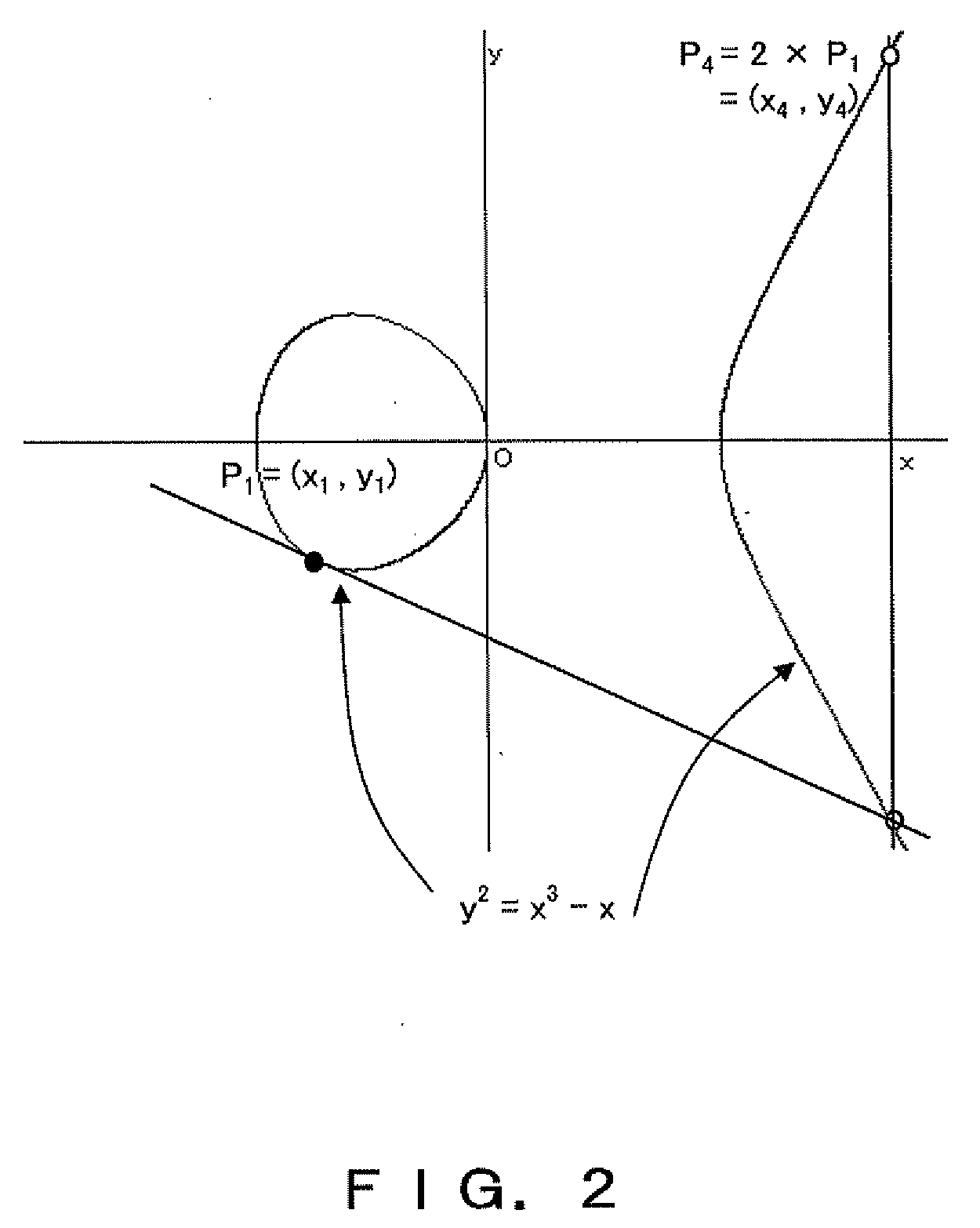Patents
Literature
149 results about "Random choice" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
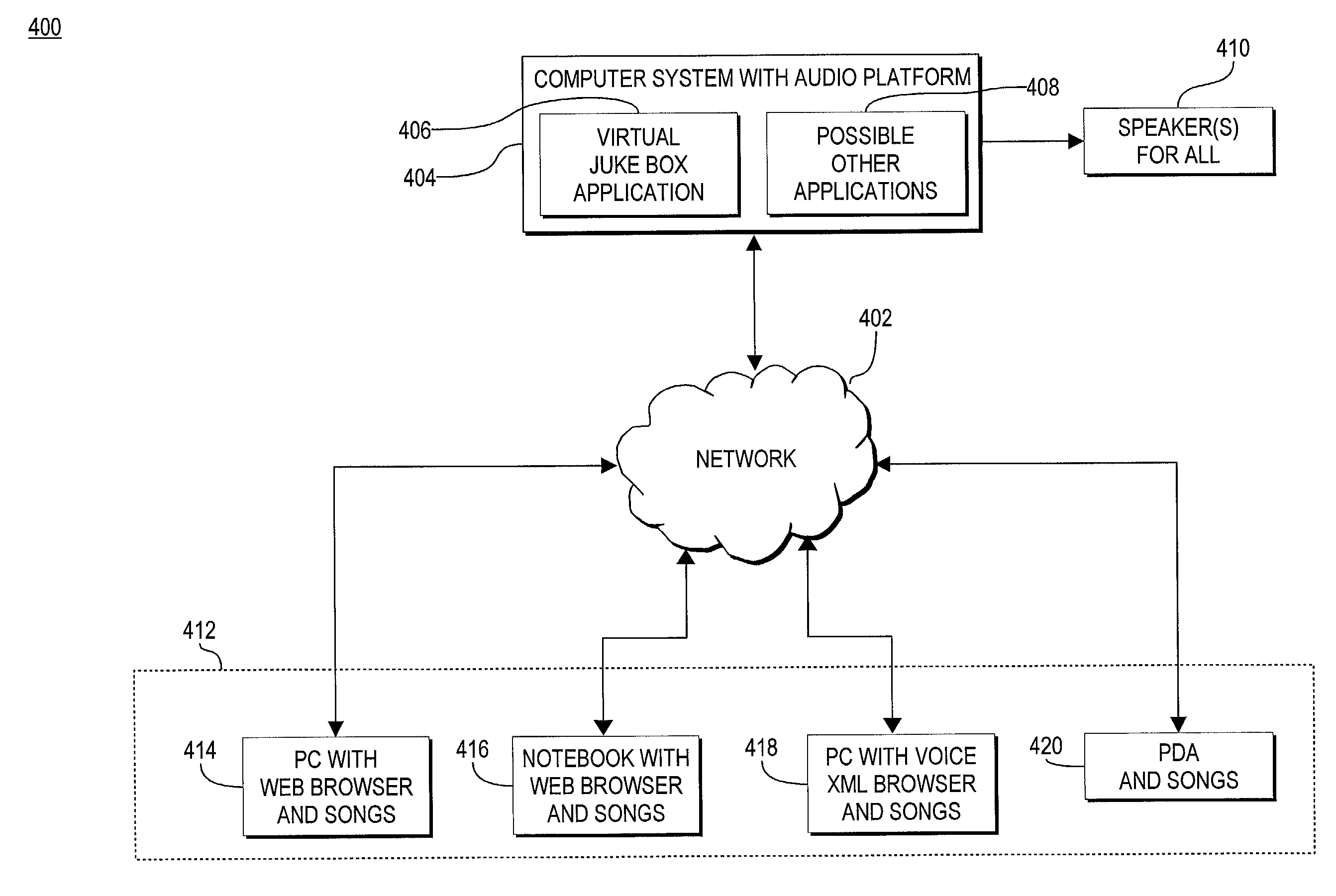
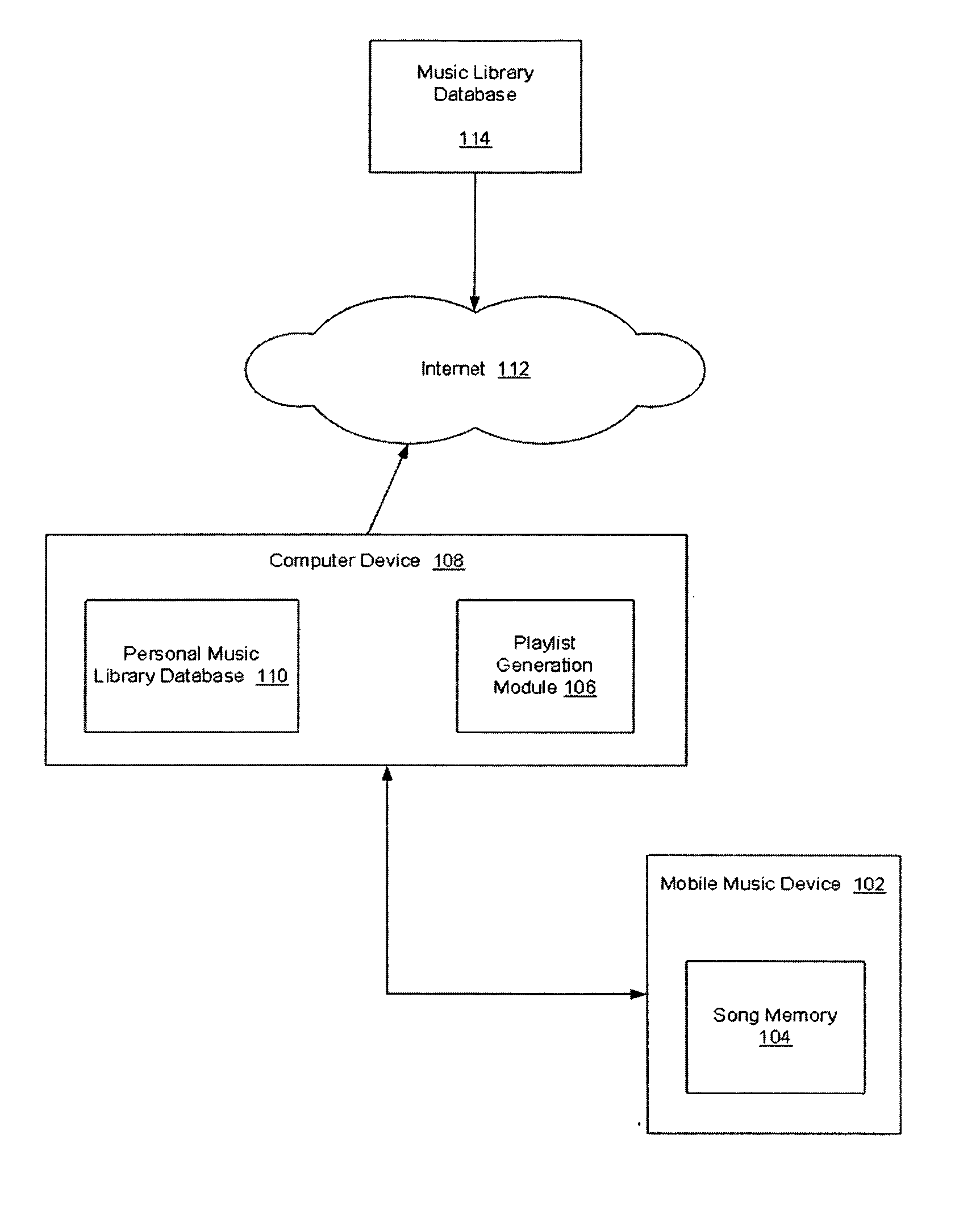
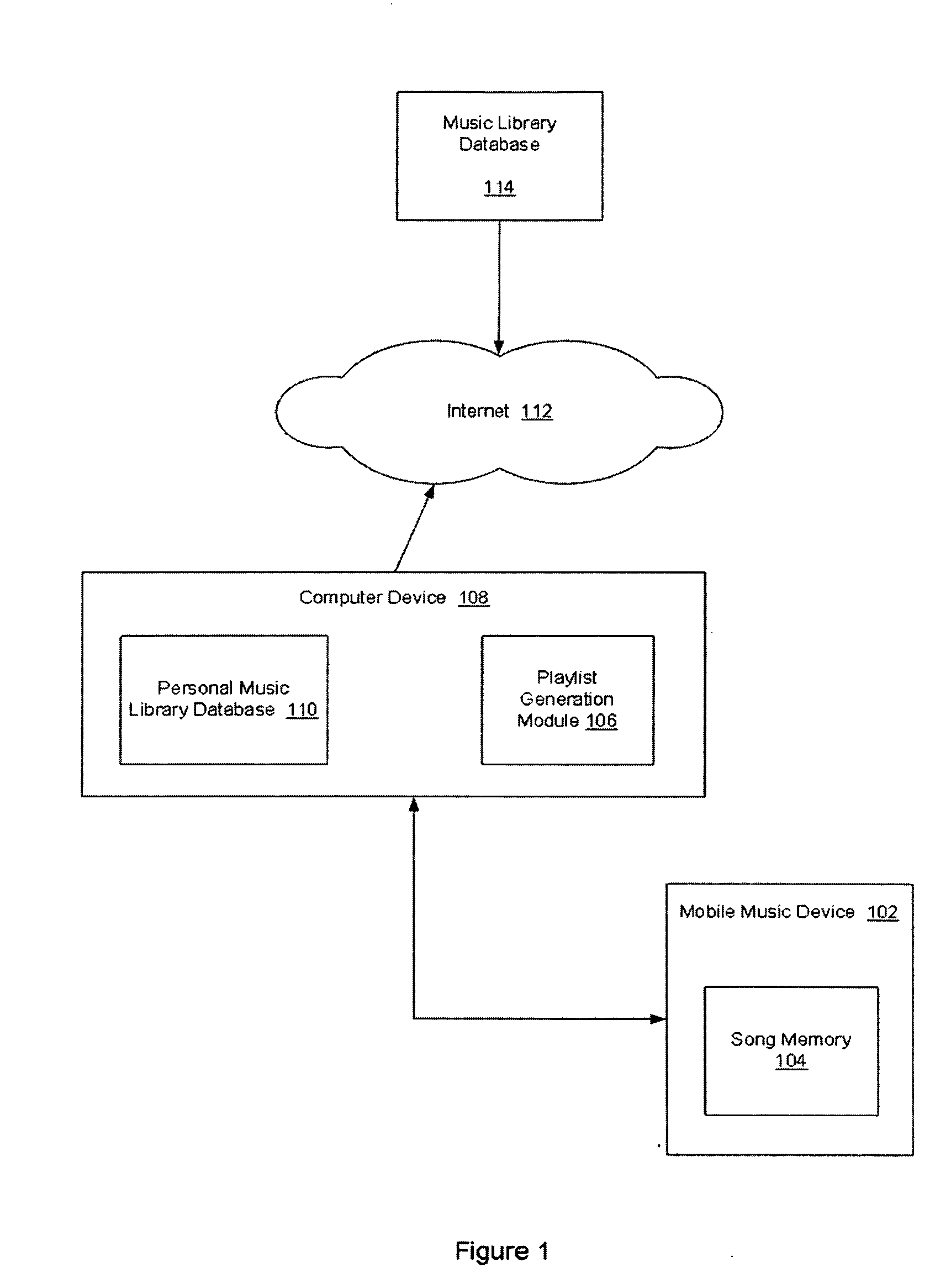
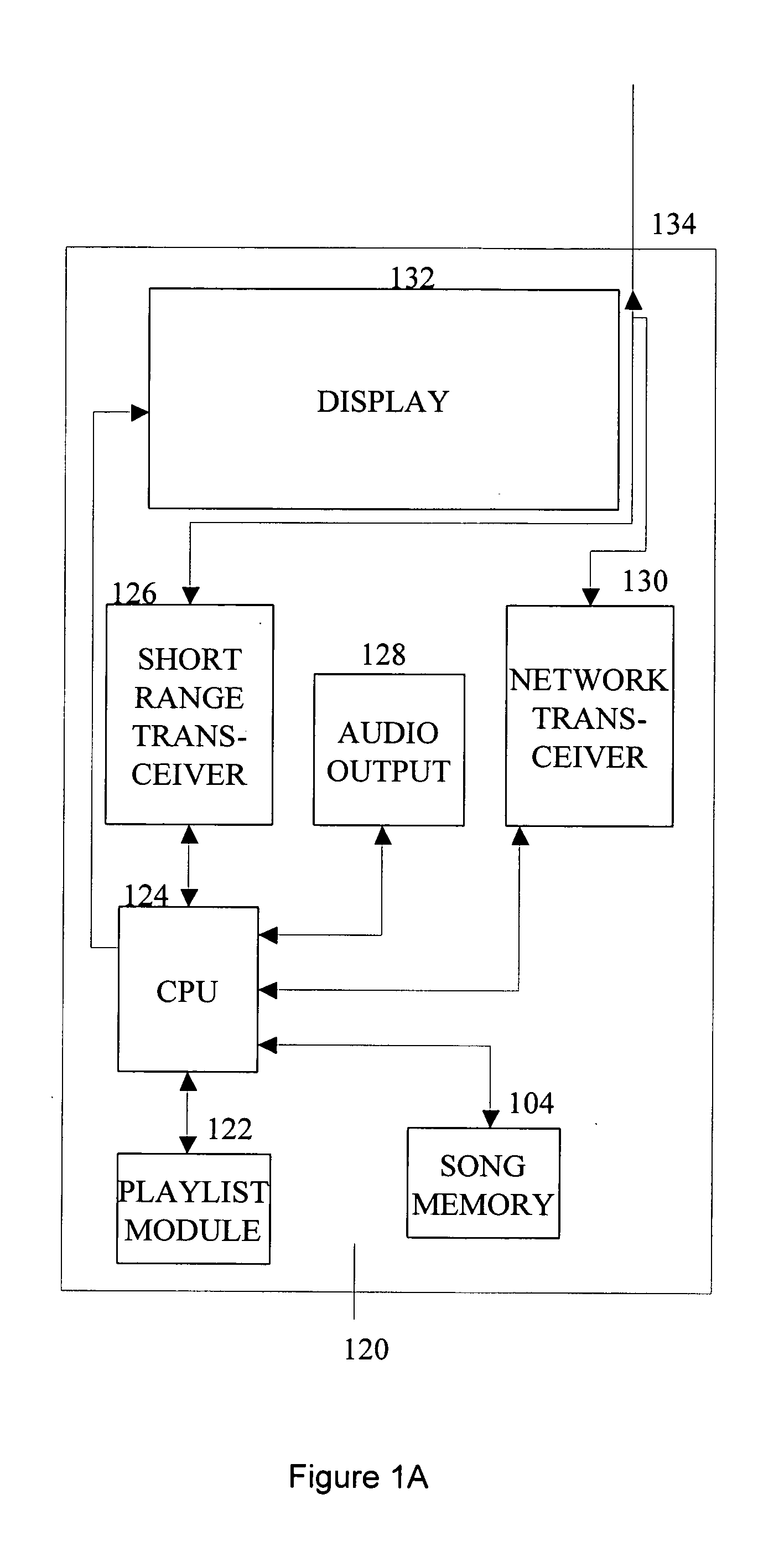
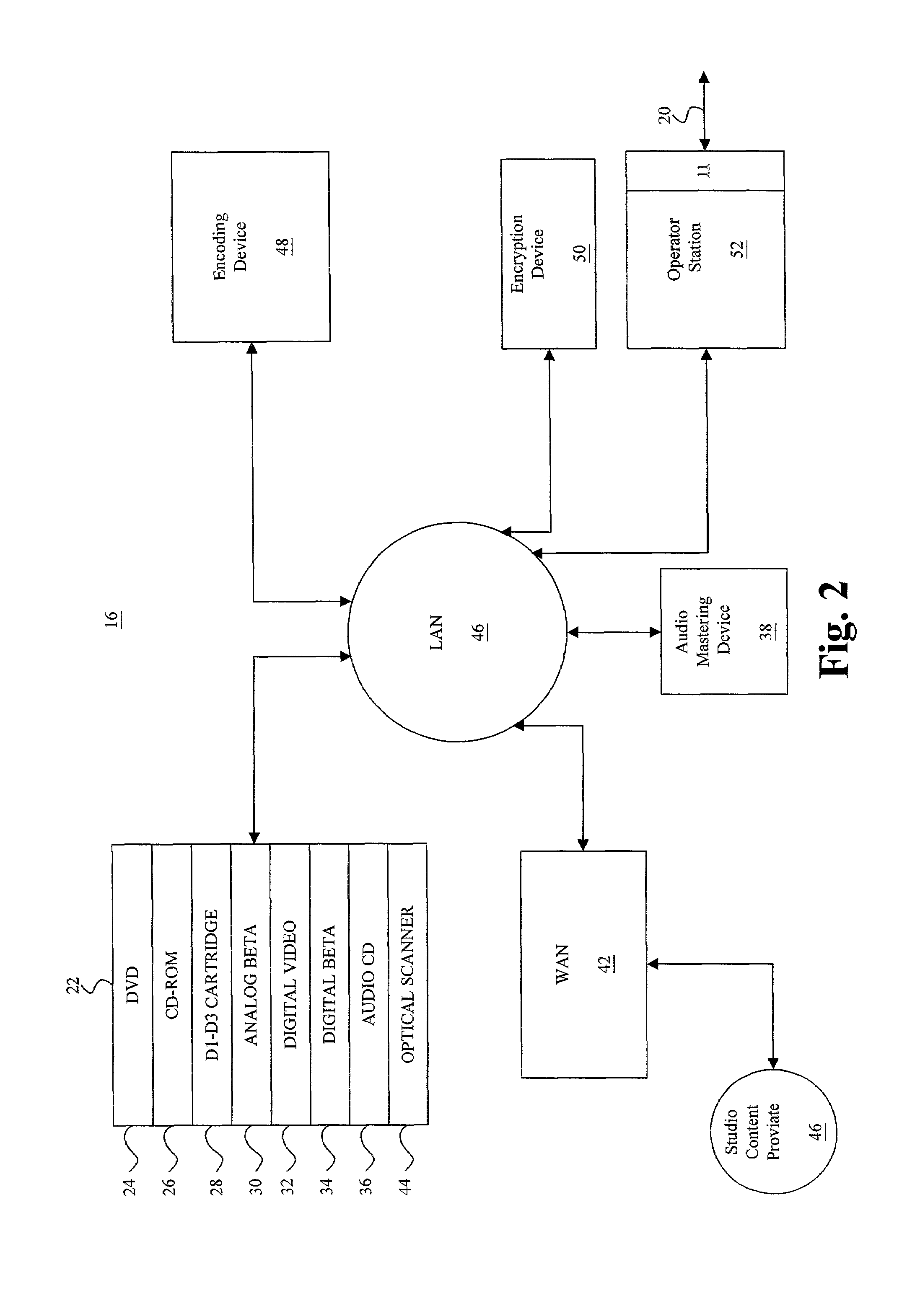
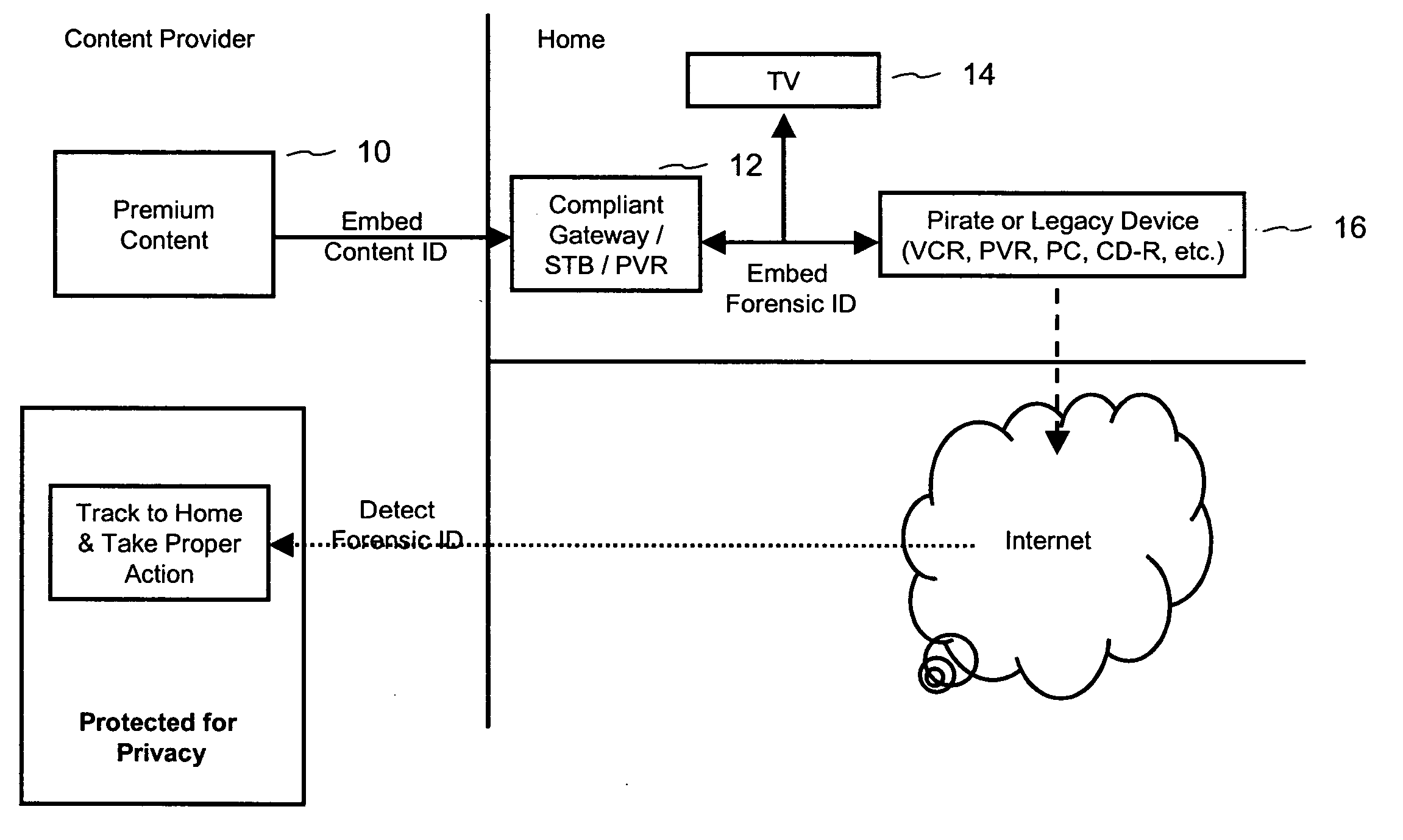
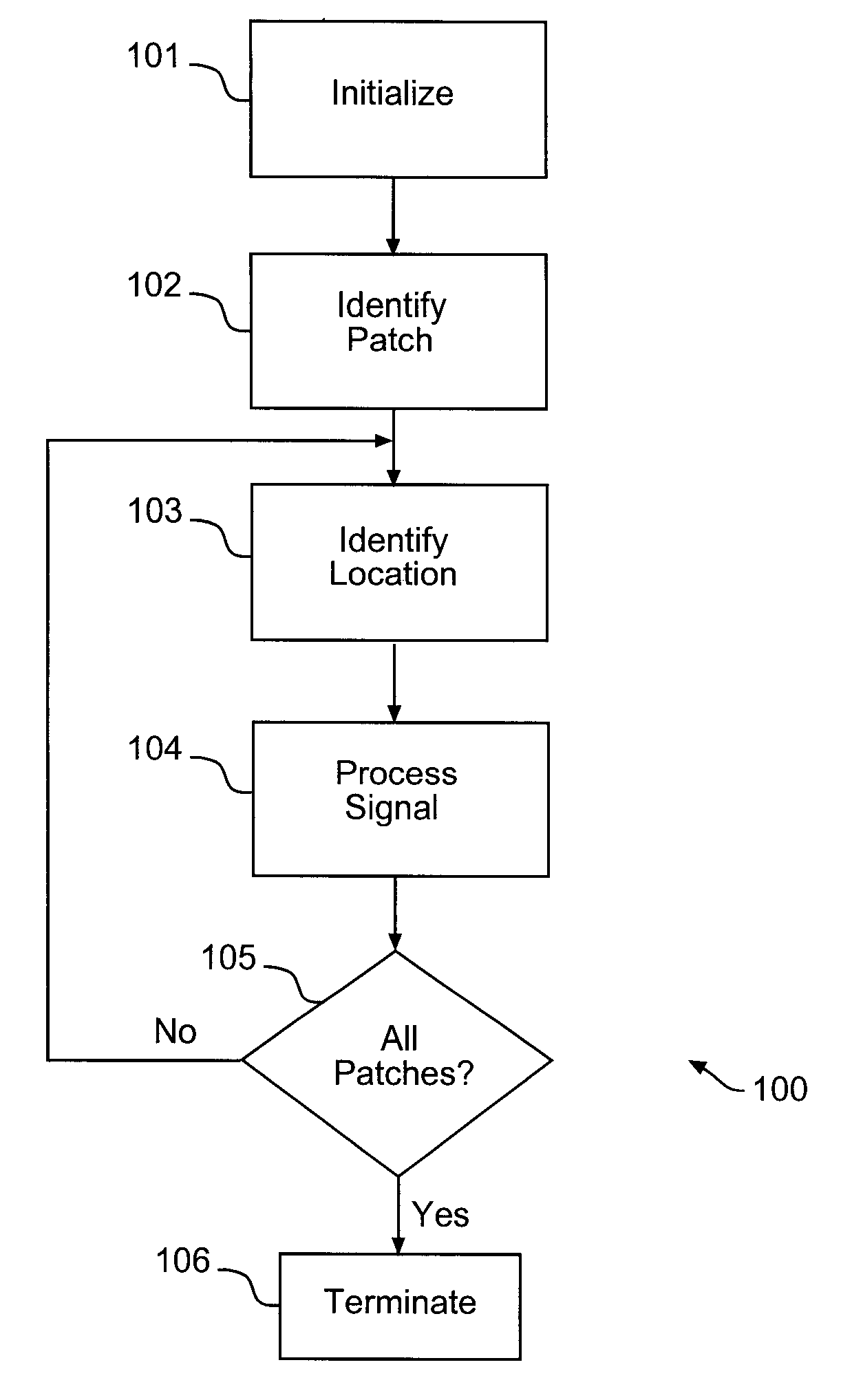
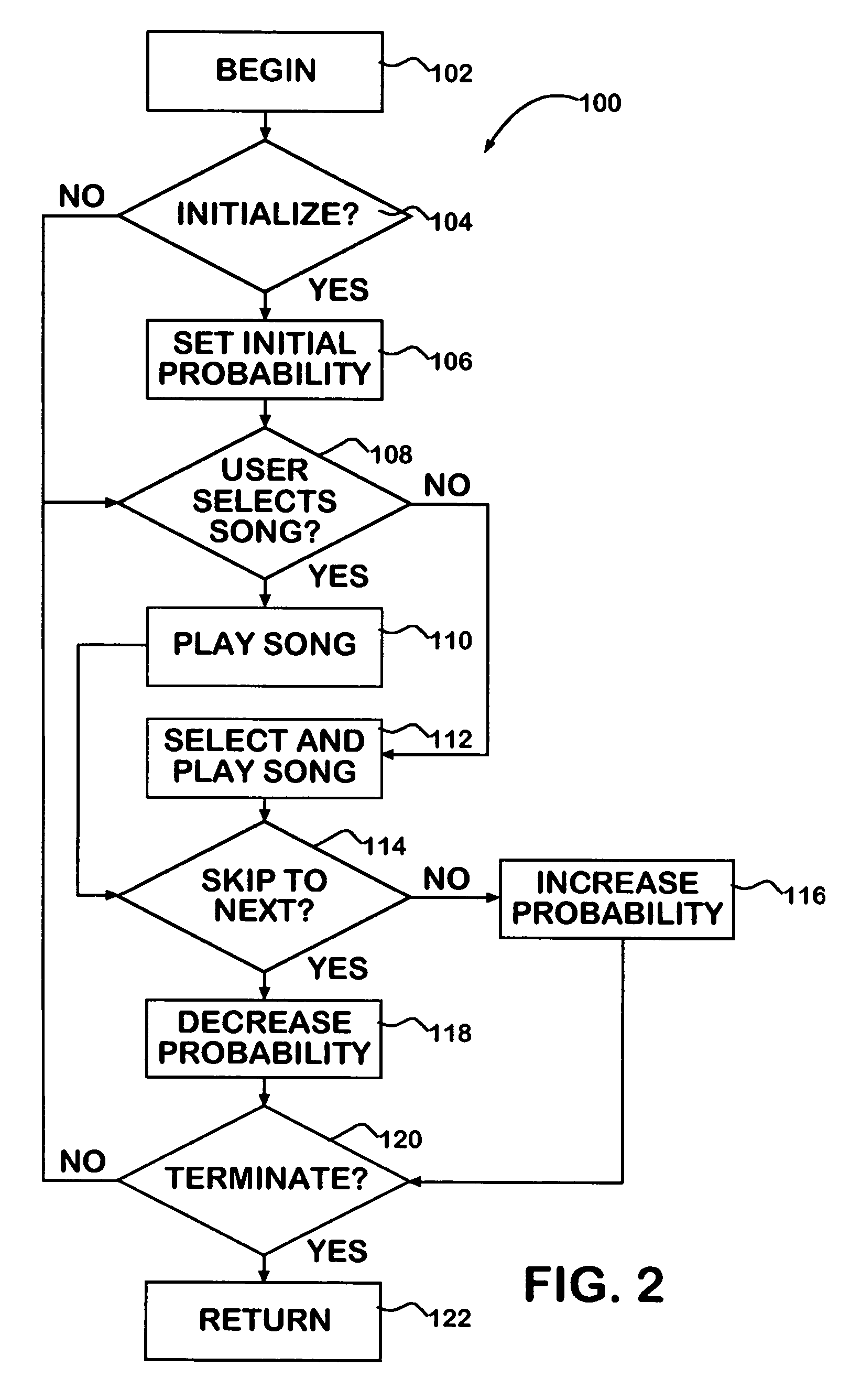
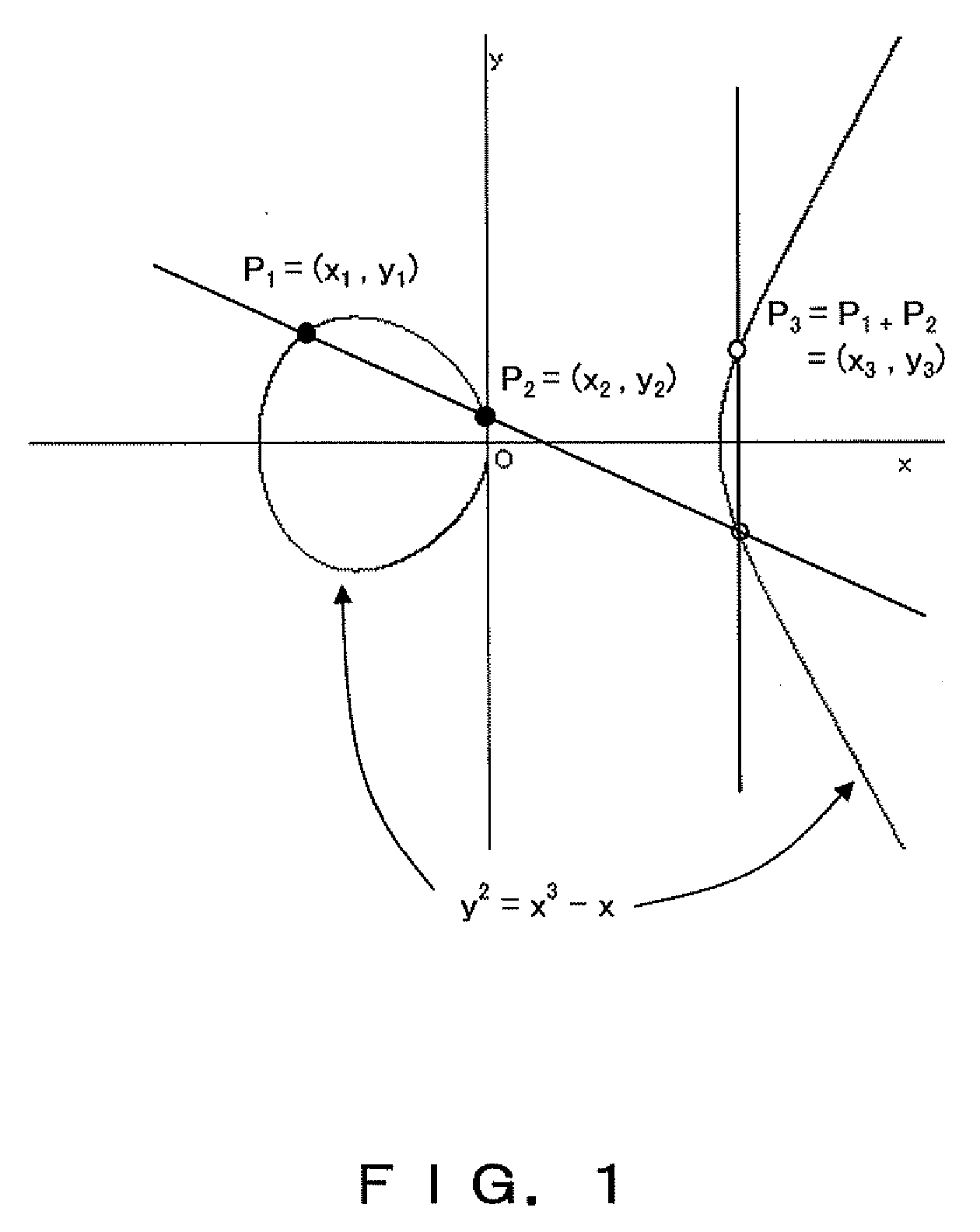
Method, computer readable media and apparatus for the selection and rendering of audio files in a networked environment
InactiveUS7113999B2Multiple digital computer combinationsElectric digital data processingRandom choiceSpeech input
Owner:IBM CORP
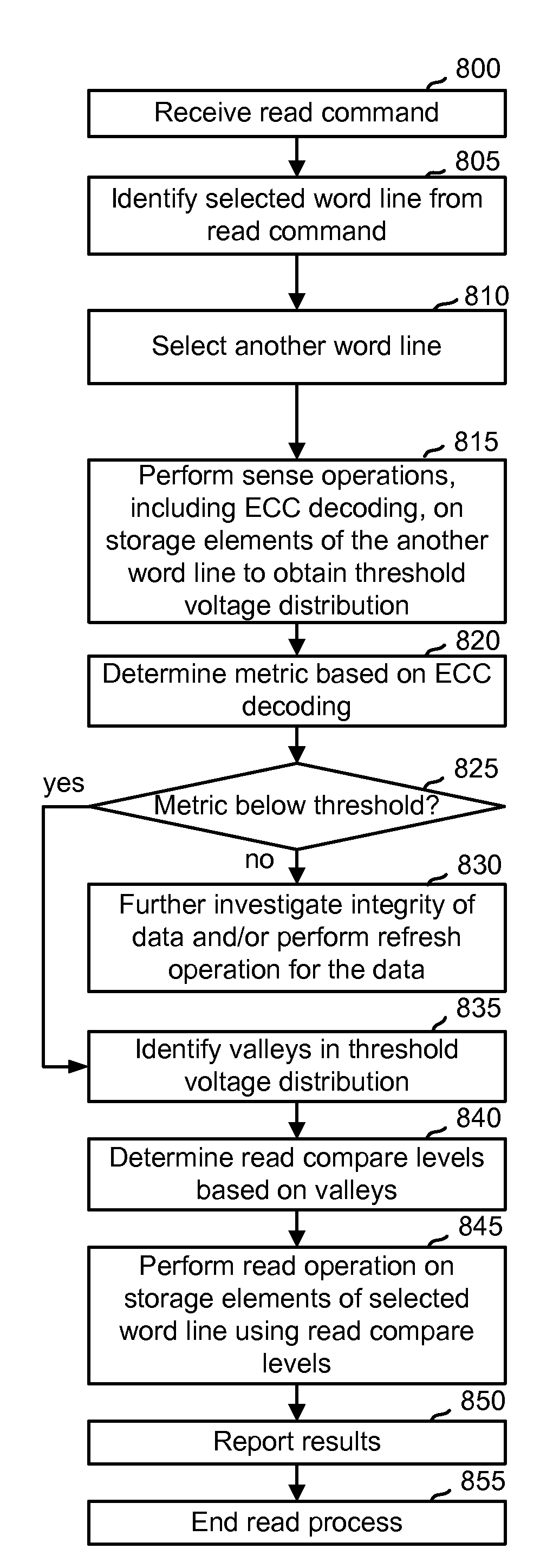
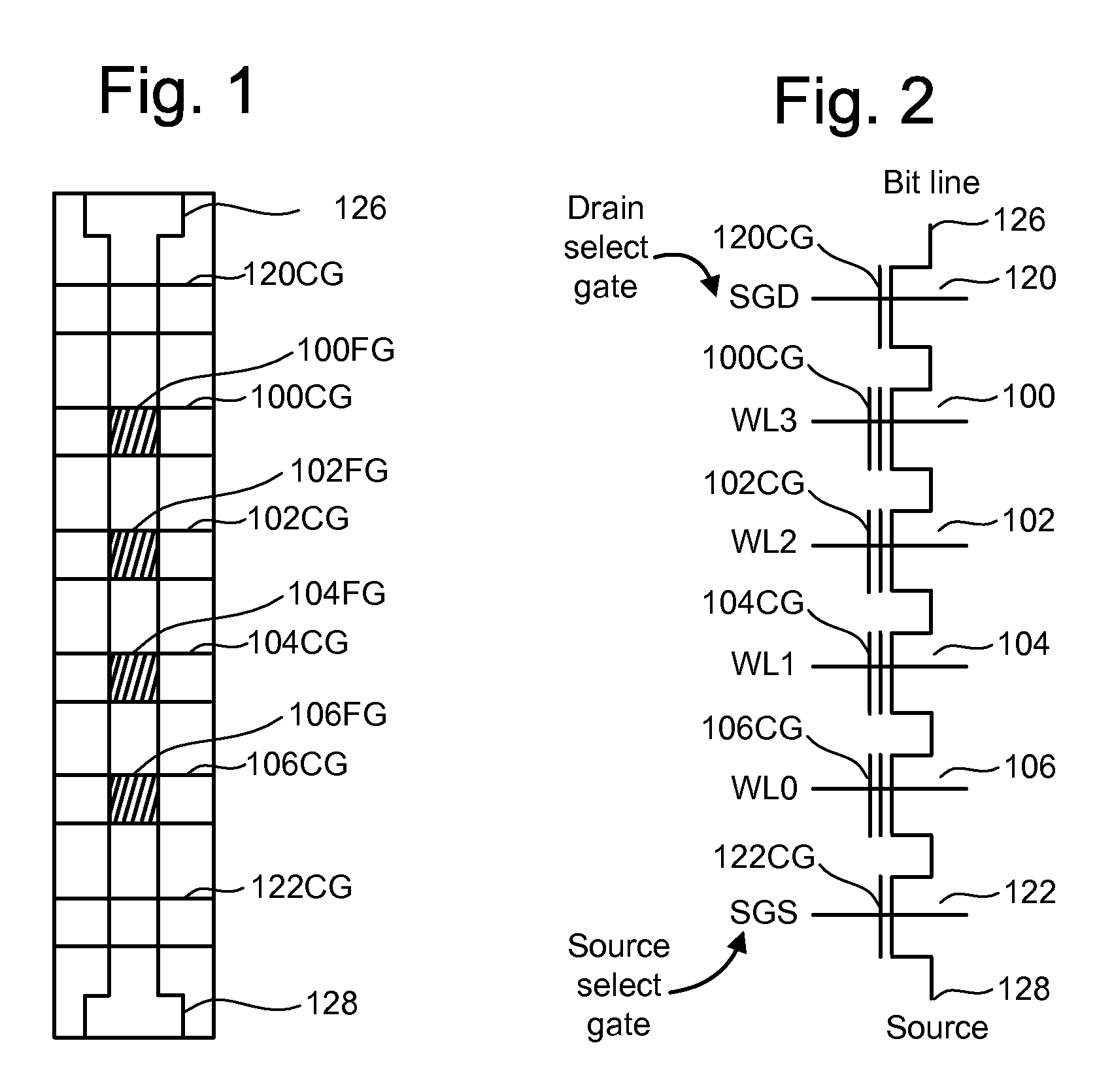
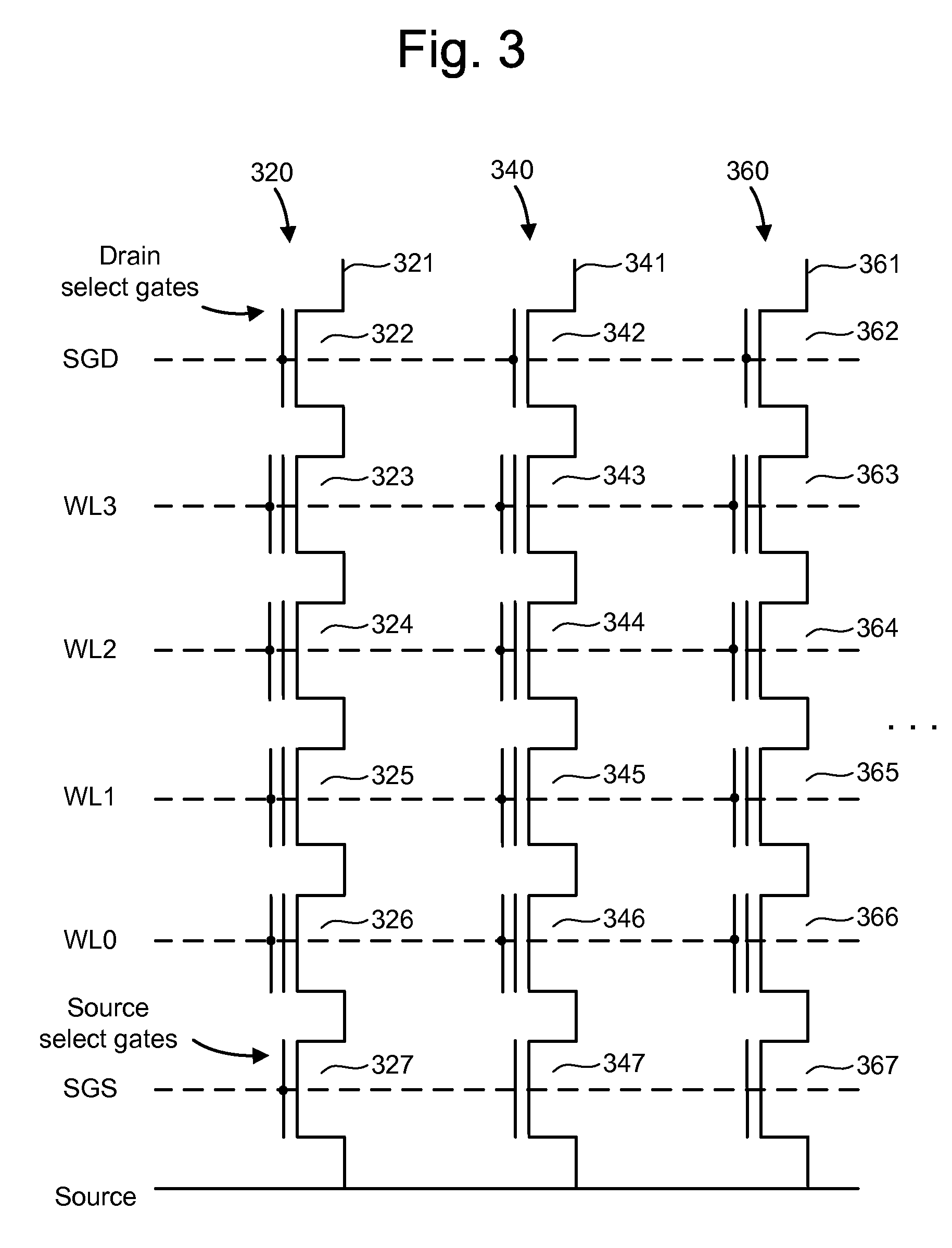
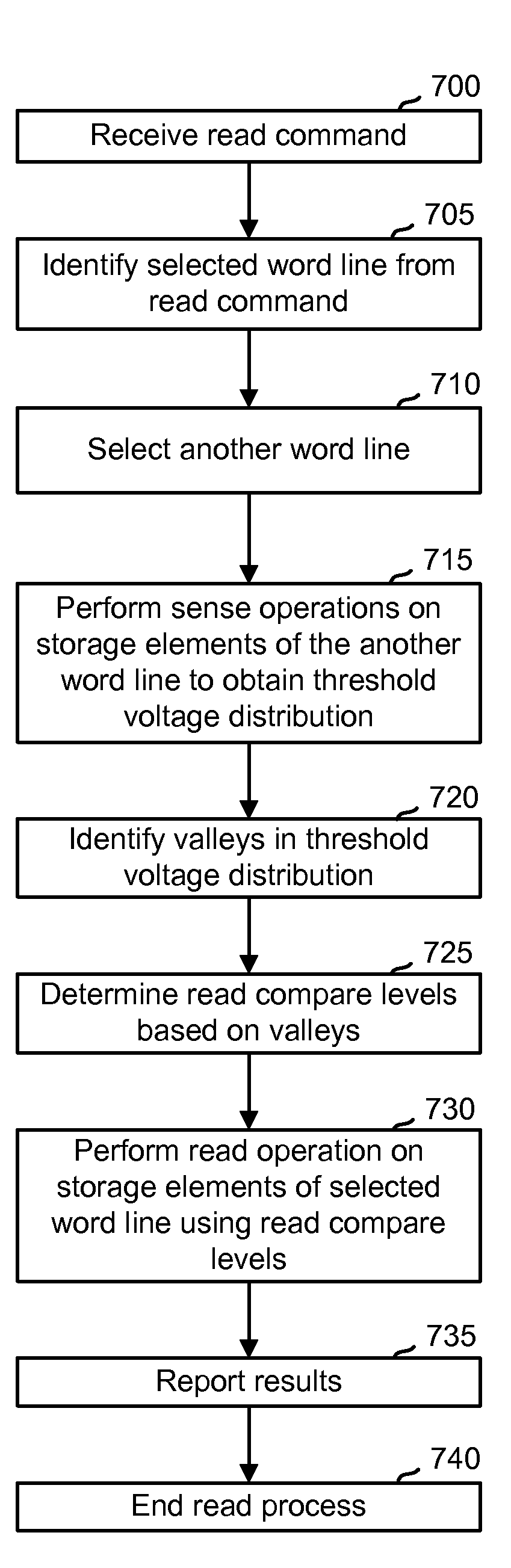
Read disturb mitigation in non-volatile memory
ActiveUS20090323412A1Mitigate read-disturbRead-only memoriesDigital storageRandom choiceComputer science
Read disturb is reduced in non-volatile storage. In one aspect, when a read command is received from a host for reading a selected word line, a word line which is not selected for reading is randomly chosen and its storage elements are sensed to determine optimized read compare levels for reading the selected word line. Or, a refresh operation may be indicated for the entire block based on an error correction metric obtained in reading the storage elements of the chosen word line. This is useful especially when the selected word line is repeatedly selected for reading, exposing the other word lines to additional read disturb. In another aspect, when multiple data states are stored, one read compare level is obtained from sensing, e.g., from a threshold voltage distribution, and other read compare levels are derived from a formula.
Owner:SANDISK TECH LLC
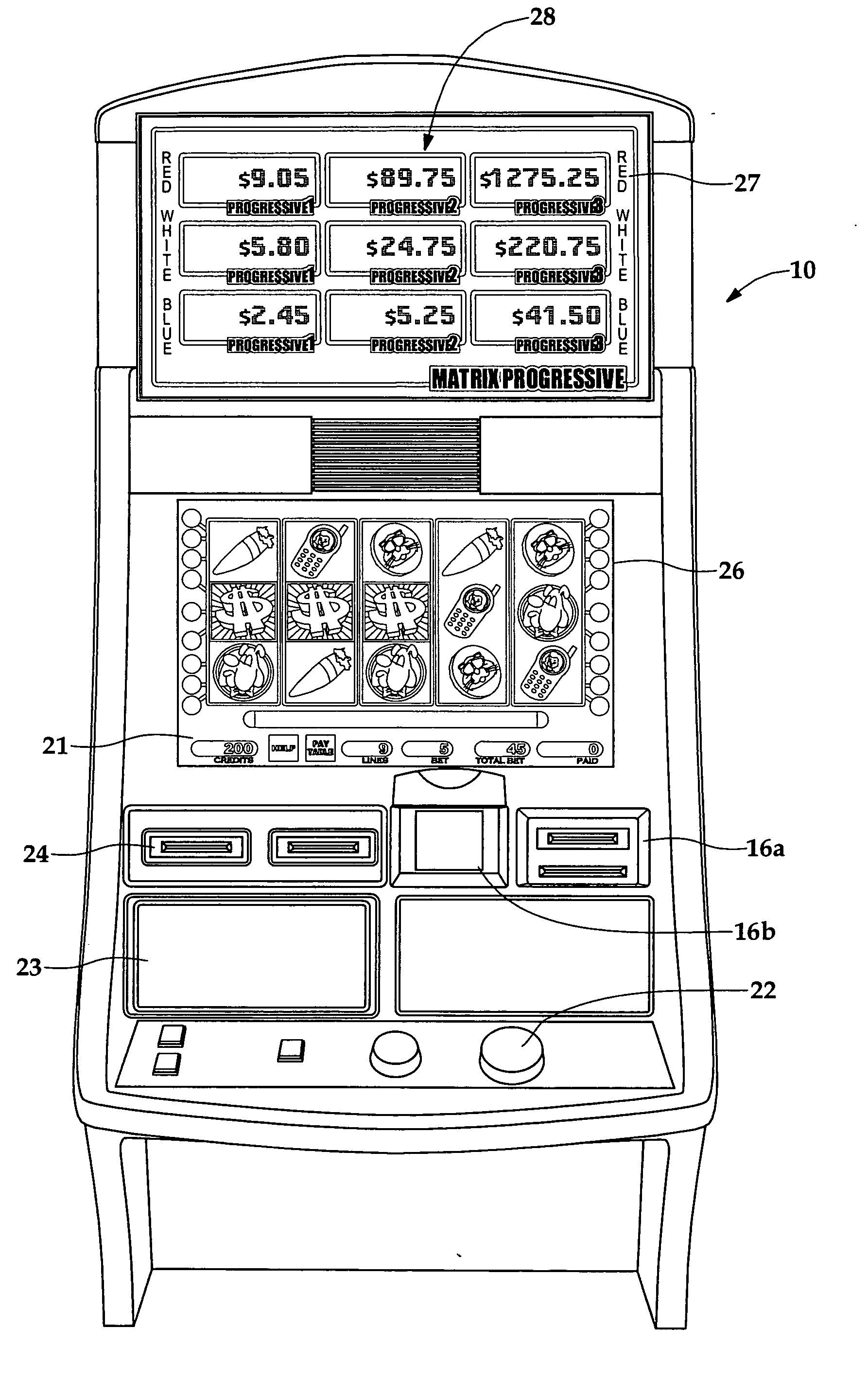
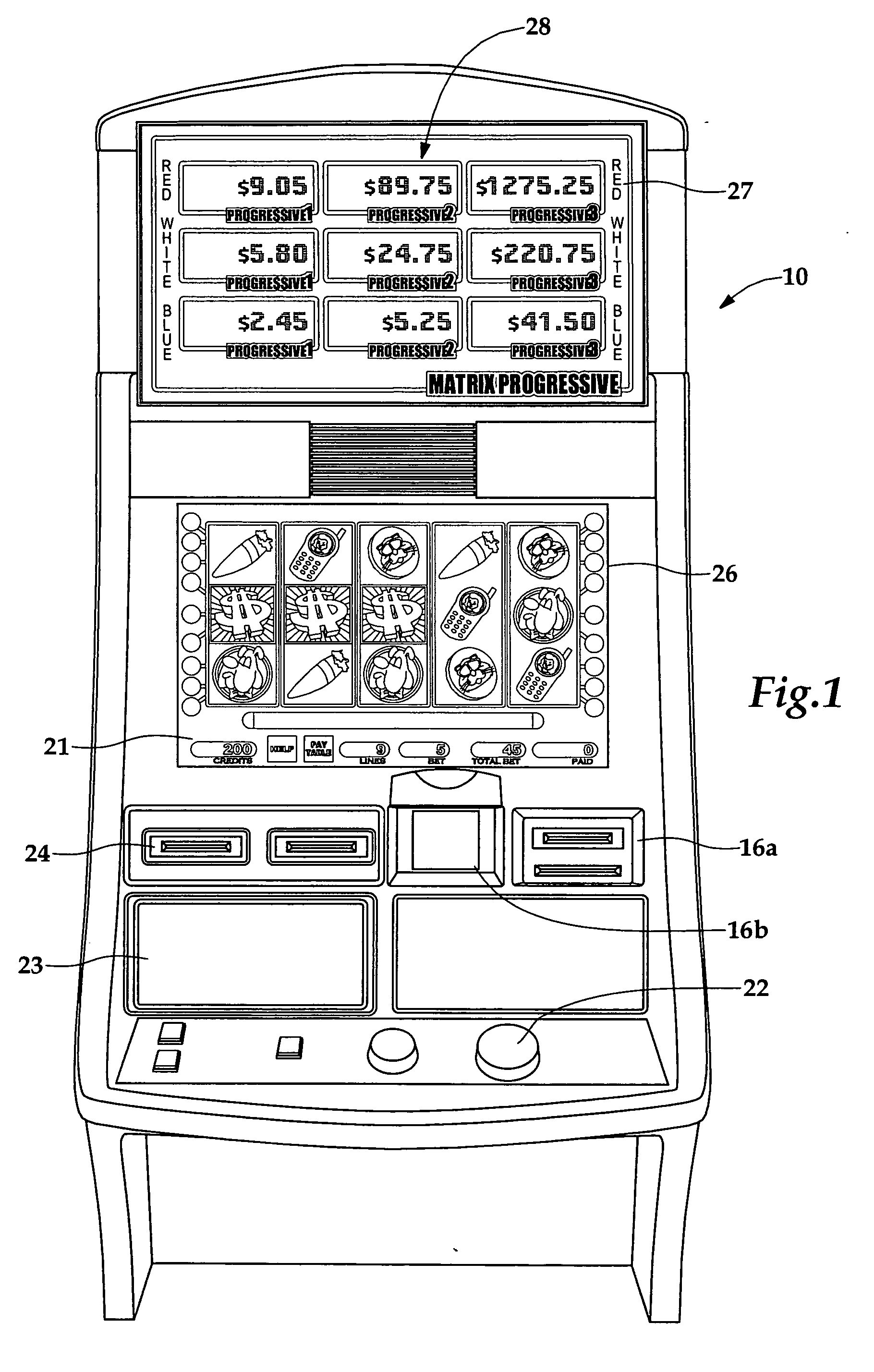
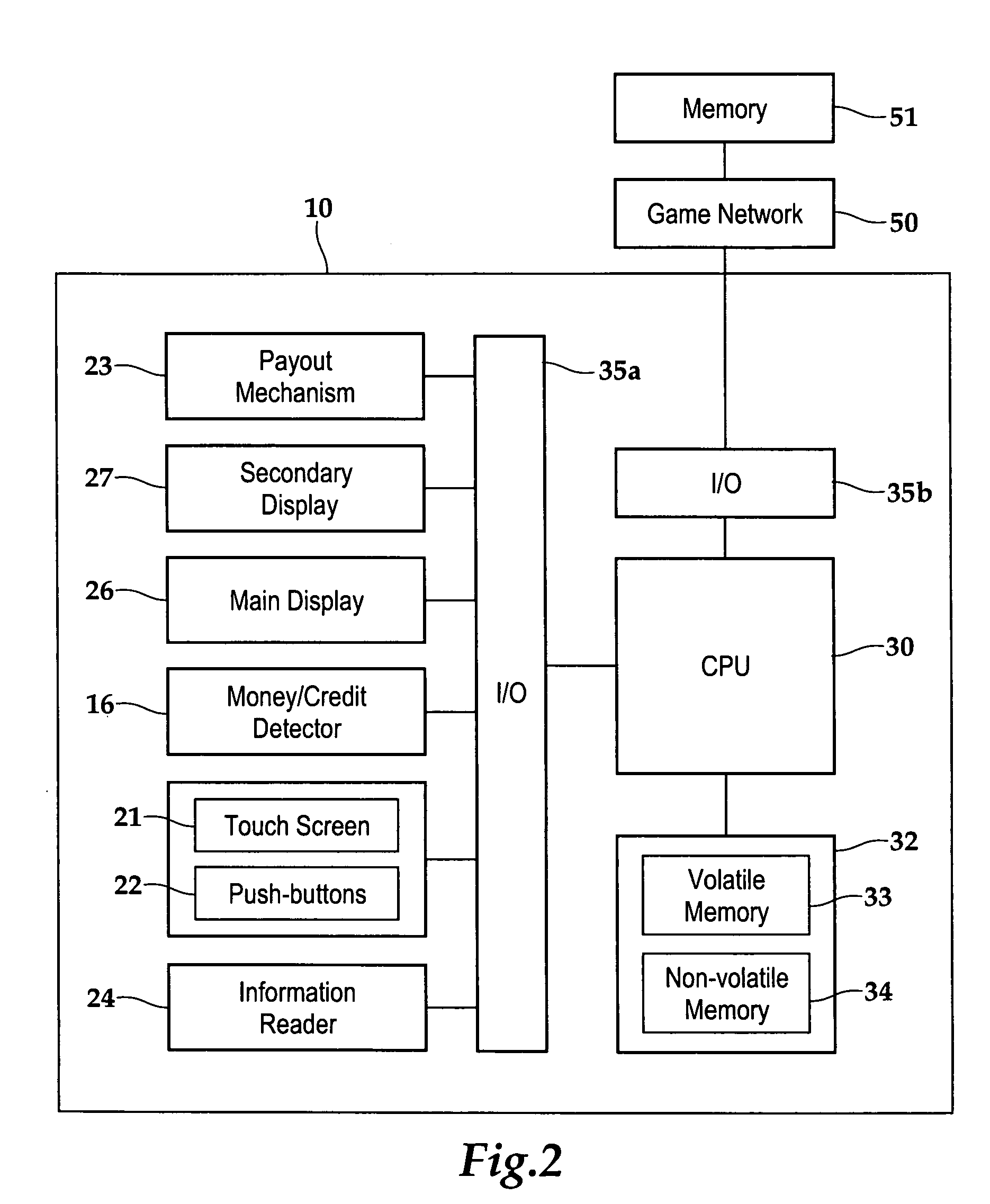
Wagering game with payoff rounding feature
InactiveUS20060035706A1Apparatus for meter-controlled dispensingVideo gamesRandom choiceArtificial intelligence
A method for playing a wagering game allowing a player to be eligible for a progressive jackpot having an actual value. The method comprises conducting the wagering game that has a randomly selected outcome selected from a plurality of outcomes, and displaying a displayed value of the progressive jackpot to the player. The method further includes increasing the displayed value by increments of a first denomination, and awarding a player an award value of the progressive jackpot in response to the player achieving the progressive jackpot. The award value is greater than the displayed value and is equally divisible by a second denomination that is larger than the first denomination. Other methods are provided for creating an escrow pool for funding the difference between the displayed and award values, and also for awarding multiple jackpots from a plurality of progressive jackpots.
Owner:BALLY GAMING INC
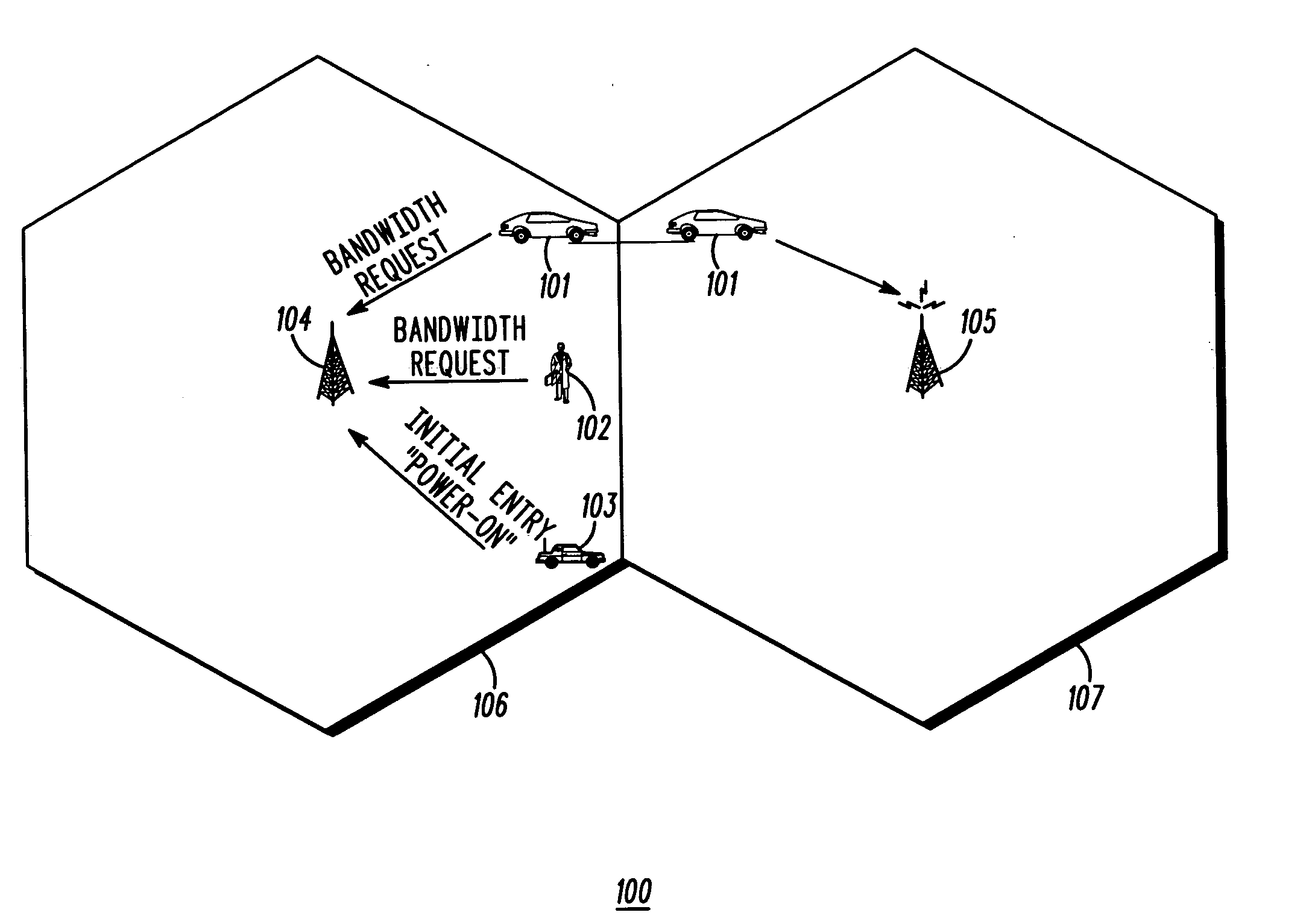
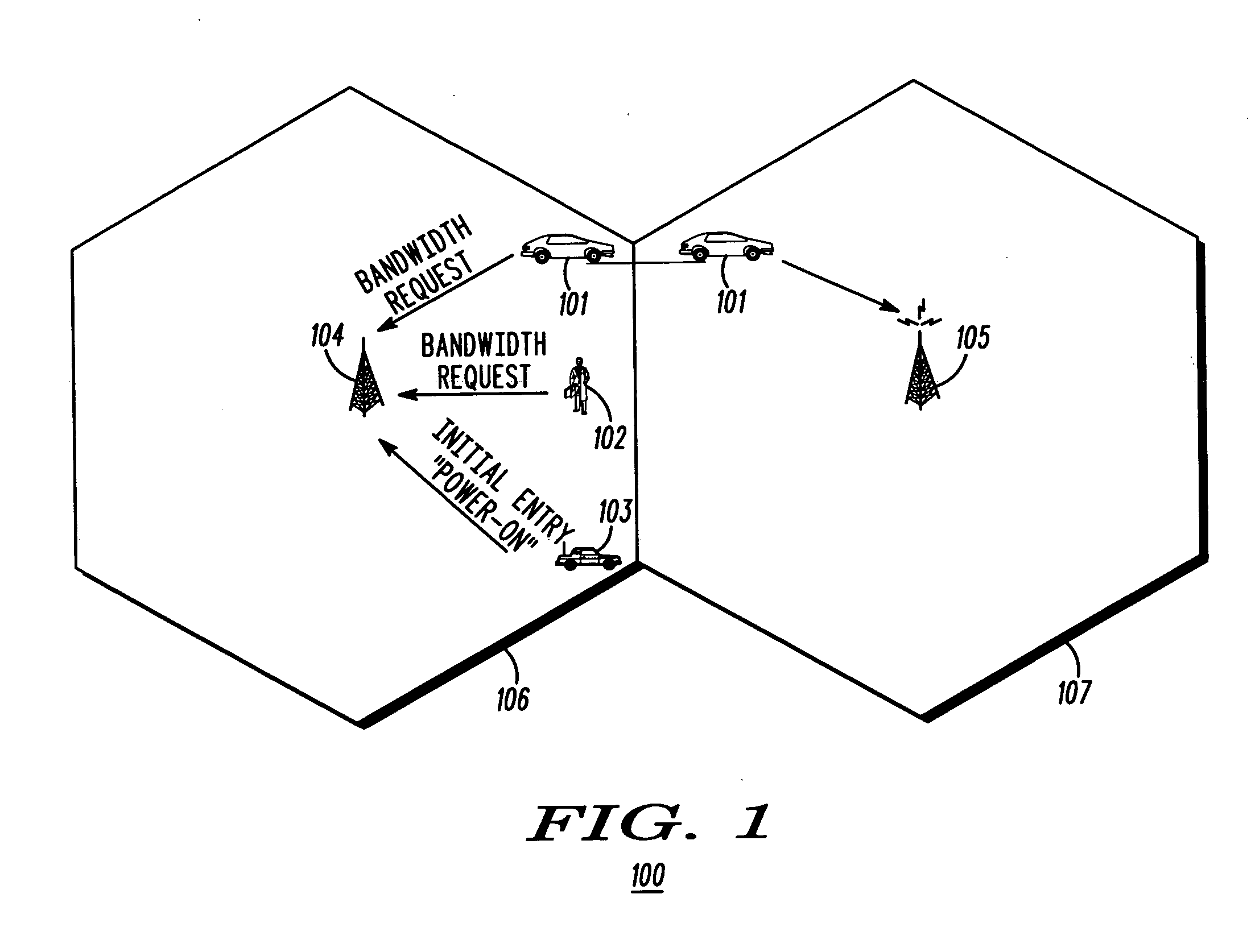
Method and apparatus for accessing a wireless communication system
Access to a wireless communication system (100) by a subscriber station (101-103) is facilitated by selecting (705) an access sequence from a set of sequences that have been identified to have a low average of peak-to-average-power-ratios of access signals generated by the set of sequences and also based on a good cross-correlation of the access signals; forming (714) the access waveform by generating an access signal using the access sequence and appending in the time domain a cyclic prefix to the access signal; and transmitting (715) the access waveform. In some implementations, the access waveform is cyclically shifted (820) before the cyclic prefix is appended, and in some implementations, the signal is transmitted (710, 810) in a randomly selected sub-band of an access interval.
Owner:GOOGLE TECH HLDG LLC
Automatic personal playlist generation with implicit user feedback
ActiveUS20050098023A1Electrophonic musical instrumentsProgram control using stored programsRandom choiceSelection system
Owner:NOKIA TECHNOLOGLES OY
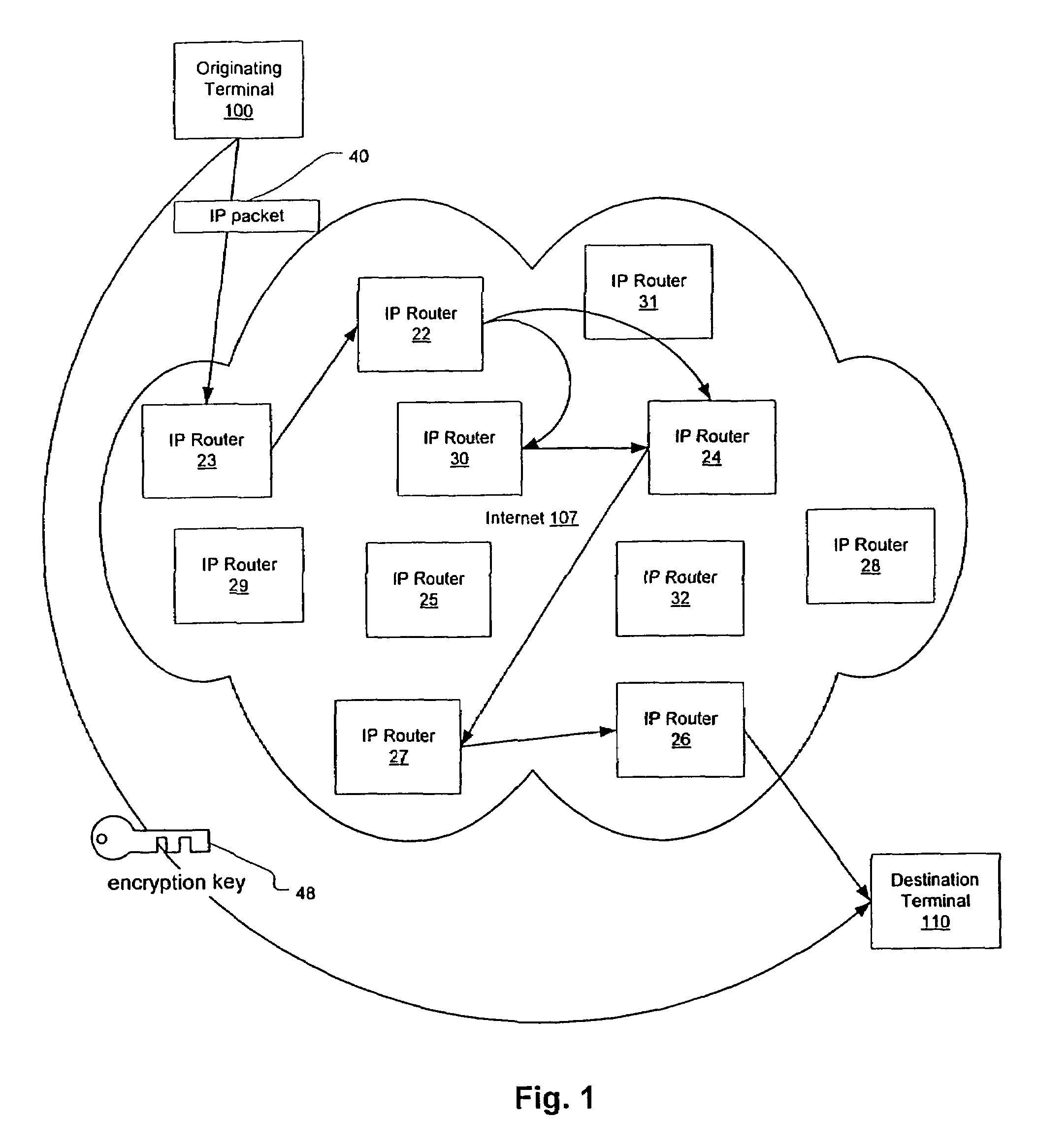
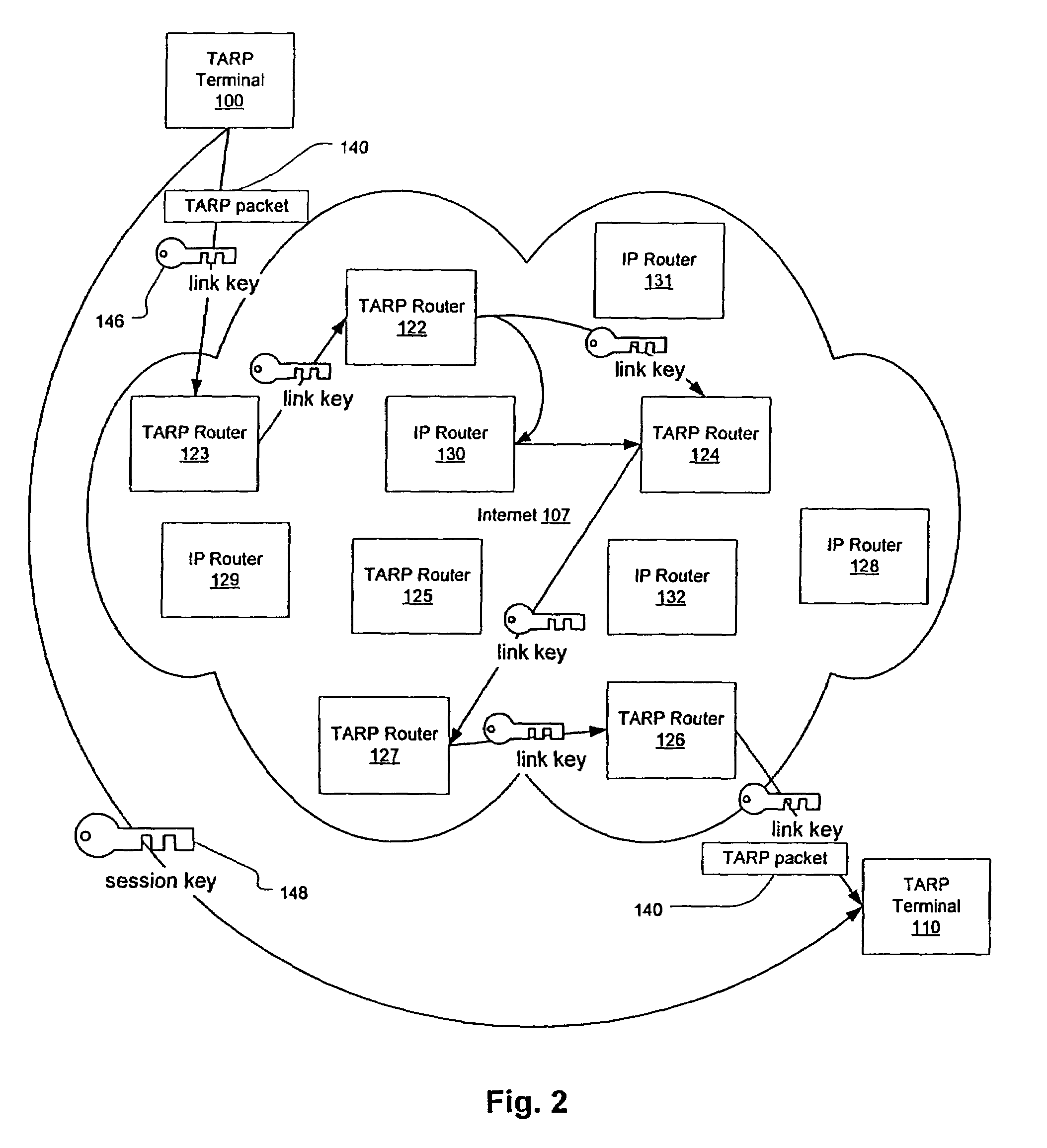
Agile network protocol for secure communications with assured system availability
InactiveUS7010604B1Reduce network loadSmall sizeKey distribution for secure communicationData stream serial/continuous modificationDiscriminatorComputer hardware
A plurality of computer nodes communicates using seemingly random IP source and destination addresses and (optionally) a seemingly random discriminator field. Data packets matching criteria defined by a moving window of valid addresses are accepted for further processing, while those that do not meet the criteria are rejected. In addition to “hopping” of IP addresses and discriminator fields, hardware addresses such as Media Access Control addresses can be hopped. The hopped addresses are generated by random number generators having non-repeating sequence lengths that are easily determined a-priori, which can quickly jump ahead in sequence by an arbitrary number of random steps and which have the property that future random numbers are difficult to guess without knowing the random number generator's parameters. Synchronization techniques can be used to re-establish synchronization between sending and receiving-nodes. These techniques include a self-synchronization technique in which a sync field is transmitted as part of each packet, and a “checkpoint” scheme by which transmitting and receiving nodes can advance to a known point in their hopping schemes. A fast-packet reject technique based on the use of presence vectors is also described. A distributed transmission path embodiment incorporates randomly selected physical transmission paths.
Owner:VIRNETX
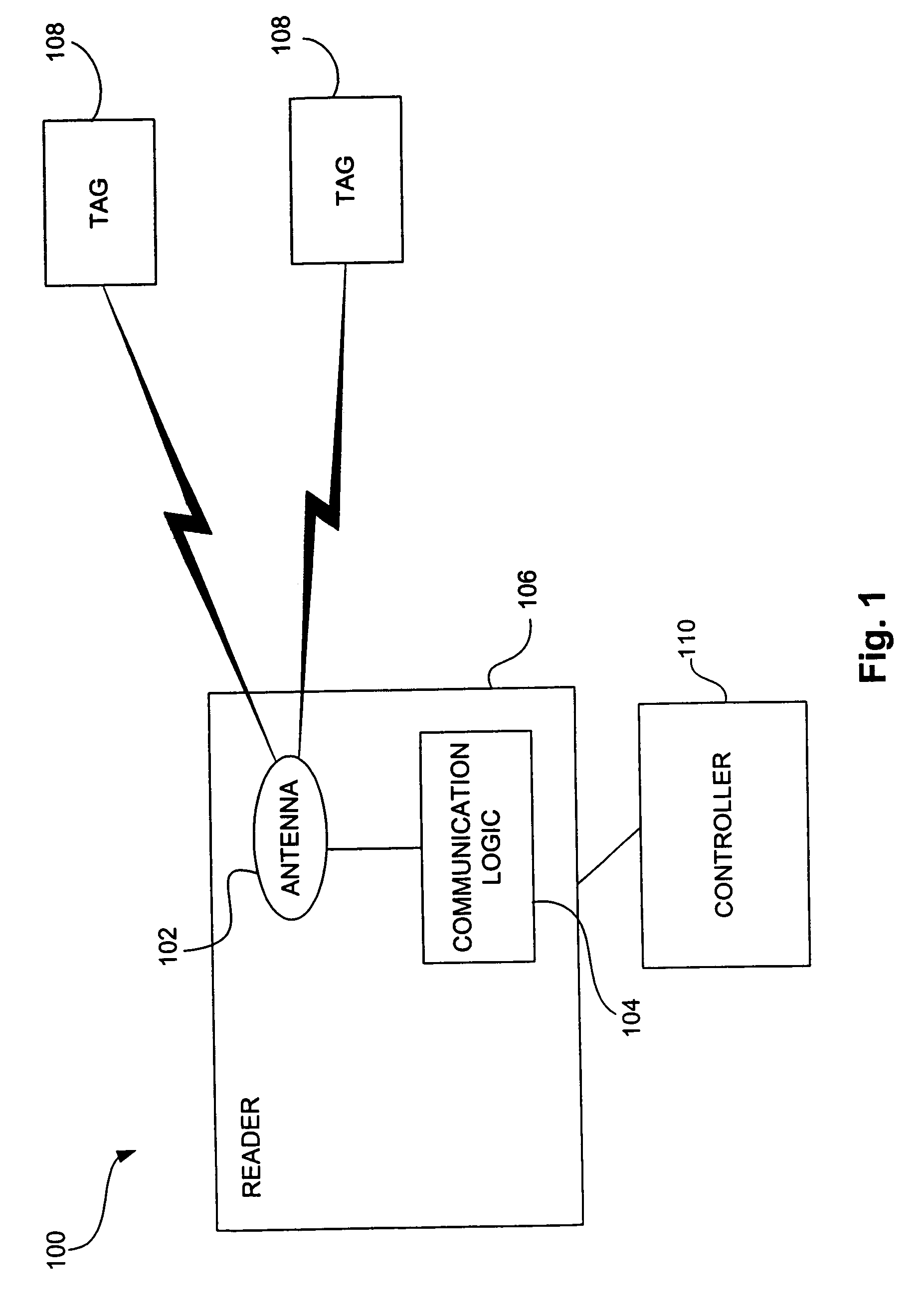
System and method for concurrently addressing multiple radio frequency identification tags from a single reader
InactiveUS6952157B1Increases range and throughputLow costElectric signal transmission systemsDigital data processing detailsRandom choiceRadio frequency
A system and method are provided in which each reader may conduct concurrent, yet independent, dialog with multiple tags at the same time using two or more phase channels. The reader itself may communicate with multiple tags via the same antenna, or using multiple antennae where each antenna operates on a separate phase channel. Upon receipt from the reader of an instruction for the tags to randomize, the tags randomly choose and assign a phase channel that will be their time reference for subsequent operation, or the channel can be assigned by the reader. The tags receive reader data encoded in the clock signal from the reader, and select the reader data pertaining to the particular tag based on the selected phase channel.
Owner:RUIZHANG TECH LTD CO
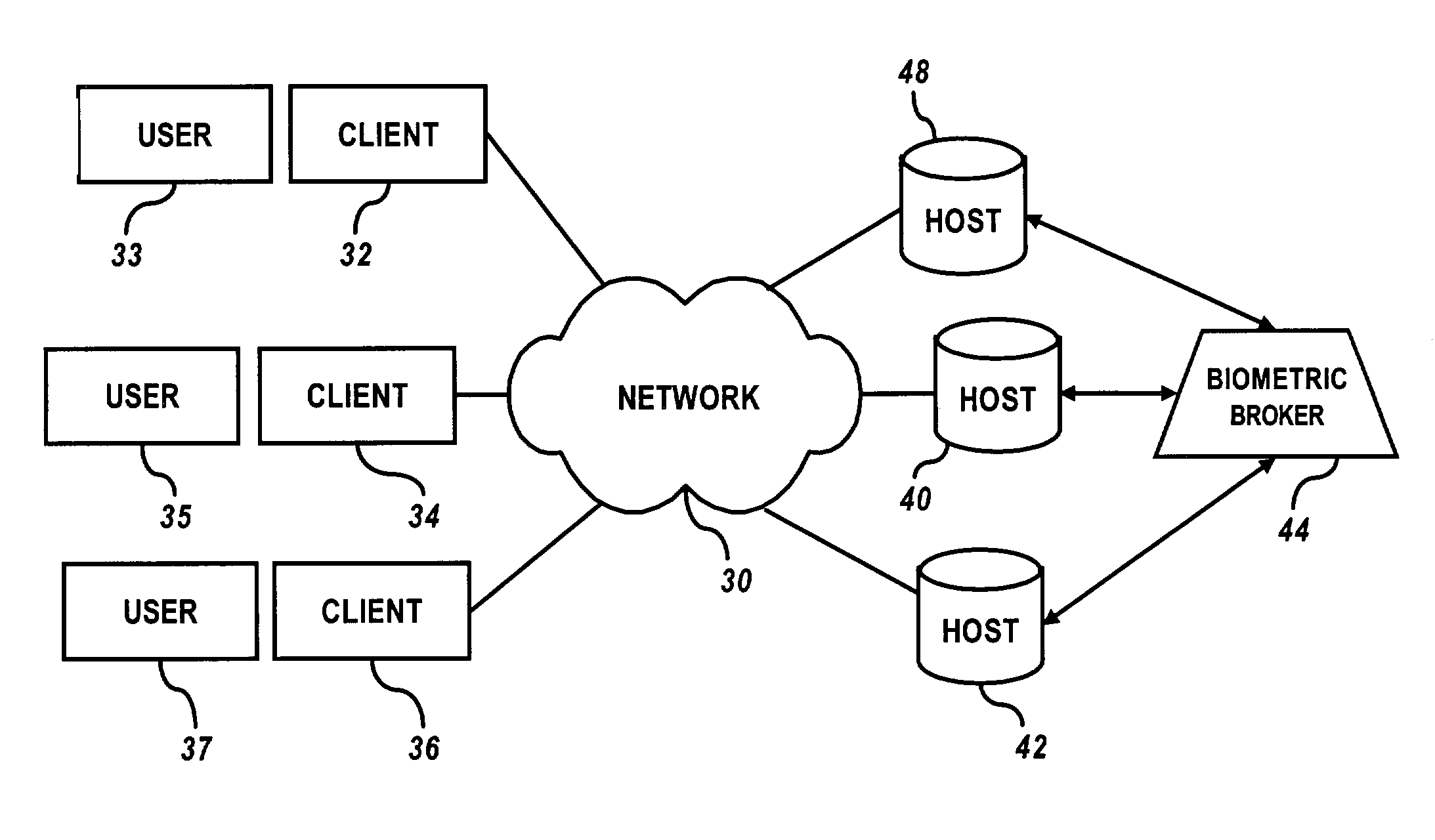
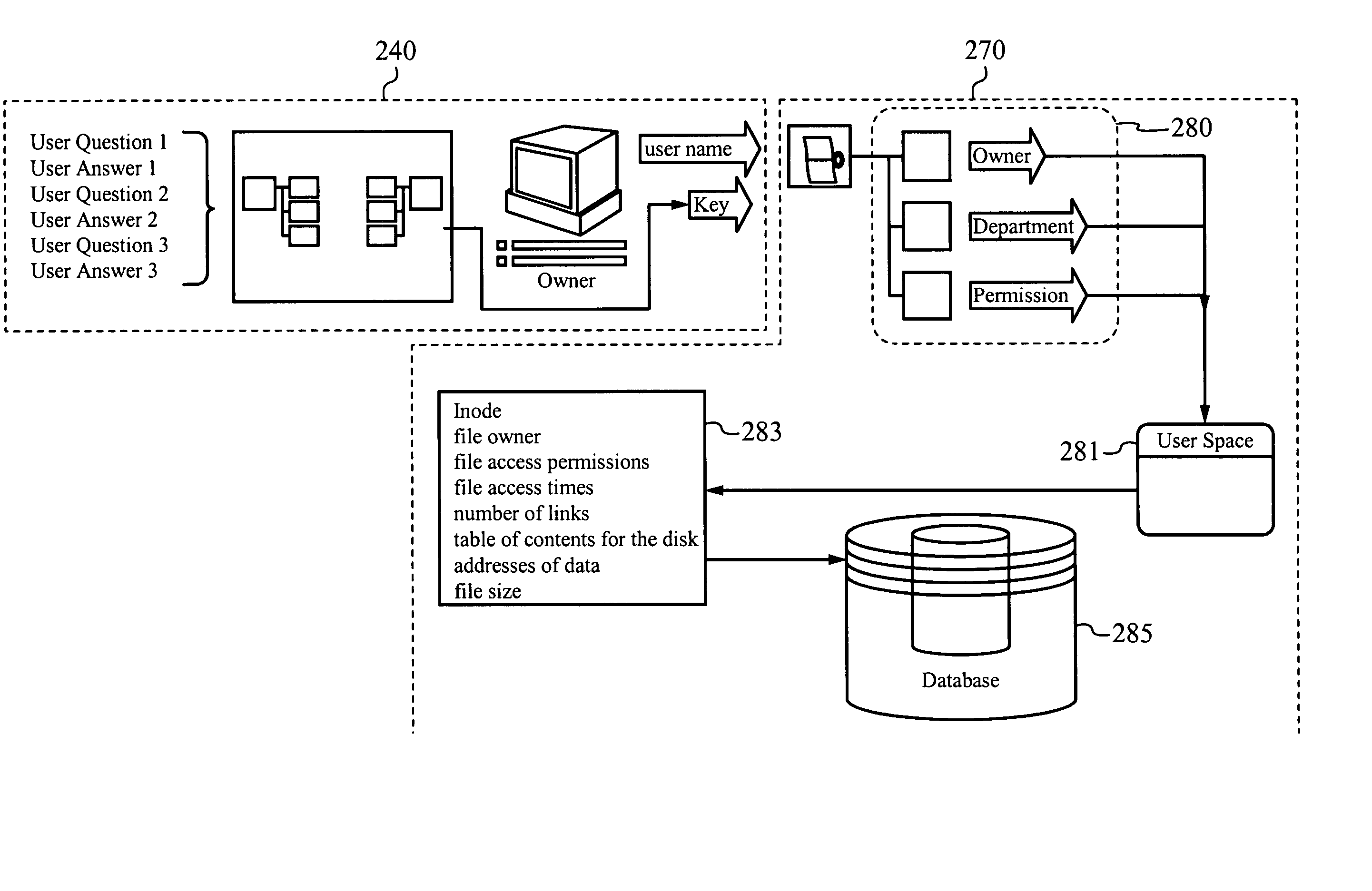
Identity collection, verification and security access control system
InactiveUS20090276839A1Digital data processing detailsMultiple digital computer combinationsInternet privacyControl system
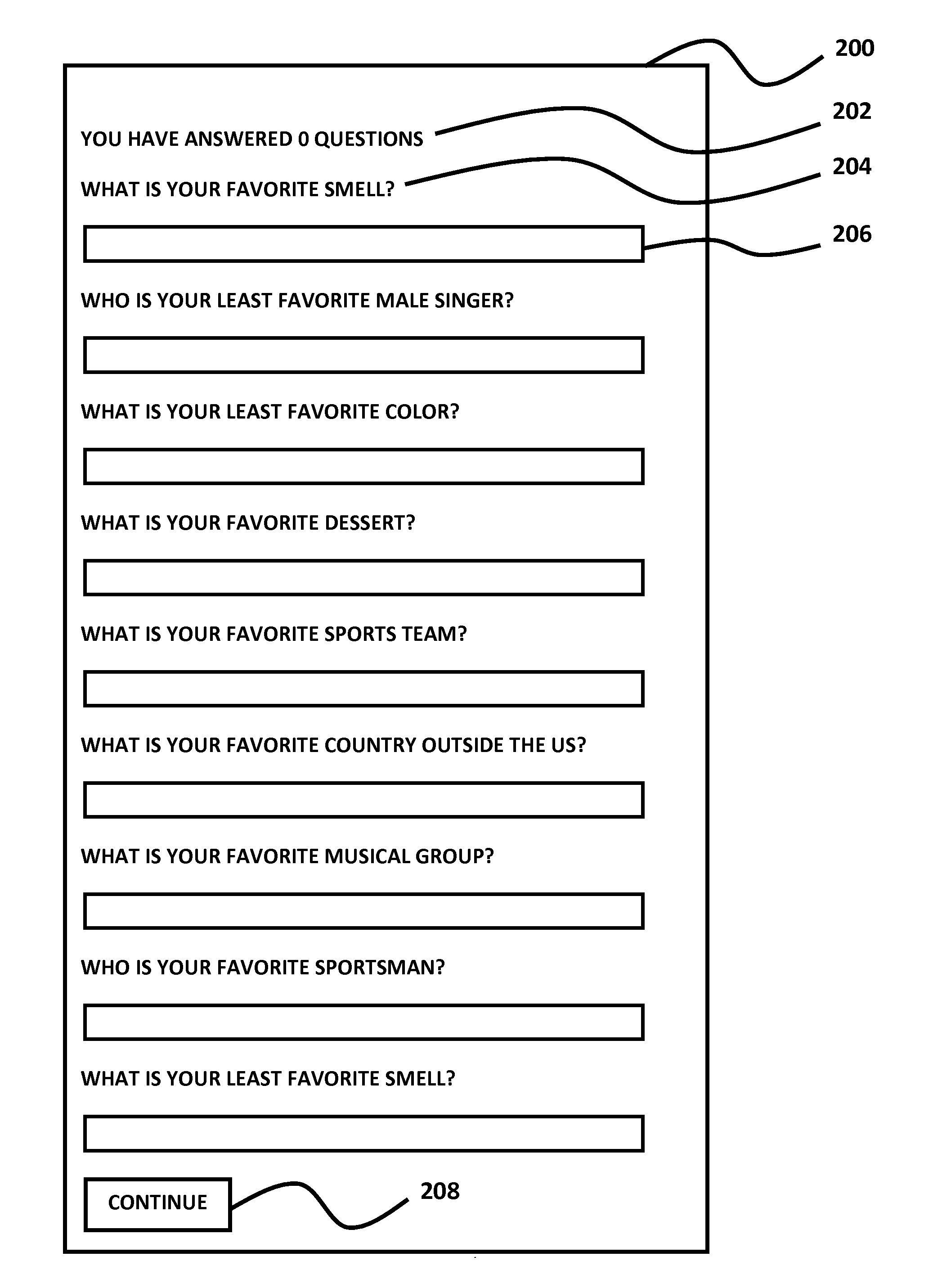
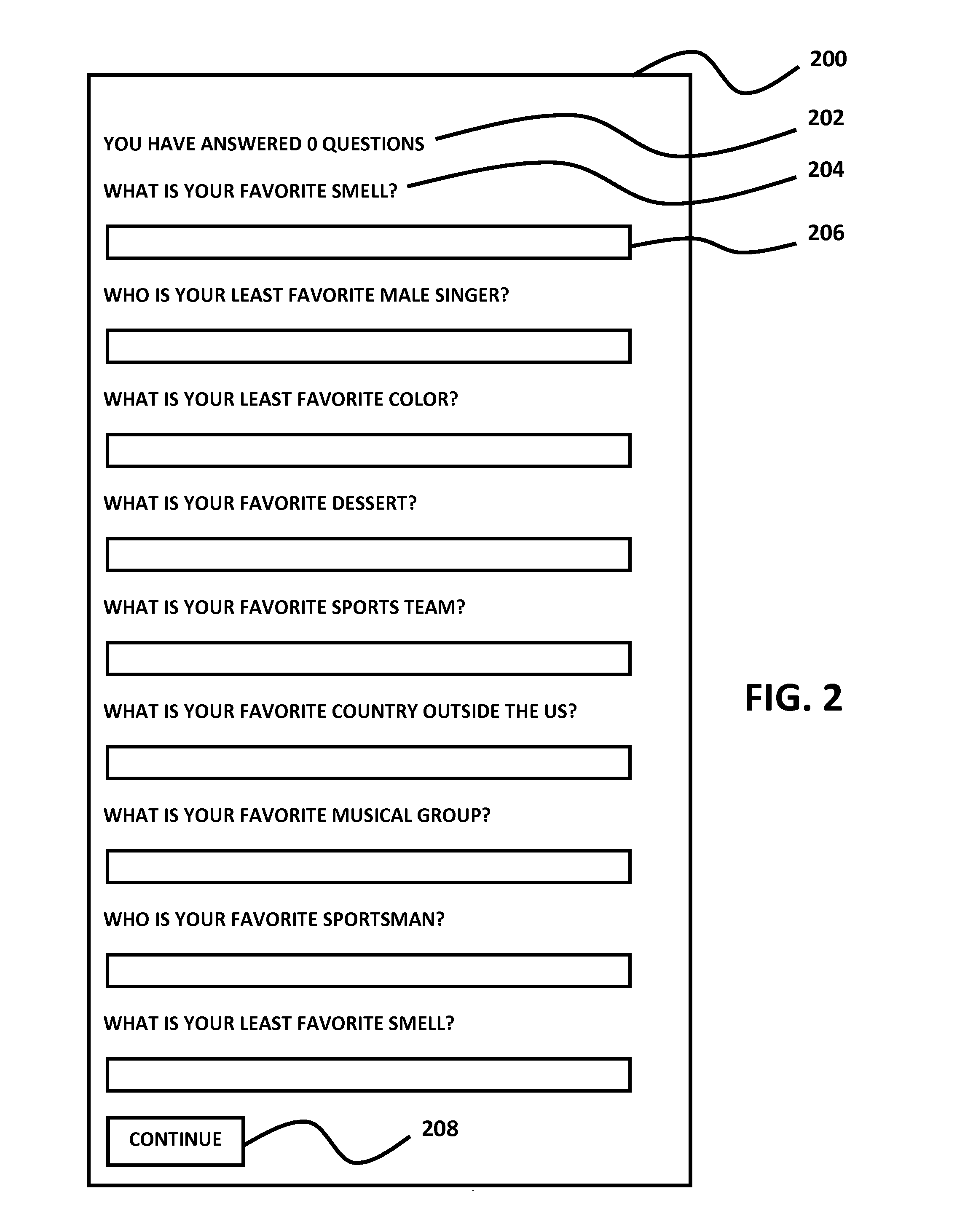
A system for collecting personally identifying information from individuals and using that information in verifying their identity and permitting their access to one or more secure systems via a single login authentication system. Based on a series of questions (opinion-based), a database of answers is developed for each user. To access a secure system at a base level of security, a user is asked to answer a group of questions randomly selected from the database and presented to the user for answers. If the questions are correctly answered, the user is permitted access to the secure system. Once access is granted, under certain circumstances, the user can access additional secure systems either as a result of the base level of security previously established, or a higher level of security, which requires the user to correctly answer additional randomly selected questions.
Owner:FORTKNOCK PROTECTION
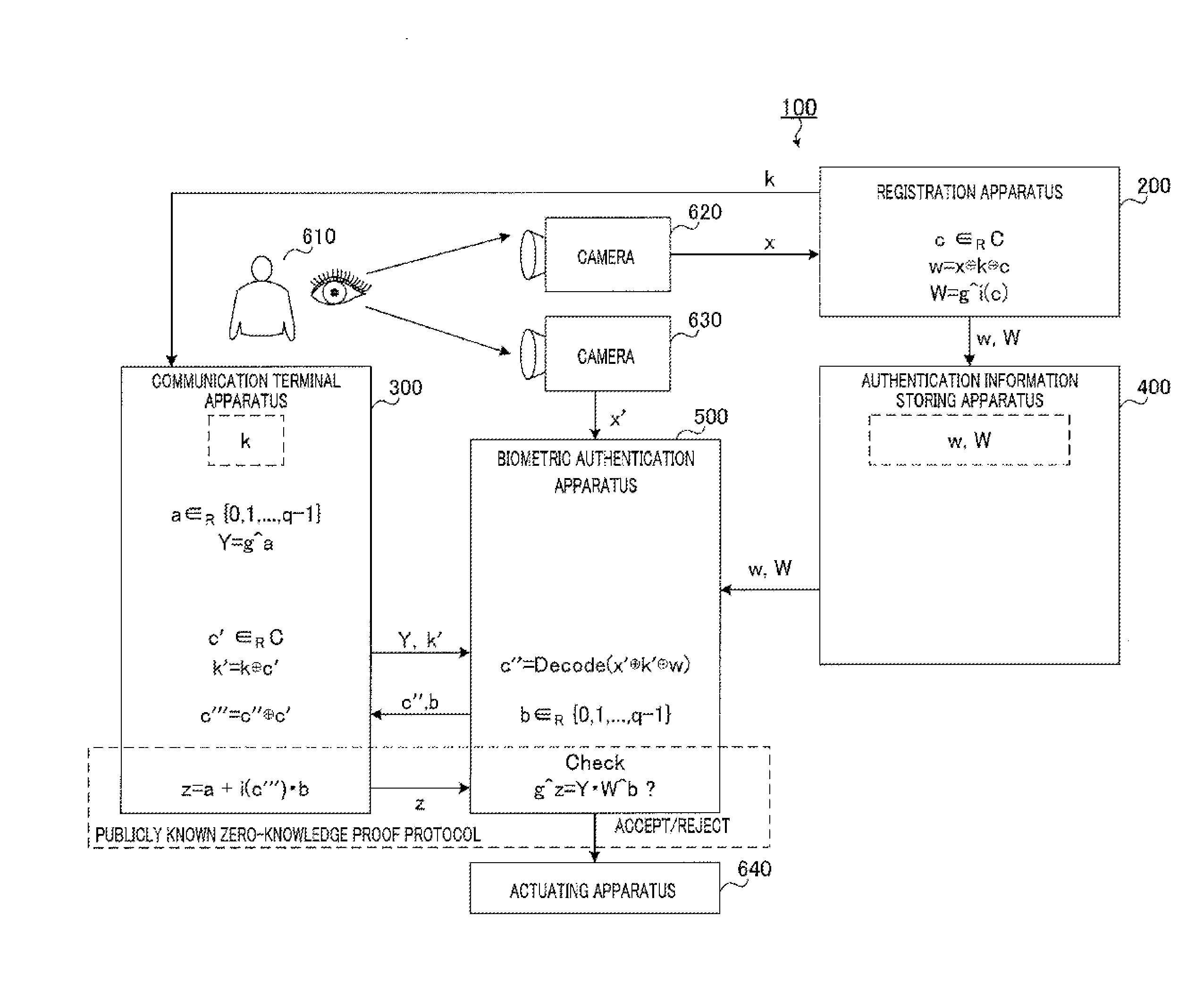
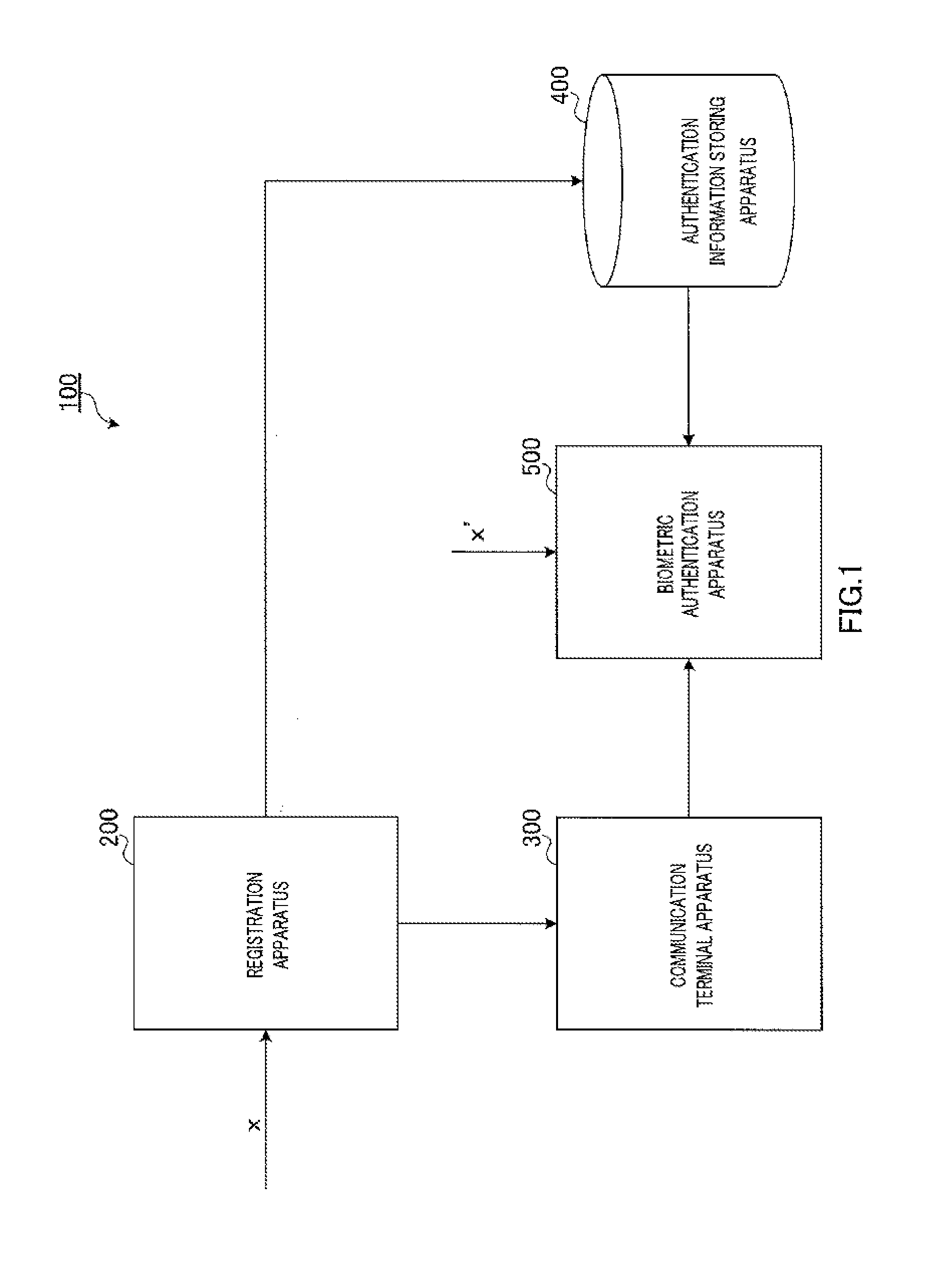
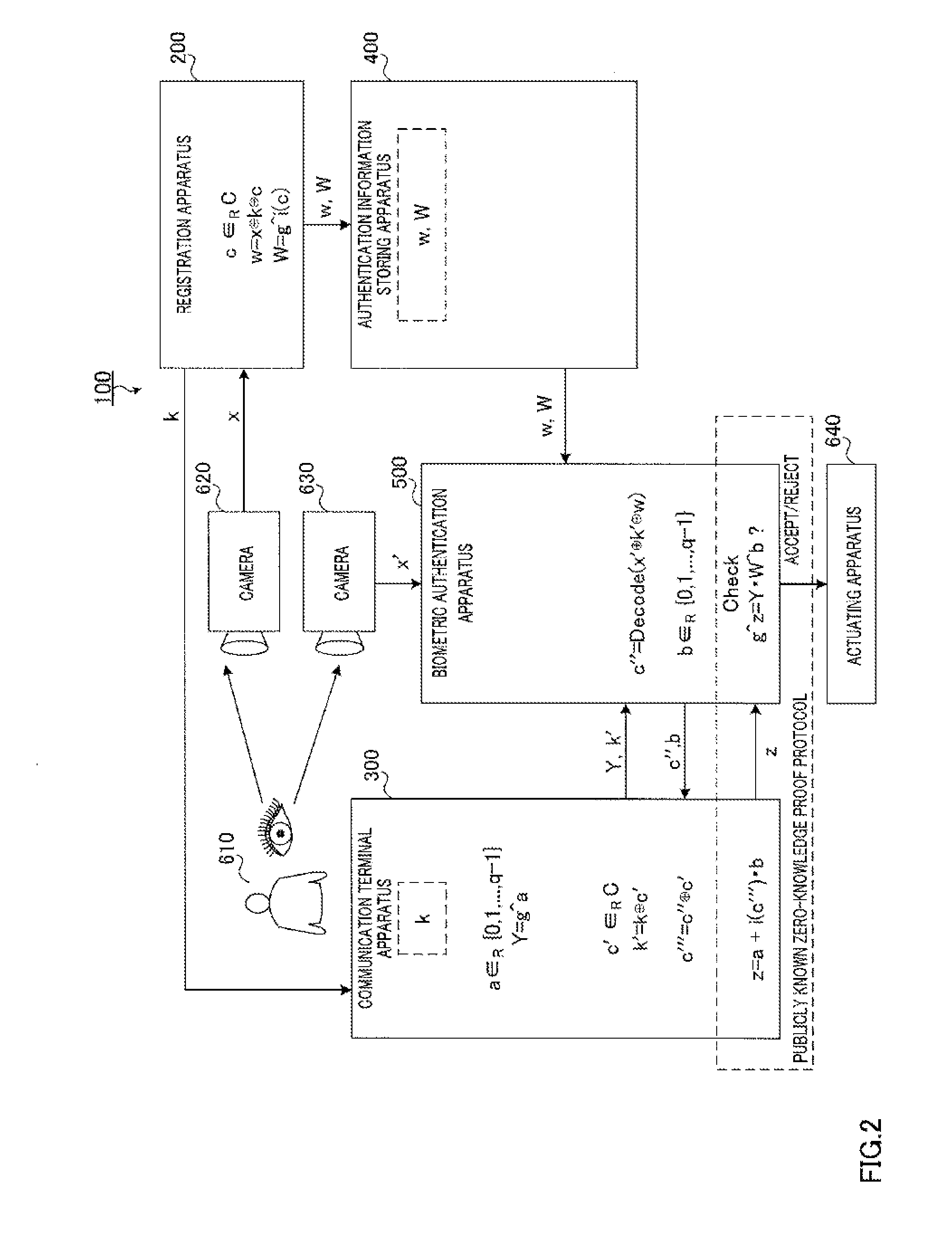
Biometric authentication system, communication terminal device, biometric authentication device, and biometric authentication method
ActiveUS20130174243A1Avoid attackDigital data processing detailsMultiple digital computer combinationsExclusive orTerminal equipment
Provided is a biometric authentication system capable of preventing spoofing attacks even if leakage of key information and a registration conversion template occurs. A communication terminal device (300) calculates secret key information k′ which is exclusive OR of key information k of the registration biological information and masked value c′ which is randomly selected from a predetermined error correction code group, and calculates verified information c′″ which is exclusive OR of sent information c″ and value c′. A biometric authentication device (500) calculates exclusive OR of authentication biological information, information k′, and registration conversion template w, as information c″, wherein the template w is exclusive OR of information x, information k, and authentication parameter c randomly selected from the code group; and performs biometric authentication on the basis of a degree of matching between information c′″ corresponding to information c″, and the parameter c.
Owner:PANASONIC CORP
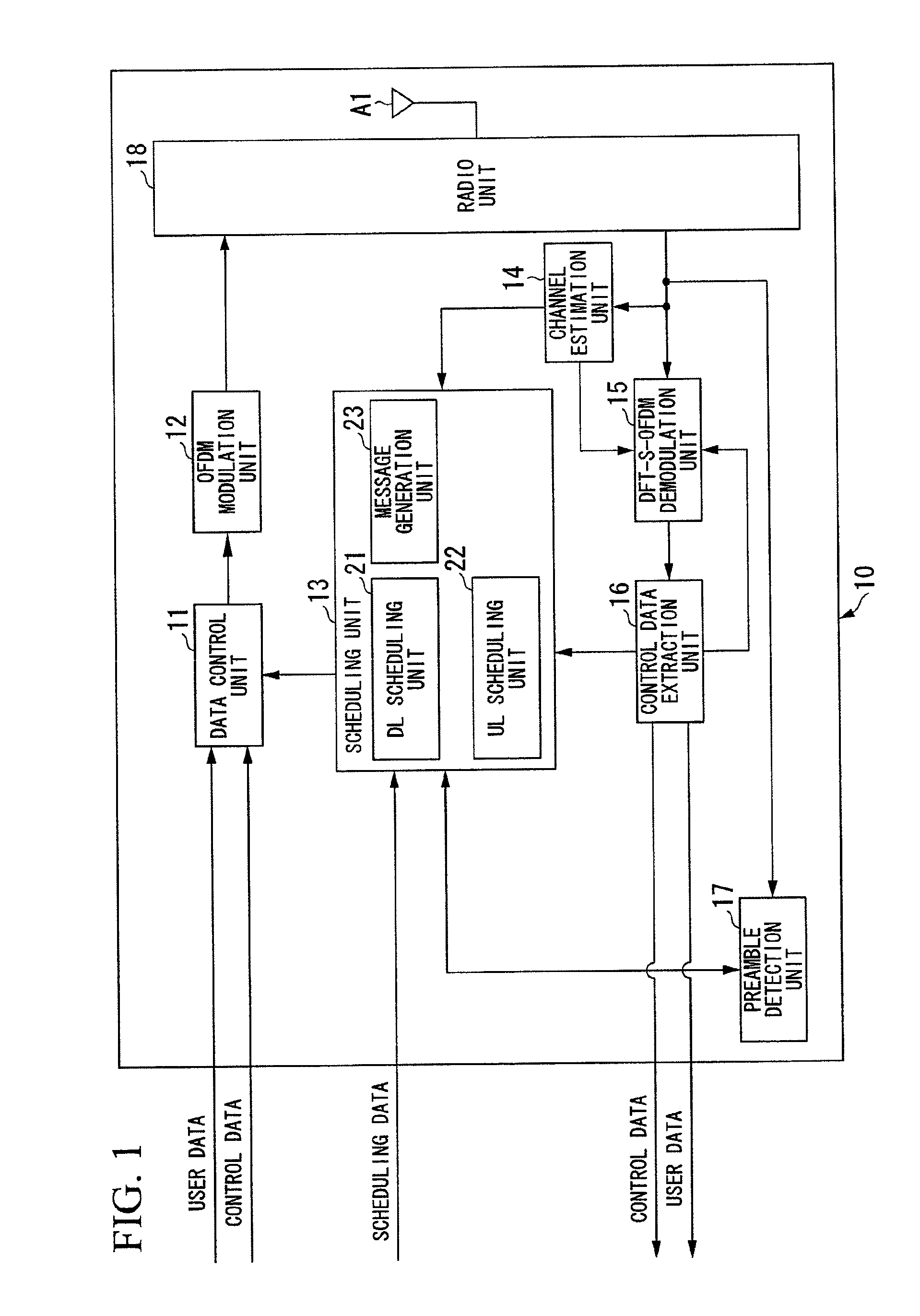
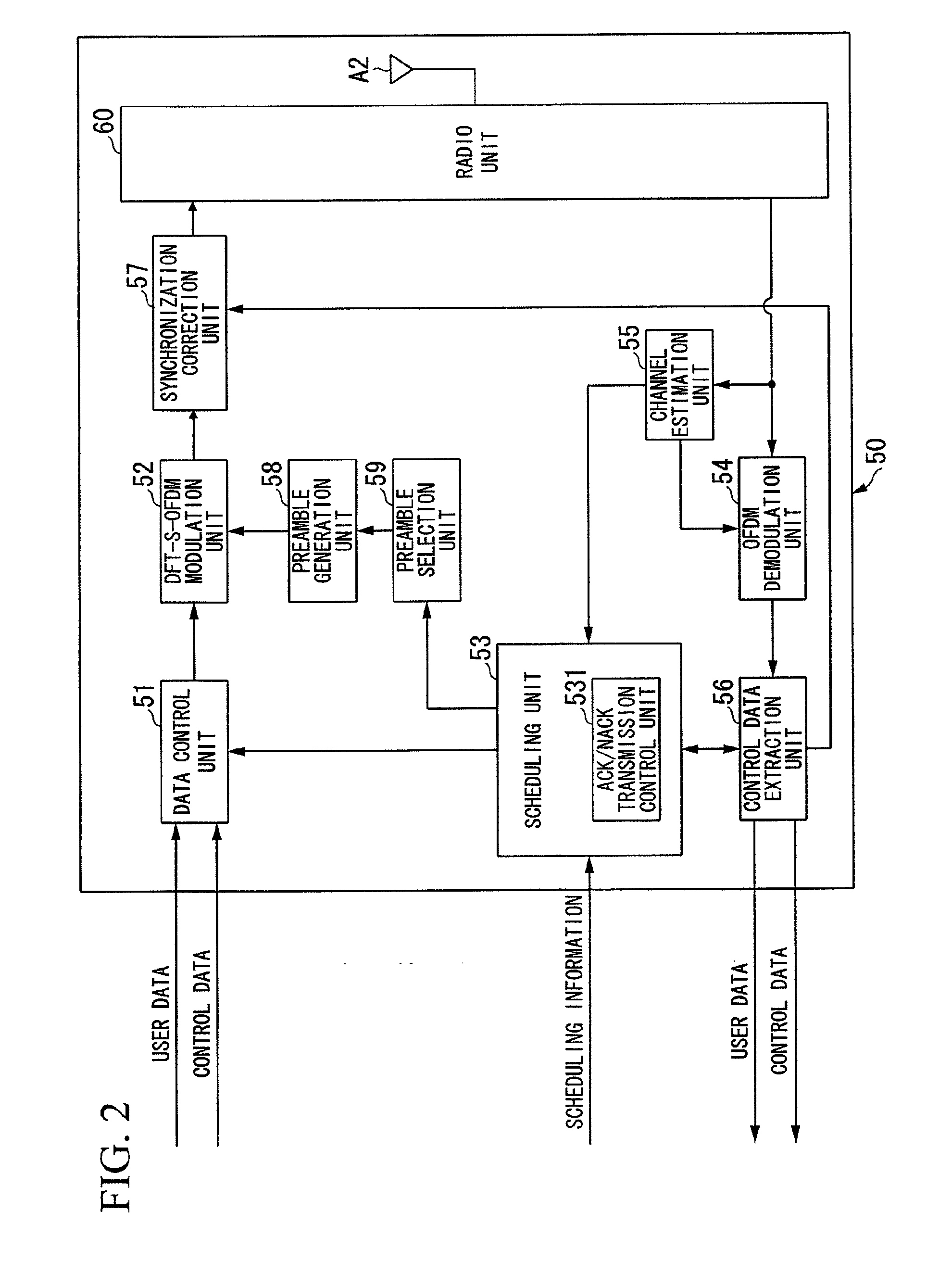
Radio communication system and mobile station device
ActiveUS20090316678A1Efficient communicationSynchronisation arrangementTime-division multiplexBase station identity codeCommunications system
A mobile station device transmits a random access preamble to a base station device and performs uplink timing alignment based on the synchronization timing deviation information included in a random access response which the base station device transmits in response to the transmitted random access preamble, wherein in an uplink synchronous status, the mobile station device does not perform uplink timing alignment based on synchronization timing deviation information included in a random access response, which is a response to a random access preamble whose preamble ID is randomly selected by the mobile station device.
Owner:HUAWEI TECH CO LTD
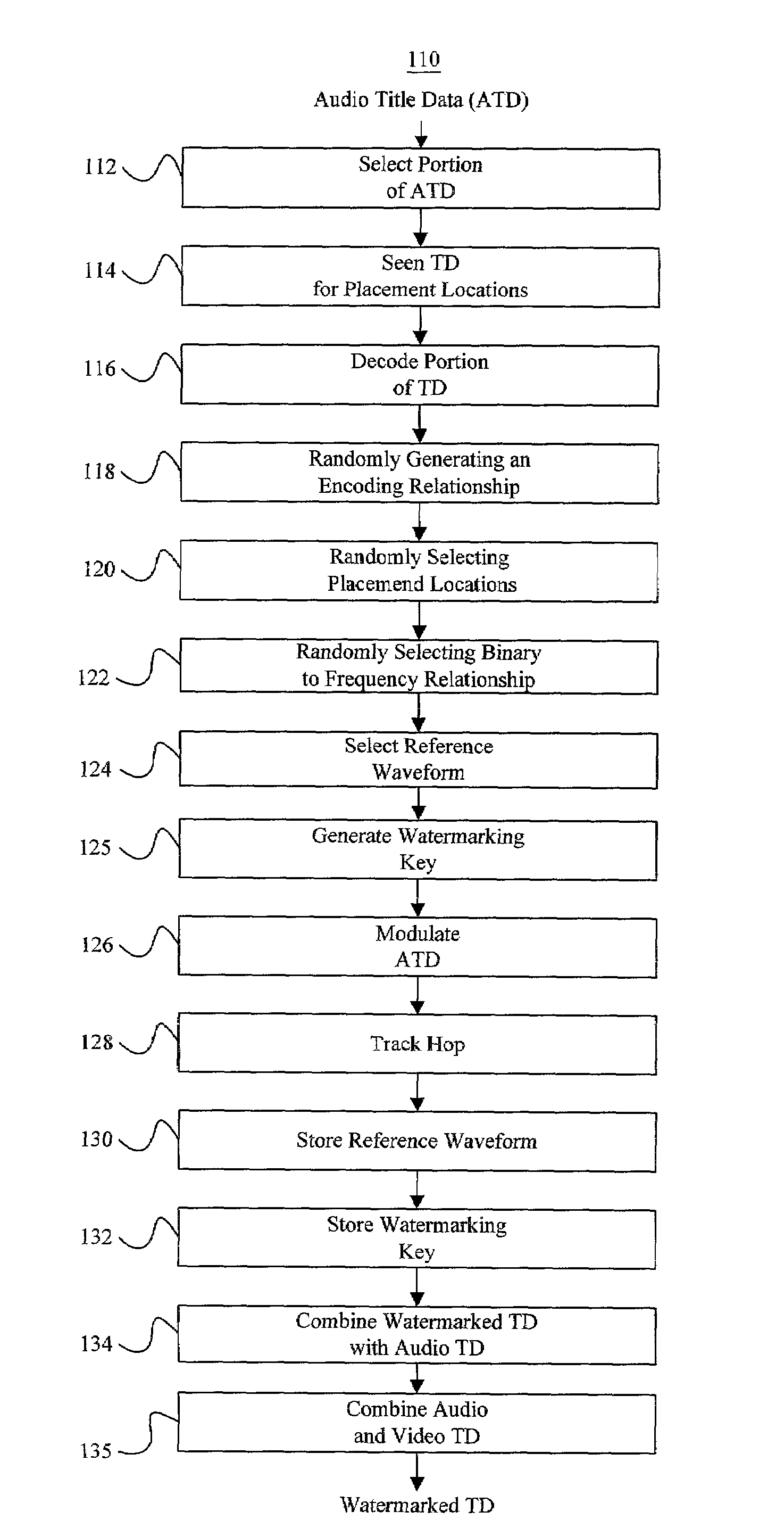
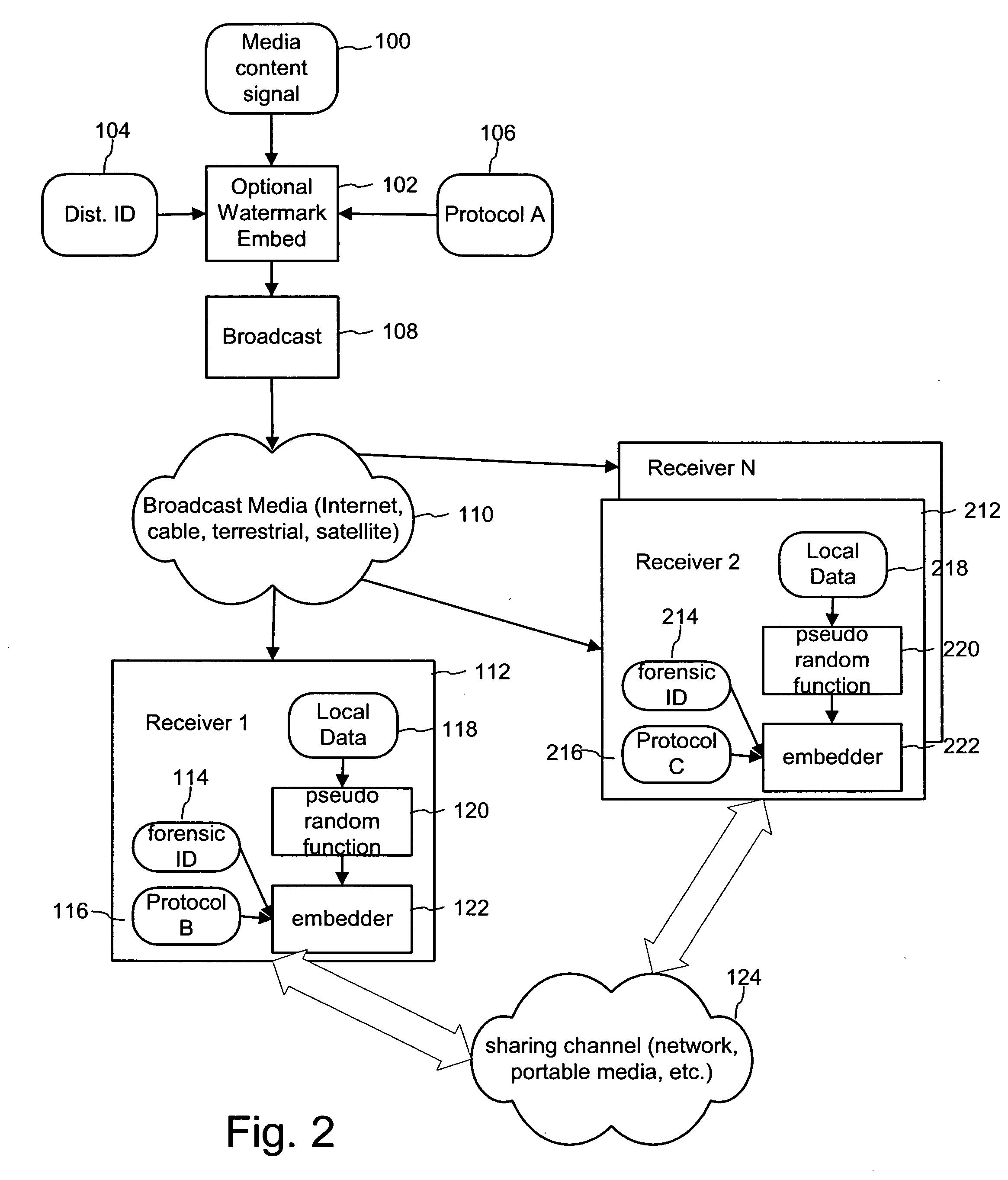
Method and system for data delivery and reproduction
ActiveUS7447907B2Digital data processing detailsUser identity/authority verificationRandom choiceFrequency modulation
A system and method for distributing title data, such as songs, videos or computer games. The title data is provided from a central location to a customer who may purchase or rent a copy of the title data. The title data is made available on a computer readable media, which may be physical media, such as a CD or DVD, or virtual media, such as a computer network. Before distribution, the title data is watermarked with information to identify the customer to whom the title data was distributed. The watermark may be created using identifying information to modulate the title data using a randomly selected modulation scheme at multiple randomly selected locations. The system stores an indication of the locations and frequency modulation scheme, allowing the identifying information to be recovered from the watermarked copy of the title data.
Owner:IPLA HLDG
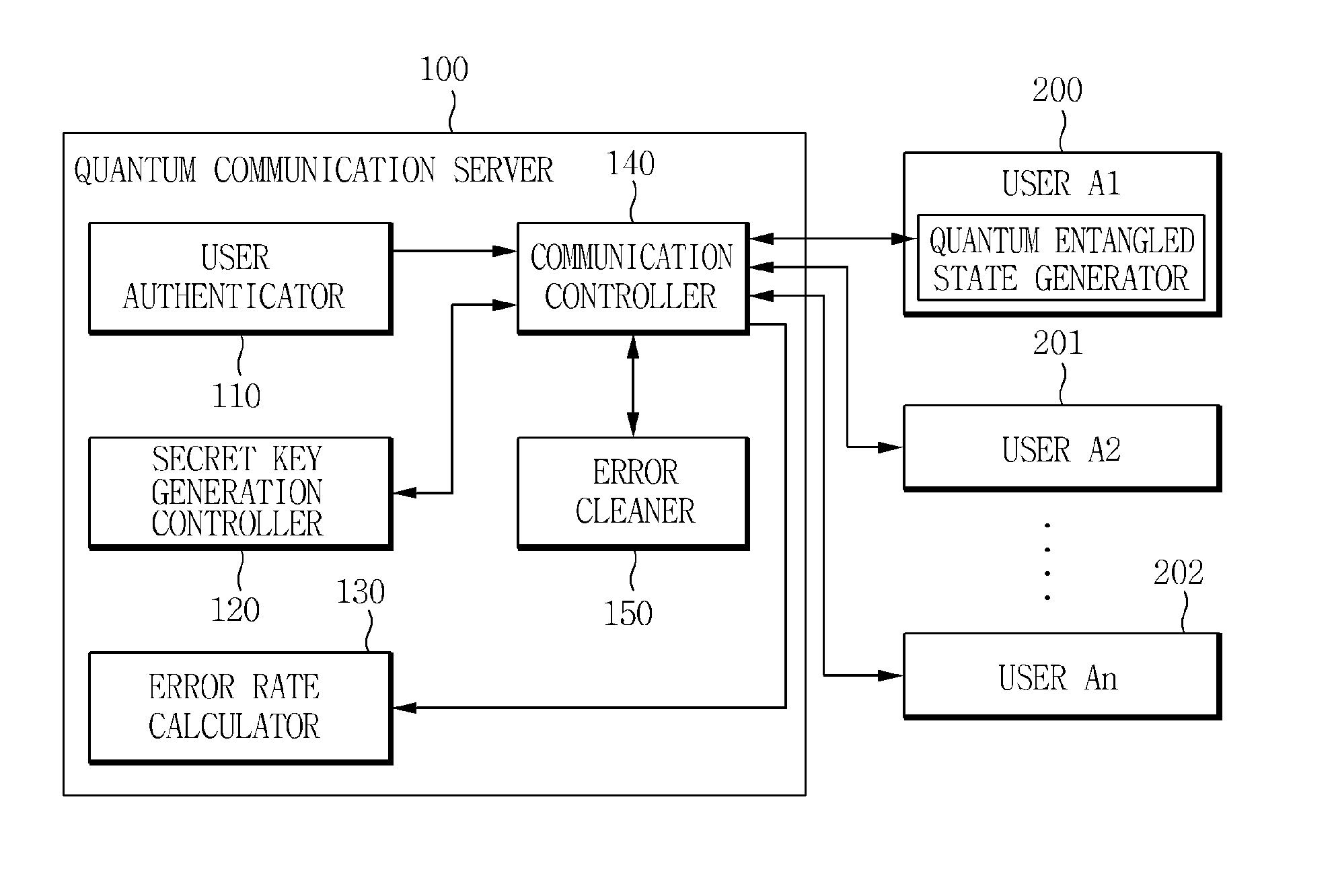
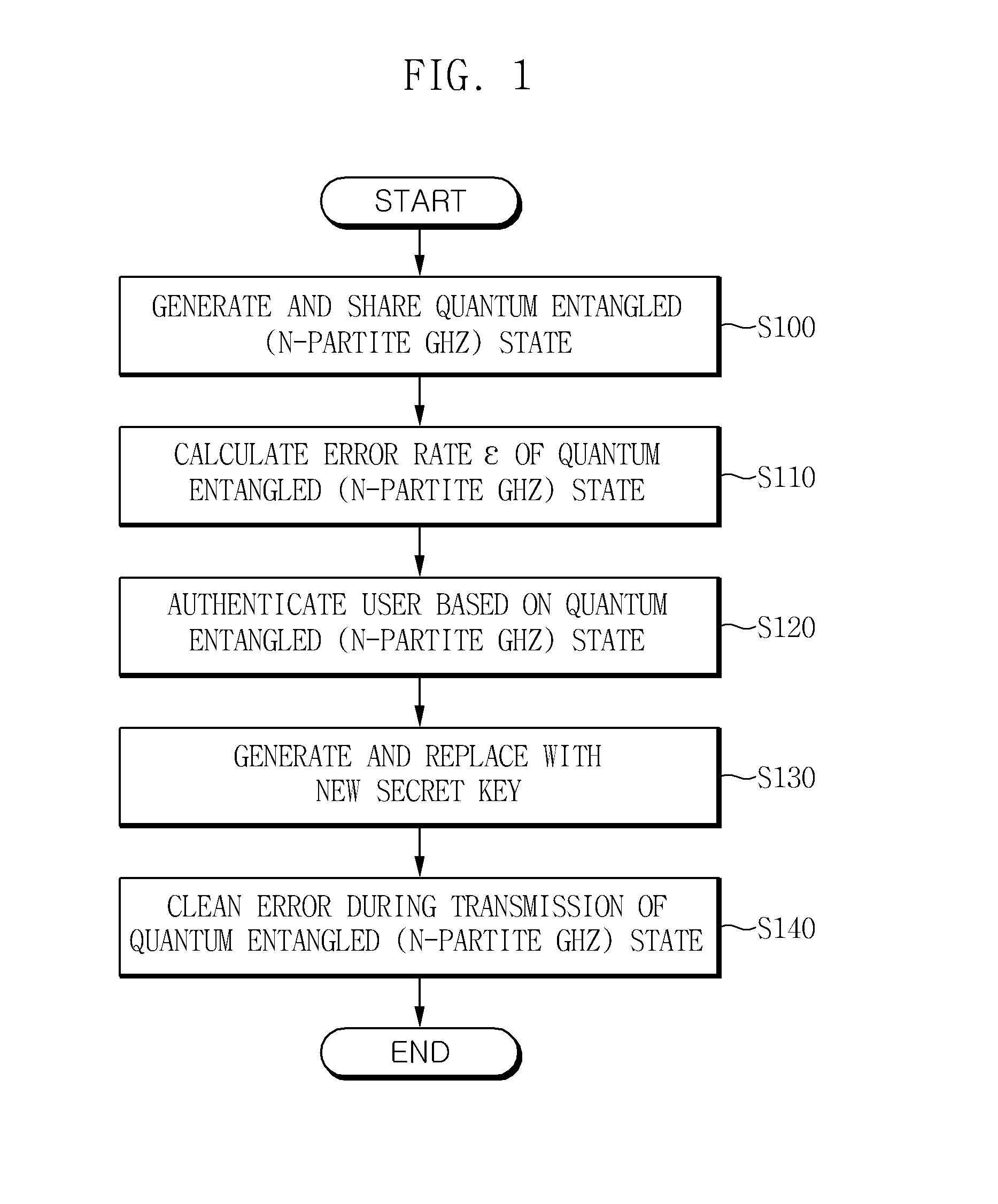
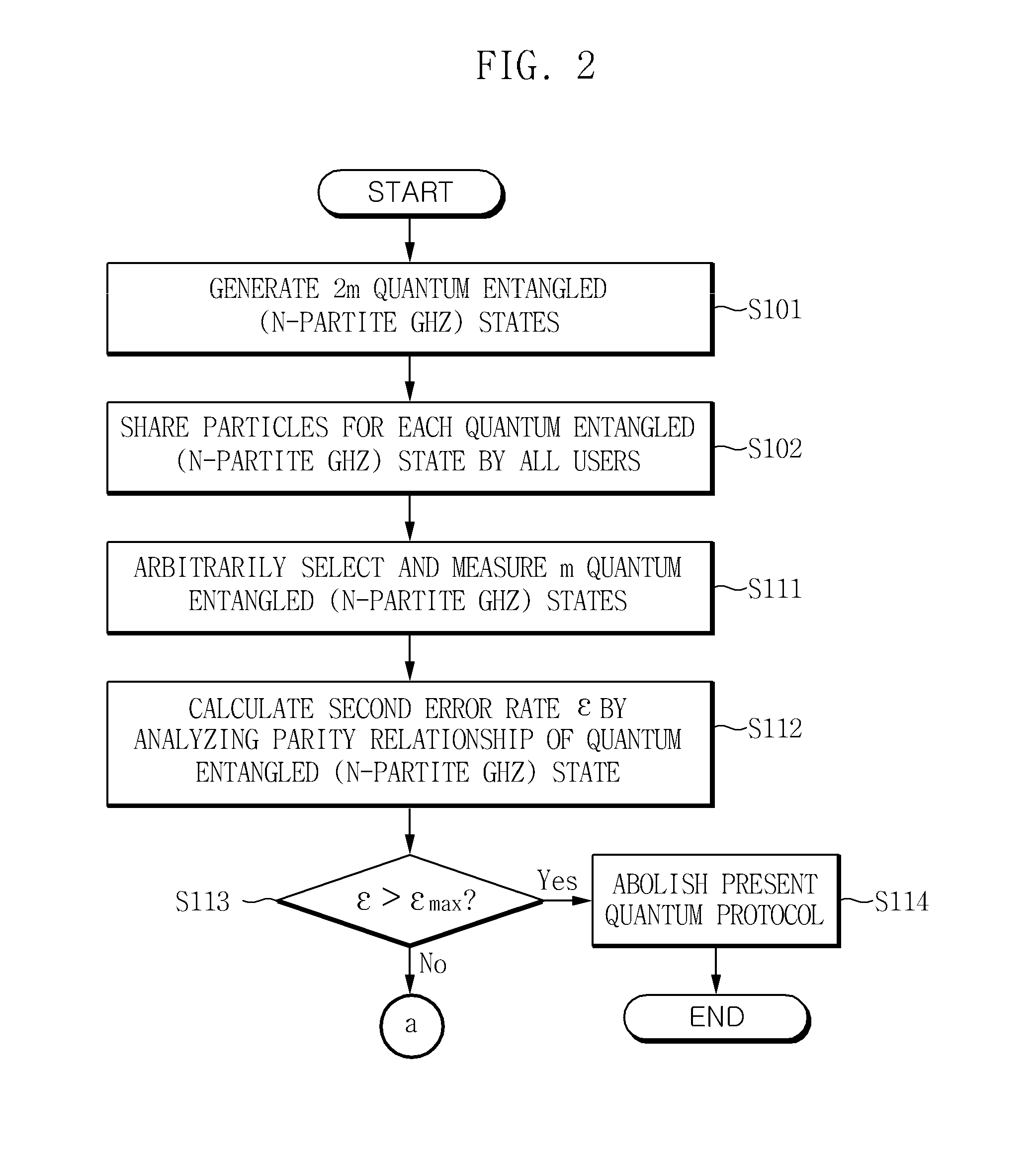
Method and apparatus for authenticating user in multiparty quantum communications
InactiveUS20140068765A1Ensure safetyMemory loss protectionError detection/correctionQuantum entanglementRandom choice
Owner:ELECTRONICS & TELECOMM RES INST
Digital watermarking with variable orientation and protocols
InactiveUS20050039020A1Improve the immunityAccurate detectionUser identity/authority verificationAnalogue secracy/subscription systemsRandom choiceDigital watermarking
The invention provides a method of forensic digital watermarking that randomly selects an orientation and / or embedding protocol for a digital watermark signal to be embedded in the content signal. It then embeds the digital watermark signal at the selected orientation in the content signal. The embedding applies a different orientation to the forensic watermark for each instance of embedding a watermark. This thwarts averaging and over-embedding attacks.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
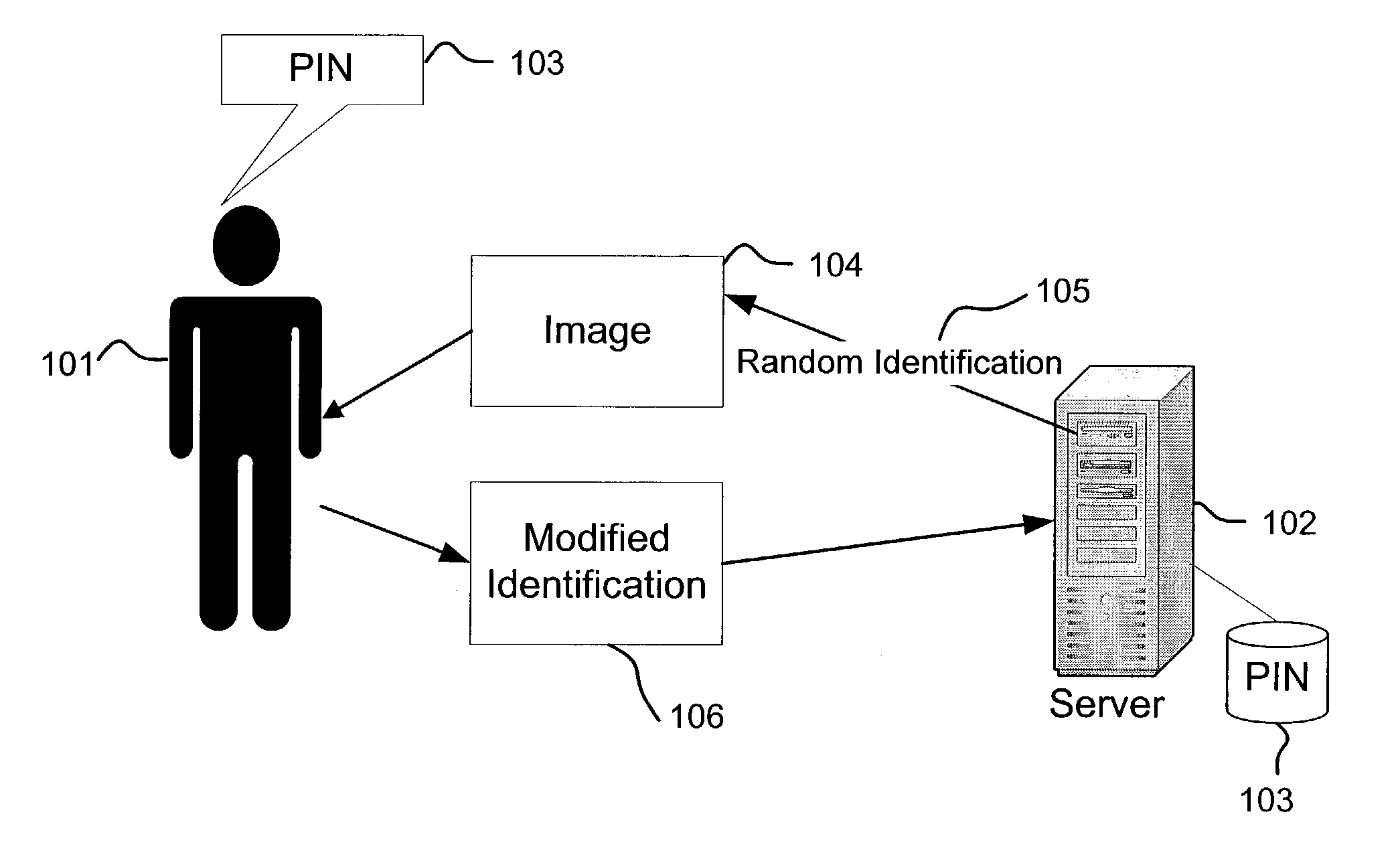
Establishing a secure channel with a human user
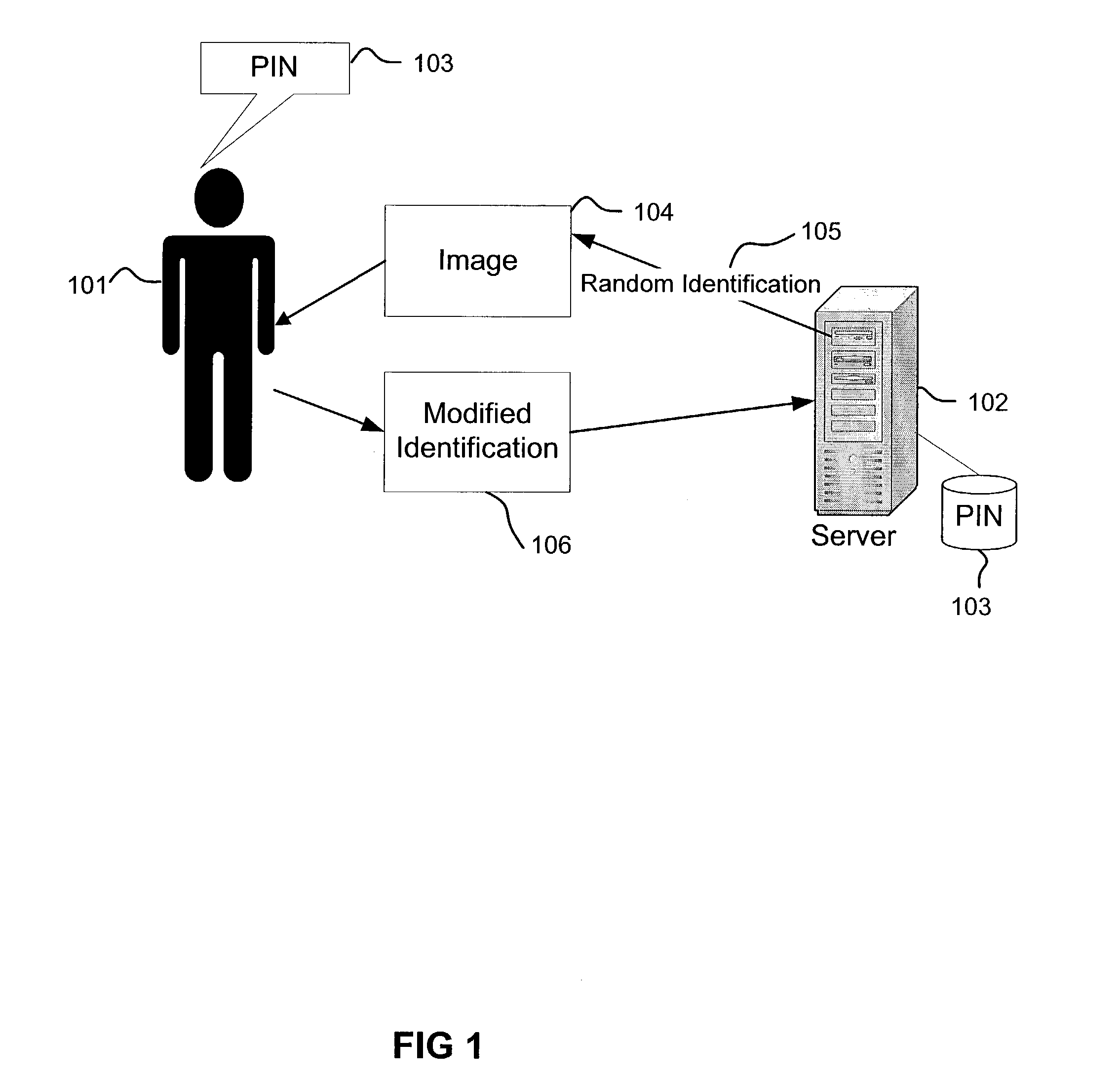
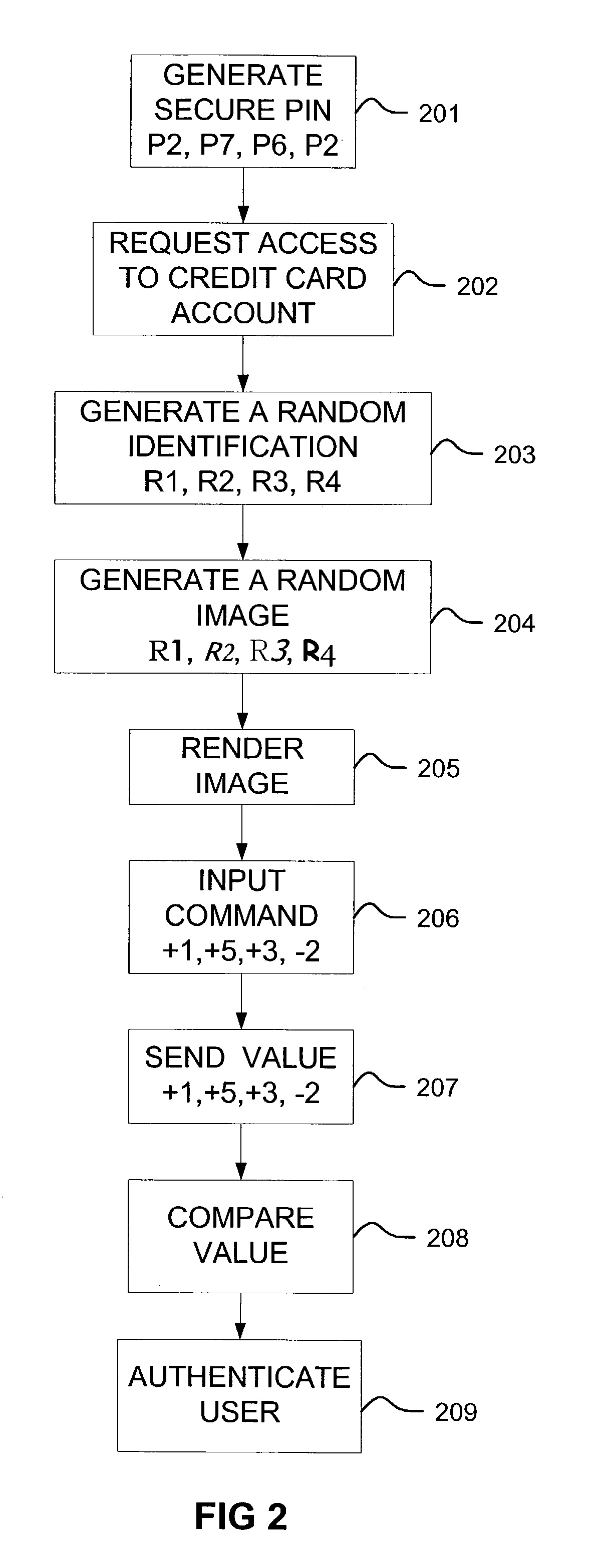
ActiveUS7149899B2Digital data processing detailsUser identity/authority verificationRandom choiceUnique identifier
A method of establishing a secure channel between a human user and a computer application is described. A secret unique identifier (“PIN”) is shared between a user and an application. When the user makes a request that involves utilizing the PIN for authentication purposes, the application renders a randomly selected identifier. The randomly selected identifier is in a format that is recognizable to a human but is not readily recognizable by an automated agent. The randomly selected identifier is then presented to the human user. The user identifies the relationship between the randomly selected identifier and the PIN. If the user's input reflects the fact that the user knows the PIN, then the user is authenticated.
Owner:INTERTRUST TECH CORP
Wireless communication system, communication control method and communication node
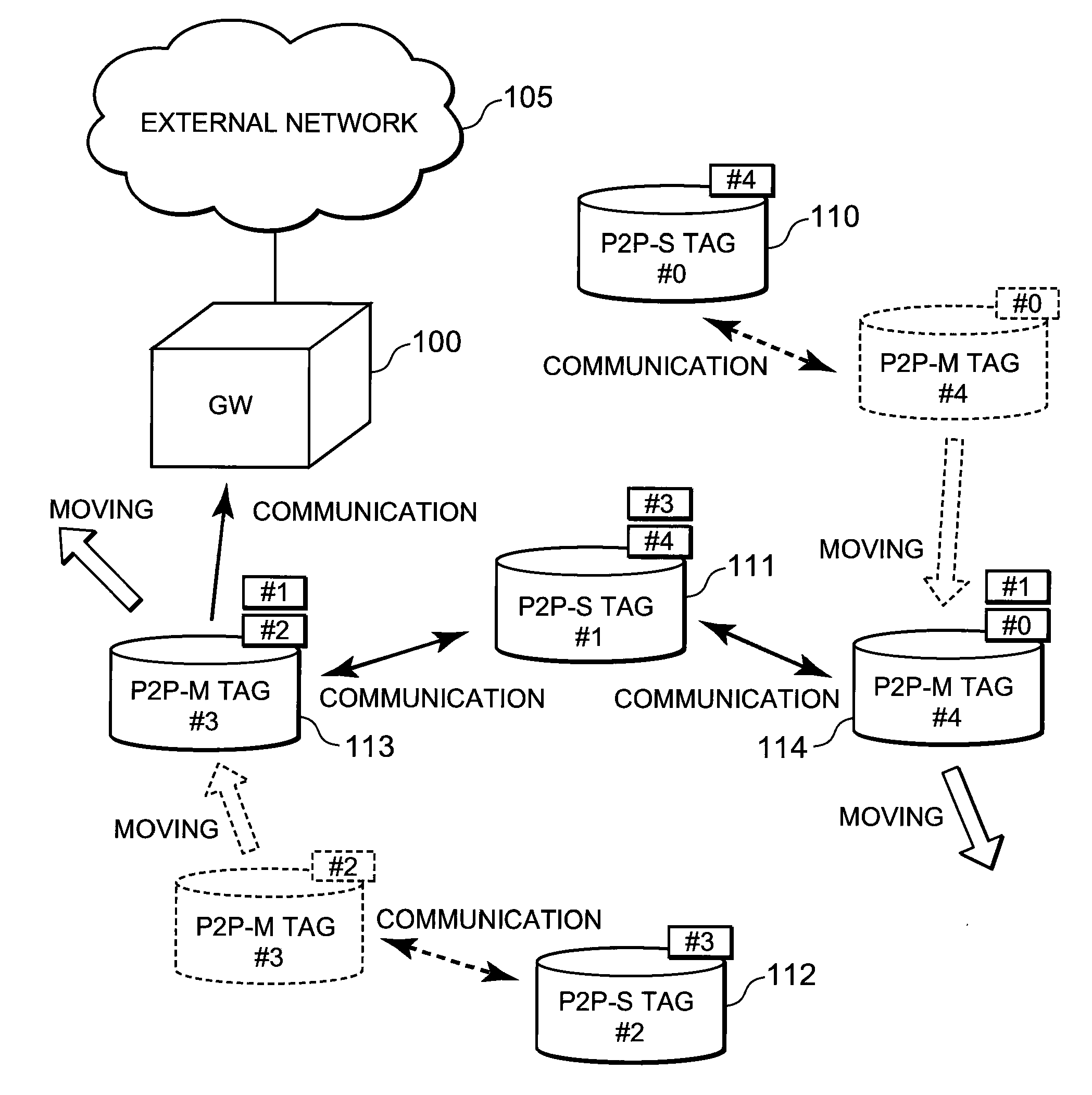
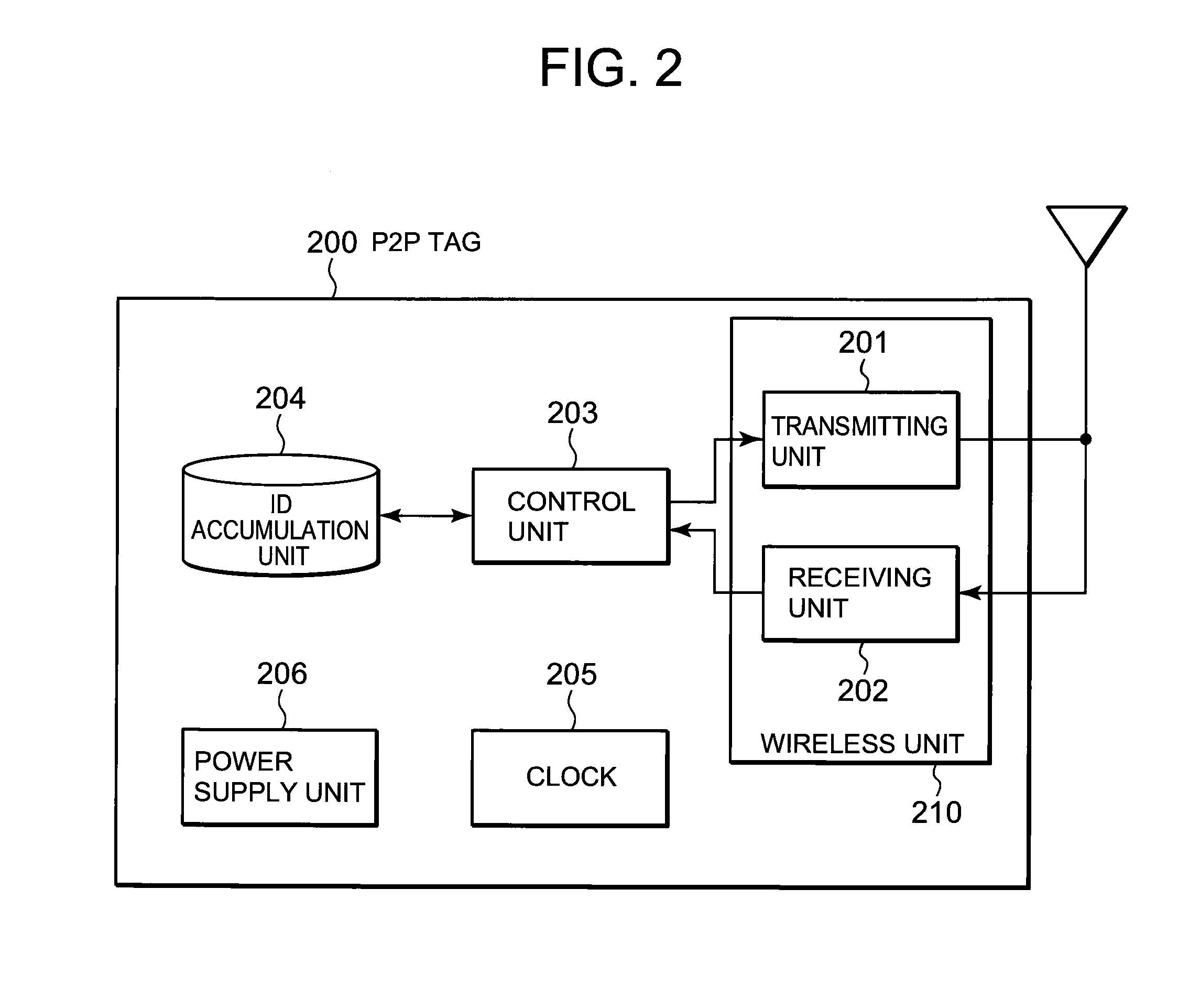
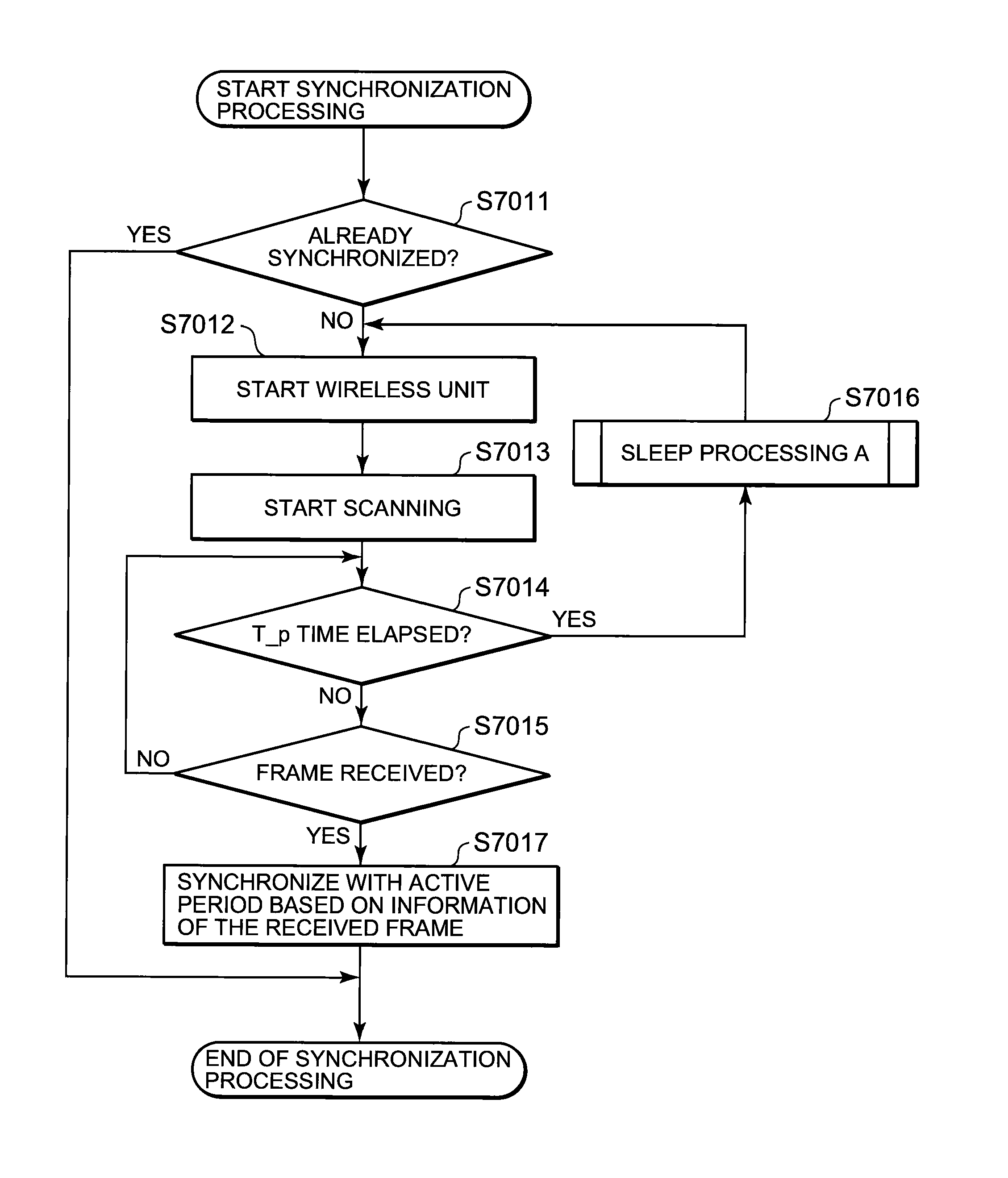
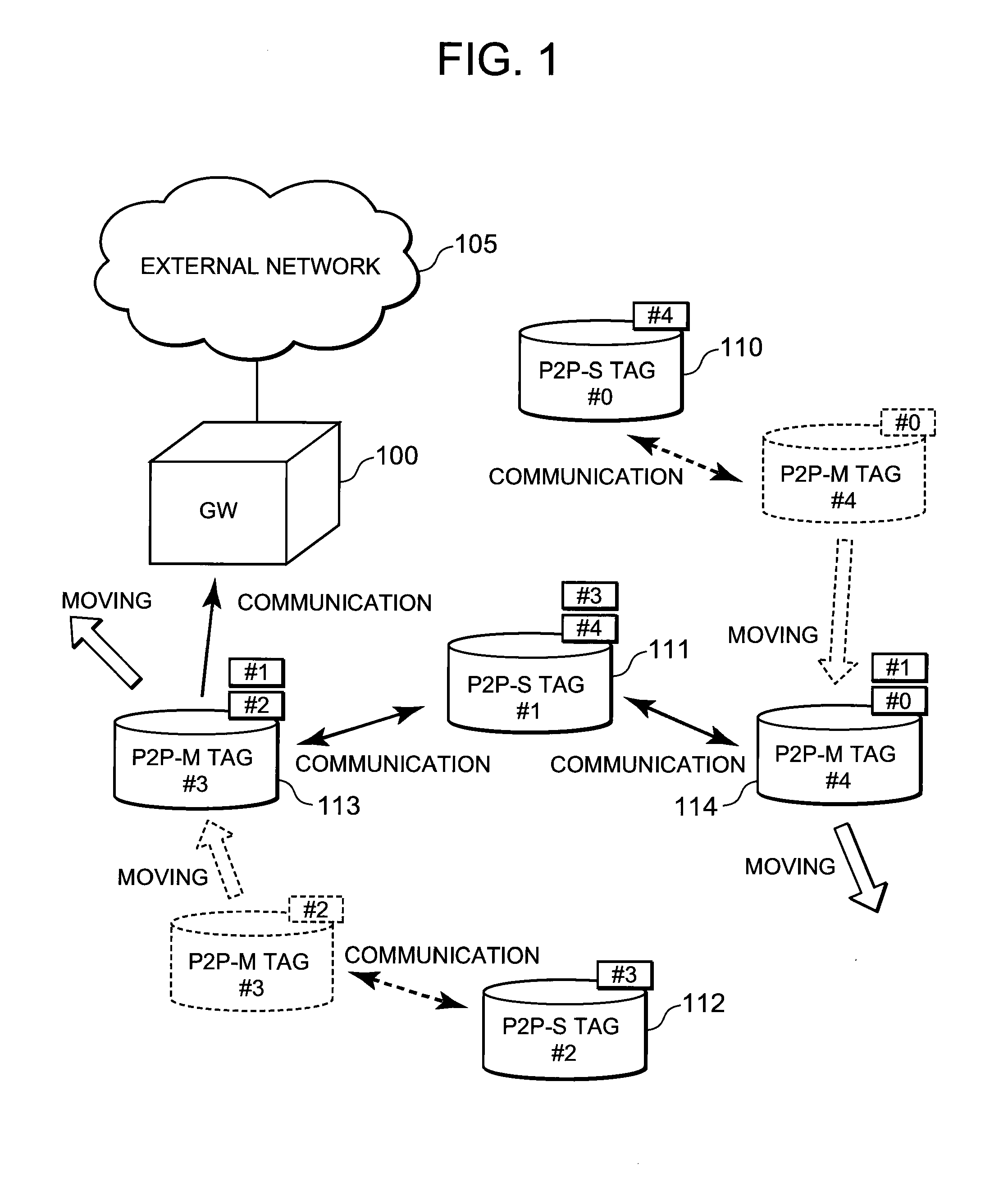
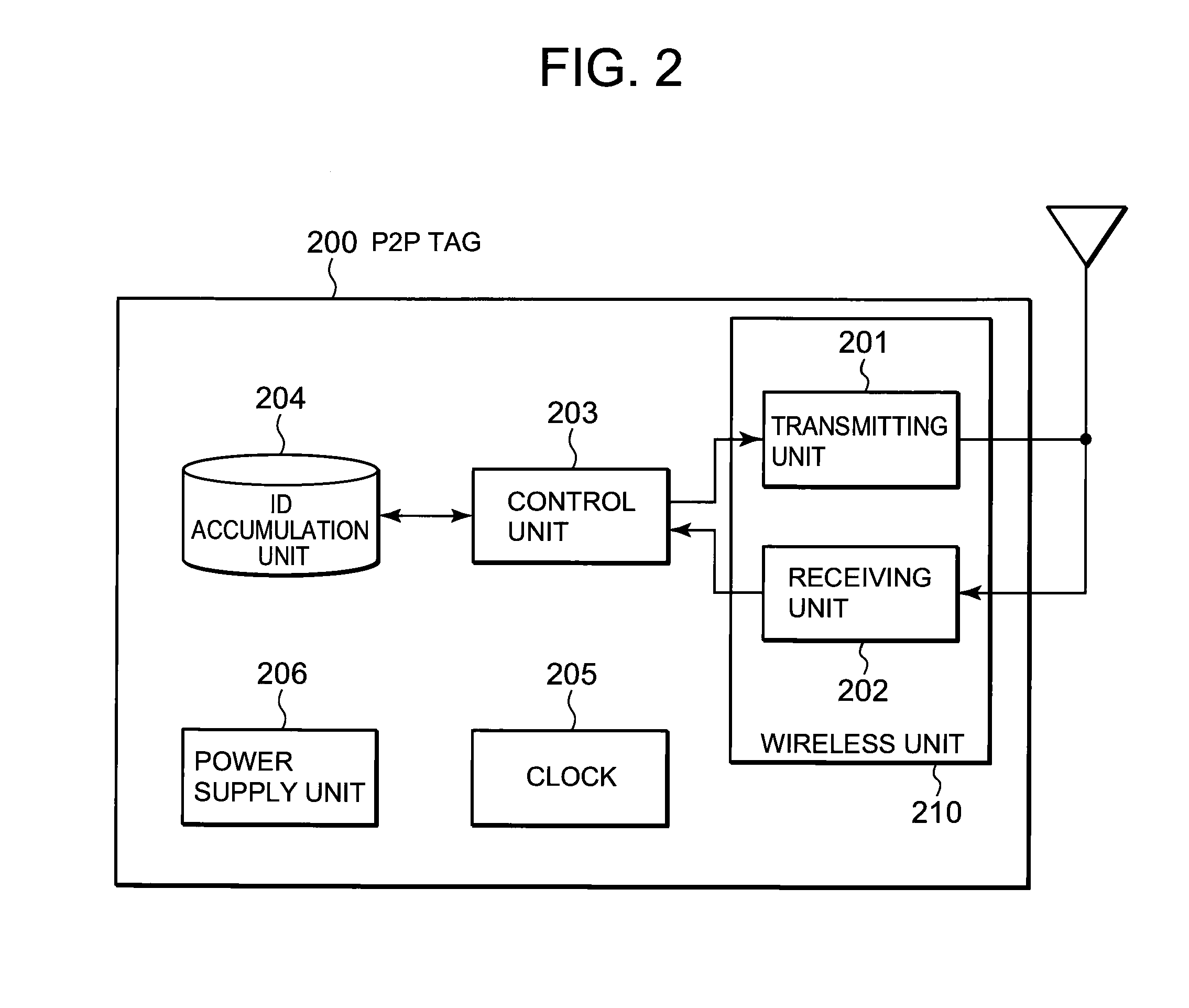
InactiveUS20100278087A1Effective controlReduce power consumptionEnergy efficient ICTPower managementCommunications systemWaiting period
A technique is disclosed, by which it is possible to achieve the reduction of power consumption of each wireless node and to perform efficient access control in wireless communication system. According to this technique, a given period with a beacon transmitted from a gateway (GW) 100 at the foremost position is divided to an active period where each wireless node (P2P tag) transmits and receives a frame and a sleep period where transmitting and receiving of the frames are stopped. Further, the active period is divided to a plurality of timeslots each with a fixed length, and the period is partitioned to sub-periods where each type of a GW, a fixed node (P2P-S tag), and a mobile node (P2P-M tag) can transmit frames respectively. Each of the P2P tags selects a timeslot at random from the period for each type, and after waiting for a waiting period at random at the selected timeslot, it transmits a frame including information to identify the selected timeslot or the waiting period in addition to its own ID.
Owner:PANASONIC CORP
Read disturb mitigation in non-volatile memory
ActiveUS7808831B2Mitigate read-disturbRead-only memoriesDigital storageRandom choiceComputer science
Read disturb is reduced in non-volatile storage. In one aspect, when a read command is received from a host for reading a selected word line, a word line which is not selected for reading is randomly chosen and its storage elements are sensed to determine optimized read compare levels for reading the selected word line. Or, a refresh operation may be indicated for the entire block based on an error correction metric obtained in reading the storage elements of the chosen word line. This is useful especially when the selected word line is repeatedly selected for reading, exposing the other word lines to additional read disturb. In another aspect, when multiple data states are stored, one read compare level is obtained from sensing, e.g., from a threshold voltage distribution, and other read compare levels are derived from a formula.
Owner:SANDISK TECH LLC
Watermarking with random zero-mean patches for copyright protection
InactiveUS6522766B1Efficient detectionUser identity/authority verificationCharacter and pattern recognitionRandom choiceProtection system
A steganographic method embeds hidden information like digital watermarks and digital fingerprints into an image by applying one or more zero-mean patches to a digital signal that conveys the image. Each zero-mean patch comprises elements having an average value substantially equal to zero. A copyright protection system is implemented by selecting one or more zero-mean patches in pseudo-random fashion, modifying the patches by perturbing their elements in pseudo-random fashion, and applying the patches to image pixels at locations that are selected in pseudo-random fashion. The copyright protection system further includes a procedure for checking for the presence of a watermark in a digital signal.
Owner:SEIKO EPSON CORP
Random biometric authentication apparatus
InactiveUS7793109B2Digital data processing detailsUser identity/authority verificationElectronic systemsUser input
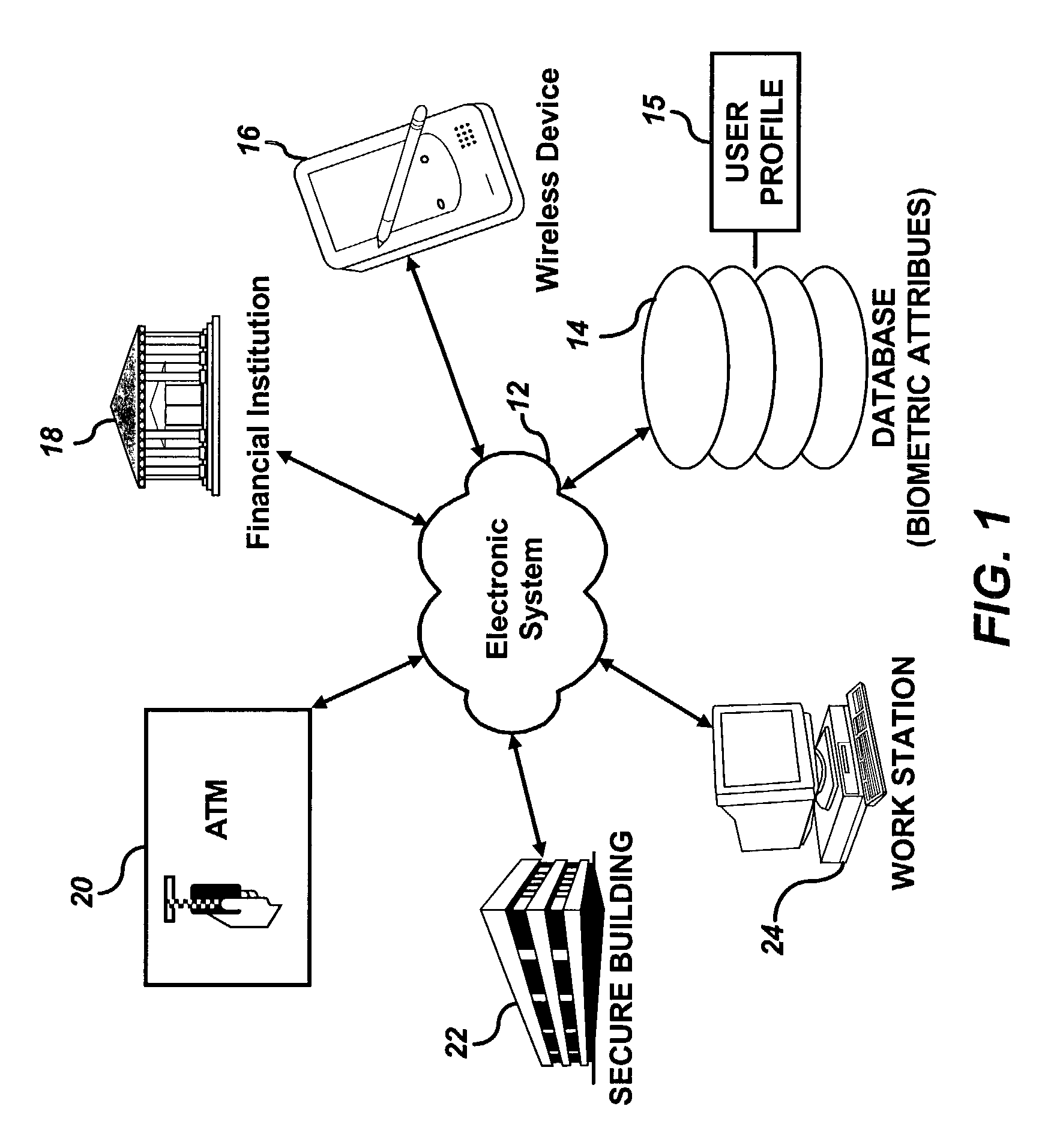
A biometric apparatus for biometrically securing access to an electronic system is disclosed. Such an apparatus can be configured to include a hardware unit having an input area integrated therein for inputting at least one biometric attribute. The hardware unit can communicate with an electronic system, such as, for example, a building, a computer, a computer network, wireless network, ATM machine, electronic database, etc. A display area can be integrated with the hardware unit, wherein the display area displays data which prompts a user to input to the input area one or more biometric attributes randomly selected from a user profile containing biometric attributes of the user. A biometric module can also be associated with the hardware unit, wherein the biometric module permits the user to perform a user-desired activity, if one or more biometric attributes input by the user via the input area matches at least one biometric attribute randomly selected from the user profile.
Owner:IP VENUE LLC
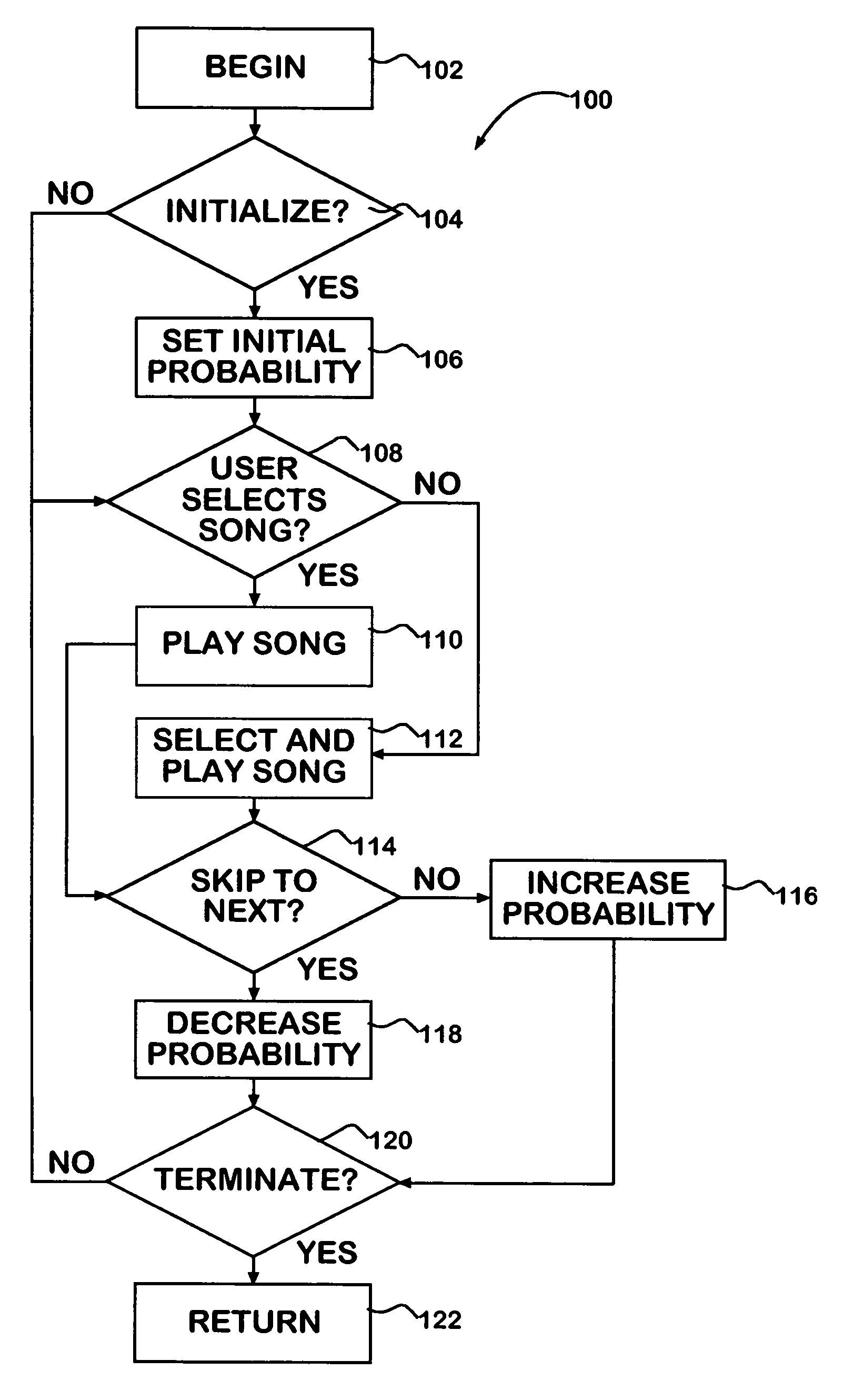
Preference-weighted semi-random media play
Owner:GALE JOSHUA
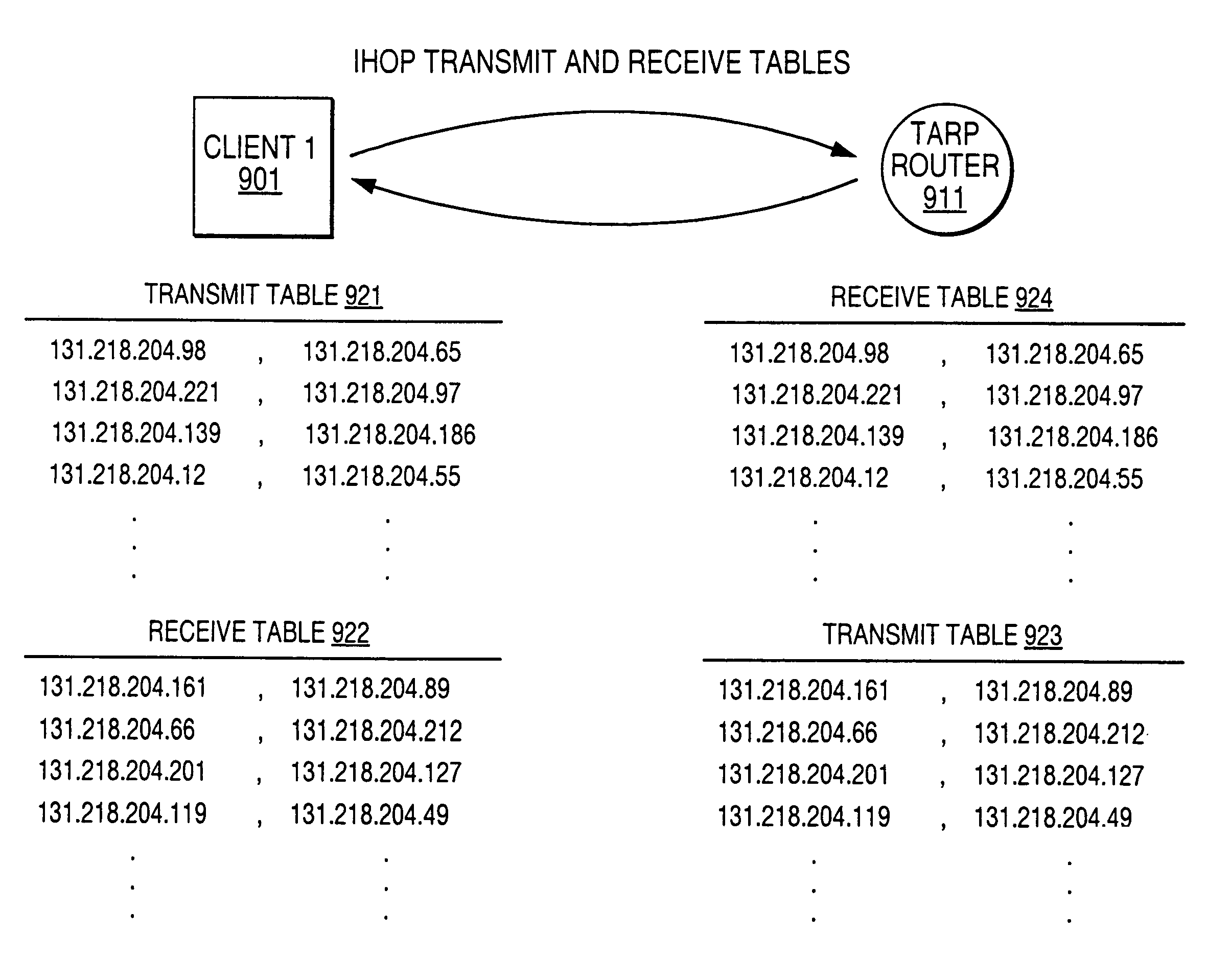
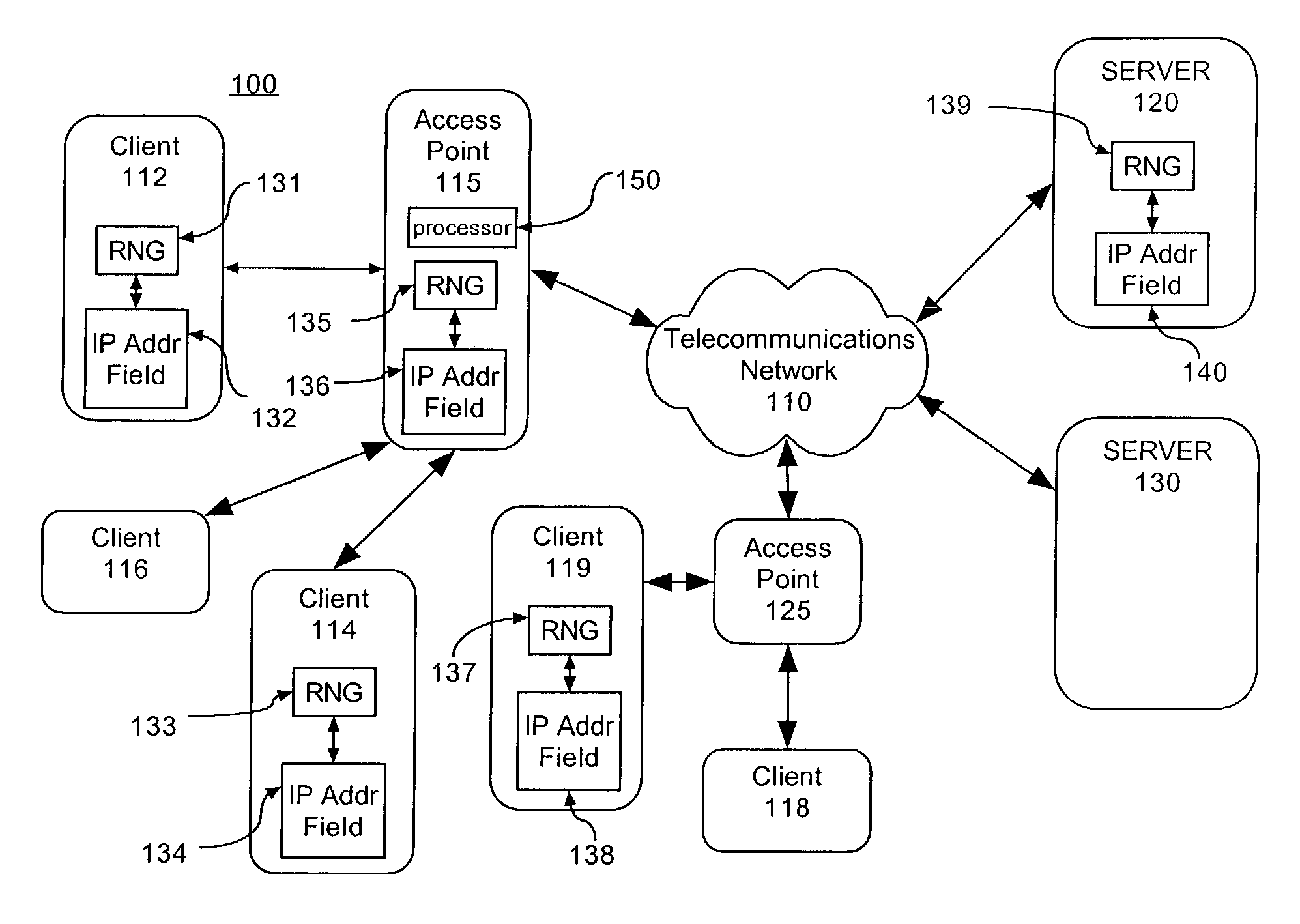
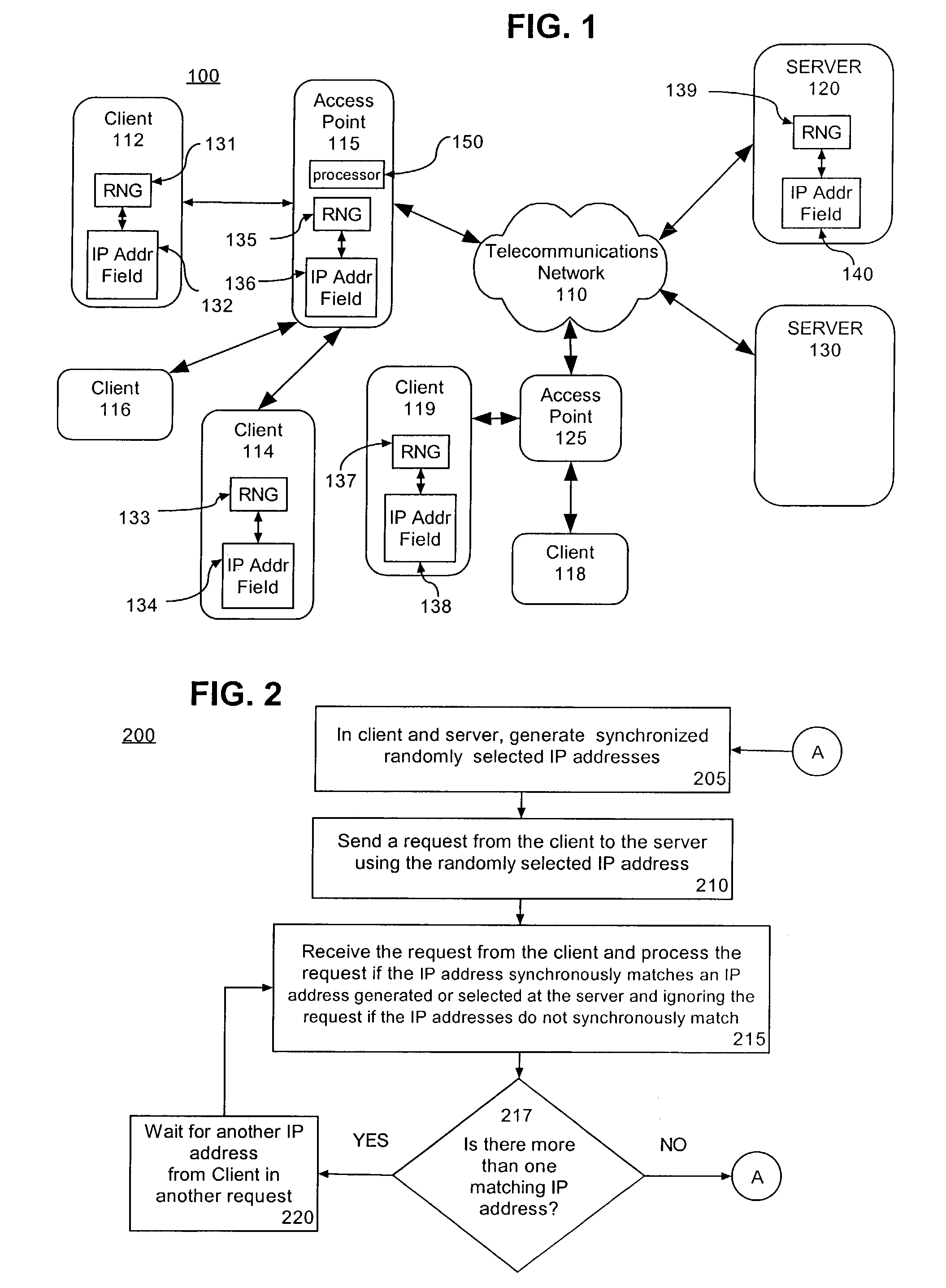
Secure communication overlay using IP address hopping
ActiveUS7216359B2Random number generatorsUser identity/authority verificationSecure communicationCommunication interface
A server (115) having a communication link comprises an application execution environment, a random IP address generator application (135) executing within the application execution environment of the server to randomly select (205) an IP address, a communications interface configured to send outbound data or to receive inbound data thereby establishing the communications link in coordination with the random IP address generator application and a processor (150). Preferably, the processor is programmed to receive a request from a client (112 or 114) and process the request if an IP address randomly selected at the client synchronously matches the randomly selected IP address at the server. Additionally, the processor can be further programmed to ignore the request from the client if the IP address randomly selected at the client fails to synchronously match the randomly selected IP address at the server.
Owner:TREND MICRO INC
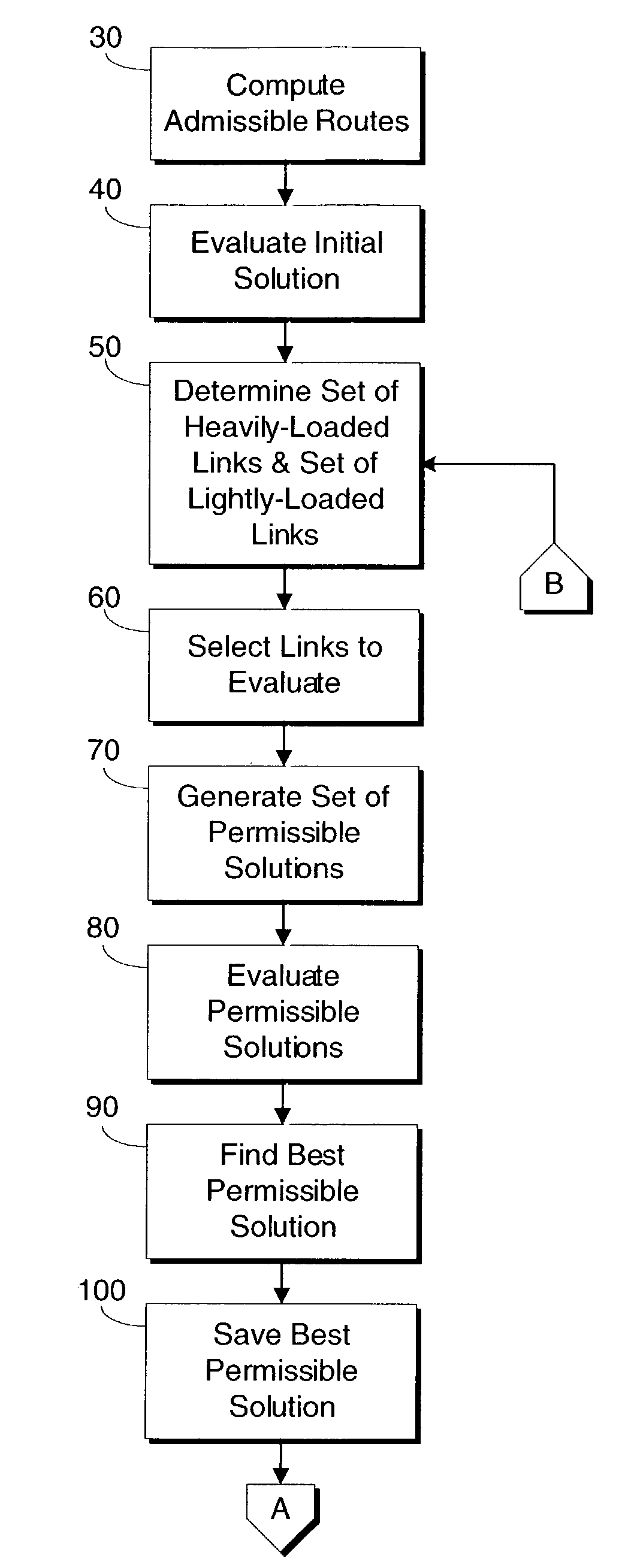
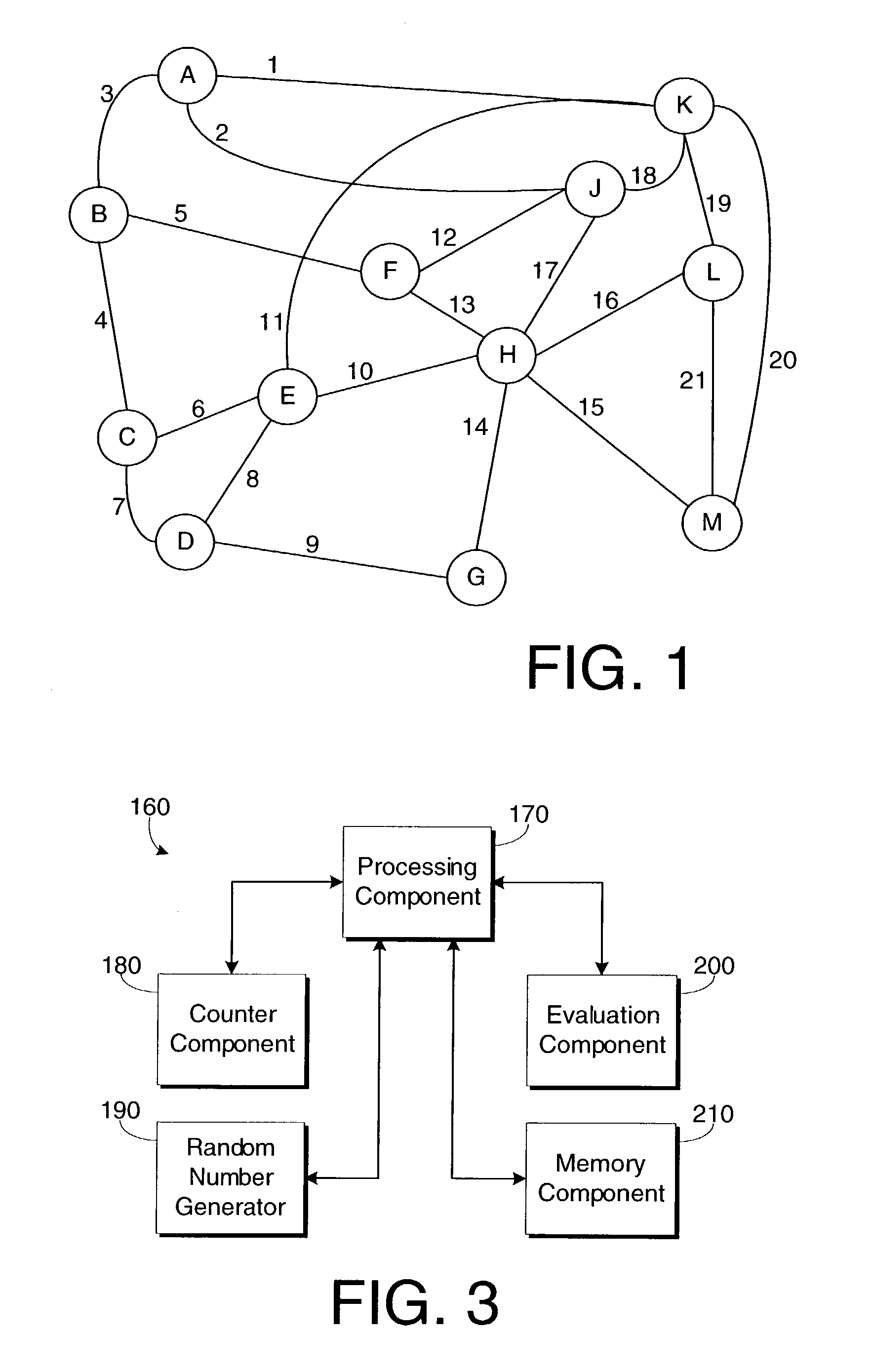
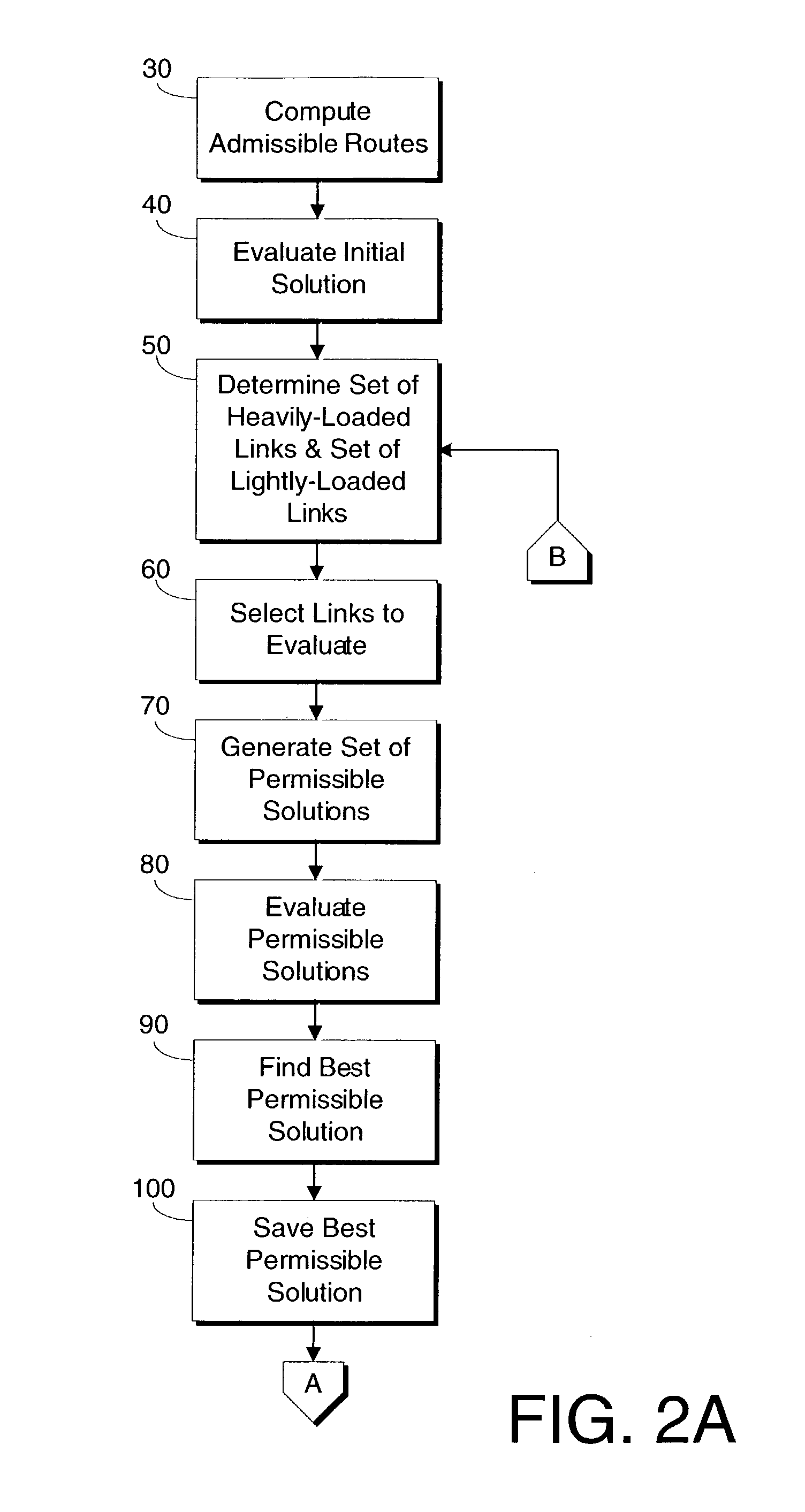
Method for assigning link weights in a communications network
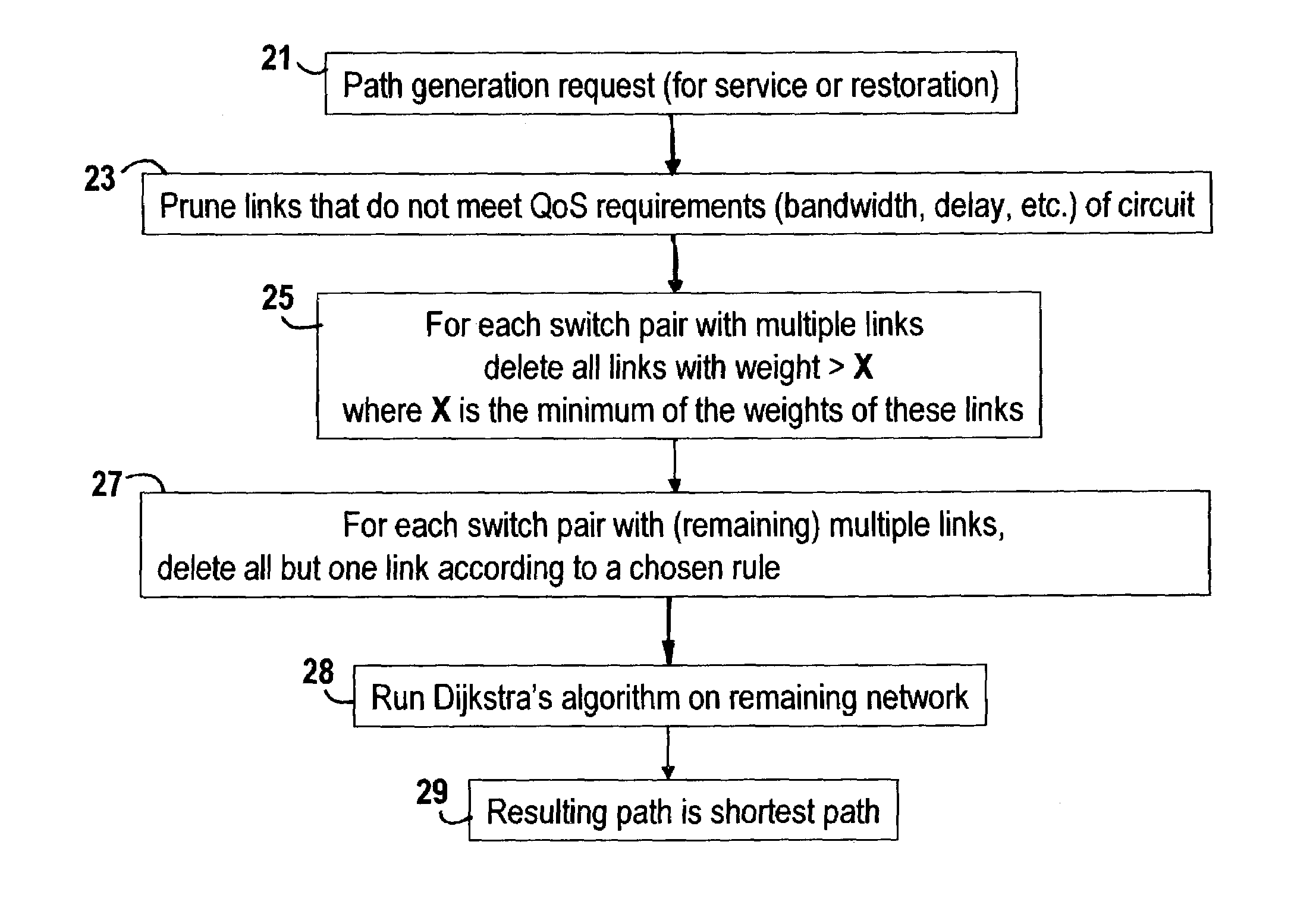
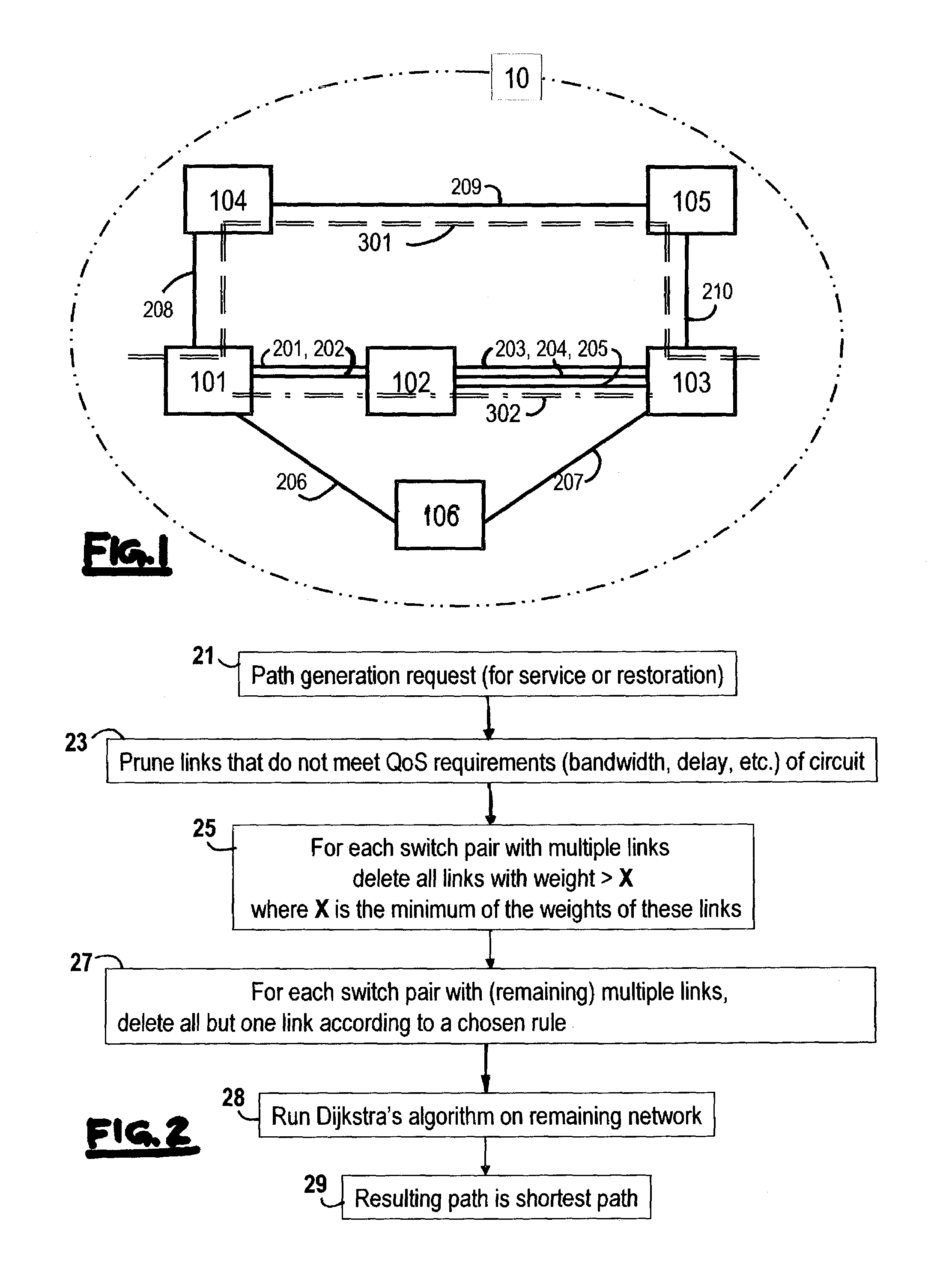
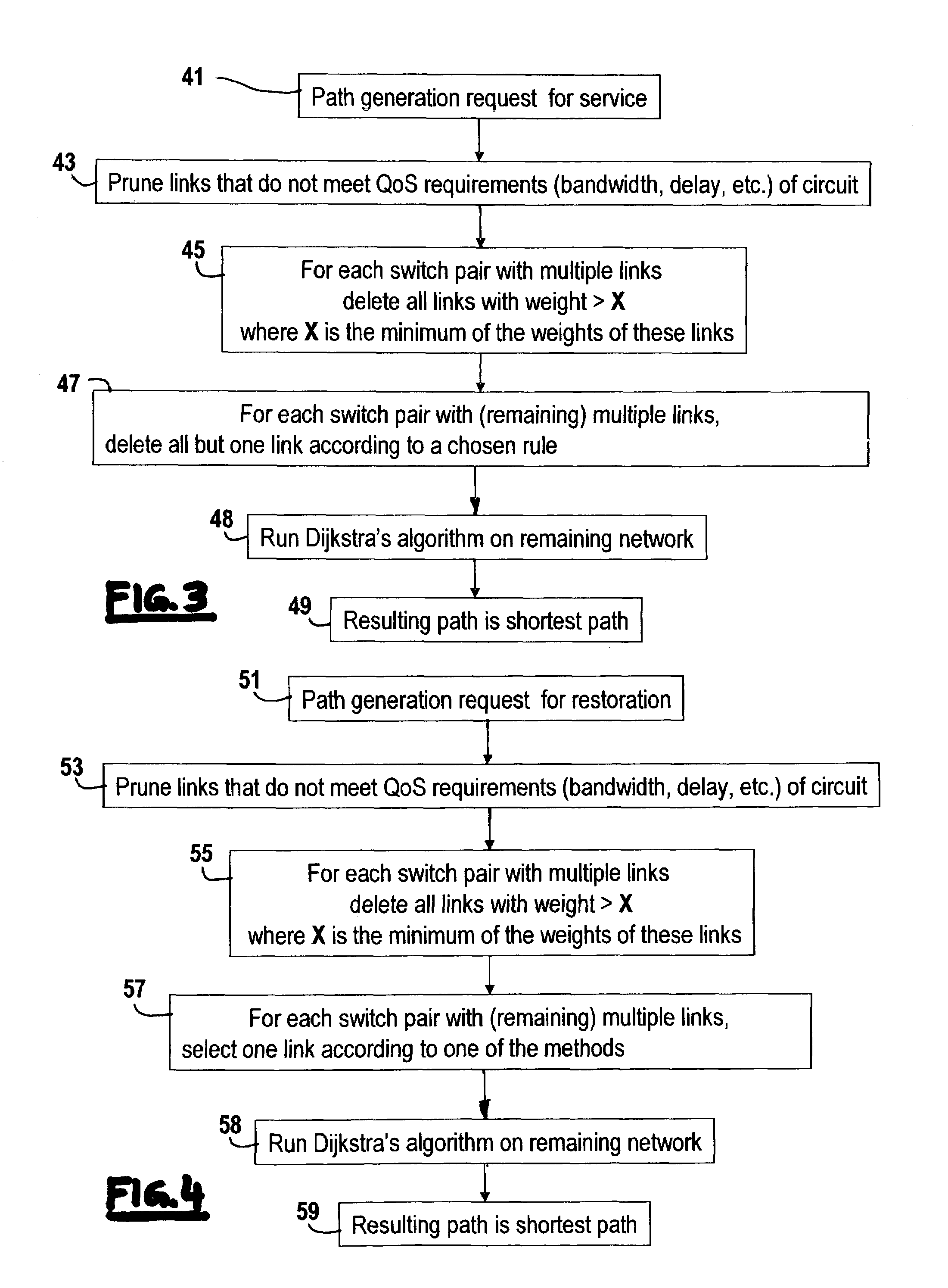
InactiveUS7395351B1Improve performanceEfficient workError preventionFrequency-division multiplex detailsLink weightRandom choice
The present invention includes a method and system for determining link weights that when utilized will optimize the performance of a network in the event of a link failure without the need to alter the link weights. The method includes determining two sets of links, one that includes links with a significant amount of loading and one that includes links with a modest amount of loading. A set of permissible solutions is generated utilizing one randomly chosen link from each set. After omitting recent best permissible solutions, the remaining permissible solutions are evaluated by analyzing for the complete network topology and for the topologies corresponding to all single-link failure states and the best permissible solution is found. If the best permissible solution is better than the current optimal solution, then the best permissible solution is made the optimal solution. These steps are repeated until a predetermined number of iterations have been evaluated without a change in the optimal solution. When that occurs, the number of links used to generate the set of potential solutions is randomly changed and the above-described steps are repeated. The method is complete after a second predetermined number of iterations have been evaluated no matter how many changes to the optimal solution.
Owner:SPRINT CORPORATION
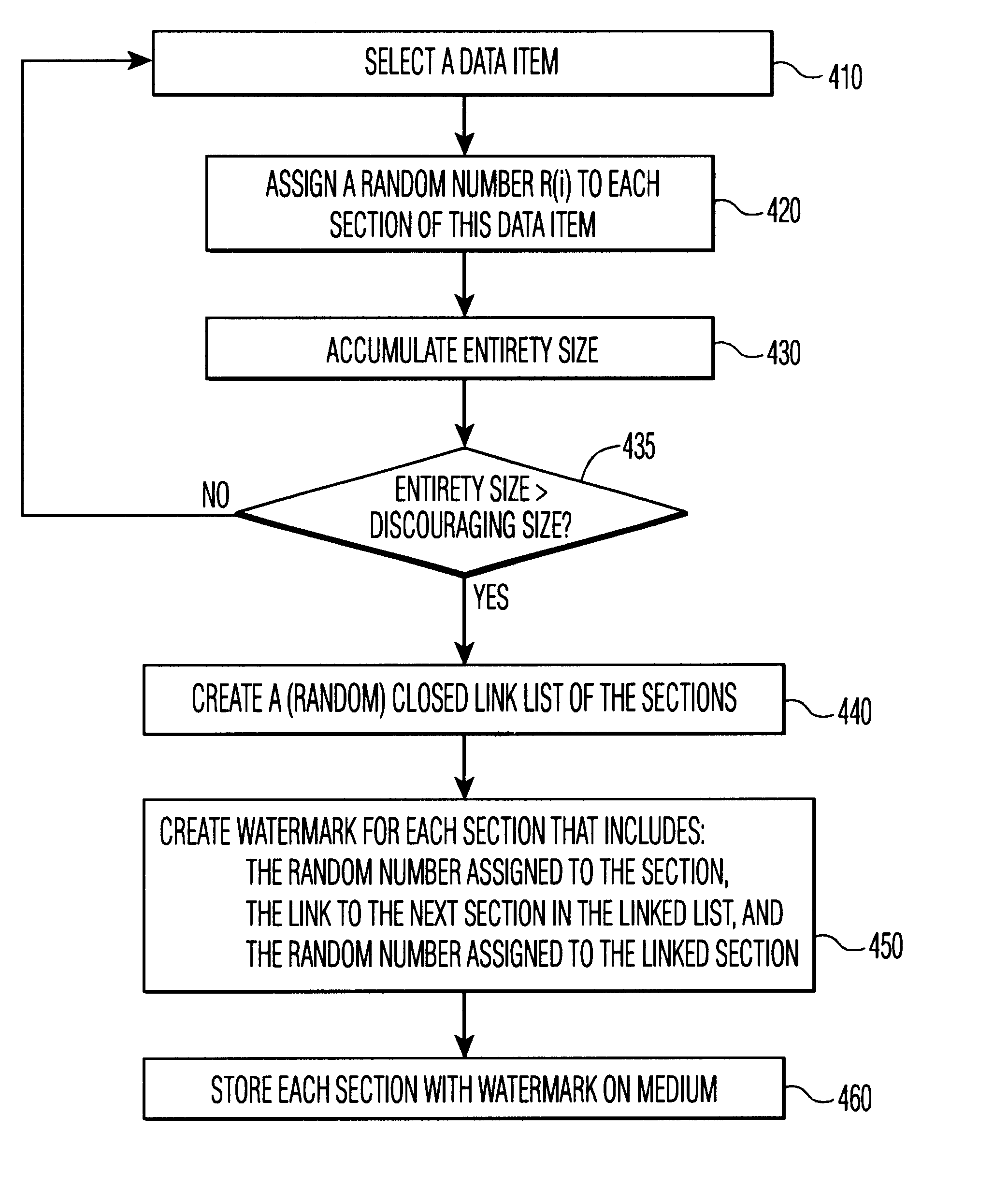
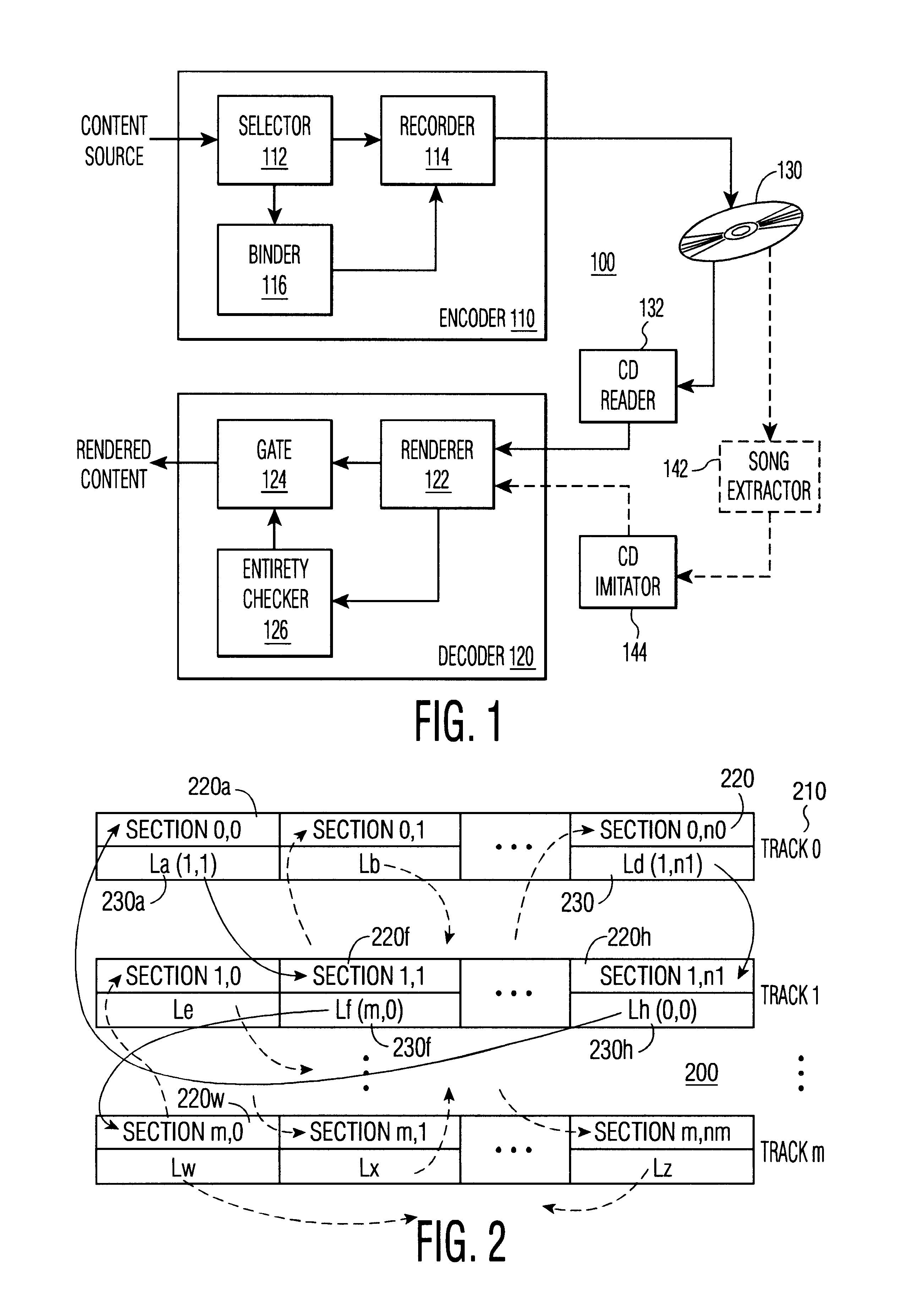
Protecting content from illicit reproduction by proof of existence of a complete data set via a linked list
InactiveUS6865676B1Avoid spreadingData of data set is preventedData processing applicationsDigital data processing detailsComplete dataData set
A sufficient number of data items are selected for inclusion in a data set so as to discourage a transmission of the entire set over a limited bandwidth communications path, such as the Internet. Each data item comprises one or more sections, which taken together constitute the complete data set. Each section of the data set is linked to another section of the data set, and each section's link is bound to the section via the use of one or more watermarks. Upon presentation of material for rendering, the presence of the entirety of the data set is verified by ascertaining the presence of linked-to sections. For further security, the links between sections is formed by a random selection of each linked-to section. To verify that each linked-to section corresponds to the original section that was linked-to, each link contains an identifier of the linked-to section that can be used to determine that a retrieval of a linked-to section corresponds to the originally assigned linked-to section. If the identifier associated with the linked-to section does not properly match the presented linked-to section, a rendering of the data items of the data set is prevented. In a preferred embodiment, a closed linked list is formed, so that every section of the data set can be included in the verification process, if desired.
Owner:KIOBA PROCESSING LLC
Wagering game with player-determined symbol function
Owner:LNW GAMING INC
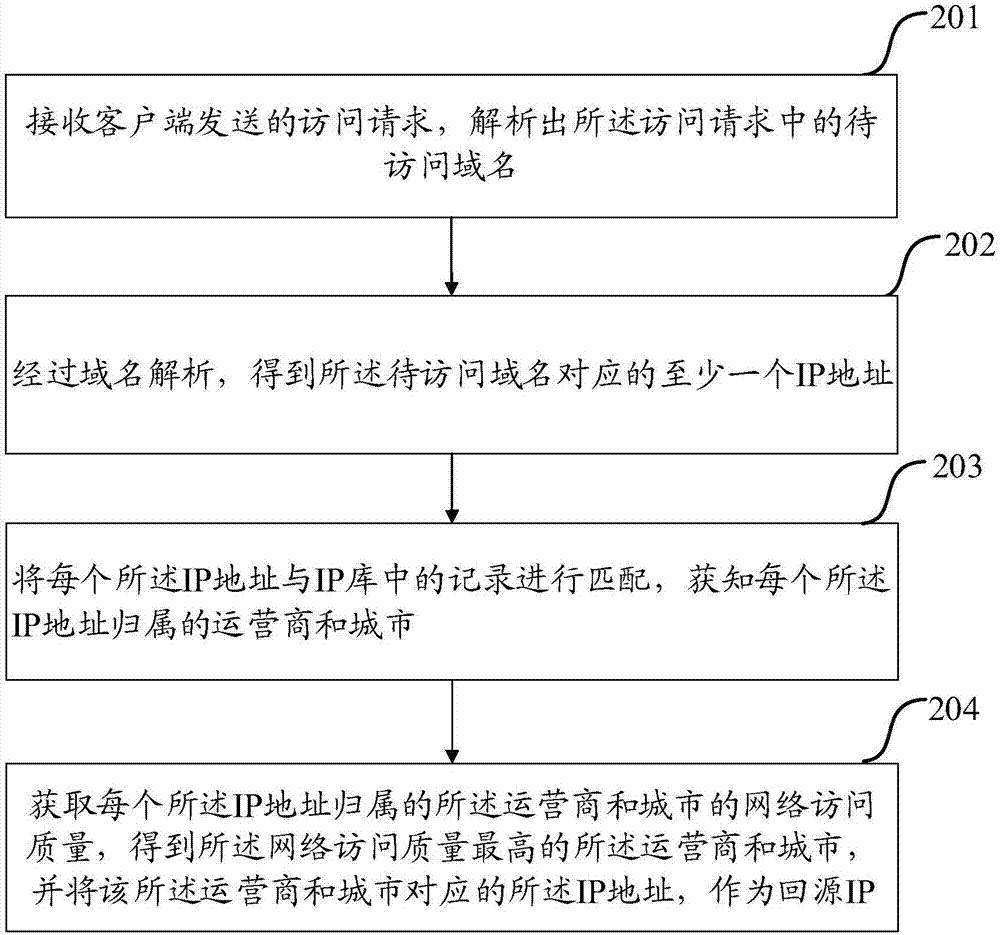
Selection method for source returning path and server
The embodiment of the invention discloses a selection method for a source returning path and a server. The method comprises the steps that after at least one IP address corresponding to a to-be-accessed domain name is determined according to the to-be-accessed domain name, the network access quality of operators and cities to which the IP addresses belong is acquired, and the IP address corresponding to the operator and the city which have the highest network access quality is taken as a source returning IP address. Accordingly, the purpose that when multiple operator lines exist, the source returning IP address is selected according to the network access quality of the operators and the cities without selecting a line simply and randomly, it is guaranteed that a user can access resources at the highest speed, and the access efficiency is effectively improved.
Owner:CHINANETCENT TECH
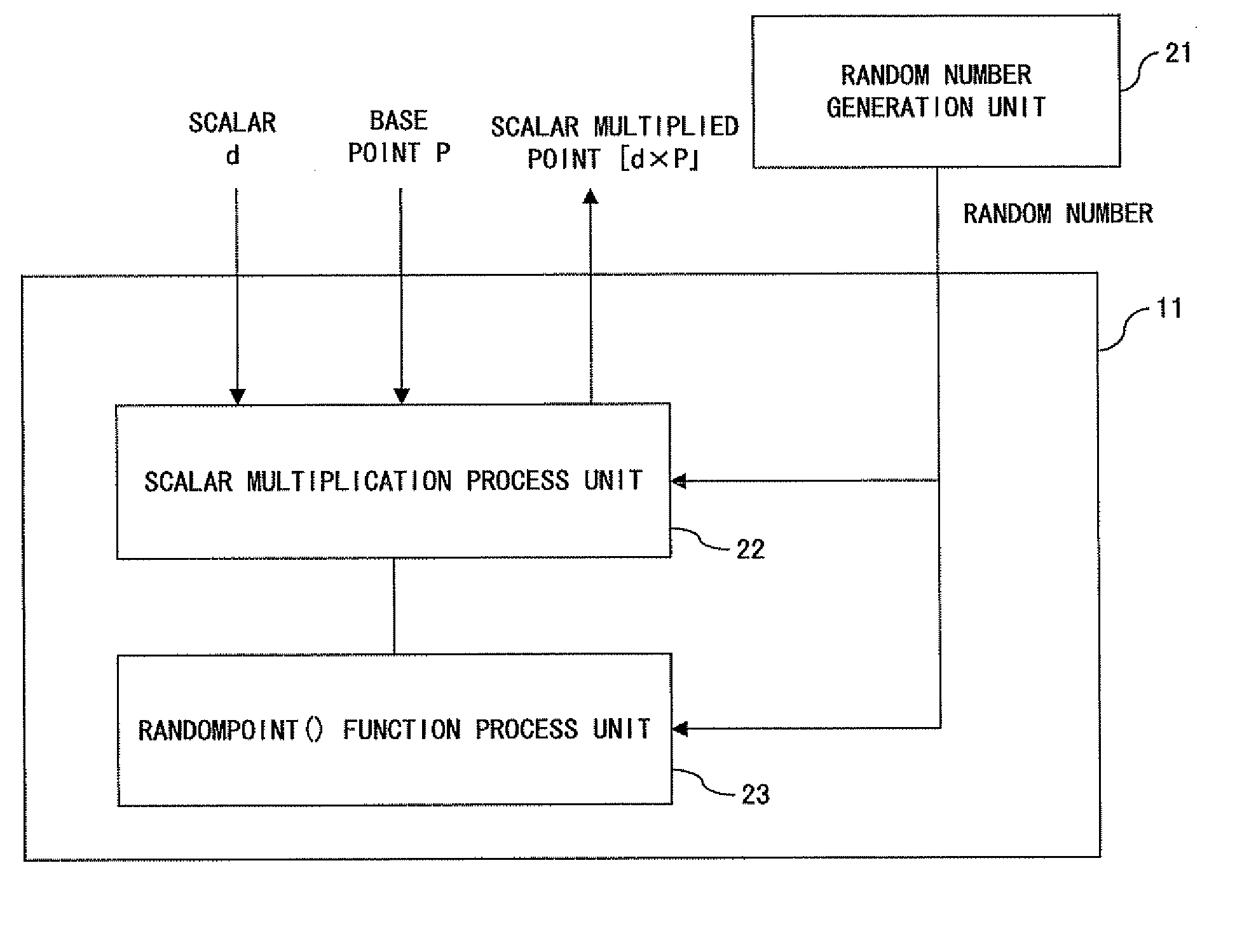
Cryptographic device having tamper resistance to power analysis attack
InactiveUS20080025500A1Improve securityIncrease the difficultyRandom number generatorsPublic key for secure communicationPower analysisTamper resistance
A randomly selected point on an elliptic curve is set as the initial value of a variable and calculation including a random point value is performed in an algorithm for calculating arbitrary scalar multiple operation on an elliptic curve when scalar multiplication and addition on an elliptic curve are defined, then a calculation value obtained as a result of including a random point is subtracted from the calculation result, whereby an intended scalar multiple operation value on an elliptic curve is determined.
Owner:FUJITSU LTD
System for and method of managing access to a system using combinations of user information
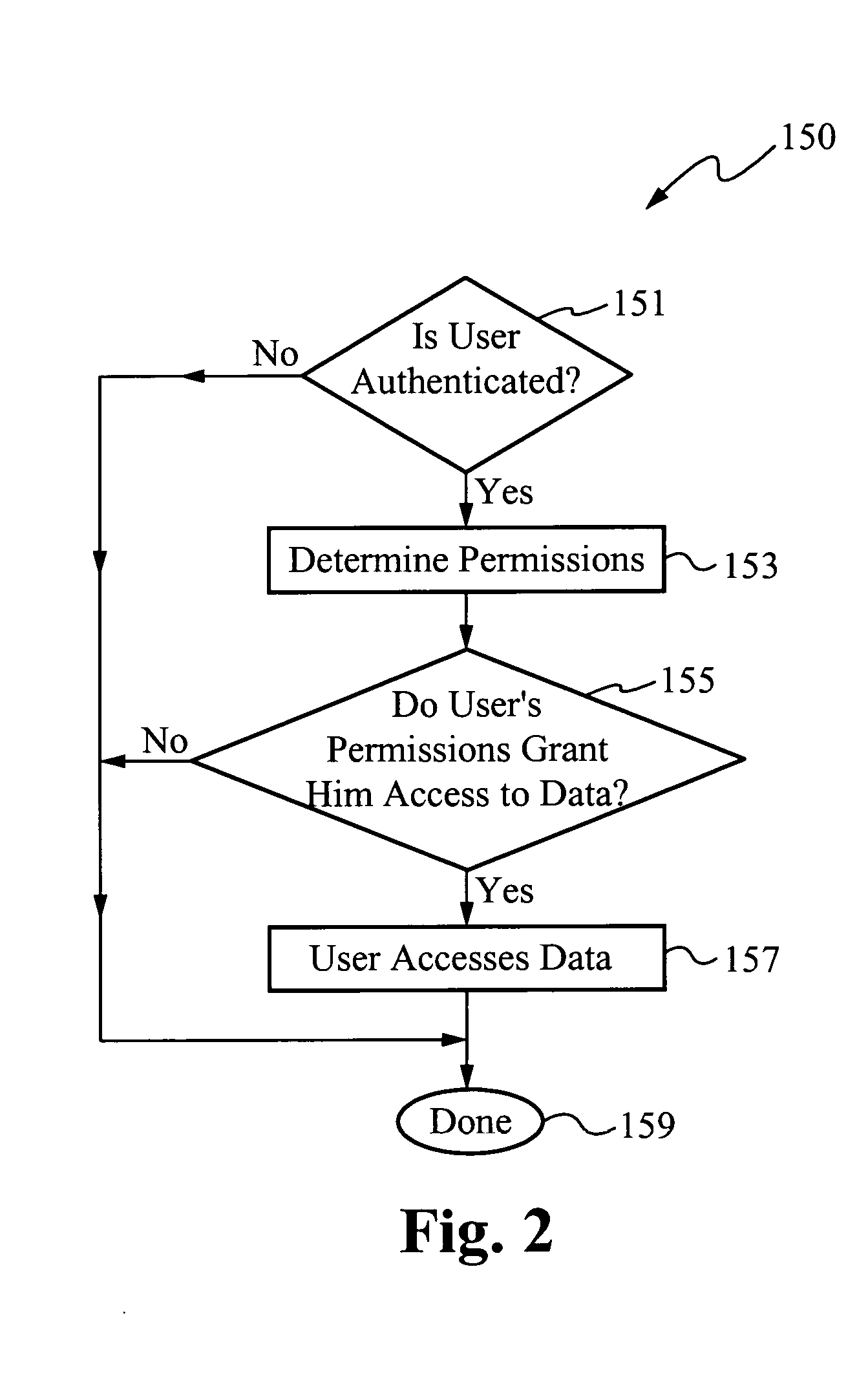
InactiveUS20070107051A1Improve securityDigital data processing detailsUser identity/authority verificationInternet privacyRandom choice
The present invention is directed to systems for and methods of controlling access to computer systems. A method in accordance with the present invention comprises performing a test that includes comparing input responses to randomly selected questions with corresponding pre-determined responses to the questions and granting access to the system in the event the test is passed. A first condition of passing the test is that each input response matches a corresponding pre-determined response. Once passing the test, the user is granted permissions to access data based on his position. For example, a corporate director generally has greater permissions than an engineer. Preferably, the user's permissions determine an encryption key and a decryption key that the user is able to use to access protected data.
Owner:ENCRYPTHENTICA
Scheme for randomized selection of equal cost links during restoration
InactiveUS7391732B1Efficient and economical mannerEfficient and economicalError preventionTransmission systemsCross connectionRandom choice
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
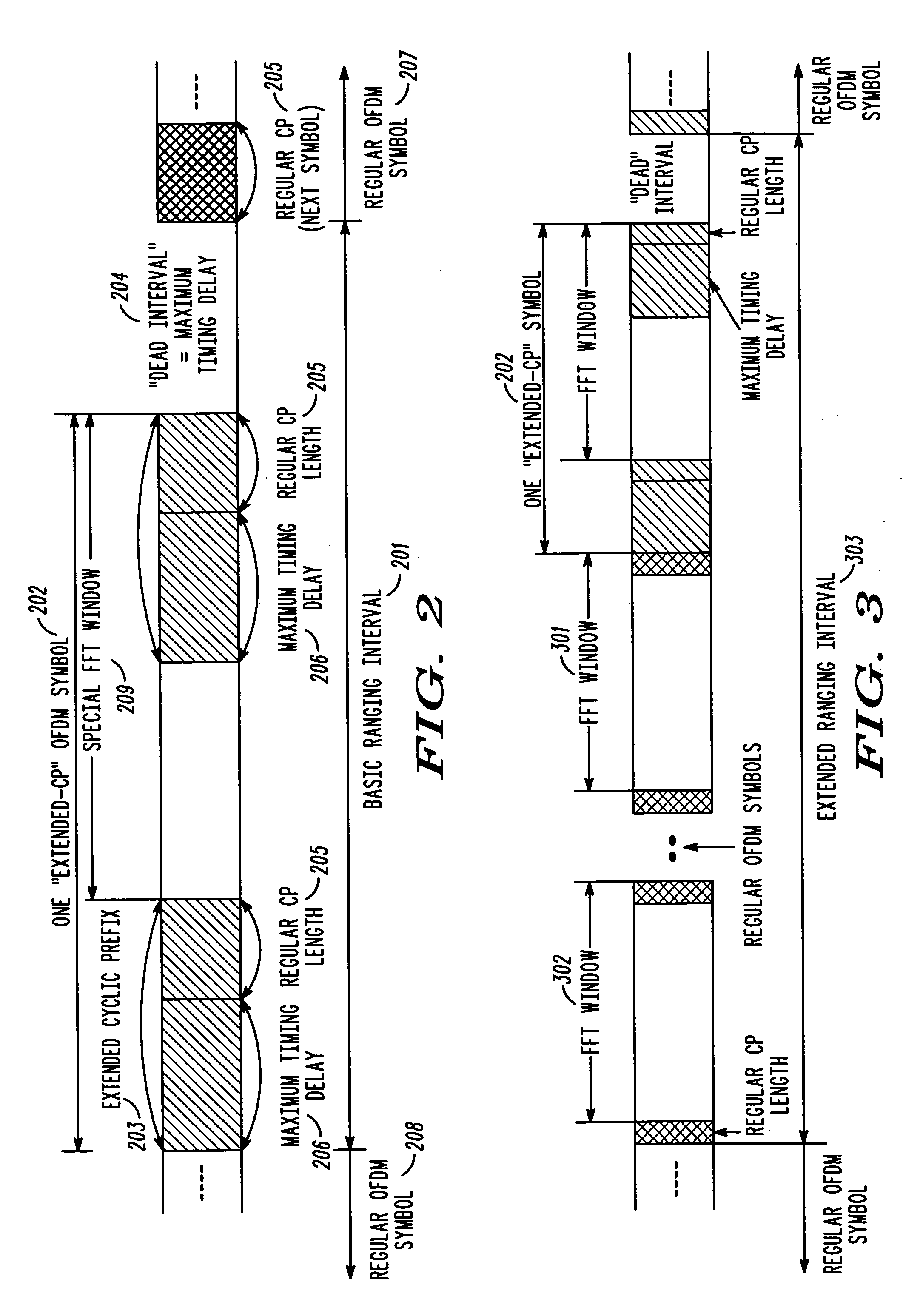
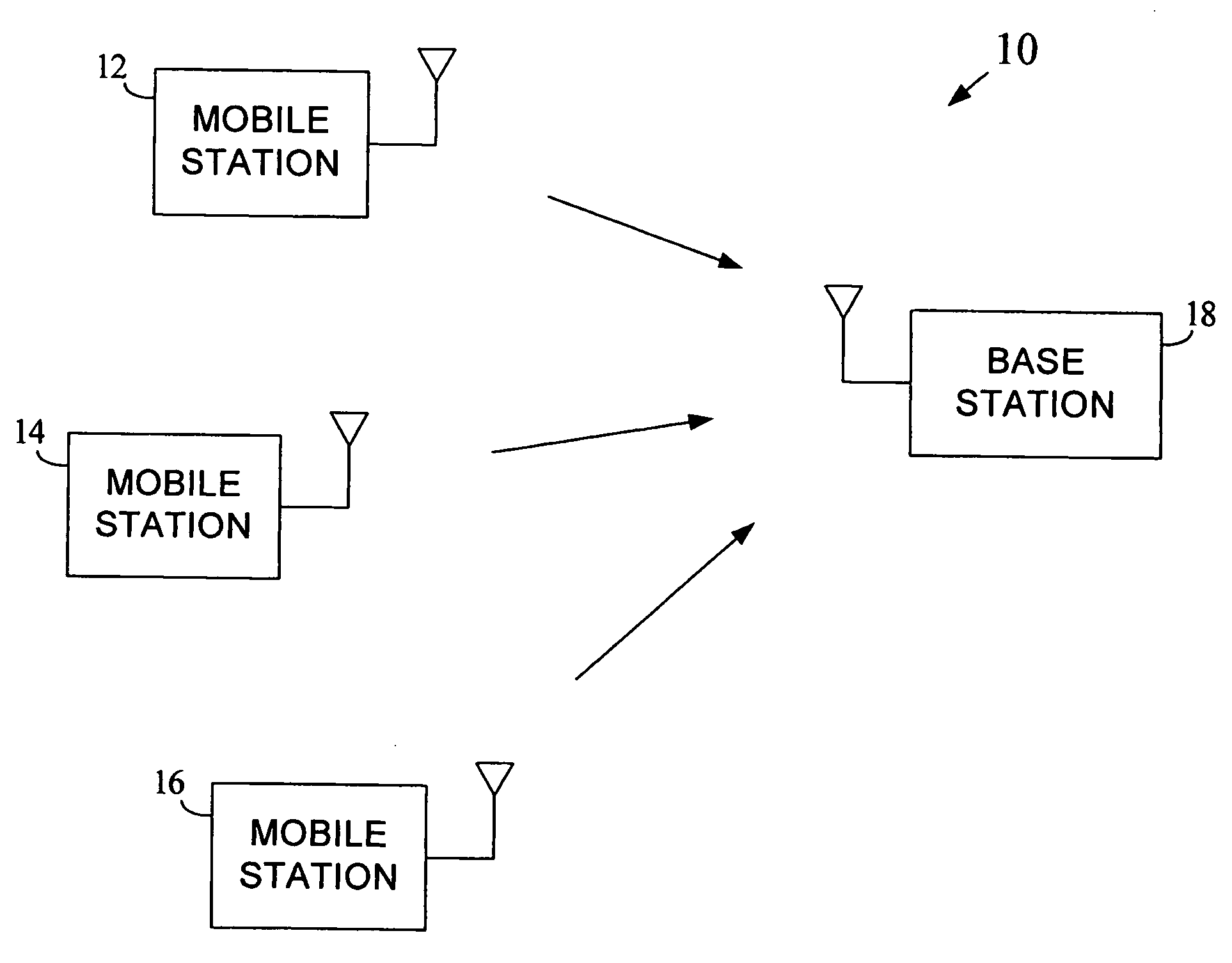
OFDMA contention-based random access channel design for mobile wireless systems
Short spreading is used within a random access channel in an OFDM based network to spread data for transmission through the channel. The resource allocation of the random access channel is divided into a number of resource blocks in frequency, time, or both frequency and time. Each resource block has a dimension that is only a portion of the overall size of the resource allocation. During contention, a randomly selected short spreading code may be used to provide data spreading within a randomly selected resource block.
Owner:INTEL CORP
Detector and method for estimating data probability in a multi-channel receiver
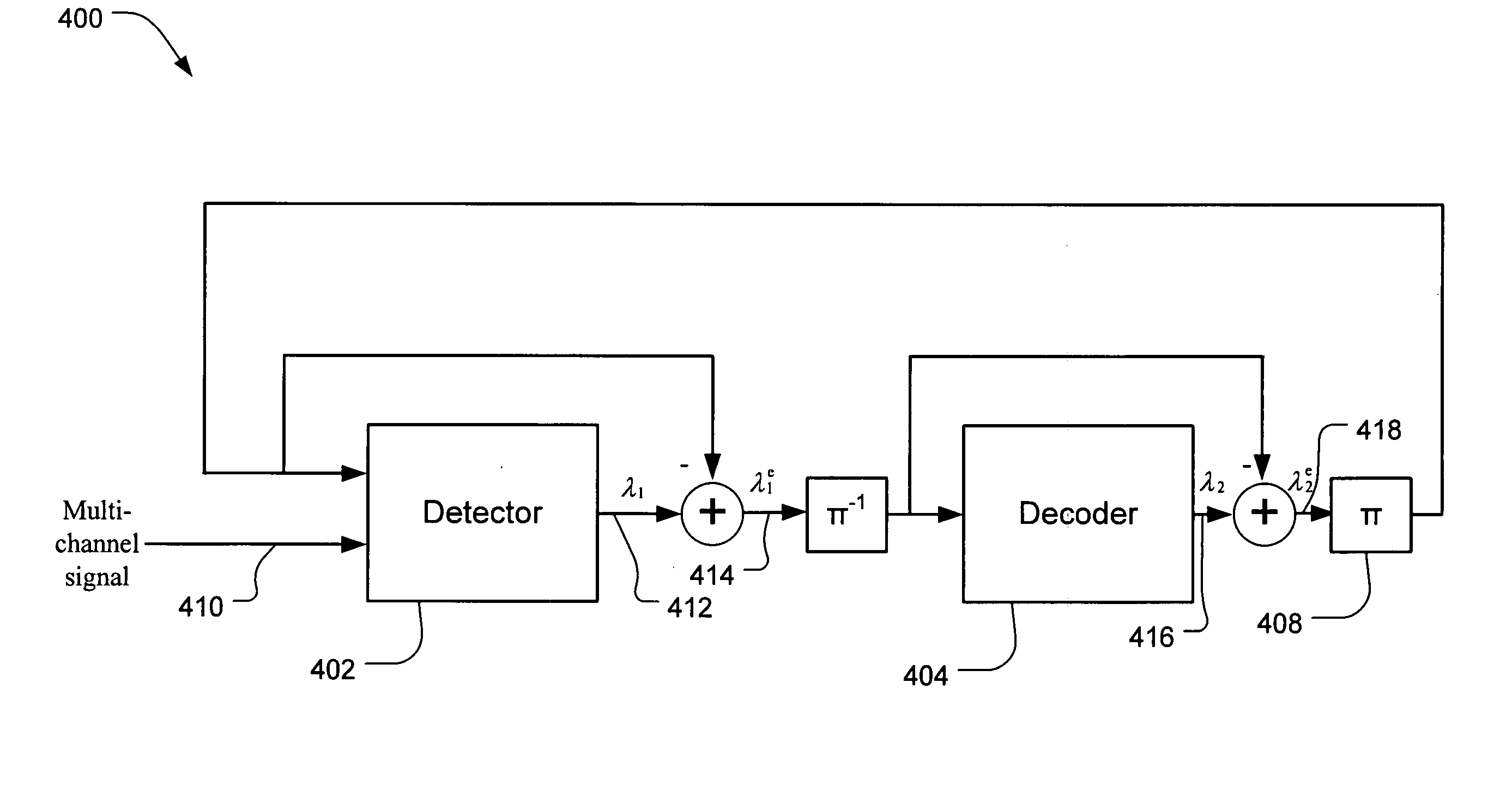
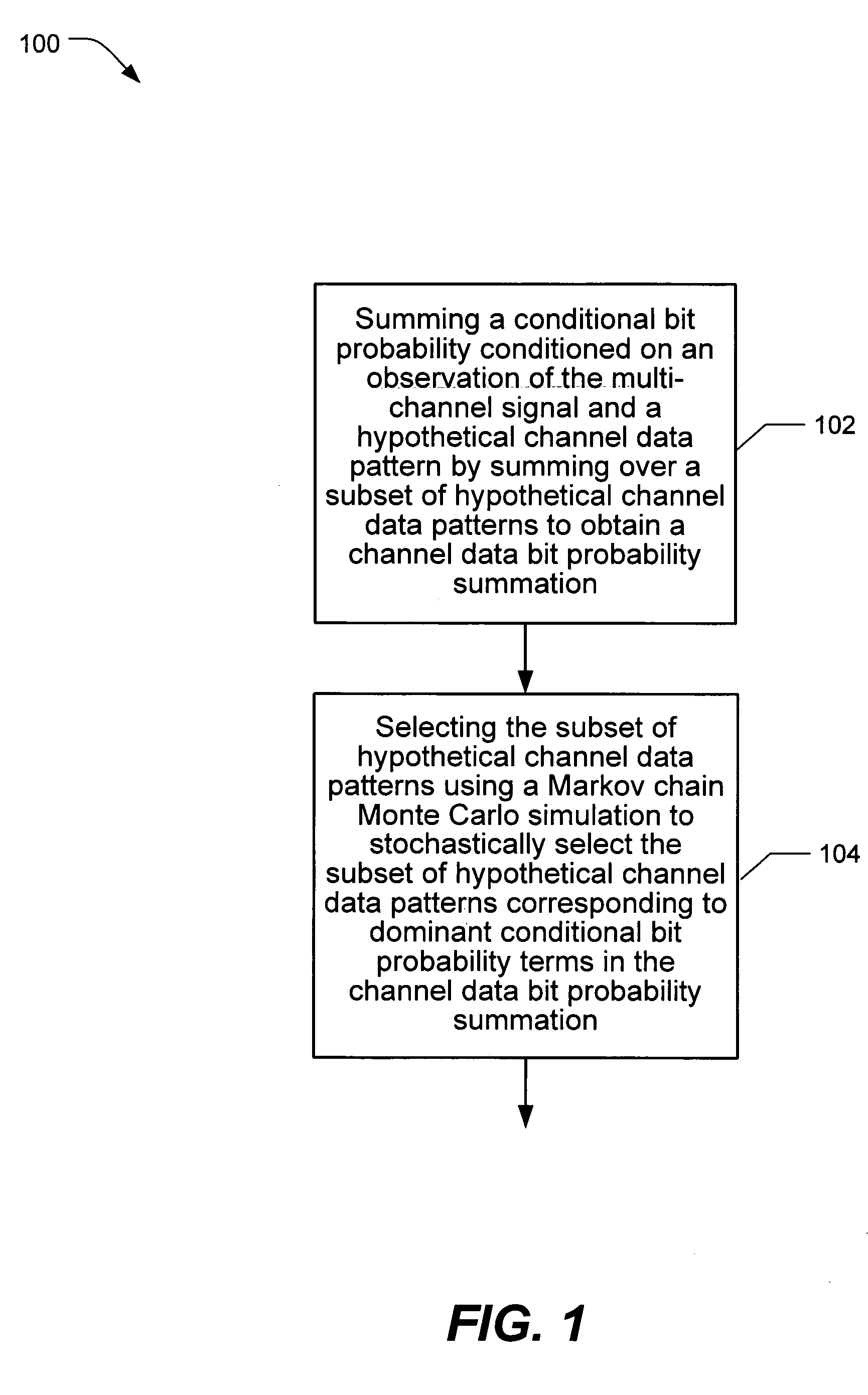
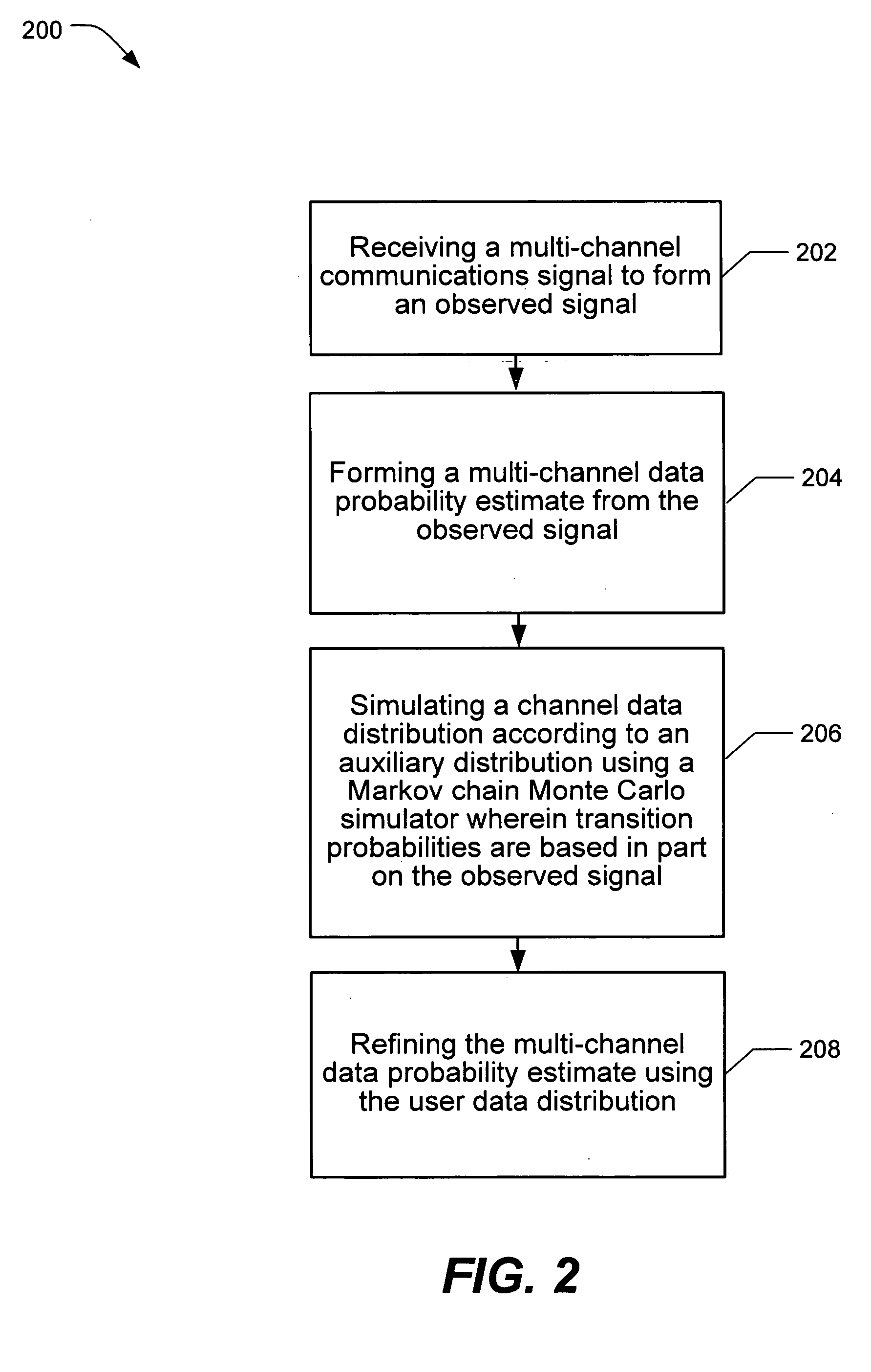
InactiveUS20060023636A1Improve performanceTransmission systemsFrequency-division multiplex detailsPattern recognitionChannel data
A detector and method for estimating channel data probability in a multi-user or multiple-input multiple-output communication system includes summing conditional bit probabilities conditioned on hypothetical channel data patterns over stochastically selected hypothetical channel data patterns. Various detailed hardware structures and circuits are also described.
Owner:THE UNIV OF UTAH +1
Wireless communication system, communication control method and communication node
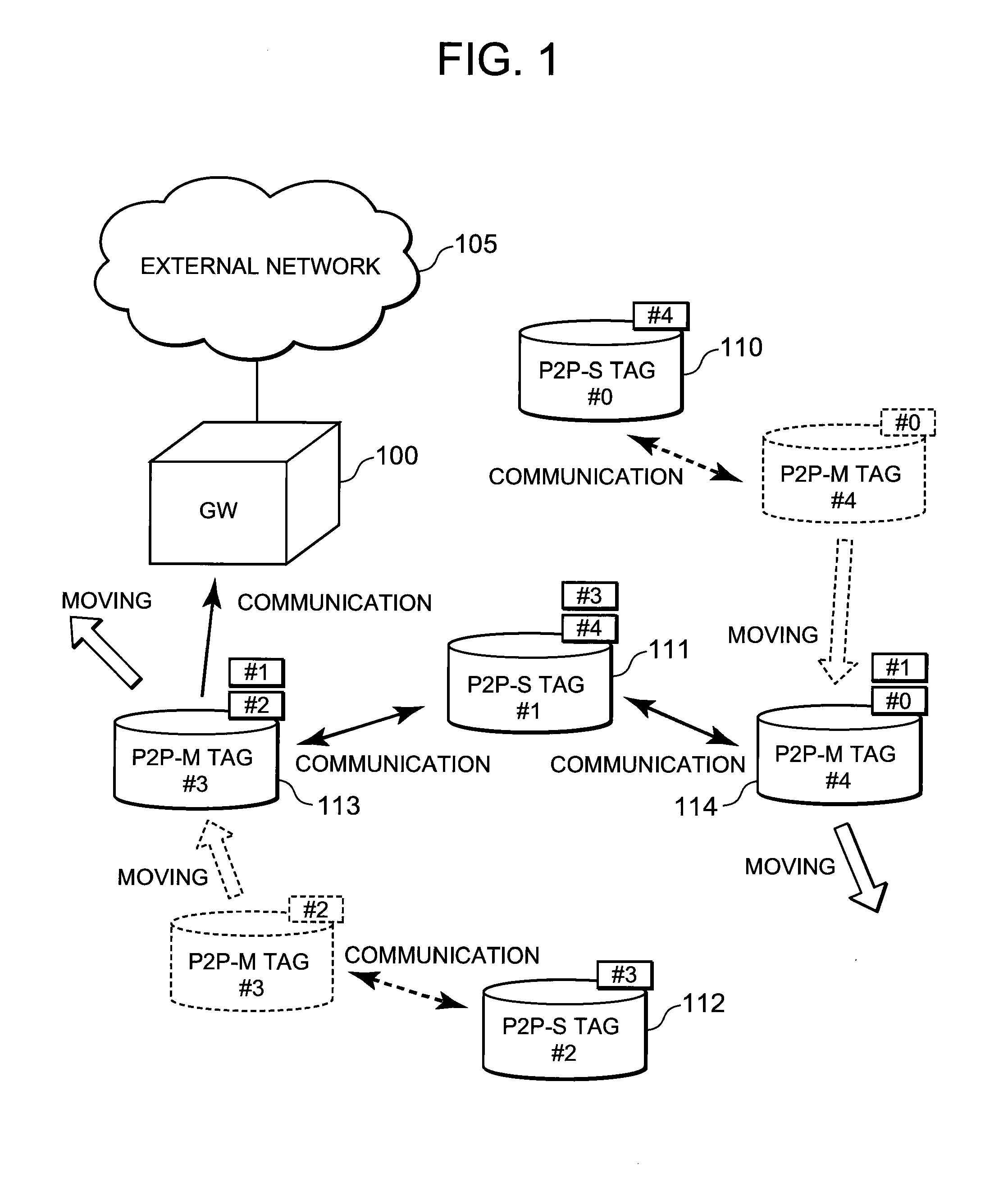
InactiveUS8503343B2Effective controlReduce power consumptionPower managementEnergy efficient ICTCommunications systemRandom choice
A technique is disclosed, by which it is possible to achieve the reduction of power consumption of each wireless node and to perform efficient access control in wireless communication system. According to this technique, a given period with a beacon transmitted from a gateway (GW) 100 at the foremost position is divided to an active period where each wireless node (P2P tag) transmits and receives a frame and a sleep period where transmitting and receiving of the frames are stopped. Further, the active period is divided to a plurality of timeslots each with a fixed length, and the period is partitioned to sub-periods where each type of a GW, a fixed node (P2P-S tag), and a mobile node (P2P-M tag) can transmit frames respectively. Each of the P2P tags selects a timeslot at random from the period for each type, and after waiting for a waiting period at random at the selected timeslot, it transmits a frame including information to identify the selected timeslot or the waiting period in addition to its own ID.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com