Patents
Literature
334results about How to "Implement access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
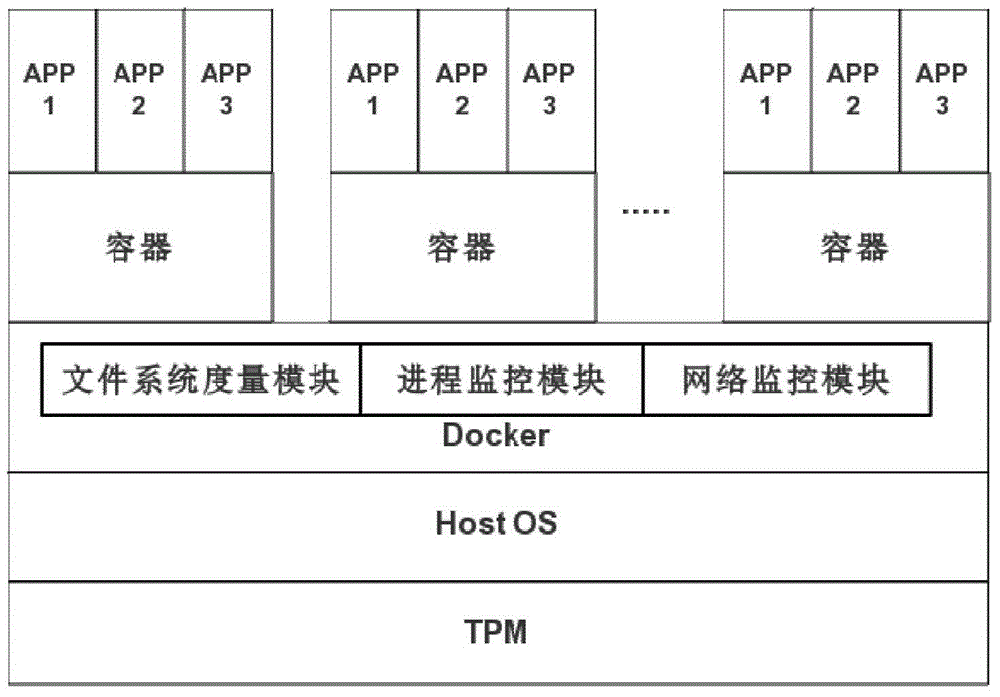
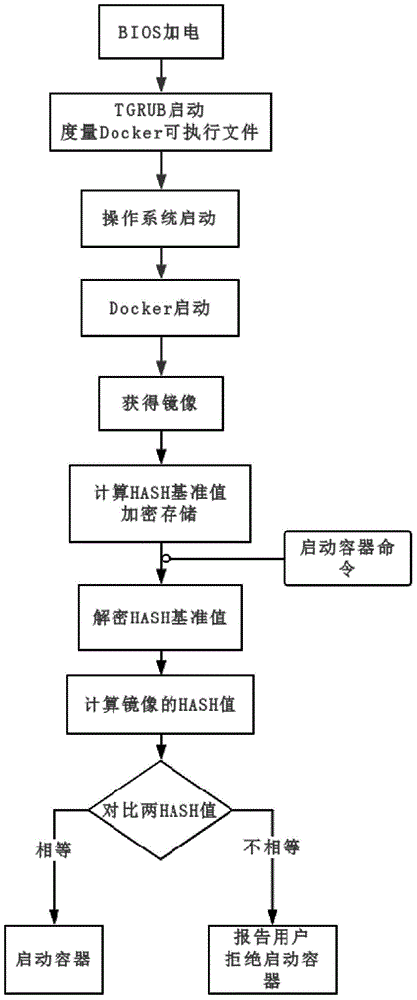
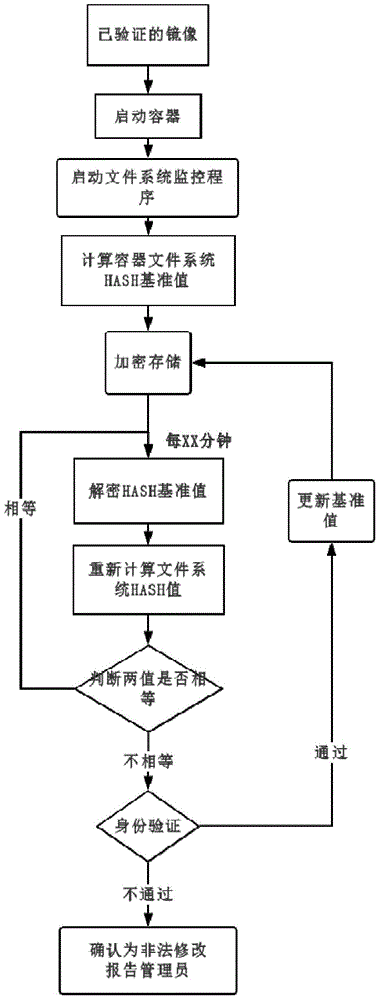
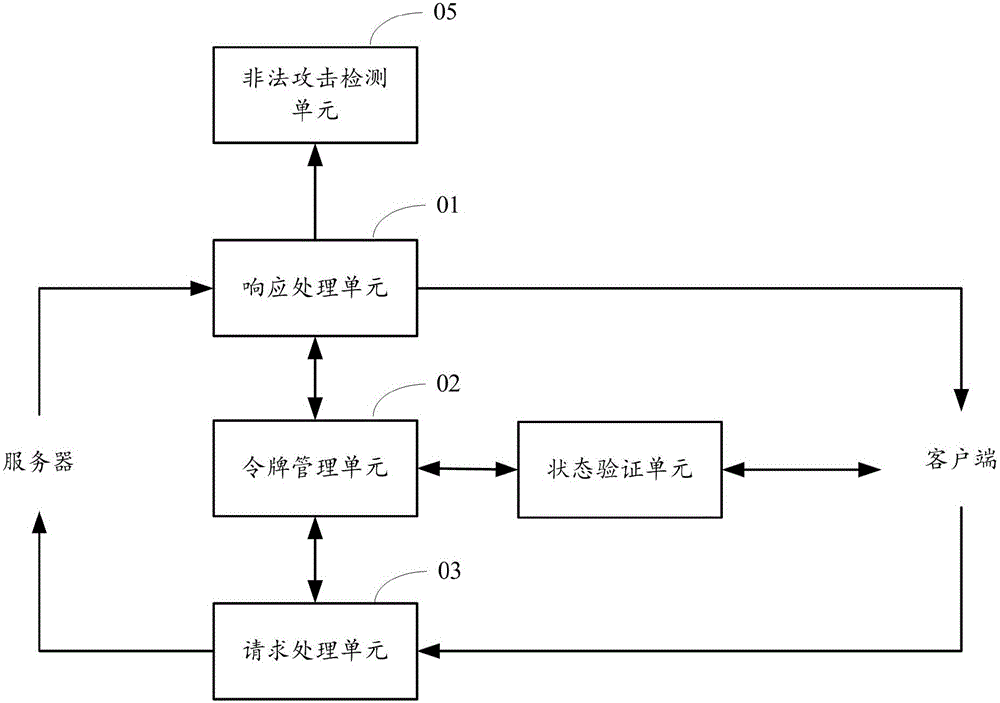
Security reinforcement method for credible container based on Docker
ActiveCN105069353ATrusted bootGuaranteed normal startupPlatform integrity maintainanceNetwork communicationMirror image
The invention discloses a security reinforcement method for a credible container based on Docker used for performing security reinforcement on a Docker container system, and realizes the credible container based on the Docker, as well is applied to a server cluster based on the Docker. The credible container based on the Docker comprises a container program Docker, a container credible measurement module, a progress monitoring module and a network communication monitoring module, wherein the container credible measurement module comprises a credible booting sub-module and a file measurement sub-module. The reinforcement method focuses on the credibility of the Docker container; a credible computing and integrity measurement technology is matched with a real-time monitoring module to reinforce the container system based on the Docker, so that the container and a mirror image are prevented from tampering; and meanwhile, a network communication behavior of the container is limited, and an inner progress of the container is monitored, so as to realize the security reinforced credible container.
Owner:WUHAN UNIV
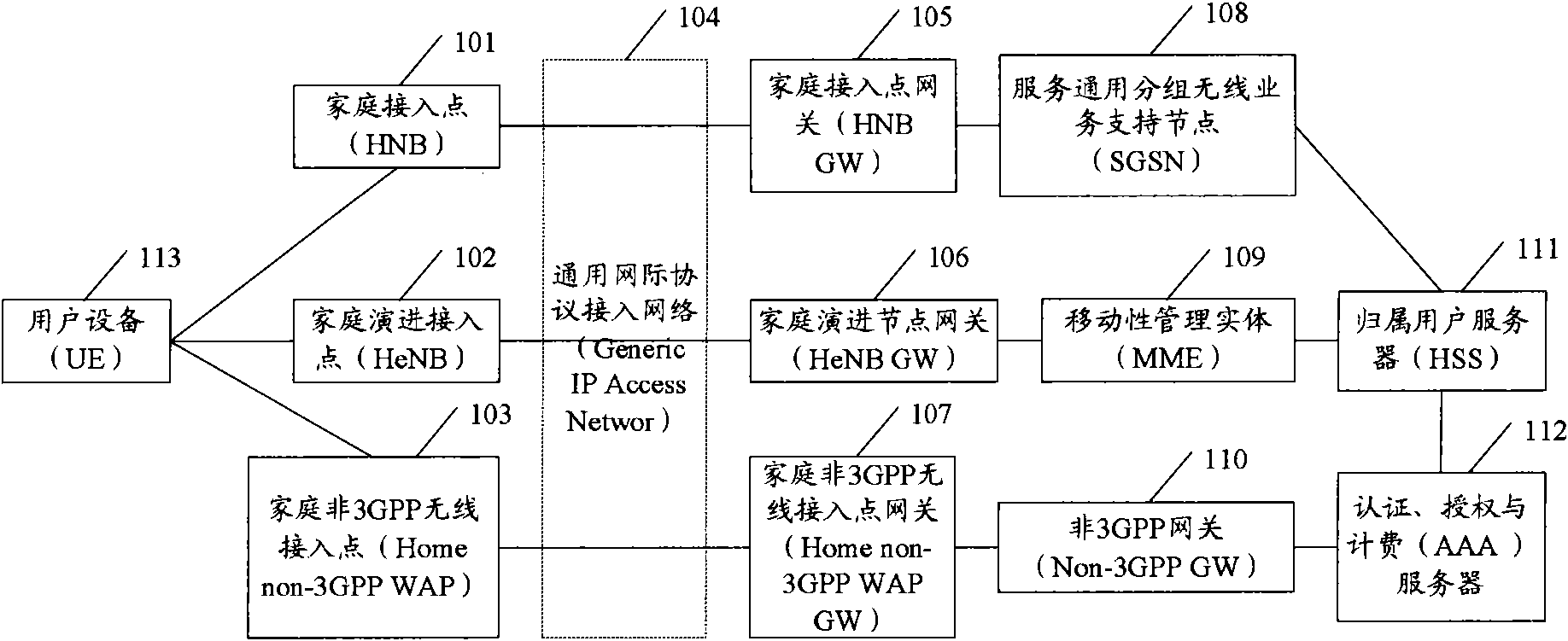
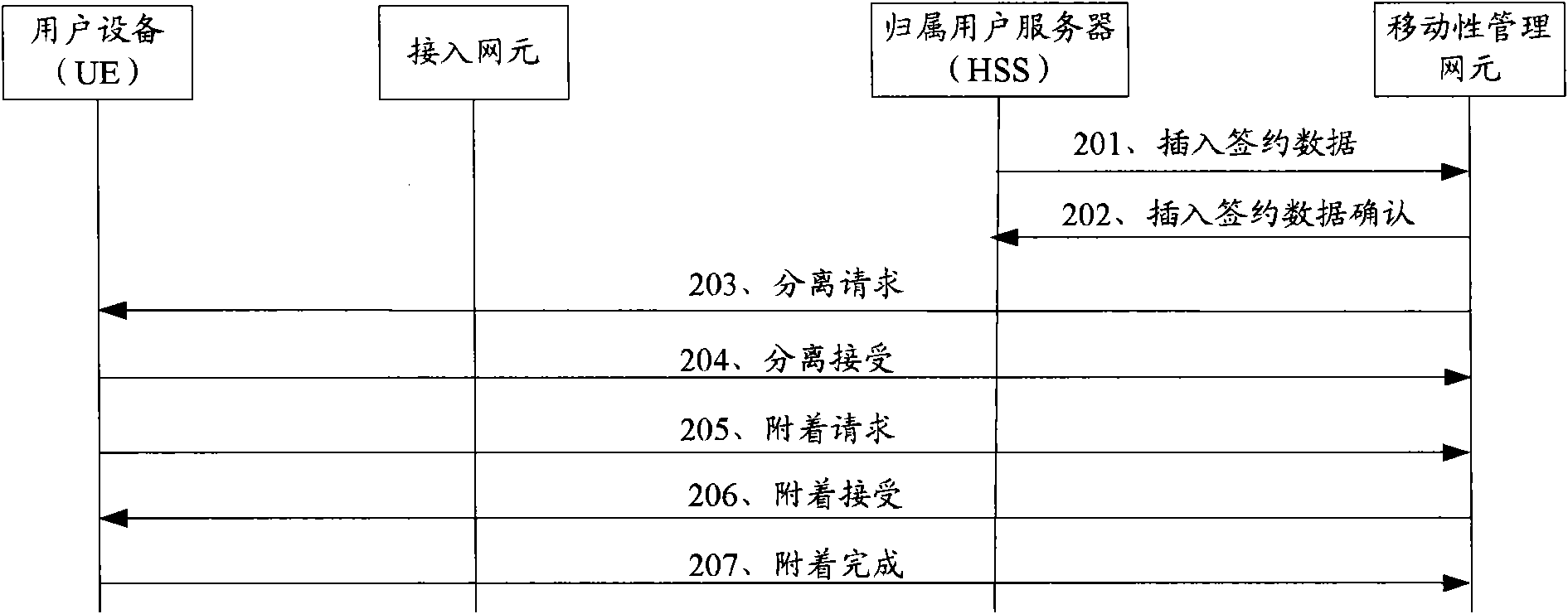
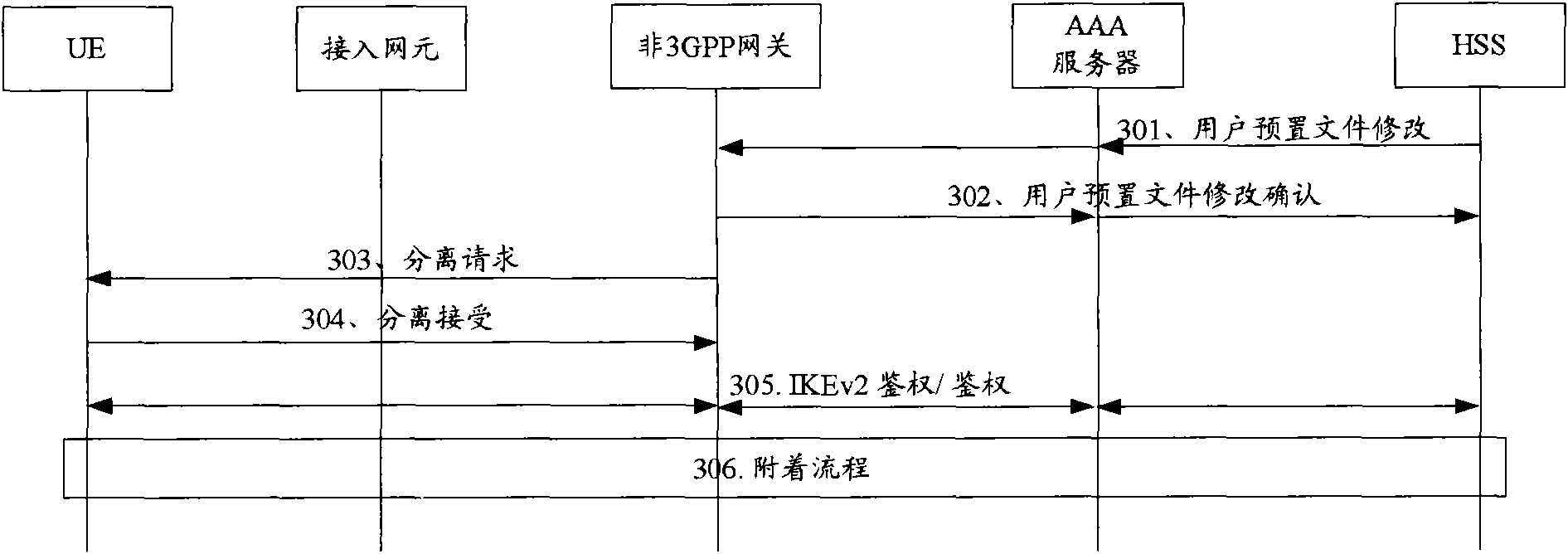
Method for transferring mobile management entity/user interface entity
InactiveCN101039506AEnsure uninterrupted communicationImplement access controlRadio/inductive link selection arrangementsWireless communicationUser interfaceAnchor point
Owner:HUAWEI TECH CO LTD
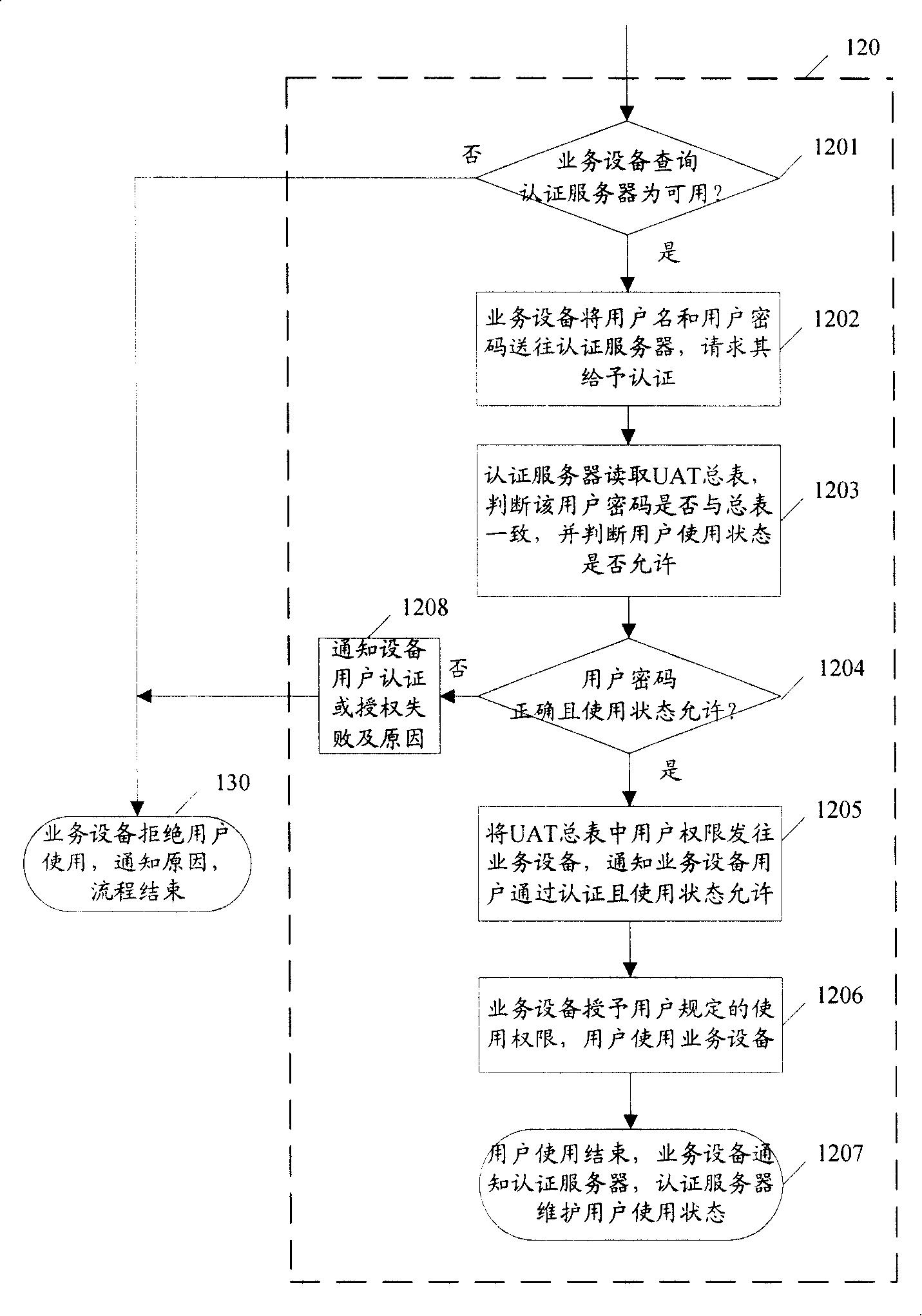
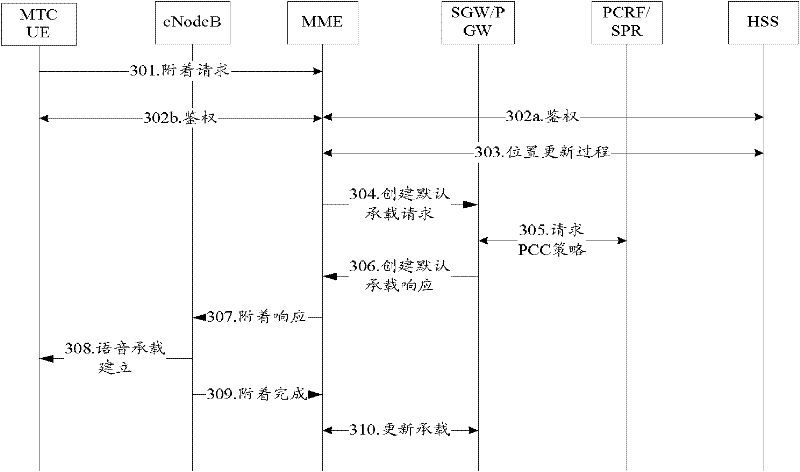
Method, system, service device and certification server for realizing device access control
ActiveCN101170409AAuthentication does not affectAuthentication is convenientUser identity/authority verificationData switching networksManagement processControl system
The embodiment of the invention discloses an equipment access control method, which comprises the following steps: a user sends a service request to authentication equipment, which authenticates and authorizes according to the service request and pre-set authentication information in a user authorization list; service equipment provides a service for the user according to the authentication and authorization result. The method reduces the complexity of the service equipment access control. The invention also discloses an equipment access control system, and the service equipment and an authentication server to realize the control of the equipment access. The equipments simply realizes the authentication, authorization and management processes of the service equipment access control, and reduces the complexity of the equipment access control as well with safety and effectiveness and convenient use.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
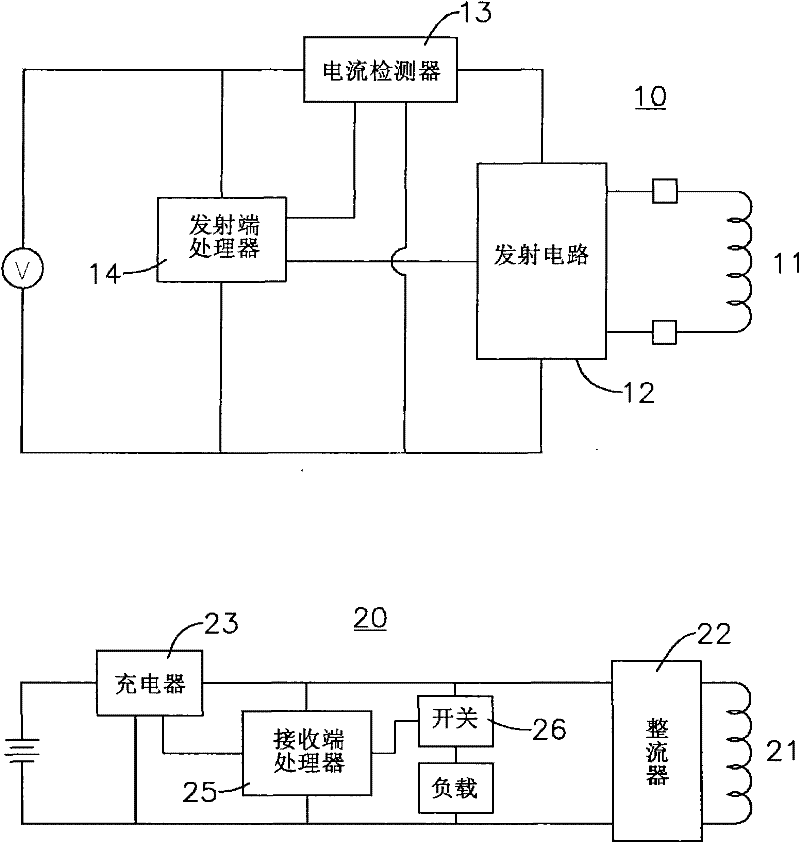
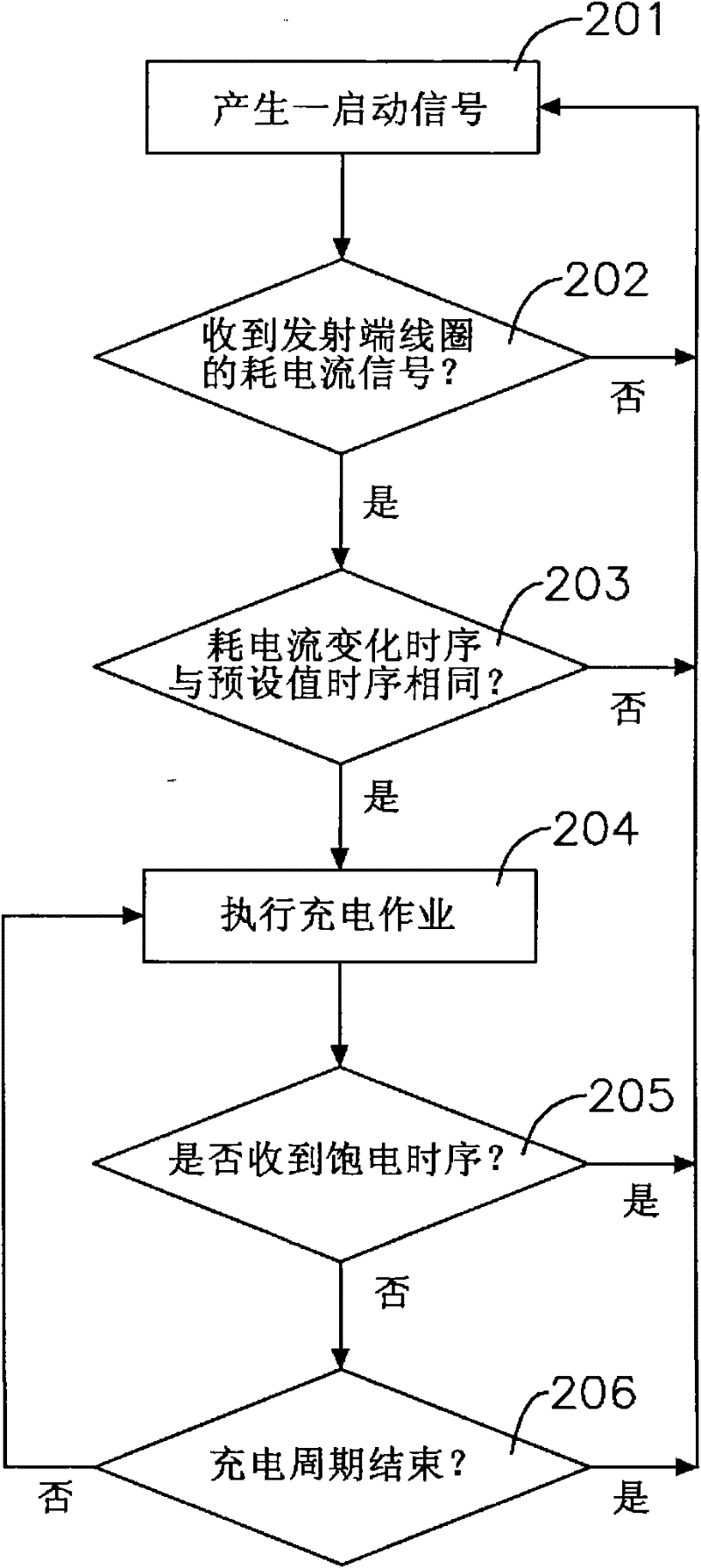
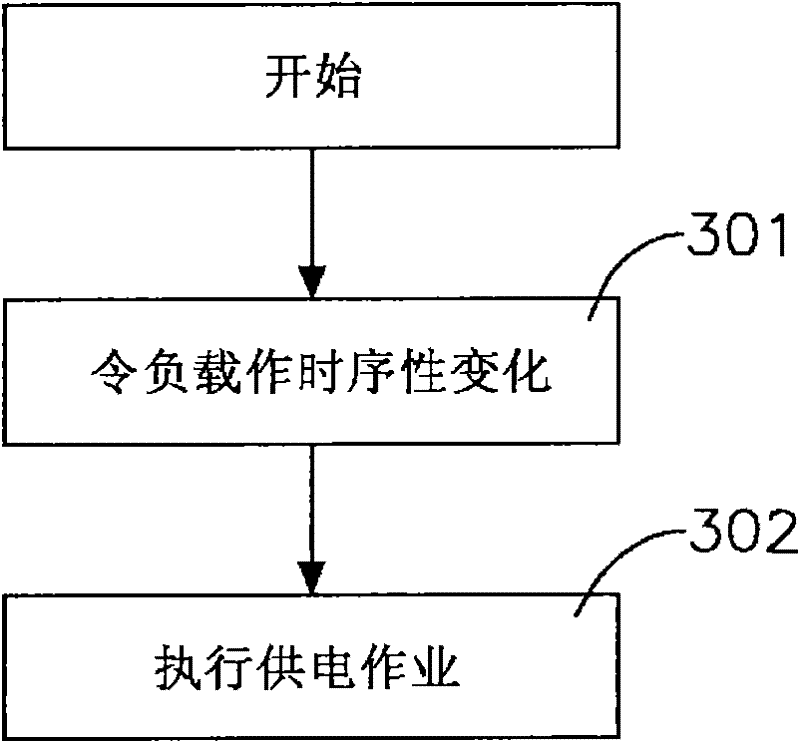
Wireless charging device and charging method thereof
InactiveCN102130477AImplement access controlGuarantee the safety of useBatteries circuit arrangementsElectromagnetic wave systemEngineeringElectric equipment
The invention relates to a wireless charging device and a charging method thereof, which are mainly used for charging electric equipment in an electromagnetic induction way by a wireless charging seat. The wireless charging sear is periodically started to judge whether the electric equipment enters an induction range or not; once the electric equipment enters the induction range, a transmission coil of the wireless charging seat transmits electromagnetic waves, a receiving coil of the electric equipment induces the electromagnetic waves to generate current and performs switching-on or switching-off according to a given built-in time sequence to relatively change the consumption current of the transmission coil in the wireless charging seat; and then the wireless charging seat judges the change time sequence of the consumption current is consistent with the built-in time sequence or not, and the transmission coil continuously charges the electric equipment if the change time sequence of the consumption current is consistent with the built-in time sequence, and stops charging the electric equipment if the change time sequence of the consumption current is inconsistent with the built-in time sequence. Therefore, the damages caused by different voltage designing of the wireless charging seat and the electric equipment are prevented, and safety in use is ensured.
Owner:KYE SYST CORP
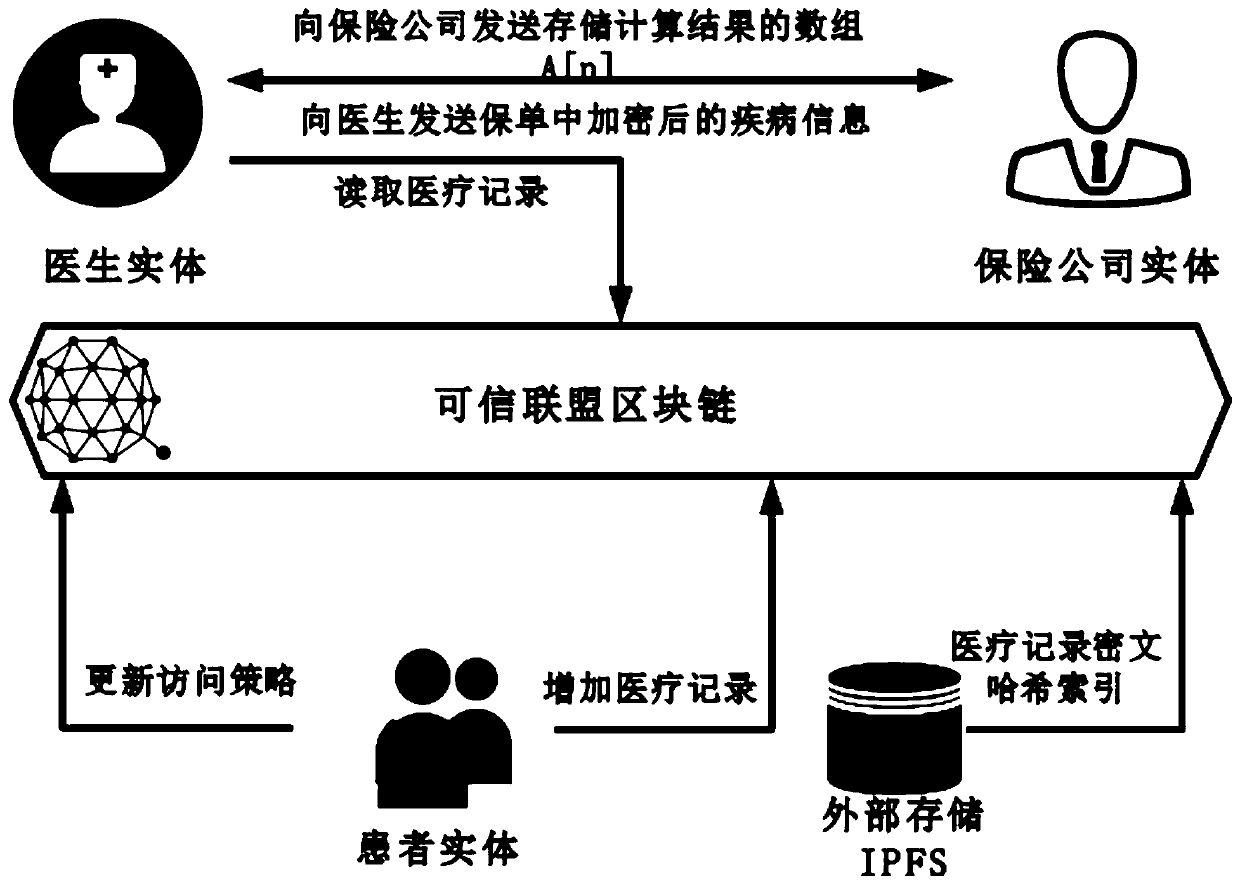
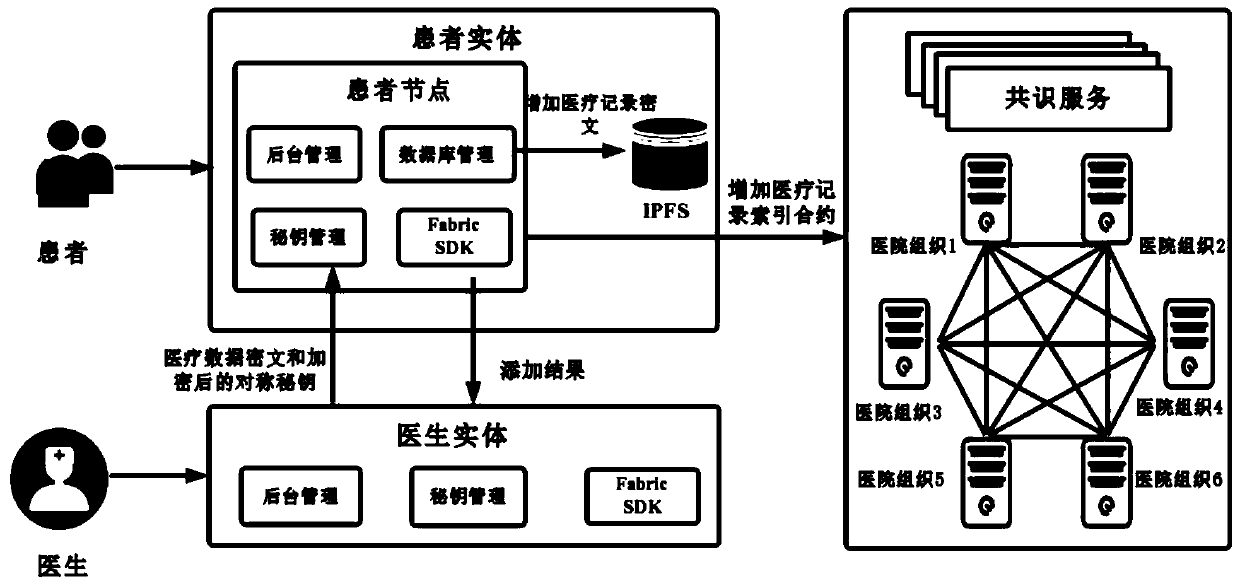
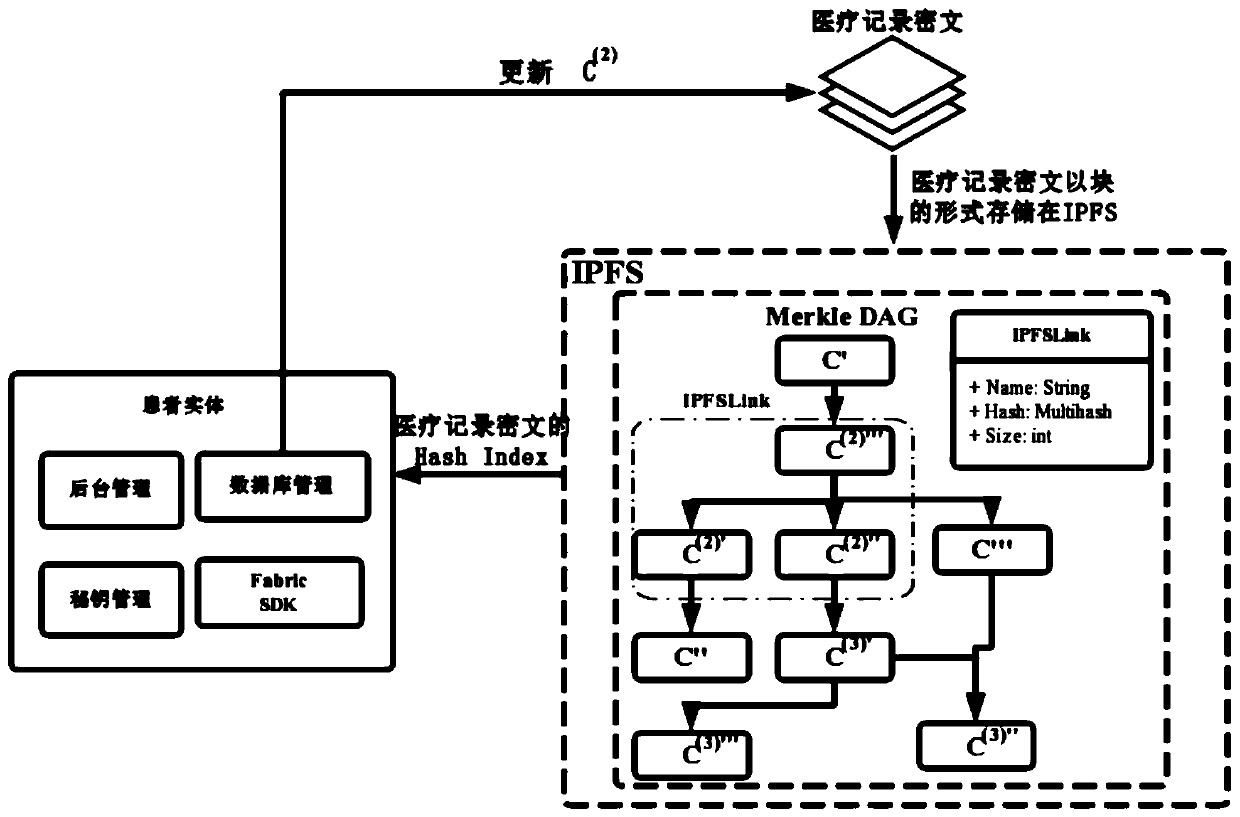
Medical record storage, sharing and security claim settlement model and method based on a block chain
ActiveCN110008746AGuaranteed privacyIncrease resistanceDigital data protectionPatient healthcareMedical recordThird party
The invention belongs to the technical field of medical data management, and relates to a medical record storage, sharing and security claim settlement model and method based on a block chain. Firstly, credible sharing of medical data of patients among medical institutions is achieved through the blockchain technology, and a lifelong medical record is established for the patients; based on a Hashchain type storage structure, the medical data cannot be tampered; secondly, an improved CP-ABE-based cryptographic primitive SHDPCPC-CP-ABE is proposed, security encryption and fine-grained access control on the medical data are realized, and a patient can conveniently and efficiently access and authorize a medical institution to read the medical data; and finally, a Paillier homomorphic encryption technology is utilized to realize safe medical insurance claim settlement, and the privacy of the patient is protected when the patient interacts with a third-party non-medical institution. According to the invention, security, confidentiality, reliability and integrity of medical data can be realized, and confidential sharing of private data is supported.
Owner:DALIAN UNIV OF TECH
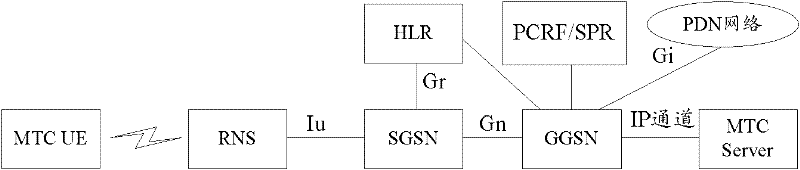
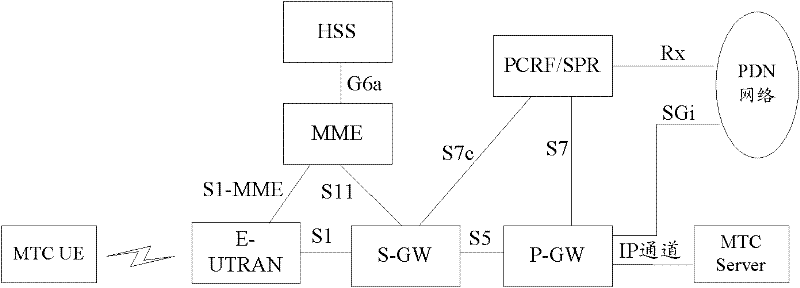
User equipment (UE) access restriction method and system thereof
InactiveCN102457938AImplement access controlAvoid mobilityAssess restrictionLow mobilityCharge control
The invention discloses a user equipment (UE) access restriction method. The method comprises the following steps that: after receiving an access request of the UE, a network side carries position information of the UE when requesting policy and charging control (PCC) from a policy and charging rules function (PCRF); the PCRF determines whether the UE is in an allowable position area scope according to the position information of the UE and notifies the network side when the user equipment is not in an allowable position area scope; then the network side restricts the access of the UE. The invention also discloses a UE access restriction system for realizing the above method. In the invention, through carrying out access restriction management to the UE with a low mobility by a user plane network element, problems of mobility management and charging chaos caused by abnormal moving of the UE with the low mobility can be avoided. Simultaneously, the position information of the UE can be timely reported to a machine type communication (MTC) Server. And the MTC Server can timely process an abnormal mobile event of the UE.
Owner:ZTE CORP
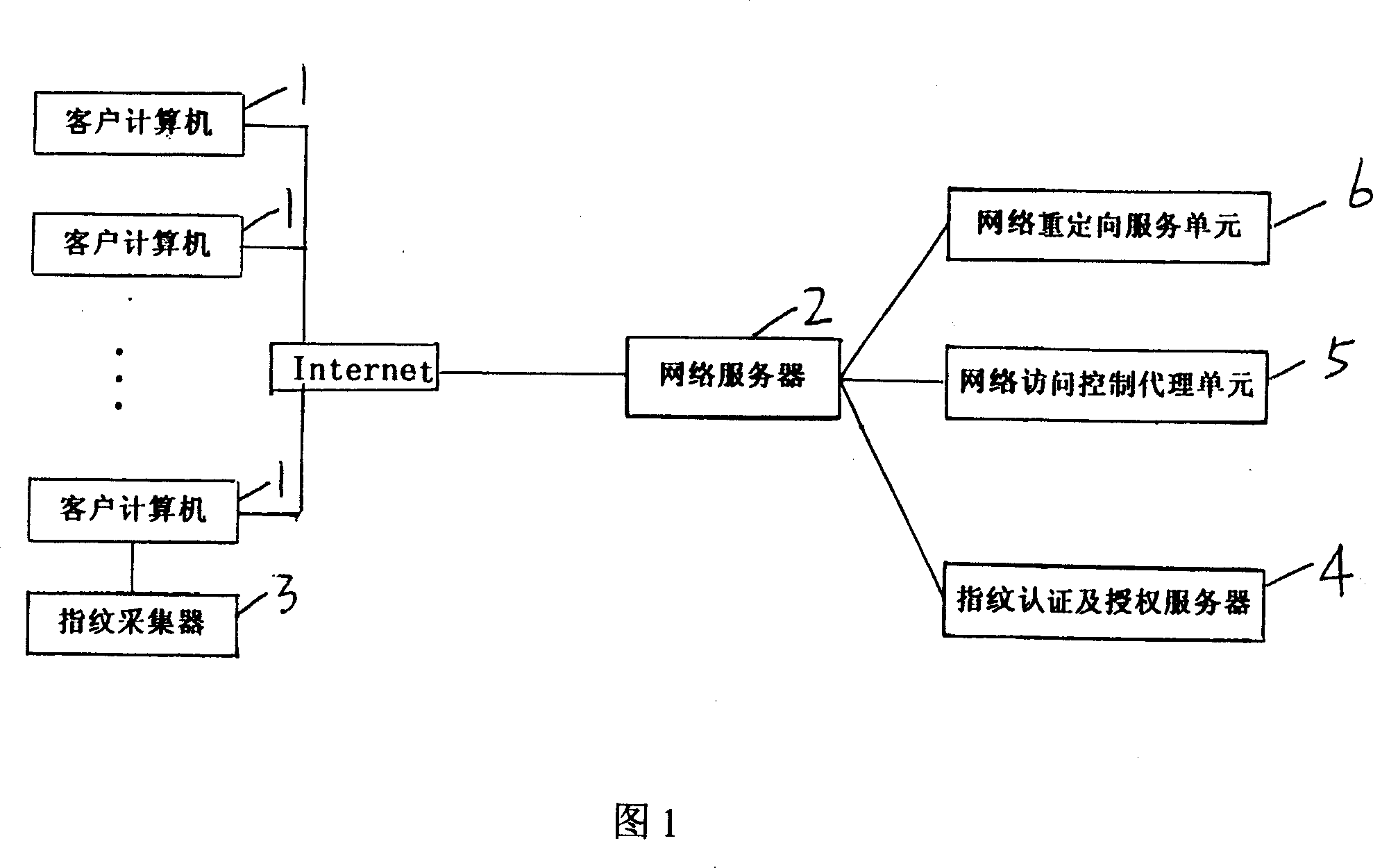
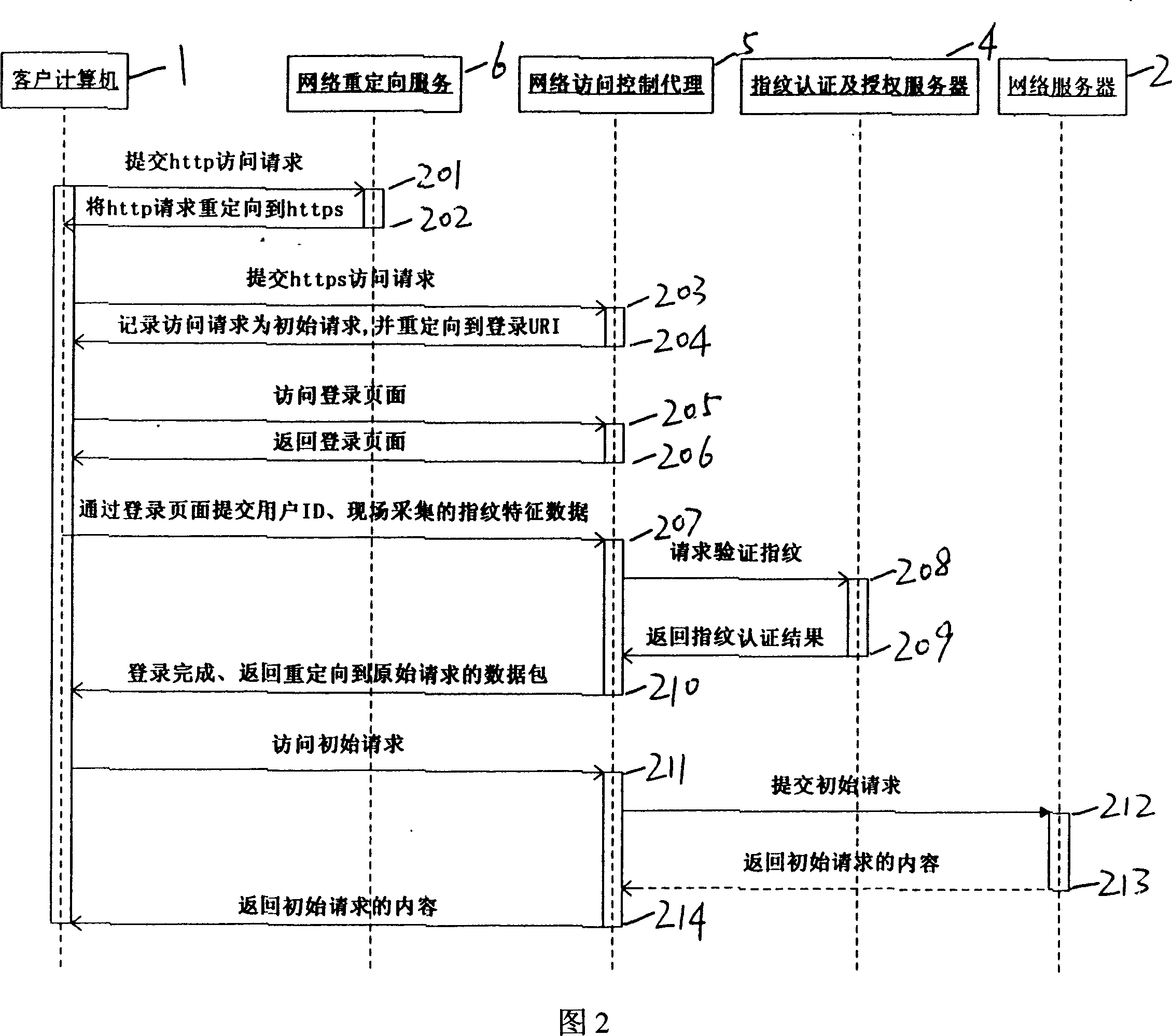
Network access control system and its control method
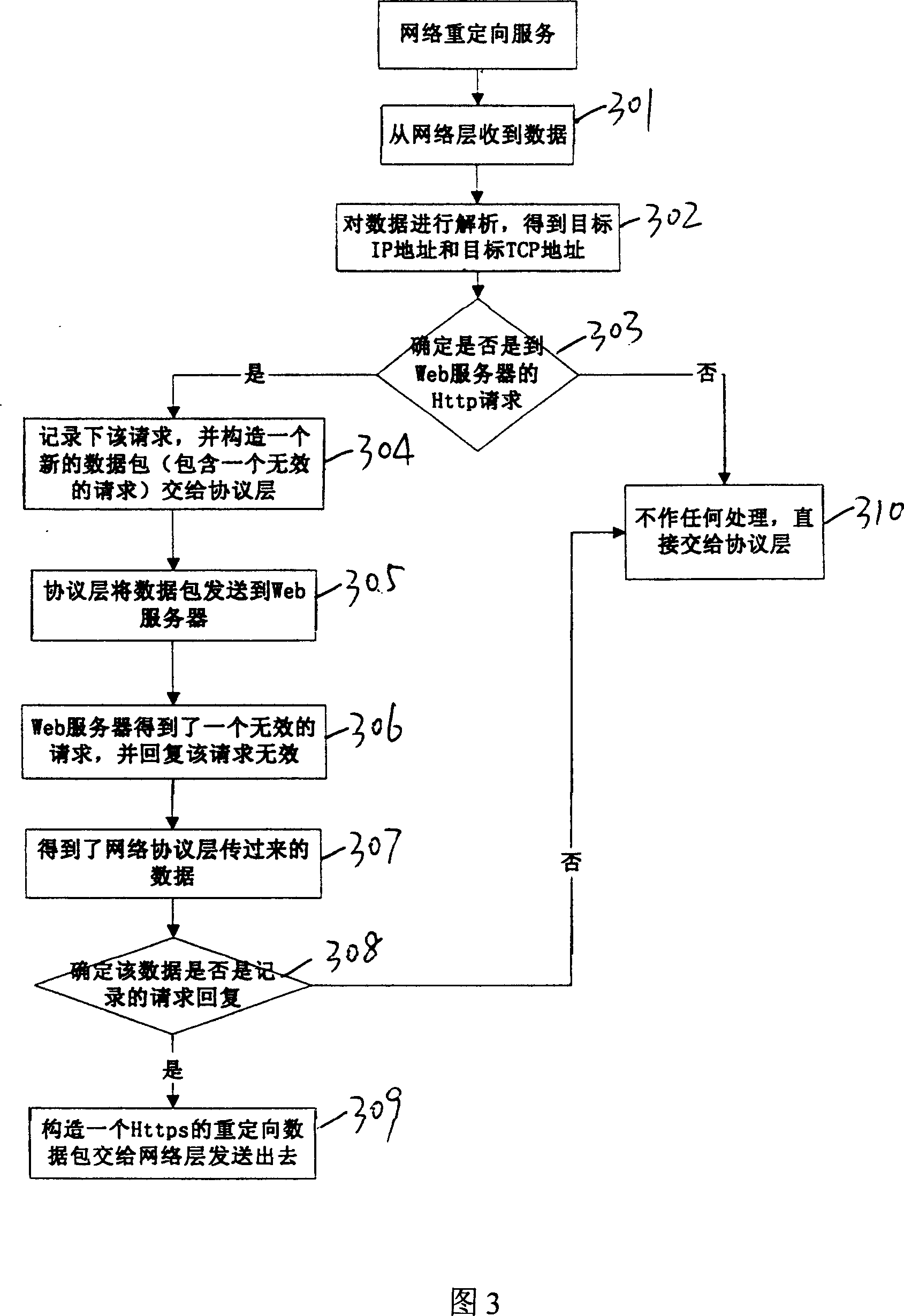
InactiveCN101034981AImplement access controlImprove confidentialityUser identity/authority verificationCharacter and pattern recognitionNetwork access serverInformation transmission
The invention discloses a network access control system, comprising network reorienting service unit and network access control agent unit installed on network server, fingerprint authentication and authorization server connected with the network access control agent unit, and client end computer equipped with fingerprint collector. And the system implements control of the network server access, and has an obvious advantage of being able to complete interactive information encryption between network browser and network server and access control of the network server only in need of simple configuration without changing client's network environment and second development, where the system implements secrecy and integrity of information transmission and interaction by PKI technique, and implements user ID authentication by fingerprint recognition technique, and implements access control of the network server by united access authorization mechanism.
Owner:上海品伟数码科技有限公司
Method and device for access control
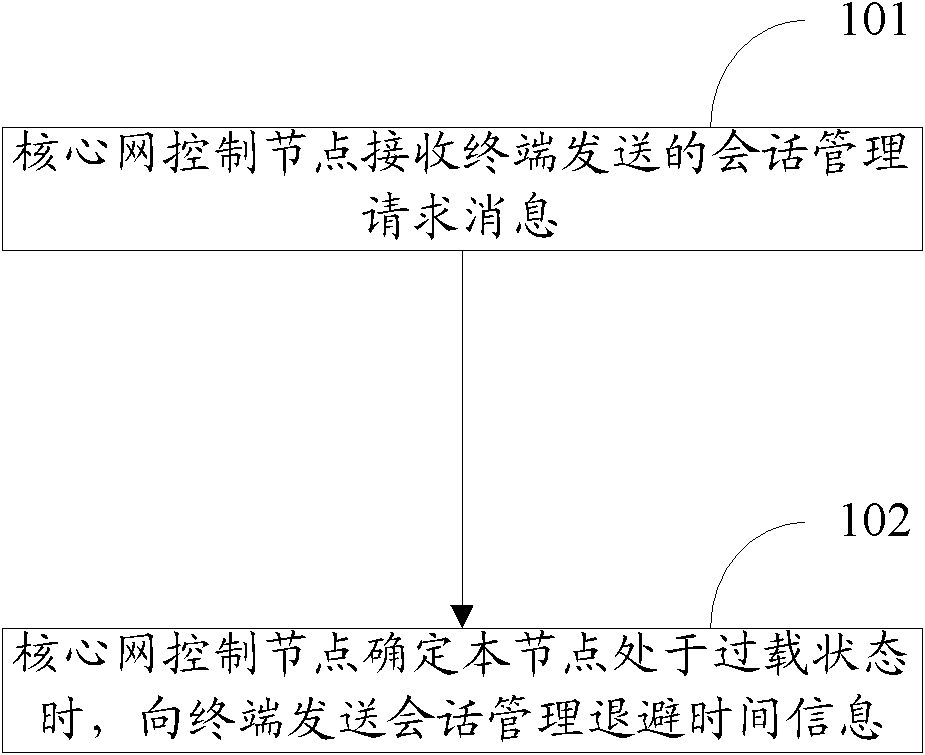
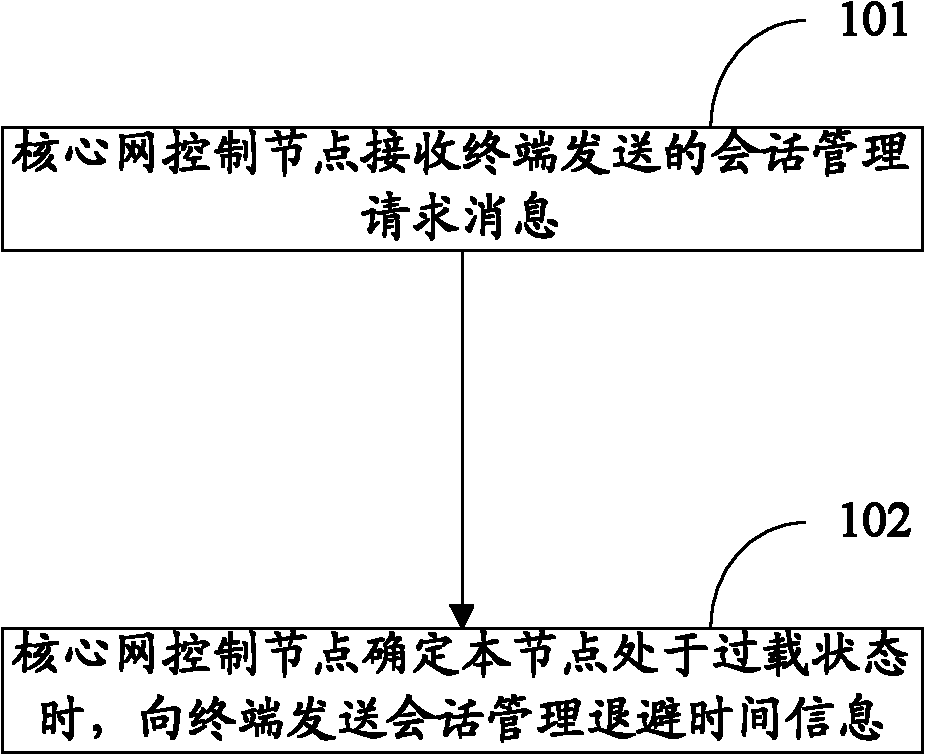
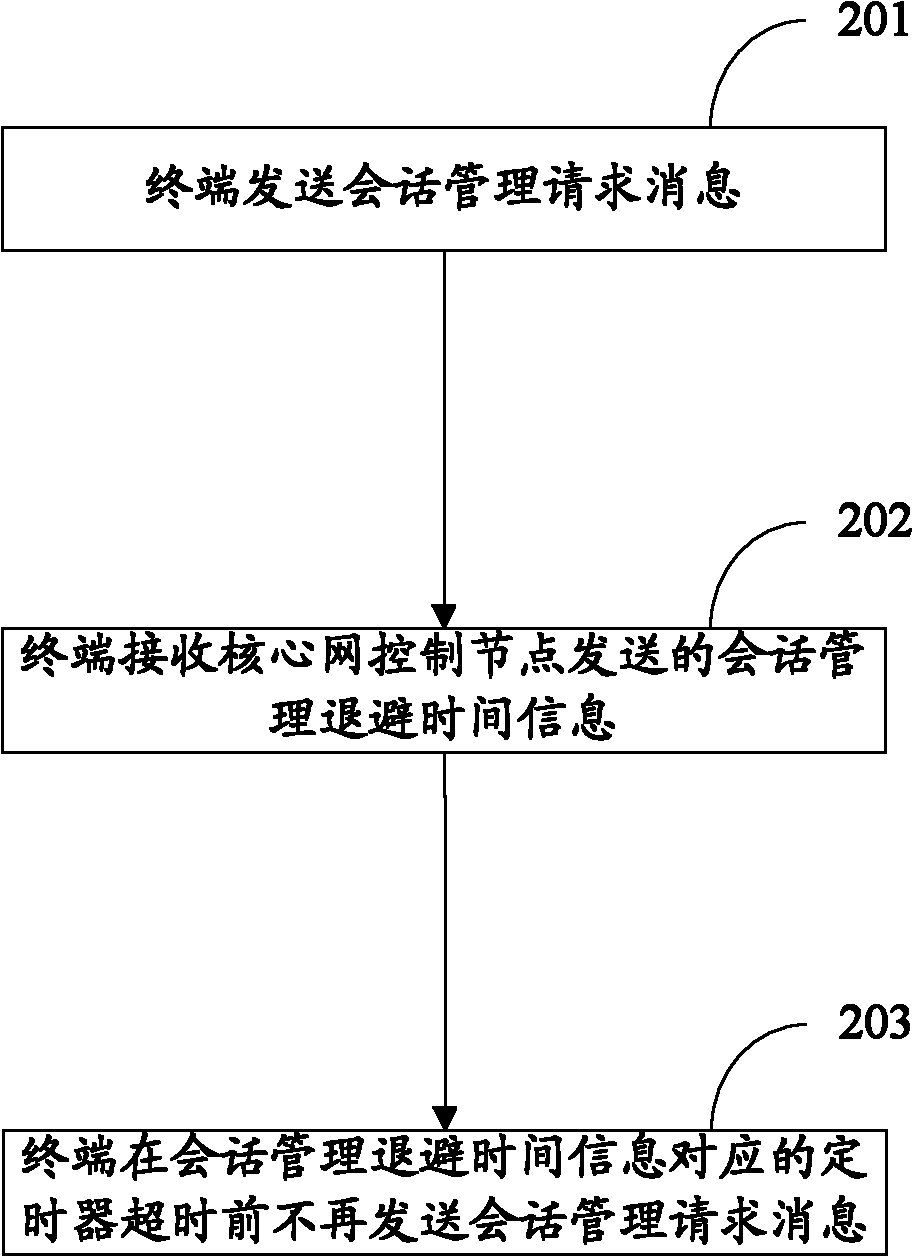
PendingCN102098759AImplement access controlImprove the SessionManagementCongestionControl mechanismAssess restrictionConnection managementSession managementMedia access control
The invention discloses a method for access control for realizing excellent access control. The method comprises the following steps: a core network control node receives session management request messages sent by a terminal; and the core network control node sends session management back-off timer messages to the terminal when the core network control node determines that the node is in an overload state. The invention further discloses a device for realizing the method.
Owner:CHINA ACAD OF TELECOMM TECH
Wireless local area network (WLAN) access control method and device thereof
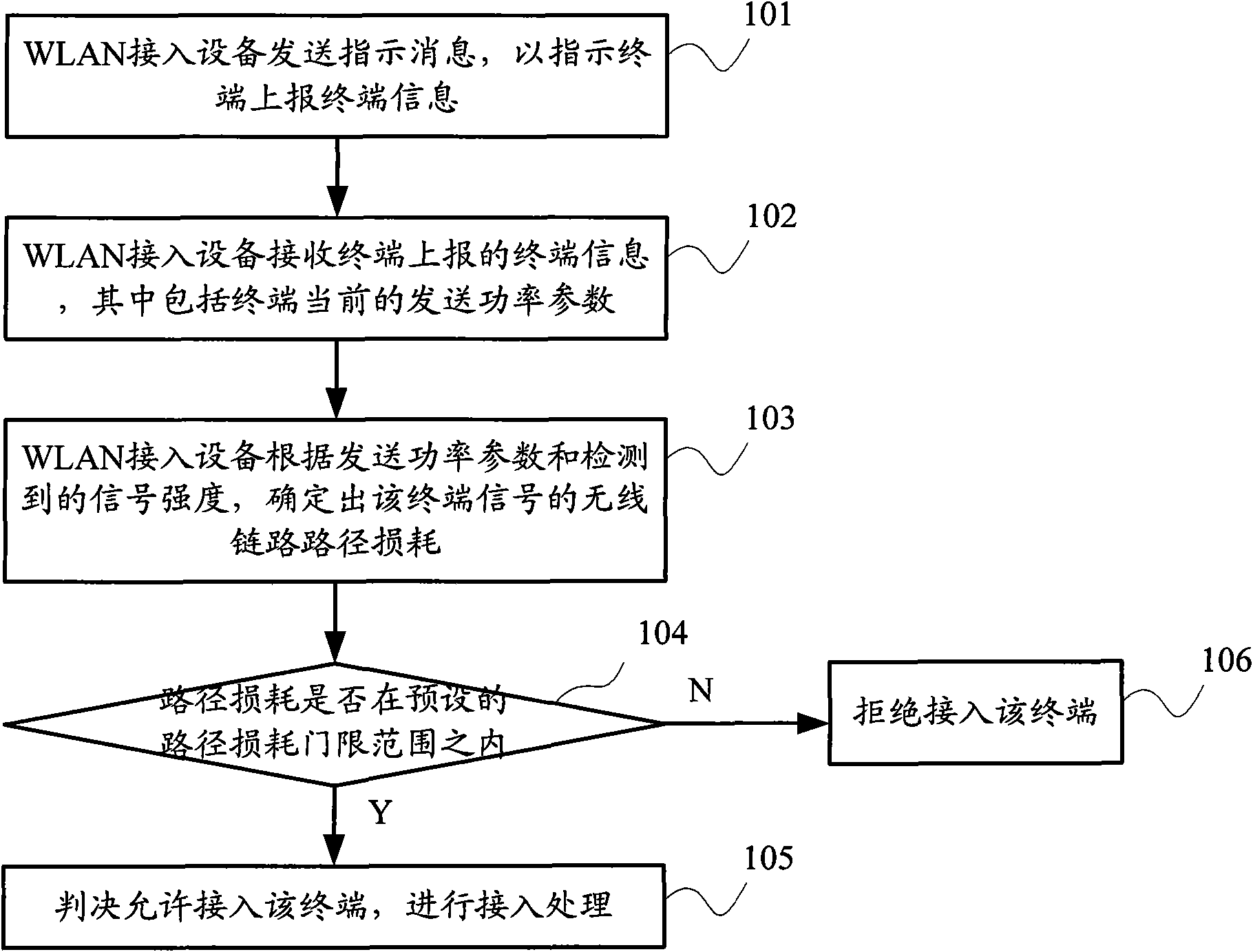
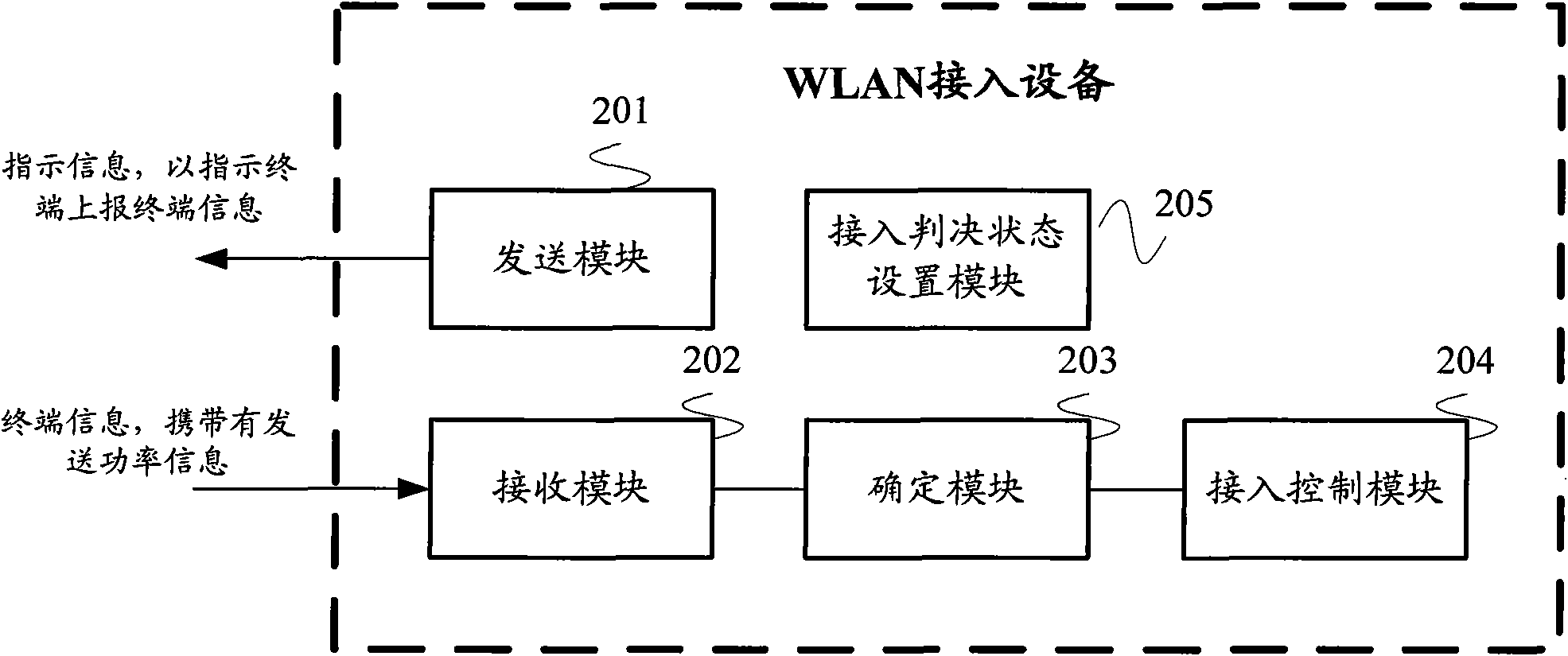
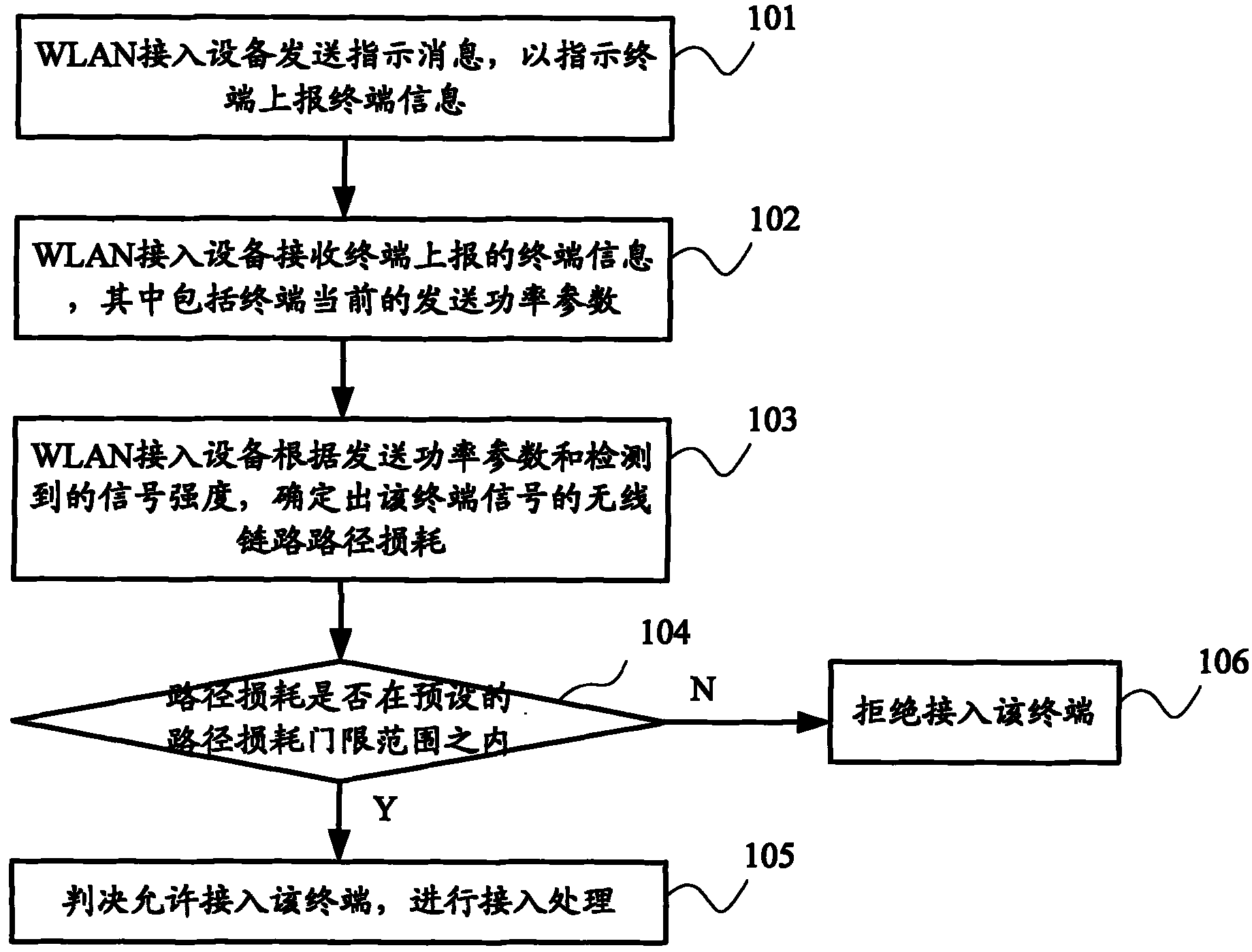
InactiveCN101959282AImplement access controlEasy to operatePower managementAssess restrictionTelecommunicationsControl treatment
The invention discloses a WLAN access control method and a WLAN access control device. The method comprises the steps that: when WLAN access equipment is in an access judgment state, an indicating terminal reports terminal information; a receiving terminal of the WLAN access equipment receives the terminal information reported according to indication, wherein the terminal information carries the current sending power information of the terminal; the WLAN access equipment determines the wireless link route loss of the terminal according to signal intensity when the terminal information is received and the sending power information in the terminal information; and the WLAN access equipment judges the access of the terminal according to the wireless link route loss and an access judgment threshold, and enters control treatment according to a judgment result. When the method and device are used, the security of WLAN access can be improved and access control operation can be simplified.
Owner:NEW H3C TECH CO LTD
Ethernet confirming access method
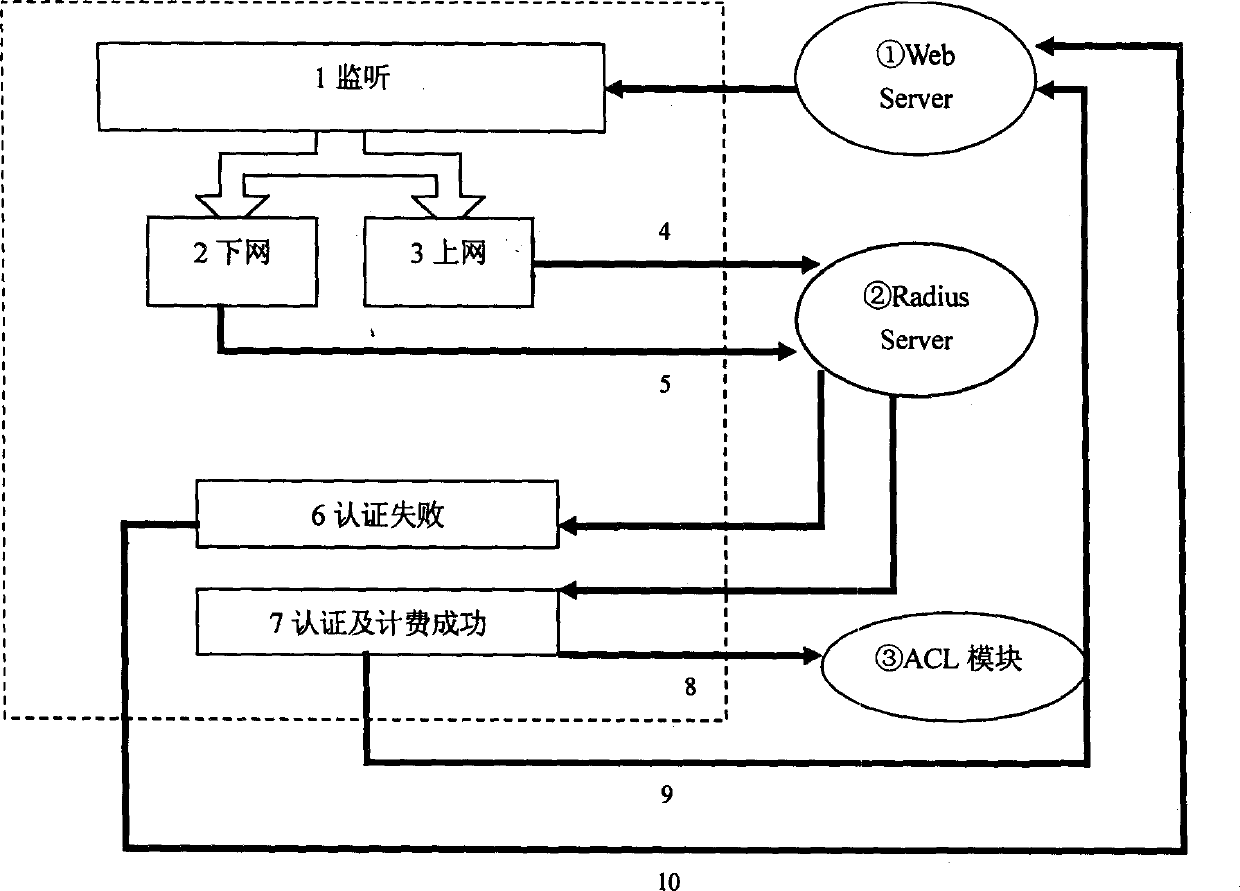
InactiveCN1403952ABandwidth controlEnsure normal communicationData switching networksSpecial data processing applicationsOperational systemAccess method
The Ethernet confirming access method is a wideband access method for computer network. The present invention adopts unique double web page server technology, and performs the access control and bandwidth limitation via the user access list operation. The unique forced entrance guard technology can re-orient the unauthorized user request imperatively. The present invention realizes the conformation, authorization, charge and bandwidth limitation of users via web page confirming process without needing any client end software, and this simplifies the user's operation, is independent with the user's operation platform and can operate simple and practically.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Trusted network access and access control system and method
ActiveCN104618396AImplement access controlImplement network access controlUser identity/authority verificationNetwork access serverNetwork Access Protection
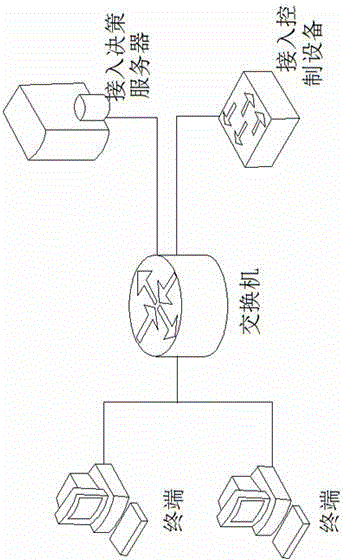
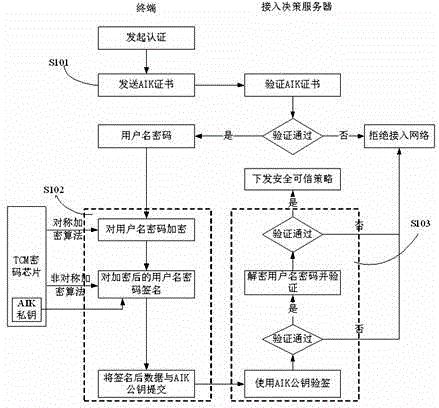
The invention discloses a trusted network access and access control system. The control system comprises a network access requester, a network access decision-maker and a network access controller. When the network access requester accesses to the network, platform identity authentication is carried out, and secure and trusted states of the requester are detected; the secure and trusted states are sent to the network access decision-maker, and the decision-maker judges the secure and trust level of the requester and gives a network access decision; the network access decision is sent to the network access controller, and the controller limits the requested network access. The invention further discloses a trusted network access and access control method. The control system carries out the platform identity authentication on the basis of TCM and ensures the network access control while avoids identity forging. Network areas are divided on the basis of a digital label technology and dynamically updated, network self-adaption is realized, and the access security of different logical areas is ensured. Secure and trusted strategies are configured, and combined with the TCM cryptographic algorithm, so that the security and credibility of the platform state of the requester are ensured.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Radio sensor access control method based on key chain
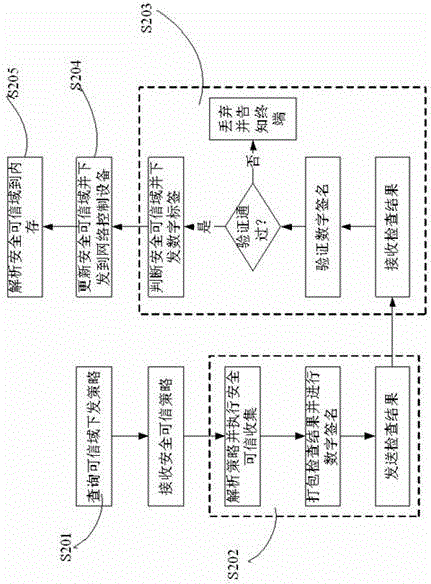
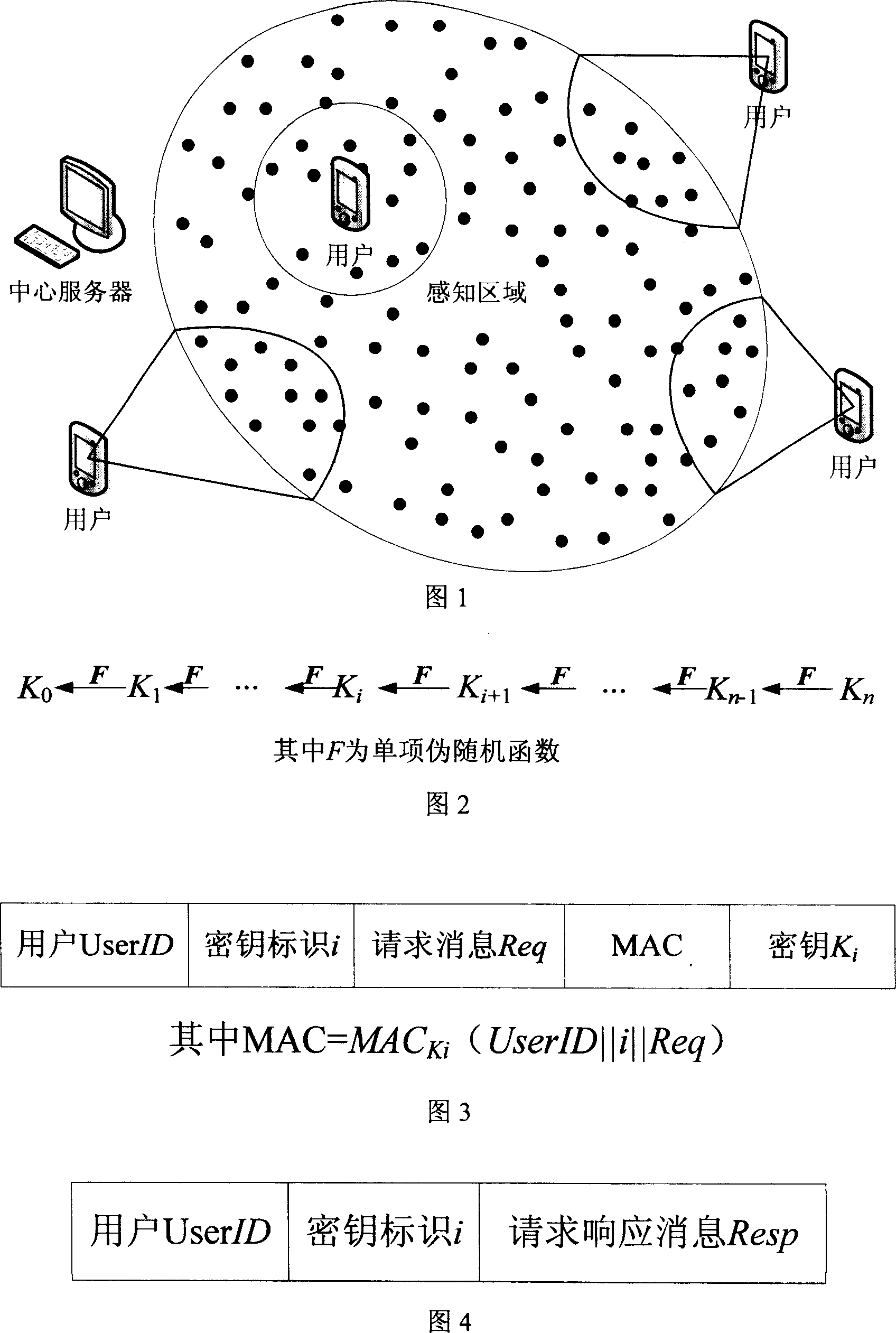
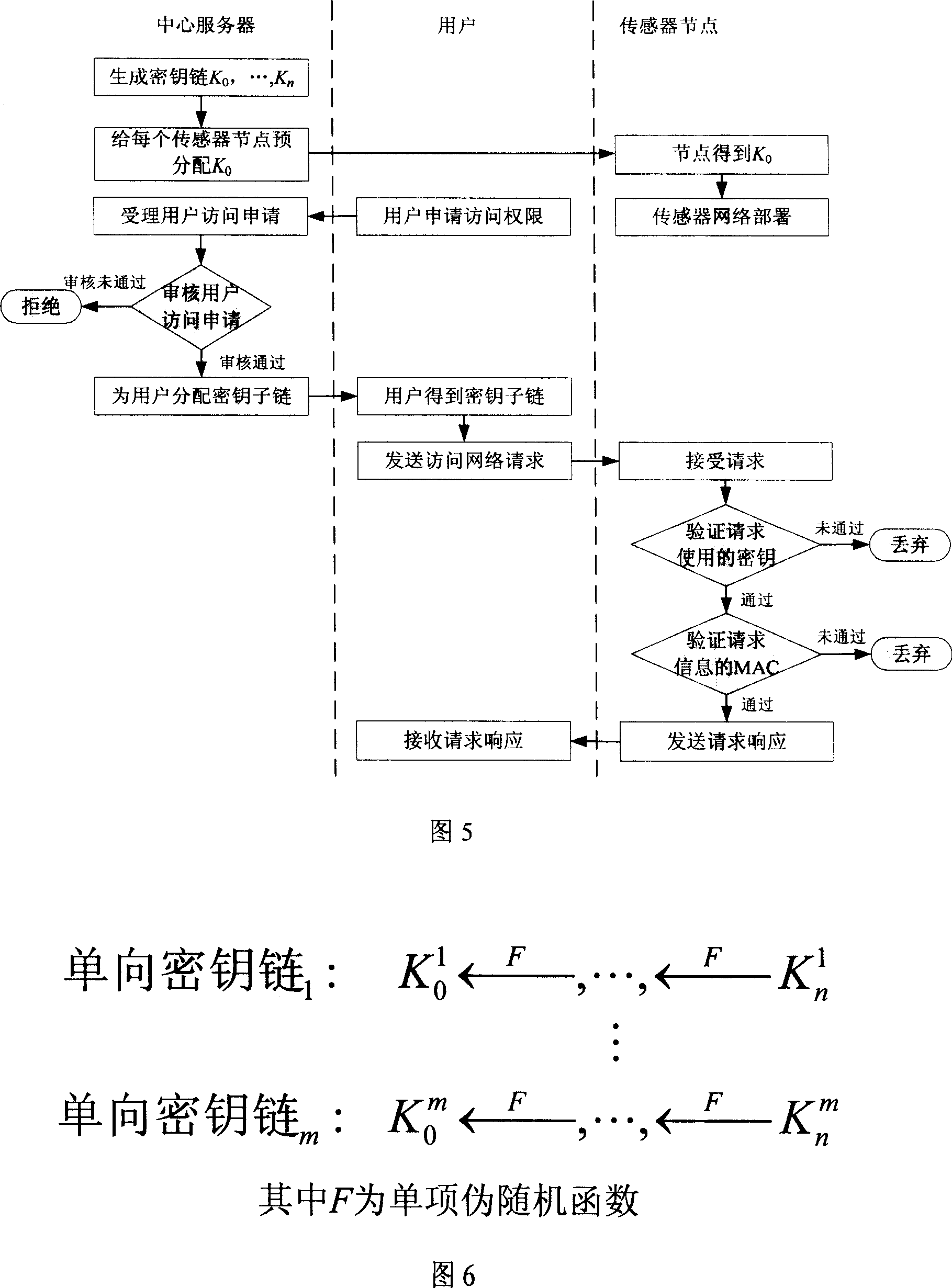
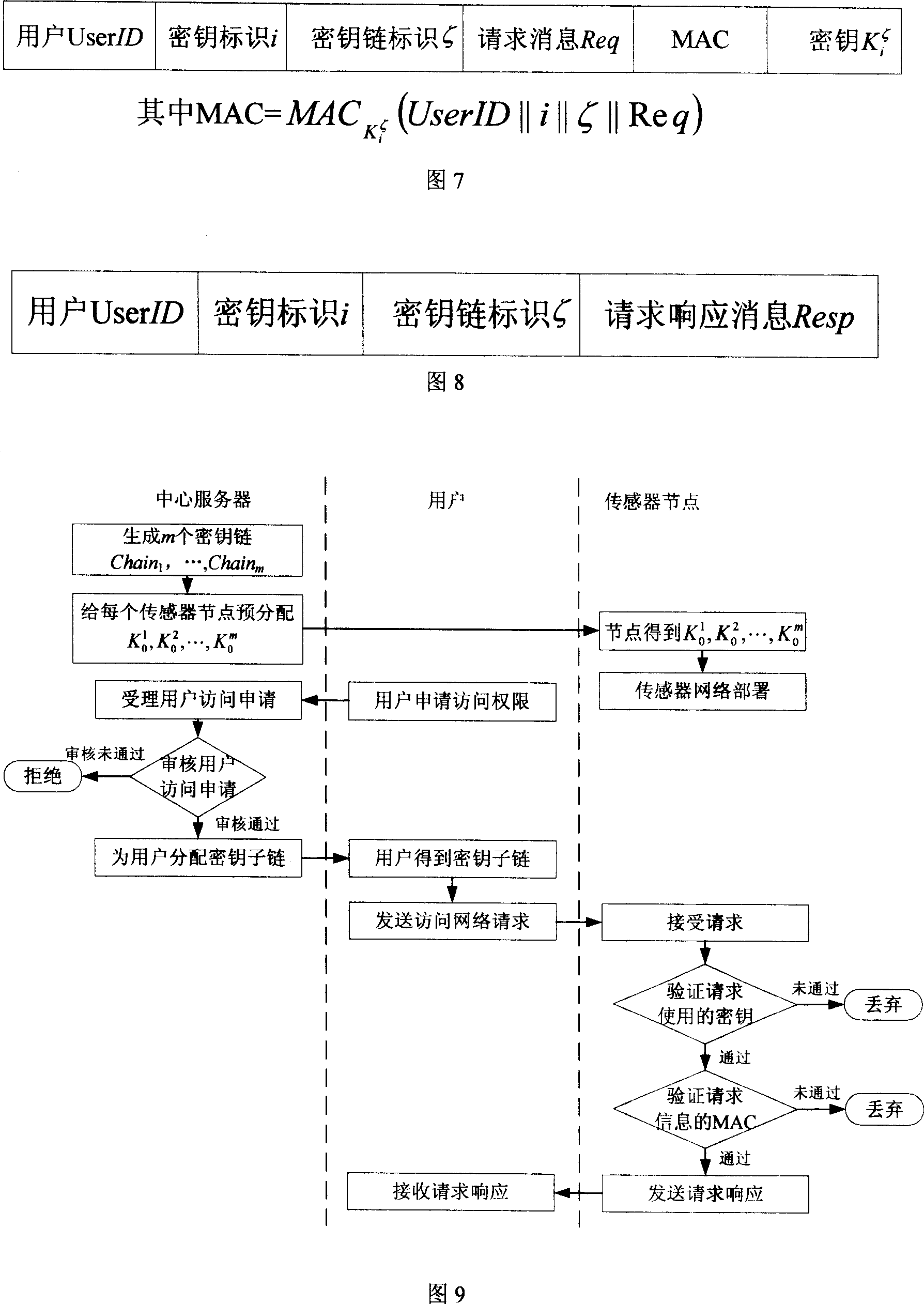
InactiveCN101005459AImplement access controlReduce computational overheadKey distribution for secure communicationUser identity/authority verificationLine sensorExtensibility
The invention is based on five highly-effective sensor network access control modes: which are one-way key chain access control, multi key chain access control, Merkle tree-based access control, expanded Merkle tree access control, and an mode of canceling the key chain of captured users with Merkle. The method uses said five access control modes to reduce the storage expense of sensor node and increase the flexibility and expandability of access control so as to support mass users to access network. The invention is compatible with current sensor network data broadcast protocol.
Owner:XIDIAN UNIV
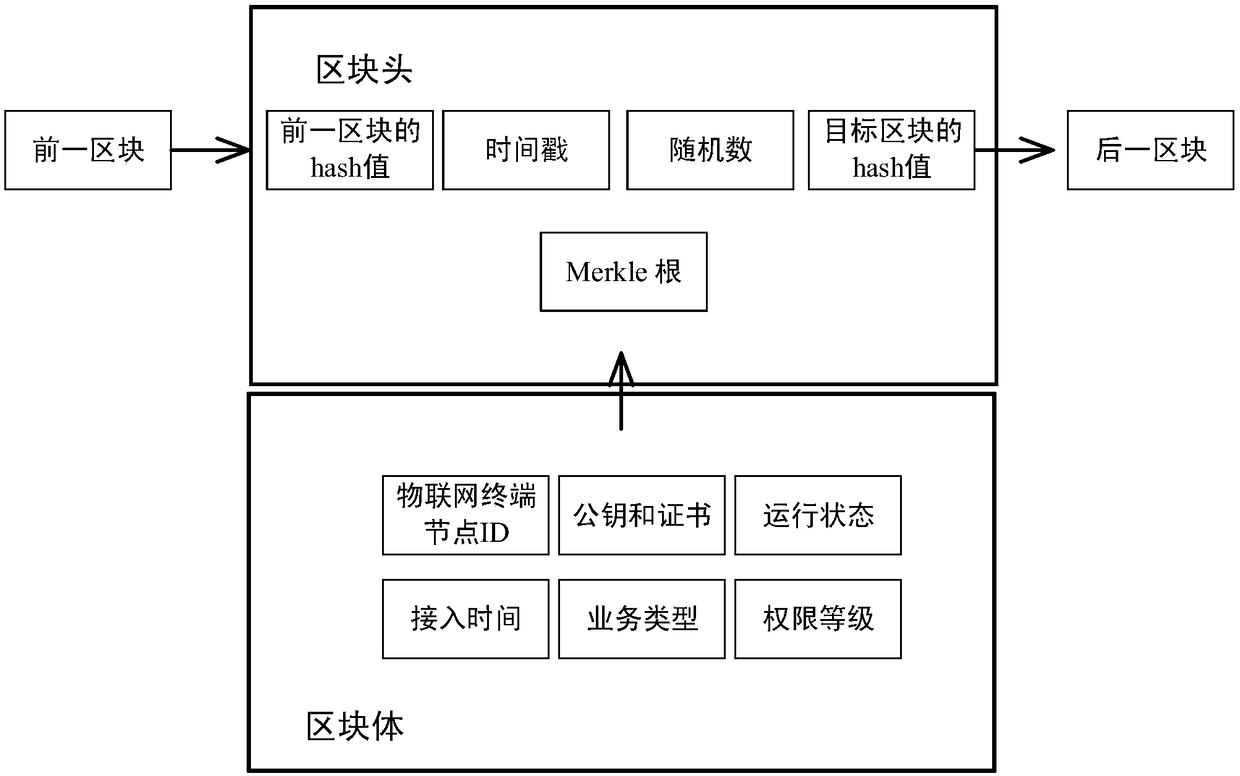
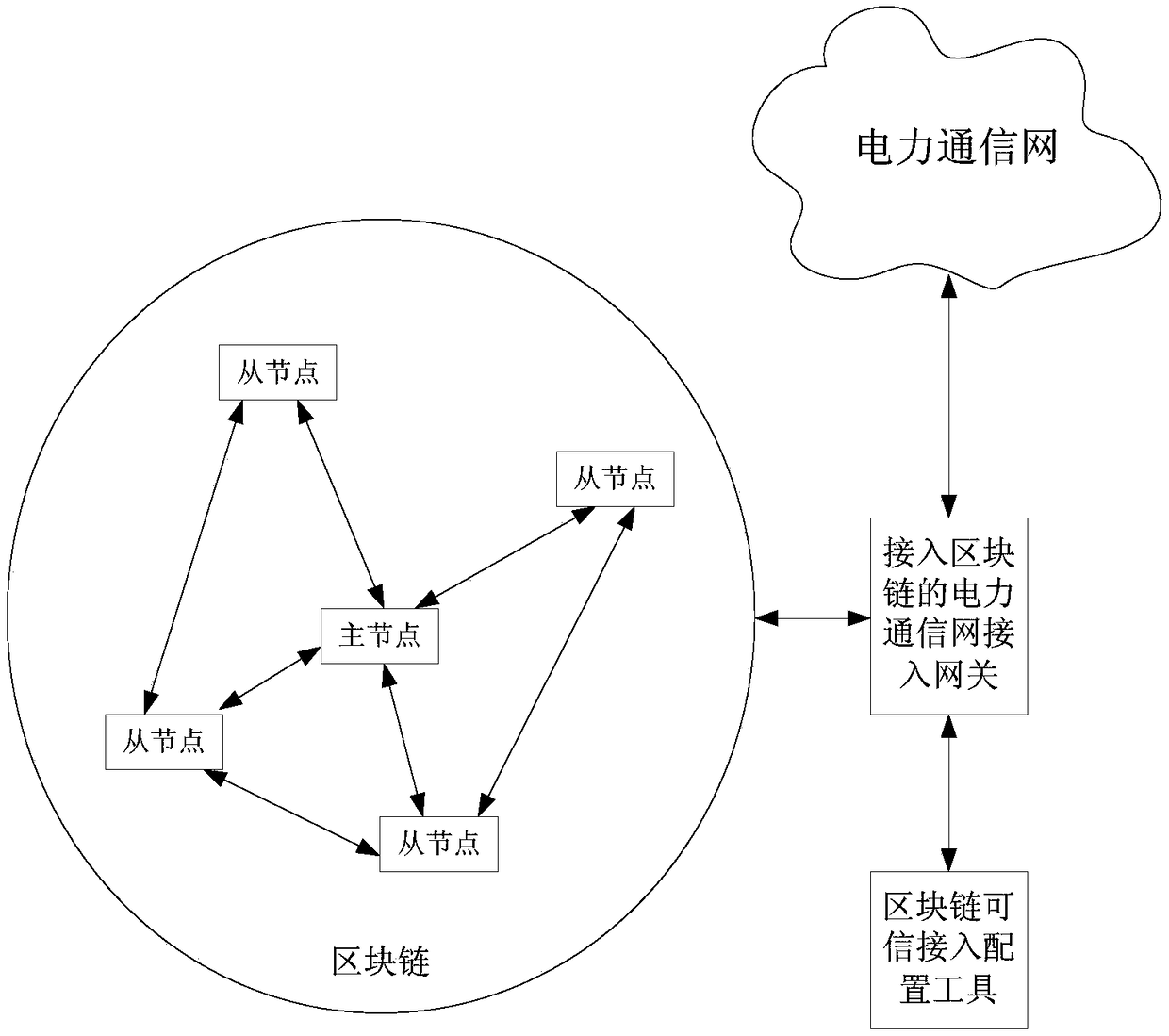
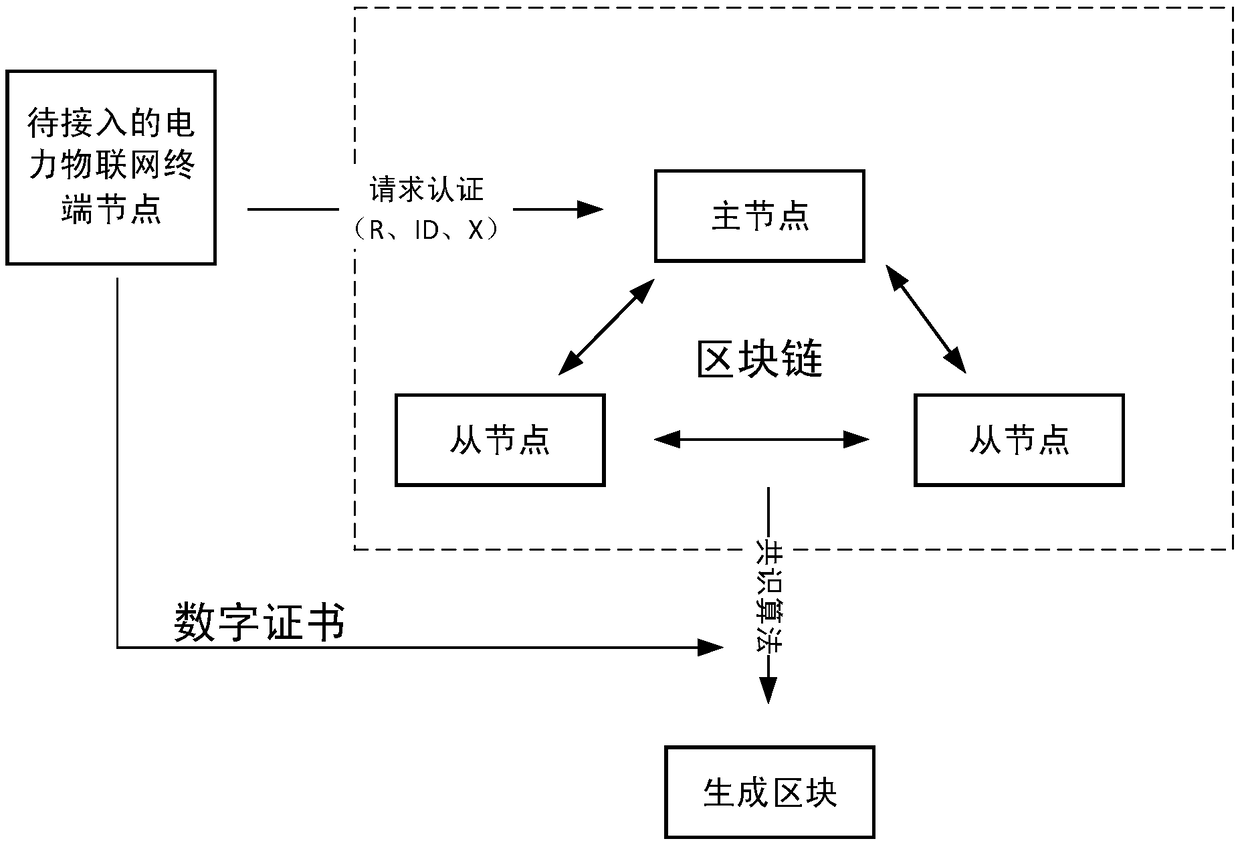
Block chain-based method for accessing power Internet of Things terminal
InactiveCN109495516AReduce communication pressureReduce computing pressureKey distribution for secure communicationUser identity/authority verificationAccess methodCiphertext
The invention provides a Block chain-based method for accessing a power Internet of Things terminal, comprising the steps of: connecting a to-be-accessed power Internet of Things terminal to a masternode, and initiating an authentication request; the master node responding to the authentication request, and randomly selecting nodes that meet the condition of a threshold number from the block chain to form an authentication group; encrypting a public key G and an identity ID of the to-be-accessed power Internet of Things terminal by using a private key to obtain a digital signature ciphertextX, and sending the identity ID, a terminal public value R and the digital signature ciphertext X to the master node; the master node encapsulating and sending the authentication request information toa member node of the authentication group; the authentication group running PBFT consensus algorithm, and obtaining an authentication result by performing distributed authentication through two-two exchanging of the authentication information between the nodes of the authentication group; generating a new block in the block chain, and returning confirmation information to the to-be-accessed powerInternet of Things terminal; and the power Internet of Things terminal returning encrypted confirmation information to an access gateway. The block chain-based power Internet of Things terminal access method can improve the security and efficiency of authentication.
Owner:JIANGSU ELECTRIC POWER CO
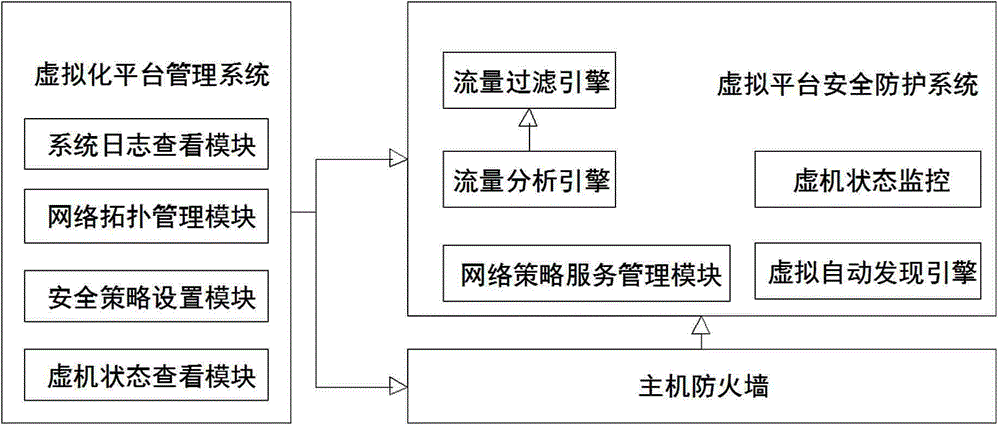
Virtual platform information security protection method
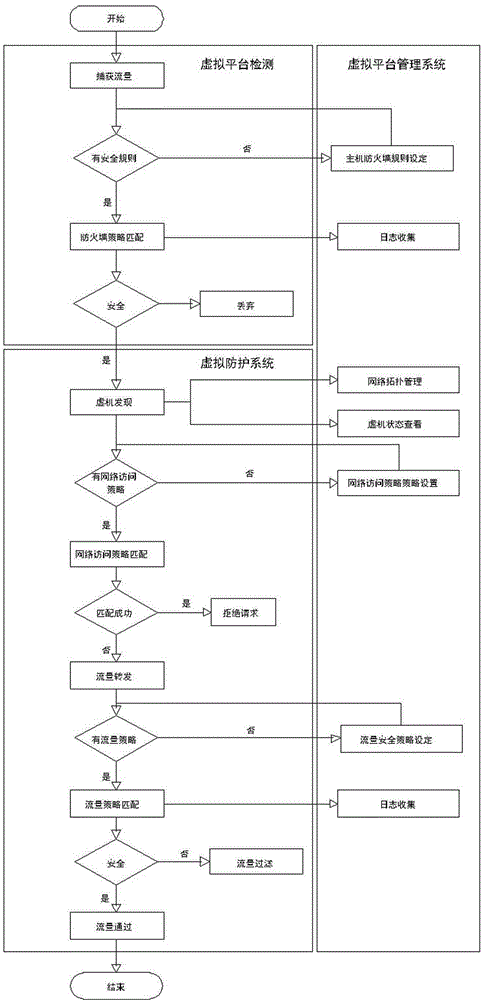
InactiveCN104378387AImplement access controlMeet customized development needsTransmissionProtection layerProtection system
The invention discloses a virtual platform information security protection method. The method includes setting a virtual platform detection system, a virtual platform protection system and a virtual platform management system; acquiring network traffic, and performing host firewall security rule matching on the traffic through the virtual platform detection system; allowing a virtual interpreter to forward the matched traffic on the hypervisor layer of the virtual platform protection system, judging whether a set network access control strategy is met or not through a virtual platform protection layer after forwarding, and refusing to forward if the strategy is met; analyzing traffic information without limitation, when a traffic security strategy is not met, filtering the traffic. Compared with the prior art, the method had the advantages that the access control between virtual machines can be implemented; by means of QoS arrangement, VLAN classification and traffic filtering functions, the probability of malicious traffic communication can be reduced.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Wireless network medium access control system and channel parameter regulation method
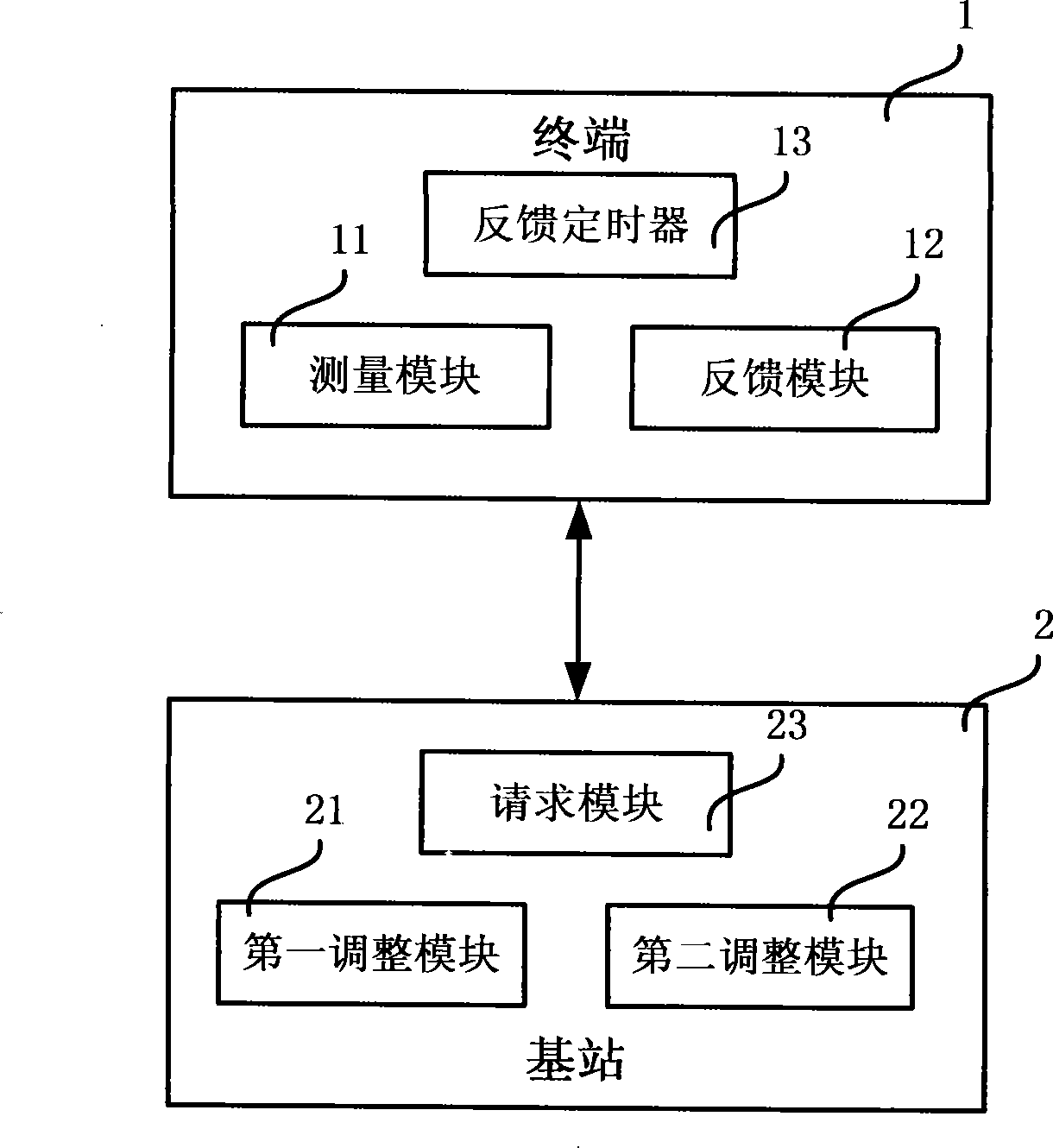
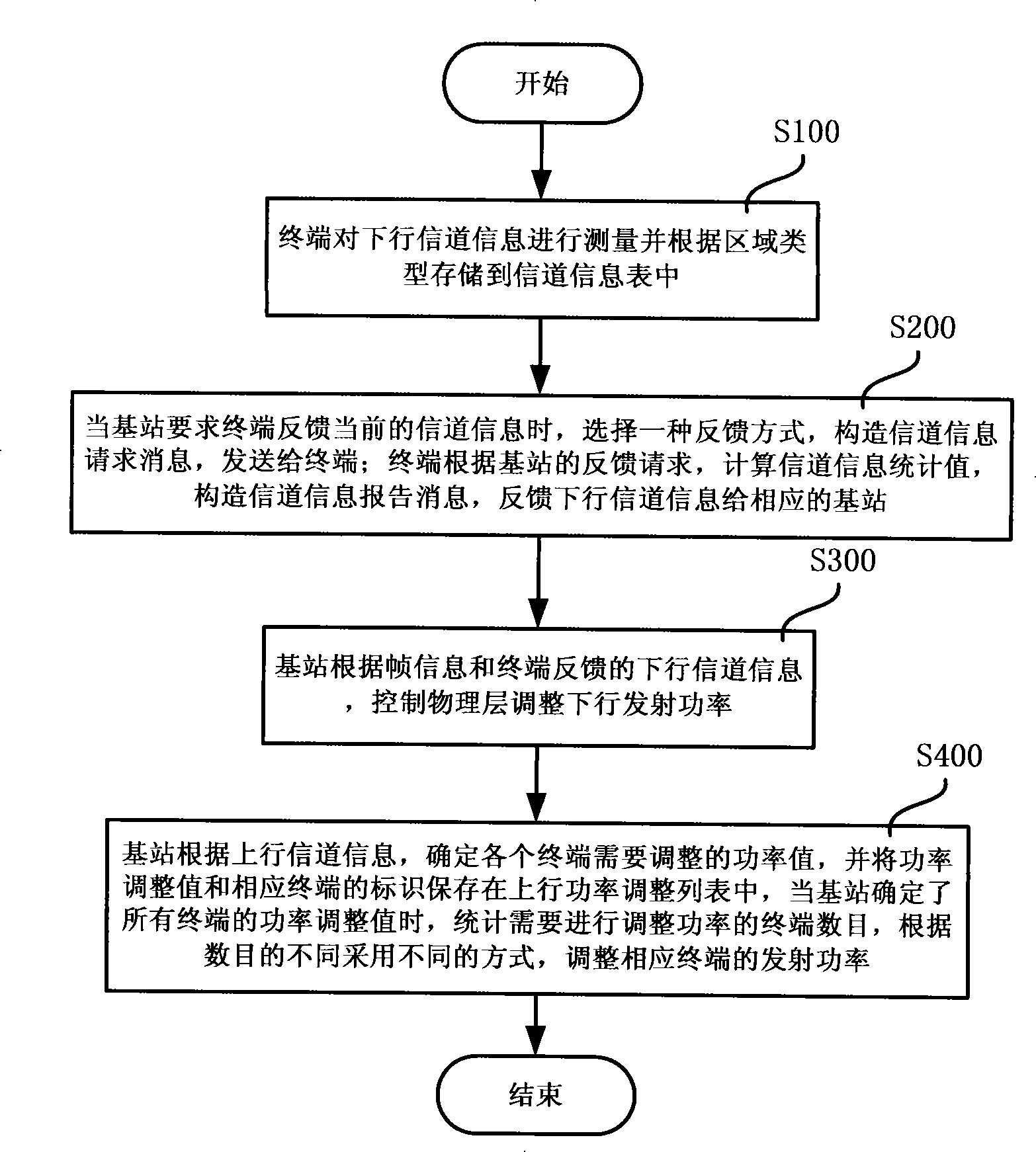
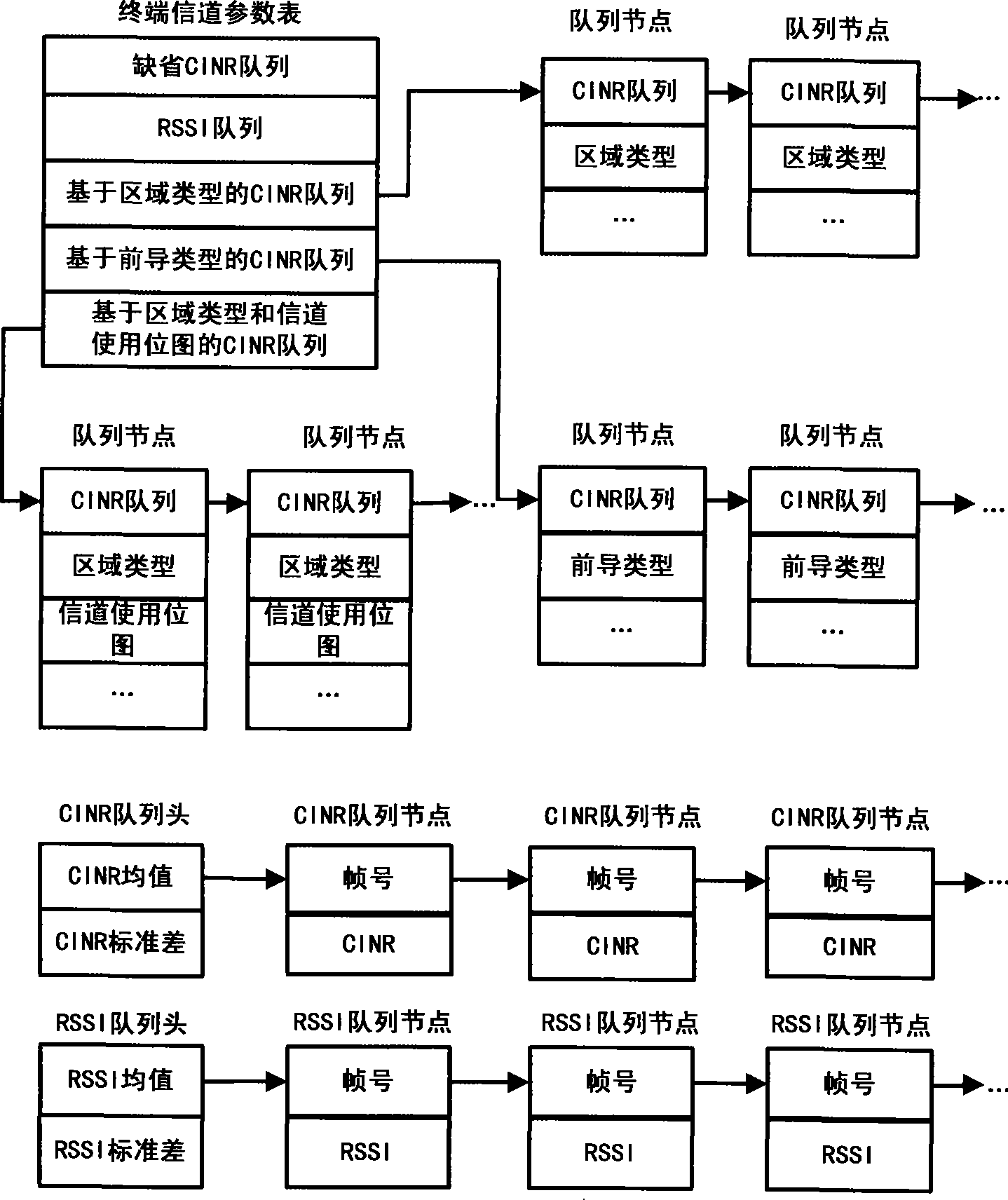
ActiveCN101252379AImplement access controlTransmission control/equalisingRadio transmission for post communicationChannel state informationChannel parameter
The invention discloses a wireless network media access control system and the channel parameter adjusting method of the system. The system comprises a base station and a terminal; the terminal comprises a measuring module used for measuring the downlink channel information and storing the channel information in the channel information table and a feedback module used for calculating the channel information statistical value, constructing the report message of the channel information and sending the feedback report message to the corresponding base station; the base station comprises a request module used for selecting a feedback mode, constructing the request message of the channel information and sending the request message to the terminal when the base station requests the terminal to send the current feedback channel information; the base station comprises a first adjustment module used for controlling the physical layer to adjust the downlink transmission power and a second adjustment module used for determining the power value needed to be adjusted of each terminal, storing the power adjusted value and the identification of the corresponding terminal in the uplink power adjustment table, counting the number of the terminals needed to be adjusted in power and adjusting the uplink transmission power of the corresponding terminal. The wireless network media access control system and the channel parameter adjusting method of the system make the wireless network media access control be well realized.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
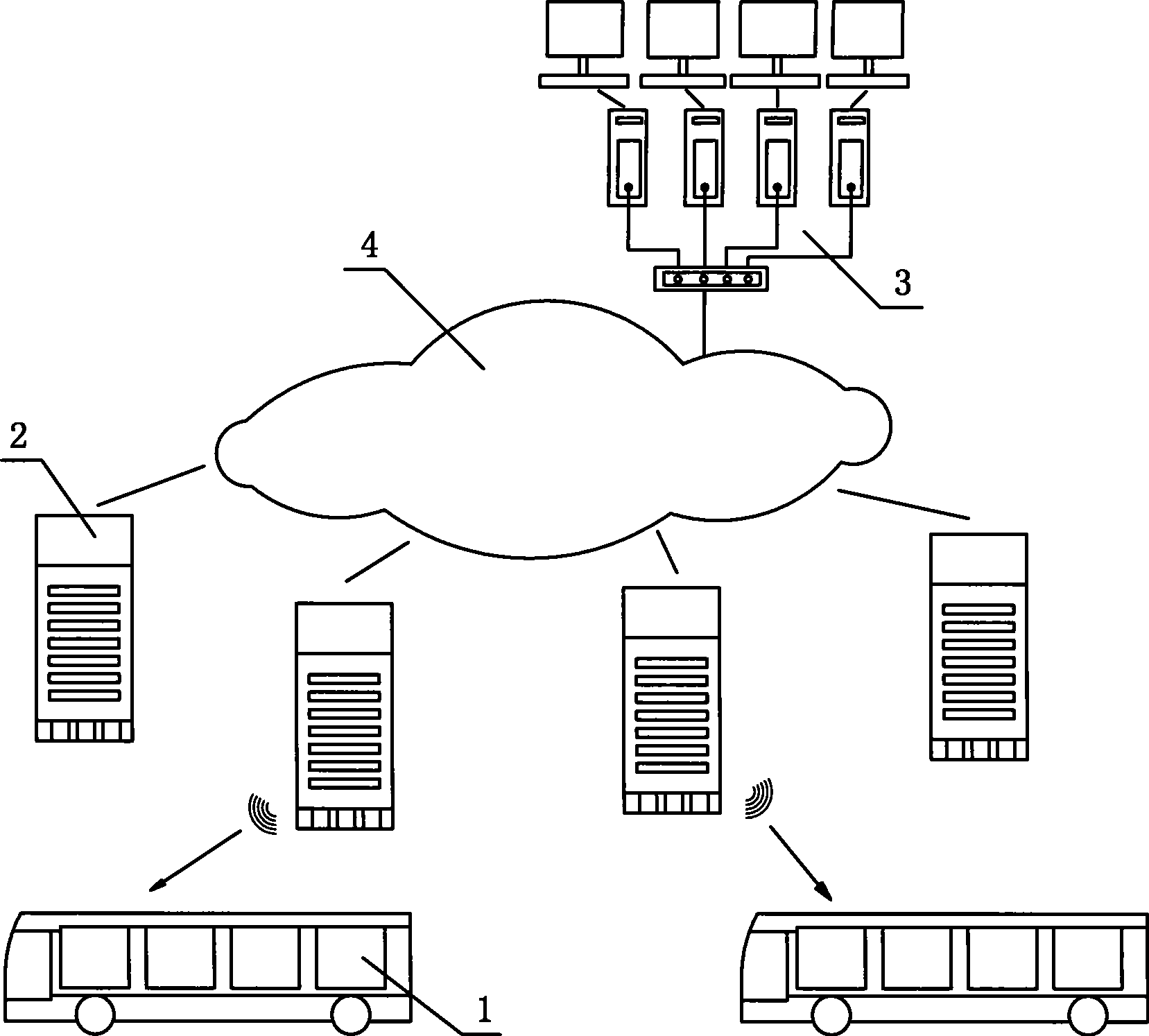
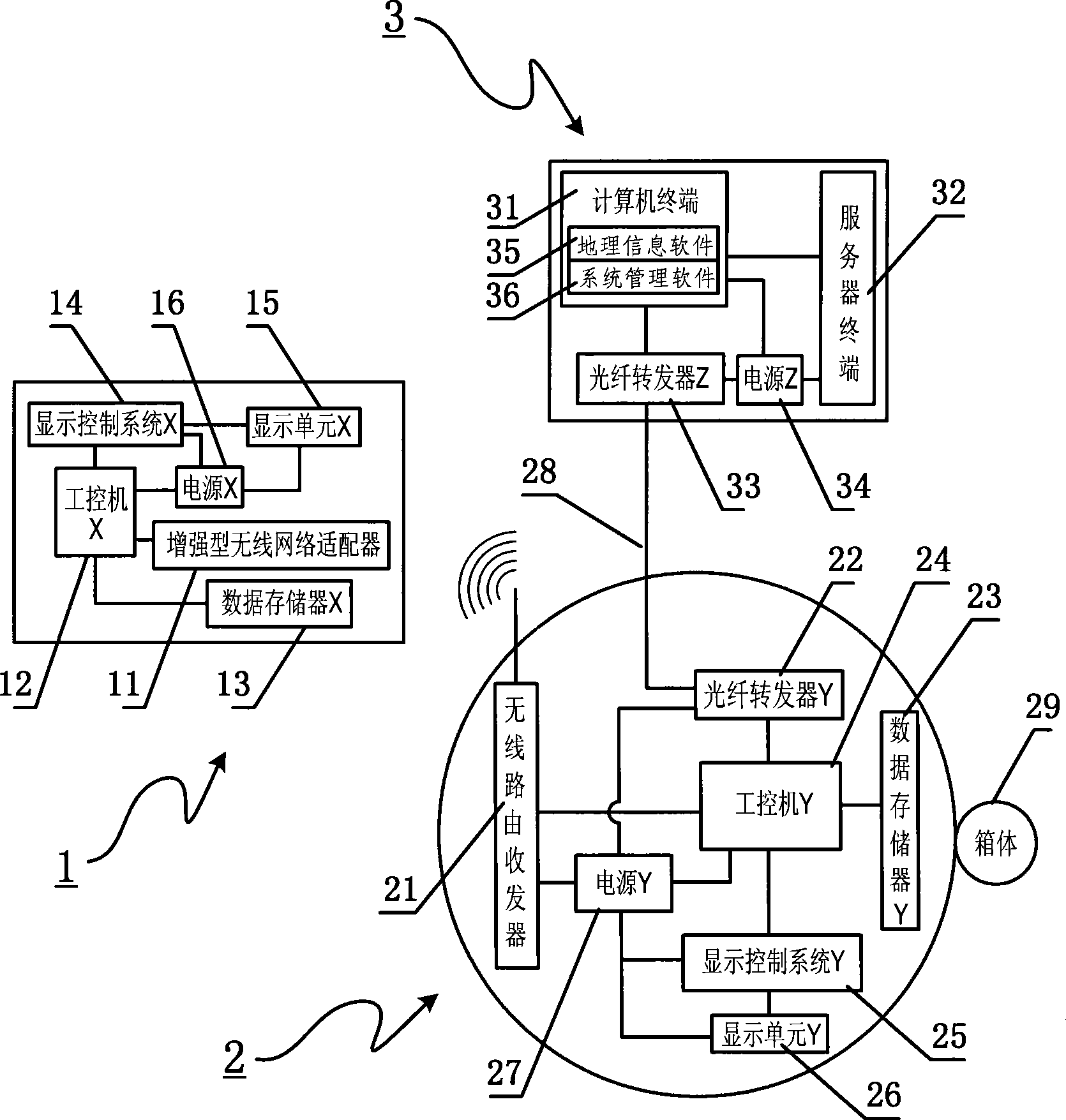
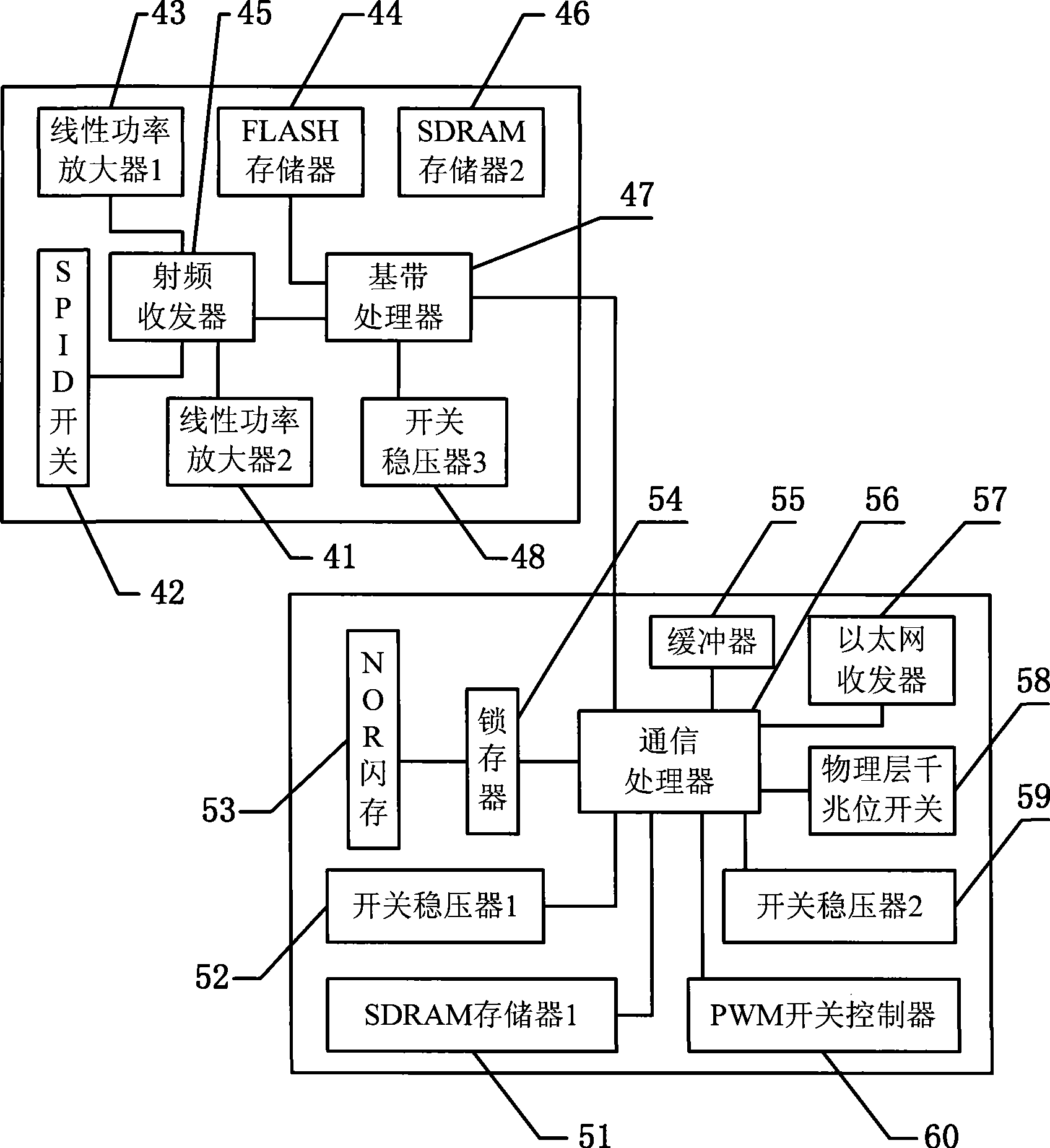
Digital public transport information publishing and cluster controlling method and device
InactiveCN101398975AWide coverageIntegrity guaranteedDetection of traffic movementTelecommunications linkEngineering
The invention relates to a method used for digital bus information releasing and group control and a device thereof. The technical measure comprises the following steps: a vehicle terminal system, an electronic station board system and a vehicle technical information management centre are arranged, the electronic station board system is the vehicle technical information management centre are connected into a bi-directional communication network by line link, the vehicle terminal system transmits the vehicle information to the electronic station board system in a wireless communication, the electronic station board system reports the information to the vehicle technical information management centre, the bus coming to station at each station can be found out by inquiring a database, the station arriving time of the bus is calculated according to experimental data including average running speed, average running time between the stations and the like, finally, the arriving time is fed back to the electronic station board system, and the arriving time is displayed to the waiting passengers in a digital way. The method can effectively solve the problems of bus reduction in city and dispatching, information releasing, passenger facilitation, intelligent management control and the like. Therefore, the method realizes intelligent bus dispatching.
Owner:JIANGSU HANDSON INTELLIGENT TECH CO LTD
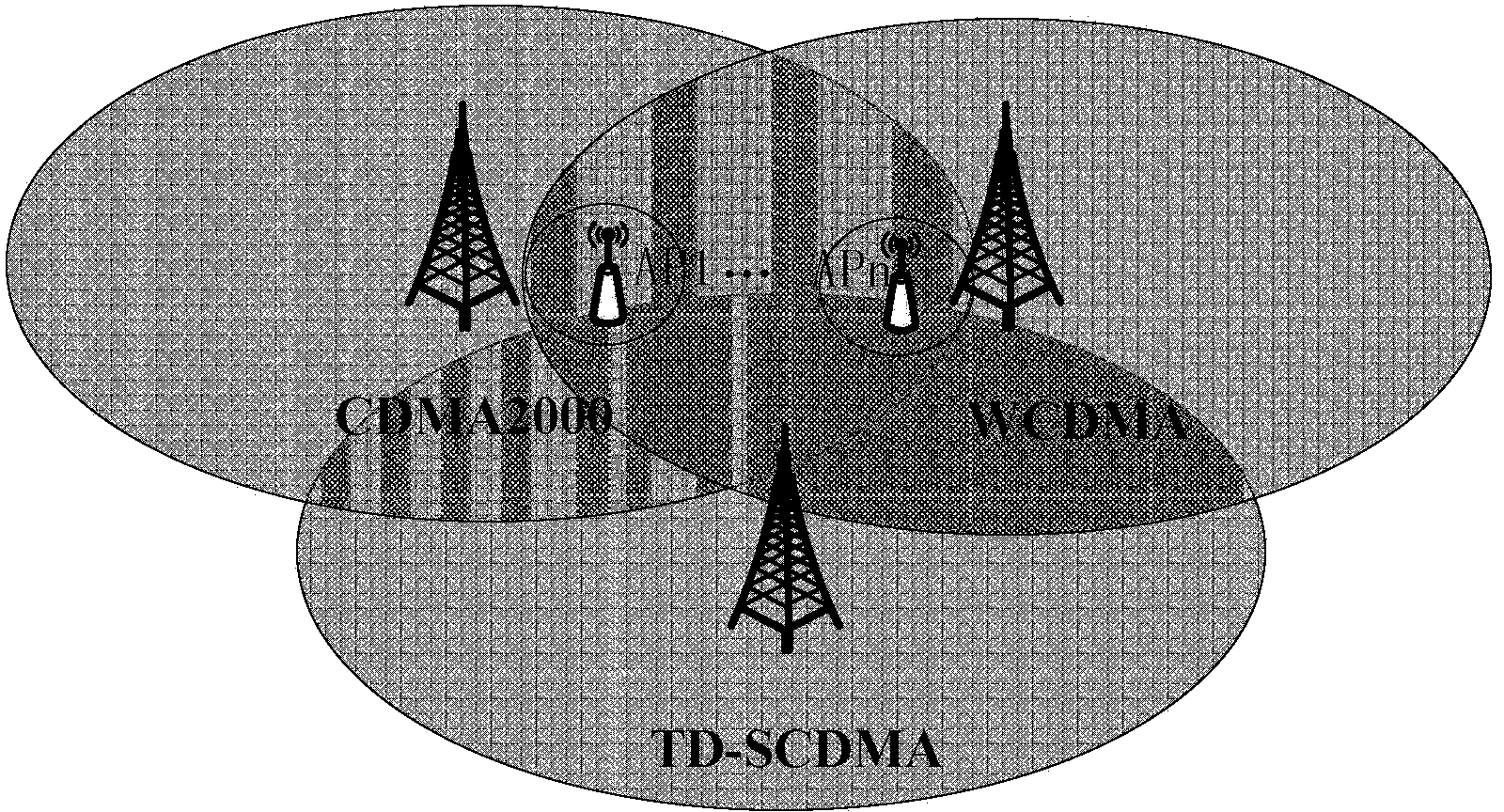
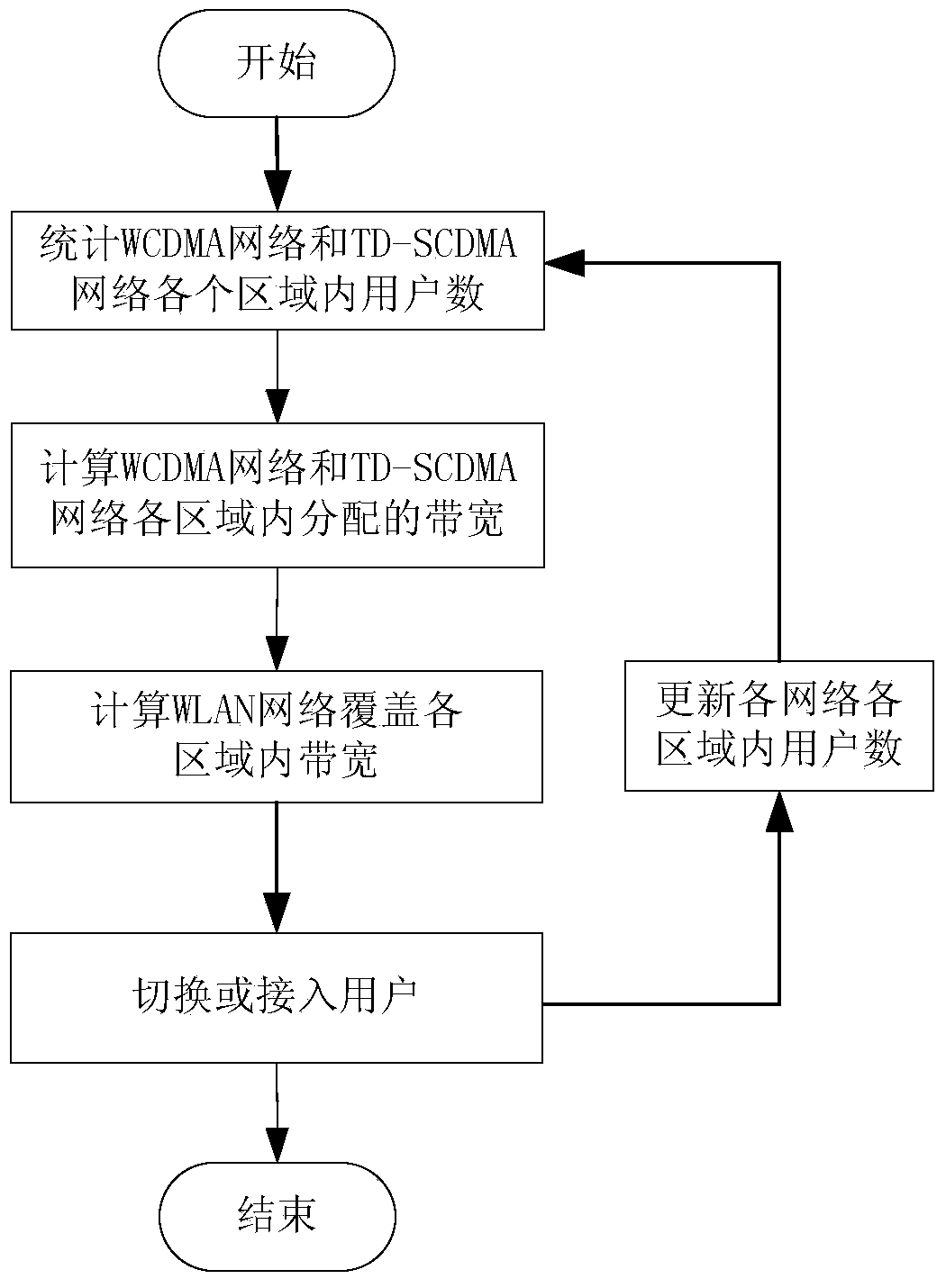
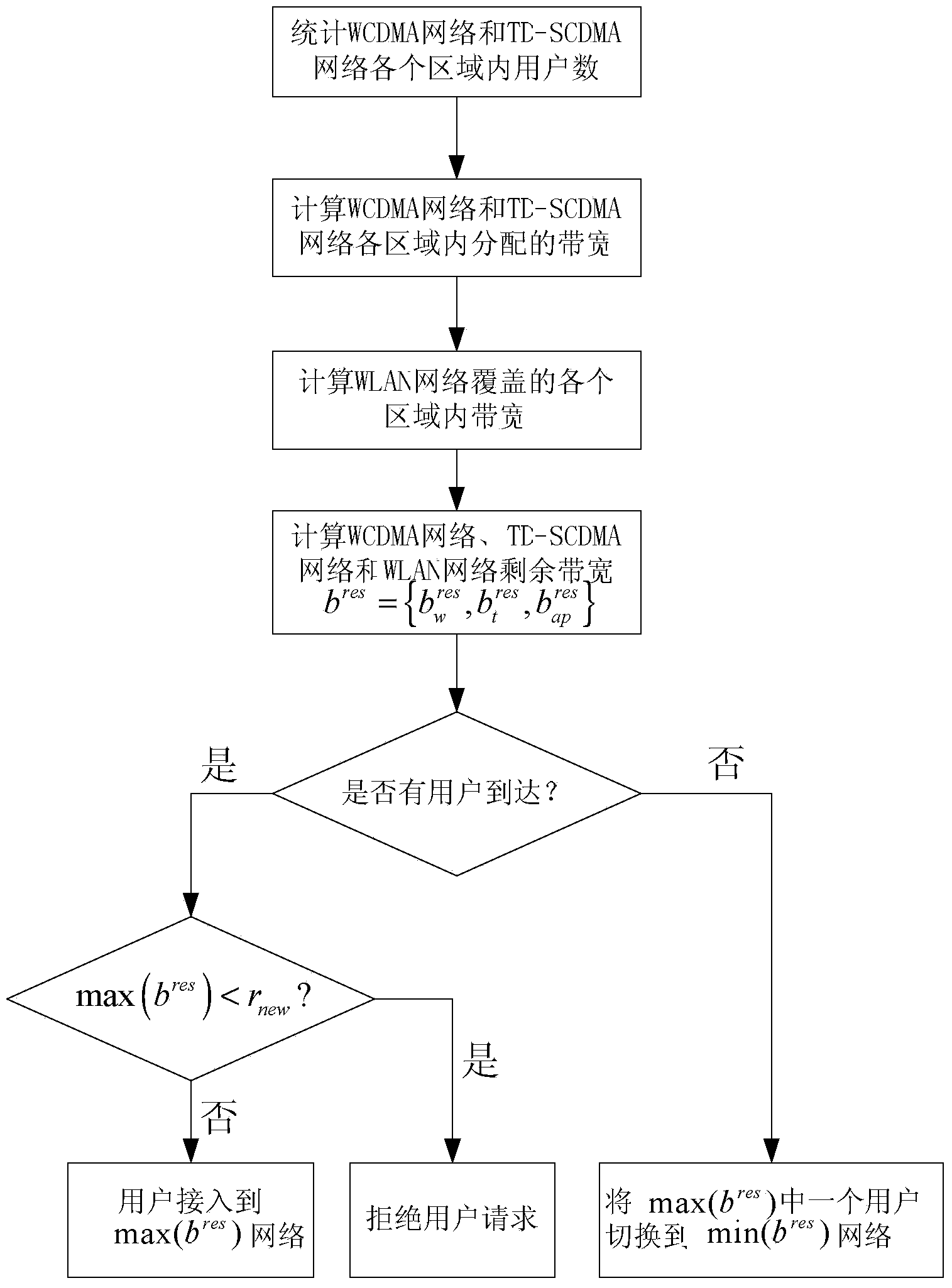
Non-cooperation game resource allocating-based 3G (the third generation telecommunication) / WLAN (wireless local area network) heterogeneous network accessing control method
ActiveCN103634848AImprove user fairnessOptimize system resource utilizationNetwork traffic/resource managementLocal area networkResource utilization
A non-cooperation game resource allocating-based 3G (the third generation telecommunication) / WLAN (wireless local area network) heterogeneous network accessing control method belongs to the technology of a wireless heterogeneous network, and solves the problems such as low network effectiveness, unbalanced resource allocation in each area and low resource utilization rate in the existing heterogeneous network resource allocating and accessing control. The method comprises the steps of establishing a 3G / WLAN non-cooperation game model to obtain an effectiveness expression of the WCDMA (wideband code division multiple access), the TD-SCDMA (time division-synchronization code division multiple access) and the CDMA (code division multiple access) 2000, solving the non-cooperation game Nash equilibrium solution of the three networks as the optimal time solution of the total network effectiveness in the whole service area and proving the uniqueness of the Nash equilibrium. The bandwidth in each covering range is obtained according to the allocating result of the CDMA, TD-SCDMA and the CDMA2000 network game sources, the rest bandwidths of the WCDMA, TD-SCDMA, the CDMA2000 and the WLAN network are computed, the accessing of a new user and the switching of the user in the network are judged and the method is suitable for the field of the wireless heterogeneous network.
Owner:HARBIN INST OF TECH
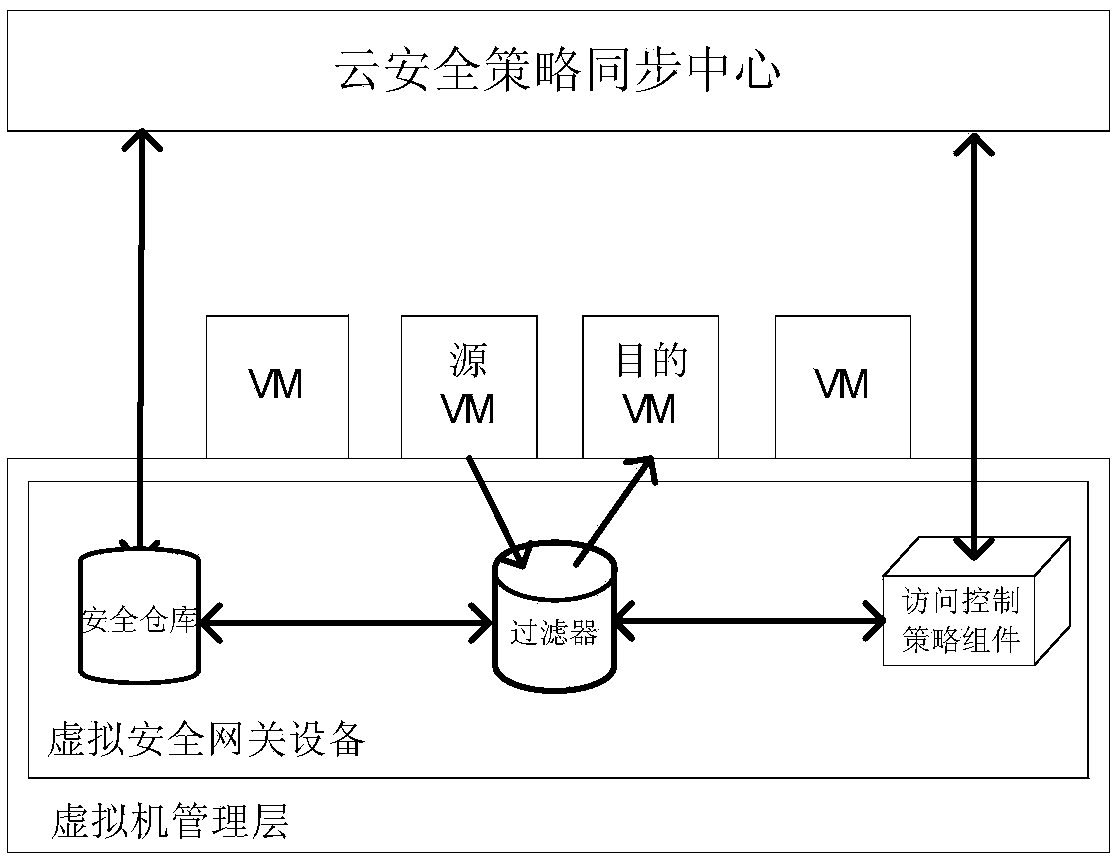
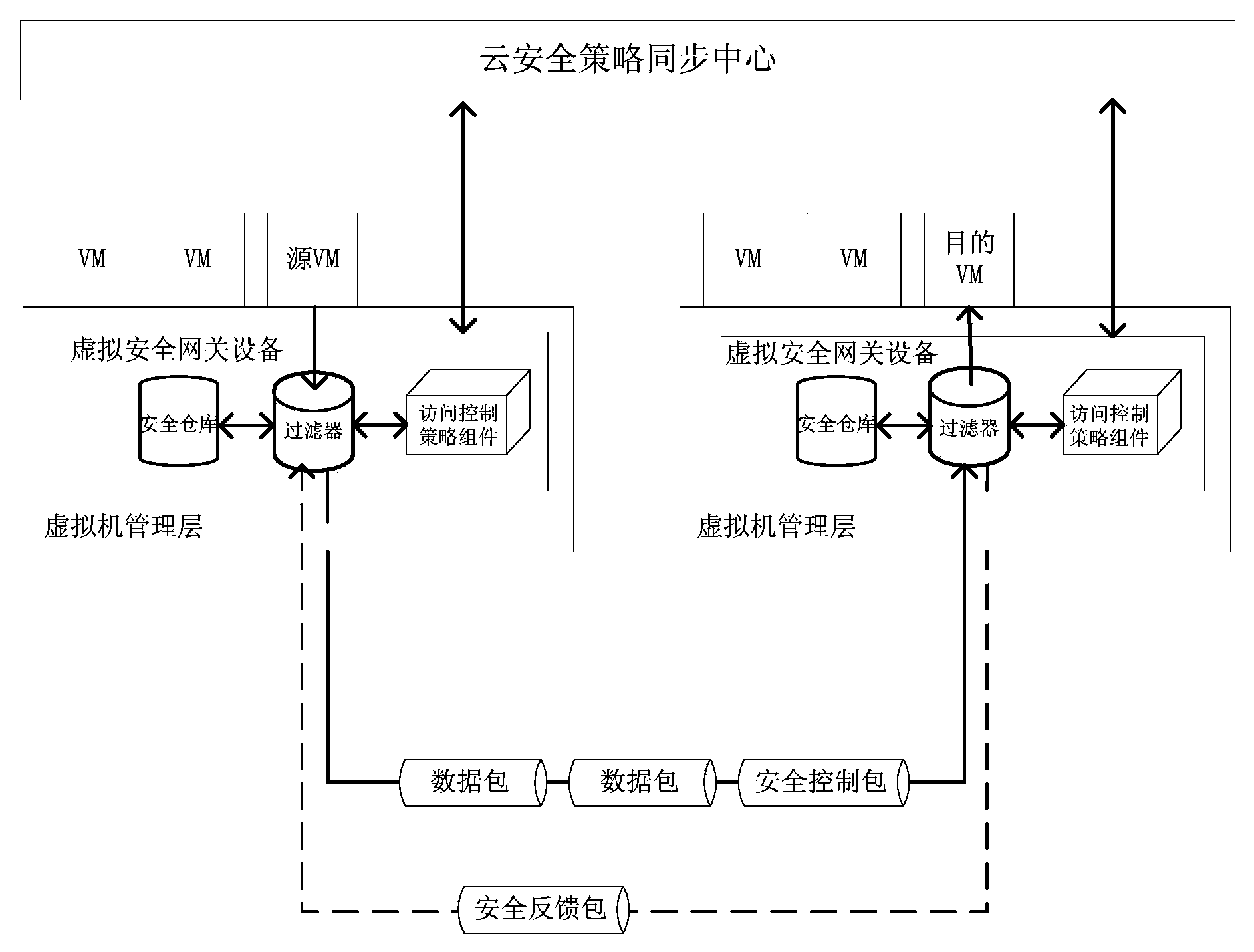
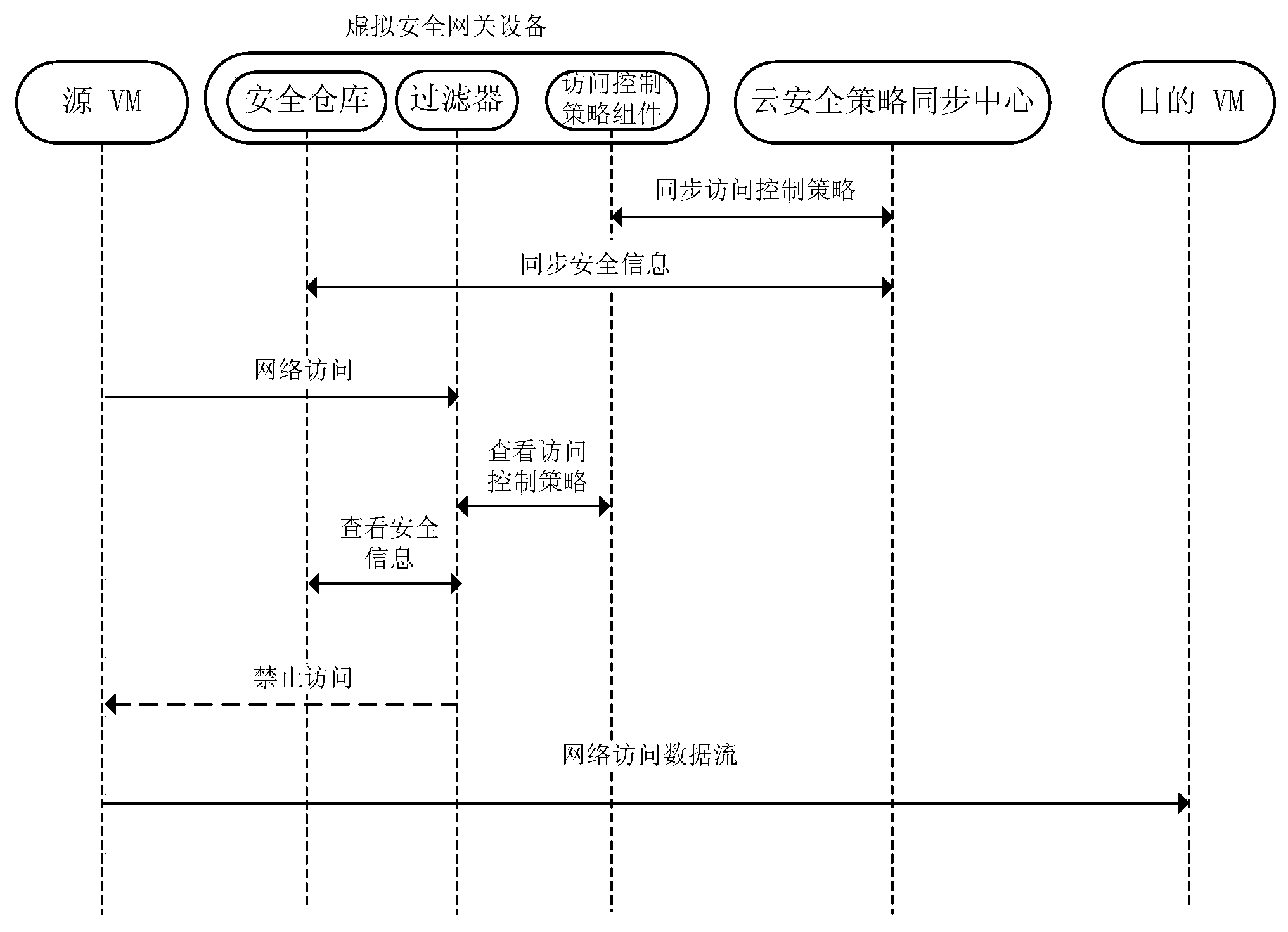
Access control method and system of self-adaptation cloud computing environment virtual security domain
ActiveCN103458003AImplement access controlImplement cross-domain access controlTransmissionCloud computingSecurity domain
The invention relates to an access control method and system of a self-adaptation cloud computing environment virtual security domain. The access control method of the self-adaptation cloud computing environment virtual security domain comprises the steps of (1) deploying a virtual security gateway device on a virtual machine management layer, carrying out interaction with a cloud security policy sync center in a cloud computing environment through the virtual security gateway device to obtain security policy information, monitoring a network communication behavior of a virtual machine on the virtual machine management layer according to a security policy, directly carrying out access control on network communication data packets inside the same physical machine, and (2) adding a security control packet to a network communication data packet across the physical machine, and carrying out self-adaptation access control across the physical machine through the security control packet and a security feedback packet which contains access control policy dynamic-adjustment information. The access control method and system of the self-adaptation cloud computing environment virtual security domain can achieve the function of carrying out fine-grained access control on communication among different virtual machines on the same physical machine or different physical machines, an access control policy can be adjusted in a dynamic mode, and access control over the self-adaptation cloud computing environment virtual security domain can be achieved.
Owner:CEC CYBERSPACE GREAT WALL
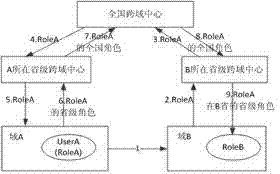
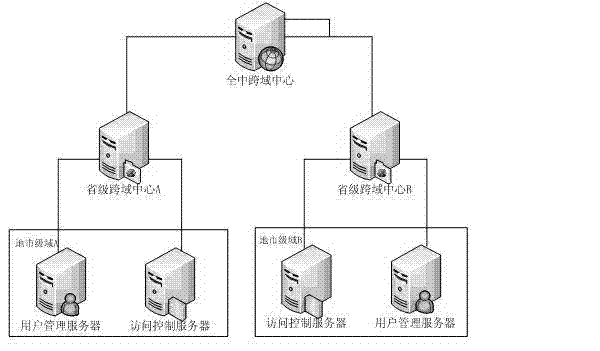
System and method for multilevel cross-domain access control
ActiveCN102761551AImplement access controlRealize managementData switching networksMunicipal levelThree level
The invention relates to a system and method for multilevel cross-domain access control in case of a multilevel administrative domain. The cross-domain access control is realized through a multilevel-role-based mapping mechanism; the method is realized based on all cross-domain access centers deployed in the entire country and provincial levels; the cross-domain access centers provide cross-domain role application and query services; and administrators can administrate all cross-domain access centers. The method comprises two steps of authorizing the cross-domain access control and carrying out access control on cross-domain access behaviors of users according to the authorization, wherein the authorizing of the cross-domain access control comprises the step of establishing corresponding cross-domain roles in related cross-domain access centers, and the control on user access comprises the steps of obtaining the access authority of cross-domain subjects to objects according to the mapping relationship between the cross-domain roles and domains where the subjects and the objects are located, and carrying out control by the domains where the objects are located. The system and the method are used for administrating the cross-domain access of three levels, i.e. a national level, a provincial level and a municipal level, in a security service platform, so that the cross-domain access control has the characteristics of self-government administration, user transparency and convenience in extension.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
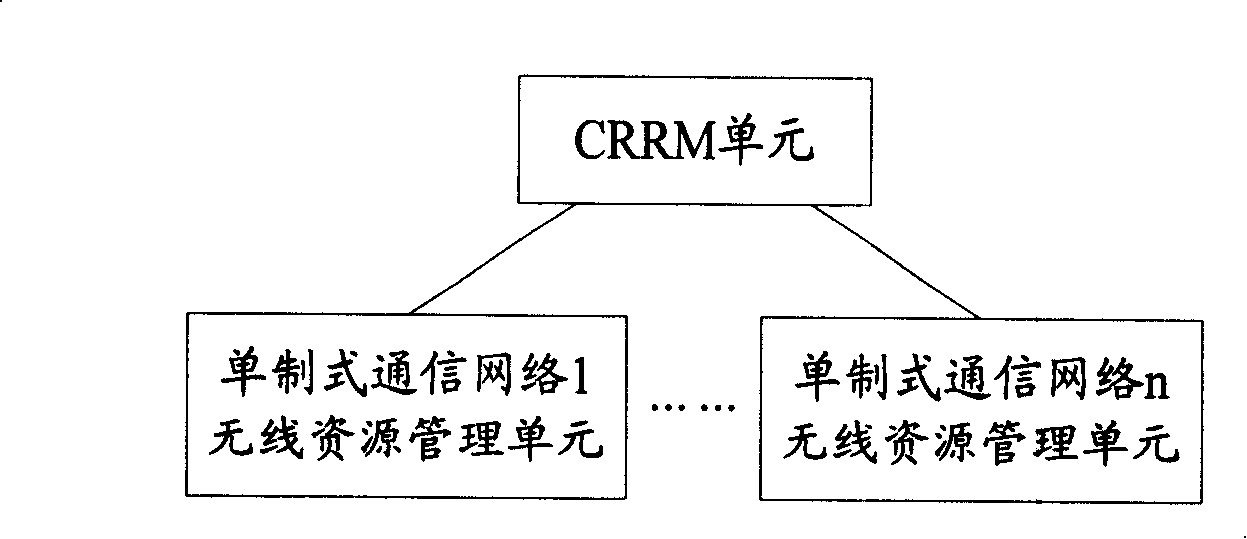
System, device, and method for implementing radio resource management in multi-standard communication network
InactiveCN101212761ARealize unified managementAchieve accessNetwork traffic/resource managementRadio/inductive link selection arrangementsWireless resource managementResource information
The embodiment of the invention discloses a system for achieving wireless resource management in a multi-system communication network and a method thereof. The system provided by the embodiment of the invention comprises a wireless resource management unit and a CRRM unit of a plurality of different single systems, wherein, the wireless resource management unit is used for reporting wireless resource information of each single system communication network to the CRRM unit and the CRRM unit is used for centralized management of wireless resources of the multi-system communication network on the basis of the wireless resource information. According to the provided proposal of each embodiment of the invention, the centralized management of wireless resources of the multi-system communication network is achieved by introducing the CRRM unit to the multi-system communication network; loading conditions and system operation state of the multi-system communication network can be completely controlled; real-time control and integrated optimization of the wireless resources of the multi-system communication network can be realized, thus making the best use of the wireless resources of the multi-system communication network and protecting investment of operators.
Owner:HUAWEI TECH CO LTD
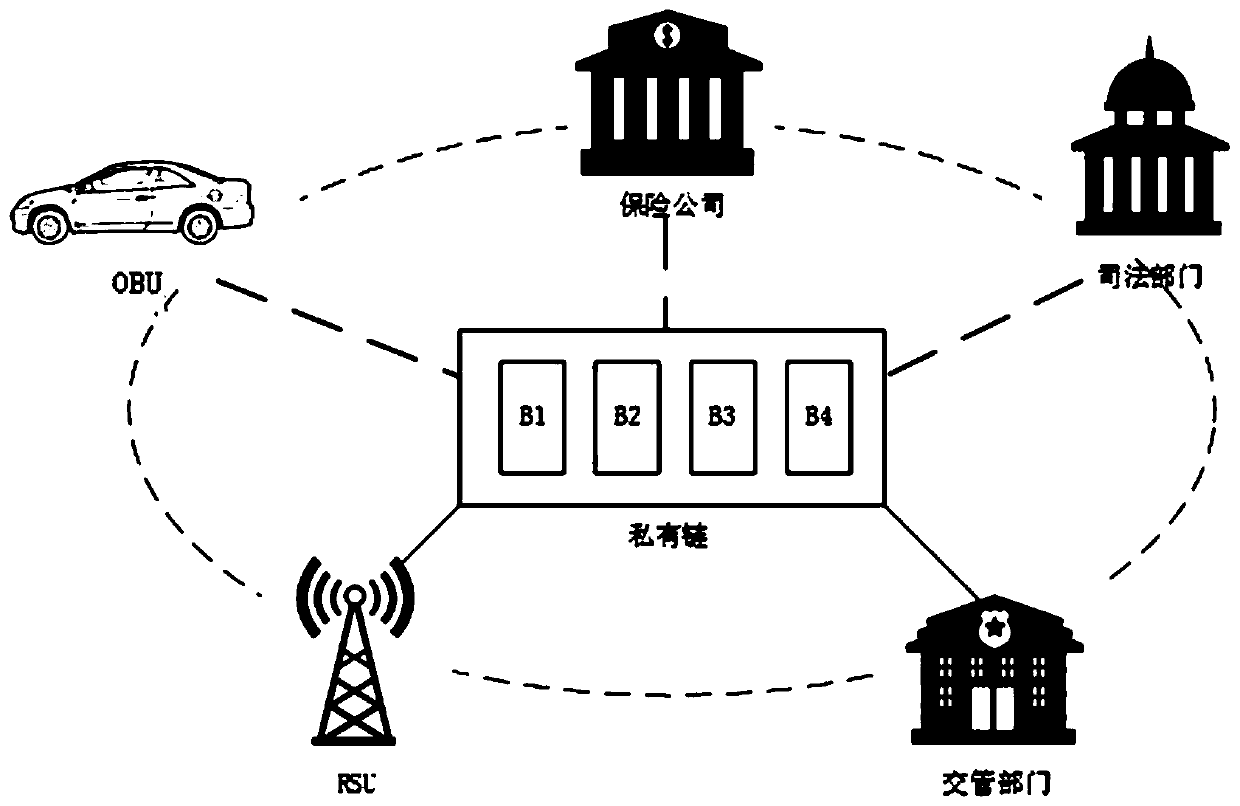
Electronic evidence obtaining device and method based on block chain in Internet-of-Vehicles environment
ActiveCN111464980AProtection against the risk of tamperingImprove access efficiencyData processing applicationsParticular environment based servicesComputer networkTraffic crash
The invention provides an electronic evidence obtaining device and method based on a block chain in an Internet-of-Vehicles environment. The method comprises the following steps of S10, offline registration, S20, vehicle online identity registration, S30, real-time evidence storage and S40, query and evidence obtaining. According to the electronic evidence obtaining device and method based on theblock chain in the Internet-of-Vehicles environment, the block chain technology is used for traffic accident electronic evidence obtaining, the integrity, non-repudiation and permanence of evidence are guaranteed through the characteristics of block chain distributed data storage and the like, many problems of traditional traffic accident evidence obtaining are solved, and the evidence obtaining efficiency is high.
Owner:NANTONG UNIVERSITY
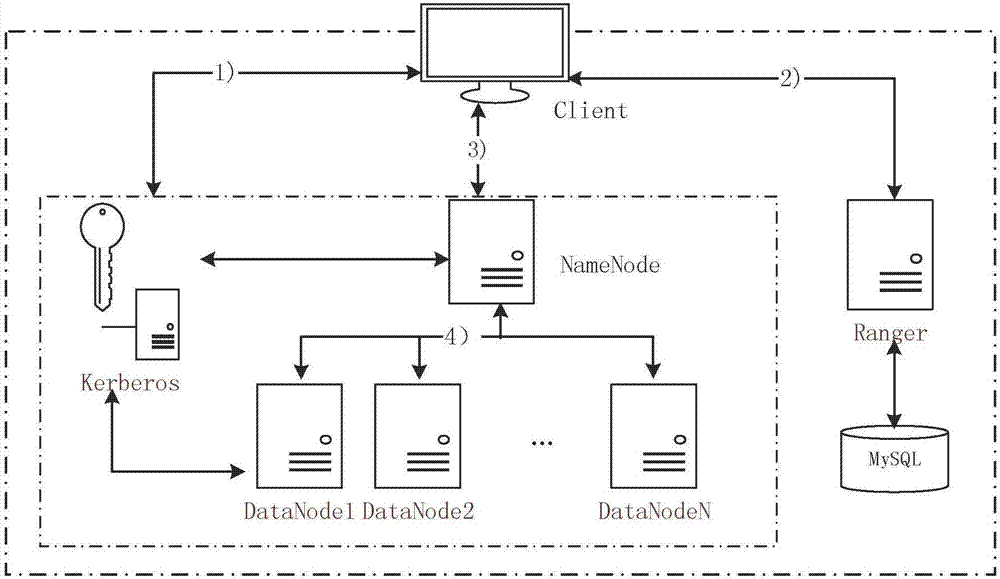
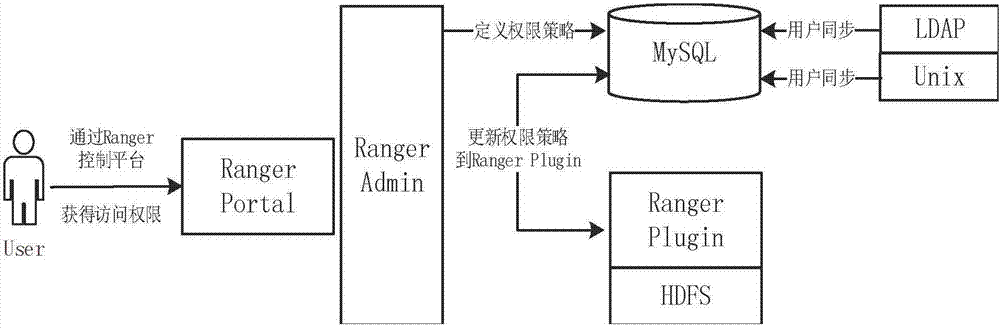
Access control method for distributed storage under cloud environment
InactiveCN107483491ARealize cloud data isolationEfficient access control managementTransmissionDistributed File SystemMedia access control
The invention relates to an access control method for distributed storage under a cloud environment. The method adopts an HDFS distributed file system of a Hadoop cluster to serve as a basic cloud storage system, and a safe access control function is added on the basis of the basic cloud storage system. An access control technology in the cloud storage system is broken through via Ranger, and a fine-grained access control authorization system based on a role is built, so that the cloud storage system can reliably support operations of effective isolation and integrity protection on different levels or types of information of multiple users, and isolation of cloud data can be achieved. Access control to a specific data node in the cloud storage system is achieved via Kerberos, and an access control problem in the Hadoop cluster, and between a client and a management node, between the management node and the data node and between the data nodes is solved.
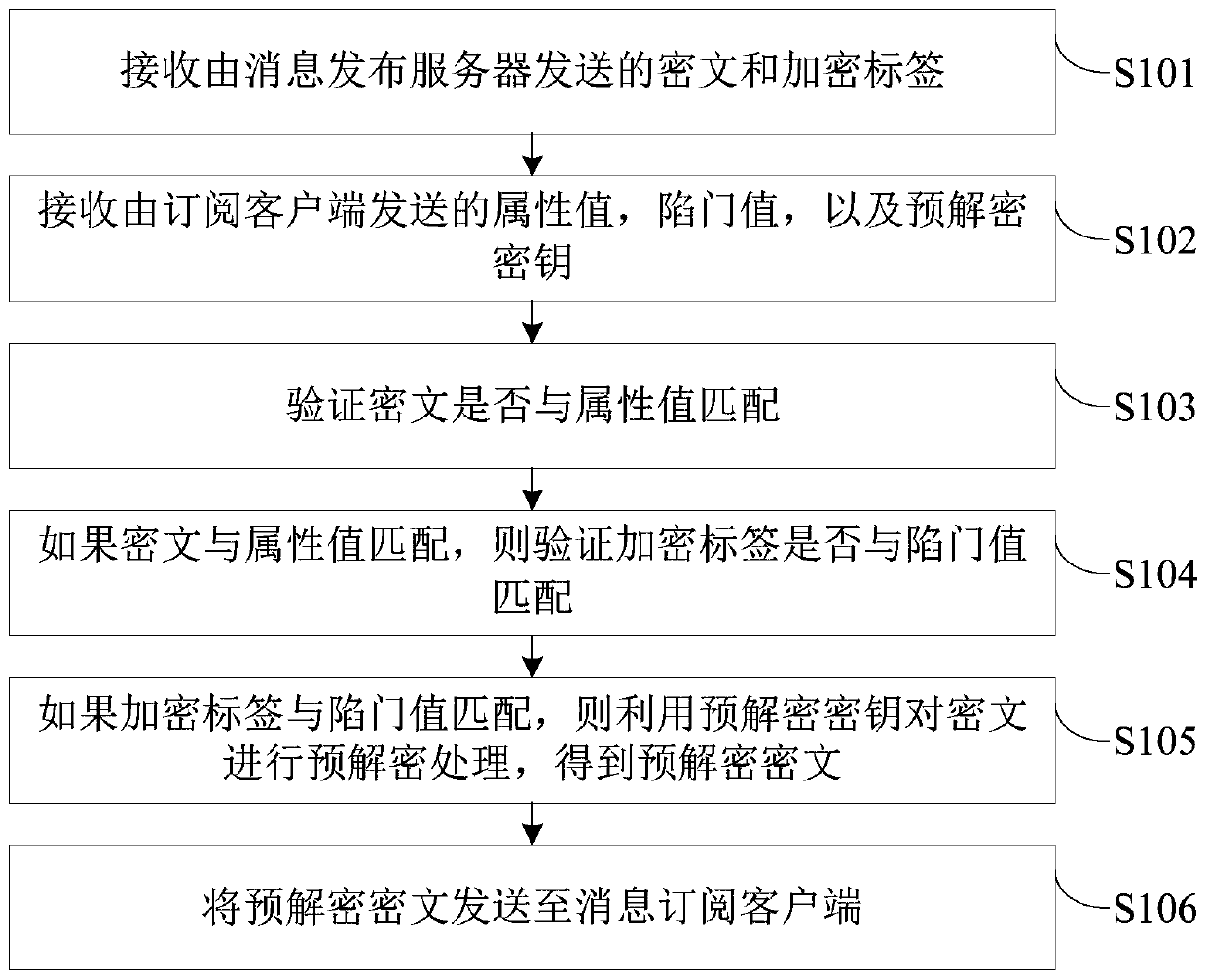
Owner:SHANDONG UNIV
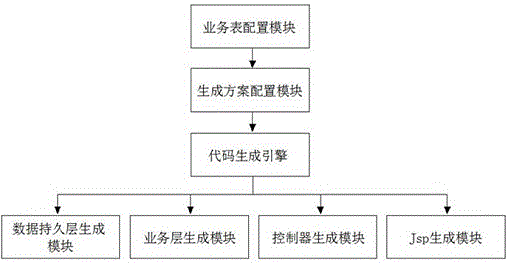
Code generator integrated based on Spring MVC framework, Apache Shiro framework and MyBatis framework
InactiveCN105824619AQuality improvementImplement access controlSpecific program execution arrangementsCreation/generation of source codeProgramming languageActive systems
The invention provides a code generator which is integrated based on a Spring MVC framework, an Apache Shiro framework and a MyBatis framework. The code generator comprises a service table configuring module, a generating scheme configuring module, a code generating engine, a data persistence layer generating module, a service layer generating module, a controller generating module, and a Jsp generating module, wherein codes are generated by the code generator based on integration of the Spring MVC framework, the Apache Shiro framework and the MyBatis framework, common single tables, multiple tables, tree form structure tables and various service related logic in an active system can be treated, and automatic generation of user access control and MyBatis mapper map files based on roles and right is realized; generated codes can be used when being unpacked, and convenience is provided for subsequent secondary development and expansion, and the development efficiency and the code quality of the system are improved.
Owner:SICHUAN VOCATIONAL & TECHN COLLEGE OF COMM
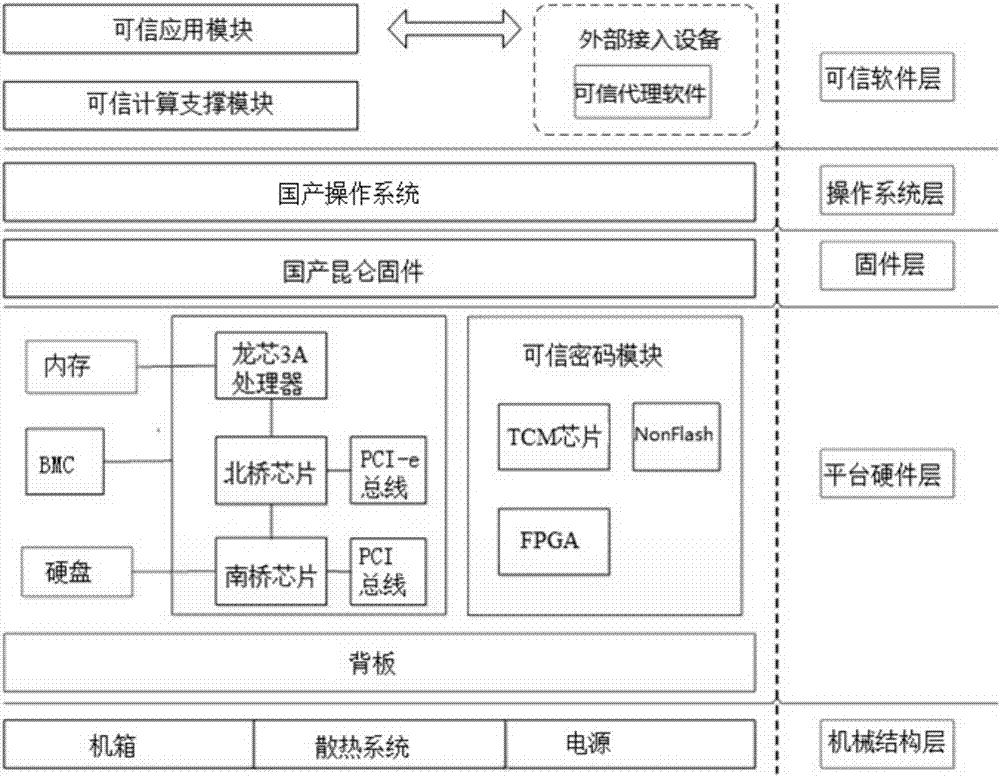
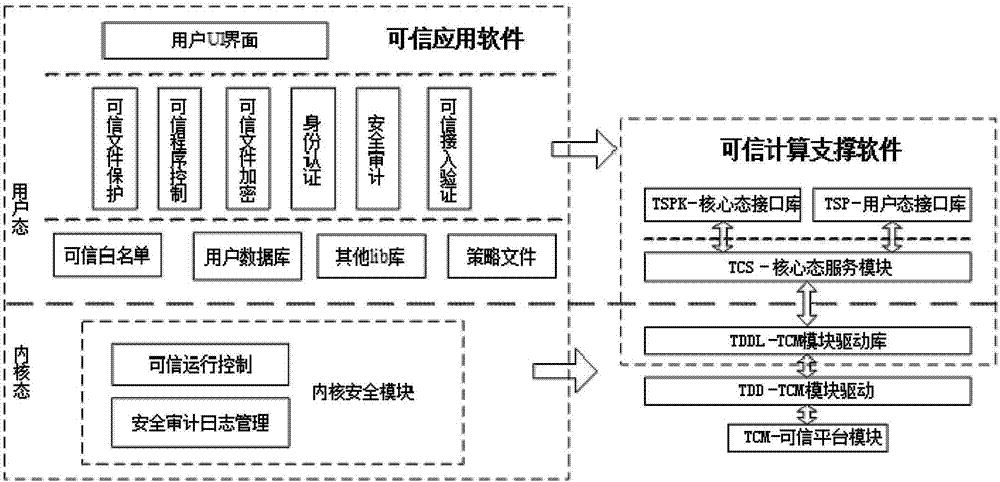
Dependable computing unit based on homemade TCM and operation method thereof
InactiveCN106991329AImprove computing speedVersatilePlatform integrity maintainanceOperational systemInformation security
The invention relates to a dependable computing unit based on a homemade TCM and an operation method thereof. The dependable computing unit comprises a mechanical structure layer, a platform hardware layer, a firmware layer, an operation system layer and a dependable software layer; the mechanical structure layer comprises a case, a heat dissipating system and a power source; the firmware layer comprises firmware; the operation system layer comprises an operation system; the platform hardware layer comprises a backboard, a computing unit module and a dependable code module; the dependable software layer comprises a dependable application module and a dependable computing supporting module. The dependable computing unit is complete in function, high in algorithm computing efficiency and large in concurrence work capacity; serving as the dependable computing unit, the unit can provide high-performance data encryption / decryption service for an information safety transmission system and serve as main code equipment and core member of a host data safety storage system, an identity authentication system and a symmetric and asymmetrical secret key management system, and has wide system application potentiality.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
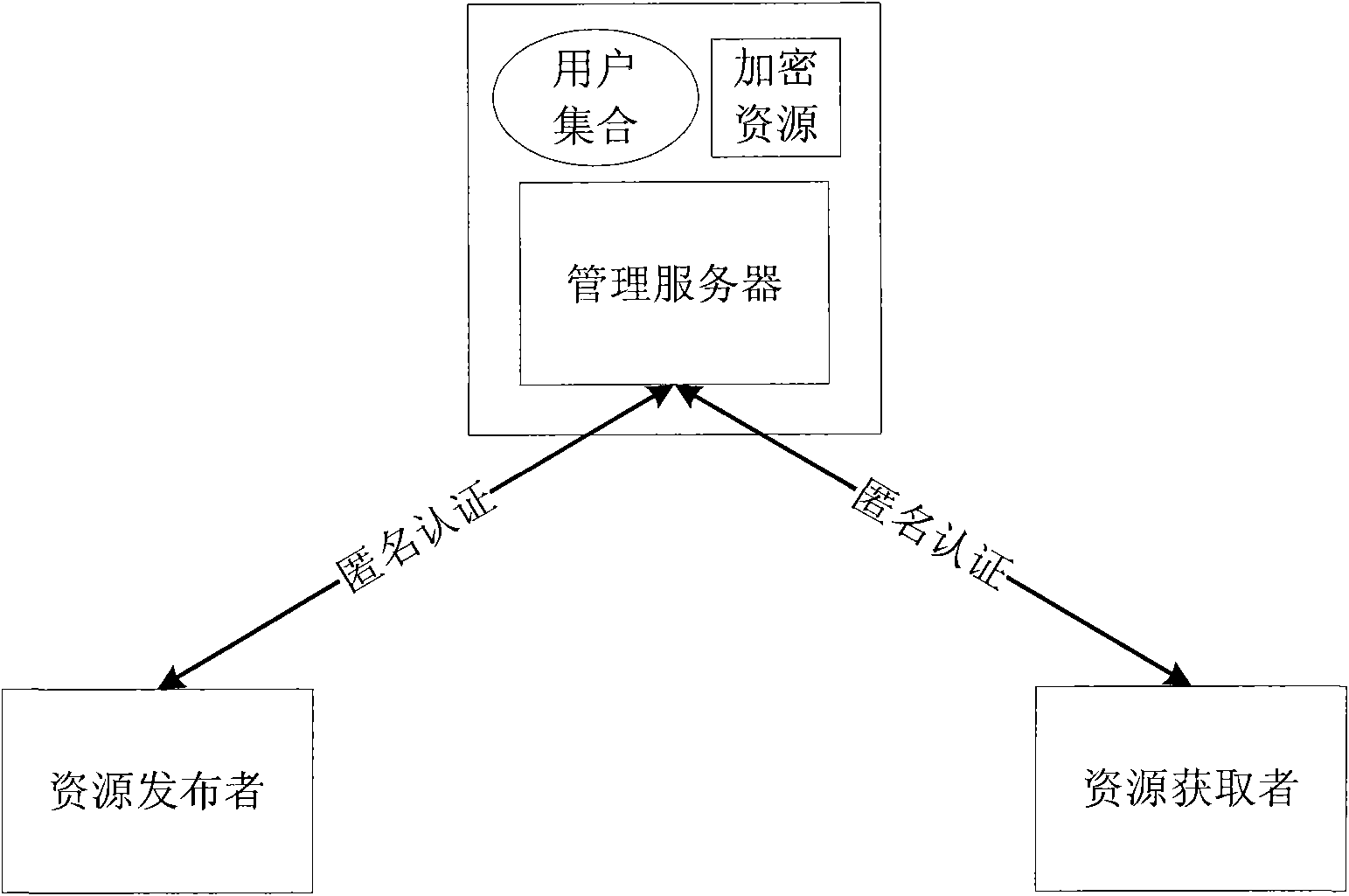
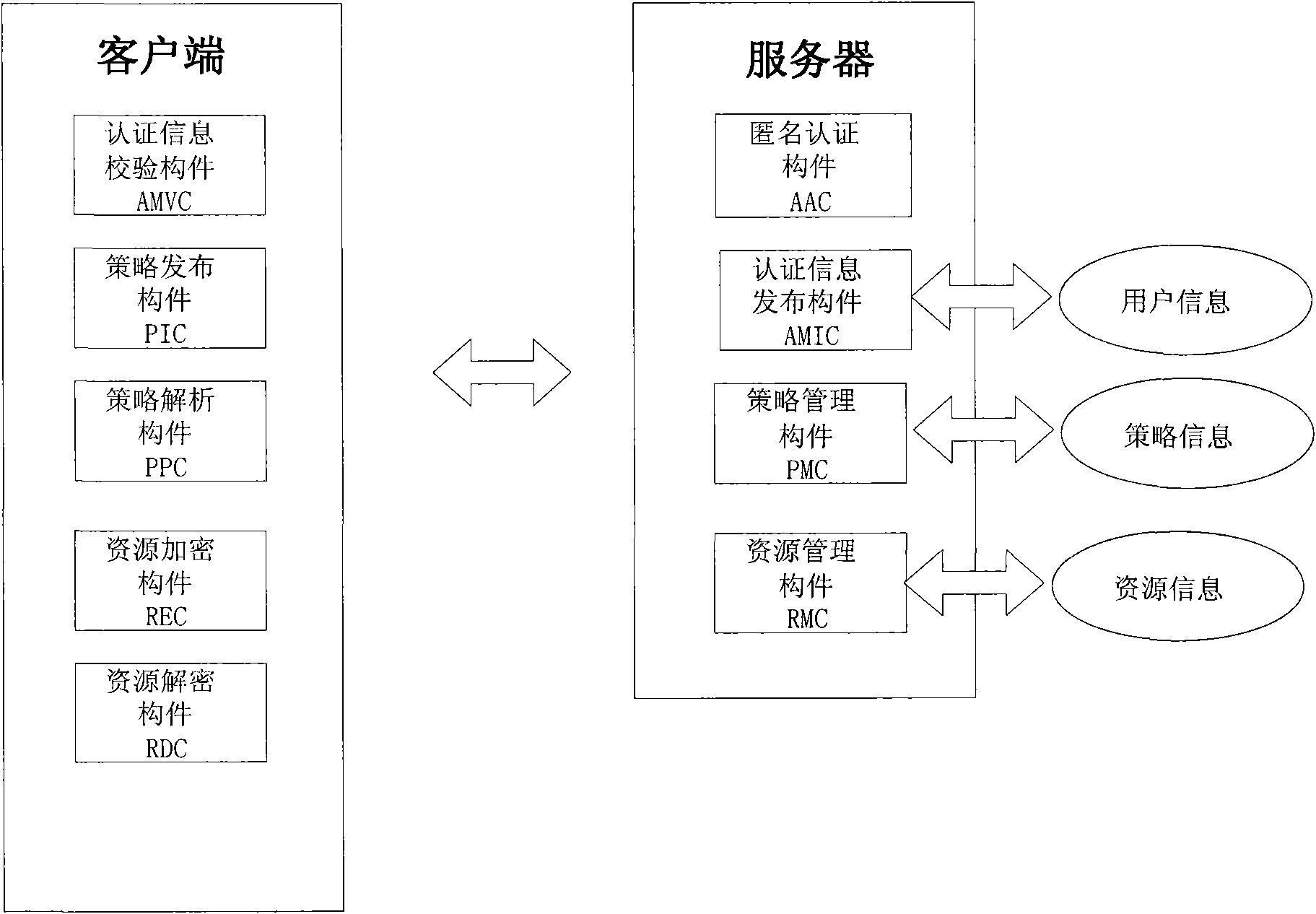
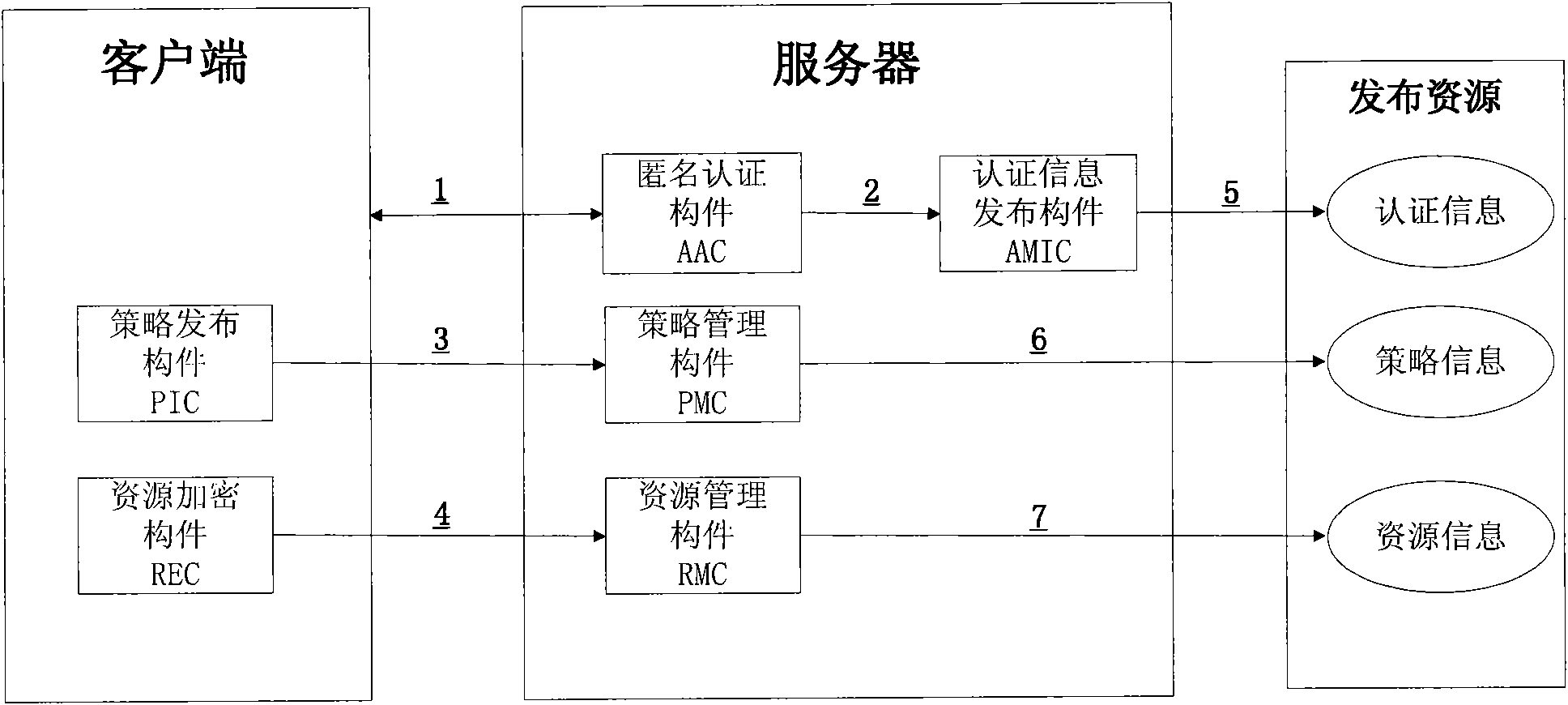
Method and system for sharing anonymous resource
InactiveCN101834853AProtect personal privacyProtection of personal informationTransmissionResource managementResource Provider
The invention discloses a method and a system for sharing an anonymous resource, which belong to the technical field of computer information. The method for sharing the resource comprises the following steps that: a resource provider initiates a resource publishing request to a resource management server; the resource management server performs an anonymous authentication on the request; the resource provider generates a resource acquisition strategy, uses the resource acquisition strategy as a cipher key to encrypt the resource, and sends the acquisition strategy and the encrypted resource to the resource management server; the resource management server stores a binary group and releases resource description information; a resource acquirer retrieves the resource description information and initiates a resource acquisition request; the resource management server performs the anonymous authentication on the resource acquirer; and the resource acquirer acquires and decrypts the resource after acquiring a strategy verification. The invention also discloses a system sharing the resource, which corresponds to the method. The method and the system can be used for computer information technical application such as network resource sharing and the like.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Information processing method for closed subscriber group, access control method, system and device
ActiveCN101646248AImplement access controlAssess restrictionRadio transmission for post communicationInformation processingClosed subscriber groups
The invention discloses an information processing method for a closed subscriber group, an access control method, a system and a device. The information processing method for the closed subscriber group comprises the following steps: acquiring information on the closed subscriber group (CSG) of modified user equipment (UE); and sending a message to the UE, wherein the message carries correlative information on the CSG. The method and the corresponding system and device can make the UE be capable of acquiring that the stored CSG information is changed.
Owner:NOKIA TECHNOLOGLES OY
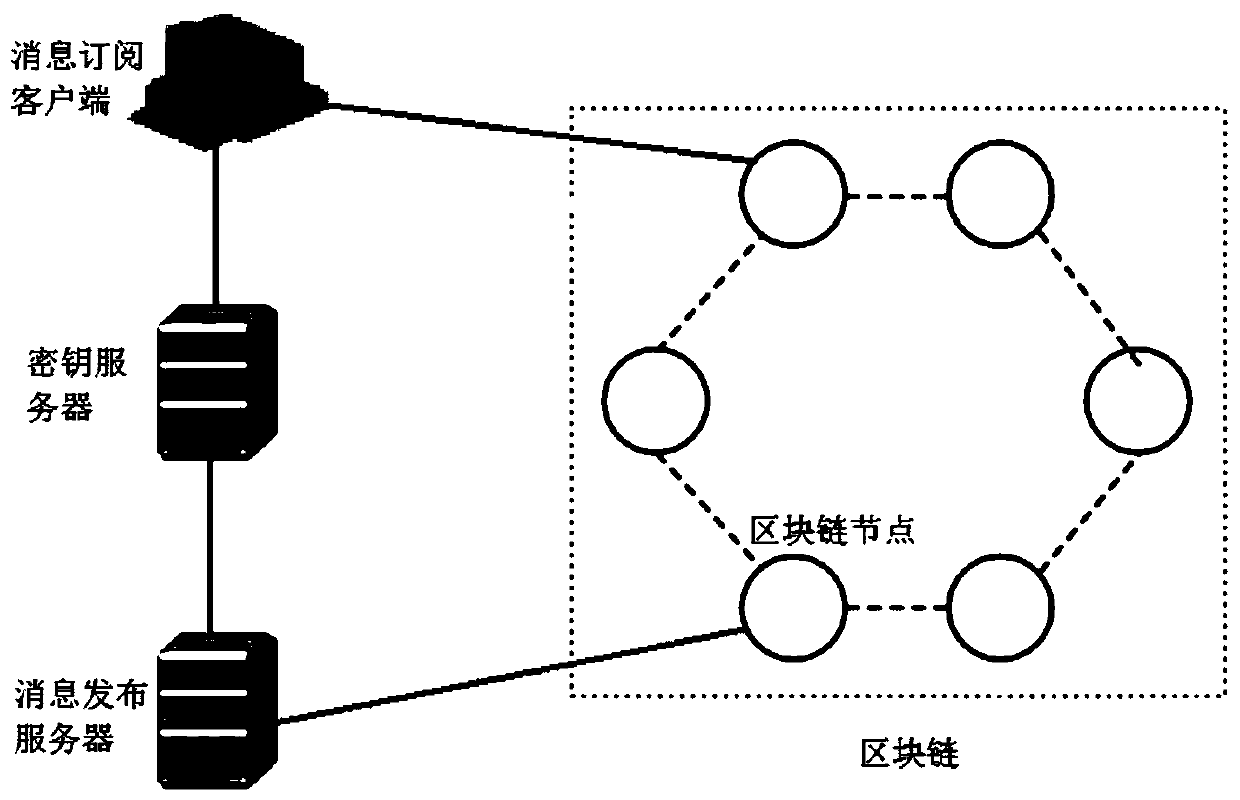
Security publishing and subscribing system and publishing and subscribing method based on block chain technology
ActiveCN109981641AImprove securityPrevent malicious tamperingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextClient-side
The embodiment of the invention provides a secure publishing and subscribing system and method based on a block chain technology. The system comprises a key server, a message subscribing client, a message publishing server and a block chain comprising a plurality of block chain nodes, the method comprises the following steps: receiving a ciphertext and an encryption tag sent by a message publishing server; receiving an attribute value, a trap door value and a pre-decryption key sent by the subscription client; verifying whether the ciphertext is matched with the attribute value or not; if yes,verifying whether the encryption tag is matched with the trap door value or not; if so, pre-decrypting the ciphertext by using the pre-decryption key to obtain a pre-decrypted ciphertext; and sendingthe pre-decrypted ciphertext to the message subscription client, so that the message subscription client decrypts to obtain a subscription message. According to the embodiment of the invention, the security of the stored data in the publishing and subscribing system can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
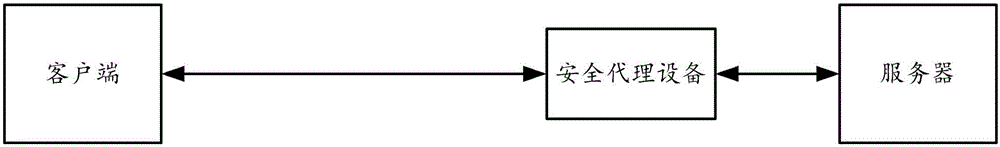
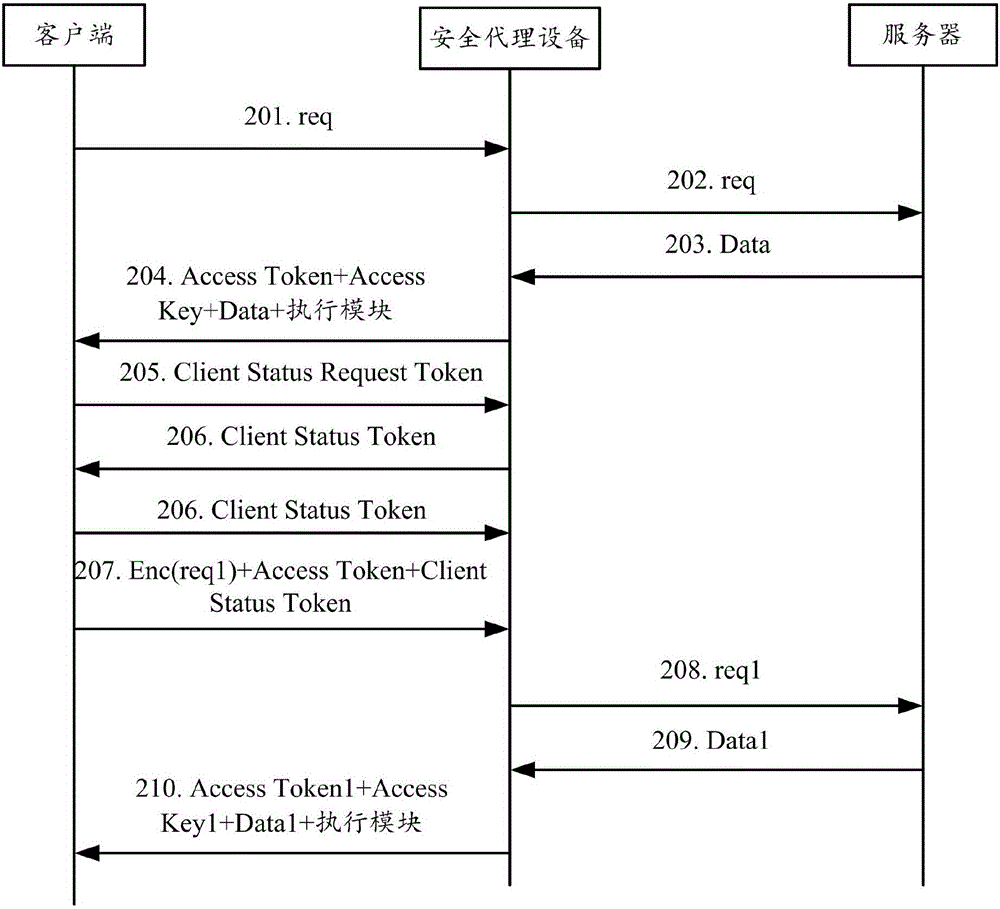
Secure communication method and device
ActiveCN105491001AImplement access controlProtection securityComputer security arrangementsSecuring communicationSecure communicationCommunications security
The invention provides a secure communication method and device. Secure proxy equipment is arranged between a client and a server. The secure communication method comprises the following steps: after the secure proxy equipment receives data returned to the client by the server, allocating a token to the client, and transmitting the token, the data returned to the client by the server and an execution module to the client; and receiving a request sent by the execution module running on the client through the token, verifying the token, and forwarding the request to the server if verification passes. Through adoption of the secure communication method and device, the communication security between the client and the server is enhanced, and various automatic attacks to the server can be prevented.
Owner:RIVER INFORMATION TECH SHANGHAI CO LTD
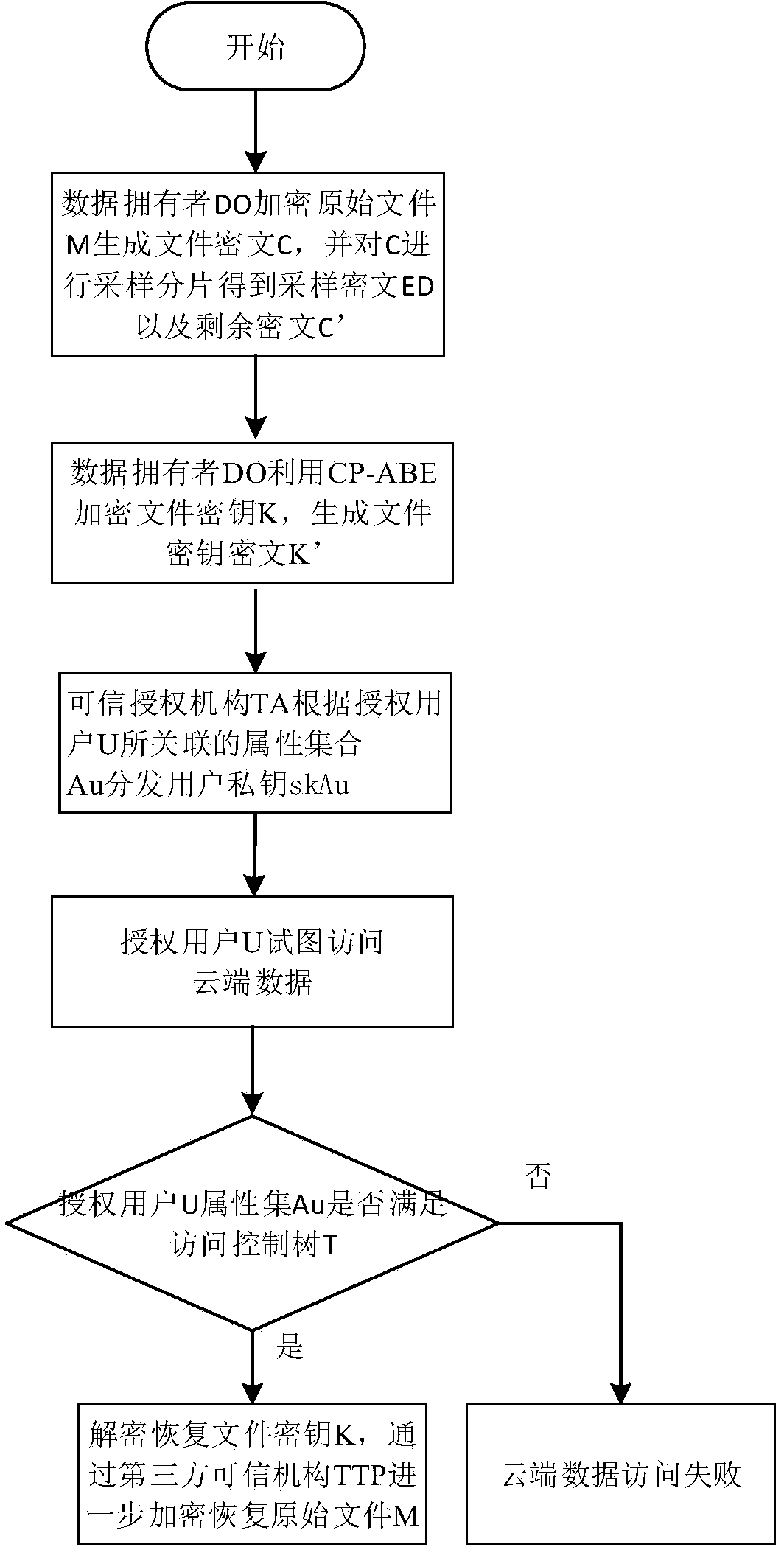
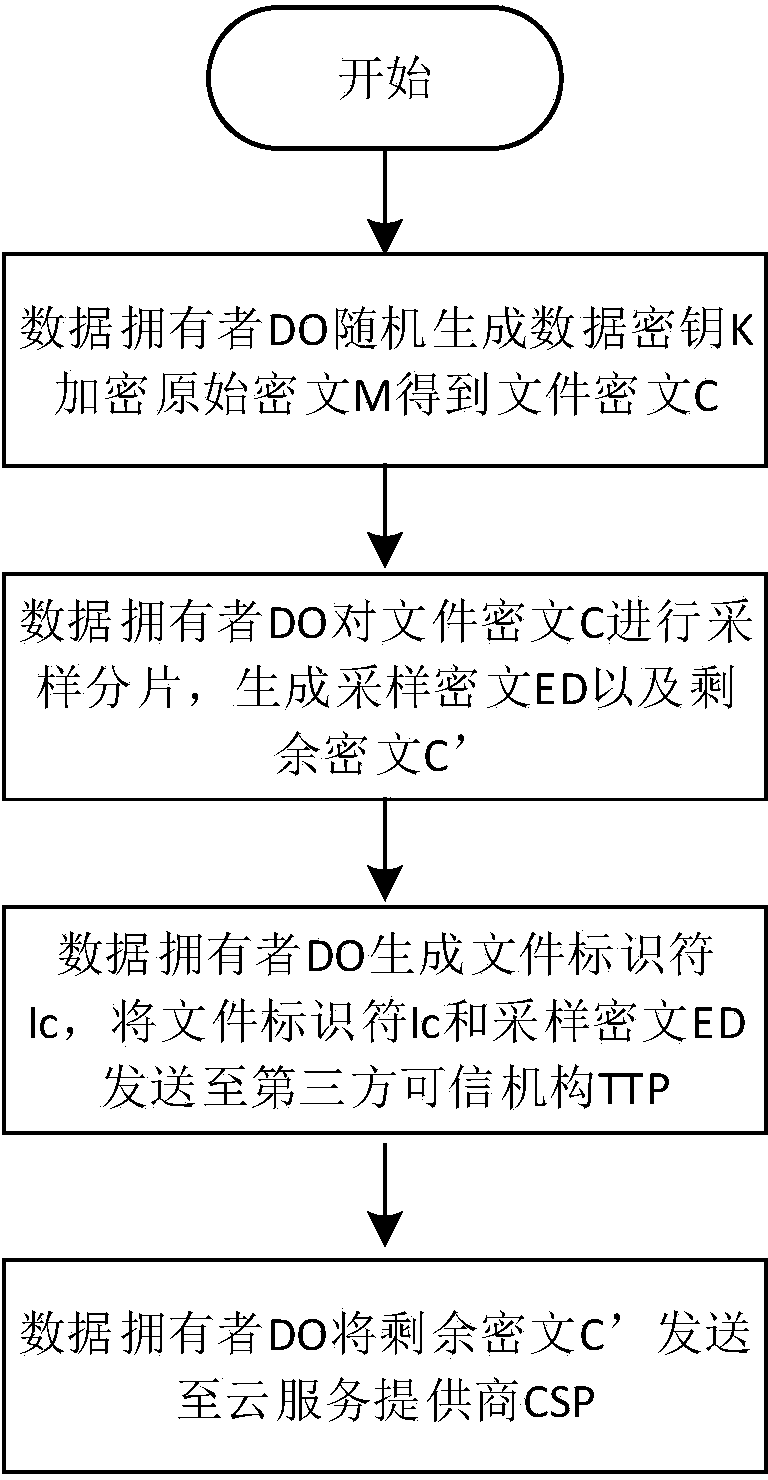
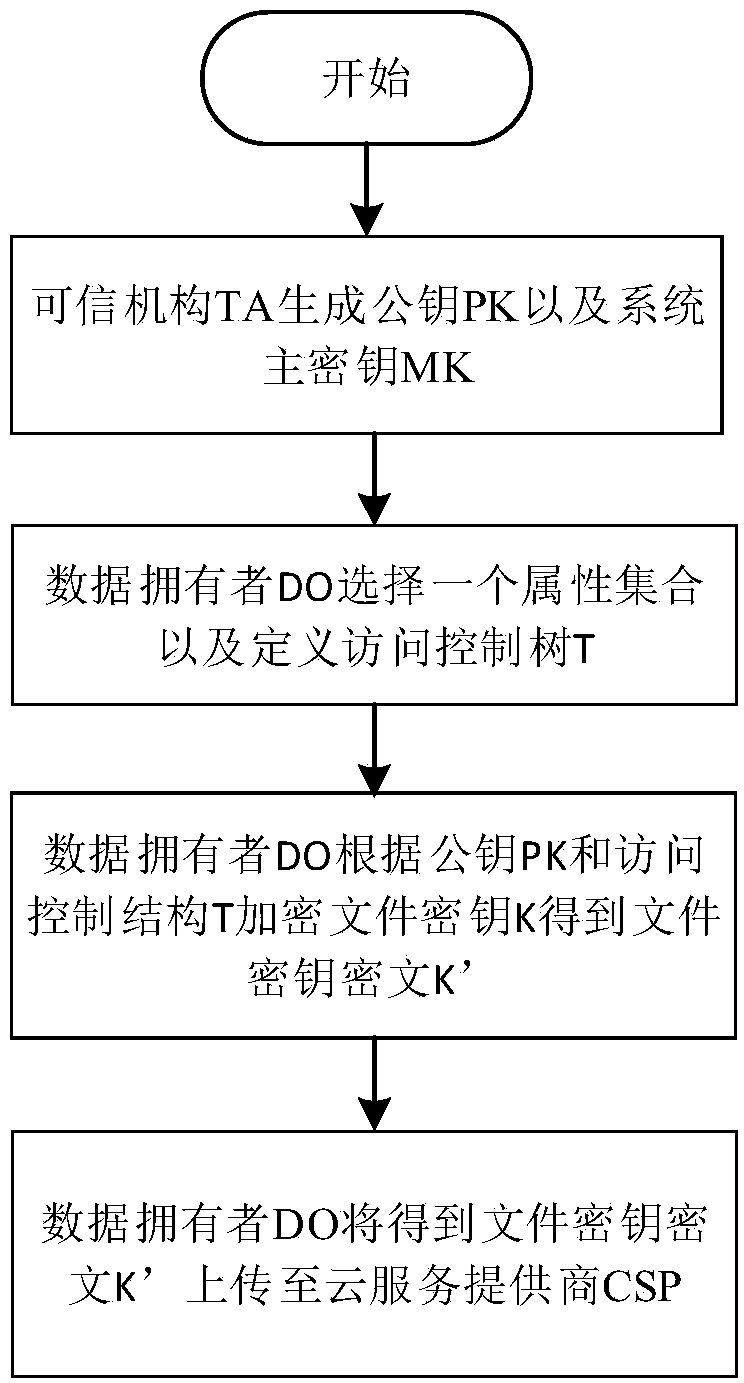
Deterministic cloud data deleting method based on sampling and fragmenting of cryptograph
ActiveCN104023027AImprove granularityReduce computationEncryption apparatus with shift registers/memoriesUser identity/authority verificationCloud service providerService provider
The invention discloses a deterministic cloud data deleting method based on sampling and fragmenting of a cryptograph. The method mainly solves the problems that the fine granularity of access control is low and the safety is low in the prior art. The method comprises implementation steps that (1) a data owner carries out sampling and fragmenting on the cryptograph to generate a sampling cryptograph and a residual cryptograph, and the sampling cryptograph and the residual cryptograph are sent to a credible third-party mechanism and a could service provider respectively; (2) a file secret key is shared by a plurality of users in a cloud storage environment; (3) when an authorized user accesses the cloud data, the credible third-party mechanism merges the cryptograph of a file, and the authorized user decrypts the cryptograph of the file; (4) the cryptograph sampling and fragmenting technology is adopted to prevent the cloud service provider from acquiring the integrated cryptograph of the file, the credible third-party mechanism destroys the sampling cryptograph, and then deterministic data deleting is achieved. By means of the method, real-time deterministic deleting of data in cloud storage services can be achieved, and the privacy of user data can be improved. The method can be used for guaranteeing safe access of the user data in the cloud storage mode.
Owner:XIDIAN UNIV
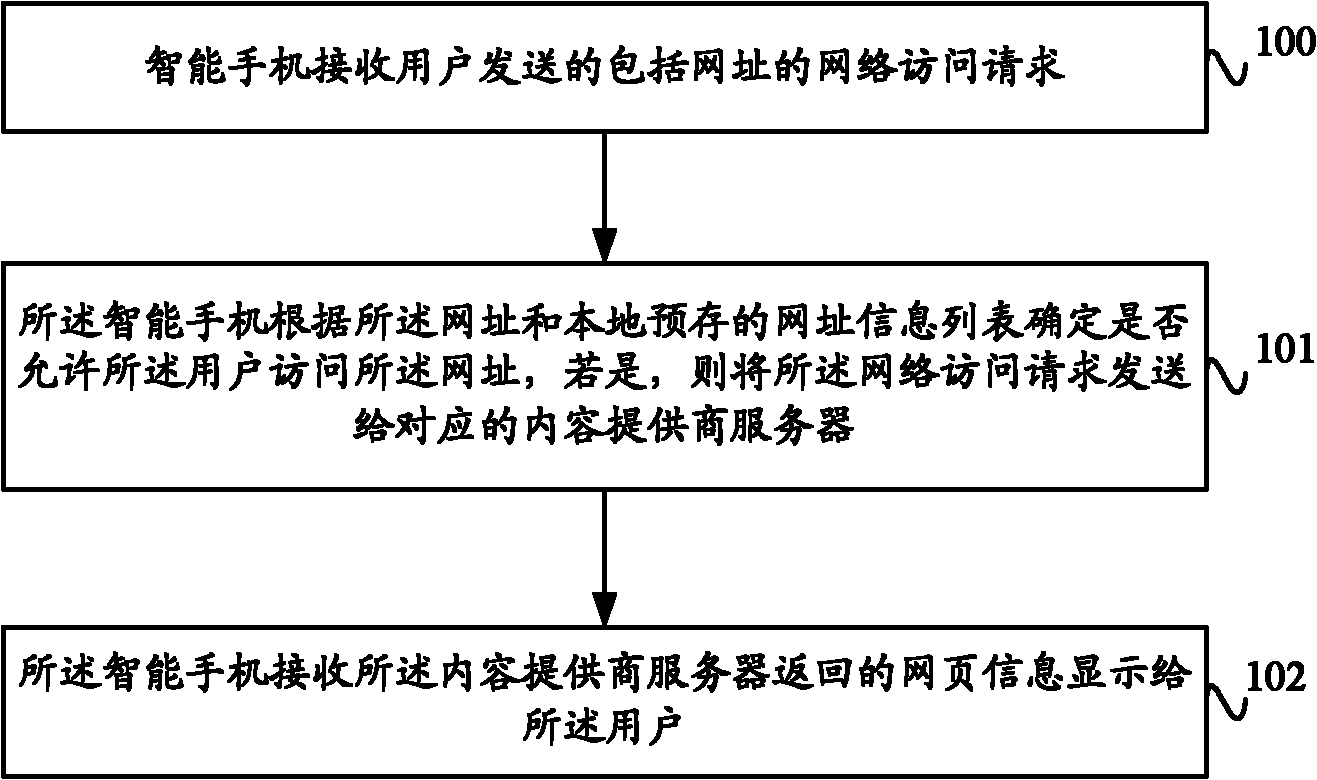
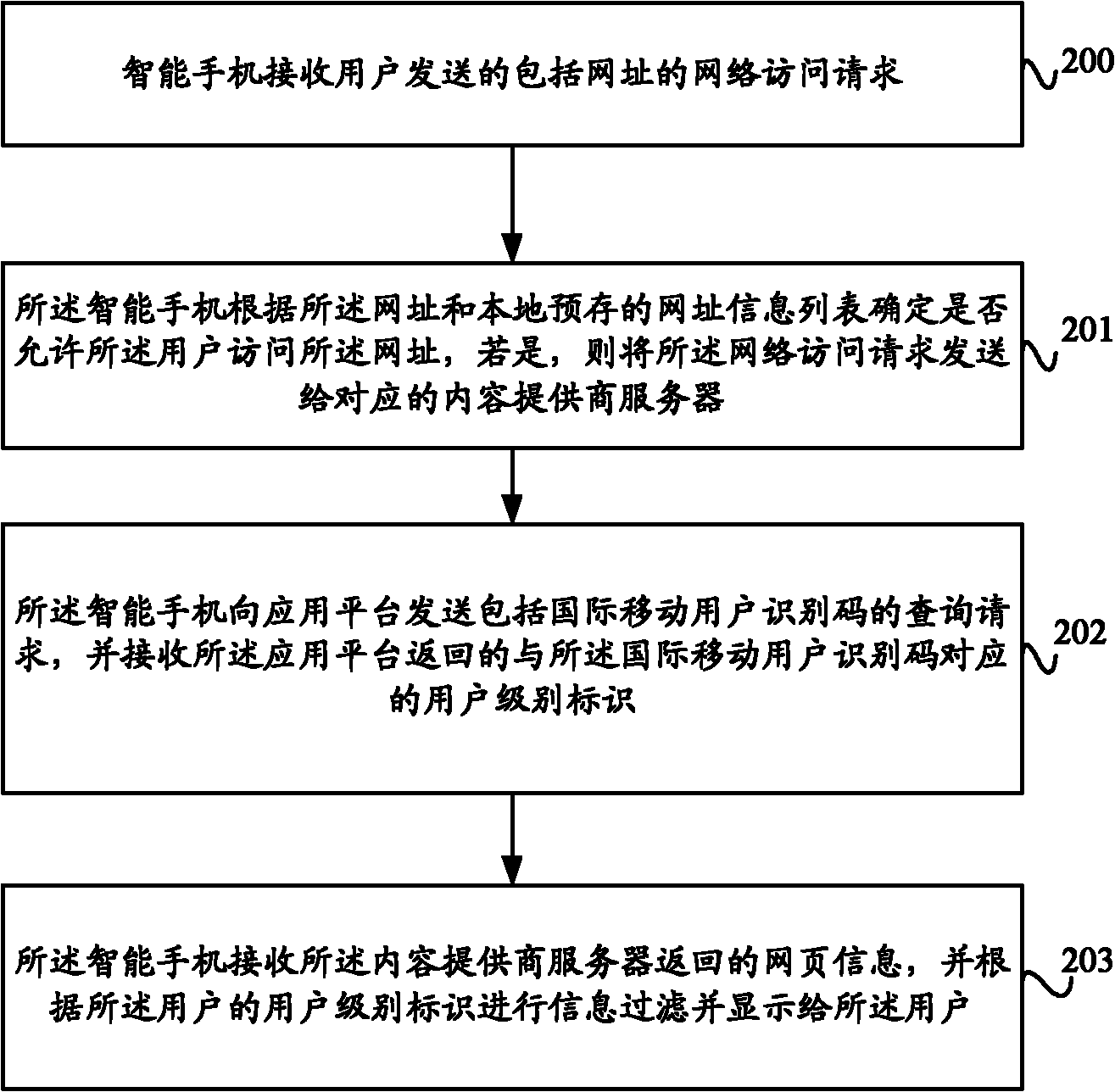
Smart-phone-based webpage access control method, system and smart phone
InactiveCN102497632AImplement access controlPrevent intrusionSecurity arrangementInternet privacyAccess control
The invention provides a smart-phone-based webpage access control method, a smart-phone-based webpage access control system and a smart phone. The method comprises the following steps that: the smart phone receives a network access request comprising a website from a user; the smart phone judges whether the user is permitted to access the website or not according to the website and a locally pre-stored website information list, and transmits the network access request to a corresponding content provider server if the user is permitted to access the website; and the smart phone receives webpage information returned by the content provider server, and displays the webpage information to the user. By the smart-phone-based webpage access control method, the smart-phone-based webpage access control system and the smart phone, the smart phone can control the access of the user, the security of network access is ensured, and the invasion and harassment of spam websites can be avoided.
Owner:BEIJING BENY WAVE SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com