Privacy protection mobile service recommendation method, client and recommendation system
A technology for privacy protection and service recommendation, which is applied in the field of privacy protection network service recommendation methods and recommendation systems, can solve the problems of incompatibility between user privacy protection and recommendation service quality, and achieve the effect of maintaining recommendation accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
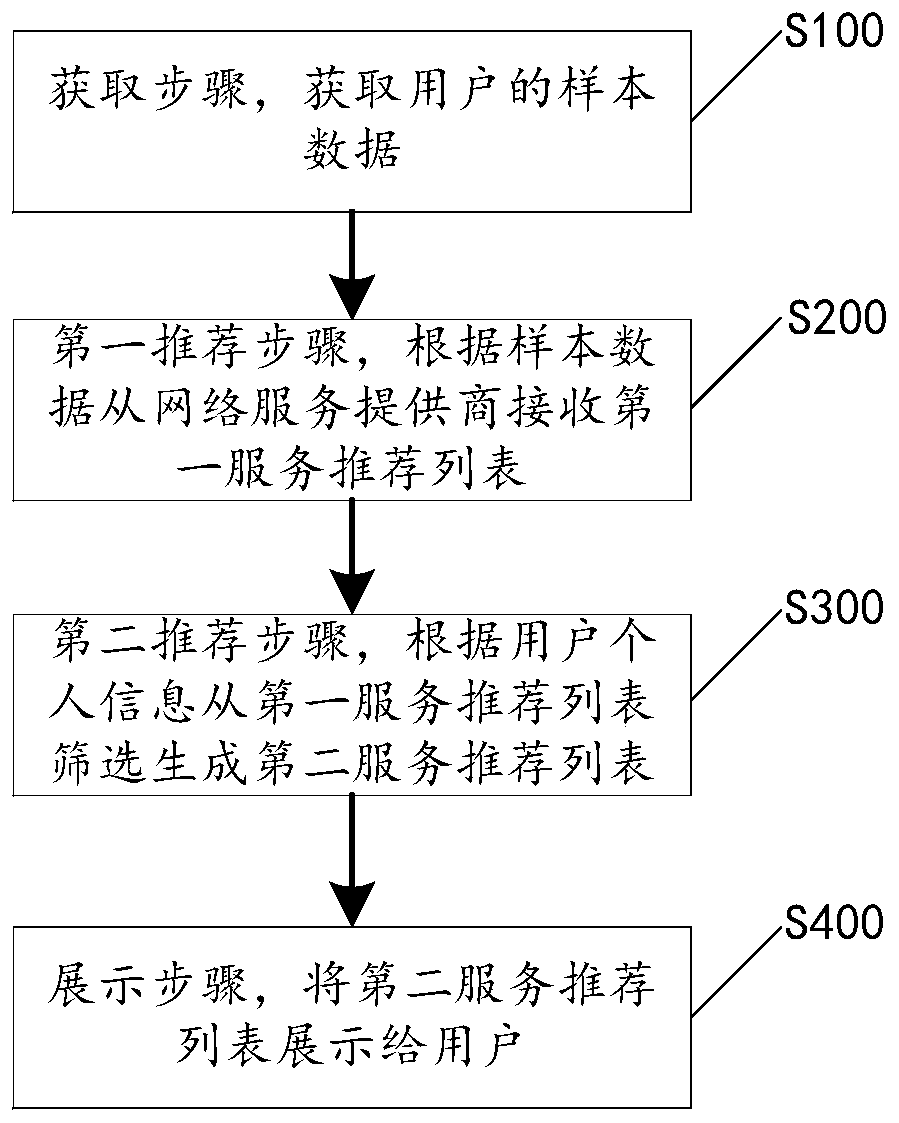
[0033] Please refer to figure 1 , the present application discloses a method for recommending privacy-protected mobile services, which mainly includes steps S100-S400, which will be described respectively below.
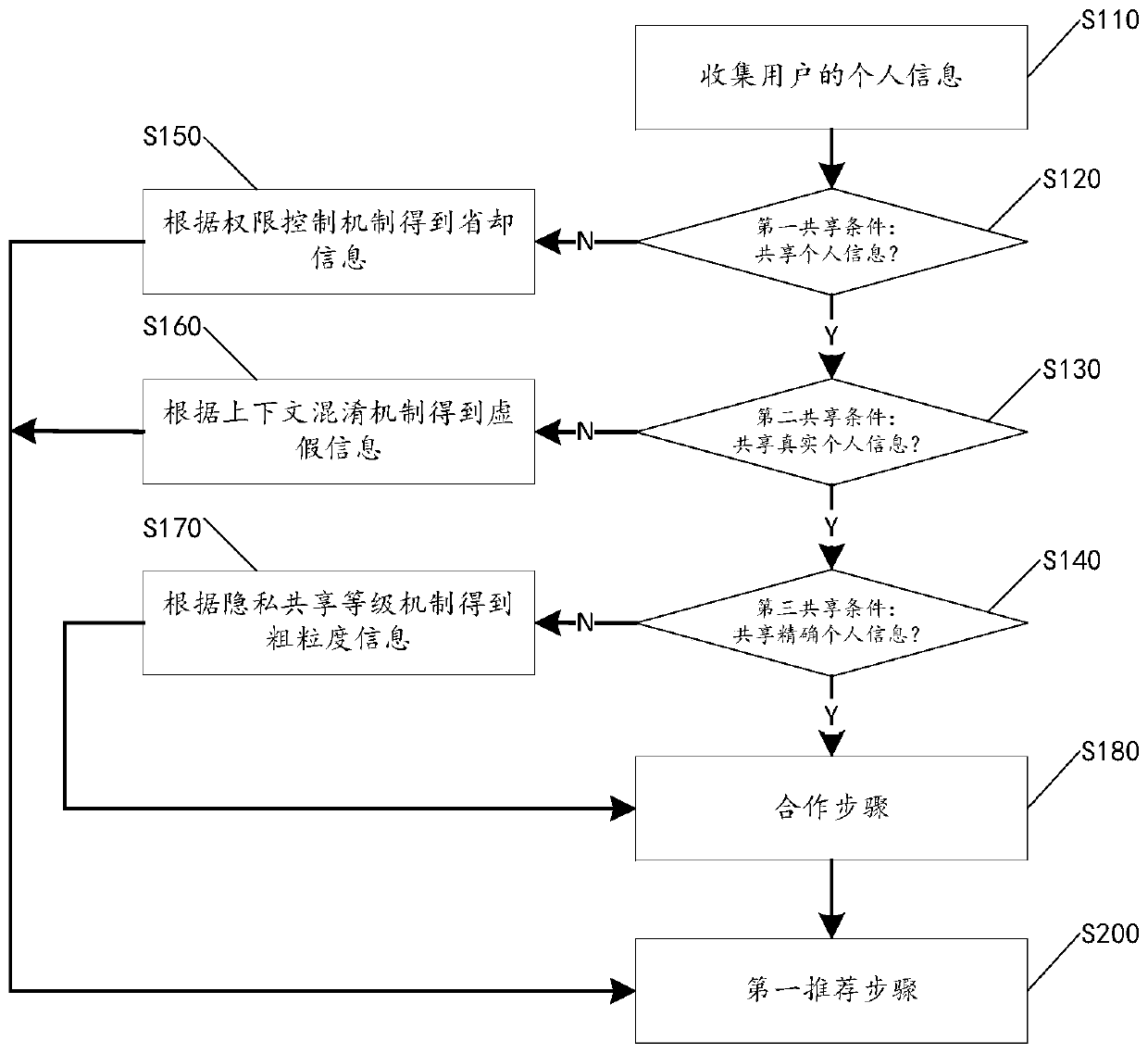
[0034] Step S100, namely the obtaining step, obtains sample data of the user, where the sample data is omission information, false information, coarse-grained information or fine-grained information of the user's personal information. In a specific example, see figure 2 , the step S100 may include steps S110-S180, which are respectively described as follows.
[0035] Step S110, collecting user's personal information. The user's personal information includes but is not limited to name, gender, age, country, language, sports hobbies, food hobbies, film and television hobbies, music hobbies, shopping interests, current geographical location, etc. The user's personal information can be preset in the user On the terminal device, it is enough to read the user's persona...
Embodiment 2
[0088] Please refer to Figure 4 , on the basis of the privacy protection mobile service recommendation method disclosed in Embodiment 1, this embodiment also discloses a recording step S500, which is located after step S400, which may include steps S510-S530, which will be described below.
[0089] Step S510, generating a click record in response to the user's click operation in the second service recommendation list, where the click record includes the access address of the clicked recommended item and the user's network identity information.
[0090]For example, after the user browses the second service recommendation list (such as a commodity purchase list) on the client device, he will often select a recommended item (such as one of the commodities) in the second service recommendation list to view, and at this time A click operation is generated through touch click, mouse click, gesture recognition, etc., then a click record will be generated, recording the access addres...
Embodiment 3
[0095] Please refer to Figure 5 , a privacy-protected client 6 in the present application, the client 6 mainly includes an acquisition unit 61 , a first recommendation unit 62 , a second recommendation unit 63 and a display unit 64 , which will be described separately below.
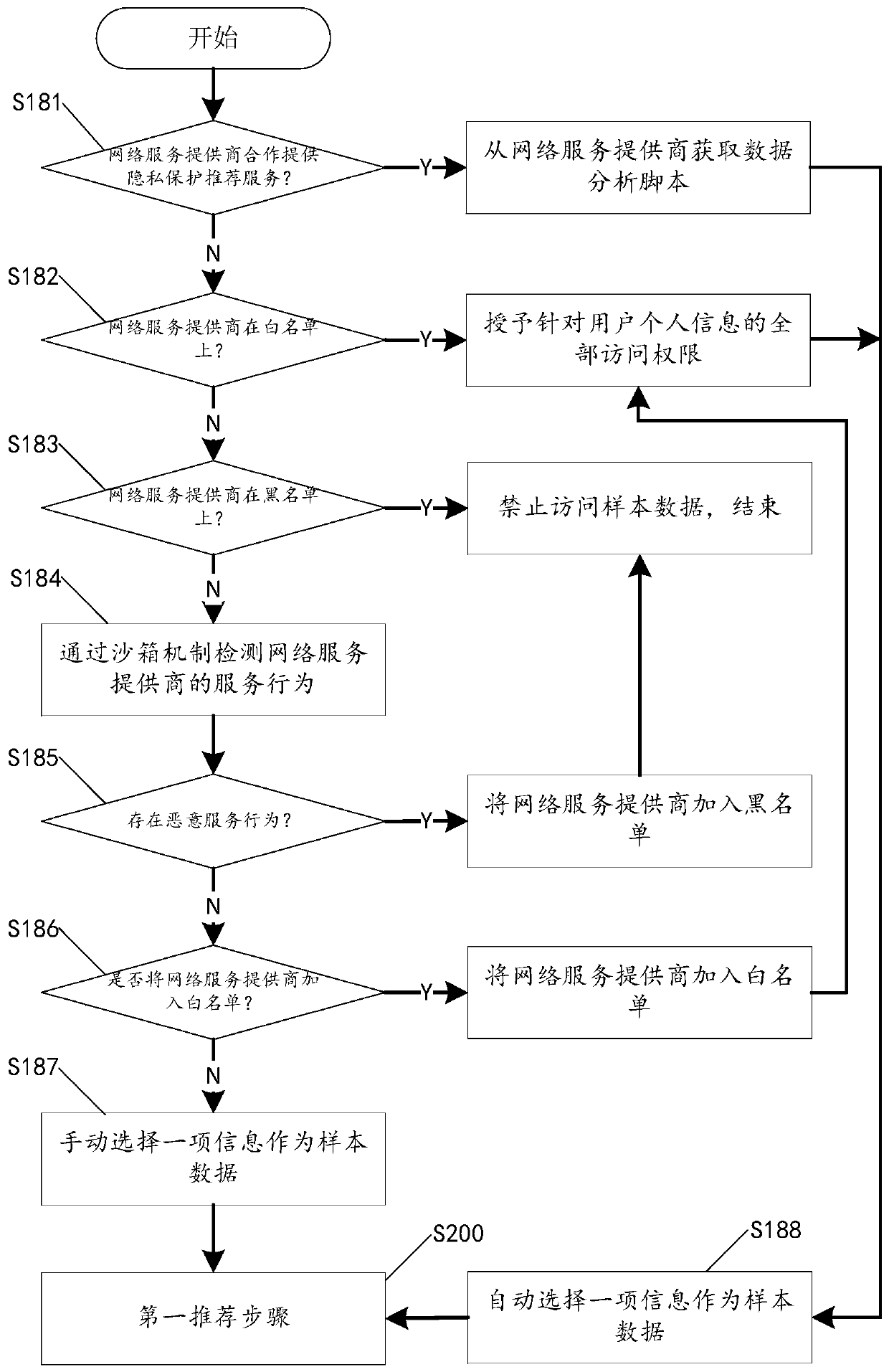
[0096] The obtaining unit 61 is used to obtain sample data of the user, where the sample data is omitted information, false information, coarse-grained information or fine-grained information of the user's personal information. In a specific embodiment, the acquisition unit 61 collects the personal information of the user on the client device, and selects and generates omitted information, false information or coarse-grained information according to a preset first mechanism; the first mechanism here includes: judging the personal information When the first sharing condition is not satisfied, the omission information is obtained according to the preset authority control mechanism; or, when the second sha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com