Entry management method and device
A technology for table entry management and equipment, applied in digital transmission systems, electrical components, transmission systems, etc., it can solve problems such as incorrect changes to neighbor entries, changes in security requirements, and the inability of equipment to serve users, so as to ensure reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
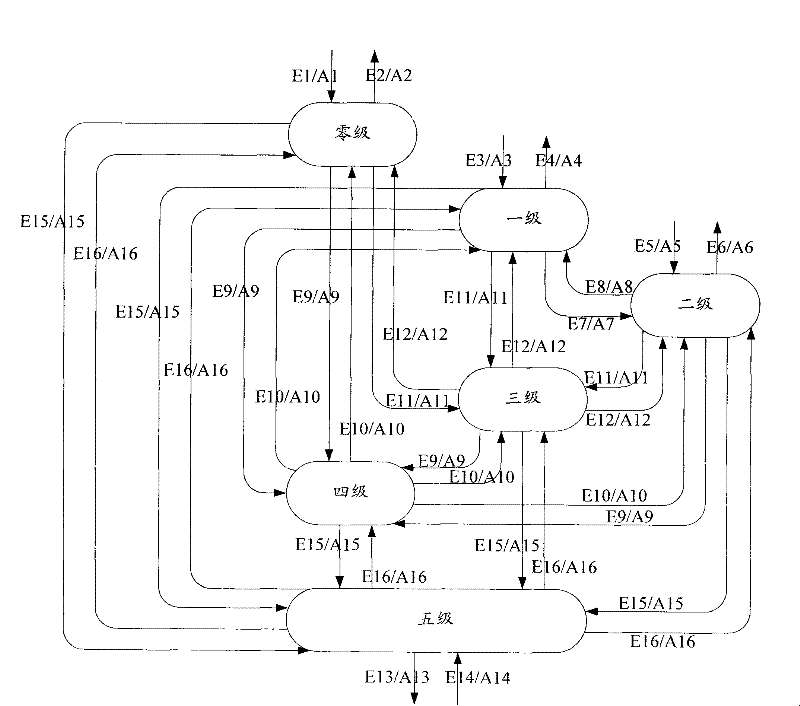
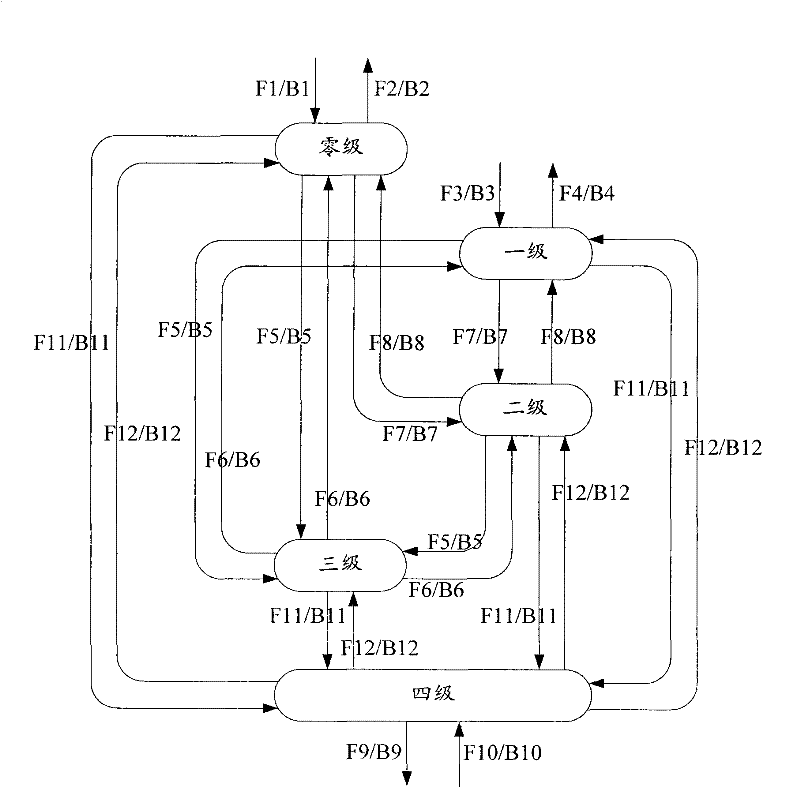
Image
Examples
Embodiment Construction
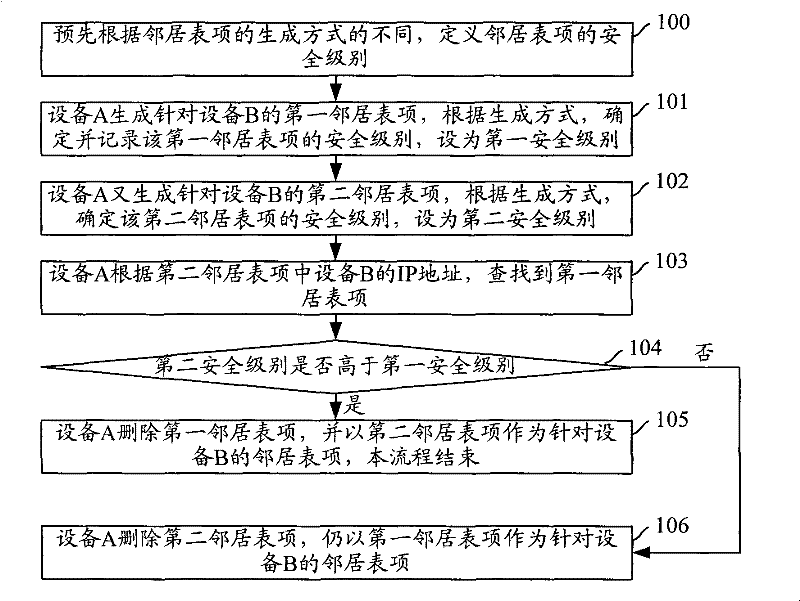
[0080] The core idea of the present invention is: to define the security level of neighbor entries in advance according to the different ways of generating neighbor entries; after a device generates a neighbor entry for a neighbor device, if it is found entry, and the security level of the newly generated neighbor entry is higher than the security level of the existing security entry, then update the existing neighbor entry with the newly generated neighbor entry, and use the security level of the newly generated neighbor entry Update the security level of an existing neighbor entry.
[0081] figure 1 The flow chart of the entry management method provided by the embodiment of the present invention, such as figure 1 As shown, the specific steps are as follows:
[0082] Step 100: Define the security level of the neighbor entry in advance according to the different ways of generating the neighbor entry.
[0083] Step 101: Device A generates a first neighbor entry for device ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com