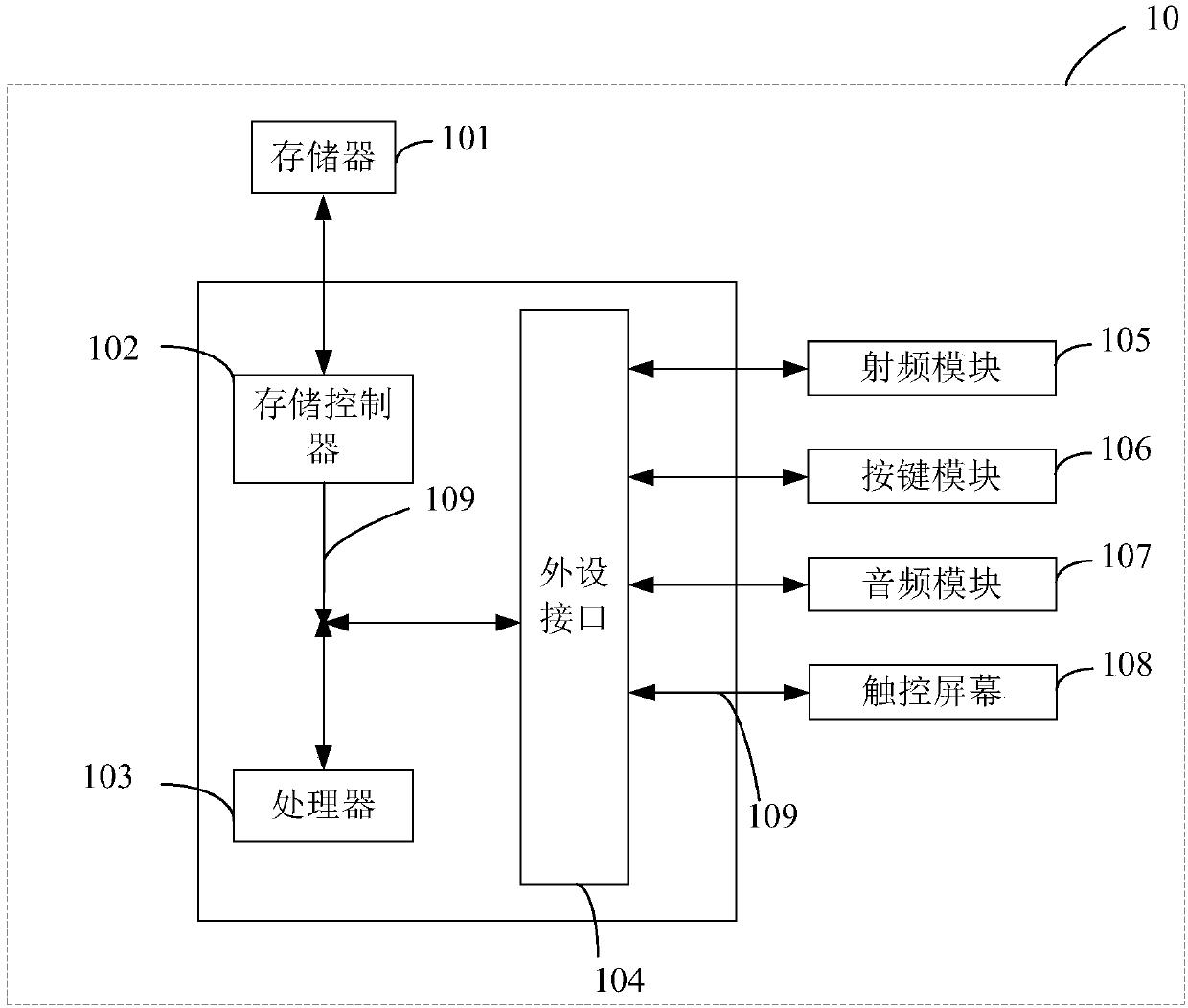
Patents
Literature
112results about How to "Protection of personal information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
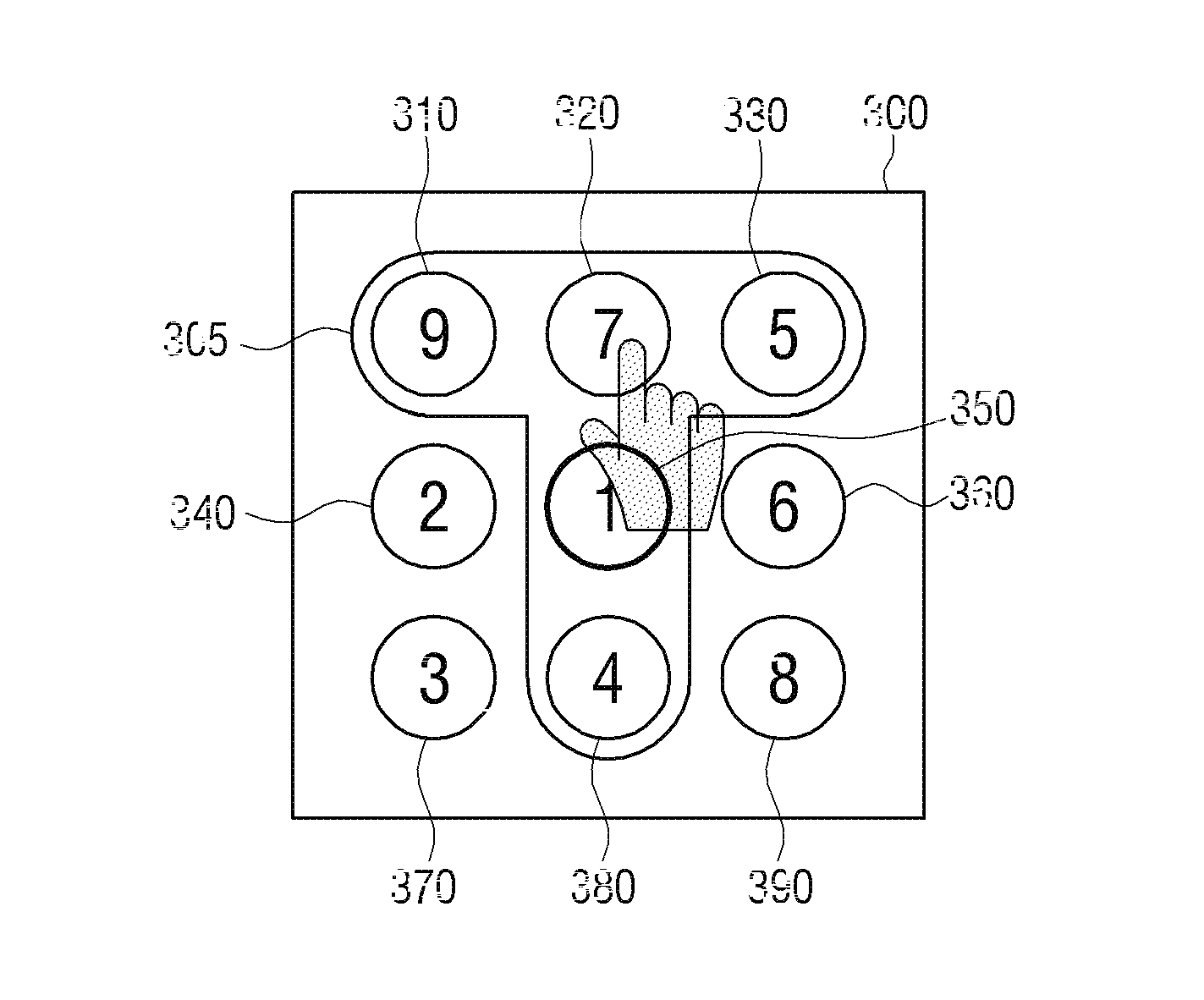
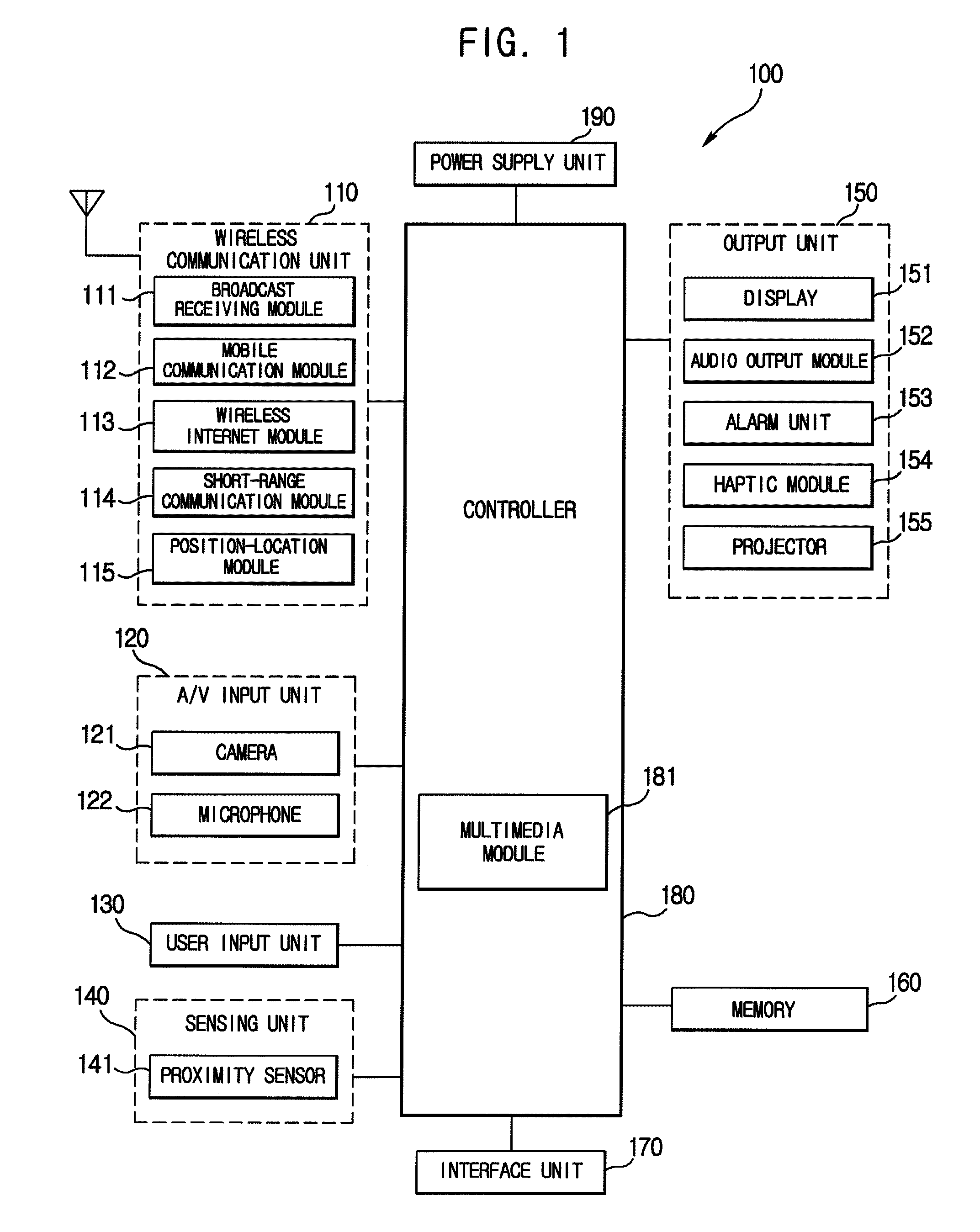
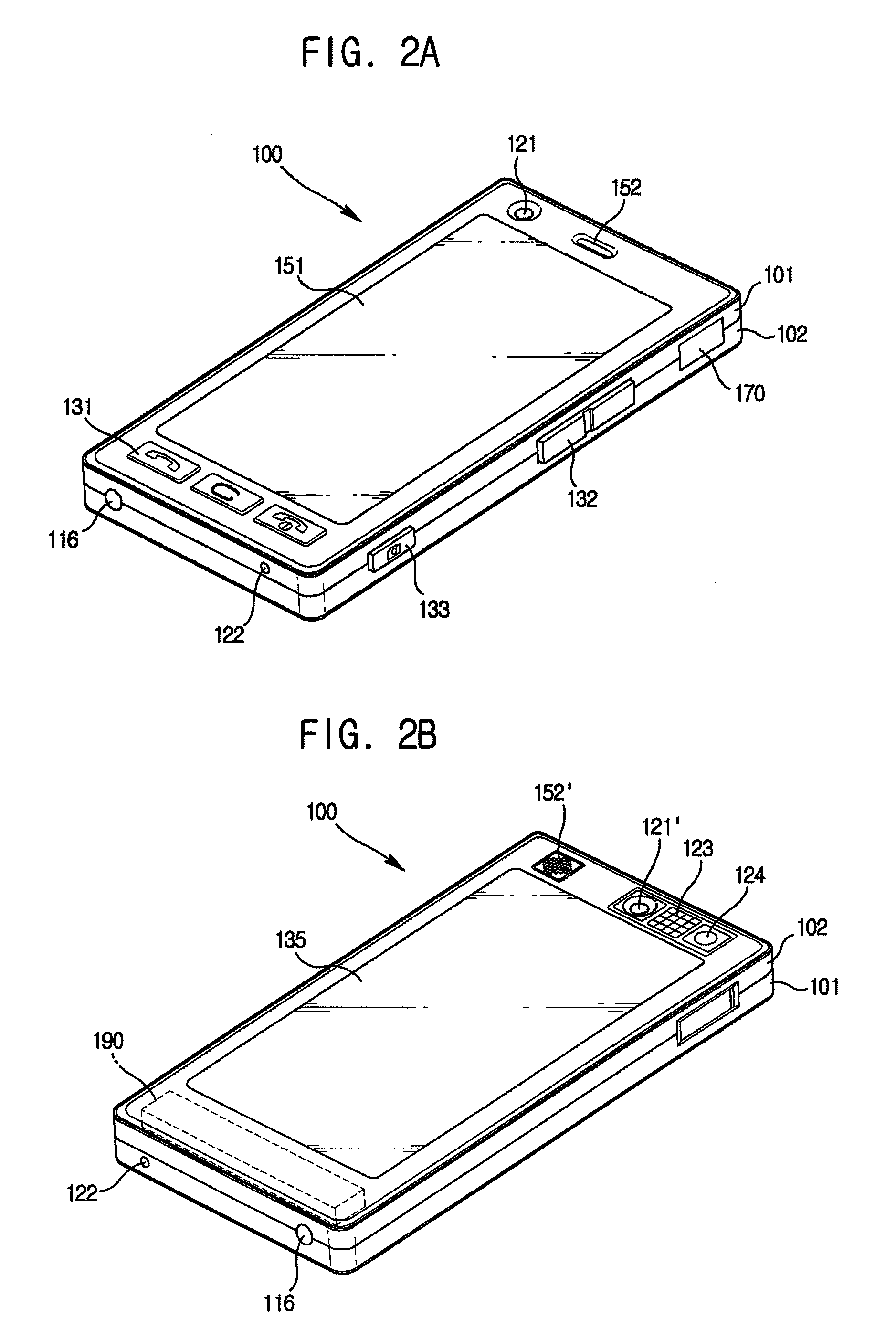
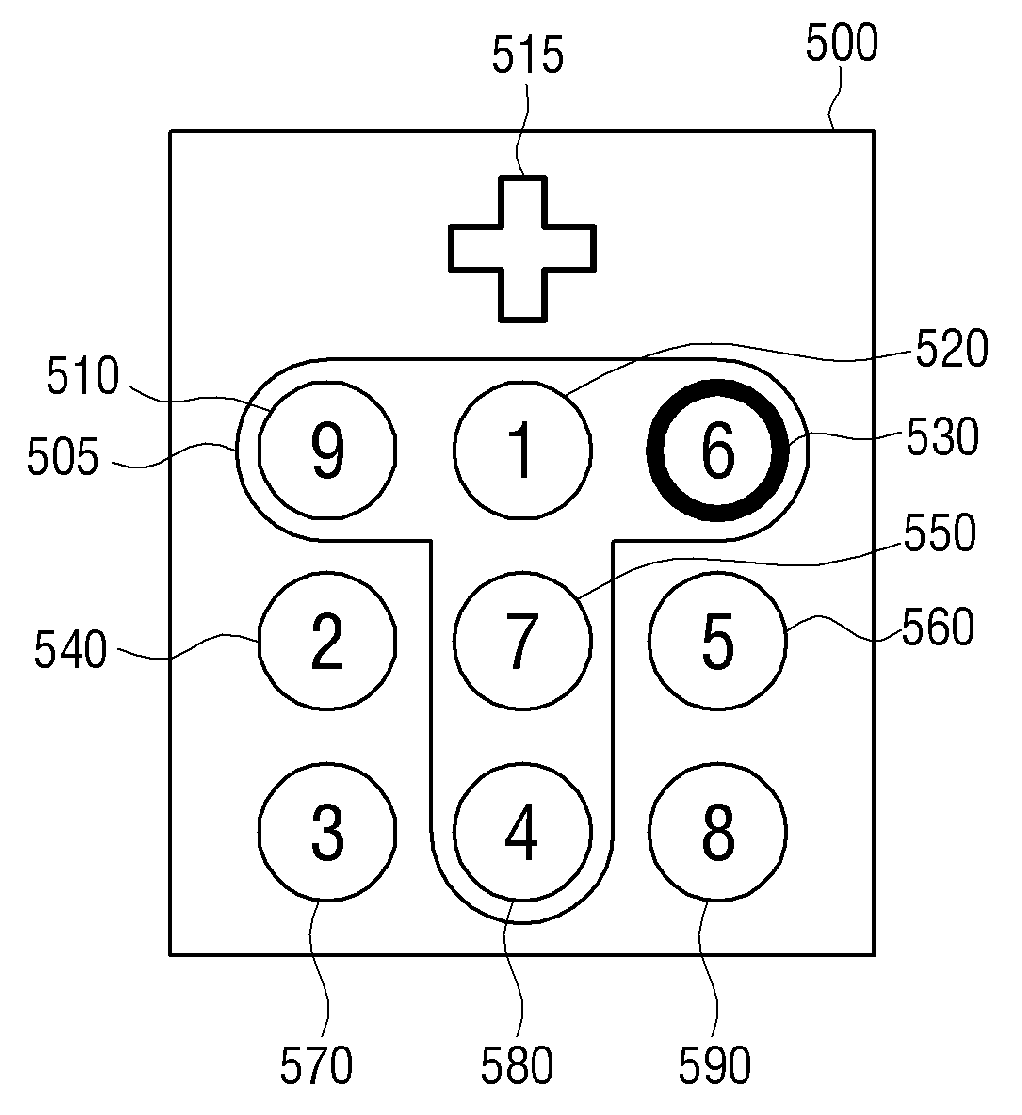
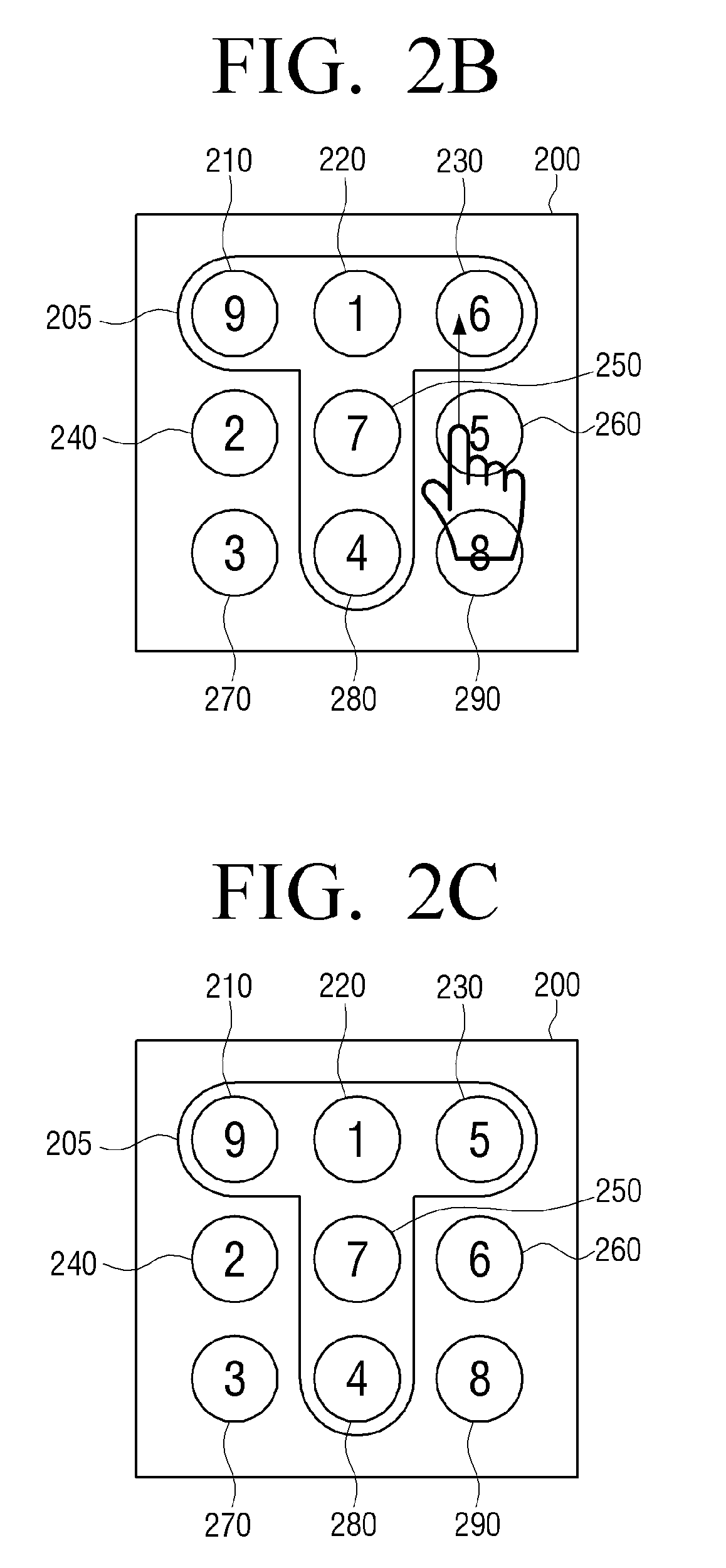
Method of authenticating password and portable device thereof
InactiveUS20130139248A1Increased complexityProtection of personal informationDigital data processing detailsUnauthorized memory use protectionPasswordComputer science
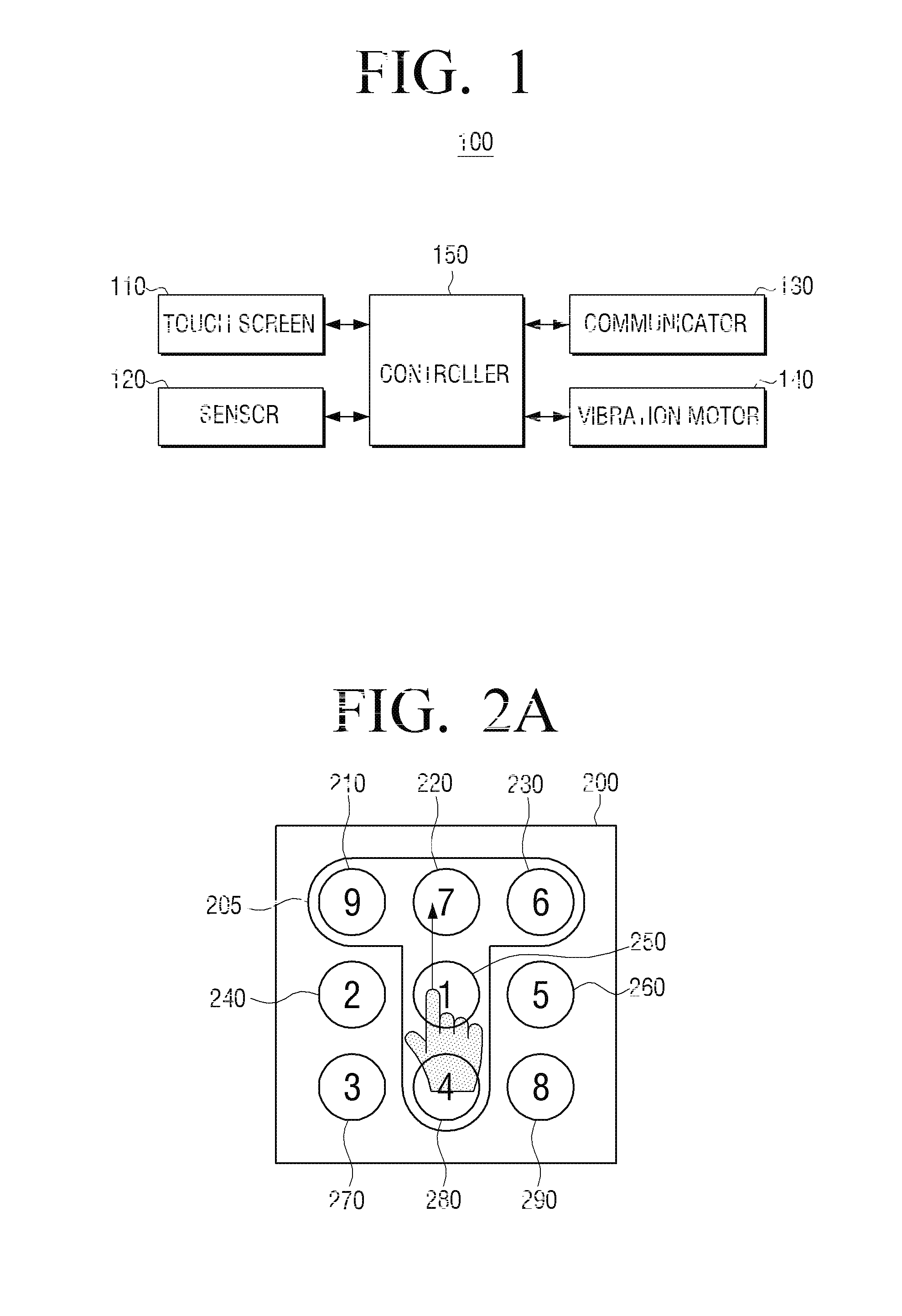
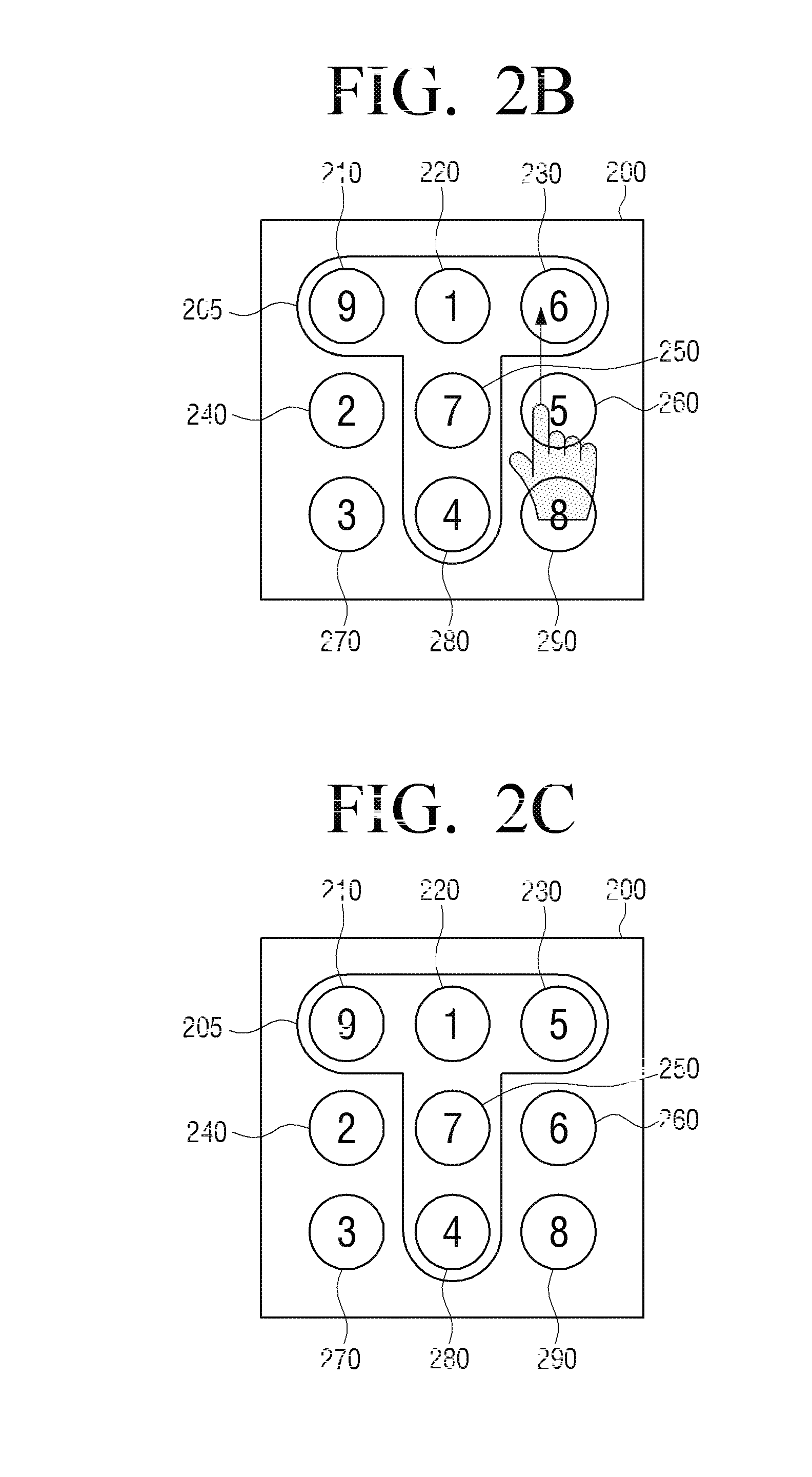
A method of authenticating a password and a portable device thereof are provided. The method includes: displaying an input keyboard on which a plurality of objects are arranged; changing an object arranged on the input keyboard according to a manipulation of a user; and if an object pattern arranged in a designated position of the input keyboard corresponds to a preset password pattern, authenticating the user. Therefore, it is difficult to use artifacts on the display screen to trace a password after entry, and thus security is improved. As a result, a protection of personal information of a user is strengthened.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and device for detecting access right of wireless network and router
InactiveCN103619018AImprove securityPrevent leakageSecurity arrangementSpecial data processing applicationsWireless mesh networkWireless network coding
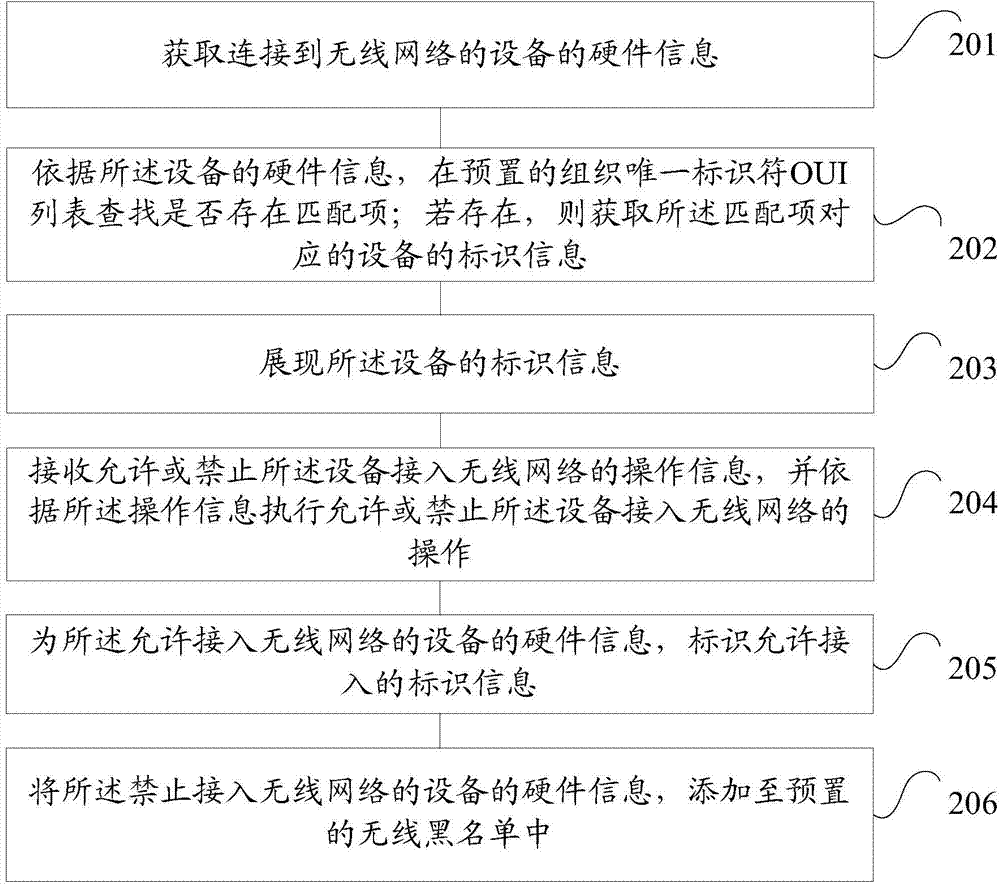
The invention discloses a method and device for detecting the access right of a wireless network and a router. The method for detecting the access right of the wireless network comprises the steps that hardware information of a device having access to the wireless network is obtained; whether a matching item exists in a preset OUI list is judged through searching according to the hardware information of the device; the identification information, corresponding to the matching item, of the device is obtained if the matching item exists in the preset OUI list; the identification information of the device is presented; operation information allowing the device to have access to the wireless network or preventing the device from having access to the wireless network is received, and the device is allowed to have access to the wireless network or is prevented from having access to the network according to the operation information. The method and device for detecting the access right of the wireless network and the router are used for preventing data from being leaked, protecting personal information of users and improving the safety performance of the wireless network.
Owner:BEIJING QIHOO TECH CO LTD +1
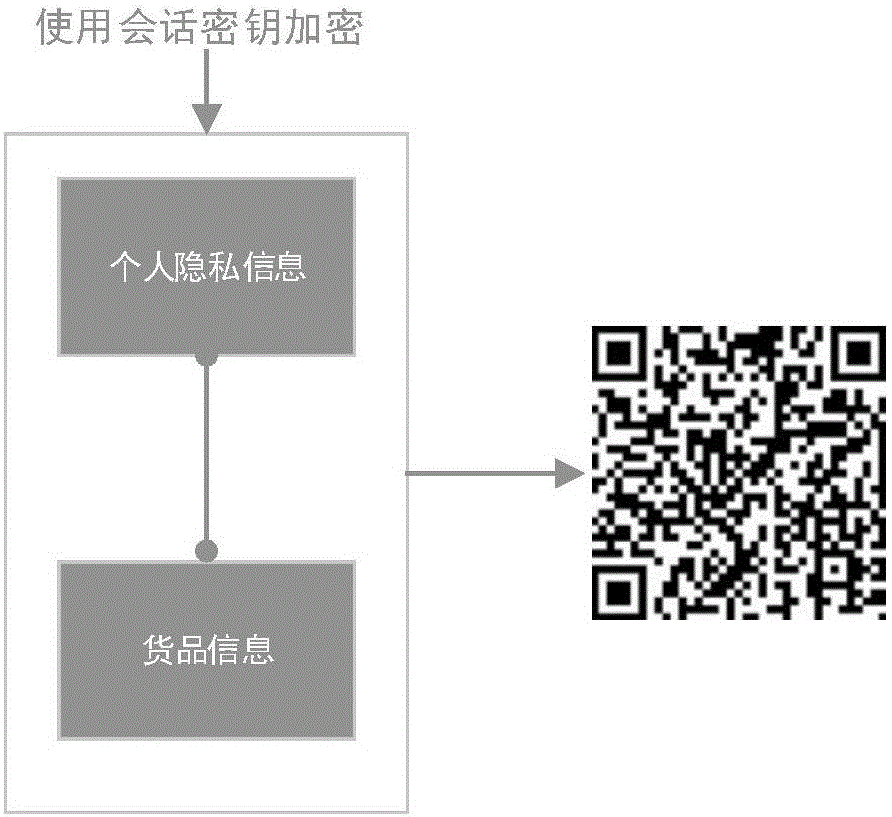
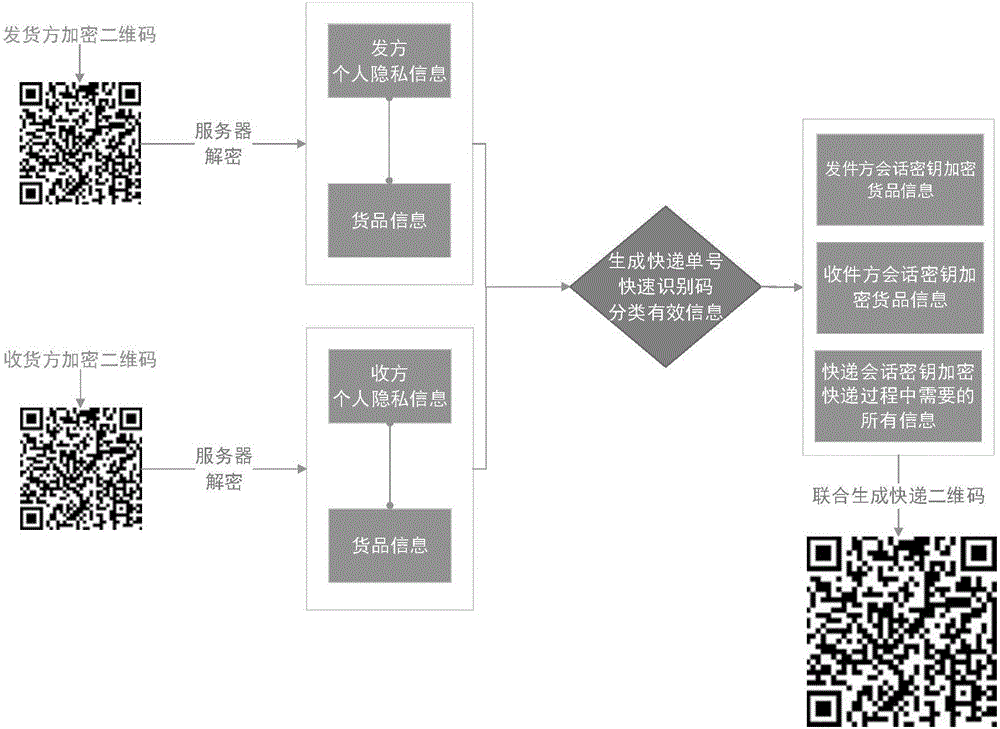
Method for encrypting privacy information on express waybills
InactiveCN105719120APrevent theftReduce exposureKey distribution for secure communicationLogisticsPlaintextInternet privacy
The invention discloses a method for encrypting privacy information on express waybills and belongs to the technical field of encryption for the privacy information on the express waybills. By adoption of the method, the problem that in the express receiving and sending process, personal information is printed on parcels in a plaintext manner, so that the disturbance due to leakage of personal information is caused, and the personal and property safety is worried is solved. The method comprises the following steps of (1) acquiring personal privacy information of senders, personal privacy information of receivers and goods information; and (2) respectively encrypting the acquired personal privacy information of the senders, personal privacy information of the receivers and goods information by role-identity public keys and session keys consulted by the role public keys, and finally generating two-dimensional codes of encrypted information of the express waybills. The method disclosed by the invention is used for protecting the privacy information on the express waybills in the express receiving and sending process.
Owner:成都木马人网络科技有限公司
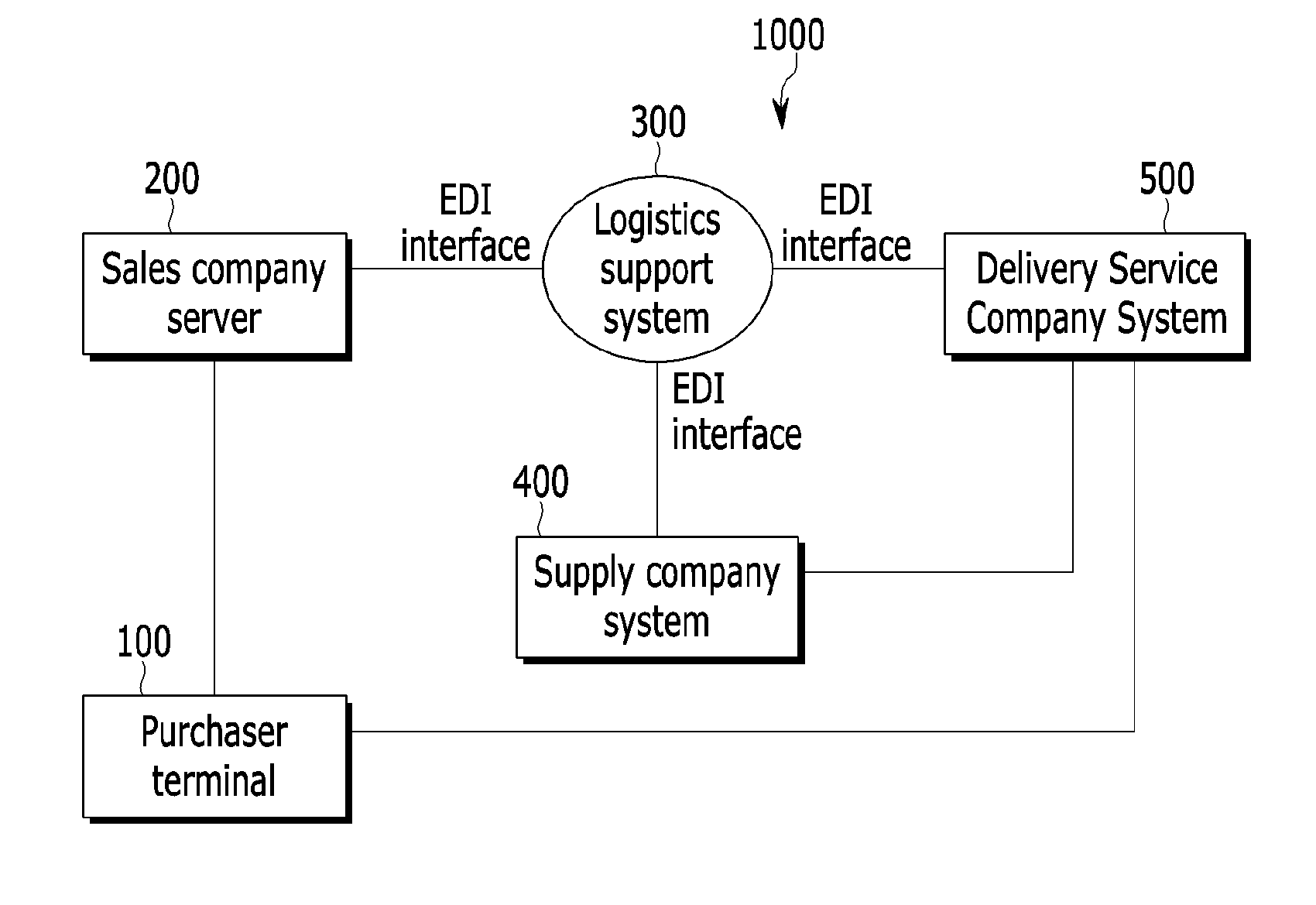
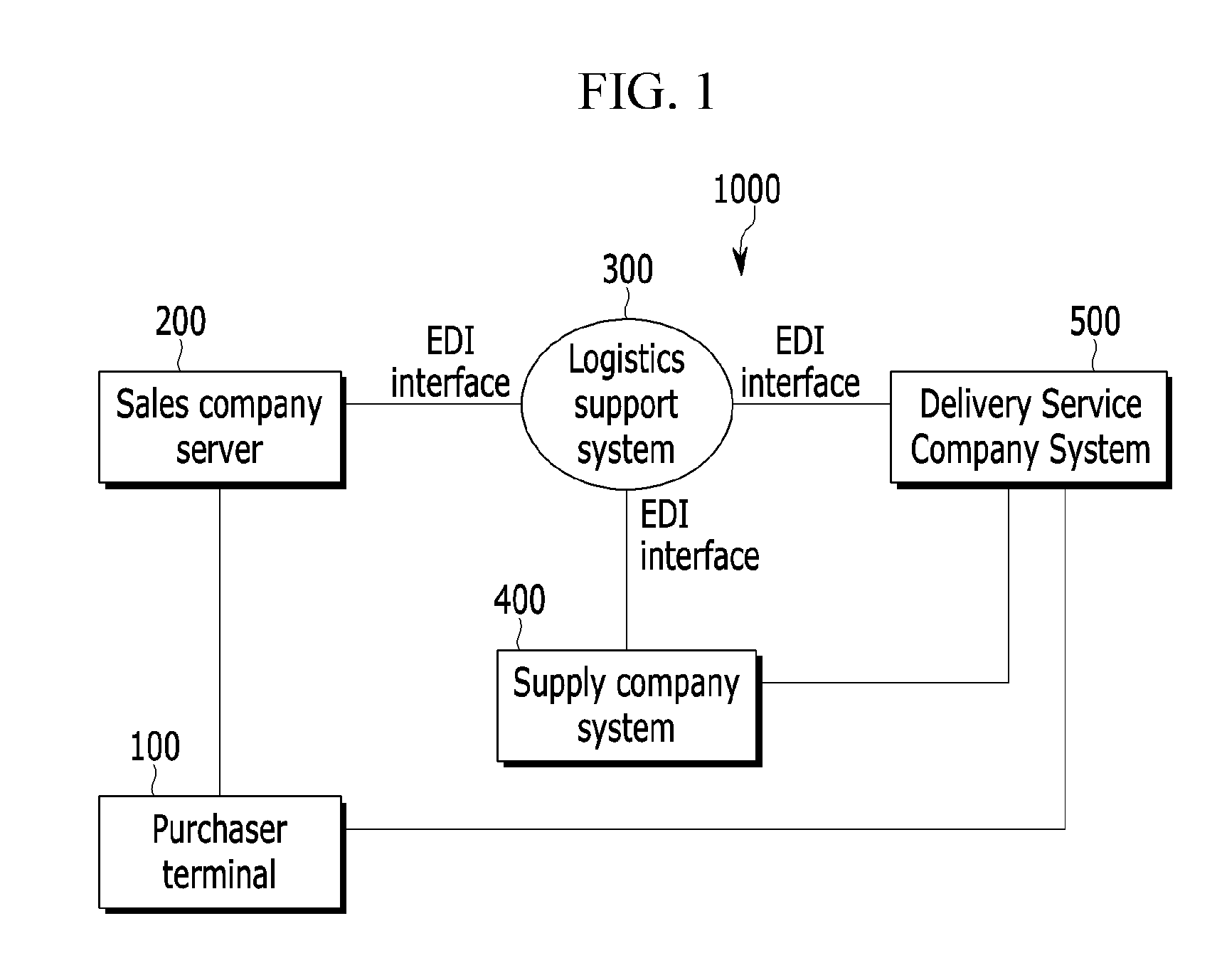
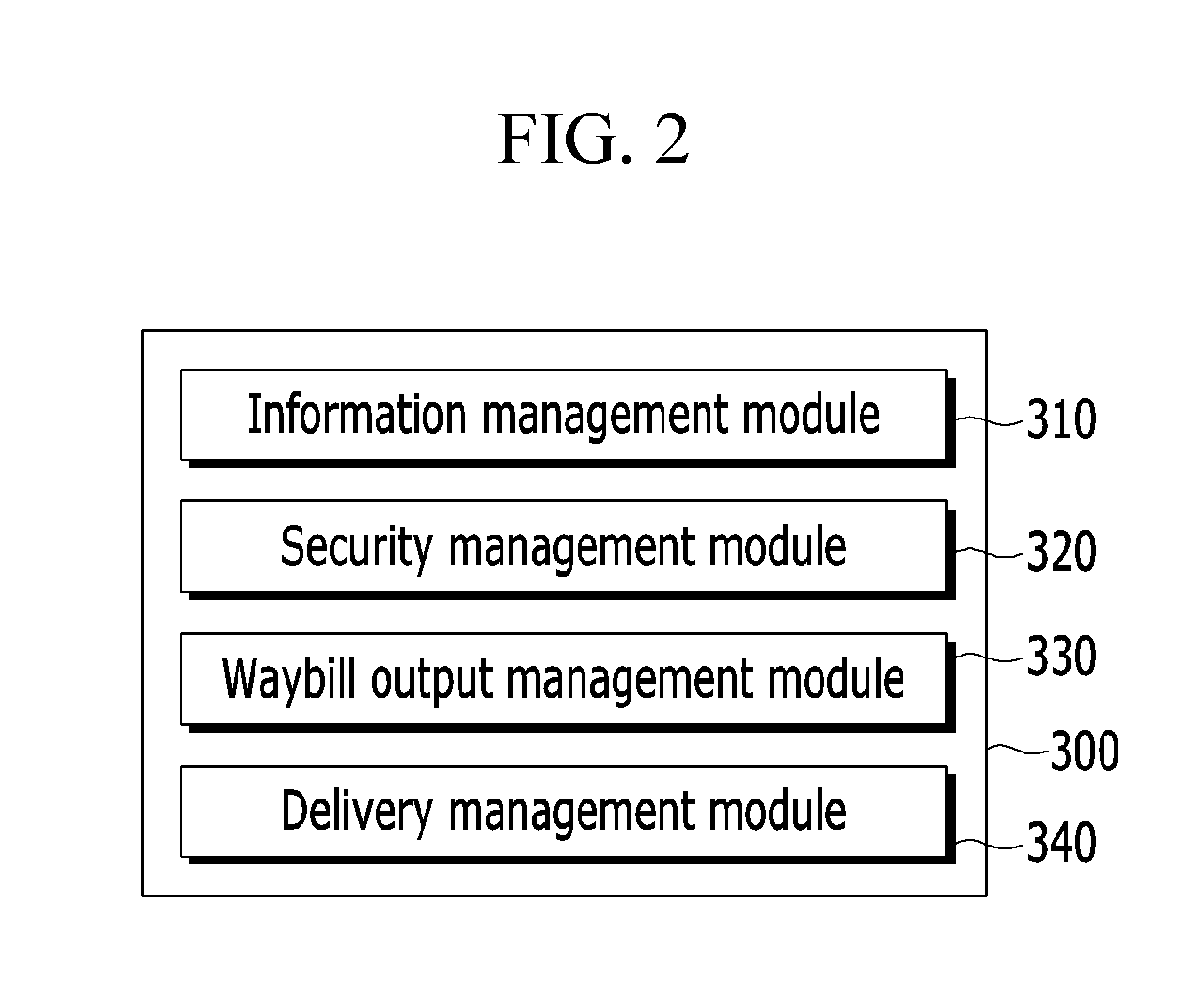
Logistics support method and system for online shopping
InactiveUS20130138536A1Reduce personal informationEasy to operateBilling/invoicingBuying/selling/leasing transactionsSupporting systemProduct order
A logistics support method of a logistics support system for supporting online shopping includes: receiving a usable range for a waybill number from at least one delivery service company system; receiving product order information, except for personal information, from a sales company server selling a product; receiving a request for waybill output information containing the product order information from a supply company system supplying the product or the delivery service company system delivering the product; receiving and encrypting the personal information corresponding to the product order information from the sales company server; generating the waybill output information containing the encrypted personal information, the product order information, and a waybill number belong to the usable waybill number range; and transmitting the waybill output information to the supply company system or the delivery service company system.
Owner:I CIUS
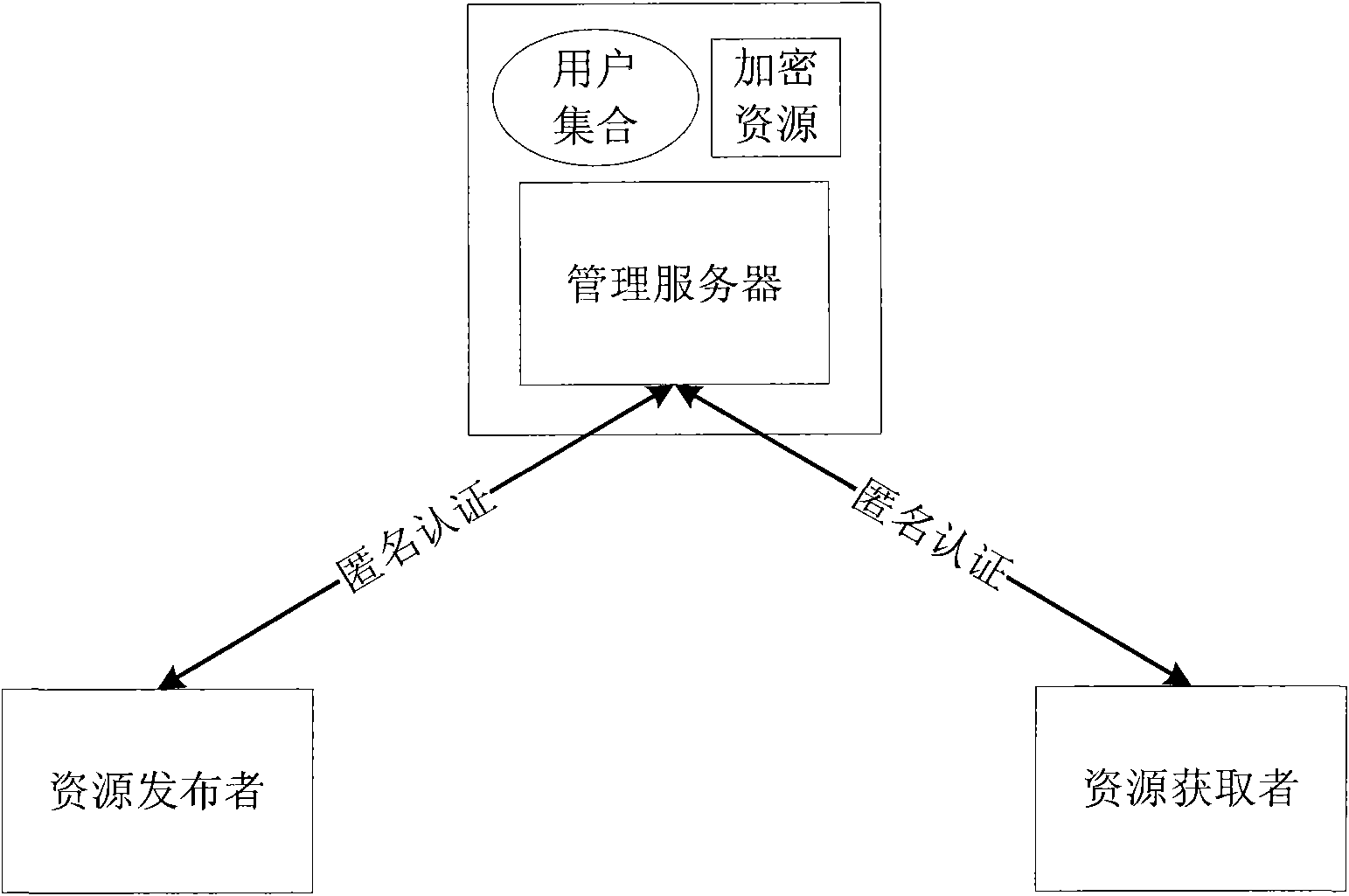
Method and system for sharing anonymous resource
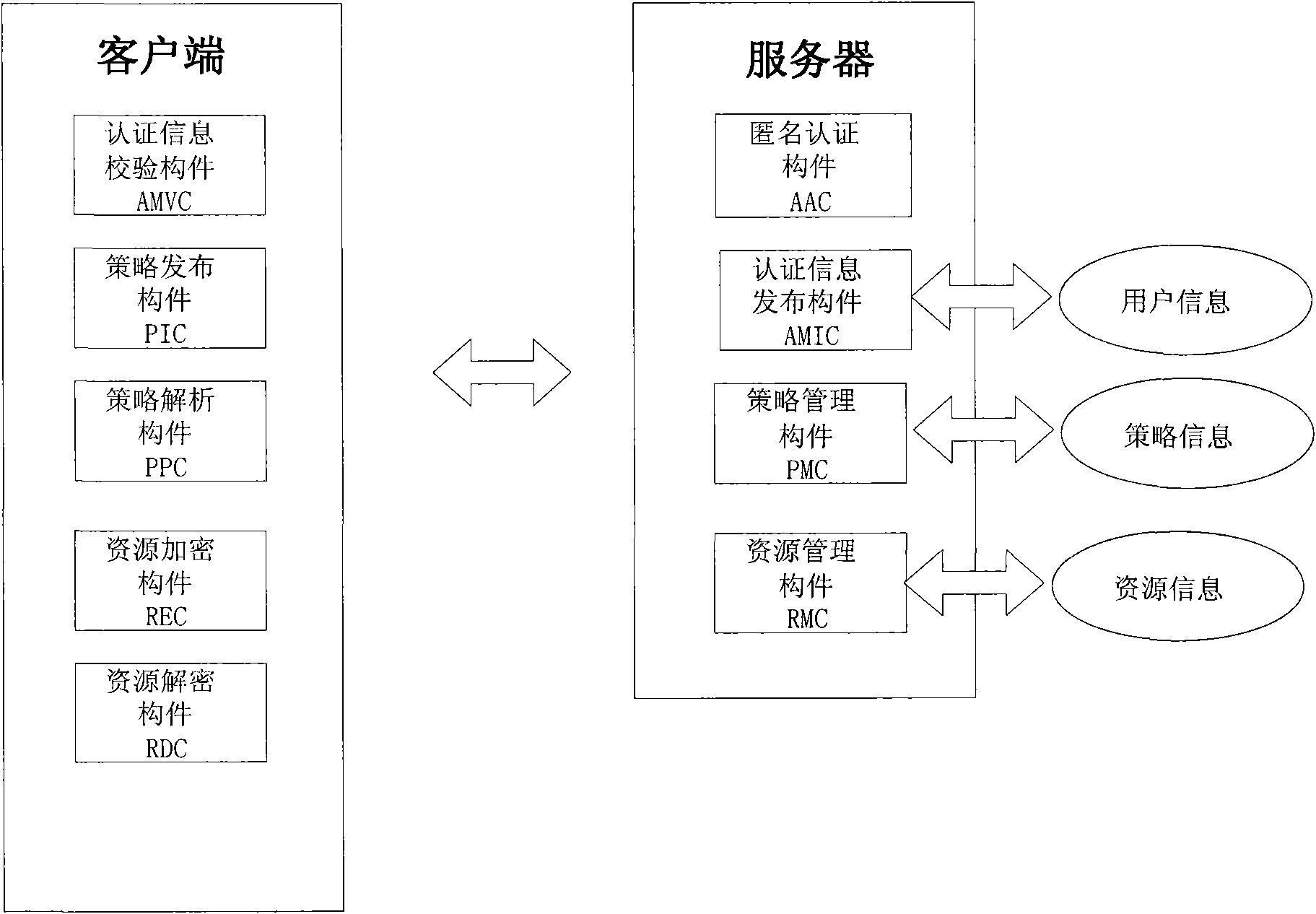
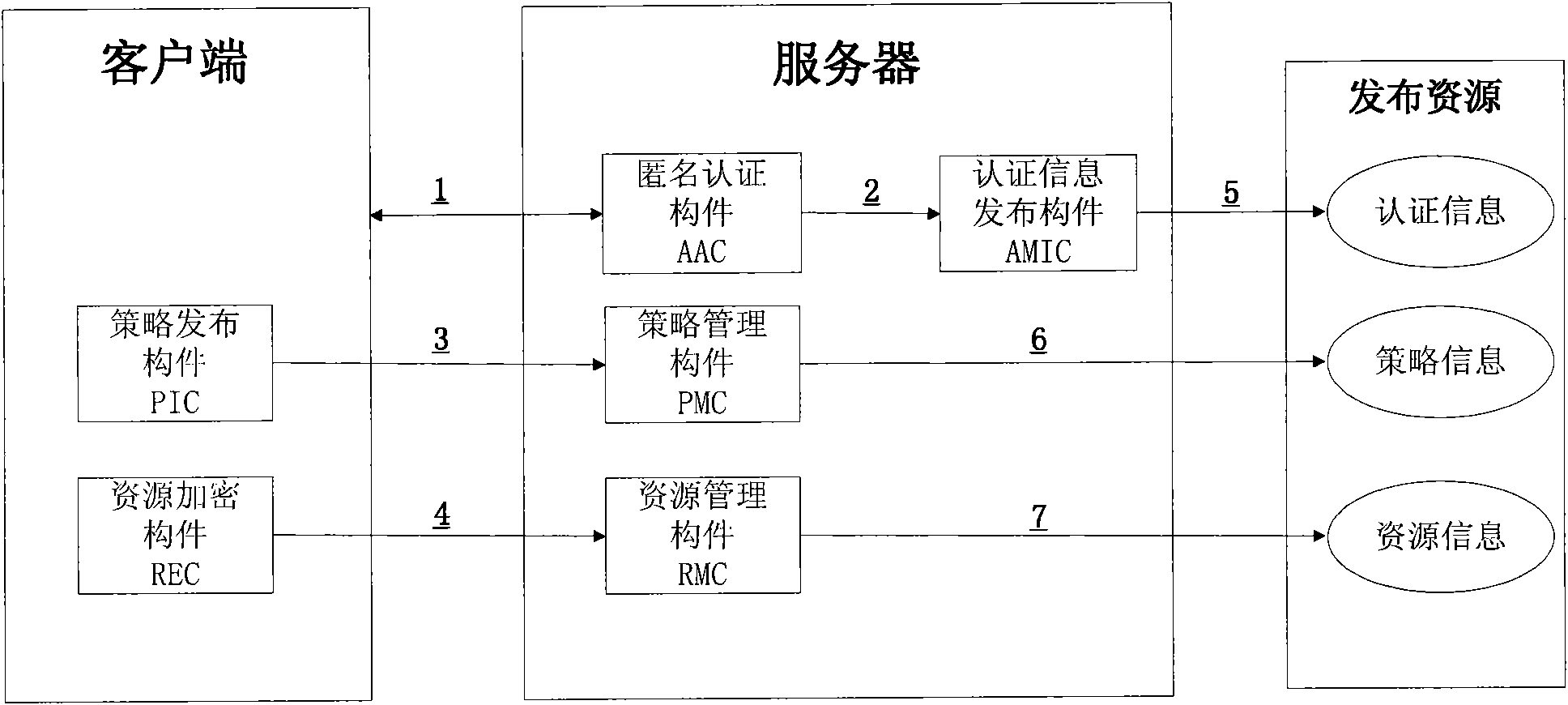
InactiveCN101834853AProtect personal privacyProtection of personal informationTransmissionResource managementResource Provider
The invention discloses a method and a system for sharing an anonymous resource, which belong to the technical field of computer information. The method for sharing the resource comprises the following steps that: a resource provider initiates a resource publishing request to a resource management server; the resource management server performs an anonymous authentication on the request; the resource provider generates a resource acquisition strategy, uses the resource acquisition strategy as a cipher key to encrypt the resource, and sends the acquisition strategy and the encrypted resource to the resource management server; the resource management server stores a binary group and releases resource description information; a resource acquirer retrieves the resource description information and initiates a resource acquisition request; the resource management server performs the anonymous authentication on the resource acquirer; and the resource acquirer acquires and decrypts the resource after acquiring a strategy verification. The invention also discloses a system sharing the resource, which corresponds to the method. The method and the system can be used for computer information technical application such as network resource sharing and the like.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Group chat communication system and method thereof
InactiveCN104639556AProtection of personal informationProtect sensitive informationSpecial service provision for substationInformation transmissionCommunications system
The invention discloses a group chat communication system and a method thereof. The system comprises a first user module, a user name / nick name identity switch processing module, a nick name identity distribution module and second user modules, wherein the first user module is used for managing information on users, including group managers and other group members, who have been participated in a group chat through a client; the user name / nick name identity switch processing module is used for responding to a user name / nick name switching request initiated through the client and re-calculating identities of the users, participating in current group chat communication, by a preset algorithm in a server; the nick name identity distribution module is used for distributing identity information, which is calculated by using the user name / nick name identity switch processing module, to corresponding users existing in a current group chat session, so as to enable each user to correspondingly obtain a relatively unique identity, namely a nick name ID (Identity), in the current group chat; the second user modules are used for supporting the other group members to be in group chat communication with the first user module through the server. By adopting the system and the method, the users can protect personal information on the group members during the group chat and information generated during the group chat, and the security during information transmission is ensured.
Owner:BEIJING JINGYUE INTERACTIVE TECH
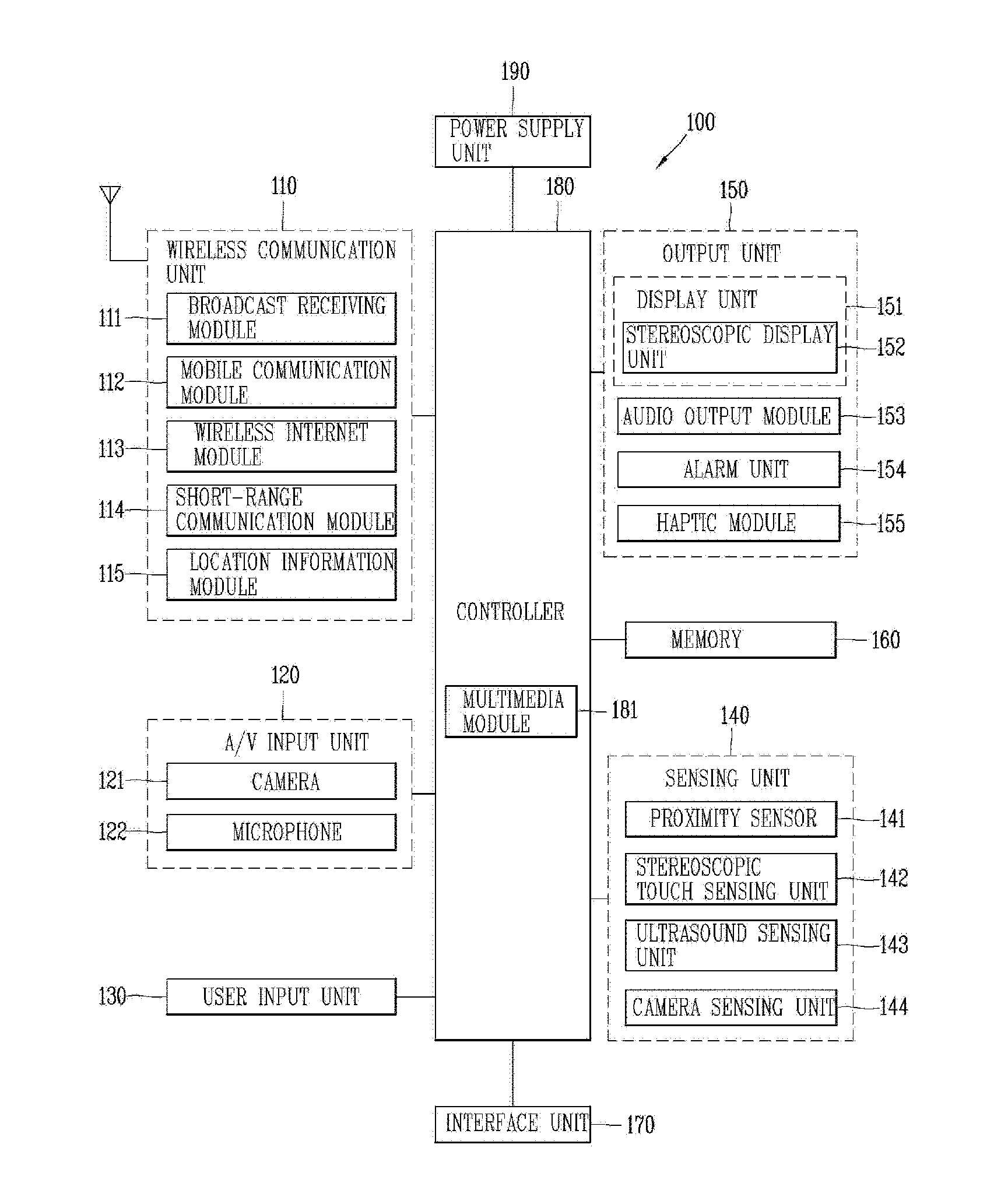
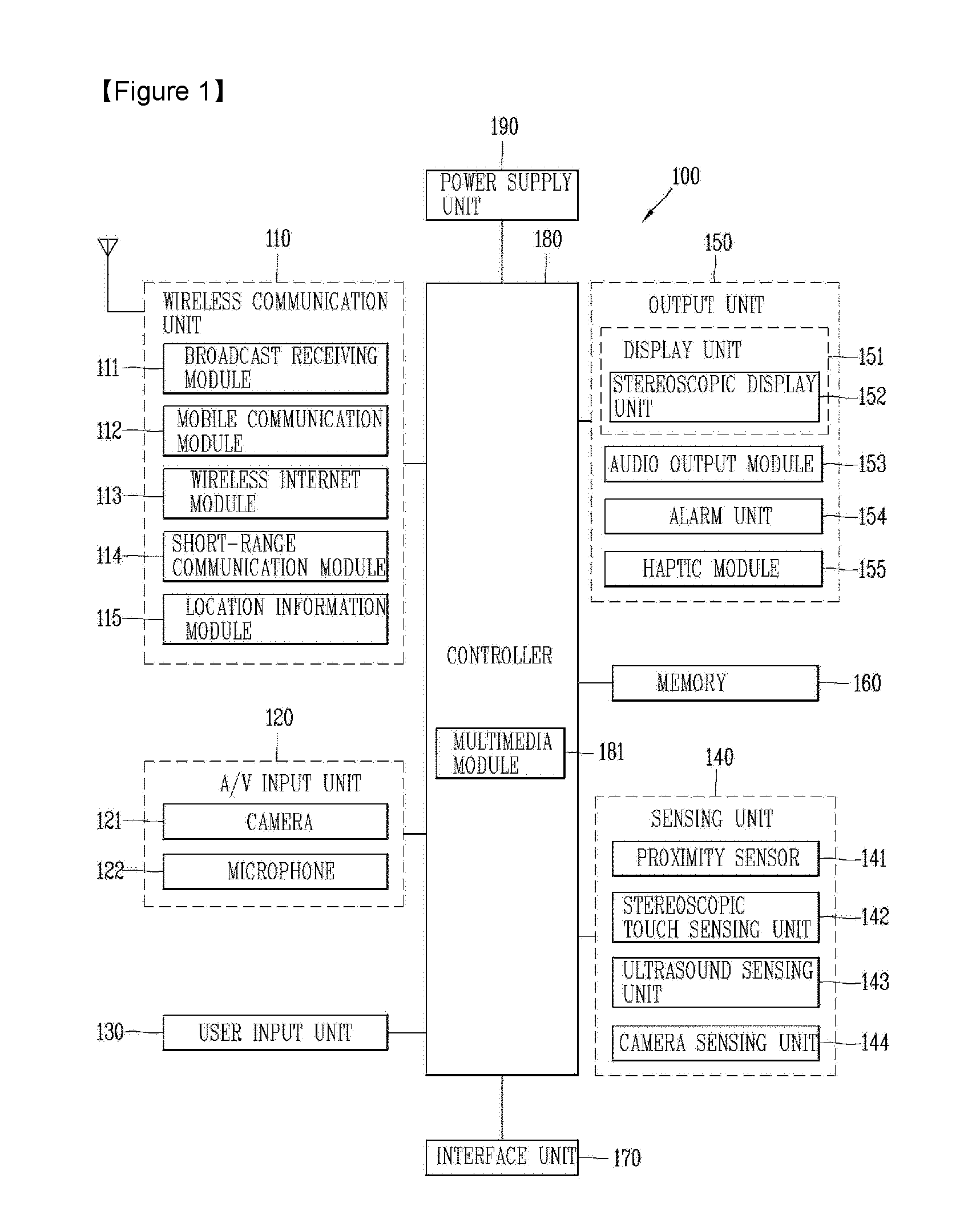
Mobile terminal and control method thereof
InactiveUS20160180322A1Improve convenienceProtection of personal informationDigital data information retrievalFinanceUser inputFinancial transaction
The present invention relates to a mobile terminal capable of transmitting and receiving position information, and a control method thereof. The mobile terminal comprises: a user input unit configured to receive, from a user, at least one of information to be considered to search for a financial transaction terminal adjacent to the user, and authentication information; a controller configured to search for one or more financial transaction terminals adjacent to the user, based on the information to be considered to search for a financial transaction terminal, and configured to detect usage situation information on said one or more financial transaction terminals; and a display unit configured to output the usage situation information, wherein if the user moves to arrive at one of said one or more financial transaction terminals, the controller transmits the input authentication information to said one financial transaction terminal.
Owner:LG ELECTRONICS INC
Screen recording method and device, and terminal
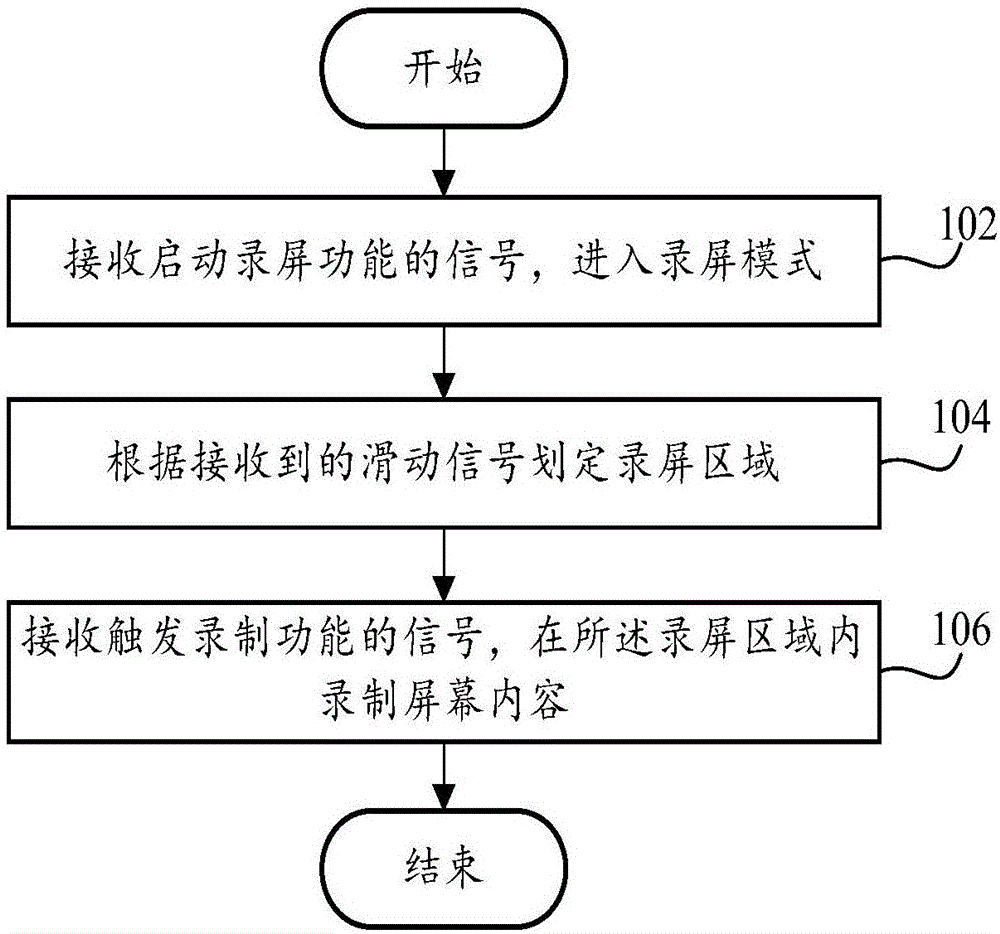
PendingCN106598380AHighlight the subject of the recordingProtection of personal informationInput/output processes for data processingUser privacyComputer hardware
The invention relates to a screen recording method, a screen recording device, and a terminal, relates to the technical field of video recording, and provides the screen recording method, the screen recording device, and the terminal. The screen recording method comprises the steps of receiving a signal of starting a screen recording function, and entering a screen recording mode; defining a screen recording area according to a received sliding signal; and receiving a signal of triggering a recording function, and recording screen content in the screen recording area. According to the technical scheme of the method and the device provided by the invention, partial screen recording can be achieved, and an unnecessary area is prevented from being captured and recorded into a video during screen recording, so that the effect of protecting user privacy and highlighting a recording subject is achieved, gesture control on a whole recording process can also be achieved, an operation interface and an operation method under the screen recording mode are simplified, and user experience on the screen recording function is enhanced.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
System and method for requesting and issuing an authorization document
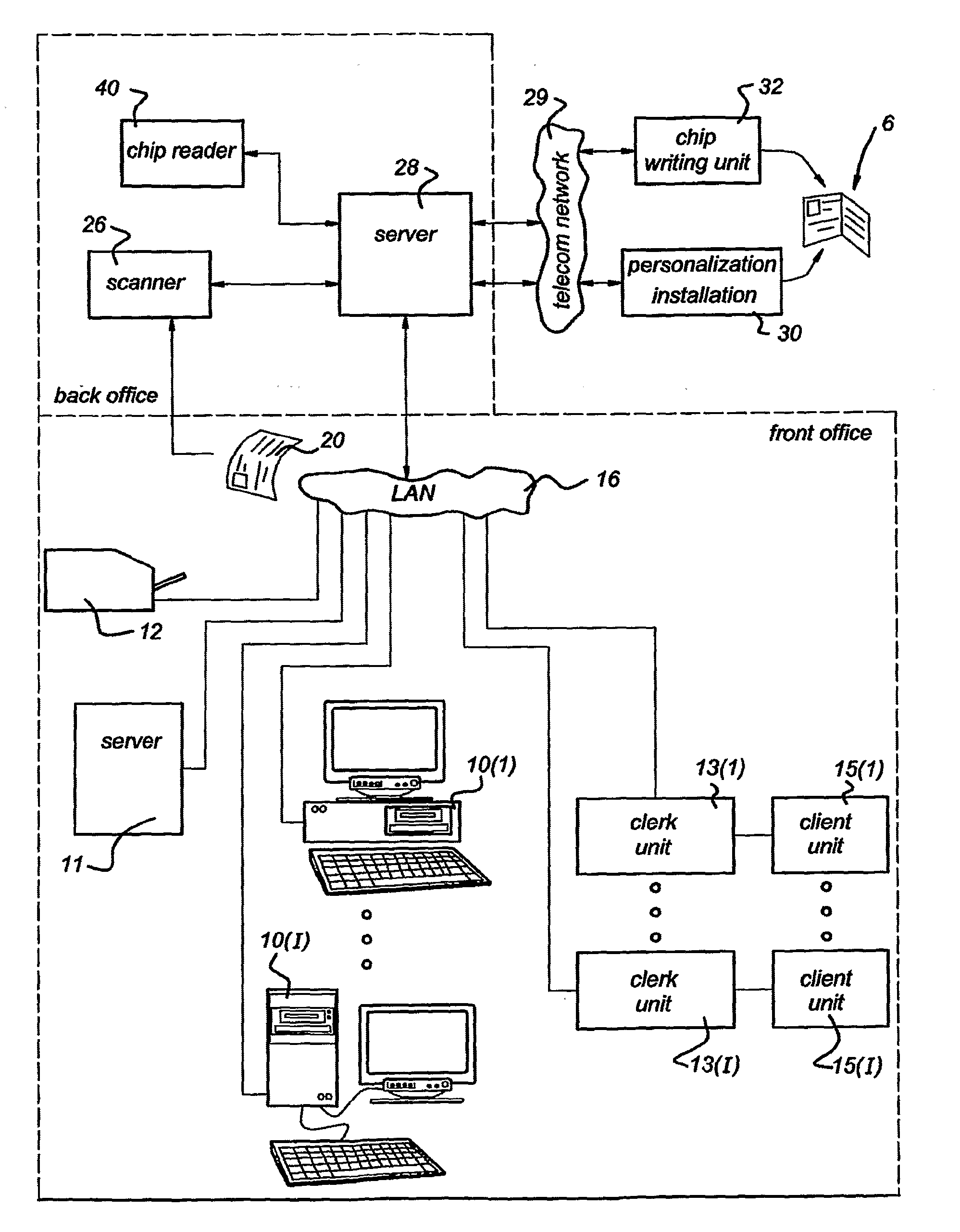
InactiveUS20100223460A1Protection of personal informationImprove protectionDigital data authenticationOffice automationPaper documentDocument preparation
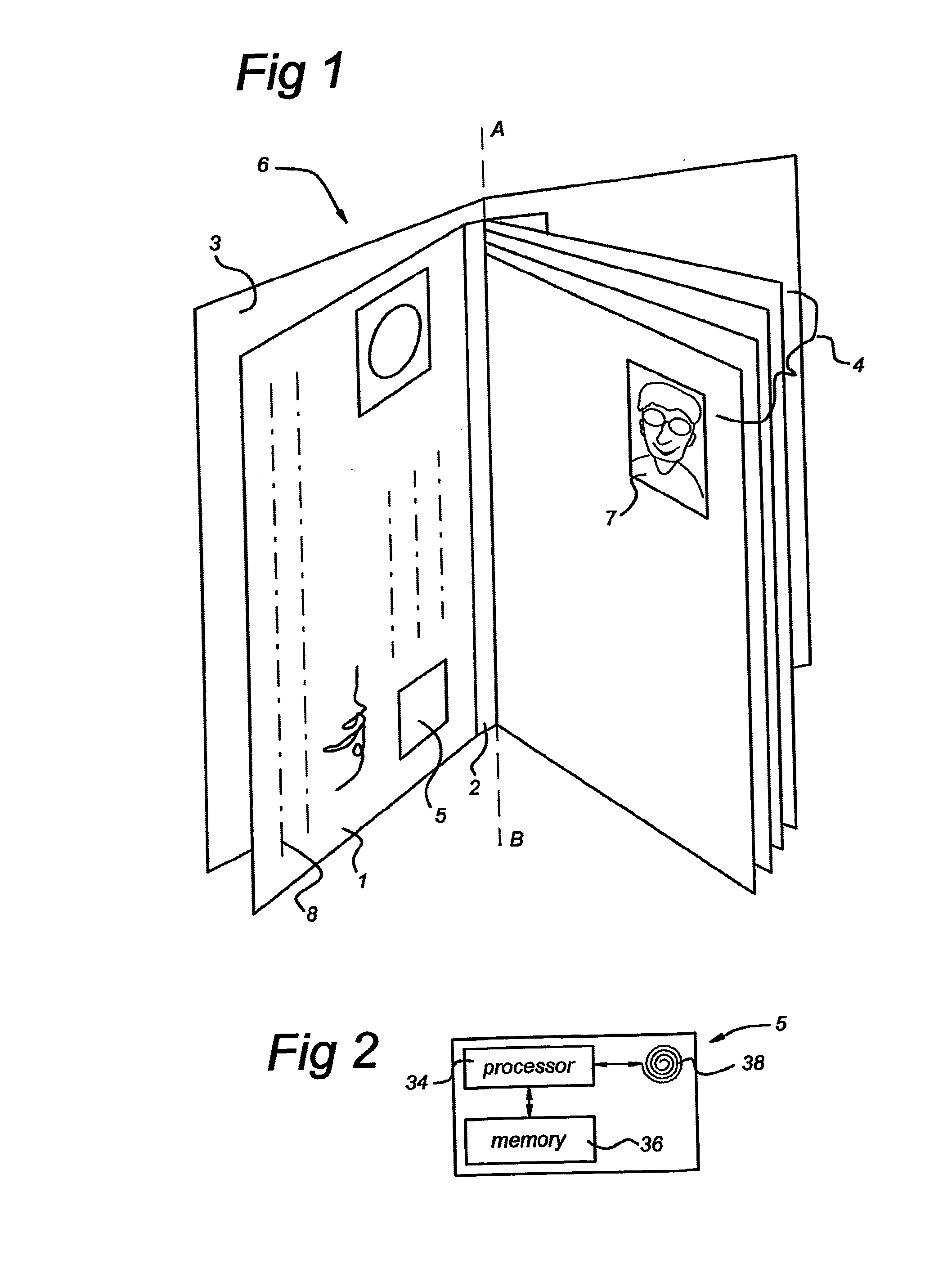
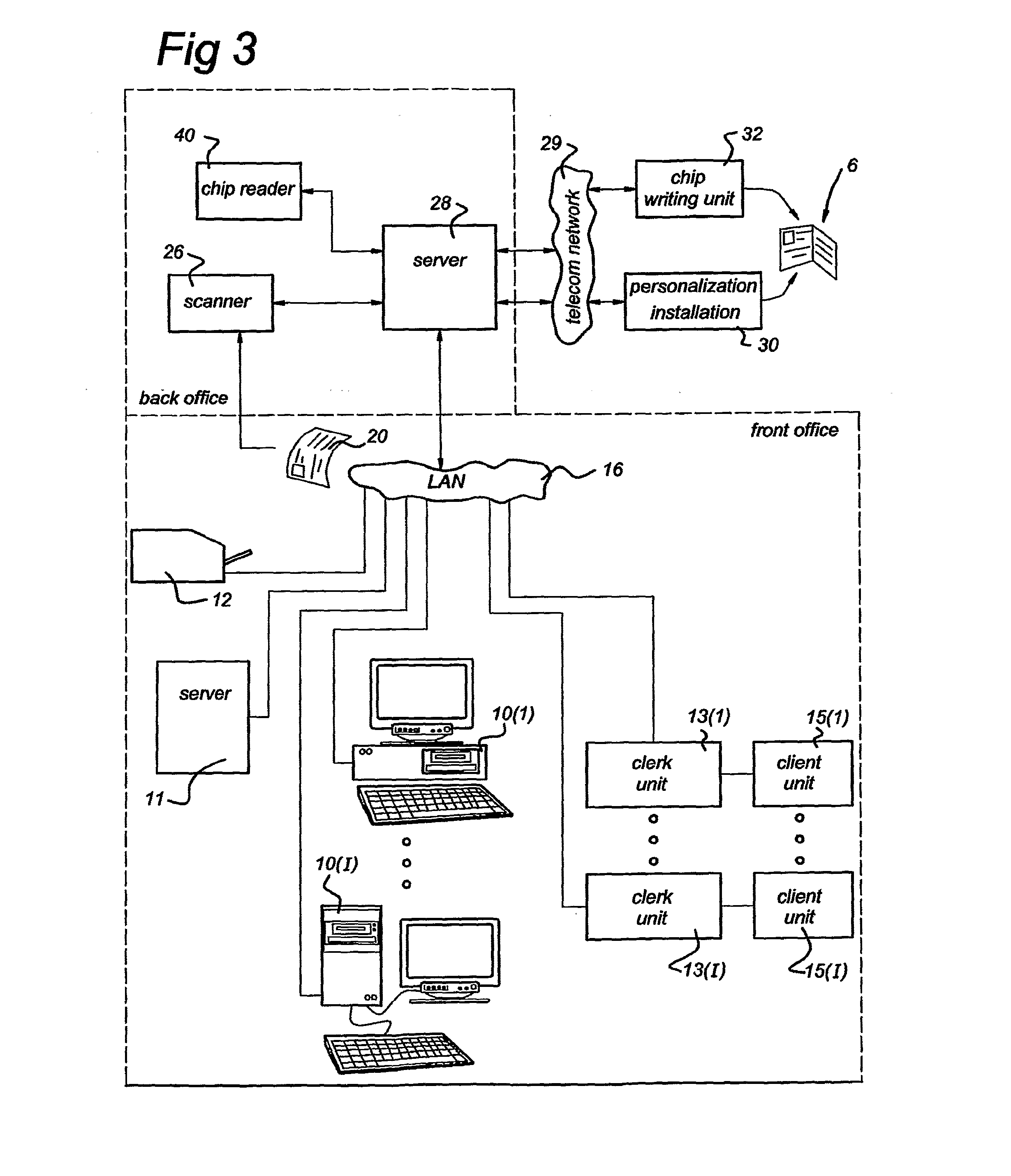
A device and method for supporting the issuing of an authorization document (6) to an applicant; the said device comprising: a computer (10(i)) comprising a first processor and a first memory containing stored first data and instructions to allow the first processor to execute a first defined program, a clerk unit (13(i)) comprising a second processor (17) and a second memory containing stored second data and instructions to allow the second processor (17) to execute a second defined program, as well as a secure application module (41), and a client unit (15(i)) comprising at least a biometric characteristic reader unit (27; 31) for reading a biometric characteristic of the applicant, wherein the client unit (15(i)) and the second processor (17) can communicate with each other, and the first processor and the second processor (17) can communicate with each other in the form of a secure session that makes use of a cryptographic key stored in the secure application module (41).
Owner:SDU IDENTIFICATION
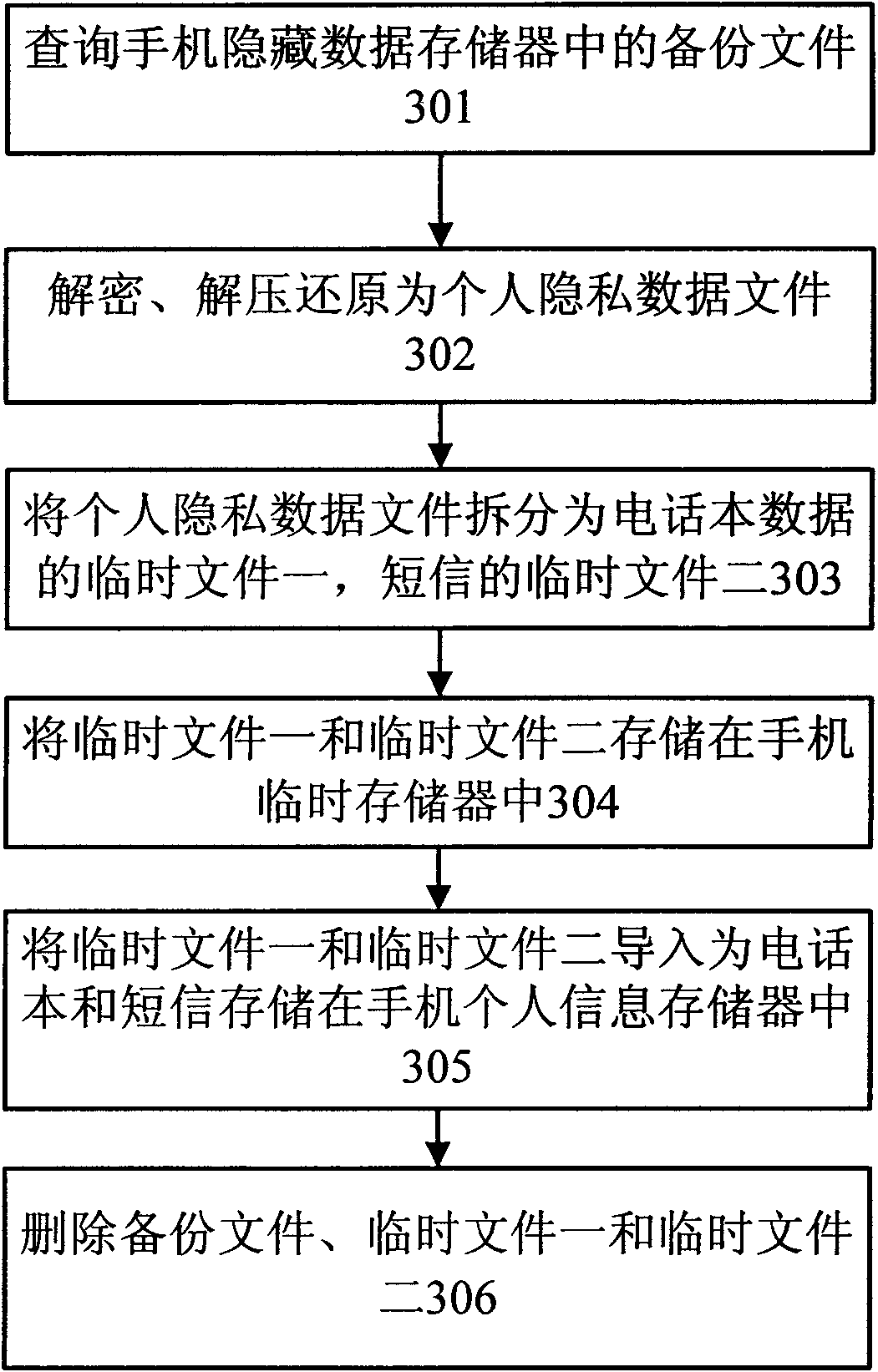
Method for hiding or recovering personal information when changing SIM card and system thereof
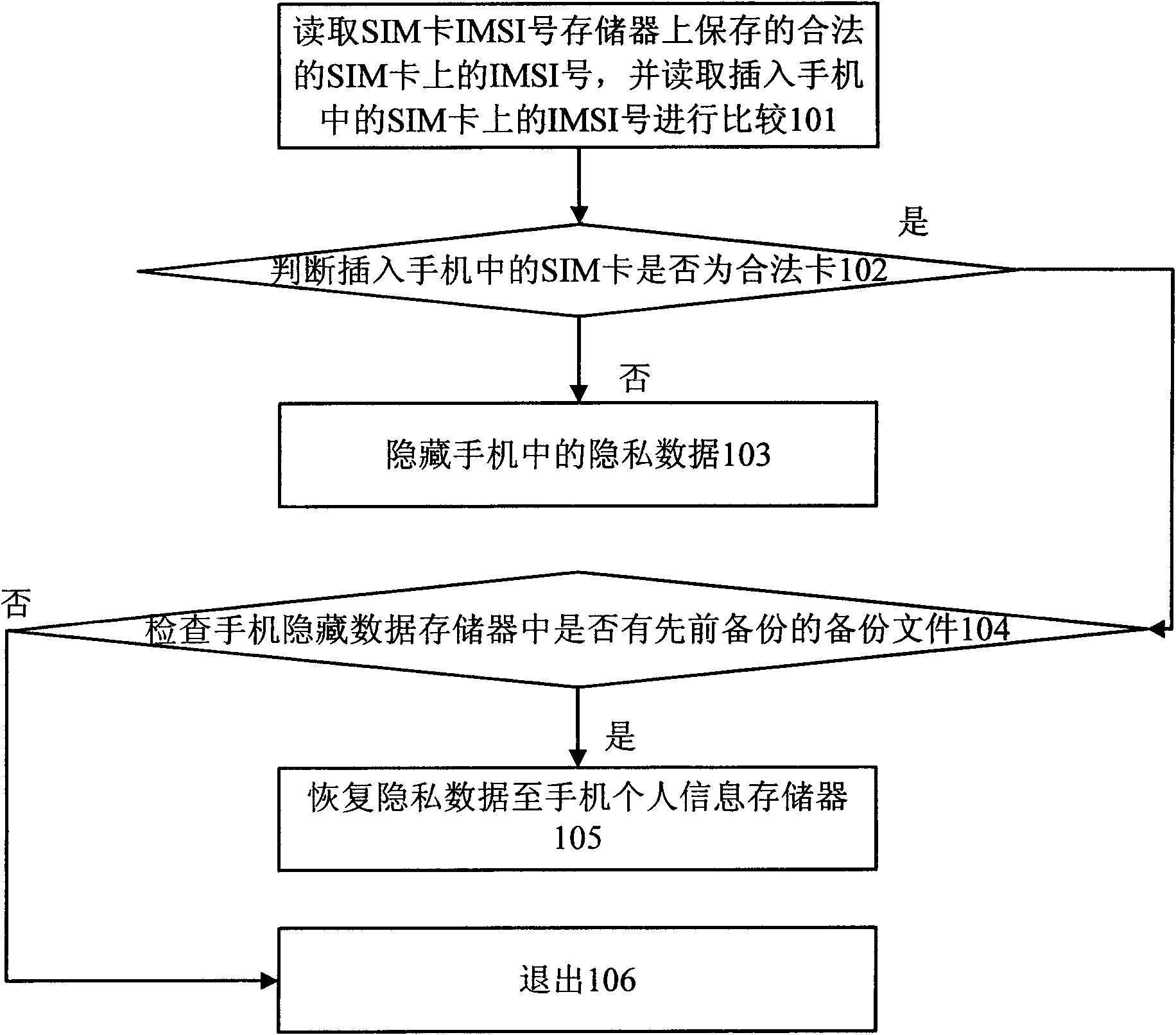
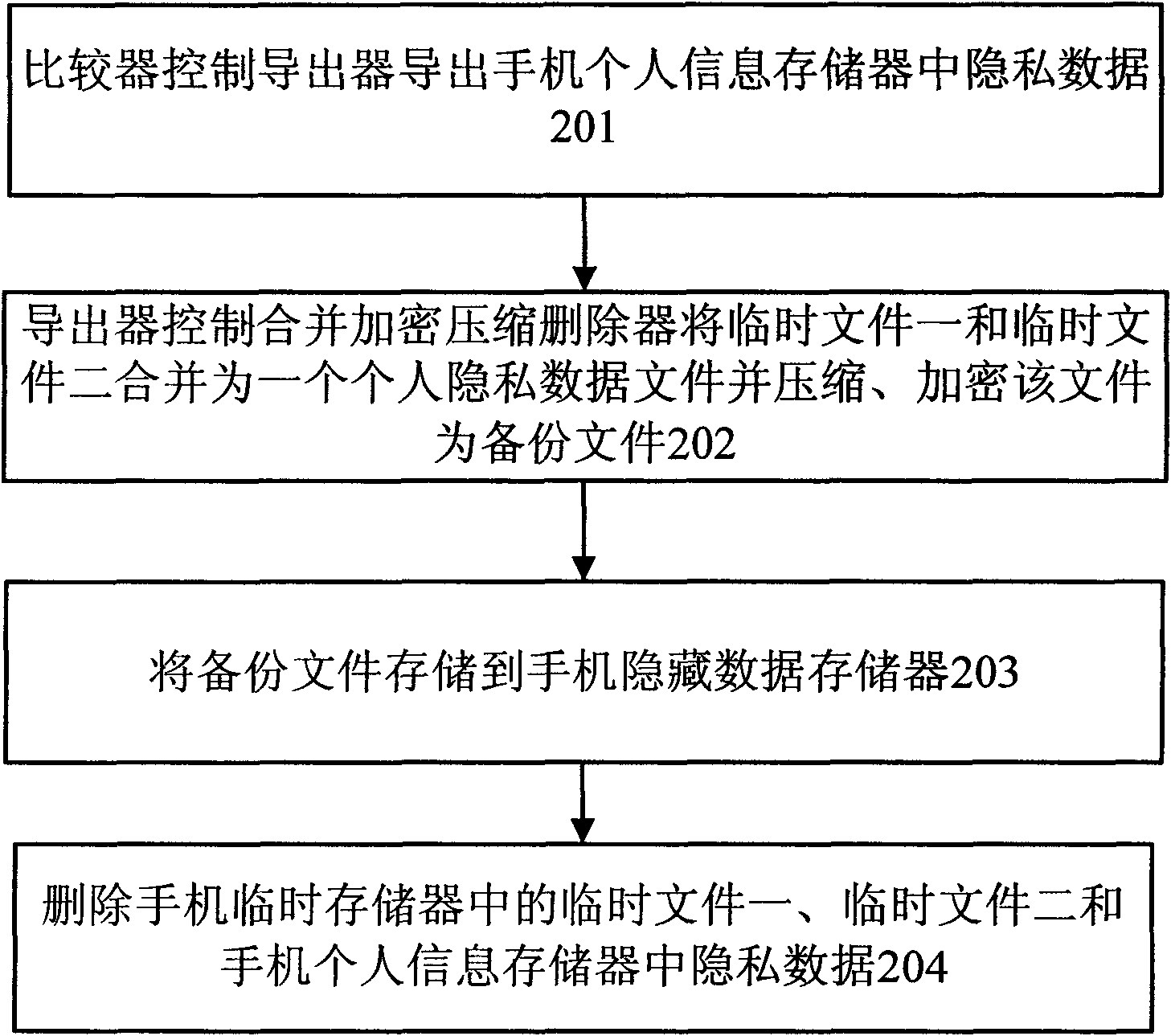
The invention discloses a method for hiding or recovering personal information when changing a SIM card, comprising the steps: reading an IMSI number on the SIM card; comparing the IMSI number with alegal number memorized on a legal IMSI number memory; judging the legality of the SIM card; when the SIM card is illegal, deriving private data from a mobile phone personal information memory and compressing the private data to be a standby file, memorizing the standby file into a mobile phone hidden data memory, and cancelling the private data memorized in the mobile phone personal information memory; and when the SID is legal, decompressing the standby file memorized in the mobile phone hidden data memory into the private data to be memorized into the mobile phone personal information memory, and cancelling the standby file memorized in the mobile phone hidden data memory. Therefore, the invention provides the method and a system for hiding or recovering the personal information when changing the SIM card so as to effectively protect the mobile phone personal information.
Owner:联信摩贝软件(北京)有限公司
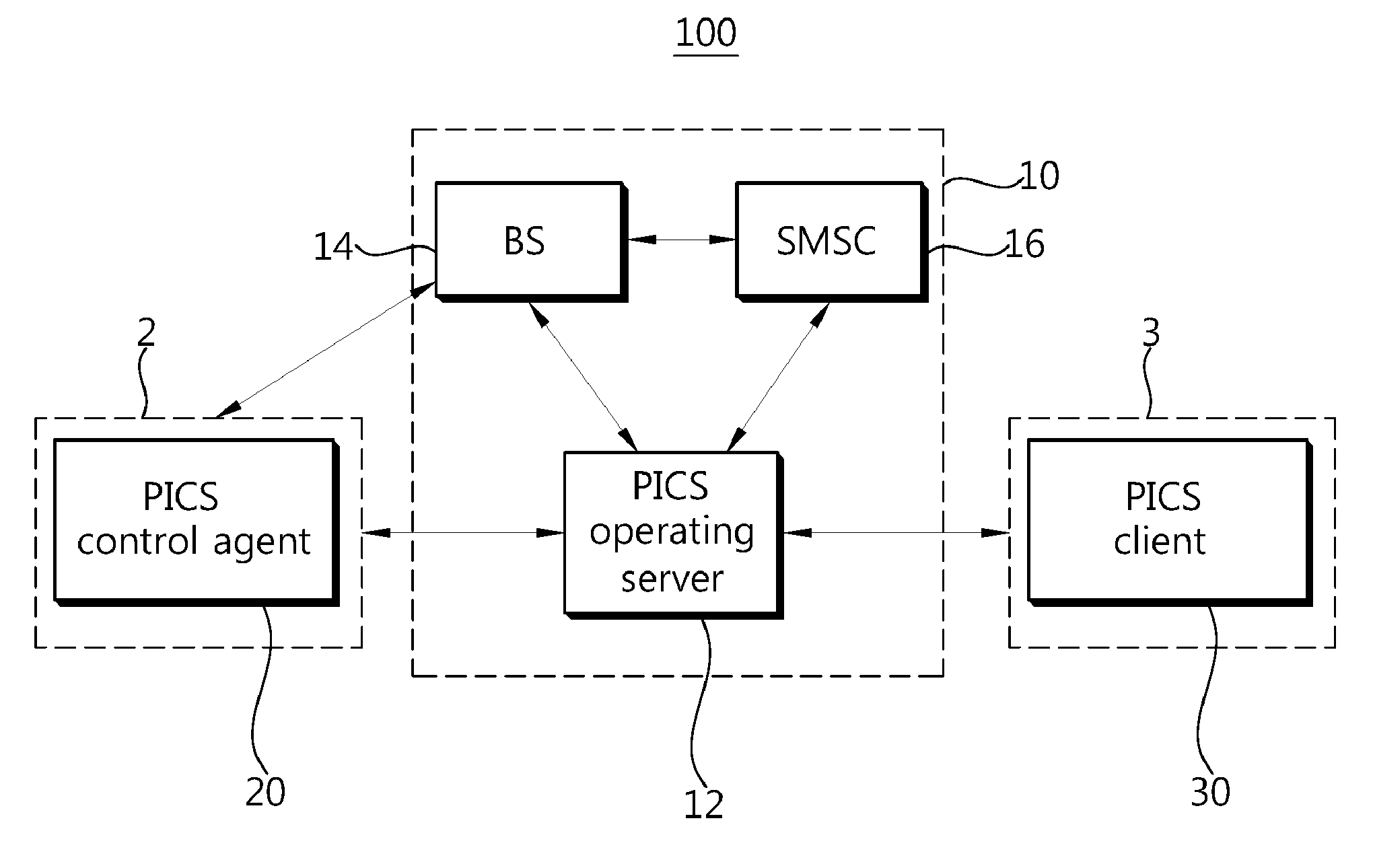
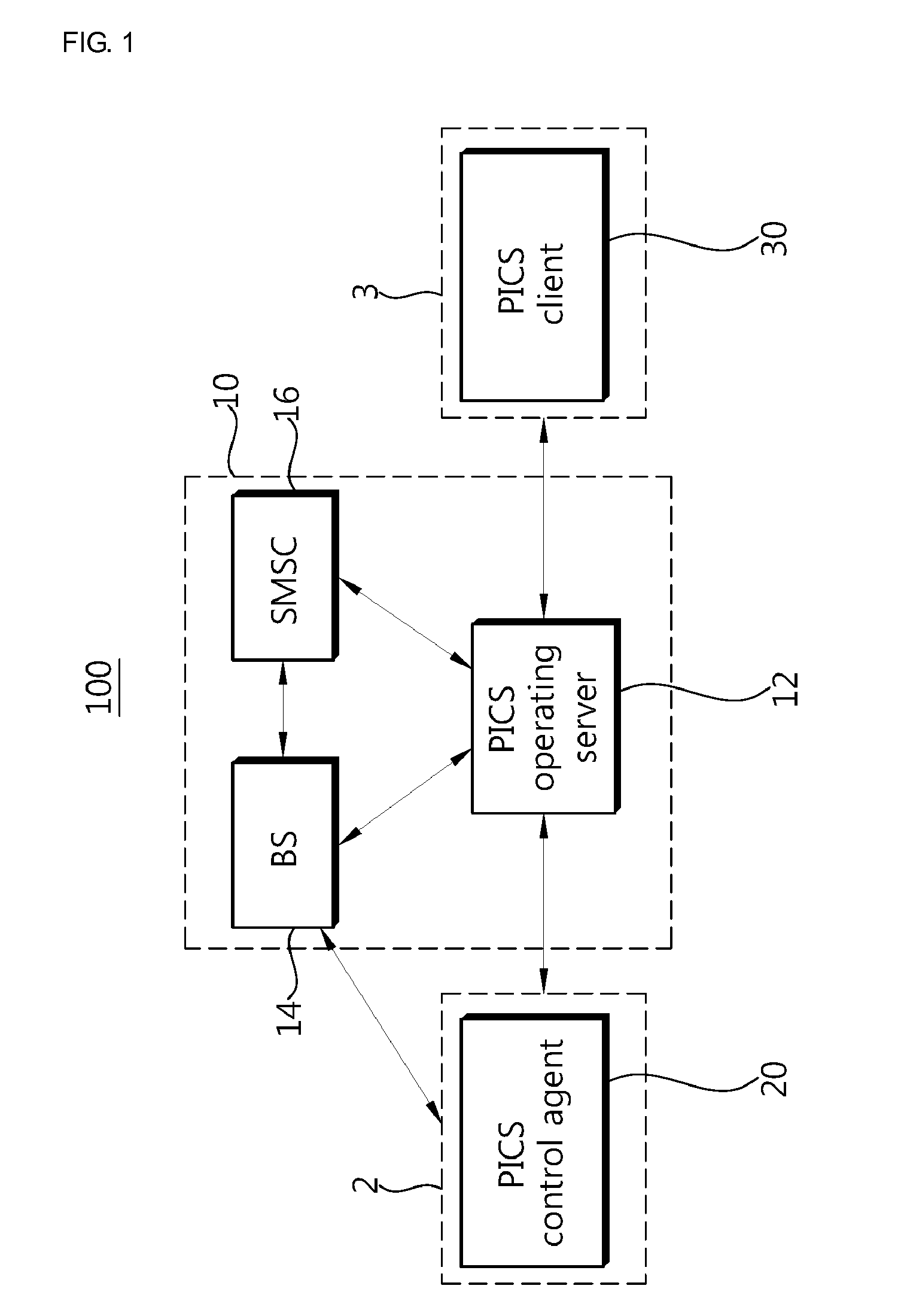
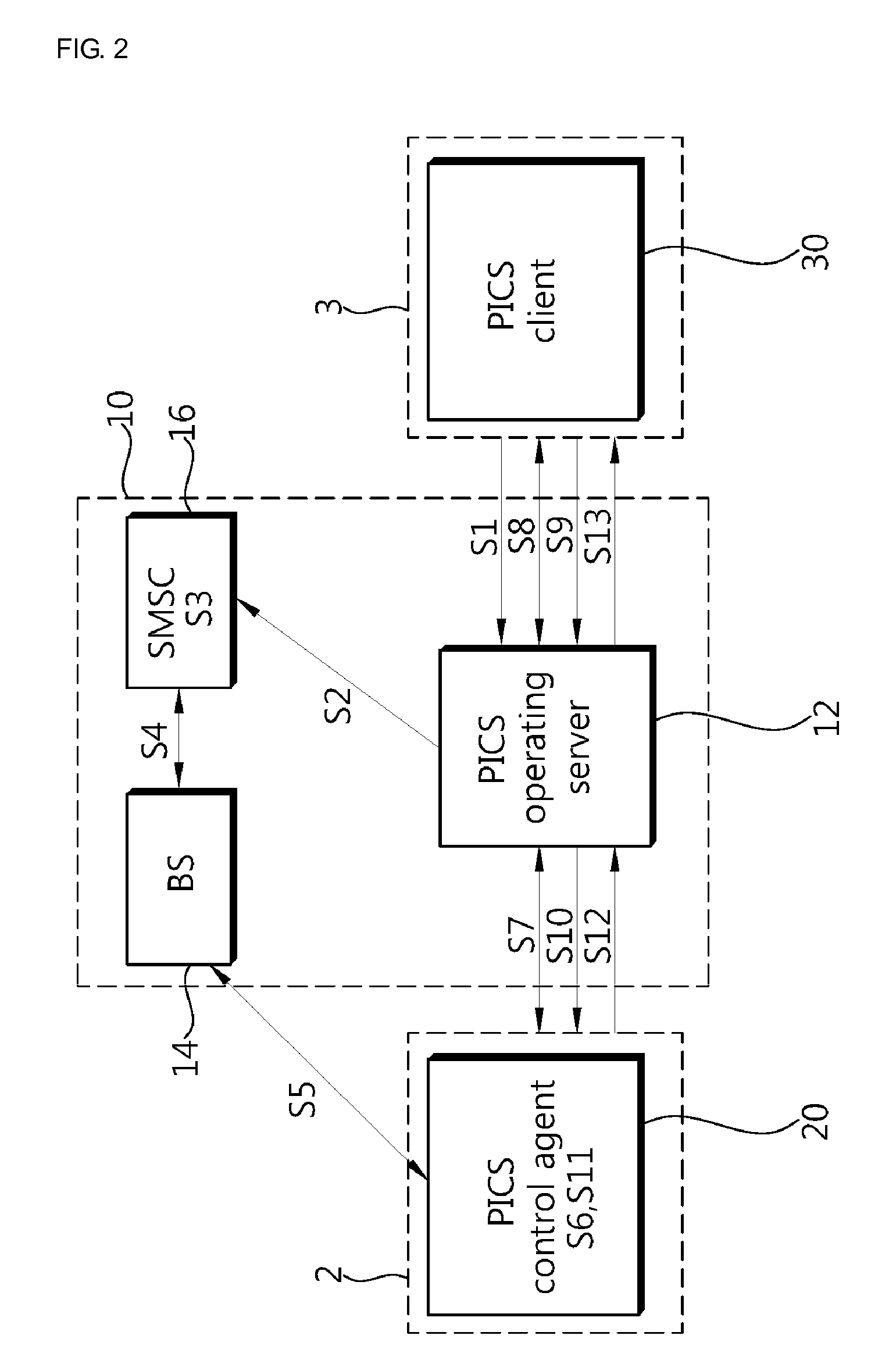
Method and system of providing personal information control service for mobile communication terminal
InactiveUS20110003581A1Protection of personal informationImprove protectionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInformation controlOperational system
A method and system for providing a personal information control service for a mobile communication terminal are disclosed. The method for providing personal information control service for a mobile communication terminal includes: transmitting, by a service client, a loss registration control command to a service operating system; notifying, by the service operating system, that a mobile communication terminal of a user has been lost by using one of a method of transmitting a particular form of loss control message to the user mobile communication terminal and a method of originating a call using a particular origination number to the user mobile communication terminal in response to the loss registration control command; and activating, by a control agent provided in the user mobile communication terminal, a service function of the control agent to protect personal information of the mobile communication terminal based on the notification about the loss. When the mobile communication terminal is lost, it can be controlled by transmitting a particular form of message or originating a call using a particular origination number.
Owner:SSOMON
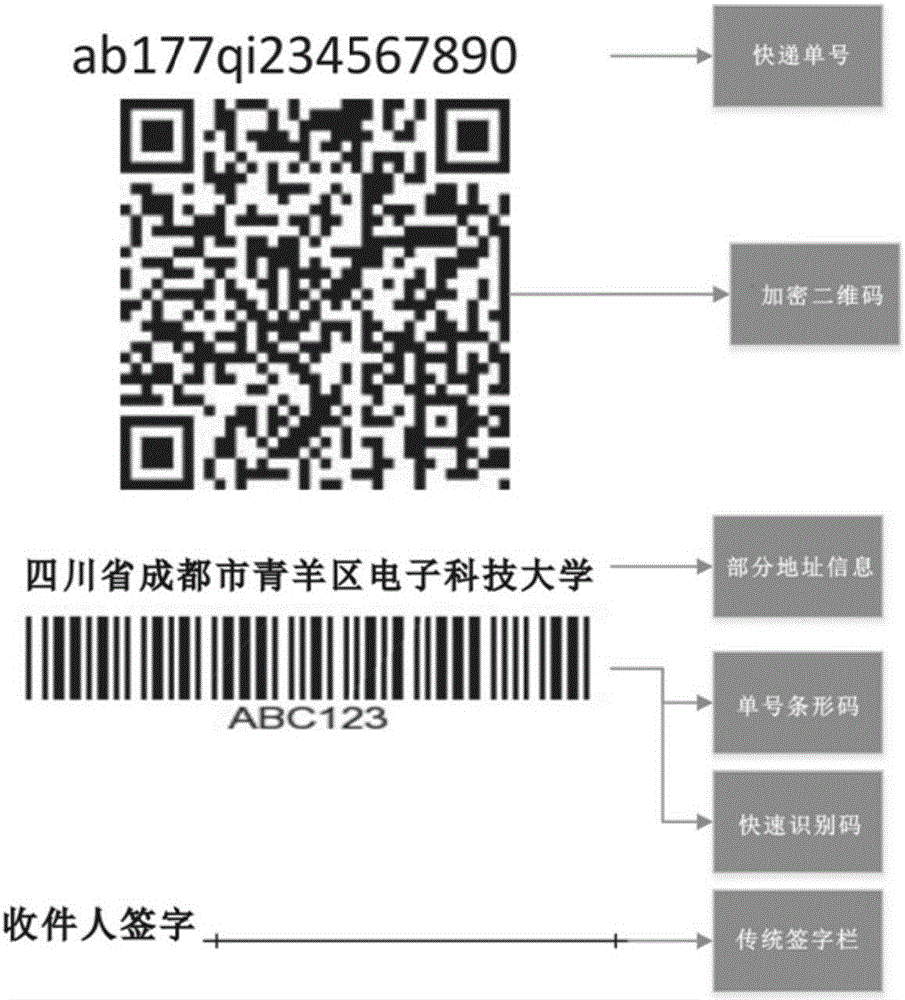
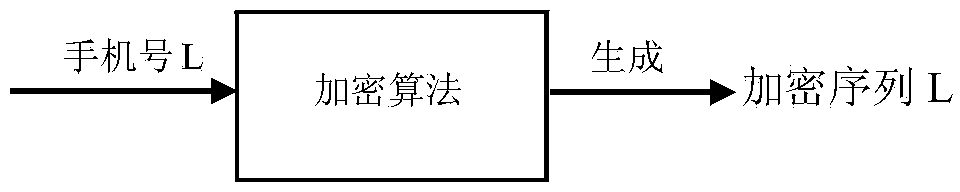
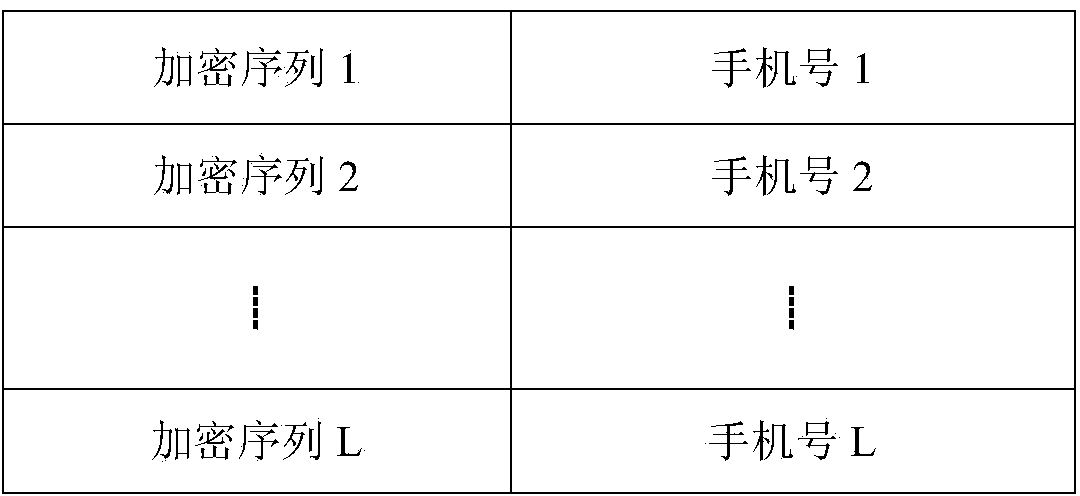
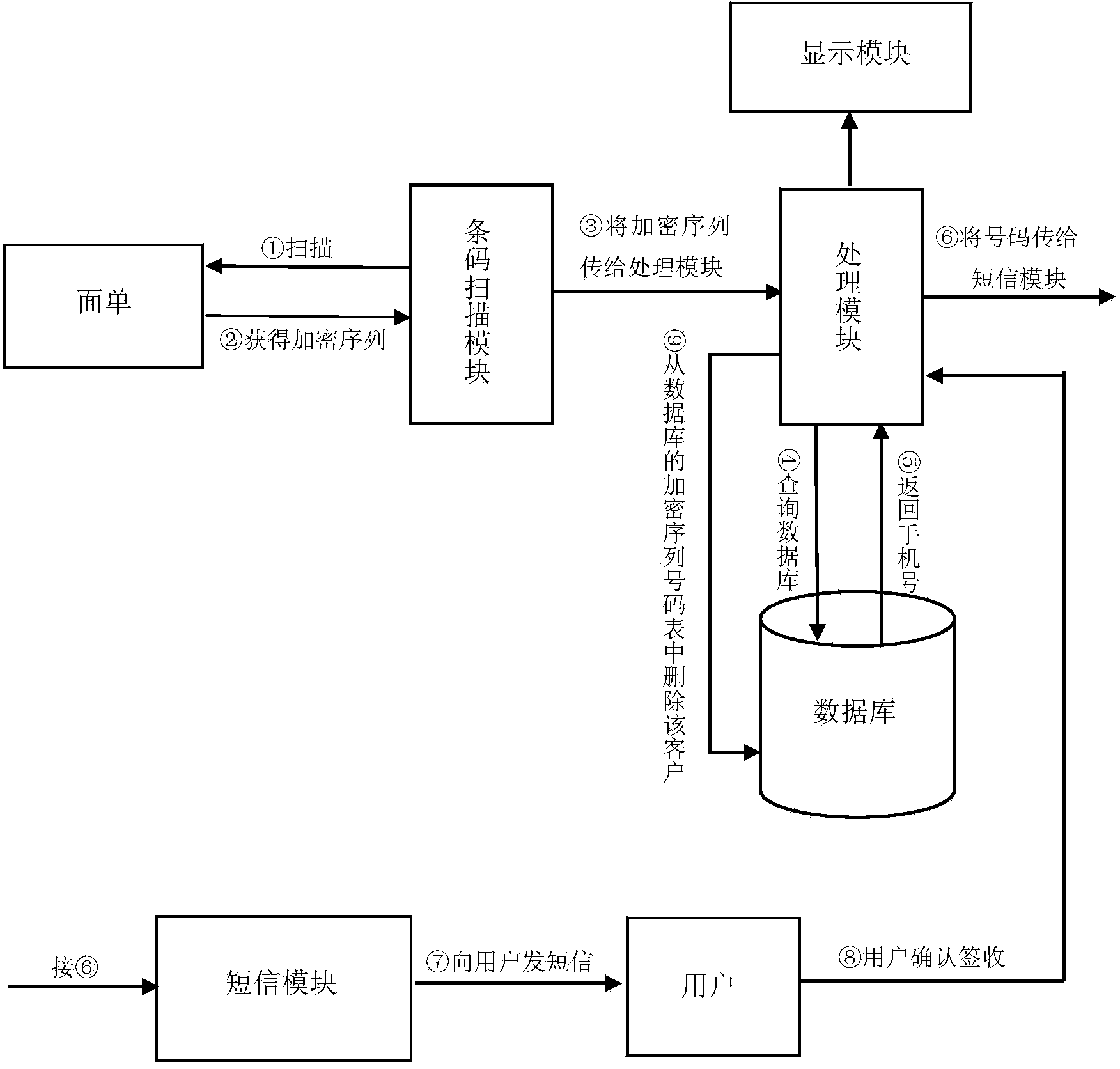
Text-message distribution system capable of identifying encrypted bar code and realization method thereof
InactiveCN104166923ACan't decipherImprove distribution efficiencyCo-operative working arrangementsCommerceUser privacyBarcode
The invention discloses a text-message distribution system capable of identifying an encrypted bar code and a realization method thereof. The system includes an encrypted sequence, an encrypted algorithm database, an encrypted sequence number table, a bar-code scanning module, a processing module, a text message module, and a terminal display module. In the system and the realization method thereof, one encryption algorithm is randomly selected from the encrypted algorithm database and a number is used as input to generate a unique encryption sequence and at last, the encryption sequence and a cellphone number are used as one item of record and stored into the encrypted sequence number table and the encryption sequence is printed on an express waybill in the form of a bar code or a two-dimension code. During express distribution, the bar-code scanning module scans the bar code on the waybill so that an encryption sequence number is obtained. According to the sequence number, a bar code-number table is searched so that the cellphone number is obtained and the text message module distributes a text message which is edited in advance to a customer. The system is capable of improving express distribution efficiency, and protecting user privacy in a specific degree at the same time.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and system of providing personal information control service for mobile communication terminal
InactiveUS8233901B2Protection of personal informationImprove protectionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInformation controlOperational system
A method and system for providing a personal information control service for a mobile communication terminal are disclosed. The method for providing personal information control service for a mobile communication terminal includes: transmitting, by a service client, a loss registration control command to a service operating system; notifying, by the service operating system, that a mobile communication terminal of a user has been lost by using one of a method of transmitting a particular form of loss control message to the user mobile communication terminal and a method of originating a call using a particular origination number to the user mobile communication terminal in response to the loss registration control command; and activating, by a control agent provided in the user mobile communication terminal, a service function of the control agent to protect personal information of the mobile communication terminal based on the notification about the loss. When the mobile communication terminal is lost, it can be controlled by transmitting a particular form of message or originating a call using a particular origination number.
Owner:SSOMON
Information delivery system, information delivery method, short-range communication device, information delivery apparatus, and server
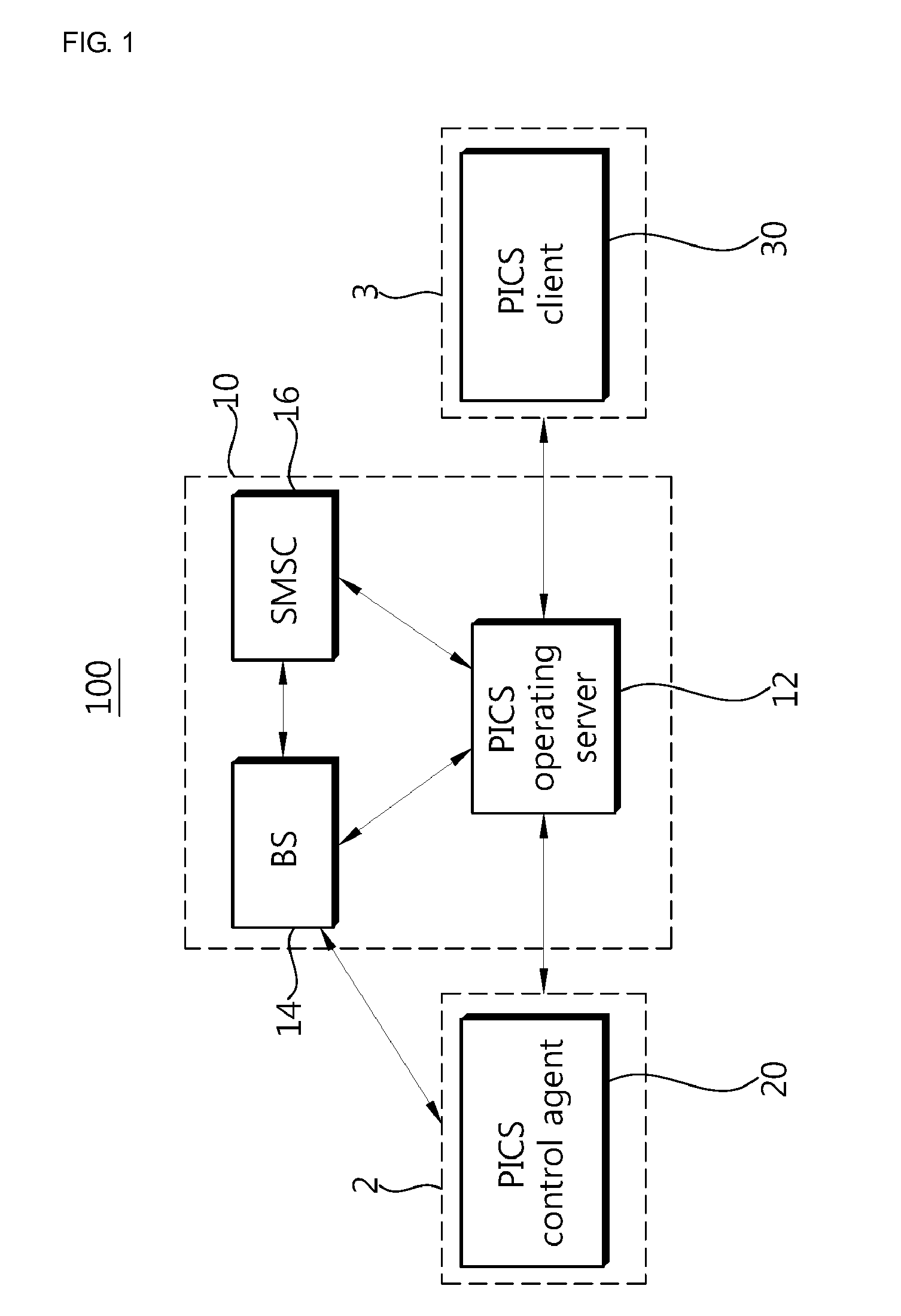
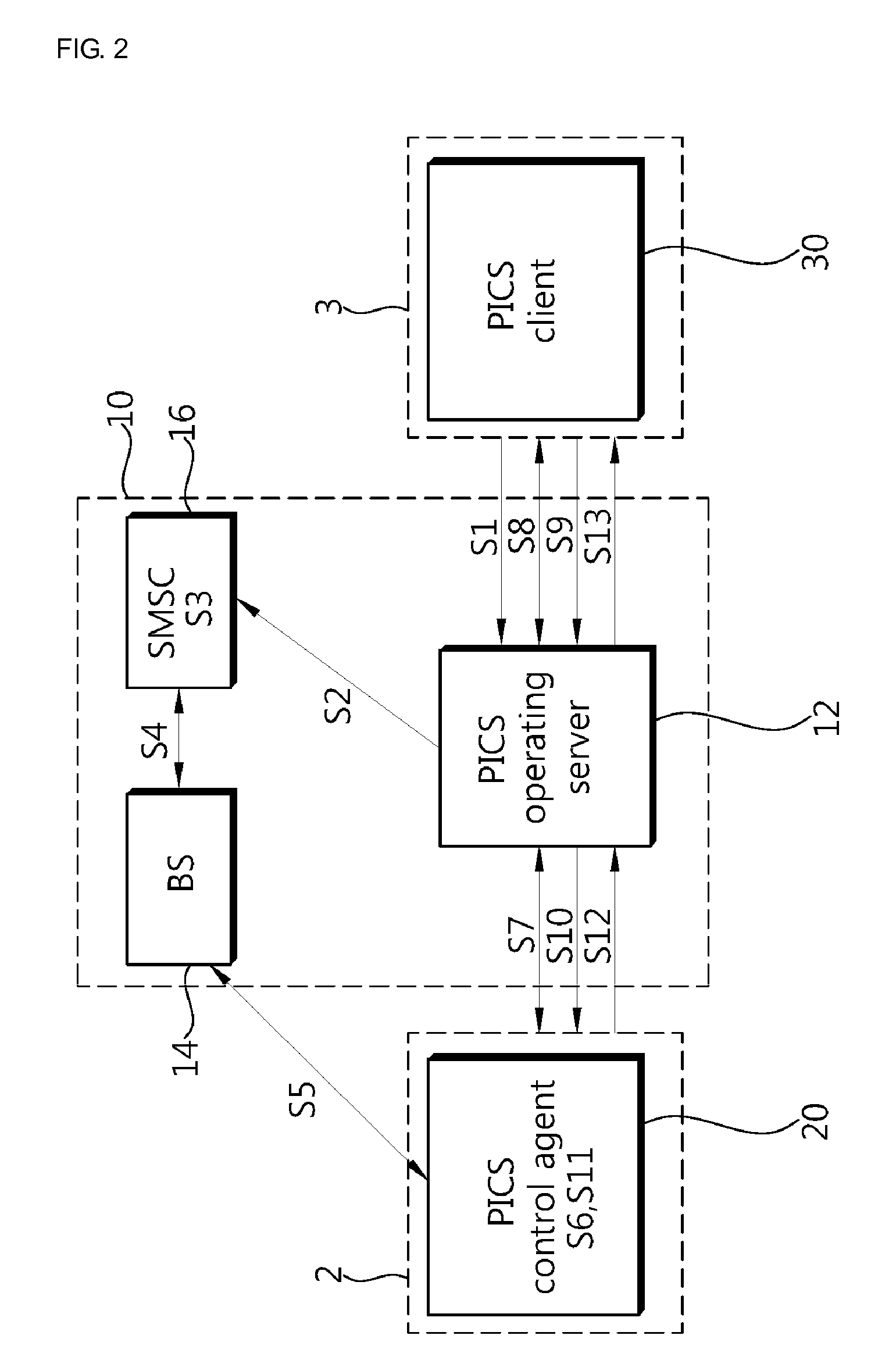
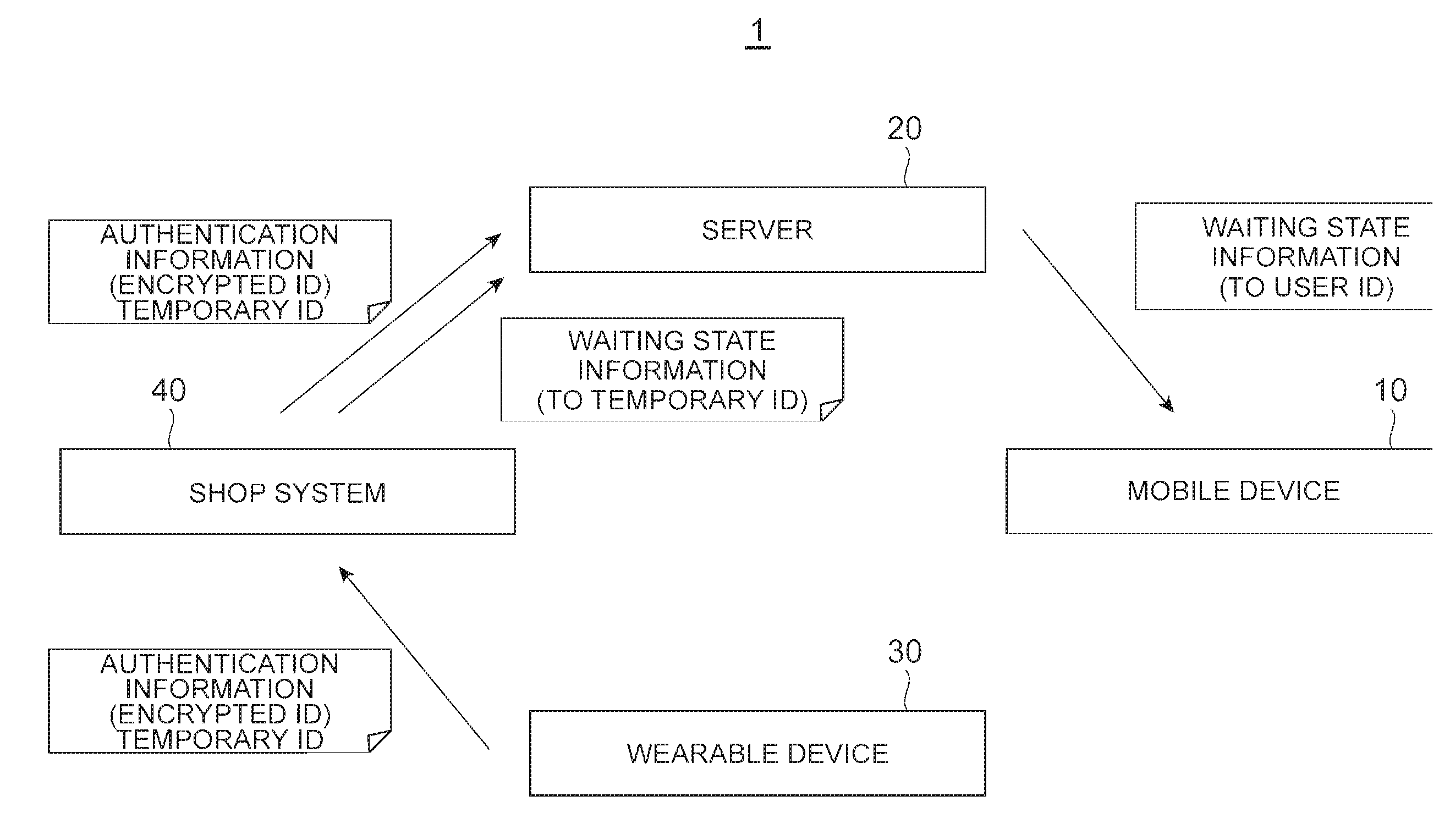
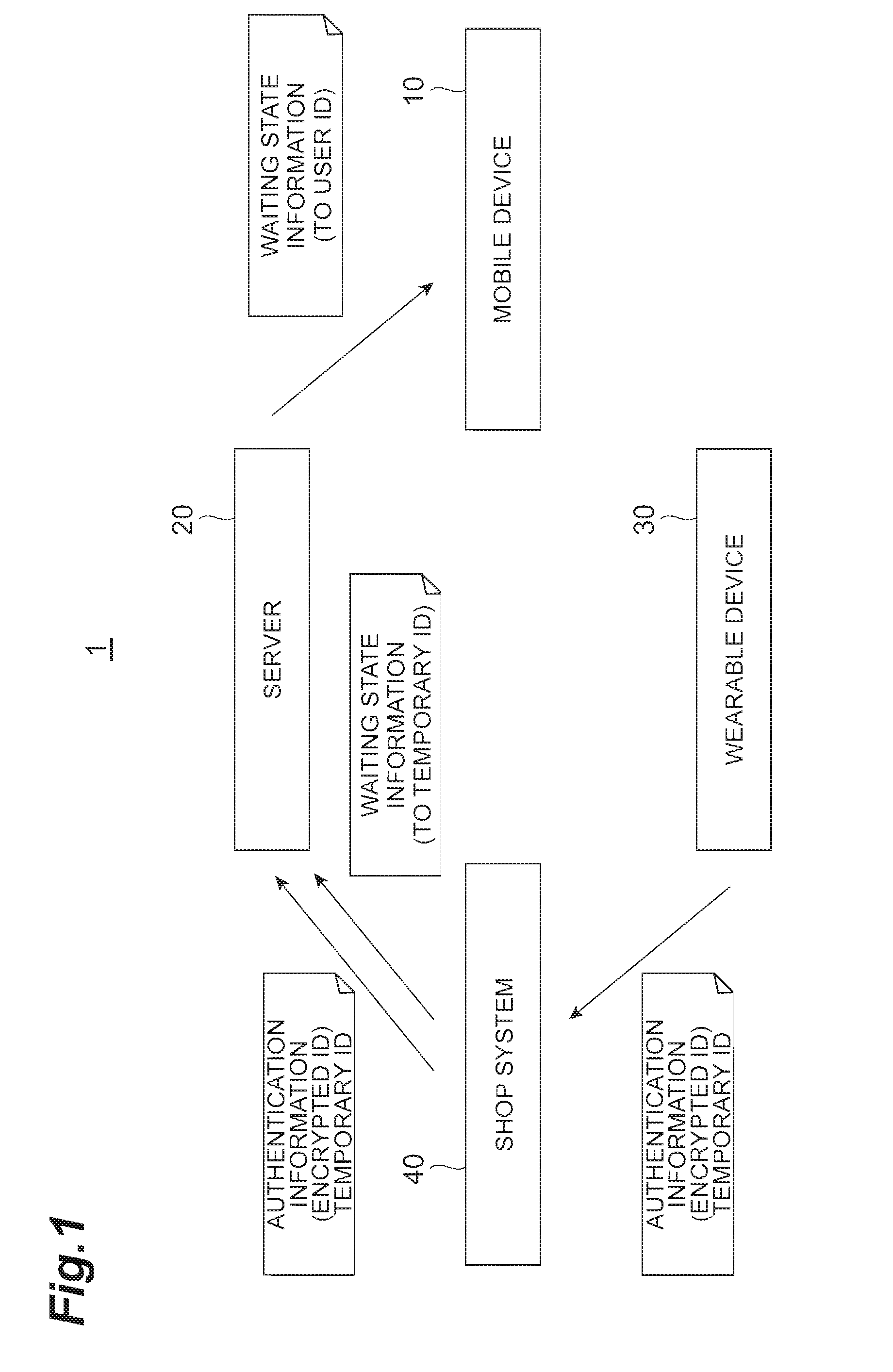
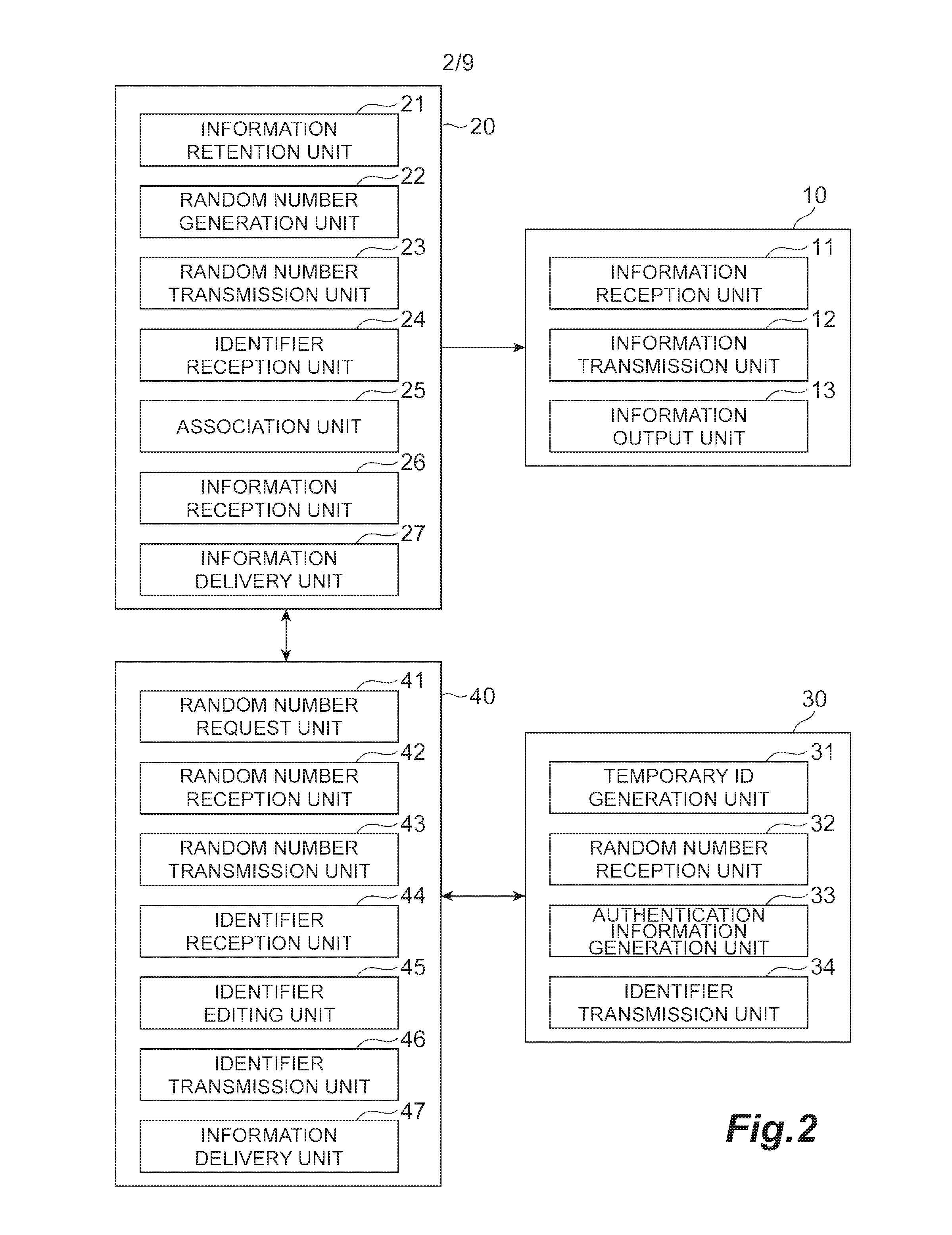
ActiveUS20170019257A1Easy to operateProtection of personal informationKey distribution for secure communicationMultiple keys/algorithms usageUser identifierWait state
A wearable device generates a temporary ID, generates an encrypted user ID, and transmits the temporary ID and the encrypted user ID to a shop system. The shop system receives the temporary ID and the encrypted user ID, transmits a temporary ID corresponding to the received temporary ID and the encrypted user ID to a server, and transmits the temporary ID transmitted by an identifier transmission unit and waiting state information to the server. The server stores the user ID in association with an information delivery destination of the user ID, receives the encrypted user ID and the temporary ID, associates the temporary ID and the information delivery destination of the user ID, receives the temporary ID and the waiting state information, and transmits the waiting state information to the information delivery destination of the user ID corresponding to the temporary ID.
Owner:NTT DOCOMO INC
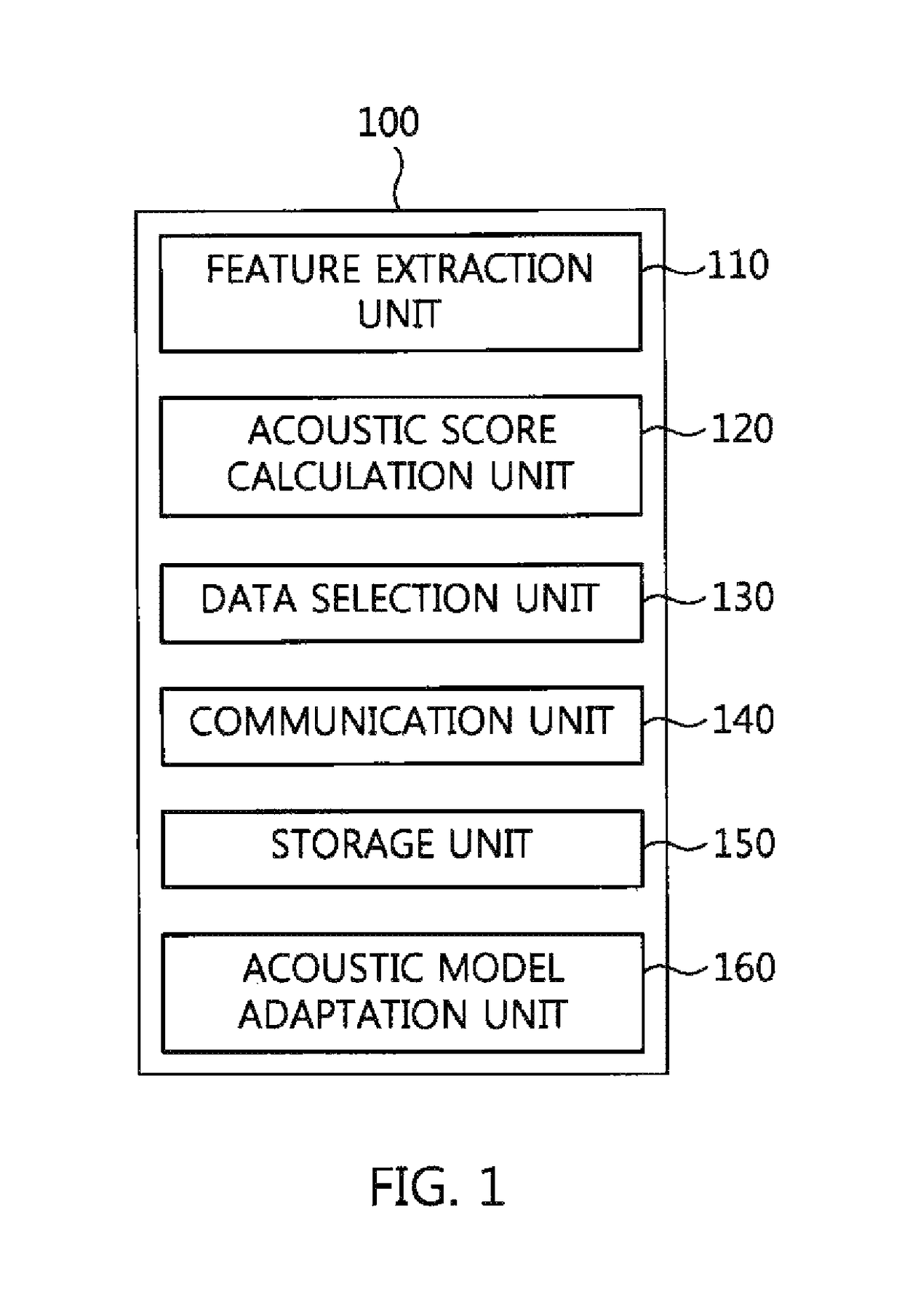
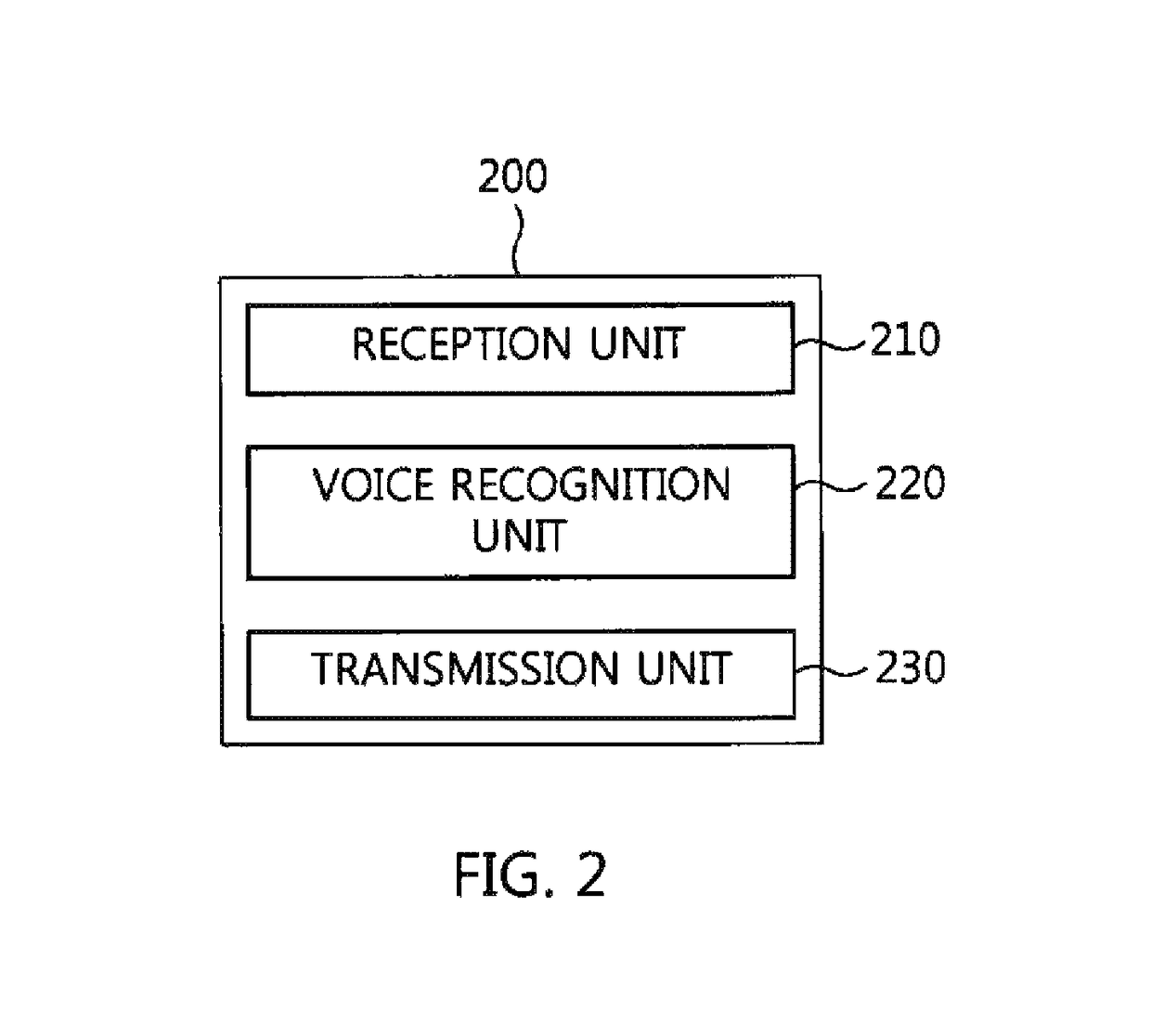
Voice recognition terminal, voice recognition server, and voice recognition method for performing personalized voice recognition
ActiveUS20170194002A1Protection of personal informationReduce computational loadSpeech recognitionSpeech identificationPersonalization
Owner:ELECTRONICS & TELECOMM RES INST
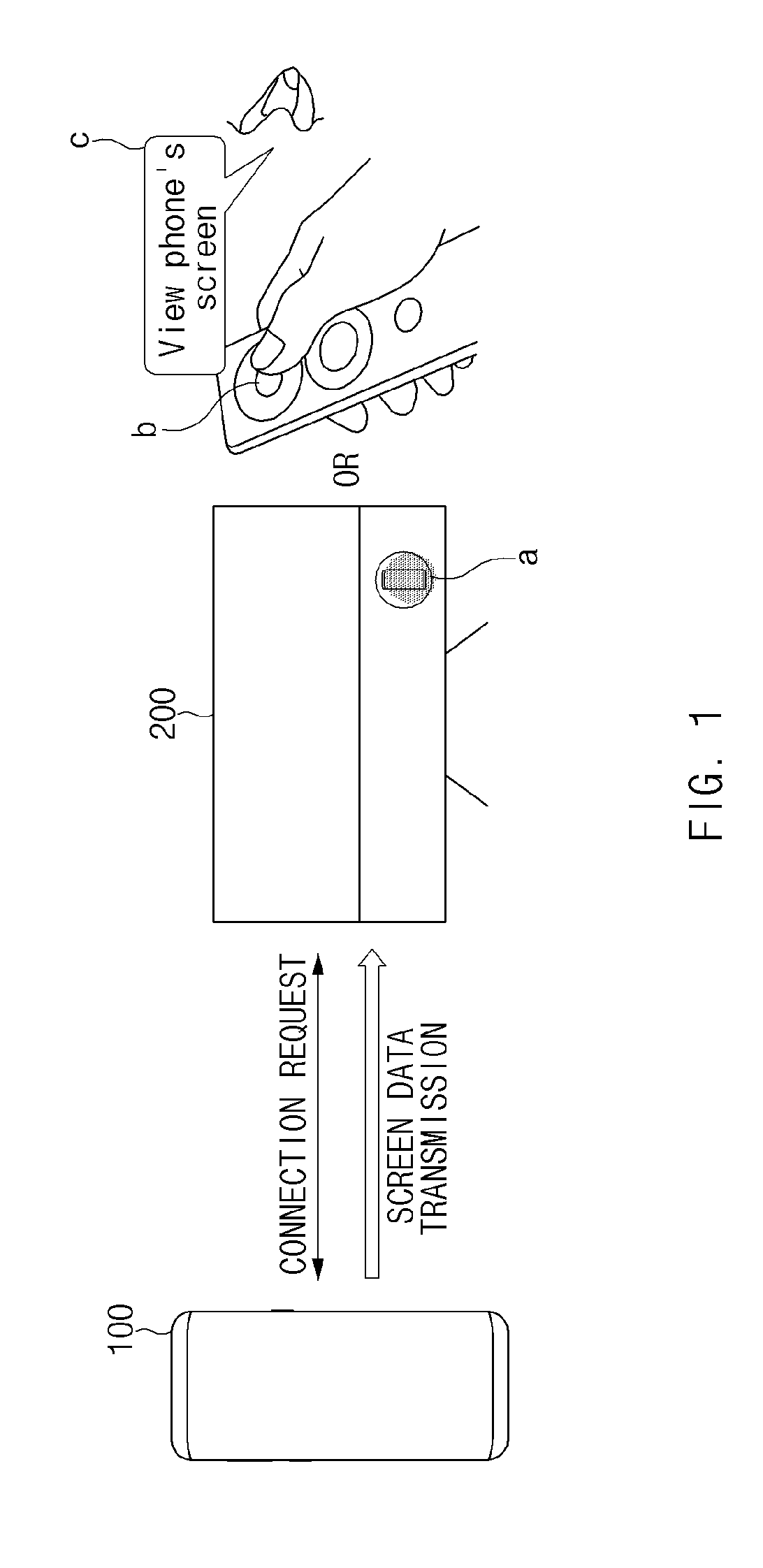
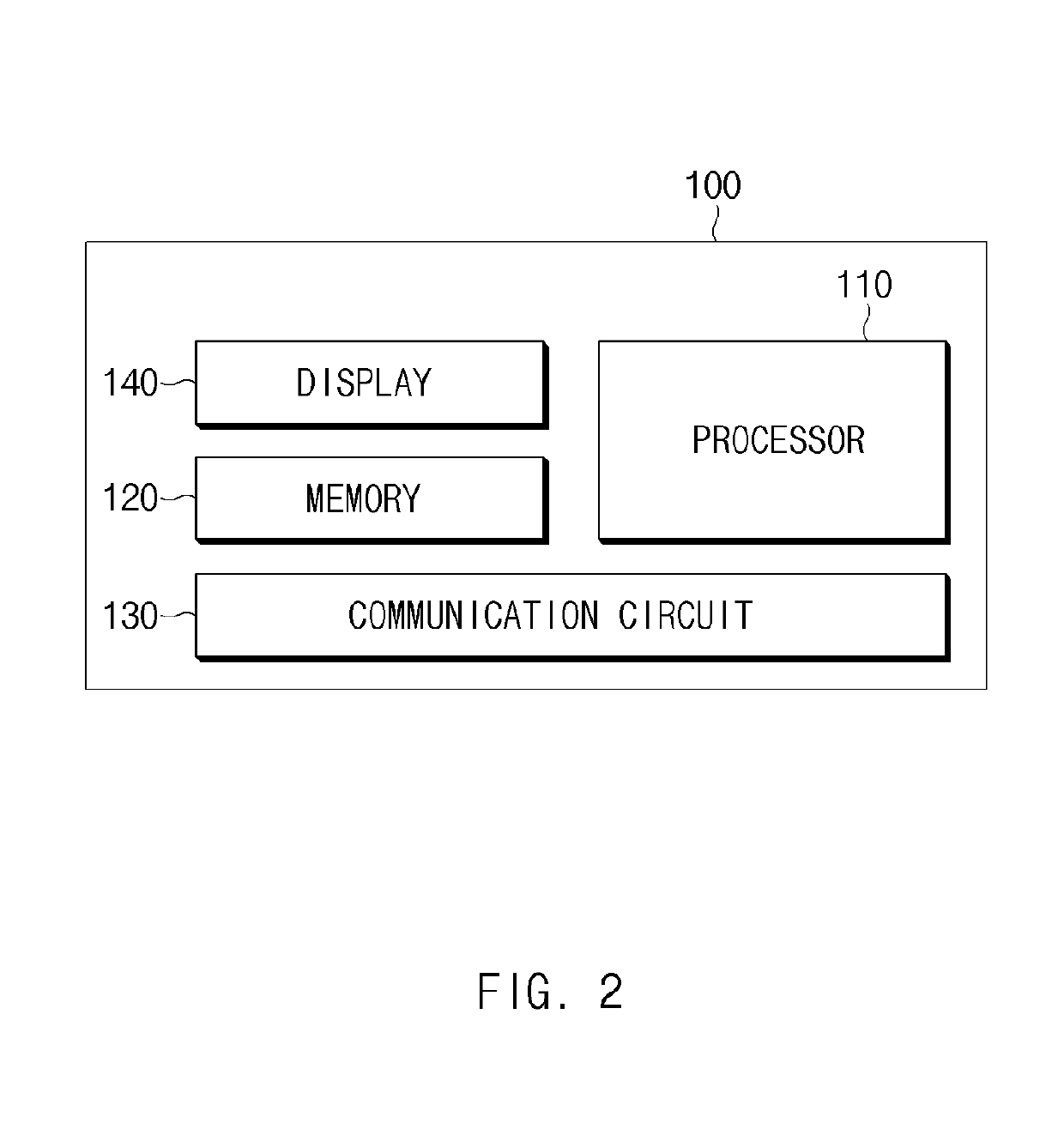
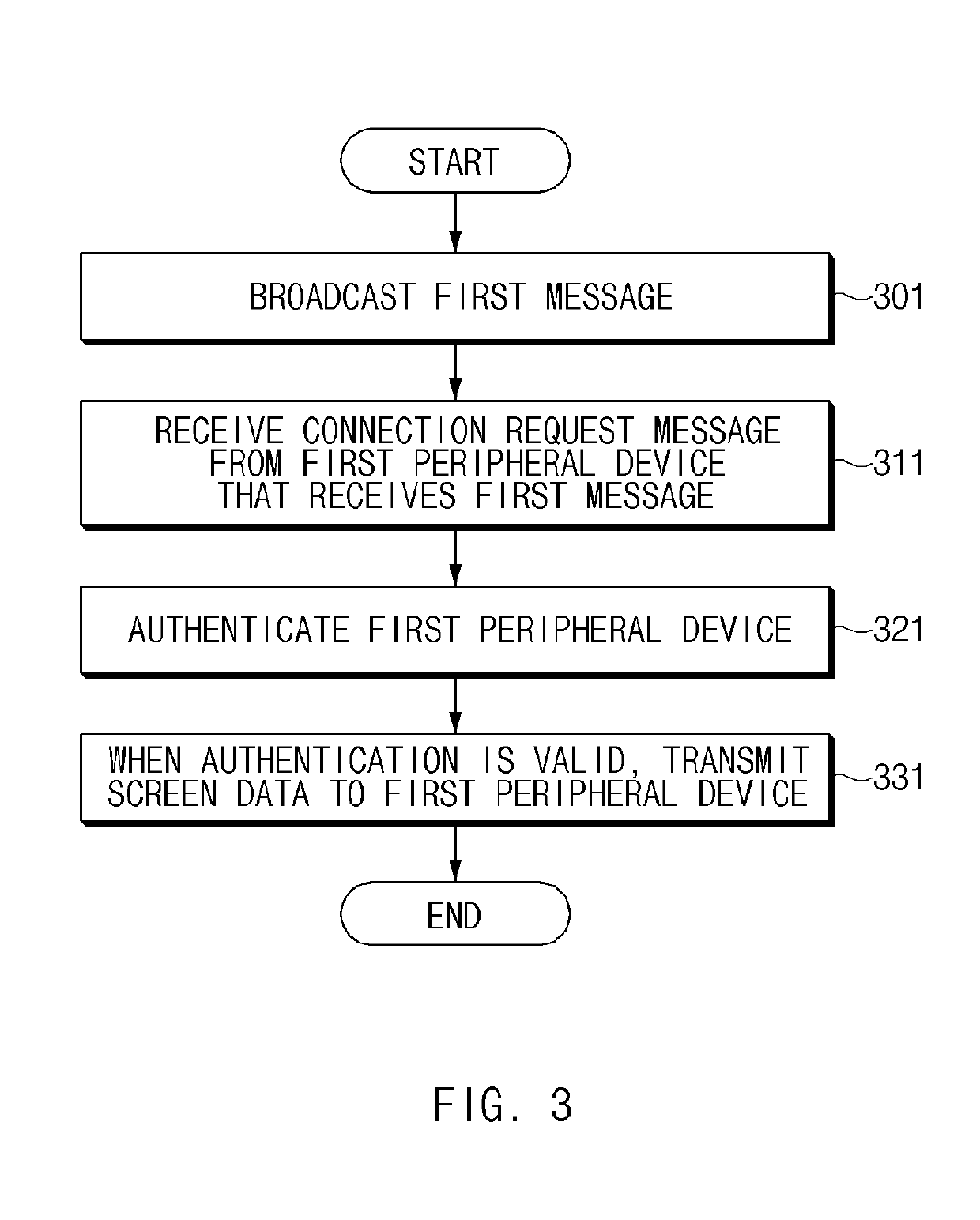
Electronic device and method for sharing screen data
ActiveUS20190265938A1Protection of personal informationStatic indicating devicesDigital data authenticationComputer hardwareDisplay device
An electronic device is disclosed. An electronic device comprises a display, a communication circuit configured to communicate with a first peripheral device, a memory configured to store first authentication information associated with the first peripheral device, and a processor, wherein the processor is configured to control the electronic device to: broadcast a first message via the communication circuit, receive a connection request message from the first peripheral device receiving the first message, authenticate the first peripheral device based on the first authentication information associated with the first peripheral device in response to the reception of the connection request message, and transmit screen data being displayed on the display to the first peripheral device via the communication circuit based on the authentication being valid.
Owner:SAMSUNG ELECTRONICS CO LTD
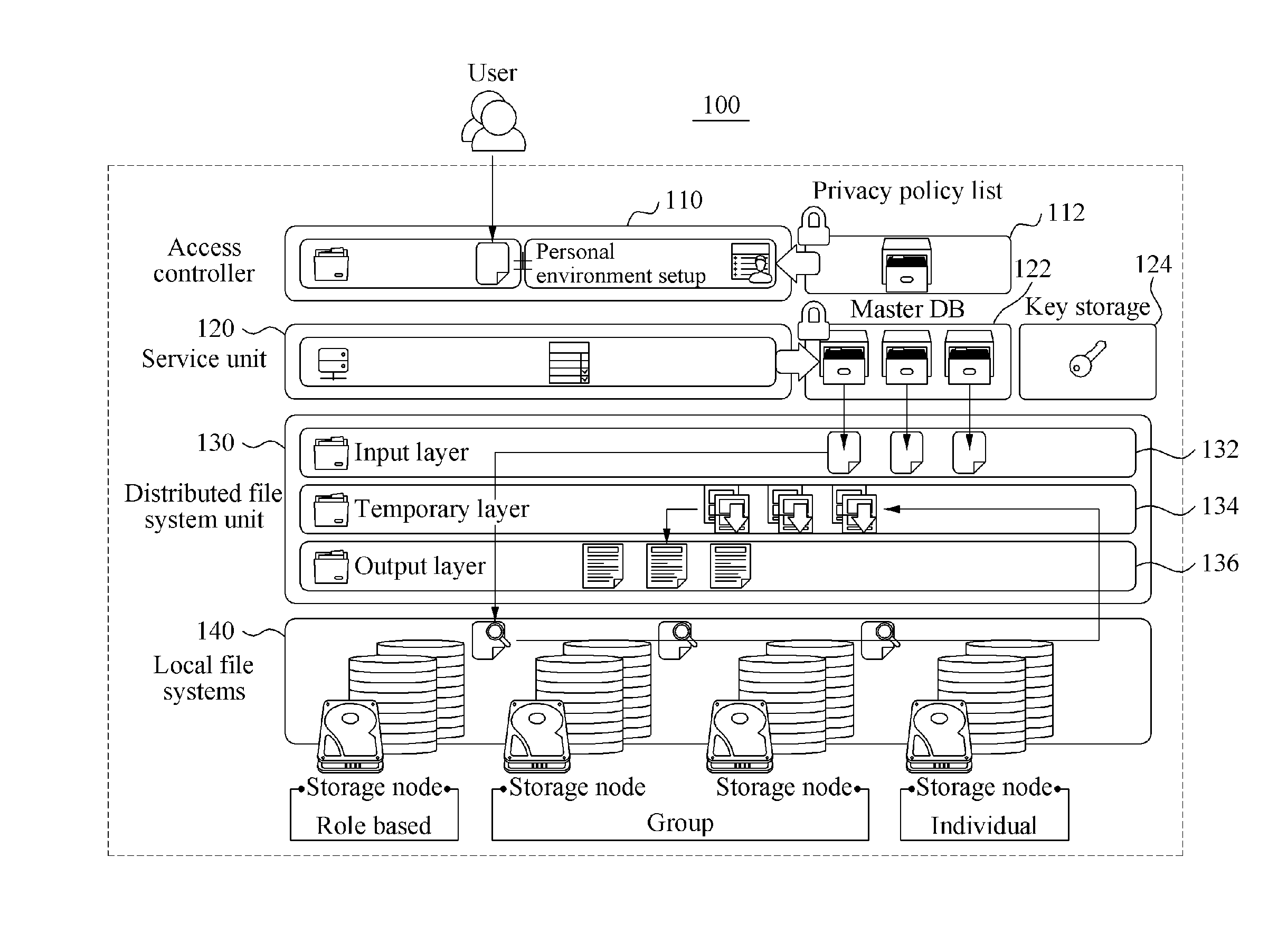
Method and apparatus for providing data sharing
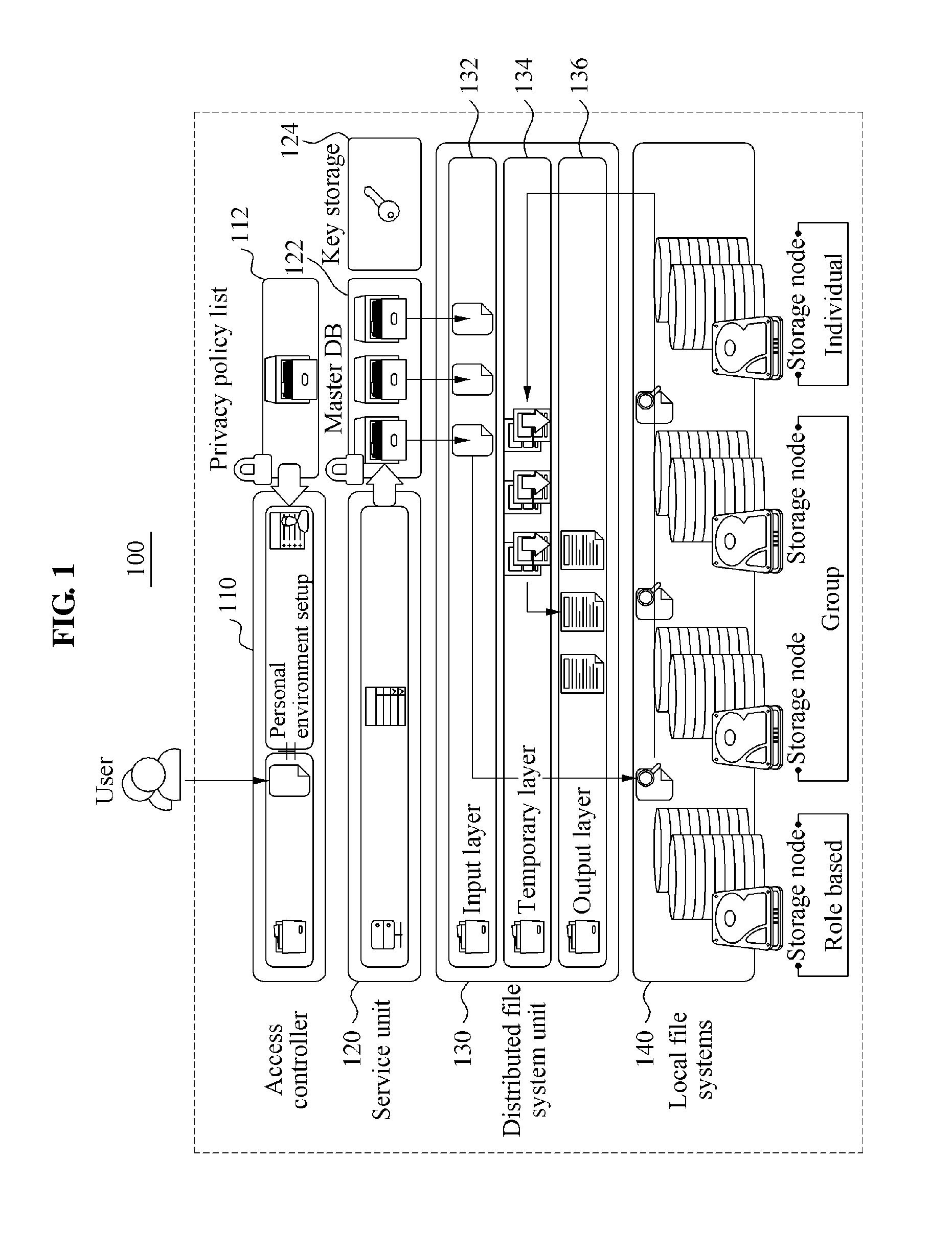
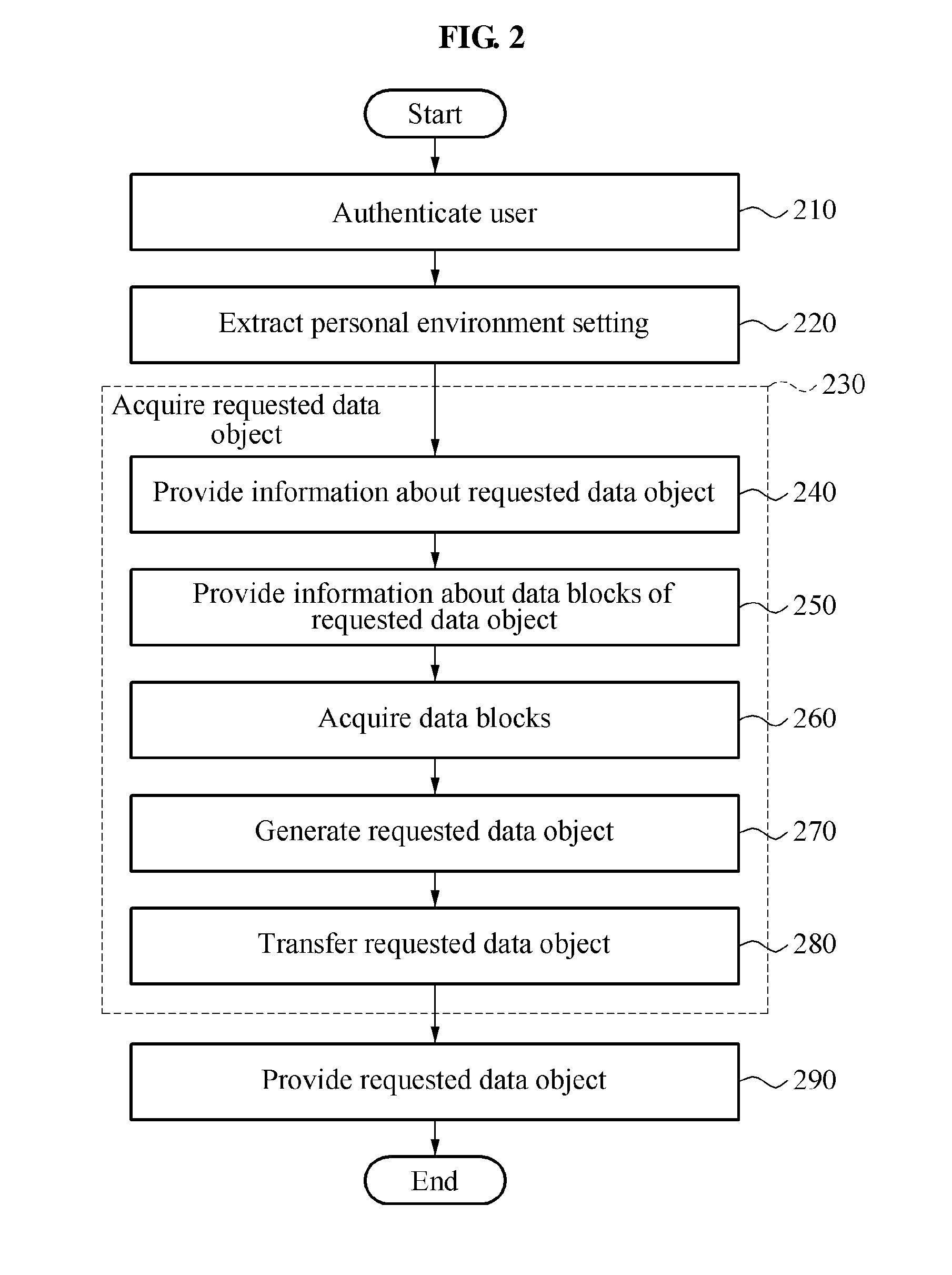
InactiveUS20150205973A1Fix security issuesProtection of personal informationDigital data processing detailsUser identity/authority verificationDistributed File SystemPersonal environment
Provided are a method and apparatus for data sharing based on an individual environment setup. An access control unit authenticates the user having requested a data object, and extracts the individual environment setup of the user. The individual environment setup includes a list of data objects possessed by the user and access information on each data object in the list. A service unit acquires the data object requested from a distributed file system unit using the individual environment setup, and provides the requested data object to the user.
Owner:INTELLECTUAL DISCOVERY CO LTD
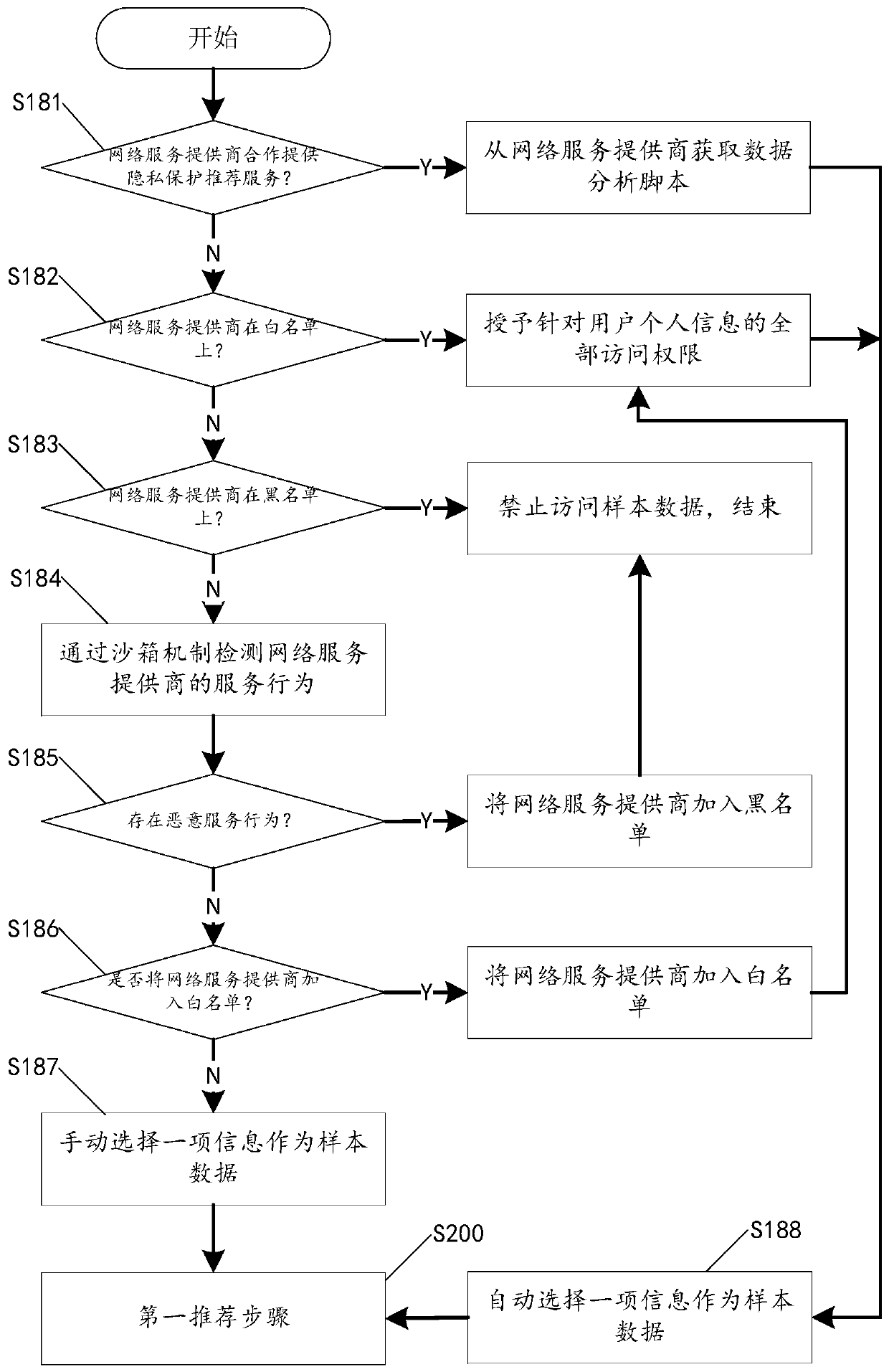
Privacy protection mobile service recommendation method, client and recommendation system
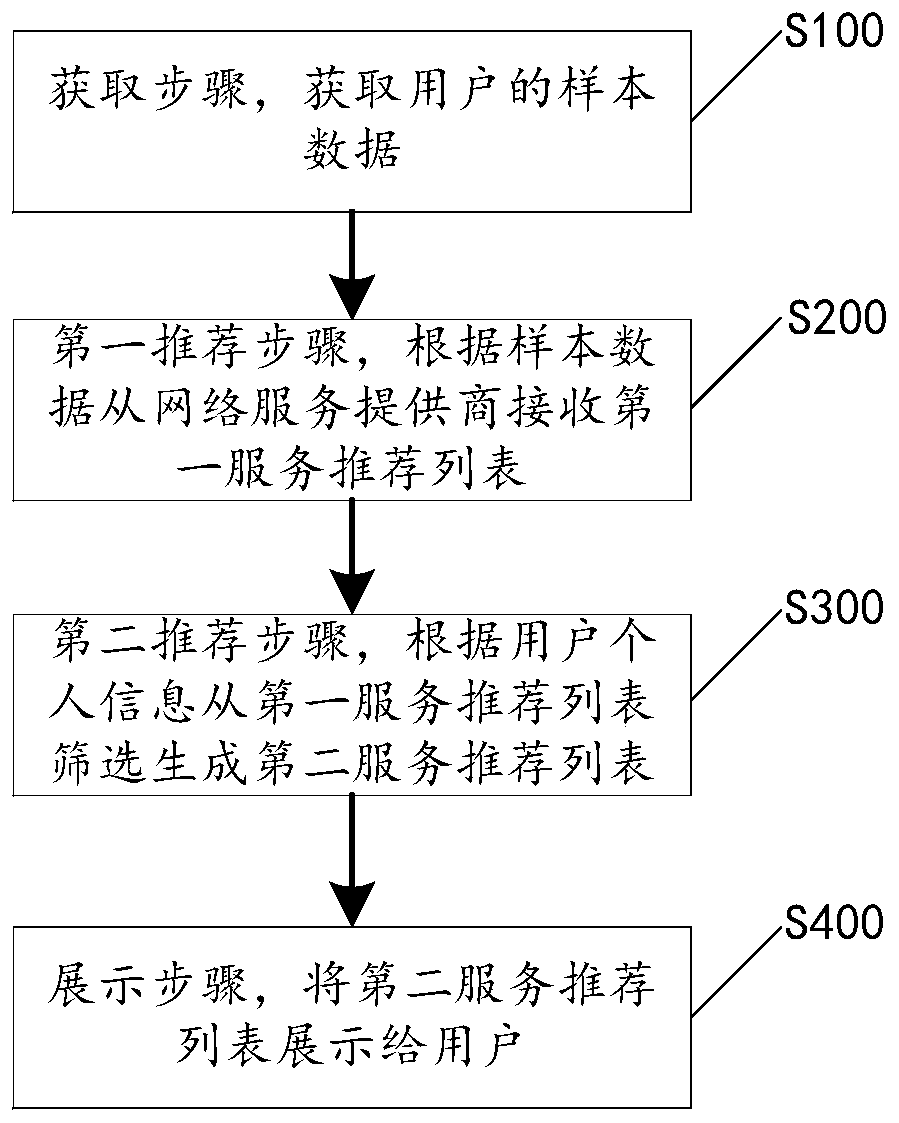
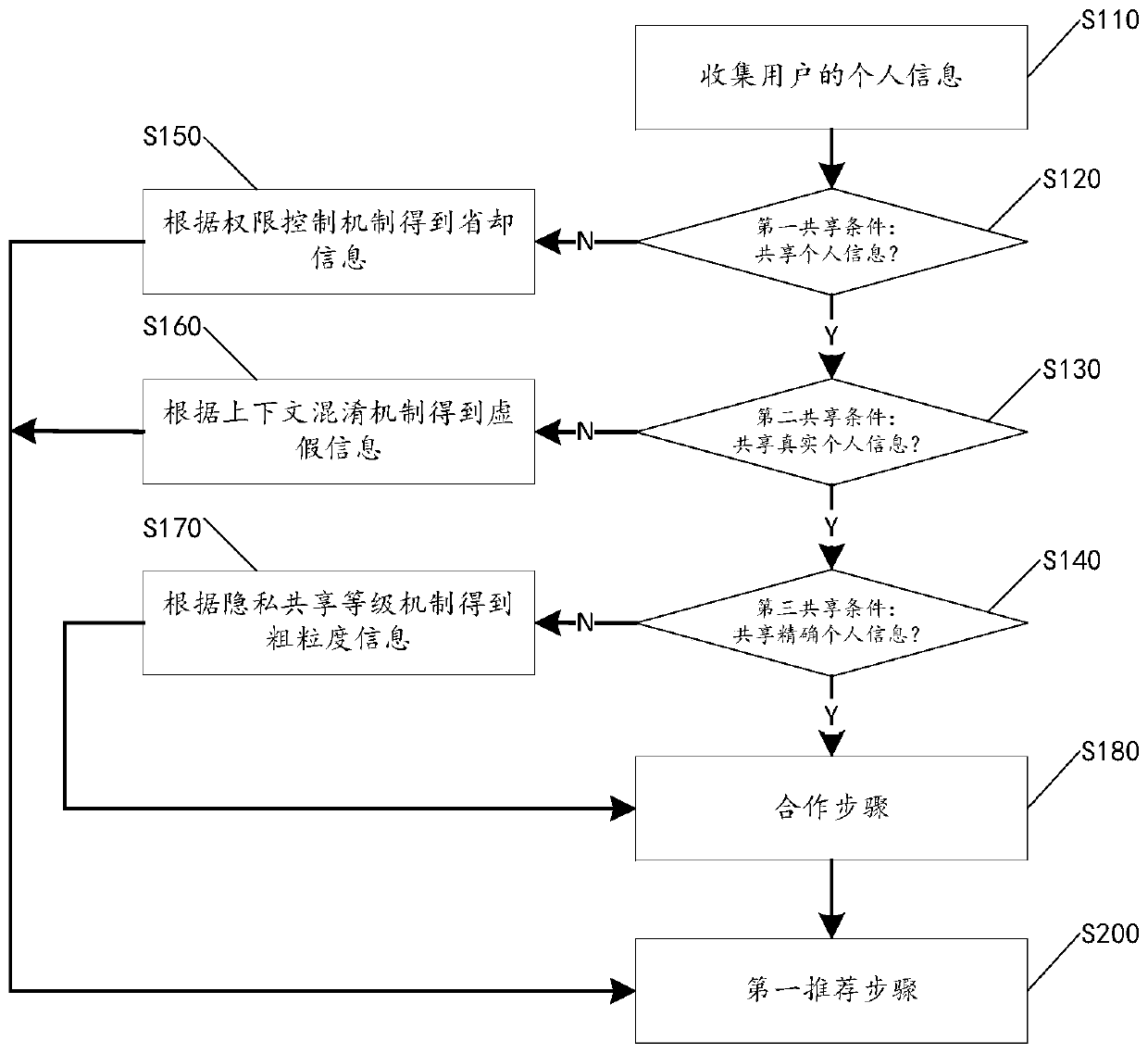
ActiveCN110321479AEasy to manageEnsure balanceDigital data information retrievalDigital data protectionUser needsUser privacy
The invention discloses a privacy protection mobile service recommendation method, a client and a recommendation system, and the privacy protection mobile service recommendation method comprises the following steps: obtaining sample data of a user, the sample data being saving information, false information, coarse-grained information or fine-grained information of personal information of the user; receiving a first service recommendation list from a network service provider according to the sample data; screening and generating a second service recommendation list from the first service recommendation list according to the fine-grained information of the user; and displaying the second service recommendation list to the user. The first service recommendation list is downloaded to the local client to assist in generating the second service recommendation list meeting the user requirements; therefore, on the premise of ensuring that the personal information of the user is not invaded bya network service provider, the function of providing accurate recommendation service for the user is realized, the balance between mobile service recommendation precision and user privacy protectioncan be maintained, and the user can better manage the personal information.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
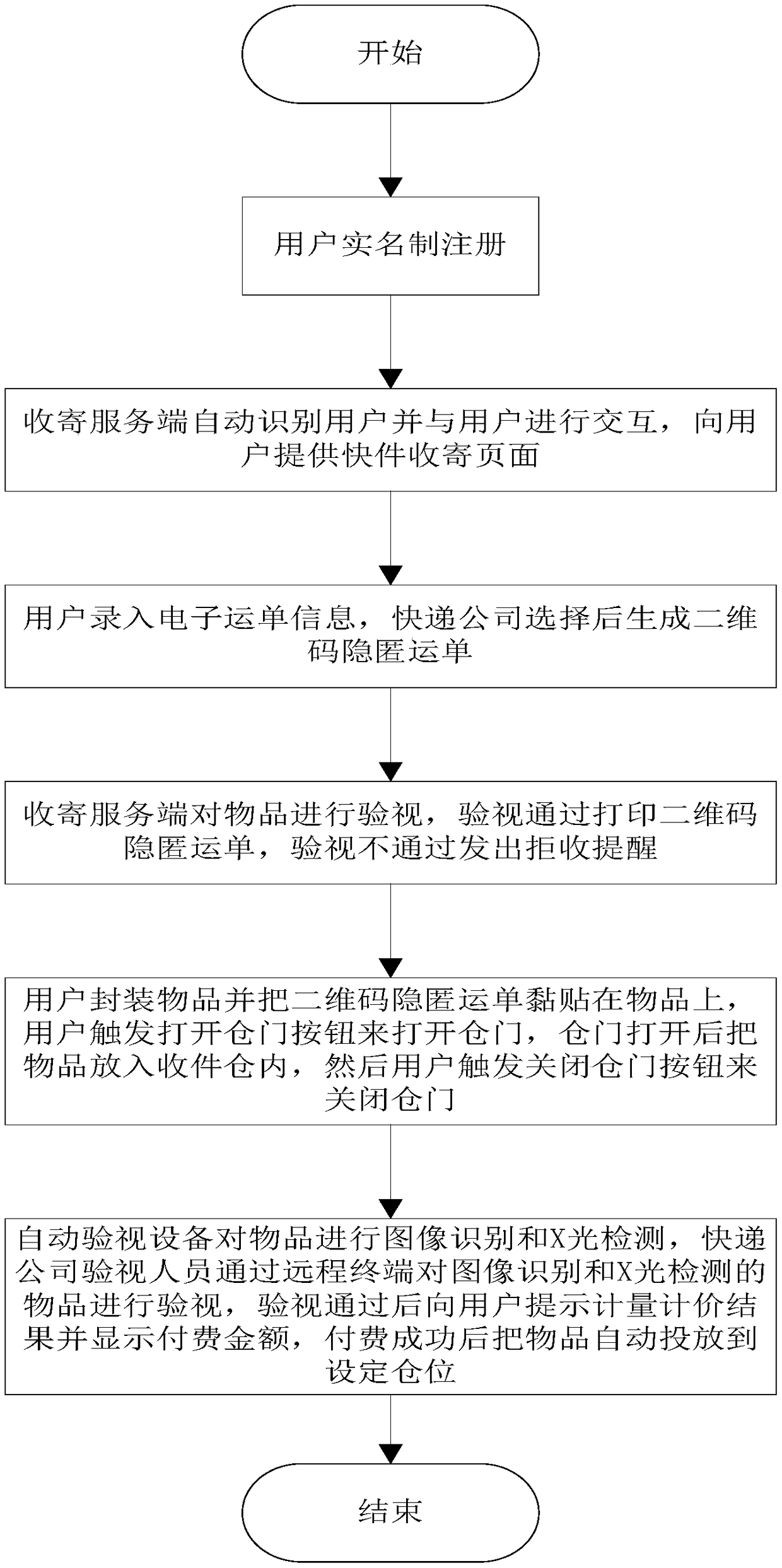
Method for safe self-service receiving and sending of expresses
The invention discloses a method for the safe self-service receiving and sending of expresses, and the method comprises the steps that a user carries out the real-name registration; a receiving and sending server actively recognizes the information of the user when the user completing the real-name registration carries out the self-service receiving and sending and delivery of expresses; the receiving and sending server carries out the voice interaction with the user, so as to remind the use of selecting a receiving and sending function; the user inputs the electronic waybill information intothe receiving and sending server, and selects an express company to generate and display a QR code hiding waybill; the receiving and sending server carries out the inspection of articles and allows the article to pass, and then the receiving and sending server prints the QR code hiding waybill for the user; the user packages the articles and then pastes the QR code hiding waybill; the user opens an express receiving cabin door and then puts the articles into an express receiving cabin, and closes the express receiving cabin door; an automatic inspection device in the express receiving cabin carries out the image recognition and X-ray detection of the articles, gives a prompt of a metering and pricing result and displays a to-be-paid amount; and the articles is put at a set cabin position after successful payment. The method saves a large amount of manpower, and reduces the operation cost.
Owner:王俊杰
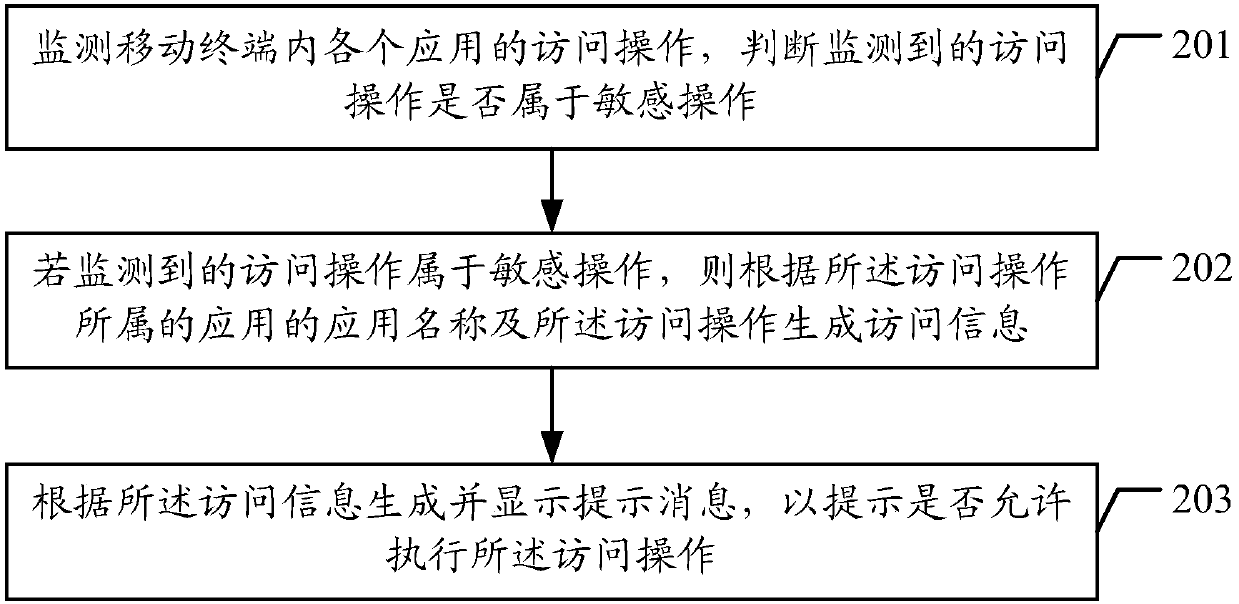
Access operation monitoring method and device, mobile terminal and readable storage medium
InactiveCN107563187ASensitive operations are blocked in timeProtection of personal informationHardware monitoringPlatform integrity maintainanceOperating systemComputer science
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
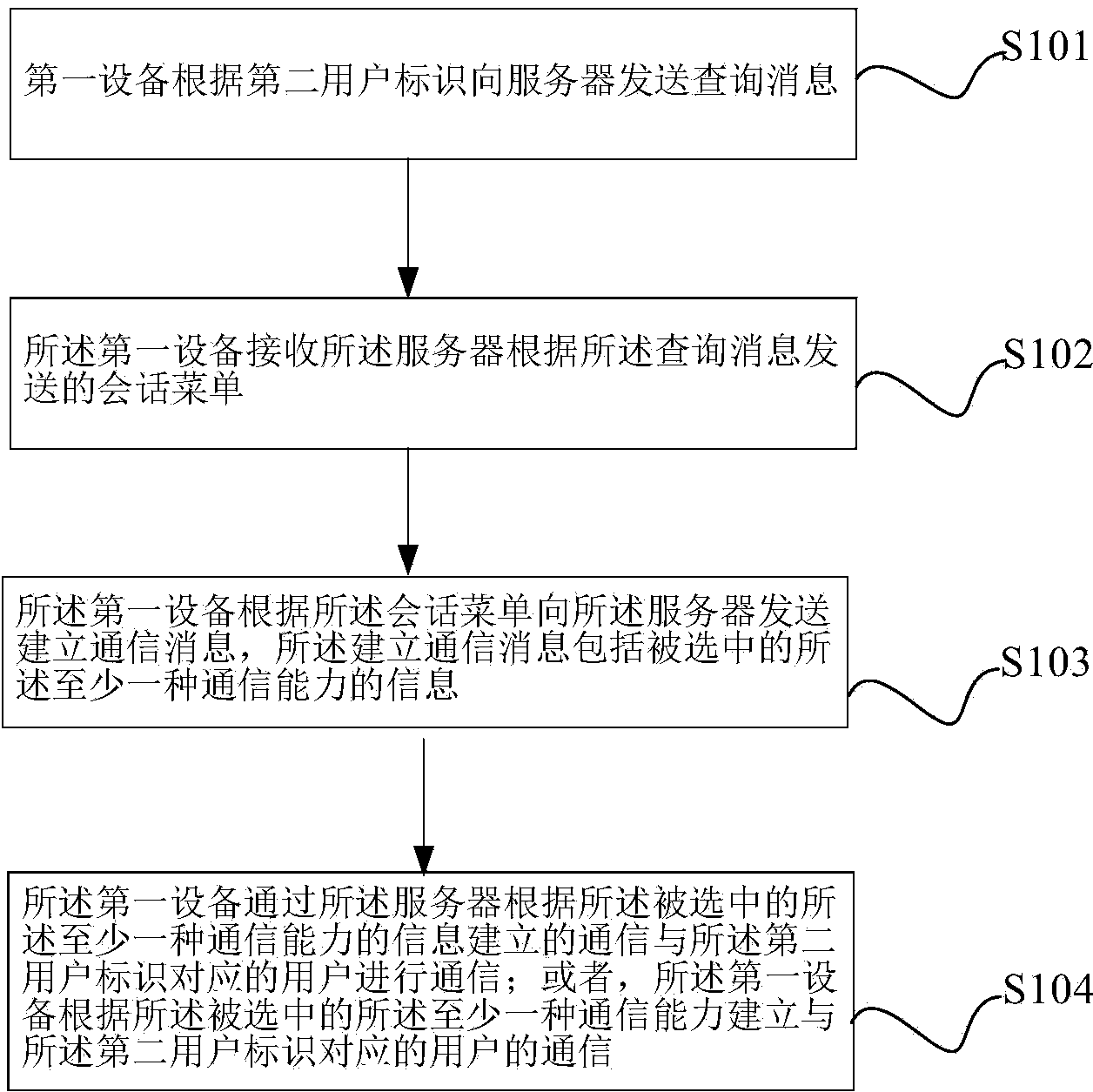
Method for communication construction, device and system
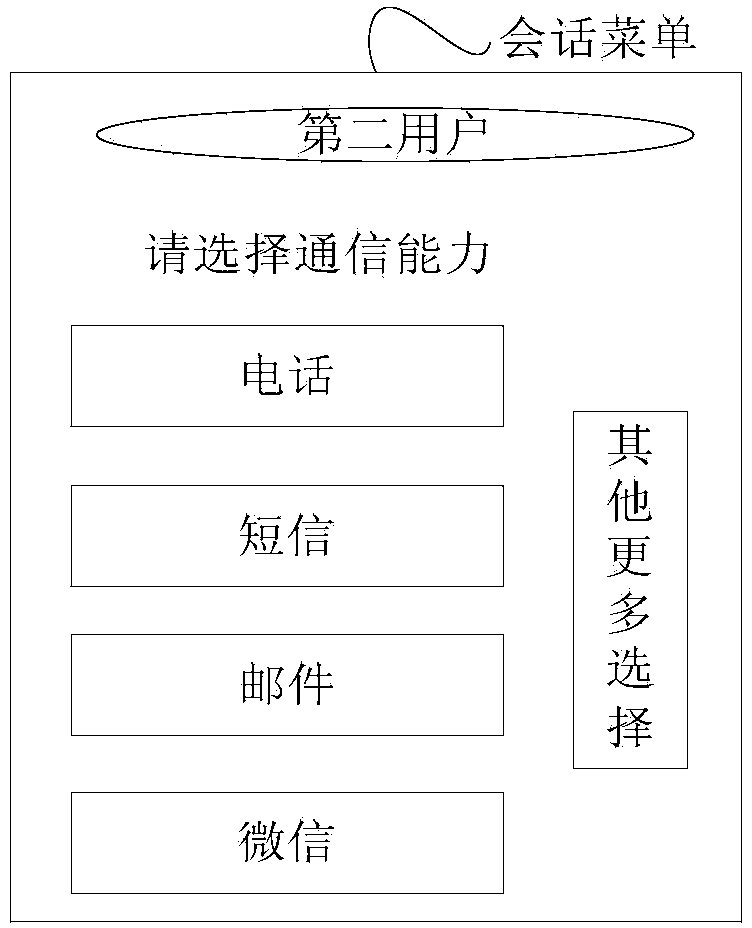
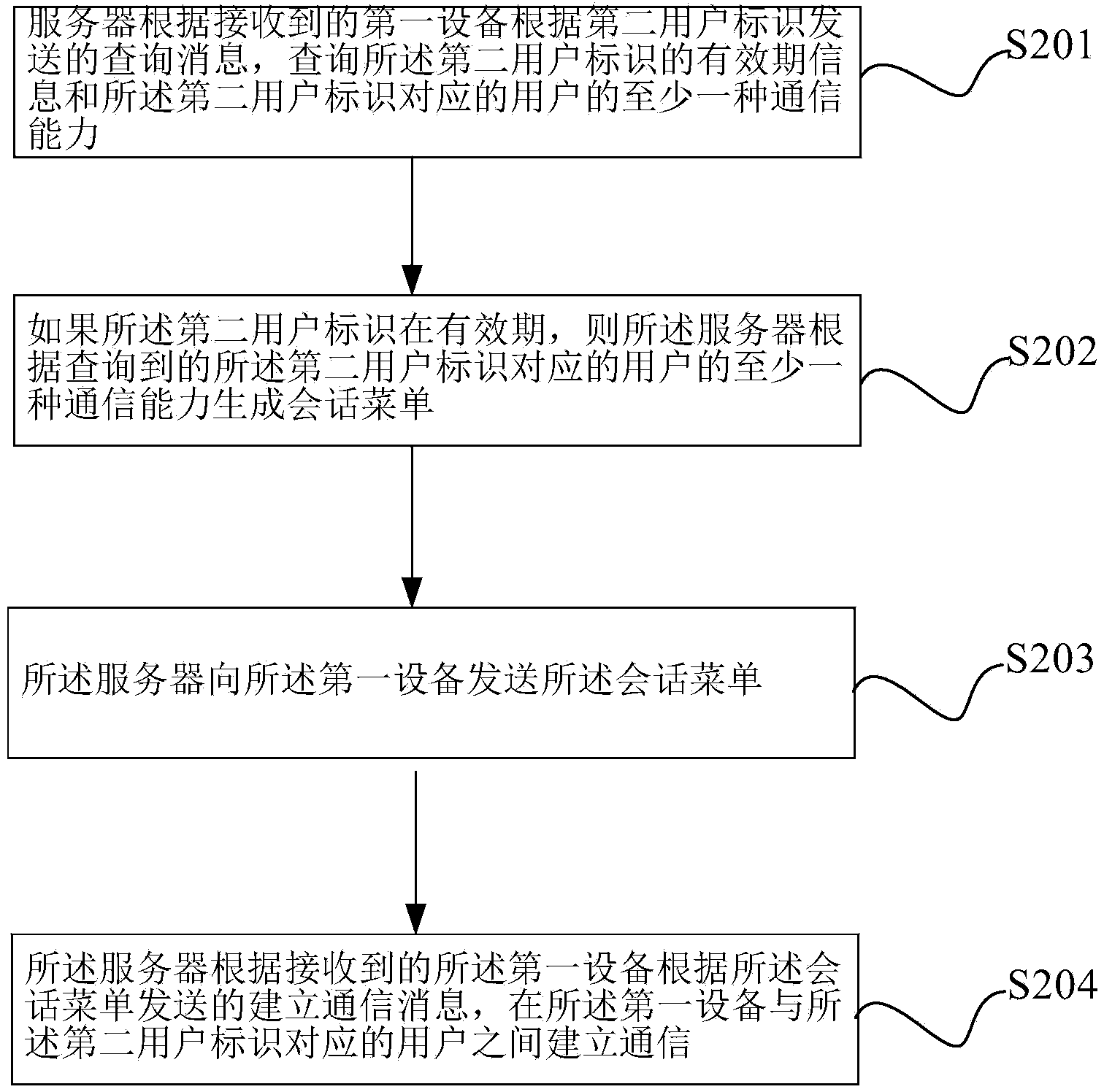
ActiveCN104067596AProtection of personal informationImprove user experienceTransmissionUser identifierContact method
An embodiment of the invention provides a method for communication construction. The method comprises that a first device sends an inquiry massage to a server through a second user identifier, and the server sends a conversation menu having at least one communication function of a user corresponding to the second user identifier to the first device according to the inquire massage, the first device receives the conversation menu sent by the server according to the inquire massage; the first device sends a communication construction massage to the server based on the conversation menu, wherein the communication construction massage is that a massage server of the selected at least one communication function establishes communication between the first device and the user corresponding to the second user identifier according to the selected at least one communication function; or, the first device establishes communication with the user corresponding to the second user identifier according to the selected at least one communication function. Meanwhile, a device, a server and a system are provided by the invention, in order to solve technical problems that in the prior art, leakage of contact information leads to personal information leakage of a user, benefits of the user are damaged, application and development of technologies are affected. Thus, protection of personal information of a user is achieved, and technical application and development are promoted.
Owner:HUAWEI TECH CO LTD
Vehicle movement method with privacy protection and server
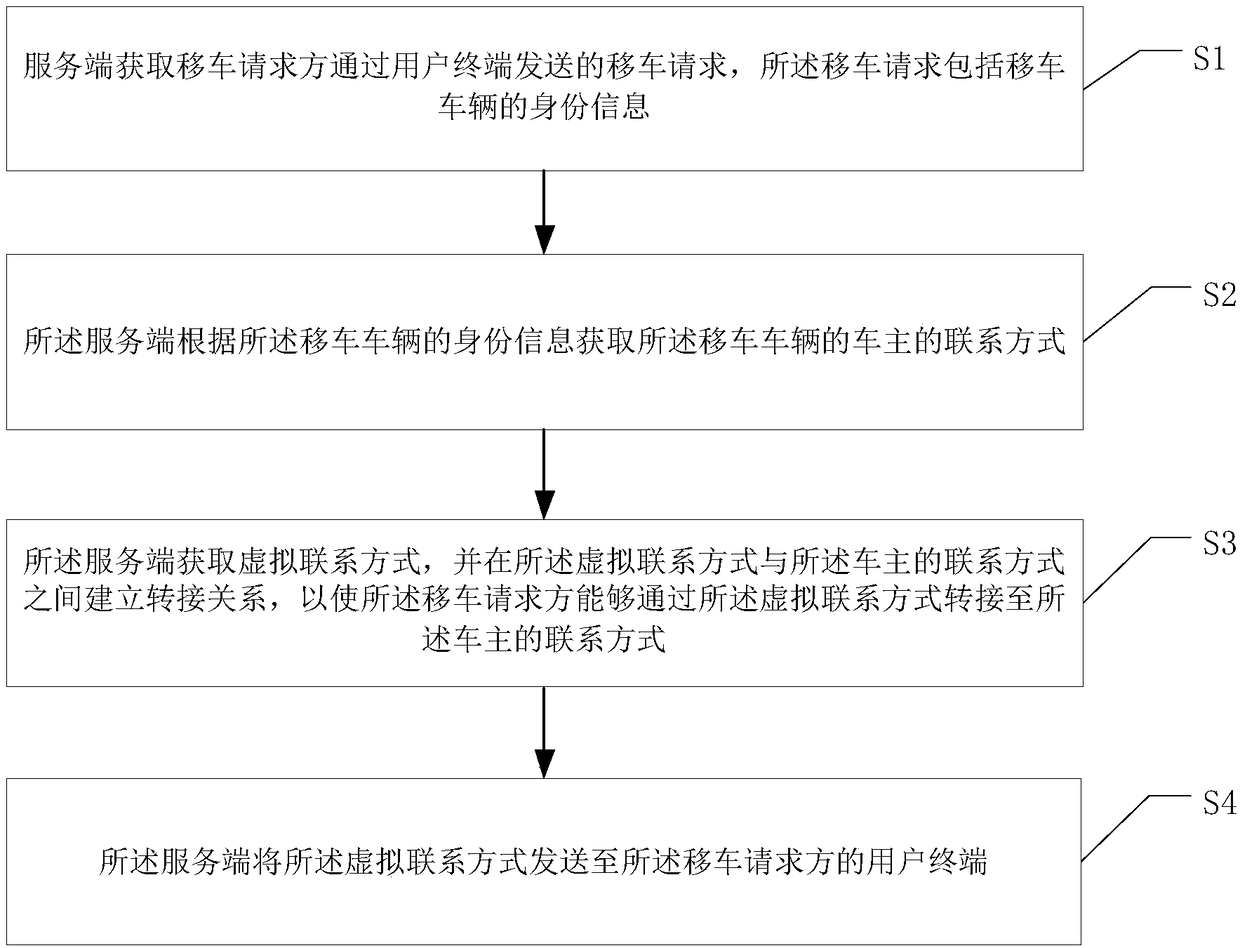
InactiveCN108848277AProtection of personal informationSpecial service for subscribersContact methodPrivacy protection
The invention discloses a vehicle movement method with privacy protection and a server. The vehicle movement method comprises the steps as follows: S1, the server acquires a vehicle movement request sent by a vehicle movement requester via a user terminal, wherein the vehicle movement request comprises identity information of a vehicle moving vehicle; S2, the server acquires a contact mode of thevehicle owner of the vehicle moving vehicle according to the identity information of the vehicle moving vehicle; S3, the server acquires a virtual contact mode and builds a switching mode between thevirtual contact mode and the contact mode of the vehicle owner, and thus the vehicle movement requester can be switched to the contact mode of the vehicle owner from the virtual contact mode; and S4,the server sends the virtual contact mode to the user terminal of the vehicle movement requester. According to the vehicle movement method provided by the invention, the vehicle movement requester cancontact the vehicle owner without acquiring the contact mode of the vehicle owner, and thus personal information of the vehicle owner can be effectively protected, and the method is convenient and quick.
Owner:愉悦时代(北京)科技有限公司
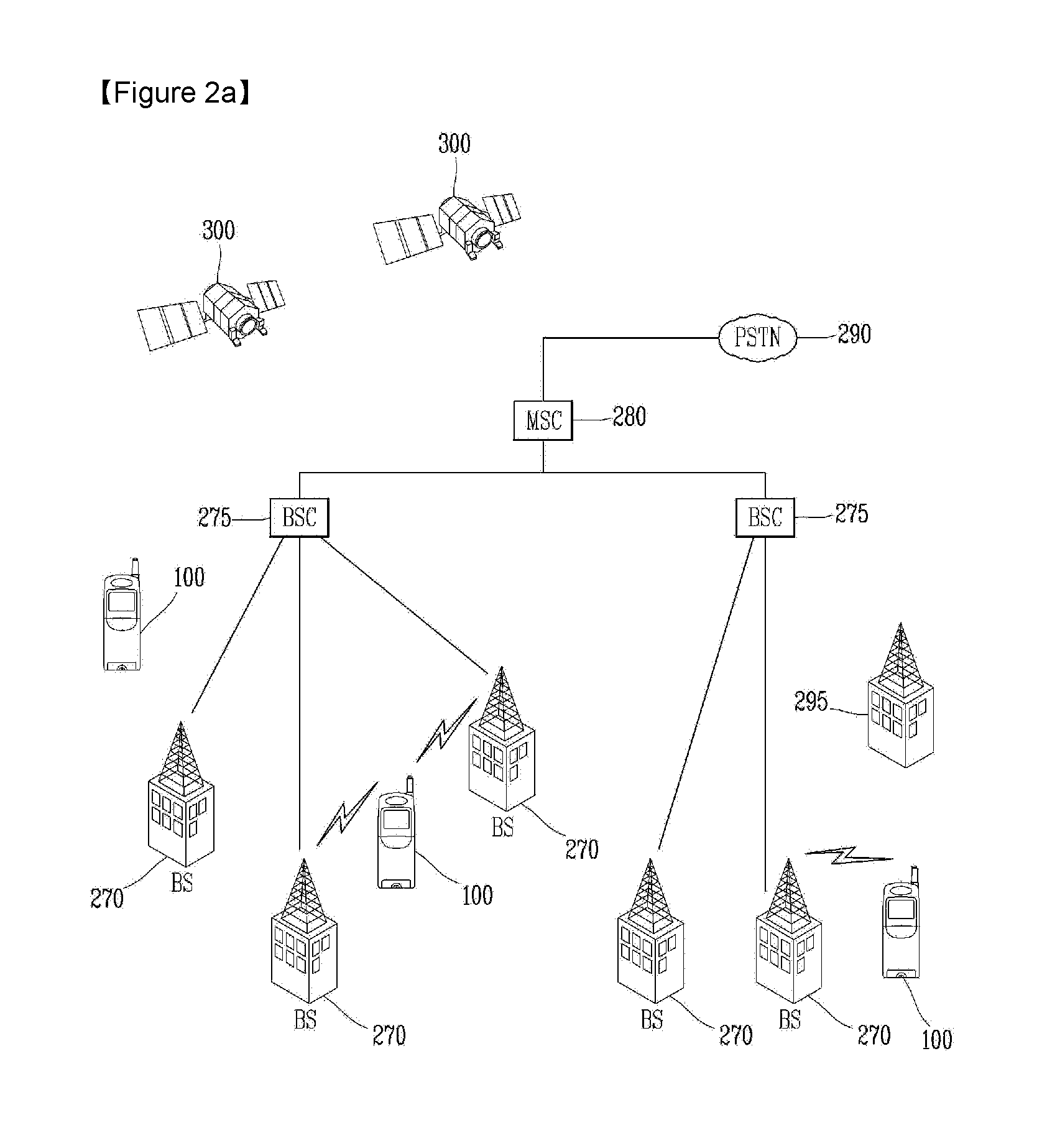
Method for transmitting and receiving data in mobile terminal and mobile terminal using the same
InactiveUS20110009101A1Protection of personal informationSpecial service for subscribersSubstation equipmentWeb siteCommunication unit
A method of controlling a mobile terminal, the method including displaying, via a display on the mobile terminal, a list of contacts included on the mobile terminal, selecting, via an input unit on the mobile terminal, a first contact included in the list of contacts, accessing, via a wireless communication unit, a web site corresponding to the first contact, displaying, on the display, a list of contacts of the first contact included on the web site corresponding to the first contact without displaying personal contact information for the list of contacts of the first contact, selecting, via the input unit, a second contact from the list of contacts of the first contact, displaying, via the display, a plurality of options for communicating with the second contact without displaying personal contact information of the second contact that is used for communicating with the second contact, selecting, via the input unit, one of the plurality of options for communicating with the second contact, and communicating, via the wireless communication unit, with the second contact via the selected communication option without displaying the personal contact information that is used for communicating with the second contact.
Owner:LG ELECTRONICS INC
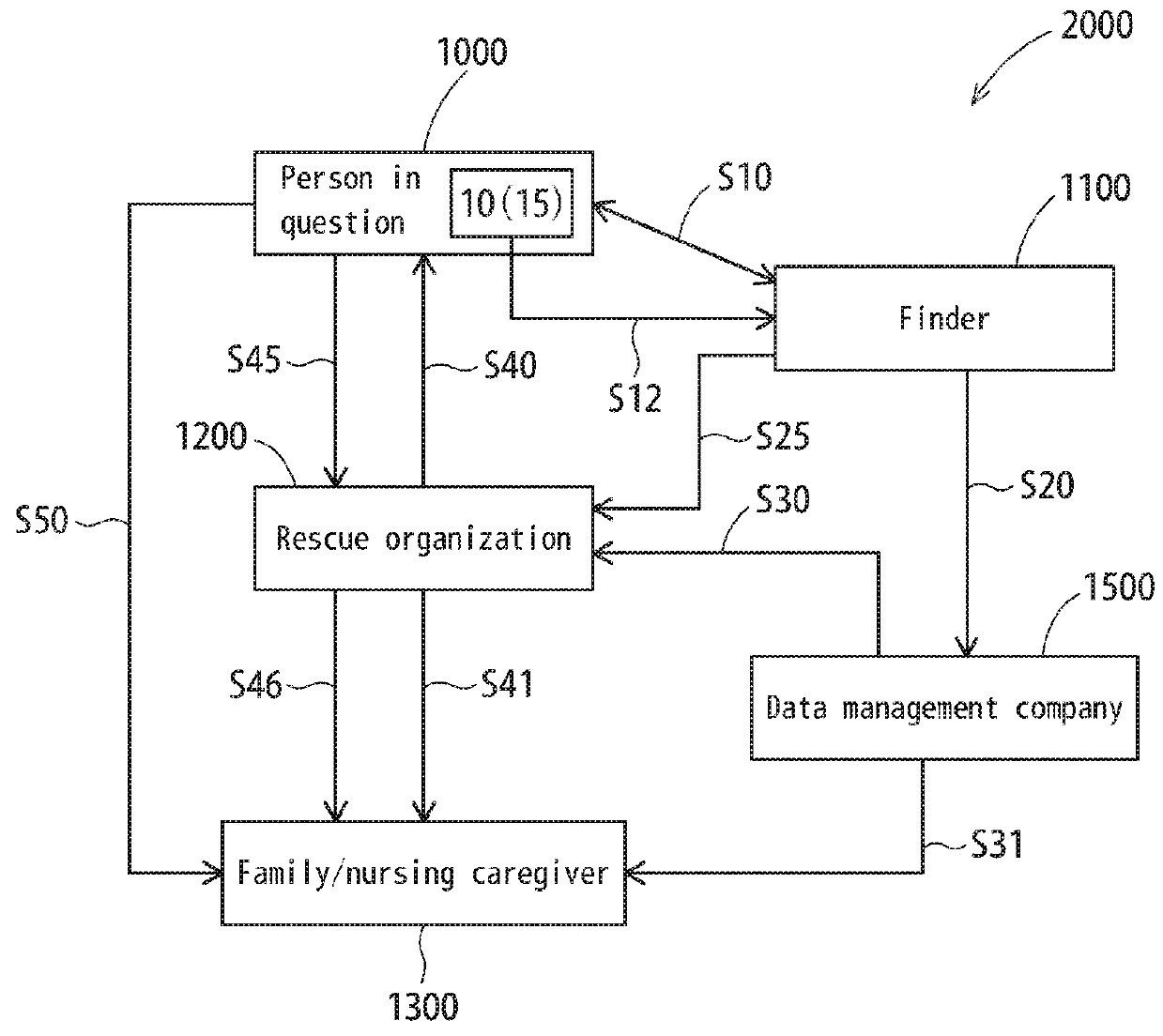
Rescue Method, Rescue System, Wandering Person Care Method, And Wandering Person Care System
ActiveUS20180096579A1Easy to manageLow costMedical communicationDiagnostic recording/measuringSystem of careData management
A rescue method for identifying and rescuing a person in question, the rescue method comprising an operation in which a user wearing a jewelry item having a serial number is encountered and the serial number on the jewelry item is recognized, an operation in which the serial number is conveyed to a data management company that stores the serial number as identification information pertaining to the user, an operation in which the identification information pertaining to the user is conveyed to a rescue organization, and an operation in which a command to rescue the user is issued at the rescue organization.
Owner:COLAN TOTTE CO LTD
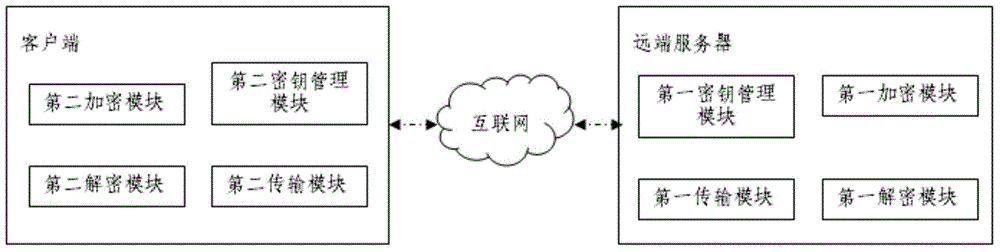
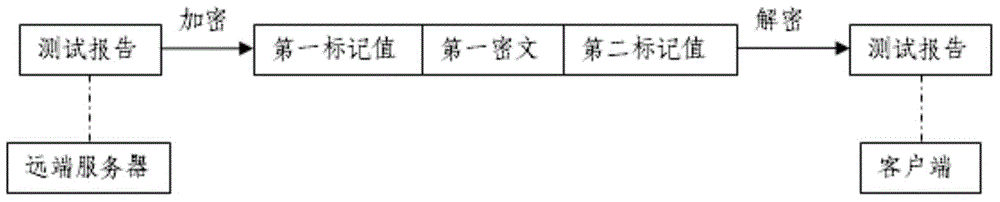
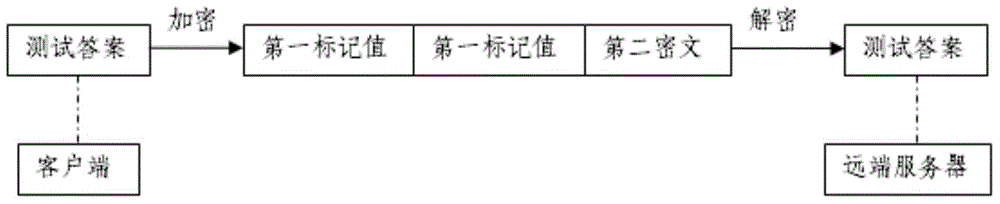
Cognitive ability test value encryption and transmission method based on internet
The invention relates to a cognitive ability test value encryption and transmission method based on the internet. The method at least comprises the steps that a first secret key management module in which at least one secret key pair is prestored randomly generates a first mark value representing an encryption secret key when a far-end server encrypts the generated test report; a first encryption module in which at least one encryption algorithm is prestored converts the test report into a first cryptograph according to the encryption algorithm randomly selected by the first encryption module and the first mark value, and the encryption module is provided with second mark values corresponding to the encryption algorithms in a one-to-one way; the first cryptograph, the first mark value and the second mark values are transmitted to a client terminal via a first transmission module; and the client terminal converts the first cryptograph into a plaintext test report according to the first mark value and the second mark values.
Owner:BEIJING HUANDU INST OF WISDOM MIND TECH LTD
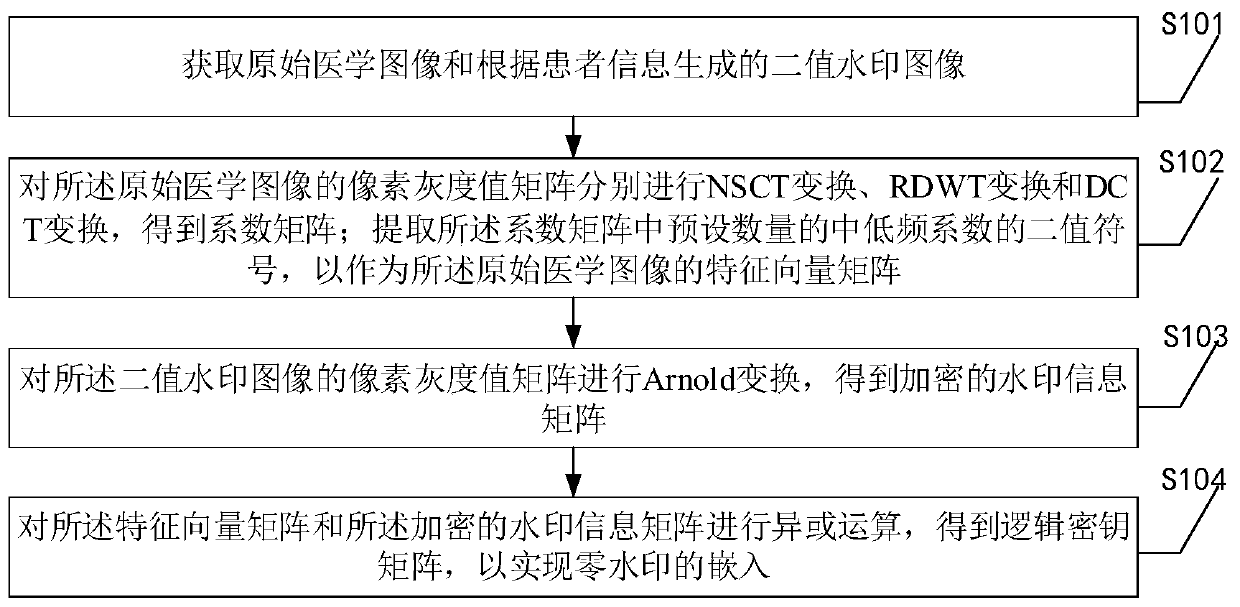
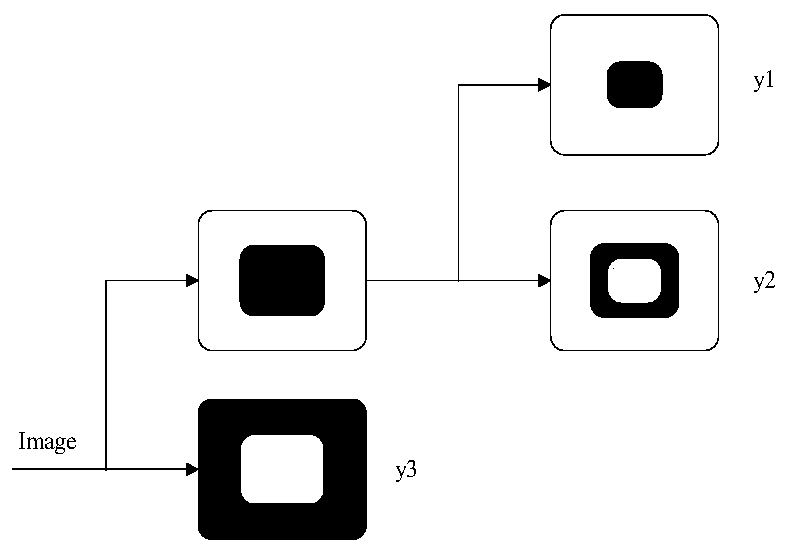
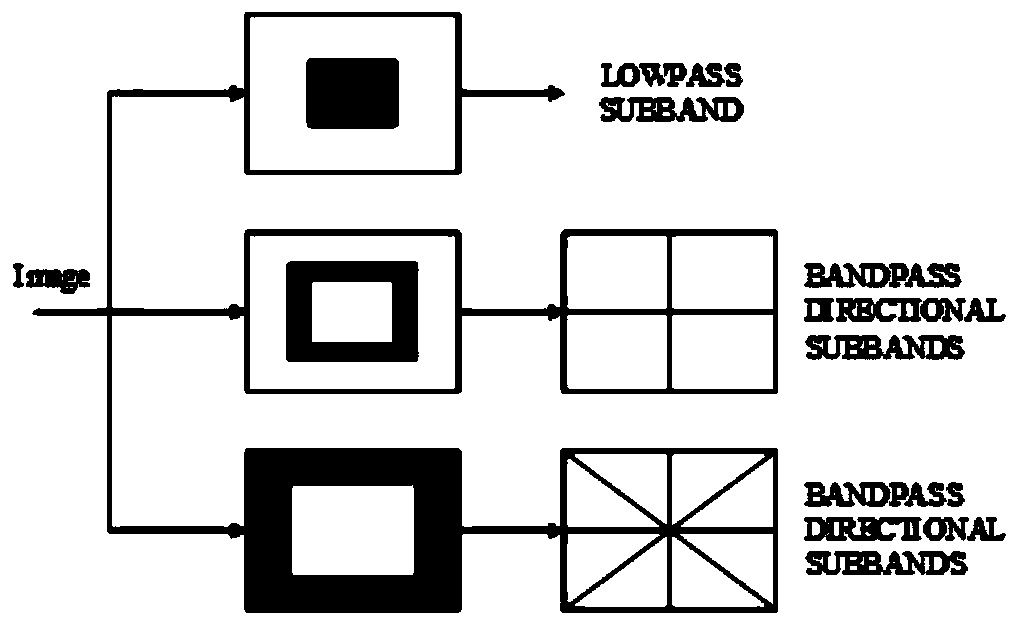
Medical image zero-watermark embedding method based on NSCT combined transformation
ActiveCN110517182AImplement embeddingIntegrity guaranteedImage watermarkingMedical imagesFeature vectorArnold transformation
The invention discloses a medical image zero-watermark embedding method and device based on NSCT combination transformation, equipment and a readable storage medium. The scheme is implemented on the basis of hybrid transformation and Arnold transformation of NSCT, RDWT and DCT, and in the watermark embedding process, firstly, a more robust medical image feature vector is extracted in combination with the NSCT, the RDWT and the DCT so as to resist geometric attacks. Secondly, the watermark is encrypted by utilizing Arnold transformation, so that the security of watermark information is enhanced; and finally, watermark embedding is realized by using a zero watermark technology, so that the integrity, the watermark capacity and the invisibility of the medical image are ensured, the defect oforiginal image data modification caused by a traditional watermark embedding technology is avoided, and the quality of the medical image is ensured. Therefore, even if the patient information is attacked intentionally or unintentionally, the medical image and the watermark cannot be cracked as long as the unauthorized user does not know the secret key, so that the personal information of the patient is truly protected.
Owner:HAINAN UNIVERSITY
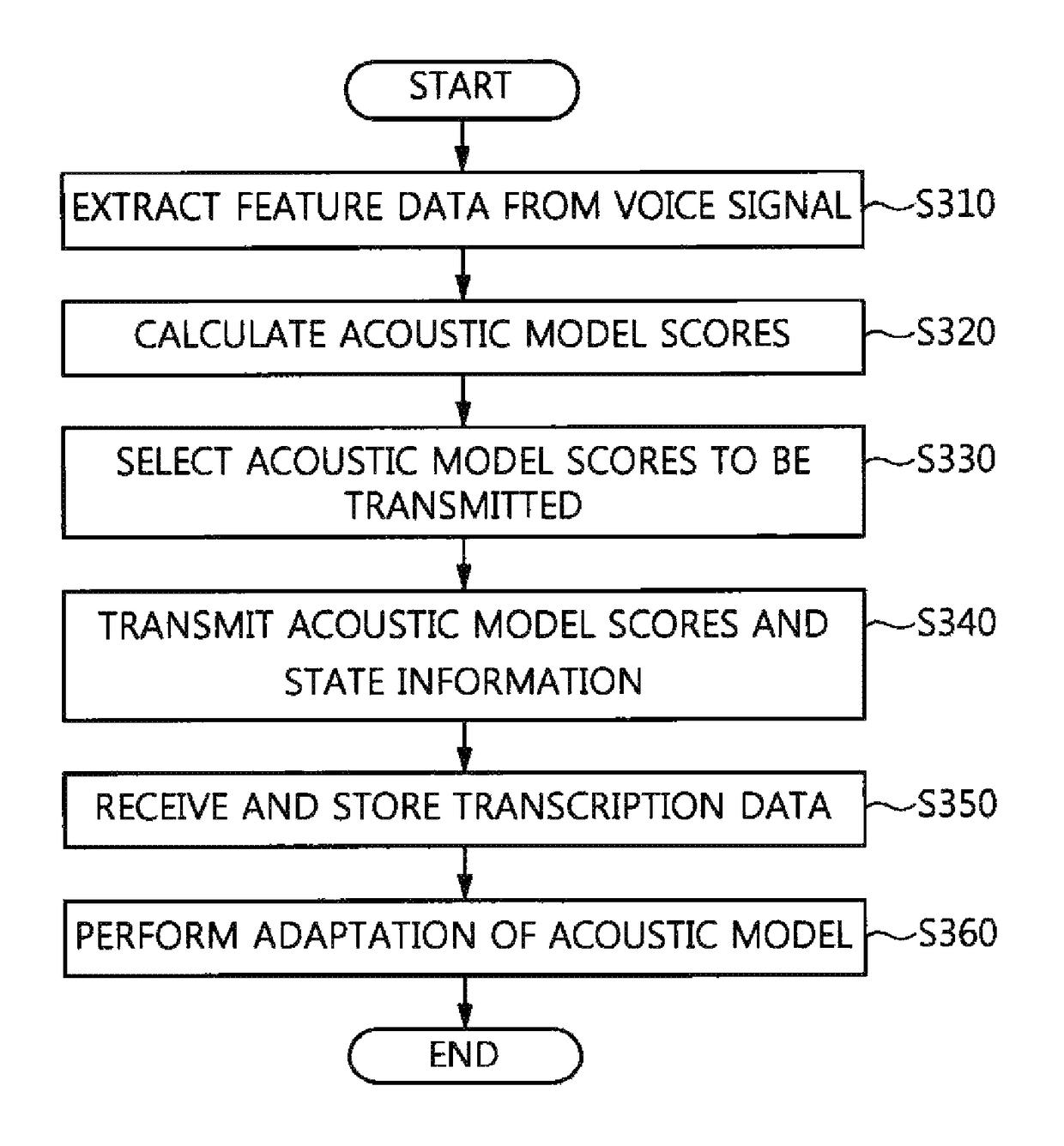
Voice recognition terminal, voice recognition server, and voice recognition method for performing personalized voice recognition
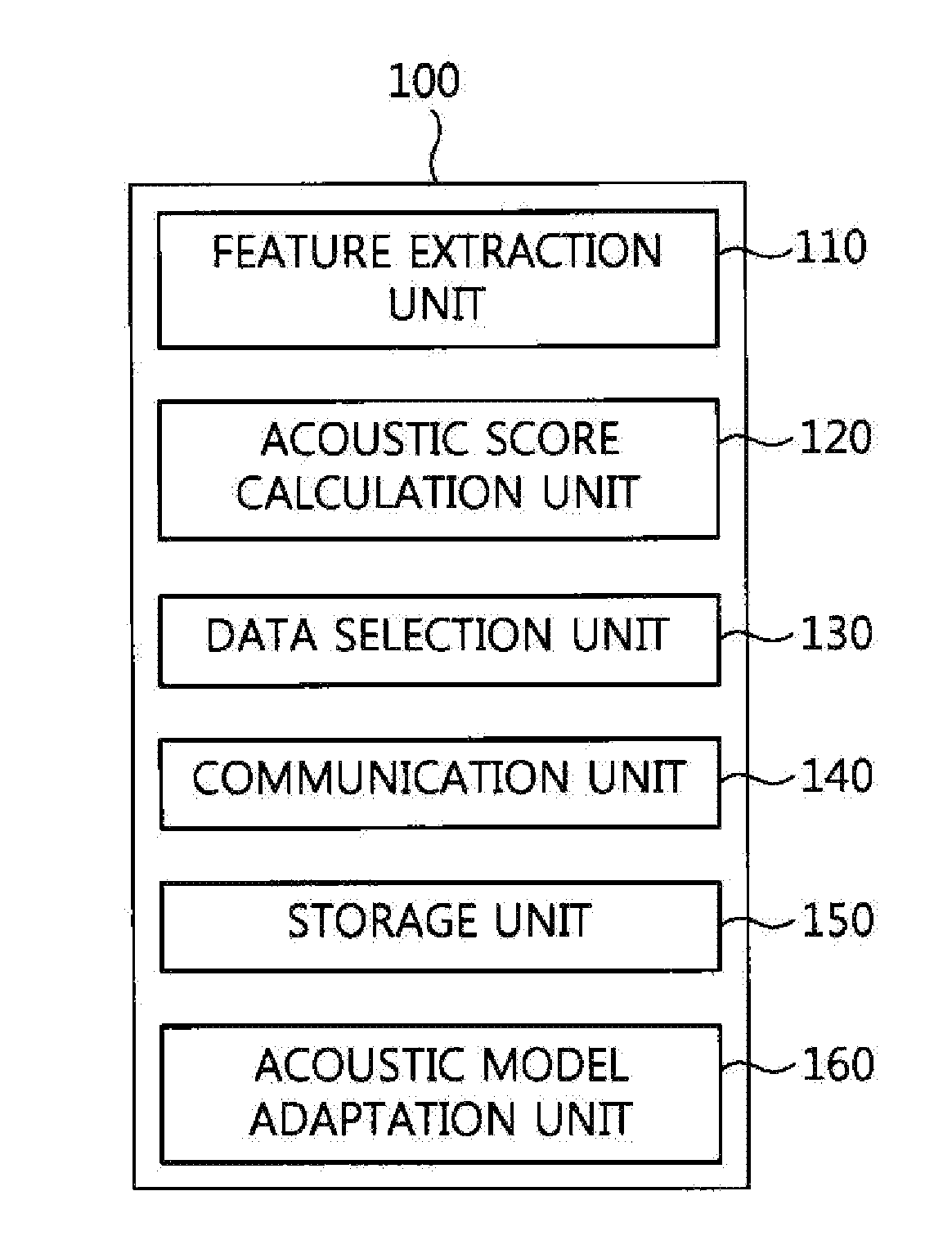
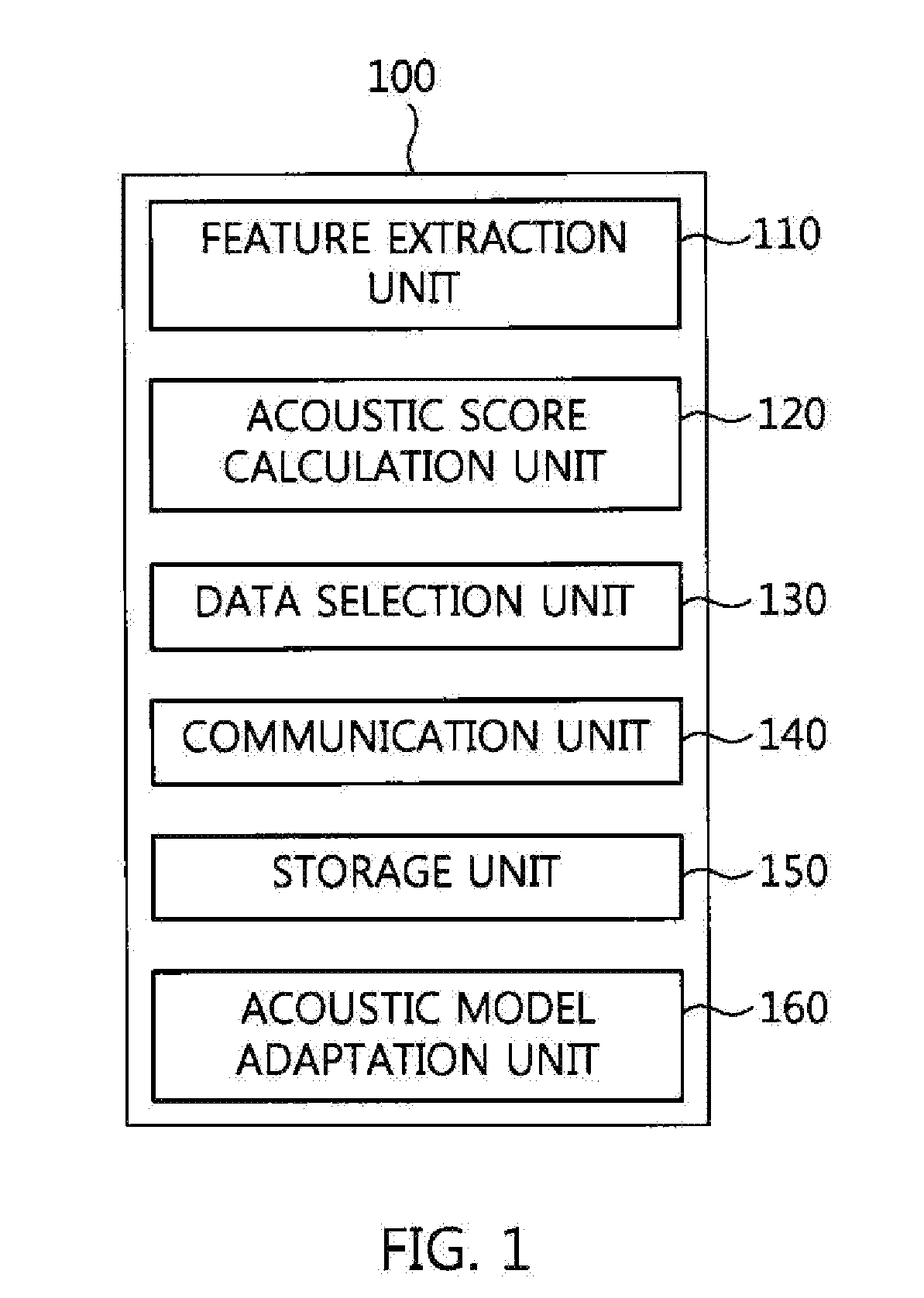
ActiveUS10079022B2Protection of personal informationReduce computing loadSpeech recognitionMultiple fluid pressure valves simultaneous measurementCommunication unitFeature extraction
A voice recognition terminal, a voice recognition server, and a voice recognition method for performing personalized voice recognition. The voice recognition terminal includes a feature extraction unit for extracting feature data from an input voice signal, an acoustic score calculation unit for calculating acoustic model scores using the feature data, and a communication unit for transmitting the acoustic model scores and state information to a voice recognition server in units of one or more frames, and receiving transcription data from the voice recognition server, wherein the transcription data is recognized using a calculated path of a language network when the voice recognition server calculates the path of the language network using the acoustic model scores.
Owner:ELECTRONICS & TELECOMM RES INST
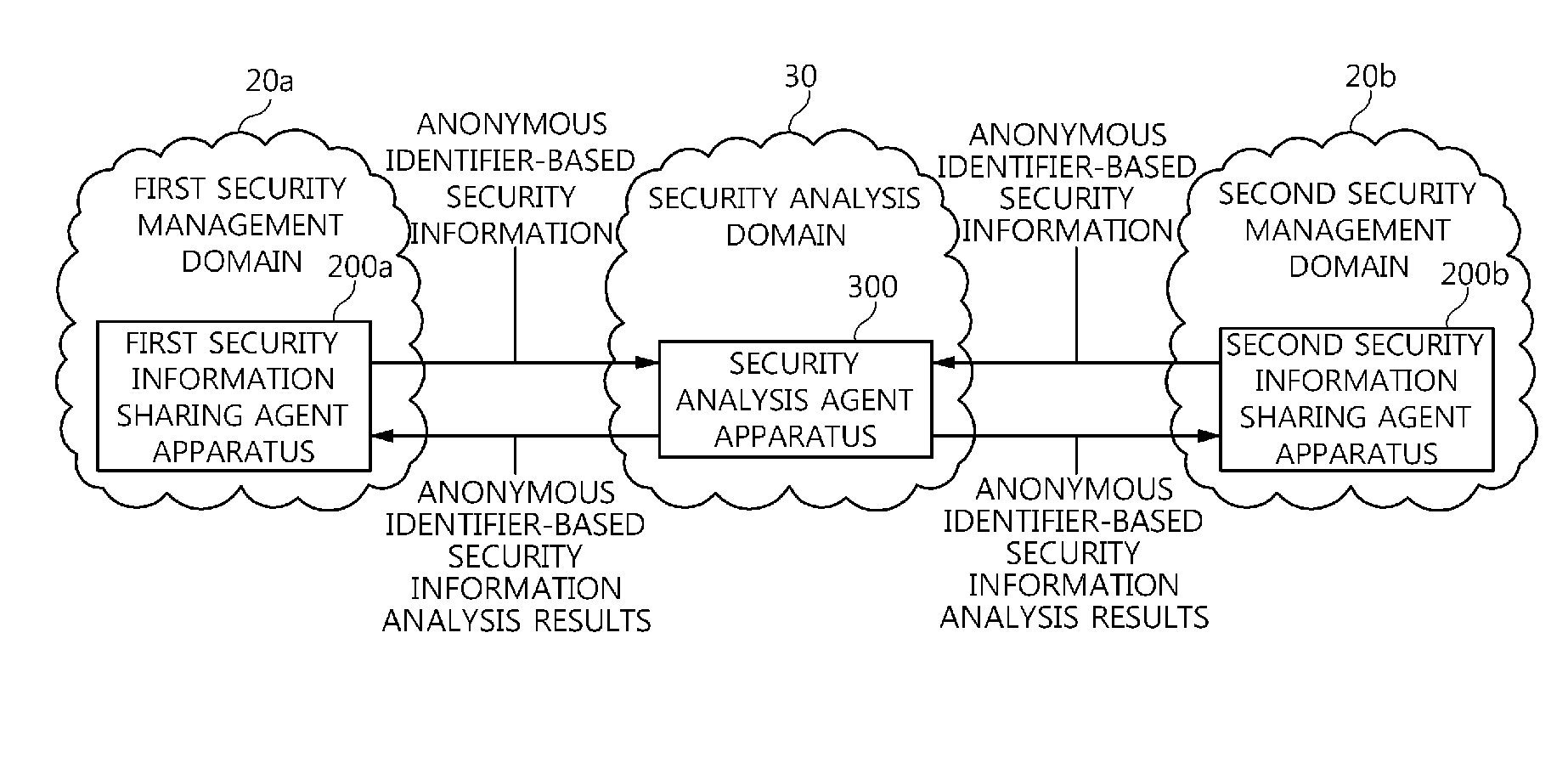
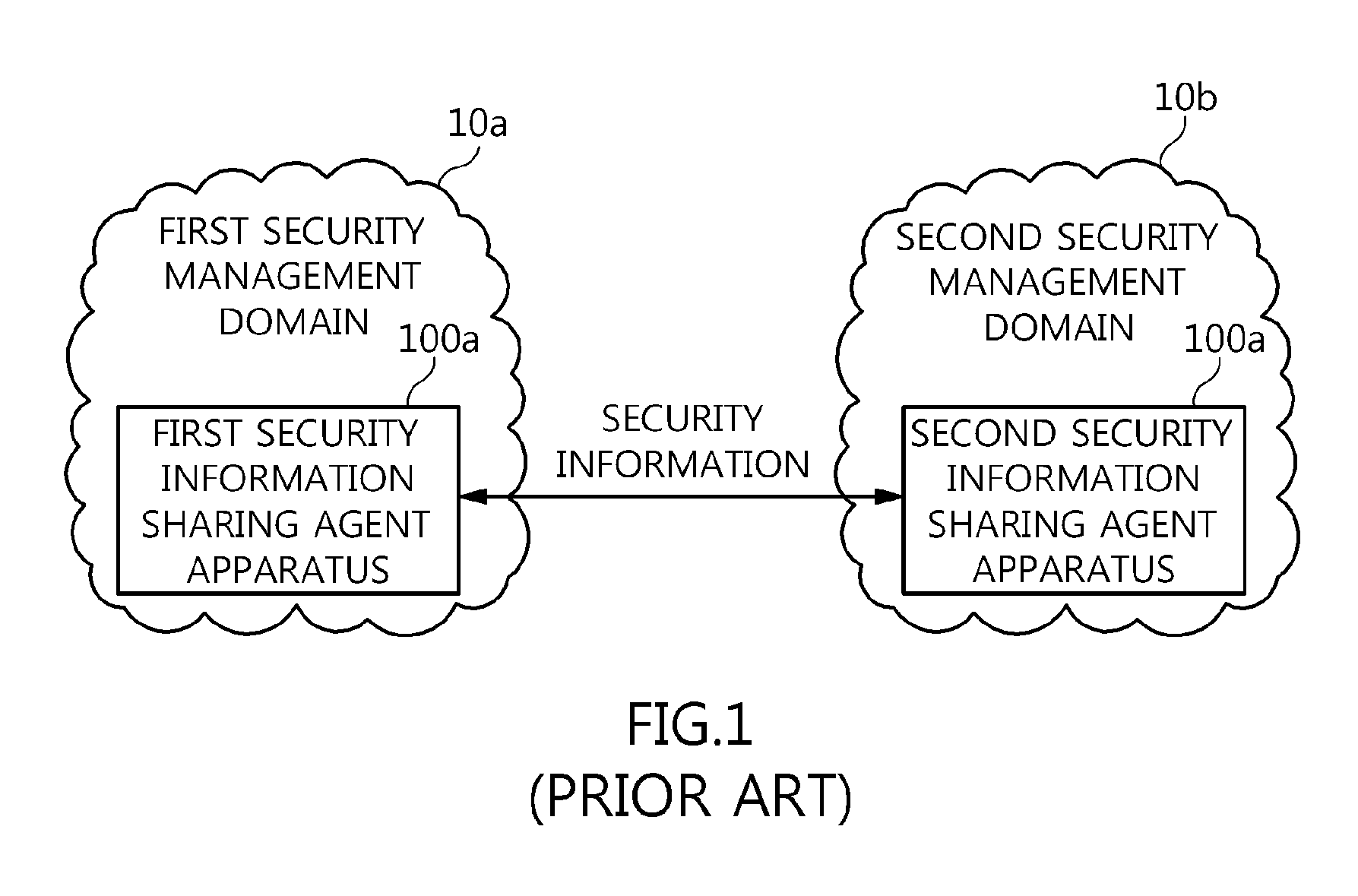
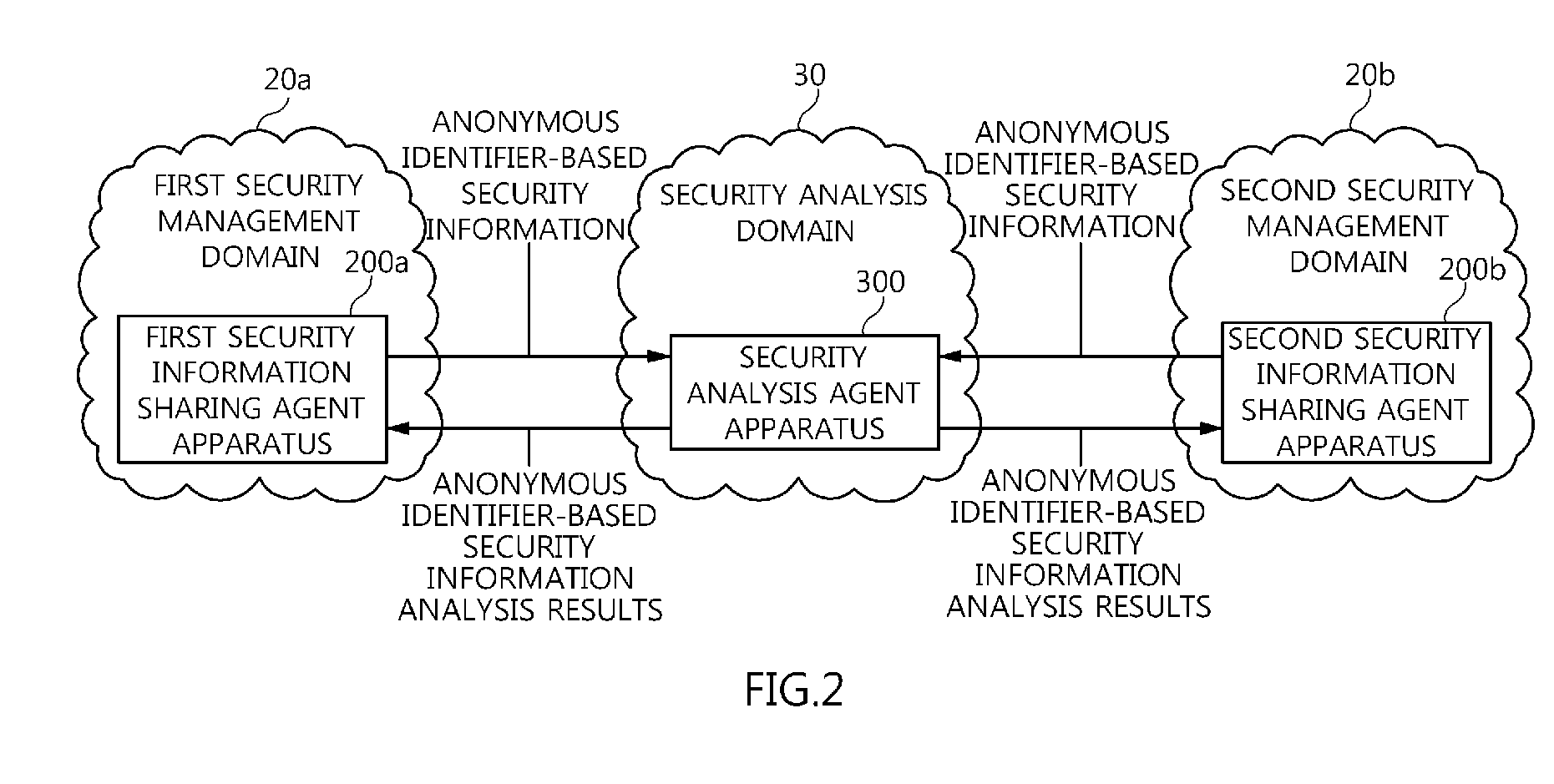
Agent apparatus and method for sharing anonymous identifier-based security information among security management domains
ActiveUS8789200B2Prevent leakageProtection of personal informationDigital data processing detailsUser identity/authority verificationCommunication unitInternet privacy
The present invention relates to an agent apparatus and method for sharing anonymous identifier-based security information among security management domains. A plurality of security information sharing agent apparatuses respectively located in a plurality of security management domains and configured to collect security information and transmit collected security information to outside of the security management domains. Each security information sharing agent apparatus includes an identifier conversion unit for converting real name identifier-based security information into anonymous identifier-based security information by converting a real name identifier included in the security information into an anonymous identifier, and a security information communication unit for transmitting the anonymous identifier-based security information obtained by the identifier conversion unit to outside of a corresponding security management domain so that security information is shared among the plurality of security management domains.
Owner:ELECTRONICS & TELECOMM RES INST
Method of authenticating password and portable device thereof
InactiveUS9165132B2Increased complexityProtection of personal informationDigital data processing detailsUnauthorized memory use protectionPasswordCipher
A method of authenticating a password and a portable device thereof are provided. The method includes: displaying an input keyboard on which a plurality of objects are arranged; changing an object arranged on the input keyboard according to a manipulation of a user; and if an object pattern arranged in a designated position of the input keyboard corresponds to a preset password pattern, authenticating the user. Therefore, it is difficult to use artifacts on the display screen to trace a password after entry, and thus security is improved. As a result, a protection of personal information of a user is strengthened.
Owner:SAMSUNG ELECTRONICS CO LTD
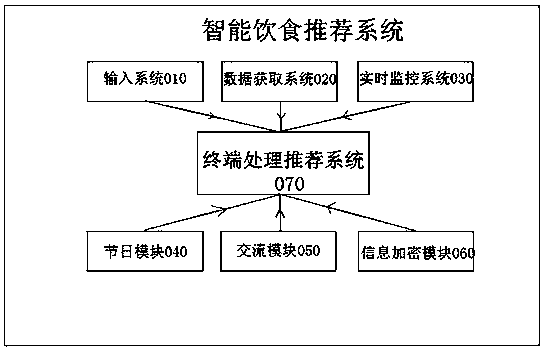
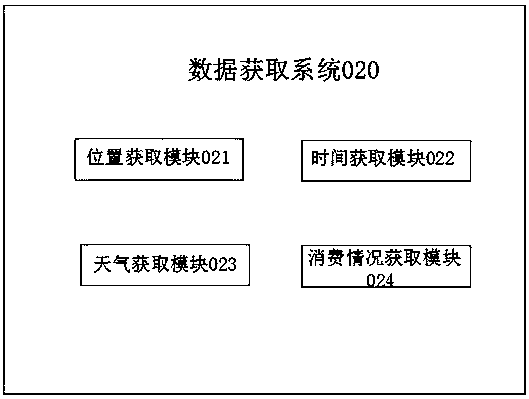
Intelligent diet recommending system
InactiveCN110164526AImprove quality of life and physical healthProtection of personal informationNutrition controlBody conditionUser state
The invention discloses an intelligent diet recommending system which comprises an input system, a data acquisition system, a real-time monitoring system and a terminal processing recommending system.The input system is used for actively inputting self original data by a user and establishes a user database according to the original data. The data acquisition system is used for acquiring the particular information and the real-time geographical information of the user. The real-time monitoring system is used for monitoring the user state in real time, wherein the user state comprises a user body condition and a diet condition. The terminal processing recommending system is used for connecting with the input system, the data acquisition system and the real-time monitoring system, comprehensively processes the information transmitted from the systems, establishes a user diet state database and recommends most suitable diet data to the user. Through setting the system, the diet which satisfies a body requirement can be effectively recommended to the user.
Owner:吴静
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com