User equipment (UE) access restriction method and system thereof
A terminal access and terminal technology, applied in access restrictions, electrical components, wireless communications, etc., can solve problems such as high network maintenance costs and no restrictions on low-mobility areas
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
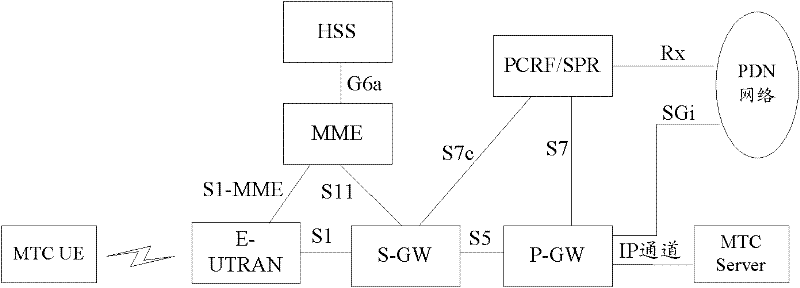
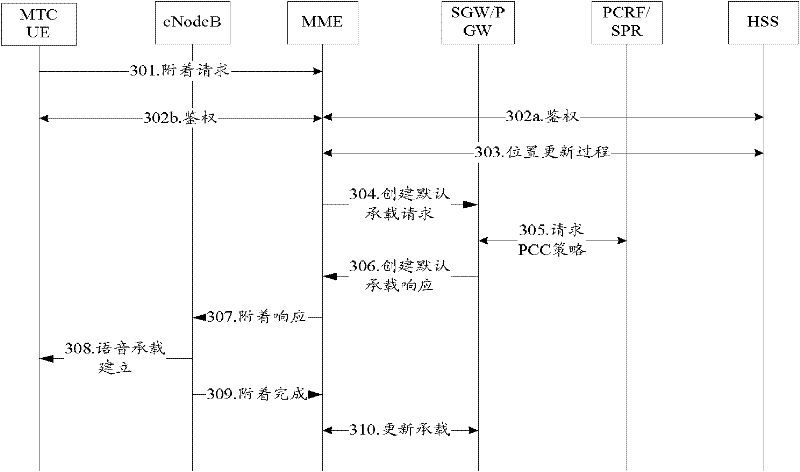
[0100] When the terminal attaches to the EPS network for the first time, it carries the location information of the terminal, and the MME (control plane network element) selects a PDN GW (user plane network element) serving M2M for it, and sends a request to the PDN GW to create a default bearer. The PDN GW initiates a policy request to the PCRF, carrying the location information of the terminal. The PCRF can learn the low mobility characteristics of its subscription from the SPR, and download the differentiated PCC policies corresponding to different areas of the terminal's allowed access area information (also available in the PCRF static configuration), PCRF finds that its location is outside the scope of the allowed location area, and rejects the policy request, and carries the value of the cause (cause) of the area restriction. After receiving the policy request rejection message, the PDNGW rejects the creation of the default bearer, and the MME rejects the terminal Attach...
Embodiment 2
[0113] When the terminal initiates to attach to the EPS network for the first time, there is no location area restriction, and it attaches to the EPS network normally. When the location of the terminal changes, a location update request needs to be initiated, carrying the location information of the terminal, and the MME notifies the PDN GW of the updated location information of the terminal through the bearer modification request. The PDNGW initiates a policy request to the PCRF, carrying the updated location information of the terminal. When the PCRF finds that its location is outside the allowed location area, it rejects the policy request and carries the cause value of the restricted area. After the PDN GW receives the policy request rejection message, it All PDN connections of the terminal are deleted, and access of the terminal in the network is restricted. Figure 6 It is a flow chart of the MTC UE with low mobility characteristics in the present invention performing lo...
Embodiment 3
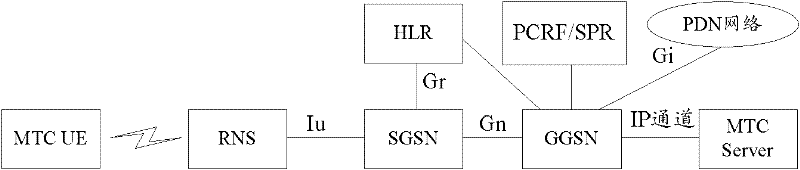
[0136] When the terminal attaches to the GPRS network and carries the location information of the terminal in the activate PDP context message, the SGSN selects a GGSN serving M2M for it, and initiates a PDP context creation request to the GGSN. The GGSN initiates a policy request to the PCRF, carrying the location information of the terminal. The PCRF can learn the low-mobility characteristics of its subscription from the SPR, and download the terminal's allowed access area information corresponding to the differentiated PCC strategy for different areas (also can be statically configured in the PCRF). PCRF finds that its location is outside the range of the allowed location area, Just reject the policy request and carry the cause value of the restricted area. After receiving the policy request rejection message, the GGSN rejects the establishment of the PDP context. The SGSN rejects the terminal to activate the PDP context in the GPRS network and restricts the terminal's acces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com