Method and system for sharing anonymous resource
A resource sharing and resource technology, applied in the field of computer information, can solve problems such as increasing server burden, unknown threats, and leaking user personal information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] Example 1. Anonymous authentication method
specific example
[0056] a. When the anonymous authentication system is established, the authentication server generates and publishes system parameters (q, G, G, g, g, e), where g, g are the generators of the group G and G respectively, and the order of the group is q, e It is a bilinear map e: G×G→G.
[0057] b. The authentication server chooses its private key x,y∈Zq, and generates its public key X=g x , Y=g y , the Zq represents an integer group of order q.
[0058] c. When the authenticator registers with the authentication server, randomly select t∈Zq and send C=g t To the authentication server, the server randomly selects α∈Zq, and calculates a=g α , and use its private key to generate an anonymous credential σ=(a, a y , a x C αxy ), denoted as (a, b, c), the authentication server sends σ to the authenticator.
[0059] d. When the authenticator performs authentication, the authenticator uses its anonymous credential σ and a random number s=(s 1 ,s 2 ) to generate a blinded signa...
Embodiment 2
[0065] Embodiment 2. Resource sharing method and system
[0066] This embodiment aims to provide a specific example of the resource sharing method and system of the present invention.
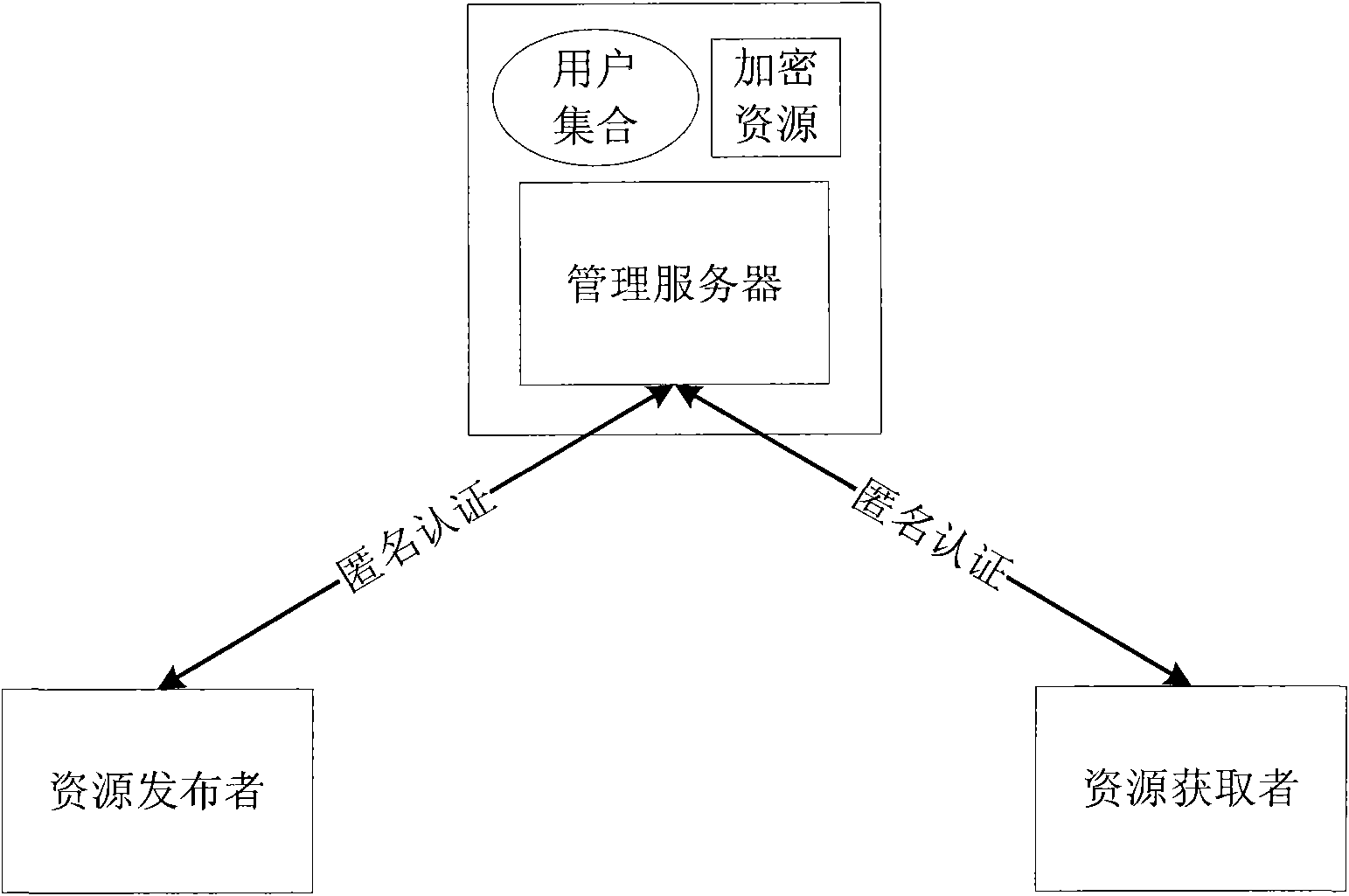
[0067] This embodiment is based on the following scenario setting: users A and B have registered on the resource server S, A wishes to publish resources through the resource server and restricts the attributes that users who obtain the resources should have, and B wishes to obtain the resources released by A and verify Properties that its publisher has. Therefore, in this setting, user A (or the computer client where user A is located) is the resource publisher, and user B (or the computer client where user B is located) is the resource acquirer.
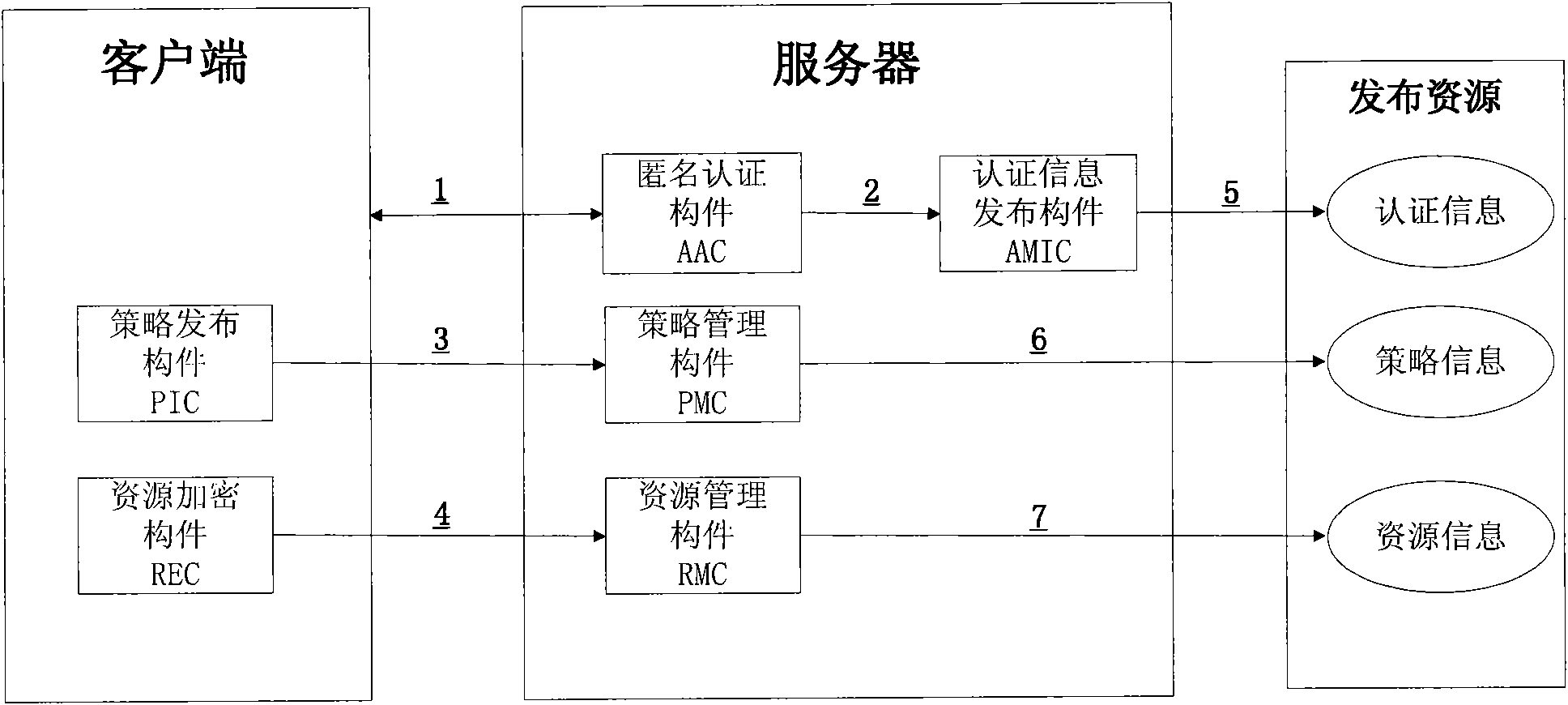
[0068] The process for user A to publish resources is as follows: image 3 As shown, the specific content is as follows:
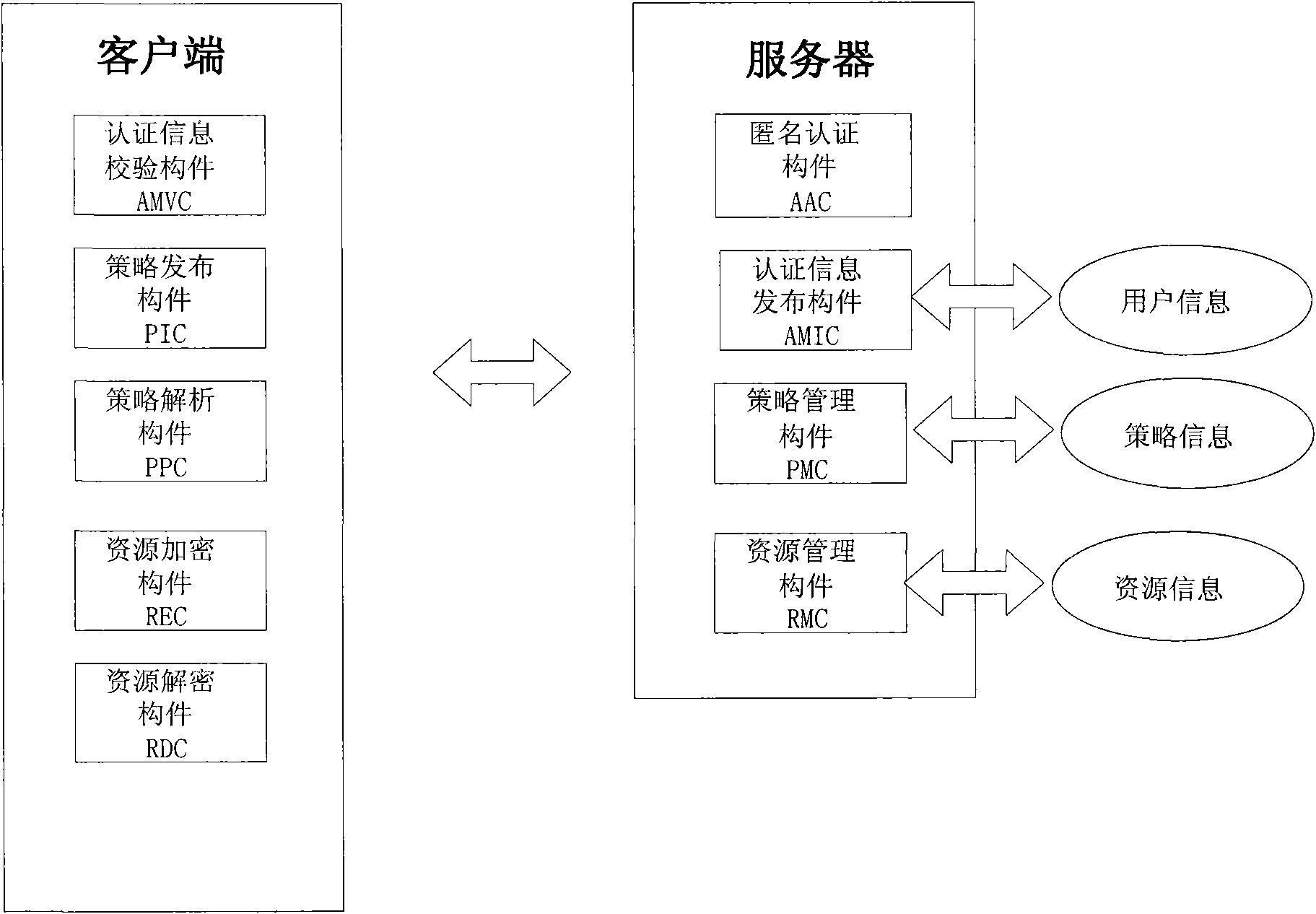
[0069] 1. Client A accesses server S and submits a resource publishing request. After obtaining the request, S calls the AAC...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com