Dynamic cookie verification method and device for network protection
A verification method and verification device technology, applied in the field of network security, can solve problems such as inability to adapt to different operating environments, and achieve the effect of preventing access attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
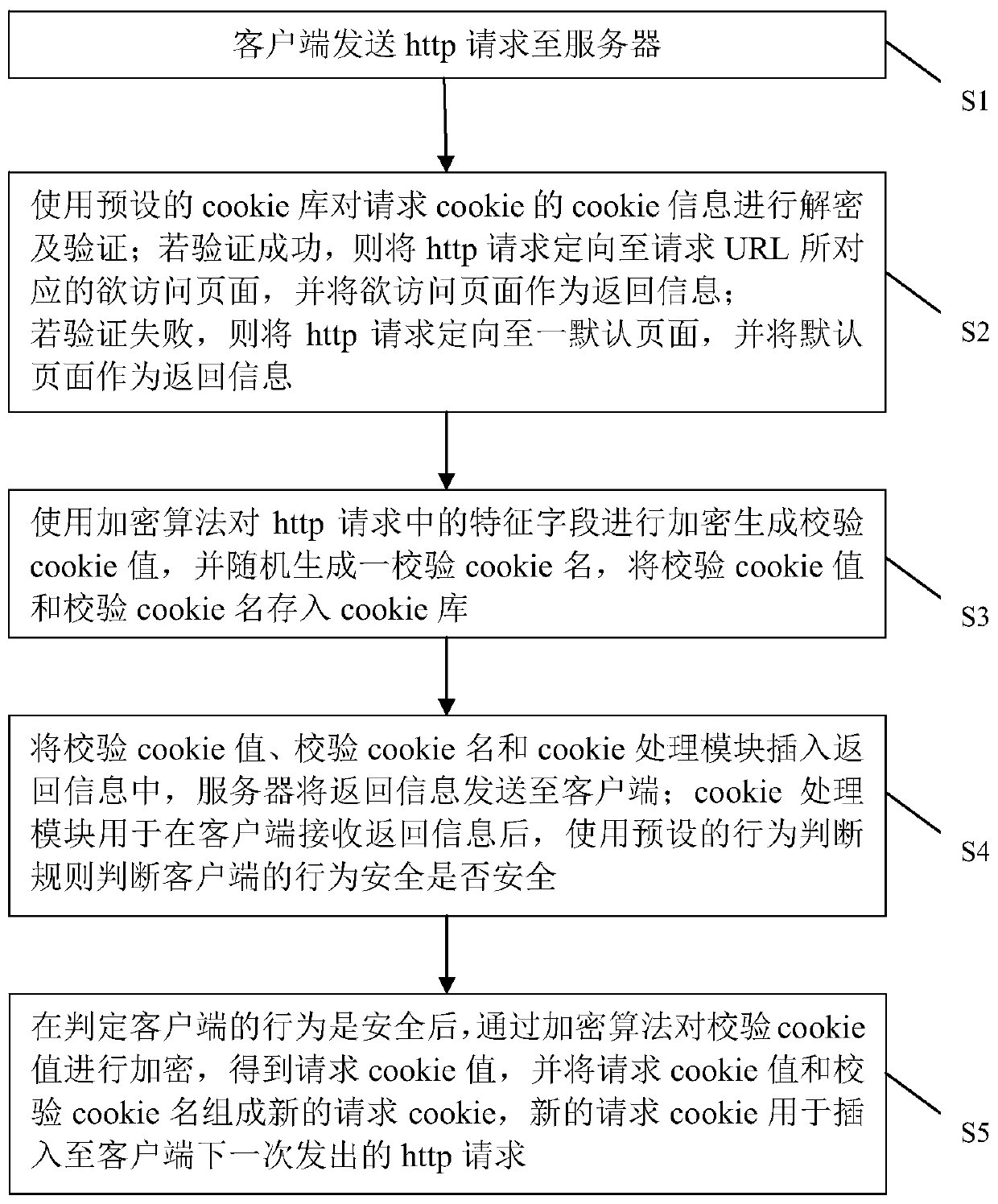
[0074] Such as figure 1 As shown, this embodiment discloses a dynamic cookie verification method for network protection, comprising the following steps:
[0075] S1. The client sends an http request to the server; the http request includes a request cookie and a request URL;
[0076] S2. Use the preset cookie library to decrypt and verify the cookie information of the requested cookie; the cookie information includes cookie name and cookie value;
[0077] If the verification is successful, the http request is directed to the page to be accessed corresponding to the requested URL, and the page to be accessed is used as the return information;
[0078] If the verification fails, the http request is directed to a default page, and the default page is used as the return information;
[0079] S3. Use an encryption algorithm to encrypt the feature field in the http request to generate a verification cookie value, and randomly generate a verification cookie name, and store the veri...
Embodiment 2
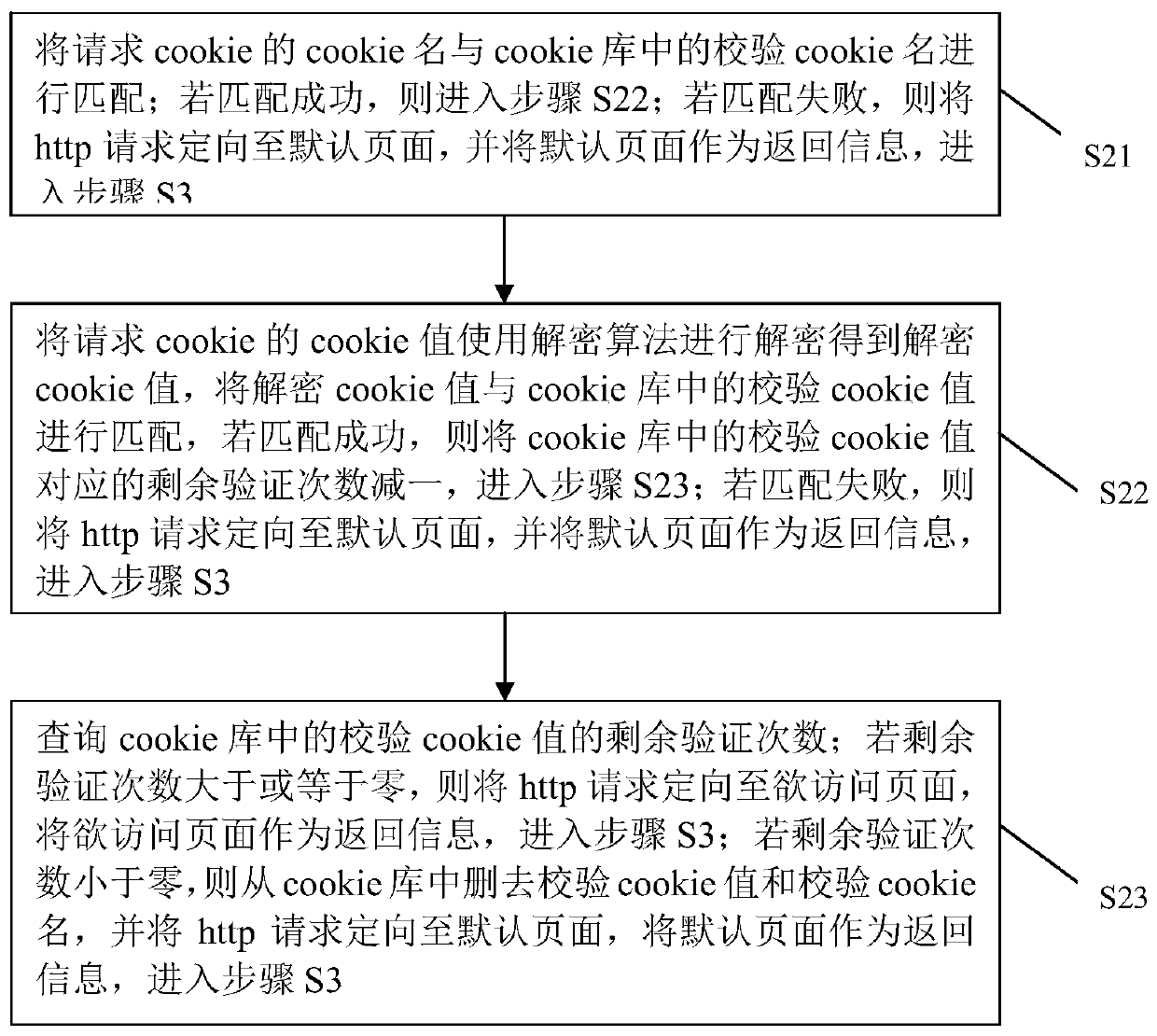
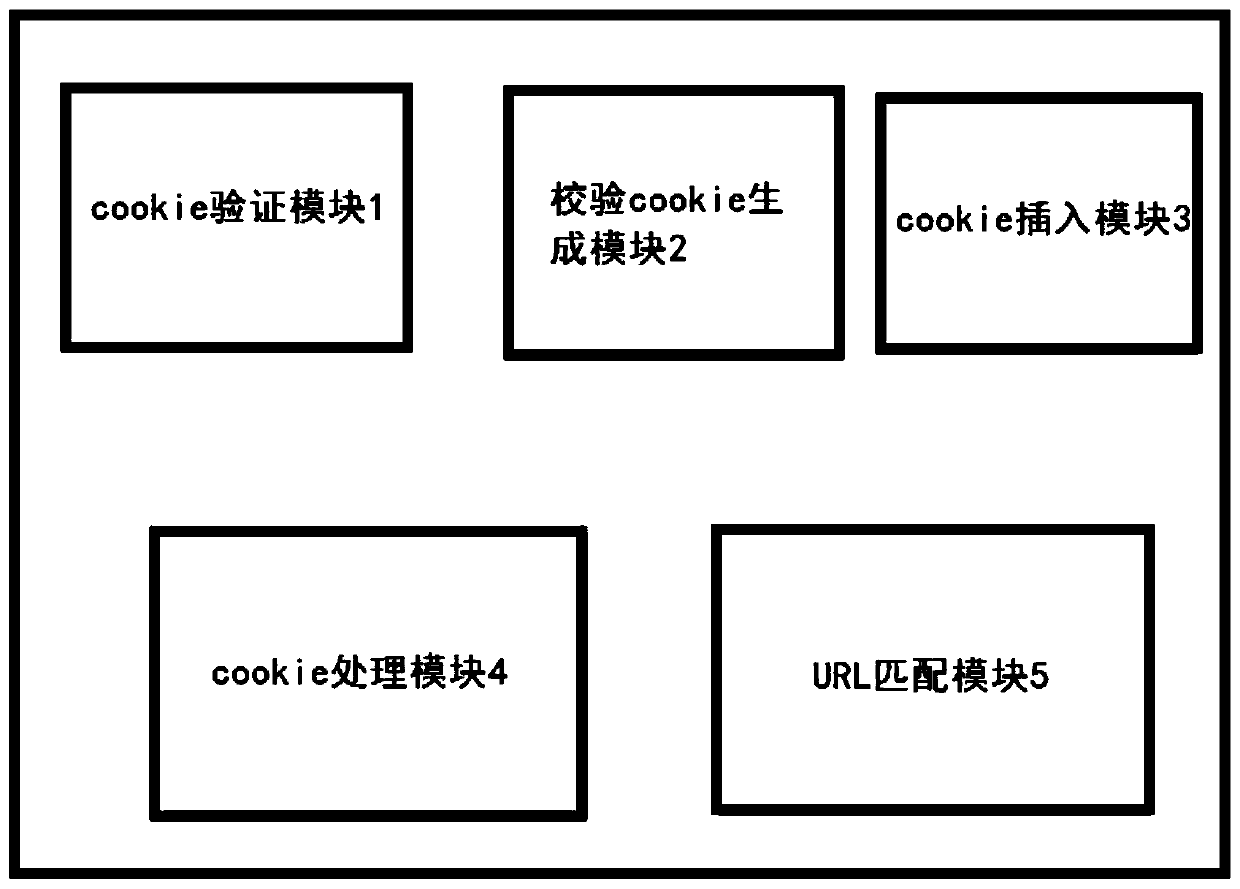
[0109] At the same time, if image 3 As shown, this embodiment also corresponds to the verification method of Embodiment 1, and discloses a dynamic cookie verification device for network protection. Its effect is similar to that of Embodiment 1, and will not be repeated here. This device includes:
[0110] cookie authentication module 1 for:
[0111] Receive the http request sent by the client to the server, the http request includes request cookie and request URL;
[0112] Use the preset cookie library to decrypt and verify the cookie information of the requested cookie; the cookie information includes the cookie name and cookie value;
[0113] When the verification is successful, the http request is directed to the page to be accessed corresponding to the requested URL, and the page to be accessed is used as the return information;
[0114] When the verification fails, the http request is directed to a default page, and the default page is used as the return information; ...
Embodiment 3
[0137] Such as Figure 5 As shown, this embodiment discloses a specific implementation of a cookie verification method, the steps of which include:
[0138] 1. The client sends an http request to the server, and the server of the present invention receives the request sent by the client.
[0139] 2. The URL matching module of the present invention will match the URL of the http request, and the URL request belonging to the protected object enters the dynamic cookie verification module of the present invention and enters the dynamic cookie verification link-1.
[0140] 3. URL requests that do not meet the matching rules are directly forwarded to the background server for normal processing.
[0141] 4. The request matching the URL rule will enter the cookie verification link-1 of the present invention to check to see if there is a cookie named cookie B, and if it exists, it will enter the cookie verification link-2.
[0142] 5. If the URL rule is matched, but there is no cooki...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com