Cloud platform trusted log auditing method for privacy protection based on trusted third party
A privacy protection, cloud platform technology, applied in the field of cloud computing, which can solve the problems of unclear cloud audit objects, no longer clear CT and CSP security boundaries, and CSP administrator removal and destruction.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
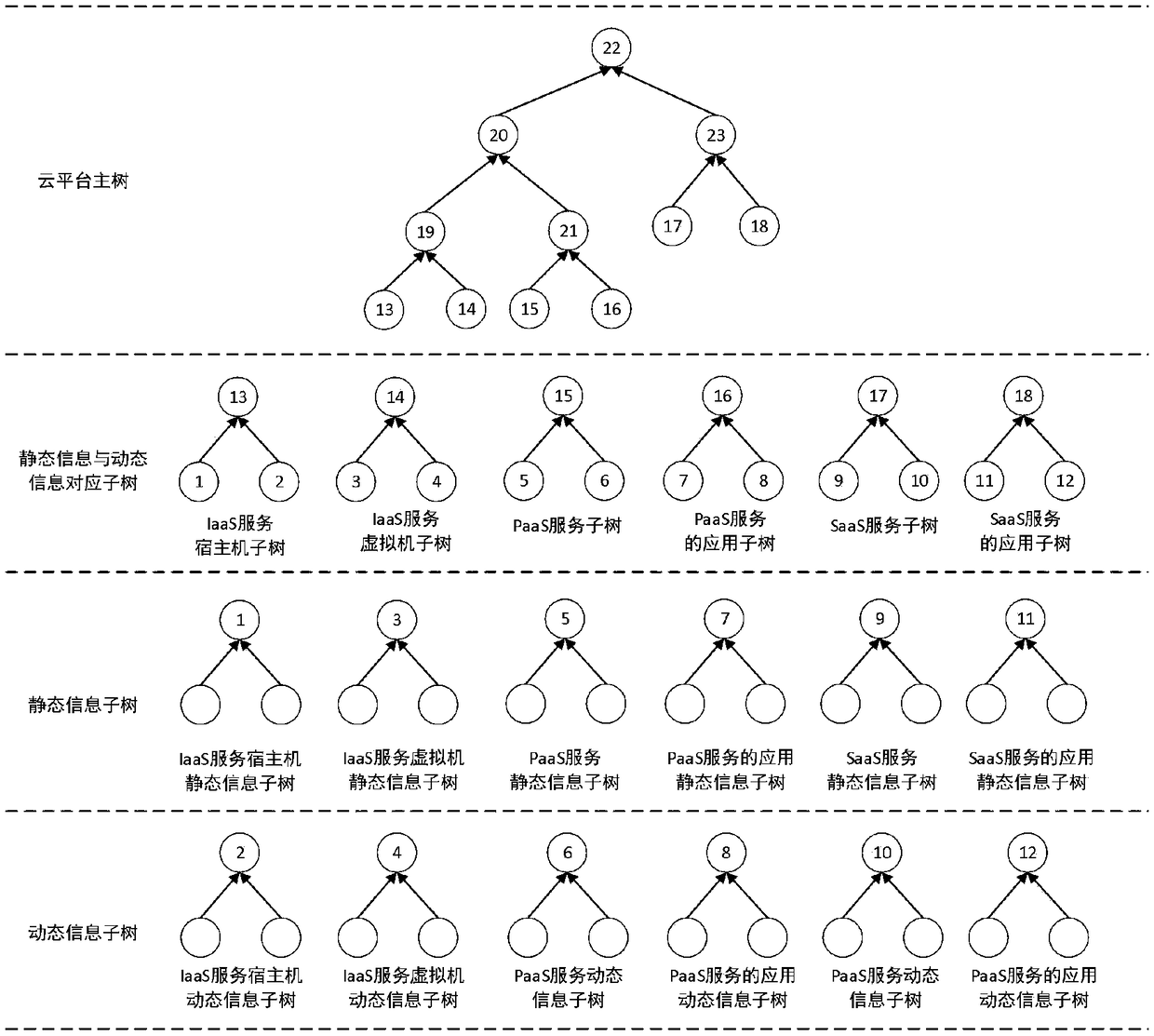
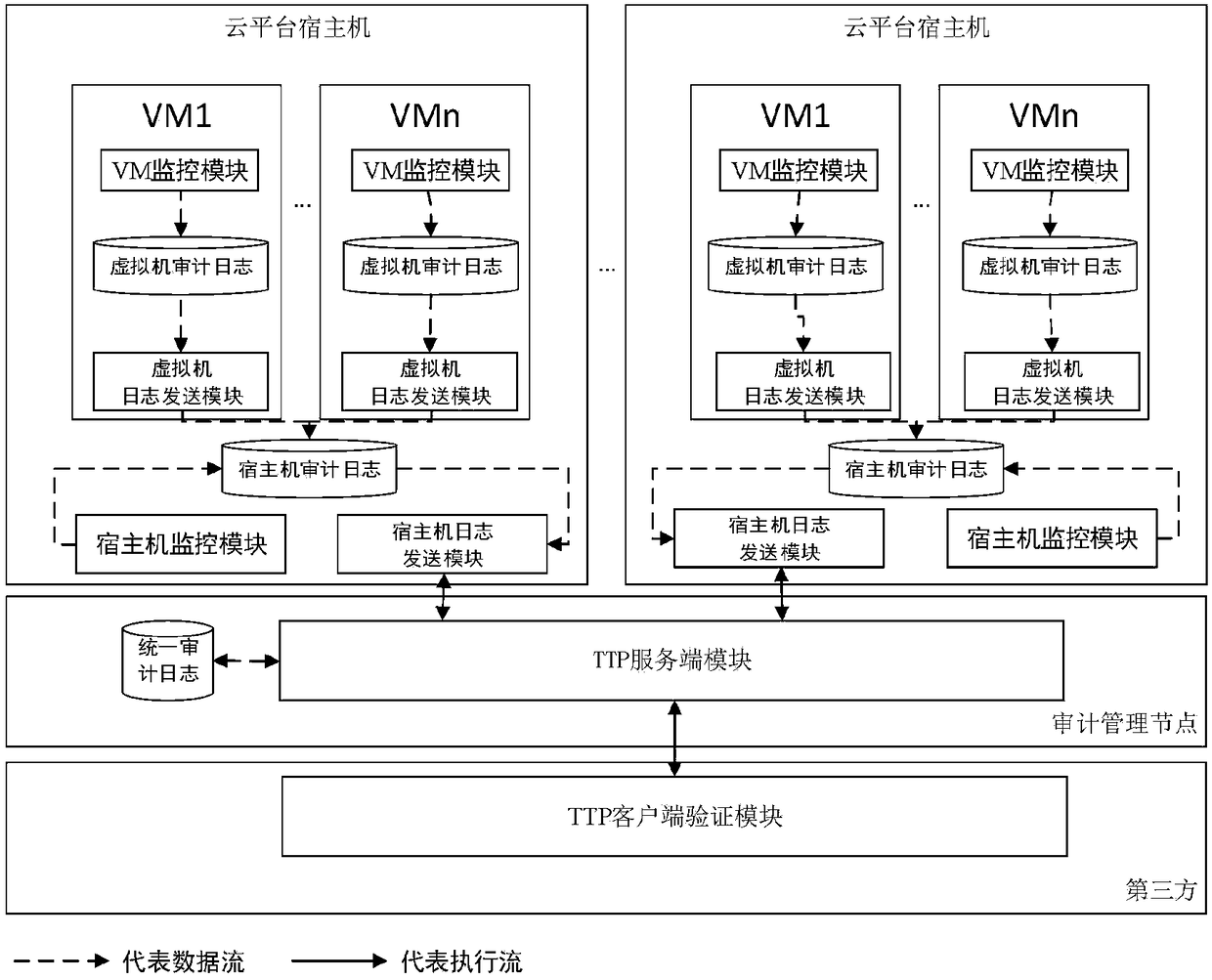
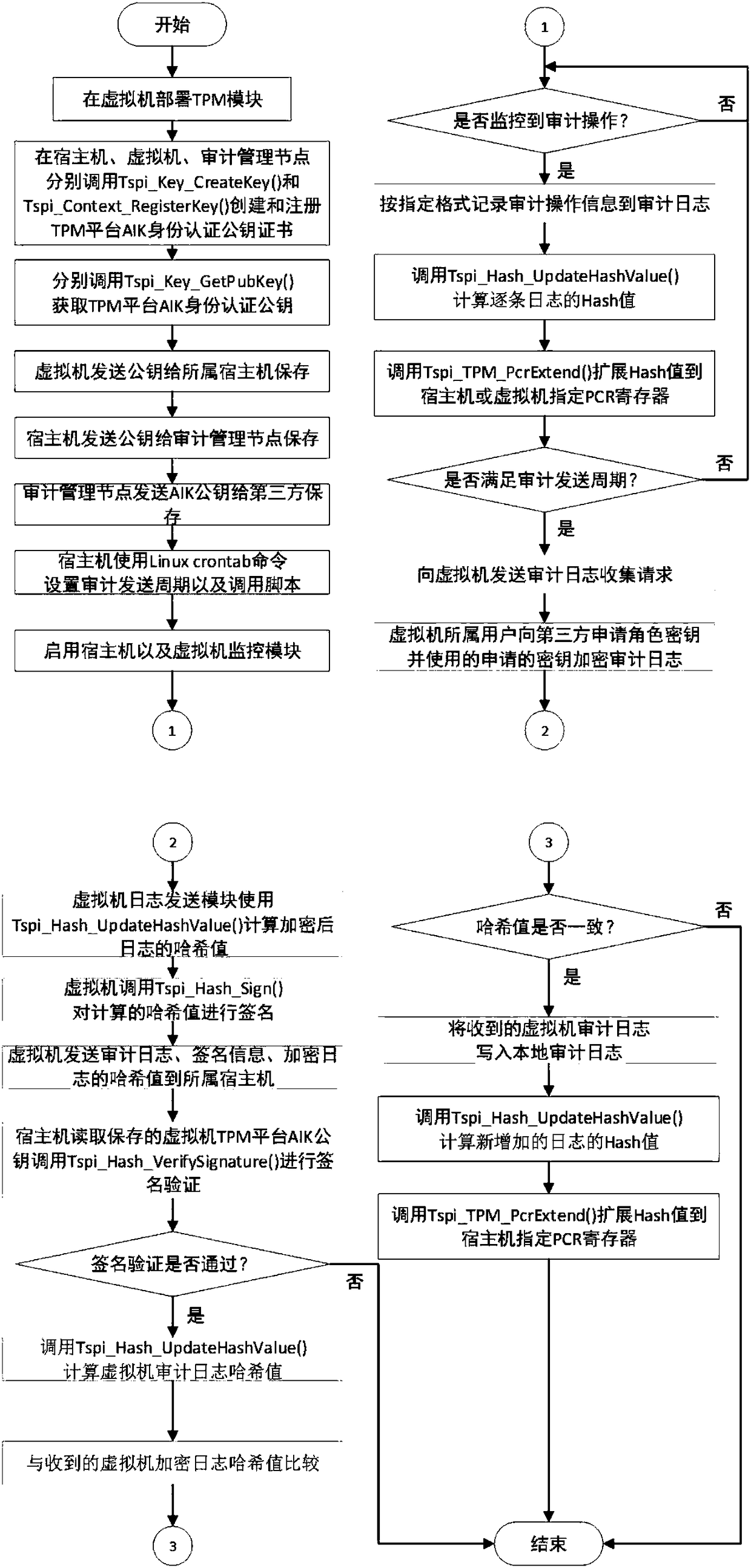
[0071] The execution flow chart of the privacy protection-oriented cloud platform trusted log audit method based on a trusted third party proposed by the present invention is shown in the attached figure 2 As shown, it mainly includes third-party hosts, cloud platform hosts, and virtual machines of different tenants.
[0072] Among them, the third party includes a client verification module, through which tenants send audit log verification requests to the server module and view verification results. Deploy the server module on the audit management node. The audit management node is responsible for storing the unified audit logs sent back by the cloud platform host and the virtual machines belonging to the tenants. The server module is used to receive the audit log sent back and the audit log verification request sent by the client verificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com