Safety metadata management method based on integrality checking
A technology of integrity verification and management method, which is applied in the fields of integrity verification, security metadata management, and storage security, and can solve the problems of ineffective management of hash values, large calculation costs, and large costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
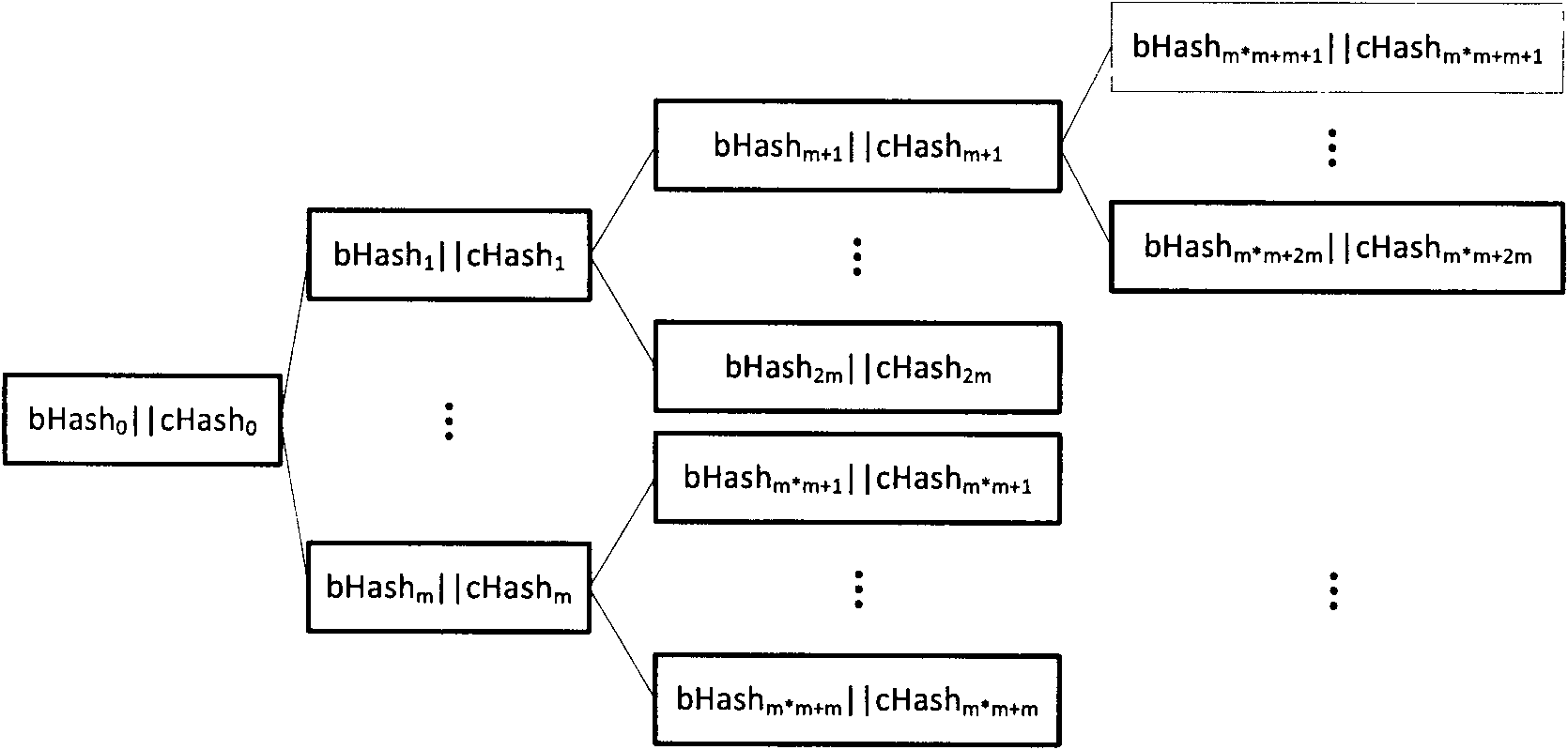
[0049] The core of the present invention is to realize the management of file security metadata on the security metadata management server. Its realization is mainly composed of the following parts, and the management operation is mainly composed of the corresponding modules of each part:
[0050] ●Client: Apply for access to the file, and is mainly responsible for calculating the hash value of the file block and encrypting the file block during the file encryption process;
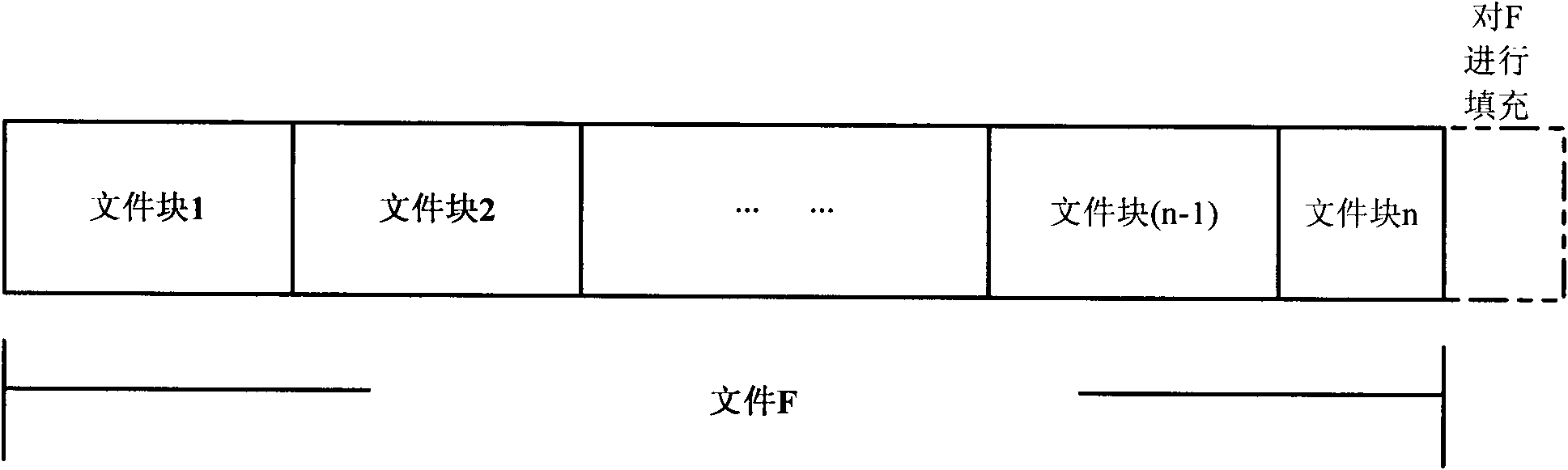
[0051] A. File block module: responsible for block operation of files, specific operations such as figure 1 shown.
[0052] For a file, divide it into multiple fixed-size file blocks;
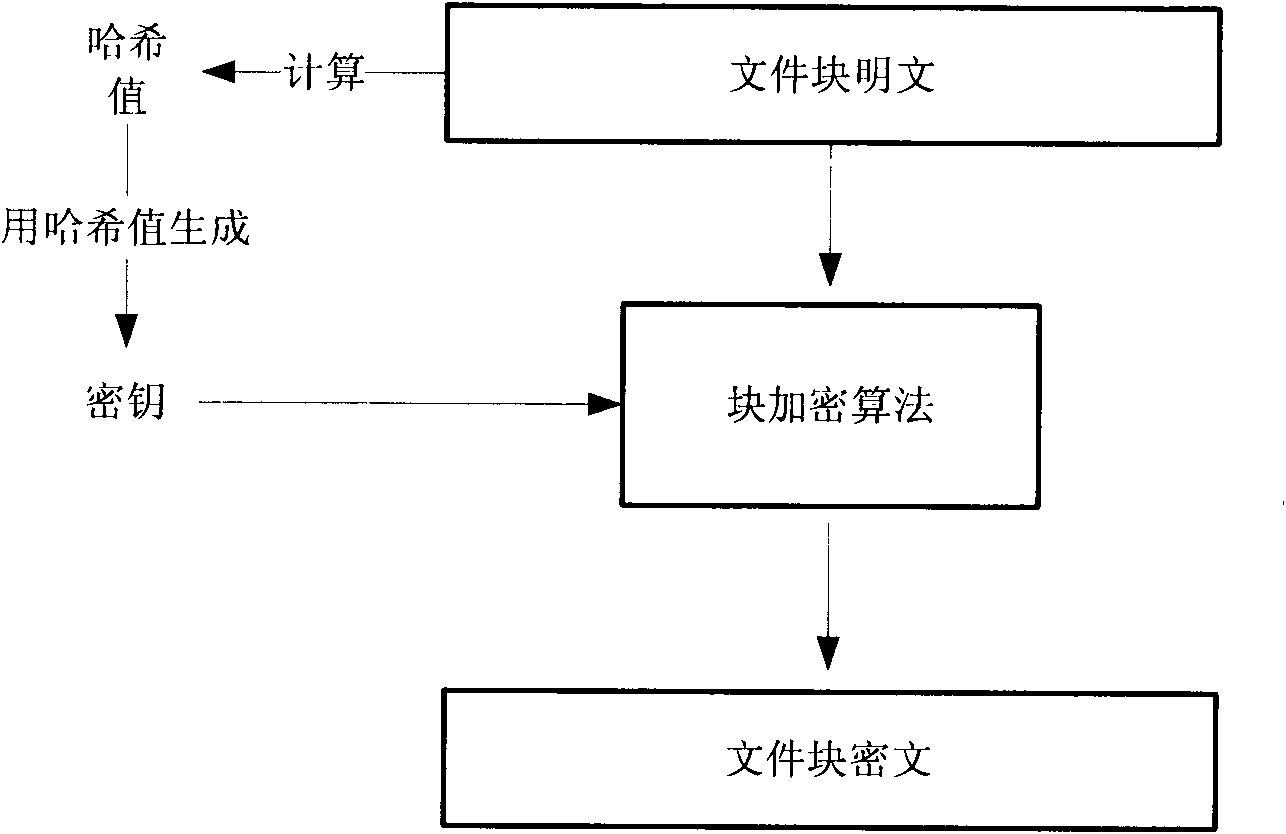
[0053] B. Self-encryption module: responsible for self-encryption operations on file blocks, specific operations such as figure 2 shown.
[0054] The encryption algorithm used in the module is the symmetric block encryption algorithm AES, where the AES algorithm is an advanced encryption standard determined by the Nati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com