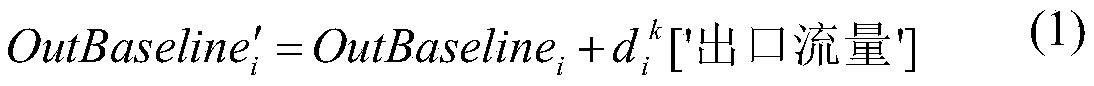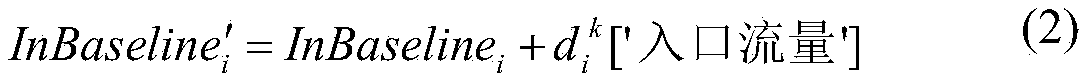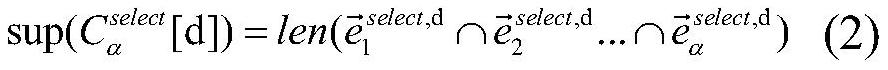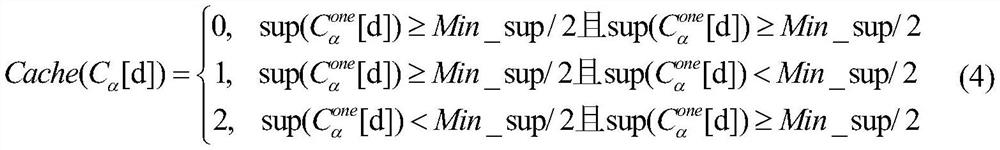Patents
Literature
31results about How to "Protect Sensitive Information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
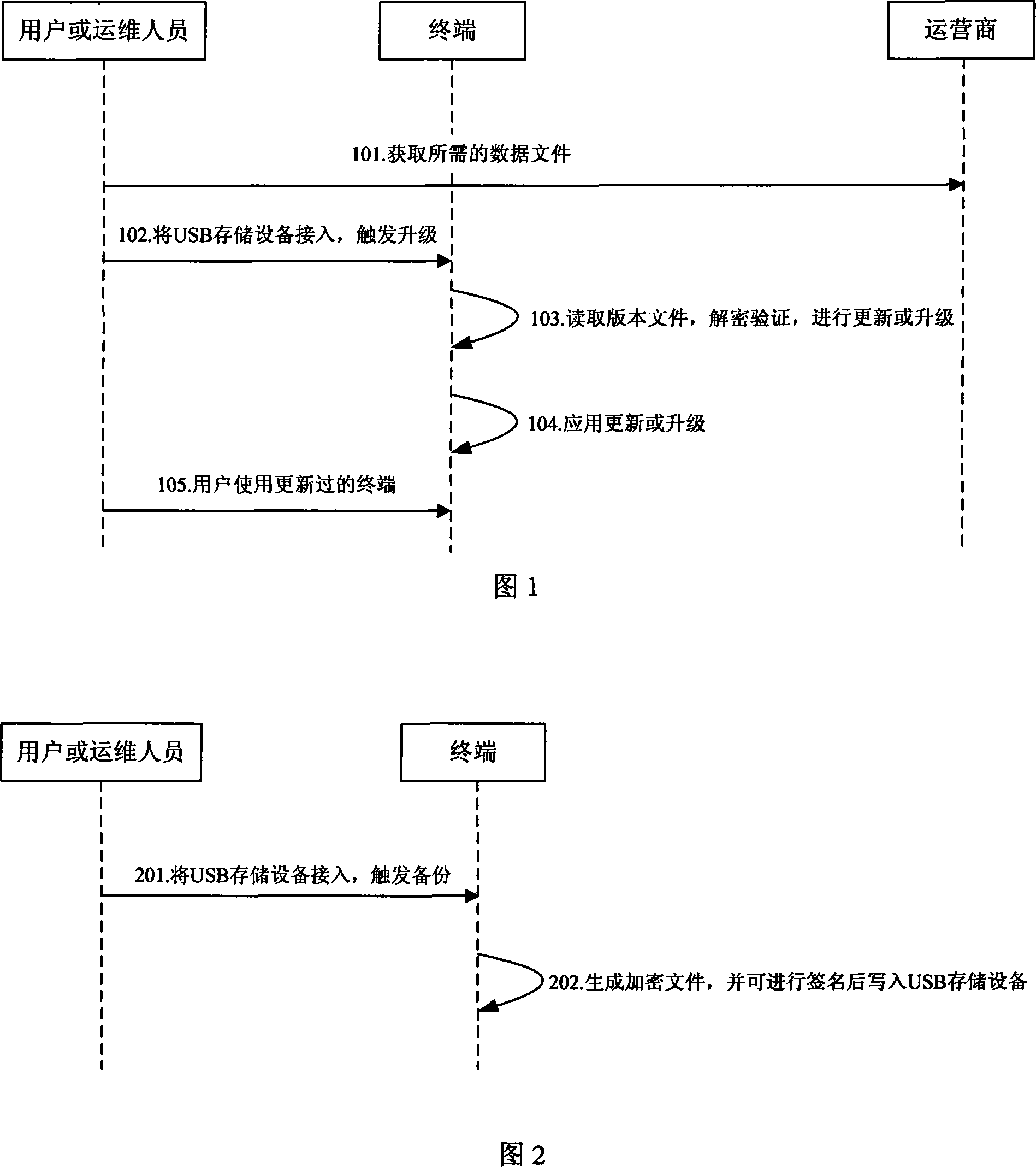
Method for realizing version upgrade and backup of terminal by switch-in USB memory apparatus
InactiveCN101183312AReduce workloadLow professional knowledge requirementProgram loading/initiatingData switching networksData fileComputer terminal
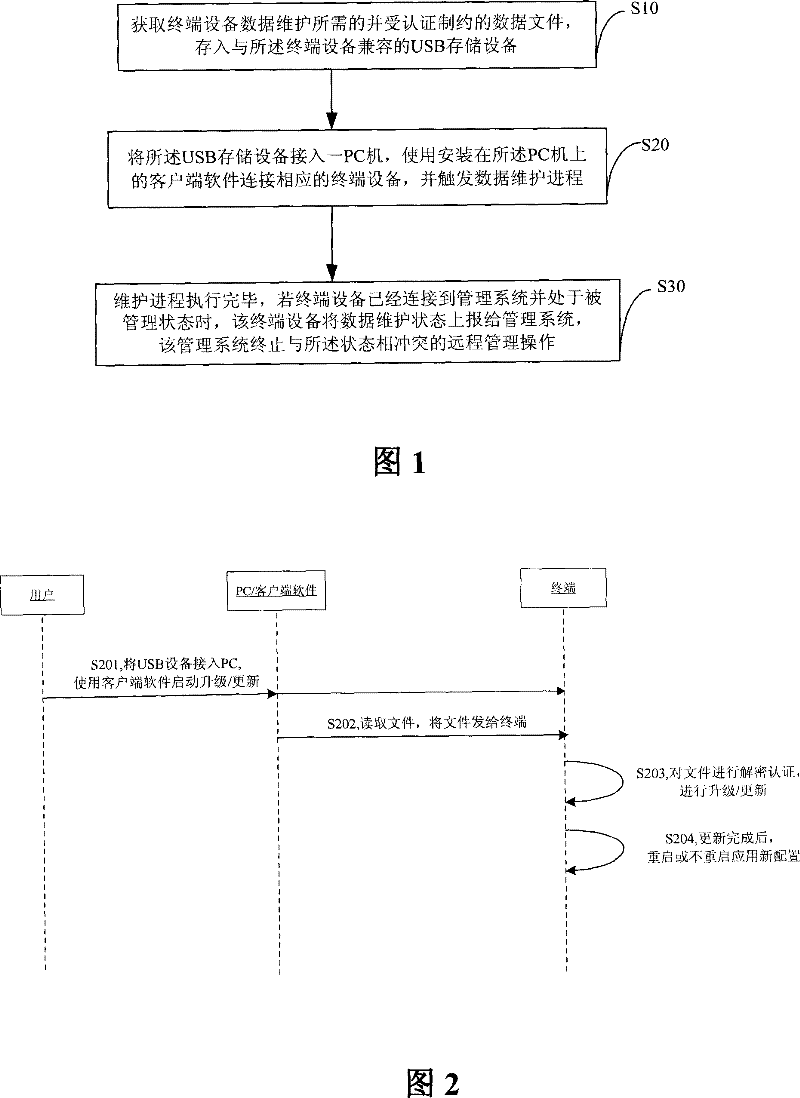
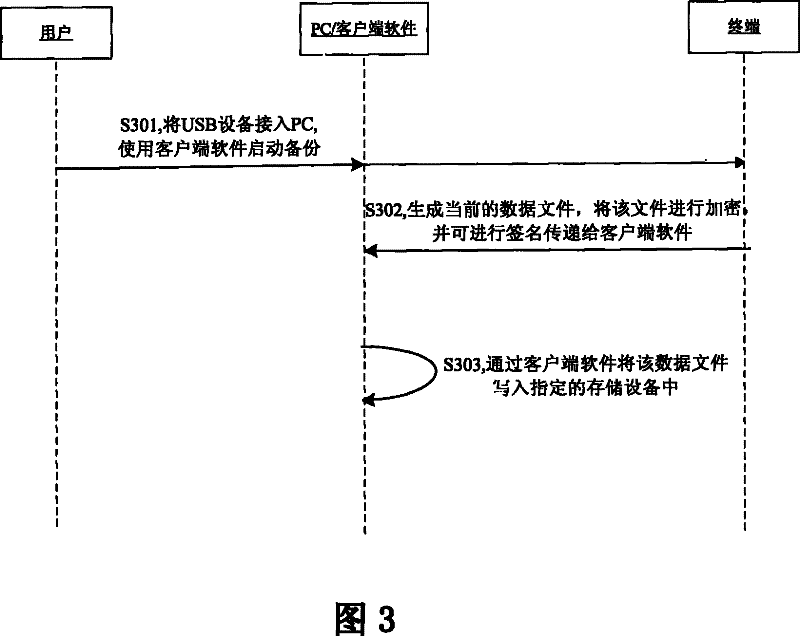
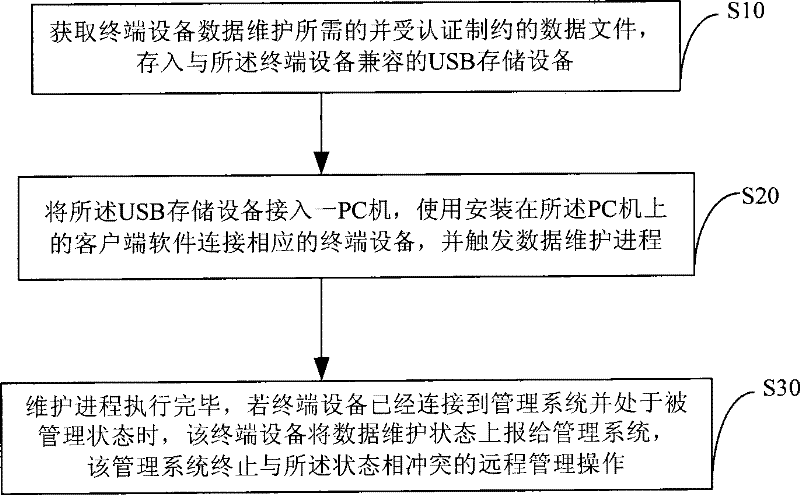
The invention discloses a version upgrade and backup method for terminal through accessing an USB memory equipment. The upgrade method comprises following procedures: reading data file through accessing the USB memory equipment with data file to trigger the terminal; updating or upgrading through decryption identification before updated or upgraded version is applied. The backup method comprises procedures as follows: accessing the USB memory equipment to the terminal triggered before current data file is generated for the terminal and encrypted. The invention has the advantages of enabling local business configuration management and version management through accessing the USB storage equipment to the USB interface of the terminal when the operator cannot perform remote management for the terminal through other management mode; when the terminal is connected with the remote management system of the operator and is under management status, the terminal can report the status such as report reading, updating, applying and backing up of corresponding file on the USB storage equipment under the mode to the management system for statistics and failure diagnosis in the future.
Owner:ZTE CORP
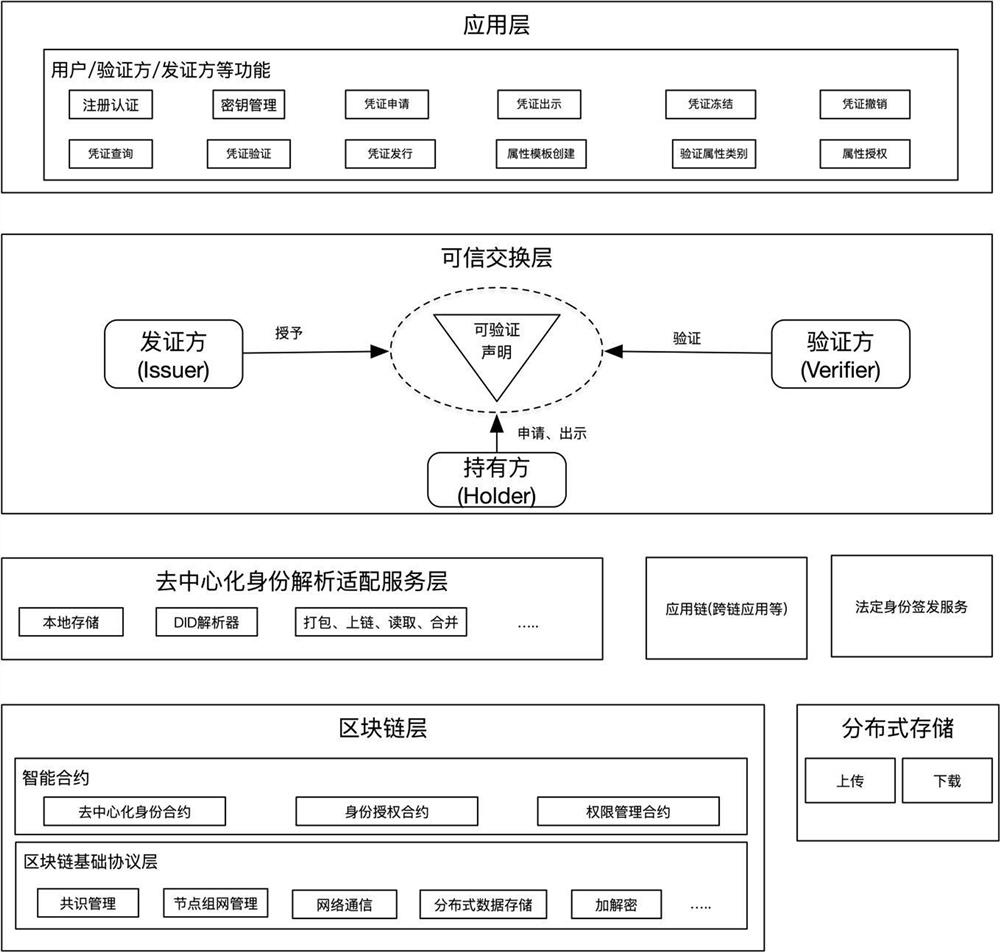
Multi-dimensional digital identity authentication system based on block chain
InactiveCN112580102ASupport large-scale accessSupport for customizable identity certificatesDigital data protectionDigital data authenticationEngineeringData store
The invention discloses a multi-dimensional digital identity authentication system based on a block chain, and relates to the technical field of block chains. The system comprises: a block chain layerused for storing and anchoring a DID document and other data needing distributed storage content; a decentralized identity analysis adaptation service layer which is used for providing a unified DIDdocument analysis service for the block chain layer, and the service can be connected with other application chains at the same time to carry out cross-chain application; a trusted exchange layer which is used for obtaining a DID document through an identity on a user agent registration chain, applying for various verifiable certificates to a certificate issuer by depending on the DID document, and finally providing the DID and the verifiable certificates to a verifier to complete a verification process; and an application layer which is used for constructing a web, wherein an application of the mobile client is provided for a terminal user to use. The system supports cross-chain and cross-platform interoperation, and can be expanded in various different modes.
Owner:ZHENGZHOU UNIV
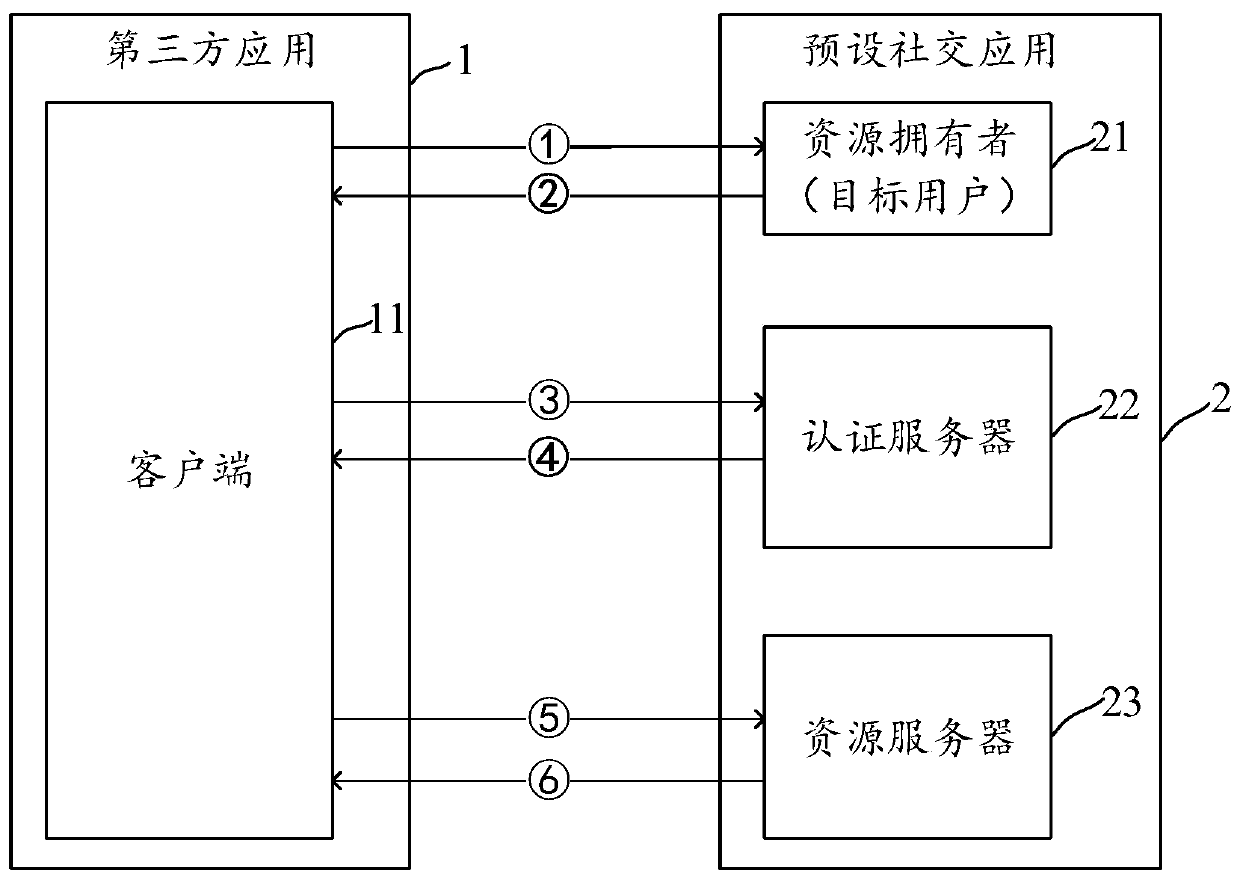
Method, apparatus and electronic device for acquiring and feeding back user resources
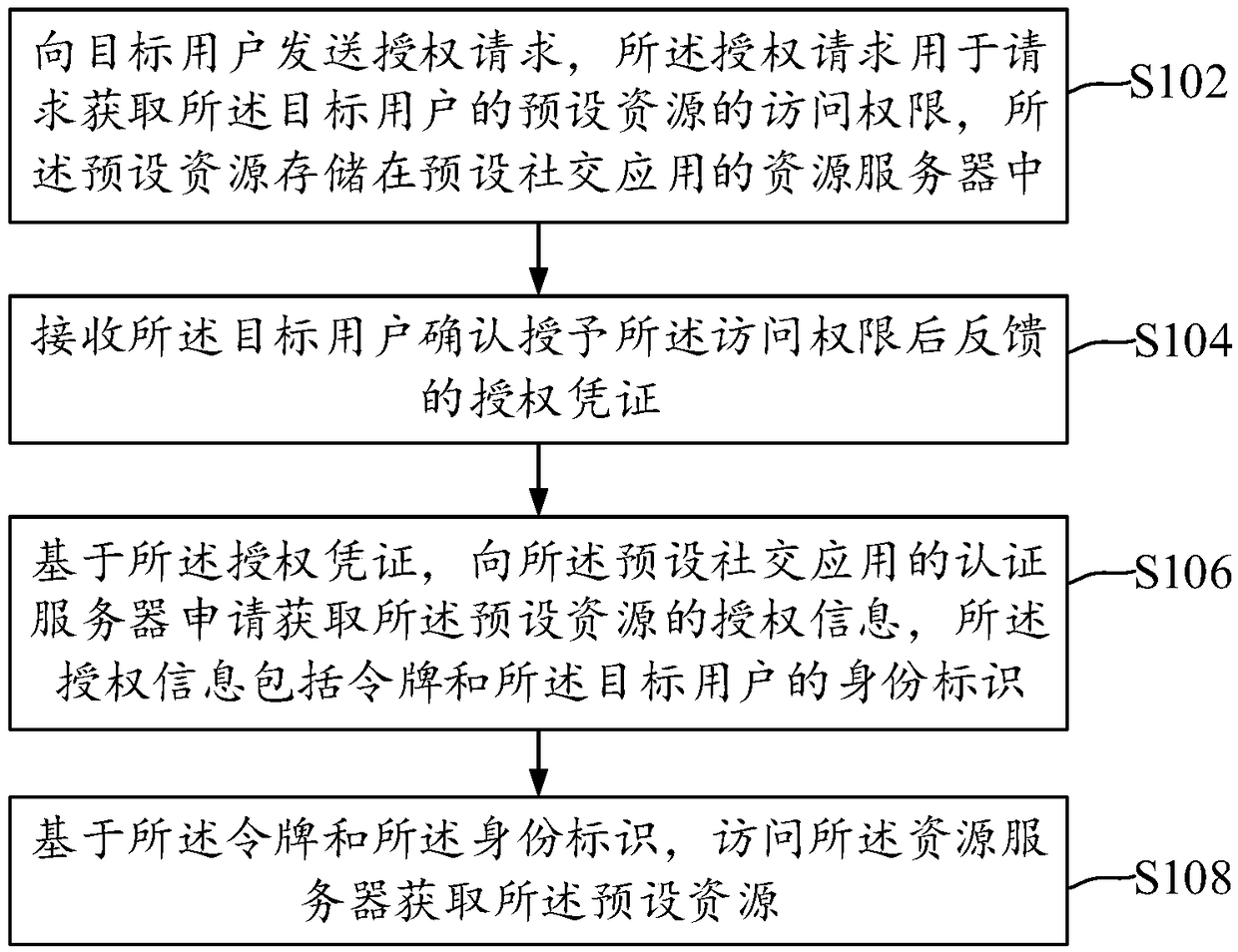
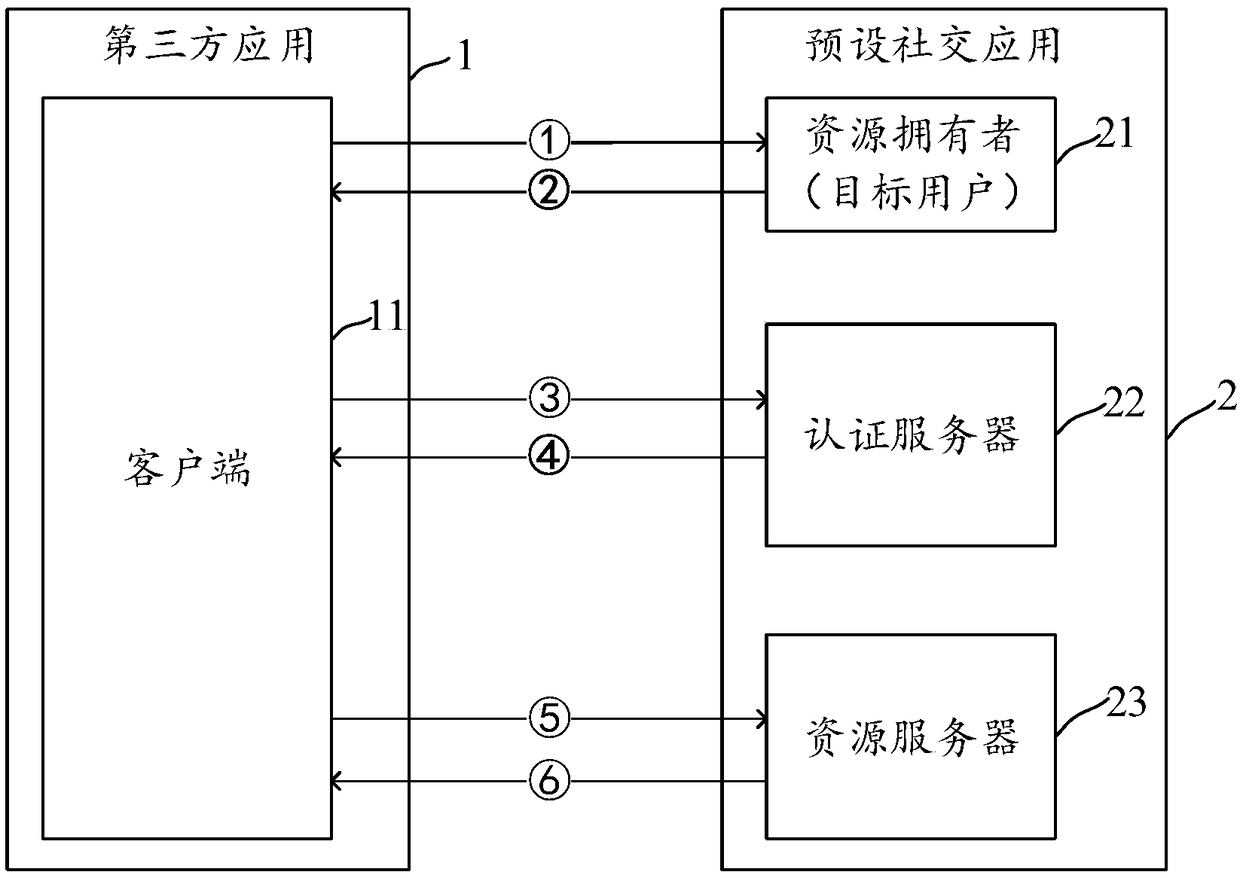
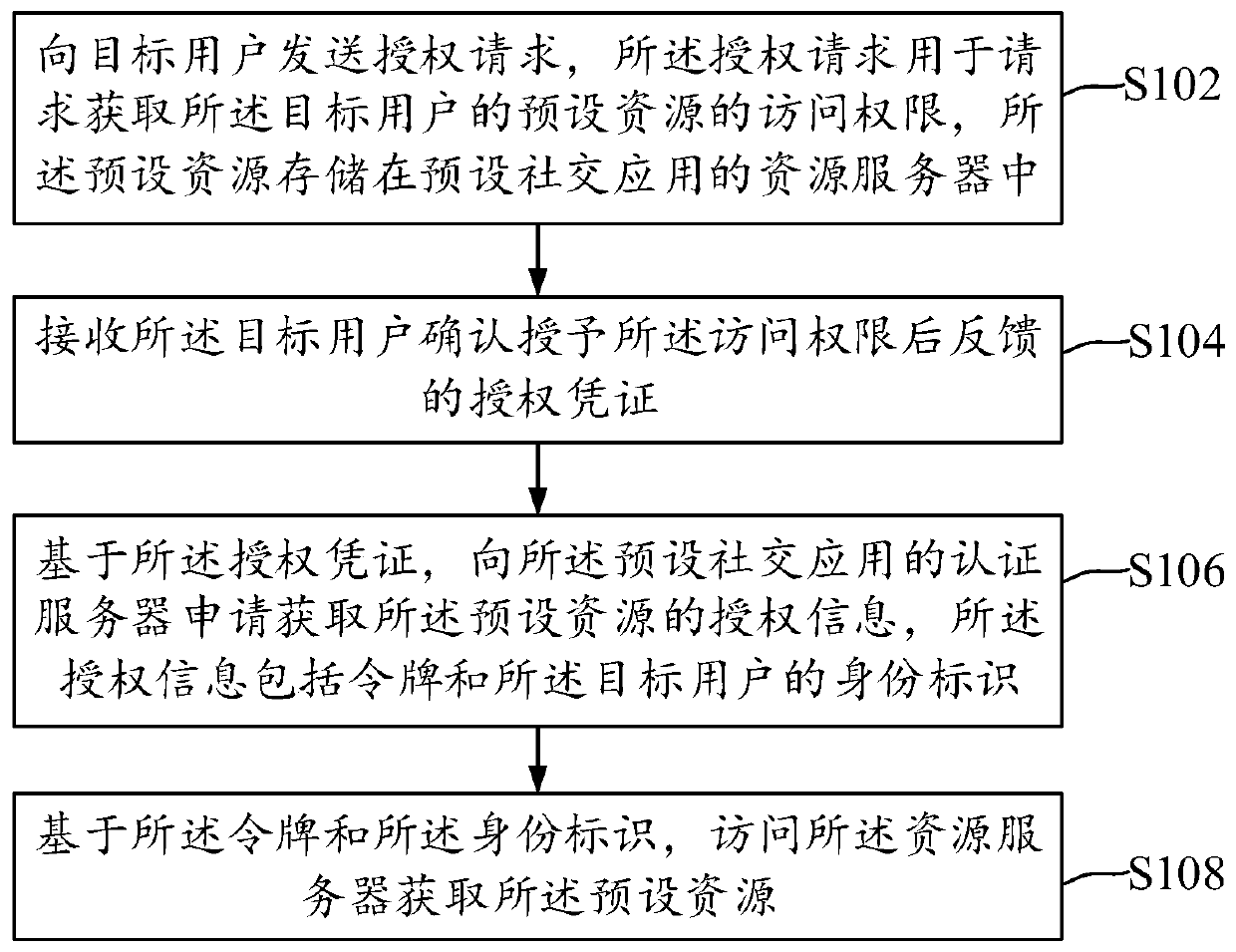
ActiveCN109033774AAvoid passing situationsProtect personal privacyDigital data authenticationAuthorization certificateResource based
The invention discloses a method, a device and an electronic device for obtaining and feeding back user resources. The method for obtaining user resources can send an authorization request for obtaining access rights of preset resources of the target user to a target user. The preset resources are stored in a resource server of a preset social application. Authorization credentials fed back by thetarget user are received after confirming the granting of the access right; it is applied for obtaining authorization information of the preset resources from an authentication server of the preset social application based on the authorization certificate, the authorization information comprises a token and an identity of the target user; the resource server is accessed to obtain the preset resource based on the token and the identity.
Owner:ADVANCED NEW TECH CO LTD
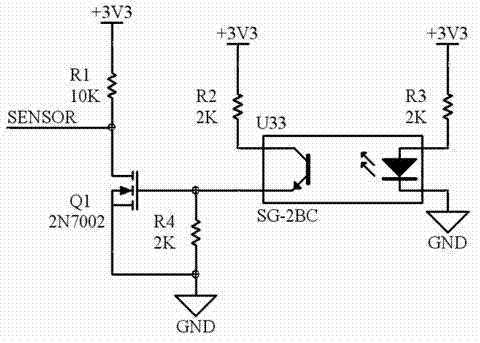
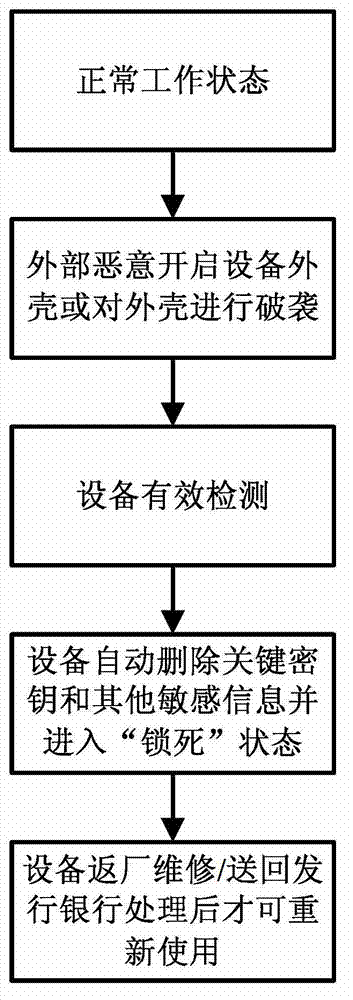
Uncovered data self-destruction device for safety payment terminal and method
InactiveCN102968854AEffective preventionProtect Sensitive InformationCoded identity card or credit card actuationComputer terminalEngineering
The invention discloses an uncovered data self-destruction device for a safety payment terminal and a method. The uncovered data self-destruction device for the safety payment terminal comprises a microprocessor, a memorizer, at least two contact points and at least one photosensitive tube detection circuit, wherein parts, corresponding to the contact points, of a front housing and a back housing of the safety payment terminal, are coated with conducting resin. The uncovered data self-destruction device for the safety payment terminal and the method are easy to implement, high in safety and low in cost.
Owner:GREATWALL INFORMATION IND +1
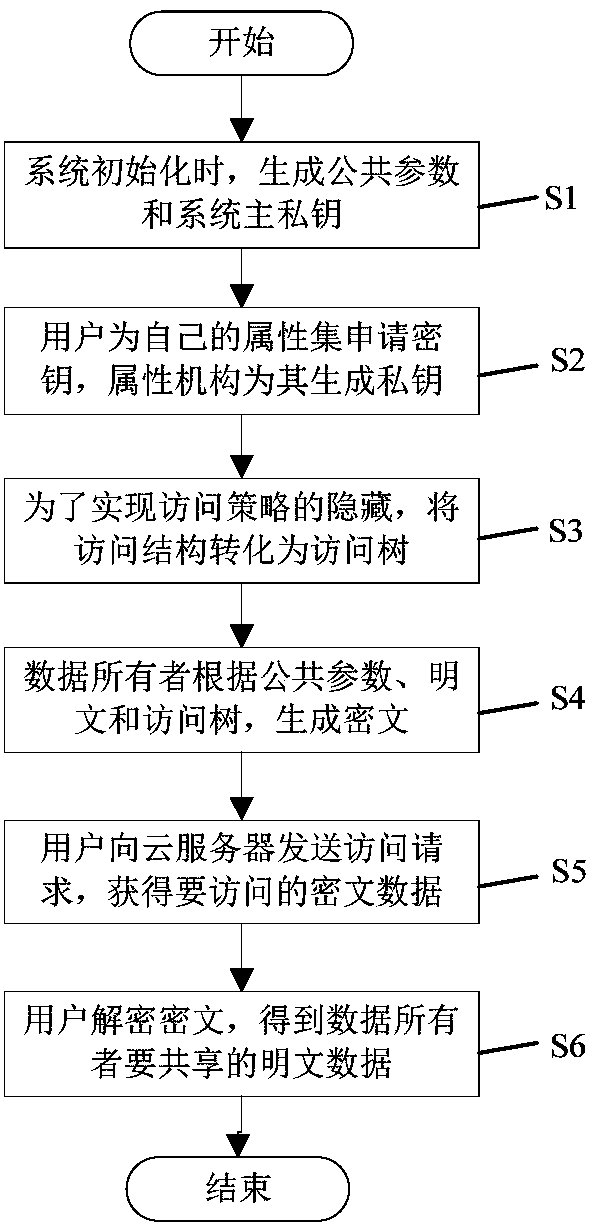
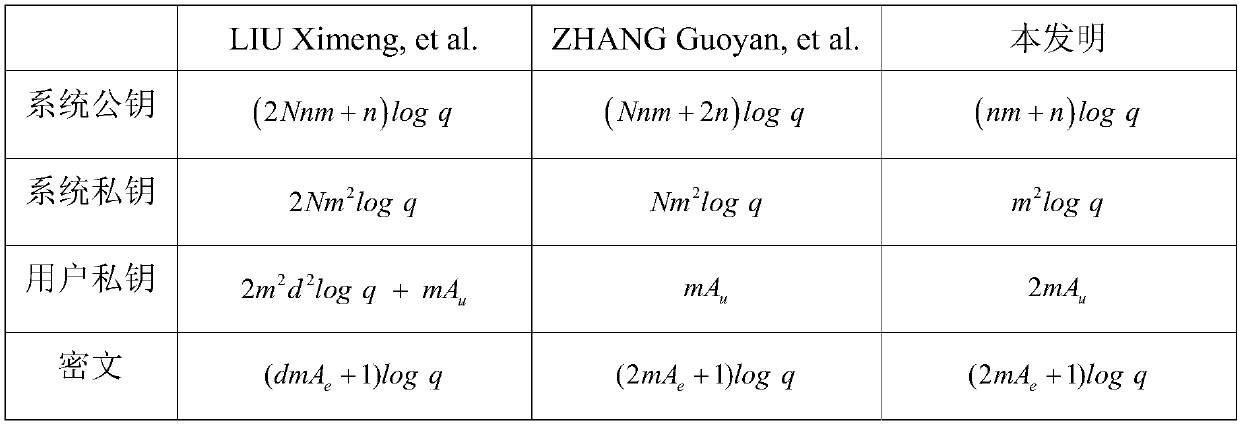
Multi-mechanism encryption method used in lattices for supporting strategy hiding
InactiveCN108512662AImprove efficiencyResistant to Quantum AttacksKey distribution for secure communicationPlaintextAccess structure
The invention discloses a multi-mechanism encryption method used in lattices for supporting strategy hiding. The multi-mechanism encryption method comprises steps that S1, during system initialization, a public parameter and a system main private key are generated; S2, a user applies for a cipher key for own attribute, and an attribute mechanism is used to generate a private key according to the public parameter, the system main private key, and the attribute set of the user; S3, an access structure is converted into a corresponding access tree to realize complete hiding of an access strategy;S4, a data owner is used to generate the ciphertext data according to the public parameter, a plain text, and the converted access tree, and the ciphertext data is uploaded to a cloud server for storage; S5, the user transmits an access request to the cloud server to acquire the ciphertext data stored in the cloud server; S6, the user uses the private key acquired from the attribute mechanism todecrypt the ciphertext data acquired from the cloud server, and the plaintext of the data owner is acquired, and related subsequent operations are carried out. The multi-mechanism encryption method isadvantageous in that the efficiency of the system is improved, and quantum attacks are prevented, and user privacy is effectively improved.
Owner:SHANGHAI MARITIME UNIVERSITY
Method for protecting SUPI through utilization of 5G-AKA
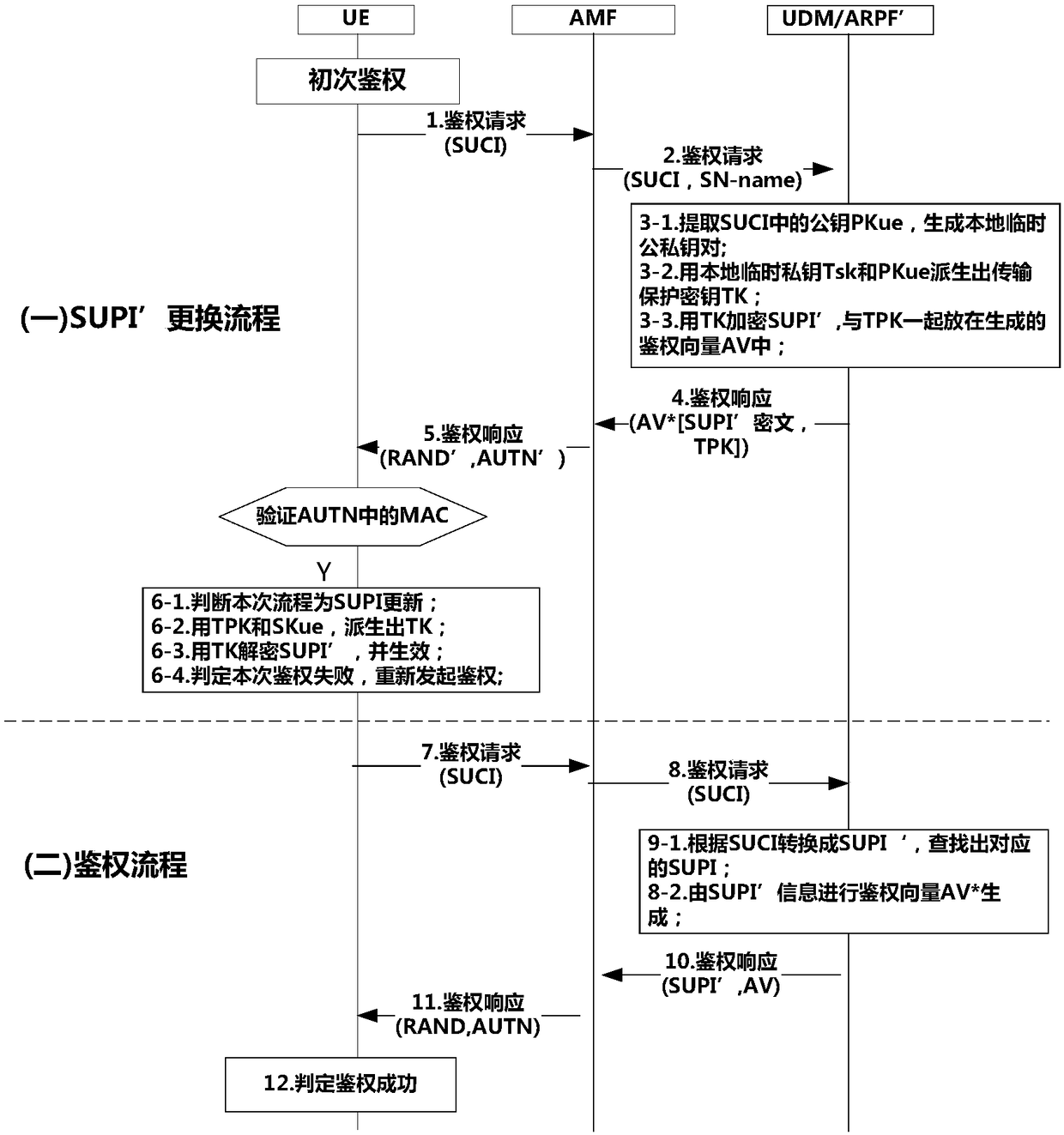
ActiveCN108848502AImprove completenessProtect Sensitive InformationSecurity arrangementNetwork data managementComputer terminalMobile communication network
The invention relates to a method for protecting a subscription permanent identifier (SUPI) through utilization of 5G-AKA and belongs to the technical field of 5G communication. The method solves theproblem that in the prior art, various important sensitive information such as an identity, a location and business of a subscriber cannot be concealed well. The method comprises the following steps:a terminal initiates an authentication request, and a core network judges whether to replace identity information or not through a level and sensitive degree of the terminal; selecting an SUPI' as a new in-use identity of the terminal when it is determined that the identity information needs to be replaced; the encrypted SUPI' is sent to the terminal; and the terminal verifies authentication response, after the in-use identity of the terminal is replaced, the terminal initiates a secondary authentication request, and the authentication is carried out through utilization of the new in-use identity. According to the method, the network modification cost is low; the subscriber is not affected; the efficiency is high; the original network authentication security is maintained; and on the premise that a current core network protocol system is not changed, the subscriber sensitive information is protected through utilization of an authentication channel from the terminal subscriber to a mobile communication network.
Owner:XINGTANG TELECOMM TECH CO LTD +1
Group chat communication system and method thereof
InactiveCN104639556AProtection of personal informationProtect sensitive informationSpecial service provision for substationInformation transmissionCommunications system
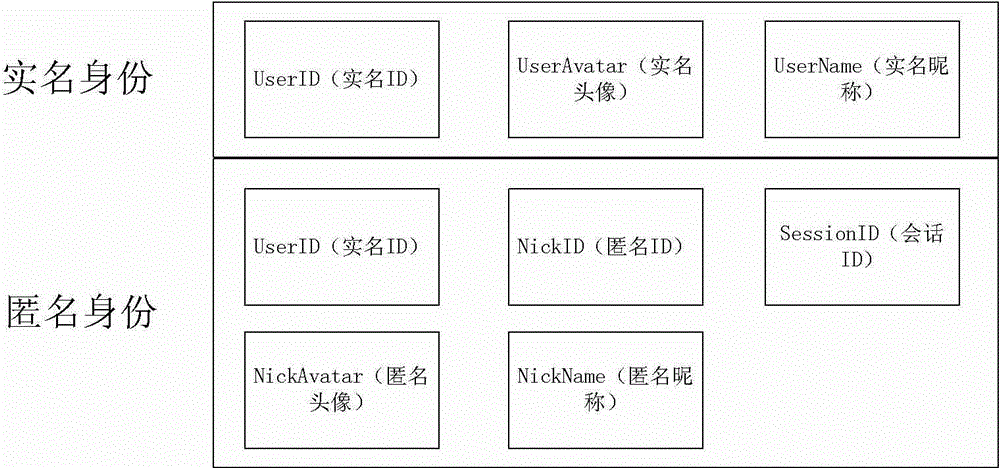
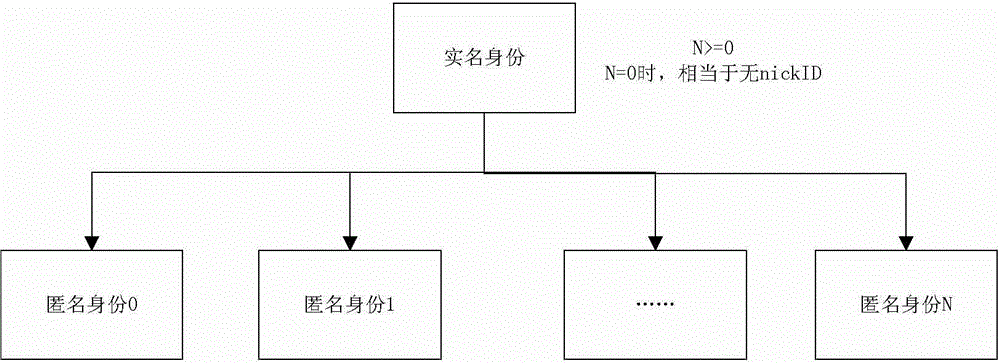
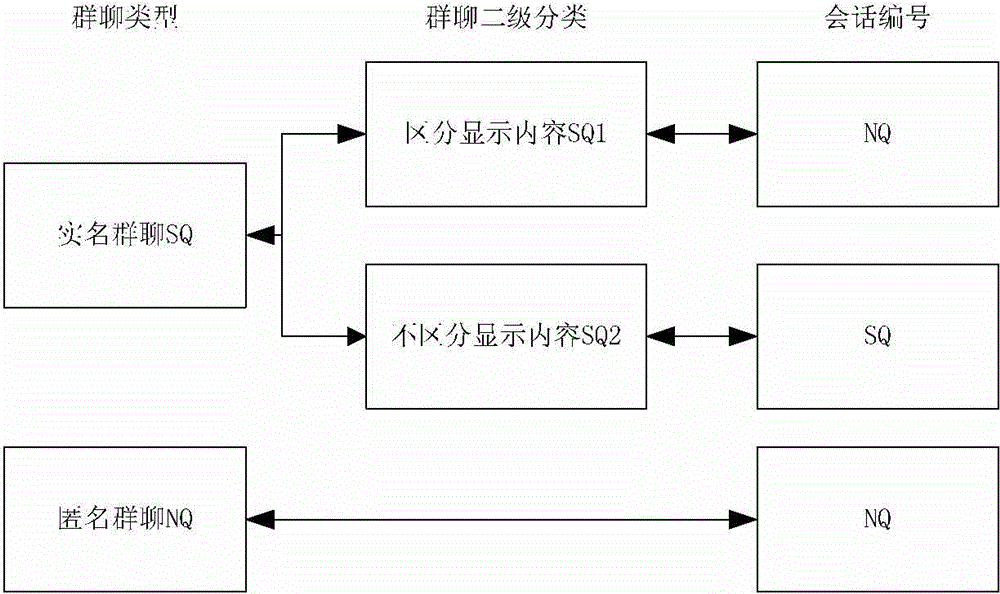
The invention discloses a group chat communication system and a method thereof. The system comprises a first user module, a user name / nick name identity switch processing module, a nick name identity distribution module and second user modules, wherein the first user module is used for managing information on users, including group managers and other group members, who have been participated in a group chat through a client; the user name / nick name identity switch processing module is used for responding to a user name / nick name switching request initiated through the client and re-calculating identities of the users, participating in current group chat communication, by a preset algorithm in a server; the nick name identity distribution module is used for distributing identity information, which is calculated by using the user name / nick name identity switch processing module, to corresponding users existing in a current group chat session, so as to enable each user to correspondingly obtain a relatively unique identity, namely a nick name ID (Identity), in the current group chat; the second user modules are used for supporting the other group members to be in group chat communication with the first user module through the server. By adopting the system and the method, the users can protect personal information on the group members during the group chat and information generated during the group chat, and the security during information transmission is ensured.
Owner:BEIJING JINGYUE INTERACTIVE TECH
System-log classification method
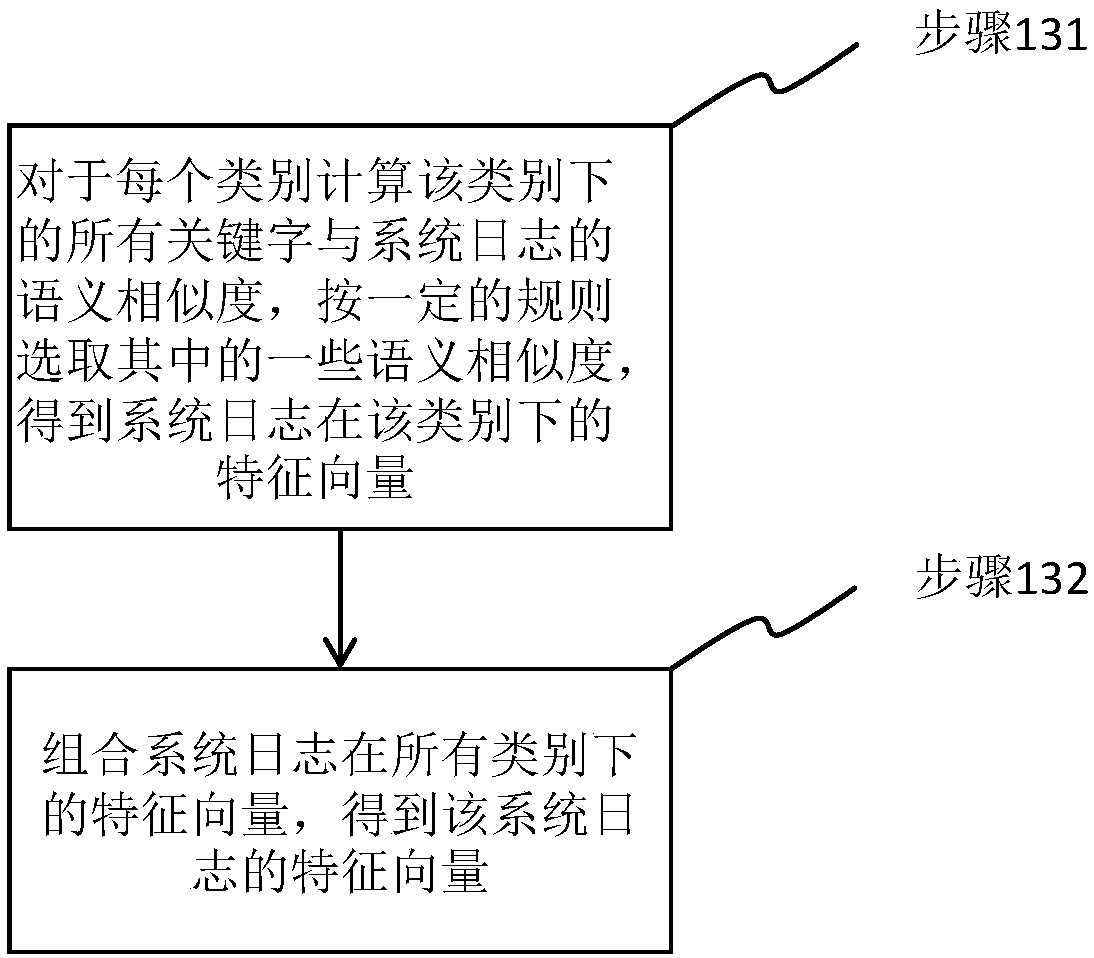
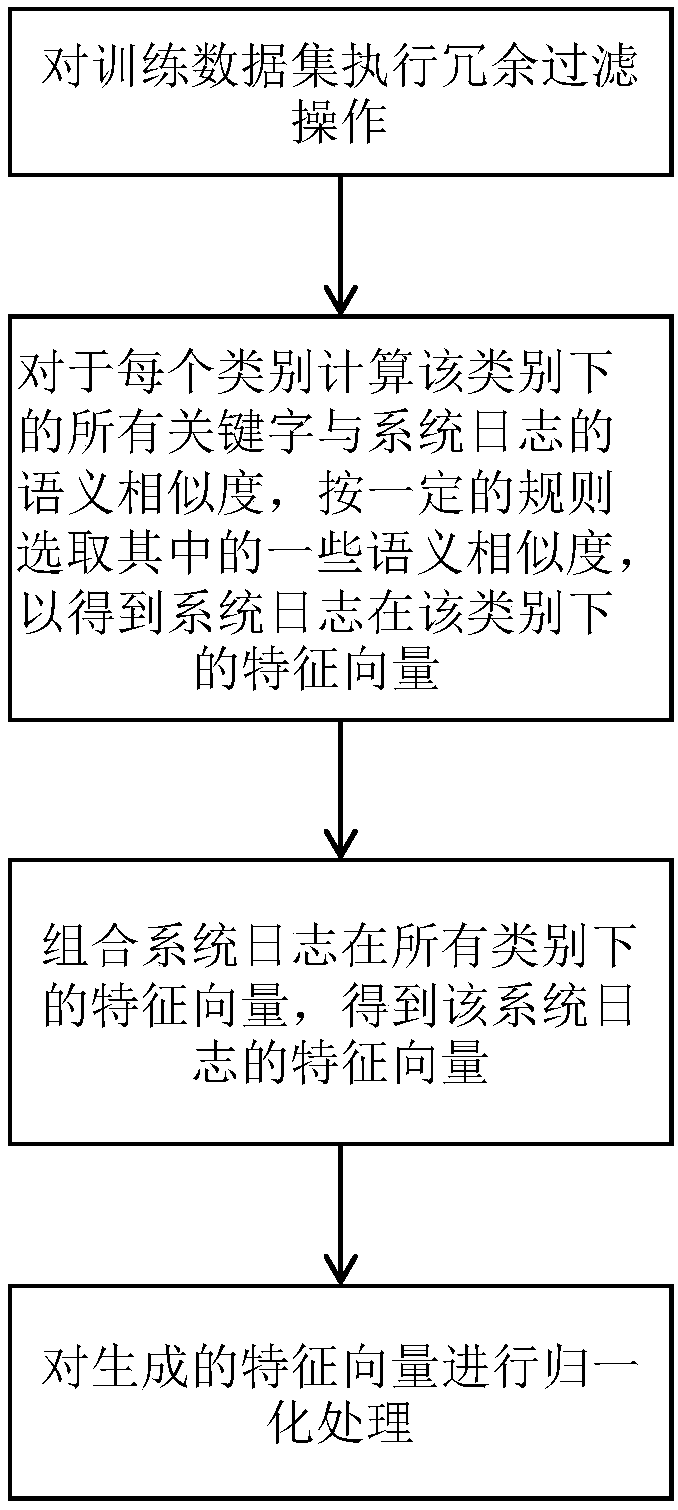
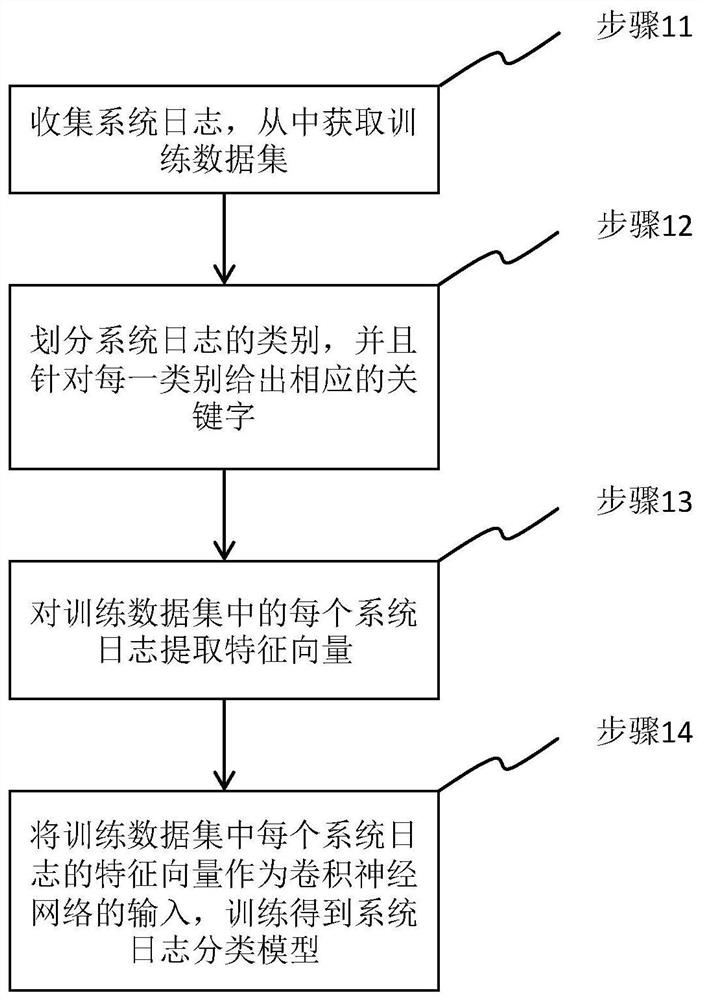
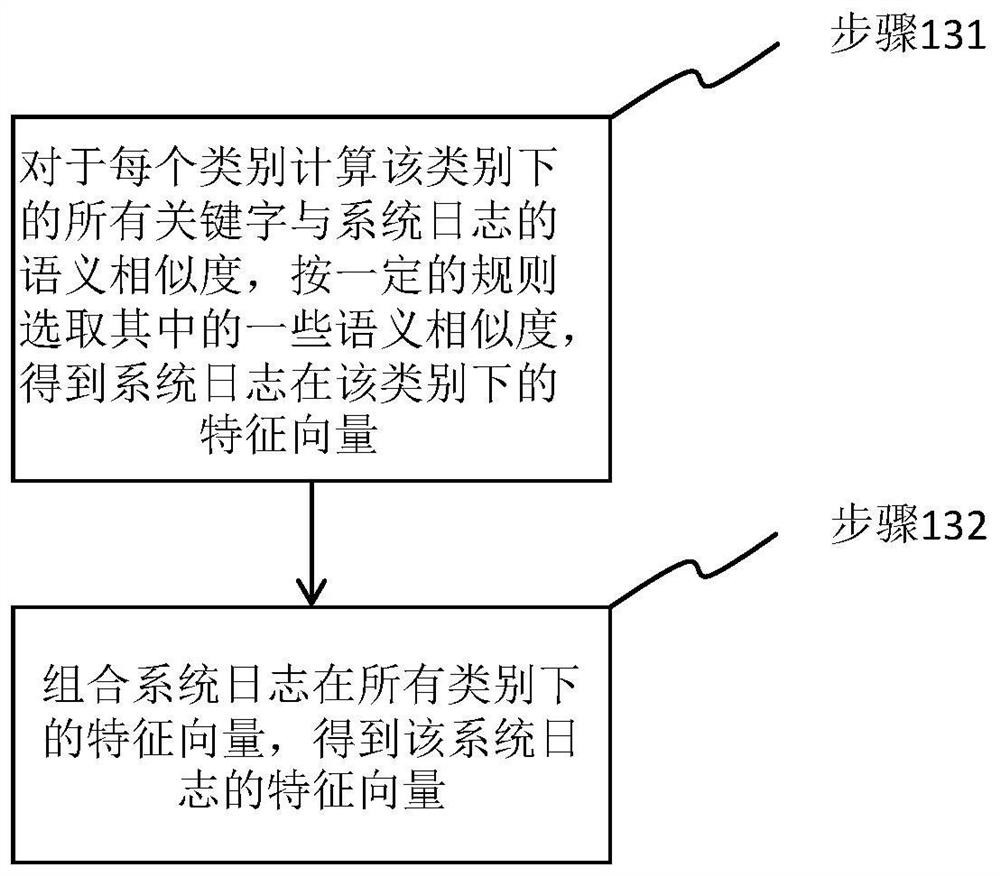
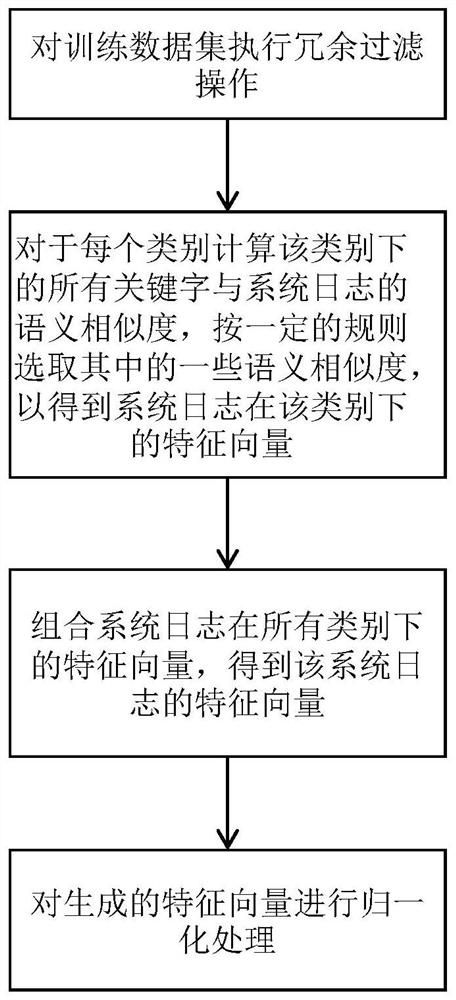
ActiveCN108427720AImprove accuracyImprove timelinessNeural architecturesSpecial data processing applicationsFeature vectorData set
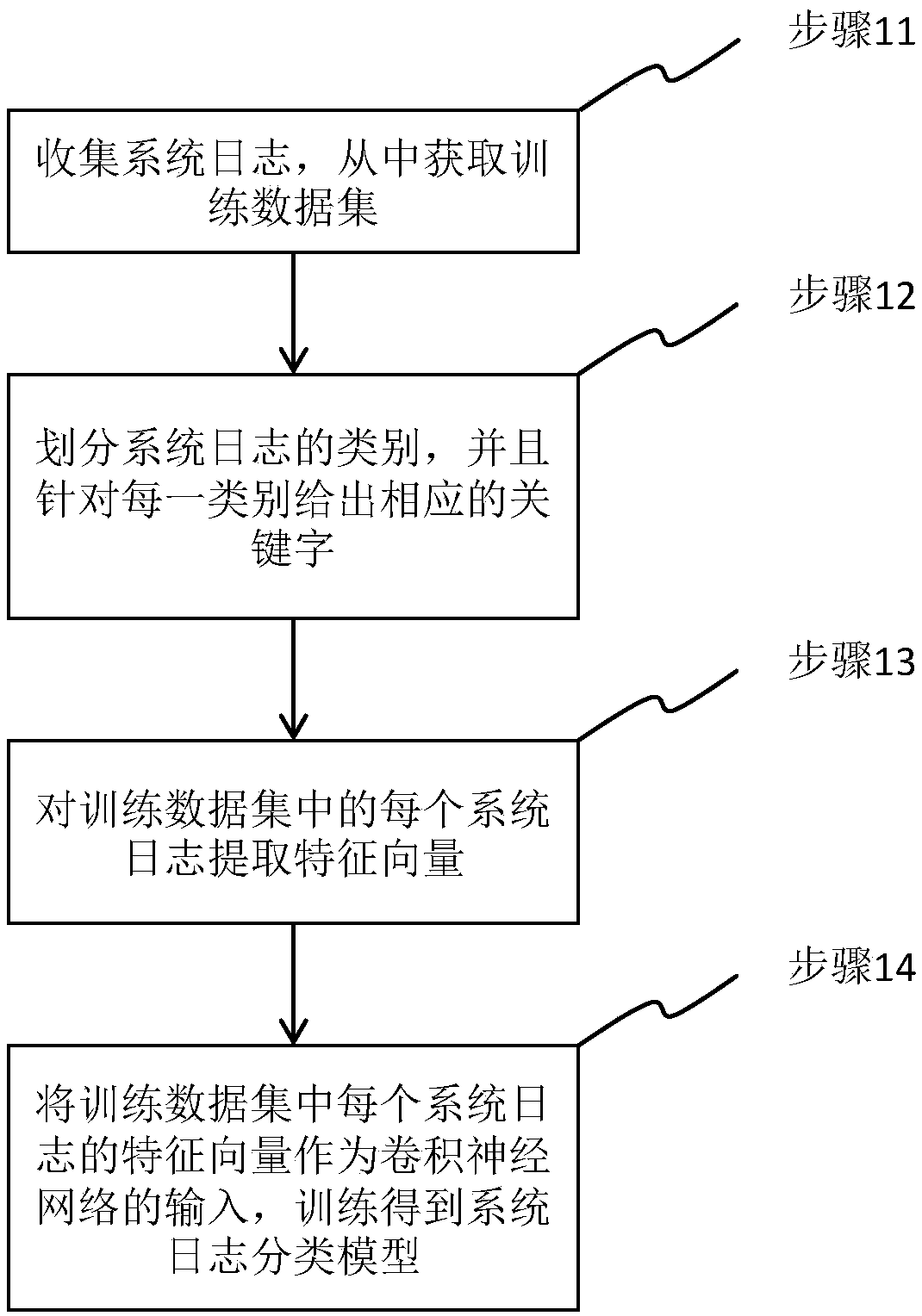
The invention provides a method of extracting a feature vector from a system log, a method of constructing a system-log classification model and a system-log classification method. The method of extracting the feature vector includes: for each category, calculating semantic similarity degrees of keywords of the category and the system log, and selecting certain similarity degrees to use the same as a feature vector of the system log under the category; and combining the feature vectors of the system log under all the categories to obtain the feature vector of the system log. According to the method of constructing the model, the method of extracting the feature vector is utilized to extract feature vectors of a training data set, and the same are used as input of a convolutional neural network (CNN) to train the model. According to the system-log classification method, the method of extracting the feature vector is utilized to extract a feature vector of a system log, and a classification result is obtained through the model. The methods can realize system-log classification of high accuracy and high timeliness.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
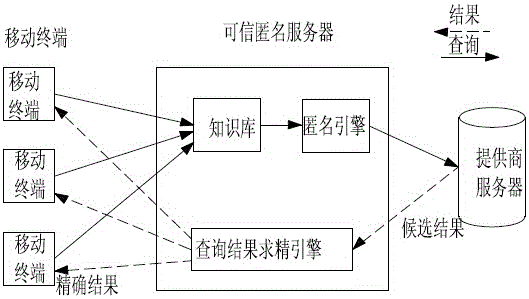
Individuation privacy protection method for sensing semantic query based on road network
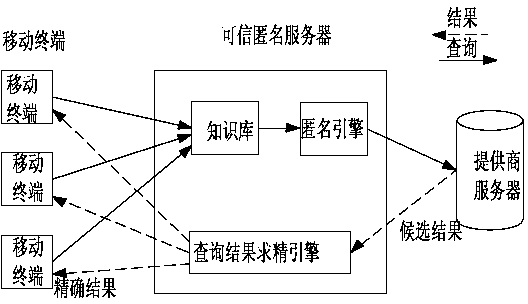
ActiveCN103984764APrevent personal privacy leakageGood serviceSpecial data processing applicationsPersonalizationService provision
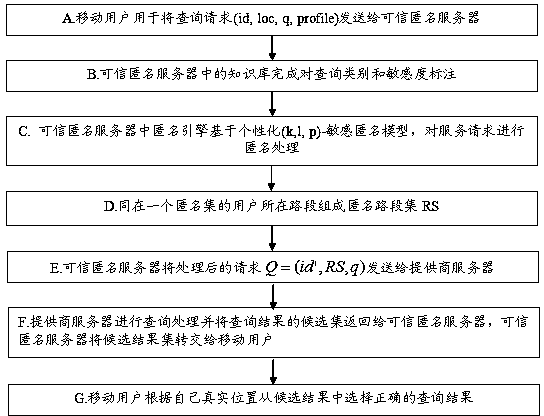
The invention discloses an individuation privacy protection method for sensing a semantic query based on a road network, and relates to the technical field of services specially used for users or terminal locations. The method comprises the following steps that A, a mobile user sends a query request to a credible anonymous server; B, a knowledge base of the credible anonymous server firstly converts the real identifier of the user into a fake name; C, an anonymous engine in the credible anonymous server carries out anonymity processing on a service request based on an individuation-sensitivity anonymous model; D, an anonymous road segment set RS corresponding to the user u is found in an idlist by the credible anonymous server, and the query request carrying the anonymous road segment set is sent to a service provider. The method can solve the problem that individual privacy disclosure happens to the user in the road network under the conditions of providing location-based services and combining the semantic query, the identifier, location and sensitive information of the user are protected, and the user can enjoy the fast and safe location-based services.
Owner:SHIJIAZHUANG TIEDAO UNIV
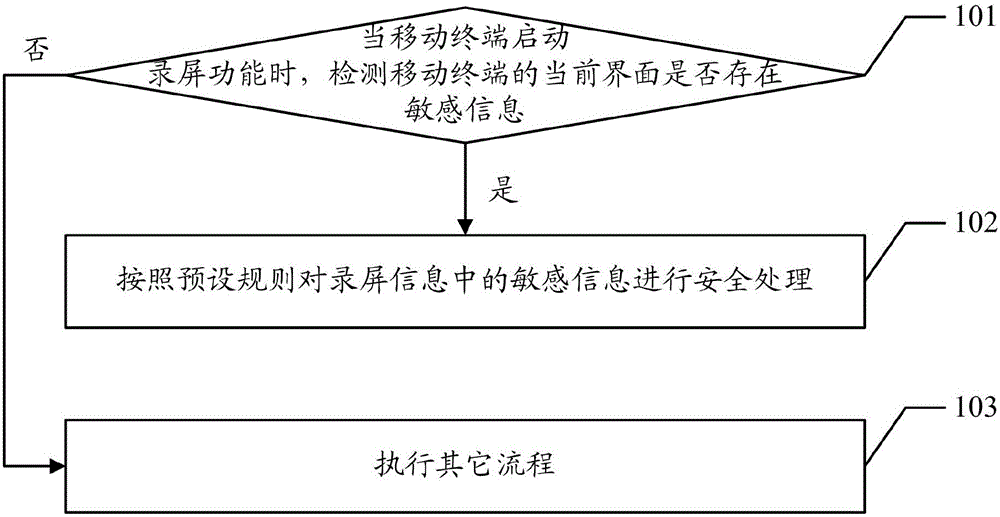
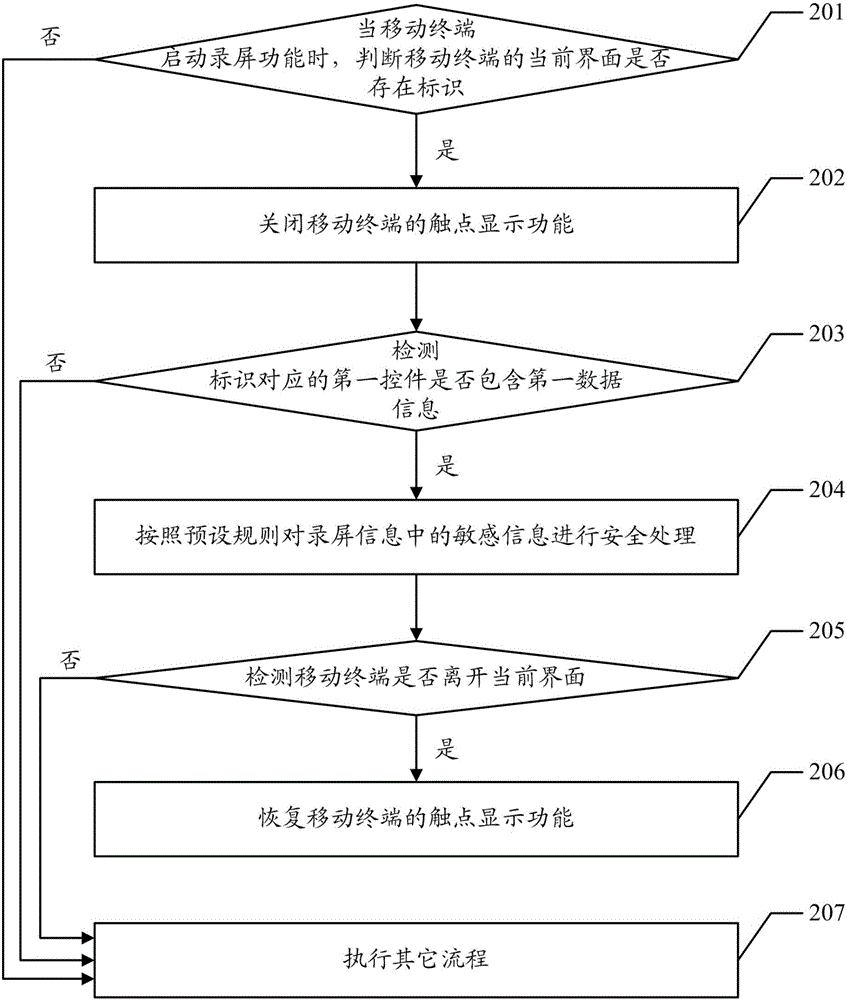
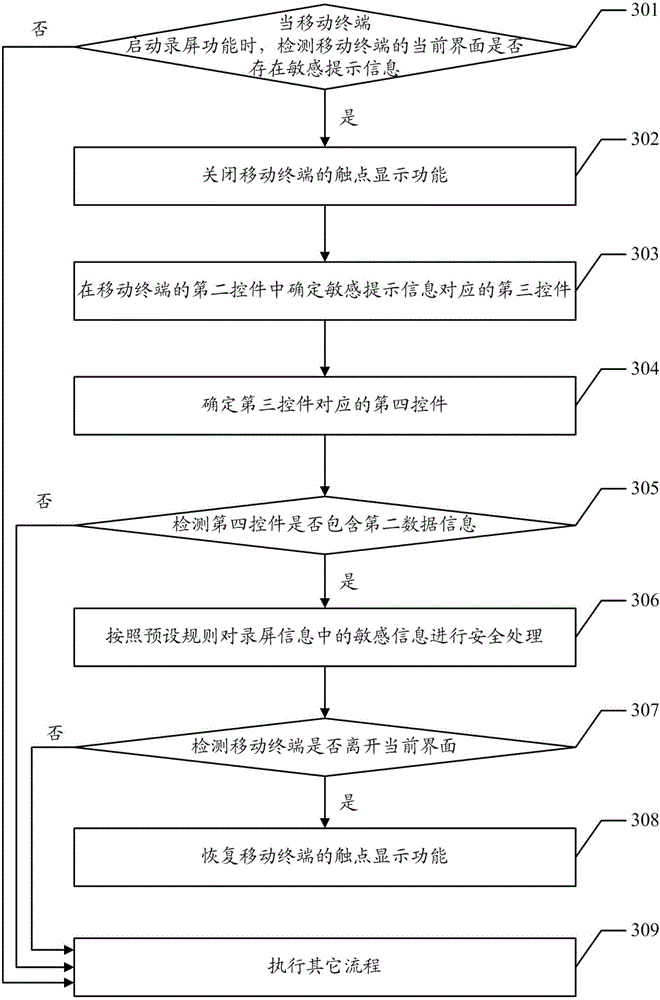
Screen recording method and device
InactiveCN106650441AProtect Sensitive InformationImprove user experienceDigital data protectionInternal/peripheral component protectionComputer terminal
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method for implementing terminal unit data maintenance by client terminal software
ActiveCN101222721BReduce workloadLow professional knowledge requirementProgram loading/initiatingData switching networksData fileTerminal equipment
The invention discloses a method for realizing terminal equipment data maintenance through a client end software which comprises the following steps that: a data file obtaining procedure used to obtain a data file needed by data maintenance of terminal equipment and restricted by certification, and store the file into USB storage equipment compatible with the terminal equipment; a data maintenance procedure used to connect the USB storage equipment into a PC computer, use a client end software installed on the PC computer to connect corresponding terminal equipment, and trigger a data maintenance process. The invention can greatly reduce the workload that the operation-maintenance personnel of the operator opens service at the home of the user, can decrease the requirement of specialized knowledge of the user personnel, and can also make data maintenance operation by using the PC connecting terminal of the client end software when the terminal has no mode to locally make data maintenance.
Owner:苏州医疗器械产业发展集团有限公司
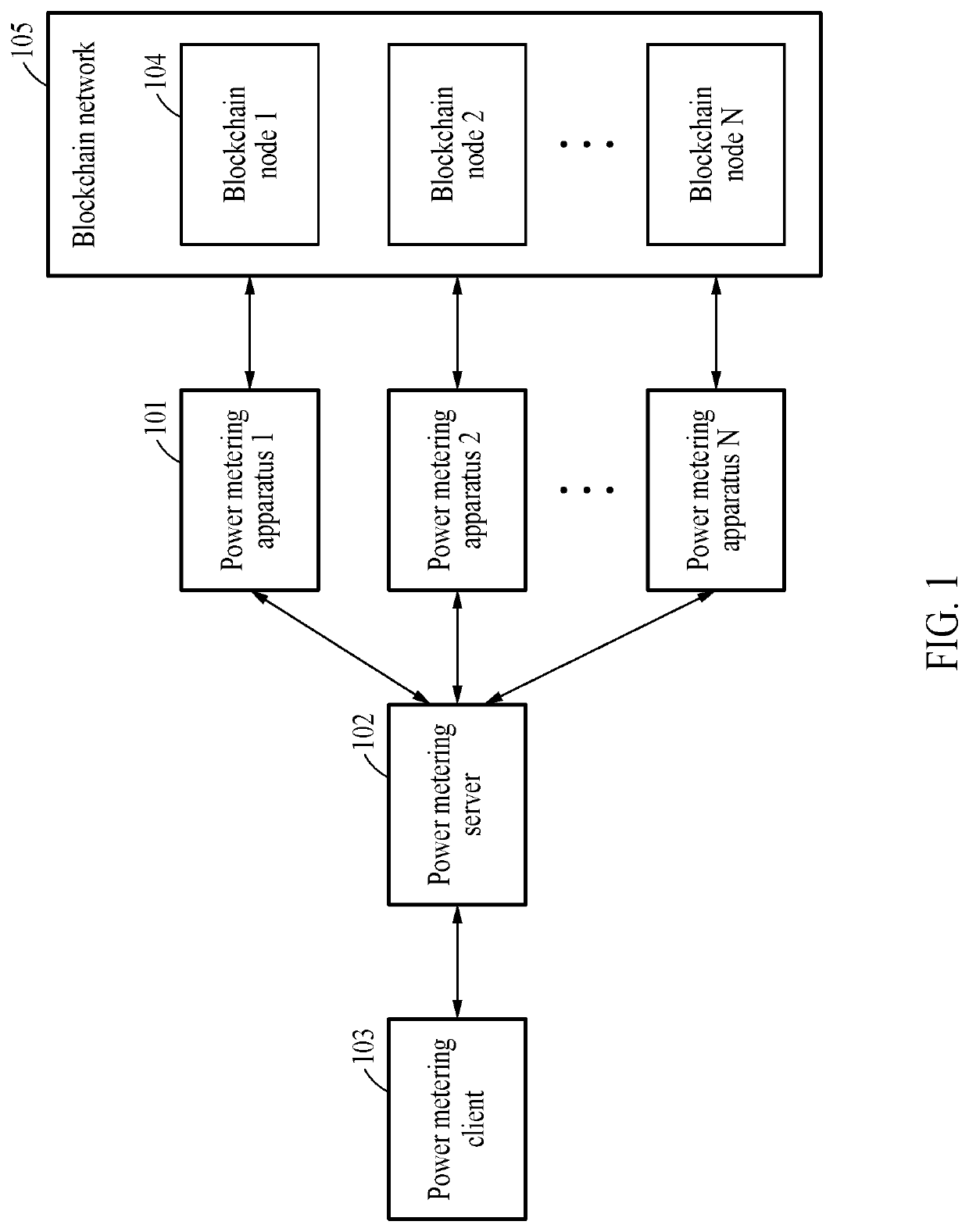
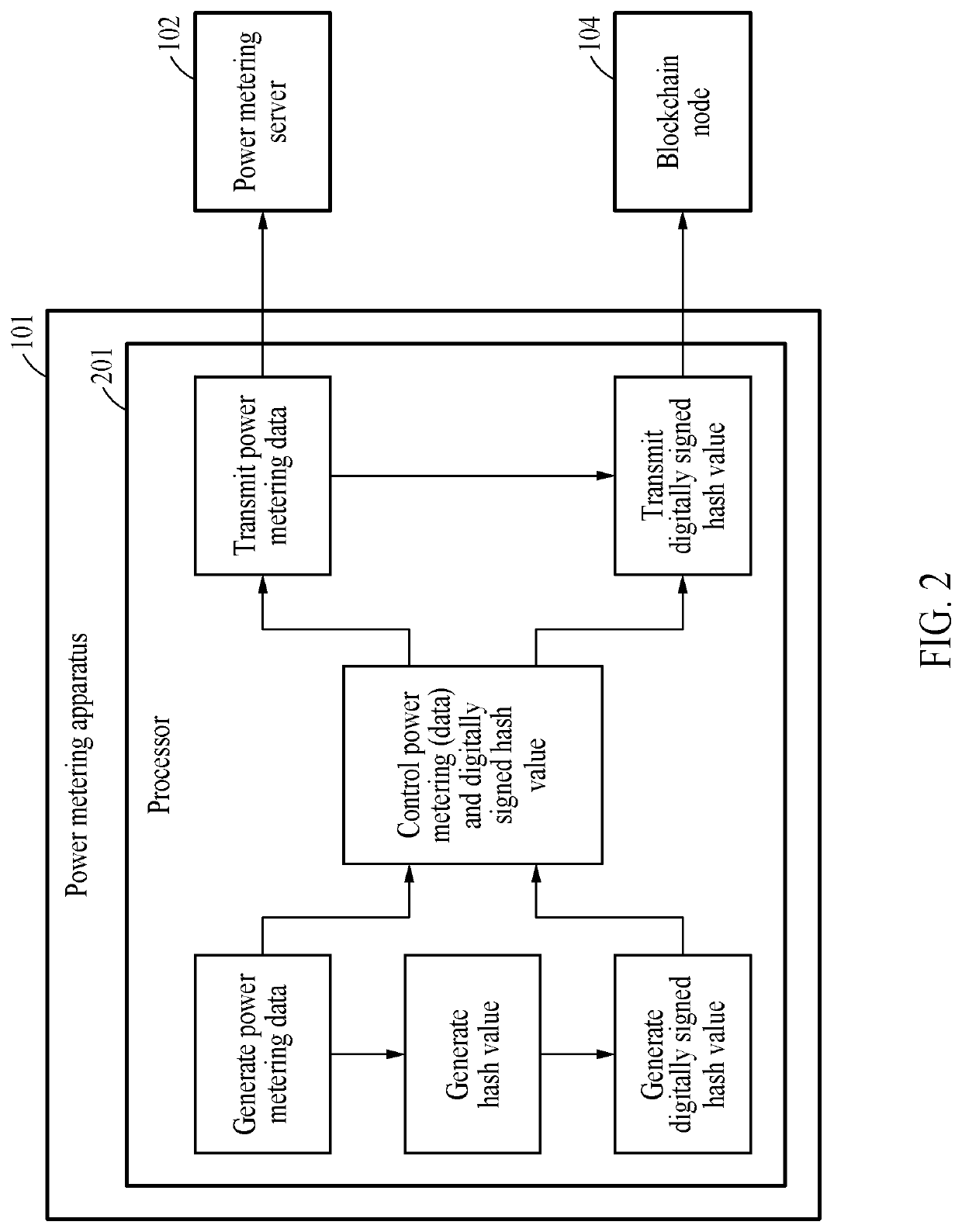
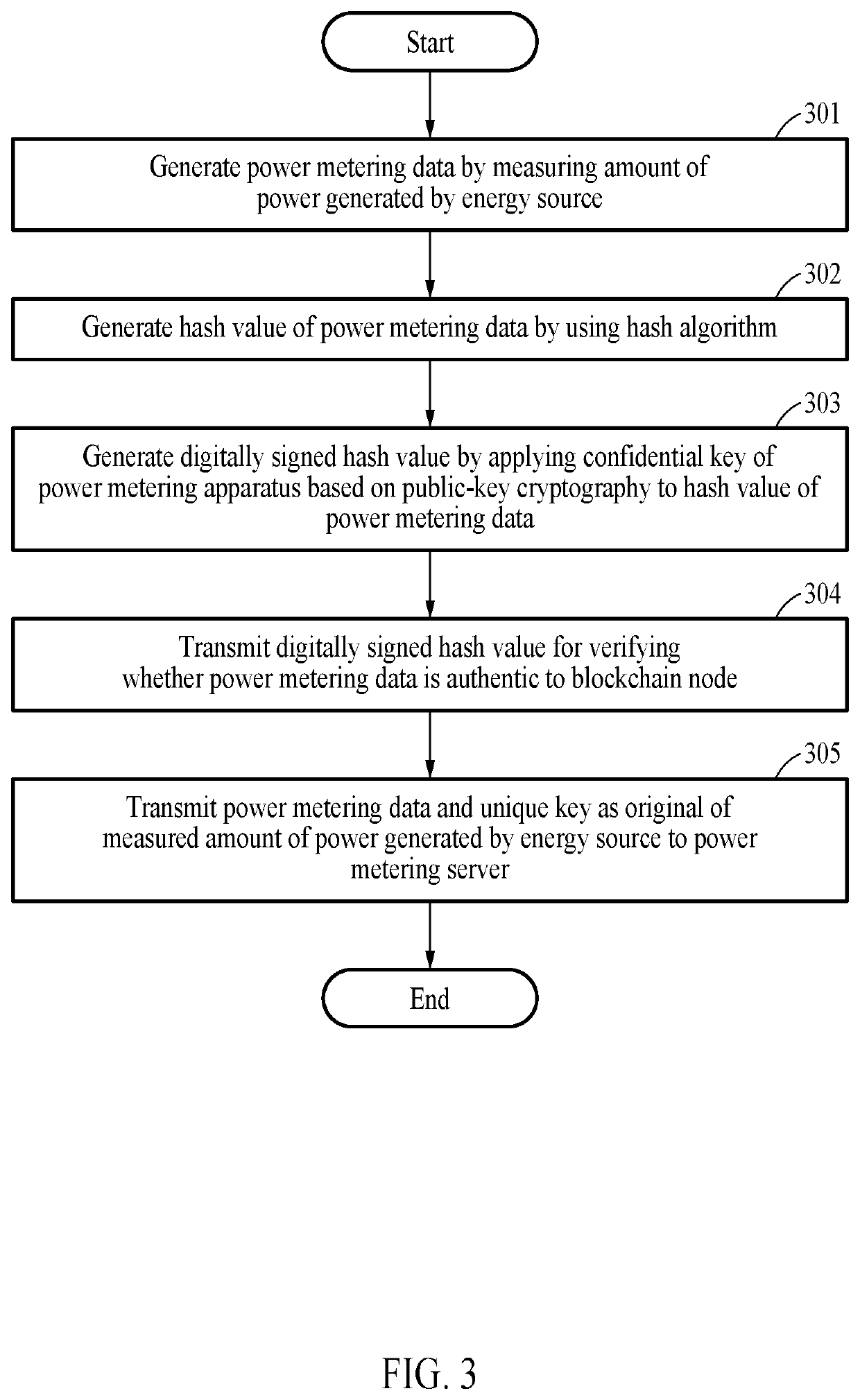
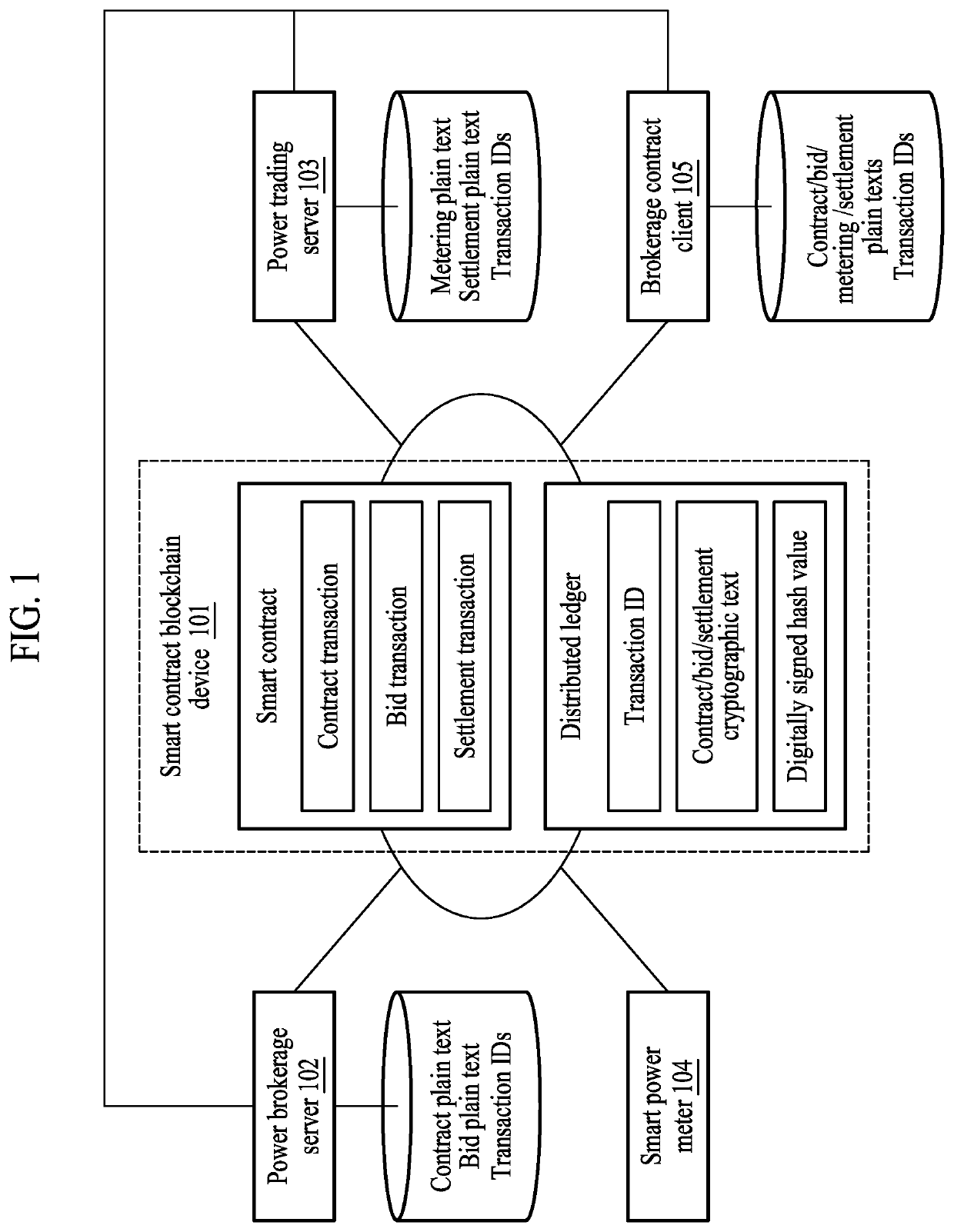
Power metering apparatus, power metering server, and power metering method based on blockchain
PendingUS20210263083A1IntegrityTransparencyCryptography processingUser identity/authority verificationDigital signatureData store
A power metering apparatus, a power metering server, and a power metering method based on a blockchain are disclosed. Particularly, in order to simultaneously assure integrity and transparency of power metering data based on a blockchain, power metering data generated by measuring an amount of power generated by an energy source and a unique key are stored in a database linked to a power metering server, and a digitally signed hash value of the power metering data is stored in a blockchain node. Accordingly, disclosed are blockchain-based power metering system and method for preventing forgery and tampering of power metering data, solving a problem associated with a blockchain storage capacity that may occur when storing the power metering data, and protecting sensitive information on the power metering data.
Owner:ELECTRONICS & TELECOMM RES INST
Unidirectional heterogeneous spectrum allocation method based on differential privacy protection
ActiveCN111954220AIncrease profitAlleviate spectrum scarcityCommerceSecurity arrangementDistributed computingOperations research
The invention discloses a one-way heterogeneous spectrum allocation method based on differential privacy protection. The method comprises the following steps: 1, determining corresponding earnings andallocation schemes under a quoted price by pricing combinations of different spectrums; 2, protecting pricing by taking the total welfare value as an availability function through a differential privacy mechanism; and 3, determining a final price, and obtaining a corresponding distribution mode according to the finally selected price. According to the method, the problem of privacy leakage in traditional one-way heterogeneous spectrum auction can be remarkably solved, so that quotation information can be effectively protected, and meanwhile, efficient spectrum allocation is realized.
Owner:ANHUI UNIVERSITY +1
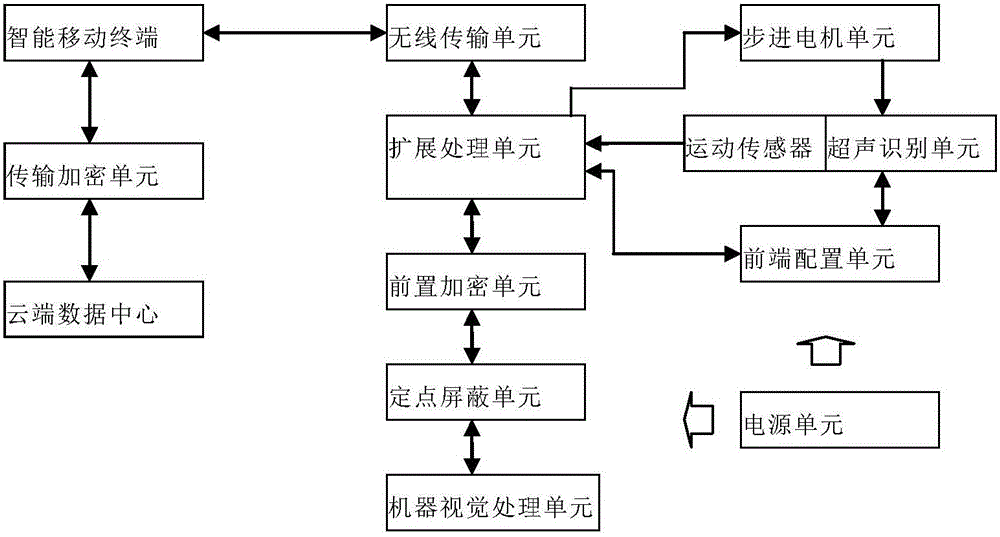
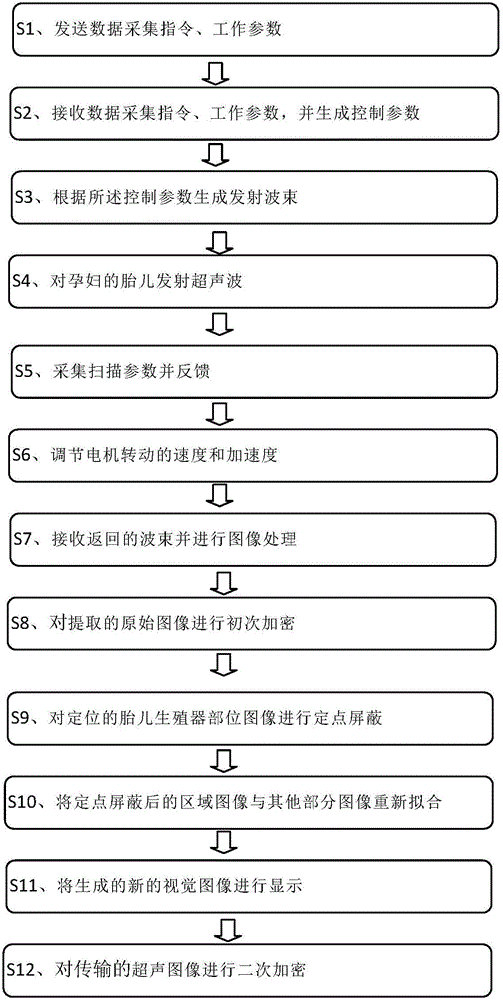
A wireless intelligent ultrasonic fetus imaging shield method
InactiveCN106108950AHigh precision of sex part targetingProtect Sensitive InformationOrgan movement/changes detectionInfrasonic diagnosticsMultiple encryptionRadiology
The wireless intelligent ultrasonic fetal imaging shielding method of the present invention can quickly and intelligently realize gender screening of fetal ultrasonic three-dimensional and four-dimensional imaging and perform shielding. The positioning accuracy of the fetal sex position is high, and through multiple encryptions of the acquired ultrasound images, the sensitive information of the fetus is better protected, which has a positive auxiliary effect on social progress.
Owner:NINGBO MARVOTO INTELLIGENT TECH CO LTD
Efficient association method of alarm logs
ActiveCN110188025AGuaranteed uptimeSmall amount of calculationHardware monitoringSerializationWorkload
The invention discloses an efficient association method of alarm logs, which comprises the following steps of: 1, serializing alarm information logs to obtain a time period-event set table; 2, averaging the time period-event set table, changing the data structure to obtain an event-time period set table; 3, iteratively calculating a frequent item set; and 4, pushing a plurality of pieces of alarminformation with the highest importance degree. According to the method, mass alarm information can be efficiently processed, and alarm items causing alarm storms are pushed, so that the workload of operation and maintenance personnel is greatly reduced, and a reliable method is provided for distributed alarm log processing.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +7
Data authority management method based on identifier analysis
PendingCN114817879AProtect Sensitive InformationGuarantee work efficiencyDigital data processing detailsDigital data protectionAnalysis dataInternet privacy
The invention discloses a data authority management method based on identifier analysis, which comprises the following steps that: a login verification module acquires identity information of a visiting user, judges whether the visiting user is a registered user, and forwards a data query request sent by the user to a dynamic calculation module if the visiting user is the registered user; if not, forwarding the data query request to a data management module; the dynamic calculation module receives the data query request, gives a corresponding query permission level according to identity information of a visiting user, binds the query permission level with the data query request and then sends the data query request to the data management module; the data management module receives the data query request and judges whether the data query request is bound with an authority level or not, and if yes, non-public identification analysis data corresponding to the authority level is called and sent to the visiting user; and if not, calling the public identifier analysis data and sending the public identifier analysis data to the visiting user. According to the data authority management method based on identification analysis, the data sharing security under an identification analysis system is effectively guaranteed.
Owner:苏州协同创新智能制造科技有限公司
Method, device and electronic equipment for acquiring and feeding back user resources
ActiveCN109033774BAvoid passing situationsProtect personal privacyDigital data authenticationAuthorization certificateEngineering
Disclosed are a method and device for acquiring and feeding back a user resource, and an electronic apparatus. The method for acquiring a user resource comprises: transmitting to a target user an authorization request used to request access permission to a preset resource of the target user, the preset resource being stored in a resource server of a preset social application; receiving an authorization certificate fed back by the target user after the target user determines to authorize the access permission; applying for authorization information of the preset resource to an authentication server of the preset social application on the basis of the authorization certificate, the authorization information comprising a token and an identity identifier of the target user; and accessing the resource server on the basis of the token and the identity identifier, so as to acquire the preset resource.
Owner:ADVANCED NEW TECH CO LTD
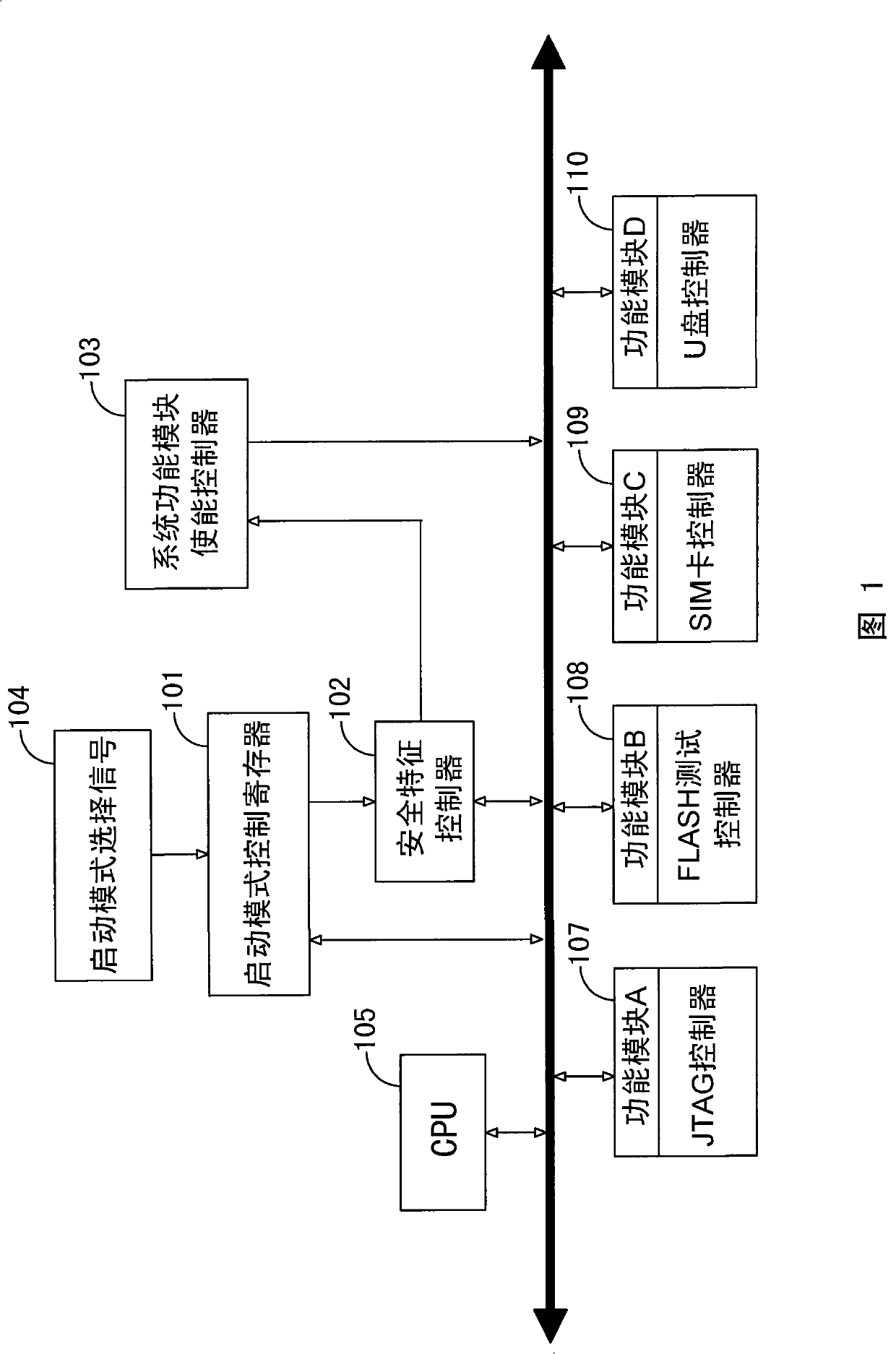
Multi-mode startup safety embedded system
ActiveCN101561857BImplement multi-mode bootEnsure safetyPlatform integrity maintainanceElectricityMode control
The invention discloses a multi-mode startup safety embedded system for ensuring the embedded system to safely enter a mode designated by a user when carrying out the multi-mode startup. The system judges the startup mode of the system according to safety feature values in a safety feature controller after being switched on, if the safety feature controller does not saves the safety feature values, the startup mode of the system is selected according to a startup mode selection signal and a startup mode control register. The different safety feature values can set the different safety levels for the startup way of the embedded system. The multi-mode startup safety embedded system can not only be used for realizing the multi-mode startup of the embedded system, but also ensure the safety offirmware and hardware in the system at the work mode which needs to be protected, thereby being applicable to the prior multi-application of the embedded system and also taking into account of the demands on the safety.
Owner:苏州国芯科技股份有限公司
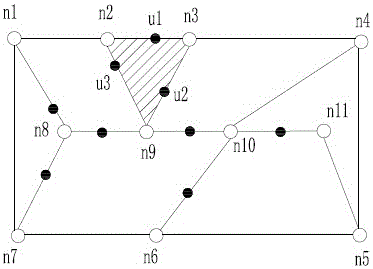
A Personalized Privacy Preservation Method Based on Road Network Aware Query Semantics
ActiveCN103984764BPrevent personal privacy leakageGood serviceSpecial data processing applicationsPersonalizationService provision
Owner:SHIJIAZHUANG TIEDAO UNIV
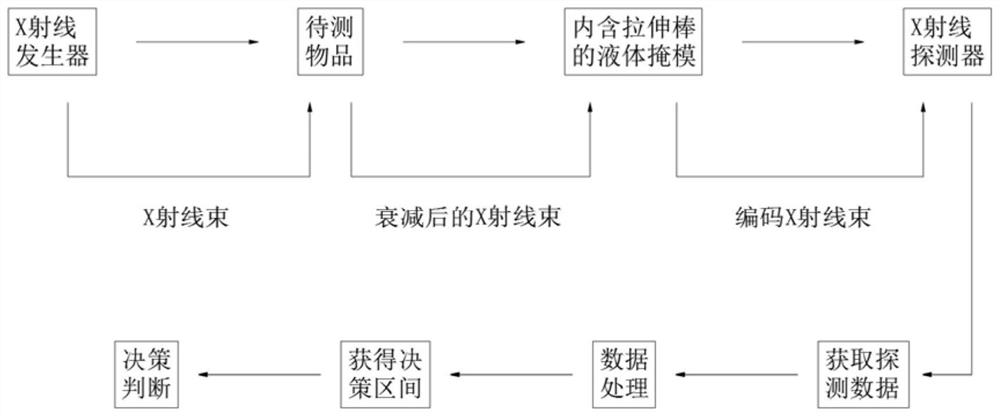
A Dense Radiation Imaging System Based on Random Thickness Liquid Mask
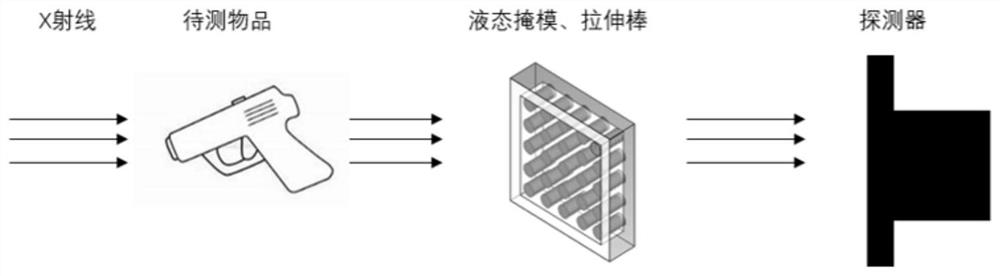
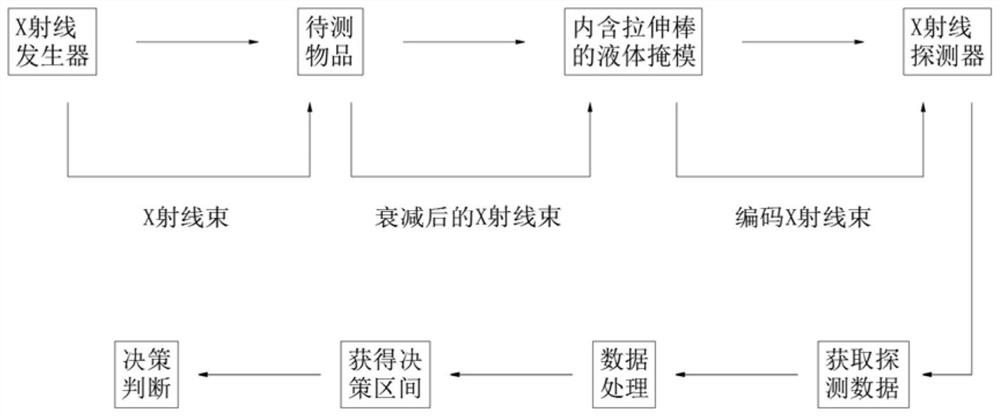
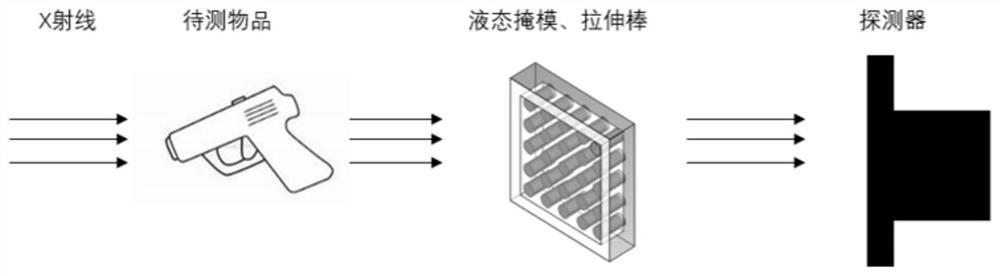
ActiveCN113466956BImplement random decayProtect Sensitive InformationCharacter and pattern recognitionNuclear radiation detectionLiquid stateRadiation imaging
The invention discloses an encrypted radiation imaging system based on a random thickness liquid mask, which includes an X-ray source, an object to be detected, a liquid metal mask, a thickness control array inside the mask, and an X-ray detector. The thickness control array randomly adjusts the thickness of the liquid mask, realizes random attenuation of the X-rays penetrating the mask, and then encrypts the sensitive information carried in the X-ray imaging, effectively protecting the sensitive information of the items to be inspected, and realizing Encryption measures of physical shielding are used for the energy and position information of the emitted particles, and the proposed security inspection technology encrypts the information carried by the emitted X-rays from the physical field, avoiding the risk of private information being leaked, and will not expose any information about the items to be inspected. For privacy information, the template comparison method is used to facilitate the confirmation of whether the items to be inspected contain contraband, and the security inspection is realized on the basis of protecting the sensitive information of the inspected items.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
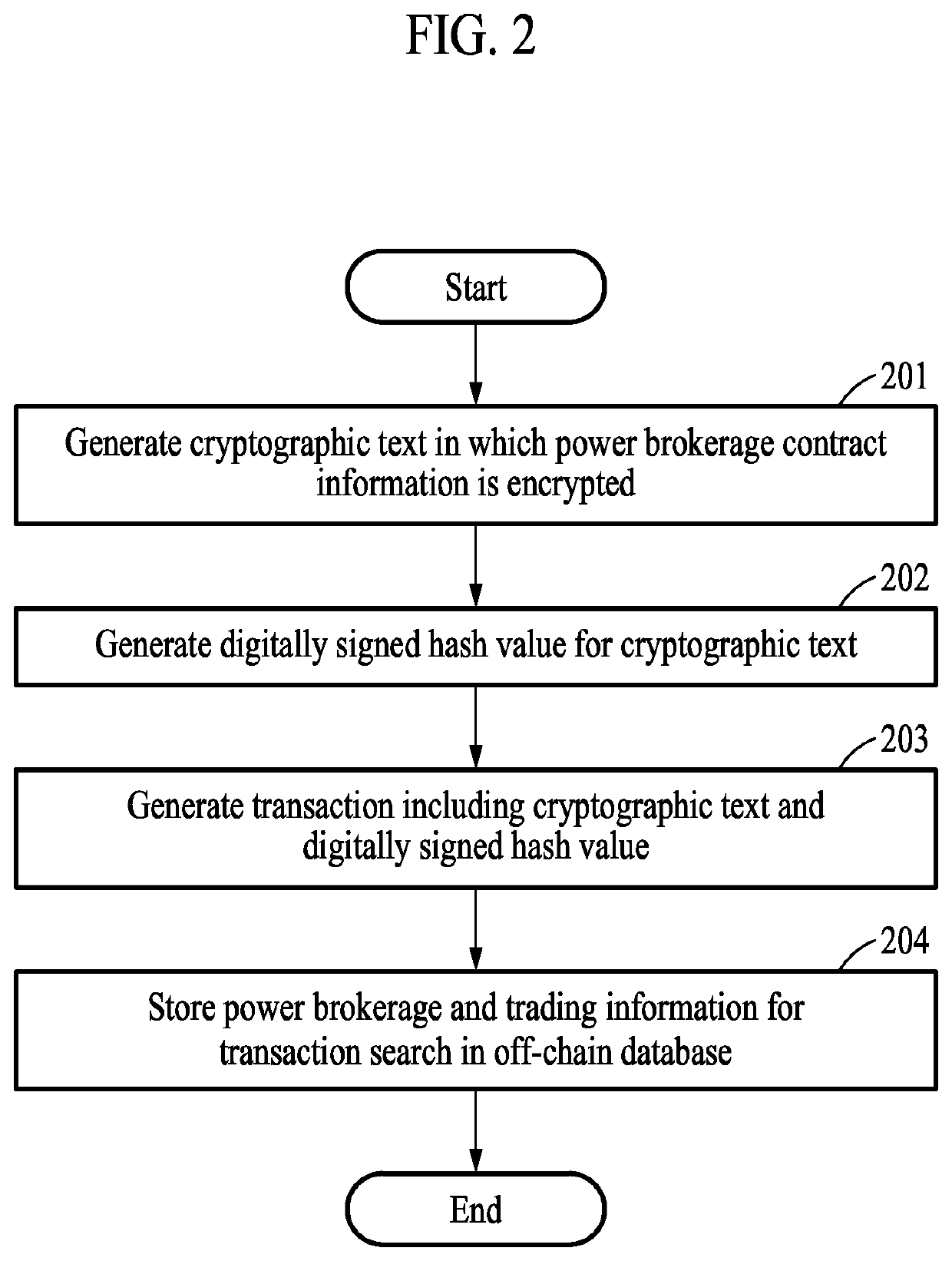
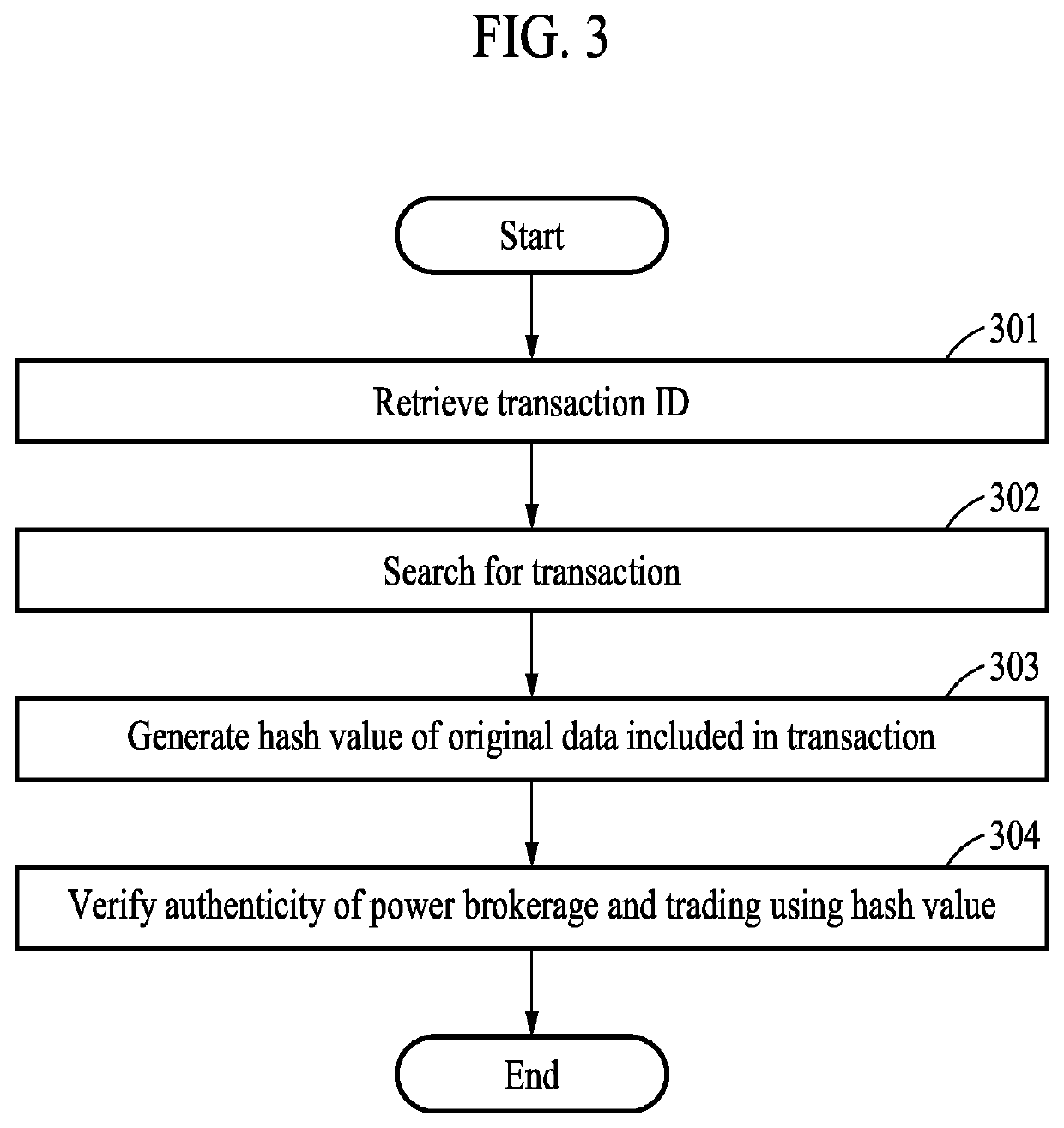
Electric power brokerage method and system with enhanced data confidentiality and integrity based on blockchain
PendingUS20220237695A1Ensure integrityEnsure transparencyFinanceUser identity/authority verificationData integrityOriginal data
Provided are a power brokerage method and a power brokerage system, and the power brokerage system stores encrypted power brokerage and trading information and a digitally signed hash value in a blockchain distributed ledger through a smart contract code running on a blockchain platform and allows the same to be retrieved. Also, the power brokerage system protects sensitive information related to a brokerage trading contract, a bid, and a settlement by allowing a participant participating in the power market to retrieve original data related to power brokerage and trading information from a power trading server and to compare and verify data forgery / falsification and, at the same time, ensures data integrity and transparency of a brokerage contract and trading.
Owner:ELECTRONICS & TELECOMM RES INST
Intelligent baseline determination and alarm method for system data of ubiquitous power Internet of Things
ActiveCN111030855AGuaranteed uptimeEasy to useData switching networksData miningReliability engineering
The invention discloses a data intelligent baseline determination and alarm method for the system data of a ubiquitous power Internet of Things, and the method comprises the following steps: 1, determining intelligent baselines, including a page view baseline, a time baseline and an error rate baseline; 2, constructing an isolated forest; 3, giving intelligent alarms, including alarm based on an intelligent baseline and alarm based on an isolated forest algorithm. According to the invention, the system data of the ubiquitous power Internet of Things can be efficiently processed, the system hasaccurate prediction capability for faults, and meanwhile, operation and maintenance personnel can detect and repair the faults in time in combination with an intelligent alarm pushing strategy, so the stability of the system is greatly improved.
Owner:STATE GRID SHANXI ELECTRIC POWER +2
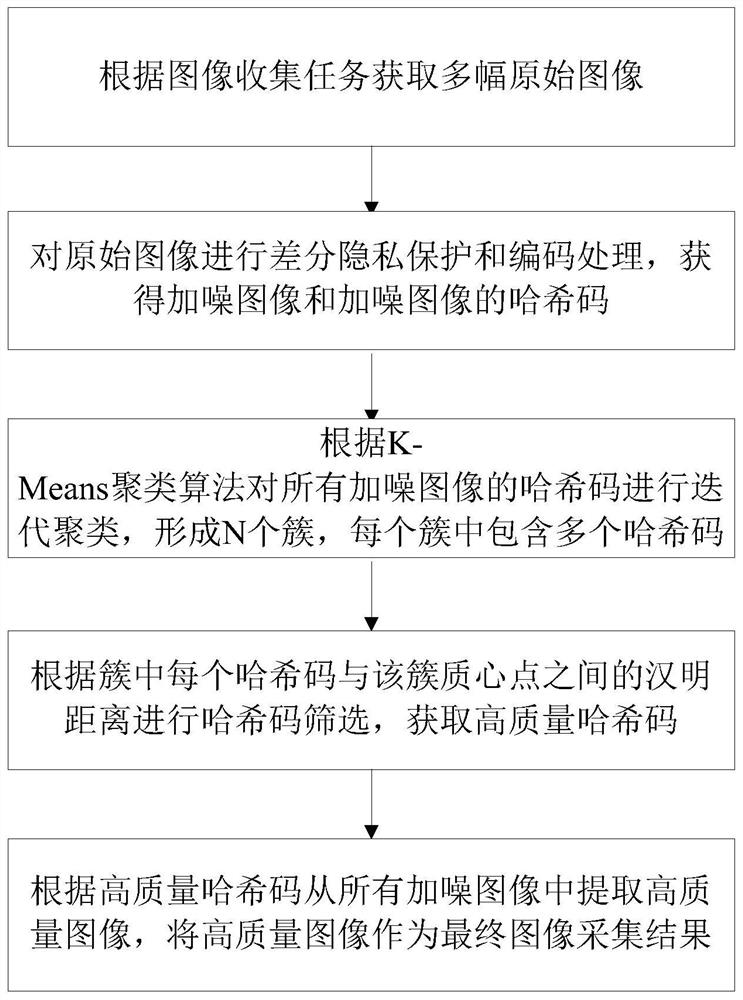
Image acquisition method and device considering privacy protection and data quality, and storage medium
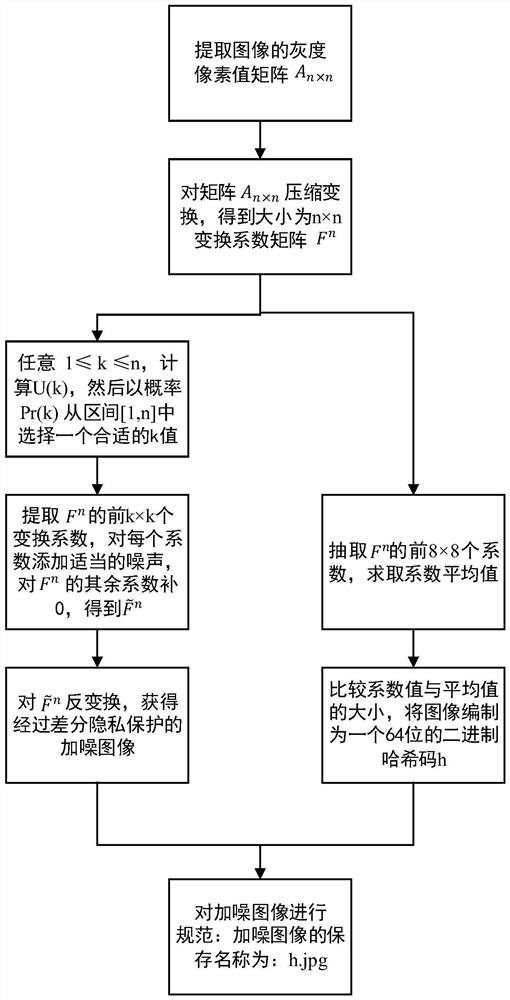
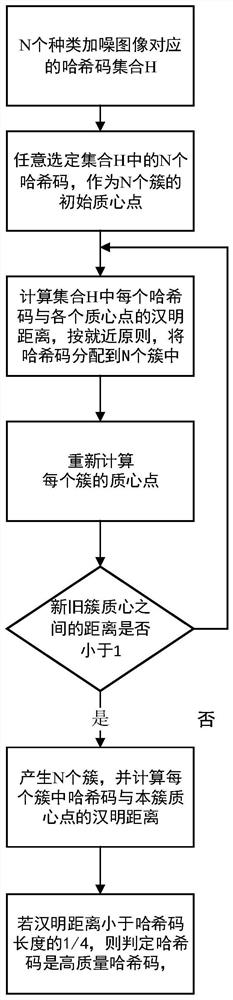
ActiveCN112383672AProtect Sensitive InformationRealize privacy protection functionCharacter and pattern recognitionPictoral communicationPrivacy protectionDifferential privacy
The invention discloses an image acquisition method and device considering privacy protection and data quality, and a storage medium, and aims to solve the technical problem that the image privacy protection effect and the data quality are difficult to consider at the same time. The method comprises the following steps: acquiring a plurality of original images according to an image collection task; carrying out differential privacy protection and encoding on the original images to obtain noise-added images and hash codes of the noise-added images; carrying out iterative clustering on the hashcodes of all the noise-added images to form N clusters, and each cluster comprises the hash codes; performing hash code screening according to the Hamming distance between each hash code in a clusterand the centroid point of the cluster to obtain high-quality hash code; and extracting a high-quality image from all the noise-added images according to the high-quality hash code, and taking the high-quality image as a final image acquisition result. Image privacy protection and data quality can be well considered, and the images not prone to privacy leakage, high in availability, high in qualityand high in reliability is obtained.
Owner:NANJING UNIV OF POSTS & TELECOMM
An Efficient Correlation Method for Alarm Logs
ActiveCN110188025BGuaranteed uptimeSmall amount of calculationHardware monitoringTime segmentData mining
The invention discloses a method for efficiently associating alarm logs. The steps include: 1. Serialize alarm information logs to obtain a time period-event set table; Time period set table; 3. Iterative calculation of frequent itemsets; 4. Push some alarm information with the highest importance. The present invention can efficiently process massive alarm information and push alarm entries that cause alarm storms, thereby greatly reducing the workload of operation and maintenance personnel and providing a reliable method for distributed alarm log processing.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +7
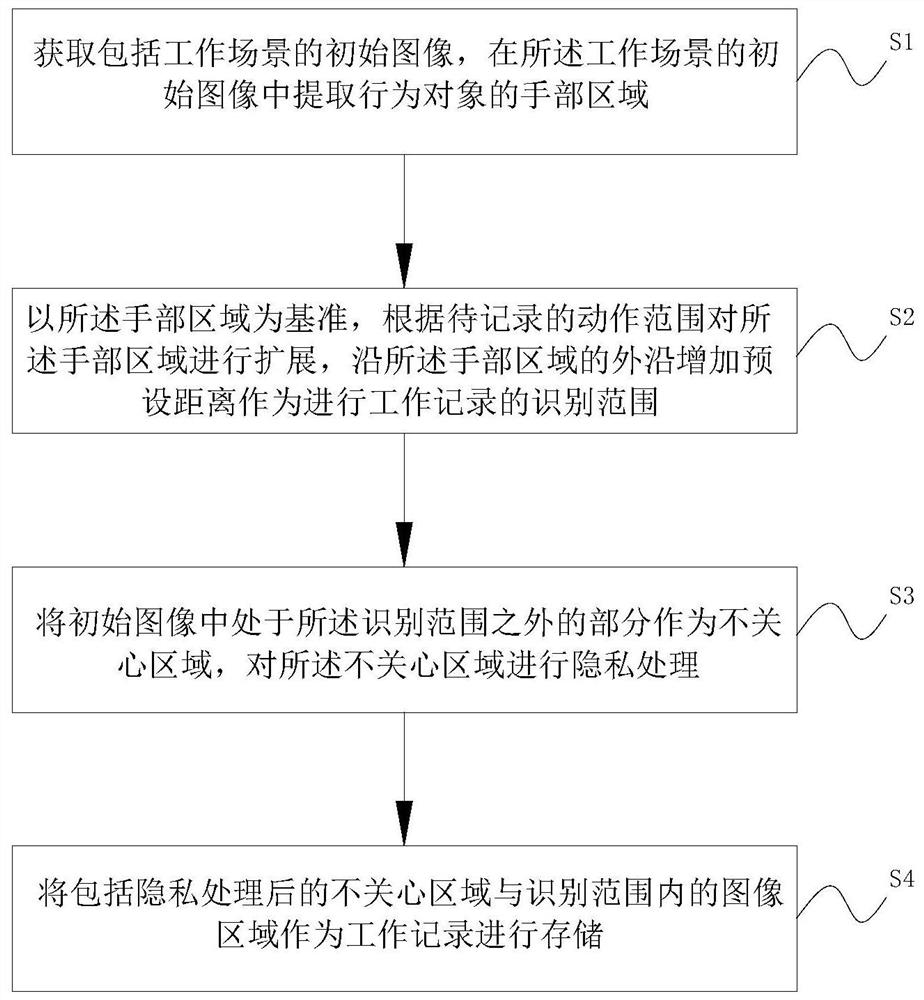
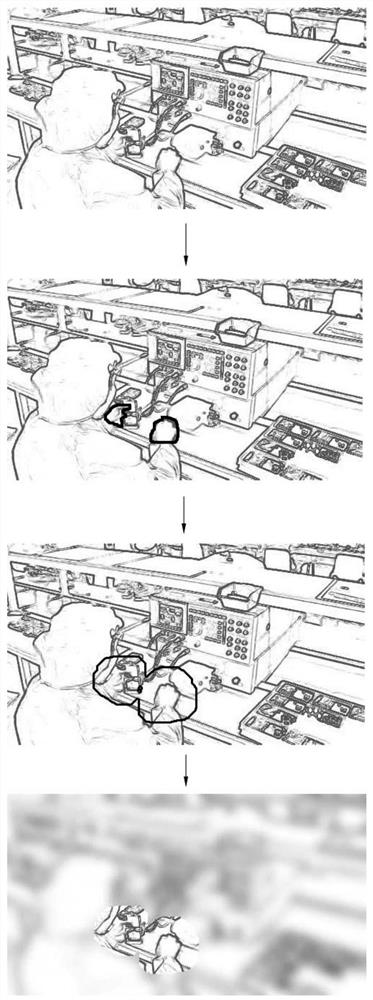
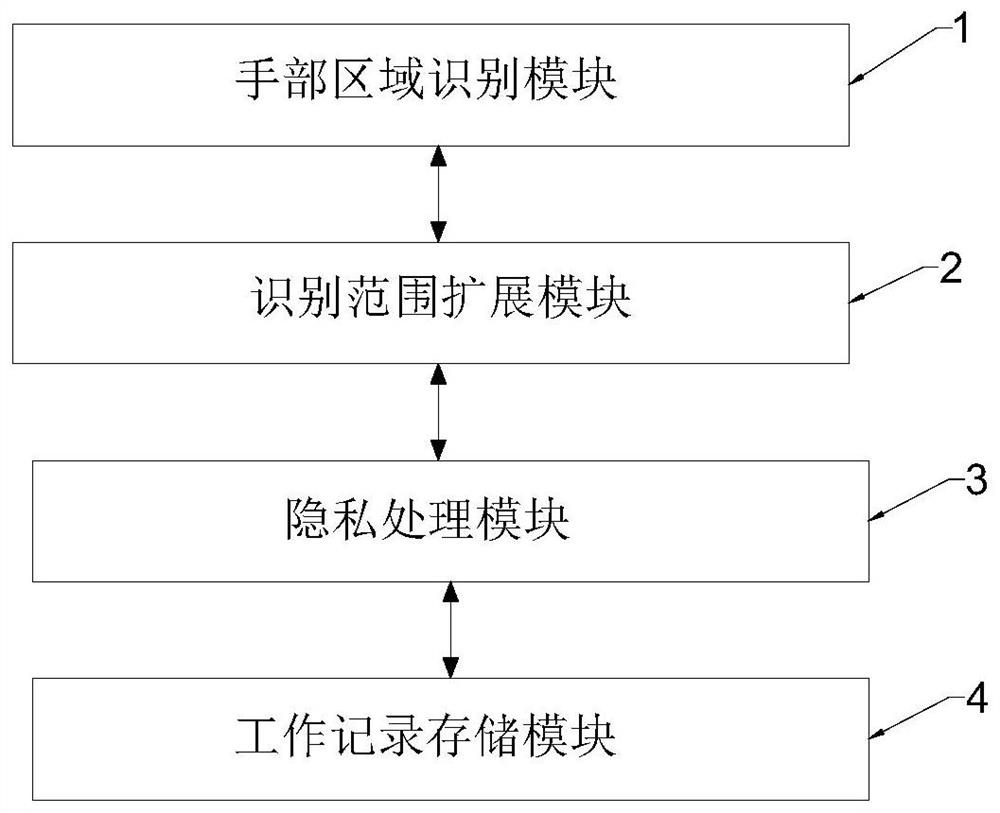
Working site work recording method and system with privacy protection effect
PendingCN113378645ASolve personal privacy issuesPrivacy protectionTelevision system detailsCharacter and pattern recognitionPrivacy protectionEngineering
The invention relates to a working site work recording method and system with a privacy protection effect, and the method comprises the steps: obtaining an initial image comprising a working scene, and extracting a hand region of a behavior object from the initial image of the working scene; taking the hand area as a reference, expanding the hand area according to a to-be-recorded action range, and increasing a preset distance along the outer edge of the hand area to serve as an identification range for working recording; and taking a part outside the identification range in the initial image as an unconcerned area, performing privacy processing on the unconcerned area, and storing the unconcerned area after privacy processing and an image area in the identification range as a work record. According to the method, the personal privacy problem, sensitive information and the like generated during traditional work recording are effectively solved, the most basic work record definition serves as a solution point, it is guaranteed that the activity condition of the hand of a behavior object can be shot in the maximum range, work records related to the hand activity are concerned and reserved, and privacy and sensitive information are effectively protected.
Owner:北京立为智图科技有限公司
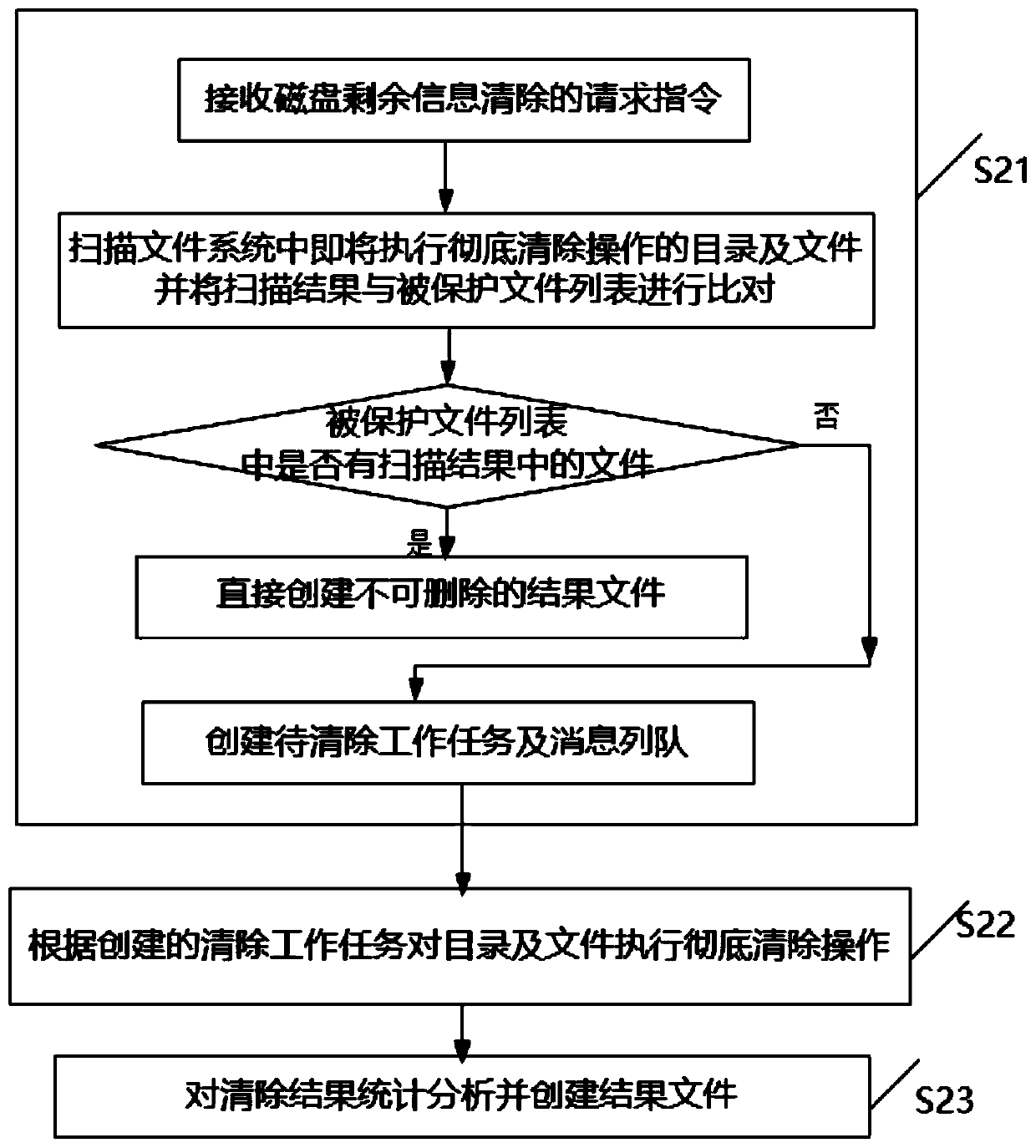
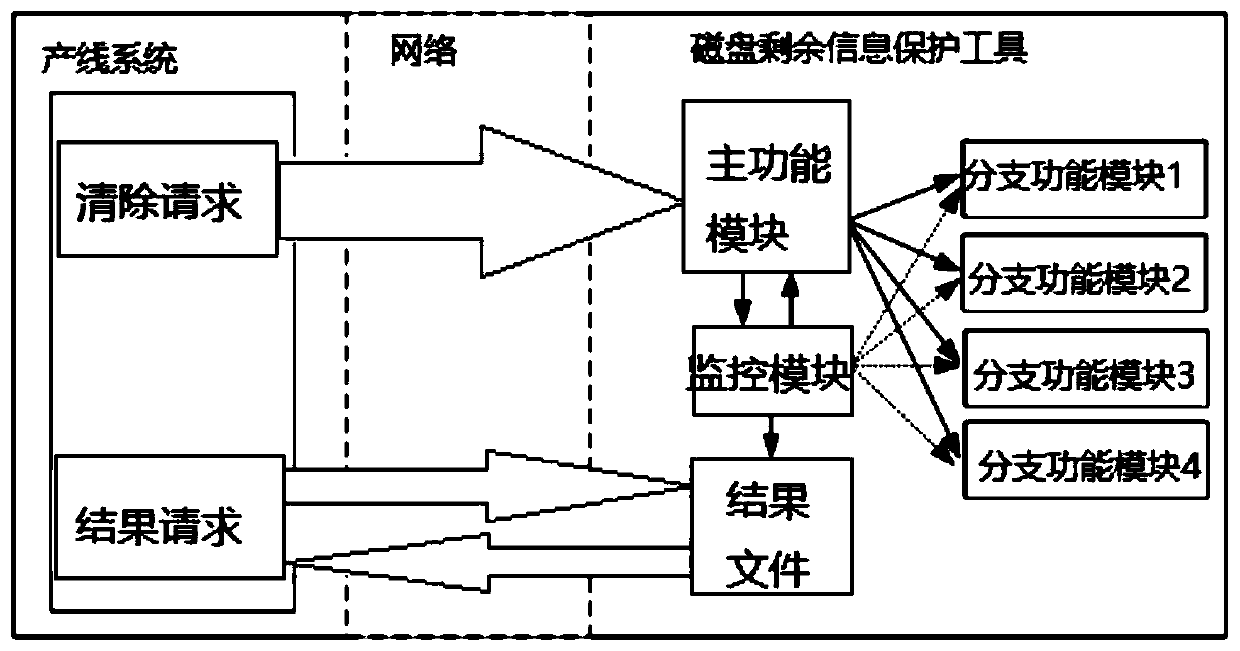
Method and tool for safely clearing residual information of disk and production line system clearing method
InactiveCN111368348AAvoid accidental deletionSafe removalInternal/peripheral component protectionMessage queueProduction line
The invention provides a method and a tool for safely clearing residual information of a disk and a production line system clearing method. The method for securely clearing the residual information ofthe disk comprises the following steps of: receiving a request instruction for clearing residual information of a disk, scanning a directory and files to be subjected to thorough clearing operation in the file system, comparing a scanning result with the protected file list, and creating a to-be-cleared work task and a message queue when it is detected that no file in the scanning result exists in the protected file list; wherein the message queue is used for loading scanned file information; according to the created clearing work task, executing a thorough clearing operation on the directoryand the file; and performing statistical analysis on the clearing result and creating a result file.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
A multi-granularity access control method in big data environment
ActiveCN107370604BSecure AccessMeet diverse access needsUser identity/authority verificationDigital data protectionThree levelCiphertext
Owner:HUAZHONG UNIV OF SCI & TECH
Protecting sensitive information using a trusted device
InactiveUS9654452B2Protect Sensitive InformationMultiple keys/algorithms usagePublic key for secure communicationInformation processingUser input
Owner:INT BUSINESS MASCH CORP
Encrypted radiation imaging system based on random thickness liquid mask
ActiveCN113466956AAvoid being leakedMeet security inspection requirementsCharacter and pattern recognitionNuclear radiation detectionSecurity checkLiquid state
The invention discloses an encrypted radiation imaging system based on a random thickness liquid mask, which comprises an X-ray source, an object to be detected, a liquid metal mask, a mask internal thickness control array and an X-ray detector. According to the invention, the thickness of the liquid mask is randomly adjusted through the mask internal thickness control array, the X-ray passing through the mask is attenuated randomly, sensitive information carried in X-ray imaging is encrypted, the sensitive information of a to-be-detected object is effectively protected, physical shielding encryption measures are adopted for energy and position information of emitted particles, the proposed security check technology encrypts information carried by the emergent X-rays from the physical field, the risk that privacy information is leaked is avoided, any privacy information of the to-be-checked article is not exposed, whether the to-be-checked article contains contraband articles or not is conveniently confirmed by adopting a template comparison method, and the security check is carried out on the basis of protecting the sensitive information of the checked article.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
System log classification method
ActiveCN108427720BImprove accuracyImprove timelinessNeural architecturesSpecial data processing applicationsFeature vectorData set
The invention provides a method for extracting feature vectors from system logs, a method for constructing a system log classification model and a system log classification method. The method of extracting feature vectors includes: for each category, calculate the semantic similarity between the category keywords and the system log, select some similarities as the feature vector of the system log under this category; combine the feature vectors of the system log under all categories to get the feature vector of the system log. The method of constructing the model utilizes the method described above to extract the feature vector of the training data set and use it as the input of the convolutional neural network to train the model. The system log classification method uses the above method to extract the feature vector of the system log, and obtains the classification result through the model. The invention can realize system log classification with high accuracy and high timeliness.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com