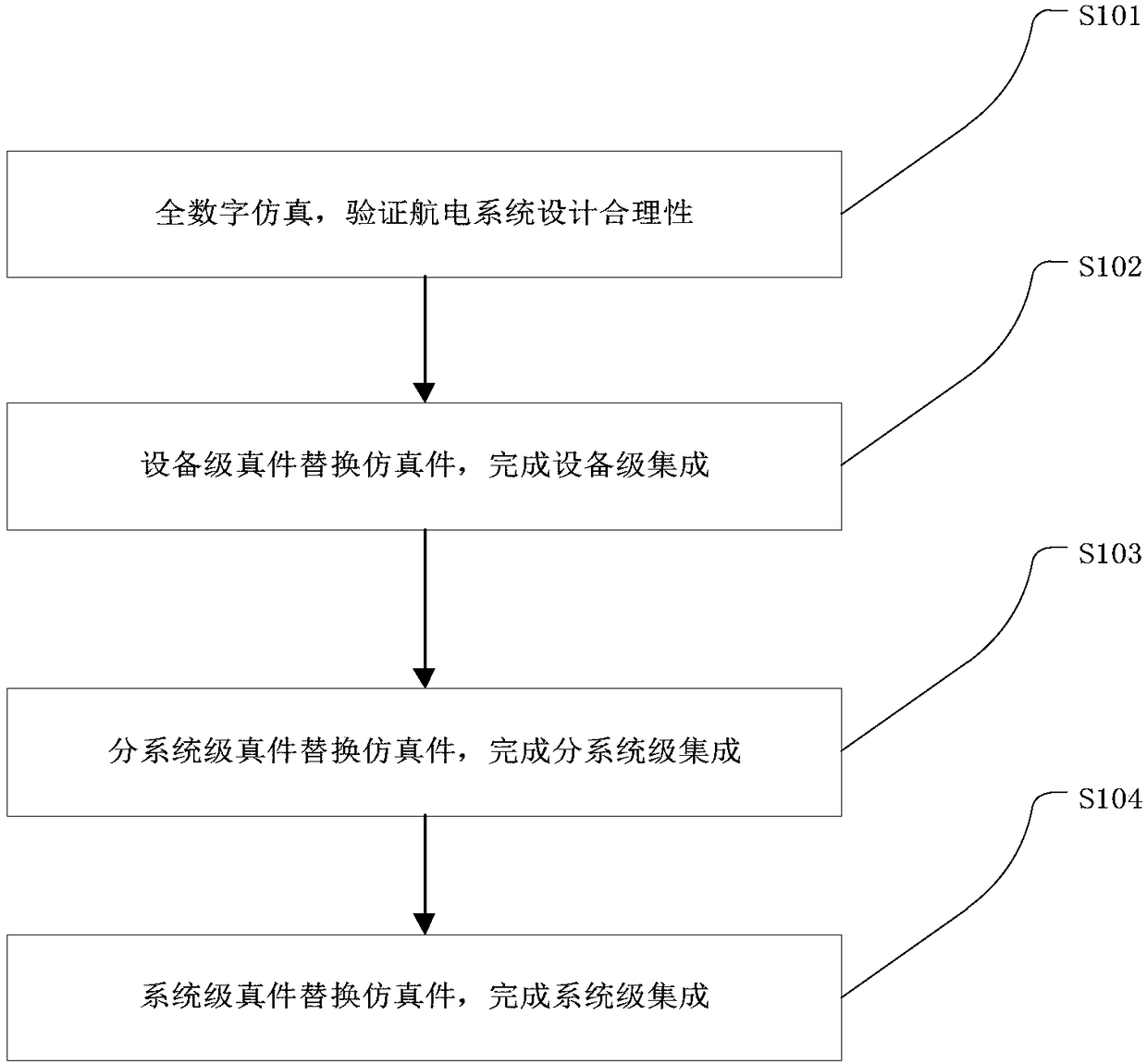
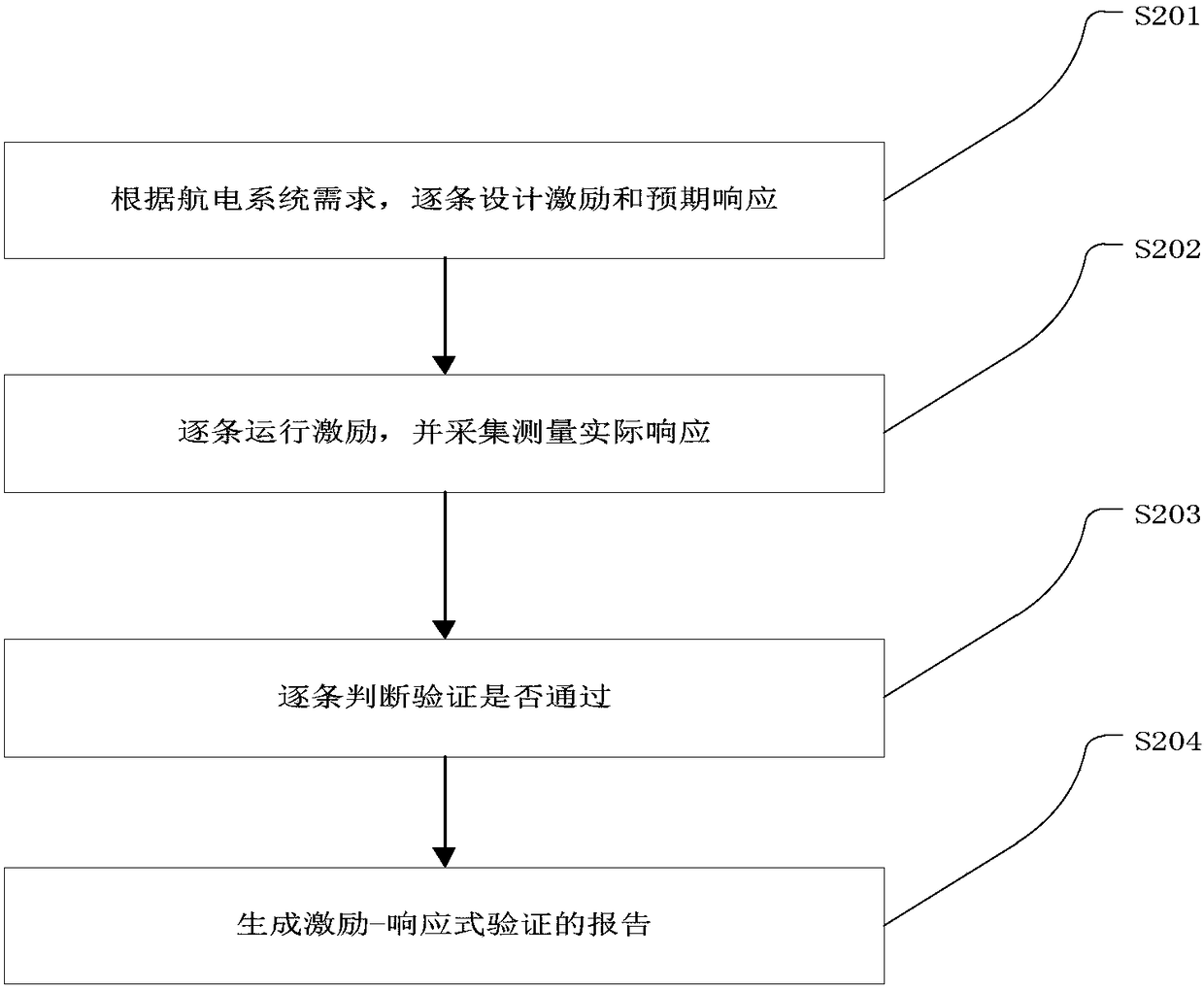
Flexible test platform for avionic system and avionic integration and verification methods
PendingCN108196141AEasy to implementLow accuracyTesting electric installations on transportElectricityValidation methods
The invention discloses a flexible test platform for an avionic system and avionic integration and verification methods. The integration method comprises the step of incremental-type system integration on the basis of simulation, and the verification method comprises the steps: excitation-response verification and dynamic integrated verification. The platform comprises a general control system (101), an avionic simulation system (102), a configuration intelligent control system (109), a rotary table (114), an electromechanical signal simulation system (103), a real cabinet system (108), a atmospheric excitation system (113), a data acquisition system (104), a virtual cabin / test cabin system (108), an electromechanical MIniRIG (112), a radio excitation system (111), a visual system (105), aflight simulation system (106) and a power system (110). According to the invention, the platform and methods can solve problems of integration and verification of large-scale avionic systems, improve the integration efficiency, reduce the manpower and time cost, improve the verification comprehensiveness and accuracy, and achieve the intelligent and automatic test.
Owner:中航通飞华南飞机工业有限公司
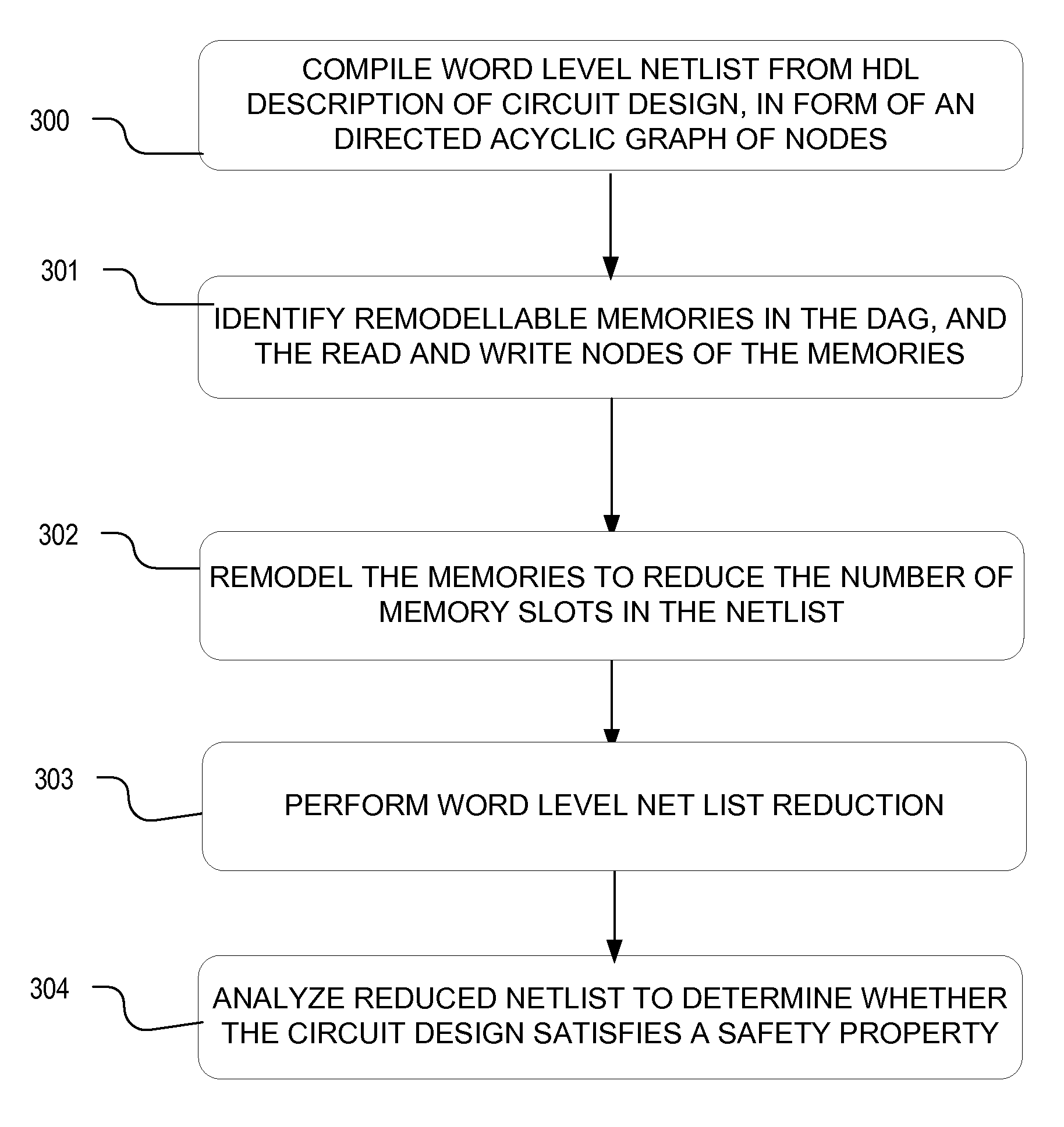
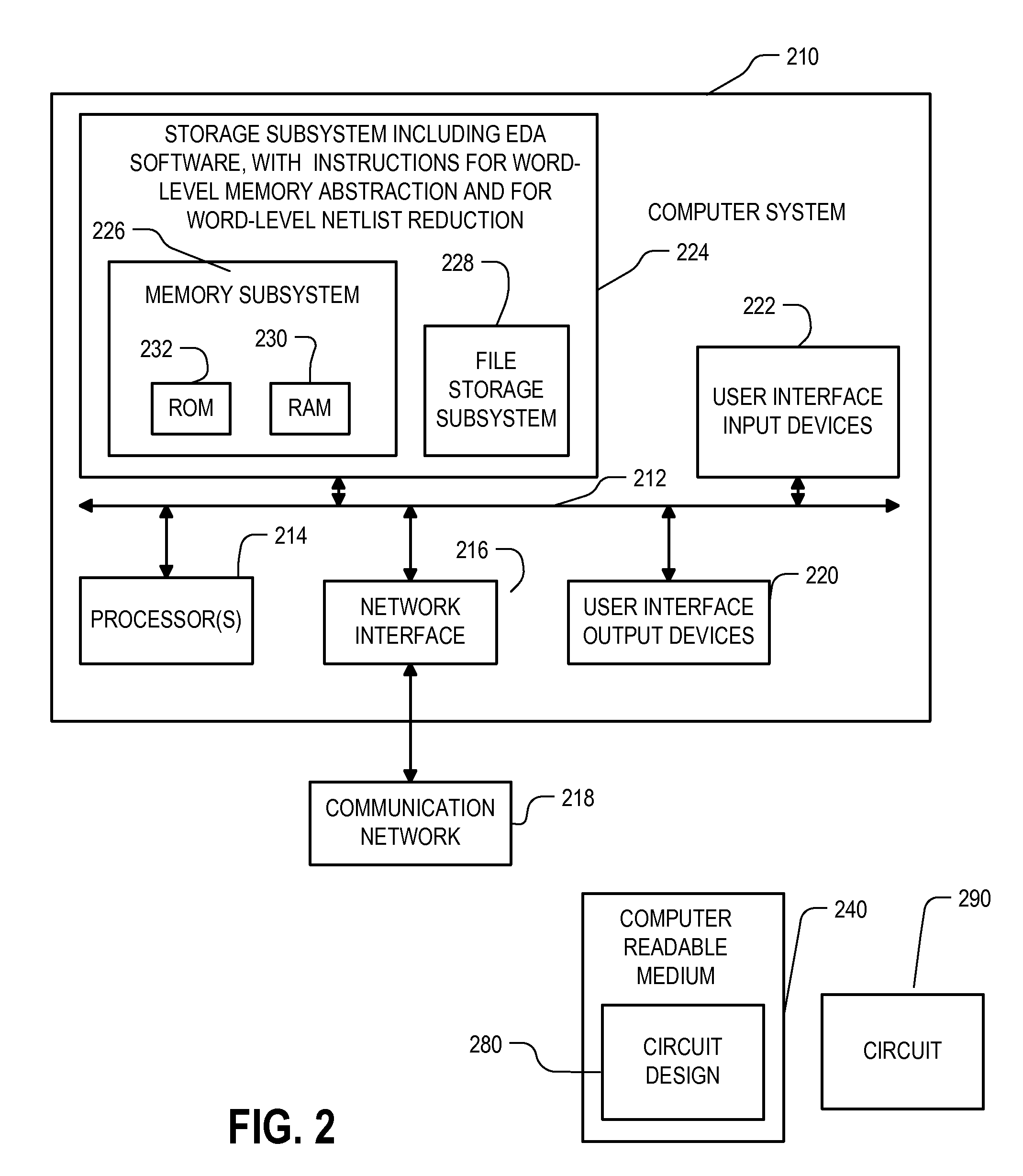
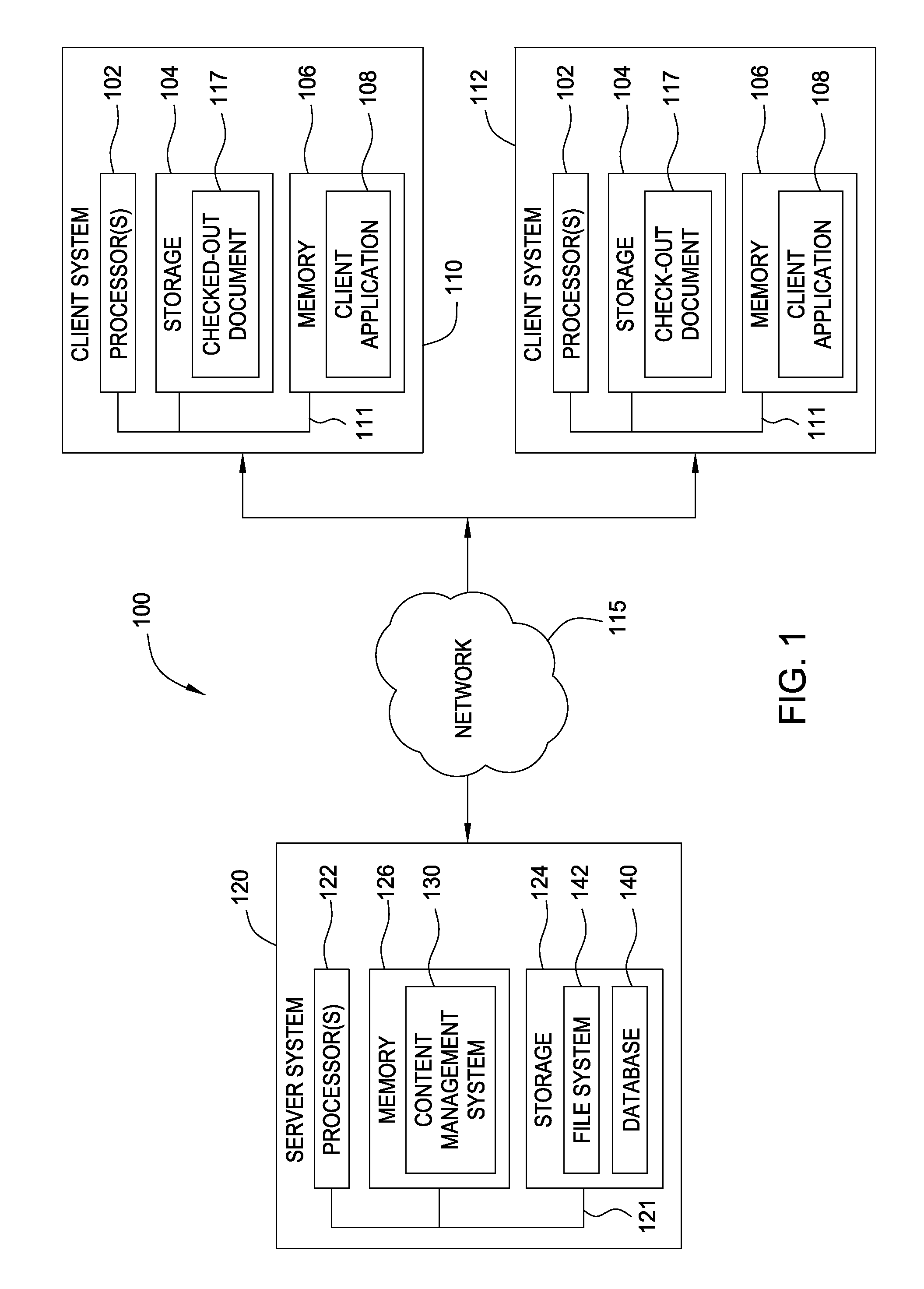
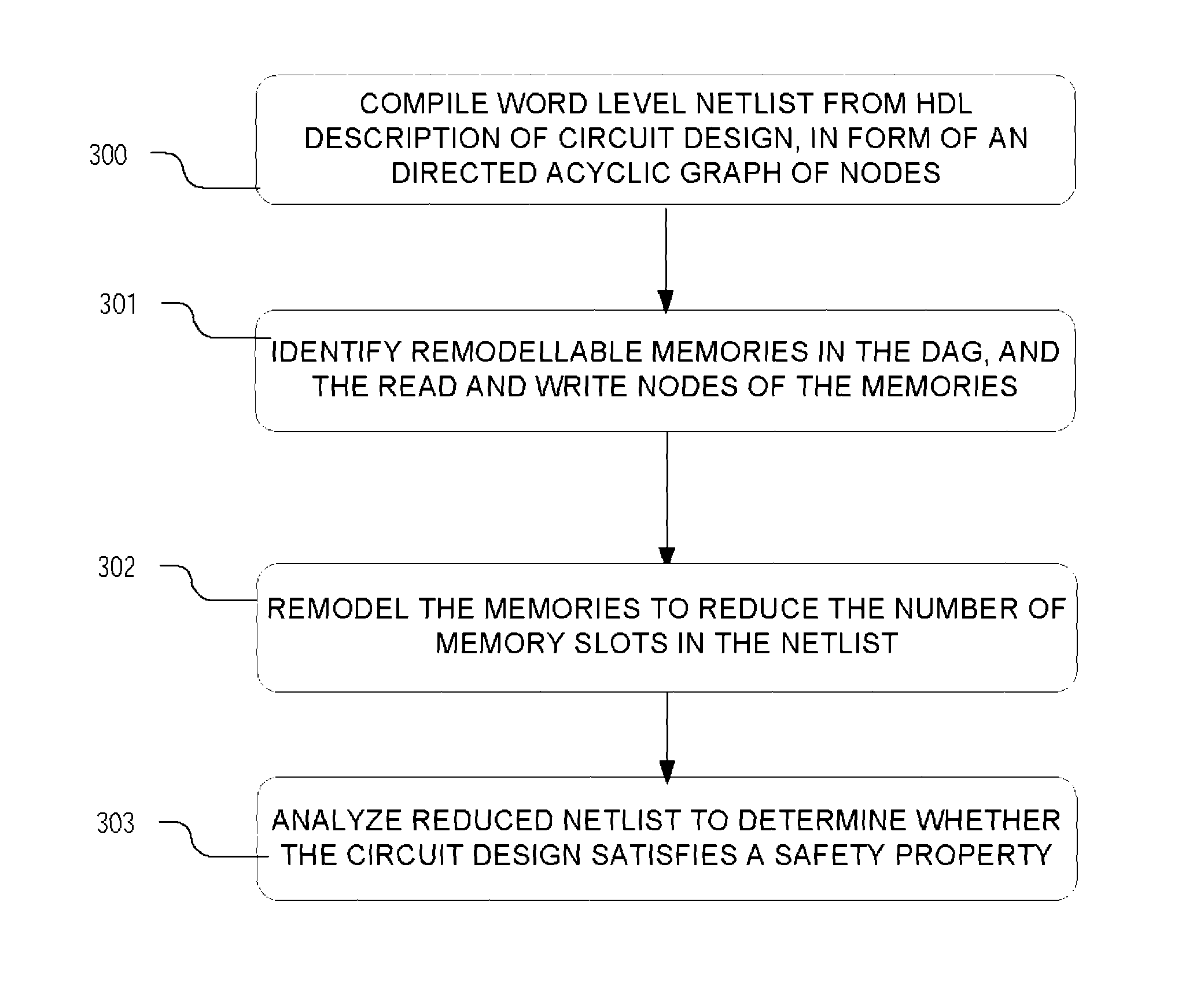
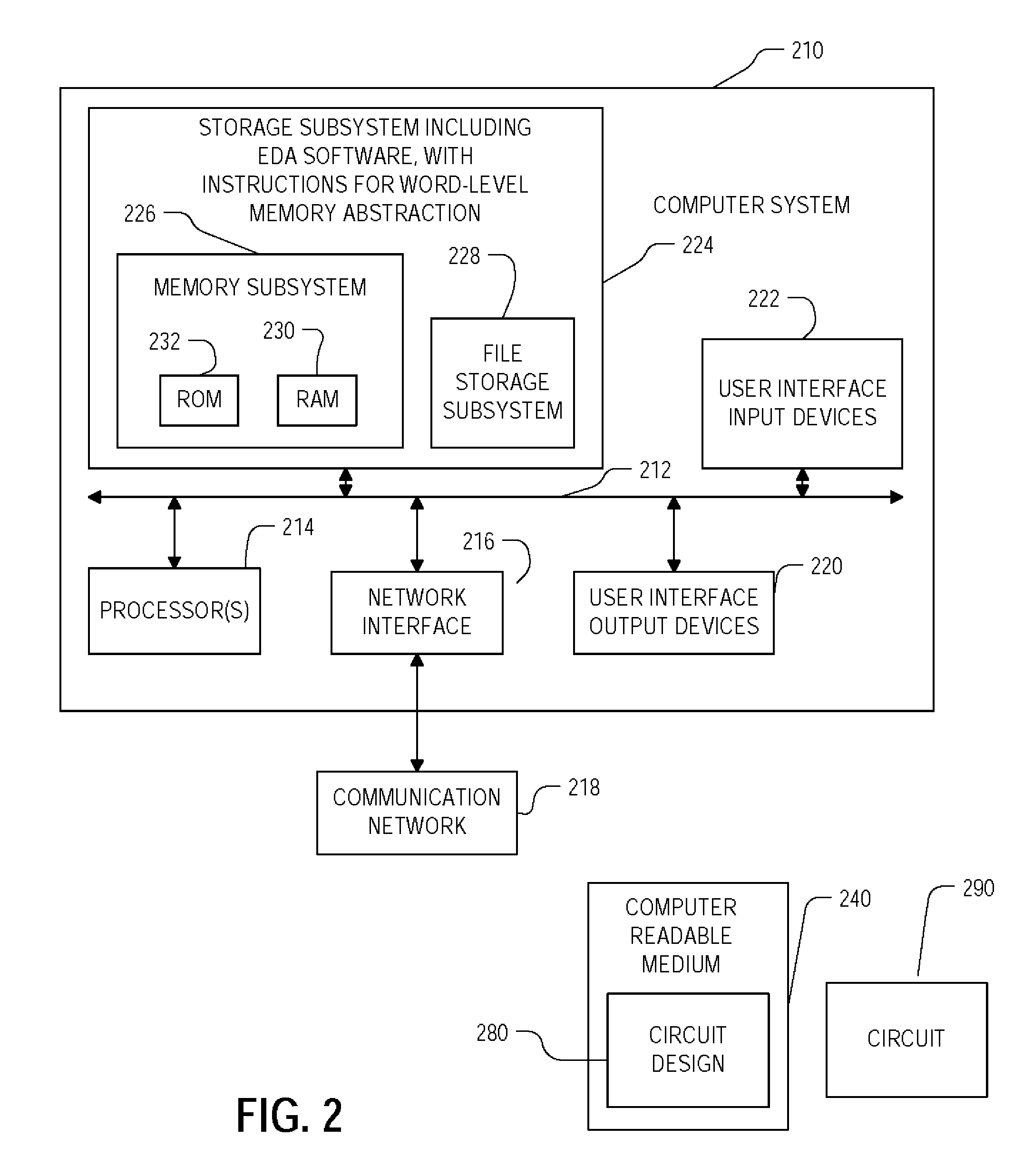
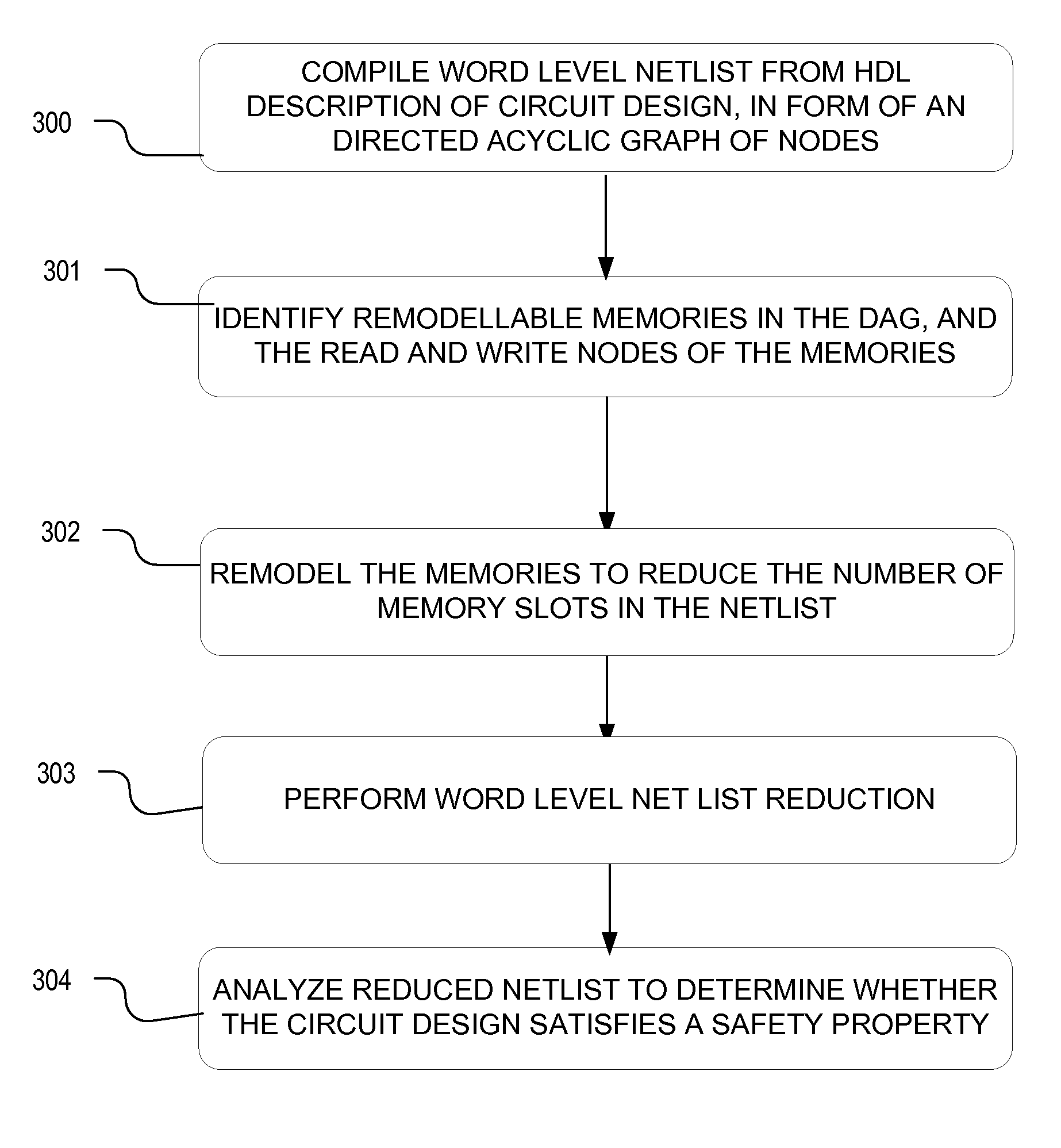
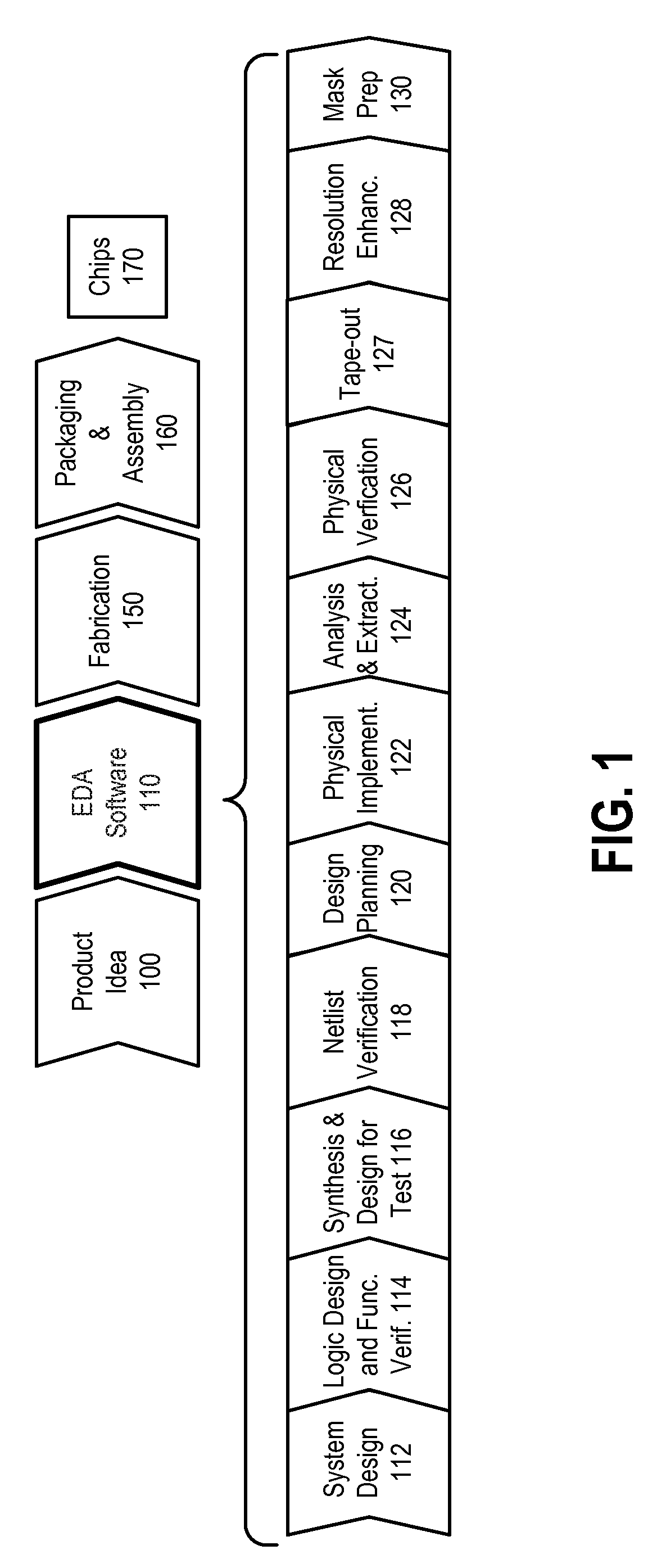
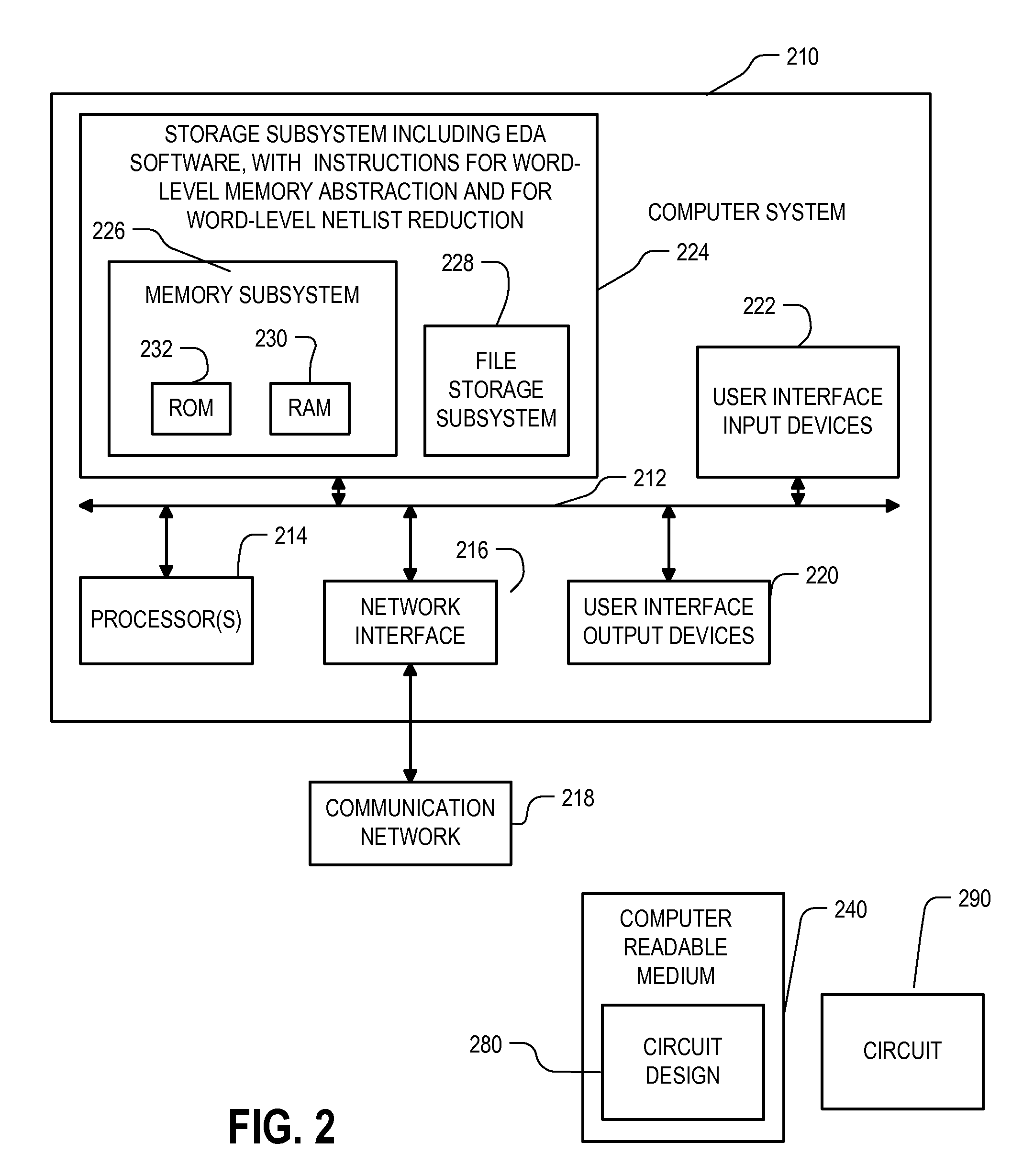
Method and apparatus for memory abstraction and for word level net list reduction and verification using same
ActiveUS20100107132A1Reduce decreaseReduced netlistComputer aided designSoftware simulation/interpretation/emulationNetlistCircuit design
A computer implemented representation of a circuit design including memory is abstracted to a smaller netlist by replacing memory with substitute nodes representing selected slots in the memory, segmenting word level nodes, including one or more of the substitute nodes, in the netlist into segmented nodes, finding reduced safe sizes for the segmented nodes and generating an updated data structure representing the circuit design using the reduced safe sizes of the segmented nodes. The correctness of such systems can require reasoning about a much smaller number of memory entries and using nodes having smaller bit widths than exist in the circuit design. As a result, the computational complexity of the verification problem is substantially reduced.
Owner:SYNOPSYS INC
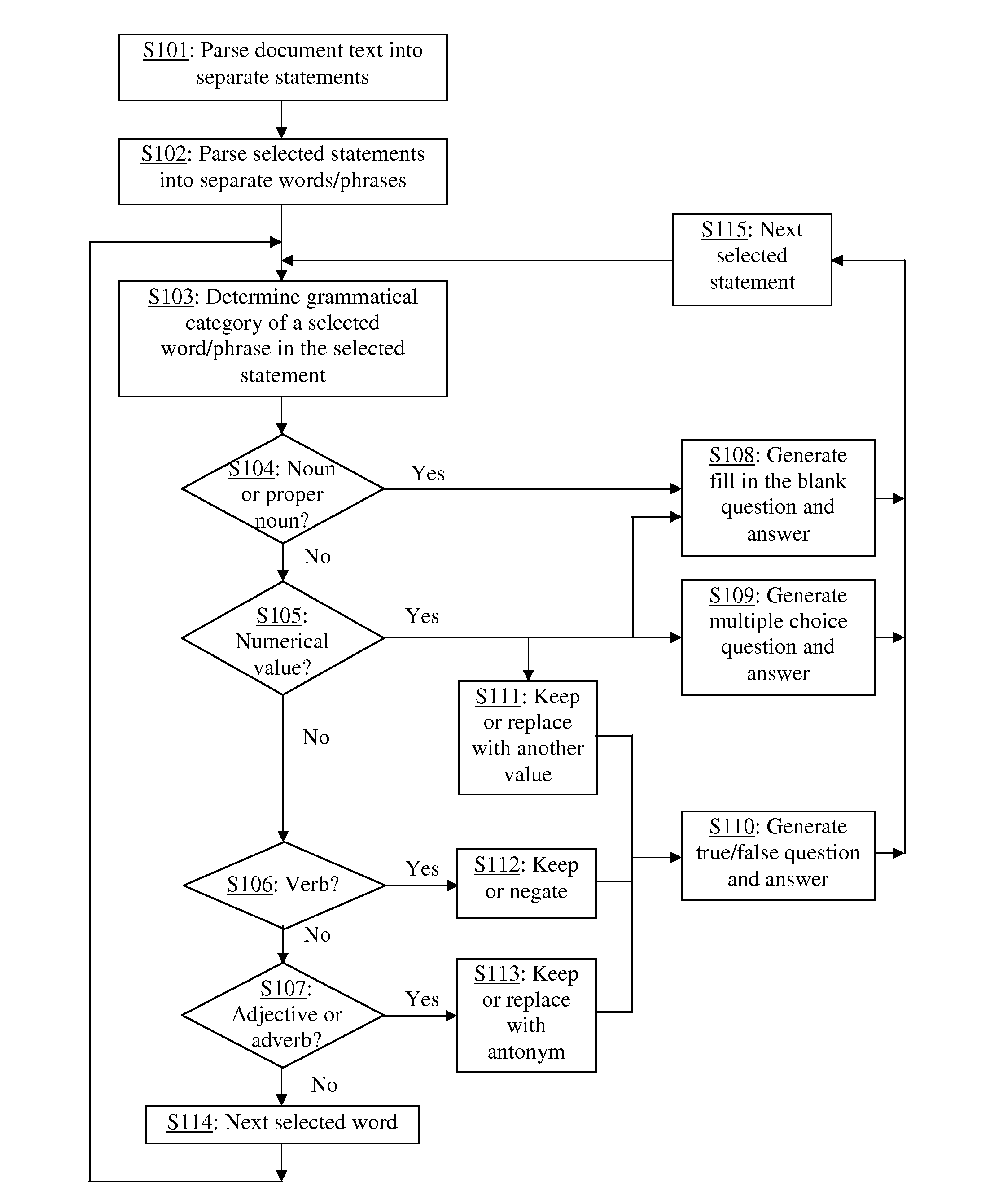
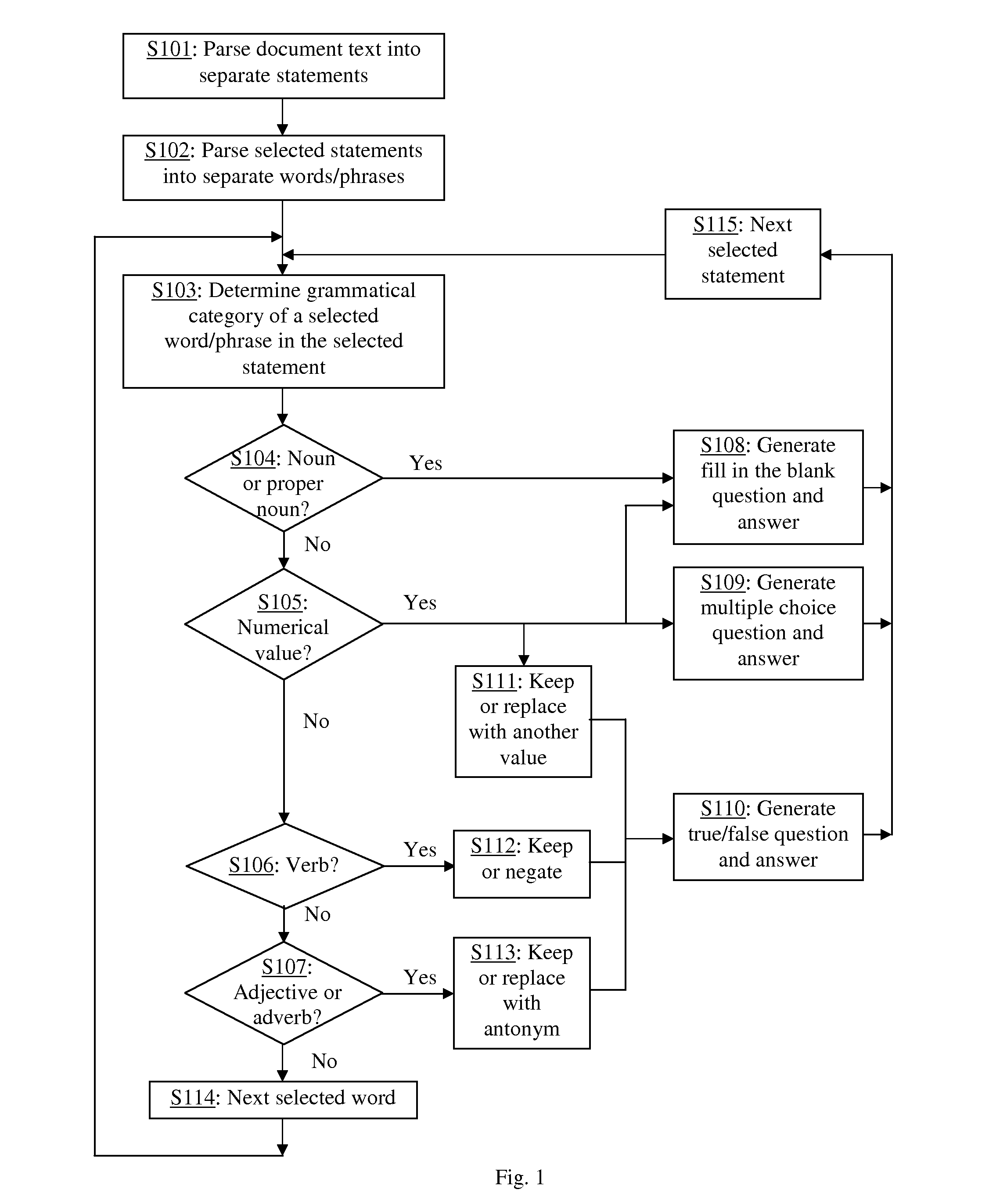
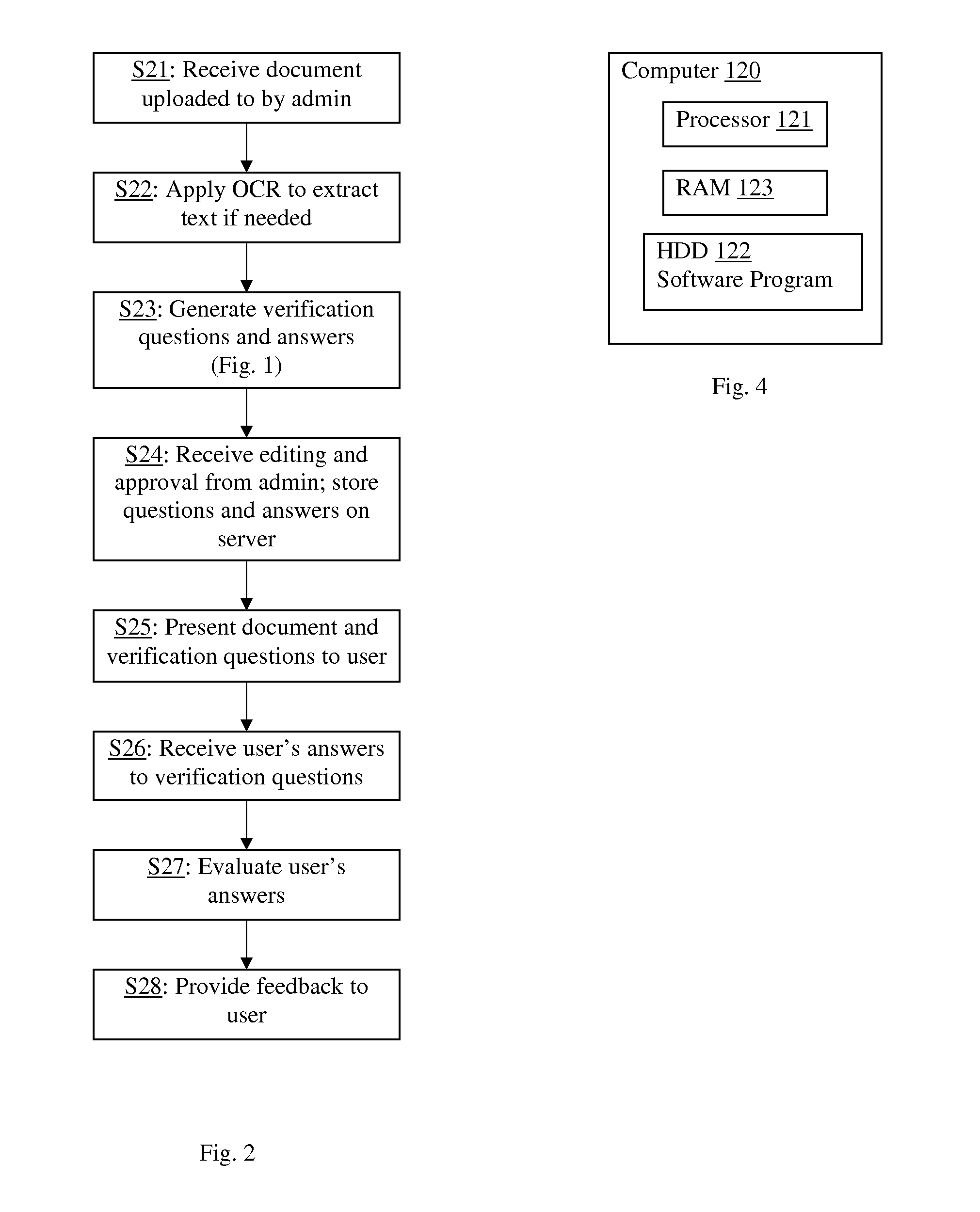
Automatic generation of verification questions to verify whether a user has read a document
InactiveUS20150199400A1Save administrative timeAccurate materialsDigital data processing detailsRelational databasesDocumentation procedureComputer science
A method for automatically analyzing the text of a document to generate verification questions to be administered to a user as a quiz for the purpose of verifying whether the user has read the document. Syntactic analysis is applied to statements (e.g. sentences) in the text to automatically generate various types of verification questions, including fill-in-the-blank, true / false, and multiple-choice questions. Nouns and proper nouns in a statement may be used to generate fill-in-the-blank questions; numerical values may be used to generate fill-in-the-blank, true / false and multiple-choice questions; and verbs, adjectives and adverbs may be used to generate true / false questions. The questions may be generated dynamically for each user, or generated once, stored and used for multiple users.
Owner:KONICA MINOLTA LAB U S A INC
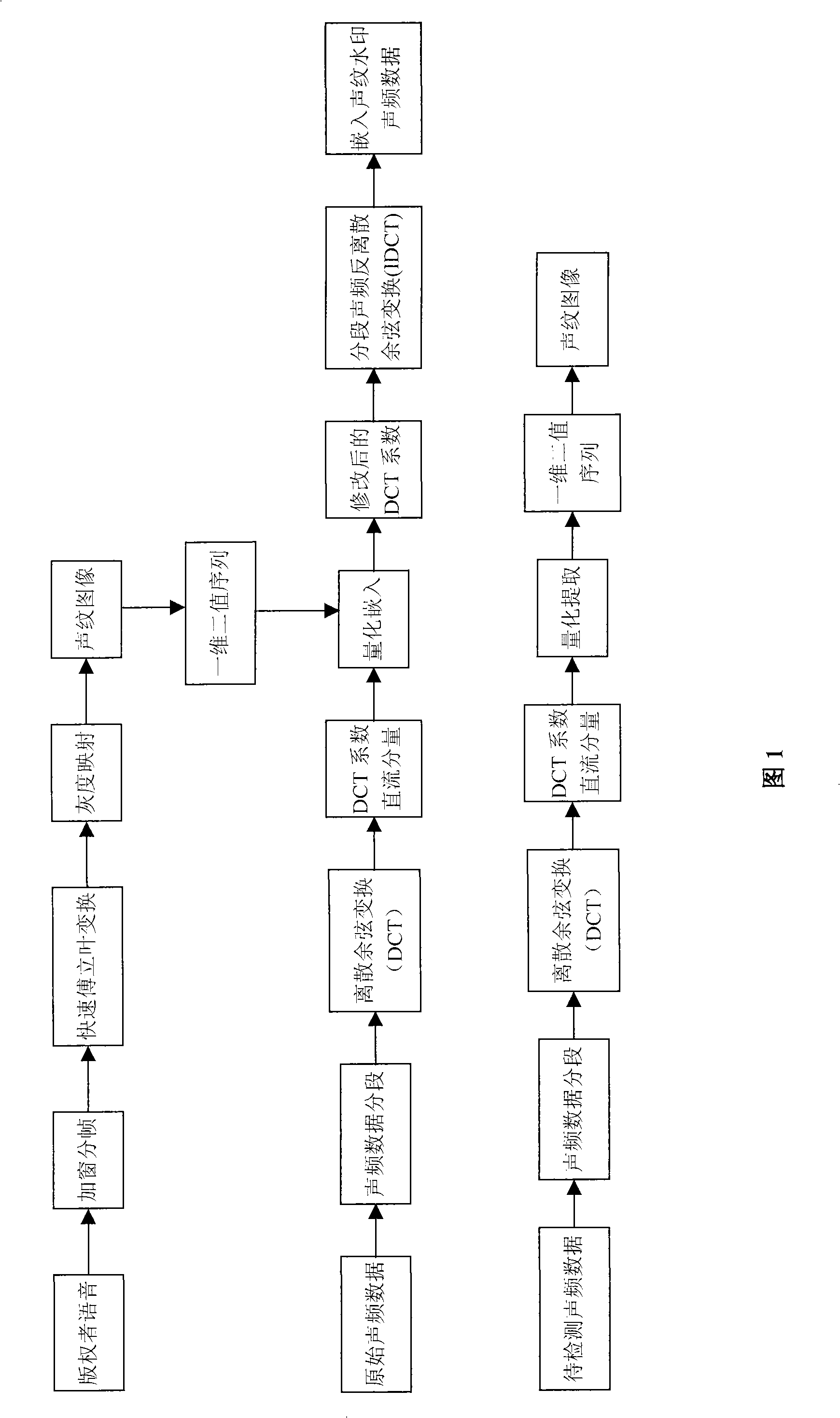
Digital watermark production and recognition method used for audio document
InactiveCN101345054AGuaranteed robustnessSolve the problem of copyright certificationSpeech analysisFrequency spectrumDigital watermarking
The invention discloses a digital watermark manufacture method and a recognition method used for audio files. The watermark is added in the audio digital file to be processed and taken as copyright marking information; the method of the invention is characterized in that the watermark is realized by adopting converted voiceprint information and comprises the steps as follows: a section of speech signals with copyright identification is colleted and a voiceprint watermark image is gained; the speech signal is converted into one-dimensional two-value sequence group; the gray-scale value of each matrix unit is presented by adopting an eight-bit binary number; the audio file where the watermark is to be inserted is divided into sections; frequency domain transformation is respectively carried out to each audio section so as to obtain the frequency spectrum file; a bit of one-dimensional two-value sequence group watermark data is embedded into each section of the frequency spectrum file; the embedding method is a method used for quantitatively modifying the frequency spectrum file coefficient; reverse conversion is carried out so as to obtain the audio data of the embedded watermark; the audio data is combined with the audio data which is processed so as to obtain the audio digital file with the digital watermark. Reverse separation operation is carried out during the recognition process. The method of the invention effectively solves the copyright verification problem of the digital audio product.
Owner:SUZHOU UNIV
Identity verification method and device
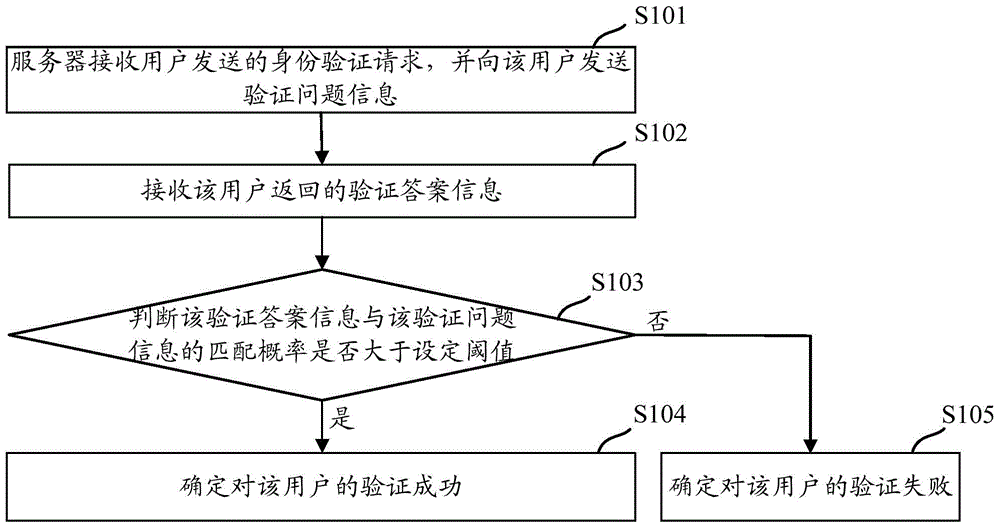
ActiveCN105471581AImprove securityImprove protectionUser identity/authority verificationAuthenticationVerification problem
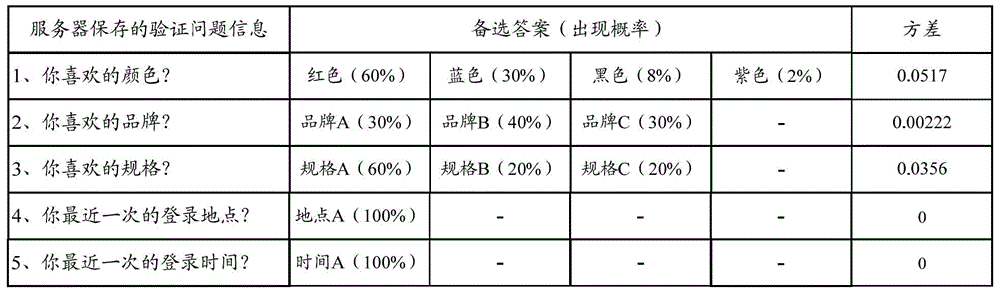
The invention discloses an identity verification method and device. The method comprises that a server receives an identity verification request sent by a user and sends verification problem information to the user; verification answer information returned by the user is received; according to the verification answer information and historical operation information of records of the user, the matching probability between the verification answer information and the verification problem information is determined; if the matching probability is greater than the set threshold, it is determined that verification of the user succeeds; and otherwise, it is determined that verification of the user fails. Historical operation information aimed at the user record changes dynamically, so that the matching probability changes dynamically instead of fixedly; and thus, the verification problem information is more reliable than a safety protection problem which is preset by the user and corresponds to the fixed answer, and the safety of user account is improved.
Owner:ADVANCED NEW TECH CO LTD
Characters per second (CPS) Modeling and verification method based on model transformation
InactiveCN102436375ASpecific program execution arrangementsValidation methodsUnified Modeling Language
The invention provides a characters per second (CPS) modeling and a verification method based on model transformation, which is mainly used for processing the CPS modeling and attribute verification problems. The related key operation includes that (1) adopting Hybrid (unified modeling language) UML to conduct CPS modeling, transforming the built Hybrid UML model into operation model Hybrid Programs of a differential dynamic logic method, defining regulations for the model transformation according to the relation of elements between the Hybrid UML and a Hybrid Programs meta-model, generating a template which the regulations are applied to, and performing model transformation to automatically generate the Hybrid Programs according to the model level application regulation; and (2) generating input codes on the obtained Hybrid Programs according to the input form of a theorem prover KeYmaera, and performing reasoning and verification in the KeYmaera.
Owner:SOUTHEAST UNIV
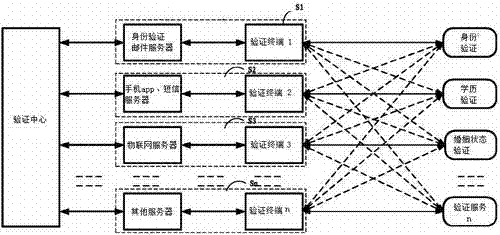
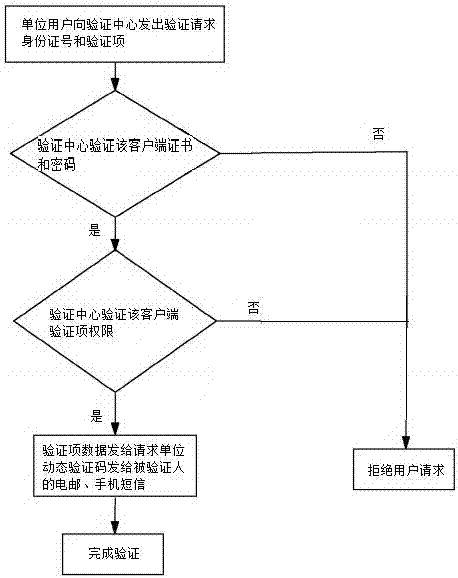
Comprehensive verification system and method for identities and documentary evidences
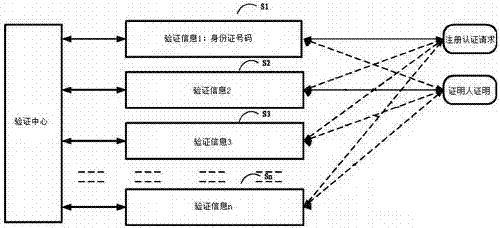
InactiveCN103944719AIncrease flexibilityImprove reliabilityUser identity/authority verificationDigital data authenticationEmail addressValidation methods
The invention relates to a comprehensive verification system and method for identities and documentary evidences, and belongs to comprehensive credential verification systems and methods. According to the comprehensive verification system, a verification system website is established, and the verification system website serves as a verification center; the verification system website is connected with a terminal of the verification system website through a network to form a verification network system. Individual registration information and unit registration information are included in the verification system website, and are the bottom layer basic information of the verification system website. According to the method, a registration method and a verification method are included, unique verification email addresses are automatically generated by using identity numbers and organizing institution codes and serve as verification bases, and simple, convenient and reliable verification is achieved. Wrong identity cards, repeat identity cards and fake identity cards can be conveniently and fast found and screened, and the problem of train ticket wiped by ticket touts can be solved; fake official seals and credentials can be identified; the problem of social insurance and birth certificate verification can be solved.
Owner:SHANGQING IND SHANGHAI +1
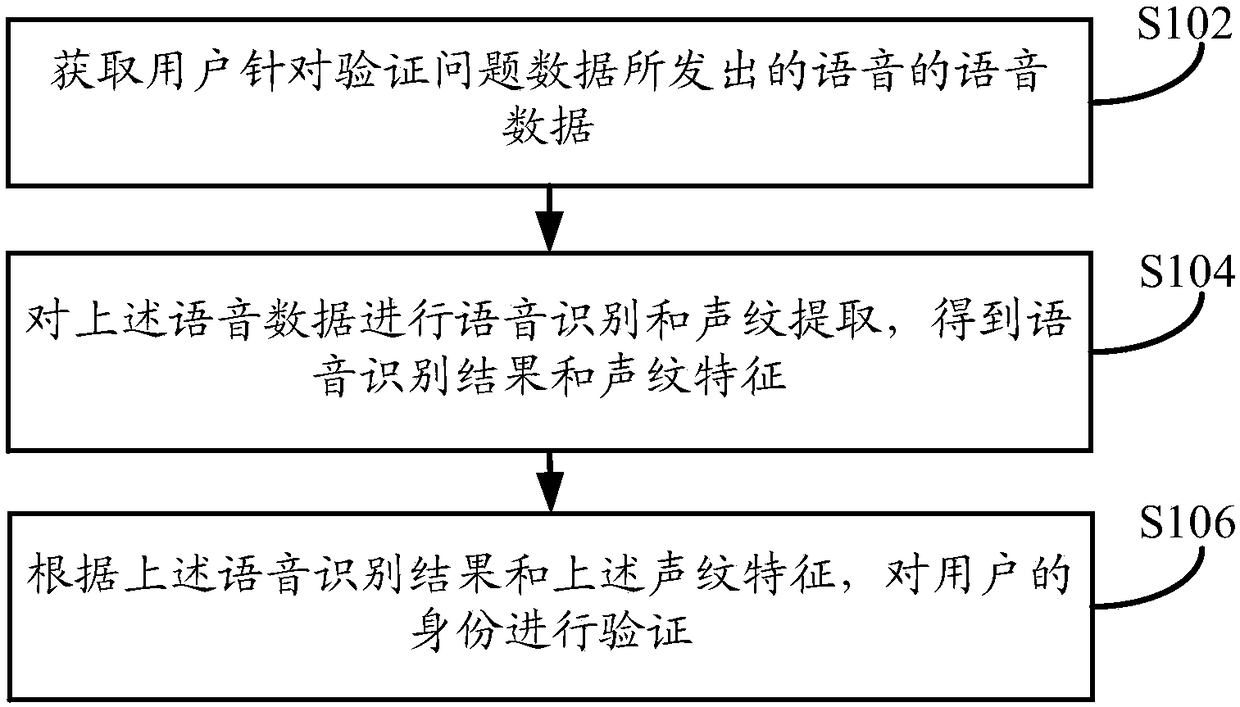
Identity verification method, device and equipment
ActiveCN109428719AReduce operating proceduresImprove convenienceUser identity/authority verificationSpeech recognitionSpeech soundVoice data
The embodiment of the invention discloses an identity verification method, device and equipment. The method comprises the following steps: obtaining voice data of voice made by a user aimed at verification problem data; carrying out voice recognition and voiceprint extraction on the voice to obtain a voice recognition result and a voiceprint characteristic; and verifying the identity of the user according to the voice recognition result and the voiceprint characteristic. The embodiment of the invention is used so that the safety of a target account of the user can be improved; moreover, the operation process of the user can be shortened; and the convenience for authentication is improved.
Owner:ADVANCED NEW TECH CO LTD
System that employs inferencing for troubleshooting complex user authentication problems
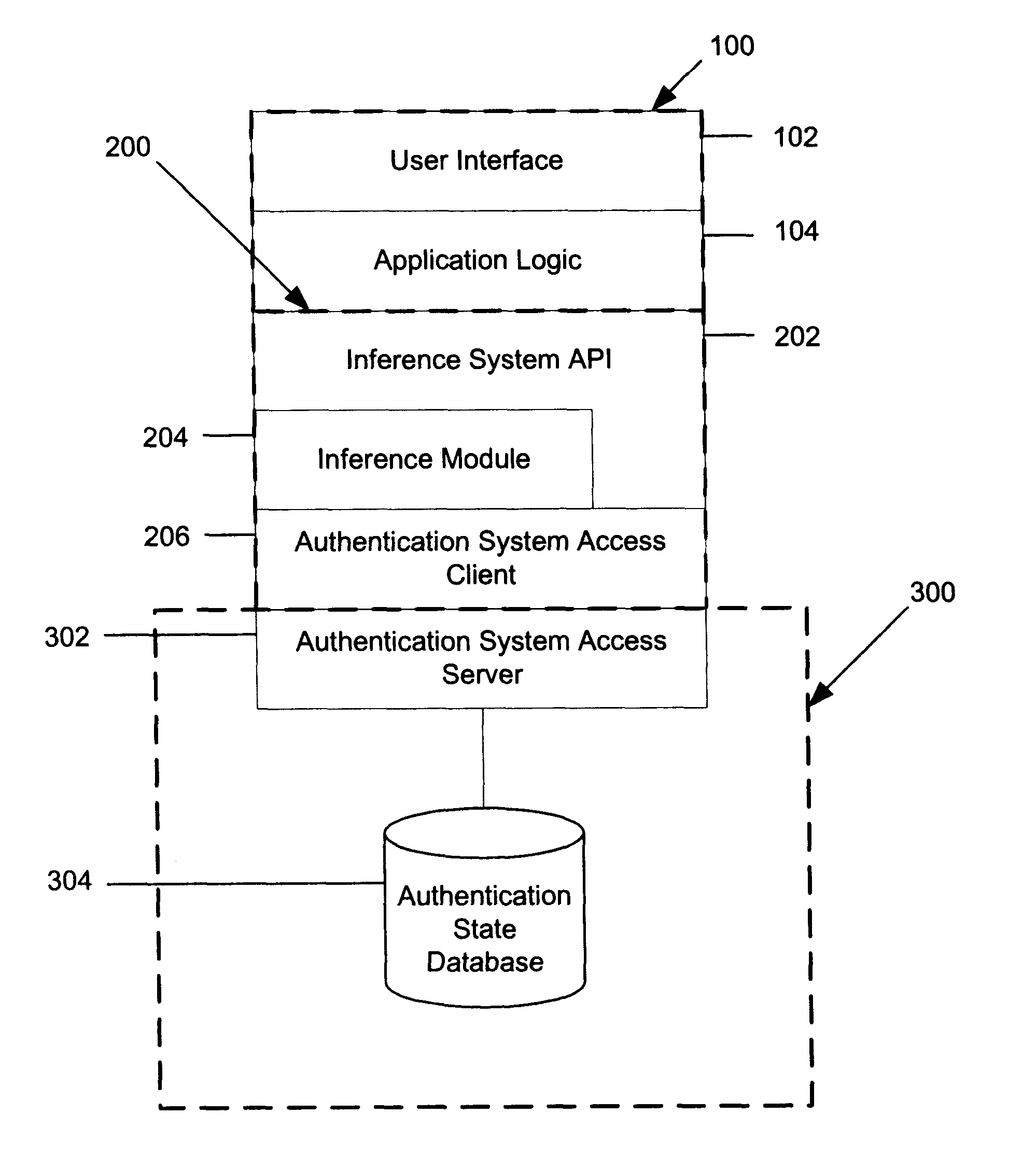
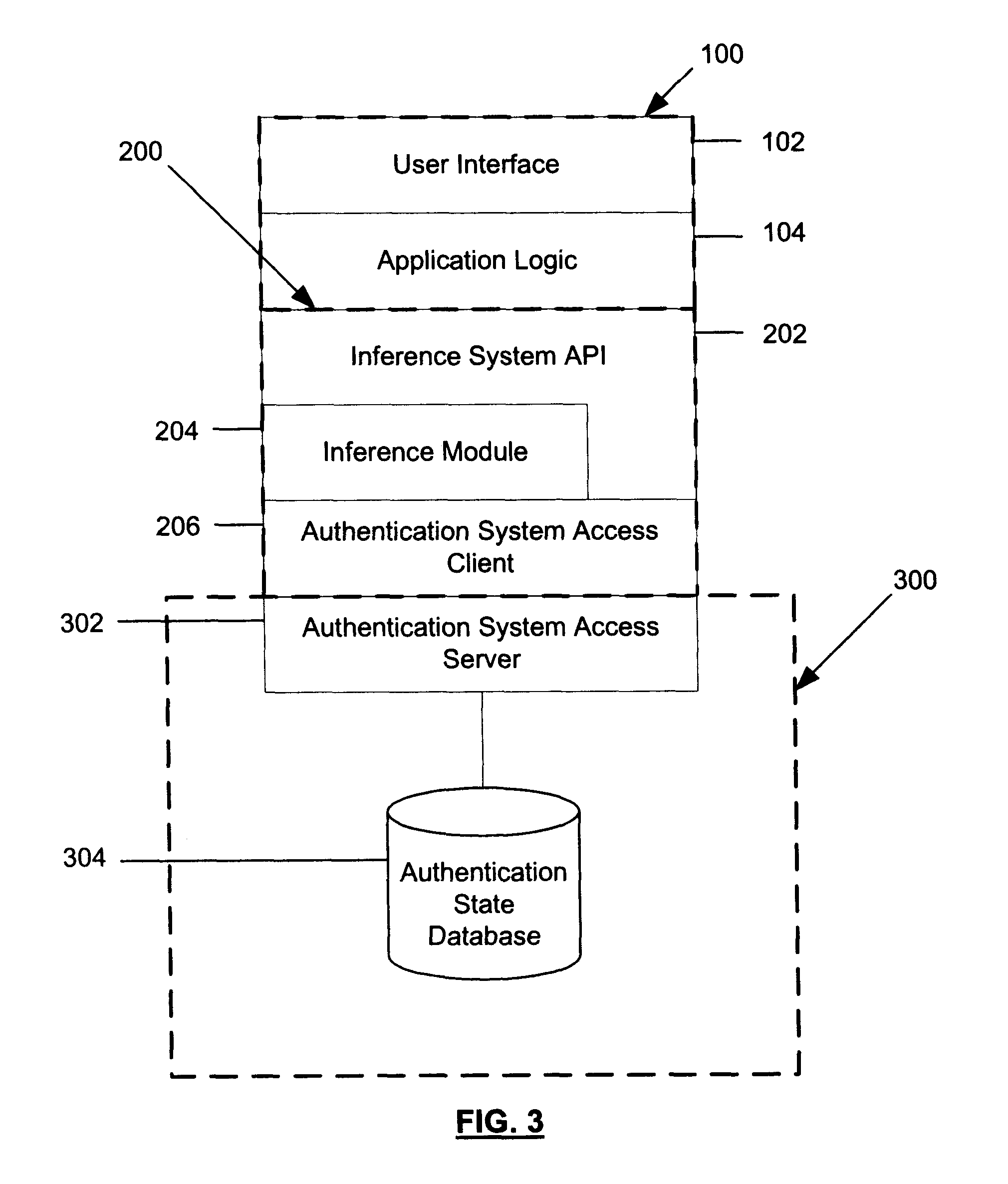
InactiveUS6587853B1Data processing applicationsDigital data processing detailsInternet privacyReasoning system
A system that uses inferencing to deal with complex authentication problems such as those that occur when users authenticate themselves by means of tokens. A troubleshooter responds to a user's request for help by inputting an identification code for the user's token into the system. The system uses the identification code to obtain the current authentication state for the token from an authentication database and then inputs the authentication state to an inferencing system such as a knowledge base. The inferencing system uses the authentication state to make inferences concerning the problem. The inferencing process may involve obtaining further information from the troubleshooter an / or the authentication database and may also provide warnings of particular security problems to the troubleshooter. Eventually, the inferencing system reaches a solution, which may include advice that the troubleshooter is to give to the user. The solution may also involve a modification to the authentication database. When that is the case, an indication from the troubleshooter that the system is to modify the database causes the system to automatically perform the modification. In a preferred embodiment, communication between the troubleshooter and the system is via World Wide Web protocols.
Owner:PLUM SOFTWARE ASSOCS
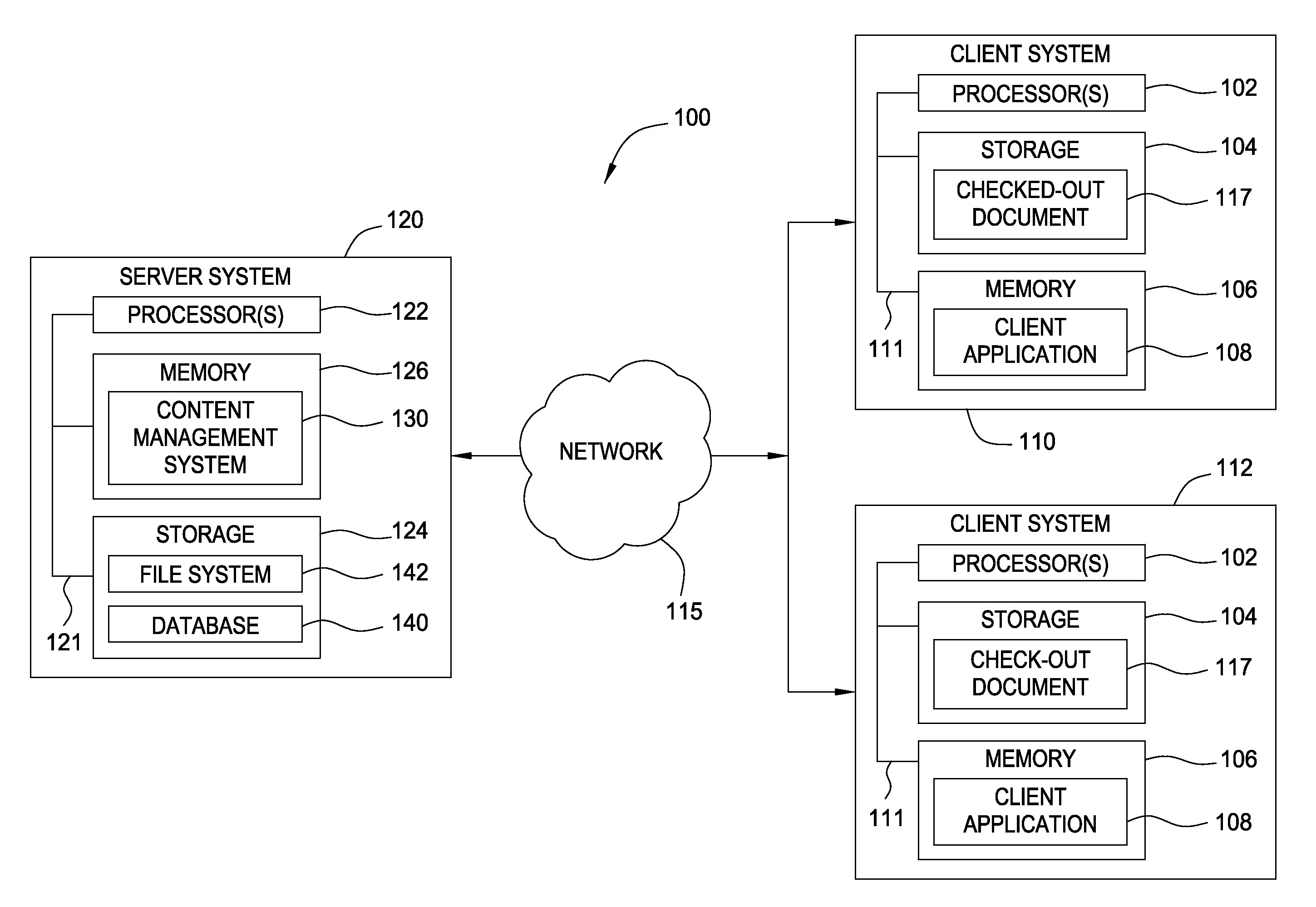
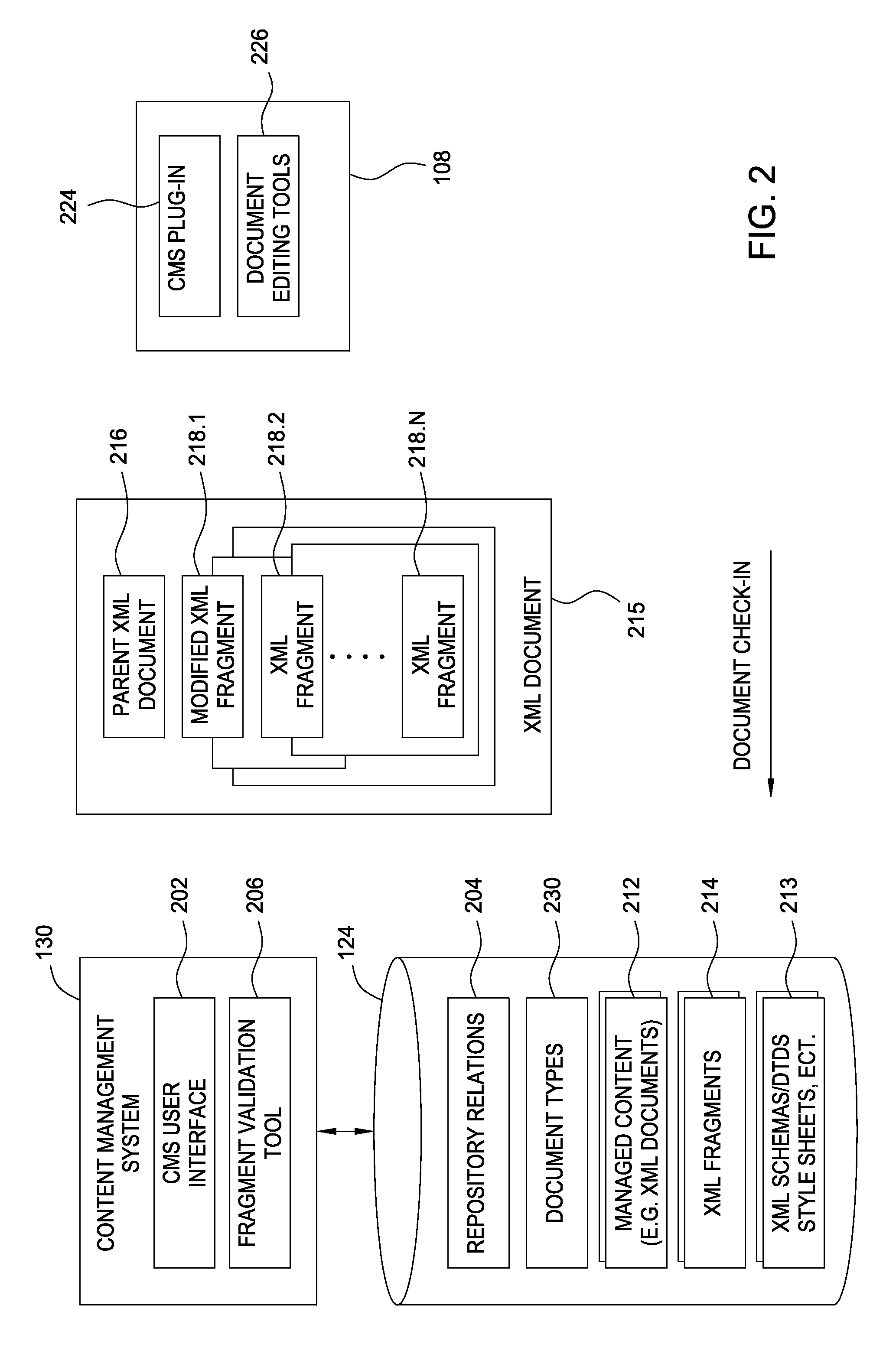
Method for multicontext XML fragment reuse and validation in a content management system
ActiveUS20080201365A1Improve reuseNatural language data processingSpecial data processing applicationsSoftware engineeringDocumentation
Method, article and apparatus for the reusability of data objects such as XML document fragments managed by a content management system (CMS). Embodiments of the invention may be used to enforce validation requirements for a multi-context XML fragment (i.e., for a fragment referenced in two or more documents managed by the CMS). When changes are made to a multi-context fragment, the CMS may detect any validation problems and take corrective action to resolve the validation problem.
Owner:DOMO
Method and apparatus for memory abstraction and verification using same
ActiveUS8001498B2Reduce decreaseReduce complexitySoftware simulation/interpretation/emulationSpecial data processing applicationsComputer architectureTerm memory
A computer implemented representation of a circuit design including memory is abstracted to a smaller netlist, which can be analyzed by standard verification tools and by other tools that operate on netlists. The correctness of such systems can require reasoning about a much smaller number of memory entries than exist in the circuit design, and by abstracting such memories to a smaller number of entries, the computational complexity of the verification problem is substantially reduced.
Owner:SYNOPSYS INC
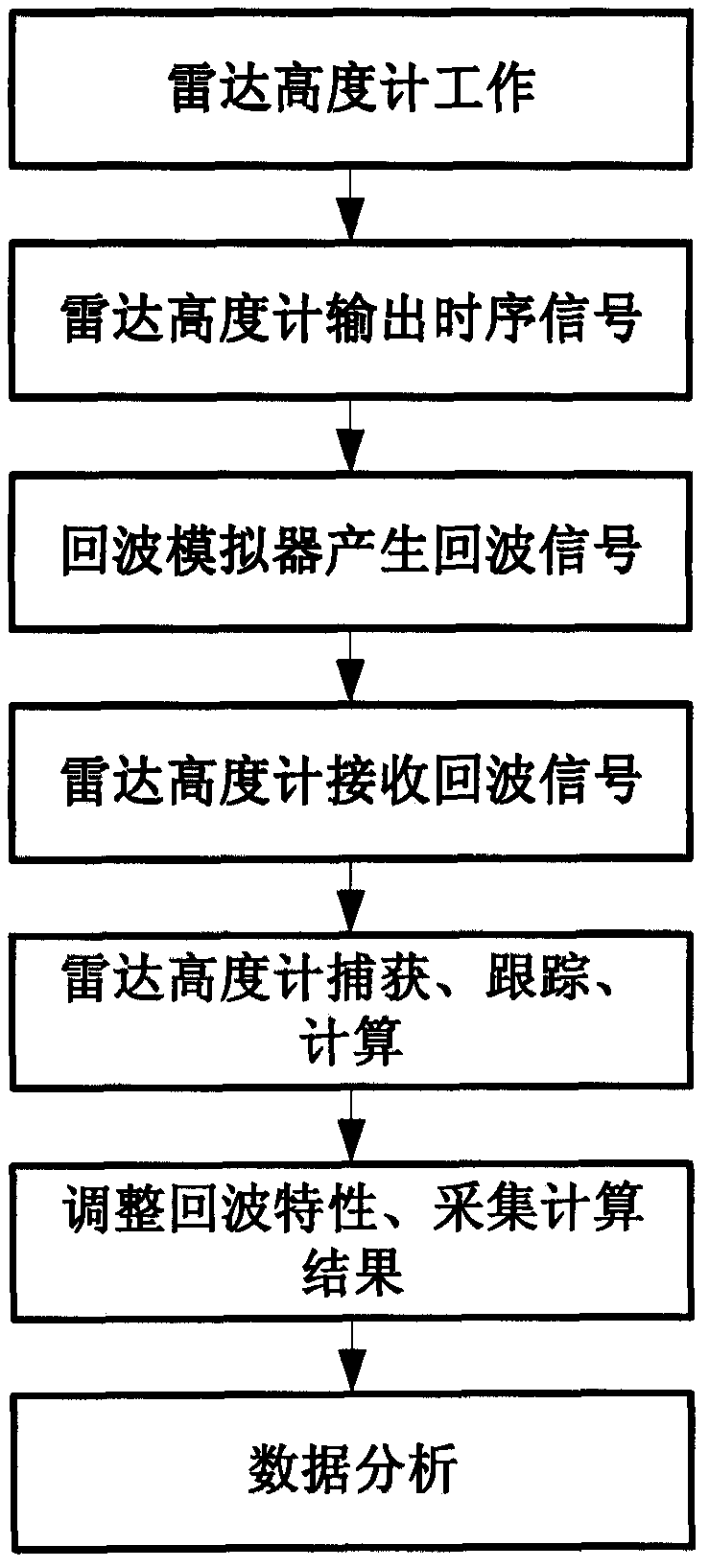
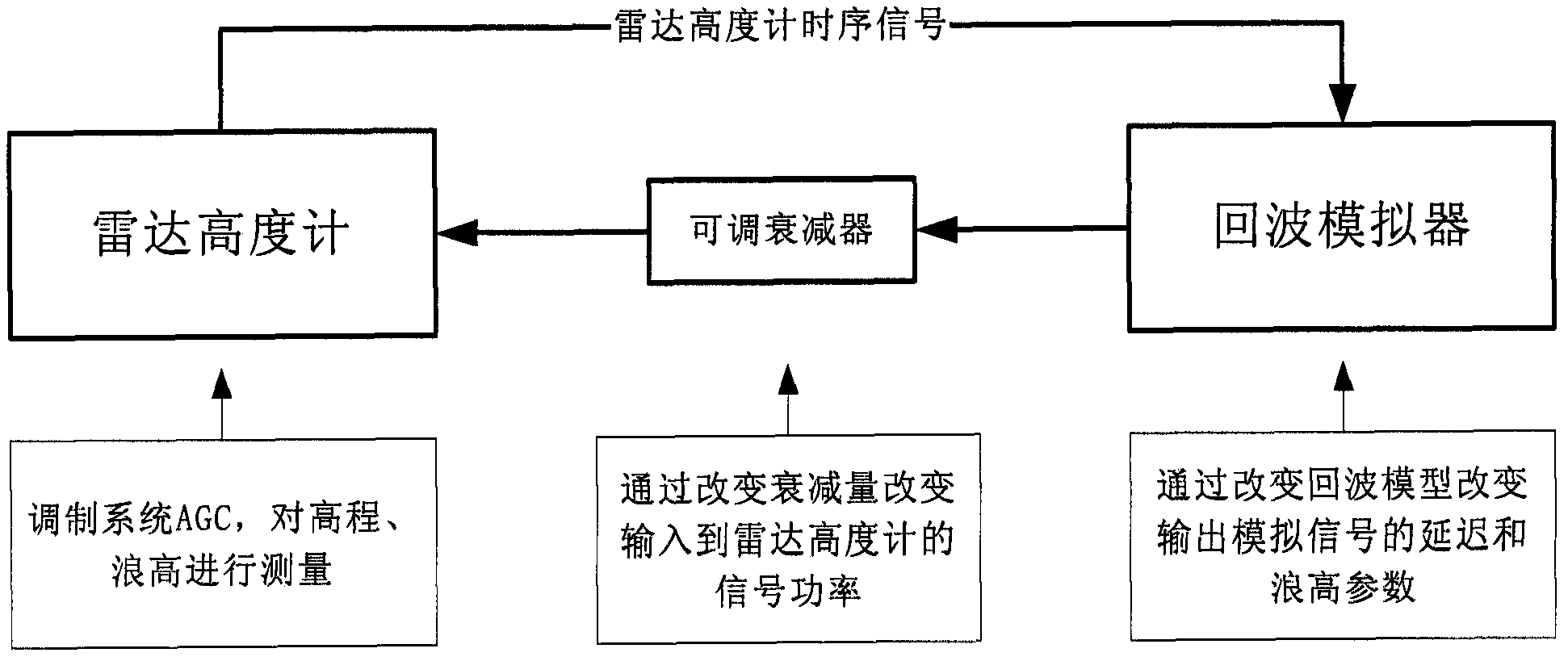
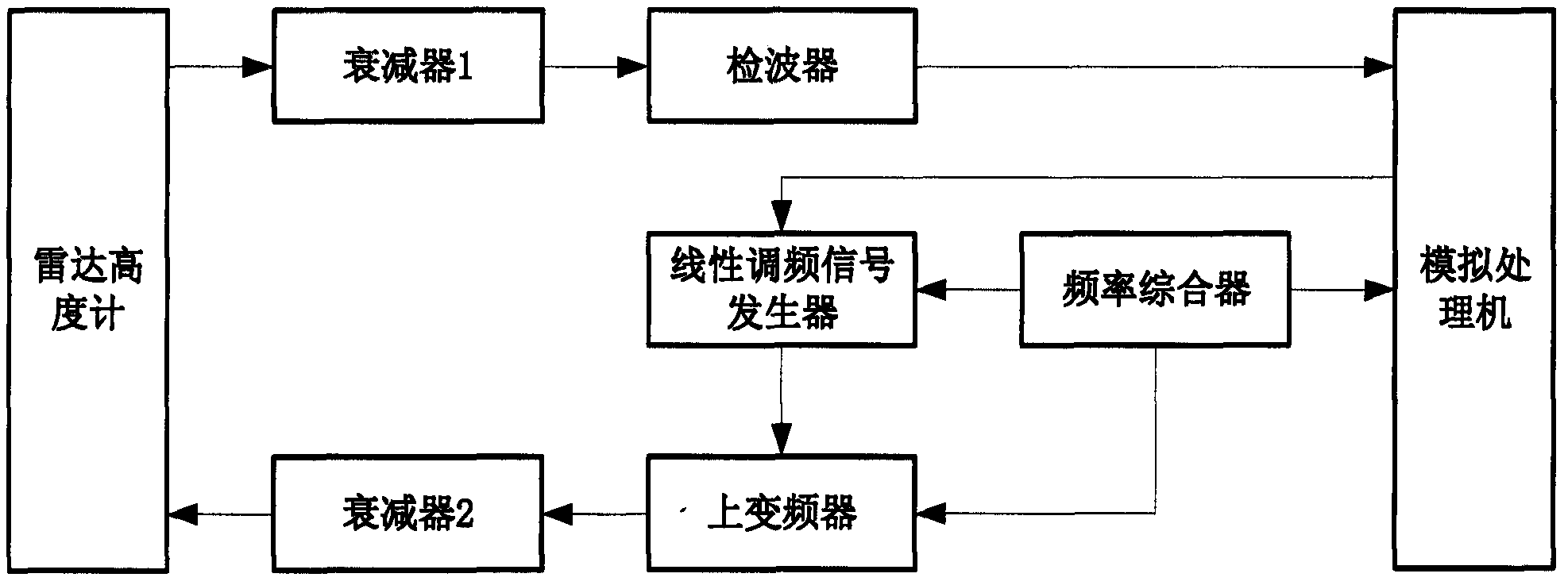
A system-level test method for radar altimeter
A radar altimeter system-level testing method, using an echo simulator to form a closed-loop test system, to test the radar altimeter's height measurement function, wave height test function, and system AGC adaptive adjustment function, so as to test the system-level measurement function of the radar altimeter A comprehensive verification is carried out, which solves the system-level verification problem of the spaceborne radar altimeter under the whole star condition. The method of the present invention utilizes the echo simulator to form a closed-loop test system, changes the input of the radar altimeter system through the setting of the echo simulator and the adjustment of the attenuator, and interprets the final test result of the radar altimeter, and the test result reflects the complete working logic of the radar altimeter, achieving The purpose of radar altimeter system level verification.
Owner:BEIJING INST OF SPACECRAFT SYST ENG
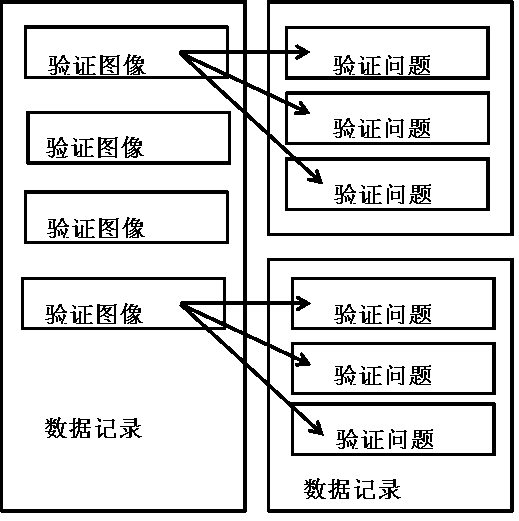
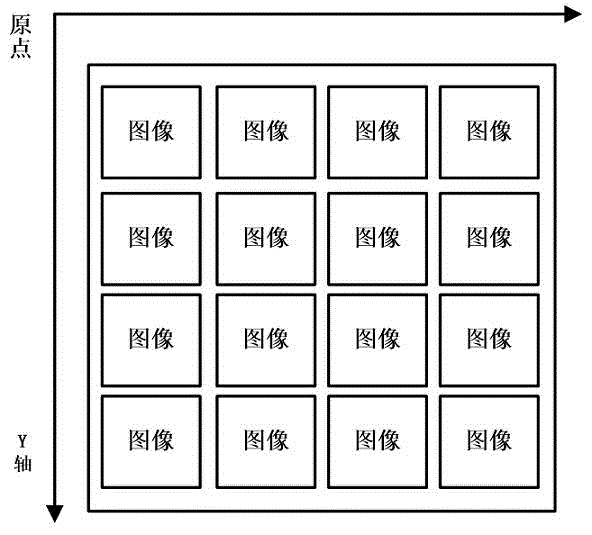
Verification code of image array
InactiveCN103942486AEasy to read by humansEasy to readDigital data authenticationTransmissionProgramming languageUser verification
The invention discloses a verification code of an image array. The verification code comprises a verification code module, a service logic module, a database and the like. According to the verification code of the image array, a series of relevant or random images are generated through a system according to verification code generation logic to form the image array, a verification problem is generated based on the content or representation of an object of the image array and displayed on a user side, a user is requested to read and comprehend the verification problem based on the image array according to prompts, the user reads the image array and the verification problem, the corresponding verification code is written, the system compares the verification answer written by the user with the answer corresponding the verification promoting mode, and if the two answers are the same, it is considered that the verification code of the use is correct. Due to the fact that the verification problem and the corresponding verification code used as the answer are generated based on the image array and the representation and semantics of the content, the safety of the system of the verification code is improved, and automatic identification of a machine program is effectively prevented.
Owner:SHANGHAI BOLU INFORMATION TECH
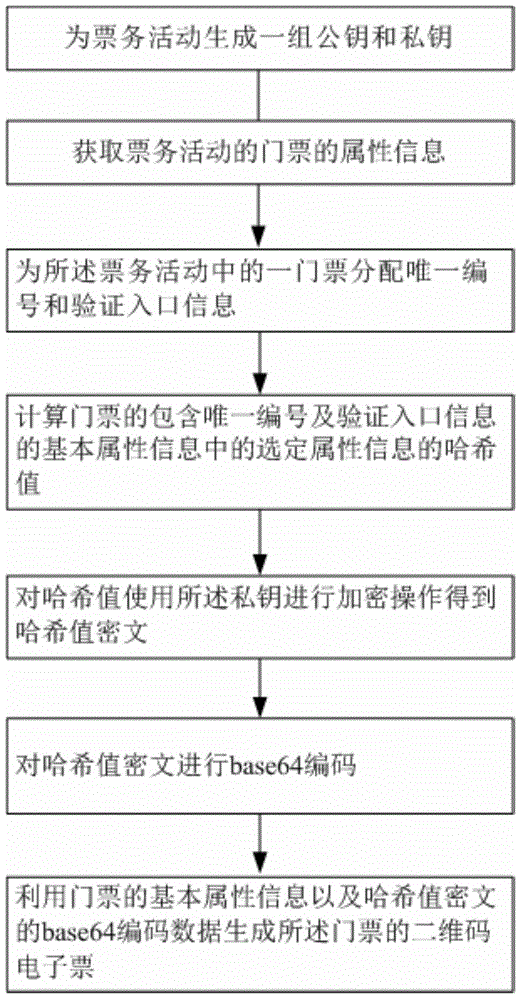
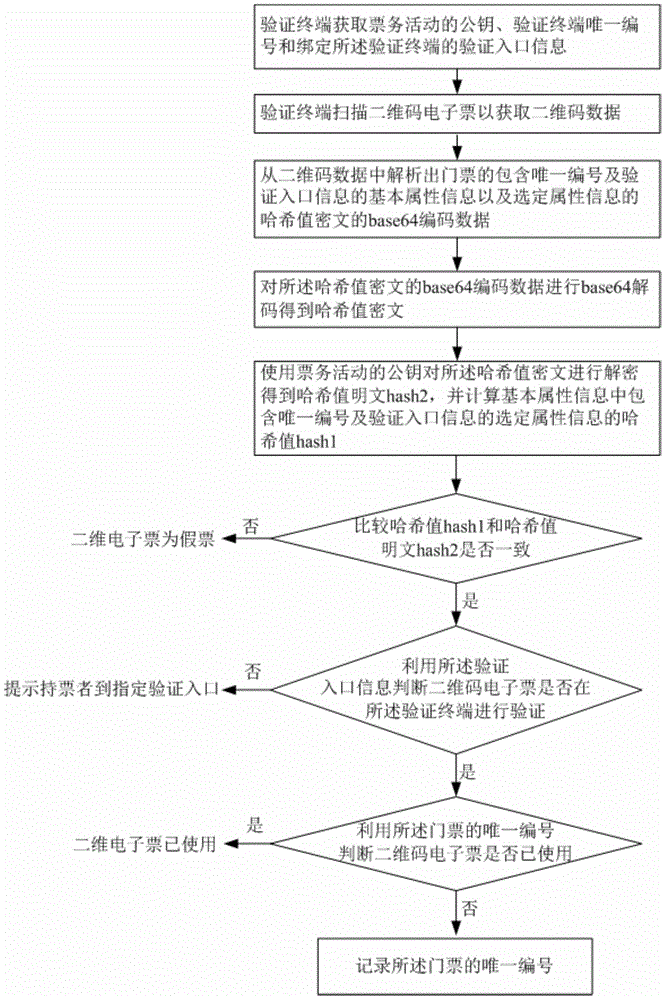
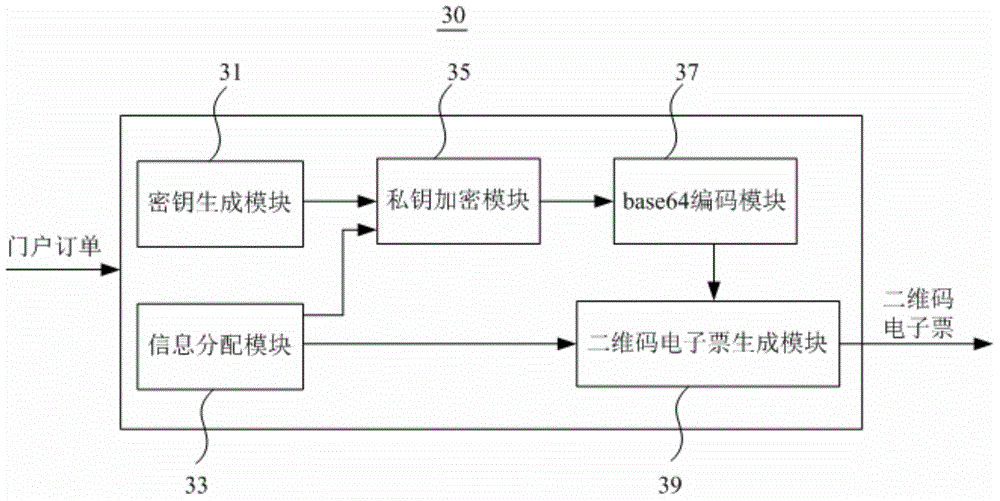
Two-dimensional code e-ticket generation method and system, two-dimensional code e-ticket verification method and verification terminal
ActiveCN105678365ARealize authenticity identificationAvoid reuseRecord carriers used with machinesSensing by electromagnetic radiationValidation methodsCiphertext
The present invention relates to a two-dimensional code e-ticket generation method and system. The method comprises the following steps: A) generating a group of public keys and private keys for an assigned ticket business activity; B) distributing the only one number and verification inlet information for one ticket of the assigned ticket business activity; C) encrypting selected attribute information in the basic attribute information of the ticket including the only one number and the verification inlet information through adoption of the private keys to obtain the selected attribute information cryptograph of the ticket, wherein the public keys are used for supply the selected attribute information cryptograph to the verification terminal for decryption; and D) generating the two-dimensional code electronic ticket of the ticket through adoption of the basic attribute information and the selected attribute information cryptograph. The present invention further provides a two-dimensional code e-ticket verification method and a verification terminal. The true and false determination of an electronic ticket, the shunting of electronic ticket verification and eradicating of reusing of the electronic ticket are realized, and the safety verification problem of the electronic ticket in the non-network environment is solved.
Owner:AEROSPACE INFORMATION
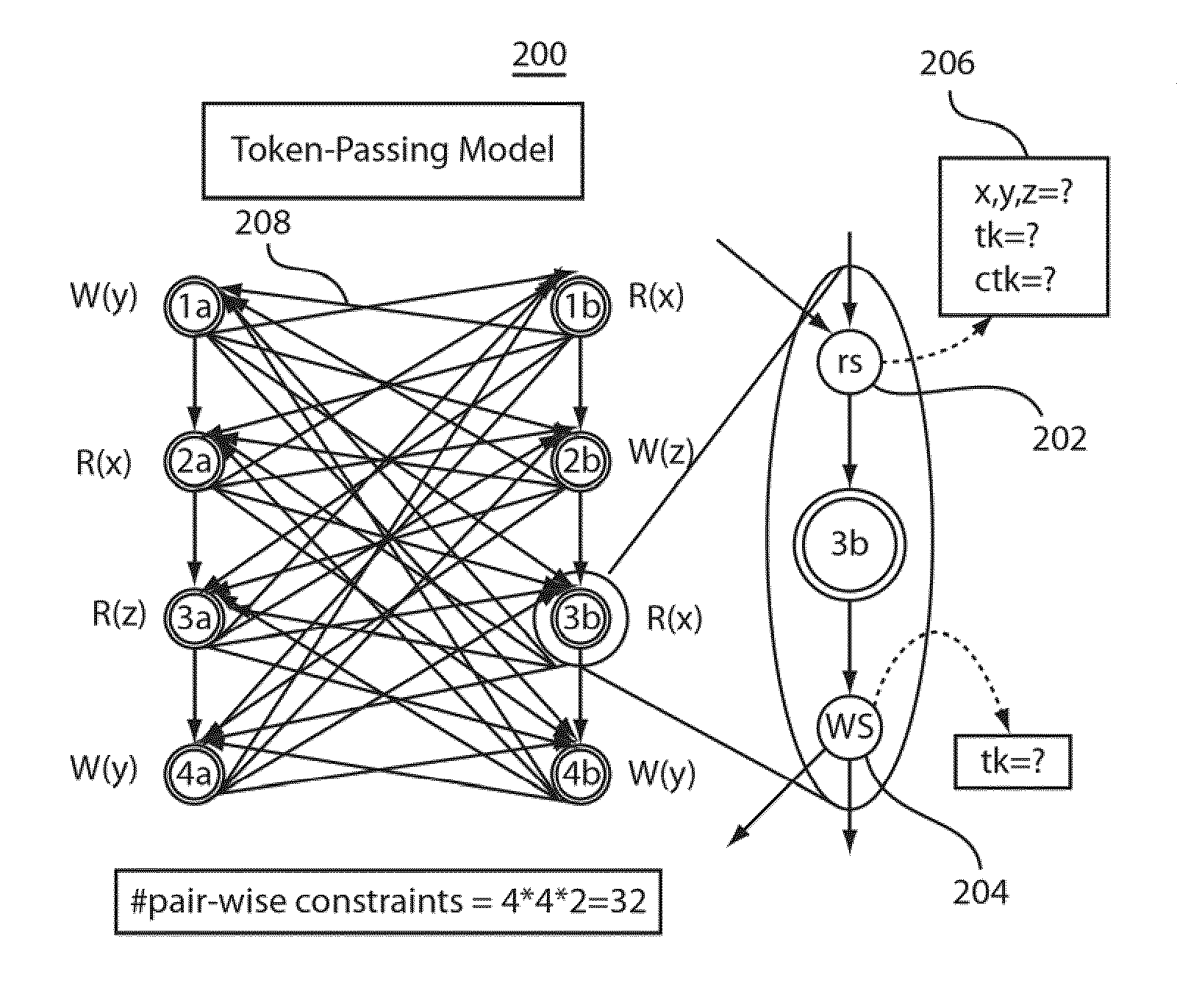
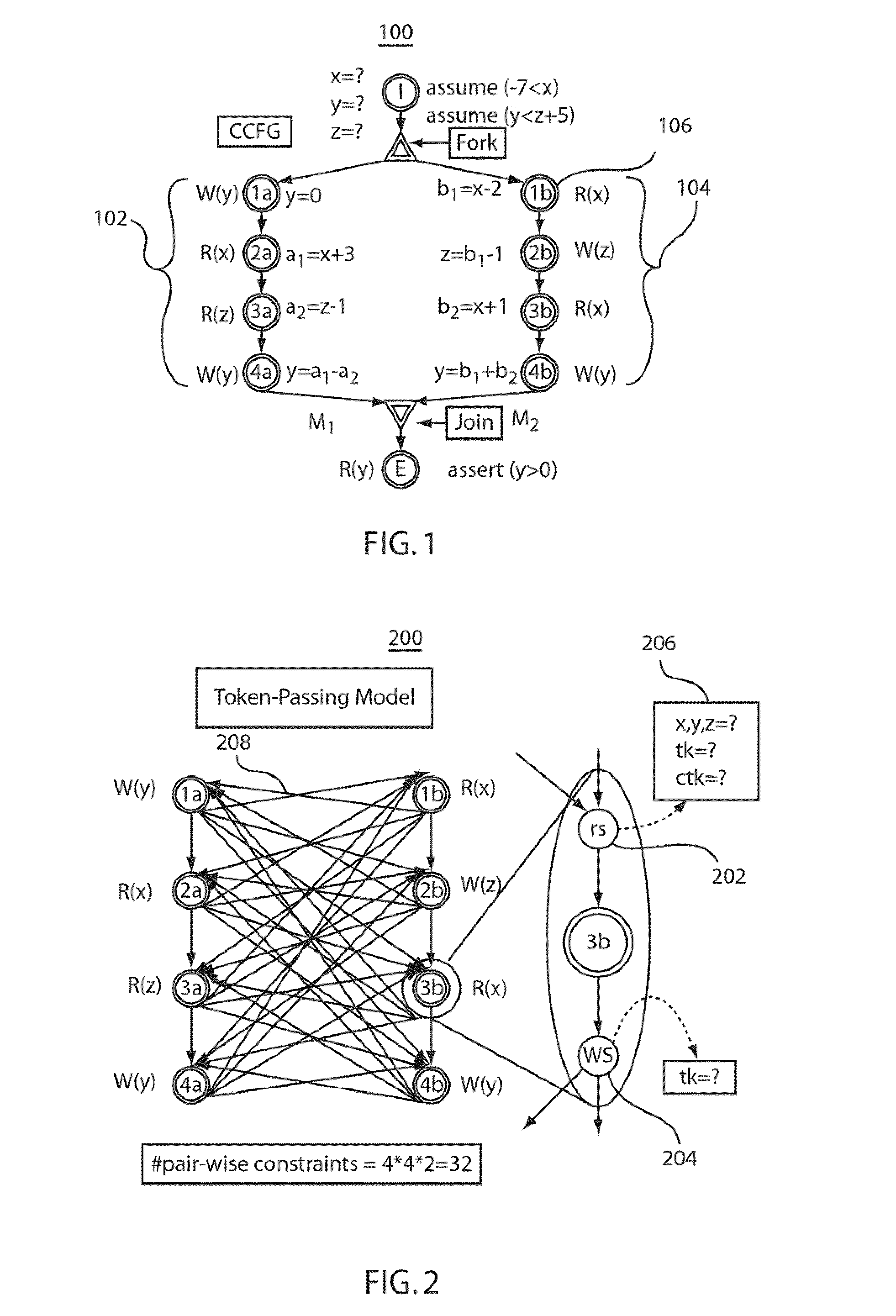
Methods and systems for reducing verification conditions for concurrent programs using mutually atomic transactions
ActiveUS20100088680A1Reduce in quantityVerify the correctness of a concurrent system of program threadsProgram synchronisationError detection/correctionState spaceProgram Thread
Methods and systems for generating verification conditions and verifying the correctness of a concurrent system of program threads are described. The methods and systems determine and employ mutually atomic transactions to reduce verification problem sizes and state space for concurrent systems. The embodiments provide both an adequate and an optimal set of token-passing constraints for a bounded unrolling of threads.
Owner:NEC CORP
Authenticating user identity when resetting passwords
InactiveUS7874011B2Digital data processing detailsUnauthorized memory use protectionInternet privacyPassword
Owner:INT BUSINESS MASCH CORP
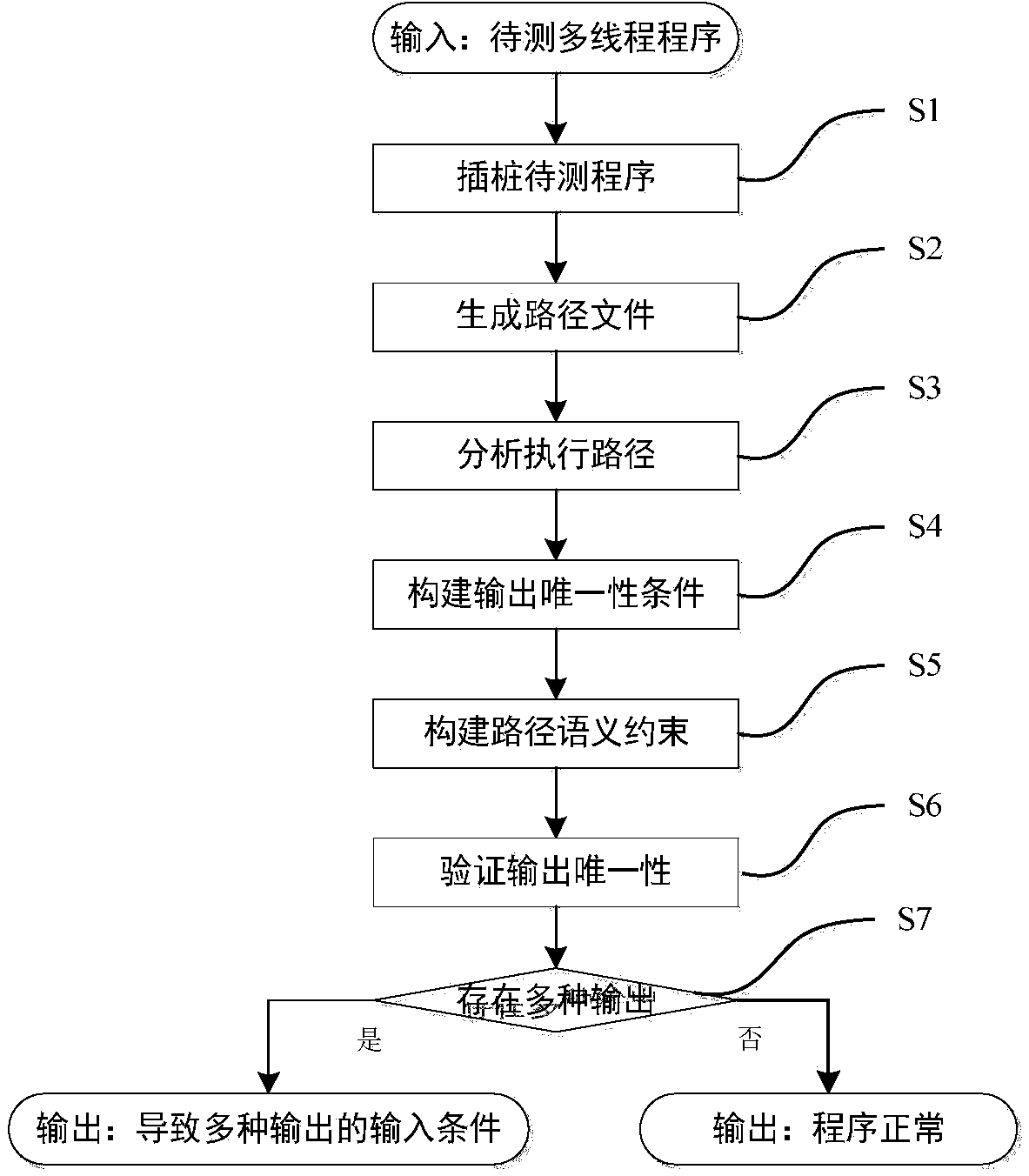
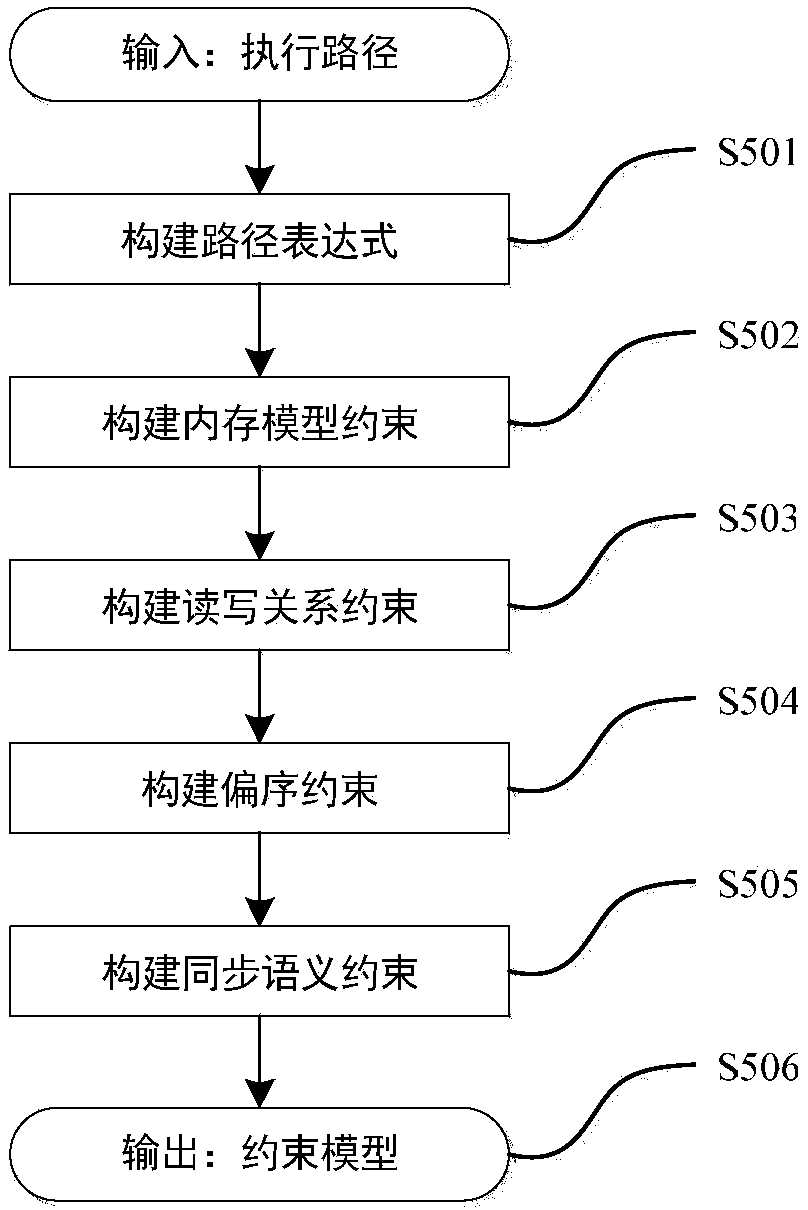
Multithreaded program output uniqueness detection and evidence generation method based on program constraint building
Owner:XI AN JIAOTONG UNIV
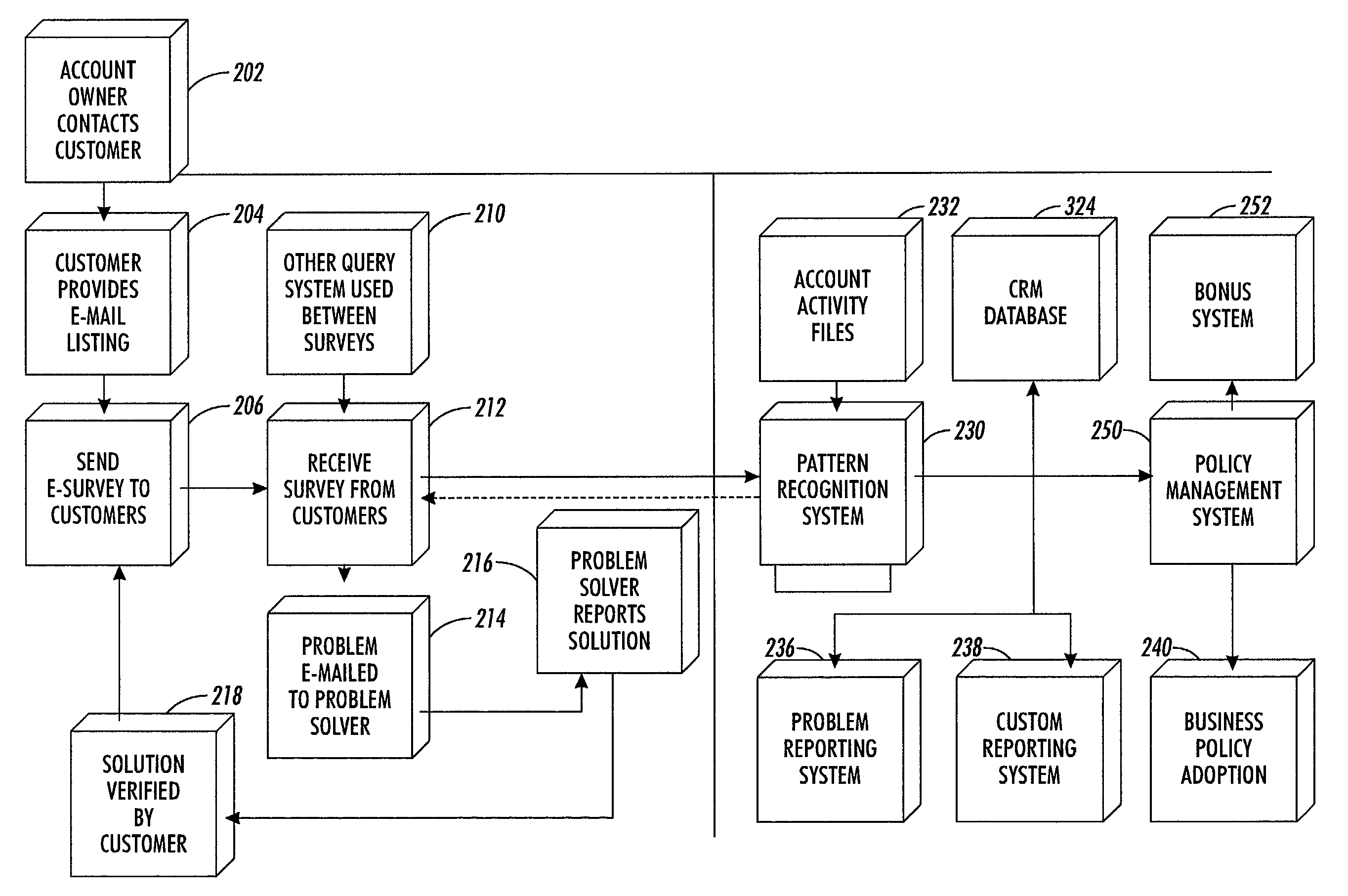
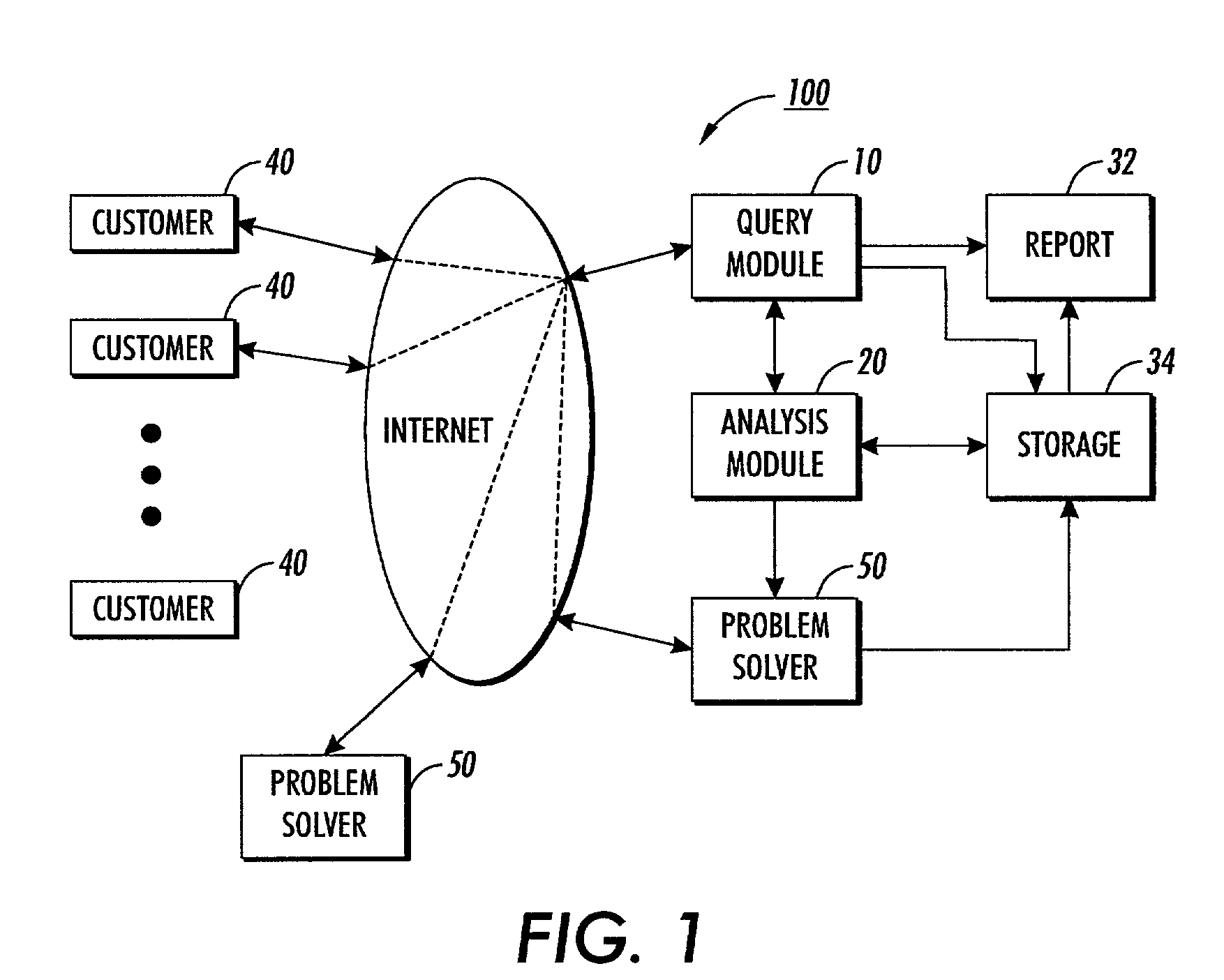
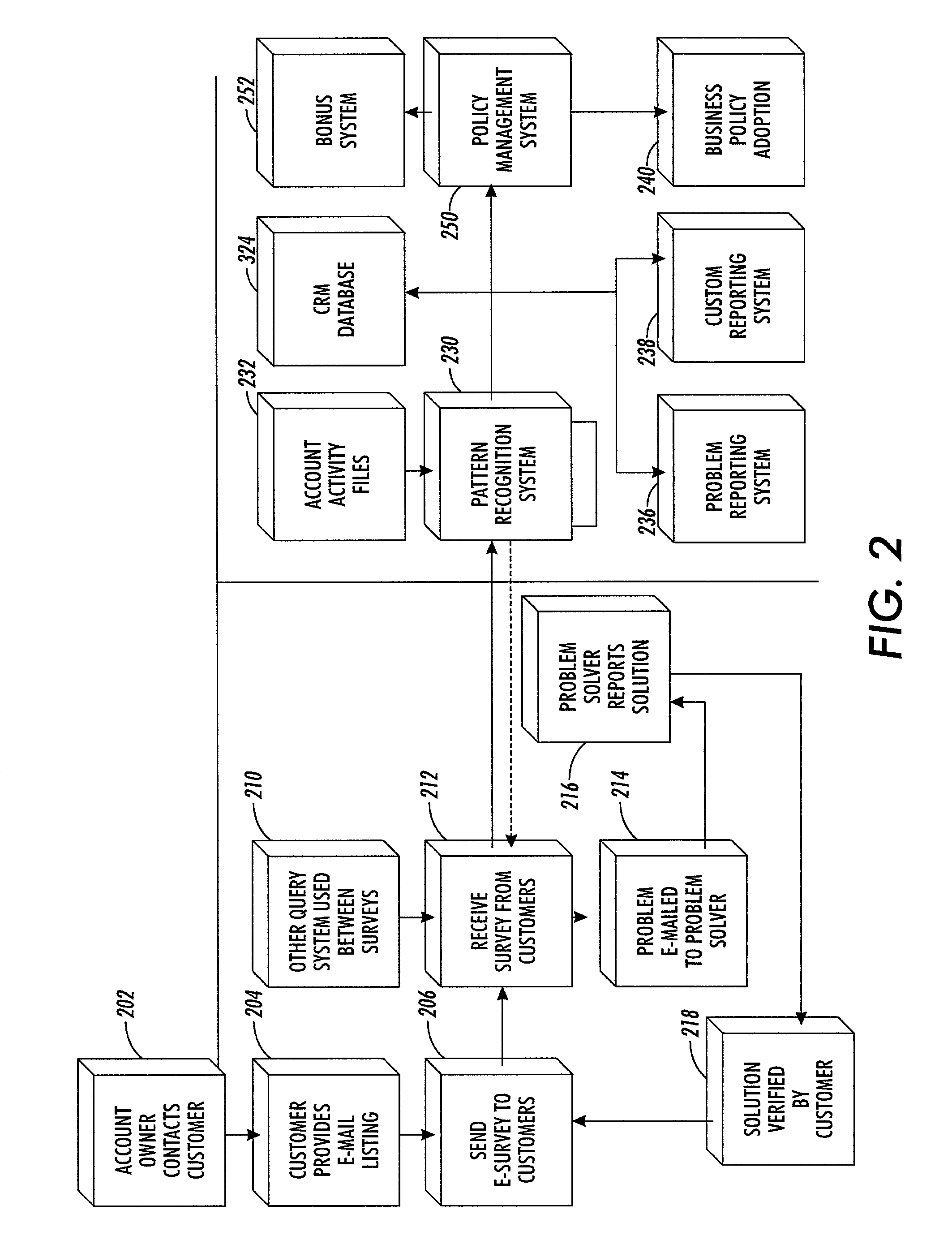
Customer satisfaction system and method
ActiveUS7698162B2Customer satisfactionSupporting profits and organizational learningMarket predictionsSpecial data processing applicationsTime scheduleData science
A customer satisfaction system, includes a query module for automatically sending queries to customers as to problems with goods or services provided by a provider according to a predetermined schedule and for receiving responses from customers to the queries; an analysis module for analyzing responses from customers and for sending responses indicating a problem to a problem solver for resolution; and at least one problem solver for responding to customer problems, for generating solutions to customer problems and for transmitting solutions to customers; wherein, upon transmission of a solution to a customer problem to a customer, the query module sends a query to the customer requesting verification that the problem has been solved.
Owner:INTEL CORP
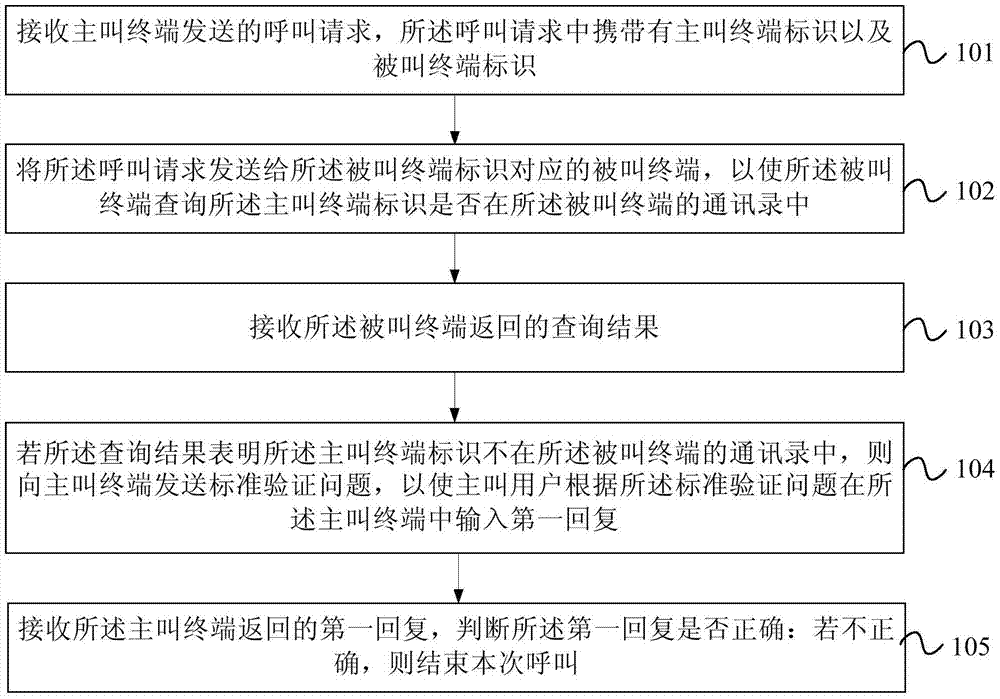
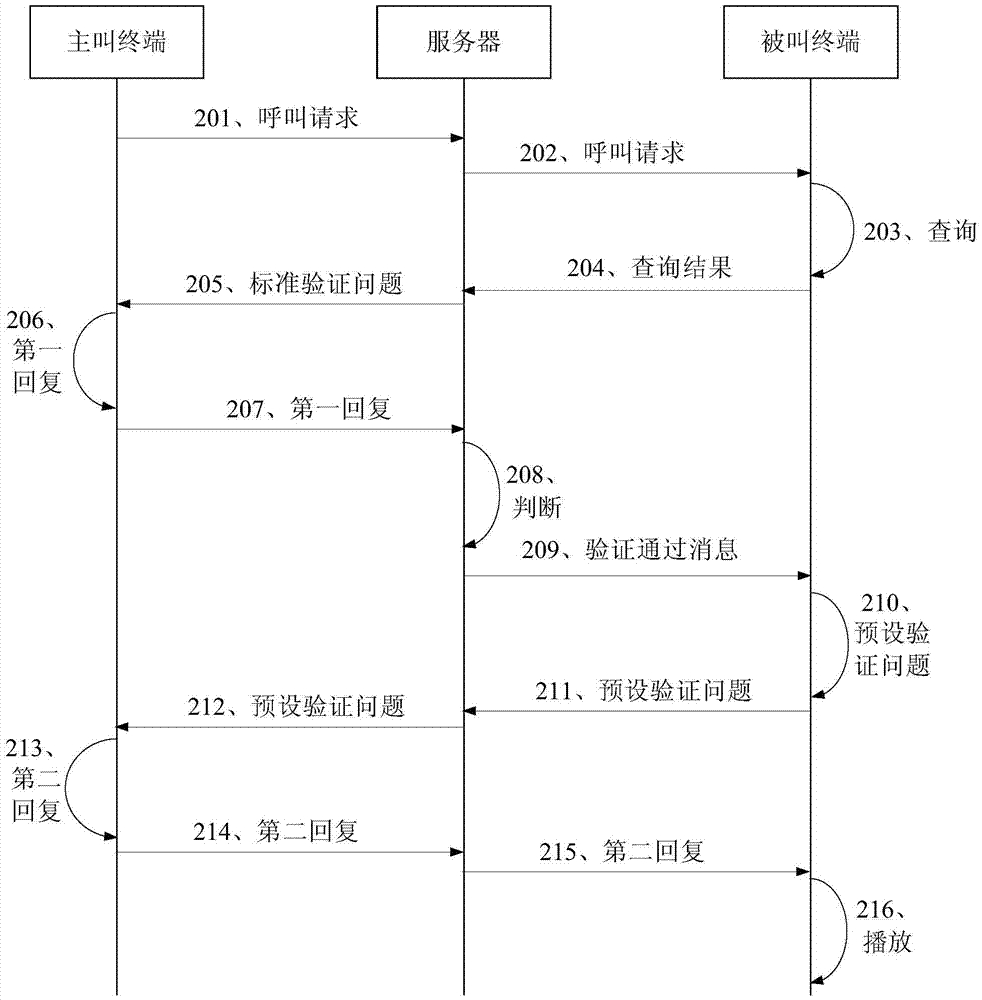
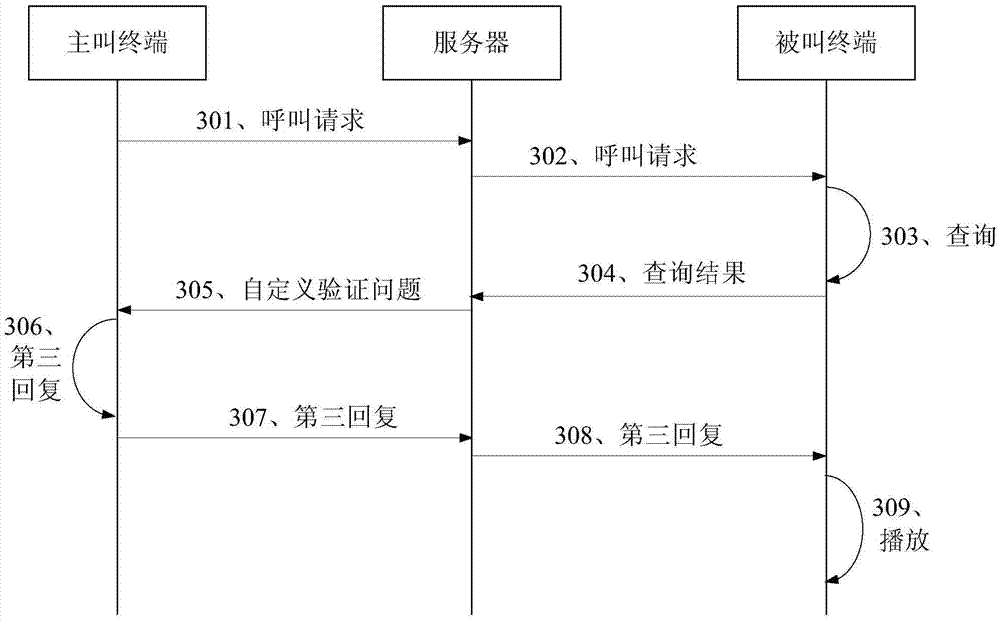
Call processing method, user terminal and server
The invention provides a call processing method, a user terminal and a server. The call processing method comprises the steps of receiving a call request sent by a calling terminal, wherein the call request contains the identifier of the calling terminal and the identifier of a called terminal; sending the call request to the called terminal corresponding to the identifier of the called terminal to enable the called terminal to find out whether the identifier of the calling terminal is in the address book of the called terminal or not; receiving a search result returned by the called terminal; if the search result shows that the identifier of the calling terminal is not in the address book, sending a standard verification problem to the calling terminal to enable a calling party to input a first replay in the calling terminal according to the standard verification problem; receiving the first reply returned by the calling terminal and judging whether the first reply is correct or not; if not correct, ending the current call. Based on the call processing method, the user terminal and the server, malicious harassment calls can be filtered out to a certain extent. Therefore, the user experience is improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
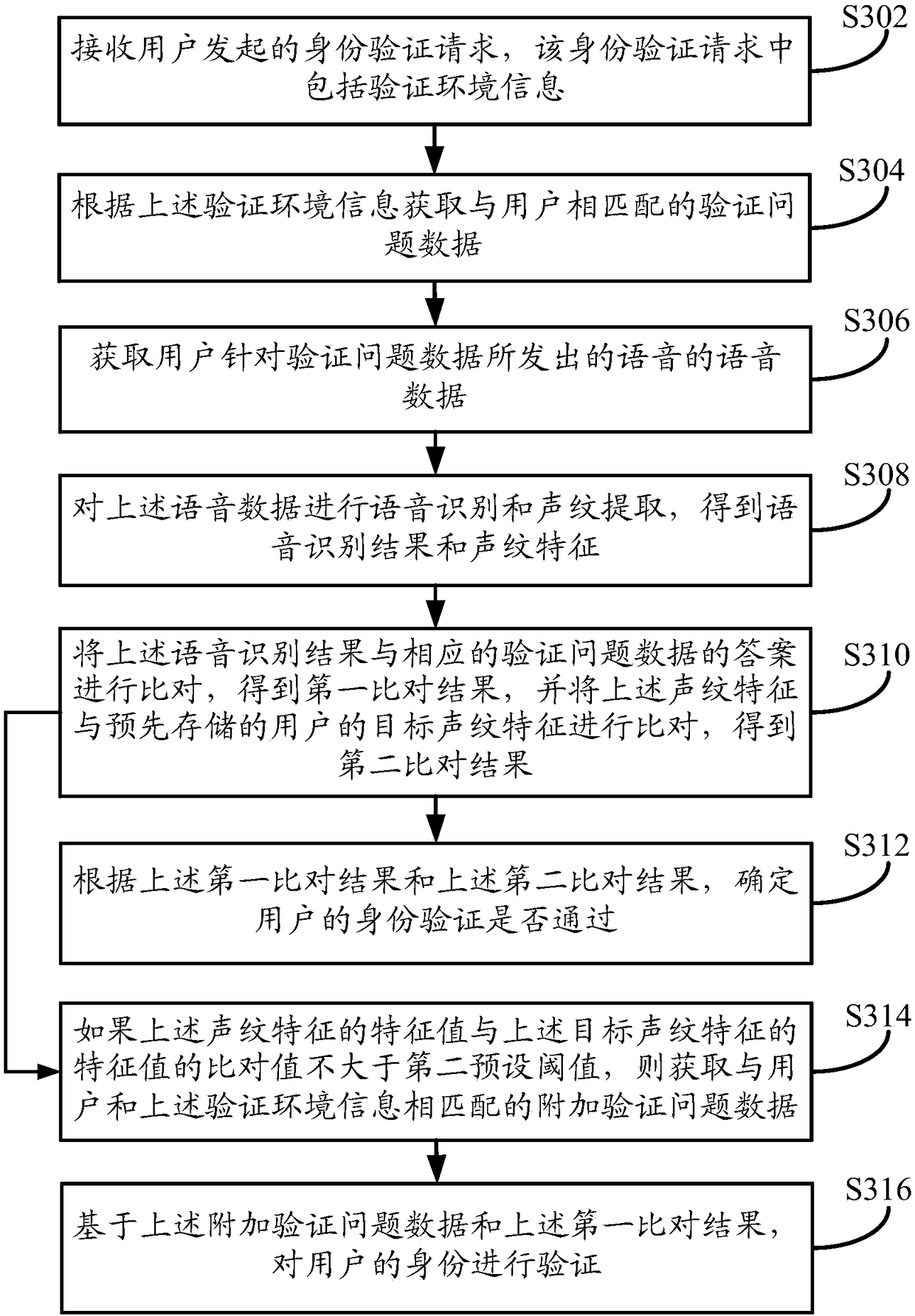
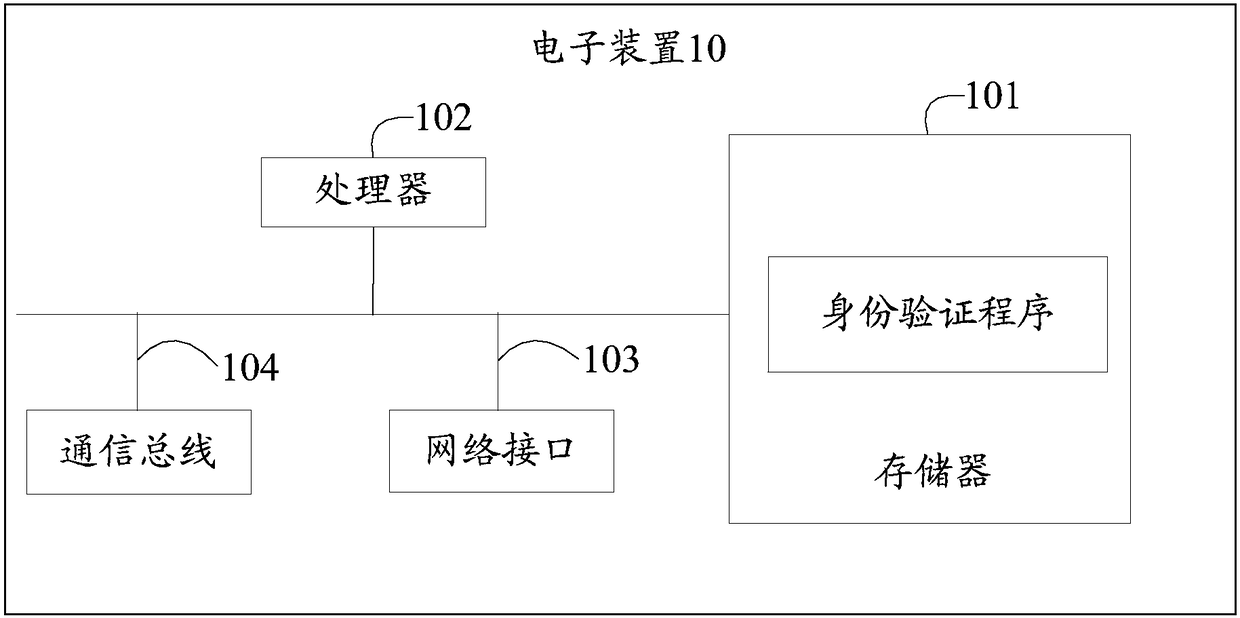
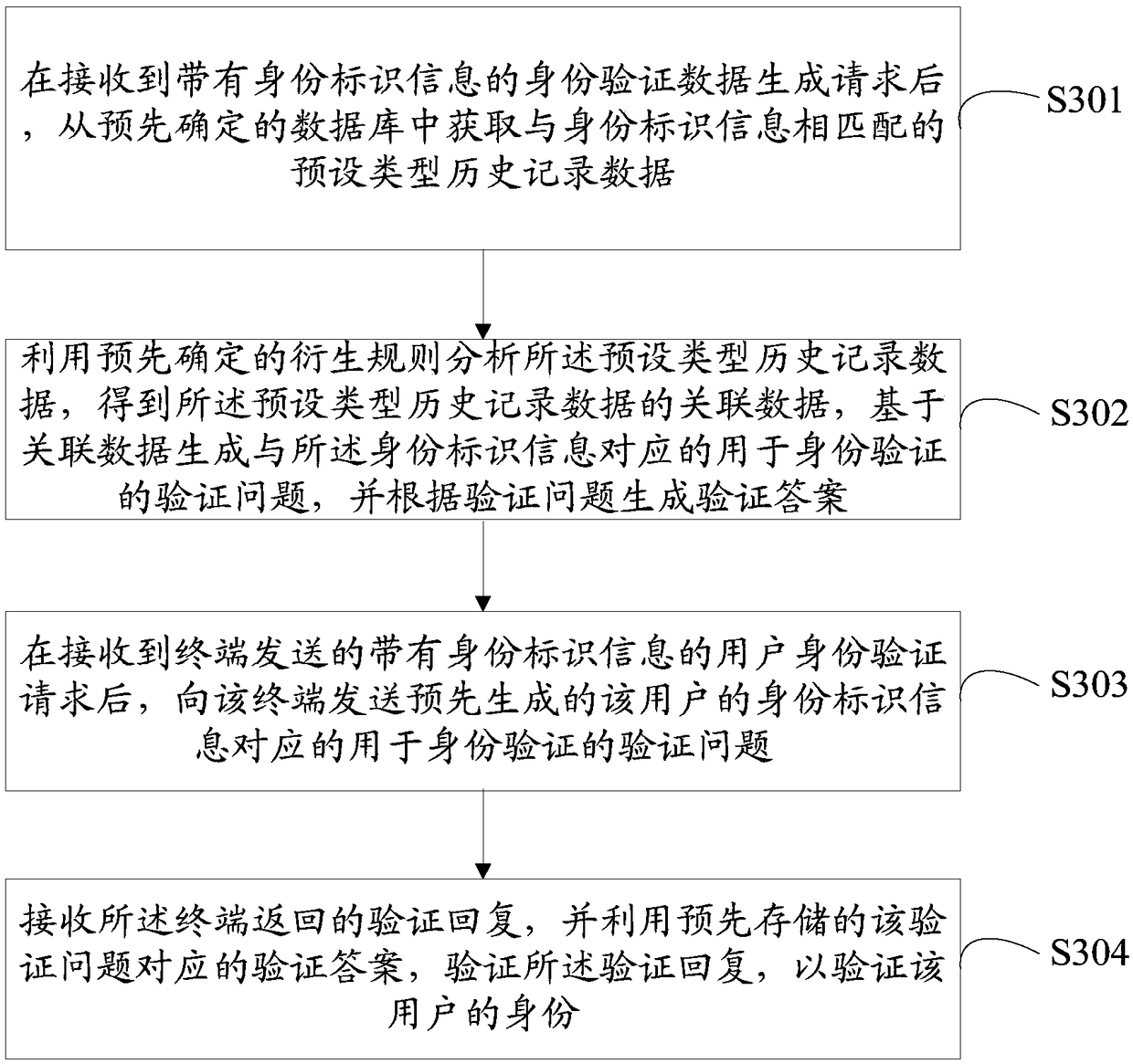
Electronic device, authentication method and storage medium
The invention discloses an electronic device, an authentication data processing method and a storage medium. The method comprises the steps that after an authentication data generation request with identity identification information is received, preset type history record data matched with the identity identification information is obtained from a predetermined database; a predetermined derivative rule is used to analyze the preset type history record data to obtain association data of the preset type history record data, and verification data used for authentication is generated based on theassociation data; after a user identity verification request with the identity identification information sent by a terminal is received, a verification question corresponding to the identity identification information of the user is sent to the terminal; a verification reply returned by the terminal is received, a verification answer corresponding to the verification problem is used to verify the verification reply to verify the identity of the user. According to the electronic device, the authentication method and the storage medium, the verification data is used to verify the identity of the user, and the security risk of identity verification can be effectively reduced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
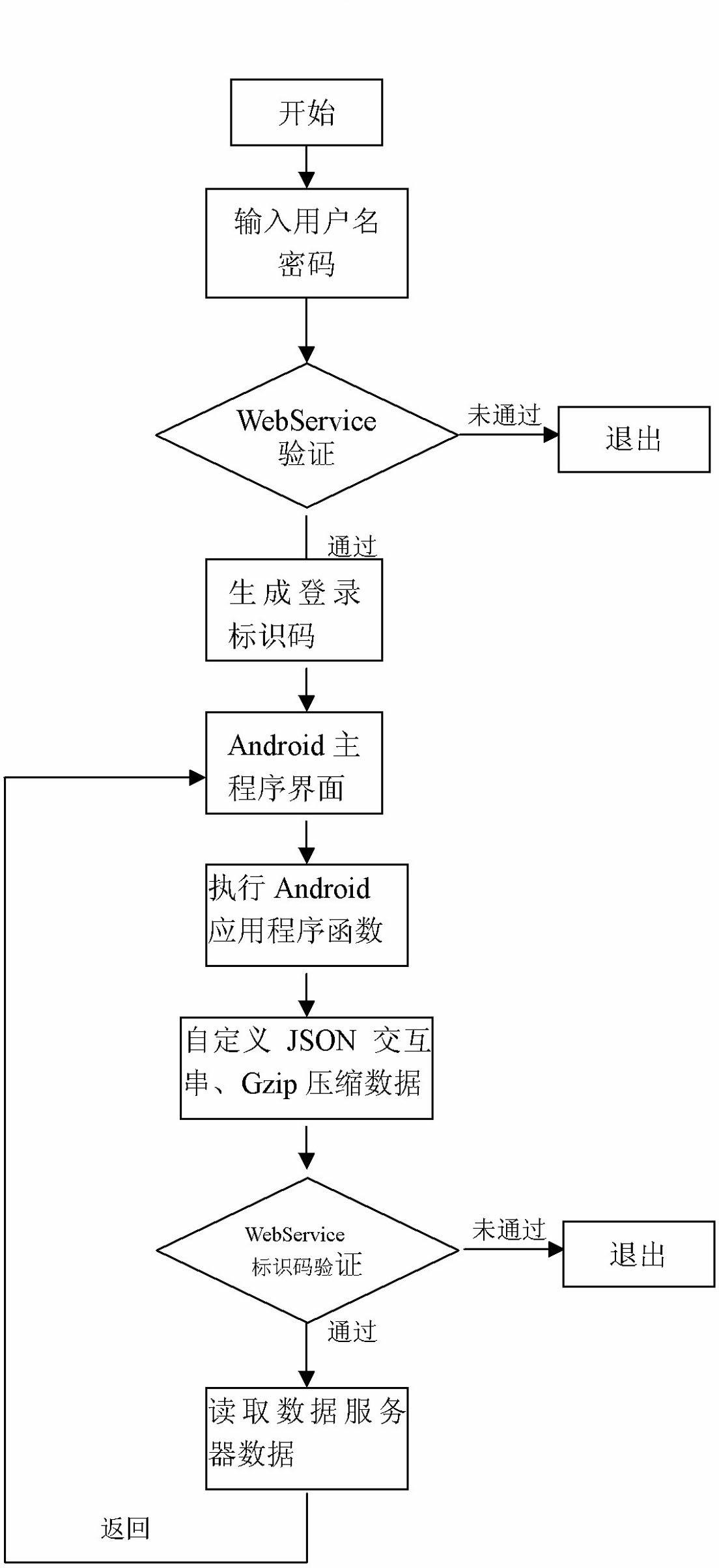
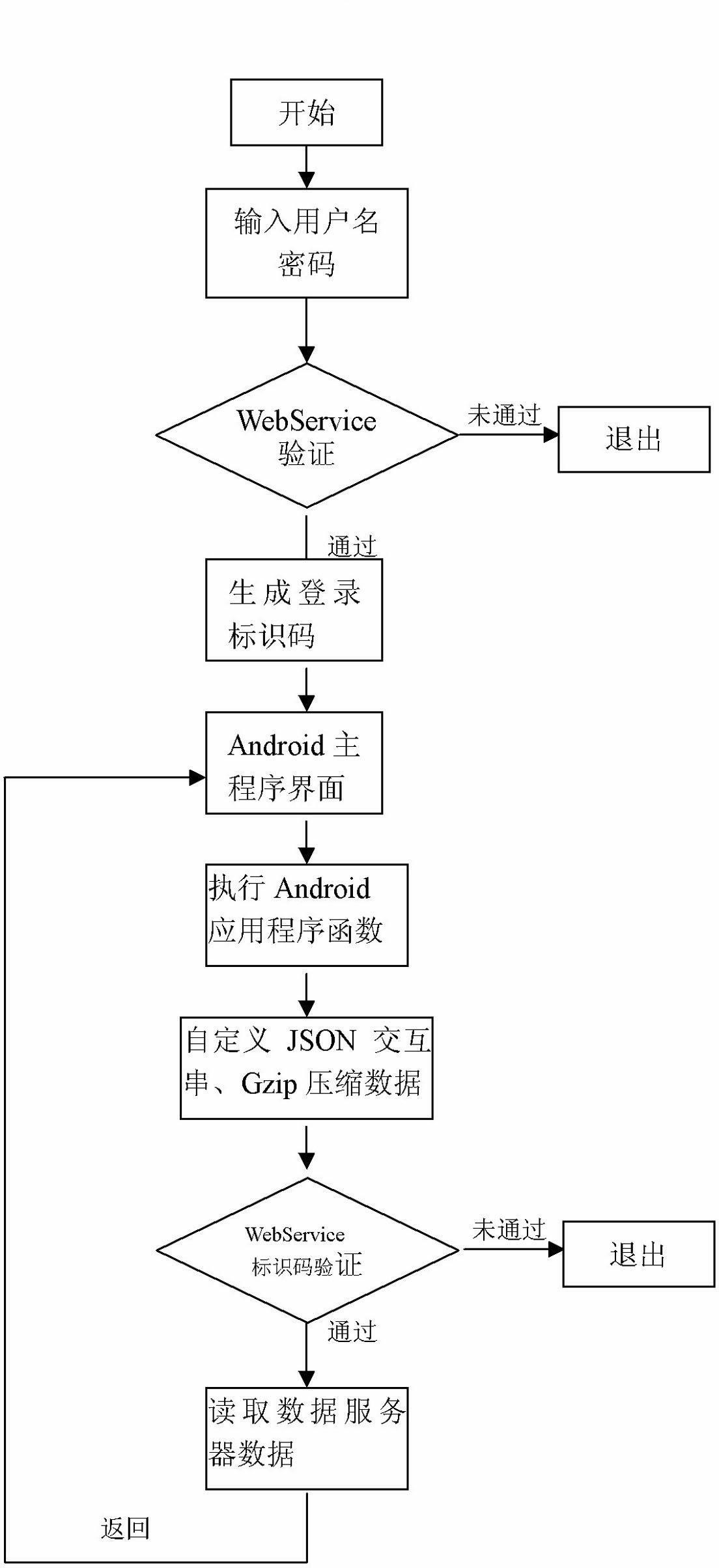
Android network application program information verification method
The invention relates to a high-efficiency Android network application program information verification method which is suitable for smart mobile phone systems. The method comprises the following steps of: establishing an Android log-in module by which a user can log in a data server after inputting a user name and a password; distributing only one log-in identification code to the user by the data server after successful log-in, encrypting the identification code and then putting into a checking table, and returning the log-in identification true code to an Android application program; defining an Android interactive data structure, and compressing transmitted data by GZip (GUN Zip); and constructing a WebService on the basis of SOAP (simple object access protocol) by the data server; verifying the log-in identification code when calling data interaction functions in the WebService after successful log-in, and then performing data interaction between a mobile phone and the data server if the verification succeeds. The method solves information verification problem when the Android accesses the server data through the WebService, and improves the security of WebService on the basis of not affecting network access performances.
Owner:STATE GRID CORP OF CHINA +3
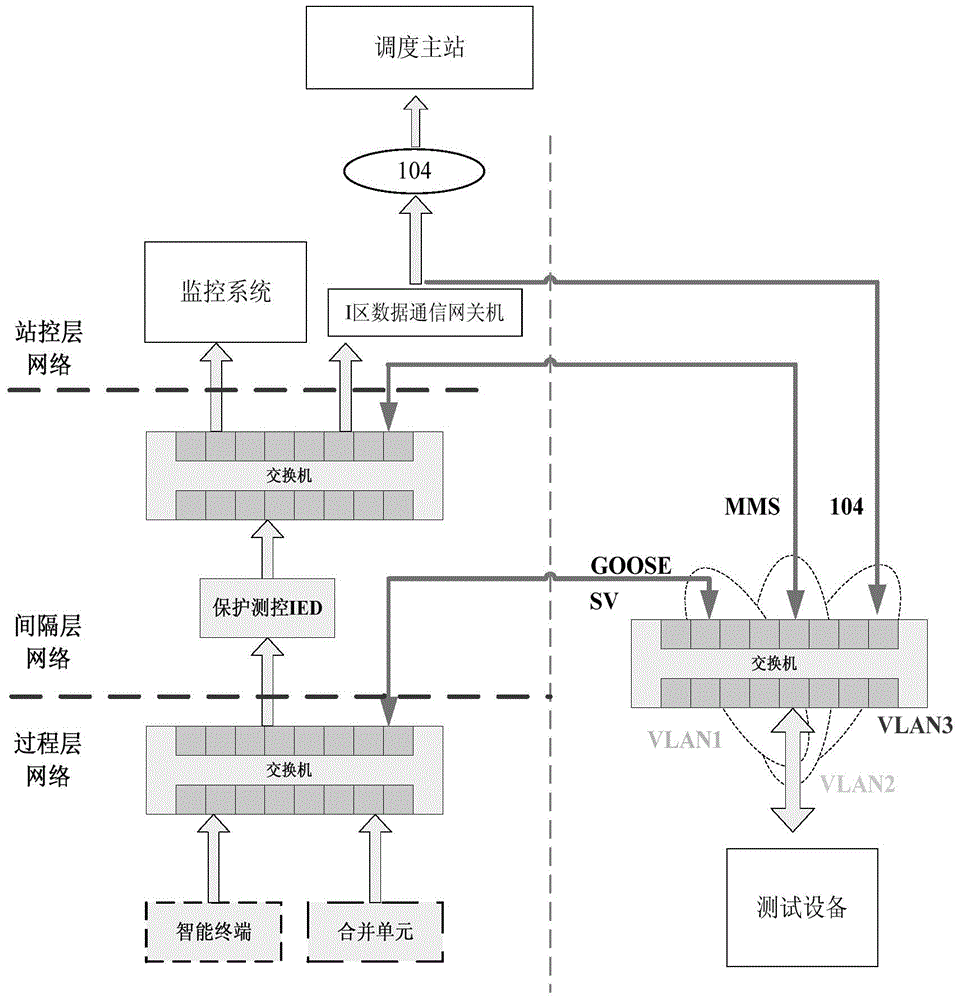
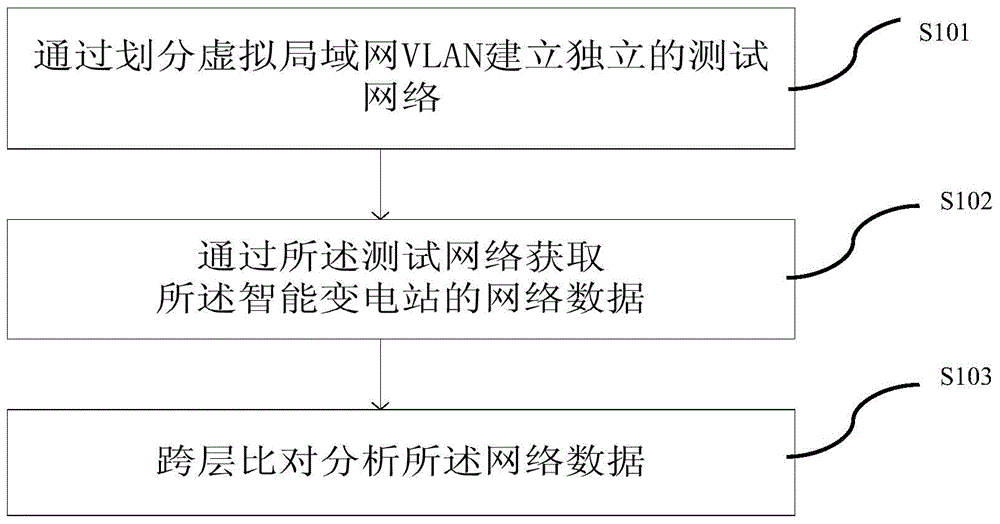
Smart substation steady state data closed-loop testing method and testing system thereof
ActiveCN104601415AGood effectClosed-loop test implementationData switching networksComputer hardwareControl layer
The invention relates to a smart substation steady state data closed-loop testing method and a testing system thereof. A smart substation comprises a process layer, a spacing layer and a station control layer. The method includes establishing a virtual local area network (VLAN); acquiring SV sampling data and GOOSE state data of the process network through the corresponded VLAN; acquiring spacing layer network MMS measurement data through the corresponded VLAN; acquiring the station control layer remote gateway computer 104 transmission data through the corresponded VLAN; performing layer-crossed comparison and analysis on all the data. By the aid of the technical scheme, the verification problem that the smart substation internal steady state data cannot be tested in a closed-loop manner effectively is solved, and reliable and precision measurement data can be provided to a master station.
Owner:STATE GRID CORP OF CHINA +1
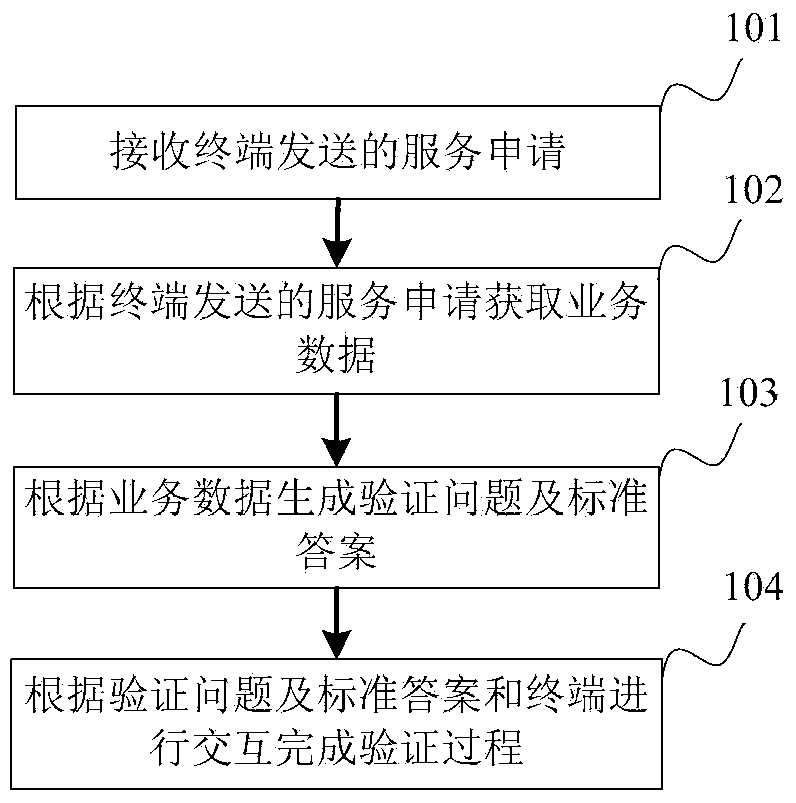
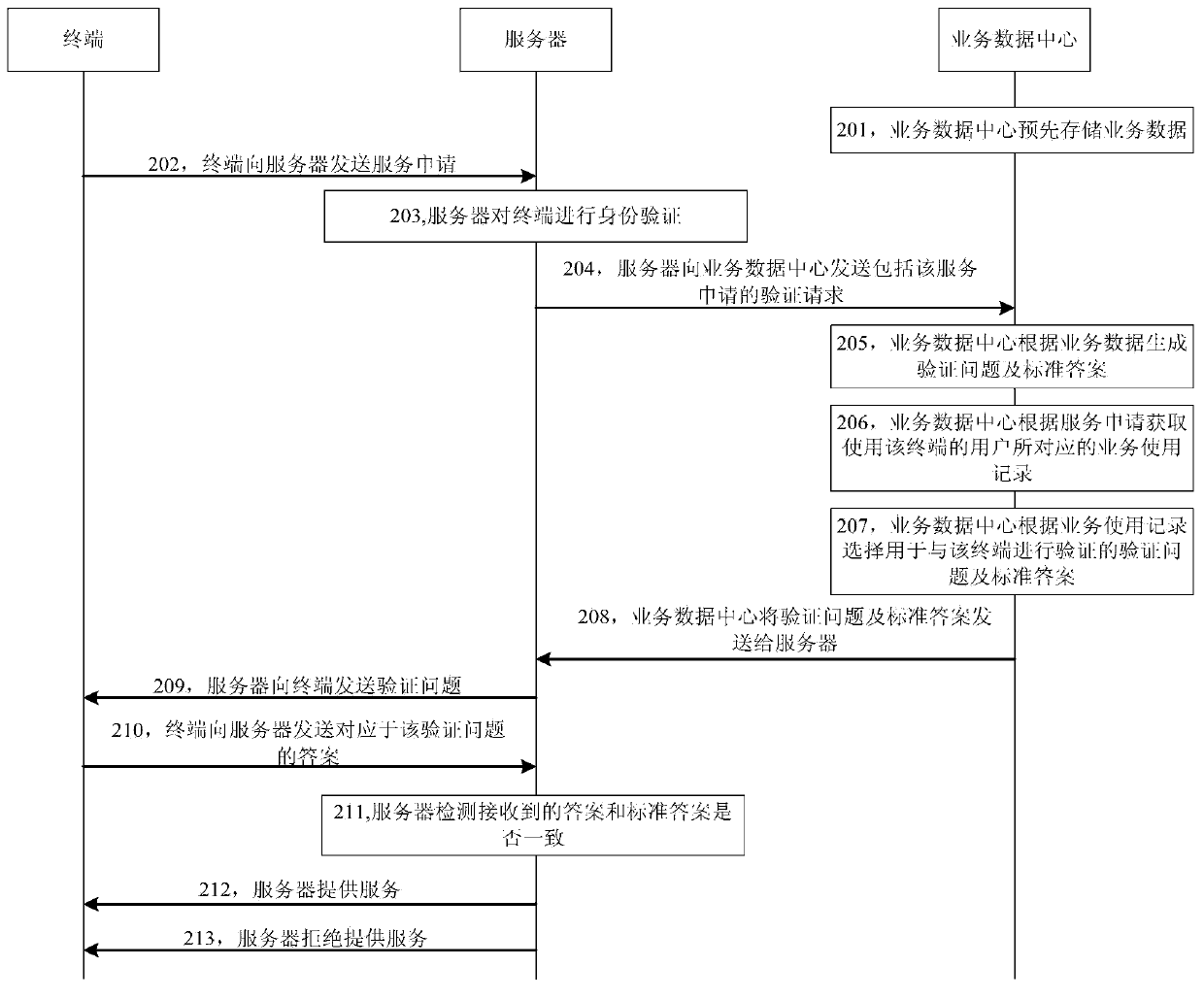
Verification method, device, server, service data center and system
InactiveCN104184709ASolve the problem of not being able to protect the security of network services The problem of network service securityUser identity/authority verificationDigital data authenticationAttackEngineering
Disclosed are a verification method, apparatus, server and system. The method includes: receiving a service request from a terminal; acquiring service data according to the service request received from the terminal; generating a verification question and a standard answer according to the service data; and interacting with the terminal according to the verification question and the standard answer to complete a verification process. The verification question and the standard answer are generated according to the service feature of the service requested by the terminal, and interaction is performed with the terminal according to the verification question and the standard answer to complete the verification process, thereby solving the problem that the network service security cannot be ensured using the verification code technology due to attacks launched by combining the machine and the manpower.
Owner:TENCENT TECH (SHENZHEN) CO LTD
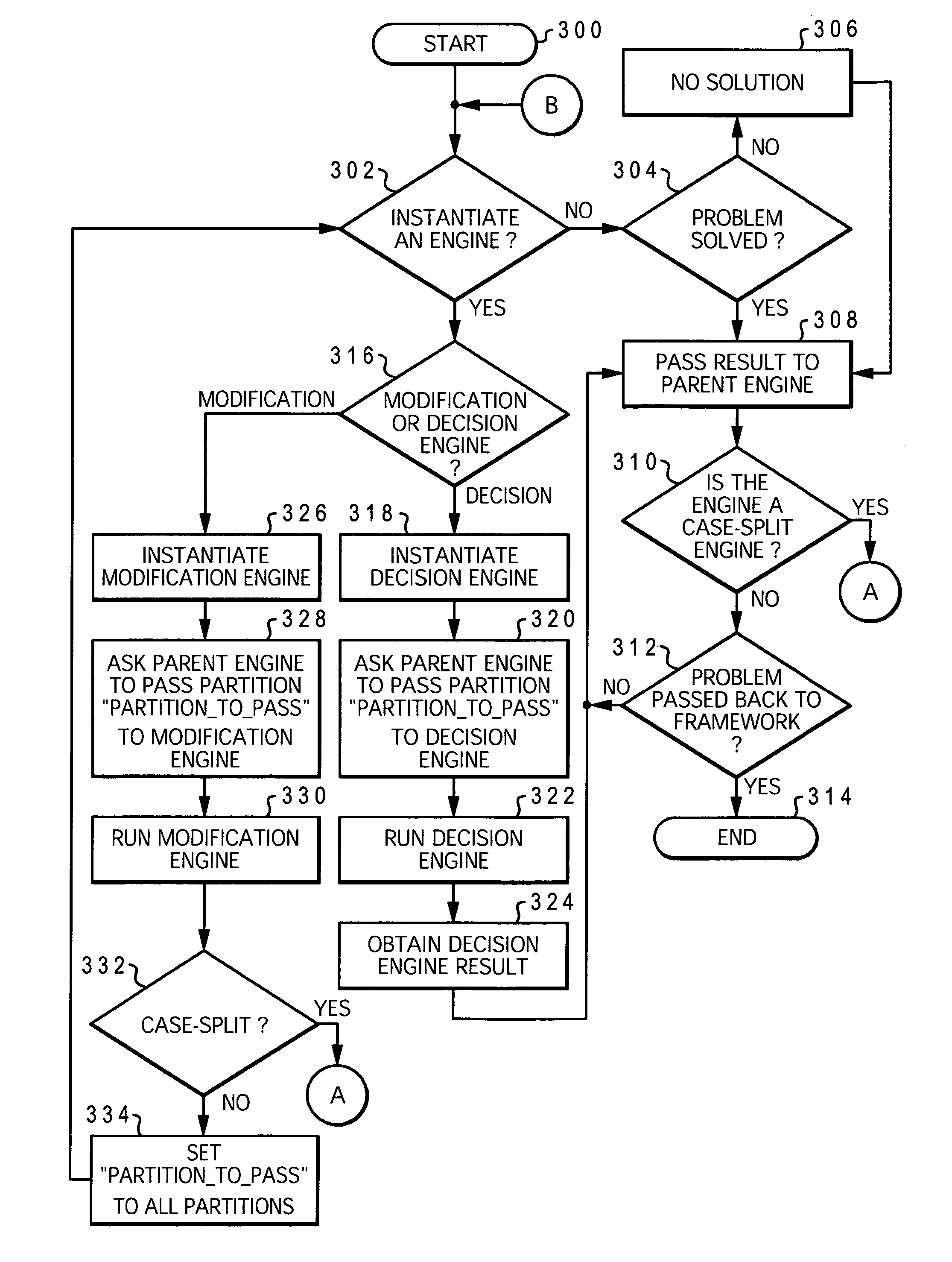
System and method for engine-controlled case splitting within multiple-engine based verification framework
ActiveUS7266795B2CAD circuit designSoftware simulation/interpretation/emulationComputer architectureVerification system
A system and method for implementing a verification system. Included is a first set of verification engines for attempting to solve a verification problem. At least one of the first set of verification engines divides the verification problem into a set of partitions and passes at least one of the set of partitions to a second set of verification engines. Each one of the set of partitions may be passed to a distinctly separate verification engine. A system framework is configured to communicate with an application program and further configured to instantiate at least one verification engine in a user-defined sequence. Included within at least one of the first set of verification engines is a means for communicating verification information to the second set of verification engines.
Owner:GOOGLE LLC
Fish bait for oxygen fish-gathering pit
The invention relates to a fish bait for an oxygen fish-gathering pit. The fish bait is prepared from, by weight, 7-20 parts of musk millet, 10-30 parts of corn grits soaked with baijiu, 15-30 parts of rice soaked with baijiu, 7-30 parts of corn flour, 12-30 parts of fine wheat germs, 15-30 parts of bentonite, 10-50 parts of rapid oxygen releasing powder, 3-10 parts of a binding agent, 0.3-5 parts of fruit essence and 1.33-3 parts of water. The fish bait for the oxygen fish-gathering pit has the advantages that the substance capable of releasing oxygen is added into the pit bait, and the fish gathering verification problem can be effectively solved; the fish bait can rapidly release the oxygen after being added into water, a fish luring substance capable of conducting up-and-down stereoscopic movement is provided, the bottom fish bait is reserved, and fish in the upper layer, fish in the middle layer and fish in the lower layer can be lured and gathered to enter the pit.
Owner:高佳泉
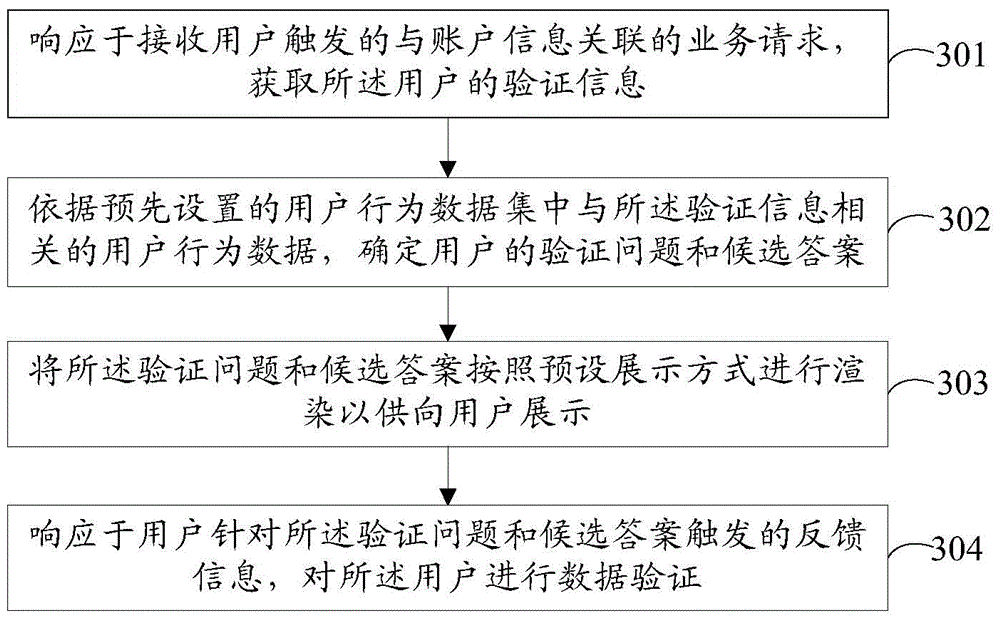
User behaviour based data verification method and device
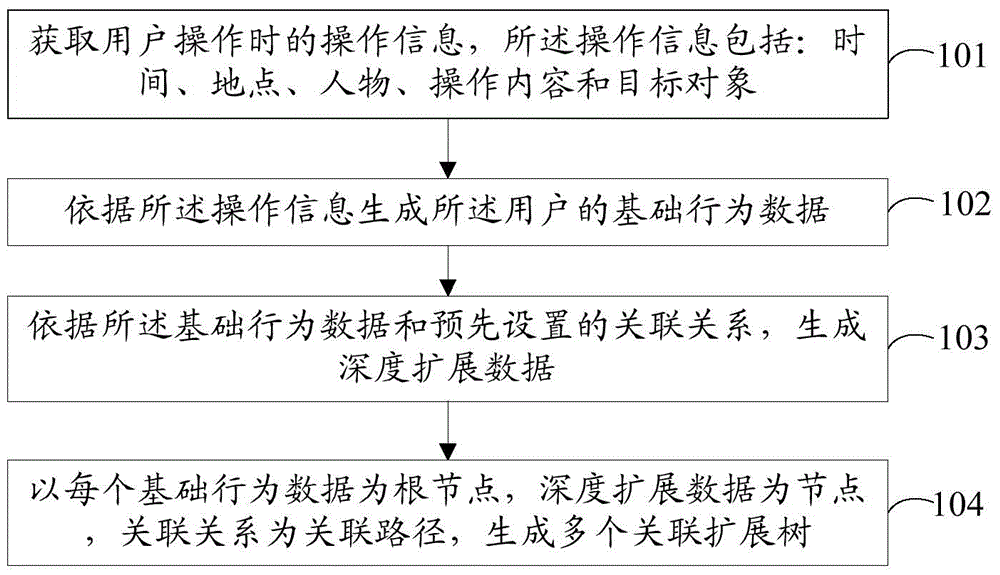
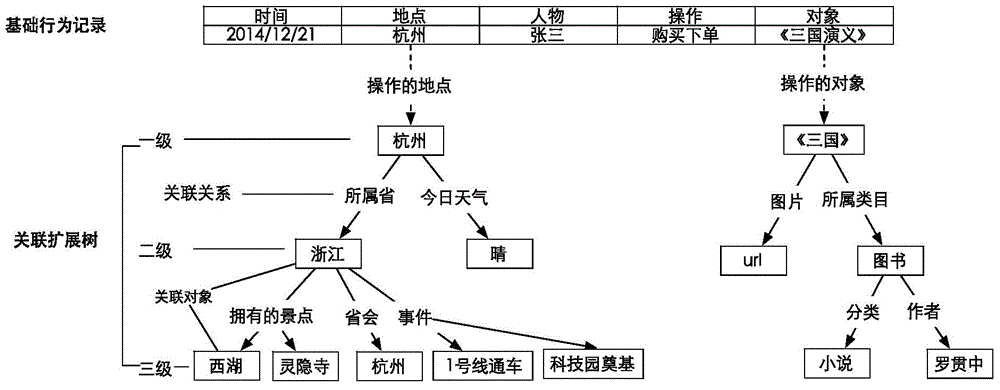
ActiveCN105989256AImprove securityReduce security risksDigital data authenticationData validationData set
The invention provides a user behaviour based data verification method and device. The method comprises the following steps: responding to a service request which is triggered by a user and related to account information, and acquiring verification information of the user, wherein the verification information comprises the account information; according to user behaviour data related to the verification information in a preset user behaviour data set, determining a verification problem and a candidate answer of the user, wherein the user behaviour data comprises basic behaviour data and deeply expanded data related to the basic behaviour data; rendering the verification problem and the candidate answer according to a preset display manner, so as to display to the user; and responding to feedback information which is triggered by the user according to the verification problem and the candidate answer, and carrying out data verification on the user. In the embodiment of the invention, data verification safety can be improved, and potential safety hazard of a user account can be reduced.
Owner:ALIBABA GRP HLDG LTD
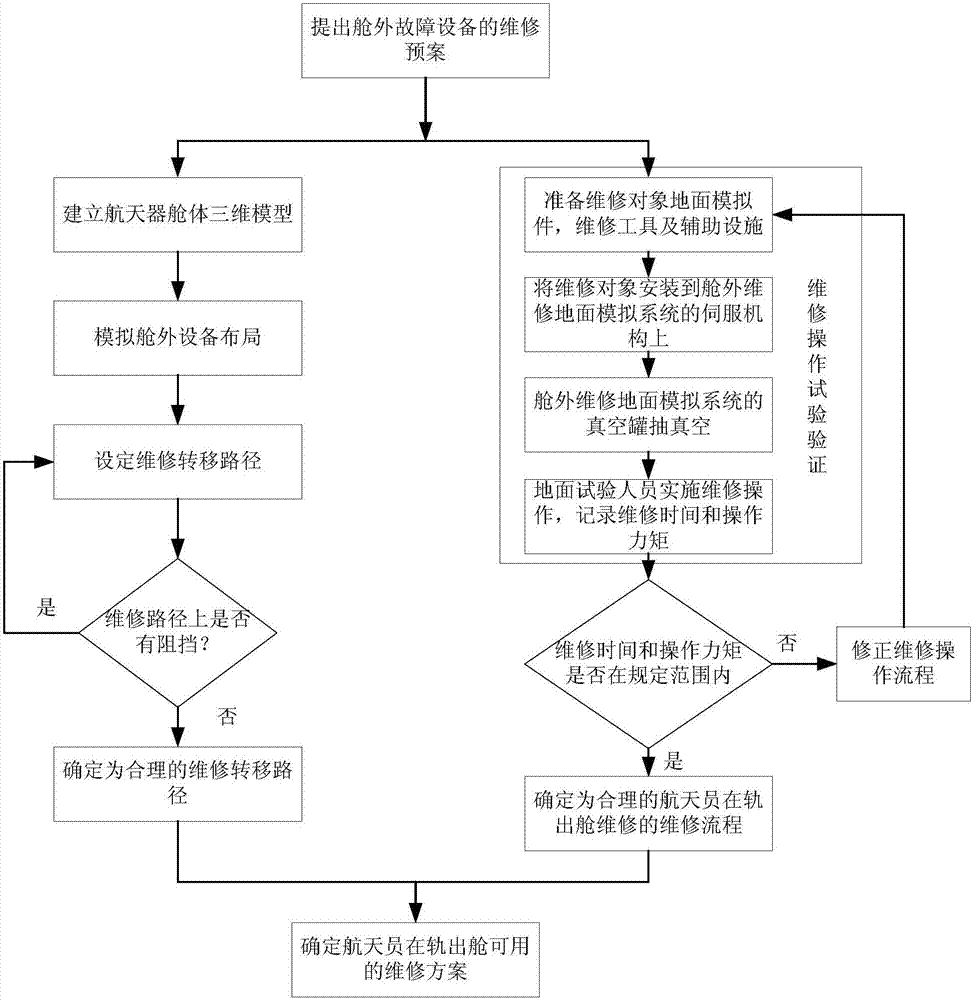
Fast response and support method for out-of-cabin in-orbit maintenance ground of spacecraft cabin
InactiveCN107255938AThe simulation verification method is simple and economicalThe verification result is accurateSimulator controlOrbitResponse capacity
The method provides a fast response and support method for the out-of-cabin in-orbit maintenance ground of a spacecraft cabin. The method comprises the steps of (1) providing a maintenance plan of the out-of-cabin fault equipment, wherein the maintenance plan comprises a maintenance transfer path, a maintenance operation process and a human-computer work efficiency evaluation standard; (2) establishing a three-dimensional model of a spacecraft cabin body, simulating the layout of all equipment outside the spacecraft cabin body, simulating and verifying the maintenance transfer path, judging whether the transfer path is blocked by external equipment or not; (3) testing and verifying the maintenance operation, recording the operation torque and the operation time; (4) judging whether the operation moment and the operation time conform to the human-computer work efficiency evaluation standard specified in the maintenance plan or not; (5) determining a maintenance scheme available for the out-of-cabin in-orbit maintenance of astronauts. Based on the method, the out-of-cabin equipment maintenance scheme of an in-orbit burst fault can be quickly determined. Therefore, the fast response capability within one hour can be realized. Moreover, the economical efficiency is excellent. The rapid verification problem of the large-mass external maintenance of a space station can be solved.
Owner:BEIJING SPACE TECH RES & TEST CENT
Method and apparatus for memory abstraction and for word level net list reduction and verification using same
ActiveUS8104000B2Reduce decreaseReduce complexityComputer aided designSoftware simulation/interpretation/emulationNetlistCircuit design
A computer implemented representation of a circuit design including memory is abstracted to a smaller netlist by replacing memory with substitute nodes representing selected slots in the memory, segmenting word level nodes, including one or more of the substitute nodes, in the netlist into segmented nodes, finding reduced safe sizes for the segmented nodes and generating an updated data structure representing the circuit design using the reduced safe sizes of the segmented nodes. The correctness of such systems can require reasoning about a much smaller number of memory entries and using nodes having smaller bit widths than exist in the circuit design. As a result, the computational complexity of the verification problem is substantially reduced.
Owner:SYNOPSYS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com