Intelligent network firewall equipment and network attack protection method
An intelligent network and firewall technology, applied to electrical components, transmission systems, etc., can solve problems such as difficulty in adapting to network attack situations and rigid firewall policies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
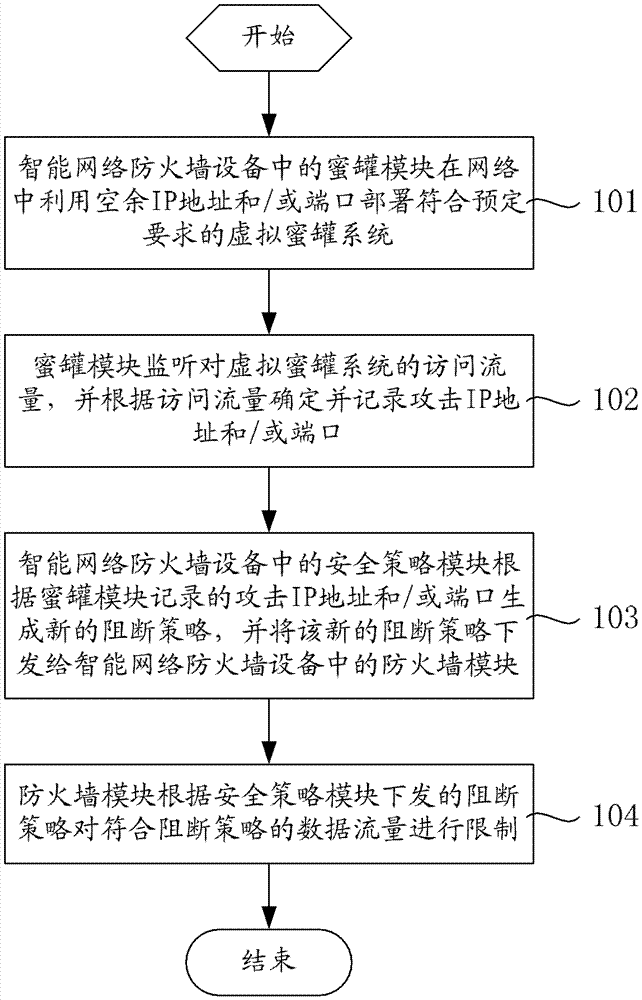
[0037] The technical solutions of the present invention will be further described in detail below through the accompanying drawings and embodiments.
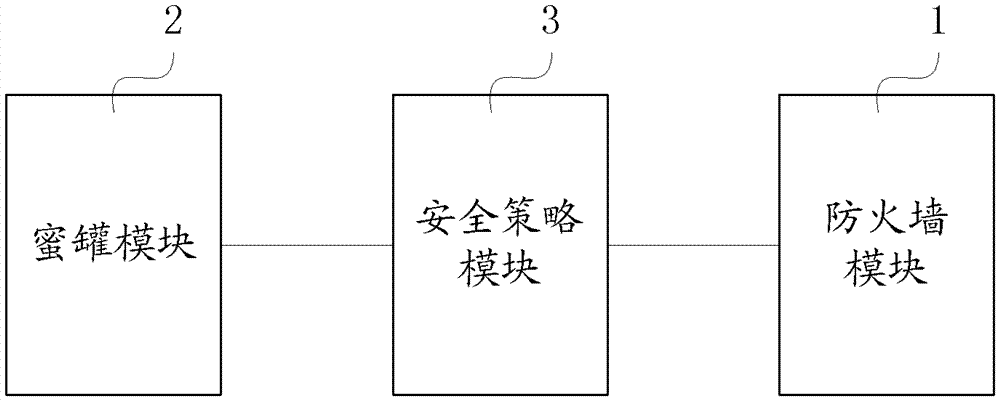
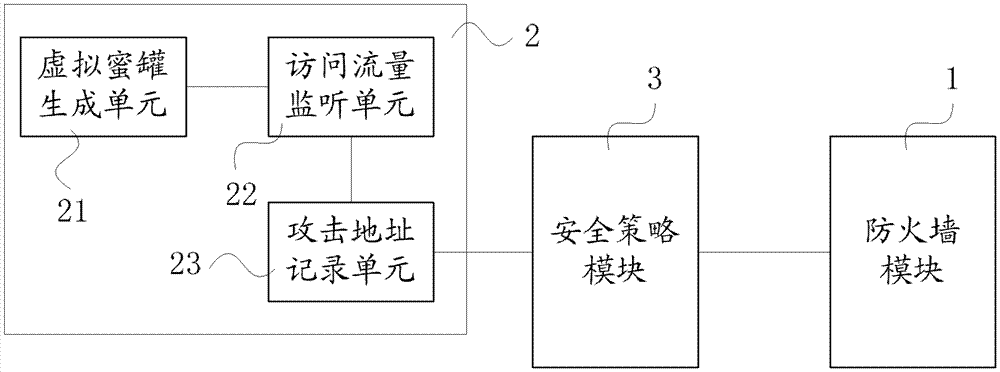
[0038] First, explain the honeypot technology. A honeypot (or honeypot system) is a system specially used to trap hackers. It can be a physically existing host with various vulnerabilities and monitoring systems deployed on it; also It can be the IP address, port, and service virtualized by the network device. It does not exist in itself, but from the perspective of an attacker on the network, this host does exist and can respond and provide services.
[0039] In the context of the present invention, the honeypot exists to attract various scans, attacks, and compromises in the network. By monitoring the network traffic flowing into / out of the honeypot, these behaviors can be analyzed to determine whether they may be malicious Cyber attacks.
[0040] Such as figure 1 Shown is a schematic structural diagram of an embodiment of an inte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com