Network access method and system based on access authentication
A technology for access authentication and access to the network, which is applied in the field of access to the network based on the secure socket layer hypertext transfer protocol access authentication, which can solve the problems of short-term and inability to access the network, and achieve the effect of solving the short-term inability to access the network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
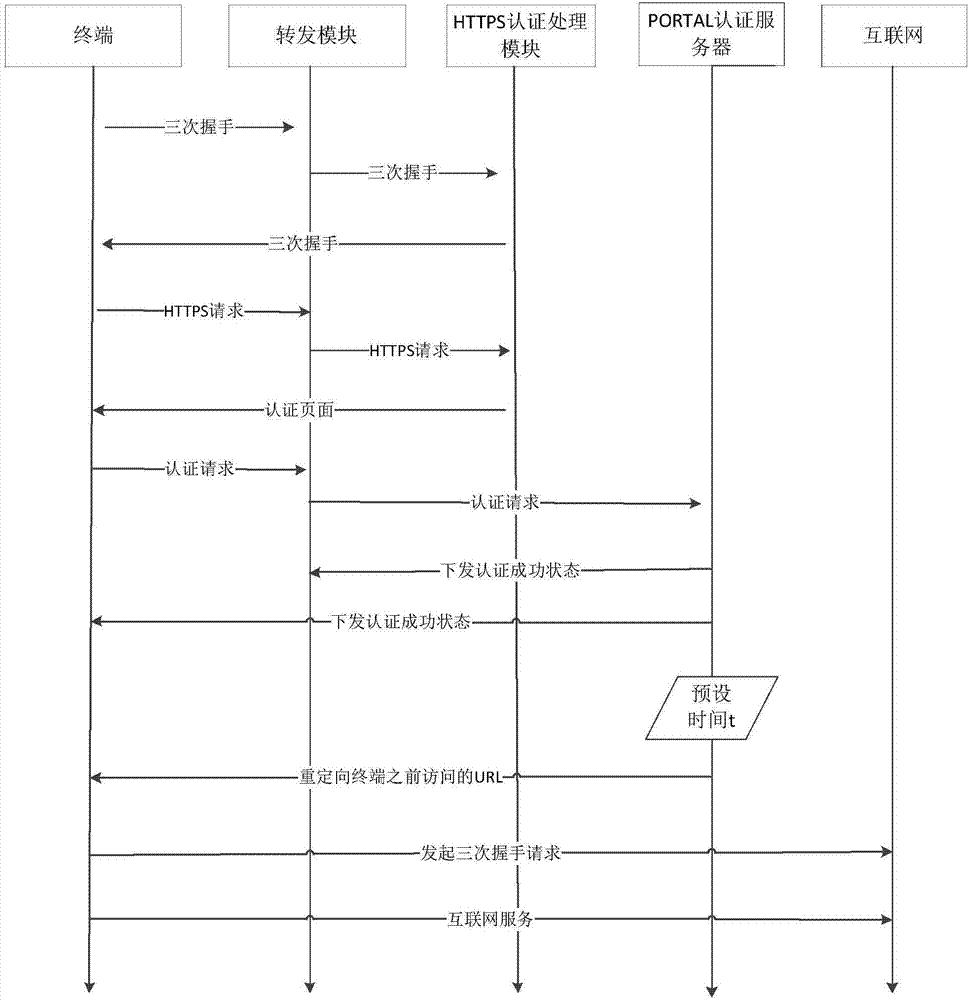
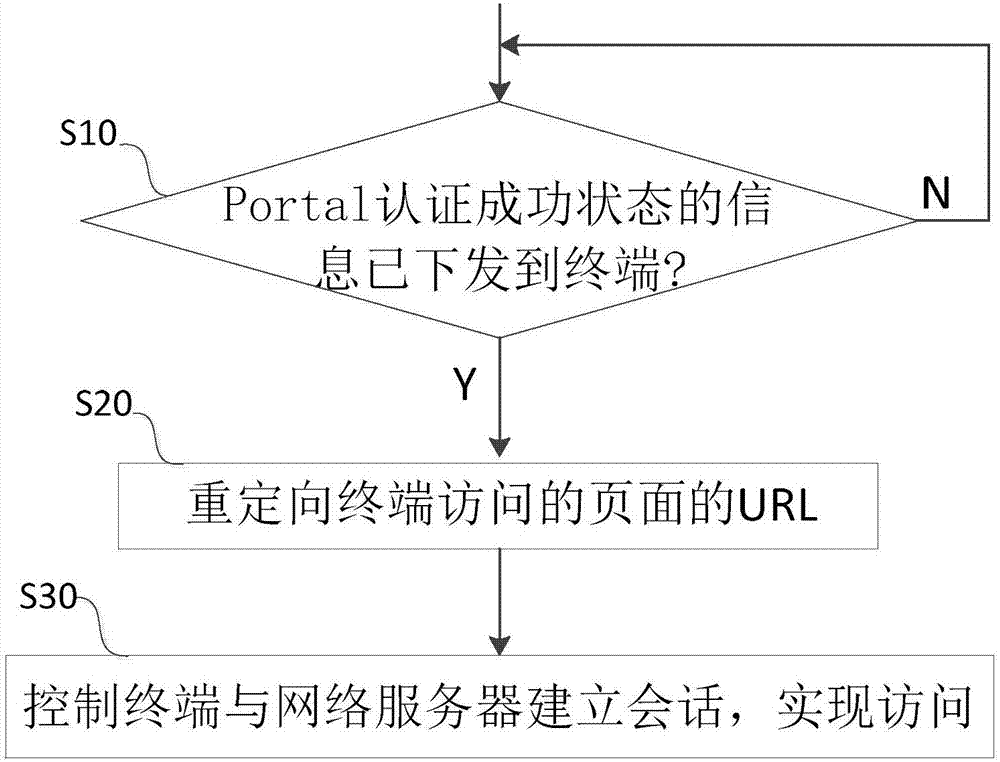
[0042] Such as figure 2Shown is a flowchart of a method for accessing a network based on access authentication described in this embodiment, and the method includes:
[0043] S10: judging whether the information about the success status of Portal authentication has been delivered to the terminal;
[0044] Before this step, the user sends a series of requests through the terminal. After receiving the request, the HTTPS authentication processing module sends an authentication page to the terminal. After the user fills in the relevant authentication information on the terminal, it sends it to the Portal authentication server for authentication. After the authentication, the Portal authentication server will judge the authentication status; if the authentication is successful, the Portal authentication success information will be sent to the terminal; if it is unsuccessful, the information will be sent to the HTTPS authentication processing module, and the HTTPS authentication pr...
Embodiment 2
[0069] The difference between this embodiment and the previous embodiments is that in this embodiment, a disconnection step is further included before redirecting the page accessed by the terminal.
[0070] Such as Figure 4 Shown is a flow chart of a method for accessing a network based on access authentication described in this embodiment, and the method further includes:
[0071] Disconnect the currently established HTTPS session connection.
[0072] If the HTTPS protocol is used for network access, the operation of disconnecting the currently established HTTPS session connection before redirecting the page accessed by the terminal can make the connection port of the terminal idle, which is convenient for establishing a session with the web server and redirecting The page accessed by the terminal is in contact with the server to form a double guarantee to ensure a smooth online experience.
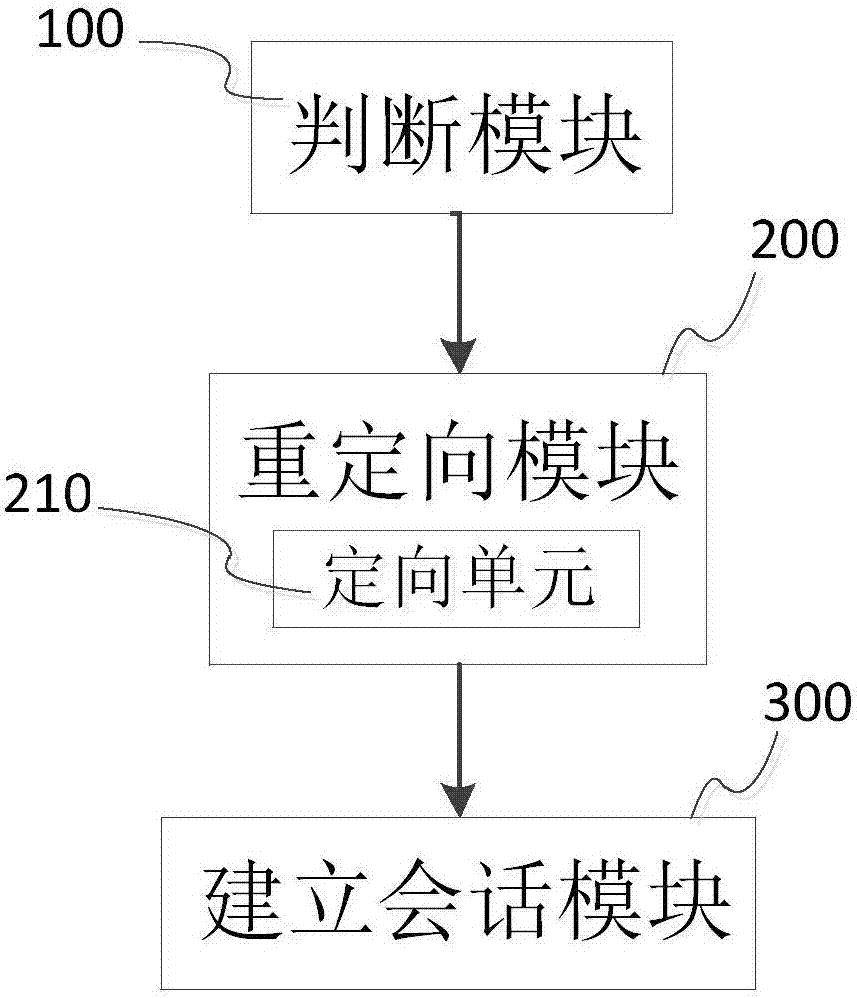
[0073] Correspondingly, such as Figure 5 Shown is a system structure diagram of...
Embodiment 3
[0076] The difference between this embodiment and Embodiment 2 is that this embodiment also includes the monitoring of time.
[0077] Such as Figure 6 Shown is a flow chart of a method for accessing a network based on access authentication described in this embodiment, and the method further includes the following steps between the step S10 and the step S20:
[0078] S11: Record the time from the successful delivery status to the start of the terminal;
[0079] S12: Determine whether the time is greater than a preset time, if yes, proceed to step S20.
[0080] In step S11, the timing unit is set to seconds, and the timing code is executed after the successful authentication status is sent, and the time from the successful status to the start of the terminal is recorded, and the timing code can use C language, C++, JAVA, etc.
[0081] Correspondingly, such as Figure 7 Shown is a system structure diagram of an access network based on access authentication described in this ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com