Office operation system reinforcing method and system
A technology of operating system and office software, applied in the field of security, can solve problems such as economic losses and hidden dangers of users and individuals, and achieve the effect of protecting rights and interests and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
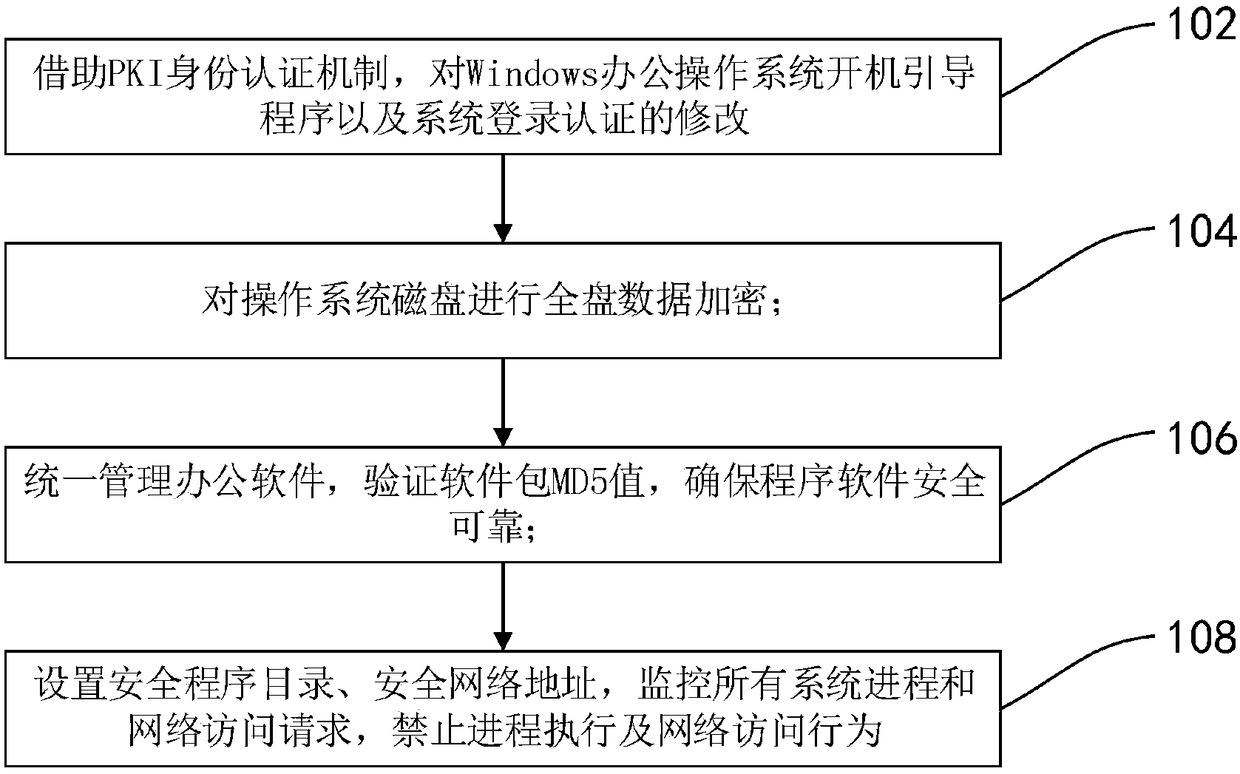
[0045] refer to figure 1 , shows a flow chart of steps of a method for strengthening a Windows office operating system. In this embodiment, the Windows office operating system reinforcement method may include:
[0046] Step 102, by means of the PKI identity authentication mechanism, modify the Windows office operating system boot program and system login authentication.
[0047] Public Key Infrastructure, PKI, a public key security infrastructure that manages secret keys and certificates. The U lock is a USB smart card computer encryption key.
[0048] PKI can provide reliable user identity certificate management, utilize credible user certificate system to set up identity certificate for the user in the present embodiment method, and store in U lock; Certificate public key hides and encrypts and preserves in Windows office operating system local disk ;Modify the boot program of the Windows operating system. In the booting link, it is required to insert the U-lock, and veri...
Embodiment 2
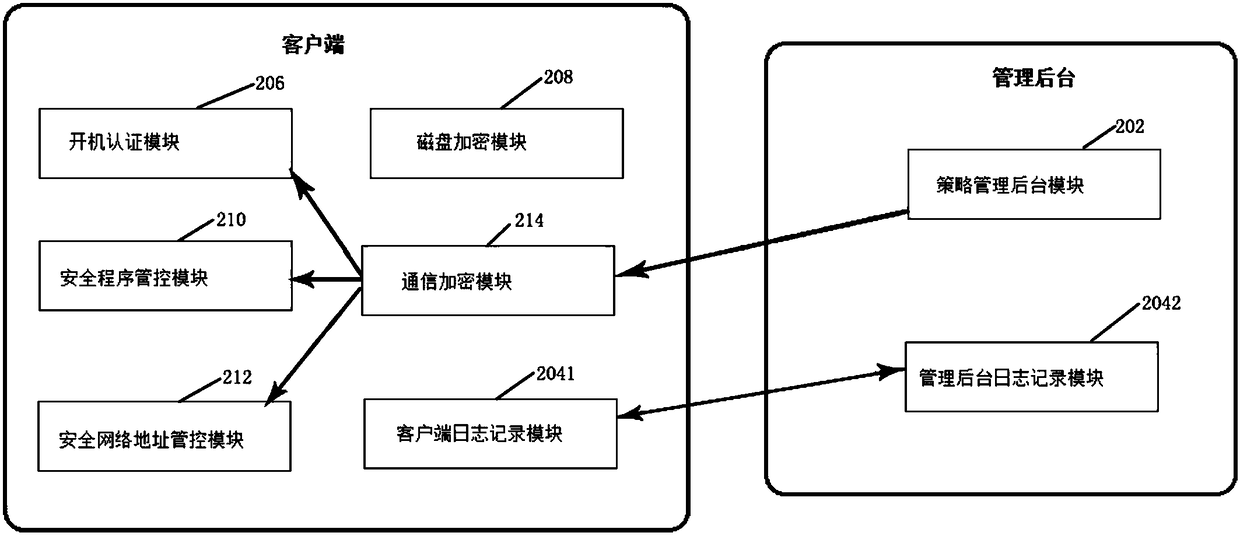
[0056] Based on the same inventive concept as the above-mentioned method embodiment, refer to figure 2 , shows a structural diagram of a Windows office operating system hardening system.
[0057] In this embodiment, the operating system hardening system includes:
[0058] Management background, client;
[0059] The management background includes:
[0060] The policy management background module 202 is used to implement user management of Windows office terminals inside the office network, management of security software and security network reinforcement policies;
[0061] Management background log recording module 2042: used for network access operation log information, synchronizing and managing client log records in the background.
[0062] Clients include:
[0063] The power-on authentication module 206 hides and encrypts the user public key certificate locally in the Windows operating system, revises the Windows office operating system boot guide and login authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com