Account number information protection method and mobile terminal
A mobile terminal and account information technology, applied in the field of information security, can solve problems such as oversimplification, hijacking or cracking by attackers, incomplete encryption mechanism, etc., to achieve the effect of avoiding losses and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
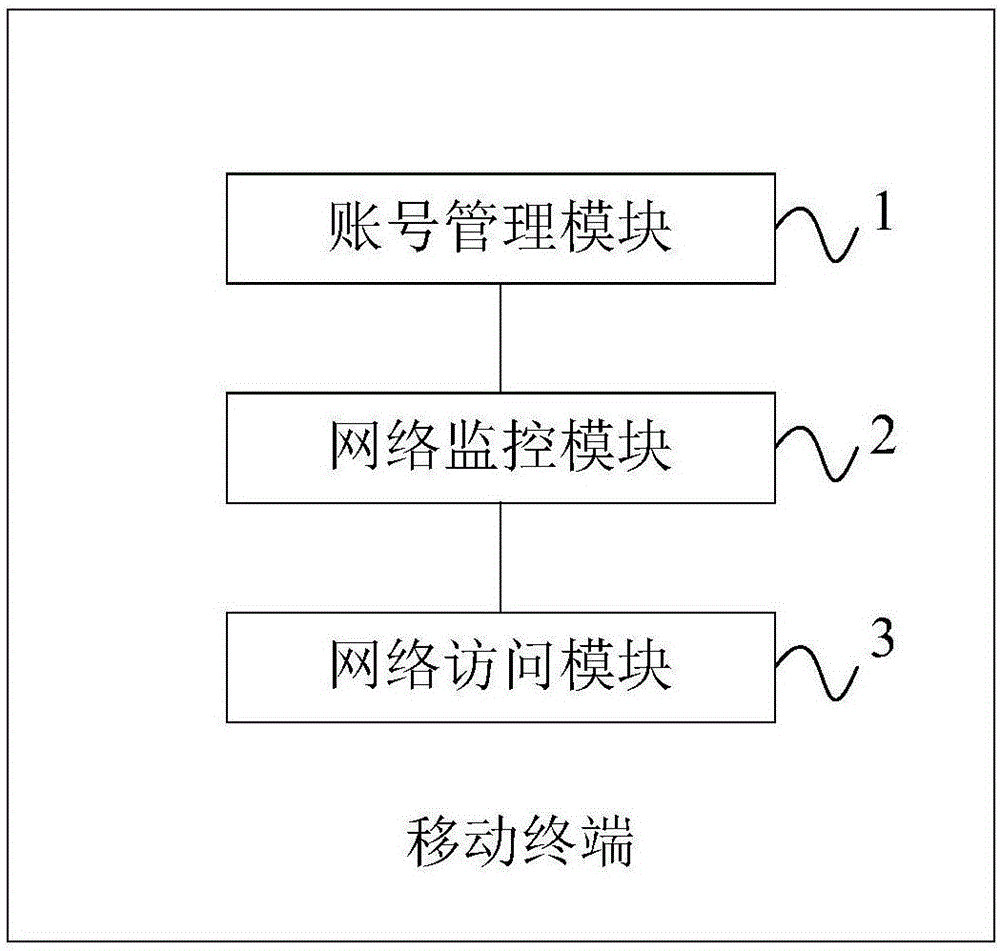
[0044] Such as figure 1 As shown, the mobile terminal of this embodiment includes an account management module 1, a network monitoring module 2 and a network access module 3;
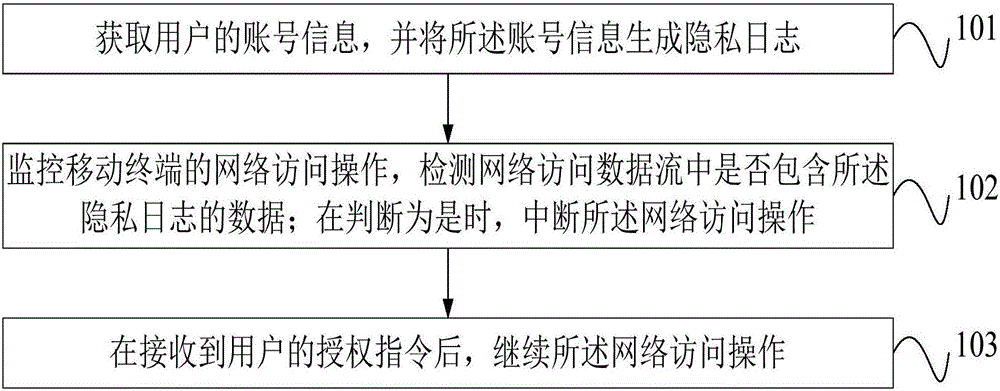
[0045] Wherein, the network monitoring module 2 is connected in communication with the account management module 1 and the network access module 3 respectively, and the account management module 1 is used to obtain user account information and generate a privacy log for the account information; The network monitoring module 2 is used to monitor the network access operation of the mobile terminal, and detects whether the network access data flow includes the data of the privacy log generated by the account management module 1; when the detection is yes, call the network access module 3. Interrupt the network access operation; the network access module 3 is configured to continue the network access operation after receiving an authorization instruction from the user.
[0046] In this embodiment, the acco...
Embodiment 2
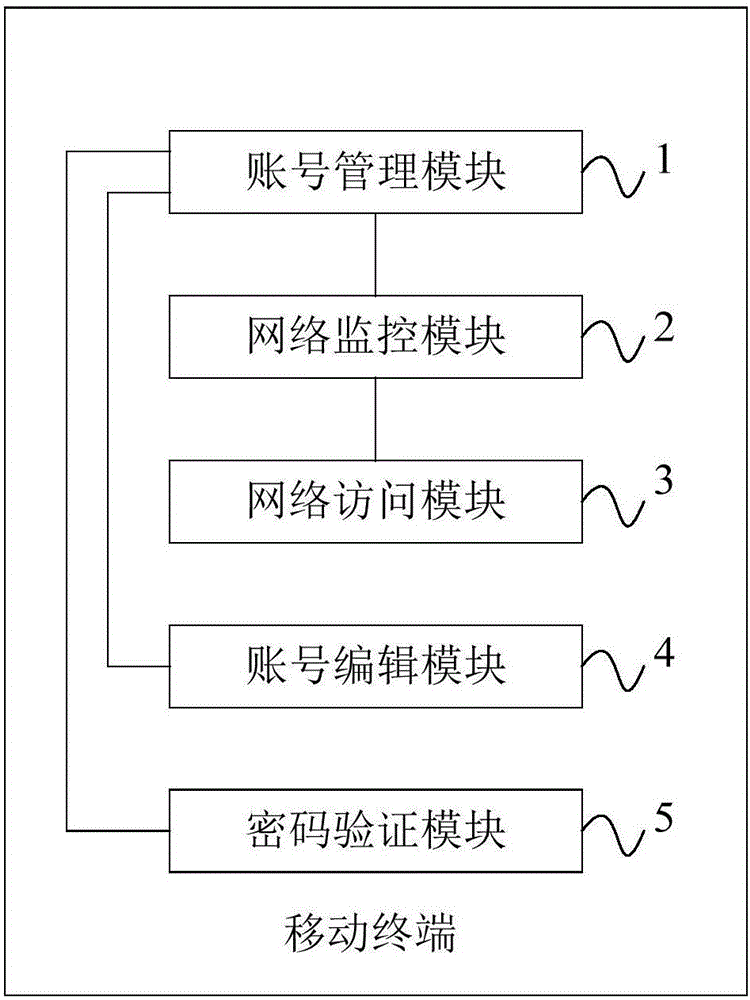
[0053] Such as image 3 As shown, on the basis of Embodiment 1, the mobile terminal of this embodiment also includes an account editing module 4 and a password verification module 5;
[0054]In this embodiment, the password verification module 5 is connected in communication with the account management module 1, the password verification module 5 will verify the management password input by the user, and only call the account management module 1 when the verification is passed. Obtain the account information of the user, that is, in this embodiment, only when the management password input by the user passes through, it indicates that the user has the authority to manage the account information; set management password, you can also set the secret protection question of the management password, etc. Follow-up operations are possible. In this embodiment, the account information obtained by the account management module 1 can have many kinds, such as account information of vari...
Embodiment 3
[0064] Such as Figure 5 As shown, on the basis of Embodiment 1, the mobile terminal of this embodiment also includes an authority setting module 6;
[0065] In this embodiment, specifically, the account management module 1 also uses an encryption algorithm to encrypt the privacy log data, thereby further ensuring the security of the privacy log data;
[0066] The network monitoring module 2 will monitor the network access operation of at least one application program in the mobile terminal, that is, monitor whether the network access operation performed by the application program in the mobile terminal needs to call the user's account information, so as to realize the mobile terminal. The application program monitors to ensure that the application program of the mobile terminal is allowed to call the account information of the corresponding user only when the user issues authorization.
[0067] The authority setting module 6 in this embodiment is connected in communication w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com