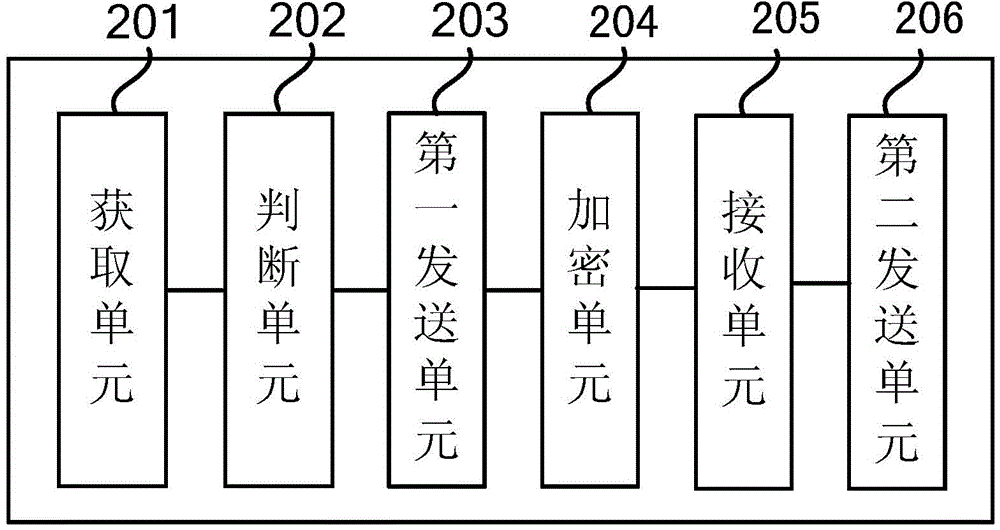
Patents
Literature
30 results about "Network Access Protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network Access Protection (NAP) is a Microsoft technology for controlling network access of a computer, based on its health. With NAP, system administrators of an organization can define policies for system health requirements. Examples of system health requirements are whether the computer has the most recent operating system updates installed, whether the computer has the latest version of the anti-virus software signature, or whether the computer has a host-based firewall installed and enabled. Computers with a NAP client will have their health status evaluated upon establishing a network connection. NAP can restrict or deny network access to the computers that are not in compliance with the defined health requirements.
Network Access Protection
ActiveUS20100325710A1Impossible to guessImprove system securityDigital data processing detailsUser identity/authority verificationNetwork Access ProtectionPassword
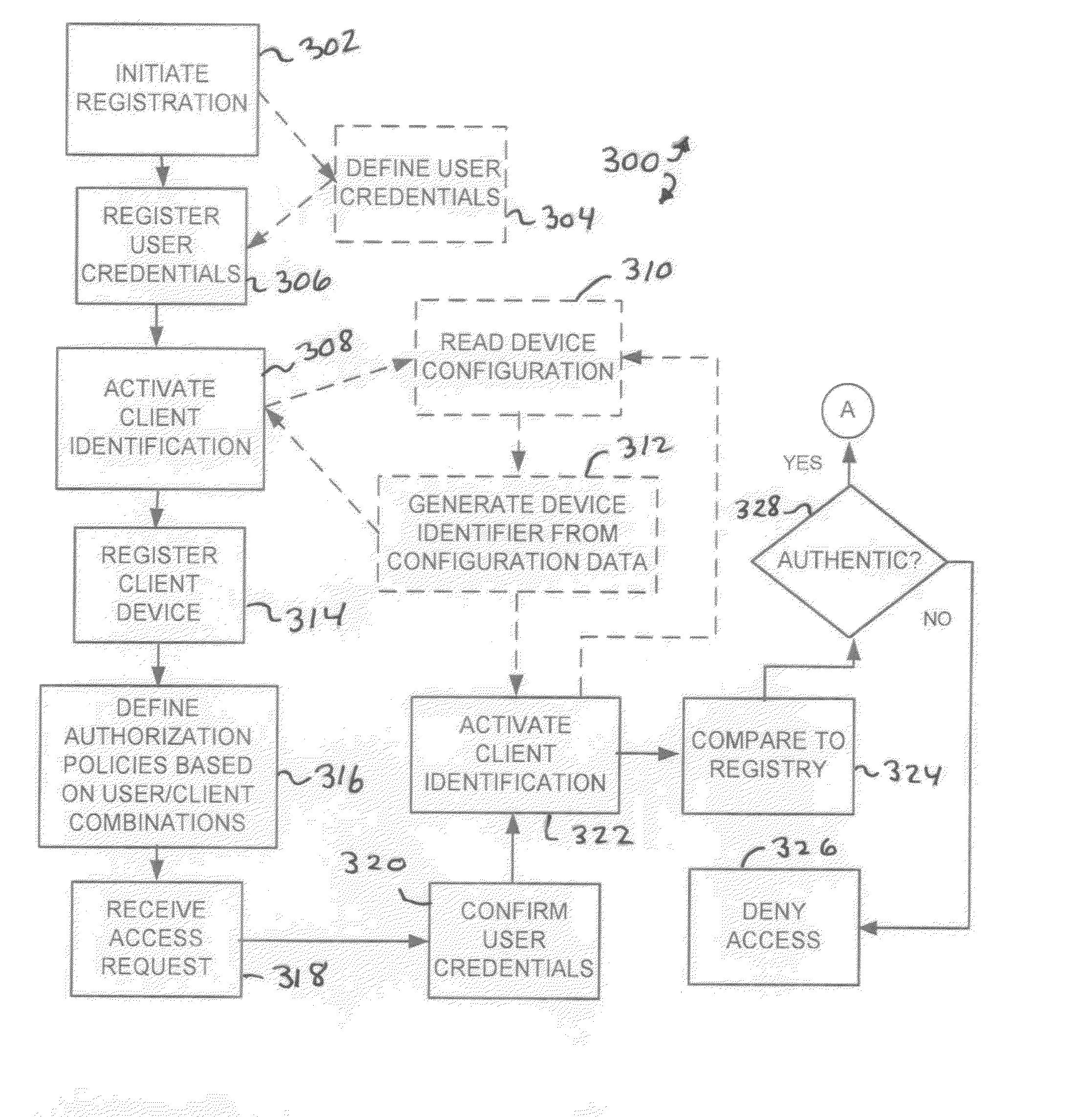
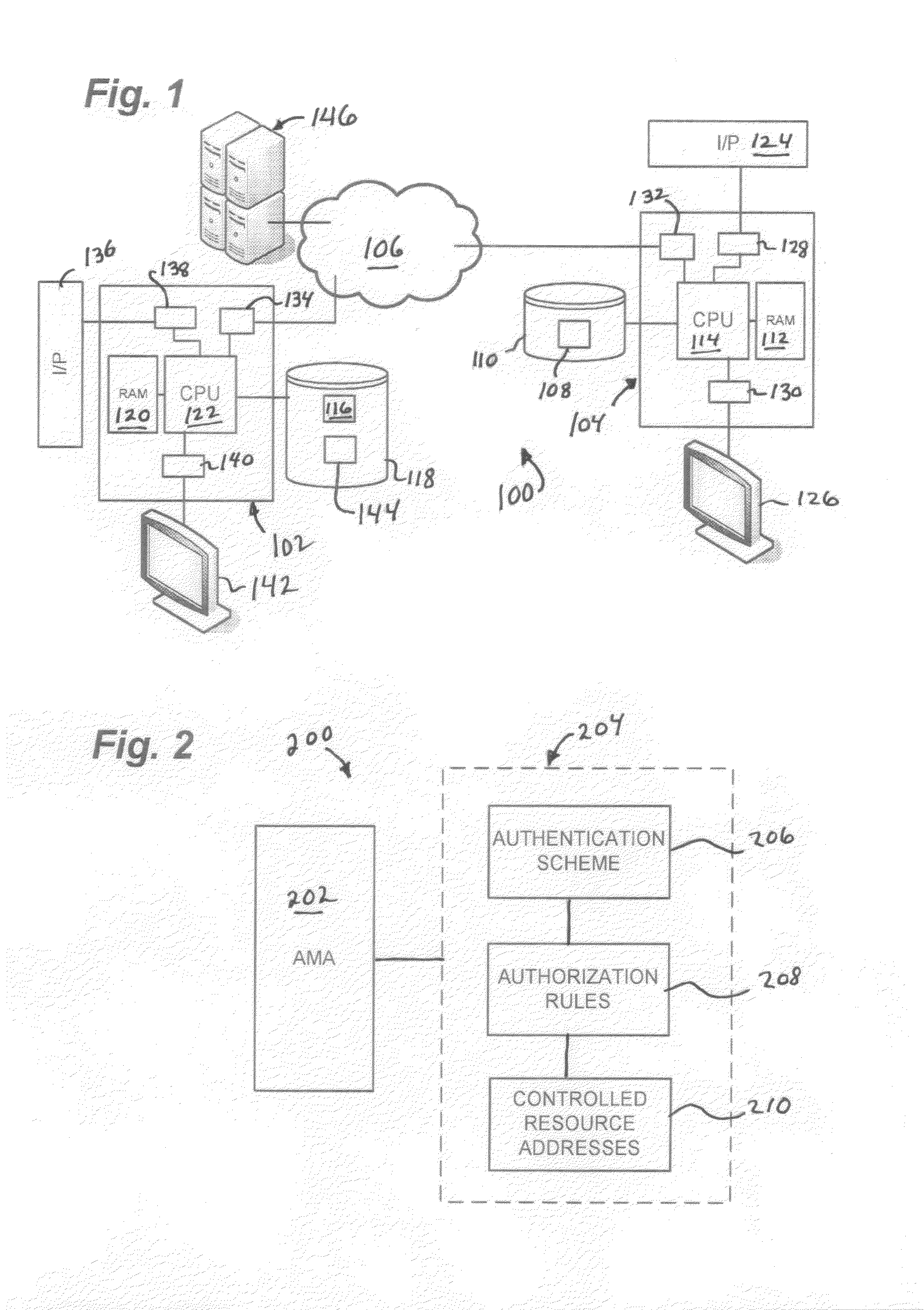
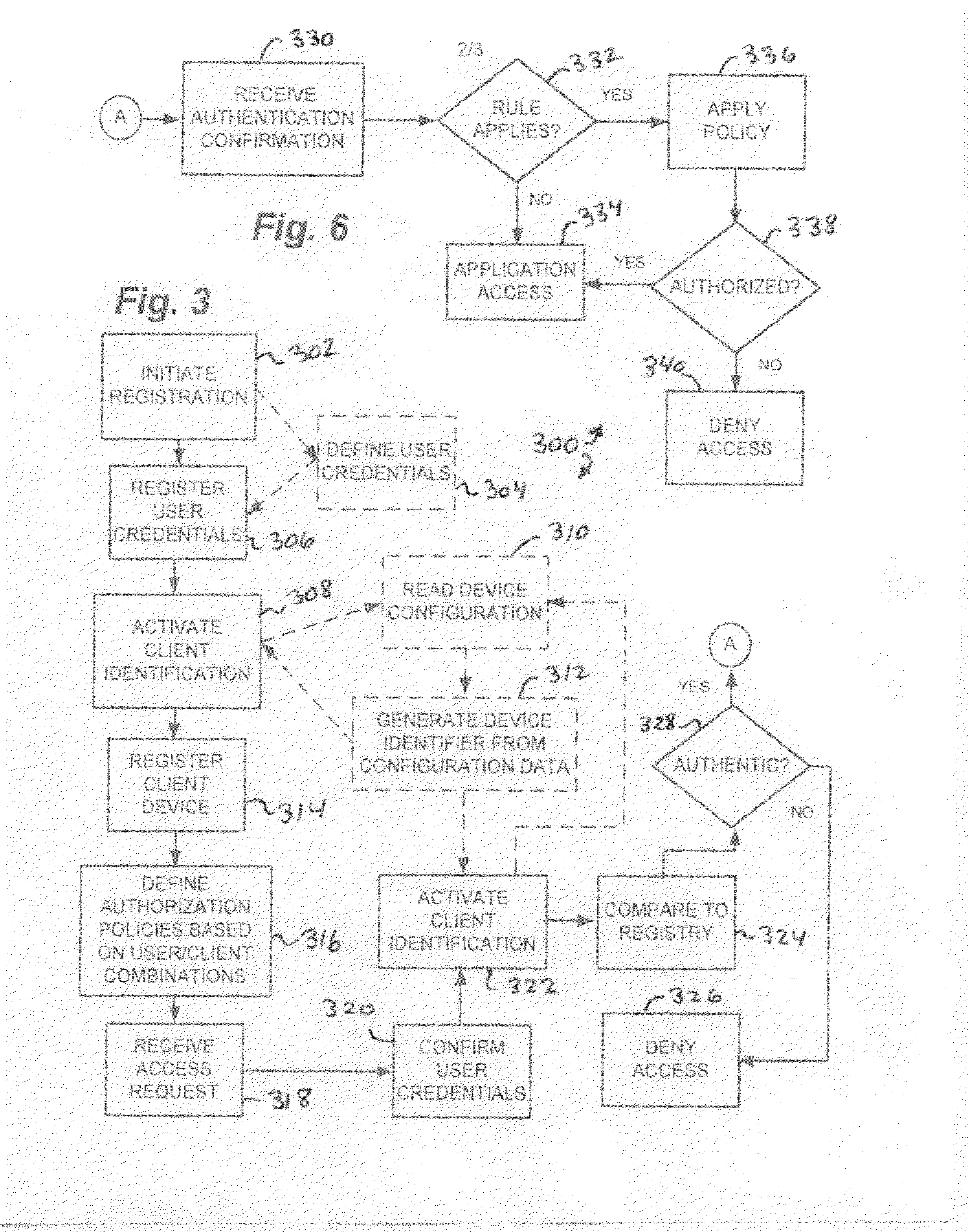
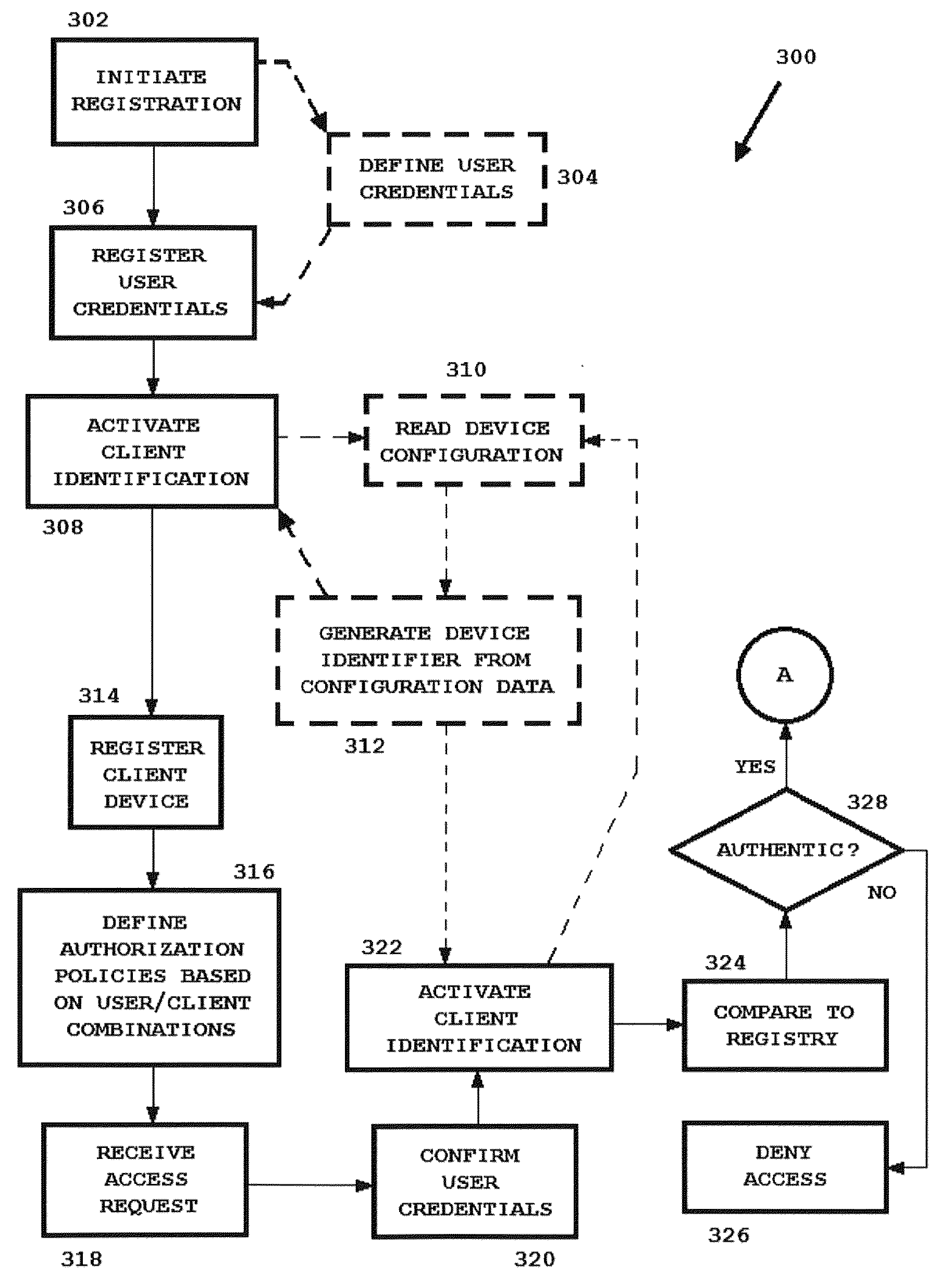
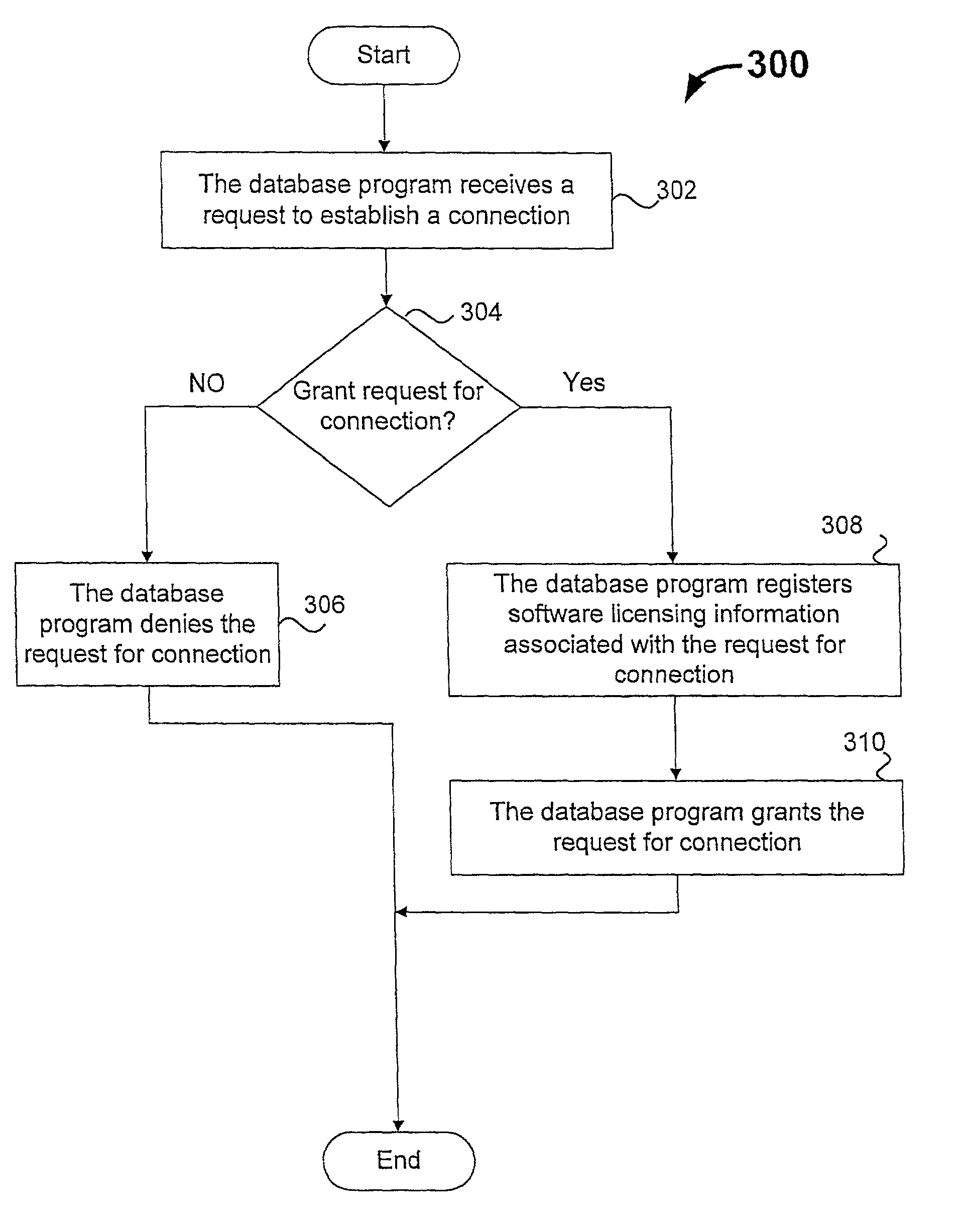
A system or method for network access protection executes steps for receiving, at a server, an access request for access to at least one network resource from a client machine, the access request including account authentication information comprising an account identifier and password, obtaining a client machine identifier from the client machine in response to receiving the request for access, and controlling access to the network resource in response to the access request by authorizing access to the network resource for the access request if the client machine identifier matches a registered machine identifier that is registered for use with the account authentication information and the account authentication information matches registered information for a valid account, but denying access to the network resource if the client machine identifier does not match a registered client machine identifier that is registered for use with the account authentication information.
Owner:DEVICE AUTHORITY LTD
Trusted network access and access control system and method
ActiveCN104618396AImplement access controlImplement network access controlUser identity/authority verificationNetwork access serverNetwork Access Protection
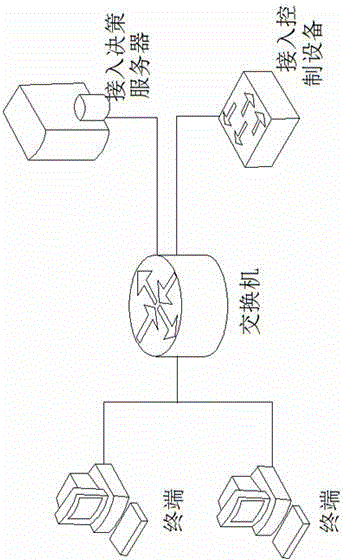
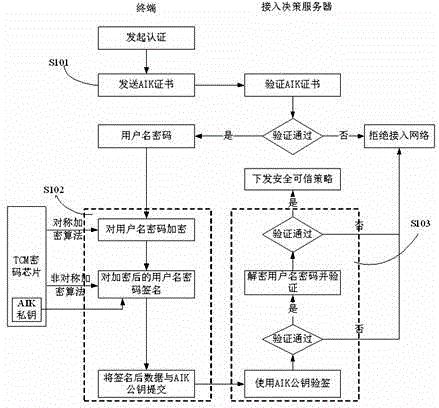
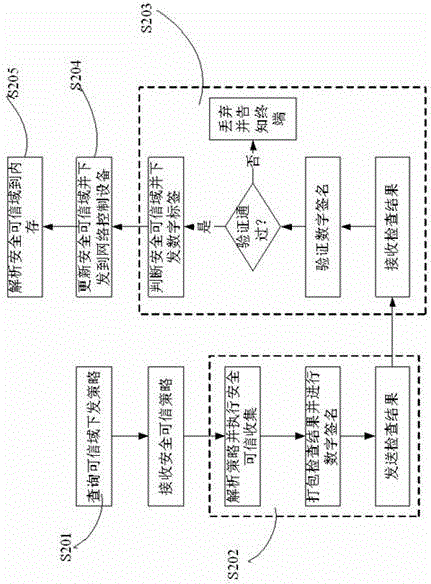
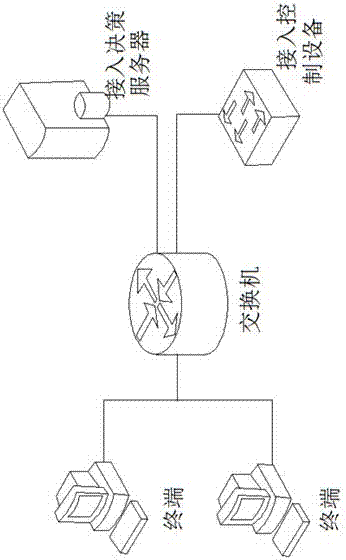
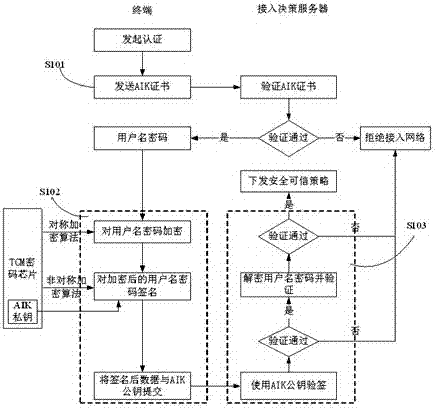
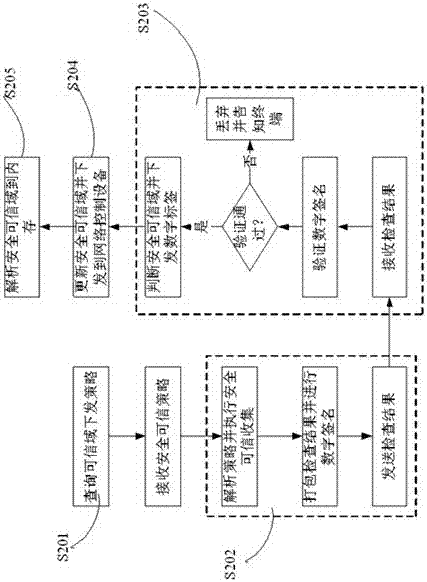
The invention discloses a trusted network access and access control system. The control system comprises a network access requester, a network access decision-maker and a network access controller. When the network access requester accesses to the network, platform identity authentication is carried out, and secure and trusted states of the requester are detected; the secure and trusted states are sent to the network access decision-maker, and the decision-maker judges the secure and trust level of the requester and gives a network access decision; the network access decision is sent to the network access controller, and the controller limits the requested network access. The invention further discloses a trusted network access and access control method. The control system carries out the platform identity authentication on the basis of TCM and ensures the network access control while avoids identity forging. Network areas are divided on the basis of a digital label technology and dynamically updated, network self-adaption is realized, and the access security of different logical areas is ensured. Secure and trusted strategies are configured, and combined with the TCM cryptographic algorithm, so that the security and credibility of the platform state of the requester are ensured.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
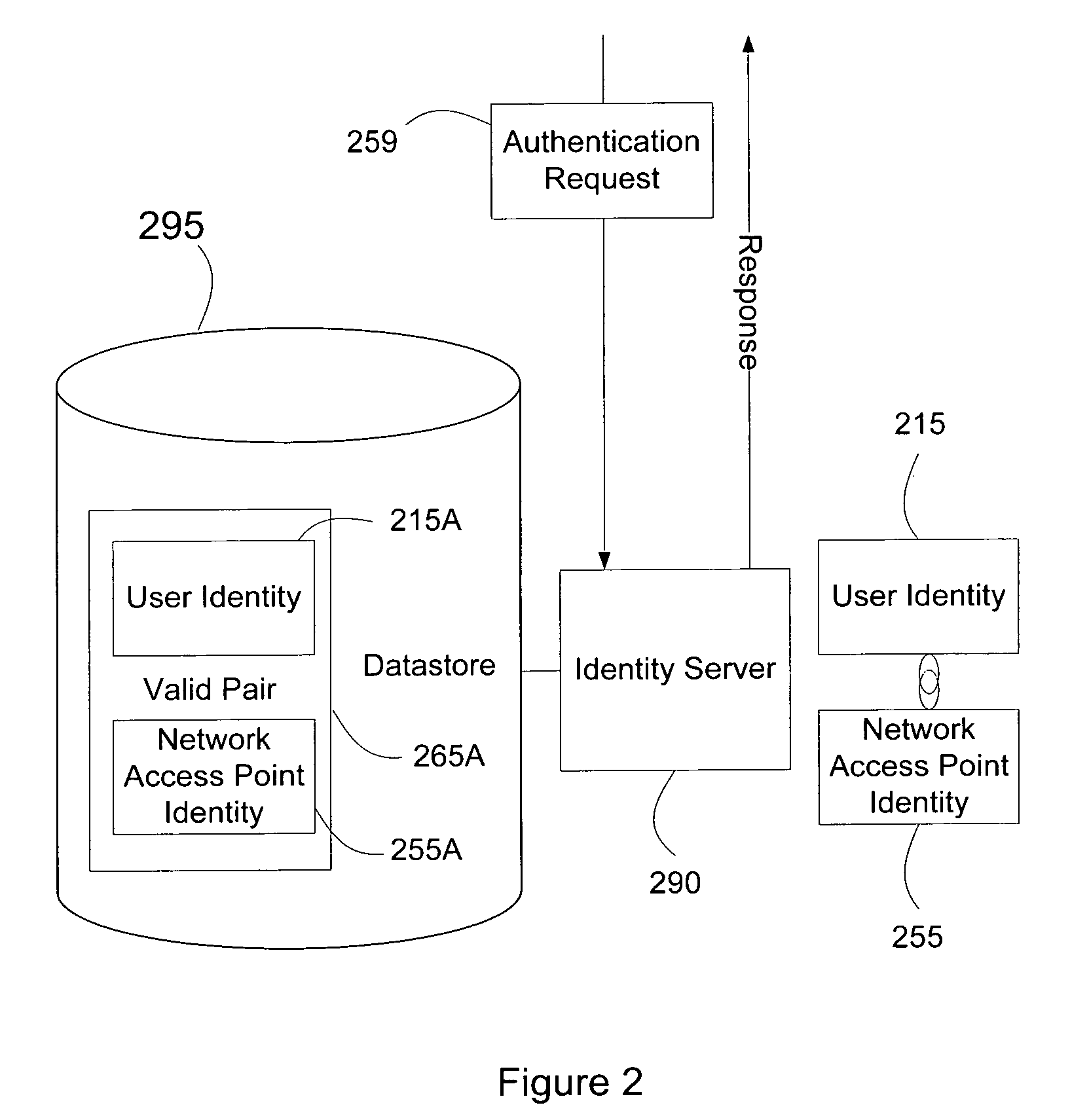
Systems and methods for user access authentication based on network access point
ActiveUS8151322B2Digital data processing detailsUnauthorized memory use protectionTime informationNetwork Access Protection
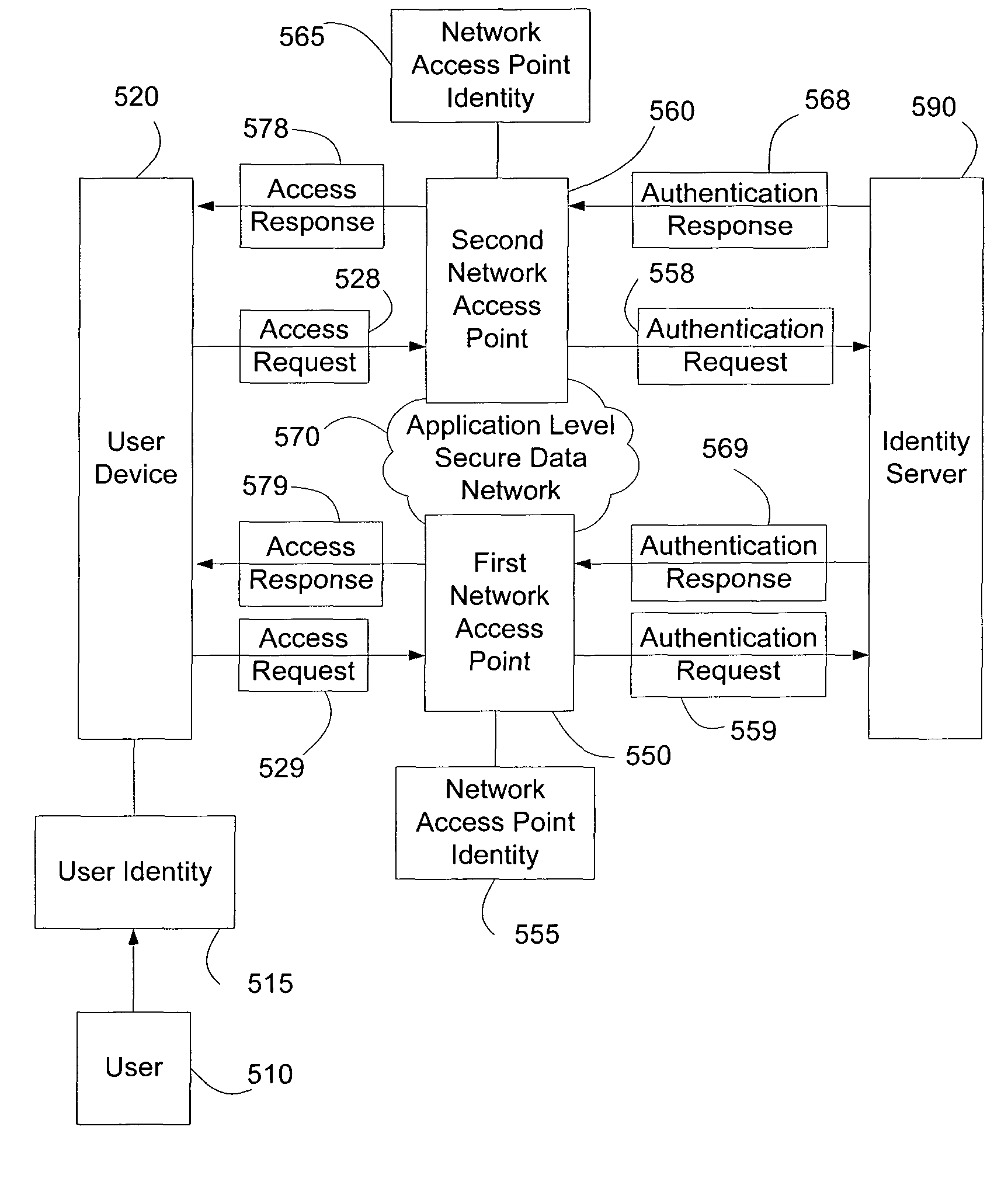
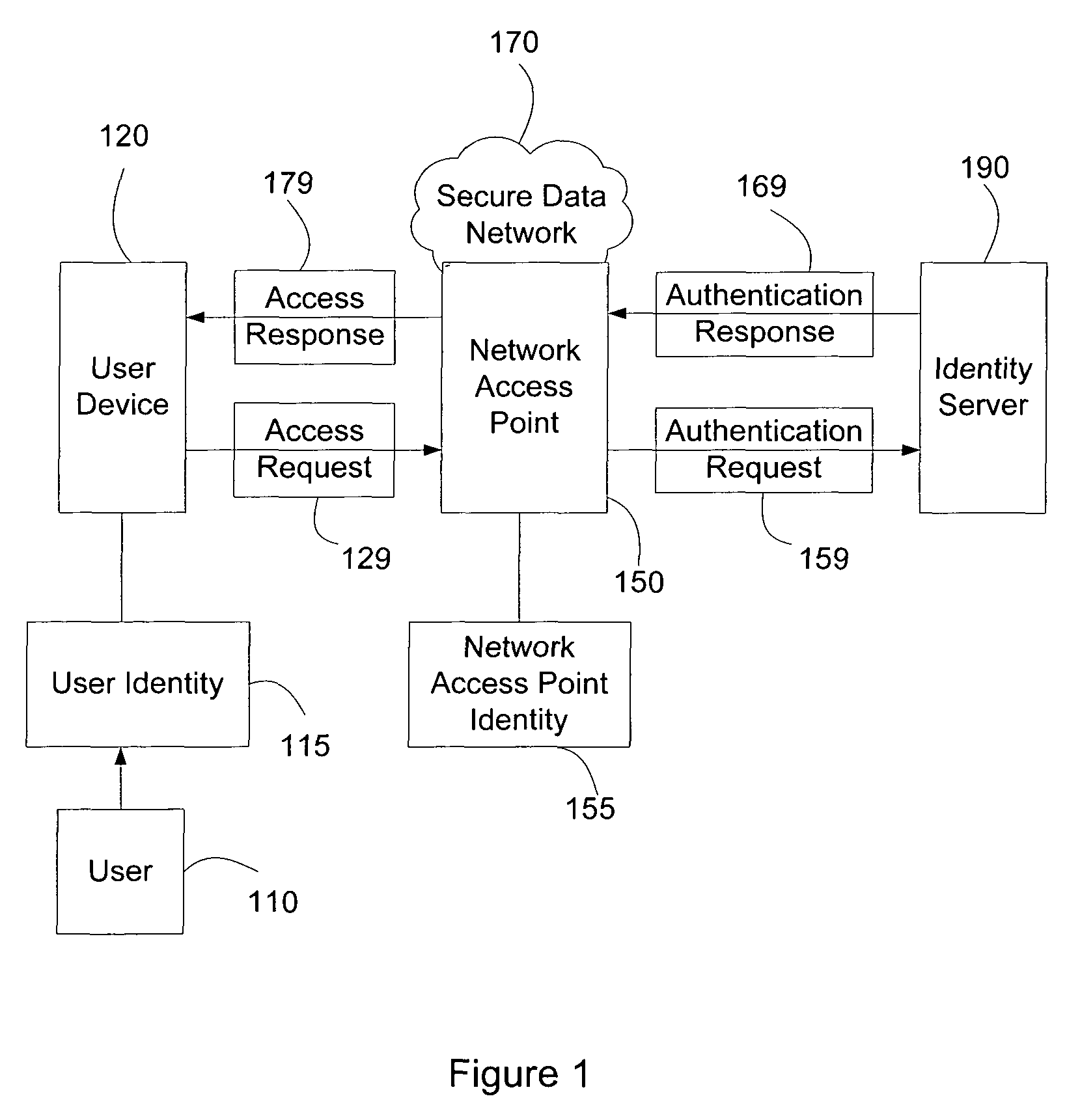
Systems and methods of authenticating user access based on an access point to a secure data network include a secure data network having a plurality of a network access points serving as entry points for a user to access the secure data network using a user device. The user is associated with a user identity, each network access point with a network access point identity. The user uses a user device to send an access request, requesting access to the secure data network, to the network access point, which then sends an authentication request to an identity server. The identity server processes the authentication request, by validating the combination of the user identity and the network access point identity, and responds with an authentication response, granting or denying access, as communicated to the user device via an access response. The secure data network may comprise an application level secure data network, in which the user uses the user device to request access to a network application. Furthermore, the identity server may validate the combined user identity and network access point identity data in conjunction with time information, access allowance data, and / or traffic volume data.
Owner:A10 NETWORKS
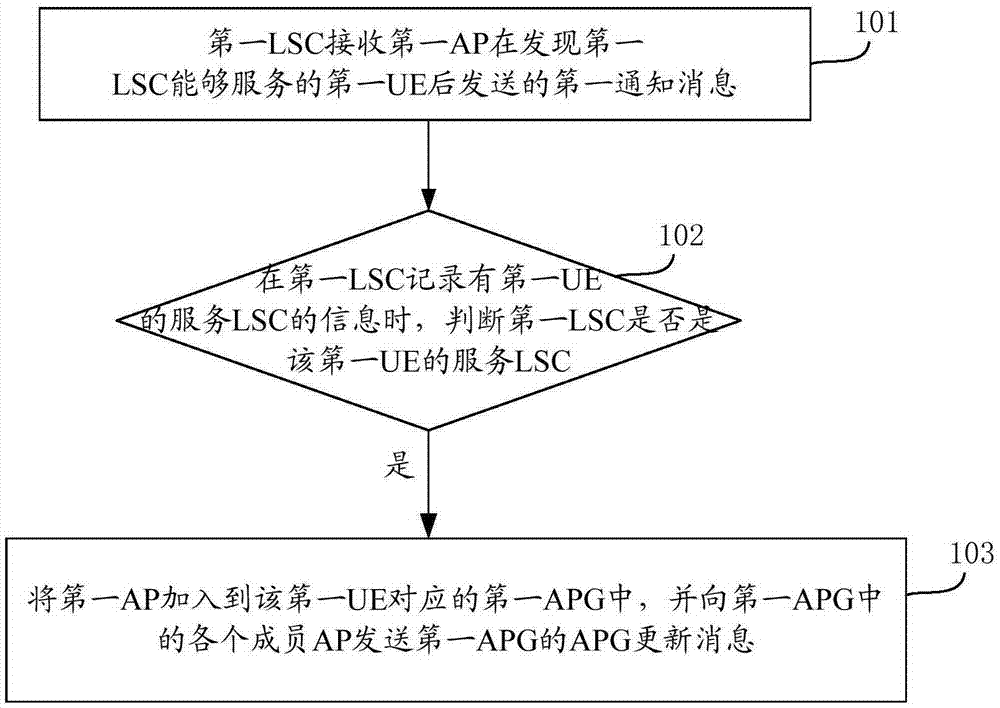
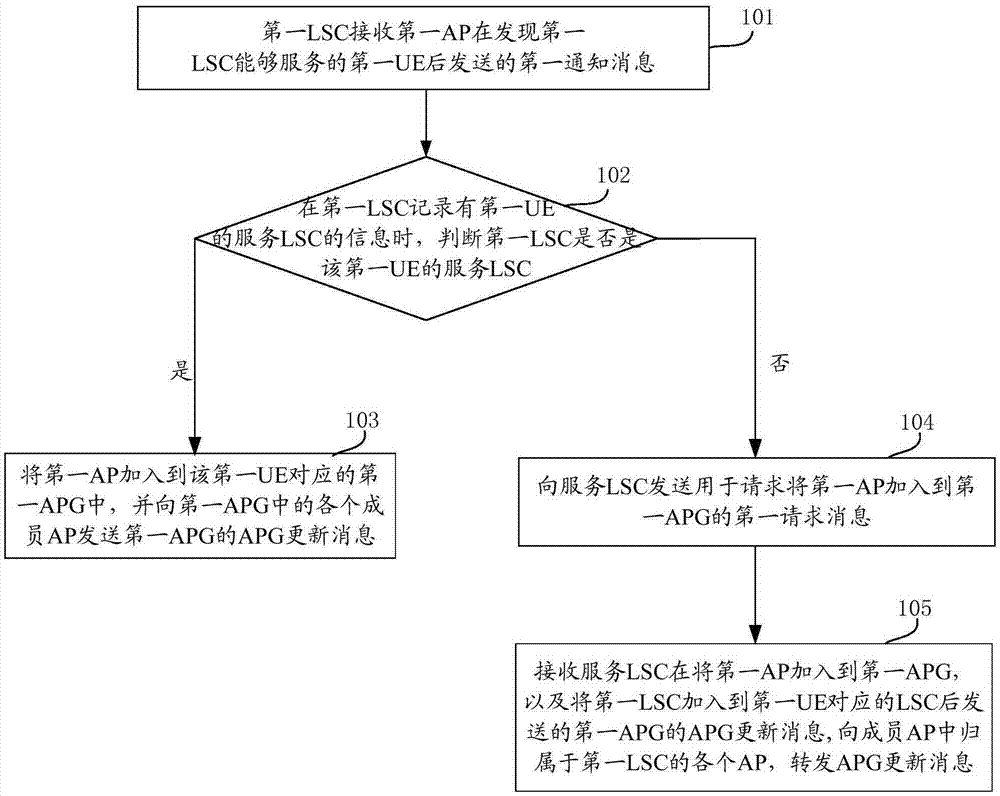
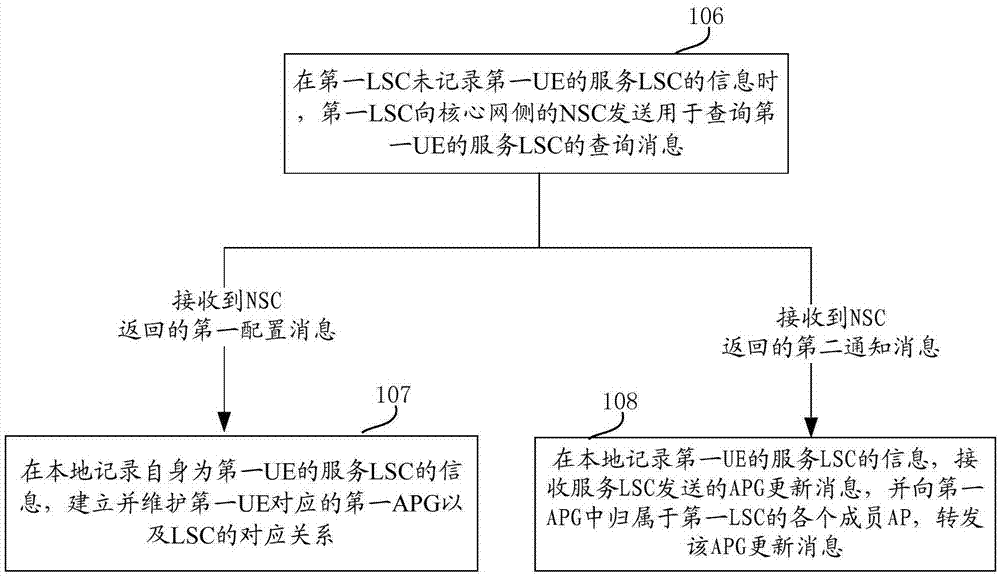
Dynamic networking method and equipment for network access points
ActiveCN105451250AReduce switching timesAvoid frequent perceptionNetwork traffic/resource managementNetwork data managementNetwork Access ProtectionStatic mode
The invention provides a dynamic networking method and equipment for network access points. According to the embodiment of the invention, the traditional network-centered idea is changed into the user-centered idea and services are provided for users, thereby preventing the user from sensing the network environment frequently and providing a data transmission service of the user in a low-speed or static mode by an APG. Moreover, during the movement process of the user, the user service transmission can be realized based on dynamic APG updating and AP cooperation in the APG. Therefore, the number of times for user switching can be reduced and user switching in the APG does not need to use the core network, thereby reducing the signaling load of the core network.
Owner:DATANG MOBILE COMM EQUIP CO LTD
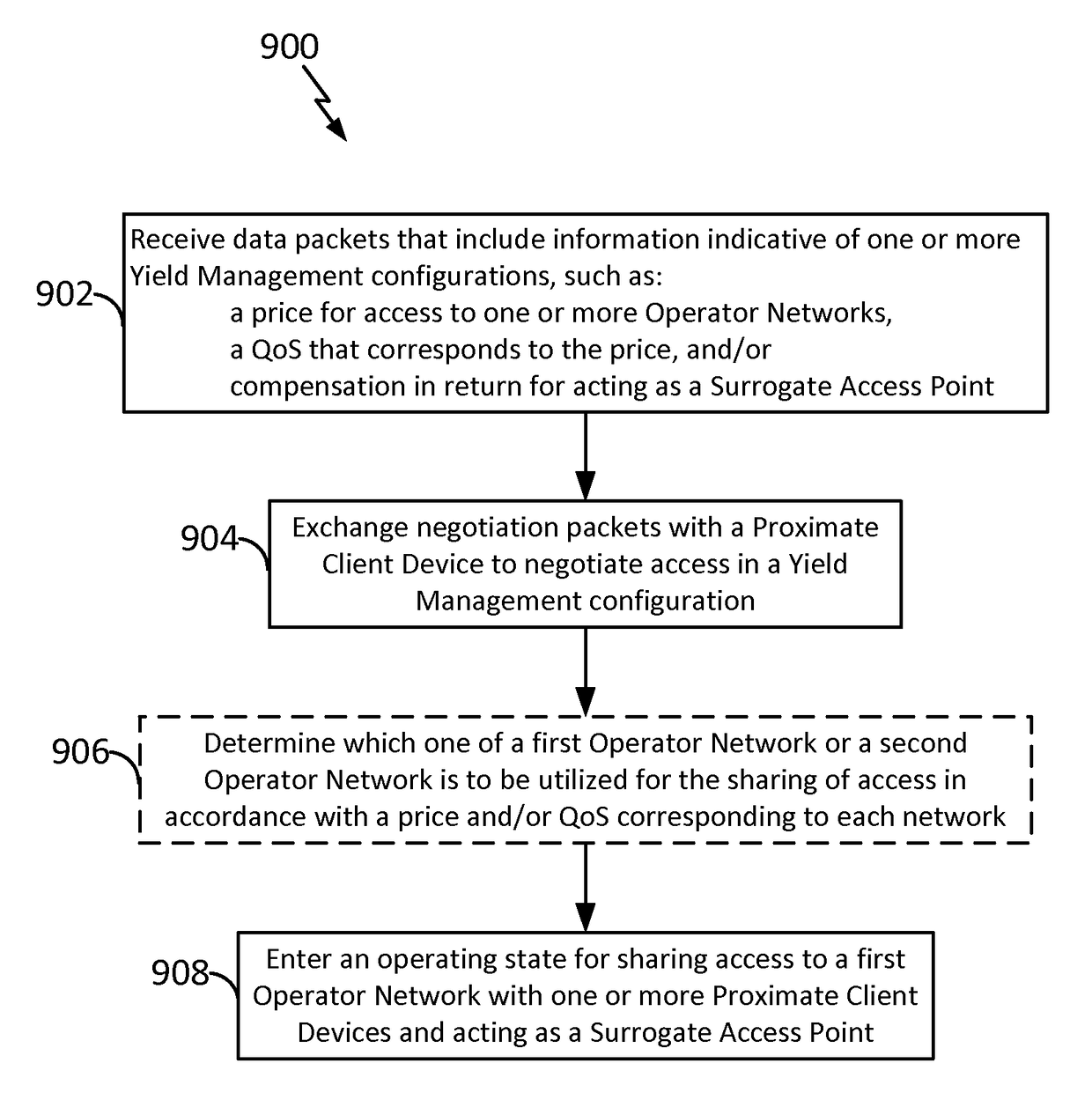
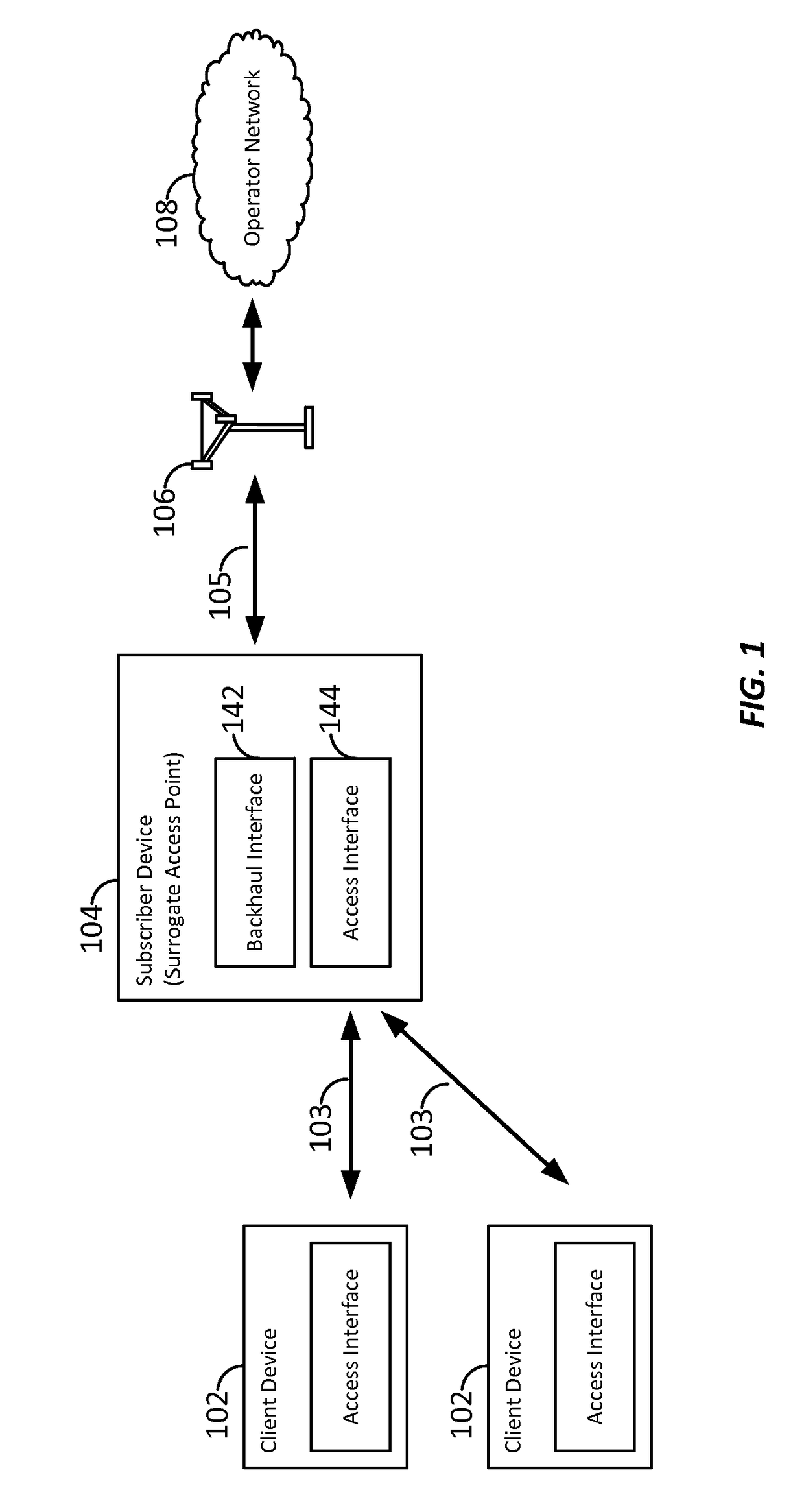
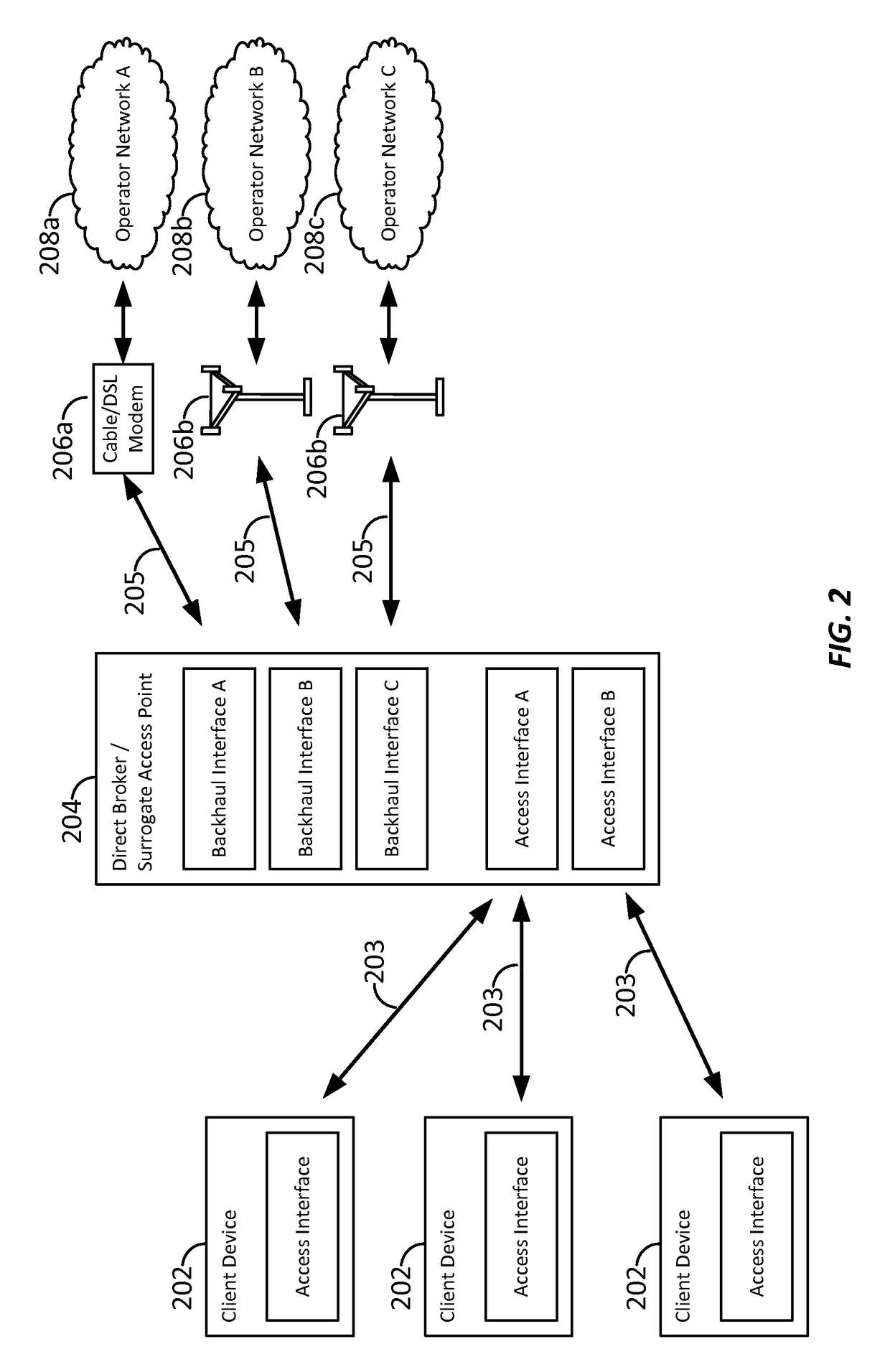
Peer-enabled network access extension using yield management
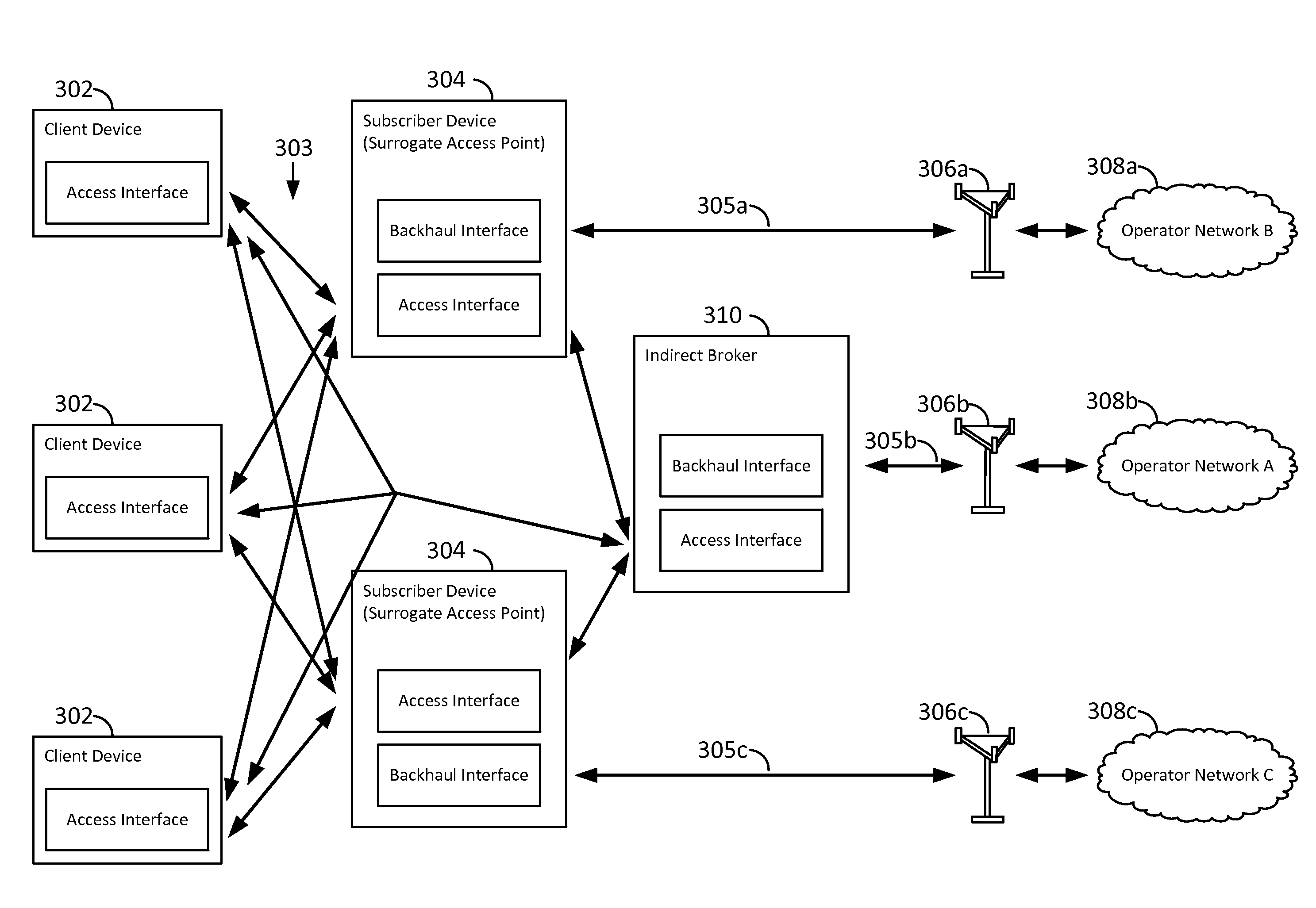
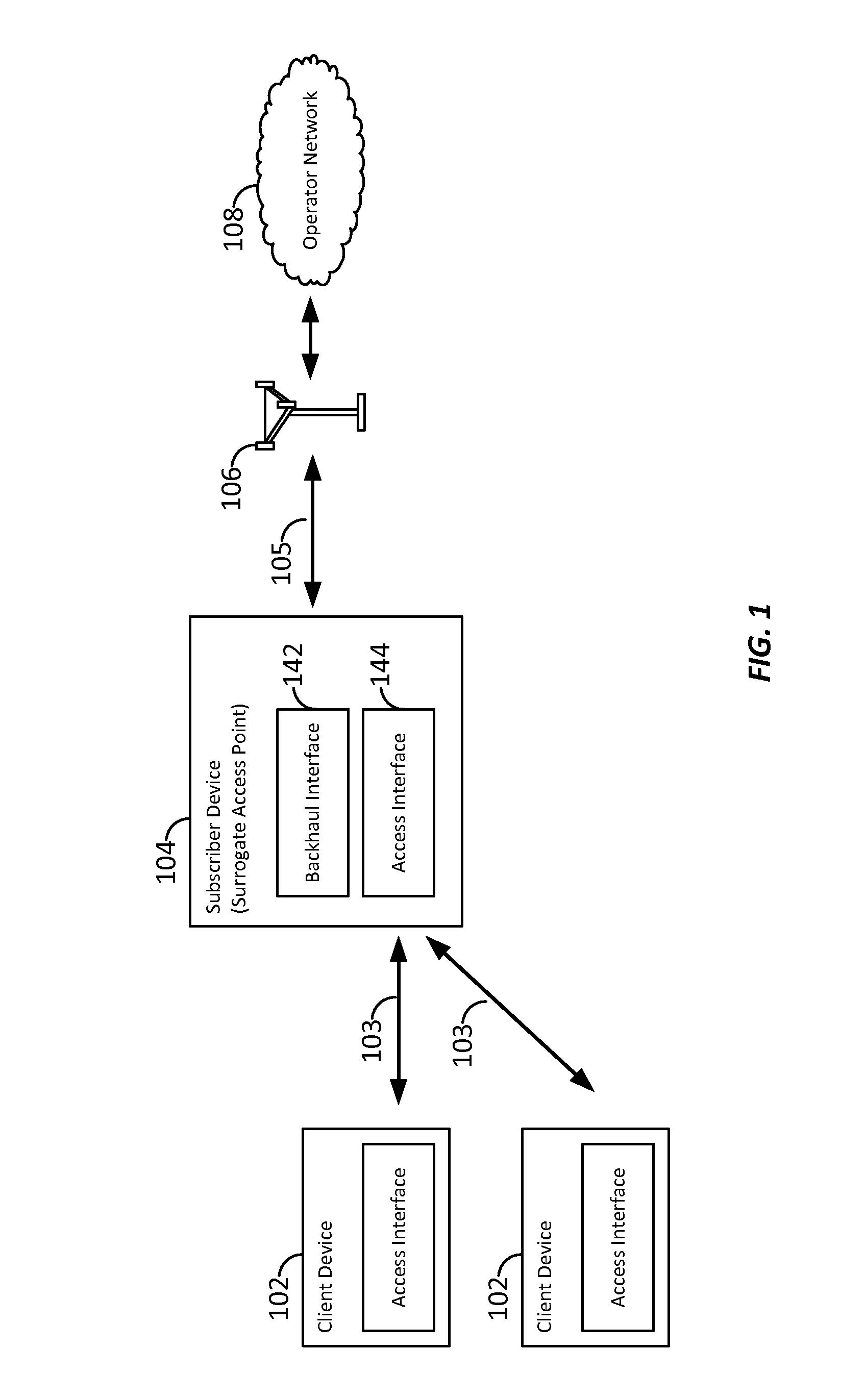
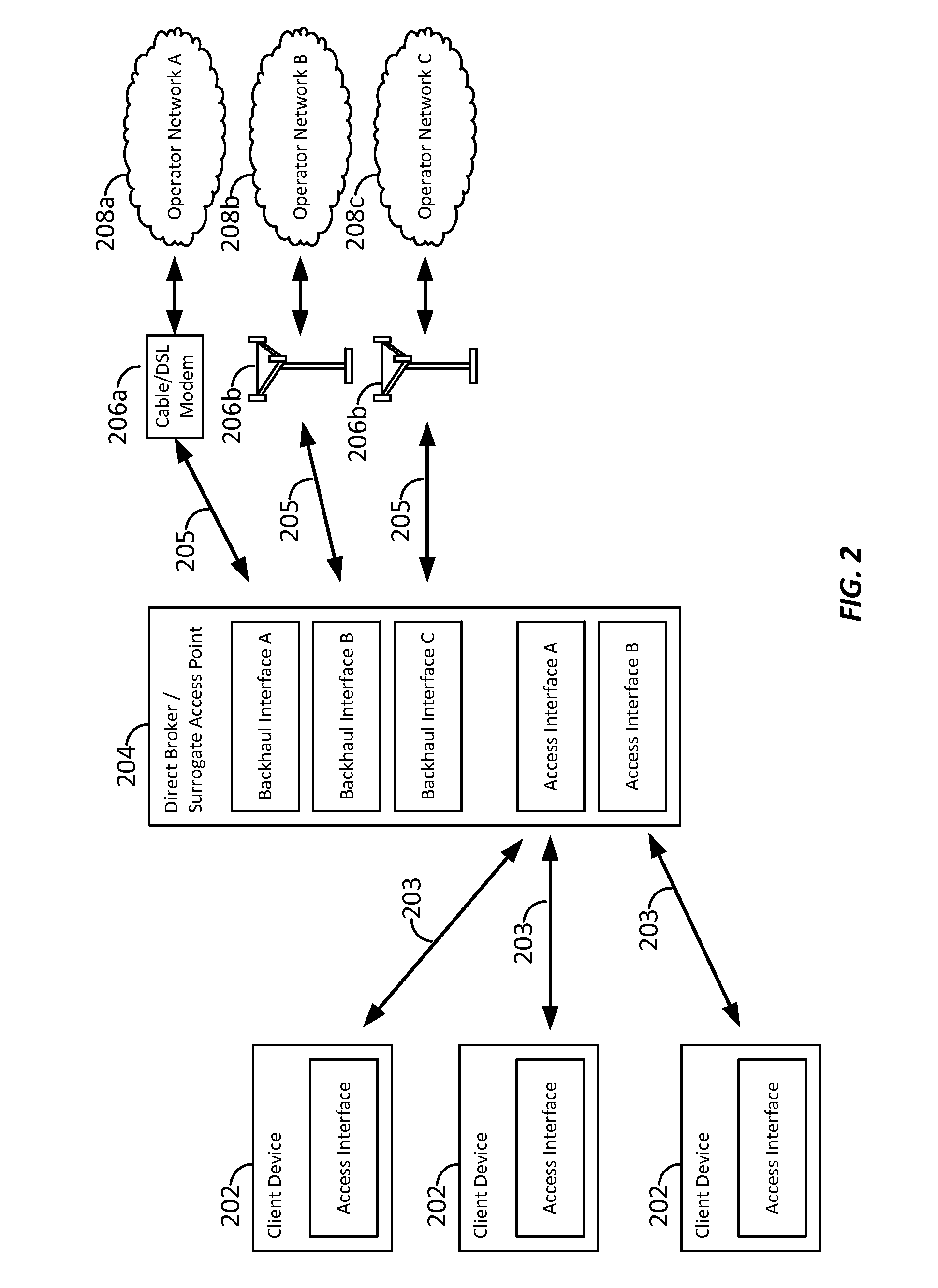
ActiveUS20160204951A1Well formedMultiplex system selection arrangementsSpecial service provision for substationCommunication interfaceNetwork Access Protection
Aspects of the present disclosure provide for yield management models for dynamically pricing access to wireless communication services. In some examples, access to a network is intermediated by a surrogate access point, which may act as a proxy or relay, expanding communication services to client devices that otherwise may lack a subscription, or may lack a suitable communication interface, to communicate directly with the wireless network. Here, the surrogate access point may be a subscriber device or user equipment. By utilizing the yield management model, the surrogate access point may receive compensation for sharing its connection to the network with nearby client devices. Other aspects, embodiments, and features are also claimed and described.
Owner:QUALCOMM INC
Trusted network access method and system for mobile terminal
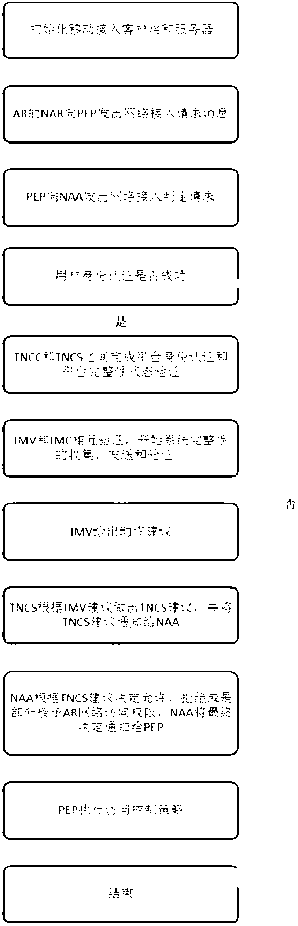
The invention discloses a trusted network access method and a trusted network access system for a mobile terminal, and belongs to the technical field of trusted network access. The method comprises the following steps that: 1) the mobile terminal loads an integrity measurement collector and detects the integrity of the integrity measurement collector, and a policy decision point loads an integrity measurement verifier and detects the integrity of the integrity measurement verifier; 2) the mobile terminal transmits a network access request to a policy enforcement point; 3) after receiving the network access request, the policy enforcement point transmits a network access judgment request to the policy decision point, and authenticates the user identity of the mobile terminal; 4) after the user identity passes authentication, platform identity authentication is performed between the policy decision point and the mobile terminal, the policy decision point and the mobile terminal mutually authenticate system integrity, and a platform trust relationship between the policy decision point and the mobile terminal is established; and 7) the policy decision point transmits a suggestion indicating whether to access the policy enforcement point according to the platform trust relationship, and the policy enforcement point authorizes network access permission to the mobile terminal according to the suggestion. By the method and the system, network resources can be well protected.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Network access protection
ActiveUS9047458B2Digital data processing detailsUser identity/authority verificationNetwork Access ProtectionPassword
A system or method for network access protection executes steps for receiving, at a server, an access request for access to at least one network resource from a client machine, the access request including account authentication information comprising an account identifier and password, obtaining a client machine identifier from the client machine in response to receiving the request for access, and controlling access to the network resource in response to the access request by authorizing access to the network resource for the access request if the client machine identifier matches a registered machine identifier that is registered for use with the account authentication information and the account authentication information matches registered information for a valid account, but denying access to the network resource if the client machine identifier does not match a registered client machine identifier that is registered for use with the account authentication information.
Owner:DEVICE AUTHORITY LTD
Download method and system based on home gateway, and home gateway
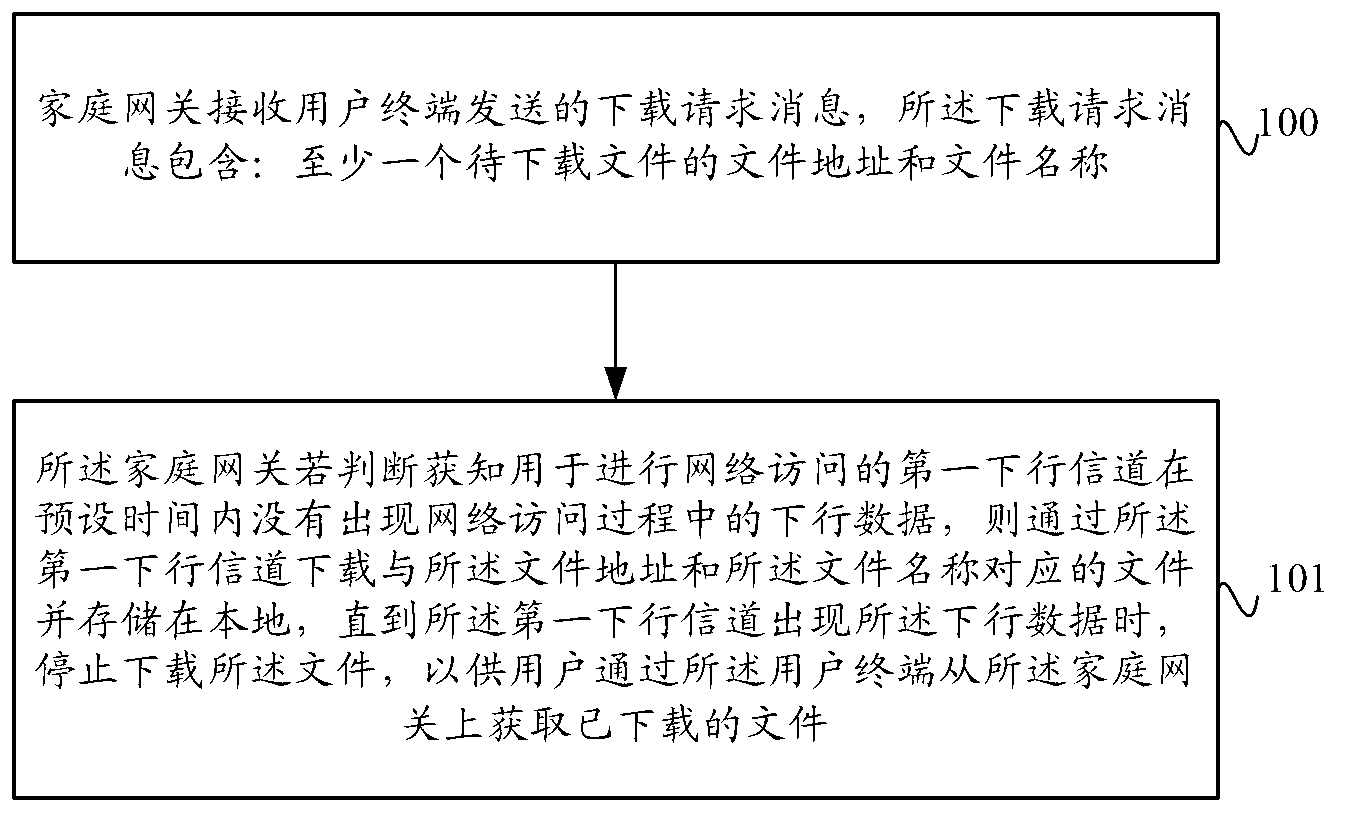
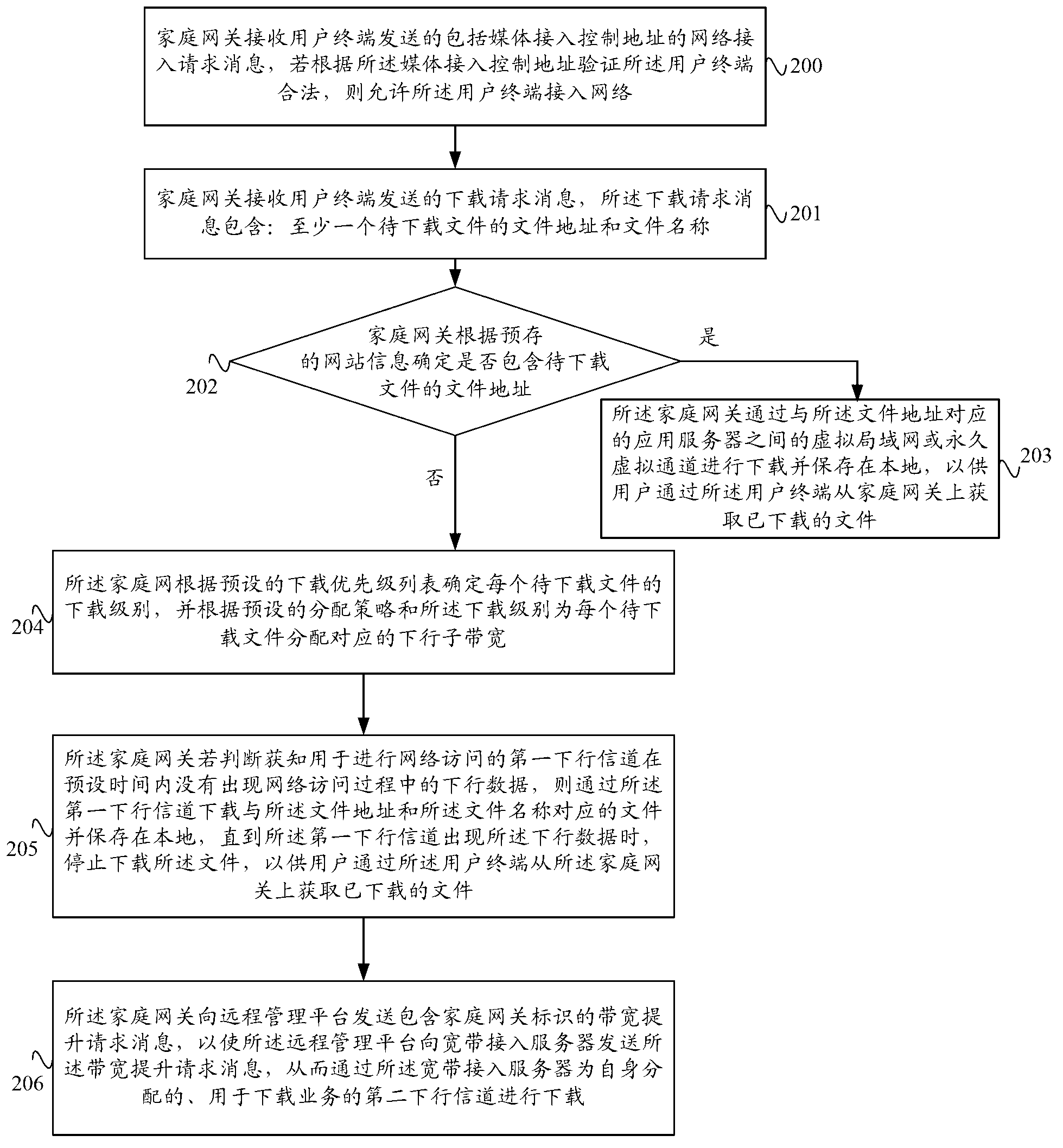
ActiveCN102916907AAffect normal network access businessAffect network access businessNetwork connectionsNetwork Access DeviceNetwork Access Protection
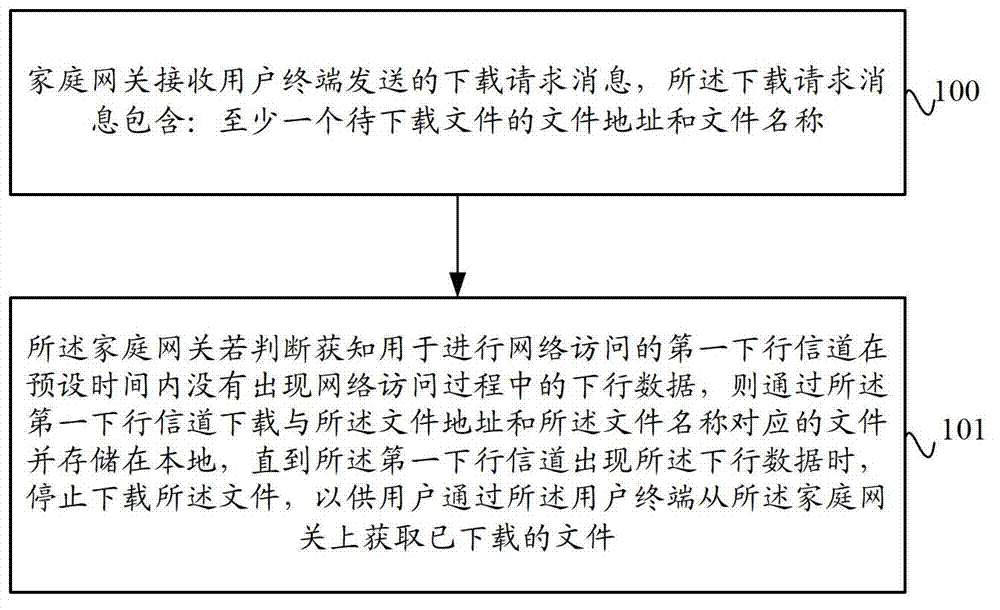
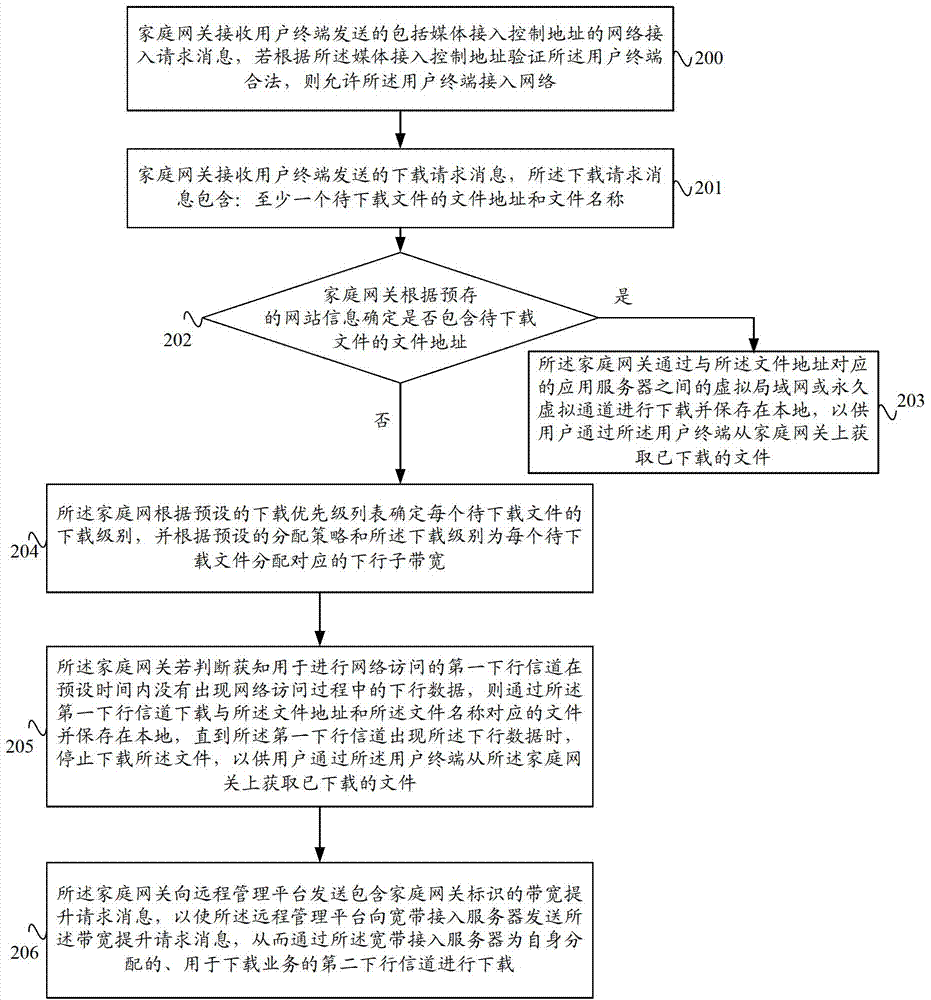
The invention provides a download method and a download system based on a home gateway, and the home gateway, and the home gateway, wherein the method comprises the following steps: a download request message, including the document address and the document name of at least one document to be downloaded, sent by a user terminal is received by the home gateway; if the downlink data in the network access process does not appear within the preset time of a first downlink channel used for performing the network access, the document corresponding to the document address and the document name is downloaded through the first downlink channel, and the downloading of the document is stopped until the downlink data occur on the first downlink channel. Through the download method and the download system based on the home gateway, and the home gateway provided by the invention, the document can be downloaded through the home gateway when the user terminal does not perform the network access, thereby the network bandwidth is more fully and reasonably utilized, the download in the prior art when the user terminal performs the network access is avoided; and the occupation of a large quantity of bandwidths can influence the normal network access business of a user.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Technique for downloading a network access profile
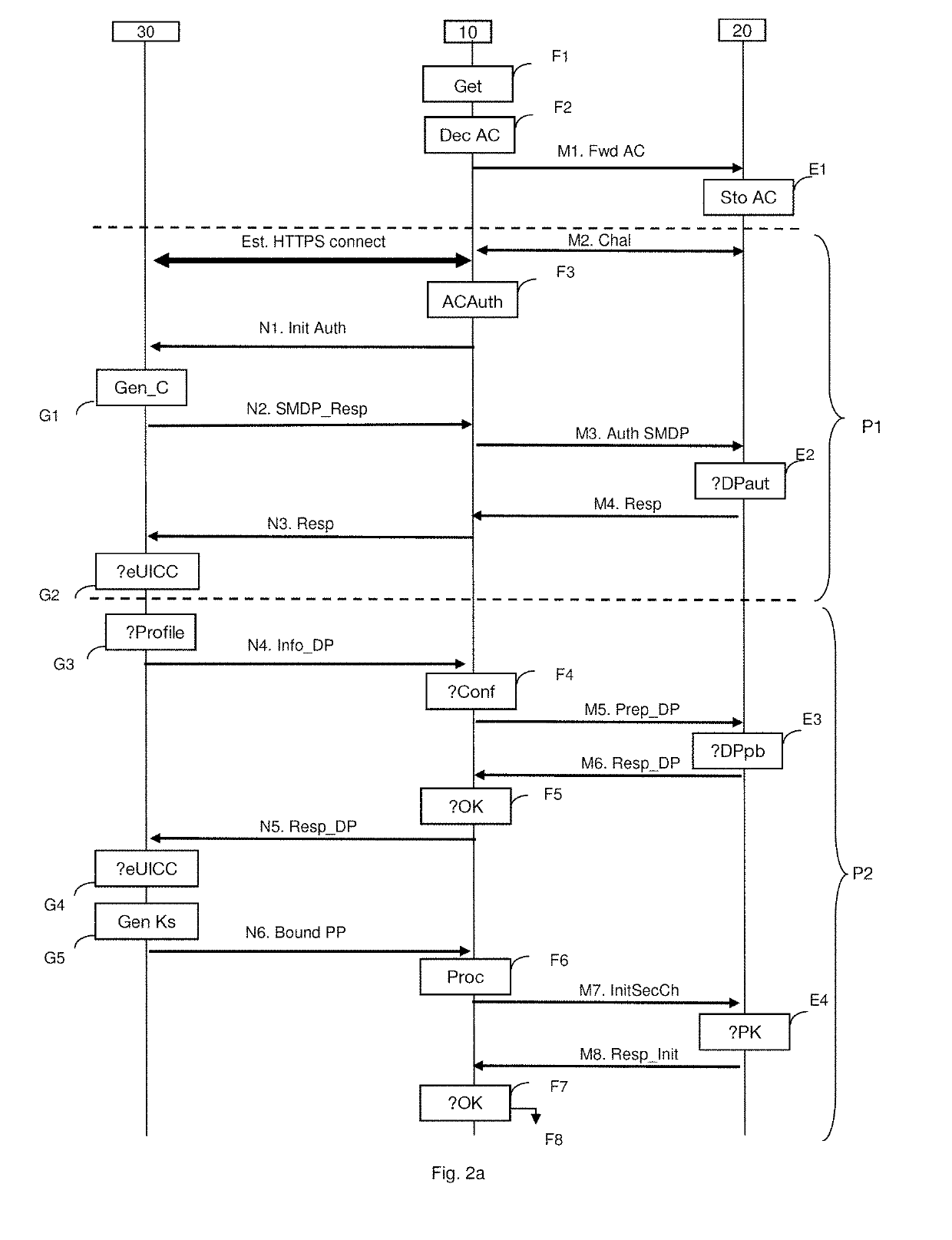
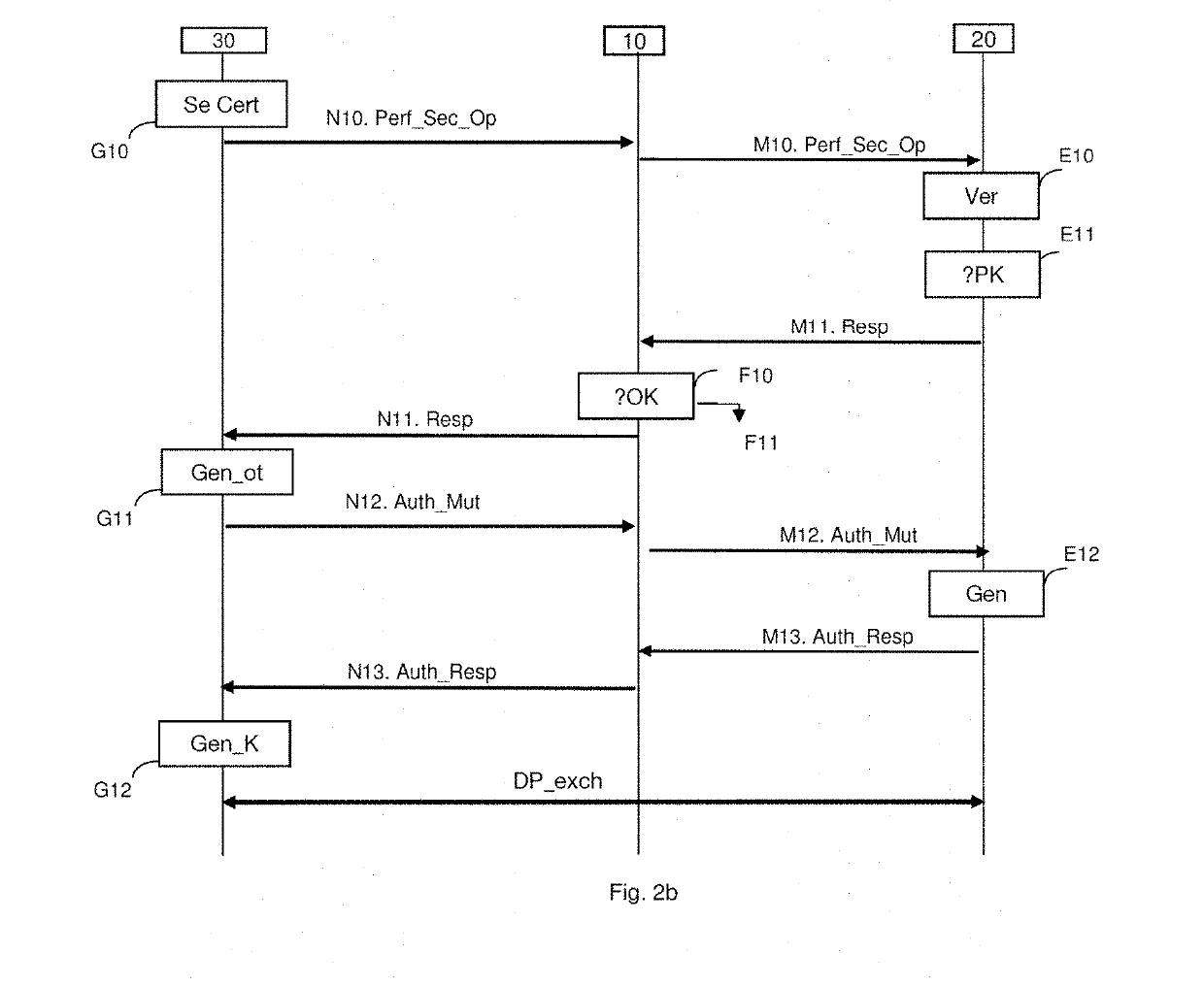
ActiveUS20190230087A1Service provisioningUser identity/authority verificationData validationNetwork Access Protection
A technique for downloading a profile for access to a communication network by a security module. This access profile has been prepared by a network operator and is available from a server configured to provide this access profile by downloading to the security module. The security module obtains a first verification datum prepared by the network operator. A secure downloading session is established thereafter. During establishment, session keys are jointly generated between the server and the security module and the server is authenticated by the security module using a public downloading key. The security module verifies authenticity of the public downloading key by using the first verification datum enabling verification that the server uses a secret downloading key corresponding to that provided by the network operator during preparation of the first verification datum. When the public downloading key is not authentic, the security module interrupts downloading of the access profile.
Owner:ORANGE SA (FR)
Online authentication system
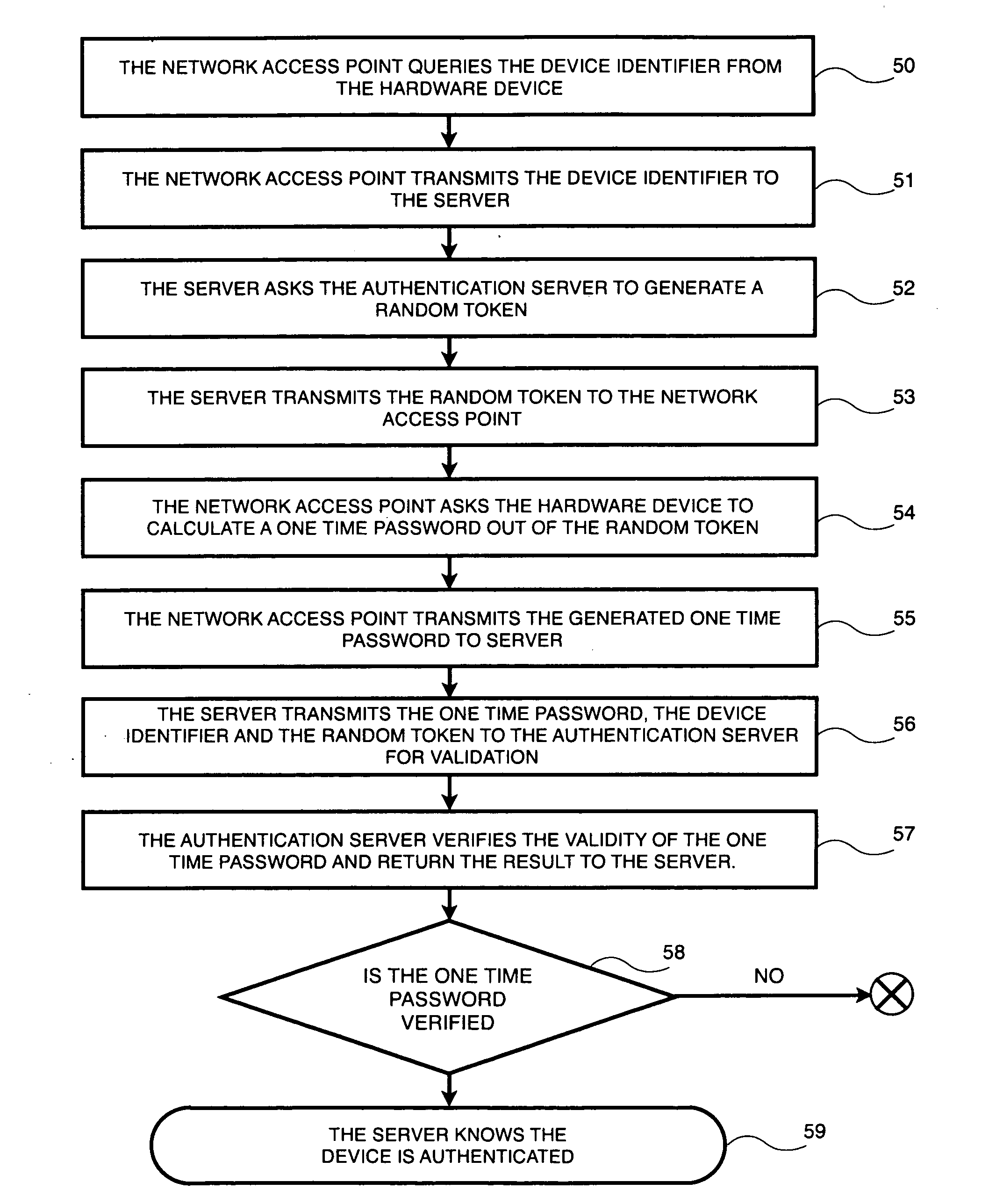
InactiveUS20100229227A1Digital data processing detailsMultiple digital computer combinationsNetwork Access ProtectionOne-time password
A hardware device connected to a network access point to authenticate itself to a server is disclosed. The device stores authentication software, and applicative data. The device is used to generate a one-time password to uniquely identify itself to a server.
Owner:ANDRE LUC +2
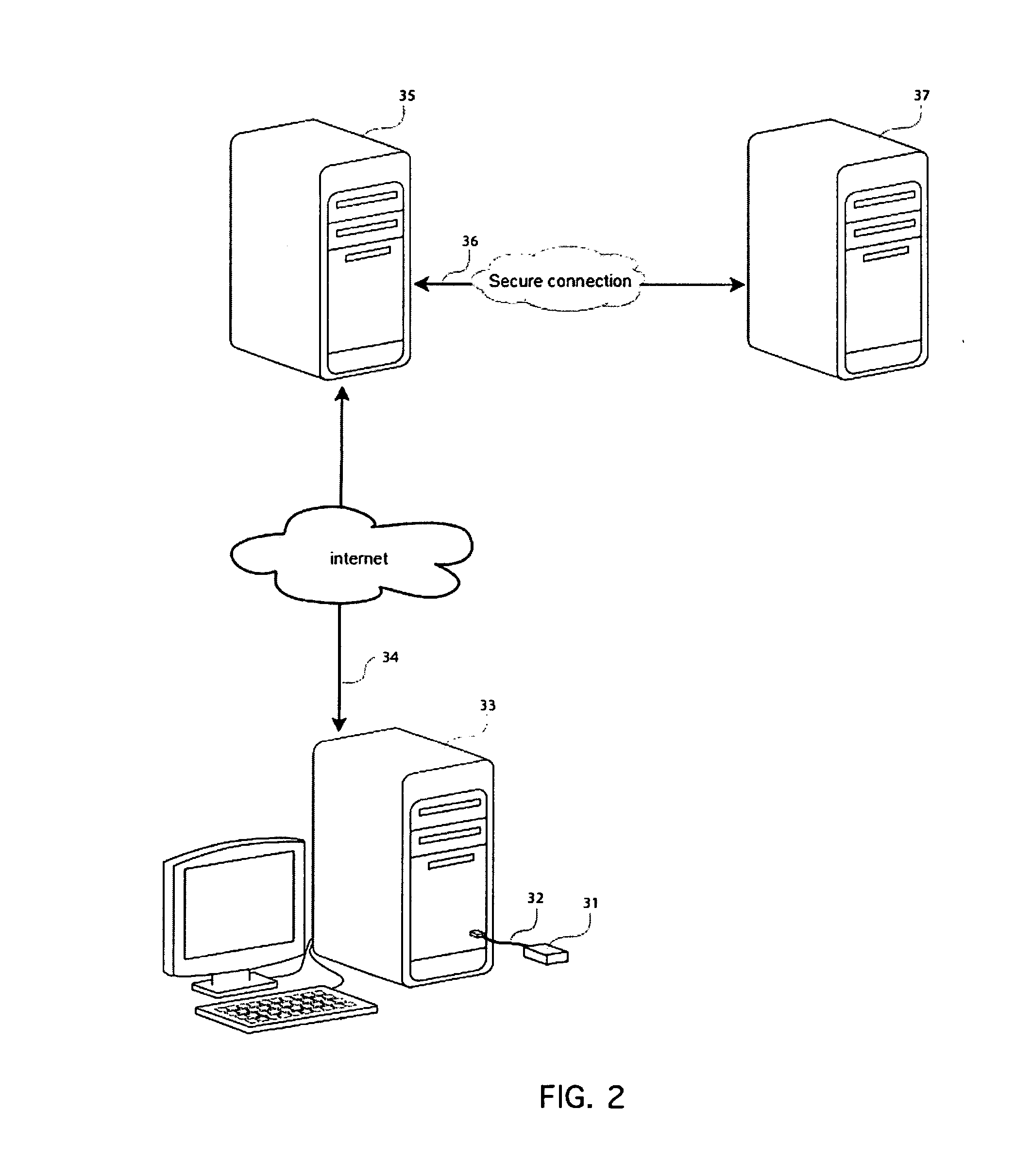
Network copy protection for database programs
ActiveUS6954860B1Digital data processing detailsUser identity/authority verificationNetwork Access ProtectionNetwork Communication Protocols
Owner:APPLE INC
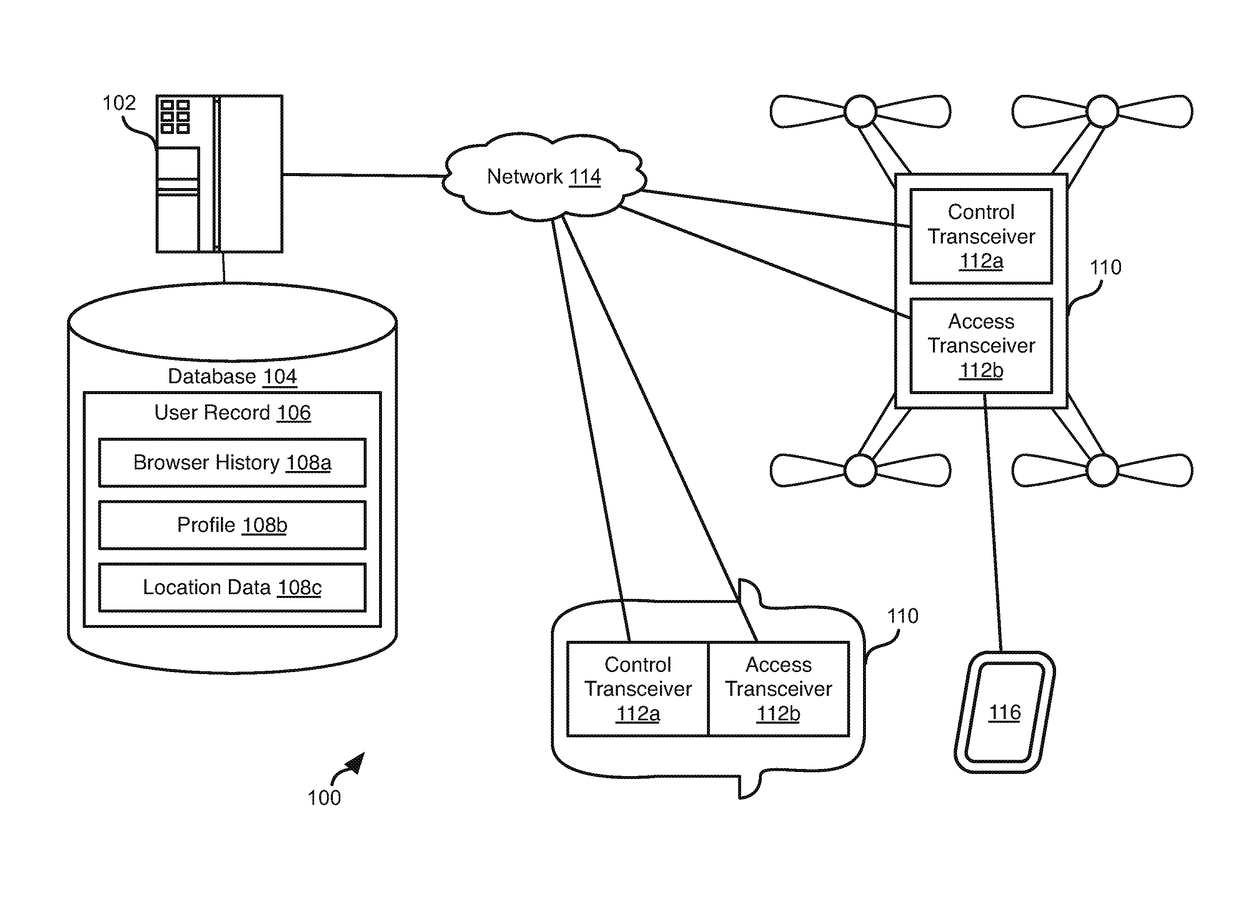
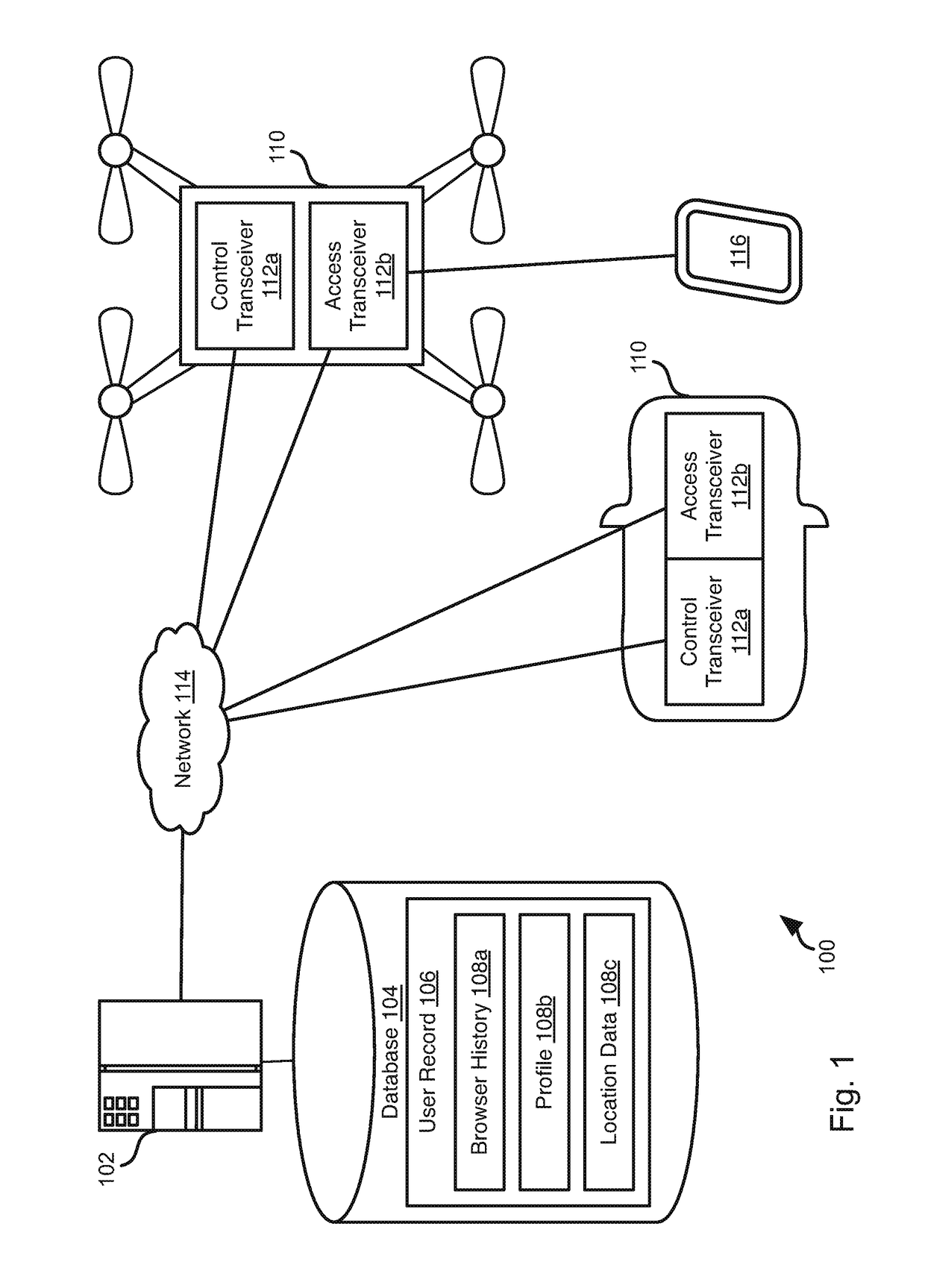
Providing wireless internet access using autonomous vehicles
ActiveUS20170302362A1Assess restrictionNetwork topologiesNetwork Access ProtectionCable Internet access
Autonomous vehicles such as UAVs or cars provide network access points. User devices connect to the network access points and network access is monitored. User location data is also monitored. A profile of the user is generated from the gathered data. Advertisements are selected based on a profile of the user and the current location of the user. The autonomous vehicles may be distributed geographically to provide a network access to a geographic area. In response to detecting that a user device is moving out of a coverage area of an autonomous vehicle, nearby autonomous vehicles are identified. If the user device is in the coverage area of a nearby autonomous vehicle, the network connection to the user device is transferred to that vehicle.
Owner:WALMART APOLLO LLC
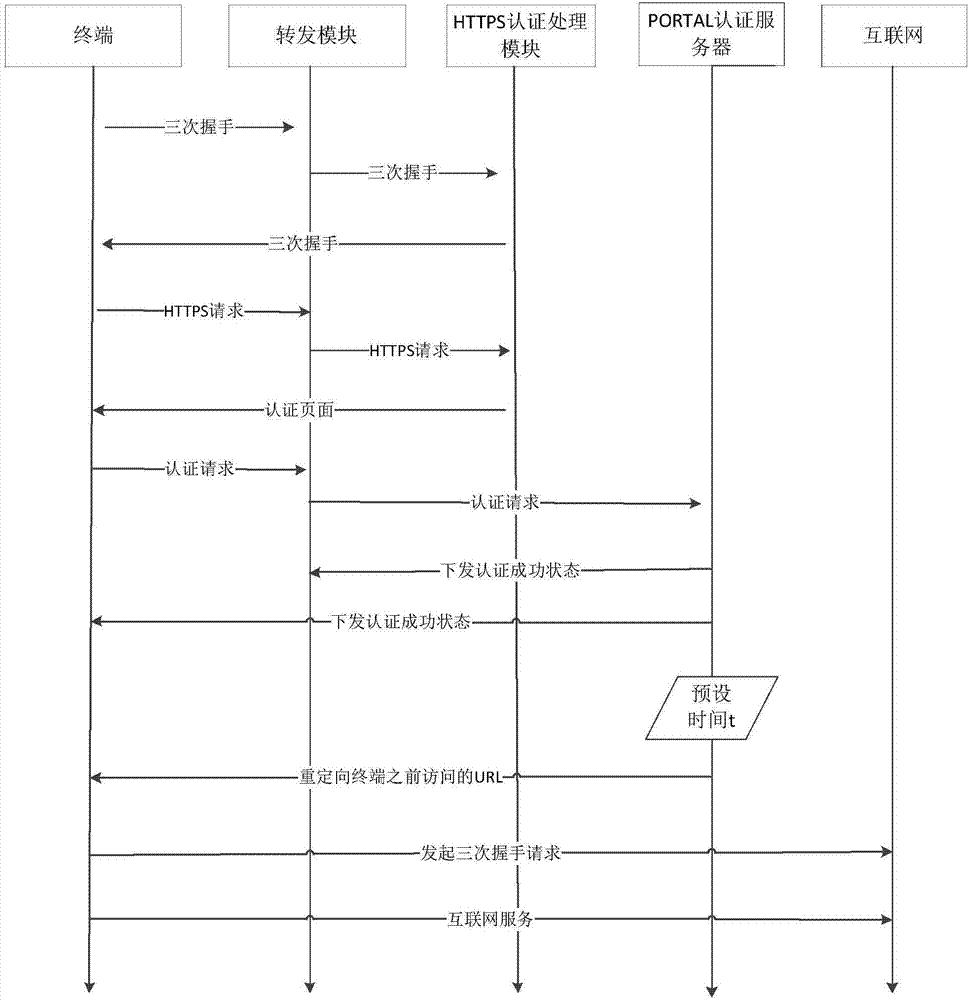
Network access method and system based on access authentication
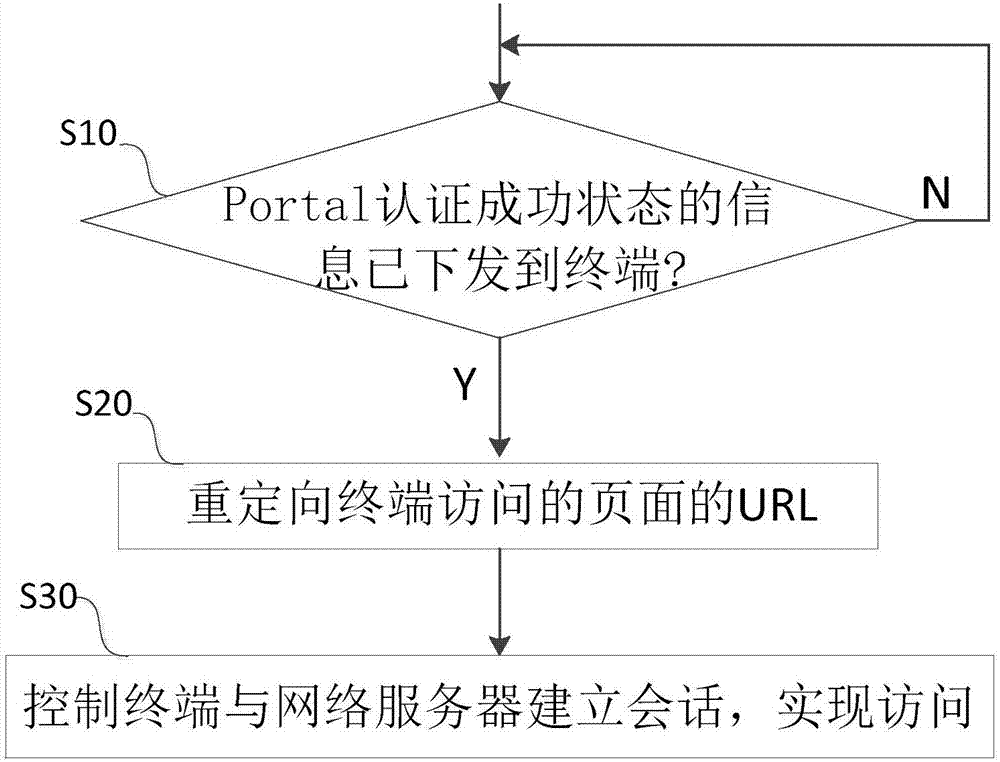
InactiveCN107070947ATime does not affectSolve the problem of not being able to access the networkTransmissionNetwork Access ProtectionAccess method
The invention discloses a network access method and system based on access authentication, wherein the method comprises the steps of: S10, judging whether information in an access authentication success state is sent to a terminal or not; S20, if the fact that the information in the access authentication success state is sent is determined, redirecting a page accessed by the terminal; and S30, according to the redirected page information, controlling the terminal and a network server to establish a session, so that access is realized. By means of the access method, the problem that a current wireless product cannot access a network for a short time in a network access process after access authentication based on a hypertext transfer protocol over a secure socket layer is successful can be solved; access is relatively efficient and intelligent; and thus, the user experience is relatively smooth.
Owner:PHICOMM (SHANGHAI) CO LTD
Network audit subsystem applied to cloud audit system
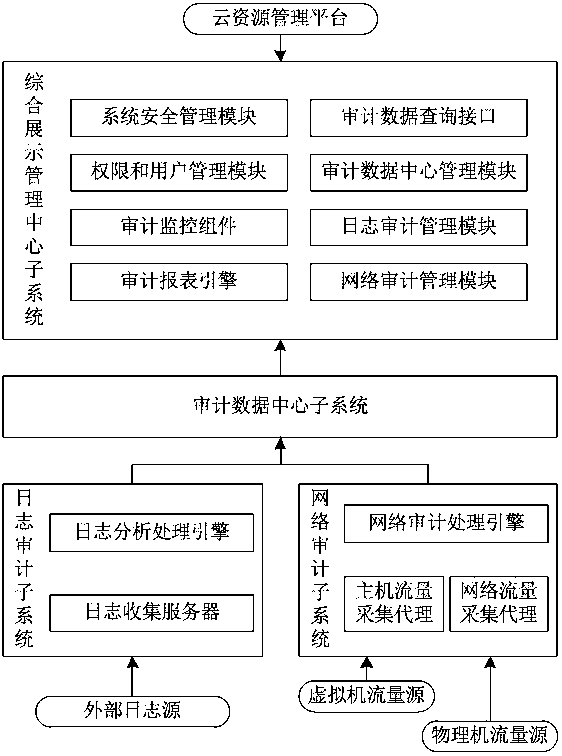
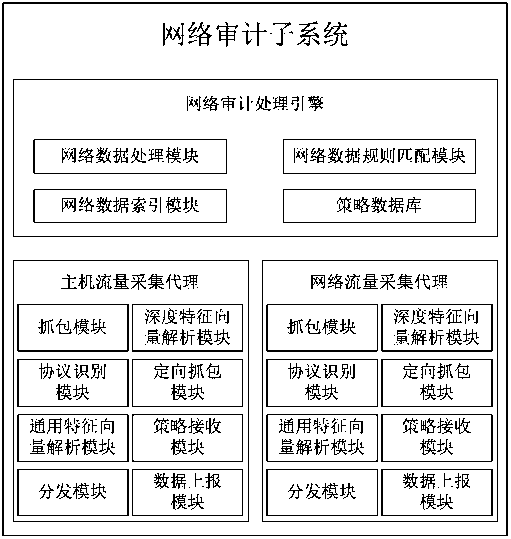
The invention discloses a network audit subsystem applied to a cloud audit system. The network audit subsystem comprises a network audit processing engine, a host traffic acquisition proxy and a network traffic acquisition proxy, wherein the network audit processing engine is used for auditing virtual machine traffic and physical machine traffic in a network acquired from cloud data; the host traffic acquisition proxy is used for acquiring the virtual machine traffic and distributing the virtual machine traffic to the network audit processing engine; and the network traffic acquisition proxy is used for acquiring the physical machine traffic and distributing the physical machine traffic to the network audit processing engine. The invention generally aims to acquire network data packets from network equipment, hosts and the like for analyzing and recording according to a certain rule and strategy setting. All acquired network access records are written into a database; the system can perform work such as network security vulnerability analysis and intrusion detection; data can be supplied to an audit data center for analysis, presentation and the like; and the data are to be storedin the database for later checking.
Owner:CHINA SOUTHERN POWER GRID COMPANY
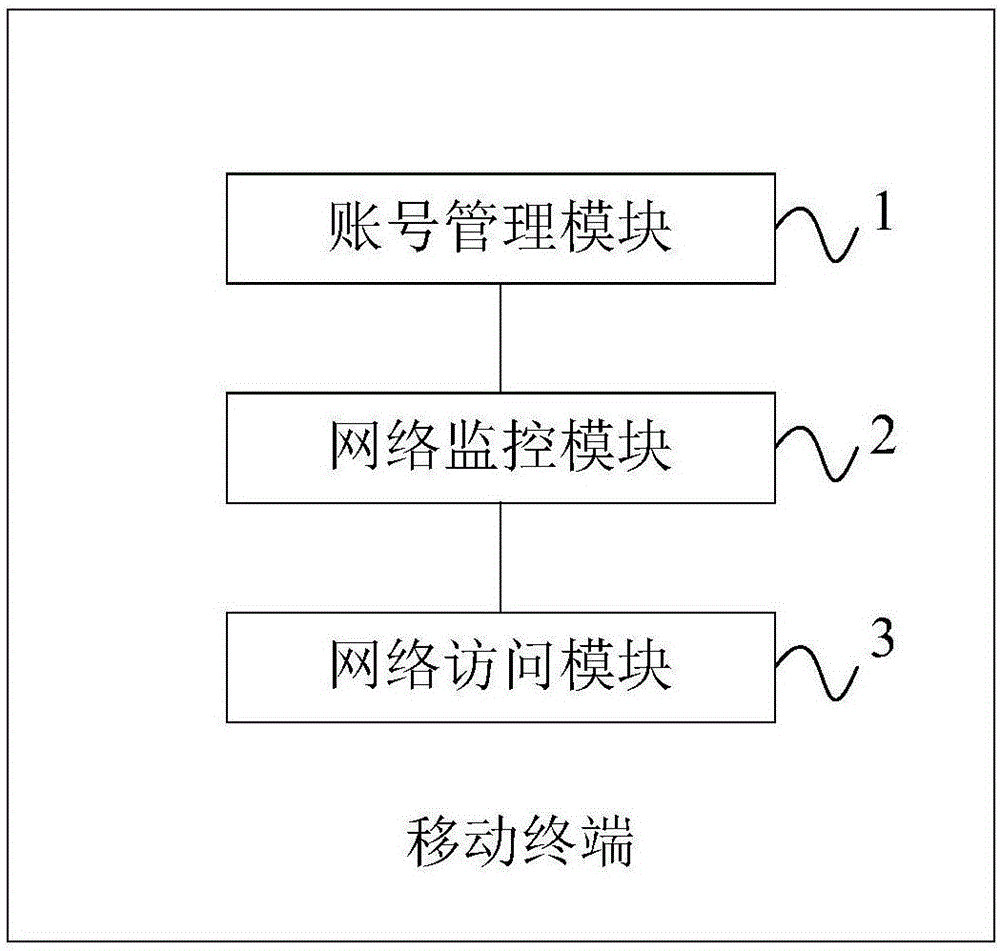
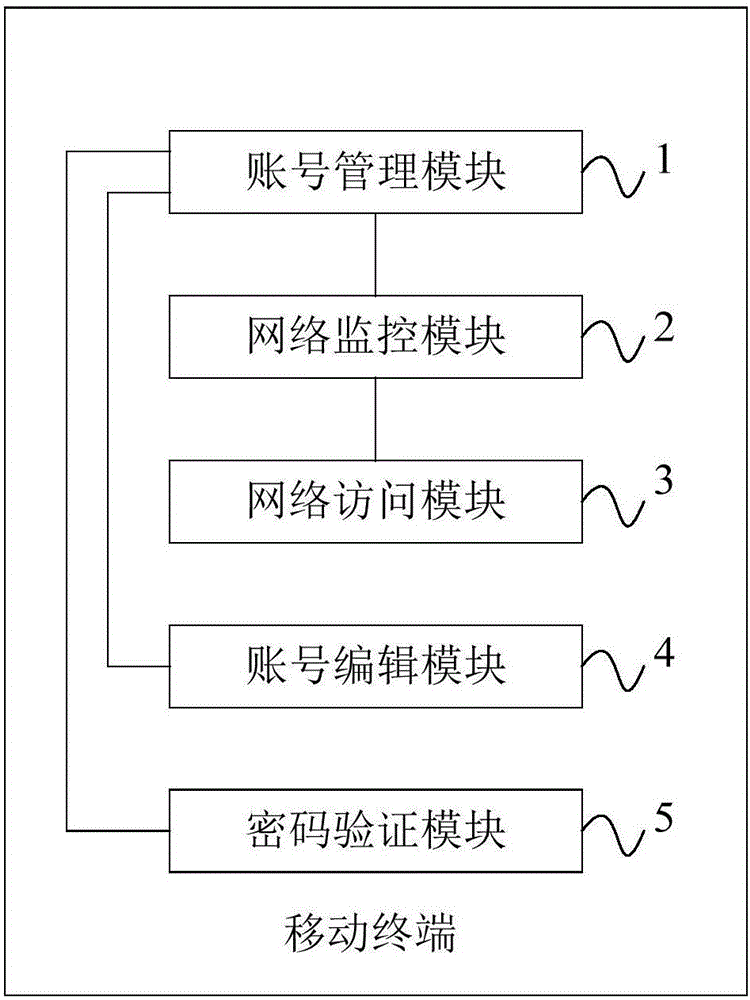
Account number information protection method and mobile terminal
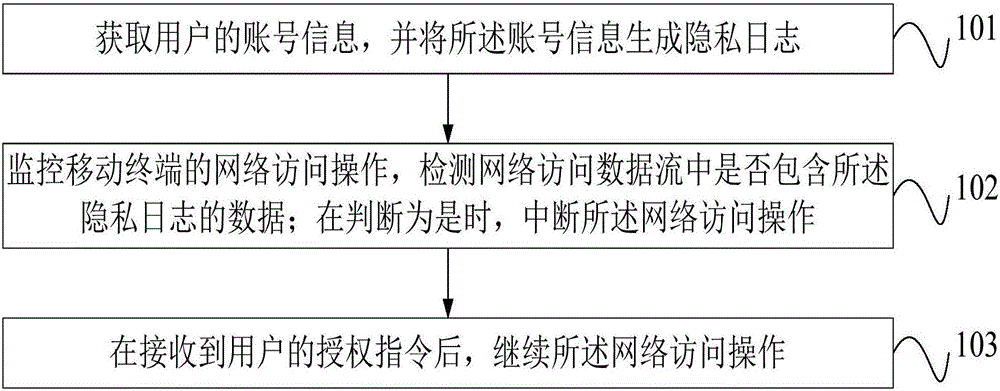
InactiveCN106778334AAvoid lostPrevent theftDigital data protectionDigital data authenticationNetwork Access ProtectionData stream
The invention discloses an account number information protection method and a mobile terminal. The account number information protection method is implemented in the mobile terminal and comprises the following steps of obtaining account number information of a user, and generating a privacy log through the account number information; monitoring a network access operation of the mobile terminal, and detecting whether network access dataflow includes data of the privacy log or not; if yes, interrupting the network access operation; after an authorization instruction of the user is received, continuing to perform the network access operation. The privacy log is generated through the account number information, and the network access operation of the mobile terminal is monitored in real time, so that it is ensured that the privacy log data is accessed only under the user authorization condition, the user privacy account number information security is effectively ensured, the phenomenon that information is stolen under the user unknowing condition is avoided, and user losses are avoided.
Owner:SHANGHAI CHUANGGONG COMM TECH
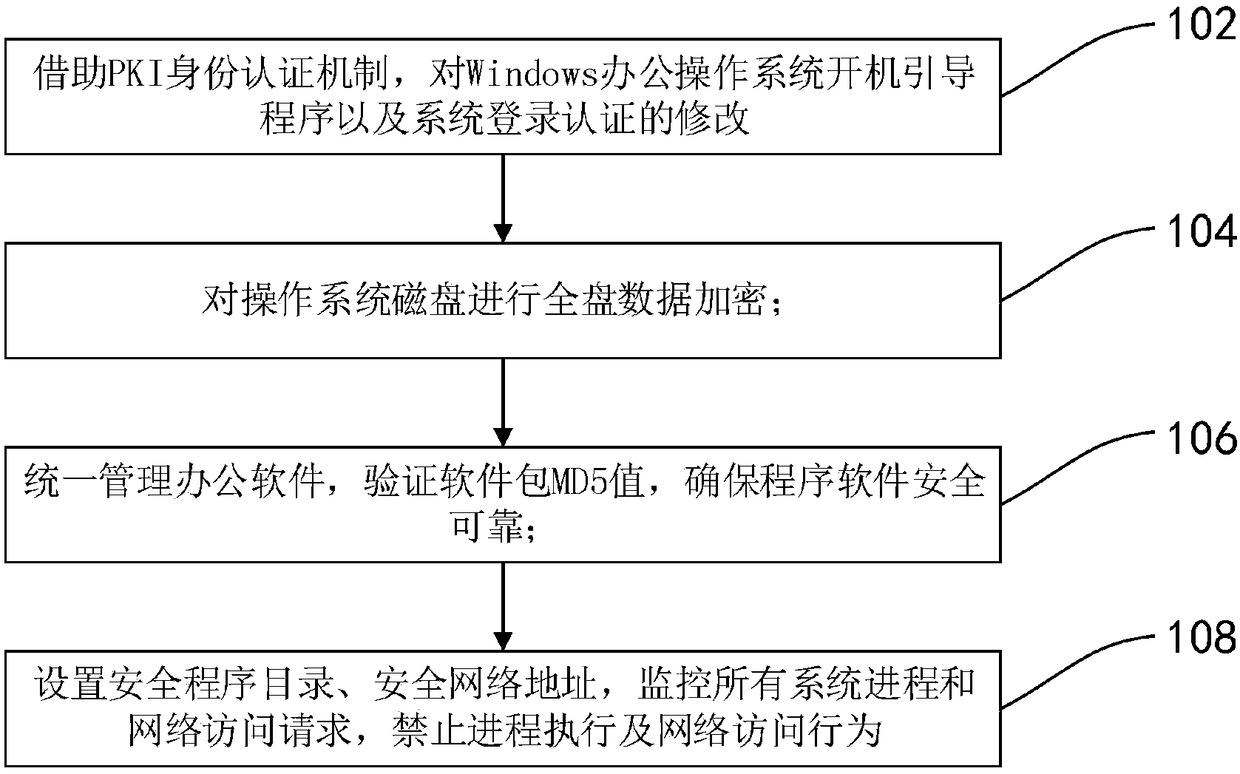
Office operation system reinforcing method and system
InactiveCN108388792ATo achieve reinforcementAchieve data protectionDigital data protectionInternal/peripheral component protectionOperational systemNetwork Access Protection
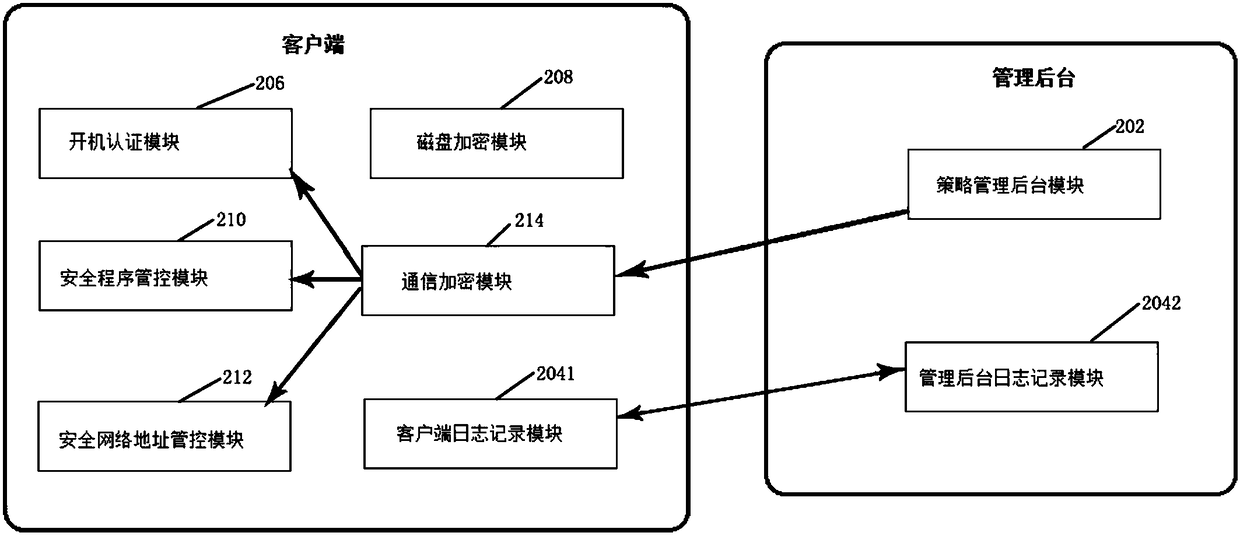
The invention discloses an office operation system reinforcing method and system. The office operation system reinforcing method comprises the following steps: modifying a boot program and system login authentication of a Windows office operation system by means of a PKI identity authentication mechanism; performing full-disk data encryption on an operation system disk; uniformly managing office software, verifying MD5 value of a software package and ensuring security and reliability of program software; and setting a secure program directory and a secure network address, monitoring all systemprocesses and network access requests, and prohibiting process execution and network access behaviors. The office operation system reinforcing method and system provided by the invention realizes data protection, process protection and network access protection for the Windows office operation system, improves the security of the system, and protects the rights of users of the office operation system.
Owner:北京力鼎创软科技有限公司
Intelligent network firewall equipment and network attack protection method
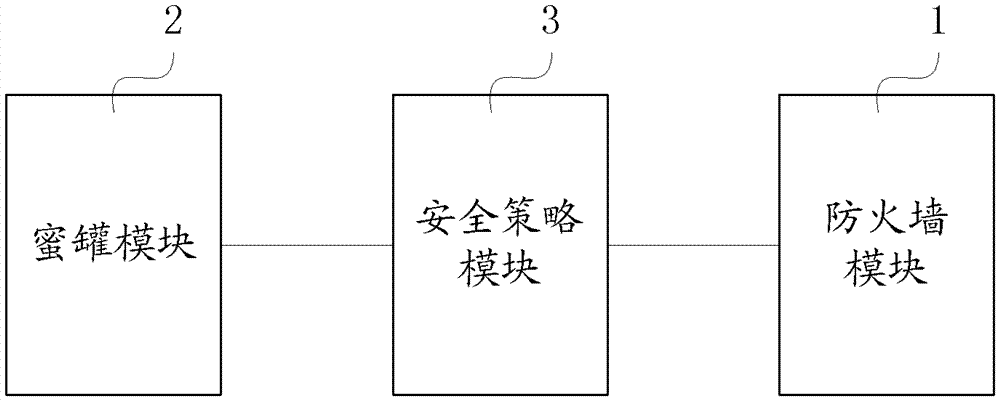
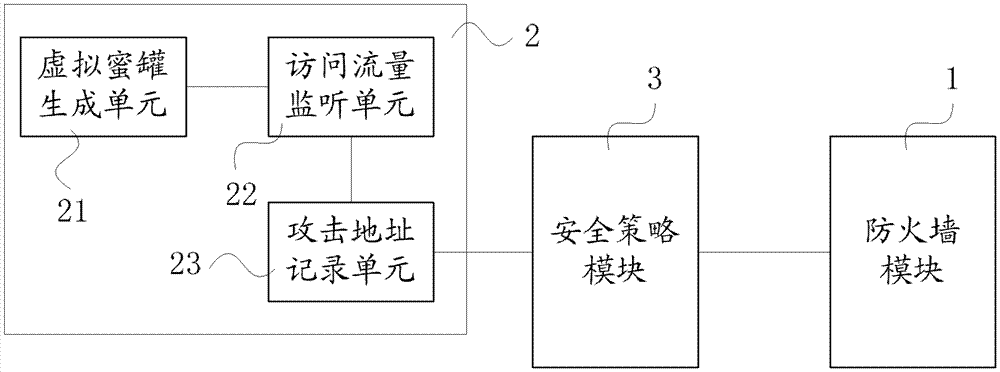
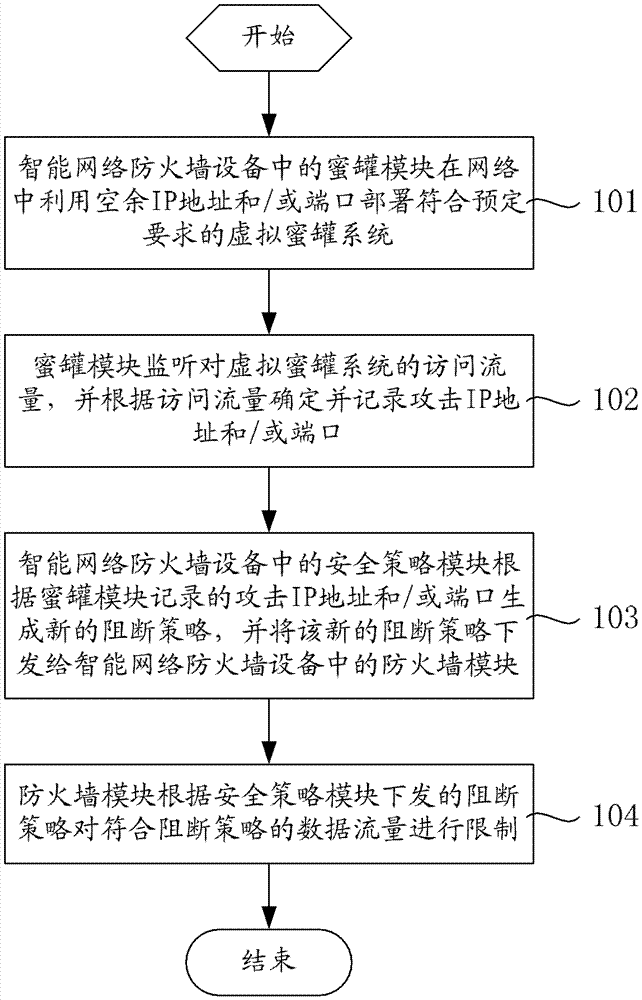
The invention relates to an intelligent network firewall device which comprises a firewall module used for limiting data traffic in accordance with a blocking strategy according to the issued blocking strategy, a honey pot module used for arranging a virtual honey pot system in accordance with preset requirements using unoccupied Internet protocol (IP) addresses and / or ports in a network, monitoring access traffic to the virtual honey pot system, and then determining and recording attack IP addresses and / or ports according to the access traffic, and a safety strategy module used for generating a new blocking strategy according to the attack IP addresses and / or ports recorded by the honey pot module and issuing the net blocking strategy to the firewall module. The invention further relates to a network attack protection method. The virtual honey pot system in a firewall device is used for attracting illegal network attacks, and therefore network attack IP addresses and / or ports can be identified, the safety strategies of the firewall device are dynamically adjusted, the network attack situation which changes dynamically can be adapted to, and new network safety requirements can be adapted to.
Owner:CHINA TELECOM CORP LTD
Peer-enabled network access extension using yield management
ActiveCN107113704AAccounting/billing servicesAssess restrictionCommunication interfaceNetwork Access Protection
Aspects of the present disclosure provide for yield management models for dynamically pricing access to wireless communication services. In some examples, access to a network is intermediated by a surrogate access point, which may act as a proxy or relay, expanding communication services to client devices that otherwise may lack a subscription, or may lack a suitable communication interface, to communicate directly with the wireless network. Here, the surrogate access point may be a subscriber device or user equipment. By utilizing the yield management model, the surrogate access point may receive compensation for sharing its connection to the network with nearby client devices. Other aspects, embodiments, and features are also claimed and described.
Owner:QUALCOMM INC
A two-way network access authentication method based on digital certificate
ActiveCN103237038BUpdate admin keyReduce riskKey distribution for secure communicationUser identity/authority verificationDigest access authenticationNetwork Access Protection
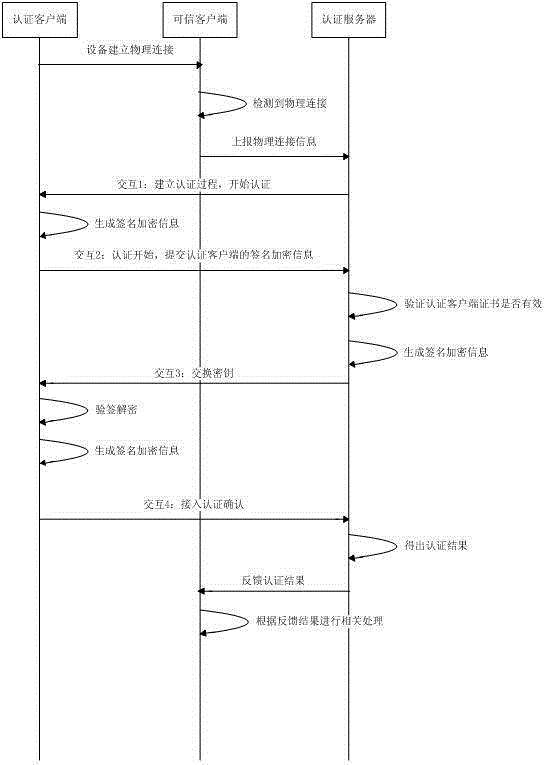
The invention relates to the technical field of network security. The invention discloses a two-way network access authentication method based on a digital certificate, which specifically includes the following steps: Step 1: Divide the network access authentication system into an access area and a trusted area, and classify the client to be authenticated. The terminal accesses the physical port of the trusted client; Step 2. After receiving the access information of the client to be authenticated, the authentication server actively initiates network access authentication to the client to be authenticated; Step 3. After the client to be authenticated receives the network access authentication, Submit the device authentication information to the authentication server, the authentication server starts authentication after receiving the authentication information, and feeds back the authentication result to the client to be authenticated. By physically connecting the client to be authenticated and the trusted client, the authentication server actively initiates network access authentication to the client to be authenticated after receiving the access information, so as to realize network access identity authentication of routing devices, switching devices, security protection devices, etc. , which improves the security and practicability of the network.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Cloud host-oriented full-flow network access protection method and device
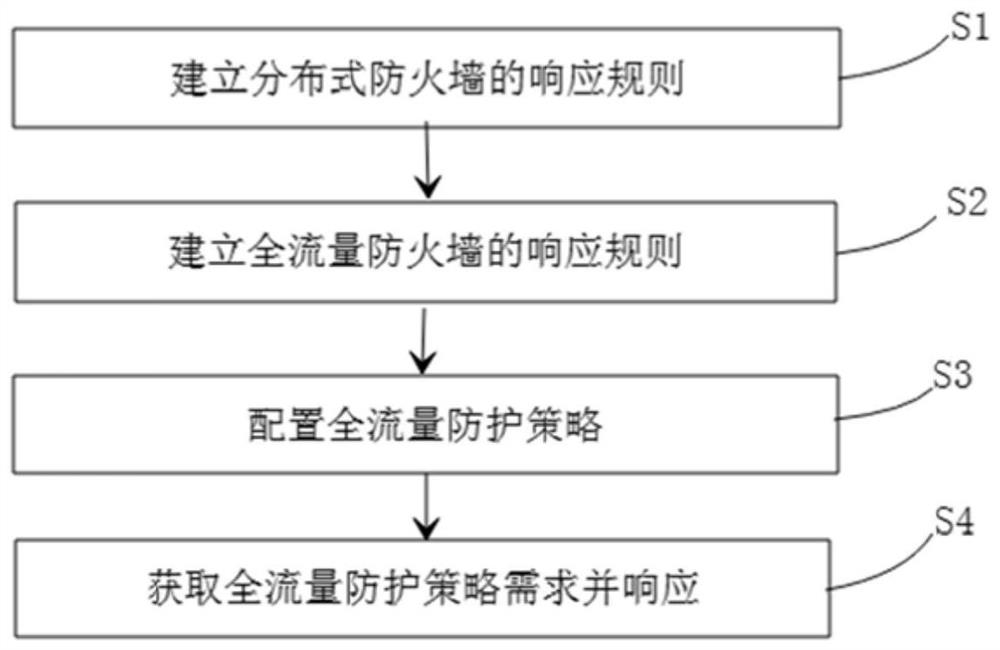
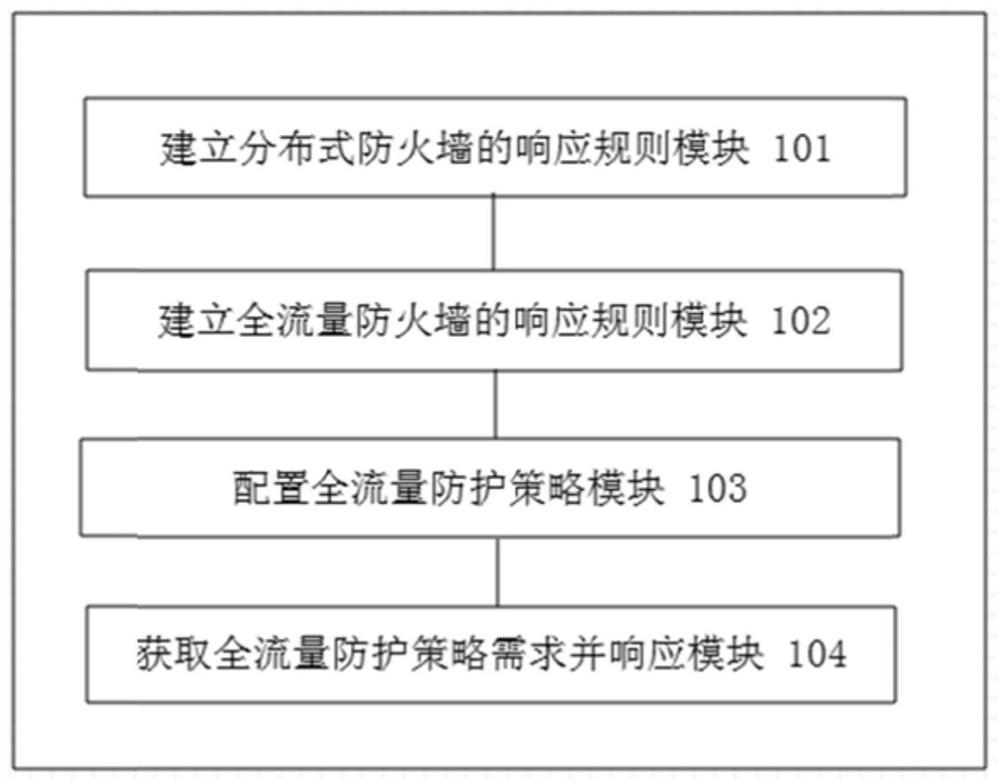
ActiveCN114374526APrecise north-south flow restrictionQuick configurationSecuring communicationHigh level techniquesNetwork Access ProtectionEngineering
The invention relates to the technical field of cloud computing and information security, in particular to a cloud host full-flow network access protection method and device. Under the traditional north-south flow protection, the protection capability of the east-west level of cloud resources is realized through the cloud computing service arrangement and automation technology, and the protection capability is complementary with the north-south flow protection to form full-flow network access protection. The method specifically comprises the following steps: establishing a response rule of a distributed firewall, establishing a response rule of a full-flow firewall, configuring a full-flow protection strategy, obtaining a full-flow protection strategy demand and responding, thereby automatically realizing protection of full-flow network access. The invention further provides a corresponding device, and the problems that the professional requirement of a traditional firewall technology is high, protection strategy configuration conflicts exist in a protection mode, protection strategy configuration among multiple cloud hosts lacks collaboration, operation steps are tedious and the like are solved.
Owner:COSCO SHIPPING TECH CO LTD
Peer-enabled network access extension using yield management
ActiveUS9735972B2Metering/charging/biilling arrangementsAccounting/billing servicesCommunication interfaceTelecommunications
Aspects of the present disclosure provide for yield management models for dynamically pricing access to wireless communication services. In some examples, access to a network is intermediated by a surrogate access point, which may act as a proxy or relay, expanding communication services to client devices that otherwise may lack a subscription, or may lack a suitable communication interface, to communicate directly with the wireless network. Here, the surrogate access point may be a subscriber device or user equipment. By utilizing the yield management model, the surrogate access point may receive compensation for sharing its connection to the network with nearby client devices. Other aspects, embodiments, and features are also claimed and described.
Owner:QUALCOMM INC
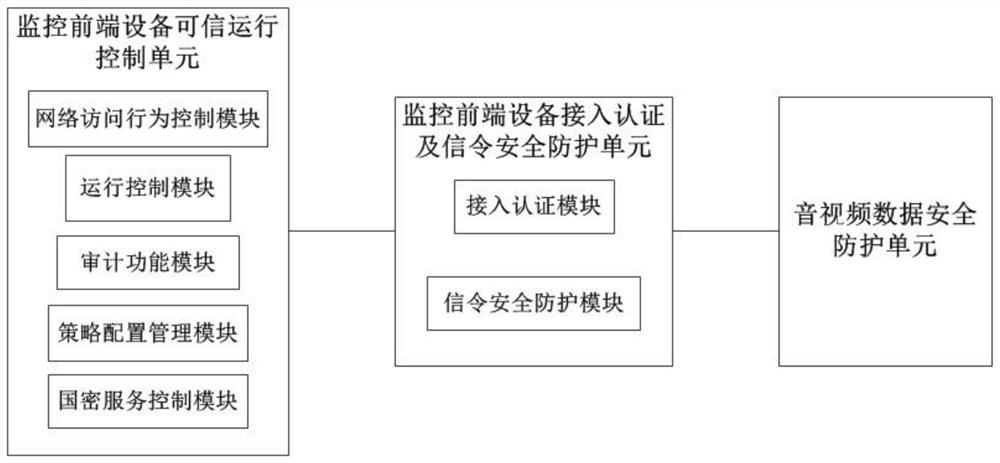
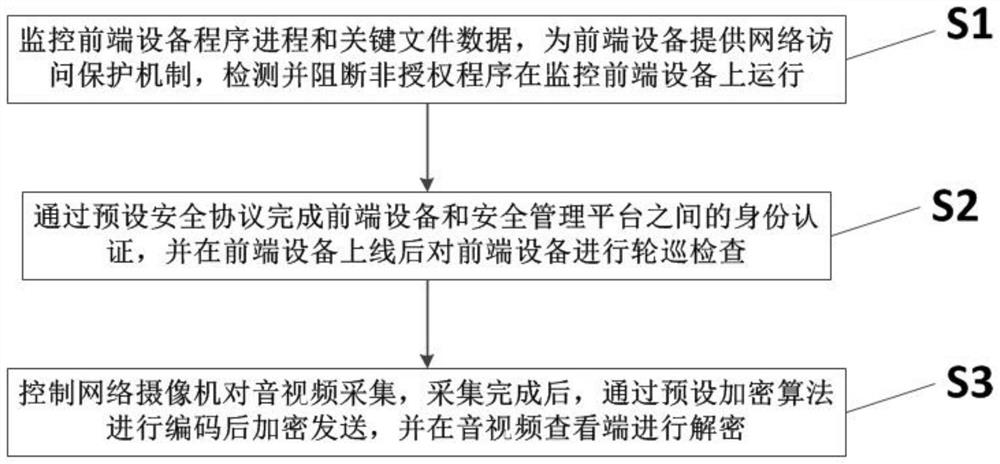
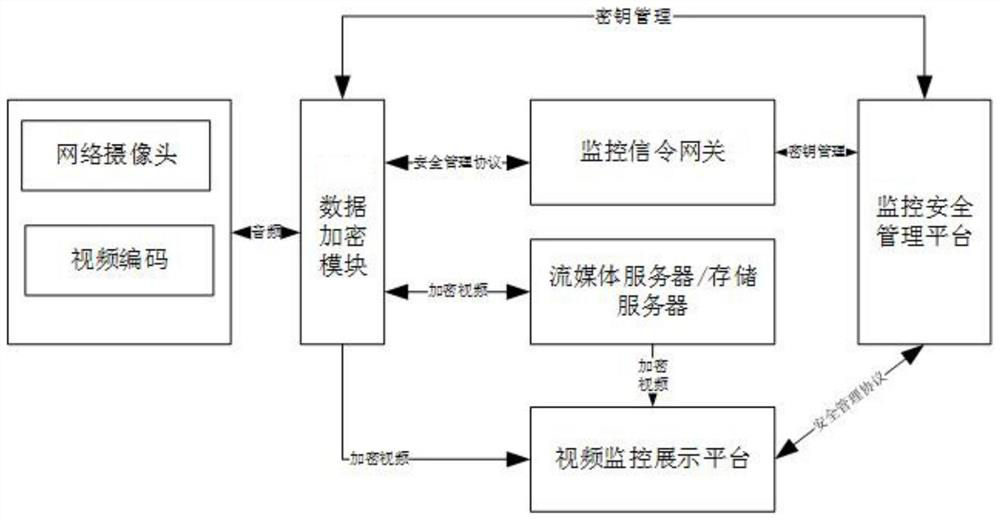
Video acquisition security processing system and method based on zero trust mechanism
InactiveCN112804215AEffective reinforcement methodEnhance the ability to resist Trojan virus invasionClosed circuit television systemsTransmissionNetwork Access ProtectionEmbedded system
The invention provides a video acquisition security processing system and method based on a zero-trust mechanism, and the system comprises a monitoring front-end equipment trusted operation control unit which is disposed in a network camera operation system, and is used for monitoring the program process and key file data of front-end equipment, providing a network access protection mechanism, detecting and blocking the operation of the unauthorized program on the monitoring front-end equipment; the monitoring front-end equipment access authentication and signaling security protection unit is used for completing identity authentication between the front-end equipment and the security management platform through a preset security protocol and carrying out polling inspection on the front-end equipment; and the audio and video data security protection unit is used for controlling the network camera to collect the audio and the video, encoding the audio and the video through a preset encryption algorithm, encrypting and sending the audio and the video, and decrypting the audio and the video at the audio and video viewing end. According to the invention, the control security, the service signaling security and the audio and video data security of the front-end camera are effectively improved, so that the data security of each link of video acquisition is ensured.
Owner:SHANDONG ZHONGFU INFORMATION IND +3
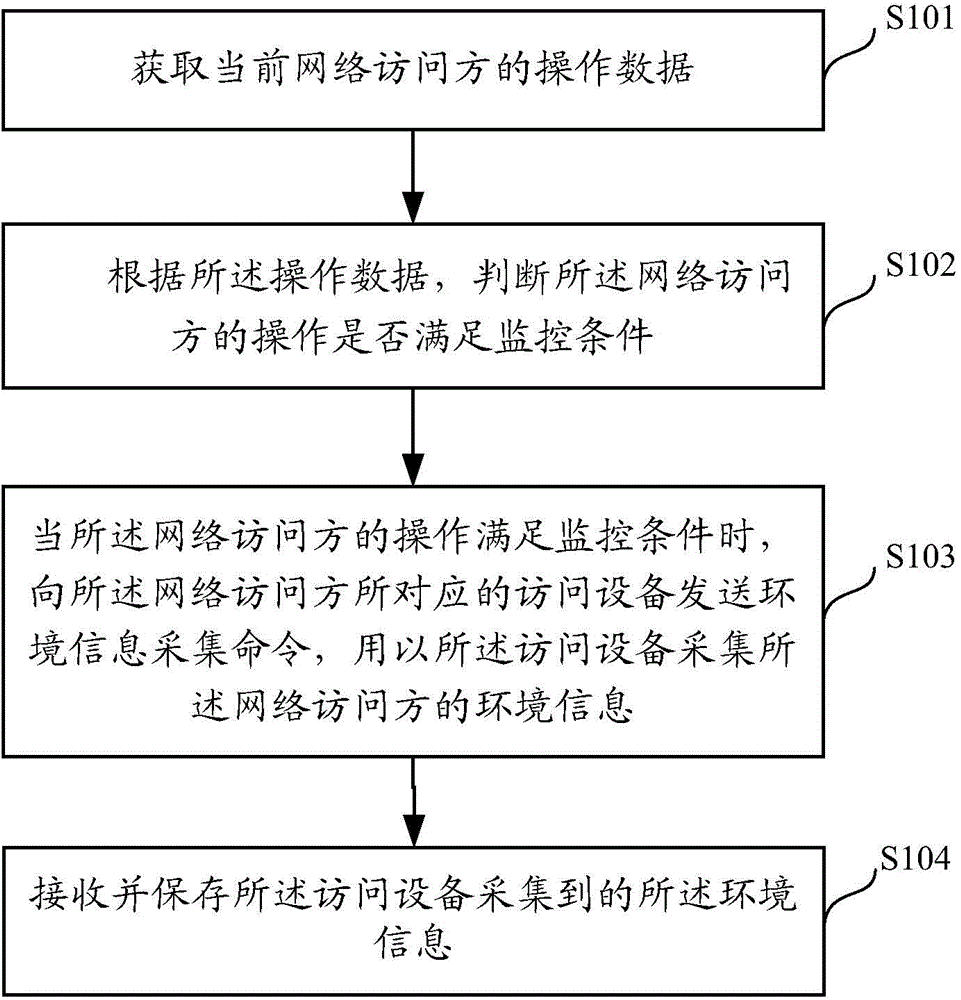
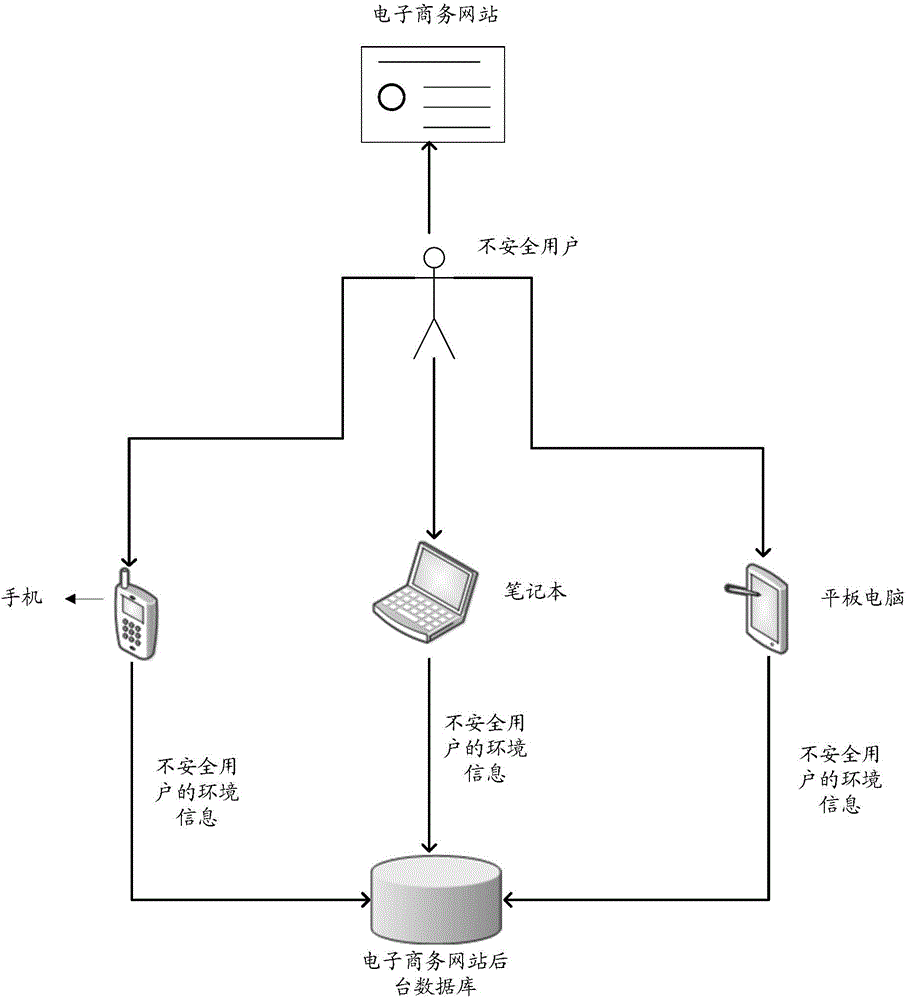
Environment information collection method and device for network access party
ActiveCN105471668AAvoid safety hazardsData switching networksNetwork Access ProtectionCollection methods
Owner:ADVANCED NEW TECH CO LTD
Method for accessing network, proxy server and network access system
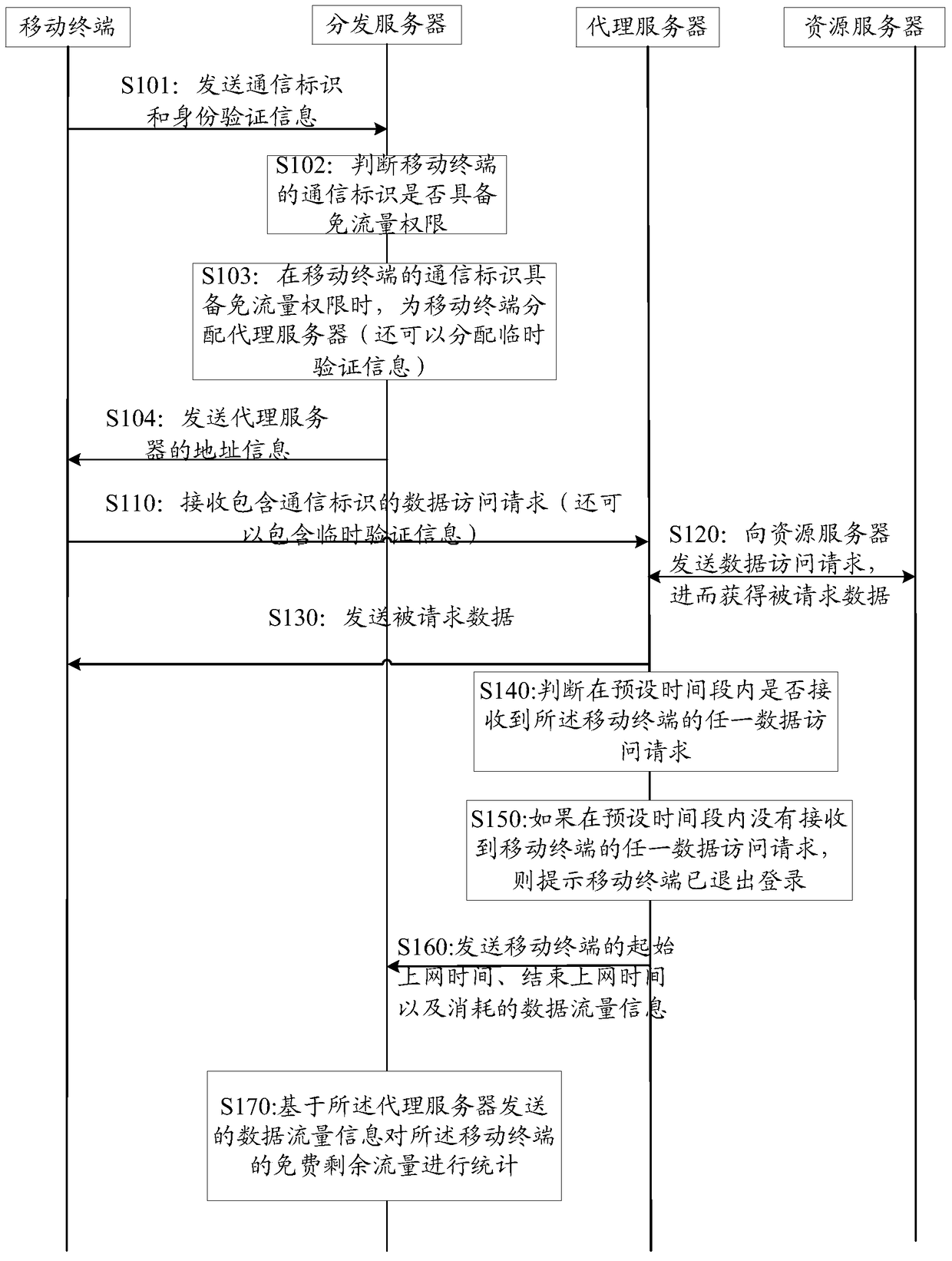
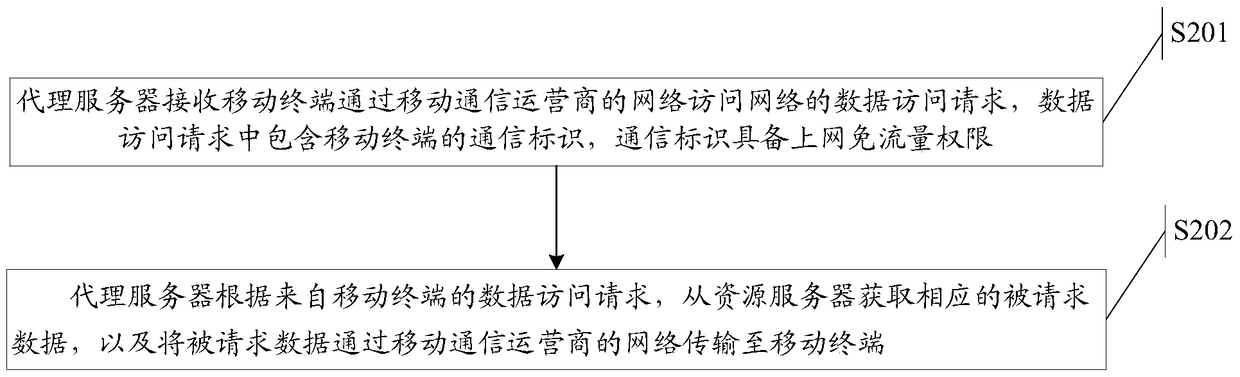
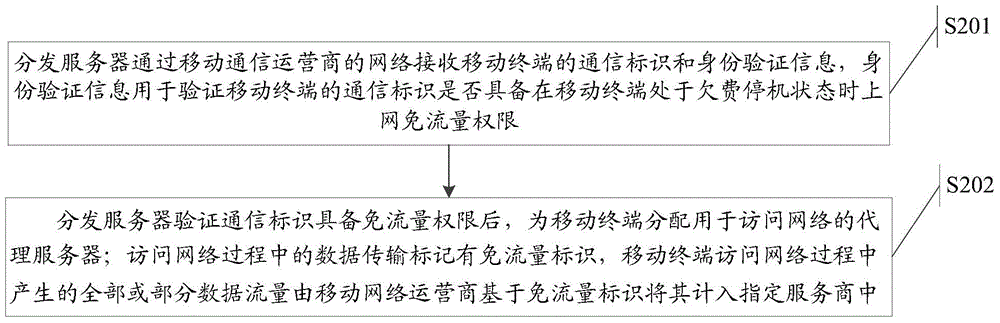
ActiveCN104954489BIncrease motivationConducive to wide disseminationData switching networksNetwork Access ProtectionData access
The invention relates to the field of communications, and discloses a method for accessing a network, a proxy server and a network access system, so as to solve the technical problem that a large amount of data traffic of the mobile terminal needs to be consumed when the mobile terminal accesses the network in the prior art. The method includes: a proxy server receives a data access request from a mobile terminal to access a network through a network of a mobile communication operator; the proxy server obtains corresponding requested data from a resource server according to the data access request from the mobile terminal, and passes the requested data through The network of the mobile communication operator is transmitted to the mobile terminal; the data transmission in the process of accessing the network by the mobile terminal is marked with a traffic-free identifier, and all or part of the data traffic generated in the process of accessing the network by the mobile terminal through the proxy server is determined by the mobile network operator based on the free-flow identification. Traffic ID counts it against the designated service provider. The technical effect of reducing the data flow of the mobile terminal when the mobile terminal accesses the network is achieved.
Owner:北京鸿享技术服务有限公司
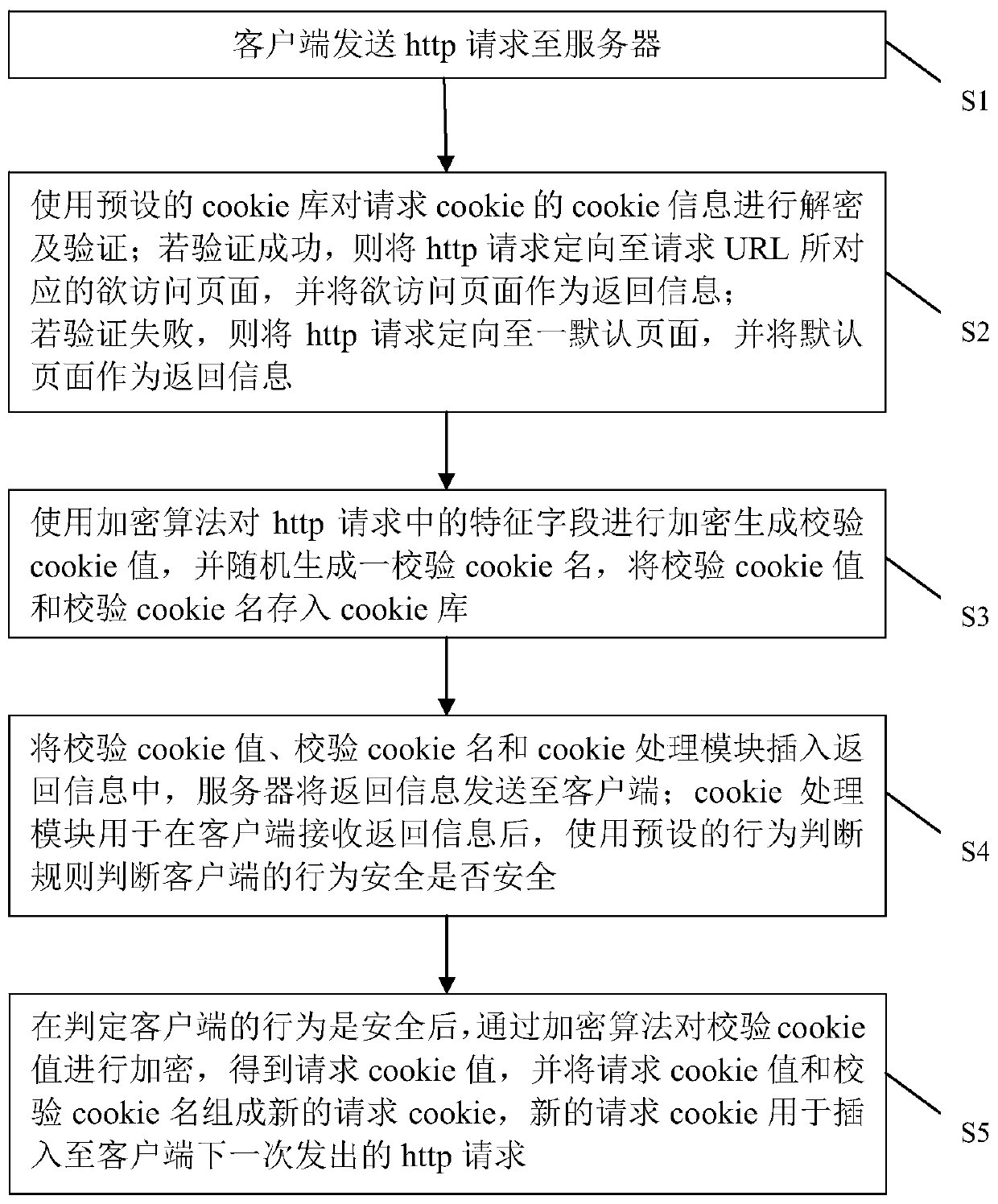
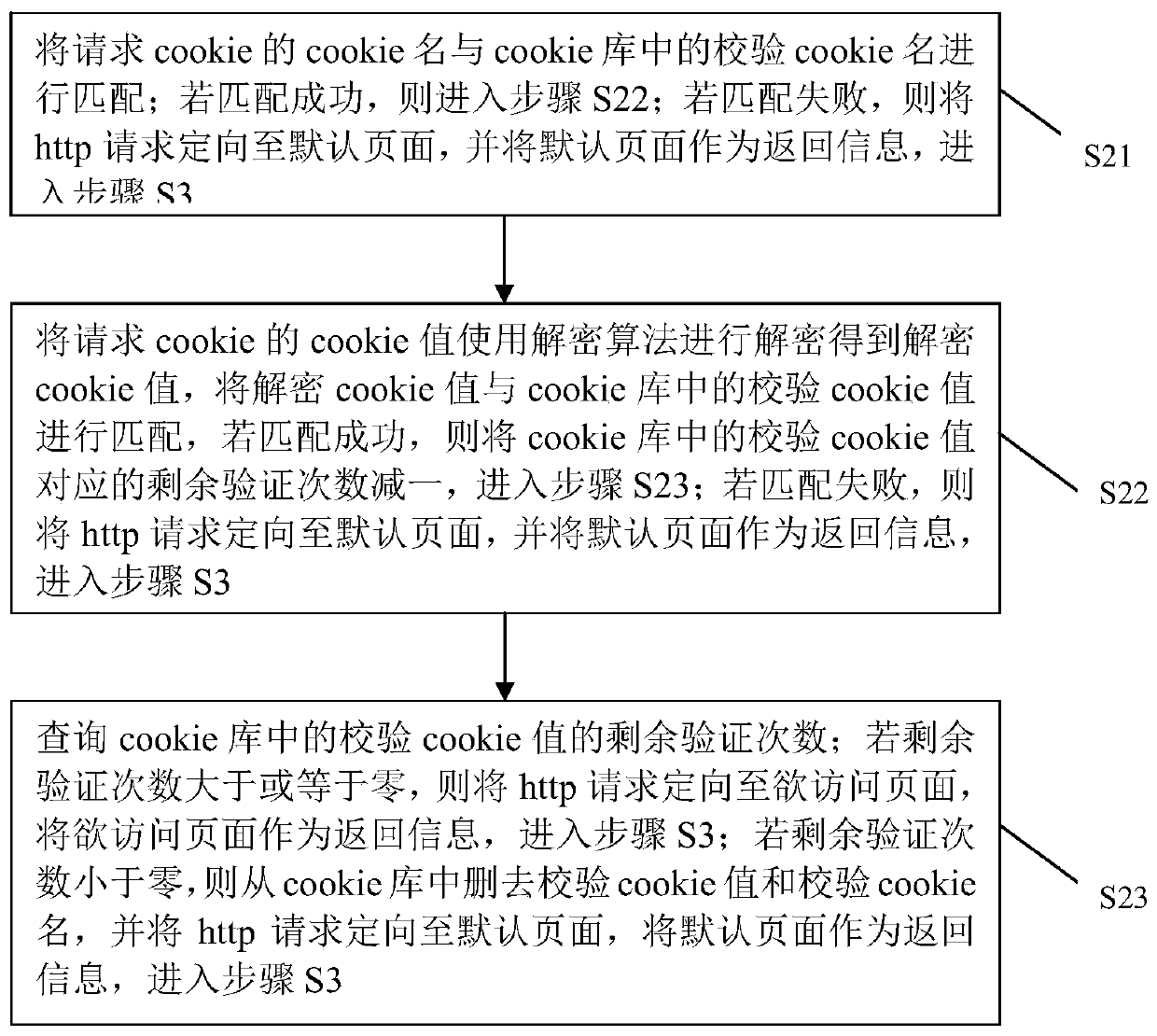
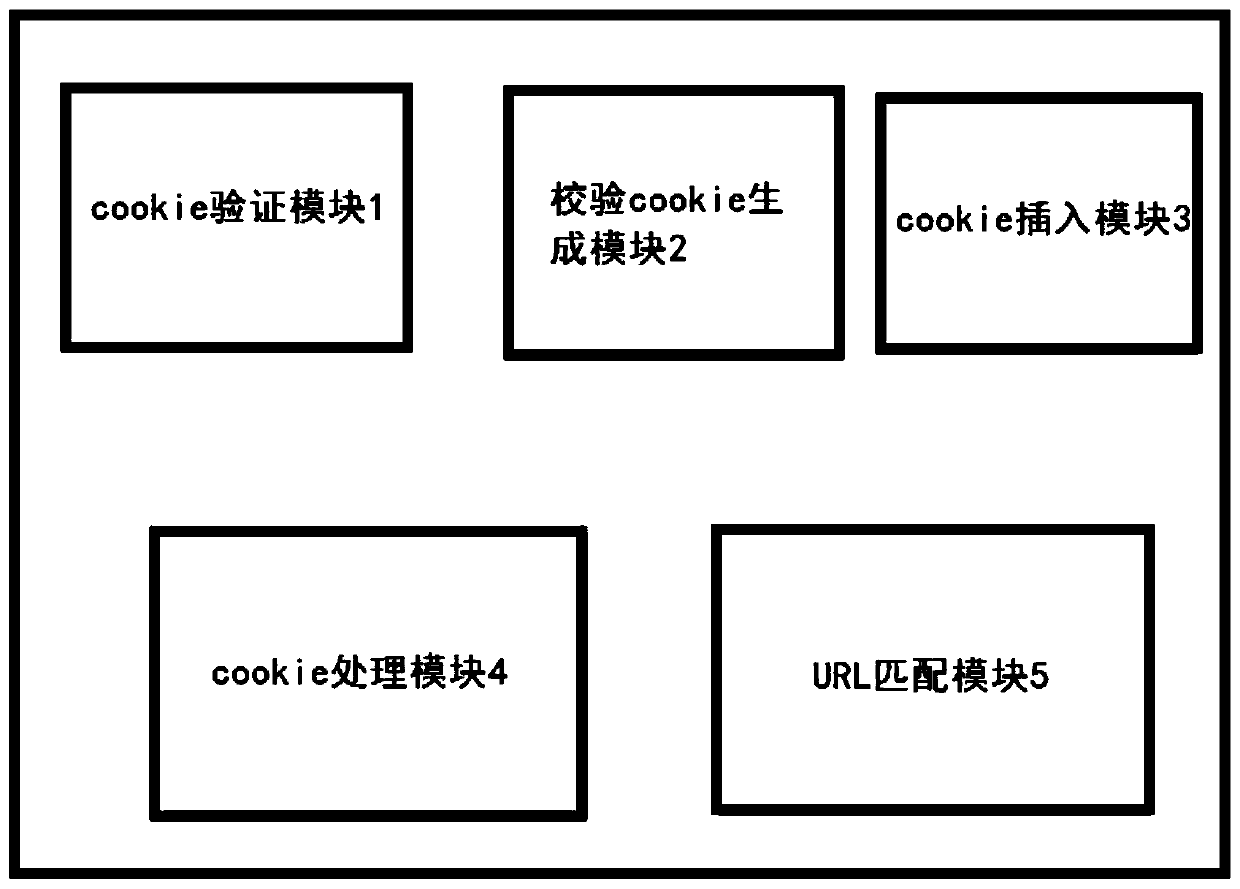
Dynamic cookie verification method and device for network protection
ActiveCN110046500APrevent repeated access attacksPrevent access attacksDigital data protectionPlatform integrity maintainanceNetwork Access ProtectionClient-side
The invention discloses a dynamic cookie verification method and device for network protection, the cookie in the http request transmitted by the client can be verified; after verification, the http request is sent to the server for processing; a network attacker is prevented from using a large number of unverified requests to carry out DDOS attack on the server and comsuming processing resourcesof servers, and the network infrastructure will not be paralyzed and even damaged; meanwhile, for the http request which does not pass the verification, the behavior of the client side is judged through the inserted cookie processing module, and after it is judged that the behavior of the client side is a safe and normal machine rather than an automatic malicious program, the client side can be screened to prevent malicious attacks.
Owner:广州安锐信息技术有限公司
A trusted network access and access control method
ActiveCN104618396BAvoid identity forgeryAchieve adaptiveUser identity/authority verificationNetwork access serverNetwork Access Protection
The invention discloses a trusted network access and access control system. The control system comprises a network access requester, a network access decision-maker and a network access controller. When the network access requester accesses to the network, platform identity authentication is carried out, and secure and trusted states of the requester are detected; the secure and trusted states are sent to the network access decision-maker, and the decision-maker judges the secure and trust level of the requester and gives a network access decision; the network access decision is sent to the network access controller, and the controller limits the requested network access. The invention further discloses a trusted network access and access control method. The control system carries out the platform identity authentication on the basis of TCM and ensures the network access control while avoids identity forging. Network areas are divided on the basis of a digital label technology and dynamically updated, network self-adaption is realized, and the access security of different logical areas is ensured. Secure and trusted strategies are configured, and combined with the TCM cryptographic algorithm, so that the security and credibility of the platform state of the requester are ensured.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Download method and system based on home gateway, and home gateway
ActiveCN102916907BAffect normal network access businessAffect network access businessNetwork connectionsNetwork Access ProtectionComputer terminal
The invention provides a download method and a download system based on a home gateway, and the home gateway, and the home gateway, wherein the method comprises the following steps: a download request message, including the document address and the document name of at least one document to be downloaded, sent by a user terminal is received by the home gateway; if the downlink data in the network access process does not appear within the preset time of a first downlink channel used for performing the network access, the document corresponding to the document address and the document name is downloaded through the first downlink channel, and the downloading of the document is stopped until the downlink data occur on the first downlink channel. Through the download method and the download system based on the home gateway, and the home gateway provided by the invention, the document can be downloaded through the home gateway when the user terminal does not perform the network access, thereby the network bandwidth is more fully and reasonably utilized, the download in the prior art when the user terminal performs the network access is avoided; and the occupation of a large quantity of bandwidths can influence the normal network access business of a user.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
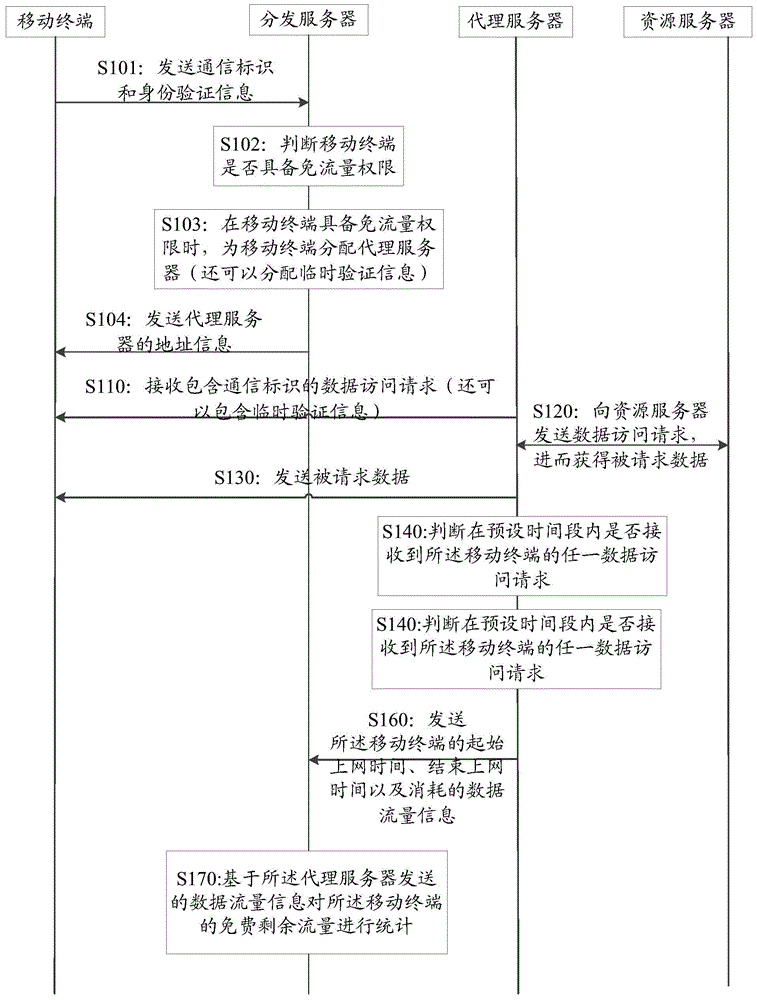
Network access method in charge overdue and out-of-service state, distribution server as well as system
The invention discloses a network access method in a charge overdue and out-of-service state, a distribution server as well as a system. The method comprises the following steps: whether a mobile terminal is in the charge overdue and out-of-service state is judged, a traffic-free mode is started, a data access request for network access is sent to a proxy server in the mode when the mobile terminal is in the charge overdue and out-of-service state, wherein the data access request contains the communication identification of the mobile phone, and the communication identification has traffic-free internet surfing permission when the mobile terminal is in the charge overdue and out-of-service state; the mobile terminal receives requested data acquired by the proxy server from a resource server on the basis of the data access request, data transmission during network access is marked with traffic-free identification, and all or part of data traffic produced in the network access process of the mobile terminal is calculated into an assigned service provider by a mobile network operator on the basis of the traffic-free identification, so that the technical problem that network access cannot be performed through the network of the mobile network operator when the mobile terminal is in the charge overdue and out-of-service state in the prior art is solved.
Owner:北京鸿享技术服务有限公司
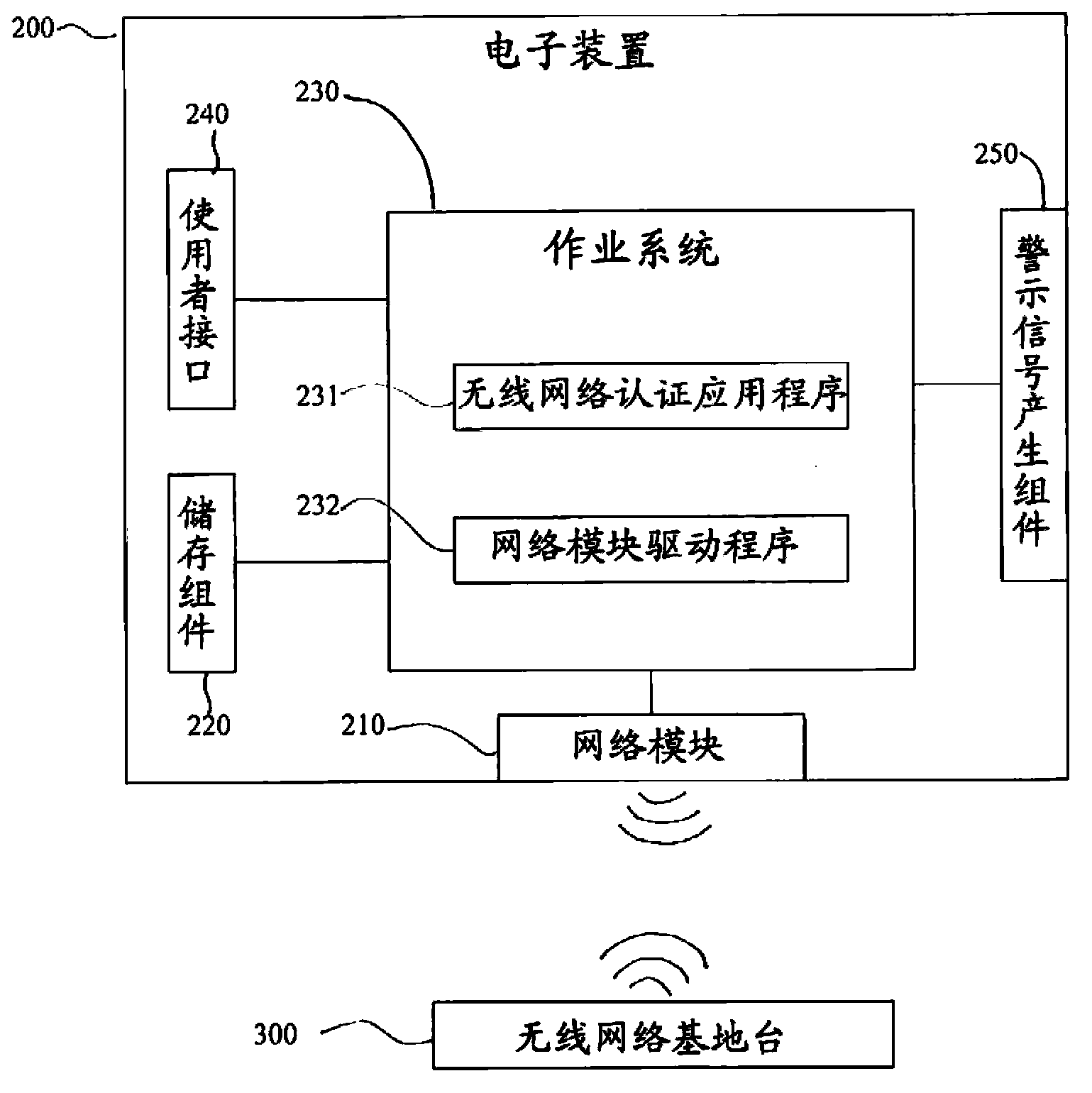
Computer readable storage medium for storing application program for network certification
InactiveCN103906060ANot easy to moveNot easy to reproduceNetwork topologiesTransmissionNetwork Access ProtectionApplication software
Owner:COMPAL ELECTRONICS INC
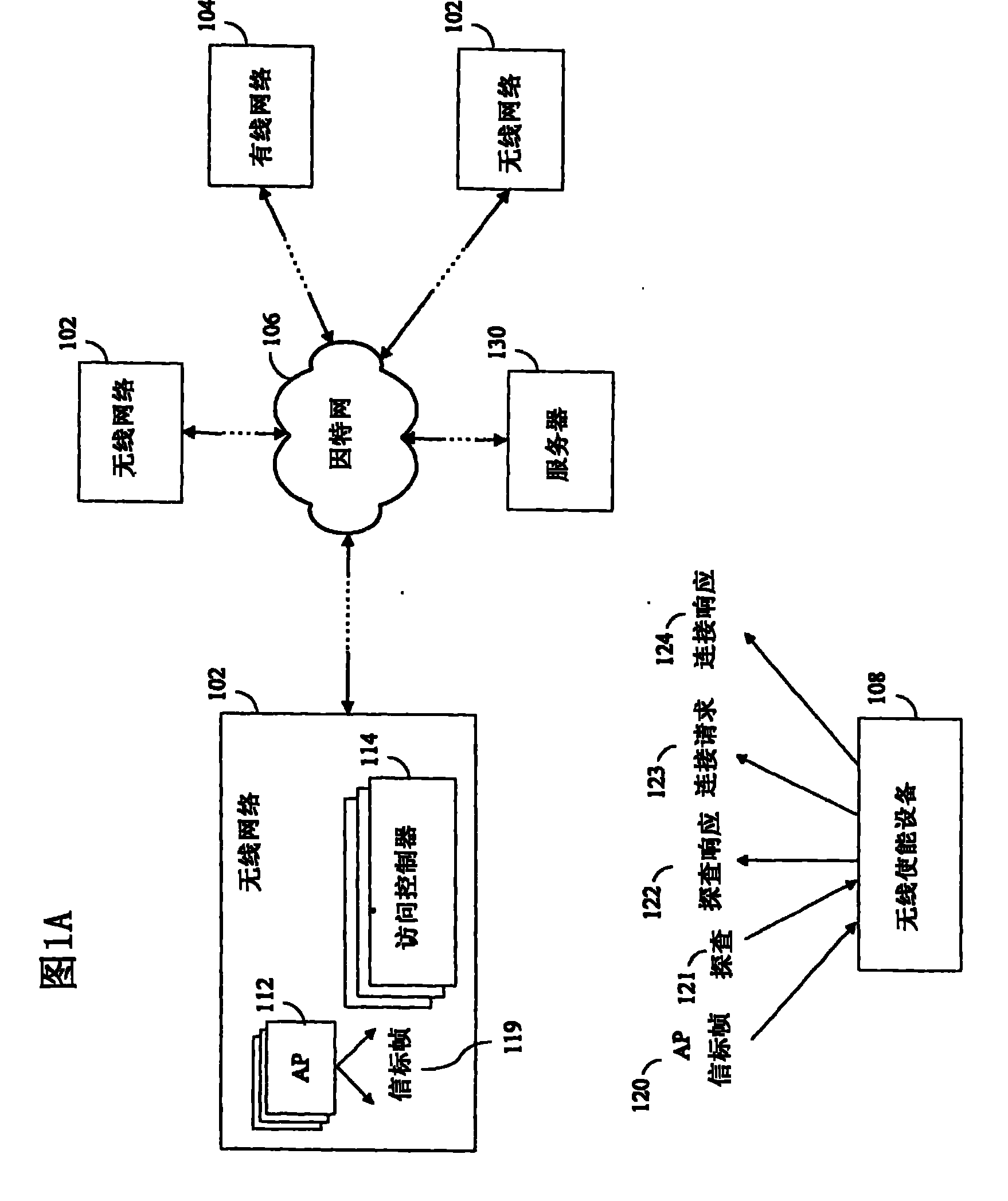
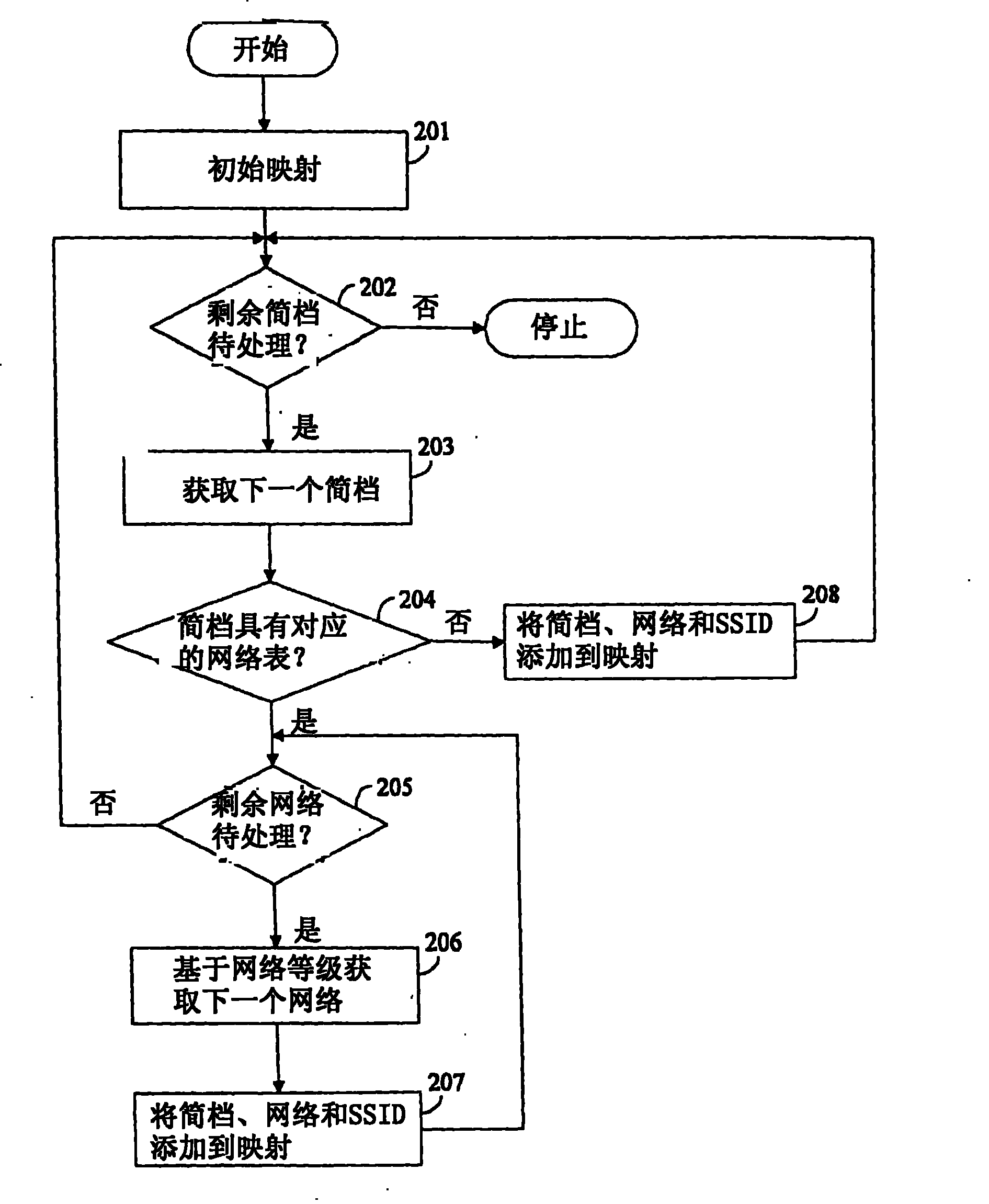
Network access point detection and use
ActiveCN101480032BIncrease choiceReduce processing timeAssess restrictionSpecial service for subscribersNetwork Access ProtectionUsability
A system and method of network point of access detection and use is disclosed. In accordance with such system and method, suitability of a given wireless network for access and use can be determined. Such system and method are fully-configurable and incrementally-updatable using configuration information. The configuration information, which can include network profiles and scripting functions, can be used to dynamically configure a client device to perform test network points of access, to determine usability status of network points of access, without modifying an underlying operating platform (e.g., an operating software platform) of the client device. The usability status can be cached by a client device and used to facilitate subsequent network detection and to make an informed selection of a network point of access.
Owner:BOINGO WIRELESS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com