Method and tool for safely clearing residual information of disk and production line system clearing method
A disk and security technology, applied in the field of information security, can solve problems such as information security protection that cannot meet the requirements of remaining information protection, and achieve the effect of reliable design principles, preventing accidental deletion, and highlighting substantive features
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0037] An embodiment of the present invention provides a method for safely clearing remaining information on a disk, including the following steps:
[0038] S11: Receive a request command to clear the remaining disk information, scan the directory and files in the file system that are about to perform a complete clear operation, and compare the scan result with the list of protected files. When it is detected that there is no file in the scan result in the list of protected files When, create to-be-cleared work task and message queue; Wherein, described message queue is used for loading the file information of scanning;
[0039] S12: Perform a thorough clearing operation on directories and files according to the created clearing task;
[0040] S13: Statistically analyze the cleaning results and create a result file.
Embodiment 2
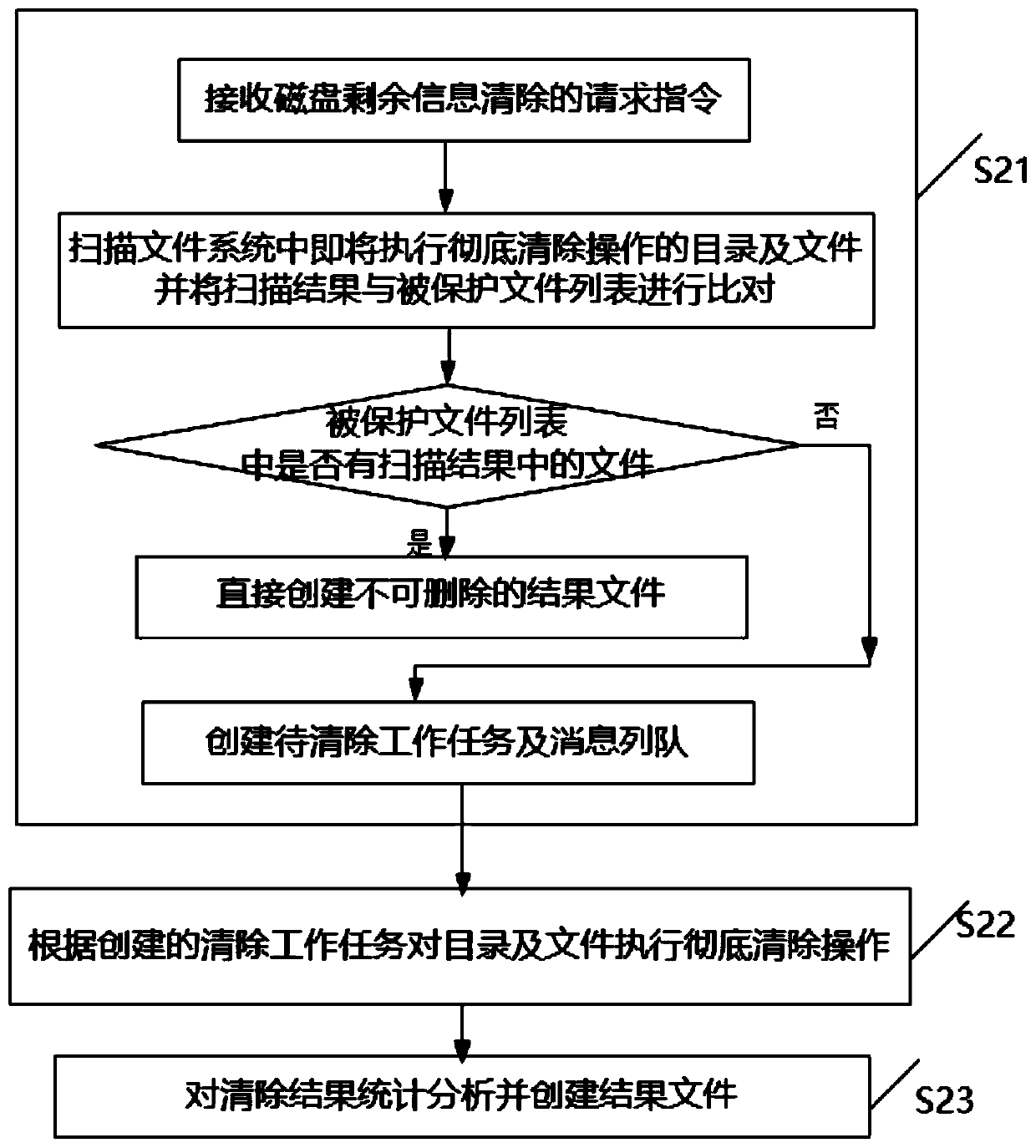
[0042] Such as figure 1 As shown, the embodiment of the present invention provides a method for safely clearing the remaining information on the disk, including the following steps:
[0043] S21: Receive a request instruction for clearing the remaining disk information, scan the directory and files in the file system that are about to perform a thorough clearing operation, and compare the scanning result with the list of protected files. When it is detected that there is no file in the scanning result in the list of protected files When, create task and message queue to be cleared; Wherein, described message queue is used for loading the file information of scanning; When detecting the file in the scanning result in the list of protected files, then directly create the undeletable result file; It should be noted that a list of protected files needs to be created before performing this step;
[0044] S22: Perform a thorough clearing operation on directories and files according...
Embodiment 3
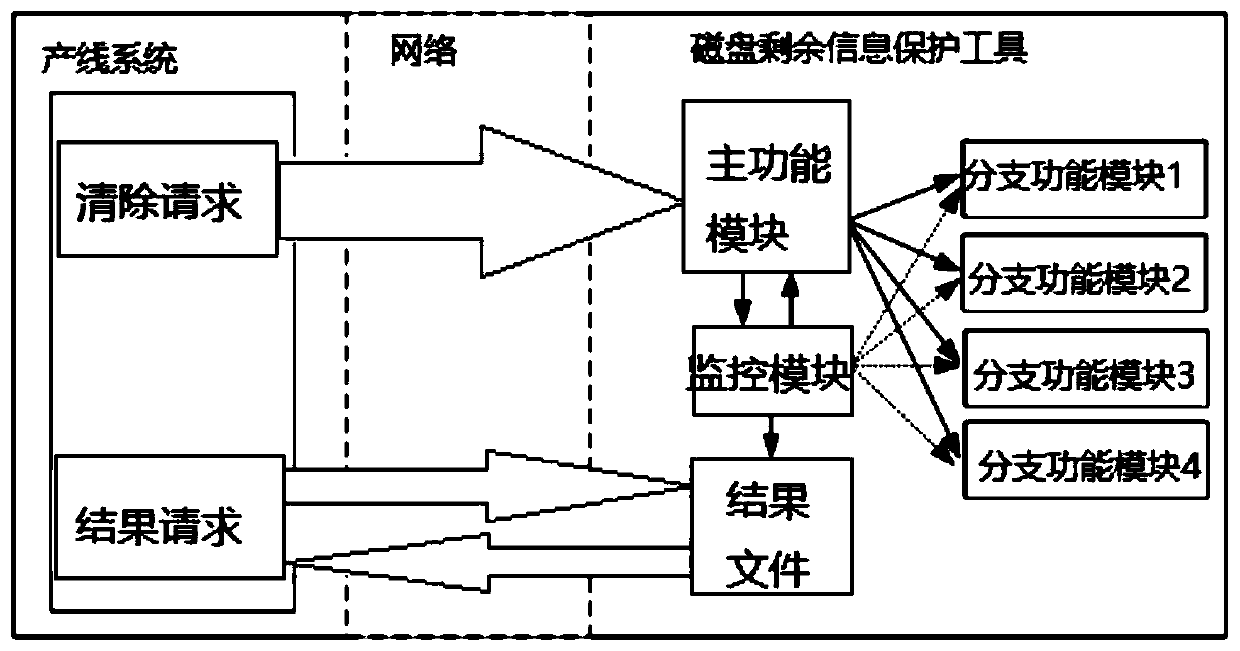
[0048]The technical scheme of the present invention provides a tool for safely clearing the remaining information on the disk. The tool is a tool for safely clearing the remaining information on the disk to prevent important files from being accidentally deleted, and is an executable file program (executable file) deployed on the server. . The main function module, branch function module and monitoring module of the tool. In this embodiment, there are multiple sub-function modules, wherein the main function module and the branch function modules interact through message queuing;
[0049] The main function module is used to receive the request command for clearing the remaining information on the disk, scan the directories and files in the file system that are about to be completely cleared, and compare the scanning results with the list of protected files. When it is detected that there is no scan in the list of protected files When the file in the result, create the task to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com