Call processing method, user terminal and server
A technology of call processing and server, which is applied in the field of communication to achieve the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
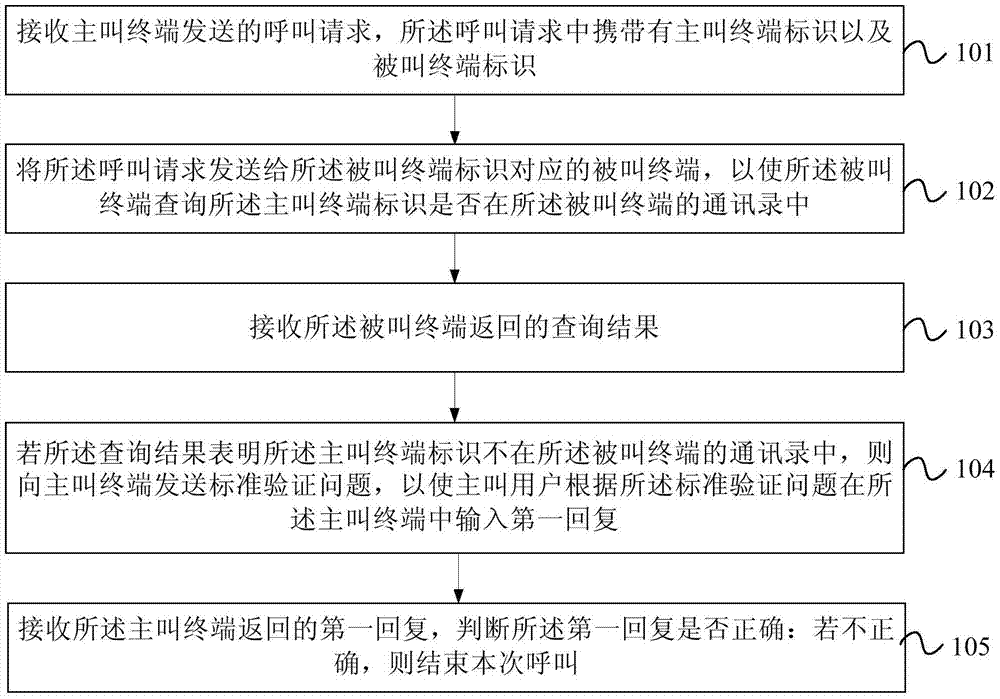
[0036] Embodiment 1 of the present invention provides a call processing method. figure 1 It is a flow chart of the call processing method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the method in this embodiment may include:
[0037] Step 101. Receive a call request sent by a calling terminal, where the call request carries an identifier of the calling terminal and an identifier of the called terminal.
[0038] Specifically, the execution subject in this embodiment may be a server. The calling terminal identifier may be the calling terminal number or account, and the called terminal identifier may be the called terminal number or account.
[0039] Step 102: Send the call request to the called terminal corresponding to the called terminal identifier, so that the called terminal inquires whether the calling terminal identifier is in the address book of the called terminal.
[0040] After the query is completed, the called terminal may send a...
Embodiment 2
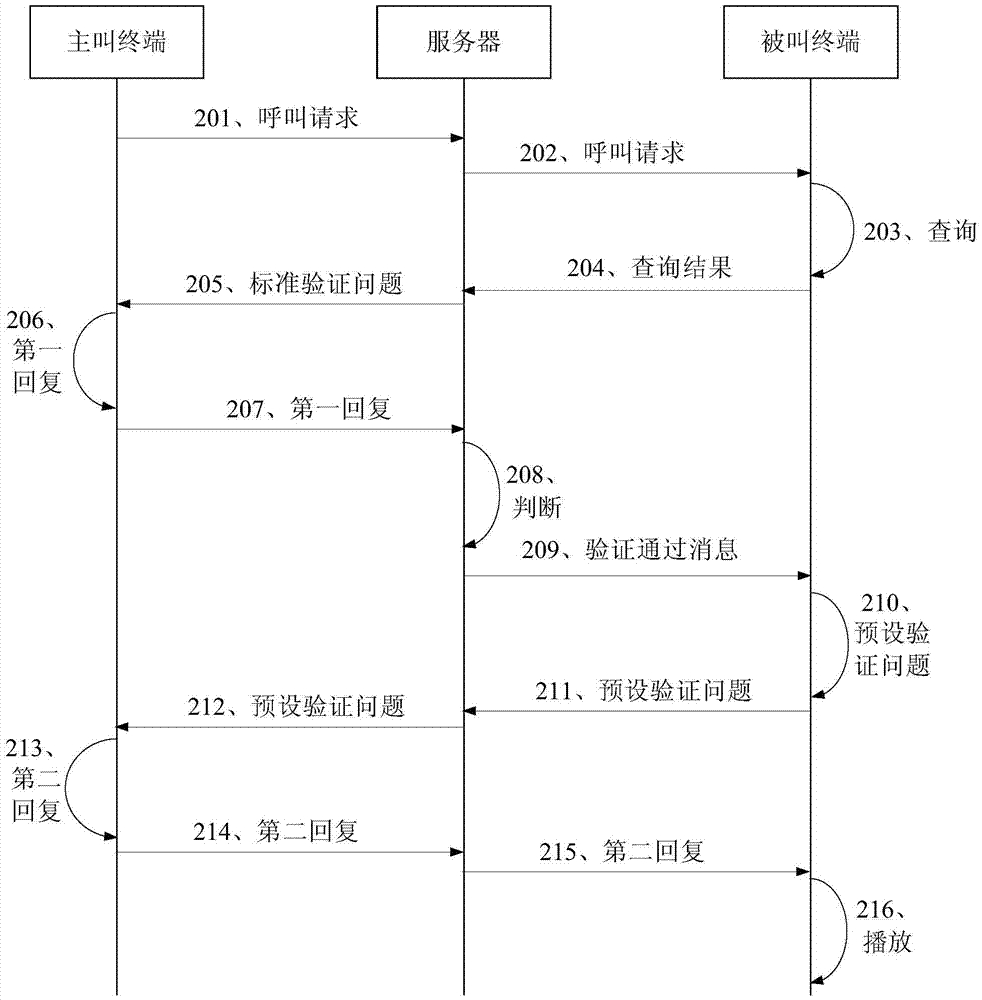
[0055] Embodiment 2 of the present invention provides a call processing method. In this embodiment, on the basis of the technical solution provided in Embodiment 1, further verification is performed on the calling terminal when the first reply is correct. figure 2 It is a flow chart of the call processing method provided by Embodiment 2 of the present invention. Such as figure 2 As shown, the method in this embodiment may include:
[0056] Step 201, the server receives a call request sent by a calling terminal, and the call request carries an identification of the calling terminal and an identification of the called terminal.
[0057] Step 202, the server sends the call request to the called terminal corresponding to the called terminal identifier.
[0058] Step 203, the called terminal queries whether the calling terminal identifier is in the address book of the called terminal.
[0059] Step 204, the server receives the query result returned by the called terminal.
...
Embodiment 3
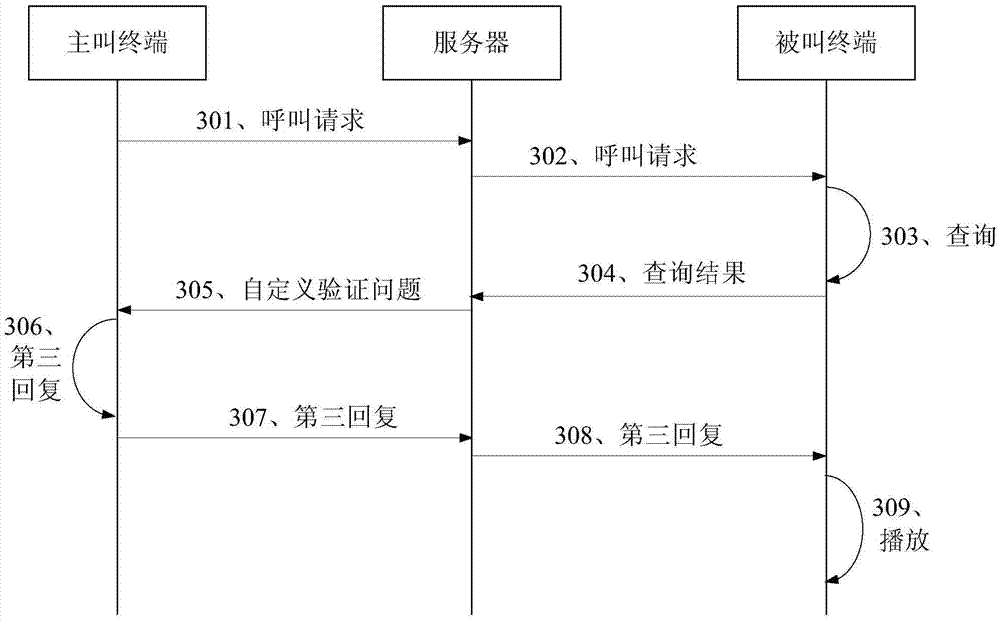
[0082] Embodiment 3 of the present invention provides a call processing method. This embodiment is based on the technical solution provided by the first embodiment, and provides a call processing method when the identification of the calling terminal is in the address book of the called terminal. image 3 It is a flow chart of the call processing method provided by Embodiment 3 of the present invention. Such as image 3 As shown, the method in this embodiment may include:
[0083] Step 301, the server receives a call request sent by a calling terminal, and the call request carries a calling terminal identifier and a called terminal identifier.
[0084] Step 302, the server sends the call request to the called terminal corresponding to the called terminal identifier.
[0085] Step 303, the called terminal inquires whether the calling terminal ID is in the address book of the called terminal: if it is in the address book, the called terminal searches for the calling terminal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com