Trusted network access and access control system and method
A network access and access control technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of high resource occupation, inflexibility, and difficult deployment, so as to achieve network self-adaptation and avoid identity forgery , to ensure the effect of safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
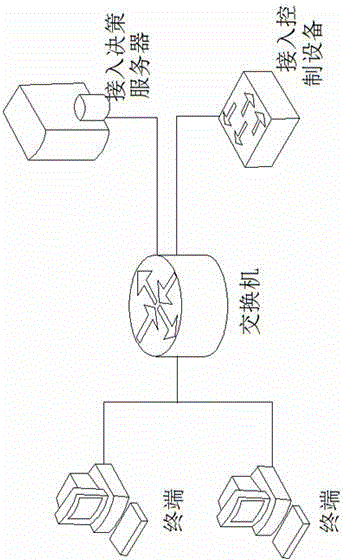
[0048] A trusted network access and access control system, such as figure 1As shown, the network access controller device and the network access decision-making device are usually added on the basis of the original network. The two can be the same device. In order to ensure the security and reliability of the network access terminal, the network access decision Trusted domain and secure trusted domain attribute, the secure trusted domain attribute includes digital label characteristics, security level, and the network access decision server sets the security trusted policy, which is used for the terminal to check the security and trusted status.
Embodiment 2
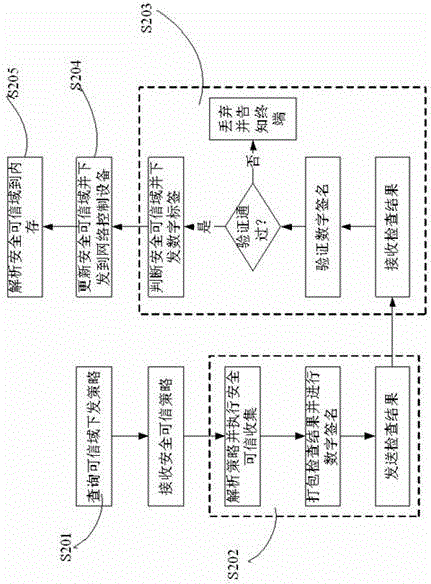
[0050] A trusted network access and access control method. The network access decision maker uses digital label technology to divide the entire network into different security domains. The network access requester initiates a network access request through identity authentication, and then accesses the network from the network. The decision maker receives the network access control policy, and the network access requester performs a security and credibility check according to the network access control policy, and sends the check result to the network decision maker. The decision maker judges the security status of the requester based on the check result, and sends the The digital label feature of the security domain is sent to the requester, and the requester digitally labels the network data packet during the subsequent network access process, and the network access controller judges whether the requester's network access is legal according to the digital label in the network ...
Embodiment 3
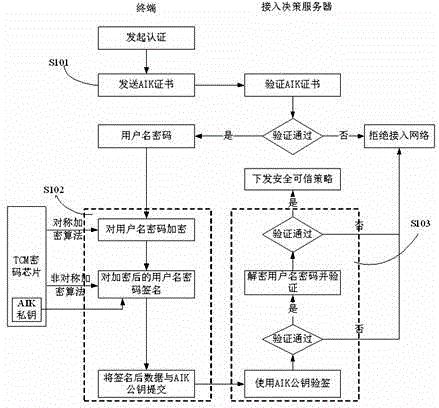
[0052] Such as figure 2 As shown, the specific implementation steps of network access requester identity authentication are as follows:
[0053] Step S101: The access terminal initiates a network access request, sends the platform identity AIK certificate to the network access decision server, and the network access decision server authenticates the platform identity, and prohibits network access if the authentication fails;
[0054] Step S102: the authentication is successful, the network access decision server returns the platform identity authentication result to the terminal, the terminal encrypts the user name and password entered by the user through the TCM symmetric encryption algorithm, signs it with the AIK private key, and sends it to the decision server after signing;
[0055] Step S103: After receiving the terminal authentication information, the decision server verifies the authentication information, decrypts the authentication information, performs identity aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com