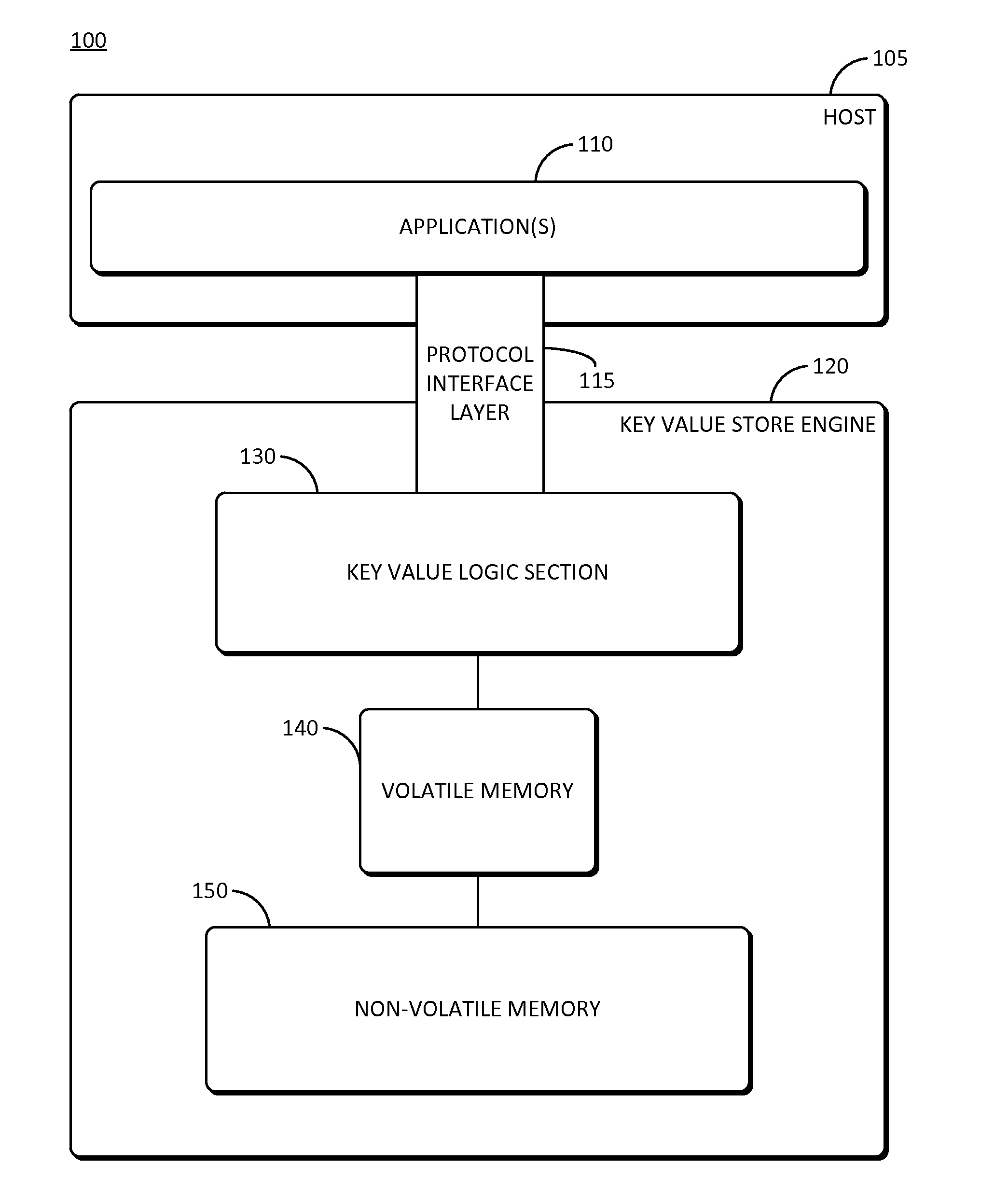
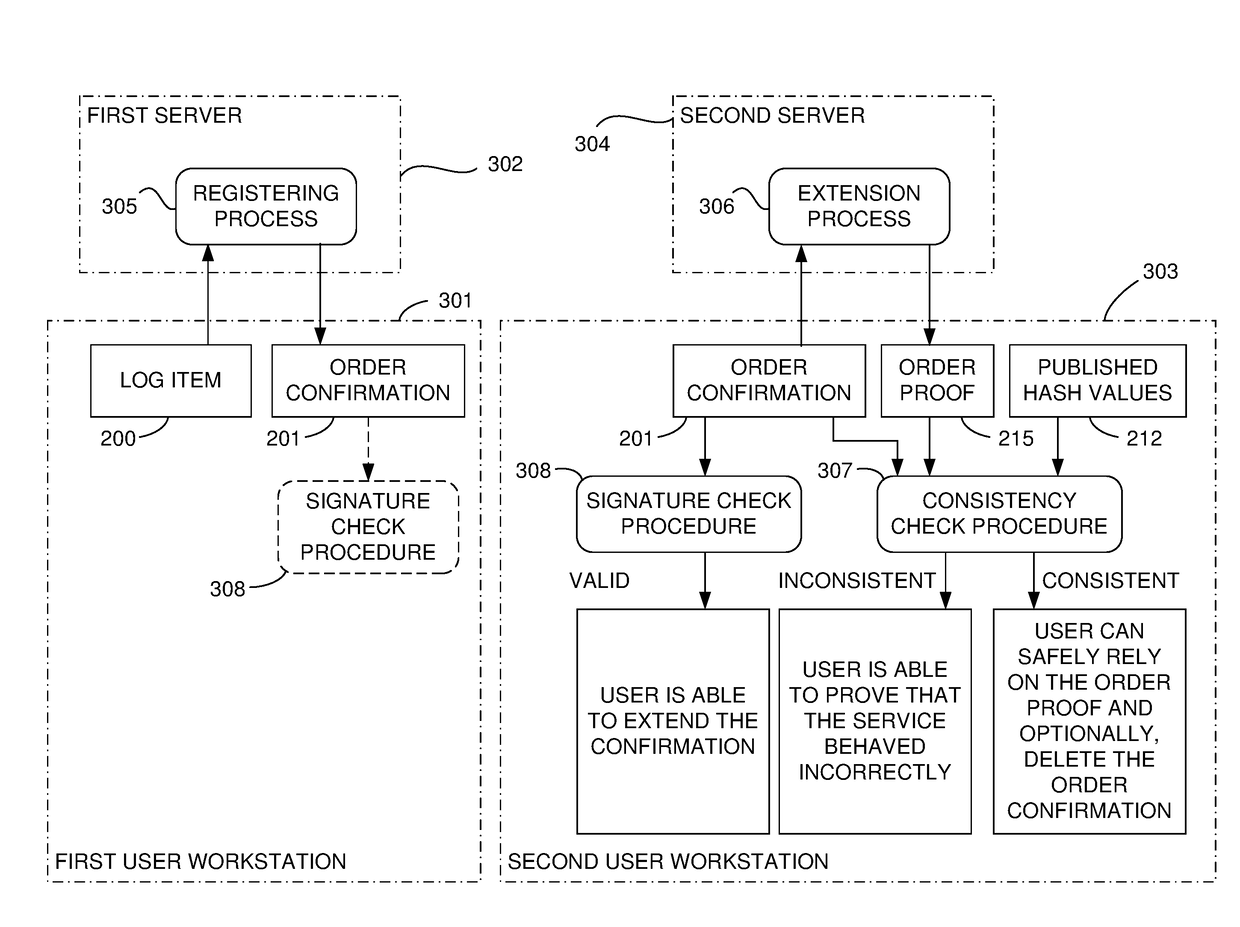
Patents
Literature
331 results about "Merkle tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
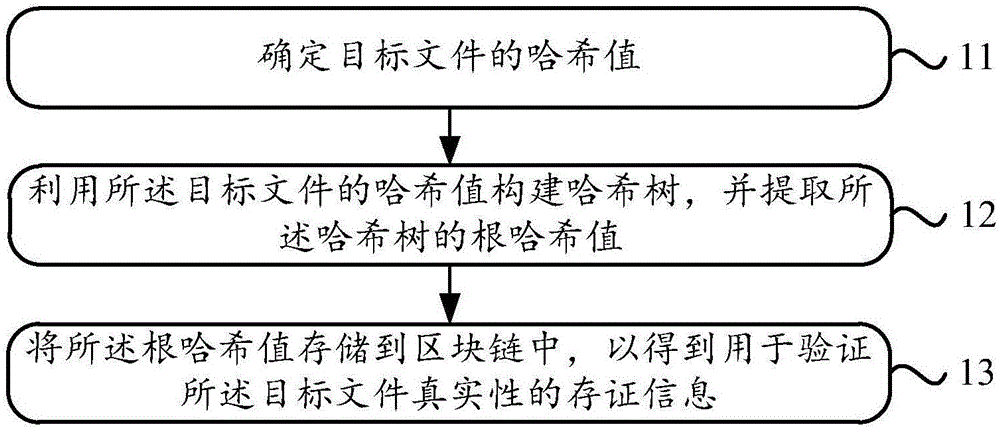
Patent Type
Patent Status
Application Year
Inventor
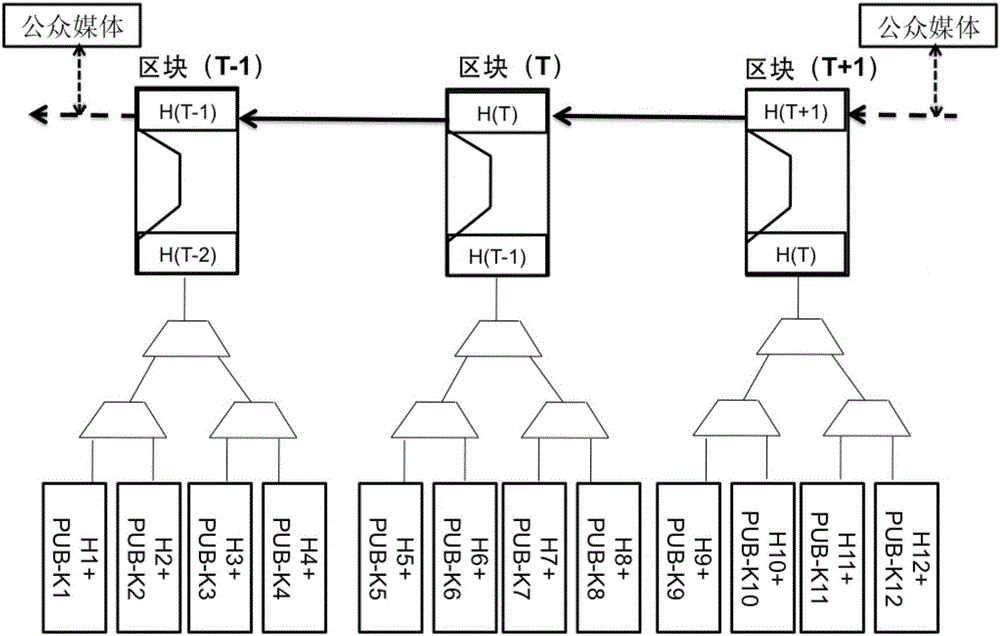
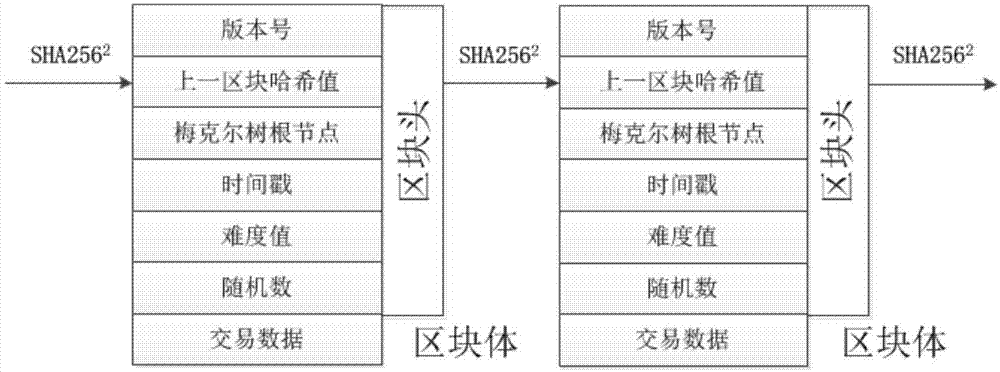
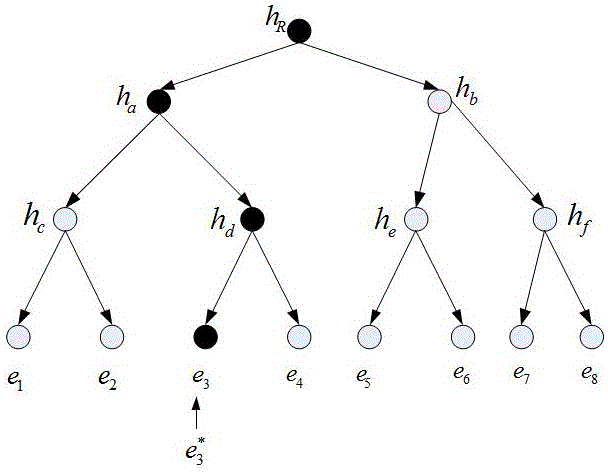
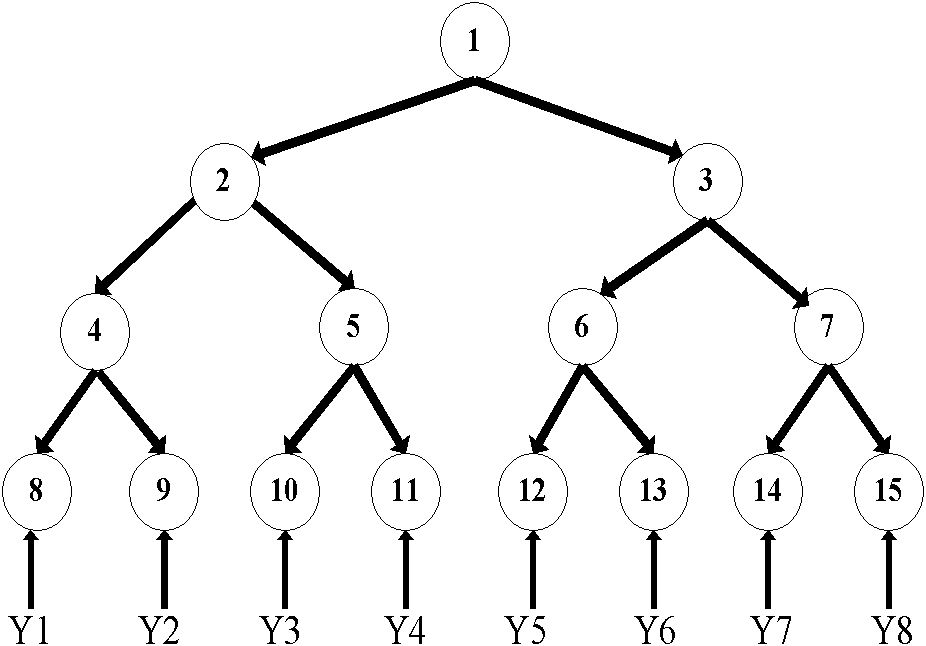
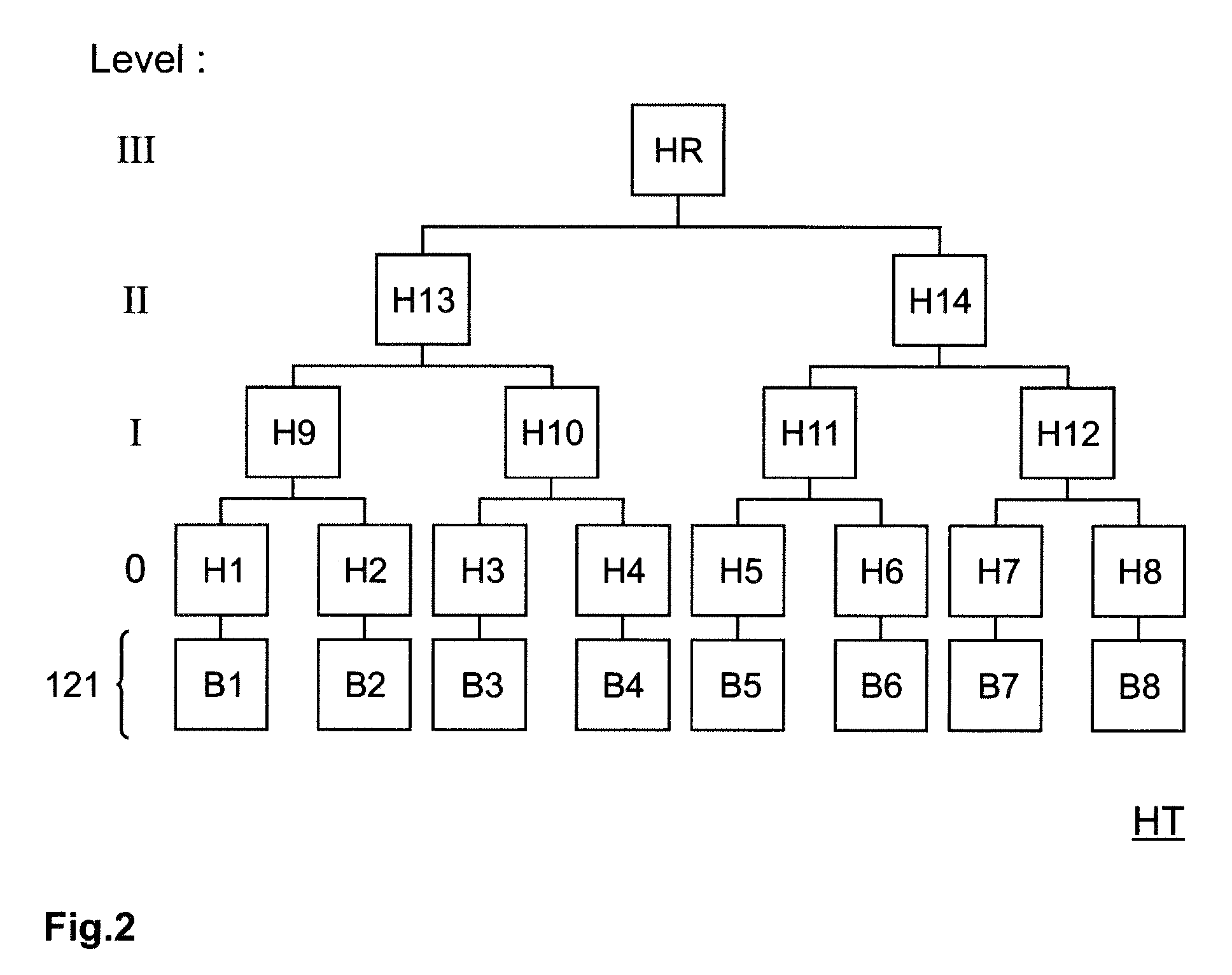
In cryptography and computer science, a hash tree or Merkle tree is a tree in which every leaf node is labelled with the hash of a data block, and every non-leaf node is labelled with the cryptographic hash of the labels of its child nodes. Hash trees allow efficient and secure verification of the contents of large data structures. Hash trees are a generalization of hash lists and hash chains.
Block chain data comparison and consensus method
ActiveCN105719185AWill not limit performanceNo capacity constraintsFinanceFinancial transactionFile comparison
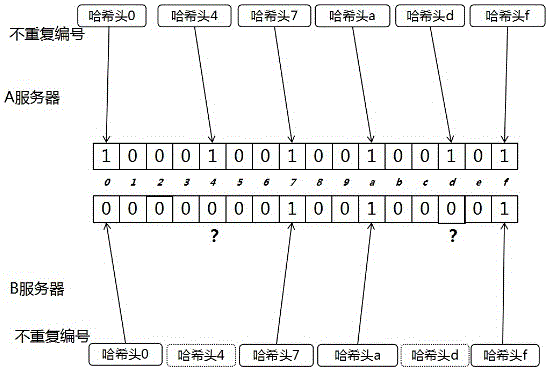
The invention discloses a block chain data comparison and consensus method used for hash value calculation of content of each transaction. By changing the random numbers, the numbers of some bits of the hash values are set not to be repeated in a time period, and can be called as unrepeated serial numbers. Accounting servers are used to compare the numbers of the preset bits of the hash values to determine whether the transactions are identical or not. The unrepeated serial number comparison can be carried out in a way of establishing the Merkle-like tree, and because the numbers of the preset bits of the hash values of the transactions are not repeated, and can be used as the serial numbers, and can be disposed in the Merkle-like tree according to the certain rule, and therefore for different accounting servers, the positions of the hash values of the same transaction on the Merkle trees are totally identical, and the differences can be found out quickly, the data transfer amount can be reduced, and the time required by the consensus can be greatly accelerated.
Owner:HANGZHOU FUZAMEI TECH CO LTD
Method and system for constructing electronic evidence
ActiveCN105790954AReduce identification costsImprove objectivityUser identity/authority verificationTimestampChain system
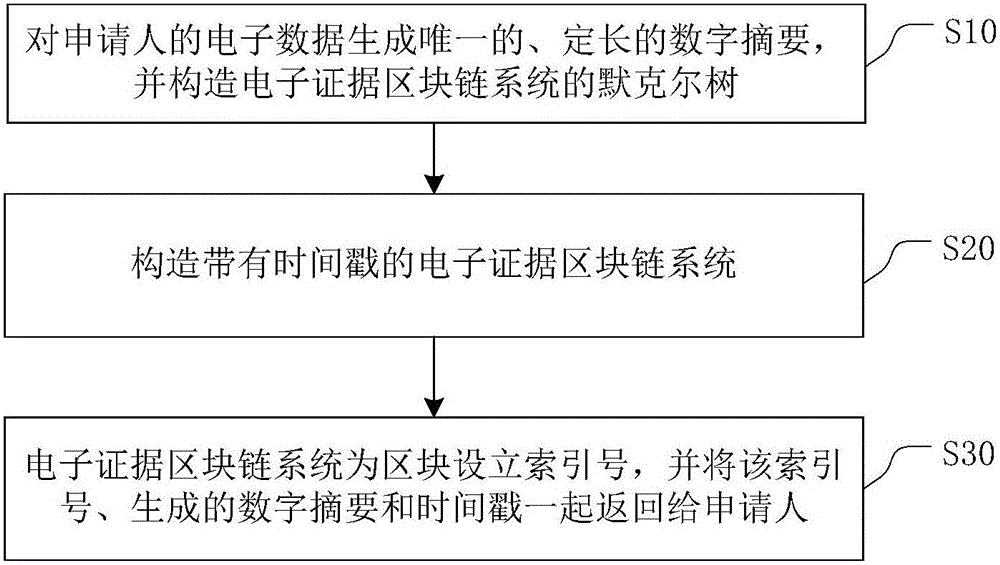
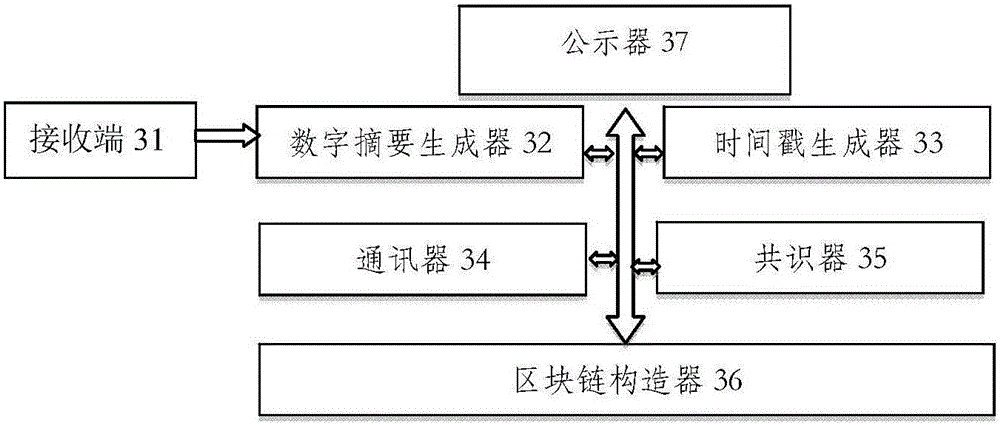
The invention relates to a method for constructing an electronic evidence. The method specifically comprises the following steps: generating a unique length-fixed digital abstract for electronic data of an applicant, and constructing a Merkle tree of an electronic evidence block chain system; constructing the electronic evidence block chain system with a timestamp; and setting an index number for a block by the electronic evidence block chain system, and returning the index number, the generated digital abstract and the timestamp to the applicant together. According to the method and the system disclosed by the invention, all participating parties can construct jointly, maintain jointly and supervise jointly, thereby meeting the right to know and the supervision right of each party; the identification cost of the electronic evidence is reduced, the identification efficiency is improved, and the objectivity and the reliability of the electronic evidence are enhanced.
Owner:BUBI BEIJING NETWORK TECH CO LTD
Node consensus verification method under league chain network through asynchronous mode
InactiveCN106529951AImprove throughputImprove network throughputFinanceElectronic credentialsValidation methodsChain network
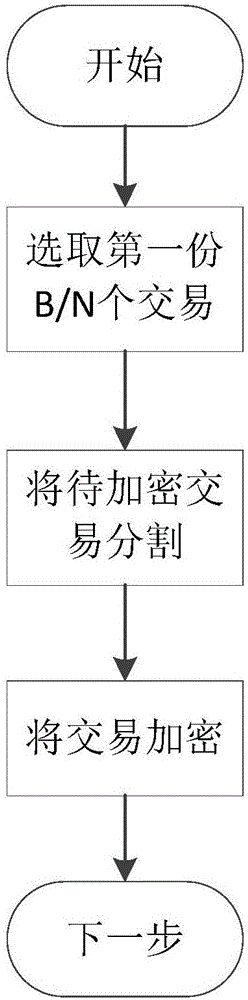
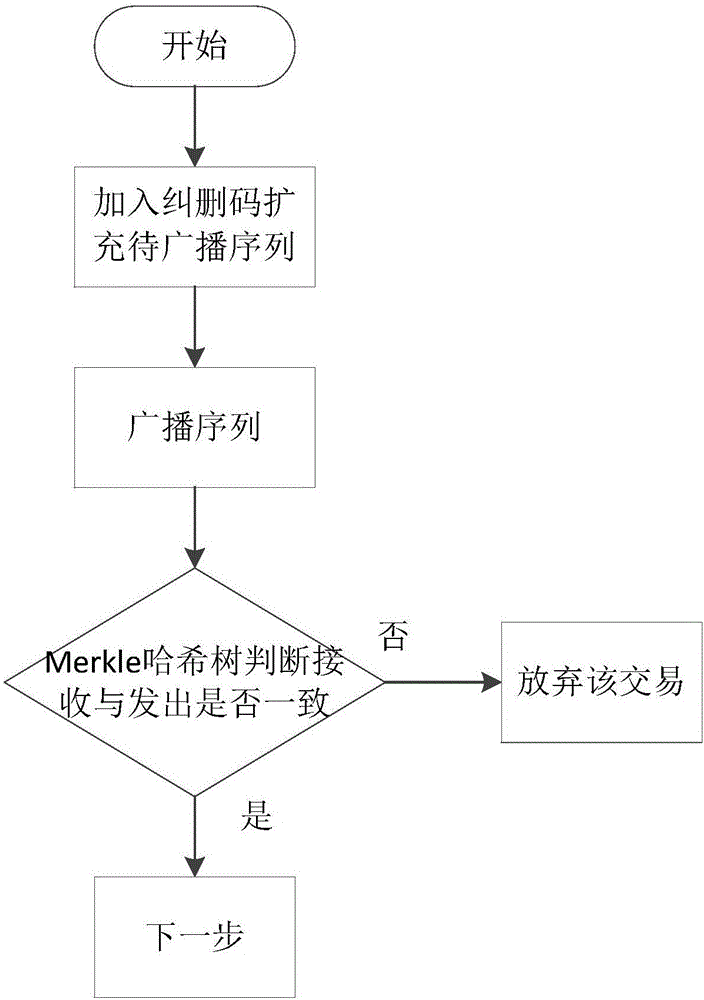
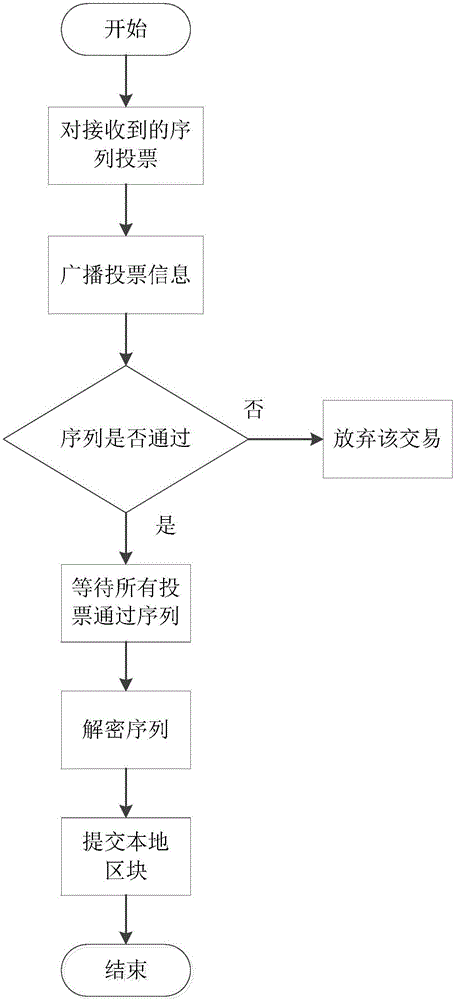
The invention discloses a node consensus verification method under a league chain network through an asynchronous mode. Each node takes a transaction request from the head of a buffer queue to act as a transaction sequence to be submitted and then encrypts the sequence by using threshold encryption; each node broadcasts the encrypted transaction sequence, ensures the integrity of the transmitted message by using an erasure code and ensures message consistency of different nodes by using a Merkle tree; and all the nodes vote the transaction sequences by using the binary Byzantine consensus agreement to reach a consensus, each node waits for local receiving all the voted transaction sequences and then decrypts the transaction sequences by using threshold decryption so as to finally obtain the decrypted transaction information to act as the transaction request written in blocks within the period. The method is completely decentralized, the system has no timeout mechanism and the broadcast message completely depends on the network bandwidth so that the method has higher network throughput when a large number of nodes exist in the network in comparison with the conventional synchronization Byzantine fault tolerance consensus method.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Hash-based electronic signatures for data sets such as dnssec
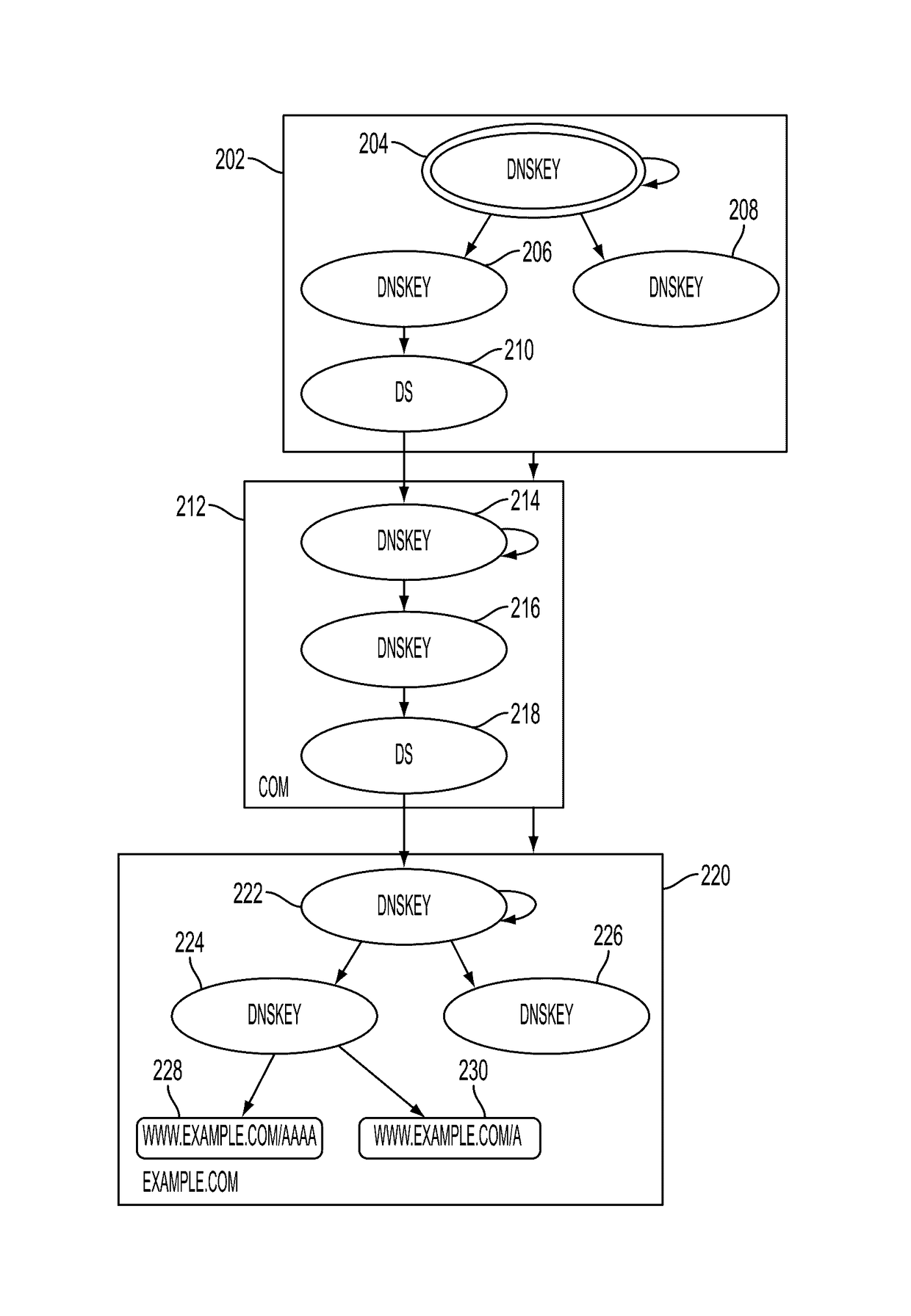
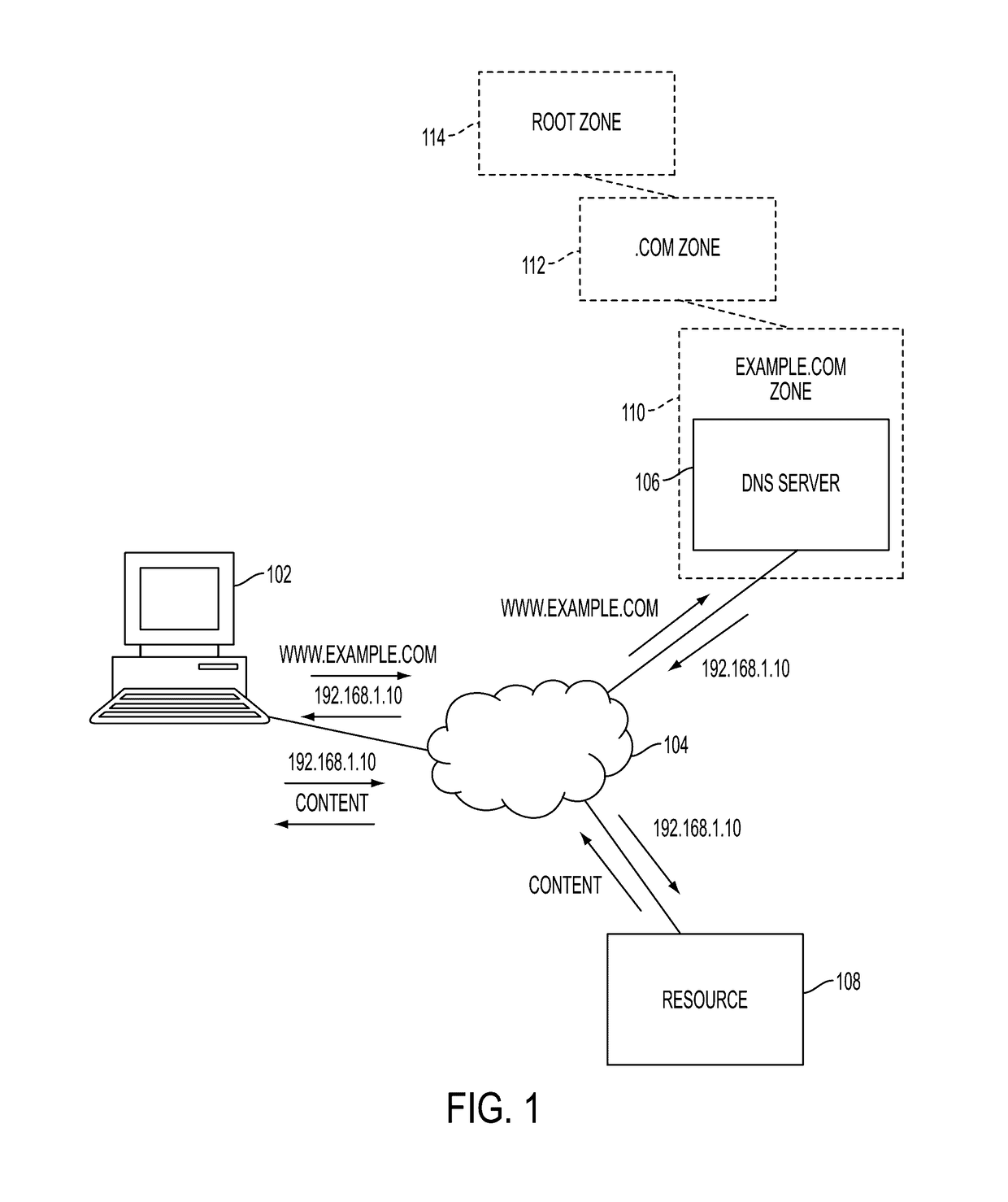
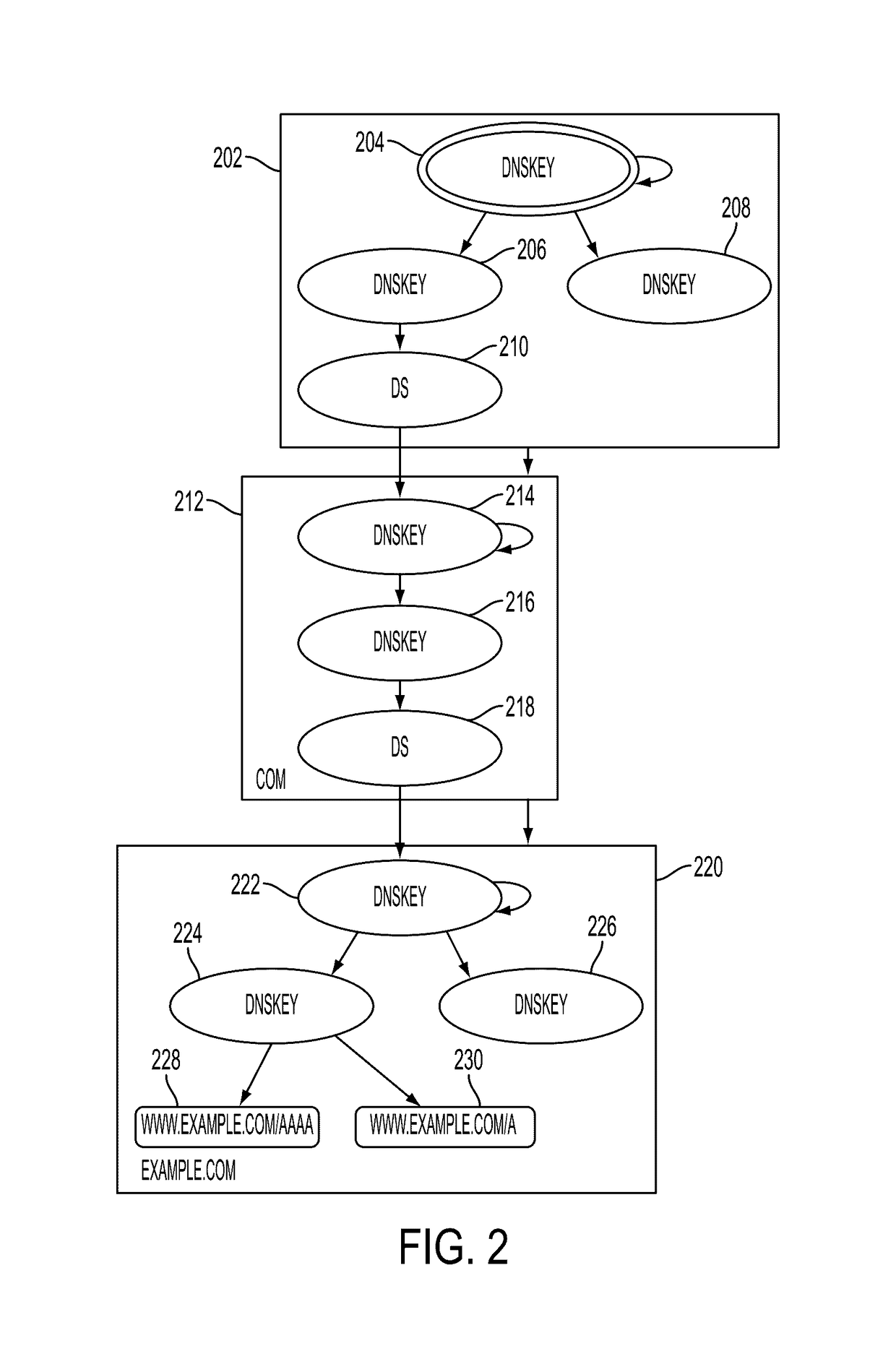
Techniques for electronically signing DNS records stored in a zone file for an internet DNS zone are presented. The techniques include electronically accessing a plurality of DNS resource records of a DNS zone stored on one or more DNS servers of a distributed DNS database; generating a plurality of leaf nodes from the plurality of DNS resource records; constructing a recursive hash tree from the plurality of leaf nodes, where the recursive hash tree includes a plurality of nodes including a root node and the plurality of leaf nodes, where each node of the plurality of nodes includes either a leaf node or a hash of data including child nodes; storing the root node in a DNS key resource record for a zone signing key for the zone; and publishing, in a DNS resource record signature resource record, validation data including path data from the recursive hash tree.
Owner:VERISIGN
Data storage method, data verification method and device
ActiveCN106815530AAuthenticity checkDigital data protectionComputer hardwareSource Data Verification
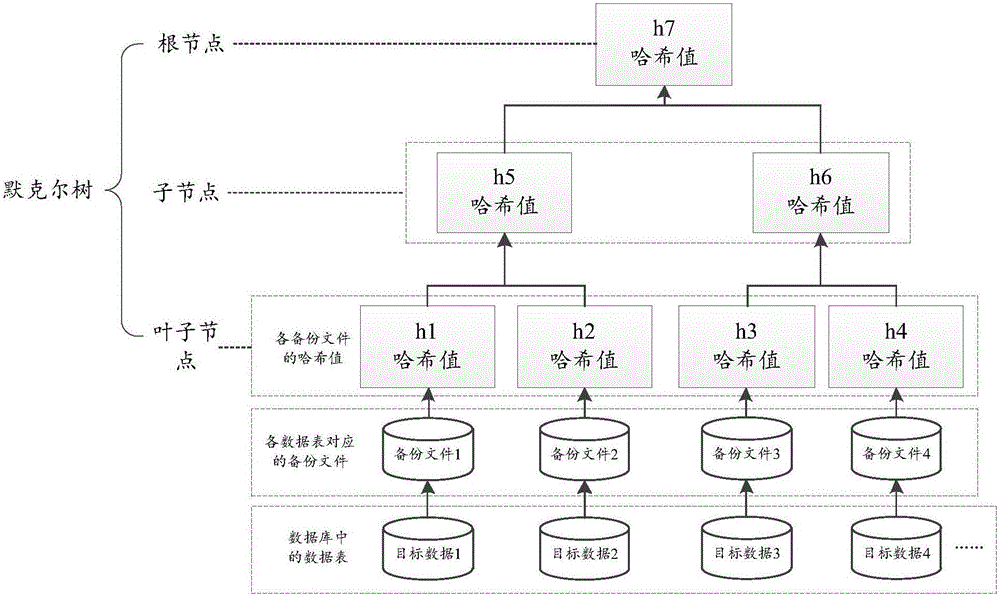
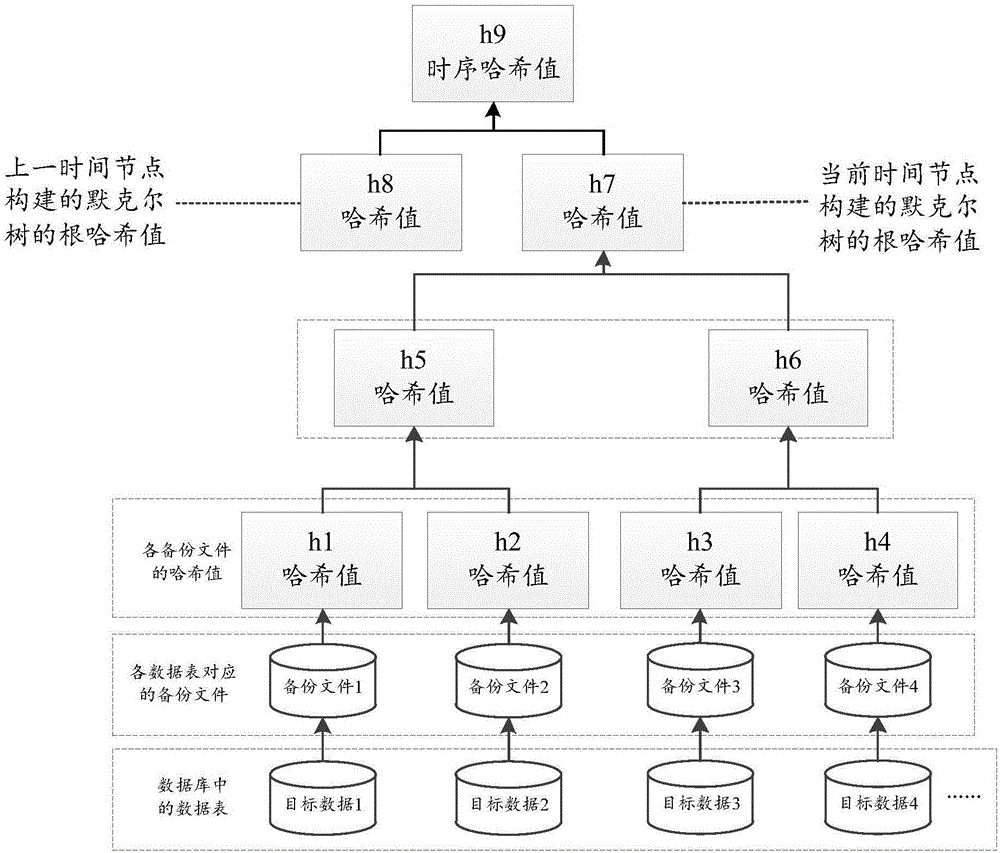
The invention discloses a data storage method. The data storage method is used for solving the problem that the truth of the data cannot be guaranteed in the prior art. The method comprises the following steps: confirming a Hash value of a target file; utilizing the Hash value of the target file to construct a Hash tree and extracting a root Hash value of the Hash tree; storing the root Hash value in a block chain, thereby acquiring storage information of the truth of the target file, wherein the storage information includes a sign of a block of the Hash value of the target file, a storage time stamp of the target file and the Hash value of the target file. The invention also discloses a data storage device, a data verification method and a data verification device.
Owner:北京爱接力科技发展有限公司
Block-chain based P2P network cloud storage method in big data environment
ActiveCN107360156AEnsure data storage securityEnsure safetyUser identity/authority verificationCloud storageMerkle tree
The invention relates to a block-chain based P2P network cloud storage method in a big data environment. The block-chain based P2P network cloud storage method in the big data environment comprises the steps of dividing data into blocks, encrypting the data and numbering the data according to a sequence; uploading the processed data into a computer with idle storage space in the whole P2P network; storing an encrypted file in a computer around a user who needs the storage space randomly by regarding the block-chain as a transaction mechanism; and finally carrying out completeness verification for all the transaction information by using a Meckel Hash Tree in the network and detecting whether the transaction information is tampered. The block-chain based P2P network cloud storage method in the big data environment is characterized in that the related information of the stored file block rather than the file block per se is stored in the block-chain while encrypted file blocks are randomly stored in the computer around the user who needs the storage space.
Owner:GUANGDONG UNIV OF TECH
Method and apparatus for secure and small credits for verifiable service provider metering
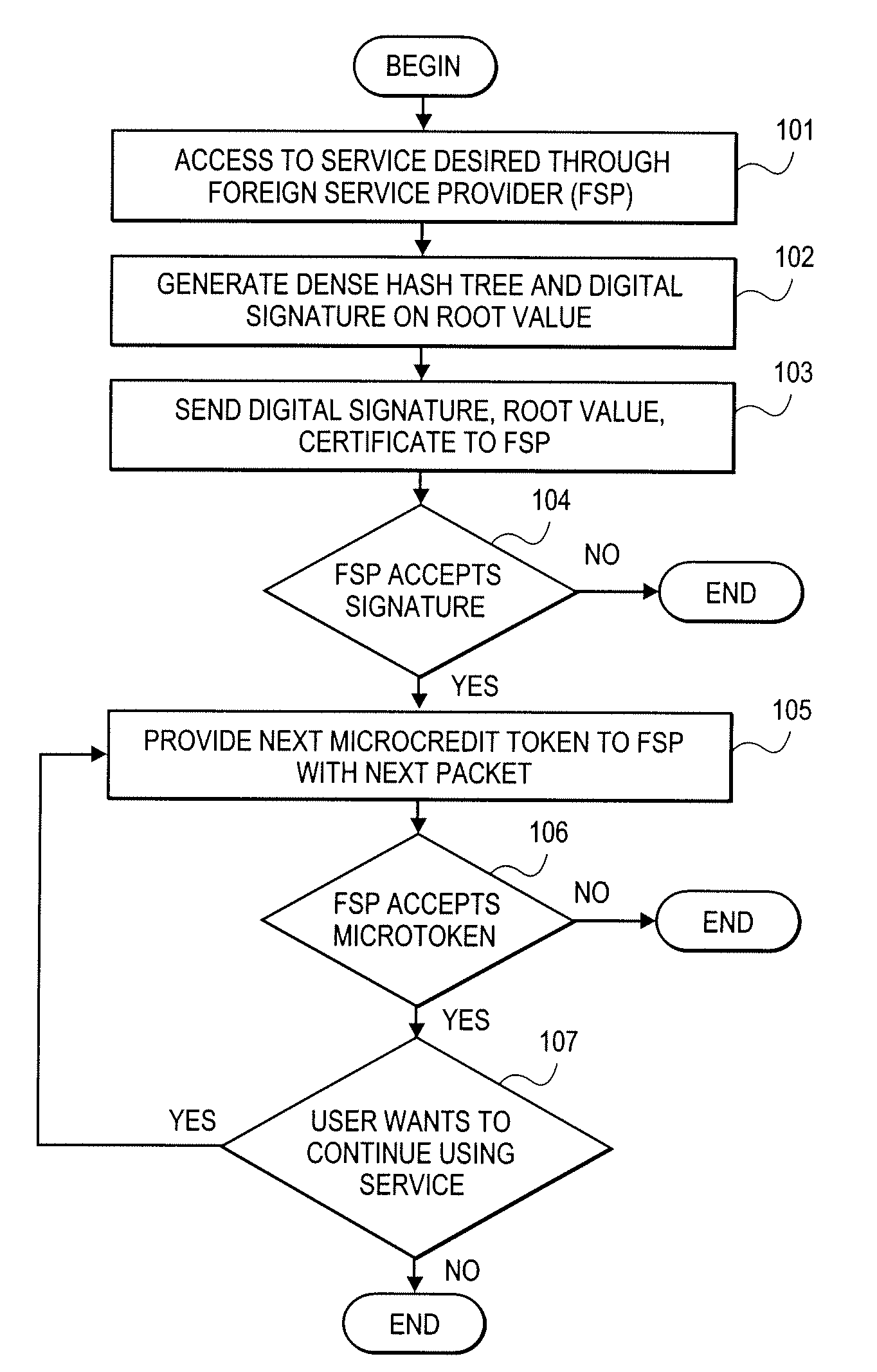
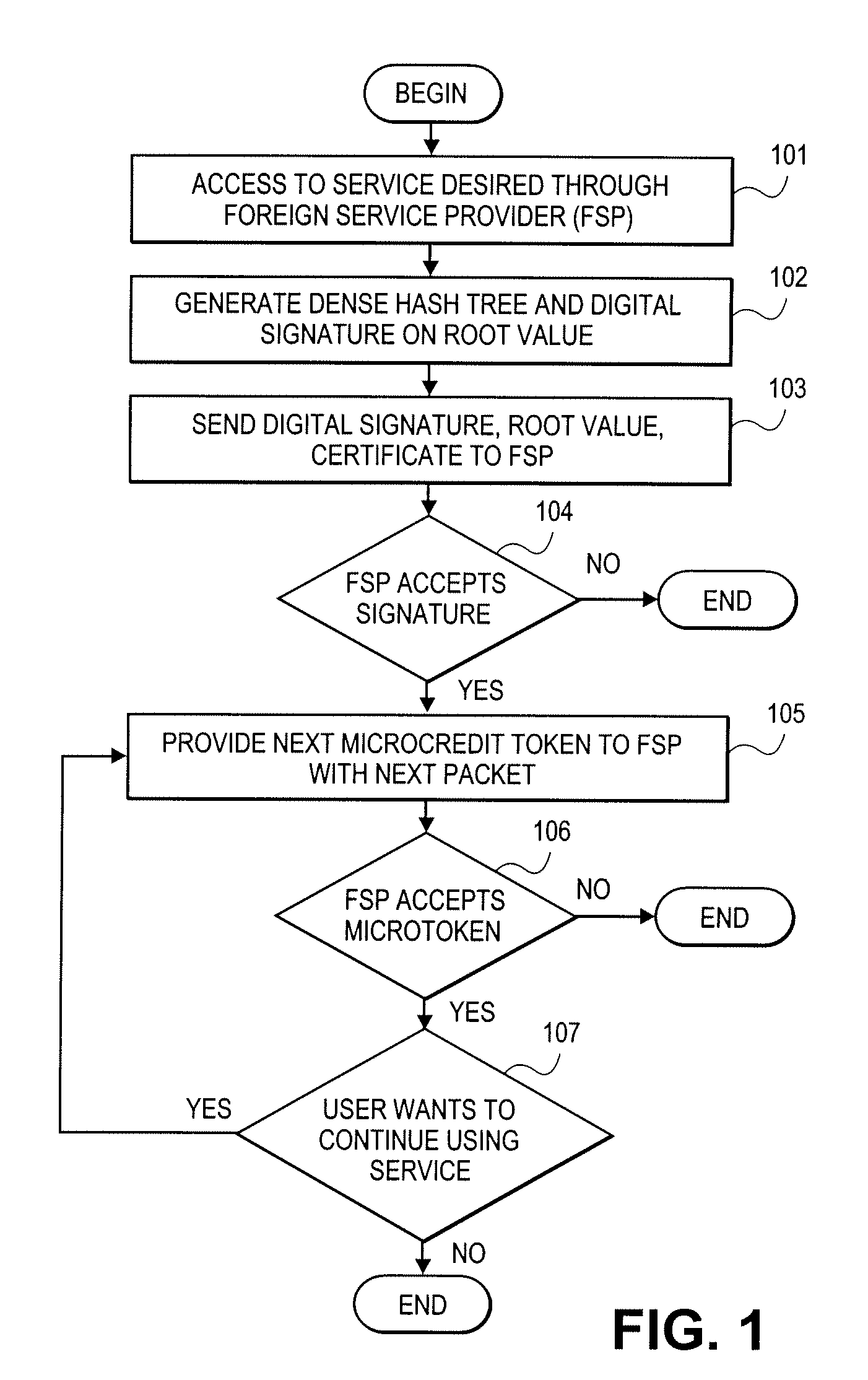
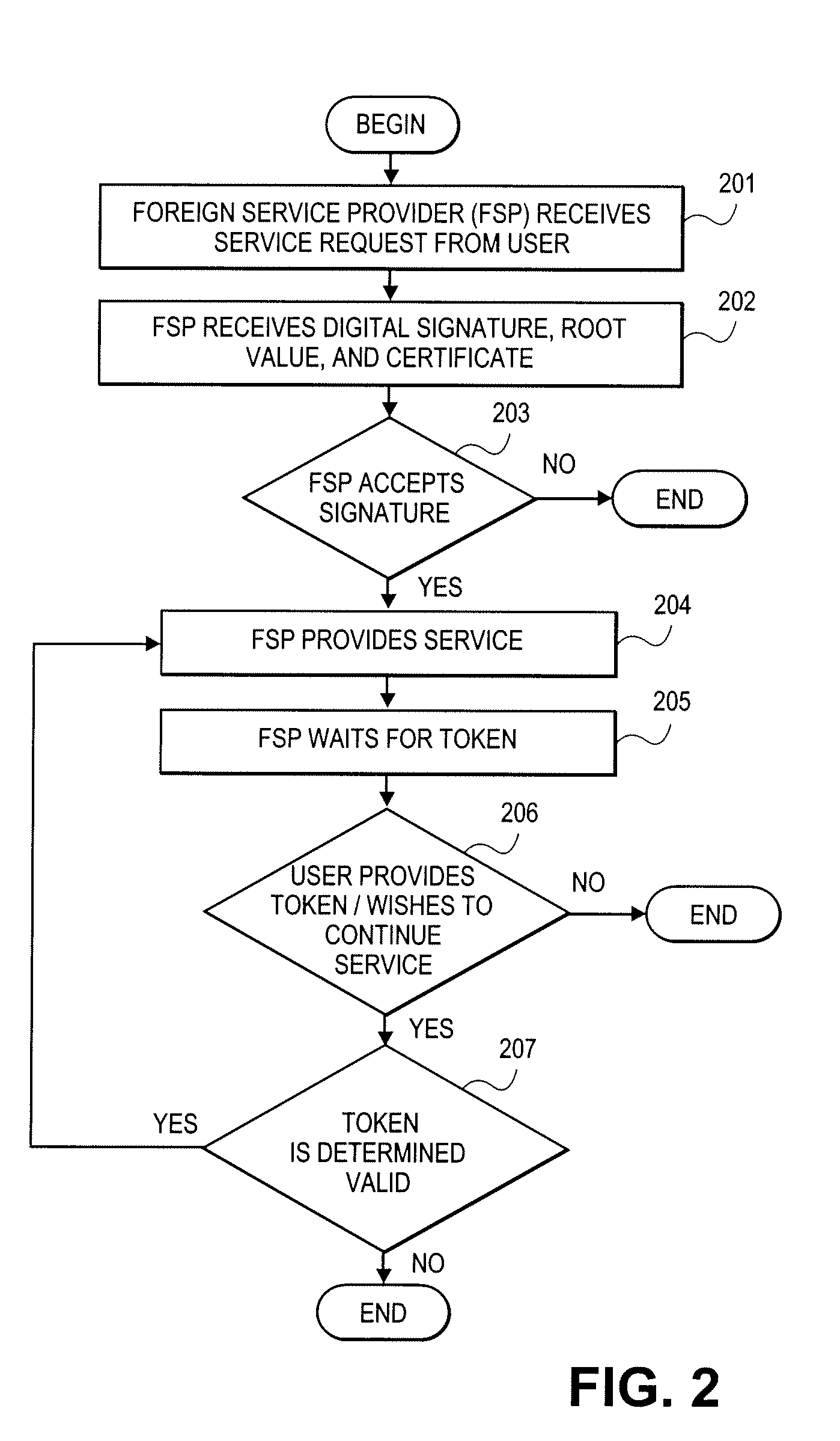
A method and apparatus for obtaining access to services of service providers. In one embodiment, the method comprises requesting a desired service through a foreign service provider. (101), generating a hash tree and generating a digital signature on a root value of the hash tree (102), sending the digital signature and the root value to the foreign service provider (103), providing one or more tokens to the foreign service provider with the next packet if the foreign service provider accepts the signature (105) and continuing to use the service while the foreign service provider accepts token (107).
Owner:NTT DOCOMO INC
Finding Read Disturbs on Non-Volatile Memories
ActiveUS20150262714A1Memory architecture accessing/allocationRead-only memoriesGranularityData access
In non-volatile memory devices, the accessing of data on word line can degrade the data quality on a neighboring word line, in what is called a read disturb. Techniques are presented for determining word lines likely to suffer read disturbs by use of a hash tree for tracking the number of reads. Read counters are maintained for memory units at a relatively coarse granularity, such as a die or block. When the counter for one of these units reaches a certain level, it is subdivided into sub-units, each with their own read counter, in a process that be repeated to determine frequently read word lines with a fine level of granularity while only using a relatively modest amount of RAM on the controller to store the counters.
Owner:SANDISK TECH LLC
Safety metadata management method based on integrality checking
InactiveCN101976322AGuaranteed confidentialityWarranty requirementsDigital data protectionSpecial data processing applicationsMetadata managementData management
The invention relates to a safety metadata management method based on integrality checking, belonging to the field of storage safety. The method is characterized in that a self encryption technology for file data is used at a client to encrypt the file data, thereby improving the storage efficiency; a 64-heap hash tree is used at a safety metadata management server end to maintain the hash value of a file block, thereby providing integrality protection on the hash value of the file data block and realizing the high-efficiency verification on the user's access to file and the high-efficiency data updating; and simultaneously a root hash virtual linked list technology is used, thereby ensuring the integrality of root hash values of multiple 64-heap hash trees belonging to one file and supporting the user's concurrent access to the file to a certain extent.
Owner:TSINGHUA UNIV
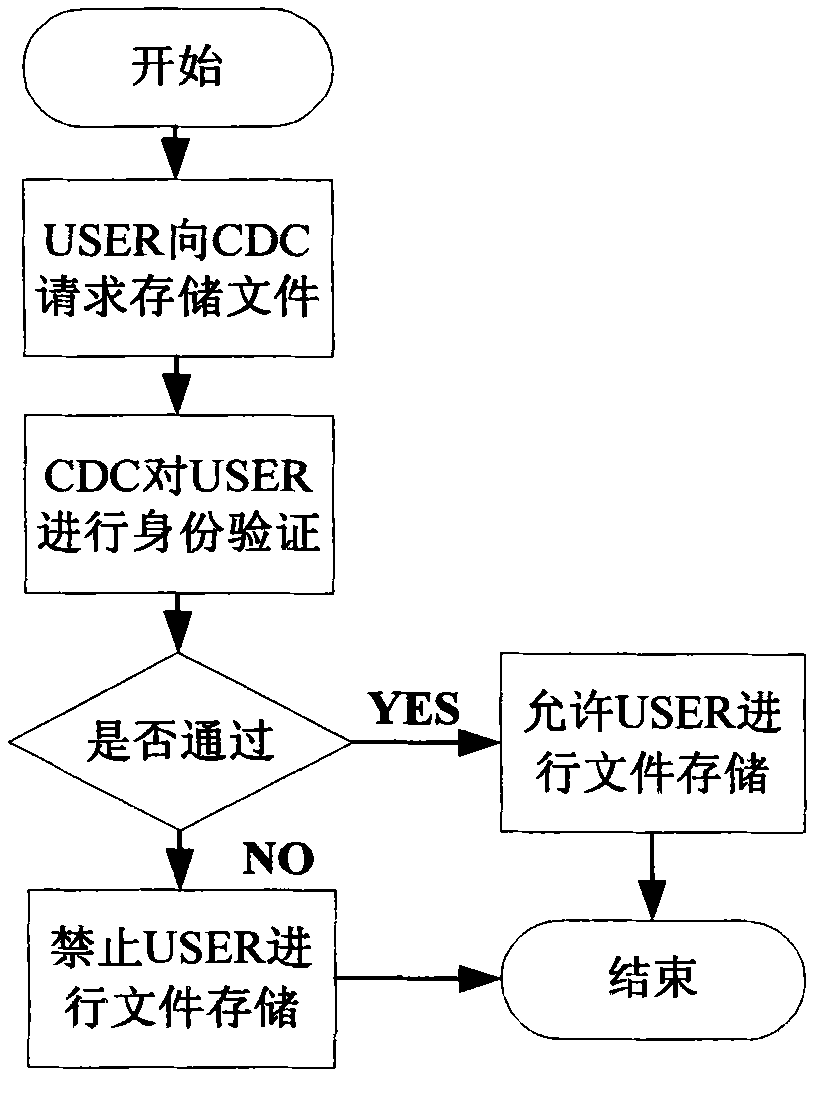
Hash tree-based data dynamic operation verifiability method
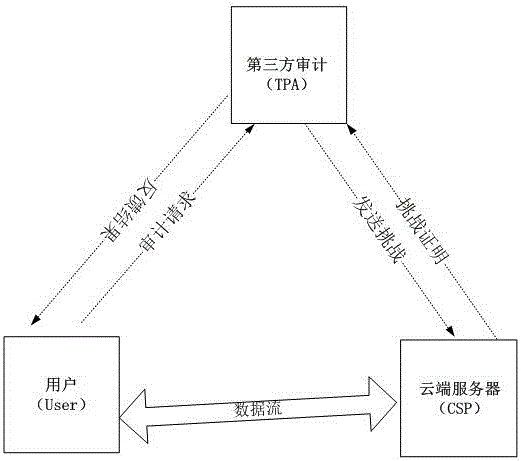
InactiveCN103218574AReliable communication channelShorten the timeDigital data protectionThird partyData file
The invention discloses a hash tree-based data dynamic operation verifiability method, which consists of three parts, i.e., a USER, a cloud data center (CDC) and a third party administrator (TPA) connected through a communication network, wherein the USER is used as a party of making a data memory service request, who hopes to store a data file owned by the party into a cloud storage space of the cloud data center, and can be both a personal user and an enterprise user; the CDC is used for responding to the data storage service request of the USER, storing the data file of the USER into the huge data center of the CDC according to a certain rule and managing and maintaining the data file; and the TPA is used as a reliable TPA and is commissioned by the USER to check the completeness and the consistency of the data file stored in the CDC data center. According to the hash tree-based data dynamic operation verifiability method, the verification problem of the completeness and the consistency of the user data file under a cloud computing environment is solved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
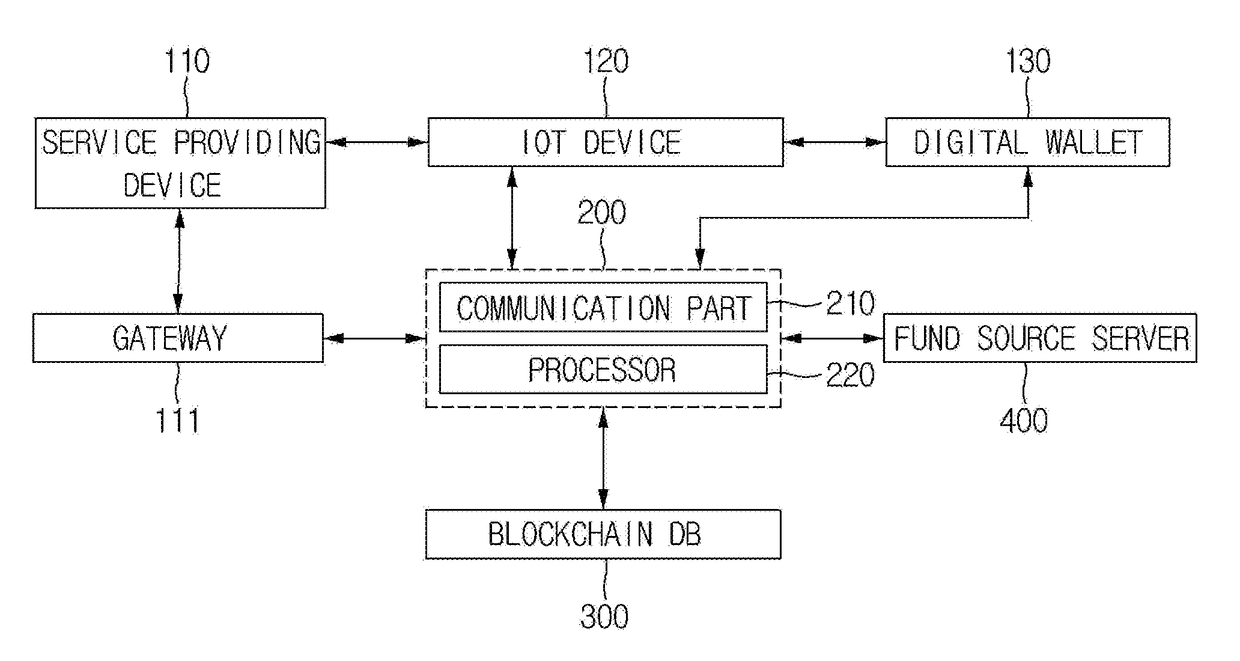
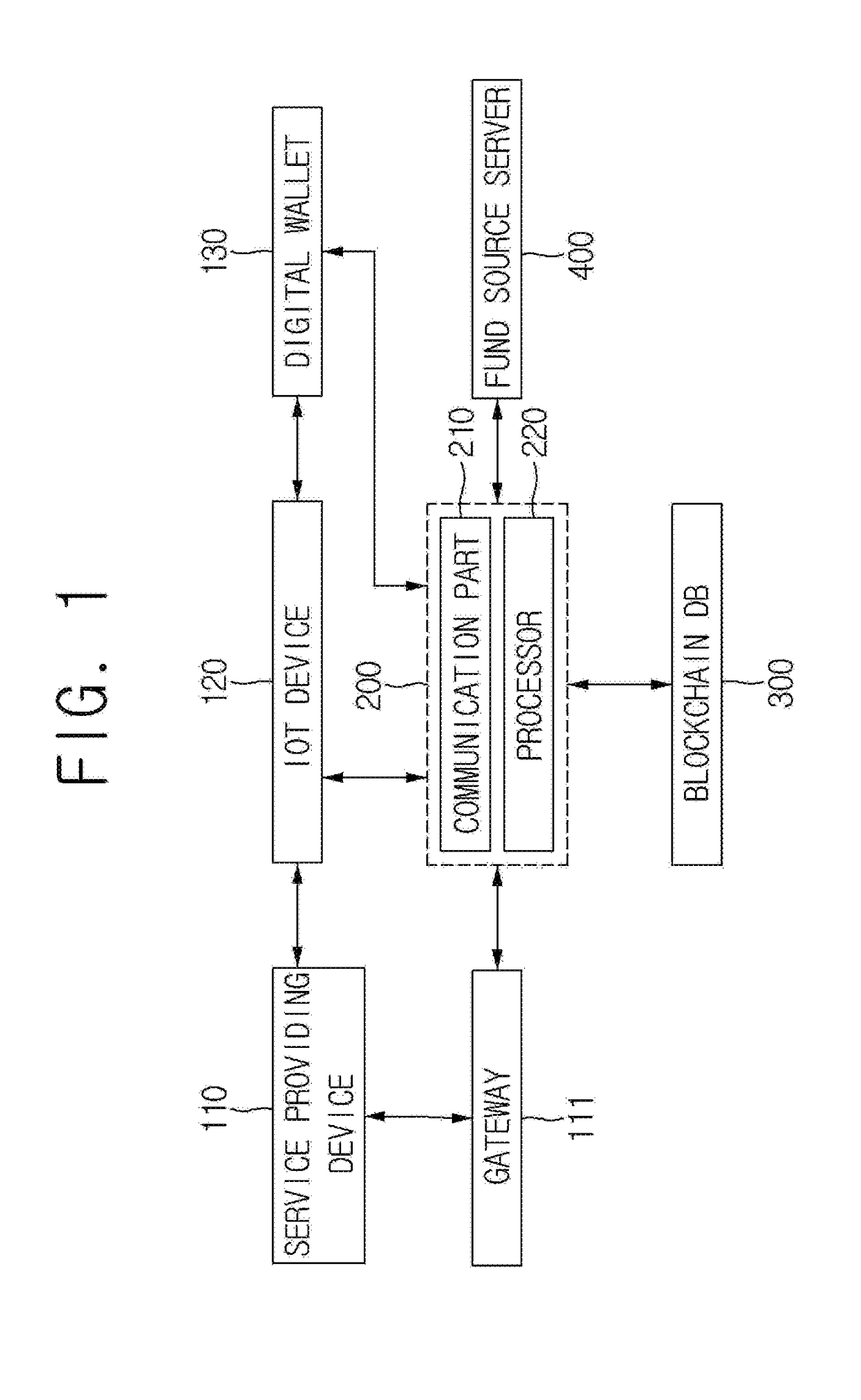
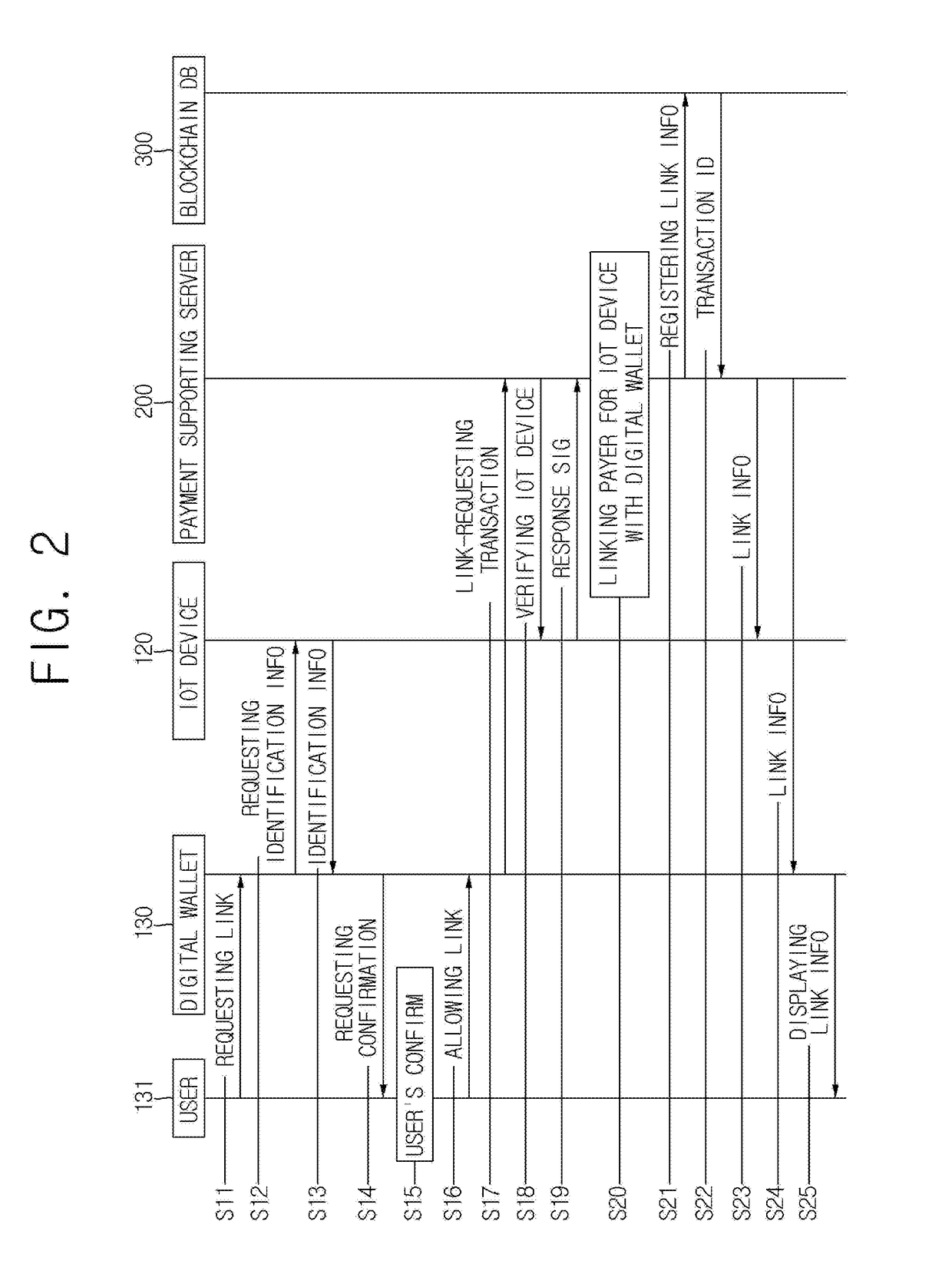
Method for paying cost of IoT device based on blockchain and merkle tree structure related thereto, and server, service providing terminal, and digital wallet using the same
ActiveUS20180330349A1Efficient managementEncryption apparatus with shift registers/memoriesCryptography processingPaymentStructure of Management Information
A method of a payment for an Internet of Things (IoT) device is provided. The method includes steps of: a payment supporting server (a) on condition that the payment supporting server has registered certificates of the IoT device, a service providing device, and a digital wallet in a first blockchain, manages their transaction IDs, has registered a representative hash value in a second blockchain, manages their transaction IDs, and manages link information between the IoT device and the digital wallet, confirming validity of a billing transaction, and (b) acquiring identification information on the digital wallet; and (c) paying the billing detail using the digital wallet, registering its payment result in the first blockchain, registering in the second blockchain, if one anchoring condition is satisfied, a first representative hash value, and transmitting the payment result to the service providing device, the IoT device, and the digital wallet.
Owner:COINPLUG LNC
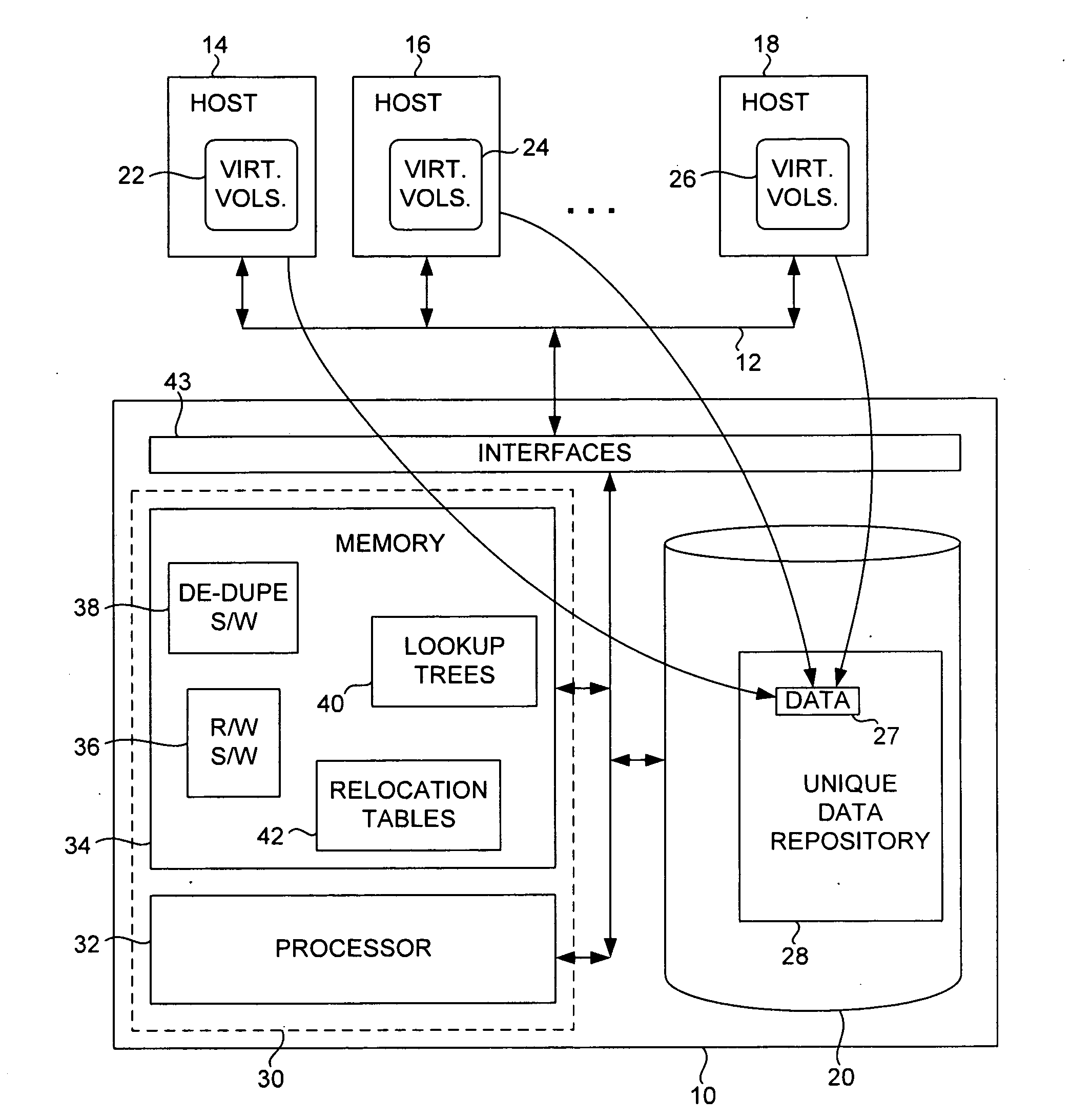
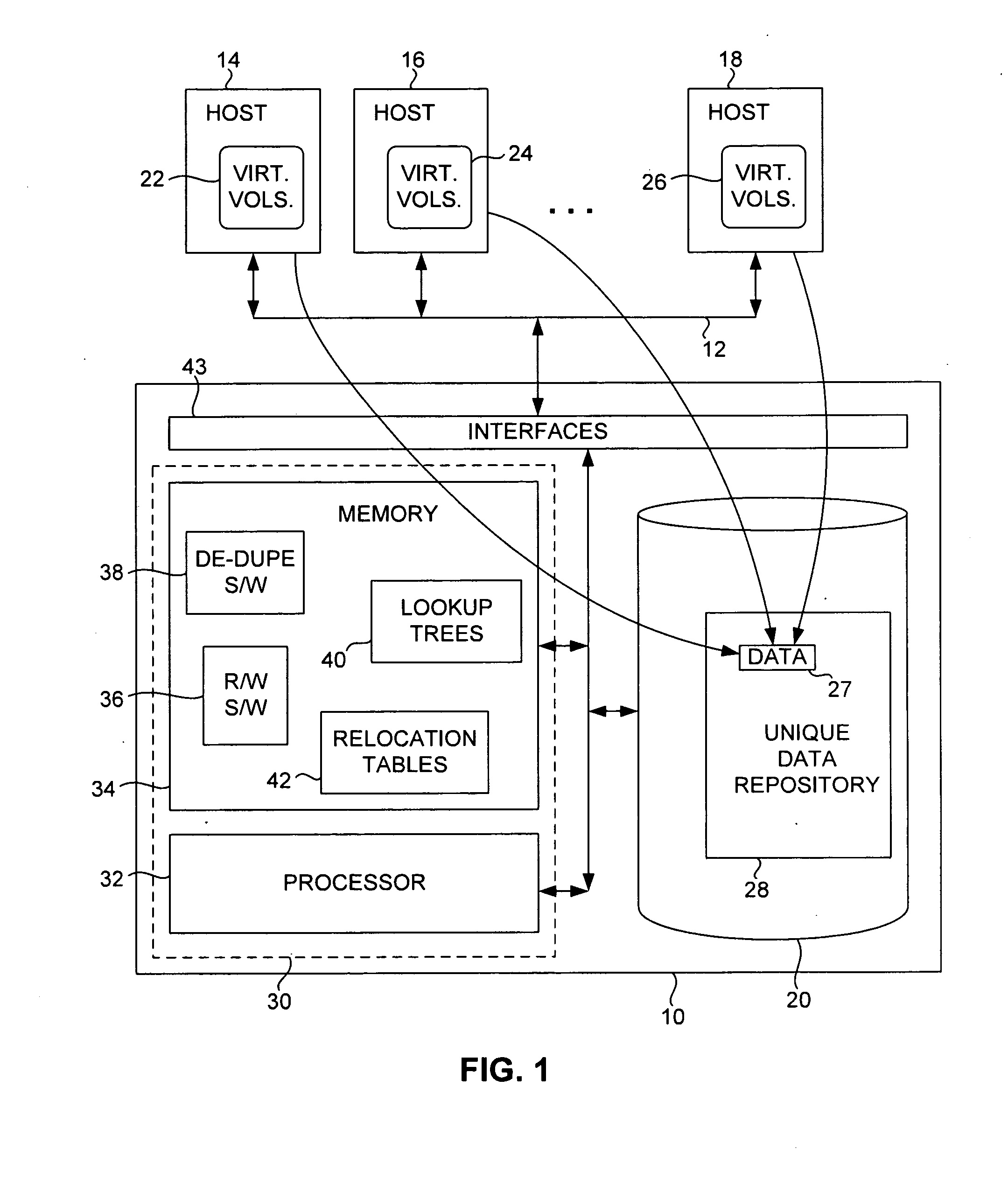
Block-level data de-duplication using thinly provisioned data storage volumes
InactiveUS20110016152A1Digital data processing detailsSpecial data processing applicationsData segmentData mining
Data segments are logically organized in groups in a data repository. Each segment is stored at an index in the data repository. In association with a write request, a hash algorithm is applied to the data segment to generate a group identifier. Each group is identifiable by a corresponding group identifier. The group identifier is applied to a hash tree to determine whether a corresponding group in the data repository exists. Each existing group in the data repository corresponds to a leaf of the hash tree. If no corresponding group exists in the data repository, the data segment is stored in a new group in the data repository. However, if a corresponding group exists, the group is further searched to determine if a data segment matching the data segment to be stored is already stored. The data segment can be stored in accordance with the results of the search.
Owner:AVAGO TECH INT SALES PTE LTD
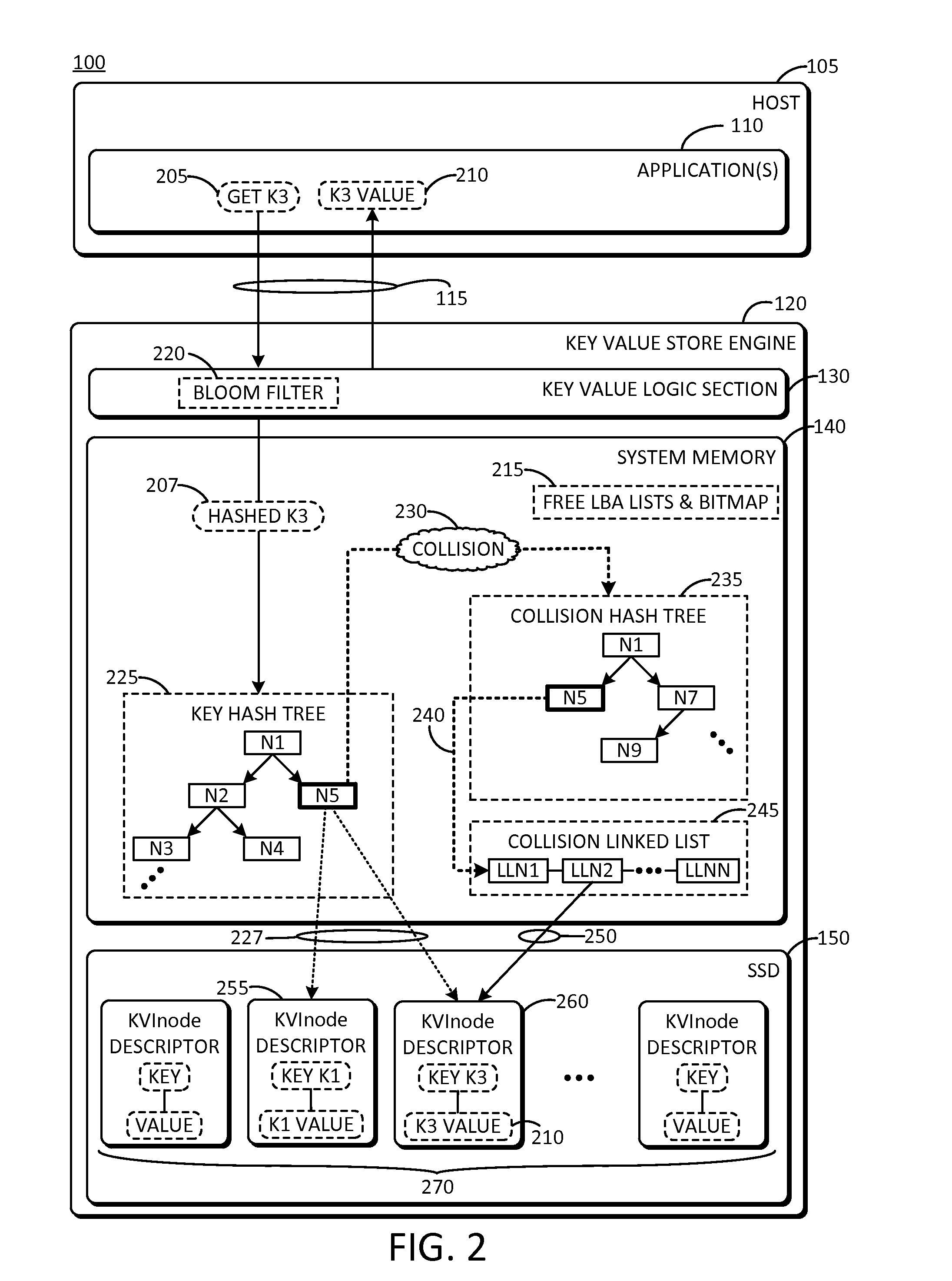
Efficient key collision handling
ActiveUS20160110292A1Efficient key collision handlingEasy to handleMemory architecture accessing/allocationMemory adressing/allocation/relocationTheoretical computer scienceLogical part
Inventive aspects include a key value store engine including non-volatile memory configured to store key-value inode descriptors each including a key and an associated value. The key value store engine can include a volatile memory to store a key hash tree and a collision hash tree. The key hash tree can include nodes each having a hash of one of the keys. The collision hash tree can include nodes each having a collided hash associated with two or more different keys. Each of the nodes of the key hash tree can include a collision flag indicating whether two or more different hashes correspond to a collided hash. The volatile memory can store a collision linked list including linked list nodes each having a key-value inode number indicating a location of a corresponding key-value inode descriptor stored in the non-volatile memory. The key value store engine can include a key value logic section.
Owner:SAMSUNG ELECTRONICS CO LTD
Blockchain-supported, hash tree-based digital signature infrastructure
InactiveUS20180152442A1User identity/authority verificationDigital data protectionDigital signatureTree (data structure)
Transformations of digital records are used as lowest level inputs to a tree data structure having nodes computed as digital combinations of child node values up to a current calendar value. Signature vectors are generated for each of the digital records and have parameters that enable recomputation of the respective current calendar. Recomputation yields the same calendar value only if a candidate digital record is an exact version of the original digital record included in the original computation of the value. Either the current calendar value, or a function of a plurality of calendar values over a period, is encoded in a transaction value that is stored in a block of a blockchain.
Owner:GUARDTIME SA
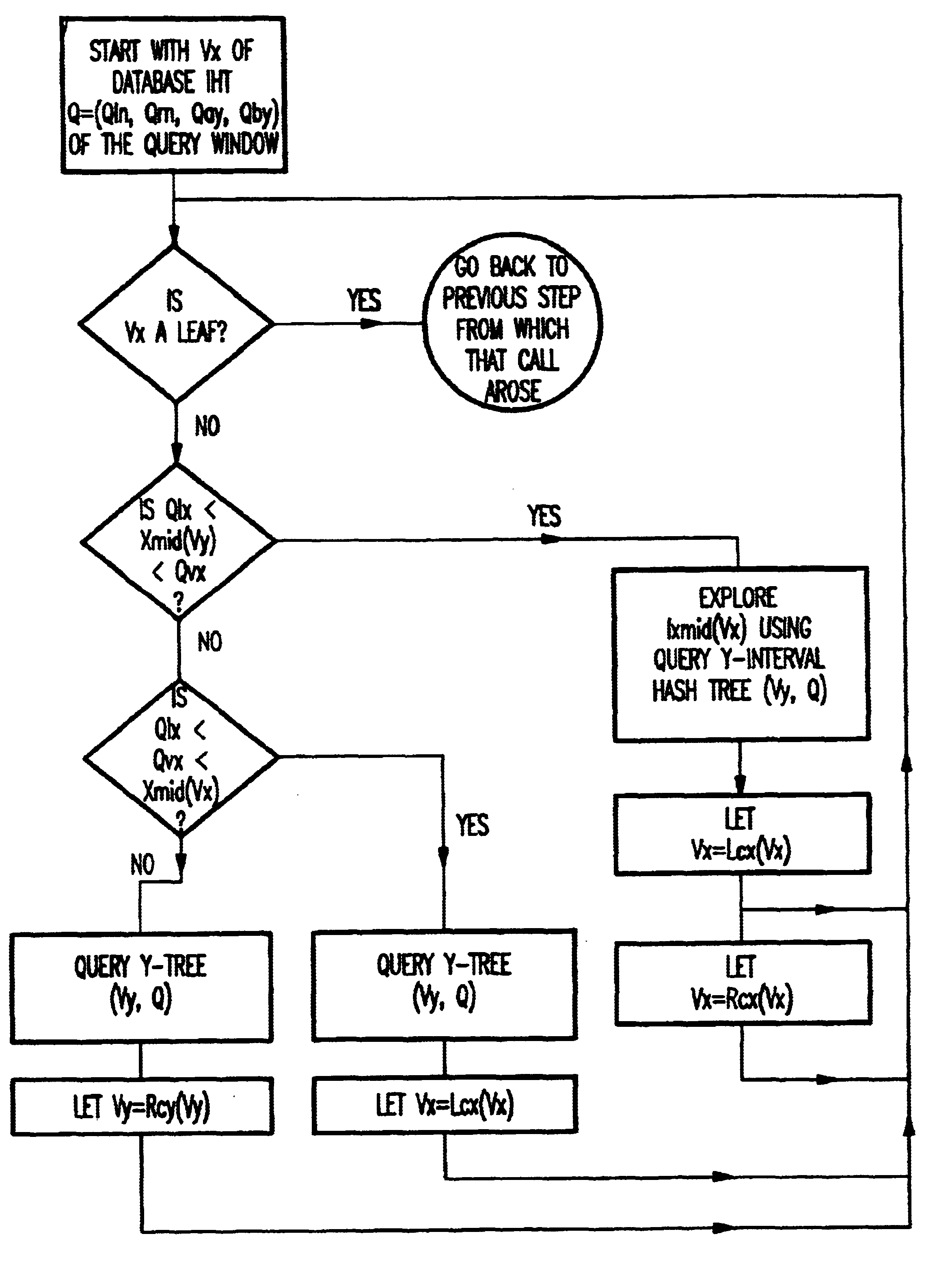
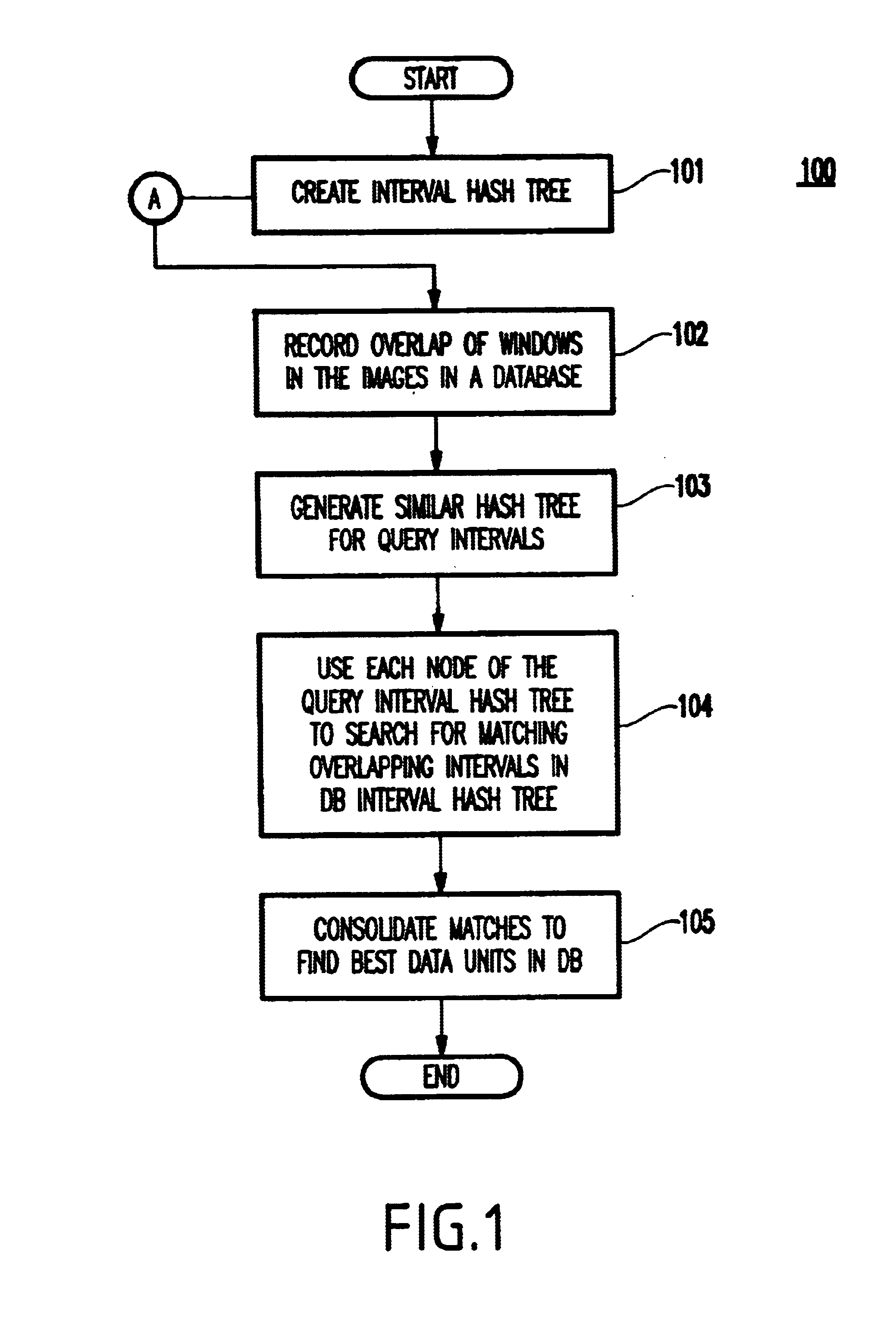
Method and apparatus for representing database and query information using interval hash tree
InactiveUS6757686B1Quick indexData processing applicationsStill image data indexingInterval treeData mining
A method and system for representing database and query information for multiple windows, includes defining an interval hash tree as a two-way interval tree, constructing a first interval hash tree for database windows, constructing a second interval hash tree for query windows, and matching the second and first interval hash trees node by node.
Owner:GOOGLE LLC
Dynamic verification method of cloud storage data using lattice-based linearly homomorphic signatures
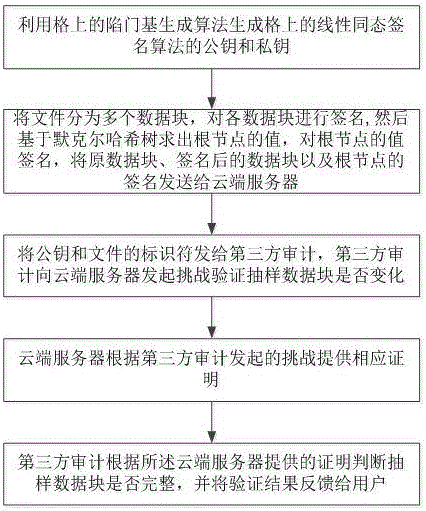
ActiveCN106301789AGuaranteed unforgeabilityImprove computing efficiencyKey distribution for secure communicationUser identity/authority verificationThird partyData integrity
The invention discloses a dynamic verification method of cloud storage data using lattice-based linearly homomorphic signatures. The method comprises data integrity verification including: a public key and a private key of a linearly homomorphic signature algorithm on a lattice are generated, a file is divided into a plurality of data blocks, each data block is signed, the value of a root node is calculated on the basis of a Merkle hash tree, the value of the root node is signed, and the data blocks, signatures of the data blocks and a signature of the root node are sent to a cloud server; IDs of the public key and the file are provided for a third-party audit, which initiates a challenge to the cloud server to verify whether the data blocks changed or not; the cloud server provides corresponding proof for the challenge initiated by the third-party audit; and the third-party audit judges whether the data blocks are complete according to the proof provided by the cloud server and feeds a verification result to a user. The method can resist quantum attacks initiated by quantum computers in the future and support cloud dynamic operation verification while protecting user private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method and system for auditing Merkle Hash tree cloud data integrity
InactiveCN106845280AGuaranteed real-timeEnsure safetyDigital data protectionTransmissionThird partyData integrity
An embodiment of the invention discloses a method and a system for auditing Merkle Hash tree cloud data integrity. According to the method and the system, the utilization rate of a node is increased by storing data block information on the node; length of an authentication path is reduced by adopting a local authoritative root node, and computation cost of a third-party auditing side and a user side is reduced; all that is needed for the third-party auditing side is to calculate a Hash value of the local authoritative root node according to a Hash value of a node in a possession certificate returned by a cloud storage server and sign the Hash value of the local authoritative root node with a secrete key to obtain local authoritative root node signature, the third-party auditing side can compare and verify the obtained local authoritative root node signature with local authoritative root node signature returned by the cloud storage server, calculation for obtaining unique root node signature for integrity verification is not required, so that integrity auditing efficiency of the third-party auditing side and the user side is greatly improved, and freshness of node information is maintained by adding vision ID to the node.
Owner:GUANGDONG UNIV OF TECH
Technique for finding rest resources using an n-ary tree structure navigated using a collision free progressive hash
InactiveUS20090164485A1Easy to adaptBroaden applicationDigital data information retrievalData processing applicationsRepresentational state transferPattern matching
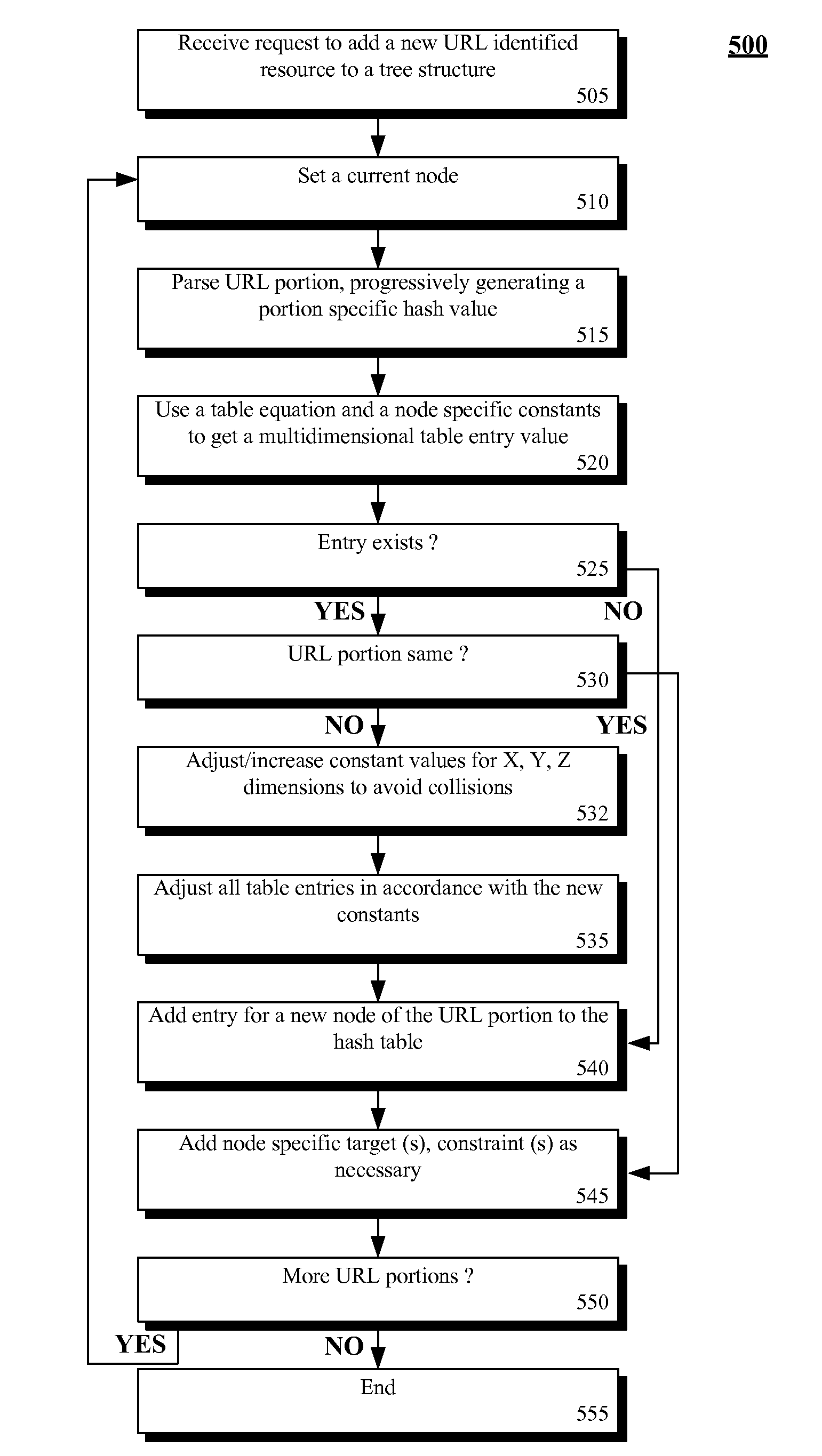
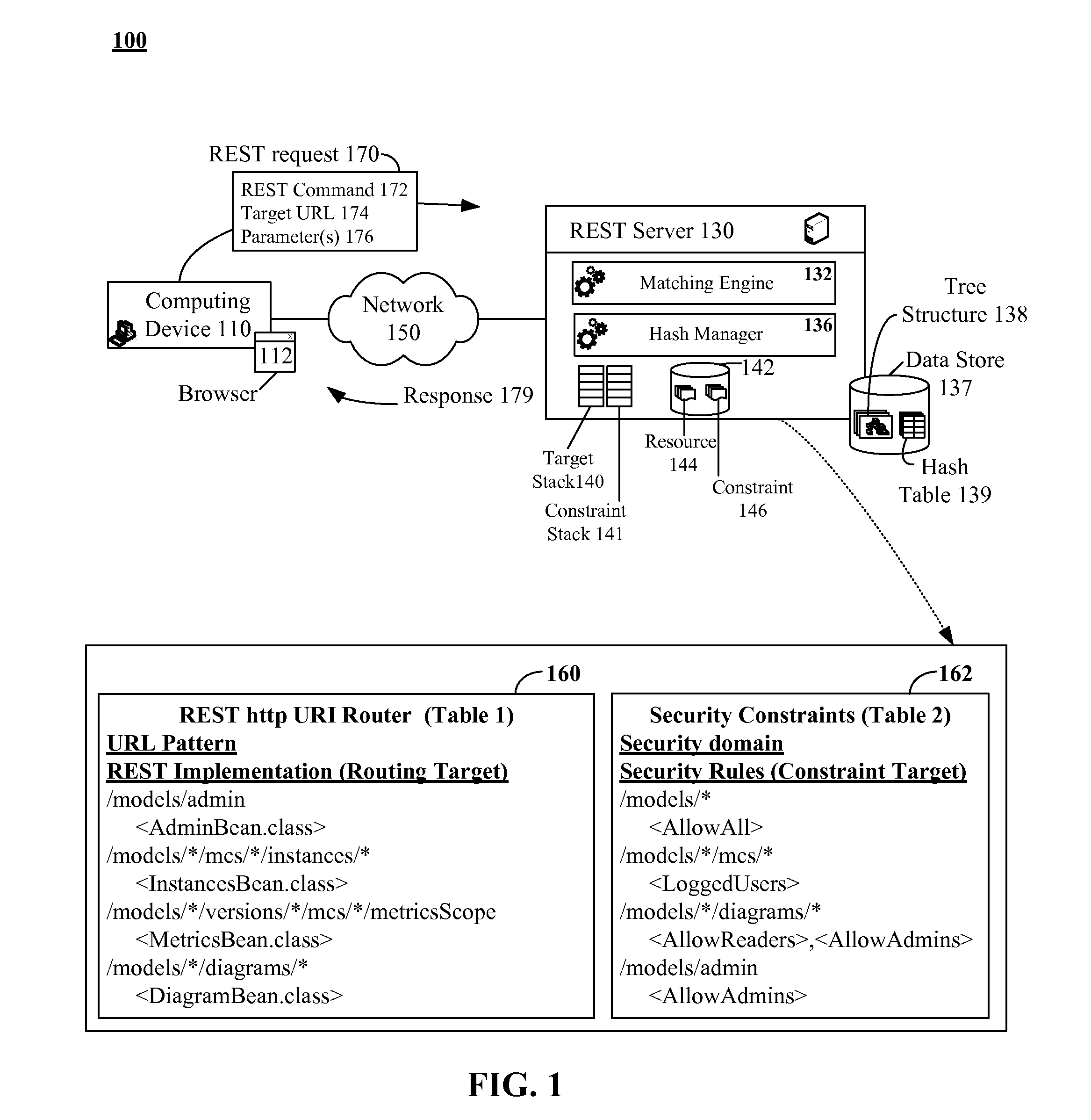
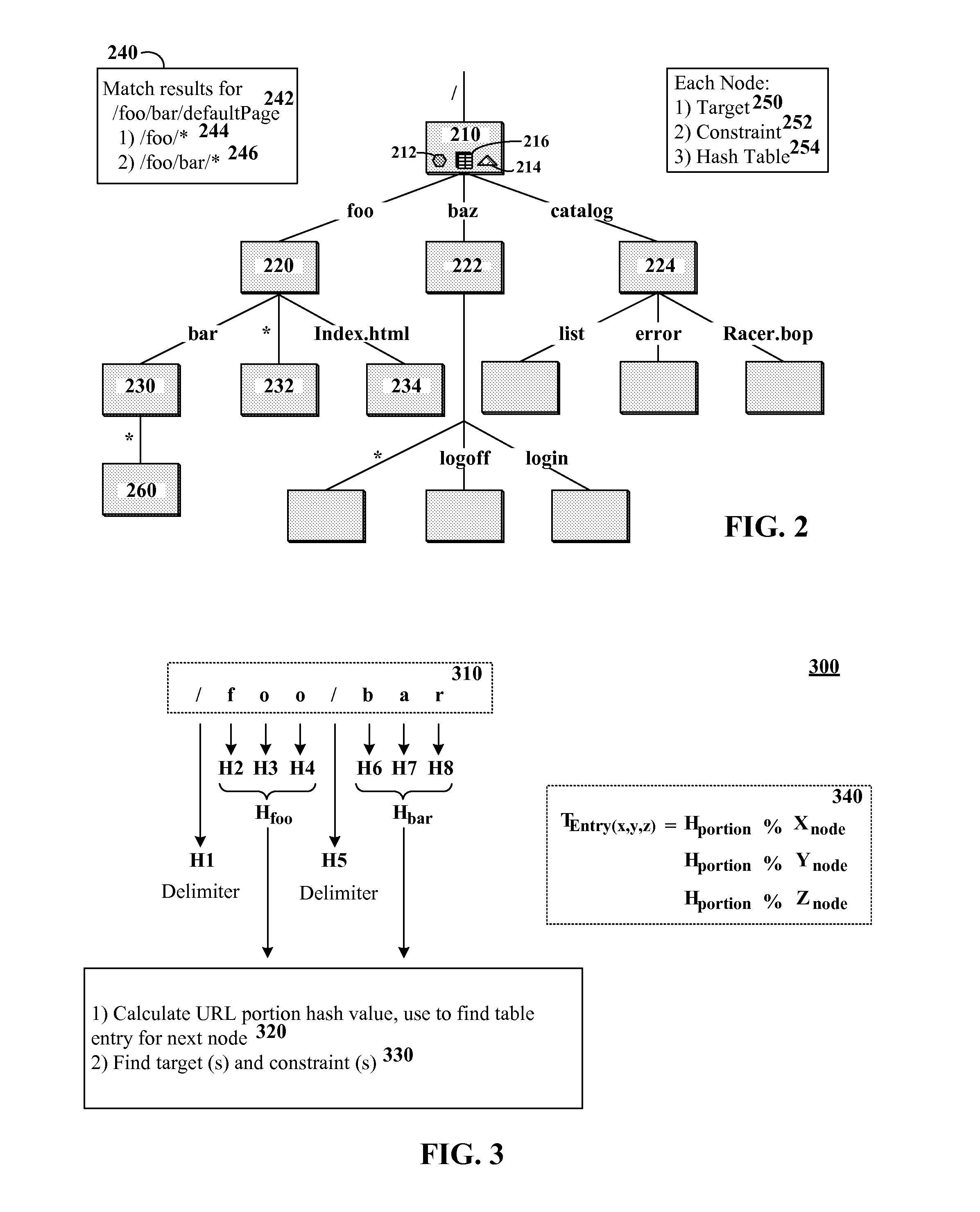
The present invention discloses a data structure which, given an identifier for a Representational State Transfer (REST) resource, can rapidly yield a configured target and simultaneously yield all configured pattern based rules and constraints for the target. The disclosed data structure is a tree structure including nodes for URL portions. Each node is associated with a hash tree specifically grown in a manner that ensures collision occurrences are non-existent. The tree structure is effectively two or more superimposed trees; one for URL pattern matching to determine a target, another for determining constraints. A single tree traversal, which can be based on a progressive hash, can be used to concurrently determine a target and a set of constraints, which represents improved performance over conventional implementations that require multiple, distinct query / response operations to produce equivalent results.
Owner:LINKEDIN
Cloud platform trusted log auditing method for privacy protection based on trusted third party
ActiveCN108322306ARealize the collectionGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationThird partyCloud user
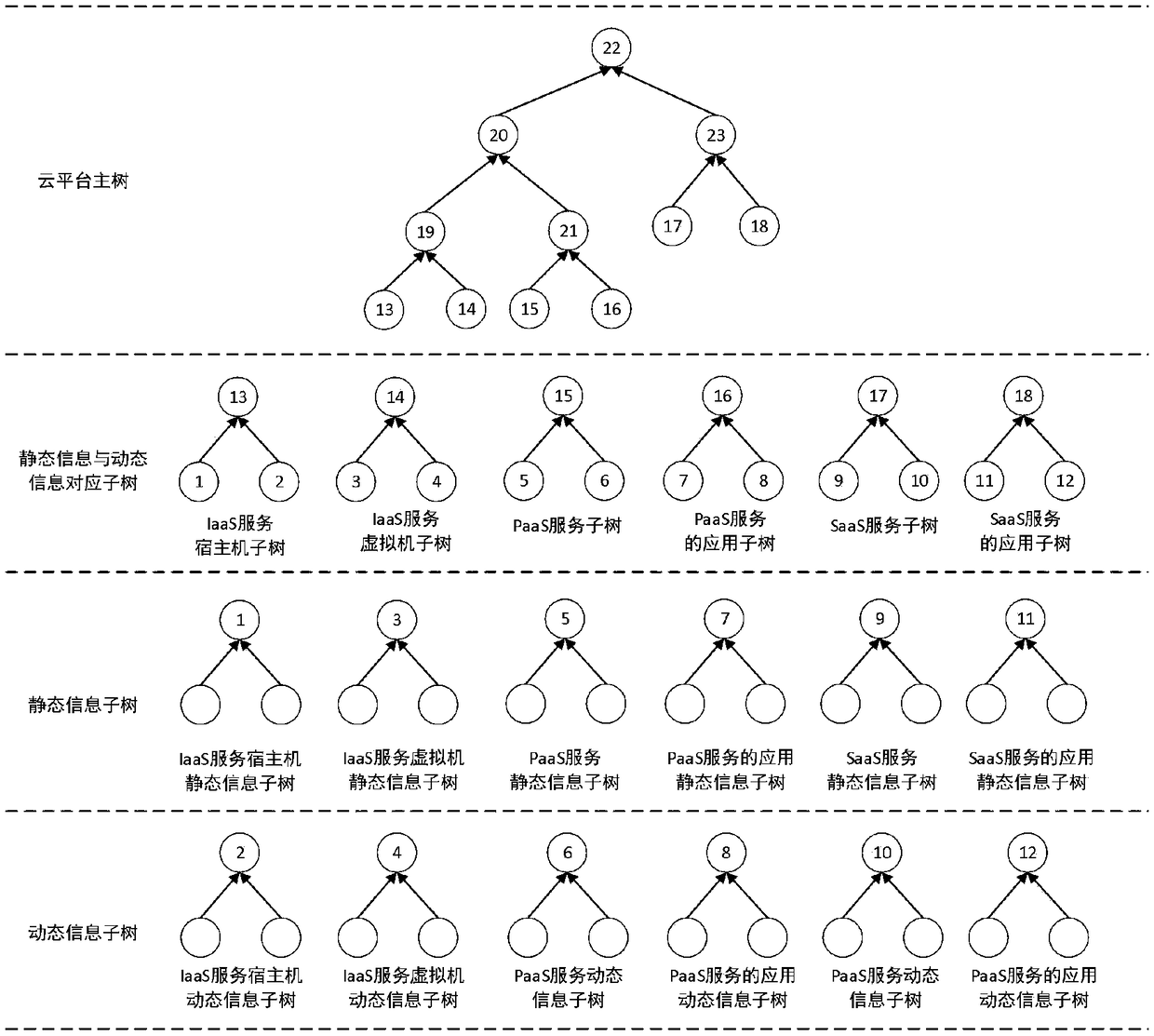
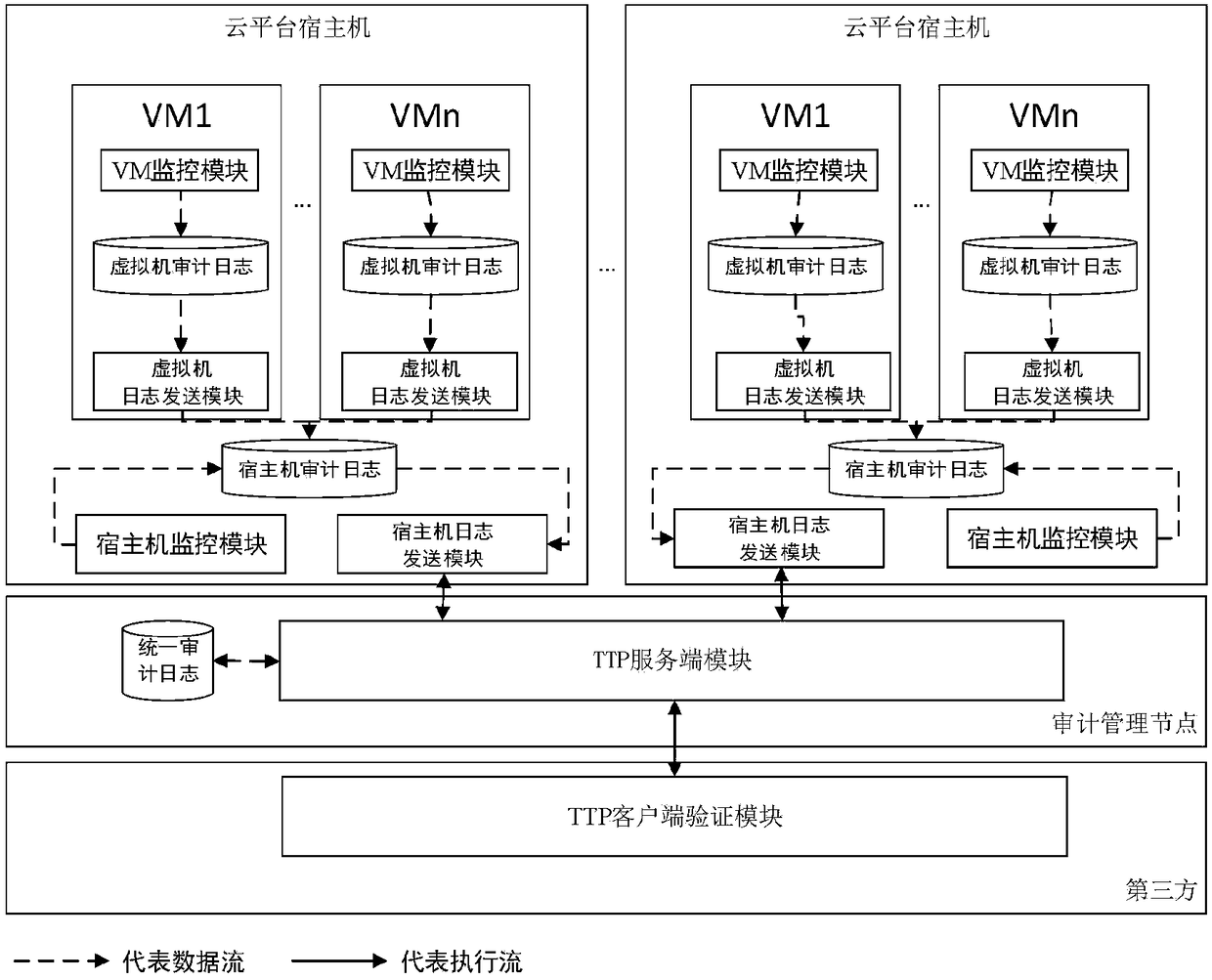
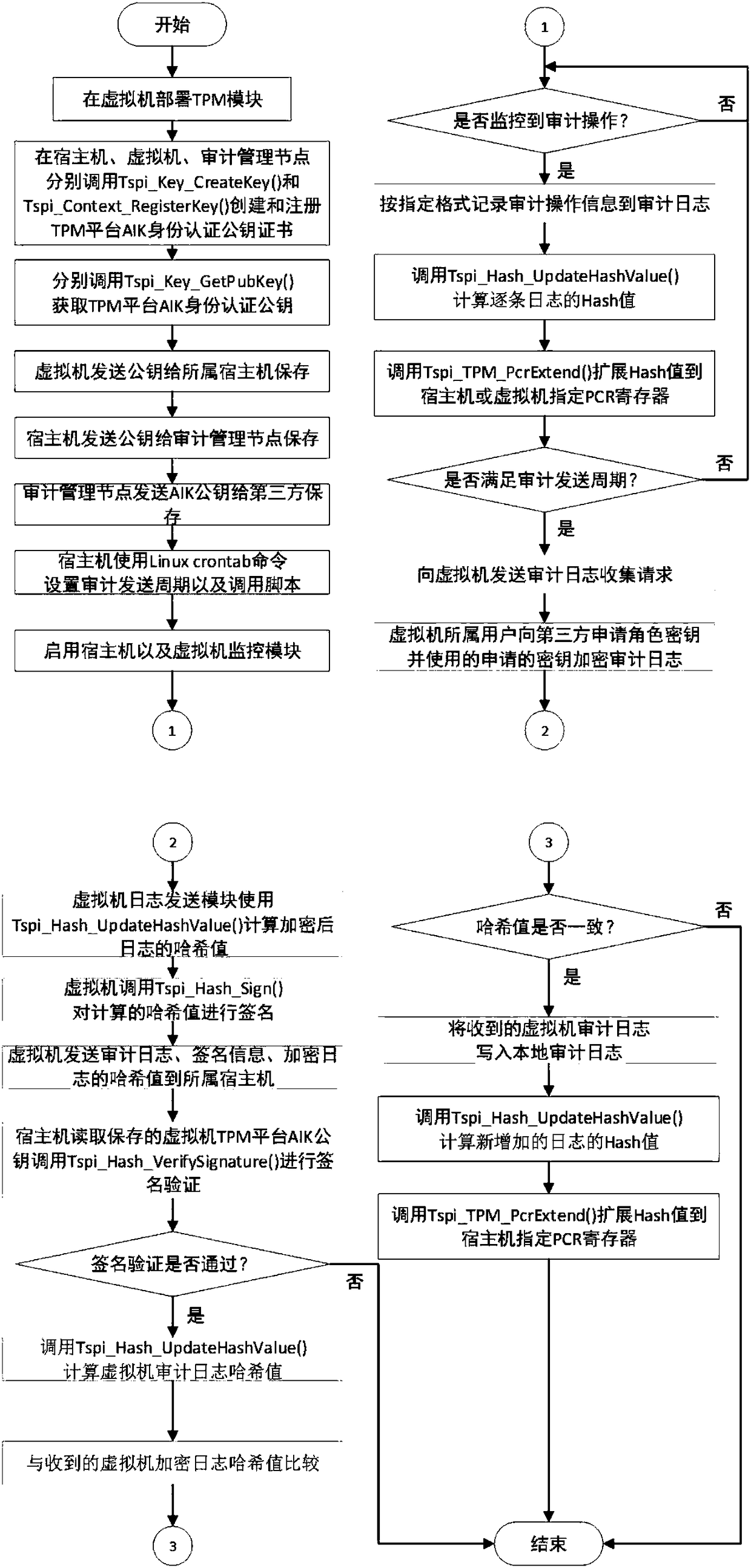
The invention discloses a cloud platform trusted log auditing method for privacy protection based on a trusted third party, and belongs to the field of cloud computing. The method comprises the following steps: step 1: collecting a cloud platform auditing log; step 2: securely transmitting the auditing log; step 3: generating and publishing a verification data structure of a third party auditing log; and step 4 verifying the auditing logs of a cloud service provider and the cloud user. Auditing responsibility association objects are added in the auditing events of different cloud service modes(IaaS, PaaS, SaaS), reliable collection and transmission of the auditing logs are provided based on trusted hardware, auditing log verification supporting privacy protection is provided based on a hierarchical random Merkle hash tree, and the cloud auditing responsibility chasing of cloud service providers and cloud users is supported.
Owner:BEIJING UNIV OF TECH
Data range-based method for synchronizing data in database
ActiveCN102054035ASolve the problem of content synchronization and achieve final consistencySpecial data processing applicationsData segmentData storing
The invention relates to a data range-based method for synchronizing data in a database. The method comprises the following steps of: segmenting the data stored in the database; determining a data segment with changed content; and updating the original content of the data segment. In the data range-based method for synchronizing data in database, provided in the invention, the data are segmented and then calculated by utilizing a Merkle Tree algorithm, compared and restored; the contents are synchronized among different data storage nodes in a large distributed data storage system to achieve the final data consistency.
Owner:BORQS BEIJING +2
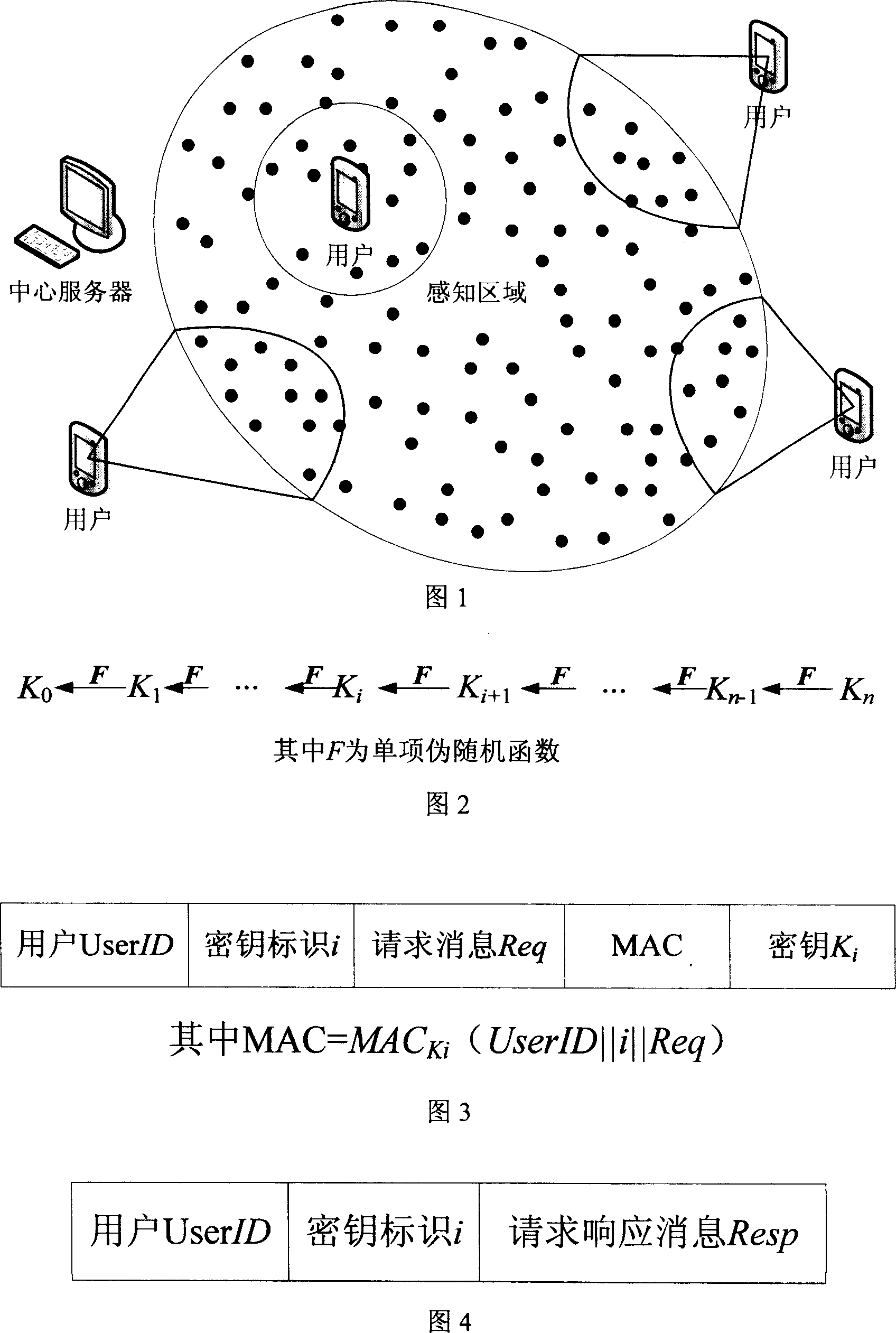
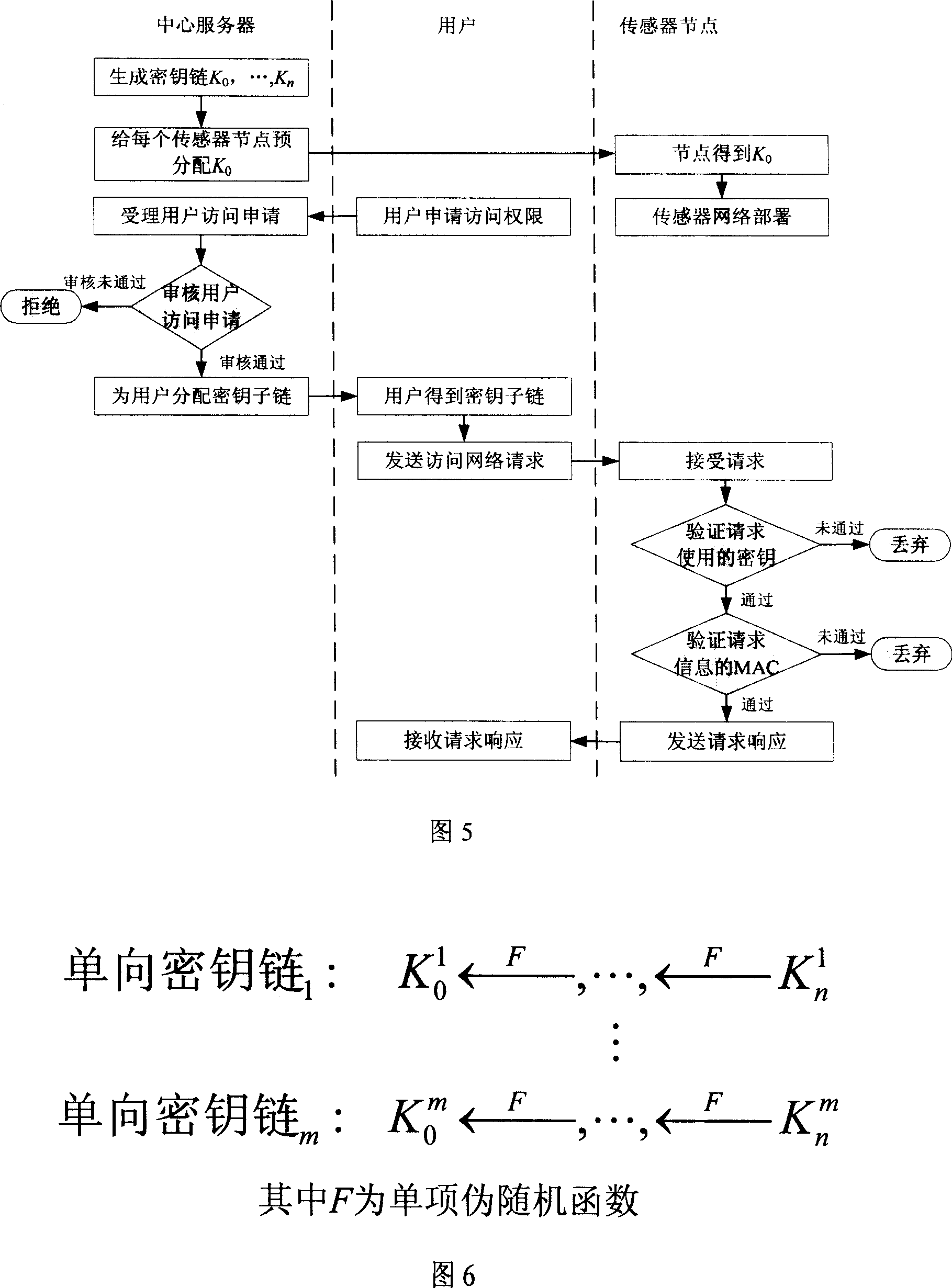
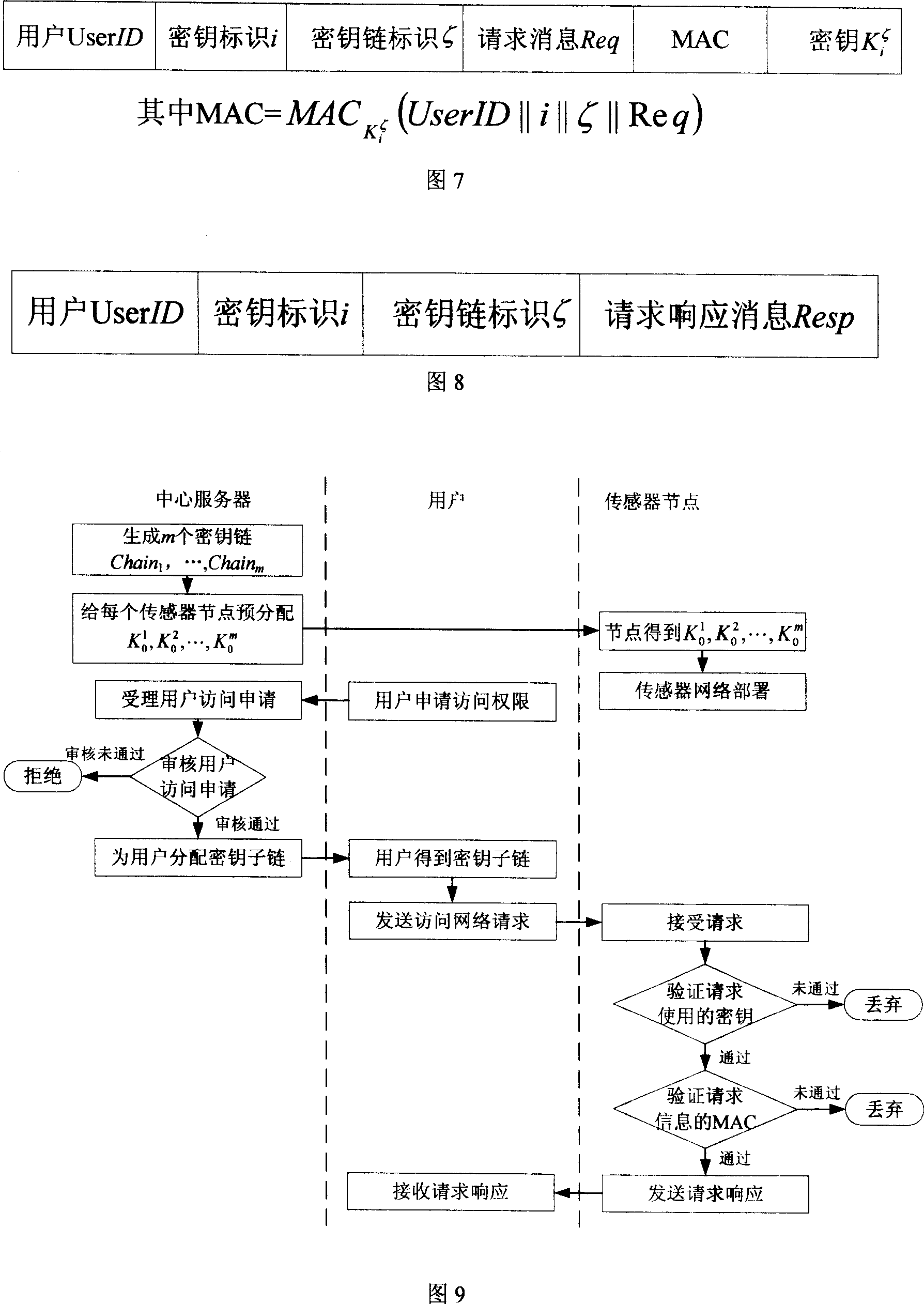
Radio sensor access control method based on key chain
InactiveCN101005459AImplement access controlReduce computational overheadKey distribution for secure communicationUser identity/authority verificationLine sensorExtensibility
The invention is based on five highly-effective sensor network access control modes: which are one-way key chain access control, multi key chain access control, Merkle tree-based access control, expanded Merkle tree access control, and an mode of canceling the key chain of captured users with Merkle. The method uses said five access control modes to reduce the storage expense of sensor node and increase the flexibility and expandability of access control so as to support mass users to access network. The invention is compatible with current sensor network data broadcast protocol.
Owner:XIDIAN UNIV
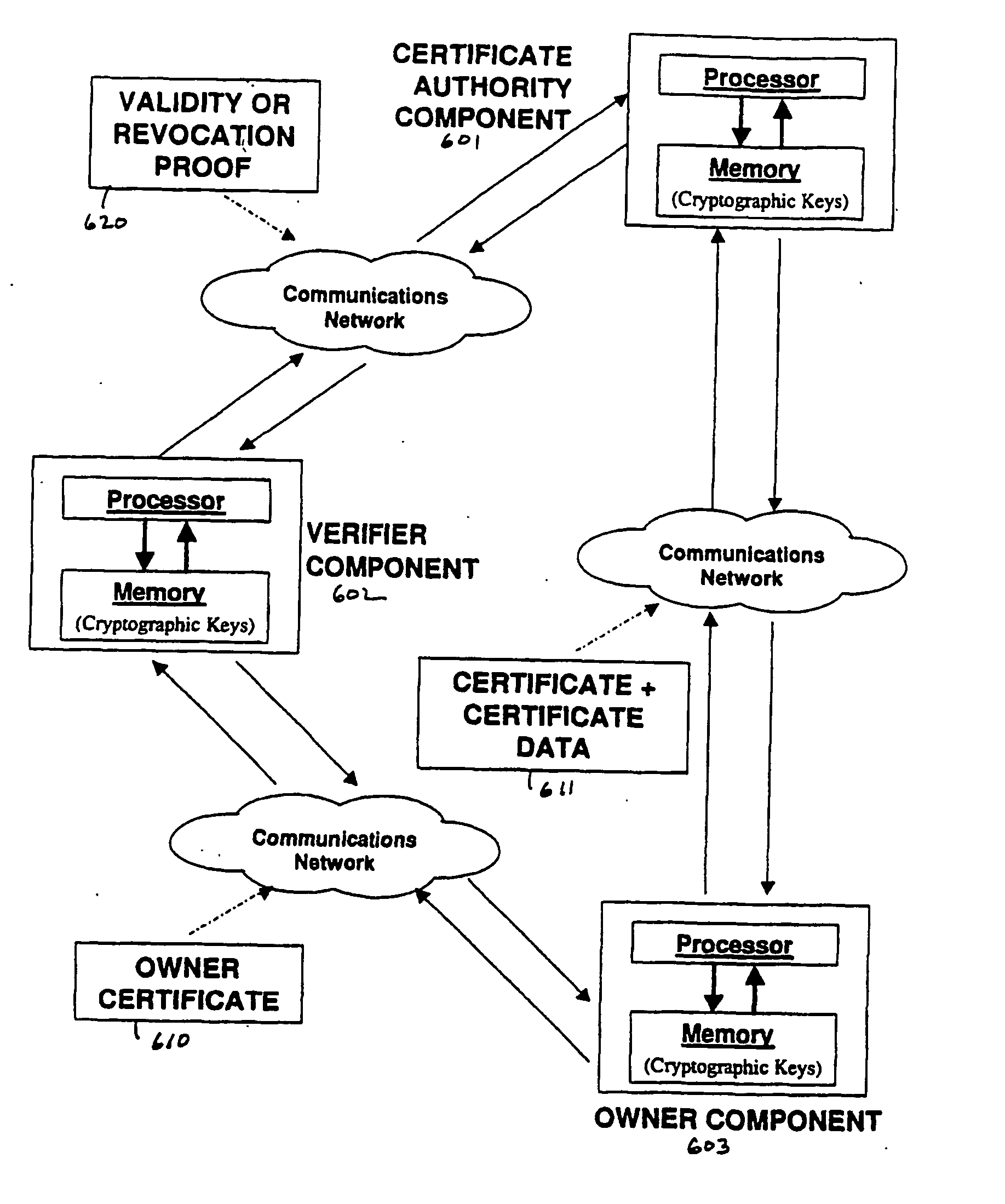
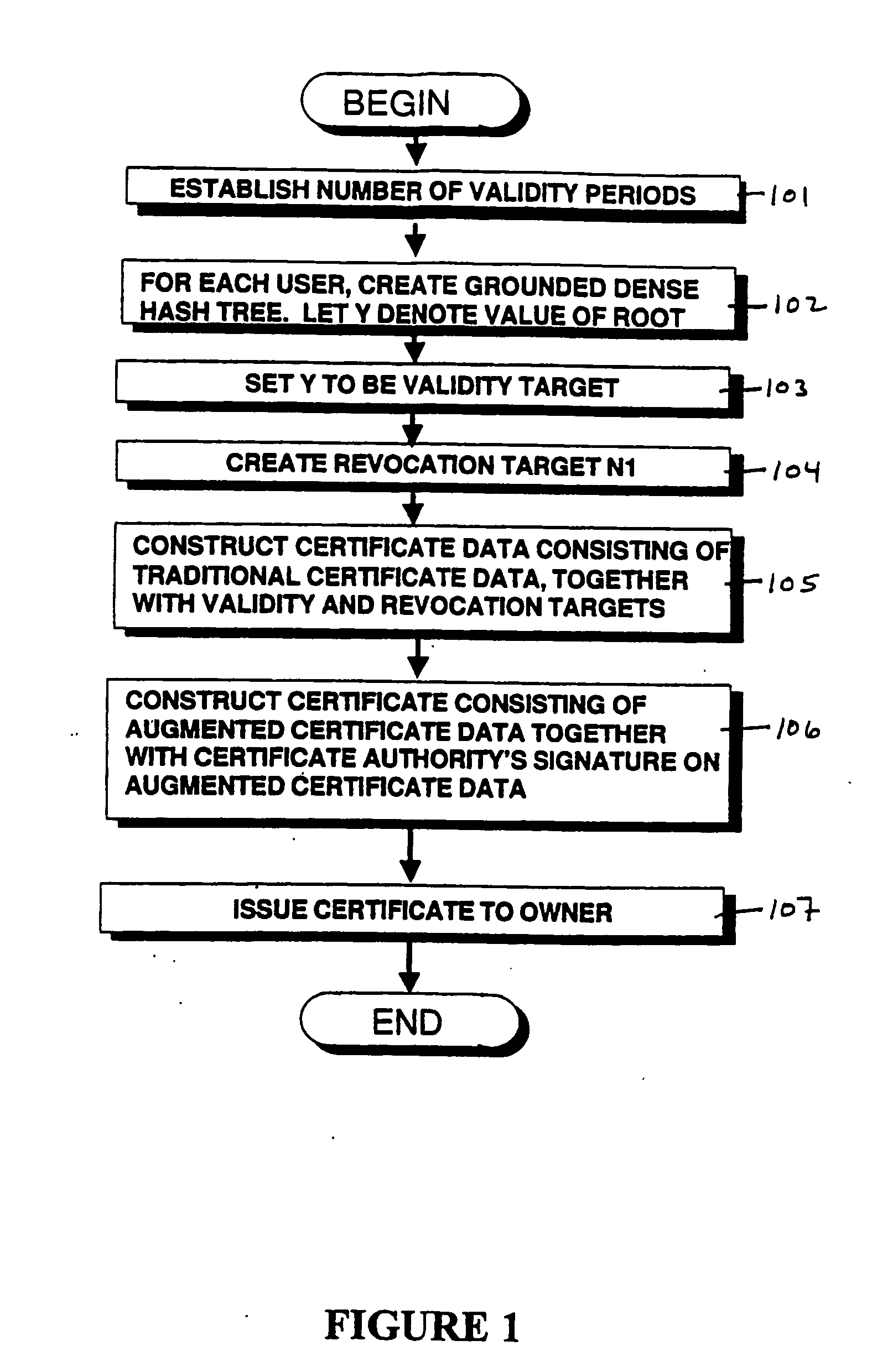
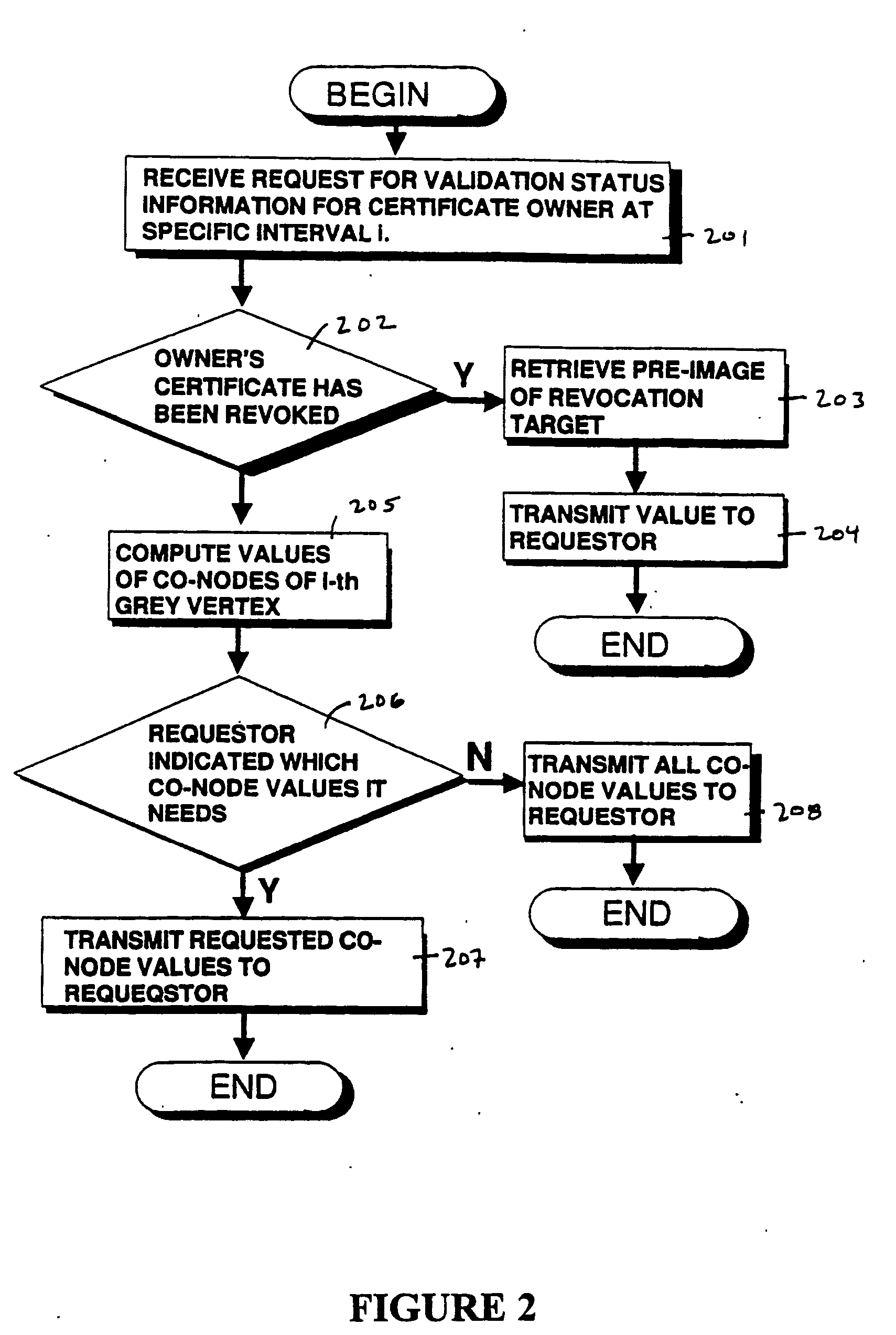
Method and apparatus for efficient certificate revocation
ActiveUS20060129803A1Digital data processing detailsUser identity/authority verificationMerkle treeRevocation
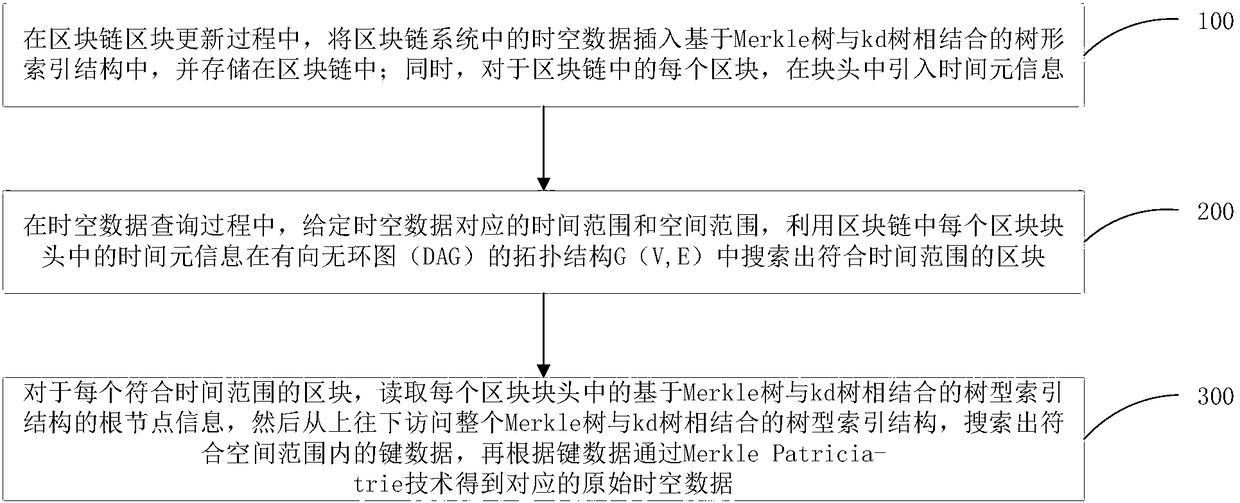
Revocation of digital certificates in a public-key infrastructure is disclosed, particularly in the case when a certificate might need to be revoked prior to its expirations. For example, if an employee was terminated or switched roles, his current certificate should no longer be valid. Accordingly, novel methods, components and systems are presented for addressing this problem. A solution set forth herein is based on the construction of grounded dense hash trees. In addition, the grounded dense hash tree approach also provides a time-communication tradeoff compared to the basic chain-based version of NOVOMODO, and this tradeoff yields a direct improvement in computation time in practical situations.
Owner:NTT DOCOMO INC
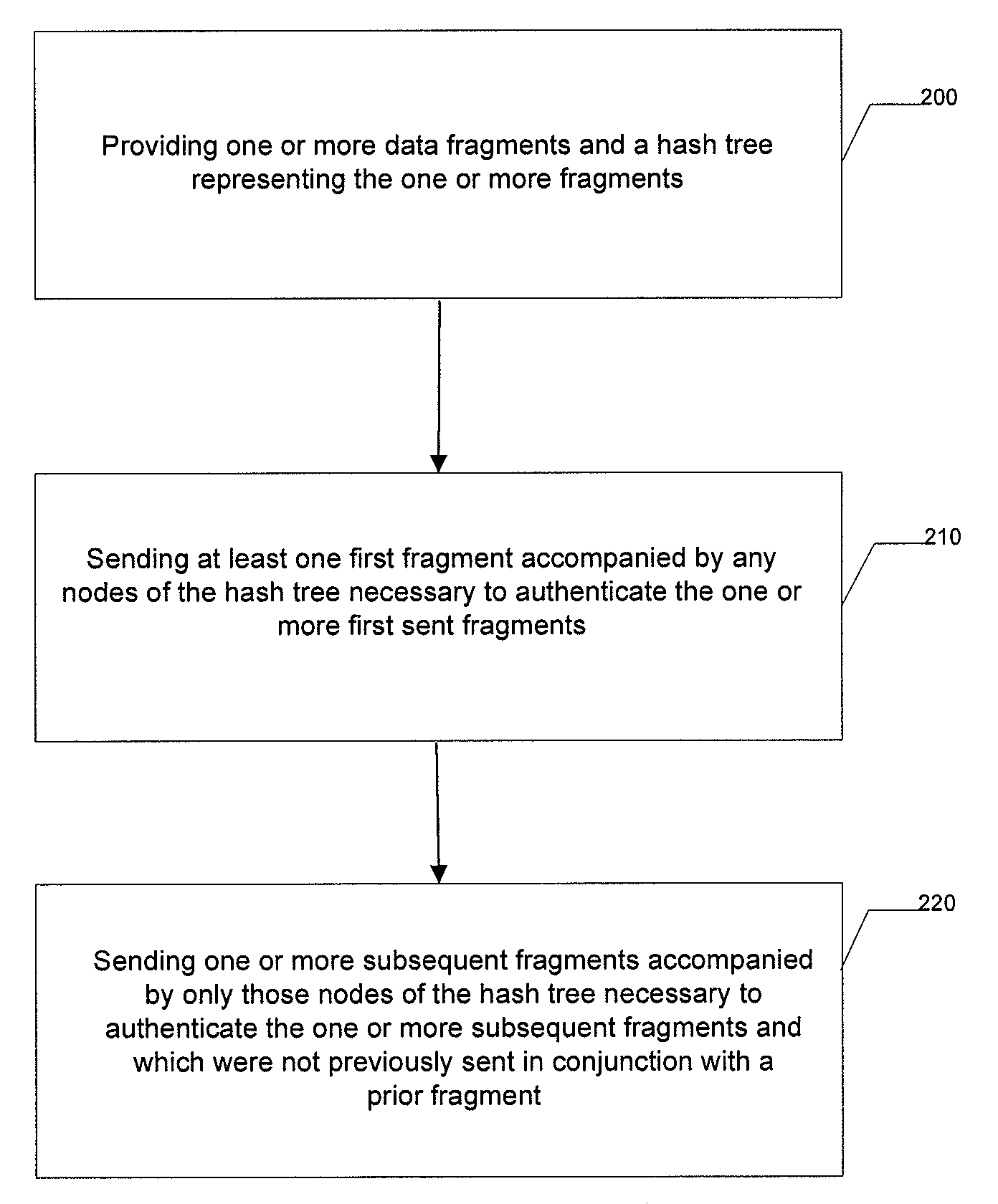
Methods, apparatuses, and computer program products for authentication of fragments using hash trees
InactiveUS20090164783A1Improve efficiencyImprove reliabilityDigital data processing detailsUser identity/authority verificationMerkle treeAuthentication
An apparatus for authentication of fragments using hash trees may include a processor. The processor may be configured to provide one or more data fragments and a hash tree representing the one or more fragments, send at least one first fragment accompanied by any nodes of the hash tree necessary to authenticate the one or more first sent fragments, and send one or more subsequent fragments accompanied by only some, but not all, of the nodes of the hash tree necessary to authenticate the one or more subsequent fragments with the other nodes that are not sent but are necessary for authentication having been previously sent in conjunction with a prior fragment.
Owner:NOKIA CORP
Data integrity verification method suitable for embedded processor
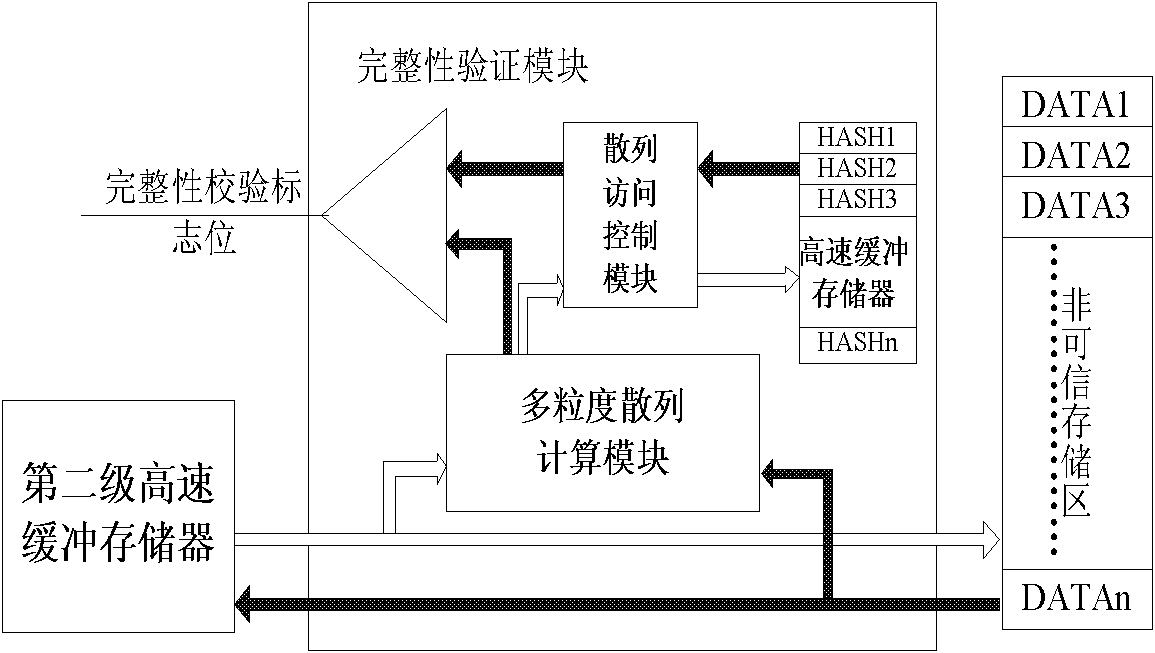
InactiveCN101853190AImprove hit rateImprove verification effectError detection/correctionCountermeasureData integrity
The invention discloses a data integrity verification method suitable for an embedded processor. The method comprises a multi-granularity hash computation method, an address conversion method and a hash node access control method, wherein the multi-granularity hash computation method is used for generating a multi-granularity Merkle tree which is cached in a hash cache and is in charge of computing a hash value of a data block in a memory when nodes of the tree are absent; the address conversion method is used for providing a unique corresponding address for each node; and the hash node access control method is mainly in charge of accessing the nodes of each hash tree and adopting different strategies particularly during reading absence and writing operation. Due to the multi-granularity hash computation method, the hash tree generated by the data integrity verification method has less nodes and layers so as to reduce a memory space and hardware area overhead, shorten initialization time and improve the performance.
Owner:HUAZHONG UNIV OF SCI & TECH
Storage system and method for updating a hash tree
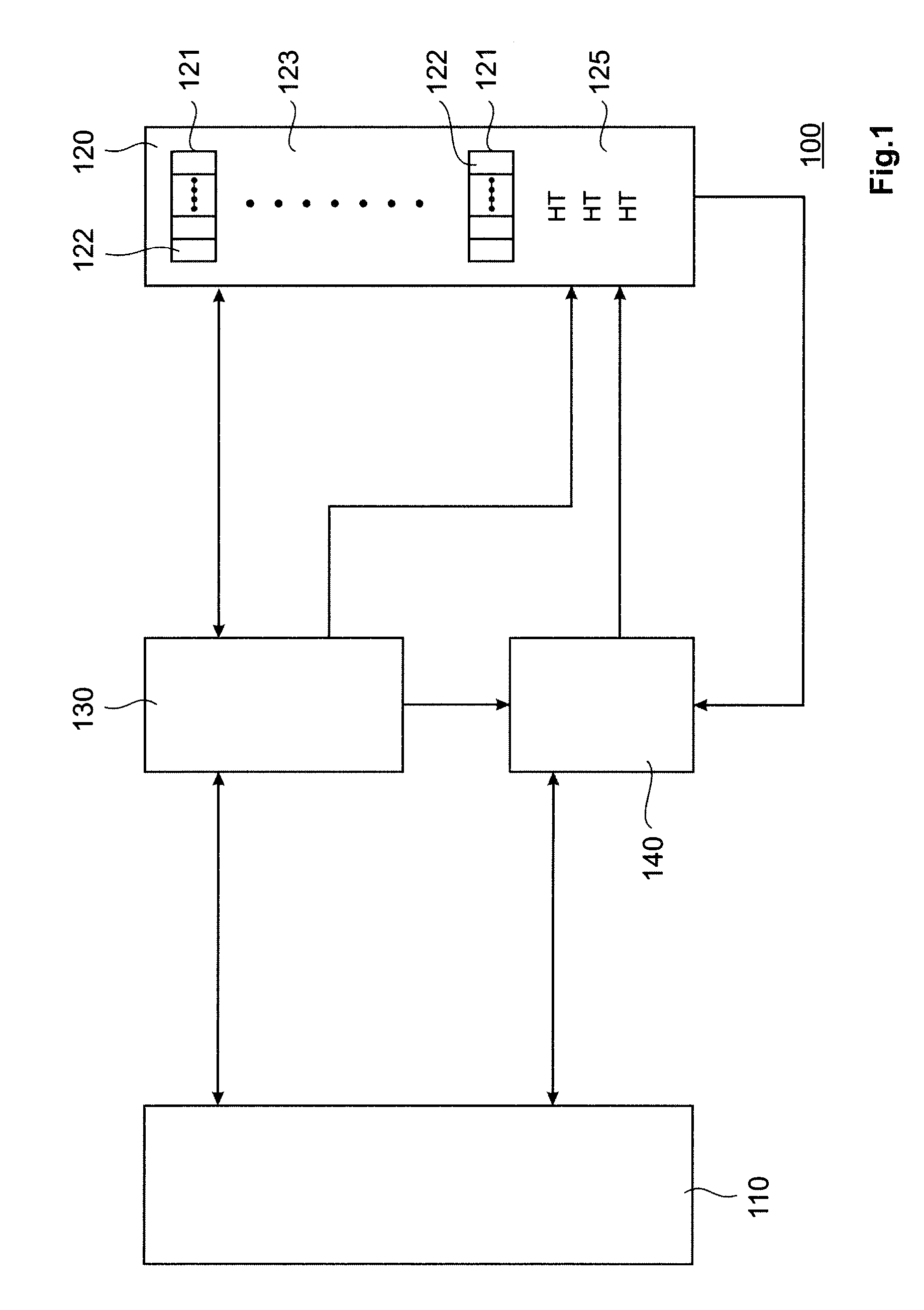
InactiveUS20090037491A1Digital data protectionSpecial data processing applicationsComputer hardwareMerkle tree
A system and method is provided for updating a hash tree in a protected environment. An integrity protection controller is provided for observing one or more system parameters of a storage system and one or more hash tree parameters of the hash trees, and for updating a hash tree in dependence on the storage system parameter and the hash tree parameter.
Owner:IBM CORP
Block chain spatio-temporal data query method and system and electronic equipment
ActiveCN108595720AQuery method is efficientMeet the requirementsSpecial data processing applicationsTime rangeStructure of Management Information
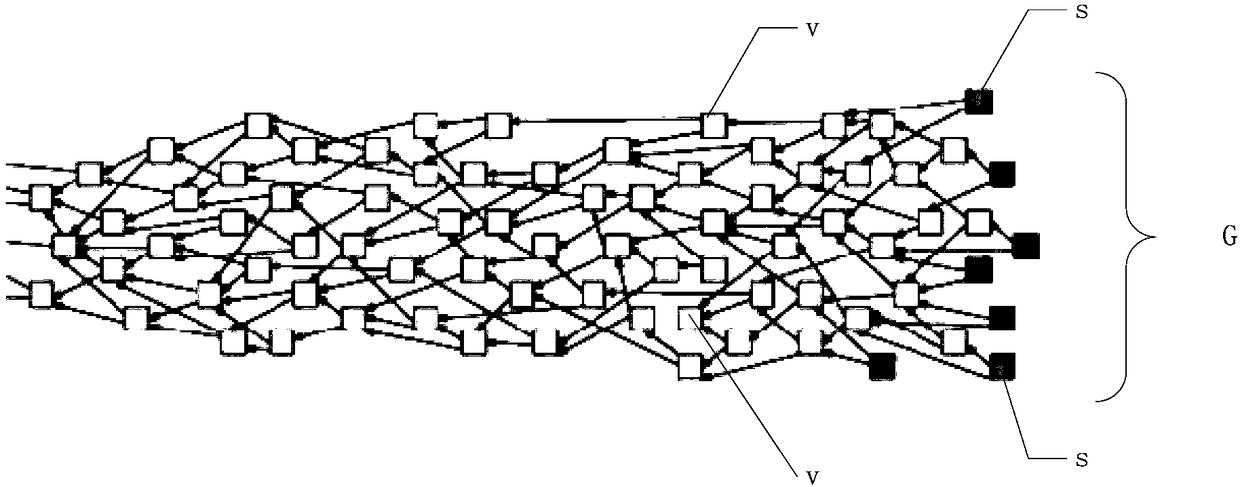
The invention relates to a block chain spatio-temporal data query method and system and electronic equipment. The method comprises the following steps of: a, inserting spatio-temporal data in a blockchain system into a Merkle tree and kd tree combined tree index structure, storing the spatio-temporal data in a block chain module, and for each block in the block chain module, importing tempon information in a block head; b, giving a corresponding time range and a corresponding space range for the spatio-temporal data, and searching blocks according with the time range in a topological structure G of a directed acyclic graph by utilizing the tempon information in the block head of each block in the block chain module; and c, reading root node information, in the block heads of the blocks according with the time range, of the Merkle tree and kd tree combined tree index structure, searching key data according with the spce range, and obtaining corresponding spatio-temporal data accordingto the key data. The method is efficient and is capable of rapidly returning results according with given requirements in an online manner.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
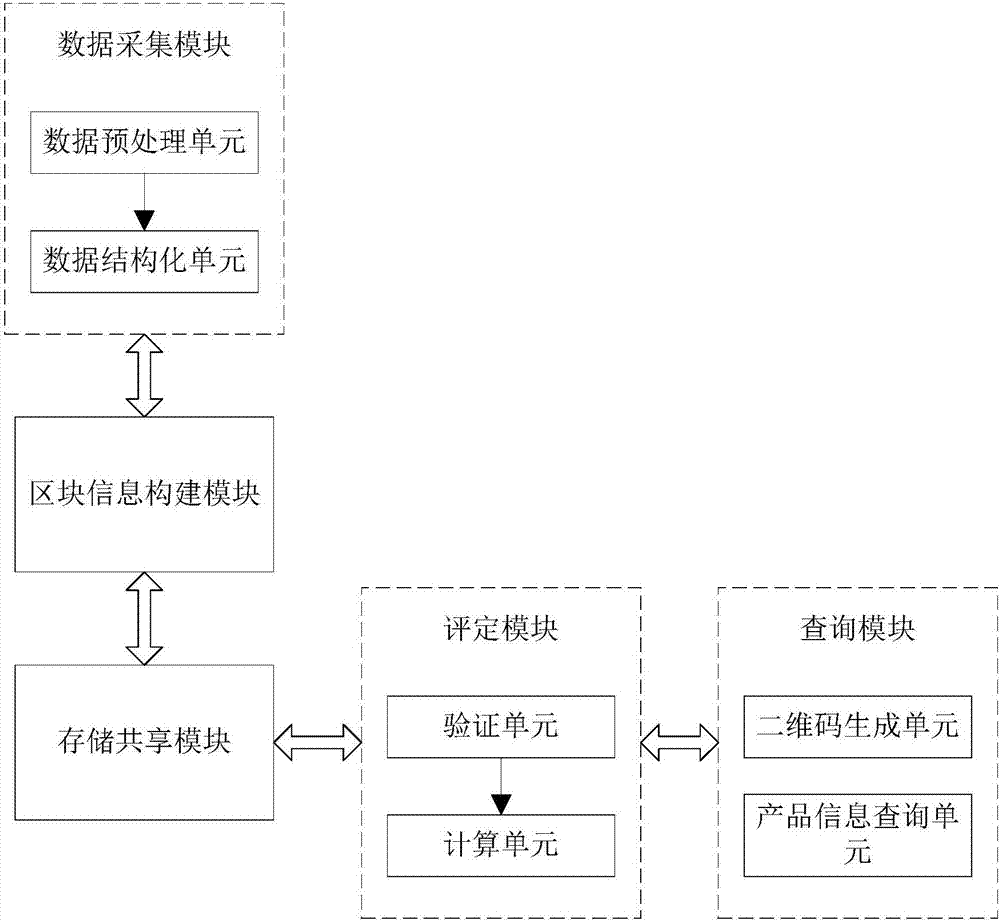
Agricultural product quality information system based on block chain
The invention discloses an agricultural product quality information system based on a block chain. The agricultural product quality information system comprises a data acquisition module, a block information construction module, a storage sharing module, an evaluation module, and a query module. The data acquisition module is used to acquire soil information and agricultural product type information, and is used to transmit the acquired information in a structured data form to the block information construction module. The block information construction module is used to allocate identity labels for the agricultural products, is used to construct a Merkle tree by using the received structured data, and is used to form block information by carrying out digital signature and time stamp service, and then the p2p transmission of the block information is carried out after work load proof. The storage sharing module is used for the work load verification of the received block information, and after data check, the block information is broadcasted. The evaluation module is used to carrying out the quality evaluation of the agricultural products to acquire quality scores. The query module is used to receive the block information and the quality scores to generate query two-dimensional codes. By introducing the block chain technology, the authoritative and unified agricultural product quality information system is constructed.
Owner:SHANGHAI JIAO TONG UNIV
Cache-based method of hash-tree management for protecting data integrity
InactiveUS20100153732A1Simplify secure data integrity check operationUser identity/authority verificationDigital data protectionData integrityRoot signature
The present disclosure relates to accessing data stored in a secure manner in an unsecure memory, based on signatures forming an integrity check tree comprising a root signature stored in a secure storage space, and lower-level signatures stored in the unsecure memory. One embodiment calculates a first-level signature from the data in a group comprising a changed datum, and temporarily stores the signature calculated in a secure memory. The embodiment calculates a signature to check the integrity of a lower-level signature by using the signature to be checked and a second signature belonging to a same group as the signature to be checked, read as a priority in the secure memory and in the unsecure memory if it has different values in the secure and unsecure memories.
Owner:STMICROELECTRONICS (ROUSSET) SAS
Redundant Fail-Safe Synchronization in a Data Authentication Infrastructure
ActiveUS20160253523A1Digital data protectionDigital data authenticationData validationDigital signature
A distributed hash tree-based authentication system for digital input records has more than one upper-level core node, each of which receives at least one uppermost value from aggregators. Communicating with each other about which aggregator values they have received, the nodes try to reach agreement as to which of these values should be included in duplicated current intra-node hash tree evaluations so as to form a consistent top-level value used as the basis for digital signatures associated with the digital input records.
Owner:GUARDTIME SA
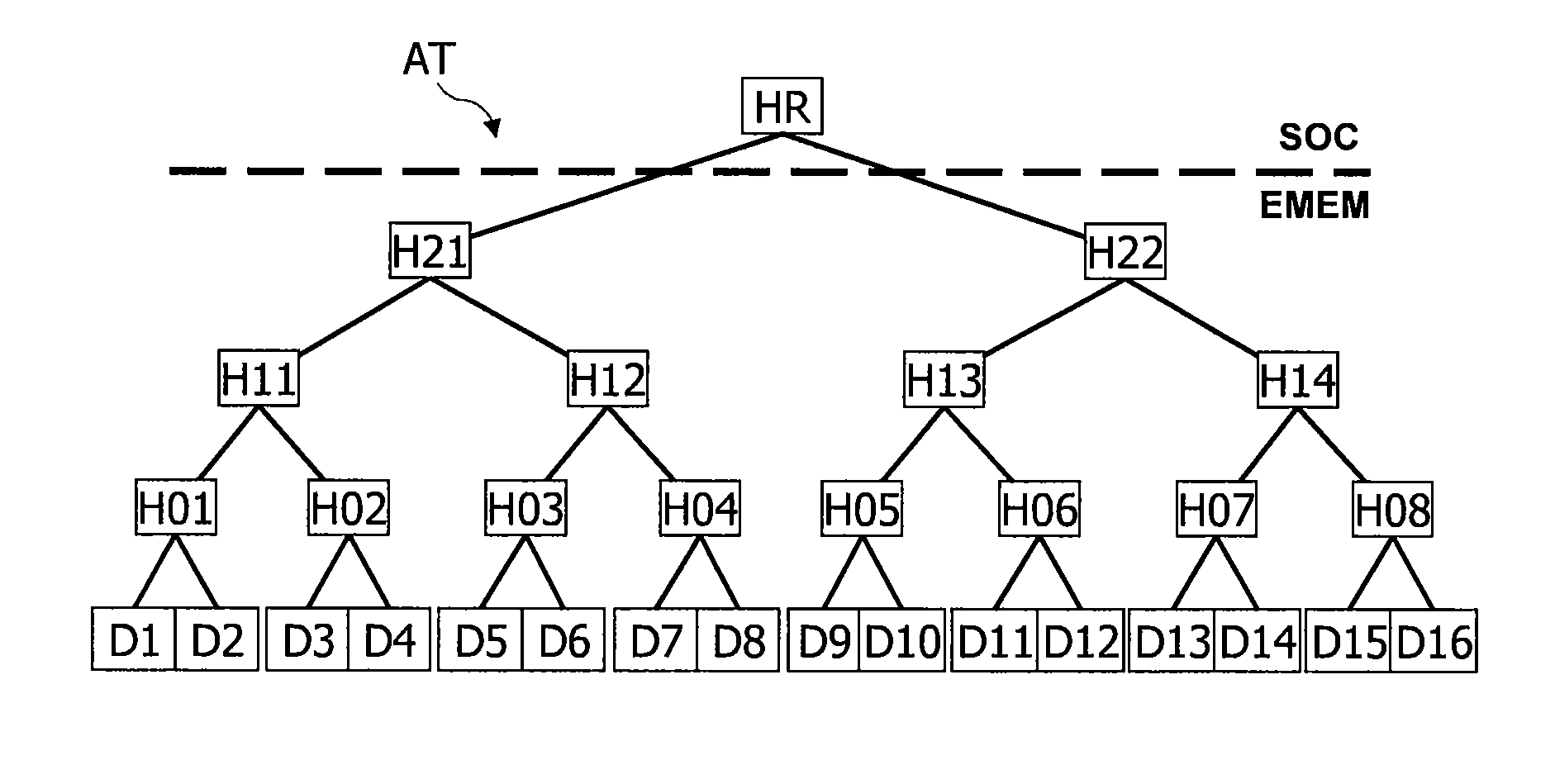
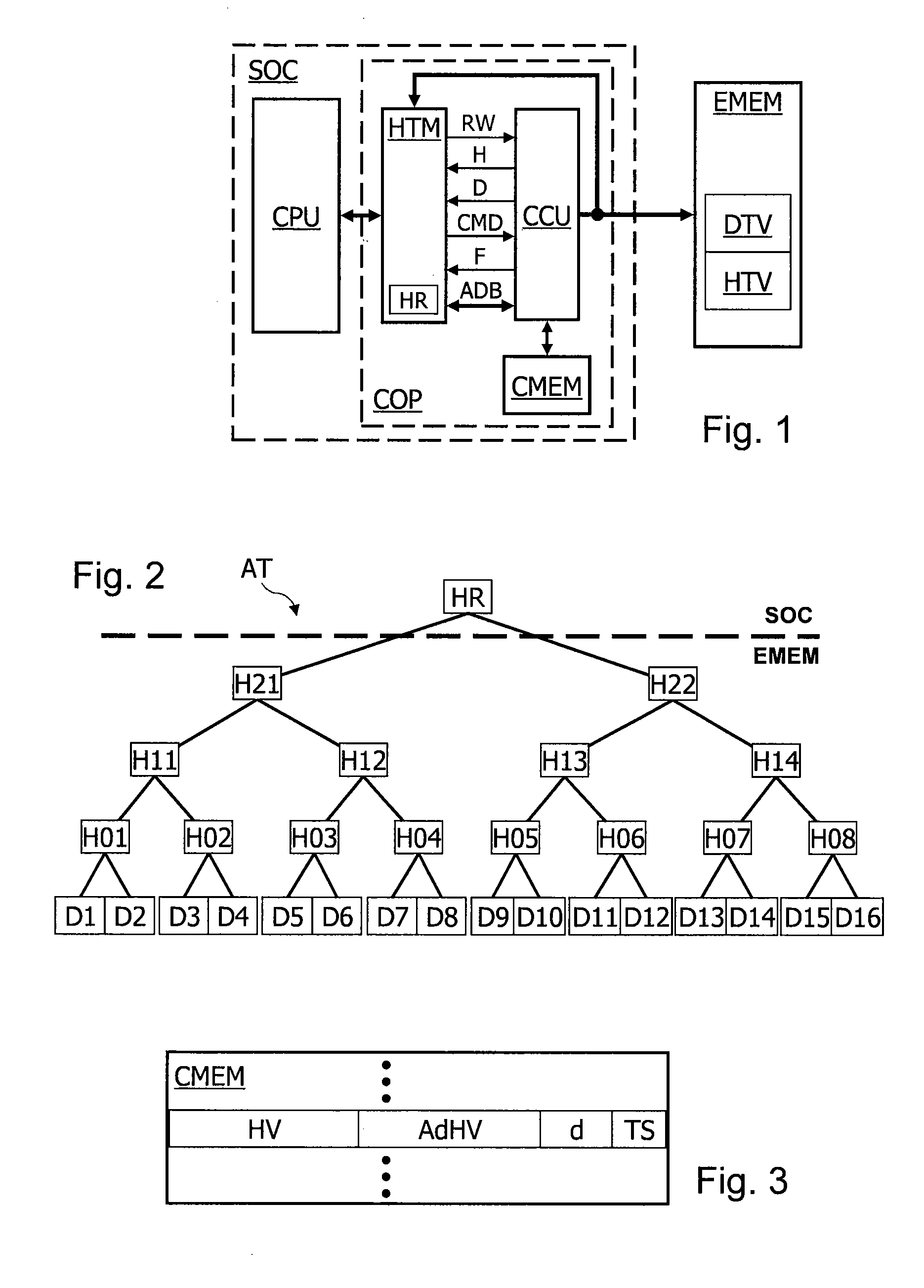
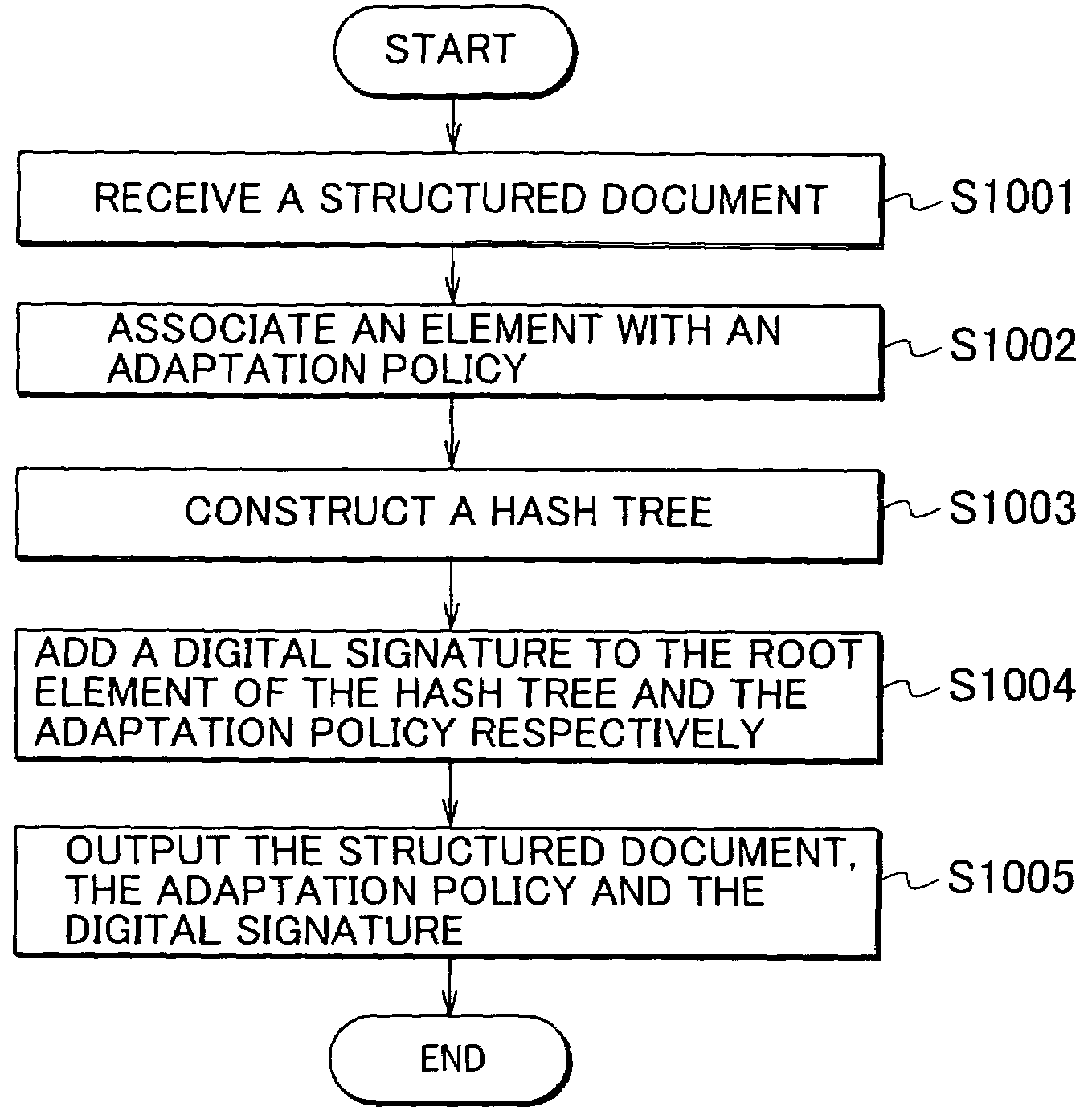
Structured document signature device, structured document adaptation device and structured document verification device
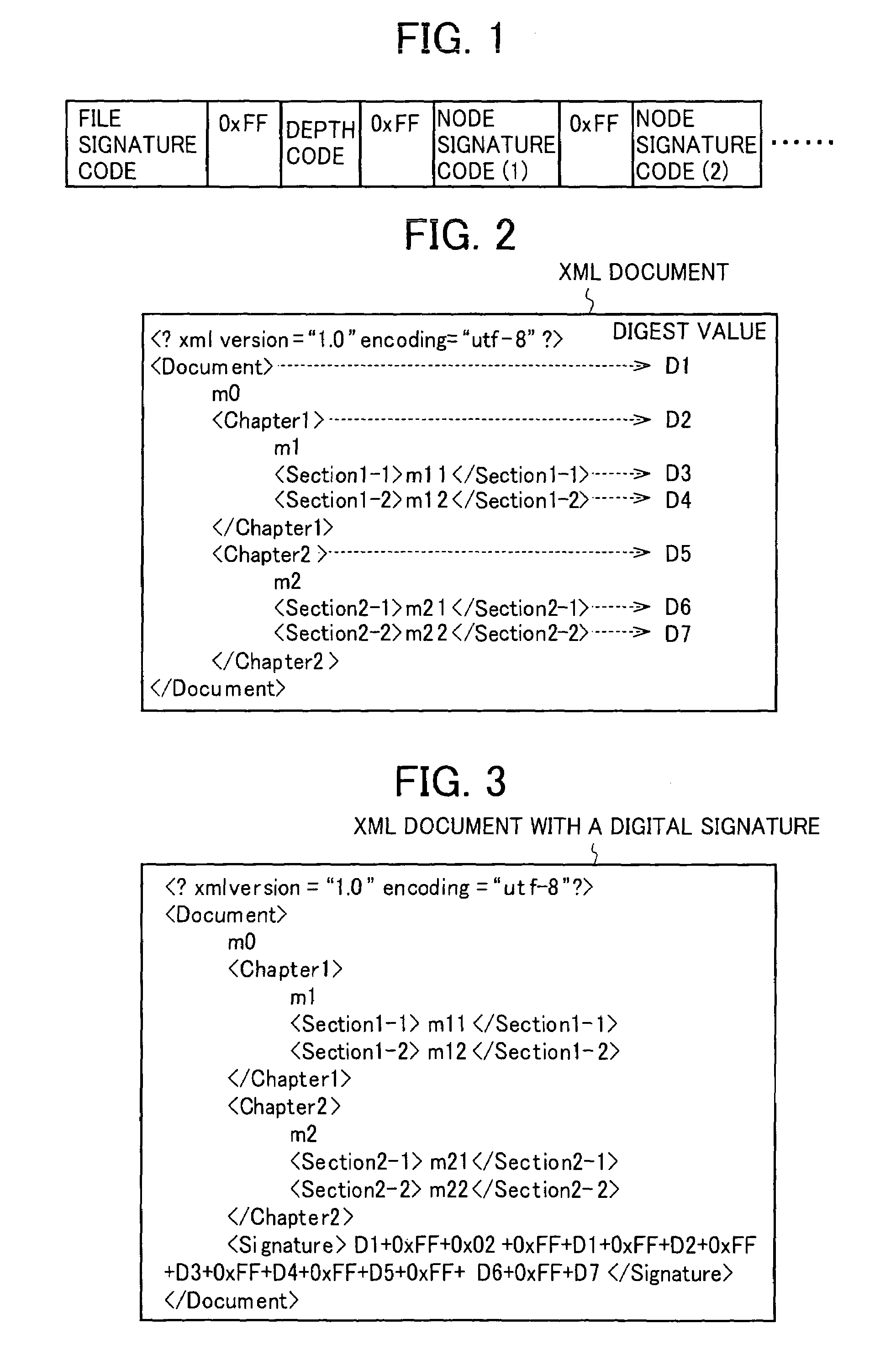
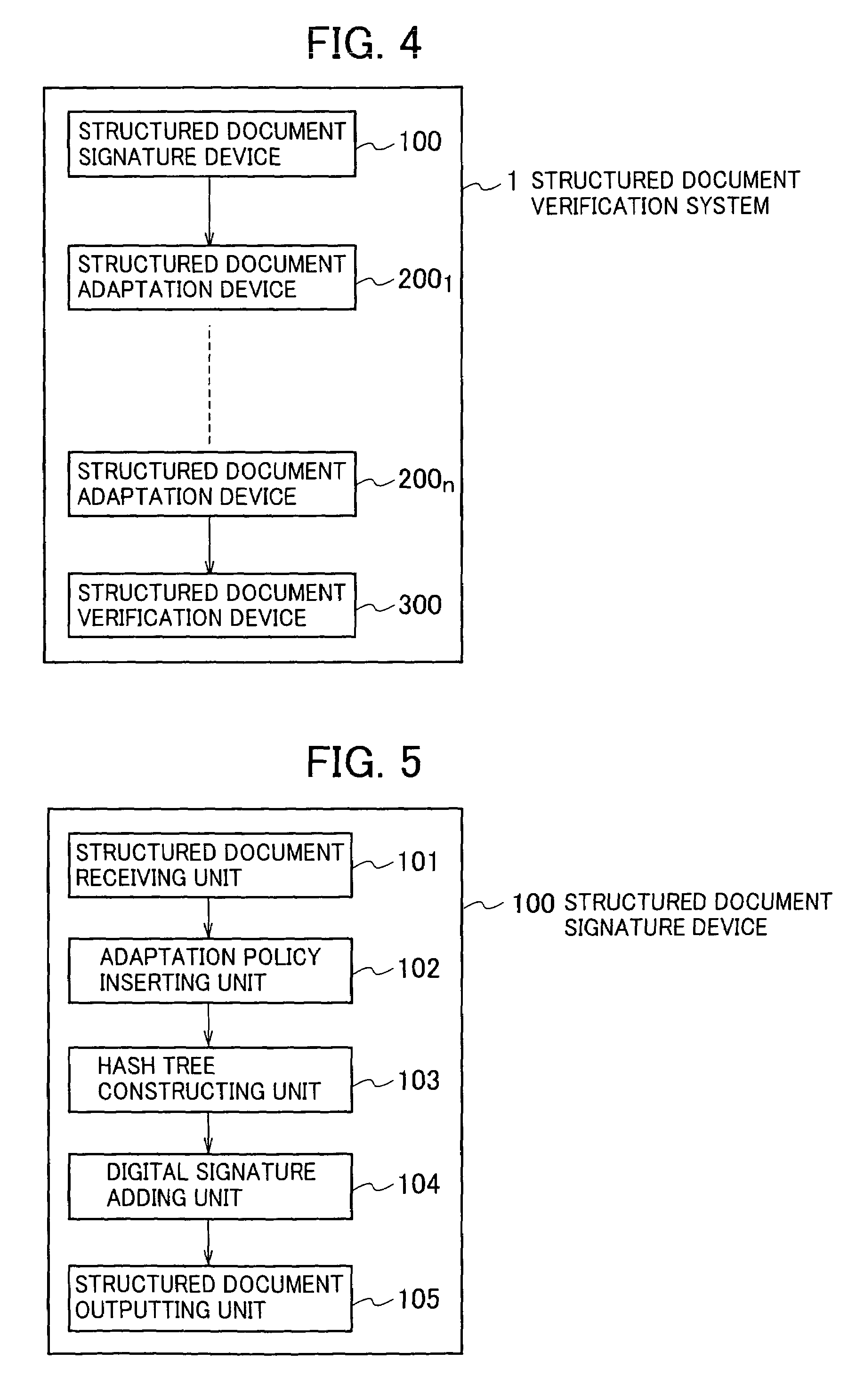
ActiveUS7639818B2User identity/authority verificationUnauthorized memory use protectionDigital signatureDocumentation
A structured document signature device includes an adaptation policy associator configured to associate each element forming a structured document with an adaptation policy indicating an action which can be adapted to a child element of the element or a value of the element; a hash tree constructor configured to insert a hash value of the child element of the element or a hash value of the value of the element into the structured document as an attribute value of the element, and to construct a hash tree including the hash value; a digital signature adder configured to add a digital signature to a root of the hash tree and the adaptation policy; and an output configured to output the structured document and the digital signature.
Owner:NTT DOCOMO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com