Hash tree-based data dynamic operation verifiability method
A data dynamic and data technology, applied in the computer field, can solve problems such as not considering the impact of computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0092] The technical solutions of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0093] security assumption
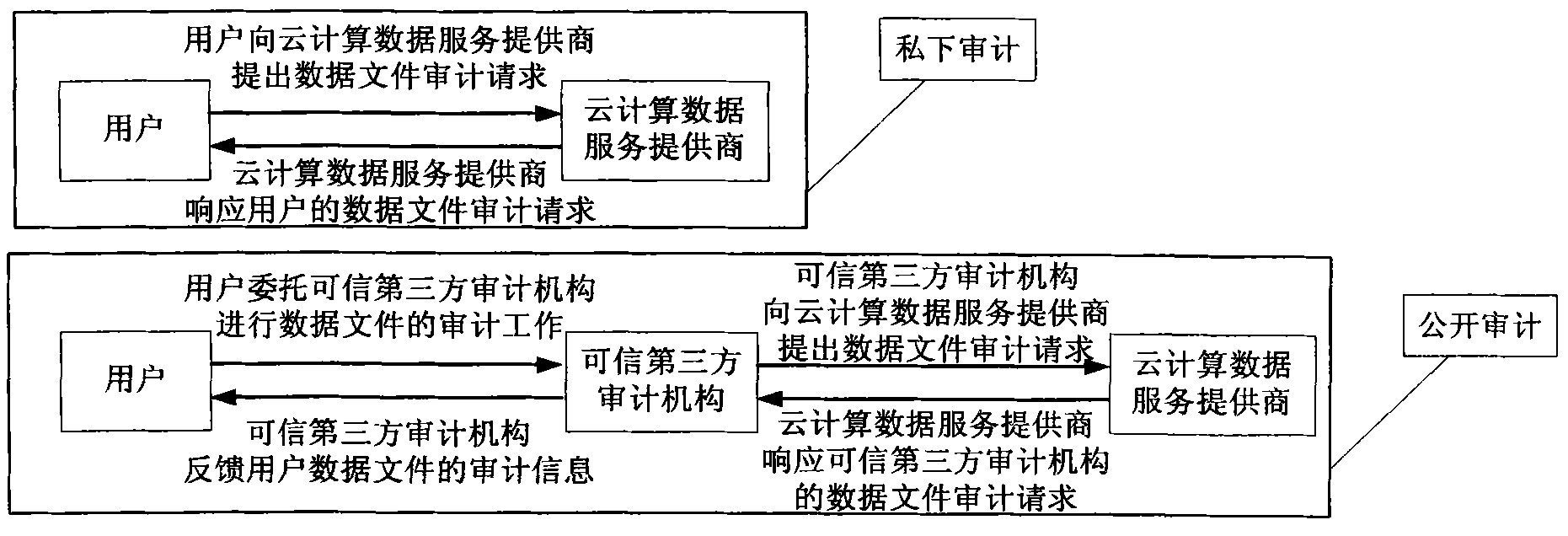
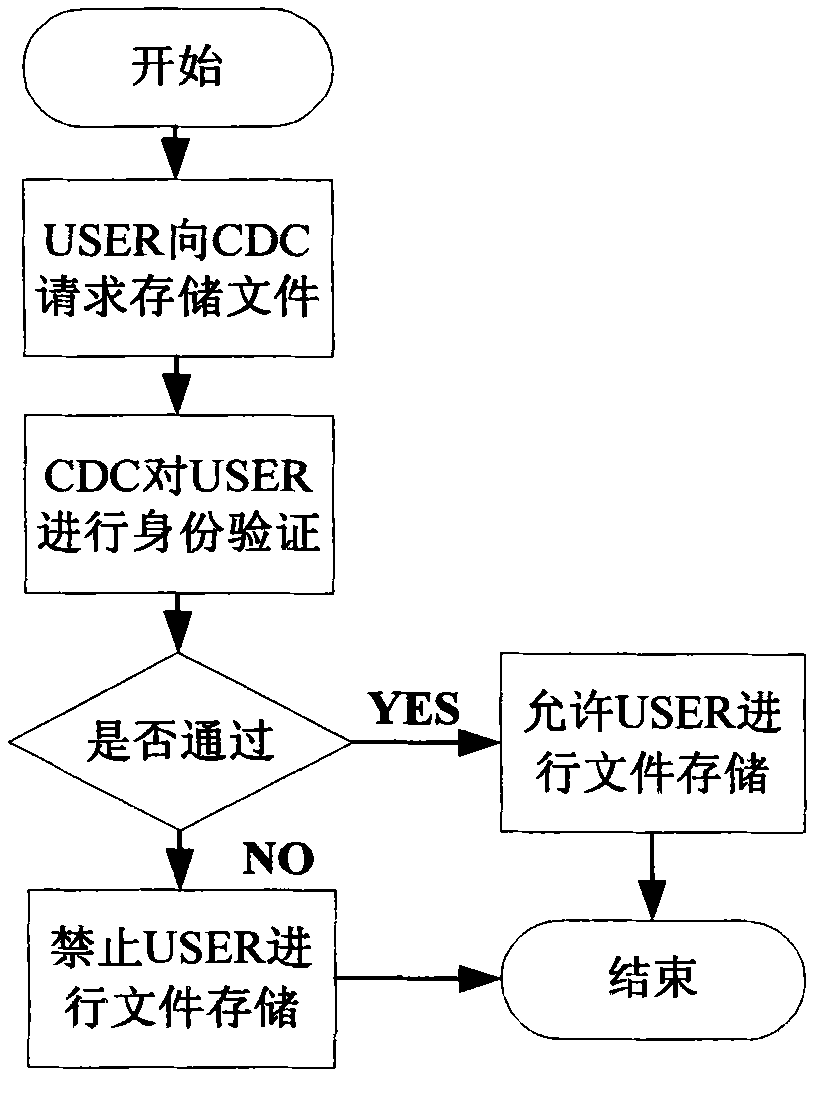
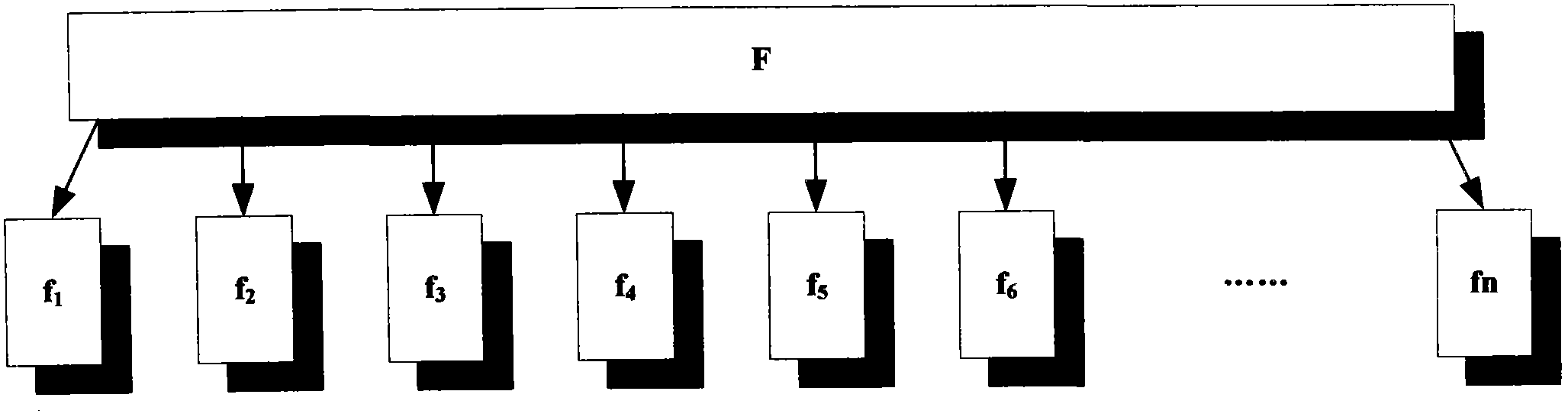
[0094] The scheme assumes that all communication channels do not have a large area of data packet loss (communication channels include three parts between USER and CDC, between CDC and TPA, and between TPA and USER). At the same time, the TPA in the scheme is an unbiased and completely credible third-party audit organization, which can faithfully complete all tasks entrusted by USER. The security assumption of CDC in the scheme is slightly different from previous studies. CDC is no longer completely untrustworthy, but has a certain degree of curiosity but can faithfully complete all tasks. CDC guarantees the correctness, non-deception and non-repudiation of all parameter calculation results undertaken by itself, and can unconditionally respond to audit requests for any user da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com