Radio sensor access control method based on key chain
A wireless sensor and access control technology, applied in key distribution, can solve the problems that the network cannot resist node capture attacks, is vulnerable to DoS attacks, user authentication protocol failure, etc., to increase flexibility and scalability, and accelerate practical application process, the effect of reducing storage overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0047] With reference to the above-mentioned drawings, the specific implementation of the various modes included in the sensor network access control method proposed by the present invention is as follows:
[0048] 1. The specific implementation steps of mode 1:
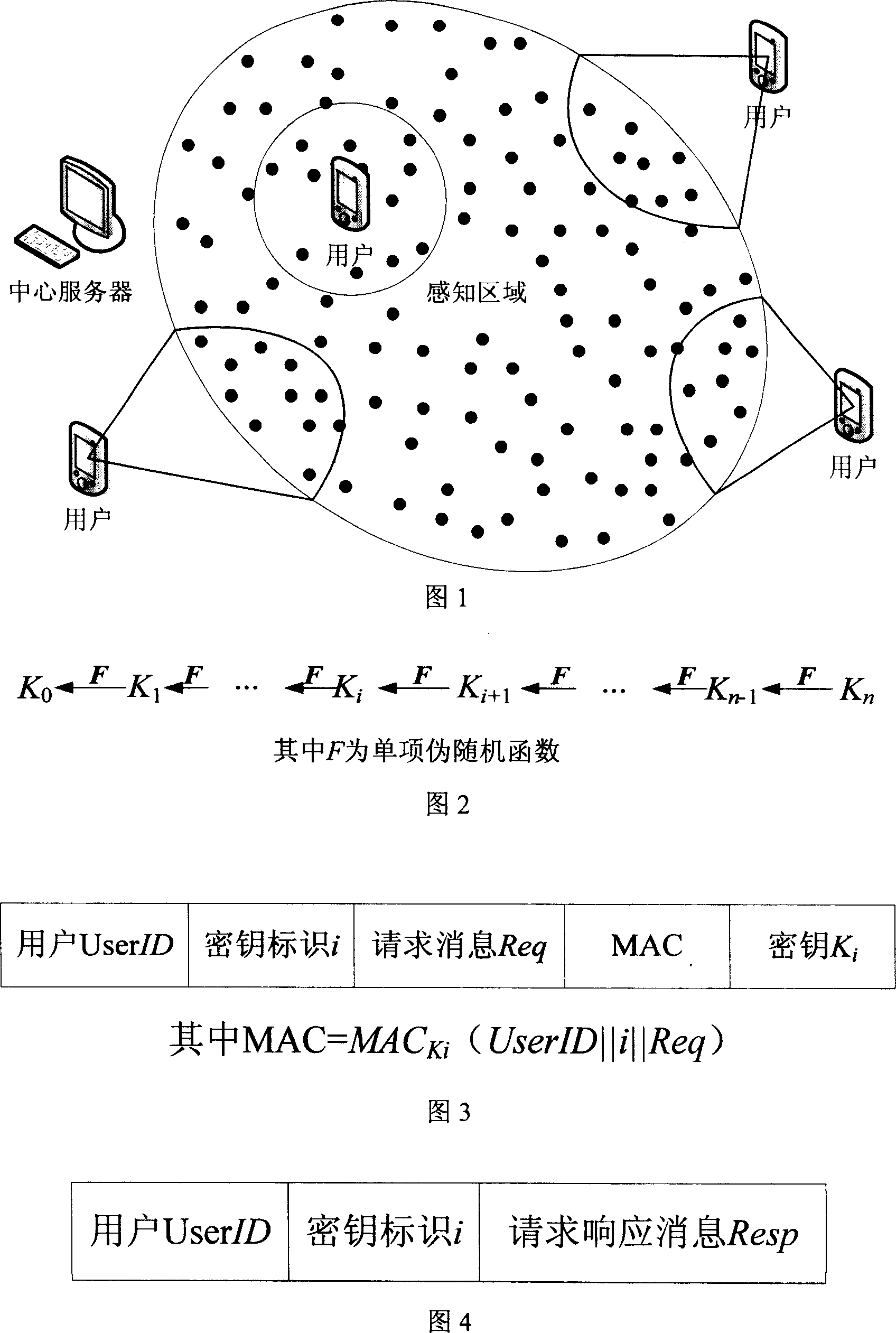
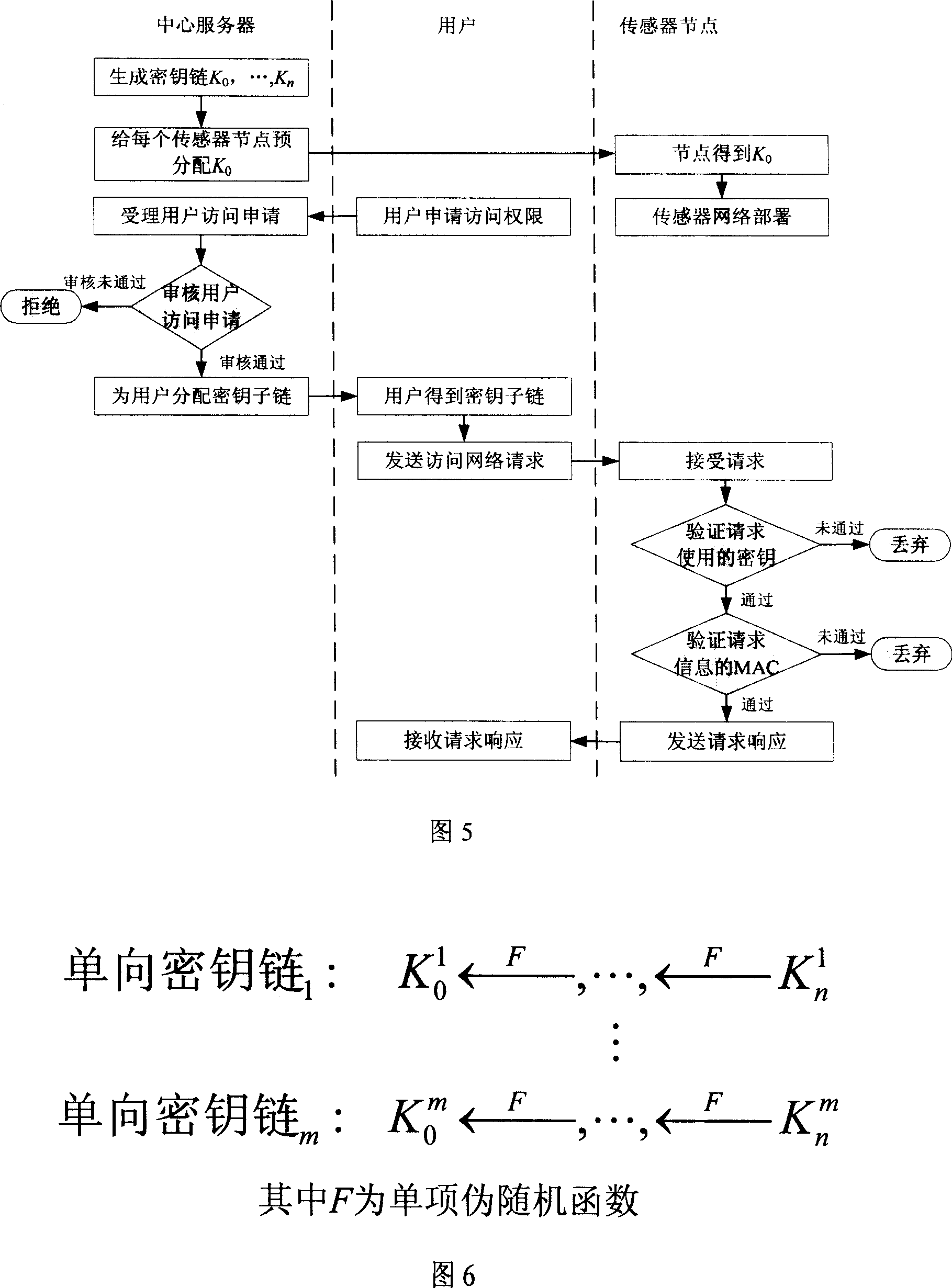
[0049] 1. One-way key chain generation: the central server first generates a one-way key chain K with length n 0 ,...,K n , the generation process is: the central server randomly selects the last key K in the key chain n , and then use a one-way pseudo-random function F (such as: hash function, MD5, etc.) to repeatedly calculate K j =F(K j+1 ), 0≤j<n, the key chain structure is shown in Figure 2;
[0050] 2. Sensor network deployment: Before the sensor network is deployed, each sensor node is pre-allocated the chain head key K of the key chain generated in step 1 0 ;
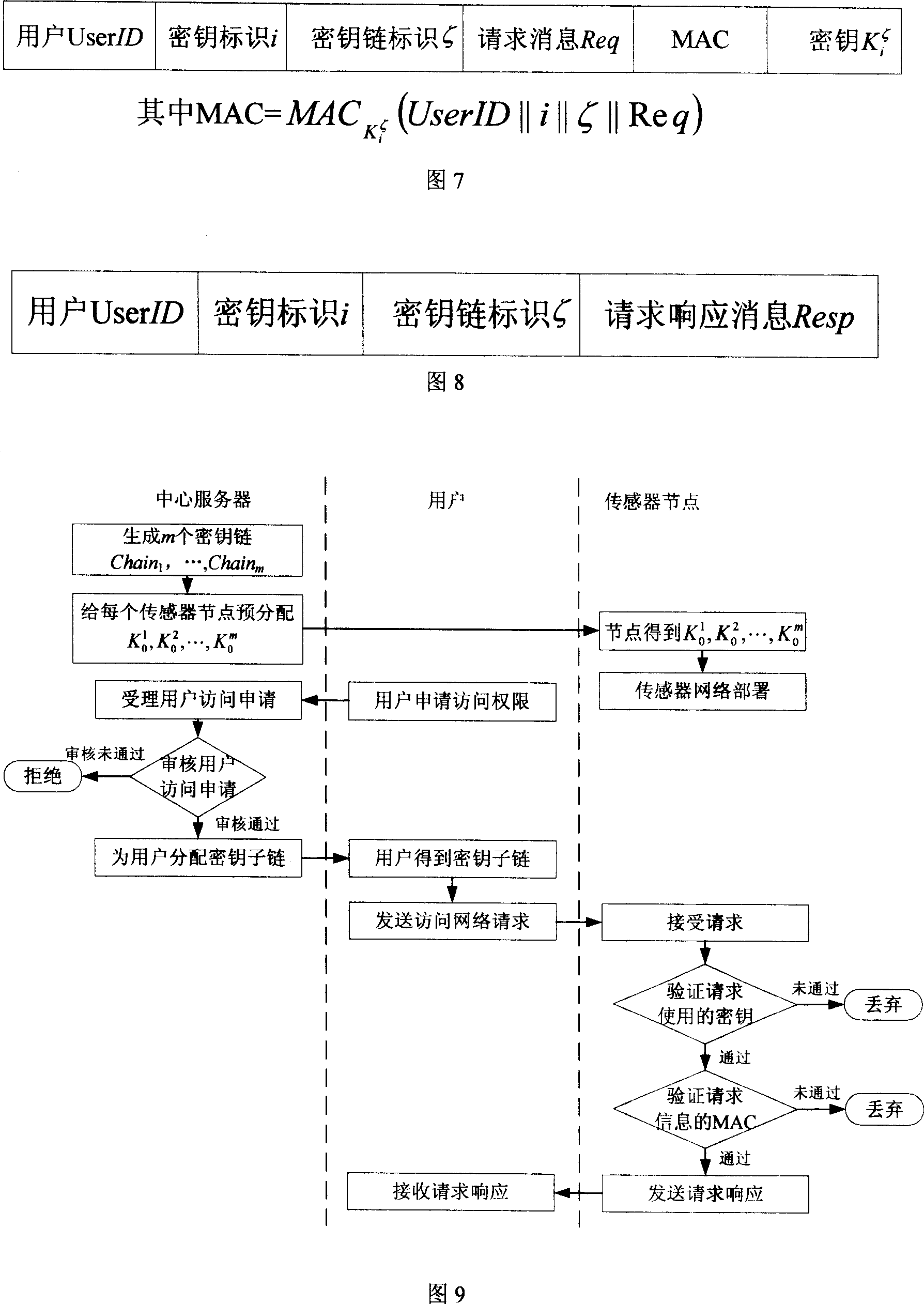
[0051] 3. User permission application: The user applies to the central server to access the sensor network, and the central server assigns the use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com