Access control method for distributed storage under cloud environment
A distributed storage and access control technology, which is applied in the field of distributed storage access control, can solve the problem of single access control method, and achieve the effect of cloud data isolation and efficient access control management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
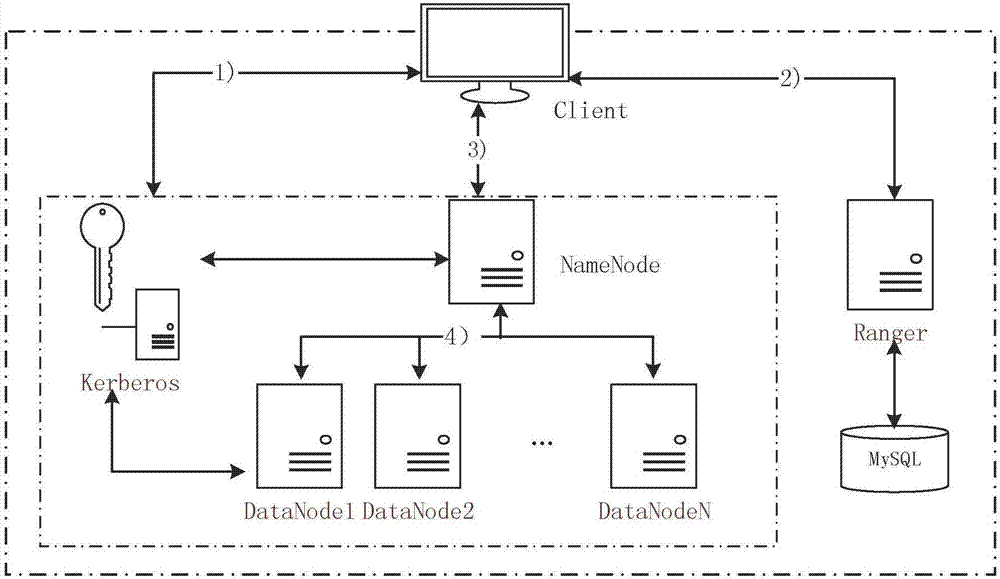
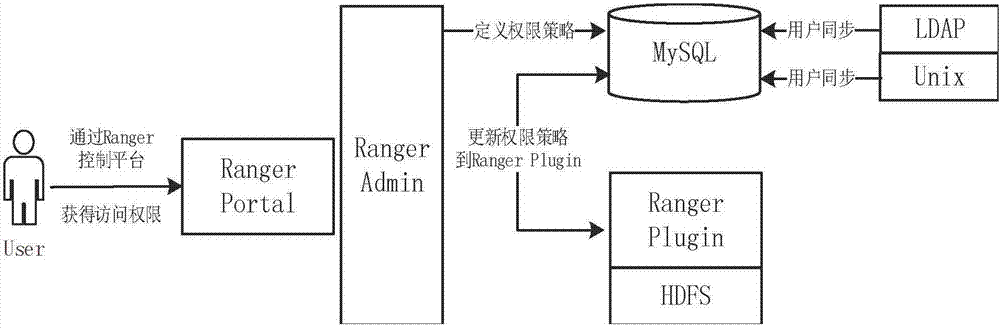
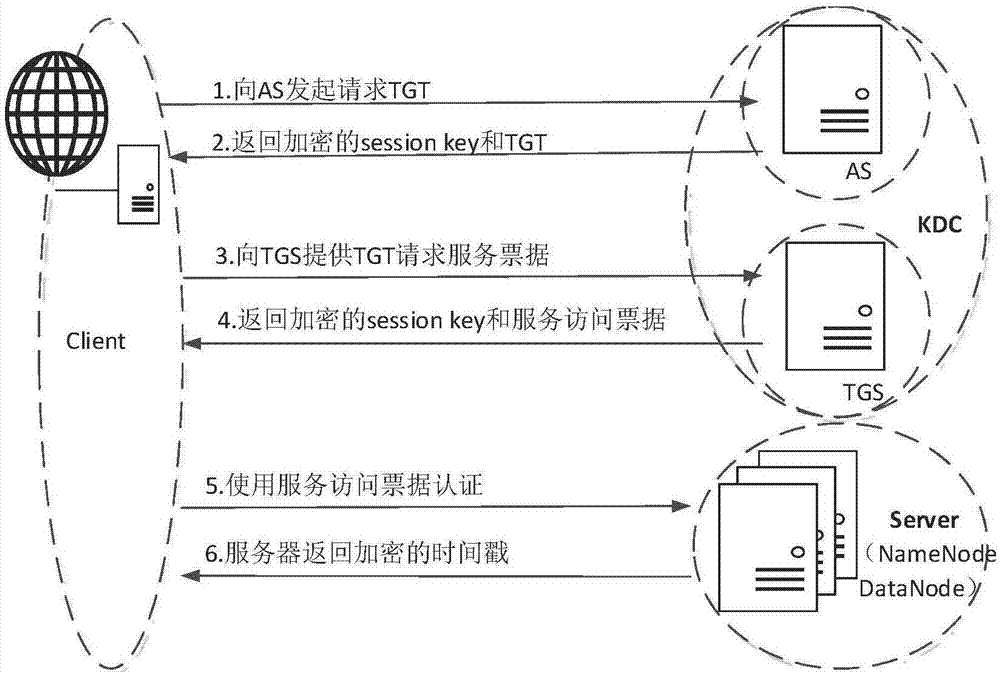
[0046] Such as Figure 1-3 shown.
[0047] An access control method for distributed storage in a cloud environment, implemented based on the Ranger framework and Kerberos; the Ranger framework includes Ranger Admin components, Ranger plugin components and Ranger Usersync components; Kerberos components include KDC and auxiliary tool ks_tool; specific function implementation steps as follows:
[0048] A. User-based access control
[0049] A1. Deploy Hadoop clusters; Hadoop clusters include at least one Master node and 3 slave nodes; Hadoop clusters realize upload, download and access to HDFS; the implementation of access control based on Ranger adds the first step to the security of cloud storage " Authentication threshold", within the Hadoop cluster, including client and management nodes, management nodes and data nodes, and identity authentication between data nodes, is implemented by Kerberos.
[0050] The implementation of distributed storage access control mainly includ...
Embodiment 2
[0068] The access control method for distributed storage in the cloud environment as described in Embodiment 1, the difference is that the authenticator encrypted using the TGSsession key includes the name / ID and timestamp of the system user; the request for a specific service transmitted in plain text is http service.
Embodiment 3
[0070] As in the access control method for distributed storage in the cloud environment described in Embodiment 1, the difference is that the RangerAdmin component is the core interface of security management, through the centralized management and control platform, the visual operation of the user is realized, and the The visualization operation is applied to HDFS to finally realize access control; the visualization operation includes creating and updating users / groups, defining services and access policies, and viewing access logs;
[0071]The Ranger plugin component is a lightweight java program embedded in the HDFS component to work; the Ranger plugin component is responsible for linking HDFS with the Ranger admin component on the one hand; on the other hand, it loads the access policy defined in the Rangeradmin component Go to the host where HDFS is located, and upload the access log of the system user to the Ranger admin component for auditing;
[0072] The Ranger Usersy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com