Video acquisition security processing system and method based on zero trust mechanism
A security processing and video collection technology, applied in the field of data security, can solve problems such as loopholes and video information security not being effectively protected, and achieve the effect of enhancing the ability to resist Trojan virus intrusion, easy promotion, and strong versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The specific embodiments of the present invention will be described below with reference to the accompanying drawings.
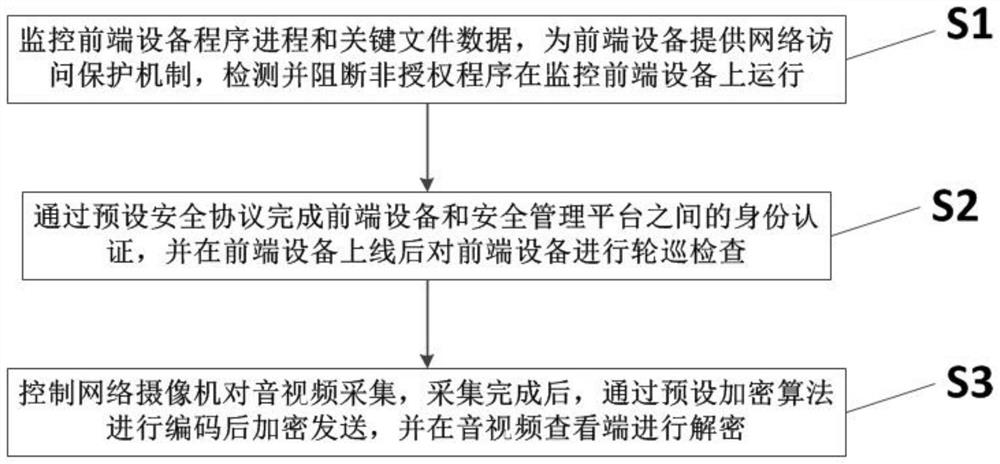
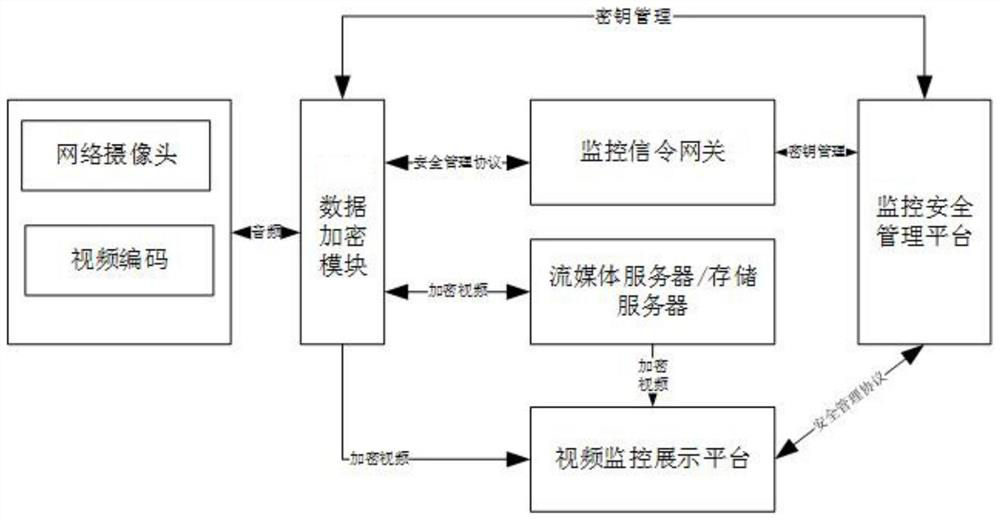
[0045] like figure 1 Shown is a video capture security processing system based on a zero trust mechanism, including:
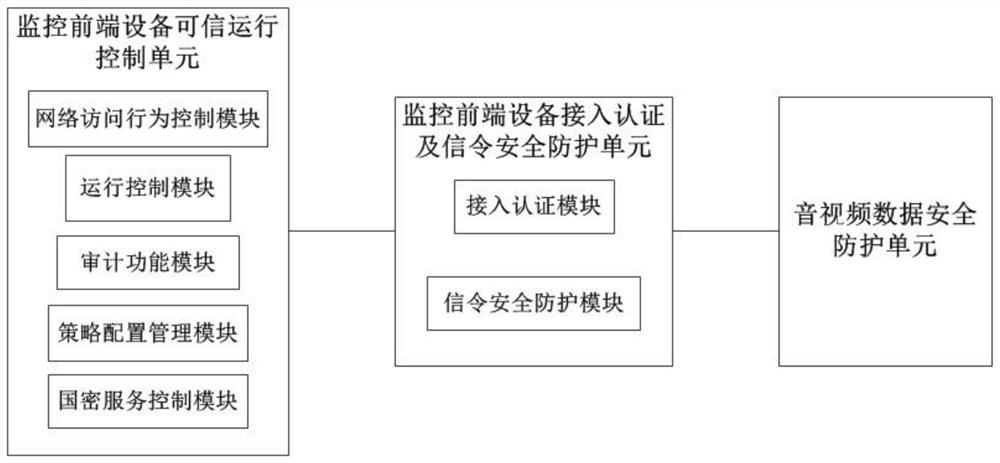
[0046] 1. The trusted operation control unit of the monitoring front-end equipment is set in the network camera operating system to monitor the program process and key file data of the front-end equipment, provide a network access protection mechanism, and detect and block unauthorized programs from running on the monitoring front-end equipment. .
[0047] This unit is based on the principle of trusted computing, and is realized by the built-in trusted operation control software in the network camera operating system. The trusted operation control software is based on the national secret encryption algorithm (SM2 / SM3 / SM4 / SM9). The trusted operation control unit for monitoring front-end equipment specifically includes:
[0048] The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com