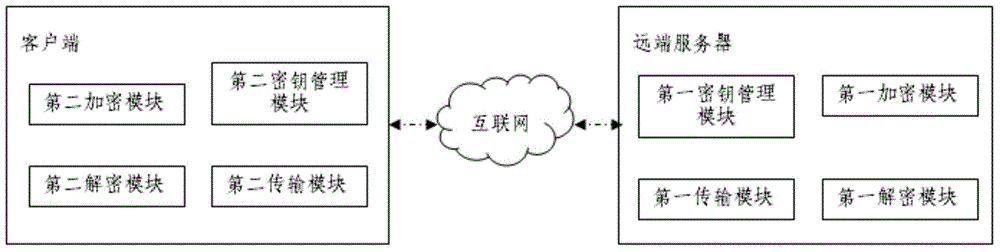
Cognitive ability test value encryption and transmission method based on internet
A transmission method and cognitive ability technology, which is applied in the field of Internet-based cognitive ability test value encryption and transmission, can solve the problems of no test answer and test result encryption and transmission, attack, and the lack of awareness of the importance of confidentiality, etc. Achieve the effects of increasing difficulty, ensuring confidentiality, and preventing viewing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
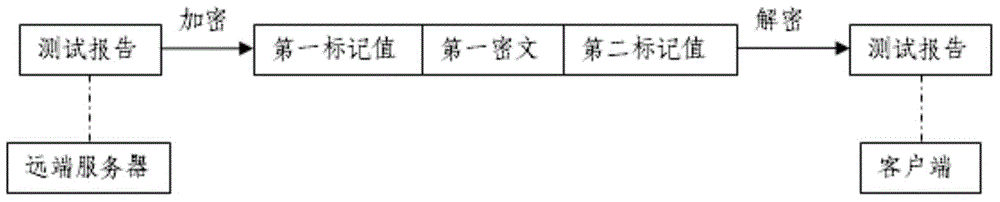
[0045] figure 2 It is a schematic diagram of a specific embodiment of the present invention. see figure 2 In this embodiment, after the remote server obtains the test report according to data analysis and processing, the first ciphertext is encrypted and sent to the client for decryption:
[0046] S01: The first key management module pre-stored with at least one key pair randomly generates a first tag value representing the encryption key;
[0047] S02: The first encryption module acquires an encryption key according to the first tag value, and at the same time, the first encryption module pre-stored with at least one encryption algorithm randomly selects an encryption algorithm. Then, the first encryption module encrypts the test report and generates the first ciphertext according to the selected encryption algorithm and encryption key;
[0048] S03: The first transmission module separately sends the first ciphertext and the first tag value and / or the second tag value to...
Embodiment 2
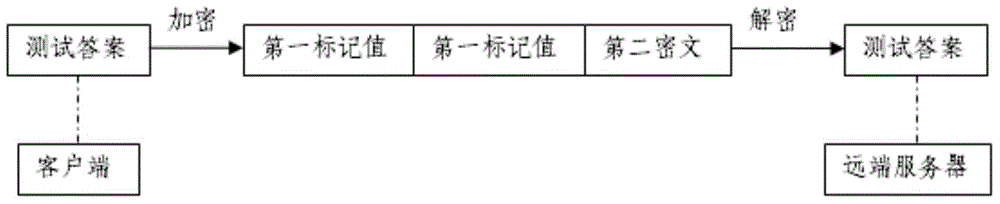
[0054] image 3 It is a schematic diagram of another specific embodiment of the present invention. see image 3 , the present embodiment is the case where the tester at the client end encrypts the test answer when performing the test, and the specific method steps of its encryption and transmission are as follows:
[0055] S01: The second key management module pre-stored with at least one key pair randomly generates a first tag value representing the encryption key;
[0056] S02: The second encryption module acquires an encryption key according to the first tag value, and at the same time, the second encryption module pre-stored with at least one encryption algorithm randomly selects an encryption algorithm. Then, the first encryption module encrypts the test report according to the selected encryption algorithm and encryption key to generate a second ciphertext.
[0057] During the testing process by the tester, the test answer of each test module is individually encrypted...
Embodiment 3
[0064] This embodiment is applicable to the case where the client encrypts the test answer and then sends it to the remote server. The difference between this embodiment and Embodiment 2 is that the encryption algorithm used is the ECC algorithm. This embodiment is based on embodiment 2, and the method for encrypting and transmitting the test answer specifically also includes:
[0065] S01: After the tester completes each test module, combine the test answers of each test module, use the ECC algorithm to encrypt the combined test answers to generate a second ciphertext, and generate a random number. Alternatively, the test answer of each test module is encrypted with an ECC algorithm and combined to generate a second ciphertext, and the test answer of each test module is encrypted to generate a random integer. The ECC algorithm is a cryptosystem based on the discrete logarithm problem of the elliptic curve. Given a point P on the elliptic curve and a certificate k, it is easy ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com