Deterministic cloud data deleting method based on sampling and fragmenting of cryptograph
A deletion method and deterministic technology, applied in the field of information security, can solve the problems of untrusted control keys by key managers, theft of control keys, failure to achieve deterministic deletion of data, etc. Strong, small amount of computation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
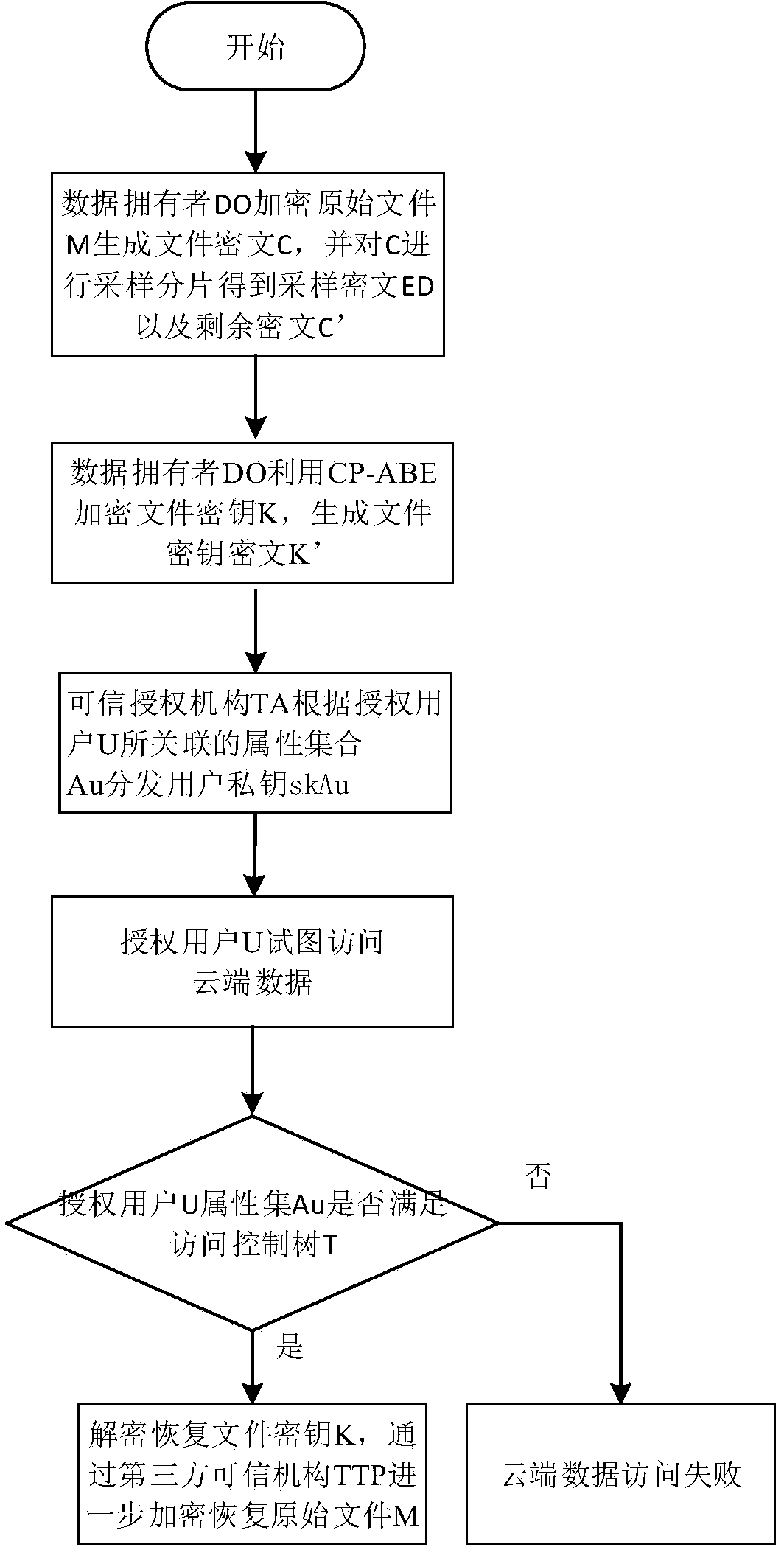
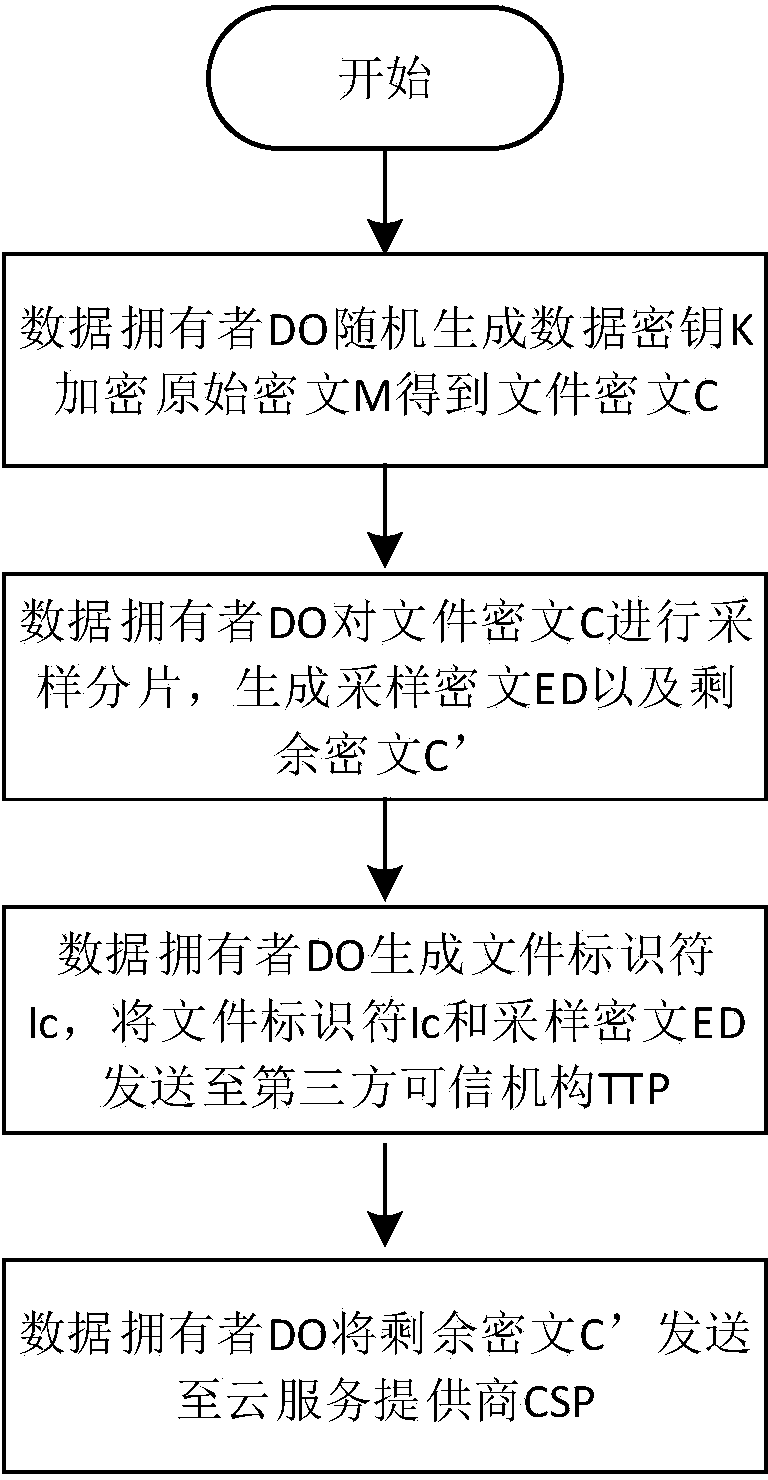
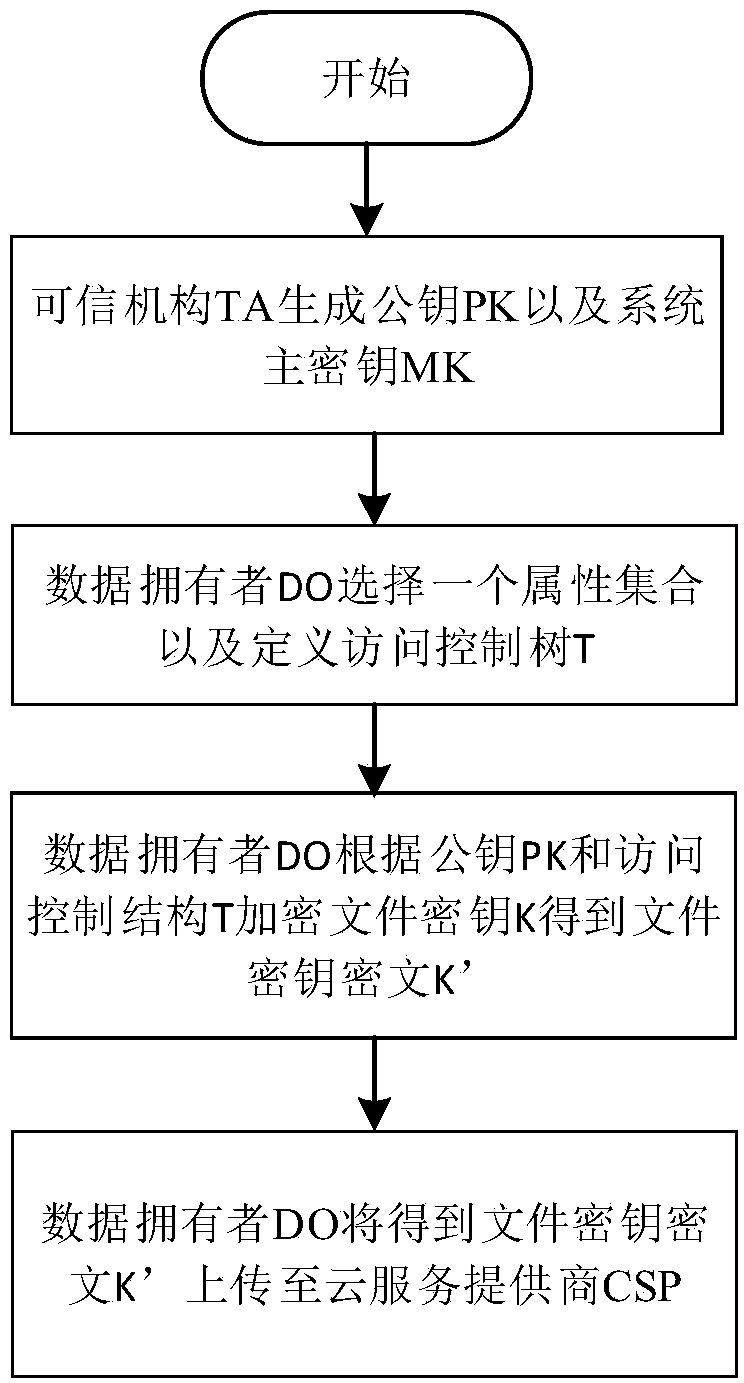
[0055] Symbols and Abbreviations
[0056] PK is the public key, MK is the master key;
[0057] M is the original file;
[0058] C is the file ciphertext;
[0059] ED is the sampled ciphertext obtained based on file ciphertext sampling
[0060] C' is the remaining ciphertext after sampling
[0061] K is the file key;
[0062] K' is the file key ciphertext, that is, the ciphertext form of the file key K encrypted by CP-ABE;
[0063] A u is the set of attributes owned by the authorized user U;
[0064] skAu is the user private key corresponding to authorized user U;
[0065] T is an attribute-based access control structure;
[0066] Enc K (M) is a symmetric encryption scheme, using the key K to encrypt M;
[0067] December K (C) is a symmetric decryption scheme, using the key K to decrypt C.
[0068] Ω is the set of system properties;
[0069] a j It is an attribute element in the system attribute collection;
[0070] G 0 is a multiplicative cyclic group of order ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com