A two-way network access authentication method based on digital certificate
A technology of digital certificates and authentication methods, which is applied to user identity/authority verification and key distribution, can solve problems such as inability to authenticate server identity authentication, and network access authentication cannot realize non-host network access authentication, so as to increase implementation costs, improve security and Practicality, the effect of improving the efficiency of management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
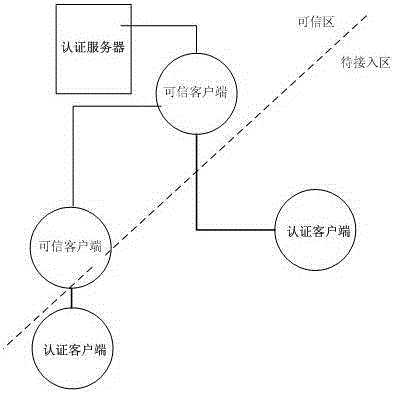
[0027] Such as figure 1 As shown in the divided area diagram of network access authentication, the two-way network access authentication method based on digital certificates disclosed in the present invention divides the network access authentication system into an area to be accessed and a trusted area, and the area to be accessed includes at least one customer to be authenticated The trusted zone includes an authentication server and at least one trusted client that has passed the authentication.
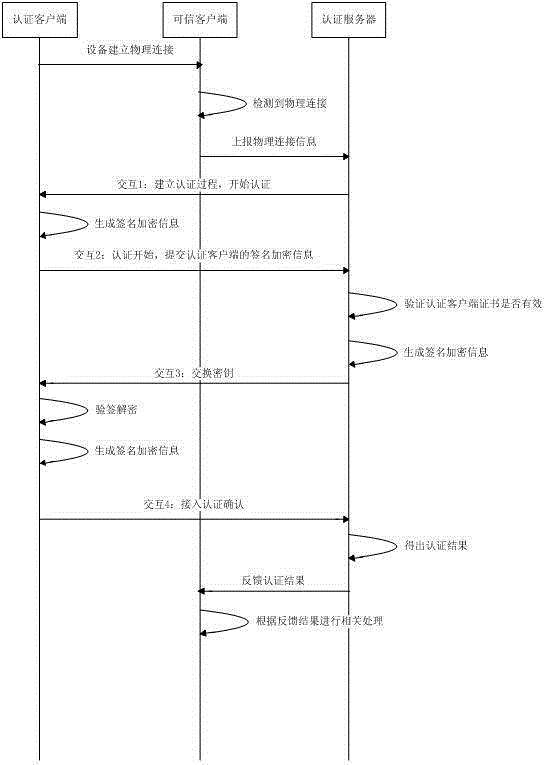
[0028] Such as figure 2 The flow chart of the two-way network access authentication method based on digital certificates is shown. The invention discloses a two-way network access authentication method based on a digital certificate, which specifically includes the following steps:
[0029] Step 1, divide the network access auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com